#website security monitoring
Explore tagged Tumblr posts
Text
Website: https://www.turacolabs.com/
Address: 31a Charnham Street, Hungerford, Berkshire, RG17 0EJ, United Kingdom
Turaco Labs specializes in eCommerce cybersecurity, offering ThreatView, a state-of-the-art cyber threat detection and PCI DSS compliance monitoring solution. Their services focus on protecting online businesses from malware, digital skimmers, loaders, and data theft. With a free security scan, breach protection warranty, and forensic-level monitoring, they provide a proactive defense system for online stores using platforms such as Magento, WordPress, OpenCart, and Joomla. Their ThreatView solution ensures continuous monitoring, detects the latest cybersecurity threats, and helps eCommerce merchants comply with PCI DSS standards.
LinkedIn: https://www.linkedin.com/company/turaco-labs-threatview/
Keywords: eCommerce cyber security website malware scan scan website for malware PCI compliance monitoring free website security scan website security monitoring website compliance audit security services website website malware scanning tools eCommerce security solutions eCommerce fraud prevention ecommerce fraud prevention companies prevent ecommerce fraud website malware scanner PCI compliance services pci compliance service provider pci compliance consulting services cybersecurity services for small businesses Magecart protection Google Tag Manager malware hacked website recovery eCommerce security best practices website security services malware removal from weebly website website malware removal website malware removal service how do i remove malware from my website how to remove malware from website how to remove malware from wordpress website malware removal for websites malware removal website remove malware from website best website malware removal how to remove virus from website website protection services best website protection service website malware protection services ecommerce fraud protection services
#eCommerce cyber security#website malware scan#scan website for malware#PCI compliance monitoring#free website security scan#website security monitoring#website compliance audit#security services website#website malware scanning tools#eCommerce security solutions#eCommerce fraud prevention#ecommerce fraud prevention companies#prevent ecommerce fraud#website malware scanner
1 note
·
View note
Text
Top 5 Best Small Business Wireless Access Points for 2024

Wireless Access Points (WAPs) play a crucial role in modern networking, particularly for Internet Service Providers (ISPs). This comprehensive guide aims to demystify the world of WAPs, providing valuable insights for both seasoned professionals and those new to the field. From understanding the core principles of WAP technology to practical deployment strategies, we cover it all. Additionally, we delve into the latest trends and innovations in the industry, ensuring you're equipped with the knowledge to make informed decisions when selecting ISP supplies for your network.
Read More: Top 5 Best Small Business Wireless Access Points for 2024
#wifi6#wifi#wifi connection#free wifi#tech news#security#monitor#lady wifi#networking#wireless#internet#the internet#websites#the two towers#cambium#tp link#wisp#wisp (oc)#equipment#startup#software engineering#marketing
2 notes
·
View notes
Text
youtube.com/watch?v=xw9-Wsz_uyU
Leveraging AI and SEO (AI and Innovation Theme)* (youtube.com)
Cloudways seo Leveraging AI and SEO (AI and Innovation Theme)* (youtube.com)
#- Cloudways hosting#- Managed cloud hosting#- Cloud hosting services#- Server management#- Website performance#- Cloud server solutions#- Scalable hosting#- Server security#- Cloudways platform#- Website optimization#- Cloud server management#- Performance monitoring#- Cloudways features#- Cloud hosting benefits#- Website speed optimization#- Cloud server reliability#- Hosting control panel#- Cloud server customization#- Cloud hosting reviews#- Cloud server maintenance#- Managed server hosting#- Cloud server security#- Website uptime#- Cloud hosting solutions#- Cloud server backups#- Cloud server migration#- Cloud hosting pricing#- Cloud server support#- Cloud server speed#- Website hosting options
0 notes
Text
Top 5 Tools for Website Security Monitoring and Auditing in 2024
In the current digital era, maintaining robust website security is essential for safeguarding sensitive data and ensuring the smooth operation of online services. Regular website security audits play a pivotal role in identifying vulnerabilities, ensuring compliance with security standards, and protecting against cyber threats. This article delves into the top five tools for website security monitoring and auditing, highlighting their features, benefits, and why they are indispensable for organizations.
Acunetix
Netsparker
OpenVAS
Burp Suite
Qualys Web Application Scanning (WAS)
0 notes
Text
The child sextortion group 764 and the global collective of loosely associated groups known as “The Com” are using tools and techniques normally used for financially motivated cybercrime tactics — such as SIM swapping, IP grabbing and social engineering — to commit violent crimes, according to exclusive law enforcement and intelligence reports reviewed by CyberScoop. The reports offer insight into the underbelly of the global network, showing how they are using traditional cybercriminal tools to identify, target, groom, extort, and cause physical and psychological harm to victims as young as 10. They were shared with police nationwide and in some cases, with foreign-allied governments. [...] The group “appears to be situated at the nexus of communities of users who share gore material, [Racially or Ethnically Motivated Violent Extremist-White Supremacist] adherents such as M.K.U. and child exploitation actors like 764.” M.K.U., it says, is a neo-Nazi group with a presence in Russia and Ukraine. [...] The groups use methods to trick children into sending sexually explicit photos of themselves, threaten to make the photos public unless they harm themselves, and kill or harm animals, among other crimes. The group’s members have coerced children into attempting suicide, harming themselves, siblings and animals. (x)
///
Wired reported this week that a 19-year-old working for Elon Musk‘s so-called Department of Government Efficiency (DOGE) was given access to sensitive US government systems even though his past association with cybercrime communities should have precluded him from gaining the necessary security clearances to do so. As today’s story explores, the DOGE teen is a former denizen of ‘The Com,’ an archipelago of Discord and Telegram chat channels that function as a kind of distributed cybercriminal social network for facilitating instant collaboration. [...] Internet routing records show that Coristine runs an Internet service provider called Packetware (AS400495). Also known as “DiamondCDN,” Packetware currently hosts tesla[.]sexy and diamondcdn[.]com, among other domains. DiamondCDN was advertised and claimed by someone who used the nickname “Rivage” on several Com-based Discord channels over the years. A review of chat logs from some of those channels show other members frequently referred to Rivage as “Edward.” From late 2020 to late 2024, Rivage’s conversations would show up in multiple Com chat servers that are closely monitored by security companies. In November 2022, Rivage could be seen requesting recommendations for a reliable and powerful DDoS-for-hire service. Rivage made that request in the cybercrime channel “Dstat,” a core Com hub where users could buy and sell attack services. Dstat’s website dstat[.]cc was seized in 2024 as part of “Operation PowerOFF,” an international law enforcement action against DDoS services. (x)
DOGE teen is a pedophile cybercriminal involved in a neonazi CSA-producing cybergang. and he has access to your SSN.
680 notes
·
View notes
Text
"Starting this month [June 2024], thousands of young people will begin doing climate-related work around the West as part of a new service-based federal jobs program, the American Climate Corps, or ACC. The jobs they do will vary, from wildland firefighters and “lawn busters” to urban farm fellows and traditional ecological knowledge stewards. Some will work on food security or energy conservation in cities, while others will tackle invasive species and stream restoration on public land.
The Climate Corps was modeled on Franklin D. Roosevelt’s Civilian Conservation Corps, with the goal of eventually creating tens of thousands of jobs while simultaneously addressing the impacts of climate change.
Applications were released on Earth Day, and Maggie Thomas, President Joe Biden’s special assistant on climate, told High Country News that the program’s website has already had hundreds of thousands of views. Since its launch, nearly 250 jobs across the West have been posted, accounting for more than half of all the listed ACC positions.
“Obviously, the West is facing tremendous impacts of climate change,” Thomas said. “It’s changing faster than many other parts of the country. If you look at wildfire, if you look at extreme heat, there are so many impacts. I think that there’s a huge role for the American Climate Corps to be tackling those crises.”
Most of the current positions are staffed through state or nonprofit entities, such as the Montana Conservation Corps or Great Basin Institute, many of which work in partnership with federal agencies that manage public lands across the West. In New Mexico, for example, members of Conservation Legacy’s Ecological Monitoring Crew will help the Bureau of Land Management collect soil and vegetation data. In Oregon, young people will join the U.S. Department of Agriculture, working in firefighting, fuel reduction and timber management in national forests.
New jobs are being added regularly. Deadlines for summer positions have largely passed, but new postings for hundreds more positions are due later this year or on a rolling basis, such as the Working Lands Program, which is focused on “climate-smart agriculture.” ...
