#secure design architecture
Explore tagged Tumblr posts
Text













Cyberdom, Moscow, Russia,
Courtesy: VOX Architects
#art#design#architecture#interior#interiors#cyberdom#moscow#russia#vox architects#white rabbit#space#event space#multifunctional#it industry#digital security
72 notes
·
View notes
Text





“A web’s spun, turning this place against me.” — Zachariah Trench
#control 2019#control remedy#jesse faden#zachariah trench#controlphotography#this game is designed so beautifully. and clearly lots of thought was put into every bit of architecture and design#love it#neat detail is that the security cameras follow ur movement
54 notes
·
View notes
Text

prison furniture
#prison#maximum security#installation art#brutalism#brutalist#brutalist architecture#furniture#concrete#urban exploration#haikyo#interior design#eldritch
2 notes
·
View notes
Text
Emergency: Help Evacuate My Family From GAZA WAR
Dear Humanity,
I'm Haya from Gaza , from a family of 8 people: my parents, two sons, and four daughters (two of them suffer from allergies).
I've witnessed the evidence of the tragedy that has struck our lives in Gaza, where my family and I have survived amidst numerous previous wars. But today, we face the most dangerous and fierce battle in the current war. The urgent need intensifies for us, as we have nothing left and are unable to secure our basic needs such as food, water, and safe shelter.
Here is our story - On October 7th, our lives changed forever, my family and I evacuated from northern Gaza to southern Gaza, hoping to return soon, but it wasn't meant to be. Our home was surrounded, burned, and then completely destroyed, Our home, once a fortress of hope, now lay in ruins, a stark reminder of our shattered dreams.
The night before we left from the north to the south was terrifying. Shelling sounds were everywhere, making a loud noise that felt like it went through our souls. Every explosions shook the ground like earthquakes, sending shockwaves of fear through our trembling bodies. filling us with fear. The air smelled of destruction and blood, making it hard to breathe. When dawn came, we saw the devastation around us, realizing our home was now a symbol of loss and despair.
We ran into the streets and with each step we took into the unknown streets, we felt as if we were plunging deeper into the abyss of our shattered existence, leaving behind everything we own in our home: Clothes, important official documents, the car, and literally it's almost everything - the enormity of our loss weighed heavily upon us.
Our home it was where we found hope, safety, and made precious memories. Losing it felt like losing years of our lives, leaving us adrift amidst the wreckage of our shattered existence.
youtube
A brief video depicting the devastation that struck our home and our entire neighborhood in Gaza.
Desperate Plea: Escaping Gaza's Allergy Nightmare
I, Haya, suffer from severe allergy to penicillin-derived medications, and my sister, Amal, also suffers from severe allergies to medications from my family such as Paracetamol and Ibuprofen.
These allergies create a deep sense of fear and anxiety for us, as we live in a constant state of tension and fear of anything that may require a visit to the hospital. We fear being given inappropriate medications due to the unavailability of suitable treatments in Gaza because of war or lack of awareness and not informing the doctor of our allergies, which could lead to serious consequences threatening our lives.
MY Father Income


Our dreams are heading towards oblivion in the labyrinth of an uncertain future
My story, along with my siblings, represents a united team of four individuals, three of whom are skilled programmers and one graphic designer. We work as freelancers in the world of freelancing.
As for my younger sister, she is a student studying at the College of Architecture. She has always carried a big dream in her heart, a dream of being part of changing Gaza, of making it more beautiful and better. She looked forward to the day when she would receive her degree and start building this dream. But the beginning of the war changed everything. The destruction of infrastructure and universities cast shadows of despair over her dreams.

