#SQL Server transaction logging
Explore tagged Tumblr posts
Text
Effective Strategies for Auditing Inserts, Updates, and Deletes in SQL Server Without Traditional Auditing Features
In the dynamic world of database management, ensuring the integrity and tracking of data changes is paramount. Interestingly, SQL Server professionals often seek methods to audit insert, update, and delete (IUD) transactions without relying on built-in audit features. This article explores practical T-SQL code examples and applications to achieve this, providing a robust alternative for database…
View On WordPress
#database change tracking#SQL IUD operations#SQL Server monitoring#SQL Server transaction logging#T-SQL audit techniques
0 notes
Text
⏱Hangfire + Serilog: How EasyLaunchpad Handles Jobs and Logs Like a Pro

Modern SaaS applications don’t run on user actions alone.
From sending emails and processing payments to updating user subscriptions and cleaning expired data, apps need background tasks to stay efficient and responsive.
That’s why EasyLaunchpad includes Hangfire for background job scheduling and Serilog for detailed, structured logging — out of the box.
If you’ve ever wondered how to queue, manage, and monitor background jobs in a .NET Core application — without reinventing the wheel — this post is for you.
💡 Why Background Jobs Matter
Imagine your app doing the following:
Sending a password reset email
Running a weekly newsletter job
Cleaning abandoned user sessions
Retrying a failed webhook
Syncing data between systems
If these were handled in real-time within your controller actions, it would:
Slow down your app
Create a poor user experience
Lead to lost or failed transactions under load
Background jobs solve this by offloading non-critical tasks to a queue for asynchronous processing.
🔧 Hangfire: Background Job Management for .NET Core
Hangfire is the gold standard for .NET Core background task processing. It supports:
Fire-and-forget jobs
Delayed jobs
Recurring jobs (via cron)
Retry logic
Job monitoring via a dashboard
Best of all, it doesn’t require a third-party message broker like RabbitMQ. It stores jobs in your existing database using SQL Server or any other supported backend.
✅ How Hangfire Is Integrated in EasyLaunchpad
When you start with EasyLaunchpad:
Hangfire is already installed via NuGet
It’s preconfigured in Startup.cs and appsettings.json
The dashboard is live and secured under /admin/jobs
Common jobs (like email dispatch) are already using the queue
You don’t have to wire it up manually — it’s plug-and-play.
Example: Email Queue
Let’s say you want to send a transactional email after a user registers. Here’s how it’s done in EasyLaunchpad:
_backgroundJobClient.Enqueue(() =>
_emailService.SendWelcomeEmailAsync(user.Id));
This line of code:
Queues the email job
Executes it in the background
Automatically retries if it fails
Logs the event via Serilog
🛠 Supported Job Types
Type and Description:
Fire-and-forget- Runs once, immediately
Delayed- Runs once after a set time (e.g., 10 minutes later)
Recurring- Scheduled jobs using CRON expressions
Continuations- Run only after a parent job finishes successfully
EasyLaunchpad uses all four types in various modules (like payment verification, trial expiration notices, and error logging).
🖥 Job Dashboard for Monitoring
Hangfire includes a web dashboard where you can:
See pending, succeeded, and failed jobs
Retry or delete failed jobs
Monitor job execution time
View exception messages
In EasyLaunchpad, this is securely embedded in your admin panel. Only authorized users with admin access can view and manage jobs.
🔄 Sample Use Case: Weekly Cleanup Job
Need to delete inactive users weekly?
In EasyLaunchpad, just schedule a recurring job:
_recurringJobManager.AddOrUpdate(
“InactiveUserCleanup”,
() => _userService.CleanupInactiveUsersAsync(),
Cron.Weekly
);
Set it and forget it.
🧠 Why This Is a Big Deal for Devs
Most boilerplates don’t include job scheduling at all.
In EasyLaunchpad, Hangfire is not just included — it’s used throughout the platform, meaning:
You can follow working examples
Extend with custom jobs in minutes
Monitor, retry, and log with confidence
You save days of setup time, and more importantly, you avoid production blind spots.
📋 Logging: Meet Serilog
Of course, background jobs are only useful if you know what they’re doing.
That’s where Serilog comes in.
In EasyLaunchpad, every job execution is logged with:
Timestamps
Job names
Input parameters
Exceptions (if any)
Success/failure status
This structured logging ensures you have a full audit trail of what happened — and why.
Sample Log Output
{
“Timestamp”: “2024–07–20T14:22:10Z”,
“Level”: “Information”,
“Message”: “Queued email job: PasswordReset for userId abc123”,
“JobType”: “Background”,
“Status”: “Success”
}
You can send logs to:
Console (for dev)
File (for basic prod usage)
External log aggregators like Seq, Elasticsearch, or Datadog
All of this is built into EasyLaunchpad’s logging layer.
🧩 How Hangfire and Serilog Work Together
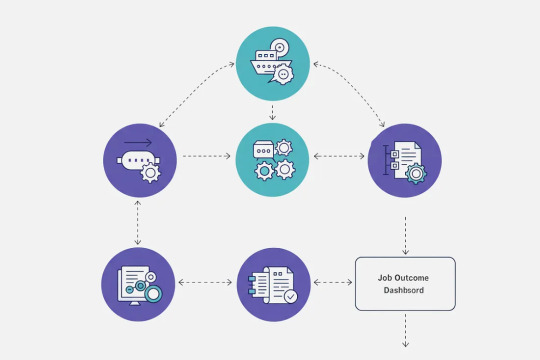
Here’s a quick visual breakdown:
Job Triggered → Queued via Hangfire
Job Executed → Email sent, cleanup run, webhook processed
Job Outcome Logged → Success or error captured by Serilog
Job Visible in Dashboard → Retry if needed
Notifications Sent (optional) → Alert team or log activity via admin panel
This tight integration ensures your background logic is reliable, observable, and actionable.