On the ACC website, applicants can sort jobs by state, work environment and focus area, such as “Indigenous knowledge reclamation” or “food waste reduction.” Job descriptions include an hourly pay equivalent — some corps jobs pay weekly or term-based stipends instead of an hourly wage — and benefits. The site is fairly user-friendly, in part owing to suggestions made by the young people who participated in the ACC listening sessions earlier this year...
The sessions helped determine other priorities as well, Thomas said, including creating good-paying jobs that could lead to long-term careers, as well as alignment with the president’s Justice40 initiative, which mandates that at least 40% of federal climate funds must go to marginalized communities that are disproportionately impacted by climate change and pollution.
High Country News found that 30% of jobs listed across the West have explicit justice and equity language, from affordable housing in low-income communities to Indigenous knowledge and cultural reclamation for Native youth...
While the administration aims for all positions to pay at least $15 an hour, the lowest-paid position in the West is currently listed at $11 an hour. Benefits also vary widely, though most include an education benefit, and, in some cases, health care, child care and housing.
All corps members will have access to pre-apprenticeship curriculum through the North America’s Building Trades Union. Matthew Mayers, director of the Green Workers Alliance, called this an important step for young people who want to pursue union jobs in renewable energy. Some members will also be eligible for the federal pathways program, which was recently expanded to increase opportunities for permanent positions in the federal government...
“To think that there will be young people in every community across the country working on climate solutions and really being equipped with the tools they need to succeed in the workforce of the future,” Thomas said, “to me, that is going to be an incredible thing to see.”"
-via High Country News, June 6, 2024
--
Note: You can browse Climate Corps job postings here, on the Climate Corps website. There are currently 314 jobs posted at time of writing!
Also, it says the goal is to pay at least $15 an hour for all jobs (not 100% meeting that goal rn), but lots of postings pay higher than that, including some over $20/hour!!
#climate corps#climate change#climate activism#climate action#united states#us politics#biden#biden administration#democratic party#environment#environmental news#climate resilience#climate crisis#environmentalism#climate solutions#jobbs#climate news#job search#employment#americorps#good news#hope
1K notes
·
View notes
Note
Angel x Joe #9 for hurt/comfort. I just love them so much



1k & Birthday Bash nav | main navigation | reqs | table of contents
#9. Taking you to the ER for an injury/sickness.
Joe Burrow x Angel
• you DO NOT have my permission to copy my work, upload as your own, translate, or repost on any other website •

It started with silence.
The kind that made Joe glance up from his iPad, the game film still rolling in slow-motion replays, his AirPods still in his ears. The TV was on mute, casting soft blue light across the living room, where Angel sat curled on the edge of the couch.
Or rather, had been sitting.
Now she was hunched forward, elbows on her knees, one hand to her forehead, her breathing shallow and fast.
Joe pulled out his AirPods. “Angel?”
She didn’t answer.
He rose quickly, crossing the room in two strides, crouching down in front of her. Her skin was pale, even under the warm-toned lamplight, and her curls stuck to her forehead with sweat.
“Babe, hey. Talk to me. What’s going on?”
“I—” Her voice cracked. “I don’t know. My head hurts. I’m dizzy. My chest is tight.”
Joe’s stomach dropped. This wasn’t like her. Angel was composed even when she was in pain, someone who once sat through a root canal and walked out like it was a teeth cleaning. But now she looked like she could barely stay upright.
“When’s the last time you drank water?” he asked.
She blinked slowly, trying to focus on him. “I—I don’t remember. I was rushing this morning. I didn’t eat lunch. I had two meetings. Then the cake tasting. I…”
Her sentence dissolved into nothing. Joe barely caught her before she collapsed.
Her body went limp in his arms, head tilting back, eyelids fluttering. For a horrifying second, he thought she was gone—until she let out a shaky breath.
“Angel!” His voice cracked. “Come on. Wake up. Hey.”
She stirred weakly, and then her back arched in his arms—a sudden, stiff jolt—and a small, guttural sound left her throat.
Panic exploded in Joe’s chest.
He didn’t think. He scooped her up, grabbed his phone with trembling fingers, and was already calling 911 before he reached the car.
·̇·̣̇̇·̣̣̇·̣̇̇·̇ •❣•୨୧┈┈┈୨୧•❣• ·̇·̣̇̇·̣̣̇·̣̇̇·̇·̇·̣̇̇·̣̣̇·̣̇̇·̇ •❣•୨୧┈┈┈୨୧•❣• ·̇·̣̇̇·̣̣̇·̣̇̇·̇
The drive to the ER was a blur.
Joe had never driven so fast in his life, one hand on the wheel, the other gripping Angel’s leg as she lay slumped in the reclined passenger seat. The dispatcher stayed on the line, guiding him with calm, clear directions—keep her head tilted, monitor her breathing, don’t panic.
Don’t panic.
But how could he not?
The woman he loved, the woman he’d been planning a life with—she wasn’t responsive, wasn’t herself. He kept glancing over at her, willing her to open her eyes, to tell him she was okay. That it was just a panic attack, or low blood sugar, or anything less terrifying than what his mind was already imagining.
He pulled into the University of Cincinnati Medical Center’s emergency lane at 1:53 AM, tires squealing. He threw the car into park and sprinted around the side, yelling for help before the door even swung open.
“Somebody—help! I think she passed out—maybe a seizure—she’s not waking up!”
Nurses rushed forward with a stretcher, and Joe gently eased her out of the car. She looked small and weightless in his arms, her head resting against his chest, her breathing faint but there.
“We’ve got her,” one of the nurses said, taking control.
Joe tried to follow them, but a security guard stepped in. “Give them a minute, sir. They’ll come get you.”
“She’s my fiancée,” he said hoarsely. “I’m not going anywhere.”
·̇·̣̇̇·̣̣̇·̣̇̇·̇ •❣•୨୧┈┈┈୨୧•❣• ·̇·̣̇̇·̣̣̇·̣̇̇·̇·̇·̣̇̇·̣̣̇·̣̇̇·̇ •❣•୨୧┈┈┈୨୧•❣• ·̇·̣̇̇·̣̣̇·̣̇̇·̇
Twenty minutes later, he was finally allowed into the exam room.
Angel was lying under crisp hospital sheets, a nasal cannula feeding her oxygen, an IV in her arm, electrodes on her chest. Her skin was still pale, but her breathing was steadier. A nurse explained the basics: extreme dehydration, compounded by stress, likely triggered a vasovagal syncope response. The moment she passed out, her body’s natural reflex had gone haywire. It wasn’t a full seizure, but close enough to terrify anyone watching.
Joe sat down beside her, covering his face with both hands.
The nurse touched his shoulder. “She’s stable. She’s going to be okay.”
He nodded, swallowing hard. “Thank you.”
“She’ll need fluids, rest, and probably a full workup to make sure there’s nothing more serious going on.”
As the nurse left, Angel stirred.
Joe shot to his feet, leaning over her. “Hey. Angel. Can you hear me?”
Her eyelids fluttered, and slowly, her eyes opened. Confused at first. Then they found him. Her voice was thin, cracked. “Joe?”
“I’m here. You’re okay. You’re safe.”
She looked around, eyes glassy. “Hospital?”
“Yeah,” he said, brushing hair back from her face. “You scared the hell out of me.”
She frowned, trying to piece things together. “What happened?”
“You passed out. You were dehydrated. And I think stress finally got the best of you.”
Her eyes filled, not with pain, but with guilt. “I didn’t want to worry you. I thought I could just push through it.”
“You don’t have to push through anything alone,” Joe said, taking her hand gently. “That’s not how this works. Not with me.”
She closed her eyes again, letting a few tears fall. “I’m sorry.”
“No,” he said firmly. “No sorries. Just get better. That’s all I want.”
·̇·̣̇̇·̣̣̇·̣̇̇·̇ •❣•୨୧┈┈┈୨୧•❣• ·̇·̣̇̇·̣̣̇·̣̇̇·̇·̇·̣̇̇·̣̣̇·̣̇̇·̇ •❣•୨୧┈┈┈୨୧•❣• ·̇·̣̇̇·̣̣̇·̣̇̇·̇
They kept her overnight for observation.
Joe stayed, refusing to leave even when the nurses brought him a cot he didn’t touch. He sat by her bed all night, holding her hand, listening to the steady beep of the monitors. The hospital window turned from black to navy to gray, and finally, pale pink as dawn broke.
Angel slept deeply, the medications doing their job, her face relaxed at last.
Joe leaned back in the chair, exhausted but wide awake.
