#vlan trunking protocol (protocol)
Explore tagged Tumblr posts
Text
Vlan Trunking Protocol namıdiğer VTP - DELT BİLGİ
Merhaba, network alanlarında internette bulamayacağınız, kısa ve öz bilgileri (delt- bilgi ; bizim tabirimizle )sunmaya devam ediyoruz. Daha öncesinde Dinamik routing nedir konusundan bahsetmiştik. Şimdi ise vtp protokolünü kısa ve basit bir şekilde anlat
Merhaba, network alanlarında internette bulamayacağınız, kısa ve öz bilgileri (delt- bilgi ; bizim tabirimizle )sunmaya devam ediyoruz. Daha öncesinde Dinamik routing nedir konusundan bahsetmiştik. Şimdi ise vtp protokolünü kısa ve basit bir şekilde anlatalım. Vtp protokolü basitçe tanımlayacak olursak switch’lerdeki vlan senkronizasyonunu sağlar. 50 tane switch’iniz var diyelim ve yeni bir vlan…

View On WordPress
0 notes
Text
The primary objective for the newly designed network is to minimize or prevent MAC layer attacks, Virtual LAN attacks, Spoofing attacks, securing network switches and configuring Virtual LAN across the network. For providing security mechanism to the internal data communication, Virtual local area networks (VLAN) are recommended. The VLAN separates the domain of the departments within the organization. VLAN uses encryption techniques for transmitting data over the network. Access policy list is also configured in the VLAN for defining the routes. Moreover, VLAN is considered as a broadcast domain. It concludes that the broadcast generates from one computer can only be received to the destination which is defined by some criteria in the broadcast domain. The advantage of VLAN implementation includes an efficient way of bandwidth utilization and eliminating the network from possible broadcast storms, which results in denial of service. Furthermore, by implementing VLANs, the capacity of switching technology is utilized to its full potential. VLAN also supports ‘VLAN trunking protocol’. The ‘VLAN trunking protocol’ will significantly reduce administration for the switched network. Addressing Security Issues and Deployment Approach for WAN A router is a core computing and packet processing devices in the Bigswitch computer network. Router connects two or more networks with different subnets, enabling the networks to expand on an enterprise level. Logically the router builds a routing table, where it stores all the route addresses. For example, the data packet source and destination is stored in the routing table. The network administrator can statically define the network addresses which are called as ‘static routes’. The dynamic routing protocol is used for the automation of exchanging data packets with other routers located in campuses of Bigswitch. The selection criterion of the router depends on the network requirements. The data transmission gauge, which is also called the maximum transmission unit (MTU), Read the full article
0 notes
Text
CCNA Course - Day 19 | VLAN Trunking Protocol | VTP Modes | Server, Transparent and Client mode
youtube
#ping#internetworkingdevices#Switch#ICMP#datalinklayer#framing#mac#macaddress#hub#bridge#collision#Applicationlayer#networklayer#icmp#ccna#ccnacourse#ccnaclasses#ccnatraining#ccna200301#ccnaonline#routing#switches#switching#router#routingprotocols#vlan#trunking#dtp#stp#Spanningtree
0 notes
Text
End-to-End and Local VLANs
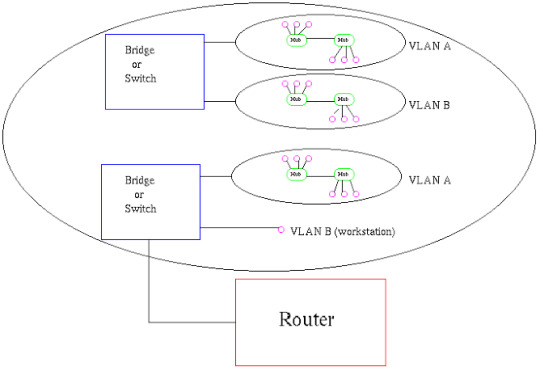
There are two models in which you can design VLANs on a network: - End-to-End - Local End-to-End End-to-End VLANs span across multiple switches within the network. Regardless of the user's physical location, they will consistently be assigned to the same VLAN. Consequently, the user's resources will belong to the same subnet. Management of end-to-end VLANs often involves utilizing VTP through trunked switches, facilitating streamlined management processes. However, reliance on VTP can sometimes lead to complications. Moreover, by extending the VLAN across the network, you enable broadcasts to traverse multiple switches. While this model may be suitable for small implementations, it may not scale effectively for larger environments. Local VLANs are confined to individual switches, typically organized according to geographic location. If a user relocates, they will be assigned to