💼 Real-World Use Cases You Can Build Right Now
-Feature and the Background Job
Welcome Emails- Fire-and-forget
Trial Expiration- Delayed
Subscription Cleanup- Recurring
Payment Webhook Retry- Continuation
Email Digest- Cron-based job
System Backups- Nightly scheduled
Every one of these is ready to be implemented using the foundation in EasyLaunchpad.
✅ Why Developers Love It
-Feature and the Benefit
Hangfire Integration- Ready-to-use queue system
Preconfigured Retry- Avoid lost messages
Admin Dashboard- See and manage jobs visually
Structured Logs- Full traceability
Plug-and-Play Jobs- Add your own in minutes
🚀 Final Thoughts
Robust SaaS apps aren’t just about UI and APIs — they’re also about what happens behind the scenes.
With Hangfire + Serilog built into EasyLaunchpad, you get:
A full background job system
Reliable queuing with retry logic
Detailed, structured logs
A clean, visual dashboard
Zero config — 100% production-ready
👉 Launch smarter with EasyLaunchpad today. Start building resilient, scalable applications with background processing and logging already done for you. 🔗 https://easylaunchpad.com
#.net development#.net boilerplate#Hangfire .net Example#easylaunchpad#Serilog Usage .net#Background Jobs Logging#prebuilt apps#Saas App Development
2 notes
·
View notes
Text
Log Shipping (or LS) in SQL Server is a disaster recovery solution that automates the backup, copy, and restore of transaction logs from a primary server to a secondary server. Let's Explore Deeply:
https://madesimplemssql.com/log-shipping-in-sql-server/
Follow us on FB: https://www.facebook.com/profile.php?id=100091338502392
&
Join our Group: https://www.facebook.com/groups/652527240081844
2 notes
·
View notes
Text
Magento 2 Security Extension — Protect Your Store from the Inside Out
Running an eCommerce business on Magento 2 gives you power, flexibility, and performance. But with great power comes great responsibility—especially when it comes to security. Magento is a widely used platform, making it a common target for cyber threats, data breaches, and fraud. That’s why installing a Magento 2 Security Extension is one of the smartest decisions any store owner can make.
This article explores how security extensions safeguard your Magento 2 store, how address validation plays a key role in fraud prevention, and which features you should prioritize when choosing the right security solution.
Why Magento 2 Needs Security Enhancements
Magento 2 offers solid built-in security features, including two-factor authentication (2FA), file system permissions, and CAPTCHA. However, these tools aren’t always enough. Most store owners still face threats like:
Fake user registrations
Fraudulent orders
Bot attacks
SQL injections
Data tampering
Checkout manipulation
Because Magento 2 is open-source and highly customizable, vulnerabilities can emerge through third-party modules, outdated plugins, or improper server configurations. A dedicated security extension provides an extra layer of defense against such risks.
The Hidden Threat: Invalid or Fake Addresses
One of the most overlooked security gaps in Magento 2 stores is invalid or fake address entries during checkout. Cybercriminals and bots often use fake addresses to:
Test stolen credit cards
Place high-risk or fraudulent orders
Flood your system with fake data
Manipulate shipping or billing info to trigger chargebacks
This is where address validation steps in—not just as a logistics tool, but as a powerful security filter.
How Address Validation Boosts Magento 2 Security
An address validation extension like the one offered by EcomPlugins doesn't just help verify locations for delivery—it helps verify the user’s intent and legitimacy.
Here’s how it strengthens your store’s security:
1. Detects Suspicious Address Patterns
Invalid zip codes, incomplete fields, or mismatched city-state combinations are red flags. Automatically detecting these issues helps you block risky transactions before they occur.
2. Reduces Chargebacks and Payment Disputes
A significant number of fraudulent orders use fake billing addresses. Real-time validation ensures that billing information aligns with what payment gateways expect, reducing the risk of false disputes.
3. Prevents Fake User Registrations
If your extension validates addresses at registration (or checkout), it becomes harder for bots or scammers to create dummy accounts with fake data.
4. Enhances Data Integrity
Address validation ensures that your CRM, analytics tools, and marketing automations only work with clean, verified data—essential for both security and performance.
Features to Look for in a Magento 2 Security Extension
While address validation is a great start, here are additional features to look for in a well-rounded Magento 2 security extension:
1. Two-Factor Authentication (2FA)
Adds an extra layer of login protection by requiring a secondary code, usually sent to a device.
2. IP Whitelisting and Blacklisting
Control which IPs can access your admin panel and block suspicious or high-risk addresses.
3. Login Attempt Limits
Prevent brute-force attacks by locking users out after a certain number of failed login attempts.
4. Admin URL Customization
Change your default admin URL so that bots and hackers can't easily guess where to target attacks.
5. Firewall Rules
Use application-level firewalls to filter traffic, restrict bots, and block known attackers.
6. Activity Logs and Alerts
Monitor admin and customer activity in real-time. Automated alerts notify you of suspicious behavior like multiple failed logins or bulk data exports.
EcomPlugins: Secure Checkout with Built-in Address Validation
If you're looking for a lightweight yet powerful solution to improve your Magento 2 store’s security, EcomPlugins’ Magento 2 Address Validation extension is a great place to start.