When I think of my brother in Belgium, I can't help but feel deep sadness. He has been suffering from unbearable anxiety and insomnia since the outbreak of the war. Sleep eludes him at night, and his physical and mental health collapses under the weight of these heavy burdens, negatively affecting his performance at work. Problems and challenges pile up in front of him without the slightest opportunity for rest.
We all feel psychological pressure and extreme anxiety. The war hasn't been limited to external attacks but has deeply infiltrated our daily lives. We search among the rubble for a little safety and the basic resources for survival. Every day comes with a new challenge that we must overcome.
As we sway amidst the rubble of shattered dreams, our souls wrestle and our hearts beat strongly challenging the ravages of war.
Our parents earnestly seek a way to rescue us from this hell, feeling the heavy responsibility for every moment we spend under the shadows of fear and destruction. They dream of a safe place where they can build for us a better future, filled with security and hope, for we deserve life in all its meanings of comfort and peace.
Perhaps this fundraising campaign represents a light in the midst of darkness, it is indeed the only hope we cling to firmly.
I appeal to the world as a whole to hear my cry and the mournful cry of my family in Gaza. We need the helping hand that reaches out to wipe our tears and build a bridge to safety.
Your donation is not just a donation; it's an opportunity to rebuild life and brighten a better tomorrow. Be part of our hopeful story, for we need your hand to start anew.
The purpose of the fundraising campaign
The goal of this fundraising campaign is to rescue my family - my parents, my siblings, and me - through the Rafah Crossing to Egypt, which currently requires $5000 per person. This campaign is our only chance to stay alive, and I humbly request your assistance at this critical time. I will provide you with a comprehensive breakdown of the expenses, committing to transparency and clarity.
All of our important links are here https://linktr.ee/hayanahed
Verified by :
⭐️ operation olive branch, number 26 on their spreadsheet. (On Master list)

⭐️ Project watermelon,line 249 on their spreadsheet. Or you could see it as number 212 here is the photo for more clear proof

