#totp generator
Explore tagged Tumblr posts
Text
0 notes
Note
hi! i just wanted to say that i am so in love with your kimberly fic. i keep trying to go leave a comment on the most recent chapter (21k!!! you spoil us!!!) but no words seem to do it justice… the way you’ve managed to fully flesh out kim’s character whilst having her remain so true to what we see in the show is just incredible. i’m SO INVESTED in her storyline — i really hope that she gets the happy ending she deserves.
also, getting more of an insight into tim’s life in SF is such a treat. the image of him sat on his fire escape gardening makes me want to cry happy tears. ILY GARDENER TIM 😭😭😭
i can’t wait to see where you take the story and how you decide to wrap it up over the course of the next 2 chapters. thank you for writing such a great story, and an even bigger thank you for choosing to share it with us all! ❤️
OH LOVE!!!!!! thank YOU for your kind words, this ask truly made me smile from ear to ear.
and i am just so flattered that you care for kim as much as i do, because i know she's definitely not the main character of the show by any chance (actually, no one in the show ever calls her kim!! people always refer to her as kimberly, which i did point out during her phone conversation with hawk. it is a very 👀 detail that may or may not come back in perhaps one of the funniest convos in the whole thing- so whenever people refer to her as kim i'm always like 🥺🥺🥺🥺)
AND GARDENER TIM!!!! GOD I WAS HAPPY TO WRITE THAT ONE!!! that's one of the many ideas for the fic i came up with while doing monotonous tasks at work (and i work at a fast food restaurant so. a lot of that) and i am just so happy with that mental image. he truly does have a beautiful life that he built for himself and i will not forget it!!!!!
and just. one thousand million kisses to you, thanks for the ask!!!!
#totp tag;#sorry about the rant about kim's name i know it's unrelated i just think it's soooo fascinating#names in general move around re: the fullers#which is and has always been on purpose!!!!#but yeah the reaslest person is nat who consistently calls kim kimmy even though i never refer to her like that in the fic#she's their little baby girl!! what can i do about that!!!!#talking tag;
3 notes
·
View notes
Note
“She is is envious of the bond Cloud has with Tifa”
Genuine question here because I see a lot of CloTi discourse talk about how Aerith is envious of Cloud and Tifa’s bond, but is this ever mentioned officially or explained? I can’t find one single inference or implication that she is, only that one could argue via subjective interpretation that she maybe wants to try to learn Cloud for who he is and not who he reminds her of.
Arguably, one could say that this interpretation is inherently describing an envy, but I’m looking at it from the perspective of Aerith wanting to learn who Cloud is in an effort to like him for him and not Zack.
(Full disclosure: I’m actually a huge CloTi, but I’ve been out of the fandom for a decade+, and I’ve been reading a lot of discussions on the LTD, and while my personal opinion is that CloTi is more or less canonical at this point, the nuance that they’ve developed with Aerith that just wasn’t there in OG is interesting/perplexing to me because I don’t have a full scope of info. And I like it when things are proven by the devs. It’s possible that there’s information I’m missing or have missed, but otherwise what I have consumed doesn’t seem to indicate she’s envious of Cloud/Tifa’s relationship specifically.)
The idea that Aerith is envious of Cloud and Tifas bond became a thing mostly after Rebirth. Before that it was also put forth at times when someone did a character study of Aerith and the evidence back then was mostly just that it fit and made sense. In essence it was an amateur diagnosis. We saw in Remake that Aerith had unresolved issues concerning her childhood during the Eligor scene, that combined with what we learned about her childhood in TotP made it so that a lot of her outgoing "life affirming" behavior made a lot of sense if she was, in essence, trying to catch up for lost time. She's enthusiastically, perhaps even desperately, trying to have the same experiences everyone else has, to have a normal life. This is also congruent with other parts of the story, like her seeing Zack in Cloud. If Cloud reminds her of Zack, and she had a bond with Zack, then watching Cloud and Tifa express that same young love that she once felt would naturally lead to her wishing she had that. After all, we've known for a long time that Aerith still isn't over Zack, so her being slightly envious of that is natural. And that doesn't have to be a bad thing. You can be happy someone has something and because of that have a positive longing to experience something similar. But where this was really made explicit is in Rebirth, where there are multiple scenes that hint or outright state that Aerith wishes she had something like what Cloud and Tifa have. The main two being the Kalm "date" and the watertower discussion. In Kalm Aerith takes Cloud on a date as a pretense to talk about the prior night, and almost the first thing she does is mention Cloud and Tifas friendship and mention that she'd have given anything to have a friend when she was growing up. As soon as she thinks of their bond her first thought is to link it to her own desires.

She continues by saying to not take Tifa for granted. Since this is something Aerith lacked she thinks it's important, and the idea of it being sullied or undermined instinctively bothers her. She wants them to value it as much as she would value such a thing. This is not her living vicariously through Cloud and Tifa or anything, but just a small nuance that paints the picture of a girl who yearns for these bonds herself enough that she is hyper aware of them with other people. All this is then stated explicitly on the water tower, where Aerith states: "Must be nice..."