a different VLAN. Under the Local VLAN model, the local switch connects to a distribution or core switch, where routing takes place. Local VLANs exist solely between the local switch and the distribution or core switch. To communicate with other networks, traffic travels from the local VLAN to the distribution/core switch and is then routed to its destination. In this setup, VTP (VLAN Trunking Protocol) is not configured, and switches operate in VTP Transparent mode. Since VLANs are not broadcasted to other switches in the network, VTP becomes unnecessary. One advantage of this model is the elimination of extended layer 2 broadcast domains throughout the network. Troubleshooting is simplified compared to end-to-end VLANs, as traffic follows a defined path. In contrast, end-to-end VLAN traffic traverses multiple switches. Read the full article
0 notes
Text
JL684A | Aruba 24G Class4 PoE 4SFP/SFP+ 370W Switch giá tốt
Switch Aruba Instant On 1930 24G Class 4 PoE 370W JL684A là mẫu switch của Aruba được thiết kế cho doanh nghiệp vừa và nhỏ. Switch sử dụng chipset Broadcom Trident2 plus cho hiệu năng cao, hỗ trợ tốc độ cổng lên tới 25GbE sẽ đáp ứng nhu cầu phát triển lâu dài.
Switch Aruba 1930 có 24 cổng 10/100/1000Base-T RJ45 và 4 cổng SFP/SFP+. Công nghệ PoE+ tích hợp trên tất cả các cổng RJ45 cho phép cung cấp nguồn DC cho các thiết bị đầu cuối như access point, camera, VoIP, triển khai hạ tầng cảm biến một cách dễ dàng. Tổng công suất PoE toàn bộ là 370W nên đáp ứng được nhiều nhu cầu triển khai hơn.
Switch Aruba 1930 hỗ trợ các chức năng L2 cơ bản như VLAN, Trunking, Spanning Tree Protocol, bảo mật 802.1x, QoS và các tính năng quản lý tiên tiến. Các chức năng này giúp quản lý, bảo mật và tối ưu hóa hiệu năng mạng. 🔋Switch được trang bị RAM 4GB cùng bộ nhớ trong 32GB giúp tải nhiều bản cấu hình hơn và hỗ trợ tốt cho việc triển khai mạ
https://sss.net.vn/thiet-bi-chuyen-mach-aruba-1930-jl684a

0 notes
Text
Mastering VTP Configuration: A Step-by-Step Guide by IPCisco

In the world of networking, efficient management of VLANs (Virtual LANs) is crucial for maintaining an organized and scalable network infrastructure. IPCisco, your trusted source for networking insights, is here to guide you through the intricacies of VTP (VLAN Trunking Protocol) configuration, ensuring you can effortlessly manage VLANs within your network.
Understanding VTP Configuration
Before we delve into the practical aspects, let's establish a clear understanding of the key components:
VTP (VLAN Trunking Protocol): VTP is a Cisco proprietary protocol used for managing VLAN configurations across a network. It simplifies the process of creating, deleting, and modifying VLANs.
Why VTP Configuration Matters
Efficient VTP configuration offers several advantages in network management:
Centralized Control: VTP allows network administrators to control VLAN configurations from a central point, simplifying network-wide changes.
Consistency: It ensures consistency in VLAN configurations across all network switches, reducing the likelihood of configuration errors.
Scalability: VTP streamlines the addition of new switches and VLANs to the network, making it suitable for networks of all sizes.
Configuring VTP with IPCisco
At IPCisco, we offer comprehensive guidance on configuring VTP. Here's how we can assist you:
Step-by-Step Tutorials: Our detailed tutorials provide step-by-step instructions for configuring VTP on Cisco switches, ensuring you understand the configuration process thoroughly.
Real-world Scenarios: We provide practical use cases and examples to illustrate how VTP simplifies VLAN management in actual networking scenarios.
Community Interaction: Join the IPCisco community to connect with networking enthusiasts, share knowledge, and seek guidance on VTP configuration and other networking topics.
Conclusion
Mastering VTP configuration is essential for network administrators and engineers, as it streamlines VLAN management and ensures network consistency. Whether you're managing a small or large network, VTP simplifies the process of handling VLANs effectively.
Let IPCisco be your guide in configuring VTP. Visit our website today to access comprehensive resources and elevate your networking knowledge.