In all his years of pressure—on the field, in the spotlight, under blitzes and injuries—he had never been more scared than he’d been watching her body go still in his arms.
Football could break bones. But this kind of fear?
This was the kind that broke hearts.
And still, there was nowhere he’d rather be than beside her.
·̇·̣̇̇·̣̣̇·̣̇̇·̇ •❣•୨୧┈┈┈୨୧•❣• ·̇·̣̇̇·̣̣̇·̣̇̇·̇·̇·̣̇̇·̣̣̇·̣̇̇·̇ •❣•୨୧┈┈┈୨୧•❣• ·̇·̣̇̇·̣̣̇·̣̇̇·̇
Angel had been home for less than twenty-four hours, and Joe was already driving her crazy.
He hovered.
He followed her from room to room like a silent bodyguard—carrying water bottles, fluffing pillows, adjusting thermostats like the air itself might try to harm her. Every time she so much as shifted her weight or scratched her head, Joe looked up from wherever he was like she’d just cried out in pain.
She loved him. Deeply.
But if he asked her one more time if she was too cold, she was going to pretend to faint just so he’d stop talking.
“Joe,” she said flatly, watching him bring her the third cup of electrolyte water that hour, “I’m not a dying plant. I’m a person. I’m fine.”
He didn’t flinch. “You were unconscious two nights ago. You’re not fine, you’re recovering.”
Angel sighed from her place on the couch, propped up with enough pillows to build a small fort. She wore one of Joe’s sweatshirts, her legs wrapped in a blanket, the IV bruise on her hand faint but still tender. “You’re treating me like I’m made of glass.”
“You passed out and scared the hell out of me. So yeah, I’m gonna treat you like you’re glass. Until the doctor clears you. Until I clear you.”
She raised a brow. “You’re not a doctor.”
“I’m quarterbacking your recovery. Same thing.”
Angel groaned, rolling her eyes. “You’re lucky you’re cute.”
Joe grinned and sat beside her, not-so-subtly checking her pulse on her wrist. She let him, because truth be told, even though his hovering was excessive, it was also kind of sweet.
“You haven’t left the house since I got back,” she said after a beat.
“I’m on a ‘mental health’ day,” he replied, shrugging. “Coach told me to take it. Said I looked like someone who hadn’t slept in a week.”
She gave him a soft look. “Because you haven’t slept in a week.”
“I’ve been busy keeping you alive,” he teased, though his eyes were still a little too serious for the joke to fully land.
Angel nudged his leg with her foot. “You can breathe now. I’m not going to pass out again.”
“You don’t know that.”
She tilted her head. “You’re scared.”
Joe exhaled slowly. “Yeah. I am.”
The room fell quiet except for the hum of the heater kicking on. He looked down at her hand in his, thumb brushing gently over her knuckles.
“I’ve had injuries. I’ve taken hits. I’ve had defenders try to take my head off,” he said. “But none of that ever made me feel like this—watching you fall and not knowing if you’d open your eyes again.”
Angel’s eyes welled with quiet tears—not from pain this time, but from something softer, heavier.
“I didn’t know I’d let myself get that run down,” she whispered. “I thought I could handle it. The wedding planning, work, the travel… being your partner means being strong.”
“Being my partner means being real,” Joe said. “Strong doesn’t mean pushing until you break. You don’t have to prove anything to me. Ever.”
She nodded slowly, overwhelmed by his gentleness.
“I’ll try to be better about listening to my body,” she said. “But you have to try not to lose your mind every time I stand up to pee.”
“No promises.”
She laughed—a real one this time—and Joe looked both relieved and proud, like he’d just completed a game-winning drive.
·̇·̣̇̇·̣̣̇·̣̇̇·̇ •❣•୨୧┈┈┈୨୧•❣• ·̇·̣̇̇·̣̣̇·̣̇̇·̇·̇·̣̇̇·̣̣̇·̣̇̇·̇ •❣•୨୧┈┈┈୨୧•❣• ·̇·̣̇̇·̣̣̇·̣̇̇·̇
Later that night, after she was asleep, Joe sat on the floor beside the couch, reading the discharge papers for the fifth time. Gallons of fluids, balanced meals, no stress. Easy instructions, hard execution.
He looked up at her, curled under the blanket, face soft in sleep.
He knew he couldn’t protect her from everything. But he’d be damned if he didn’t try.

#honeydipped1k#x black fem reader#x black!fem!reader#x black!reader#x black reader#x reader#thed.i.l.fchronicles#thed.i.l.fchroniclesasks#joey burrow#joe burrow#joey b#joe cool#joe burrow lsu#joe burrow bengals#bengals#joe burrow imagine#cincinnati bengals#joe burrow x black reader#joe burrow x black!reader#joe burrow x reader#joe burrow x y/n#joe burrow x you#joe burrow x oc#joe burrow fanfic#joe burrow angst#joe burrow au#joe burrow series#joe burrow social media au#joe burrow blurb#joe burrow fluff
160 notes
·
View notes
Text
Chat Control in a nutshell (please reblog this, US people)










Find out more about Chat Control here TAKE ACTION HERE ! OR HERE Calling is much more efficient ! The latter link will redirect you to the official websites of your respective reps. Under the "read more", you will find what you need to say/write when contacting your reps. You will also find an alternate format of this comic,and I give explicit permission for people to translate it and spread it anywhere for awareness. Credit really not needed, I don't care about that rn Even if this is a EU proposal, I am urging Americans to also share this, since it goes hand in hand with KOSA. DON'T FORGET TO JOIN OUR DISCORD SERVER AGAINST CHAT CONTROL ! https://discord.com/invite/e7FYdYnMkS

(Latest update on Chat Control was the 12 september 2024) This is a little long, so feel free to shorten it as you wish : Subject line: "2022/0155(COD) Dear Sir/Madam, I am writing to express my grave concerns regarding the proposed introduction of "Chat Control" This measure poses a serious threat to the privacy and fundamental rights of all EU citizens and stands in stark contradiction to the core principles that the European Union seeks to uphold. The proposed Chat Control contravenes Articles 7 and 8 of the Charter of Fundamental Rights of the European Union, which guarantee the right to respect for private and family life and the protection of personal data. The indiscriminate surveillance of private messages without specific suspicion or cause directly violates these fundamental rights. The General Data Protection Regulation (GDPR) sets out stringent rules for the processing of personal data. The proposed indiscriminate surveillance and scanning of private messages before end-to-end encryption is fundamentally incompatible with the principles of data minimization and purpose limitation enshrined in the GDPR. Specifically, Articles 5 and 6 of the GDPR, which govern the lawfulness and principles of data processing, would be violated by the introduction of such measures. The implementation of Client-Side Scanning (CSS) on devices means that all messages and files are scanned on the user's device before being encrypted and sent. This effectively nullifies the protection offered by end-to-end encryption and opens the door to misuse and additional security vulnerabilities. Moreover, the technical capability to scan such content could be exploited by malicious actors to circumvent or manipulate surveillance mechanisms. Such far-reaching surveillance measures not only endanger privacy but also freedom of expression. The knowledge that their private messages are being scanned and monitored could significantly restrict individuals' willingness to freely express themselves. Additionally, trust in digital communication platforms would be severely undermined. I urge you to take a strong stance against this disproportionate and unlawful measure. The privacy and digital rights of EU citizens must be safeguarded. It is imperative that we protect our fundamental rights and ensure transparency in the decision-making processes of our leaders. For more detailed information on the proposal and its implications, please refer to the following resource: Link to Netzpolitik article. https://www.patrick-breyer.de/rat-soll-chatkontrolle-durchwinken-werde-jetzt-aktiv/ Thank you for your attention to this critical matter. Sincerely, [Name] Art. 10 GG , Art. 8 & 11 EU Charta , Art. 8 EMRK (Alternate comic here V)
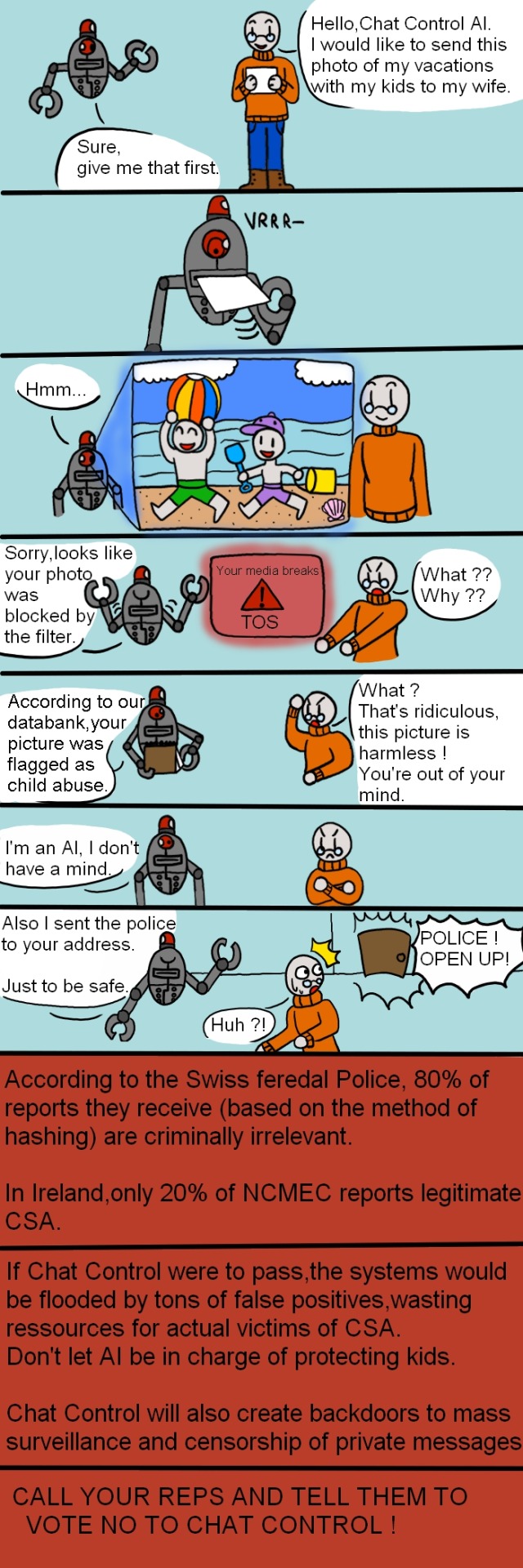
286 notes
·
View notes
Text
Update: Phishing False Positive Reports