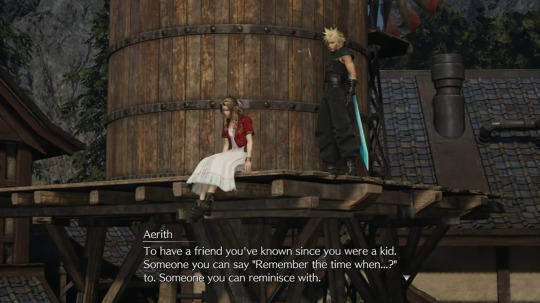

She generally willfully daydreams about how nice Nibelheim is. It all paints the same picture, a girl without a childhood who never got to experience the things that Cloud and Tifa had and lost, but wishes that she did. This is a huge part of her character and establishes the background needed to understand stuff like "no promises to keep". Some people are upset that NPTK is not a love song from Aerith to Cloud, but a deeper look into Aerith shows why it would be weird for it to be one. Because Aeriths journey isn't about romance, it isn't even just about Cloud. It's about her experiencing and developing the bonds that she felt she was denied for so long. The song is "even about Tifa and Barret" because it's about all the precious bonds she made on her journey. It's one of the things that makes Clotis version of Aerith superior to the Clerith version, because we give her so many more layers.
73 notes
·
View notes
Note
Hi. Is there really a scene in ToTP where Claudia and Tifa cook together, or where Claudia teaches her to cook? I haven’t read it but I heard people saying it was a headcanon that was canonised thanks to this novel, but from reading only a few snippets on the net all I could find was a line about the village women in general helping Tifa, not Claudia specifically.


Yup. They're making food for the shinra folks arriving the next day. Claudia isn't teaching Tifa, they're just doing the job together and chatting.
7 notes
·
View notes
Note
i’ve been wondering if in totp we’re going to see more “domestic” moments between eren and yn ? Like them watching movies together, cooking , more dates (like the one at the vineyard) , their anniversaries… just them acting like a cute little couple in general ! :))
YES,, it’s coming yall just be patient with me
3 notes
·
View notes
Note
(Part 1) Hi, I'm the multi-part headcanon asks nonnie. Thanks for the heads-up, and no worries. Ever since I read ToTP, it made think how outdated Nibelheim is when it comes to "traditional" roles when it comes to women and it just went from there, I don't believe there isn't any bigotry in the world. I think you also mentioned something similar in a previous post, too. There's another headcanon (more like an idea?) I forget to share when sending my asks since I didn't wanna spam you. XD
(Part 2) I headcanon that Nibelheim wasn't completely intolerant about homosexuality, it was more "frowned upon" since they just expect men and women to marry settle down and have kids. I'm really enjoying the idea of Cloud, who obviously rejects that way of thinking, being out and proud, and is going to throw hands with anyone who tries to insult him and his partner in the village (or if he runs into villager in Midgar since ToTP confirms that boys leave the village to find work/join the army). (Part 3/End) Honestly, the idea works so much funnier in my head due to my Rufus bias. I love the idea of an AU fic where Rufus and Cloud's relationship is public and they have to grapple with the gossip, harassment, and invasion of their privacy. Cloud is more worried how his mother is going to react, while the whole world, including Nibelheim, is shocked that little boy they all ostracized is the lover of the super hot and hunky and rich heir to the freaking Shinra Electric Power Company! XD
SO, I did acknowledge a chunk of this in your previous asks, so I don't want to be too repetitive. If anyone wants to read my responses to parts 1 & 2 above, click here for the generalized answer.
NOW, speaking of Cloud rejecting Nibel's way of thinking (I love it). There is that moment from Tifa's POV where she has this realization of like...wow, he really doesn't care what anyone thinks and just goes his own way, it's like he's really free. And she respects that, and seems a bit envious of it since she's so burdened by this feeling of trying to please everybody around her. It was so eye opening to me, because your point of view really does matter, doesn't it? It always seems like the ostracized one is lonely, wants to fit in, acts out because he/she does not fit in. But from Tifa's perspective, it was like Cloud had his eye flung so far forward into his future, he couldn't be bothered with the troglodytes of Nibelheim. I don't know if he really feels this way himself...but FUCK if that isn't exactly how I felt as a kid. Nobody around you gives a shit, they all seem spoiled or stupid, there's no hope and no future, so you just protect yourself and wait until you can run as far and as fast as you can in the other direction. Man, that really stuck with me.
Sorry, I know it's a little off topic, but I love it so much. It made me view Cloud a little differently, which is INSANE after all these years. It makes the self-indulgent idea of Cloud being in a relationship with Rufus even more satisfying...he'd have this dislike of his own poor, ignorant roots, but he'd have to balance that with his distaste for the kind of extreme wealth that Rufus represents. Tabloid fodder, for sure. Would Rufus suddenly give a shit about reviving the old R&D reactor sitting atop Mount Nibel...would Cloud even want him to? Would he be embarrassed if Shinra started pumping money into that little backwater town?! These possibilities amuse me...
#stanswers#Anonymous#tysm for these asks#they were really fun to dissect and reflect upon#headcanons#headcanon#rufus shinra#cloud strife#rucloud#strifra#rukura#ruclo
3 notes
·
View notes
Text
Youtube: "Shaggy - Boombastic (TOTP BIG HITS 1995)"
Tumblr
Tumblr notes page
BarSupplies.com "BarConic® Real Coconut Cup - Lacquered" product page
Ohuhu.com: "Ohuhu Honolulu 120 Colors Dual Tips Alcohol Art Marker" product page
Letterboxd: Hook (1991) review by user pd187
Center for an Informed America: The Strange but Mostly True Story of Laurel Canyon and the Birth of the Hippie Generation
Wikispooks.com: "Deep event"
https://pd187.neocities.org/gallery
Letterboxd: Scooby Doo on Zombie Island (1998) review by user pd187
Reddit: r/GlitchInTheMatrix "My tomato glitched and was seedless even though I bought seeded tomatoes"
6 notes
·
View notes
Text
2FA as a tech is fine, good even, the main problem is the centralisation on a relatively frequently stolen and vulnerable device the tech usually doesn't actually need The (phone) App though; you can add TOTP codes to some password managers like KeePassXC for example to generate them on a PC
theres bikes around the city you can rent but you have to use an app that needs your drivers license. theres buses that drive right to your destination, but if you dont have change you need the app. you can wash your car here if you sign into the app. you can go to the bathroom here you just have to unlock it with the app that needs your location on. you can order at this restaurant if you scan the code and download the app. im losing my freaking mind
191K notes
·
View notes
Text
Flipper Zero Unleashed Authenticator – Secure Two-Factor Authentication for Everyone
Flipper Zero Unleashed Authenticator – Secure Two-Factor Authentication for Everyone
The concept of two-factor authentication (2FA) has become essential in protecting our digital identities. Traditionally, apps like Google Authenticator or hardware keys like YubiKey have dominated this space. However, with the ever-growing versatility of Flipper Zero especially when powered by the Unleashed firmware it now offers basic 2FA functionalities through its Authenticator plugin.