Here’s what sets it apart:
USPS-based real-time address verification
Validation for both billing and shipping addresses
Auto-suggestions for correcting typos and missing details
Support for U.S. merchants and USPS standards
Quick installation and Magento 2 compatibility
Although primarily focused on logistics, this extension acts as a security filter by preventing invalid or malicious addresses from slipping through your checkout.
Why Security = Trust = Higher Conversions
Security isn’t just about protecting your site—it’s about protecting your customers. Shoppers are becoming more cautious about who they buy from. Even a small sign of weakness, like a failed order or shipping error, can reduce trust and hurt conversion rates.
By using a security-enhancing tool like an address validation extension, you demonstrate professionalism, protect customer data, and improve fulfillment accuracy—all of which build long-term trust.
Final Thoughts
Magento 2 is a powerful eCommerce platform, but it’s not invulnerable. Cyber threats are evolving every day, and relying solely on default security settings is risky. A Magento 2 Security Extension—especially one with built-in address validation—can be your first line of defense against fraudulent behavior, shipping errors, and data integrity issues.
For store owners who want to secure their operations and deliver a flawless checkout experience, EcomPlugins’ Magento 2 Checkout Address Validation extension offers the perfect blend of security, usability, and logistics support.
Protect your store from the inside out—start with smarter address validation today.
0 notes
Text
SQL Interview Questions for Database Developers and Administrators

Structured Query Language, or SQL, is the foundation of database management. Whether you're a database developer crafting robust schemas and queries or a database administrator ensuring performance, security, and data integrity, proficiency in SQL is essential. This blog will walk you through some of the most commonly asked SQL interview questions tailored for both developers and DBAs (Database Administrators), with clear examples and explanations.
Why SQL Interview Questions Matter
SQL is not just about writing SELECT queries. It's about understanding how to model data, query efficiently, prevent anomalies, and secure sensitive information. Interviewers test both practical SQL skills and conceptual understanding. Whether you're a fresher or experienced professional, preparing well for SQL questions is crucial for landing a job in roles like:
Database Developer
Data Analyst
Data Engineer
DBA (Database Administrator)
Backend Developer
Basic SQL Interview Questions
1. What is SQL?
SQL stands for Structured Query Language. It is used to store, retrieve, manipulate, and manage data in relational databases such as MySQL, SQL Server, PostgreSQL, and Oracle.
2. What is the difference between DELETE, TRUNCATE, and DROP?
Command Description Can Rollback DELETE Deletes specific rows using a WHERE clause Yes TRUNCATE Removes all rows from a table without logging No DROP Deletes the entire table (structure + data) No
3. What is a Primary Key?
A Primary Key is a column (or combination of columns) that uniquely identifies each record in a table. It cannot contain NULL values and must be unique.CREATE TABLE employees ( id INT PRIMARY KEY, name VARCHAR(100) );
4. What are the different types of joins in SQL?
INNER JOIN: Returns records with matching values in both tables
LEFT JOIN: Returns all records from the left table, and matched ones from the right
RIGHT JOIN: Returns all records from the right table, and matched ones from the left
FULL OUTER JOIN: Returns all records when there is a match in one of the tables
Intermediate SQL Interview Questions
5. What is normalization? Explain its types.
Normalization is the process of organizing data to reduce redundancy and improve integrity. Common normal forms:
1NF: Atomic columns
2NF: Remove partial dependencies
3NF: Remove transitive dependencies
6. What is an index in SQL?
An index improves the speed of data retrieval. It is similar to the index in a book.CREATE INDEX idx_lastname ON employees(last_name);
Tip: Overusing indexes can slow down write operations.
7. What is a subquery?
A subquery is a query nested inside another query.SELECT name FROM employees WHERE salary > (SELECT AVG(salary) FROM employees);
8. What are aggregate functions in SQL?
Functions that operate on sets of values and return a single value:
SUM()
AVG()
COUNT()
MAX()
MIN()
Advanced SQL Interview Questions (For Developers & DBAs)
9. What is a stored procedure?
A stored procedure is a precompiled set of SQL statements stored in the database. CREATE PROCEDURE GetEmployeeCount AS BEGIN SELECT COUNT(*) FROM employees; END;
Used for code reusability and performance optimization.
10. How do transactions work in SQL?
A transaction is a unit of work performed against a database. It follows ACID properties:
Atomicity
Consistency
Isolation
Durability
BEGIN TRANSACTION; UPDATE accounts SET balance = balance - 100 WHERE id = 1; UPDATE accounts SET balance = balance + 100 WHERE id = 2; COMMIT;
11. What is deadlock and how do you resolve it?
A deadlock occurs when two or more transactions block each other by holding locks on resources the other transactions need. To resolve:
Set proper lock timeouts
Use consistent locking order
Implement deadlock detection
12. What are triggers in SQL?
A trigger is a special stored procedure that runs automatically in response to certain events (INSERT, UPDATE, DELETE).CREATE TRIGGER before_insert_trigger BEFORE INSERT ON employees FOR EACH ROW BEGIN SET NEW.created_at = NOW(); END;
13. How do you optimize a slow-running query?
Use EXPLAIN to analyze the query plan
Create indexes on frequently searched columns
Avoid SELECT *
Use joins instead of subqueries where appropriate
Limit results using LIMIT or TOP clauses
SQL Questions for DBA-Specific Roles
14. What are the responsibilities of a DBA related to SQL?
Creating and managing databases and users
Backup and recovery
Performance tuning
Monitoring database health
Ensuring data security and access control
15. How do you implement backup and recovery in SQL Server?
Backup BACKUP DATABASE myDB TO DISK = 'D:\Backup\myDB.bak'; -- Restore RESTORE DATABASE myDB FROM DISK = 'D:\Backup\myDB.bak';
Conclusion
SQL remains the backbone of modern data management and application development. These SQL interview questions for database developers and administrators are just a sample of what you may encounter during a technical interview. To excel, practice queries, understand the theory behind relational database design, and stay updated with the latest SQL standards and features.