As of 08:30 server time today, Wednesday, September 11, the Flight Rising website is passing all security and file checks. Our engineers have attempted to recreate this flag using the reported antivirus programs (Avast and Avira) and have been unable to reproduce the reported alert. We suspect this was a false positive, triggered by an update on the anti-virus's side, that has since been patched. Our findings and community reports are consistent with previous instances similar to today's, where an anti-virus or anti-malware program flags the site as suspect after an update on their side. If (when) this happens again going forward, we ask that players receiving these alerts also report them to your anti-virus provider so they can check their own records and updates with reproducible examples and patch any false flags. This isn't to say we don't want you reporting this to us—please continue to report these issues to us as they come up, even if they turn out to be a false positive later!
Thank you again for your reports! We will continue to monitor throughout the day, out of an abundance of caution.
362 notes
·
View notes
Text
Here’s how to share sensitive leaks with the press
Published Oct. 16, 2019 Updated Jan. 31, 2025 / Freedom of the Press Foundation

[please take a moment to click the links at the bottom to give this website traffic if you can. the only reason I am copy pasting it here is for those who can access tumblr but not necessarily that site.]
~~~
Over the years, we have witnessed abuse and mismanagement in the government and private sector — sometimes bad and sometimes worse — that need to be brought to public attention. For those who would leak information about such misdeeds to the press, giving tips to journalists can be risky and may violate previous legal agreements with the leaker’s organization, such as a nondisclosure agreement or contract. But sometimes, it can also be an effective and courageous way to call attention to misconduct.
This guide describes basic steps for minimizing potential risk when sharing sensitive information with a news organization. We want to be clear that no piece of software, nor security recommendation, will be 100% effective, and the decision to blow the whistle may invite scrutiny or retaliation. At the same time, it may be a choice that drives necessary institutional change. Before reaching out to the press, think carefully about what you can do to minimize that risk and stay as safe as possible.
Before moving ahead, do you have a strong tip?
A good tip requires clear evidence and should be the basis for a story that the broader public needs to know about.
So, for instance, whether or not you have evidence, the broader public might not need to know that a neighbor refuses to pick up after her dog on the morning walk. On the other hand, allegations of corruption or illegality among public officials are certainly newsworthy, but those claims will not make it into a published story without verifiable evidence.
Who are you leaking about and how might they respond?
Think about the sensitivity of the information you’re sharing, and who might be willing to investigate the source of the leak. What are the organization’s capabilities? What resources (e.g., attention and legal, financial, or technical) can it invest in discovering the source? And how likely do you think it is that it will actually investigate?
If you share information about a large, well-resourced organization that requires discretion from employees, such as a government agency, it may have enormous legal, financial, and technical resources available for investigating a leak. If you’re sharing information about a small organization, such as a local restaurant that muzzles workers, its resources are much more constrained, and it may not have the capacity or willingness to investigate. Act accordingly.
Proceed with caution
Be cautious about behaviors that could make you readily identifiable as a source.
Keep all of your leaking activities outside the view of your organization. That means no calling from work, no emailing from a work email address, and staying off work devices or wireless networks.
It's common for well-resourced organizations to keep logs of activities on employees’ workplace devices and online activities. Likewise, sometimes workplaces have “BYOD” (bring your own device) technologies that could allow them to log your activity on your personal device. So if you work at a large organization and you're reading this article on a workplace device or Wi-Fi network, chances are your workplace already has a log that you've accessed this page. Similarly, a visit to a news organization's tip page (like https://www.nytimes.com/tips) may be logged by your workplace. This is why it's so important to limit your leaking activities to devices and networks that your workplace doesn't control.
Has your workplace ever required you to install monitoring software (or software of any kind) on your work or personal device? If so, you probably don't want to use those devices for any whistleblowing activities.
Be cautious about giving tips on anything that only you could know or materials that only you could access. And consider whether the increased risk of being caught sharing these kinds of materials is worthwhile, or if you feel you have a strong moral obligation to do so.
If you are the only one at your organization surfacing a specific grievance, and information about that grievance is later reported by the press, it may give your organization a strong hint about who shared the information.
Don’t tell anyone about your leaking activities (even perhaps the journalist or news organization you’re leaking to), except where absolutely necessary and in cases where you may want legal advice from a practicing lawyer.
Reporters generally take their commitment to protecting your identity very seriously and will do everything in their power to fight potential legal requests for identifying information about you. But often, it’s safer not to give your identity if you don’t have to. Keep in mind that journalists prefer to have proof of your claims and information to demonstrate your identity is a part of that.
Tactics for minimizing risk
There are a lot of ways to minimize the risk of a tip being tied to you, like potentially through your continued communications with reporters.
Send your materials through physical mail. You can mail electronic documents (e.g., on an SD card) or physical documents through ordinary mail. Be warned: The U.S. postal service takes pictures of the exterior of physical mail. So don’t use a return address that is associated with you and instead mail it in from a sidewalk mailbox in a location you don’t usually frequent. If you have a particular reporter you want to look into your story, copy them on the envelope.
Call from a phone number unconnected to you. For example, go to a business you don’t usually go to and ask to use their phone. You can also buy a cheap cell phone and a prepaid phone card that cannot be traced back to you. But know this involves several careful steps: You must pay with cash, and if your organization can have access to phone location records, it’s best to only turn on the phone in locations unassociated with you. That also means using the phone in locations separate from your permanent phone. If you can, remove the battery when it’s not in use.
Use Signal for private messaging. Signal is a secure, free, and open source messaging app for iPhones and Android devices. Signal gives you end-to-end encrypted messages and phone calls, and only retains your phone number, your signup date, and when you were last active. In Signal, you can also make messages automatically self-destruct for everyone in the conversation after a set amount of time. This makes it significantly harder (but not impossible) to eavesdrop on your conversations. If you want help getting started, read this beginner-friendly guide on using Signal. Note that Signal allows usernames, so you do not need to give your name or phone number to media organizations unless you choose to. Make sure your username is enabled and understand that Signal is not designed for complete anonymity.
Before looking into news organizations, consider using the Tor Browser for greater privacy. Tor Browser is a modified version of Firefox. Tor encrypts and tunnels your web traffic within a global network of computers before connecting you to your final destination. When you access a website through Tor (for example, Amazon.com), you will appear to connect from a remote location — likely another country. Again, don't use a work device or network for this kind of research.
Use a whistleblower submission system. Tools such as SecureDrop can provide protection by allowing you to share documents and communications through an anonymous and encrypted drop box.