This article examines how Flipper Zero Unleashed can be utilized as a two-factor authentication device, its limitations, its comparison to traditional solutions, and its integration into the modern cybersecurity ecosystem.
What Is the Flipper Zero Authenticator?
Flipper zero Secure Two-Factor Authentication for Everyone
is a community-developed feature that enables Flipper Zero to function as a TOTP (Time-Based One-Time Password) generator — the same type used in popular 2FA systems.
This means you can store secret keys (seeded from QR codes or manual input), and your Flipper will generate a rotating six-digit code every 30 seconds. These codes can be used to log into services like:
Google accounts
GitHub
Discord
Facebook
Any platform that supports TOTP
With this functionality, the Flipper Zero essentially acts like a portable hardware authenticator — an appealing choice for privacy-conscious users or those who want to keep authentication separate from their smartphones.
How to Set Up the Flipper Zero Authenticator
Getting started with the Authenticator plugin requires the Unleashed firmware and some setup steps:
1. Install Unleashed Firmware
Download and flash the Unleashed firmware to your Flipper Zero using the Flipper Updater or qFlipper tool.
2. Enable the Authenticator Plugin
This is available in the plugin section of the Unleashed build. Once enabled, it can be accessed directly from the Flipper's main menu.
3. Add Accounts
You can input TOTP secret keys manually or use QR code conversion tools to extract the key and format it correctly for Flipper Zero.
4. Access Codes Anytime
The Flipper will display valid 2FA codes on-screen, synced to system time, similar to how mobile apps like Authy or Google Authenticator function.
Benefits of Using Flipper Zero for 2FA
1. Device Independence
No need to rely on a smartphone or third-party app. This adds a layer of physical separation between your identity and your mobile device.
2. Open-Source Transparency
Since the Unleashed firmware and plugins are open-source, you have complete visibility into how the codes are generated — something not guaranteed with proprietary apps.
3. Offline Access
Your Flipper does not require internet or Bluetooth to generate codes ensuring that even when offline you can access your TOTP tokens.
4. Portable and Pocket-Friendly
It's a compact and all-in-one device that can be used for testing, exploration and now secure authentication.
Limitations and Security Concerns
While it's a functional 2FA tool, there are a few points to keep in mind:
No biometric or PIN lock: If your Flipper is lost or stolen, someone could access your codes unless you've taken additional steps to secure the device.
No sync or backup: Unlike cloud-based apps, there's no built-in backup system. If the Flipper is reset or bricked, you lose your tokens unless you've saved them elsewhere.
Limited UI: Flipper's screen is small and not ideal for managing large numbers of accounts.
This means that while the Flipper Zero Authenticator is great for hobbyists and enthusiasts, it may not be ideal for managing dozens of critical accounts in a professional setting.
Who Should Use It?
The Flipper Zero Authenticator is an excellent option for:
Developers and techies who already use Flipper for other purposes
Privacy advocates who want authentication tools entirely under their control
People who use the Flipper in test environments and want 2FA in a pinch
Users who dislike mobile-based apps for security reasons
Conclusion
Flipper Zero Unleashed continues to prove that it's more than just a hacking gadget. With the addition of an authenticator feature, it now offers a lightweight, flexible, and privacy-respecting alternative to traditional two-factor authentication (2FA) tools.
While it doesn't yet replace high-end solutions like YubiKey for enterprise use, it offers a viable option for users who want a simple, portable, and independent authentication method especially if they're already using Flipper as part of their daily toolkit.
1 note
·
View note
Text
How to Implement Two-Factor Authentication on a Website
These days, securing a website isn’t just a good idea—it’s a must. One of the best ways to add an extra layer of protection is through Two-Factor Authentication, or 2FA for short. If you’ve ever had to enter a code from your phone after typing in your password, you’ve used 2FA.
In simple terms, it’s a method that asks for two pieces of proof to confirm you’re really the person trying to log in. Usually, the first is your password, and the second is something like a code sent to your phone or email. This way, even if someone figures out your password, they still can’t get in without that second step.
Let’s break down how to add 2FA to your website and why it matters.
Why Two-Factor Authentication Matters
Cyber attacks are getting smarter. Passwords alone are no longer enough to keep accounts safe. Many people reuse the same passwords, and hackers often steal them from one site and try them on others. With 2FA, even if your password is leaked, your account still has a strong line of defense.
For website owners—especially those managing user data, online payments, or sensitive details—adding 2FA shows visitors that you take their safety seriously.
Basic Steps to Implement 2FA
Whether your site is built with PHP, Python, JavaScript, or a CMS like WordPress, the process follows the same general flow:
1. User Login with Username and Password
This is the regular login step. The user types in their email or username and their password.
2. Generate and Send the Second Factor
Once the password is correct, the site asks for a second piece of proof. This can be:
A one-time code sent to the user’s email or phone
A time-based code from an app like Google Authenticator
A push notification sent to an app
A hardware key (less common for general users)
Let’s take the example of using Google Authenticator. When users sign up for 2FA, you give them a QR code that they scan with their app. The app then generates new codes every 30 seconds.