#SQLInterviewQuestions#DatabaseDeveloper#DBA#SQLQueries#StoredProcedures#SQLJoins#SQLOptimization#DatabaseAdmin#TechInterviews
0 notes
Text
What are different components of SAP HANA or explain Architecture?
SAP HANA (High-Performance Analytic Appliance) is an in-memory, column-oriented, relational database management system designed for high-speed data processing and real-time analytics. Its architecture comprises several key components:
Index Server: The core component that contains the actual data engines for processing SQL/MDX, transaction management, and query execution. It handles all the database operations.
Name Server: Maintains metadata and topology information of the distributed landscape and manages the names and locations of HANA instances.
Preprocessor Server: Used for text processing and handles extraction of information from unstructured data (like PDFs).
XS Engine (Extended Application Services): Allows development and hosting of web-based applications within the HANA platform.
SAP HANA Studio: An Eclipse-based tool for administration, modeling, and data provisioning.
Persistence Layer: Manages data storage and ensures durability using save-points and logs in case of system failure.
Connection & Integration Layer: Supports connectivity via JDBC, ODBC, and other interfaces for third-party applications.
SAP HANA’s in-memory processing and parallel architecture provide extremely fast performance, making it suitable for both OLAP and OLTP workloads.

Anubhav Trainings provides in-depth, hands-on training on SAP HANA architecture, covering each component with real-time scenarios. With expert trainer Anubhav Oberoy, learners not only grasp theory but also gain practical insights, making them job-ready in today’s competitive SAP market.
#online sap training#online free sap training#sap ui5 training#online sap ui5 training#ui5 fiori training#free sap training#sap abap training
0 notes
Text
Mastering PHP Application Monitoring: Best Practices for 2025

Introduction
PHP powers over 75% of the web today, making it one of the most widely used server-side languages. From WordPress sites to complex Laravel applications, developers rely on PHP to build fast, scalable solutions. But with growing complexity comes the need for real-time visibility and control. This is where application monitoring plays a critical role.
Monitoring isn't just about tracking uptime, it's about understanding how your code behaves in production, identifying slow queries, spotting memory leaks, and proactively fixing issues before users even notice them. In this blog, we’ll explore the best practices for PHP application monitoring and how you can implement them effectively.
12 Best Practices for PHP Application Monitoring
1. Upgrade to PHP 8+
Running on the latest version ensures better performance, error handling, and compatibility with modern tools. PHP 8’s JIT compiler alone can improve execution speed significantly.
2. Follow PSR Coding Standards
Using standards like PSR-3 (logging) and PSR-4 (autoloading) leads to cleaner, more structured code that monitoring tools can process more efficiently.
3. Use Descriptive Functions and Logs
Functions like processData() aren’t helpful when debugging. Instead, use meaningful names like generateMonthlyReport() and ensure log messages are clear and contextual.
4. Leverage Popular Frameworks
Frameworks such as Laravel, Symfony, or CodeIgniter come with built-in structure and middleware support, which integrate smoothly with APM solutions.
5. Manage Dependencies with Composer
Locking versions through Composer ensures consistent environments across staging and production, reducing unexpected errors during deployment.
6. Add Caching Layers
Implement opcode, database, and object caching to reduce server load and accelerate response times.
7. Set Up Smart Alerts
Avoid alert fatigue. Configure alerts for thresholds that truly matter like a sustained increase in response time or sudden spike in 500 errors.
8. Conduct Security Monitoring
Monitor failed login attempts, suspicious user behavior, or error messages that might indicate vulnerabilities.
9. Use CI/CD Tags for Deployments
Tagging releases helps correlate performance changes with specific deployments, making it easier to roll back or debug regressions.
10. Keep Monitoring Agents Updated
Regularly check for updates to ensure compatibility with your PHP version and frameworks.
11. Profile Real User Traffic
Use profiling tools in production to identify bottlenecks during peak usage not just in local or staging environments.
12. Optimize SQL Queries
Poorly indexed or long-running queries can slow down your app. APM tools can pinpoint these with exact timings and stack traces.
Why Choose Atatus for PHP Monitoring?
Atatus is a full-stack APM and error-tracking platform that offers deep insights into PHP applications. Here’s why it stands out:
Real-time performance monitoring for PHP 7.x and 8.x apps
Transaction tracing down to database queries, external calls, and slow functions
Easy integration with Laravel, Symfony, CodeIgniter, and other frameworks
Custom alerting, dashboards, and logs in one unified interface
Error tracking with stack traces and user context to speed up debugging
Atatus helps developers detect issues early, optimize code paths, and ensure smooth performance at scale.
Conclusion
Effective monitoring is key to building fast, stable, and scalable PHP applications. By following these best practices and choosing the right tool like Atatus, you can gain full visibility into your app's performance, reduce downtime, and deliver a seamless user experience.
Whether you're managing a startup project or an enterprise-grade application, observability isn't optional, it's essential. Implementing a strong monitoring strategy today will lead to fewer production issues, faster debugging, and more confident development tomorrow.