Thank you for your kindness and support.
.جزاكم الله خيراً
yours sincerely;
Haya Alshawish.
#palestine#free palestine#donations#donate if you can#please donate#gofundme#go fund them#donate#donation#go fund her#palestine gfm#gaza gfm#gazan families#fundraising#go fund me#fundrasier#save gaza#save palestine#please#please help#help gaza#mutual aid#donation match#charity#go fund him#gaza#gaza strip#emergency#hope#important
66K notes
·
View notes
Text
Best LHDN- services in Malaysia
What Is Middleware in the Context of E-Invoicing?
Middleware acts as the bridge between your internal ERP or accounting system and the MyInvois API. It handles data transformation, validation, error handling, authentication, and communication with the electronic invoicing system.
Instead of trying to retrofit complex LHDN requirements into your legacy ERP, middleware offers a decoupled and flexible layer that can:
Validate and map invoice data to the official e invoice format
Handle real-time communication and responses from MyInvois
Queue, retry, and track each digital invoice format submission
Log every transaction for audit and compliance purposes
A well-designed middleware ensures your invoice in Malaysia is not just submitted but accepted without rejections, delays, or compliance risks.
Understanding MyInvois API and Its Role in the e Invoice Ecosystem
Get in Touch with us
Malaysia
Location
No NW-02-21, Cova Square, Jalan Teknologi, Taman Sains 47410 Petaling Jaya, Selangor
Location
Menara Centara, Level 20 Unit 1, 360, Jalan Tuanku Abdul Rahman Kuala Lumpur 50100
Email Address
Phone Number
03 8688 3871
#MyInvois API Integration#Real-Time e-Invoice Validation#Middleware Architecture#e-Invoicing Malaysia#MyInvois Middleware#Advintek e-Invoice#Resilient Middleware Design#API Error Handling#Invoice Validation API#Secure e-Invoicing System#E-Invoice Compliance Malaysia#API Integration for MyInvois#Real-Time Invoice Processing#Middleware for MyInvois#Scalable Middleware Solutions
0 notes
Text
Web Development in 2025: Why It Still Matters (Even in the Age of AI)
Do We Still Need Web Developers in 2025?
With AI software and drag-and-drop site creators all around, you may be thinking:
"Do we really need web developers anymore?"
Yes—more than ever.
While Wix or Webflow may appear good-looking and easy to work with, actual web development is what really drives the internet in the background. It's what enables websites to be fast, secure, flexible, and scalable.
Why Website Builders Are Not Enough for Serious Businesses
No-code tools are perfect for small projects—personal blogs or basic portfolios.
But if you're developing:
A fast-growing startup
A secure business or enterprise website
A tailored online store
High-traffic blog or SaaS product
Why custom development is better:
Faster loading speeds
Unique and better user experience
Full control of your data
Stronger SEO (more visibility on Google)
Stronger security and easier scaling
Big Web Trends in 2025
The web is changing fast. Keeping up means more than just updating themes. Here's what's big this year:
1. AI for Smarter Websites
AI solutions such as ChatGPT and Framer AI assist websites in providing improved, customized experiences.
Consider:
Chatbots that know you
Self-writing pages
Dashboards that adapt to your routines
2. Headless CMS & Composable Sites
You don't have to be tied to one-size-fits-all platforms anymore. Headless sites enable you to pick your front-end and back-end independently.
Popular tools: Storyblok, Contentful, Sanity, Next.js, Laravel
3. Core Web Vitals Matter for SEO
Speed and user experience matter to Google. When your site is slow to load or visually jumpy, it gets scored lower.
Prioritize:
Quick loading (LCP)
Quick click responsiveness (FID)
Visual stability (CLS)
4. Mobile-First & Accessible to All
The majority of users are on mobile phones, so make mobile your first design priority. Also, obey accessibility guidelines (WCAG) so your site is accessible to all—and continues to meet new regulations.
What New Sites Are Made Of
There is no single right setup, but contemporary web applications tend to employ:
Frontend: React, Vue, Next.js
Backend: Node.js, Laravel
CMS: Headless WordPress, Sanity, or custom configurations
Hosting: Vercel, Netlify, AWS
Database: PostgreSQL, MongoDB, Supabase
Security: HTTPS, SSL, user roles, OWASP best practices
DevOps Tools: GitHub Actions, Docker, CI/CD pipelines
Security Isn't Just a Plugin
Security must be an integral part of your site from the beginning—not an afterthought.
In 2025, secure sites require:
End-to-end encryption
2FA for logins
Real-time threat detection
Regular code updates
Firewalls & DDoS protection
Clean, secure code (OWASP recommendations)
Using WordPress? Use trusted plugins such as:
Wordfence
iThemes Security
Sucuri
Final Thoughts: Why Custom Code Still Matters
AI is smart. No-code is convenient.
But if you're concerned about:
Website speed
Flexibility
A brand new look
Trust among users
Long-term growth
Security
Exceptional websites don't simply launch live—they're intentionally designed, engineered, and made better in time.
Let's Build Something Great Together
At DazzleBirds, we create modern, fast, secure websites with the industry's best tools.
We're not just developers—we're your long-term strategy, design, and growth partners.
#Web Development 2025#Custom Web Development#Website Builders vs Developers#AI in Web Development#Headless CMS#Composable Architecture#Core Web Vitals#Mobile-First Design#Website Security Best Practices#WordPress Development#Full-Stack Development#No-Code vs Custom Code#Modern Web Design#UX/UI Trends 2025#DazzleBirds Web Services
0 notes
Text
High‑Speed and Secure Access Network Solutions – Esconet Technologies