3. User Enters the Code
After the code is sent or generated, the user types it in. The website checks if it matches the expected value.
If it’s correct, they’re logged in. If not, access is denied.
4. Add Recovery Options
What if a user loses their phone? You should give them a way to recover their account. This can be through backup codes, a recovery email, or answering security questions.
Tools and Libraries That Help
There are many tools available that make setting up 2FA easier:
Google Authenticator: Common and trusted.
Authy: A user-friendly option with cloud backup.
TOTP Libraries: If you’re coding it yourself, look into Time-based One-Time Password libraries for your language (e.g., pyotp for Python or otplib for JavaScript).
Plugins for CMS platforms: WordPress, Joomla, and others often have ready-made 2FA plugins.
If you’re not sure where to begin or need something polished, the best web design company in Bhubaneswar can help implement secure and user-friendly 2FA solutions suited for your site.
Keep It Simple for Users
Security should never make a site harder to use. A good 2FA system is quick, clear, and supports everyday users. Allow them to choose the method they prefer—text message, authenticator app, or email—and make the setup process easy to follow.
Provide clear instructions and a support option in case they get stuck.
Where to Use 2FA
You don’t have to add 2FA to every part of your site. Focus on:
Admin login areas
User accounts with personal or payment details
Business dashboards
Anything involving data management
Even if your website doesn’t store personal information, protecting your backend from unauthorized access is always a smart move.
Final Thoughts
Adding Two-Factor Authentication is one of the most effective ways to improve website security. It’s not complicated, and the benefits are huge. You protect your users, build trust, and reduce the chances of someone breaking into your system.Whether you're a small business, nonprofit, or running an e-commerce site, you don’t have to do it all alone. The best web design company in Bhubaneswar can guide you through setting up 2FA the right way—so you can focus on growing your site without worrying about security threats.
#performance marketing services bhubaneswar#digital marketing services in bhubaneswar#seo services in bhubaneswar#web development services in bhubaneswar#Integrated Digital Marketing agency#best web design company in bhubaneswar
0 notes
Text
Introducing iShield Key 2: Swissbit's next-generation hardware authenticator
Westford, Massachusetts, USA, May 8, 2025 – Swissbit, a leading manufacturer of storage and security solutions, announces the launch of the iShield Key 2, the next generation of its hardware authenticators. Powered by an NXP chip, the new product family delivers phishing-resistant authentication for enterprises and public sector organizations worldwide, offering a wide range of models and feature sets.

At its core, the iShield Key 2 series is built on the FIDO2 standard, supporting passwordless authentication with market-leading capacity for up to 300 Passkeys. The Pro versions expand functionality to include HOTP and TOTP for generating one-time passwords and PIV for smartcard integration. Setting new standards, the iShield Key 2 MIFARE variant uniquely combines digital and physical access control in a single device. This enables efficient authentication for both IT systems and physical infrastructure such as buildings or secure printing environments. For customers with the highest security requirements, a FIPS 140-3 Level 3 certified version is also available. All models are housed in a compact, lightweight, and rugged industrial-grade casing – engineered and manufactured at Swissbit’s facility in Berlin, Germany.
Comprehensive portfolio, maximum flexibility
At launch, the iShield Key 2 is available with USB-C, with USB-A variants scheduled for release by end of Q2 2025. All models support NFC for contactless use. The portfolio consists of three main lines: iShield Key 2, iShield Key 2 MIFARE, and iShield Key 2 FIPS. Each line is available in a base FIDO2-only version and a Pro version supporting HOTP, TOTP, and PIV. This breadth allows organizations to select the authenticator that best fits their specific requirements and use cases.

Physical access control and beyond
Thanks to NXP’s advanced chip technology, the iShield Key 2 MIFARE supports DESFire EV3, enabling true hybrid usage. This allows the key to integrate seamlessly into daily workflows and support custom applications based on MIFARE technology – ideal for use cases such as time tracking, cafeteria payment, or campus ID cards. Swissbit also offers optional support for leading access control technologies such as HID SEOS and LEGIC advant / LEGIC neon, providing customers with the flexibility to integrate the key into existing systems and infrastructures.
Security and certifications
All iShield Key 2 models are FIDO-certified and support OpenSC for open smartcard integration. For deployments with stringent compliance needs, the FIPS 140-3 Level 3 certified version ensures adherence to top-tier security standards. Variants with Enterprise Attestation are also available, allowing organizations to restrict access to verified, company-issued security keys.
Update Capabilities
All iShield Key 2 models can be remotely updated by using secure channel protocols which allows the provisioning of new firmware versions and applications to devices in the field.
“With the iShield Key 2, we are delivering a universal security key that not only meets the evolving demands of digital identity but also sets new standards for physical access control,” said Claus Gründel, General Manager Security Solutions at Swissbit. “This product line represents a major leap forward in authentication technology and gives our customers maximum flexibility and control across their security infrastructure.”
Swissbit Original Post : link
Swissbit iShield Key website : link
Contac us :
Phone: +55 11 5507-2627
Email: [email protected]
0 notes
Text
Authenticator App Neues Handy: How to Securely Transfer Your 2FA Credentials During a Phone Change
In an era where cybersecurity is a top priority for professionals and organizations alike, authenticator apps have become a fundamental layer of account protection. These apps—such as Google Authenticator, Microsoft Authenticator, or Authy—enable two-factor authentication (2FA) through time-based one-time passcodes (TOTP), making unauthorized access significantly harder.