0 notes
Text
VLAN Trunking Protocol | VTP Domain Name
VLAN Trunking Protocol
VTP is the layer 2 protocol means the data link layer protocol. VTP is the cisco proprietary protocol and this protocol is the protocol that work is to carries the information of the VLAN to all the switches in the domain of VTP. VTP is protocol which is used to create, delete, and modify VLANs and then that propagates to the other switches in the domain of the VTP. So VTP advertisement can be done on the basis of the ISL trunks and 802.1Q.
VTP Prerequisite
Trunk is the prerequisite of the VTP.
VTP domain name should same on all switches.
There should be at least one server in the VTP domain.
If you enable the authentication than it should match.
VTP Modes
There are the three modes of the VTP that play different role in the VTP domain:
Server
Client
Transparent
Server
Server is the mode of the VTP which is used for the creation of the VLAN and this mode is also used for the deletion and the modification of the VLANs. If you create, delete, and modify any VLAN than it propagate to all the switches in the VTP domain. In this mode the configurations are all save in the start-up configuration that is also known as the non volatile random access memory (NVRAM).
Client
Client is the mode of the VTP which is not able for the creation of the VLAN and also not for the deletion and the modification of the VLANs. Clients mode's work is only propagate the configuration to other switches.
Transparent
Transparent is the third mode of the VTP which is also used for the creation of the VLAN and this mode is also used for the deletion and the modification of the VLANs. So the roles of server and transparent are same but there is a big difference that is this mode does not participate in the VTP domain and because of this attitude of the transparent mode it used for the acquiring the privacy and security.
0 notes
Text
What is Trunk Port in Networking
As we learned and understood on Layer-2 Switch users or Ports in the same VLAN can communicate and send data. That is correct and possible if all users are connected on the same Switch. But what if users or Switches are located at other locations, floors, or Buildings. How we will communicate with them in the same VLAN. In this article, we discuss a solution and understand What is Trunk Port in…

View On WordPress
#cisco networking#computer networking#dynamic trunking protocol#dynamic trunking protocol (internet protocol)#networking protocols#networking&039;#trunking#vlan trunking protocol#vlan trunking protocol (protocol)#vtp – the vlan trunking protocol and vlans explained#what is dtp#what is dtp (dynamic trunking protocol)#what is dtp protocol in hindi#what is dynamic trunking protocol#what is dynamic trunking protocol (dtp)?#what is vlan trunking protocol
0 notes
Text
What Can I Do With A Cisco CCNA Certification?
Cisco Certified Network Associates (CCNA) are one of the world's most sought-after network professionals. Having a CCNA certification opens up a wide variety of job opportunities and can lead to higher salaries.

A Cisco CCNA certification is valuable in terms of the potential salary and employment opportunities that result from this certification. MyComputerCareer also offers his CCNA training as part of the Cybersecurity Specialist Curriculum. For more information, please contact us immediately.
This article explains what a CCNA certification is, what it includes, and the skills it teaches. We will also discuss the different positions you can get with a CCNA certificate and the salaries you can earn with this certificate.
What Is The CCNA Certification?
The Cisco Certified Network Associate (CCNA) certification is a well-known computer networking credential. CCNA certification helps entry-level network engineers, professional network engineers, support network engineers, and network administrators learn basic networking concepts.
Over one million CCNA certificates have been distributed to fully certified professionals since Cisco first introduced certificates in 1998. CCNA certifications cover a wide range of networking topics and help prepare learners for future advances in networking technology.
CCNA certification topics include:
OSI model: Physical Layer, Data Link Layer, Network Layer, Transport Layer, and Application Layer
IP routing: static and dynamic routing protocols
IP addressing: Fourth Generation IPv4 (IPv), Internet Control Message Protocol (ICMP), Address Resolution Protocol (ARP), and Cisco IOS
Network security: Firewalls, password security, virtual private networks (VPNs), and intrusion detection systems
VLANs and WLANs: Access Control Lists (ACLs), VLAN Trunking Protocol (VTP), and Cisco Wireless LAN Controller (WLC) IP Services
Routing protocols (OSPF, EIGRP, and RIP): Cisco IOS, Cisco Express Forwarding (CEF), and Cisco Dynamic Multiprotocol Label Switching (DMVPN) WAN
CCNA certification validates many of the skills a network engineer needs. You will also need various soft skills such as communication, problem solving, organization and customer service. CCNA certification also provides network professionals with the information and skills they need to effectively operate Cisco and Microsoft Office suite applications. This certification empowers aspiring and current network engineers to use industry-specific tools in their daily work.