Originally published by https://www.atatus.com/
#php monitoring#php monitoring best practices#What is PHP Monitoring#php applications#PHP Application Monitoring#PHP apm#php application performance monitoring tools#php monitoring solution#php application monitoring tools#php application performance#php performance monitoring tool#php monitoring tools#php performance monitor#php monitor#apm for php#php apm monitoring#php monitoring tool#php monitoring software#monitor php application performance#apm php#php application monitoring tool#php application performance mangement#monitoring php performance#php app monitoring#php distributed tracing
0 notes
Text
How Oracle GoldenGate works
Oracle GoldenGate operates by capturing changes directly from the transaction logs of source databases. It supports both homogeneous and heterogeneous environments, enabling real-time data replication across different types of databases, such as Oracle, MySQL, SQL Server, PostgreSQL, and more. Oracle GoldenGate Data Flow Explanation Target DatabaseThis is the destination where the replicated…
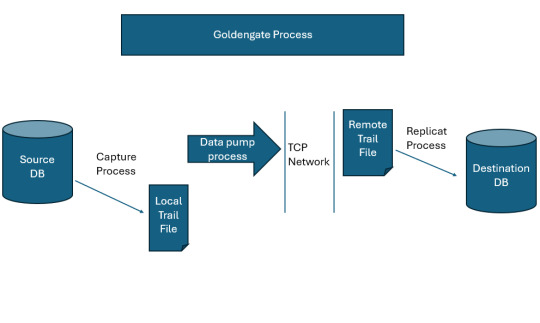
View On WordPress
0 notes
Text
Multiple Transaction Log Files Per Database?
Learn when to use multiple transaction log files per SQL Server database and the pros and cons.
Are you wondering whether it’s a good idea to have more than one transaction log file per database in SQL Server? In this article, we’ll explore the pros and cons of using multiple log files and explain when it can make sense. We’ll also show you how to remove extra log files if needed. By the end, you’ll have a clear understanding of SQL Server transaction log best practices. What are…

View On WordPress
#database performance#multiple log files#shrink transaction log#sql server transaction log#transaction log best practices
0 notes
Text

Key WooCommerce Security Tips for 2025
1. Use Strong Passwords and Enable Two-Factor Authentication (2FA)
A weak password is often the first point of vulnerability for any website. To protect your WooCommerce store, ensure that you and your team members use strong, unique passwords for all accounts related to your store. Additionally, enabling two-factor authentication (2FA) adds an extra layer of protection, requiring a second verification step when logging in.
While 2FA may seem like an added hassle, it is a powerful tool that prevents unauthorized access, even if someone obtains your password. Implementing 2FA will drastically reduce the likelihood of a security breach.
2. Keep WordPress, WooCommerce, and Plugins Updated
Regular updates to WordPress, the WooCommerce plugin, and any other installed plugins are critical for maintaining security. These updates often include security patches to fix newly discovered vulnerabilities. By updating your software regularly, you ensure that your store is protected against the latest threats.
If you don't have the time or expertise to handle updates yourself, consider seeking WooCommerce Development Services to keep your store secure and functioning smoothly. A professional team can handle the updates while ensuring no disruption to your store’s operations.
3. Implement SSL Encryption for Secure Transactions
SSL (Secure Socket Layer) certificates encrypt sensitive data that flows between the server and the user’s browser. This encryption ensures that your customers’ personal and financial details are protected. In 2025, having an SSL certificate isn’t just a security measure—it’s also essential for maintaining customer trust and improving your site’s SEO ranking.
If you're unsure how to integrate SSL encryption, a WooCommerce Developer can help set it up to ensure secure transactions and smooth customer experiences.
4. Install a Web Application Firewall (WAF)
A Web Application Firewall (WAF) acts as a barrier between your WooCommerce store and malicious traffic. It filters out harmful requests, preventing hackers from exploiting vulnerabilities in your site’s code. Implementing a WAF can block attacks such as SQL injection, cross-site scripting (XSS), and brute-force login attempts, which are common methods used by cybercriminals.
To configure the best WAF for your store, you can work with professionals who specialize in website security.
5. Backup Your Store Regularly
Data loss is one of the most detrimental effects of a cyberattack. If your store is compromised or experiences a system failure, having a recent backup ensures that you can restore your website with minimal downtime and data loss. Regular backups also give you peace of mind knowing that even in the worst-case scenario, you can recover your site quickly.
To streamline this process, WordPress Support Services often include backup solutions, providing continuous backups to keep your store secure and your data safe.
6. Limit Login Attempts
Brute force attacks involve hackers attempting to guess your login credentials by trying different combinations repeatedly. One effective way to prevent these attacks is by limiting the number of failed login attempts before temporarily locking out the user. This drastically reduces the chances of a hacker successfully gaining access to your store.
This is a simple yet effective security measure, and integrating it into your site can be done by a WooCommerce Developer who can ensure the right settings are in place to block these types of attacks.
Ongoing Maintenance and Monitoring for WooCommerce Security
Maintaining a secure WooCommerce store is an ongoing process. Regular security checks, audits, and proactive monitoring are essential to keep your site protected. Without routine maintenance, new vulnerabilities can arise, and hackers will always find new ways to exploit them.
By leveraging WordPress Website Maintenance Services, you can ensure that your store is continually monitored and updated, helping to safeguard it from emerging threats.
Conclusion
In 2025, the security of your WooCommerce store should be a top priority. By adopting strong passwords, implementing SSL certificates, enabling two-factor authentication, and keeping your software up to date, you can significantly reduce the risk of a breach.