But what happens when you change your smartphone? Whether you’re upgrading your device or replacing a lost or damaged phone, knowing how to handle your authenticator app neues Handy (authenticator app on a new phone) is critical. For professionals managing multiple secure accounts, a seamless authenticator app Handy Wechsel (authenticator app phone switch) is essential to avoid disruptions or permanent lockouts.
In this guide, we’ll walk you through the steps for transferring your authenticator app to a new phone—both with and without access to the old device—and provide expert-level best practices for handling 2FA credentials during a phone transition.
Why Authenticator Apps Matter
Authenticator apps generate 6-digit codes that refresh every 30 seconds and are used alongside your username and password to access sensitive accounts. They are widely used for:
Enterprise cloud services (Google Workspace, Microsoft 365)
Developer platforms (GitHub, AWS, Azure)
Financial and banking apps
Email and social media accounts
For IT professionals, developers, and digital entrepreneurs, keeping these codes accessible and secure during a phone change is non-negotiable.
Preparing for a Phone Switch: What to Do Beforehand
If you still have access to your old device, it’s always best to prepare before making the switch. A proactive approach simplifies the authenticator app Handy Wechsel process and ensures continuity.
Checklist Before Migrating:
✅ Install the same authenticator app on your new device
✅ Ensure your old device is unlocked and functional
✅ Check if your authenticator app supports export/import (e.g., Google Authenticator does)
✅ Back up recovery codes or store them securely in a password manager
Let’s now dive into the detailed steps.
How to Transfer Authenticator App to Neues Handy (New Phone) – With Access to Old Phone
Step 1: Install Authenticator App on the New Phone
Download your preferred app from the Google Play Store or Apple App Store. Make sure it’s the official version published by the provider (Google LLC, Microsoft Corporation, etc.).
Step 2: Export Accounts From Old Phone
For Google Authenticator:
Open the app on your old phone.
Tap the three-dot menu > Transfer accounts > Export accounts.
Authenticate with your device credentials.
Select the accounts you want to move.
A QR code will be generated.
For Microsoft Authenticator or Authy:
These apps typically offer account synchronization through cloud backup, making the transfer process even easier. Sign in on the new device using the same account credentials to restore your tokens.
Step 3: Import Accounts on Neues Handy
On your new device:
Open the authenticator app.
Choose Import accounts or Scan QR code.
Use the phone camera to scan the QR code generated on your old phone.
After successful import, test one or more logins to verify that 2FA works correctly.
Step 4: Deactivate Old Device
Once confirmed:
Remove or reset the app on the old phone.
Log out or delete tokens to prevent unauthorized use.
Alternatively, perform a factory reset if you are disposing of or selling the old device.
How to Set Up Authenticator App on Neues Handy Without Old Phone
Losing your old phone complicates the authenticator app Handy Wechsel, but it’s still possible to regain access. This process involves recovering individual 2FA-enabled accounts and re-enabling the authenticator manually.
Step 1: Install Authenticator App on New Phone
Choose and install the same authenticator app you used previously (Google Authenticator, Authy, etc.).
Step 2: Recover Each Account
For each service where you’ve enabled 2FA:
Go to the login page and click “Can’t access your 2FA device?” or a similar option.
Use backup recovery codes (if previously saved) to log in.
If no backup codes are available, follow the account recovery process (usually email or identity verification).
Once logged in, disable 2FA, then re-enable it by scanning a new QR code using the authenticator app on your new phone.
💡 Pro tip: Prioritize access to critical accounts like your primary email, password manager, and cloud service logins first.
What If You Used Authy or Microsoft Authenticator?
Some apps offer cloud-based sync, making authenticator app Handy Wechsel far more seamless.
Authy allows account sync across multiple devices (with PIN or biometric protection).
Microsoft Authenticator can back up to iCloud (iOS) or your Microsoft account (Android).
If you previously enabled cloud backup:
Log in on your new phone using the same credentials.
Restore your token list automatically.
Best Practices for Professionals Handling Authenticator App Migration
Changing devices should never compromise your security posture. Here are expert recommendations for managing the authenticator app neues Handy process efficiently:
1. Use a Password Manager
Many password managers (like 1Password, Bitwarden, and LastPass) now support integrated 2FA tokens, allowing secure storage and syncing of TOTP codes.
2. Save Backup Codes Offline
When enabling 2FA for any service, you're usually offered backup or recovery codes. Save these in an encrypted file or secure offline location. Never store them in plain text on cloud services.
3. Regularly Audit 2FA Accounts
Periodically:
Remove unused tokens
Update recovery information (email/phone)
Verify access to backup codes
This helps reduce risks during device transitions.
4. Avoid Using One Phone for All Authentication
For added security, professionals often use a dedicated device (e.g., a secure tablet or secondary phone) solely for 2FA apps.
Common Pitfalls to Avoid
❌ Failing to back up recovery codes before device reset
❌ Not verifying all logins after transfer
❌ Using third-party apps with poor security reputations
❌ Relying on SMS-based 2FA only (which is less secure than app-based)
Avoiding these mistakes can make the authenticator app Handy Wechsel much smoother.
Conclusion
For professionals and security-conscious users, changing smartphones is more than a simple upgrade—it’s a sensitive process that requires safeguarding access to critical accounts. Whether you're planning ahead or recovering from the loss of your old phone, understanding how to manage your authenticator app neues Handy setup ensures that you maintain full control of your digital footprint.
From exporting tokens and using secure backups to recovering access without your previous device, the strategies covered here can help make your authenticator app Handy Wechsel as seamless and secure as possible.