However, please note that Cisco certifications are valid for three years. If the certification expires, the holder may retake her CCNA certification exam, obtain another Associate certification, pass the Core Technology exam, or for renewal she must complete 40 Continuing Education (CE) credit must be obtained.
What IT Jobs Can You Get With a CCNA Certification?
The Cisco Certified Network Associate (CCNA) certification validates a user's knowledge and skills in network administration. Salaries for this degree average about $80,000 per year. Many employees are looking for Cisco certified professionals because of their extensive experience with Cisco routers and switches. Cisco network equipment is used by most of the Fortune 500 companies.
Network administrator: Network administrators are responsible for the day-to-day operation of computer networks. Keep your network running smoothly and resolve any issues that may arise.
System Administrator: System administrators are responsible for the maintenance and operation of computer systems. It installs new software, patches existing software, and performs other tasks to keep your system running smoothly.
Network analyst: Network analysts are responsible for analyzing computer networks and making recommendations to improve their efficiency. They may also be responsible for designing new networks or implementing changes to existing networks.
Network design engineer: Network design engineers are responsible for designing and implementing computer networks. We work with our customers to understand their needs and design networks that meet those needs.
Infrastructure Engineer: Infrastructure engineers are responsible for the physical components of computer networks such as routers, switches, and cables. Install and maintain these components to keep your network running smoothly.
Unified Communications Engineer: Unified Communications Engineers are responsible for designing and implementing unified communications systems. Unified communication systems allow users to communicate across multiple devices such as phones, computers, and tablets.
Solution designer: Solution design engineers are responsible for designing and implementing solutions to problems encountered in computer networks. They work with customers to understand their needs and design solutions that meet those needs.
Cloud Engineer: Cloud engineers are responsible for designing and implementing cloud-based solutions. Cloud-based solutions allow users to access data and applications from anywhere in the world.
Data Center Engineer: Data center engineers are responsible for the operation of data centers. Install and maintain the hardware and software that make up your data center.
Network administrator: Network administrators are responsible for the day-to-day operation of computer networks. Ensure the smooth operation of your network and fix any problems that may arise.
Cloud Architect: Cloud architects are responsible for designing and implementing cloud-based solutions. Cloud-based solutions allow users to access data and applications from anywhere in the world.
VoIP Engineer: VoIP engineers are responsible for designing and implementing Voice over IP (VoIP) solutions. VoIP solutions allow users to communicate using voice and video over the Internet.
Cooperating engineer: Collaboration engineers are responsible for designing and implementing solutions that enable users to collaborate. Collaboration solutions allow users to share data, applications, and files.
Telecom Engineer: Telecommunications engineers are responsible for the design and implementation of telecommunications systems. Telecommunications systems allow users to communicate using voice, video, and data.
Depending on your skills, years of experience, valid qualifications, and other criteria, you may be better suited for one job than another. The Cisco Certified Network Associate (CCNA) is a great place to start for anyone looking to get into networking.
Conclusion
Earning the Cisco Certified Network Associate (CCNA) certification is a great way to start your networking career. A CCNA certification contains a wealth of knowledge that will help you in your career. A CCNA certification can lead to higher salaries and help you find jobs in a variety of occupations. There are a variety of Cisco certifications you can earn, each useful in your career. A CCNA certification is just the beginning of your journey to a successful networking career.
591cert offers a certification program that includes CCNA Certification. If you're interested in becoming a CCNA and growing your IT career, take a free career assessment. We are happy to answer your questions.