For more advanced security measures and ongoing support, working with WooCommerce Development Services and WordPress Support Services ensures that your site remains secure, protected from the latest threats, and optimized for performance.
Let’s work together to make sure your WooCommerce store is as secure as possible in 2025 and beyond.
1 note
·
View note
Text
🚀 Unlock the Power of SQL TRUNCATE 🚀
Looking to quickly remove all records from a table without affecting its structure? 🤔
SQL TRUNCATE is the go-to command! It’s faster and more efficient than DELETE because it:
✅ Removes all data from a table in a snap ✅ Doesn’t log individual row deletions, improving performance ✅ Resets auto-increment counters (in some databases) ✅ Doesn't fire triggers (like DELETE does)
⚠️ Warning: You can’t roll it back once executed (unless inside a transaction).
Syntax:
TRUNCATE TABLE student;
Perfect for situations where you need a fresh start! 🧹
Want to dive deeper into SQL TRUNCATE and see how it can optimize your workflow? Check out the full post below! 🔗👇
0 notes
Text
Bhojon Nulled Script 3.0

Bhojon Nulled Script – The Ultimate Restaurant Management Solution If you're searching for a seamless, high-performance restaurant management system without spending a fortune, look no further than the Bhojon Nulled Script. Designed to simplify and elevate your restaurant operations, Bhojon delivers the perfect combination of user-friendly features, sleek UI, and top-tier functionality—all available for free through our platform. Why Choose Bhojon Nulled Script? The Bhojon Nulled Script is a complete digital restaurant management package that automates your day-to-day activities while offering a professional web presence. Whether you’re managing a local diner or a chain of restaurants, Bhojon gives you the tools you need to control operations efficiently, streamline orders, manage staff, and track sales effortlessly—all under one intuitive interface. Detailed Product Description Developed with the modern restaurateur in mind, Bhojon is packed with a range of robust features to ensure full control over your restaurant’s ecosystem. It includes everything from point-of-sale (POS) capabilities and inventory management to food ordering systems and multi-branch handling. And now, with the Bhojon Nulled Script, you can enjoy these premium features without paying premium prices. The script includes both frontend and backend modules, ensuring customers and staff can interact with the system efficiently. The responsive design ensures flawless performance on desktops, tablets, and smartphones, keeping your business connected at all times. Technical Specifications Language: PHP (Laravel Framework) Database: MySQL Compatibility: Cross-browser and mobile-responsive Modules: POS, Online Order, Inventory, Reporting, Admin Dashboard Multi-branch Support: Yes Features and Benefits POS System: Easy-to-use point-of-sale functionality for quick and accurate transactions. Multi-language Support: Serve customers in their preferred language with built-in localization options. Delivery & Dine-in Modules: Manage takeaway, delivery, and dine-in orders effortlessly. Comprehensive Reporting: Gain valuable insights into sales, customer behavior, and staff performance. Inventory Management: Keep track of stock levels and avoid shortages with smart inventory tools. Staff Role Management: Define roles and responsibilities clearly within the system. Use Cases The Bhojon Nulled Script is ideal for: Independent Restaurants Food Chains & Franchises Cafés & Coffee Shops Cloud Kitchens Food Trucks How to Install and Use Bhojon Nulled Script Download the Bhojon from our secure website. Unzip the package and upload the contents to your web server. Create a MySQL database and import the provided SQL file. Update the database credentials in the .env file. Run the installation script by visiting your domain in a browser. Log in to your admin dashboard and configure your restaurant settings. In just a few steps, you’ll have a fully operational restaurant management system at your fingertips. FAQs Is the Bhojon Nulled Script safe to use? Yes. Our version of the Bhojon Nulled Script is clean, tested, and regularly updated to ensure stability and security. Can I use Bhojon for multiple restaurants? Absolutely. Bhojon supports multi-branch functionality, allowing you to manage multiple restaurant locations from a single dashboard. Is technical support included? As this is a nulled script, official support is not included. However, we provide comprehensive documentation and community forums for assistance. Do I need coding skills to use it? No. Bhojon is designed for ease of use, with an intuitive interface and detailed setup instructions that require no programming knowledge. Download Bhojon Nulled Script Now Don't let budget constraints limit your restaurant's potential. Download the Bhojon today and experience the power of premium restaurant management tools—completely free of cost. Explore more powerful tools like the All in One SEO Pack Pro to further boost your website’s performance and visibility.
For a full-featured WordPress theme designed for multipurpose use, check out kallyas NULLED—a flexible, visually stunning theme perfect for business websites.
0 notes
Text
Aurora DSQL: Amazon’s Fastest Serverless SQL Solution

Amazon Aurora DSQL
Availability of Amazon Aurora DSQL is announced. As the quickest serverless distributed SQL database, it provides high availability, almost limitless scalability, and low infrastructure administration for always-accessible applications. Patching, updates, and maintenance downtime may no longer be an operational burden. Customers were excited to get a preview of this solution at AWS re:Invent 2024 since it promised to simplify relational database issues.
Aurora DSQL architecture controlled complexity upfront, according to Amazon.com CTO Dr. Werner Vogels. Its architecture includes a query processor, adjudicator, journal, and crossbar, unlike other databases. These pieces grow independently to your needs, are cohesive, and use well-defined APIs. This architecture supports multi-Region strong consistency, low latency, and global time synchronisation.
Your application can scale to meet any workload and use the fastest distributed SQL reads and writes without database sharding or instance upgrades. Aurora DSQL's active-active distributed architecture provides 99.999 percent availability across many locations and 99.99 percent in one. An application can read and write data consistently without a Region cluster endpoint.