More technical, but more secure: SecureDrop
With SecureDrop, which is maintained by Freedom of the Press Foundation, not even the news organization knows who you are unless you choose to tell them.
A growing number of news organizations (e.g., The New York Times, The Washington Post, The Intercept, The Guardian) are using SecureDrop to allow sources to reach out and share files or communications anonymously. With SecureDrop, not even the news organization knows who you are unless you choose to tell them.
You can access a news organization’s SecureDrop page through Tor Browser.
People on your network can’t see what you’re doing on Tor, but it’s still possible to tell that you’re using Tor. With that in mind, do not use it at work. For greater security, consider using Tor Browser only over a Wi-Fi network in a location that is not tied to you (perhaps a coffee shop you don’t normally visit) and pay with cash.
As opposed to a “.com” web address, you get to SecureDrop through a unique .onion web address, which can only be accessed through Tor.
Using SecureDrop is fairly easy
Follow the directions to download the Tor Browser at torproject.org and install it.
Launch the Tor Browser application and click "Connect" to log into the network.
Click the shield icon in the top corner > Advanced Security Settings… > Safest
Within Tor Browser, navigate to the SecureDrop directory and search for your preferred news organization: securedrop.org/directory
Find the .onion URL for your preferred publication (e.g., The New York Times: securedrop.org/directory/new-york-times), then copy and paste it into the address bar in Tor Browser.
From here, you can leave messages and files that the news organization will check from time to time.
You will be given a random “codename” for continued conversation with the news org. Keep this information safe, and don’t share it with anyone. If you lose your codename, they can’t reach you anymore.
(For more technically adept users, consider accessing SecureDrop through an operating system designed for privacy and anonymity, such as Tails.)
Dealing with file metadata
Sharing information may be less risky than sharing documents because they can be embedded with information about the file, which we call metadata. For example, if you create a .docx file, it may have identifying information about you embedded in the file. Consider carefully whether you really need to share files or just the information.
To deal with hidden metadata, rather than sending the file itself, consider taking a picture of a document with an old-fashioned camera (not a smartphone), or taking a screenshot of the document. On most operating systems, screenshots come with little useful metadata. For more technical users, you can find metadata removal tools here.
Where do you find a news organization's contact details?
First, be careful where you reach out.
Freedom of the Press Foundation maintains a list of organizations that support the secure communications practices outlined above, and how you can contact them. Such practices are becoming standard, and we hope other news organizations looking for great tips will follow suit.
Freedom of the Press Foundation hosts a directory of SecureDrop and secure tip pages for dozens of news organizations around the world. Whether you want to reach out to The New York Times, The Washington Post, The Guardian, The Intercept, or others, you can find their information here: https://securedrop.org/directory. (We would not recommend investigating this at work.)
If not you, then who?
Sharing information with the press is not always an easy decision, but your information can help to hold powerful people and institutions accountable. Just be sure to move ahead with a strong understanding of your organization’s capabilities and how to share tips safely.
https://freedom.press/digisec/blog/sharing-sensitive-leaks-press/
https://bsky.app/profile/freedom.press/post/3lh2rgopf5225
127 notes
·
View notes
Text
Stalker!Yandere!Tony Stark x Fem!Reader- To Steal and Dote On (Internet stalking, Collecting personal information without consent, Using personal information without consent, This billionaire has resources and he's going to use them, Breaking and entering, Theoretical threats of kidnapping and violence, Invading Reader's privacy without consent, Tony has Reader brainrot already)
Chapter 1 | Chapter 3 |
Chapter 2: Forget You (Not)

——————————————————————————————————
Only, Tony wasn’t able to shake off the thought of you at all. If anything, you took up his primary focus throughout his day.
A part of him did genuinely forget the party last night as he sat in mind-numbing meetings back-to-back, only attending them now due to his irate assistant chewing him out over it. She practically pushed the billionaire out of the kitchen before coffee even greeted his body, yapping his ear off over technicalities and investors he couldn't care less about. Even though Tony was itching to poke at her in this state, to mention his admiration for how her red hair looked like glowing fire spouting from a dragon when she got like this, he got the strong sense that she would quit if he missed another business meeting.
But he was incredibly bored and disinterested, and you kept plaguing his thoughts with more questions that got his brain desperately intrigued. He couldn’t even distract himself with anything else because none of it was as gear-turning as to the mystery of you.
Your confusion, your… disinterest? Never had he encountered someone who wasn’t there for him specifically, or seemed to have no interest in who he was.
And the fact you just… sat there. It was so out of place, like a nagging flaw in a blueprint he couldn't put his finger on.
Why were you there, if you didn’t care about Tony Stark?
Who were you?
That train of thought led to the male instructing his A.I. to scanning your facial profile from the security cameras of his tower right after he was finally free from the drudgery of business— contently settled into his lab with a fresh batch of coffee. Luckily, the feed from last night got a good look at you. It was a better view than the tipsy haze of his memory, he noted. The mostly-clear footage of your face allowed the system to swiftly correlate your likeness to other documented matches— a pool of candidates was completed in the time it took for him to take a long swig that burned his tongue and throat.
What came up was a compiled list of look-alikes that Tony had to manually rifle through in the hopes that one of them would be you and mentally grumbled to himself that you looked like too many people.
Tony grew more irked by the second up until the last result, which was your red carpet picture in front of his building. Tracking the source, he was led to a tabloids website and found that even the photographers had no idea who you were. Your picture was simply sourced as “guests attending a Stark party,” not counting the other woman with you in the image.
He realized that the whole thing was a waste of time. This is why he didn’t do the menial work himself: it was tedious and boring and he had nothing to show for it. Not even a name. You literally didn’t exist on any social media or content platform besides a useless picture just floating there on the internet.
Tony shot up from his chair to pace. He ran his hands through his hair, furiously muttering to himself.
“No social presence? No footprint— no… nothing?”
That’s…really smart, actually.
He hates it. And he hates to admit it, but…
But a small part of him respects you for it, too.
His head whipped back to the monitor glowing before him, patiently idling for a new order. Narrowing his eyes, the man marched back over to the console, furiously typing in a similar command. The process would take longer than he would like, but he was sure he would get his match.
“Who are you, sweetheart?” Tony mused distractedly to the image of your face on one of his monitors, hoping to find a sliver of treasure amidst a sea of coal.
——————————————————————————————————
Entering the lobby of your workplace was as it always is: white tile textured with marbling stains, wood paneling hugging the walls, a white and gray reception desk overlooking the room. Folks came and went from your line of vision, entering and disappearing into elevators and corridors, the leftover sounds of their jabbering following close behind them in the air. Many workers held various brews of caffeine or small breakfast items as they passed by, which had your stomach growling despite already filling it before you left your apartment.
It takes you a more than the typical few minutes to get to your work floor, the elevator being unusually popular for a Monday. You ponder over it to pass the time as you stand there, entertaining the thought of someone important stopping by. When the elevator dings for your stop, you step out and shuffling over to your desk, providing a couple “hellos” and “good mornings” to the associates that greet you along the way. Settling down into your office chair, you boot up your computer as you place and arrange the belongings you fish out from your purse.
You look around the drab space as you wait for the desktop to appear so you can clock in. Your friend and coworker doesn’t seem to be here yet. You contemplate what (Friend name) got up into last night, if that is her reason for running late. Or rather, who she got with. You laugh to yourself as you drag your mouse over to bring up the company time clock, setting a mental reminder to ask her later when she shows up.
You click open the app used for business emails and you sigh softly at the unreads, sucking in a breath and sitting straighter.
Back to work as usual.
——————————————————————————————————
It was quite some time later before (Friend name) bounded into the office with a pep in her step. And despite prodding her with your curiosity, she was determined to only reveal anything at lunchtime, which was a couple hours away. She also wanted to discuss it inside the building today instead of the cafe, which caused you to raise a brow. She waved you off and you had shrugged. You tried to focus back on your work, but the suspense of her answer kept eating at you until then, where you realized you didn’t get much done at all.
Now, you were both seated in one corner of the break room, had your meals and drinks pulled out, and were ready to dig in. Your brain, however, couldn’t help but bring up the topic the moment you uncapped your takeaway salad and raised your plastic fork.
“How’d your night go? Did you have fun?” You question good-naturedly before shoveling some greens into your mouth.
“Yeah,” She sighs, unwrapping a granola bar. “But I didn’t stay the night.”