0 notes
Note
hi, hope you are doing well. I noticed you are very well versed in the lore of ffvii, and I wanted to ask about Tifa, in rebirth she comment on how she always felt the need to be liked, and generally behaved in a way that pleases others. in other words internalize what she really think and feel and put on an act that suit the expectations of the other person. when she reveal that in nibelhime I thought yeah thats what we have seen from her thus far, but usually, at least in my knowledge people pleasing behavior come from low self esteem? What could have happened in child tifa’s life to cause her that supposed low self esteem? low self esteem can also manifest in perfectionism, and becoming an over achiever too, which we see highlighted in costa del sol. She was loved by her dad as far as i know? I probably don’t have all the infos here so im asking you, but also I might have completely misread her character
Societal expectations and internalised misogyny and sexism are to blame for her lack of self esteem. She grew up in a very repressed village where women go from their parents homes to their husbands and have no job besides being a wife and homemaker.
Tifa has higher aspirations and she feels pressure to repress that and conform to how the village expects her to behave. That makes her angry, which we see in ToTP when she gets letters and declarations about how she'll be saved by the boys and they'll take care of her like she isn't capable.
So part of her knows she's better than what she has, but she's been taught that's a bad thing, which makes her a bad person and a bad daughter. And that results in her modifying her behaviour to please others and keep her true thoughts and feelings to herself so people don't hate her, even though she's genuinely kind and thoughtful and there's no reason for anyone to hate her.
Tifa's psychology as a character is really interesting, grounded and relatable ❤️
30 notes
·
View notes
Text
Subverting Google Authenticator
Moral status: ecru hat.
Goal: Remove a critical dependency on the founder's phone
Say you have a lovely startup -- @startup.com, seed round, such unicorn -- where you've acquired a bunch of customers and more every day. They want you(r business) to act as a specific entity within their business, so they each give you access to a semishared google account: [email protected], [email protected], [email protected] . Maybe it's just you, maybe a bunch of their employees use it too as a shared entity.
Mandatory Multifactor Auth is here.
Your business now has an existential dependency on your CTO's cellphone & installed authenticator app. Yes, you can (, should, did) extract rescue OTPs. Yes, you always can go shamefacedly to your customers and beg them to beg IT to restore service.
But the phone is going to fall in a lake. It has so much criticality to your business, the dark side is gathering. You can hear it calling now: "bus number of 1", it croaks. Wouldn't it be nice if you could manage the account the customer gave you in a way consonant with its actual delegation of privileges?

from Imgflip Meme Generator
You can.
The hack: Extract the secrets from authenticator, put them in a safe location, and access them (more) programmatically
Environment: M1/Sonoma.
0. Ensure you are not currently under cyberattack
Also, burn some sage, scatter salt, etc. This is about to earn you some bad security karma.
1. Setup:
$ brew install oath-toolkit $ brew install protobuf $ brew install trurl
2. Exfil a secret from authenticator onto your laptop in encoded form
Go into your android "Authenticator" app and select one of your secrets to exfil.
Screenshot the export screen.
Paste the image into a new (, private) keep note.
Load that note on a second screen.
Use your phone's camera app to scan the QR code. Don't click it! Long press and copy it. Go back to the same Keep note. Paste the text there, it will be a URL like otpauth-migration://offline?data=C...%3D . This is the secret, but it's wrapped up in layers of encoding.
3. Dump the pb to extract the actual innermost secret
$ echo "otpauth-migration://offline?data=C...%3D" | trurl -f - --get '{query:data}' > /tmp/otpauthmigration.txt
This is the protobuf encoded in base64 (un-url decoded tho'). It turns out they've changed formats at some point, because there exists code & documentation on the format, but it's wrong. We want path 1.1 (a repeated secret descriptor's field 1, its actual raw secret).
$ printf $(cat /tmp/otpauthmigration.txt | base64 -d | protoc --decode_raw | sed -rn 's/ 1: "(.*)"/\1/p') | base32
This is the actual payload of the single secret you exported in step 2 encoded in base32 right there in your terminal history. (funny edit: tumblr elided the backticks from that command... Fixed now!)
Stick this in 1password, it's the thing you need going forward. Call it $SECRET.
From now on, you can
$ oathtool -v --totp -b $SECRET
and get the same result as the app, from any device (check!)
Closing remarks
Don't do this.
If you were to do this, you could no longer repudiate actions the user's account took. Is your security good enough that you can afford to smudge the actor model around like this? Isn't it easier to just pin your hopes and dreams to the survival of a single hardware device, or reengage with customers whenever anything goes wrong?
0 notes
Text
Monthly Music Diary #1
A project for myself, so I can remember the music I enjoy.
I've been on a Howard Jones kick for a few months now, but from the Howard Jones kick I've ventured into Nik Kershaw, Ultravox, Gary Numan, Simple Minds...I could go on.
I'm fully aware that my current interest in new wave is really credited to Goose, because she's introduced me to things I hadn't quite ventured into before.
So for my first Monthly Music Diary I'm looking at my January playlist - I make a playlist for every month and have been for...six years? Seven? I need to go back - there are months I didn't do it, as well. I also have been writing down all the full albums I've been listening to over the last few weeks as well.
Which is half the reason I made this tumblr for myself, because I wanted something I can go back and read.
Nik Kershaw - Radio Musicola
I was having a little Nik phase before Christmas, which resulted in me trying to argue to people that The Riddle counts as a Christmas song. I mean, obsession with lights, general temporal confusion, references to wise men...it's all there.
So I listened to Radio Musicola, and now am obsessed with it and genuinely have listened to the actual Radio Musicola single every day since.
Of course, I've also been enjoying this performance:
youtube
I love everything about it.
--
Hall and Oates - Private Eyes
I've been kind of a Hall and Oates fan for a while, insomuch as I've always been a big fan of I Can't Go For That and Private Eyes as songs. So bearing that in mind I listened to the whole album, and quickly had Your Imagination on repeat.