Aurora DSQL commits write transactions to a distributed transaction log in a single Region and synchronously replicates them to user storage replicas in three Availability Zones. Cluster storage replicas are distributed throughout a storage fleet and scale automatically for best read performance. One endpoint per peer cluster region Multi-region clusters boost availability while retaining resilience and connection.
A peered cluster's two endpoints perform concurrent read/write operations with good data consistency and provide a single logical database. Third regions serve as log-only witnesses without cluster resources or endpoints. This lets you balance connections and apps by speed, resilience, or geography to ensure readers always see the same data.
Aurora DSQL benefits event-driven and microservice applications. It builds enormously scalable retail, e-commerce, financial, and travel systems. Data-driven social networking, gaming, and multi-tenant SaaS programs that need multi-region scalability and reliability can use it.
Starting Amazon Aurora DSQL
Aurora DSQL is easy to learn with console expertise. Programmable ways with a database endpoint and authentication token as a password or JetBrains DataGrip, DBeaver, or PostgreSQL interactive terminal are options.
Select “Create cluster” in the console to start an Aurora DSQL cluster. Single-Region and Multi-Region setups are offered.
Simply pick “Create cluster” for a single-Region cluster. Create it in minutes. Create an authentication token, copy the endpoint, and connect with SQL. CloudShell, Python, Java, JavaScript, C++, Ruby,.NET, Rust, and Golang can connect. You can also construct example apps using AWS Lambda or Django and Ruby on Rails.
Multi-region clusters need ARNs to peer. Open Multi-Region, select Witness Region, and click “Create cluster” for the first cluster. The ARN of the first cluster is used to construct a second cluster in another region. Finally, pick “Peer” on the first cluster page to peer the clusters. The “Peers” tab contains peer information. AWS SDKs, CLI, and Aurora DSQL APIs allow programmatic cluster creation and management.
In response to preview user comments, new features were added. These include easier AWS CloudShell connections and better console experiences for constructing and peering multi-region clusters. PostgreSQL also added views, Auto-Analyze, and unique secondary indexes for tables with existing data. Integration with AWS CloudTrail for logging, Backup, PrivateLink, and CloudFormation was also included.
Aurora DSQL now supports natural language communication between the database and generative AI models via a Model Context Protocol (MCP) server to boost developer productivity. Installation of Amazon Q Developer CLI and MCP server allows the CLI access to the cluster, allowing it to investigate schema, understand table structure, and conduct complex SQL queries without integration code.
Accessibility
As of writing, Amazon Aurora DSQL was available for single- and multi-region clusters (two peers and one witness region) in AWS US East (N. Virginia), US East (Ohio), and US West (Oregon) Regions. It was available for single-Region clusters in Ireland, London, Paris, Osaka, and Tokyo.
Aurora DSQL bills all request-based operations, such as read/write, monthly using a single normalised billing unit, the Distributed Processing Unit. Total database size, in gigabytes per month, determines storage costs. You pay for one logical copy of your data in a single- or multi-region peered cluster. Your first 100,000 DPUs and 1 GB of storage per month are free with AWS Free Tier. Find pricing here.
Console users can try Aurora DSQL for free. The Aurora DSQL User Guide has more information, and you may give comments via AWS re:Post or other means.
#AuroraDSQL#AmazonAuroraDSQL#AuroraDSQLcluster#DistributedProcessingUnit#AWSservices#ModelContextProtocol#technology#technews#technologynews#news#govindhtech
0 notes
Text
Back-End Development: A Complete Guide for Beginners in 2025
When you visit a website, everything you see—the layout, colors, text, and buttons—is the front end. But what happens when you log in, fill out a form, or make a payment? That’s where the back-end development magic begins.
In this complete guide, we’ll explore what back-end development is, why it’s crucial for the web, what technologies and skills you need, and how you can build a thriving career in this dynamic field. Whether you're a curious beginner or someone switching careers, this article has everything you need to know.
🚀 What is Back-End Development?
Back-end development refers to the server-side part of web development. It's everything that happens behind the scenes to make a website or app function properly—like servers, databases, application logic, and APIs.
Back-end development is all about how a website works rather than how it looks.
For example:
When you submit a login form, the back end checks your credentials in the database.
When you place an order online, the back end processes the order and stores the transaction.
⚙️ How Does Back-End Development Work?
The back end interacts with three key components:
Server – The machine that handles requests.
Database – Where data like user info and product listings are stored.
Application – The logic that ties it all together.
Here’s a simplified flow:
User clicks a button (front-end)
Front-end sends a request to the server
Back-end processes the request
Data is fetched from or saved to the database
Server sends a response back to the front-end
🧰 Core Technologies in Back-End Development
To become a back-end developer, you’ll need to learn these foundational tools and languages:
1. Programming Languages
LanguageUse CaseJavaScript (Node.js)Scalable server-side appsPythonFast prototyping, AI, APIsPHPWordPress and server scriptingRubyElegant, readable server-side codeJavaEnterprise-grade backend systemsC# (.NET)Enterprise, Windows-based applications
2. Databases
TypeExamplesRelationalMySQL, PostgreSQL, MS SQL ServerNoSQLMongoDB, CouchDB, Firebase
3. Frameworks
LanguageFrameworksJavaScriptExpress.js, Nest.jsPythonDjango, FlaskPHPLaravelRubyRuby on Rails
🌐 Back-End vs Front-End Development
FeatureFront-EndBack-EndFocusUser interface (UI/UX)Server logic and databaseLanguagesHTML, CSS, JSJS (Node), Python, PHP, JavaRuns OnBrowserServerPrimary ConcernDesign, interactivityLogic, data management, securityPopular ToolsReact, Vue, BootstrapDjango, Express.js, PostgreSQL
🧑💻 Roles & Responsibilities of a Back-End Developer
What does a back-end developer do?