You pause, utensil and speared salad pieces hovering in mid-air, as you turn your head to look at her properly. She munches on the bar of oats sprinkled with fruit and nuts for a moment, catching stray crumbs at the corners of her lips and licking them off before elaborating. “Something came up and he had to take care of it, so we called it a night.” She pauses, looking at her snack thoughtfully and clearly reminiscing. “He was sorry enough to drop me off, though.”
“Oh,” you breathe, resuming the bite of your food and chewing it on one side of your mouth. “That was nice of him.”
“Yeah, it was.” (Friend name) trails off, releasing a dejected sigh. “So,” her mood shifts as she throws her hair over her shoulders and leans in toward you with vibrant green eyes sparkling of curiosity. “What did you get up to last night? Meet anyone interesting~?” You nervously smile at the sudden attention and shift in the topic, an awkward blush painting your face. You take a sip of your drink and clear your throat to gather your thoughts.
“No one special,” you shrug casually, collecting more lunch on your fork, “just some guy who was full of himself and calling me sweetheart.” There wasn't much to tell concerning the details, anyway.
Her nose wrinkles in distaste, responding with an “ew, gross.” You heartily laugh at her reaction as she shudders. She was never one for pet names like that— it reminds you of one person she dated, who never called her by her name and insisted on nicknames like that. Her features relax back into an easy smile, turning her attention back eating. “Well, I’m glad he didn’t get your number, then.”
As you look down at your lunch, a soft chuckle escapes you as you shake your head in agreement.
“Yeah, definitely not.”
——————————————————————————————————
Finally— finally— he struck gold.
Documented records of the institutions you attended in your life: really just schools and appointments, but it was something. Your yearbook photos helped, too. Only the newest information mattered, however, so he only took note of your most recent forms of contact to date.
It took a lot of outside the box thinking to get there, but that was what Tony Stark did best. He hopes you'll appreciate all the effort he took to go after you when you find yourself in his presence once more, enjoying his company and what his bed has to offer.
But first things first.
He rings up your number, already mouthing what he will say when he hears your voice. He’s more excited than he should be, but can’t find it in himself to care.
It keeps ringing.
He closes his eyes, imagining your expression when you find out it’s him— your lips curving into a smile as you start to say his name—
He gets the voicemail lady instead.
Confused, he sits there for a moment in silence before he tries again.
He’s greeted with a single ring before the same script plays. Did your phone die? Was it powered off? What was happening?
Furrowing his brows, Tony instructs his A.I. to deliver a message.
He compiles something short and flirty, just aiming to get your attention and to reel you in a bit. He sends it off, and almost immediately, the sophisticated, deadpan male voice of J.A.R.V.I.S. informs him that the message wasn't sent.
Okay.
You either blocked his number or your phone is off. Or it just sucks at texting for some reason.
The male purses his lips in thought. He needs to try a different approach, he supposed.
Going back to square one, Tony finds a piece of information that causes a playful smirk to slowly grow upon his face.
Well, he always did like a challenge.
——————————————————————————————————
“Something special just for you, (Name). —Your knight in rose-gold armor❤️💛”
That’s all the italicized note said.
The fancy slip of cardstock that was attached to the package on the floor wrapped in cellophane.
The gift sitting innocently in front of your apartment door when you arrived home from work.
Inspecting it as you bring it inside, the more confused and skeptical you get.
This…
You flipped the box over multiple times in the vain hope of finding a different answer or something new to go off of. It yielded nothing substantial, other than the fact that this was likely delivered to you from some kind of store that gift-wraps their products. Exactly who ordered this in the first place, however, is something you can’t determine. A sender’s address is nonexistent.
If this really was for you, then…
It was completely wrong.
Whoever sent this to you had no idea who you were because the assortment of chocolates had multiple flavors you didn’t care for, and would render the whole box a waste under your possession. There was only one specialty kind that you were willing to try, and even then it was filled with extra tastes that you didn’t really care for in your sweets.
You squinted at the packaging, trying to file through your memories, but you had never heard of this brand in your life.
Thankfully, the box did contain the reliable milk chocolate flavor, as well as darker coco and lighter milk and sugar versions as standalones. So, you figured, it would be a safe bet to sample that one first to see if their base for chocolate recipes were passable.
You hesitantly brought the confection to your lips and let it hover there, now wondering what kind of razor blades or poisonous concoctions were stuffed into this thing. But if someone wanted you dead, why would they make it this elaborate? Wouldn’t there have been some tell of any tampering before you opened it? Feeling ridiculous over your own thoughts, you bite the bullet. Pinching your eyes shut, you threw the piece of chocolate into your mouth.
You bit down, felt a more gooey substance ooze its way onto your tongue, and widened your eyes when the flavor hit you.
You immediately spat the thing out in the garbage can and raced over to your fridge for a palette cleanser. Snatching the first jug you saw, you drank directly from the container and realized too late that it was an acidic juice you picked out.
It paired worse than wine would, surely.
After most of the vile concoction was washed away from your taste buds, you smacked your lips and tried to process the lingering aftertaste.
Glaring at the offending box of chocolates, you took no time in propelling it towards the same bin where it belonged.
Forget figuring out where that came from.
You wouldn’t even give that to your worst enemy.
——————————————————————————————————
“You’ll thank me for this later, hun.” Tony mused to himself as he balanced the handle of a screwdriver in his mouth, putting the finishing touches on the camera in your studio-sized living room. As much as Tony wanted to cover the whole area of the unit itself, he knew not to overdo any more than he really needed to.
The man had no idea if the luxury chocolates he ordered went over well, and was itching to find out sooner rather than later. The very next day on a sunny mid-afternoon with a toolbox in tow, Tony visited your side of the city in his iron suit. He landed on the roof of your apartment, leaving the armor there as he climbed down the fire escape until he reached your level. He found an almost-closed window and had his A.I. scan for any lifeforms inside before he pushed the creaky wooden frame up and crawled through. And then Tony— after making sure you weren’t in another room and about to catch him— happened to glance down into your kitchen trash can. That hurt his feelings of course, but it fueled him to win your favor just the same. He only needed to get a sense of how you lived and what you liked, so he could woo you better when he revealed himself.
He hoped a woman like you enjoyed a mystery, because his work as Iron Man simply didn’t allow him to date you properly as he would’ve preferred— and he was too interested to simply forget about you. Even if he did manage to talk to you, a public relationship would be a no-go; the paparazzi alone would have you running for the hills. So, if you wouldn’t entertain digital communication with him, then virtually keeping tabs on you as your secret genius, billionaire, philanthropist, superhero admirer would have to do.
That was all.
Not because you were so elusive that it was driving him up the wall and he needed some reassurance grounding him that— yes, you did exist— and weren’t evading him on purpose or forgot him entirely.
No— he assured himself as he adjusted the device above him, not at all.
Besides, he got into your apartment too easily. The area you lived in was unruly, at best. And you needed protection. You could be snatched up out of thin air with no one the wiser as to your dissappearance. This way, even if he isn’t physically there for you or watching it happen back in his tower, he can at least use the footage from the cameras to gather the clues necessary to track you. Flying in as Iron Man, he’ll make the perpetrator sorry he even existed— break every bone of his that so much as touched you, and be your hero. And your relationship will blossom from there. Tony was doing you both a service by installing his tech in your apartment, if anything.
But what you didn’t know won’t hurt you.
While he was a genius, and was confident that his level of intelligence surpassed yours, he had no clue how perceptive you actually were. Installing too many surveillance cameras in your home would pose a risk to the subtlety of the operation he was trying to maintain, despite his desire to map every corner of your unit. Besides, more evidence of his work meant a higher probability of being discovered. Which meant a bigger chance for the devices to be knocked out of place and exposed to you later down the line. Even accidentally, Tony couldn’t have that.
Wiping his calloused hands on his jeans, the male assessed his additions to your apartment, triple-checking their installations and positioning. After making small adjustments here and there and test driving the feeds with his Stark phone, he was all set.
Tony’s troubleshooting finished with the last camera in your bedroom— and as he looked up, his eyes flitted over towards the ajar door leading out of the area he was standing in. Leaning forward with a squint to his eyes to peek through the crack yielded a wider expanse of the drab and cracked white tile, a mirror protruding from the wall, and various products cluttering the countertop of a sink directly under the hanging glass.
He sucked in a breath before spinning on his heel and marching right the fuck out of your bedroom.
No— he thought to himself. He would not be doing that.
It was one line he refused to cross.
——————————————————————————————————
#moi writing#tony stark x reader#yandere tony stark#yandere tony stark x reader#mdb still taking over my brain as I wrote this LOL
162 notes
·
View notes
Text
One thing I think that is so insidious about the Pro-Israel narrative is that they don't even want you donating to the Palestinian cause to provide things like food or medical care for children. There is a concerted hasbara campaign to associate any NGO that provides any aid to palestinians with terrorism.