The whole thing is kind of also related to Howard Jones, because he went on Darryl Hall's show and they did a cover of What Is Love together, and it was cute.
Also this Your Imagination performance is just...Darryl Hall really is a hugely talented vocalist. Somehow everything about this is the most 1980s thing ever.
youtube
--
Ultravox - Vienna
So I don't actually super care for the song Vienna. I can see why people like it, and I don't skip it when it comes on, but my favourite tracks off the Vienna album are All Stood Still and Mr X. There's something about Mr X that feels kind of similar to Gorillaz to me? Idk I think the soft speech in it sounds like Damon Albarn.
Also clearly this album had an impact on me because I started calling my favourite pigeon who visits the garden "Pijj (Pidge) Ure". I always know it's him because he's extra chonky and has a slight limp, plus he likes to get IN the ground feeder in a way the other pigeons don't seem to do. I love him.
--
Scritti Politti - Cupid & Psyche 85
This album isn't perfect, but for how much I like some of the tracks on it, it might as well be. This one wasn't new to me, but I do keep going back. Favourites are Hypnotize and Wood Beez, which I got into because for some reason the music Co-op plays on its in-store radio is extremely tasty?? Last time they went in they were playing my fave Kate Bush song...really just excellent choices all round.
--
Howard Jones - The 12" album
Everyday I listen to Howard, and I'm really not joking. If I don't listen to Like To Get To Know You Well at least once per day, it's a bad day. But also looking for performances led me to this absolutely mad episode of TOTP where for some reason Howard Jones is performing LTGTKYW on Platform 3 at Bristol Temple Meads????
youtube
This is so fucking funny for some reason. Also I've noticed that in performances where he doesn't get to sing live, Howard is always chewing gum.
--
Opeth - Last Will & Testament / Sorceress / Heritage
Opeth are my favourite band, and I got a copy of Last Will & Testament on vinyl for Christmas. I took a while to listen to it, because I was worried I wouldn't love it as much as I love some of their older stuff - I don't love their super early albums, because I'm not really a big death metal fan. I'm much more a fan of them when they got more folky and really leaned into the prog angle.
But, Last Will And Testament was great, and half the tracks made it onto my Jan playlist. Which is good, because I'm seeing Opeth later this month and now I know I'll definitely enjoy it.
But, this led to me listening to two of my top three Opeth albums - Sorceress, the first album of theirs I ever listened to, and Heritage, which isn't my top Opeth album but the one I consider their best. I'm really not a fan of Steven Wilson's music, but I really can't fault the man as a producer.
--
Paper Rival - Paper Rival
This band stopped existing extremely suddenly just after they dropped their second album, and I was obsessed with their first when I was a teenager. A Fox In The Garden was my favourite 'I'm so sad and i need something sad to listen to' track when I was about 15 years old, and I still have a physical copy of this CD in storage somewhere.
It just felt really comforting to listen to.
--
Elliott Smith - Either/Or
I'm a big Elliott fan, but when I listen to him I mostly listen to his self-titled album (the one with Christian Brothers, St Ides Heaven etc on it) and hadn't listened to this one in forever. I loved it, of course. I will never not be sad that he isn't still here, making music. Hope you're resting well, Elliott.
--
Simon & Garfunkel - Bridge Over Troubled Water
I come back to this album every now and then, but it's another one where I think half of it is perfect and half of it is massively skippable. I did also find myself going The Legend Of Zelda: Bridge Over Troubled Water when I realised the acronym for this album is also BOTW. Of course, that's mostly because I'm still in the middle of replaying Tears of the Kingdom.
--
Daft Punk - Discovery
Now THIS is an album that is no skips. Even if, admittedly, I don't care for One More Time, but mostly that's because I heard it over and over and over and over on TV when I was about 7 years old. I have loved this album for what feels like my whole life, and I consider Something About Us to be a perfect song.
--
Inhaler - Open Wide
I went in not knowing what to expect, honestly. The firsy few tracks kind of felt like generic jangly indie, but then as I got further through it, the quality just got better and better and better. I'm gonna be thinking about this band for a while.
--
Simple Minds - New Gold Dream 81/82/83/84
Half of the tracks from this album got added to my current monthly playlist, but Promised You A Miracle is the one I feel really stuck on at the moment.
I also love - and this is kind of just something Goose and I talk about - that a lot of stars from the 80s now look like someone's dad at this point in their lives. I think it's really sweet that Jim Kerr from Simple Minds looked like someone's dad in 1985. Genuinely adorable.
youtube
--
Malice Mizer - Merveilles
I must have been listening to Gackt again recently, because the YouTube algorithm suddenly gave me a load of Malice Mizer live videos from the Merveilles album tour. I wasn't quite sure what to think, because my forays into J-Pop haven't extended that far, and there's only been one visual kei group I've been sorted of interested in before this point. Even then, it was mostly because they had a song that was a Bleach opening/closing theme.
ANYWAY, after realising that this album is just not on Spotify at all, I managed to find it on YouTube. I was working until 7pm the week I found it, and it was really good at giving me the energy to keep going. I really enjoy Illuminaty particularly - the live of it is so fucking extra. The use of the whip crack as percussion is also just so??? Idk it scratches my brain just right.
youtube
--
I have a ton of stuff on my To Listen radar right now, but right now I'm checking out a lot of new stuff for writing/review purposes. That's it for now.
xo Ells
#Youtube#Howard Jones#Ultravox#Scritti Politti#Hall & Oates#Darryl Hall#Daft Punk#Inhaler#Paul Simon#Art Garfunkel#Malice Mizer#Gackt#Merveilles#Simple Minds#Elliott Smith#Monthly Music Diary#Paper Rival#Opeth#Nik Kershaw#Private Eyes#Readio Musicola#Either/Or#Discovery#The Last Will and Testament#Heritage#Sorceress
0 notes
Text
The Importance of Using Google Authenticator for Enhanced Security
In an era where cyber threats are growing at an unprecedented rate, securing online accounts has never been more critical. Passwords alone are no longer sufficient to safeguard personal and business data. Cybercriminals employ increasingly sophisticated techniques to breach security barriers, leading to financial loss, identity theft, and data breaches. One of the most effective solutions to counter these threats is two-factor authentication (2FA), and Google Authenticator stands out as a highly reliable tool in this domain.