2 notes
·
View notes
Text
Standardized Configurations across the Network Replace with DeVry NETW206: Introduction to Switching Submitted Your professor’s nameDate: Current dateStandardized configurations across the networkA Virtual LANs otherwise known as a VLANs which are usually defined within switches, are broadcast domain that control broadcast, multicast, and unicast within a device in layer 2. They are placed on specific ports to restrict access. One VLAN cannot communicate with the other. For them to communicate, a router needs to be installed. A VLAN is important in that it addresses issues of security by restricting access to the sensitive information, it eliminates the need of purchasing additional expensive network equipment, and it also increase the performance of the network by supporting multiple broadcast domain, hence reduces the issues of traffic.The VLANs are going to be defined in our Cisco catalyst 4300-X series switch in the VLAN Trunking Protocal (VTP). After the creation of the VLANs, there is the creation of ports. The VLANs are created using numbers and the numbers are in two ranges for the creation, that is:1-1000 For the Normal Range1025-4096 For the Extended Range,To configure VLAN, the following steps are to be followed:Configuration of the VTP- VTP is a procedure that enables the Cisco switches to maintain the consistency of the database for the purpose of trunking. It facilitates easier administration of the VLANs.Then we create the VLANs- As stated earlier, VLANs are created using numbers. The extended VLANs are presently supported on the switches that run on the COS software edition 6.1 or greater.The creation of the solution template helps in the design of a standard modular network solutions. This solution template handles the issue of all non−standard, non device−specific configuration , for instance VLAN configuration, routing protocols, spanning tree parameters, among others (Lammle, 2011). For achieveing standard hostname, a naming system should be used, e.g the Network Information Systems, Domain Name System, among others. There are three privileges levels in a router:privilege level 1 which is for the non-privileged (prompt is router>), the default level for logging inprivilege level 15 which is for the privileged (prompt is router#), the level after going into enable modeprivilege level 0 which is seldom used, but includes 5 commands: disable, enable, exit, help, and logout. These privileges are assigned with the TACACS+ and the RADIUS servers.The Secure Shell otherwise known as SSH is a secure network protocol for the Cisco devices compared to telnet. Our Cisco switch can be setup to access the SSH by following the steps below:First we configure the hostname command,Configure the DNS domain,Generate the SSH key to be used,Enable SSH transport support for the virtual type terminal (vtys).Ideally, authentication protocols like the RADIUS, LDAP, TACACS+, among others provide a means to verify a legitimate user. Read the full article
0 notes
Photo

Follow us @aiprobably . Yersinia Package Description Yersinia is a framework for performing layer 2 attacks. It is designed to take advantage of some weaknesses in different network protocols. It pretends to be a solid framework for analyzing and testing the deployed networks and systems. Attacks for the following network protocols are implemented in this particular release: Spanning Tree Protocol (STP) Cisco Discovery Protocol (CDP) Dynamic Trunking Protocol (DTP) Dynamic Host Configuration Protocol (DHCP) Hot Standby Router Protocol (HSRP) 802.1q 802.1x Inter-Switch Link Protocol (ISL) VLAN Trunking Protocol (VTP) #hacker #hacking #linux #tech #hack #technology #cybersecurity #python #programmer #computerscience #code #developer #security #computer #software #kalilinux #php #webdeveloper #cyber #ethicalhacking #anonymous #engineer #privacy #ai #geek #google #android #malware #internet #dataprotection https://www.instagram.com/p/Bx4p9csgAnc/?igshid=io5adn3fsxkw
#hacker#hacking#linux#tech#hack#technology#cybersecurity#python#programmer#computerscience#code#developer#security#computer#software#kalilinux#php#webdeveloper#cyber#ethicalhacking#anonymous#engineer#privacy#ai#geek#google#android#malware#internet#dataprotection
11 notes
·
View notes
Text
Cisco CCNA Security 210-260 Certification Exam Details
Cisco 210-260 certifications are globally accepted and add significant value to your IT professional. The certification offers you a serious knowledge of each of the workings with the network models and also the devices that are utilized from it. NWexam.com is proud to offer for you the ideal Cisco Exam Guides.
The Cisco 210-260 Exam is challenging, and thorough preparation is important for achievement. This cert guide was created to enable you to plan the CCNA Security certification exam. Its content has an in depth list of the individuals covered around the Professional exam. The following tips for your IINS might help make suggestions with the study process for the certification.