For example, if you attempt to raise money for the Palestinian Children's Relief Fund, a charity rated 4 stars by Charity Navigator, you may be linked to a page on a website called NGO Monitor. At first glance, this appears to be a neutral charity rating website similar to Charity Navigator. It's not.
Try searching any charity with no connection to the Israel-Palestine conflict on NGO Monitor, and you'll get no result.
Do a little digging, and you'll find out that NGO Monitor was founded by Gerald Steinberg, a Likud party member and former Israeli Security Council consultant. It is essentially a right-wing Israeli front posing as a legitimate charity watchdog while spreading misinformation.
Or consider this racist parody song from Israel's version of SNL. It depicts a hjiab donning woman crying and begging for money in front of an image of shelled out buildings presumably in Gaza. It then cuts away to reveal it is all a set, and her crying is acting, alluding to the Pallywood conspiracy theory. This is followed by caricatures of Hamas members swimming in riches in a luxurious hotel room in Qatar chanting "dollar bills, dollar bills" as donations pile up. The implication is clear; if you give money to Palestine, you are giving money to Hamas. The fact that this video is in English tells you who the intended audience is. It was posted on instagram by Noa Tishby, a former Israeli spokesperson.
This all reflects the true cruelty of the Israeli regime. They don't just want to harm the Palestinians; they don't want you to help them.
#hasbara#palestine#israel-palestine#free palestine#globalize the intifada#end the occupation#gaza#gazan genocide#apartheid#propaganda#pallywood#end the genocide#palestinian apartheid#ngos#charity#palestinian children's relief fund
458 notes
·
View notes
Text
Centibillionaire Elon Musk’s takeover of the former US Digital Service—now the United States DOGE Service—has been widely publicized and sanctioned by one of President Donald Trump’s many executive orders. But WIRED reporting shows that Musk’s influence extends even further, and into an even more consequential government agency.
Sources within the federal government tell WIRED that the highest ranks of the Office of Personnel Management (OPM)—essentially the human resources function for the entire federal government—are now controlled by people with connections to Musk and to the tech industry. Among them is a person who, according to an online résumé, was set to start college last fall.
Scott Kupor, a managing partner at the powerful investment firm Andreessen Horowitz, stands as Trump’s nominee to run the OPM. But already in place, according to sources, are a variety of people who seem ready to carry out Musk’s mission of cutting staff and disrupting the government.
Amanda Scales is, as has been reported, the new chief of staff at the OPM. She formerly worked in talent for xAI, Musk’s artificial intelligence company, according to her LinkedIn. Before that, she was part of the talent and operations team at Human Capital, a venture firm with investments in the defense tech startup Anduril and the political betting platform Kalshi; before that, she worked for years at Uber. Her placement in this key role, experts believe, seems part of a broader pattern of the traditionally apolitical OPM being converted to use as a political tool.
“I don't think it's alarmist to say there's a much more sophisticated plan to monitor and enforce loyalty than there was in the first term,” says Don Moynihan, a professor of public policy at the University of Michigan.
Got a Tip?
Are you a current or former employee with the Office of Personnel Management or another government agency impacted by Elon Musk? We’d like to hear from you. Using a nonwork phone or computer, contact Vittoria Elliott at [email protected] or securely at velliott88.18 on Signal.
Sources say that Riccardo Biasini, formerly an engineer at Tesla and most recently director of operations for the Las Vegas Loop at the Boring Company, Musk’s tunnel-building operation, is also at the OPM as a senior adviser to the director. (Steve Davis, the CEO of the Boring Company, is rumored to be advising Musk on cuts to be made via DOGE and was integral in Musk’s gutting of Twitter, now X, after his takeover of the company in 2022.)
According to the same sources, other people at the top of the new OPM food chain include two people with apparent software engineering backgrounds, whom WIRED is not naming because of their ages. One, a senior adviser to the director, is a 21-year-old whose online résumé touts his work for Palantir, the government contractor and analytics firm cofounded by billionaire Peter Thiel, who is its chair. (The former CEO of PayPal and a longtime Musk associate, Thiel is a Trump supporter who helped bankroll the 2022 Senate campaign of his protégé, Vice President JD Vance.) The other, who reports directly to Scales, graduated from high school in 2024, according to a mirrored copy of an online résumé and his high school’s student magazine; he lists jobs as a camp counselor and a bicycle mechanic among his professional experiences, as well as a summer role at Neuralink, Musk’s brain-computer interface company.
Among the new highers-up at the OPM is Noah Peters, an attorney whose LinkedIn boasts of his work in litigation representing the National Rifle Association and who has written for right-wing outlets like the Daily Caller and the Federalist; he is also now a senior adviser to the director. According to metadata associated with a file on the OPM website, Peters authored a January 27 memo that went out under acting OPM director Charles Ezell’s name describing how the department would be implementing one of Trump’s executive orders, “Restoring Accountability to Policy-Influencing Positions Within the Federal Workforce.” This has to do with what’s sometimes known as Schedule F—a plan to recategorize many civil service jobs as political appointees, meaning they would be tied to the specific agenda of an administration rather than viewed as career government workers. The order would essentially allow for certain career civil servants to be removed in favor of Trump loyalists by classifying them as political appointees, a key part of the Project 2025 plan for remaking the government.
“I think on the tech side, the concern is potentially the use of AI to try and engage in large-scale searches of people's job descriptions to try and identify who would be identified for Schedule F reclassification,” says Moynihan.
Other top political appointees include McLaurine Pinover, a former communications director for Republican congressman Joe Wilson and deputy communications director for Republican congressman Michael McCaul, and Joanna Wischer, a Trump campaign speechwriter.
“OPM is not a very politicized organization,” says Steven Kelman, a professor emeritus at Harvard’s John F. Kennedy School of Government. “My guess is that typically, in the past, there have been only one or maybe two political appointees in all of OPM. All the rest are career. So this seems like a very political heavy presence in an organization that is not very political.”
Another OPM memo, concerning the government’s new return-to-office mandate, appears, according to metadata, also to have been authored by someone other than Ezell: James Sherk, previously at the America First Policy Institute and author of an op-ed advocating for the president to be able to fire bureaucrats. Formerly a special assistant to the president during Trump’s first term, he is now a part of the White House Domestic Policy Council.
The return-to-office policy, according to the November Wall Street Journal op-ed authored by Musk and Vivek Ramaswamy, is explicitly geared toward forcing the attrition of federal employees.
Last week, many federal workers received test emails from the email address [email protected]. In a lawsuit filed last night, plaintiffs allege that a new email list started by the Trump administration may be compromising the data of federal employees.
“At a broadest level, the concern is that technologists are playing a role to monitor employees and to target those who will be downsized,” says Moynihan. “It is difficult in the federal government to actually evaluate who is performing well or performing poorly. So doing it on some sort of mass automated scale where you think using some sort of data analysis or AI would automate that process, I think, is an invitation to make errors.”
Last week, federal employees across the government received emails encouraging them to turn in colleagues who they believed to be working on diversity, equity, inclusion, and access initiatives (DEIA) to the OPM via the email address [email protected].
“This reminded me,” says Kelman, “of the Soviet Stalinism of turning in your friends to the government.”
The OPM did not immediately respond to a request for comment, nor did the people whom sources say now sit atop the bureaucracy.
“I am not an alarmist person,” says Kelman. “I do think that some of the things being described here are very troubling.”
69 notes
·
View notes
Note
what is the best way to get safer/more anonymous online
Ok, security and anonymity are not the same thing, but when you combine them you can enhance your online privacy.
My question is: how tech literate are you and what is your aim? As in do you live in a country where your government would benefit from monitoring private (political) conversations or do you just want to degoogle? Because the latter is much easier for the average user.
Some general advice:
Leave Windows and Mac operating systems and switch to Linux distributions like Fedora and Ubuntu (both very user friendly). Switch from Microsoft Office or Pages/Numbers/Keynote (Mac) to LibreOffice.
You want to go more hardcore with a very privacy-focused operating system? There are Whonix and Tails (portable operating system).
Try to replace all your closed source apps with open source ones.
Now, when it comes to browsers, leave Chrome behind. Switch to Firefox (or Firefox Focus if you're on mobile). Want to go a step further? Use LibreWolf (a modified version of Firefox that increases protection against tracking), Brave (good for beginners but it has its controversies), DuckDuckGo or Bromite. You like ecofriendly alternatives? Check Ecosia out.