Build APIs and server-side logic
Design and maintain databases
Secure user data and handle authentication
Ensure scalability and performance
Collaborate with front-end developers and DevOps teams
🛡️ Back-End and Security
Security is a core responsibility in back-end development.
Key areas include:
Data encryption
Secure APIs
Password hashing (bcrypt, Argon2)
Input validation
Authorization & Authentication (OAuth, JWT, etc.)
🧱 APIs and RESTful Architecture
APIs (Application Programming Interfaces) are bridges between the front end and back end.
Back-end developers often design:
REST APIs using HTTP methods (GET, POST, PUT, DELETE)
GraphQL APIs for flexible data querying
WebSockets for real-time communication
🔗 Database Management and ORM
Databases are the heart of any application.
Back-end developers use SQL for structured queries and ORMs (Object Relational Mappers) like:
Sequelize (Node.js)
Prisma
SQLAlchemy (Python)
Eloquent (Laravel)
📦 Hosting and Deployment
Once the server code is ready, it needs to be hosted.
Popular options:
Cloud: AWS, Google Cloud, Azure
Containers: Docker, Kubernetes
Serverless: Vercel, Netlify, AWS Lambda
CI/CD pipelines like GitHub Actions, Jenkins, and GitLab CI automate deployments.
🧠 Learning Path: How to Become a Back-End Developer
Here’s a structured roadmap:
Master a Programming Language – Start with Python or JavaScript (Node.js)
Understand the Internet and HTTP
Learn Databases – Start with MySQL or MongoDB
Build REST APIs
Practice Authentication & Security
Work with Real Projects
Use Git and GitHub
Explore DevOps Basics
Build a Portfolio with back-end apps
Contribute to Open Source
📊 Salary Insights and Job Opportunities (2025)
Back-end development is one of the most in-demand tech skills in 2025.CountryEntry-LevelMid-LevelSeniorIndia₹5–8 LPA₹10–20 LPA₹25+ LPAUSA$65K–$85K$90K–$120K$130K+UK£30K–£50K£55K–£75K£80K+
Common Job Titles:
Back-End Developer
Full-Stack Developer
API Engineer
Server-Side Developer
Cloud Functions Developer
💬 Real Developer Reviews
⭐⭐⭐⭐⭐ “As a back-end developer, I love building things people don’t even realize they’re using. It’s like being a wizard behind the curtain.” — Neha R., Software Engineer
⭐⭐⭐⭐☆ “Python and Django made it easy to get started. The logic is so clean and powerful.” — Mike T., Backend Developer
⭐⭐⭐⭐⭐ “Every startup needs someone who can build scalable back ends. It’s a career with massive growth potential.” — Ritika D., API Architect
🧠 Best Learning Resources (Free & Paid)
Free Platforms:
freeCodeCamp
MDN Web Docs
The Odin Project
Paid Options:
Udemy
"Node.js: The Complete Guide"
"Python & Django Bootcamp"
Coursera
"Back-End Development by Meta"
edX
Scrimba
📌 FAQs About Back-End Development
Q1. Do I need a degree to become a back-end developer?
A: No. Many successful developers are self-taught. Bootcamps and real-world projects matter more than degrees.
Q2. Which is better: back-end or front-end?
A: It depends on your interests. If you enjoy logic, data, and server operations—back-end is for you.
Q3. Is Node.js good for back-end?
A: Yes. Node.js is fast, efficient, and widely used for scalable server-side applications.
Q4. How long does it take to become job-ready?
A: With consistent learning, you can become a back-end developer in 6–12 months.
Q5. What is full-stack development?
A: Full-stack developers handle both front-end and back-end tasks. They’re skilled in end-to-end development.
Q6. What are the best languages for back-end development?
A: Python, JavaScript (Node.js), PHP, Java, and C# are top choices in 2025.
✨ Final Thoughts: Is Back-End Development Right for You?
If you love building logic, handling real-world data, working with APIs, and ensuring applications run smoothly—back-end development might be your ideal career path.
It’s a high-demand, well-paying, and technically rewarding field with endless opportunities for growth, especially with cloud computing, AI, and big data booming.
Whether you dream of joining a tech giant or launching your own SaaS app, mastering back-end development opens the door to some of the most impactful tech roles of the future.
0 notes
Text
Log Shipping (or LS) in SQL Server is a disaster recovery solution that automates the backup, copy, and restore of transaction logs from a primary server to a secondary server. Let's Explore Deeply:
https://madesimplemssql.com/log-shipping-in-sql-server/
Follow us on FB: https://www.facebook.com/profile.php?id=100091338502392
&
Join our Group: https://www.facebook.com/groups/652527240081844
2 notes
·
View notes
Text
Hızlandırılmış Veri Kurtarma ile SQL Server 2022
Hızlandırılmış Veri Kurtarma (ADR), SQL Server 2022 ile birlikte veri tabanı yönetiminde devrim niteliğinde bir yenilik sunmaktadır. Uzun süren sorguların ve olası veri kayıplarının önüne geçmek için geliştirilen bu özellik, veri tabanı kurtarma işlemlerini hızlandırarak kullanıcıların işlerindeki verimliliği artırmaktadır. ADR sayesinde, veri tabanında gerçekleşen transaction log işlemleri en…
0 notes