To have Implementing Cisco Network Security certification, you need to pass IINS 210-260 exam. This exam is produced remembering the input of pros in the market and reveals how Cisco products are found in organizations around the globe. 210-260 Implementing Cisco Network Security Exam Summary
? Exam Name: Implementing Cisco Network Security ? Exam Code: 210-260 ? Exam Price: $300 (USD) ? Duration: 90 mins ? Number of Questions: 60-70 ? Passing Score: Variable (750-850 / 1000 Approx.) 210-260 Exam Guide: ? How I pass Cisco 400-201 Certification in first attempt? ? How to arrange for 400-201 exam on CCIE Supplier Topics covered in the CCNA Security 210-260 Exam [1]. Security Concepts (12%)
1 Common security principles a) Describe confidentiality, integrity, availability (CIA) b) Describe SIEM technology c) Identify common security terms d) Identify common network security zones 2 Common security threats a) Identify common network attacks b) Describe social engineering c) Identify malware d) Classify the vectors of internet data loss/exfiltration 3 Cryptography concepts a) Describe key exchange b) Describe hash algorithm c) Assess symmetric and asymmetric encryption d) Describe digital signatures, certificates, and PKI 4 Describe network topologies a) Campus area network (CAN) b) Cloud, wide area network (WAN) c) Data center d) Small office/home office (SOHO) e) Network to protect an on-line environment
[2]. Secure Access (14%) 1 Secure management a) Compare in-band and out-of band b) Configure secure network management c) Configure and verify secure access through SNMP v3 using an ACL d) Configure and verify security for NTP e) Use SCP for file transfer 2 AAA concepts a) Describe RADIUS and TACACS+ technologies b) Configure administrative access on a Cisco router using TACACS+ c) Verify connectivity on a Cisco router to a TACACS+ server d) Explain the combination of Active Directory with AAA e) Describe authentication and authorization using ACS and ISE 3 802.1X authentication a) Identify the functions 802.1X components 4 BYOD a) Describe the BYOD architecture framework b) Describe the function of mobile phone management (MDM)
[3]. VPN (17%)
1 VPN concepts a) Describe IPsec protocols and delivery modes (IKE, ESP, AH, tunnel mode, transport mode) b) Describe hairpinning, split tunneling, always-on, NAT traversal 2 Remote access VPN a) Implement basic clientless SSL VPN using ASDM b) Verify clientless connection c) Implement basic AnyConnect SSL VPN using ASDM d) Verify AnyConnect connection e) Identify endpoint posture assessment 3 Site-to-site VPN a) Implement an IPsec site-to-site VPN with pre-shared key authentication on Cisco routers and ASA firewalls b) Verify an IPsec site-to-site VPN [4]. Secure Routing and Switching (18%)
1 Security on Cisco routers a) Configure multiple privilege levels b) Configure Cisco IOS role-based CLI access c) Implement Cisco IOS resilient configuration 2 Securing routing protocols a) Implement routing update authentication on OSPF 3 Securing the control plane a) Explain the function of control plane policing 4 Common Layer 2 attacks a) Describe STP attacks b) Describe ARP spoofing c) Describe MAC spoofing d) Describe CAM table (MAC address table) overflows e) Describe CDP/LLDP reconnaissance f) Describe VLAN hopping g) Describe DHCP spoofing 5 Mitigation procedures a) Implement DHCP snooping b) Implement Dynamic ARP Inspection c) Implement port security d) Describe BPDU guard, root guard, loop guard e) Verify mitigation procedures 6 VLAN security a) Describe the protection implications of the PVLAN b) Describe the security implications of your native VLAN

[5]. Cisco Firewall Technologies (18%)
1 Describe operational strengths and weaknesses of the different firewall technologies a) Proxy firewalls b) Application firewall c) Personal firewall 2 Compare stateful vs. stateless firewalls a) Operations b) Function of hawaii table 3 Implement NAT on Cisco ASA 9.x a) Static b) Dynamic c) PAT d) Policy NAT e) Verify NAT operations 4 Implement zone-based firewall a) Zone to zone b) Self zone 5 Firewall features on the Cisco Adaptive Security Appliance (ASA) 9.x a) Configure ASA access management b) Configure security access policies c) Configure Cisco ASA interface security levels d) Configure default Cisco Modular Policy Framework (MPF) e) Describe modes of deployment (routed firewall, transparent firewall) f) Describe types of implementing high availability g) Describe security contexts h) Describe firewall services
[6]. IPS (9%)
1 Describe IPS deployment considerations a) Network-based IPS vs. host-based IPS b) Modes of deployment (inline, promiscuous - SPAN, tap) c) Placement (positioning with the IPS inside the network) d) False positives, false negatives, true positives, true negatives 2 Describe IPS technologies a) Rules/signatures b) Detection/signature engines c) Trigger actions/responses (drop, reset, block, alert, monitor/log, shun) d) Blacklist (static and dynamic) [7]. Content and Endpoint Security (12%)
1 Describe mitigation technology for email-based threats a) SPAM filtering, anti-malware filtering, DLP, blacklisting, email encryption 2 Describe mitigation technology for web-based threats a) Local and cloud-based web proxies b) Blacklisting, URL filtering, malware scanning, URL categorization, web application filtering, TLS/SSL decryption 3 Describe mitigation technology for endpoint threats a) Anti-virus/anti-malware b) Personal firewall/HIPS c) Hardware/software encryption of local data
What type of questions is on the Cisco 210-260 exams? ? Single answer multiple choice ? Multiple answer multiple choice ? Drag and Drop (DND) ? Router Simulation ? Testlet CCNA Security 210-260 Practice Exam Questions. Grab an awareness from these Cisco 210-260 sample questions and boost your 210-260 exam preparation towards attaining an Implementing Cisco Network Security Certification. Answering these sample questions is likely to make informed about the types of questions you can anticipate for the actual exam. Doing practice with CCNA Security IINS questions and answers ahead of the exam wherever possible is the key to passing the Cisco 210-260 certification exam.