Are you, like, a journalist or political activist? Then you probably know Tor and other anonymous networks like i2p, freenet, Lokinet, Retroshare, IPFS and GNUnet.
For whistleblowers there are tools like SecureDrop (requires Tor), GlobaLeaks (alternative to SecureDrop), Haven (Android) and OnionShare.
Search engines?
There are Startpage (obtains Google's results but with more privacy), MetaGer (open source), DuckDuckGo (partially open source), Searx (open source). You can see the comparisons here.
Check libRedirect out. It redirects requests from popular socmed websites to privacy friendly frontends.
Alternatives to YouTube that value your privacy? Odysee, PeerTube and DTube.
Decentralized apps and social media? Mastodon (Twitter alternative), Friendica (Facebook alternative), diaspora* (Google+ RIP), PixelFed (Insta alternative), Aether (Reddit alternative).
Messaging?
I know we all use shit like Viber, Messenger, Telegram, Whatsup, Discord etc. but there are:
Signal (feels like Whatsup but it's secure and has end-to-end encryption)
Session (doesn't even require a phone or e-mail address to sign up)
Status (no phone or e-mail address again)
Threema (for mobile)
Delta Chat (you can chat with people if you know their e-mail without them having to use the app)
Team chatting?
Open source options:
Element (an alternative to Discord)
Rocket.chat (good for companies)
Revolt.chat (good for gamers and a good alternative to Discord)
Video/voice messaging?
Brave Talk (the one who creates the talk needs to use the browser but the others can join from any browser)
Jami
Linphone
Jitsi (no account required, video conferencing)
Then for Tor there are various options like Briar (good for activists), Speek! and Cwtch (user friendly).
Georestrictions? You don't want your Internet Provider to see what exactly what you're doing online?
As long as it's legal in your country, then you need to hide your IP with a VPN (authoritarian regimes tend to make them illegal for a reason), preferably one that has a no log policy, RAM servers, does not operate in one of the 14 eyes, supports OpenVPN (protocol), accepts cash payment and uses a strong encryption.
NordVPN (based in Panama)
ProtonVPN (Switzerland)
Cyberghost
Mullvad (Sweden)
Surfshark (Netherlands)
Private e-mails?
ProtonMail
StartMail
Tutamail
Mailbox (ecofriendly option)
Want to hide your real e-mail address to avoid spam etc.? SimpleLogin (open source)
E-mail clients?
Thunderbird
Canary Mail (for Android and iOS)
K-9 Mail (Android)
Too many complex passwords that you can't remember?
NordPass
BitWarden
LessPass
KeePassXC
Two Factor Authenticators?
2FAS
ente Authenticator
Aegis Authenticator
andOTP
Tofu (for iOS)
Want to encrypt your files? VeraCrypt (for your disk), GNU Privacy Guard (for your e-mail), Hat.sh (encryption in your browser), Picocrypt (Desktop encryption).
Want to encrypt your Dropbox, Google Drive etc.? Cryptomator.
Encrypted cloud storage?
NordLocker
MEGA
Proton Drive
Nextcloud
Filen
Encrypted photography storage?
ente
Cryptee
Piwigo
Want to remove metadata from your images and videos? ExifCleaner. For Android? ExifEraser. For iOS? Metapho.
Cloak your images to counter facial recognition? Fawkes.
Encrypted file sharing? Send.
Do you menstruate? Do you want an app that tracks your menstrual cycle but doesn't collect your data? drip.
What about your sexual health? Euki.
Want a fitness tracker without a closed source app and the need to transmit your personal data to the company's servers? Gadgetbridge.
34 notes
·
View notes
Text
so that new trailer, hey?
alright, so the security monitor thing has a dead catnap on top of it. This symbolism leads me to believe that it's probably related to the prototype, furthering its appearance as an 'all-seeing eye' in the facility.
Playtime is either a shell company for the company denoted by the square, or the square is the true 'flower' we're meant to find - Playtime's true logo.

when Yarnaby's head splits open, the two sides of his mouth resemble two hemispheres of a brain.
it seems my lobotomy headcanon wasn't too far off. It just wasn't done to Sawyer.
The ARG website is called 'icepick'. We come to see that Quinn was a mentally disturbed orphan and, in becoming Yarnaby, had his mental acuity severely limited.
This imagery is big - Yarnaby's brain splits as he opens his mouth to attack. Yarnaby's brain splits as he takes the stance of what he has become: a monster.
In the ARG, we see that Yarnaby is lost and dejected without the presence of Sawyer, his 'master'. I still hold onto some little hope that Sawyer will somehow be alive in Ch.4, but it seems a likely narrative point that The Prototype will be able to control Yarnaby by mimicking his long-gone 'master's' voice.
Imagine that you were a post-human, animalistic being, groomed for one purpose: to care only about one man. That man is, quote, "removed", and you are left lost and aimless. Then, a divine mechanical being you cannot comprehend speaks to you in his voice.
I think that Yarnaby will believe, or choose to believe, that Sawyer is truly commanding him.
We still have no definitive proof one way or the other on who the player is. How wild would it be if we played as Sawyer. Probably unlikely considering how Poppy addresses us in Ch.3 ("to get revenge on the monsters who've tortured you!"), but how cool of a narrative would it be if Yarnaby's allegiance has so fully swayed to the Prototype's version of Sawyer, that when his master returns, he follows the Prototype's command to attack.
Hell. Maybe that could be how Sawyer dies in the HoJ. He abandons Yarnaby and the Prototype comforts him by speaking to him in Sawyer's voice. Then when he takes control in the HoJ, orders him to kill Sawyer when Sawyer retreats back to his 'bodyguard' for protection from the monsters he's created.
#poppy playtime#rambles#ppt#harley sawyer#poppy playtime theory#ppt 4#poppy playtime chapter 4#ppt theory#ppt speculation#poppy playtime 4#ppt arg#poppy playtime arg#yarnaby
89 notes
·
View notes
Text
Get Informed
Join the Trump Accountability War Room, which offers fact sheets on the bad actors in Donald Trump’s Cabinet and primers on their policies, and the AFL-CIO’s Department of People Who Work for a Living, which tracks how funding cuts are affecting federal workers.
Follow MeidasTouch Network, a pro-democracy news organization with a massive social media presence and a suite of podcasts. MeidasTouch personalities such as Leigh McGowan (a.k.a. PoliticsGirl) and Aaron Parnas have reinvigorated the resistance on TikTok, Instagram, and Substack.
Monitor constitutional oversteps and the legal challenges to Trump’s executive orders with Lawfare or Just Security.
Get Strategic
Explore Choose Democracy’s interactive Choose Your Own Adventure activity, which asks you to “guide us towards a better, more humane democracy.” In “What can I do to fight this coup?,” the group offers drop-down menus of resistance techniques arranged by level of difficulty. It also provides training agendas on everything from de-escalation to mutual aid.
Study Indivisible’s Practical Guide to Democracy on the Brink, which shares strategies for defending the democratic process against authoritarian creep and a list of tactics constituents can use to pressure their elected officials.
Review the tool kits, how-to manuals, and informational leaflets at Build the Resistance’s comprehensive, crowdsourced resource hub.
Get Outside
Check NoVoiceUnheard, which compiles peaceful protest opportunities, viewable by state or by organization, across the country. For an even more expansive inventory, look at The Big List of Protests.
Brush up on your rights at the ACLU’s protesters’ rights page, which shares information on the kinds of locations where you are protected, when you need a permit, and what to do during a police encounter. Call the Resistance Hotline at 1-844-NVDA-NOW or email [email protected] with your questions, and you’ll get a response within 24 hours.
Enlist with the ACLU’s “grassroots army” of volunteers working to safeguard civil liberties. Visit the program’s website for a wealth of actions, including signing the organization’s petitions, that will take just a few minutes.
Get out Your Wallet
Donate to legal defense and bail funds. The National Bail Fund Network maintains a directory of pretrial bail funds and immigration bond funds.
Get on the Phone
Call Congress using 5 Calls, which provides policy guides, office numbers for your representatives, and call scripts.
Get in the Way
Flood the Office of Personnel Management’s anti-DEI tip line at [email protected] to protect federal employees targeted by the Trump administration’s crackdown. —Kate Mabus
Timothy Noah
Timothy Noah is a New Republic staff writer and author of The Great Divergence: America’s Growing Inequality Crisis and What We Can Do About It.
32 notes
·
View notes