Understanding Two-Factor Authentication (2FA)
Two-factor authentication (2FA) is a security process that requires users to provide two different forms of identification before gaining access to an account. Traditionally, logging in only required a username and password. However, this method is vulnerable to hacking, phishing, and credential theft.
With 2FA, even if an attacker acquires your password, they would still need the second form of authentication, typically a time-sensitive code generated by an authentication app like Google Authenticator. This extra layer of security significantly reduces the risk of unauthorized access.
What is Google Authenticator?
Google Authenticator is a free mobile application developed by Google that generates time-based one-time passwords (TOTP) for 2FA. When enabled for an account, it provides an additional layer of protection by requiring users to enter a code from the app alongside their regular password. The app does not require an internet connection to function and works on both Android and iOS devices.
How Google Authenticator Works
Enabling Google Authenticator – Users must first enable two-factor authentication on their online accounts and select Google Authenticator as their authentication method.
Scanning QR Code – A QR code is provided by the website or service, which the user scans using the Google Authenticator app.
Code Generation – The app then generates a six-digit TOTP every 30 seconds.
Verification – To complete the authentication process, users enter the displayed code within the timeframe.
Each time a user logs in, they will need to enter a new code from the Google Authenticator app, ensuring security even if their password is compromised.
Why is Google Authenticator Important?
1. Enhanced Security Against Cyber Threats
Google Authenticator provides a significant security upgrade compared to relying solely on passwords. Passwords can be easily stolen through phishing attacks, keyloggers, or data breaches. However, the dynamic and time-sensitive nature of authentication codes generated by Google Authenticator makes it nearly impossible for cybercriminals to gain unauthorized access.
2. Protection Against Phishing Attacks
Phishing is one of the most common methods used by hackers to steal login credentials. Even if a user mistakenly provides their password to a fake website, the attacker would still need the authentication code to gain access. Since the code is constantly changing, it adds a robust defense against phishing attempts.
3. Offline Functionality
Unlike SMS-based 2FA, which requires network connectivity, Google Authenticator works entirely offline. This eliminates risks associated with SIM swapping attacks, where hackers hijack a victim’s phone number to intercept authentication codes sent via SMS.
4. Faster and More Secure than SMS Authentication
Many services offer SMS-based authentication as a second factor, but this method has vulnerabilities. SMS codes can be intercepted, delayed, or redirected by hackers. Google Authenticator generates unique codes on your device, making it a faster and more secure option.
5. Wide Adoption and Compatibility
Google Authenticator is compatible with a vast range of services, including email accounts, social media platforms, banking applications, and cloud storage services. Major platforms such as Google, Facebook, Instagram, Twitter, Amazon, and Dropbox support Google Authenticator, making it a versatile and reliable tool for securing multiple accounts.
6. Simple and Convenient to Use
Once set up, Google Authenticator is simple to use. The codes are generated automatically, requiring no extra effort beyond opening the app and entering the displayed code when prompted. The app’s straightforward interface makes it user-friendly, even for those who are not tech-savvy.
Potential Drawbacks and How to Overcome Them
While Google Authenticator offers significant advantages, there are some challenges users may face:
1. Device Loss or Change
If a user loses their phone or switches to a new device, recovering Google Authenticator codes can be challenging. To mitigate this, users should:
Save backup codes provided during the initial setup.
Use Google’s built-in account recovery options.
Utilize a backup authentication app that supports cloud synchronization, such as Authy.
2. No Cloud Backup
Google Authenticator does not offer cloud-based backup, which means that users must manually transfer their accounts when switching devices. Some authentication apps like Authy offer cloud backup, but for maximum security, keeping codes stored locally remains a safer option.
3. One-Time Setup Complexity
For users unfamiliar with 2FA, setting up Google Authenticator for multiple accounts can feel cumbersome. However, most online services provide step-by-step guides to simplify the process.
How to Set Up Google Authenticator
To enable Google Authenticator on an account, follow these steps:
Download the Google Authenticator App from the Google Play Store (Android) or App Store (iOS).
Enable 2FA on the online service you wish to protect (e.g., Gmail, Facebook, Amazon, etc.).
Choose Google Authenticator as the preferred authentication method.
Scan the QR Code provided by the service using the Google Authenticator app.
Enter the Verification Code displayed in the app to confirm setup.
Save Backup Codes in case you lose access to your authenticator.
Conclusion
With cyber threats escalating daily, using only a password to protect online accounts is no longer sufficient. Google Authenticator is a highly effective tool that adds a critical layer of security through two-factor authentication. It protects against phishing, SIM swapping, and brute-force attacks while offering a simple, offline, and widely supported security solution. By integrating Google Authenticator into your security practices, you can significantly enhance the protection of your digital identity, financial data, and personal information.
Cybersecurity is a shared responsibility, and taking proactive steps like using Google Authenticator ensures that you remain one step ahead of cybercriminals. If you haven’t already enabled 2FA, now is the time to strengthen your security and safeguard your online presence.
#gst software#spine software#billing software#pharma#accounting software#distributor#industry#erp#india#software
0 notes