210-260 Implementing Cisco Network Security Sample Questions:-
01. Which type of traffic inspection uses pattern matching? a) Signature-based inspection b) Statistical anomaly detection c) Protocol verification d) Policy-based inspection Answer: a
02. Which from the following authentication mechanisms can be used with SNMP version 3? (Choose two) a) AES b) MD5 c) 3DES d) SHA Answer: b, d
03. Is there a most typical type of spoofing? a) Application spoofing b) Service spoofing c) DHCP spoofing d) Ip spoofing e) MAC address spoofing Answer: d 04. Which option mitigates VLAN Hopping and Double-tagging VLAN Hopping Attacks? a) Ensuring that the native VLAN in the trunk ports differs from the native VLAN in the user ports b) Making sure that the native VLAN with the trunk ports is the same as the native VLAN from the user ports c) Setting a corner port to “off.” d) Enabling auto trunking negotiations. Answer: a
05. The kind of attack is prevented if you configure Secure Shell (SSH)? a) DoS session spoofing b) Man-in-the-middle attack c) Dictionary attack d) Buffer overflow Answer: b
06. Which in the following is not part of an IKE Phase 2 process? a) Main mode b) Specifying a hash (HMAC) c) Running DH (PFS) d) Negotiating the transform set to utilize Answer: a
07. What are three key features of URL filtering? (Choose three) a) Predefined URL categories b) Malware protection c) Custom URL categories d) Dynamic content analysis Answer: a, c, d 08. What sort of VPN technologies are apt to be employed in a site-to-site VPN? a) SSL b) TLS c) HTTPS d) IPsec Answer: d
09. Which two statements are true of the present threatscape? (Choose two) a) We now have marketplace is the only industry that is certainly exempt from attack. b) The threat landscape is actually evolving. c) Due to recent improvements in security technology, password attacks not play a significant role in the threatscape. d) It is so complex that it must be impossible to catalog in its entirety. Answer: b, d
10. Which three statements are true about firewalls? (Choose three) a) If your system in a security zone is compromised, a firewall can help offer the attack within that zone. b) A firewall can prevent undesired access to a network security zone. c) Modern firewalls give you a complete network security solution. d) Firewalls typically will protect you between and within network security zones. e) A firewall can introduce a performance bottleneck. Answer: a, b, e
For more information about CCNA Security (210-260 IINS) go to see this useful web portal.
1 note
·
View note
Text
What is Cisco EtherChannel

EtherChannel may be a strategy utilized in Cisco switches to total transmission capacity from different switch ports. Another word for this method is bundling. On a Cisco switch you'll be able bundle two to eight ports. An example is the photo over. Two switch ports have been bundled together to put through to another switch. An illustration would be bundling eight quick ethernet ports. Each harbour is 100 Mbps. Increase 100 Mbps by eight and you get 800 Mbps. On the off chance that these were all full duplex ports you'd get 100 Mbps of bidirectional activity for each harbour totaling up to 1600 Mbps (8 x 200 Mbps) of amassed transmission capacity. In the event that these were gigabit ports you may get up to 16 Gbps (8 x 2 Gbps). When ports are put into the same EtherChannel they are considered bundled. To bundle ports, they must meet the taking after necessities: - Same Ethernet media - Same VLAN - Same duplex and speed If the bundle is going to be a trunk: - Bundled ports must be in a trunking mode - Same native VLAN - Pass the same set of VLANs - Same duplex and speed Benefits Aside from amassing transfer speed, another advantage with EtherChannel is excess. In case one of the ports within the bundle goes down, the other ports will need to choose up the slack. As a result you're utilizing EtherChannel, you're able to stack adjust the activity over different ports. Port Aggregation Protocols When configuring EtherChannel you have the choice of using two protocols: - Link Aggregation Control Protocol - Port Aggregation Protocol (PAgP) LACP is an alternative to PAgP and it is a standard (802.3ad). PAgP is a Cisco proprietary protocol. It isn't used much anymore. Read the full article
0 notes
Text
What Is VLAN Trunking Protocol? VTP
VLAN Trunking Protocol (VTP) VTP is an Cisco exclusive protocol which permits the switching of traffic between several VLANs. VTP is used to prevent the broadcast storm that occurs when two switches that have the same VLAN installed on them are connected. VLAN trunking is a mechanism that permits multiple VLANs to be connected.
The Best AndroidBooks for Beginners in 2022
1. What is VTP?
VLAN Trunking Protocol (VTP) is a protocol used to manage VLANs. VTP is utilized to provide dynamic VLAN configuration. VTP allows for VLANs to be created, deleted, and changed. VLANs facilitate network communication and network segmentation. VTP also helps ensure MAC address consistency across VLANs. VLANs were created to enable network communications and network segmentation. VLANs are used to help network communications and segmentation. VLANs are also used to provide MAC address uniformity across VLANs.
CCNA LAB Configuration Course Zero To Hero
2. What are the benefits of VTP?
VLAN Trunking Protocol (VTP) is a protocol utilized to manage the VLAN. It is used to advertise the VLAN ID and VLAN setting to switches on the network. The advantages of VLAN Trunking Protocol include: VLAN configuration and ID information is easily propagated throughout the network. It can help avoid network traffic collisionsthat could cause performance issues for the network. It can help prevent broadcast storms. - It helps to avoid redundant VLAN configurations. It can help avoid changing configurations in the event that VLANs are removed or added. It also helps avoid MAC issues with addresses.
Cisco OSPF Configuration | How To Configure OSPF
3. What are the different types of VTP?
The VLAN Trunking Protocol (VTP) is a protocol that helps manage VLANs in the network. It permits the administrator of the network to set up VLANs in a way that they are accessible on the network. VLANs are utilized to create various broadcast domains. VTP was introduced by Cisco IOS Software Release 10.2. Cisco IOS Software Release 10.2. VTP also permits creating dynamic VLANs. This can be done employing VTP Domain Name System (VTP-DNS) mode.
CSS0_ OSPF | How to set up OSPF Multi Area
4. Conclusion.
VLAN Trunking Protocol (VTP) VLAN Trunking Protocol (VTP) is a Cisco proprietary protocol that is used in Cisco devices to handle VLANs and is used to control and configure an spanning tree. VTP is utilized to ensure the consistency of VLAN configurations across a network. VTP is also used to configure VLANs on new switches, and to transfer information about VLANs between the switches and the network. VTP can be designed to keep from unplanned or unintentional configurations of VLANs on the network. VTP is not used to configure VLANs using Cisco switches but rather is employed in conjunction with Cisco switches to set up other switches.
What is Computer Networks? Types and Classification
0 notes
Text
[PDF/ePub] CCNA 200-301 Portable Command Guide - Scott Empson
Download Or Read PDF CCNA 200-301 Portable Command Guide - Scott Empson Free Full Pages Online With Audiobook.

[*] Download PDF Here => CCNA 200-301 Portable Command Guide
[*] Read PDF Here => CCNA 200-301 Portable Command Guide
CCNA 200-301 Portable Command Guide is filled with valuable, easy-to-access information-and it's portable enough to use whether you're in the server room or the equipment closet.The guide summarizes all CCNA certification-level Cisco IOS Software commands, keywords, command arguments, and associated prompts, providing you with tips and examples of how to apply the commands to real-world scenarios. Throughout, configuration examples give you a better understanding of how these commands are used in simple network designs. This book has been completely updated to cover topics in the new 200-301 exam. Use this quick reference resource to help you memorize commands and concepts as you work to pass the CCNA certification exam. Coverage includesNetwork Fundamentals: IPv4 addressing, subnetting, VLSM, route summarization, IPv6 addressing, cables/connections, CLILAN Switching Technologies: Switch configuration, VLANs, VLAN trunking protocol, inter-VLAN communication, STP, EtherChannel,
0 notes