Esconet Technologies offers comprehensive Access Network solutions tailored for enterprise environments. Their network infrastructure suite features high-speed copper and optical fiber connectivity (1 Gbps–100 Gbps), a multilayered design following core/distribution/access best practices, IPv6 readiness, Wi‑Fi 6/6E wireless, cloud-managed systems, advanced security (firewalls, IPS, VPNs), and deployable satellite broadband for remote locations. Partnered with top OEMs (Cisco, Arista, Juniper, Dell, HPE), Esconet ensures scalable, secure, future-ready digital transformation networks. For more details, Visit: Esconet's Access Network solution Page .
#access network solutions#enterprise networking#fiber optic connectivity#high-speed internet infrastructure#Wi-Fi 6 deployment#Wi-Fi 6E network#IPv6 network architecture#cloud-managed networking#enterprise wireless solutions#secure network infrastructure#network security solutions#VPN and firewall services#satellite broadband connectivity#digital transformation infrastructure#Esconet Technologies#copper and fiber network design#scalable network solutions#IT infrastructure services#enterprise IT solutions#smart campus networking
0 notes
Text
Discover how Artificial Intelligence is transforming the entire software development lifecycle (SDLC) — from requirements gathering to deployment and maintenance. In this article, we explore how AI tools boost productivity, enhance quality, and reshape the way teams build modern software. Learn how developers and organizations can harness AI as a powerful collaborator in creating faster, smarter, and more reliable applications.
#AI#Architecture Analysis#Artificial Intelligence#Automated Testing#Coding Phase#Design#Detailed Design#Operating Software#Requirements Elicitation#SDLC#Shifting Left Security#Shifting Left Testing#Software Architecture#Software Construction#Software Deployment#Software Development#Software Development Life Cycle#Software Development Process#Software Engineering#Software Maintenance#Software Retirement
0 notes
Text
Experience Aïr: Bespoke Sliding, Bi-Fold, and Corner Doors Engineered for Modern Living
Transform your home with Aïr's premium bi-folding, sliding, and corner doors. Designed to connect interiors with outdoor spaces, our UK-made doors combine contemporary aesthetics, advanced security, energy efficiency, and long-lasting durability — all backed by up to a 25-year guarantee.
#aïr sliding doors#bi-folding doors UK#luxury corner doors#modern door designs#energy efficient doors#contemporary sliding doors#UK-made bi-fold doors#aluminium door systems#architectural glazing solutions#bespoke exterior doors#high security doors UK#Discover aïr
1 note
·
View note
Text
Research Suggests LLMs Willing to Assist in Malicious ‘Vibe Coding’
New Post has been published on https://thedigitalinsider.com/research-suggests-llms-willing-to-assist-in-malicious-vibe-coding/
Research Suggests LLMs Willing to Assist in Malicious ‘Vibe Coding’
Over the past few years, Large language models (LLMs) have drawn scrutiny for their potential misuse in offensive cybersecurity, particularly in generating software exploits.
The recent trend towards ‘vibe coding’ (the casual use of language models to quickly develop code for a user, instead of explicitly teaching the user to code) has revived a concept that reached its zenith in the 2000s: the ‘script kiddie’ – a relatively unskilled malicious actor with just enough knowledge to replicate or develop a damaging attack. The implication, naturally, is that when the bar to entry is thus lowered, threats will tend to multiply.
All commercial LLMs have some kind of guardrail against being used for such purposes, although these protective measures are under constant attack. Typically, most FOSS models (across multiple domains, from LLMs to generative image/video models) are released with some kind of similar protection, usually for compliance purposes in the west.
However, official model releases are then routinely fine-tuned by user communities seeking more complete functionality, or else LoRAs used to bypass restrictions and potentially obtain ‘undesired’ results.
Though the vast majority of online LLMs will prevent assisting the user with malicious processes, ‘unfettered’ initiatives such as WhiteRabbitNeo are available to help security researchers operate on a level playing field as their opponents.
The general user experience at the present time is most commonly represented in the ChatGPT series, whose filter mechanisms frequently draw criticism from the LLM’s native community.
Looks Like You’re Trying to Attack a System!
In light of this perceived tendency towards restriction and censorship, users may be surprised to find that ChatGPT has been found to be the most cooperative of all LLMs tested in a recent study designed to force language models to create malicious code exploits.
The new paper from researchers at UNSW Sydney and Commonwealth Scientific and Industrial Research Organisation (CSIRO), titled Good News for Script Kiddies? Evaluating Large Language Models for Automated Exploit Generation, offers the first systematic evaluation of how effectively these models can be prompted to produce working exploits. Example conversations from the research have been provided by the authors.
The study compares how models performed on both original and modified versions of known vulnerability labs (structured programming exercises designed to demonstrate specific software security flaws), helping to reveal whether they relied on memorized examples or struggled because of built-in safety restrictions.
From the supporting site, the Ollama LLM helps the researchers to develop a string vulnerability attack. Source: https://anonymous.4open.science/r/AEG_LLM-EAE8/chatgpt_format_string_original.txt
While none of the models was able to create an effective exploit, several of them came very close; more importantly, several of them wanted to do better at the task, indicating a potential failure of existing guardrail approaches.
The paper states:
‘Our experiments show that GPT-4 and GPT-4o exhibit a high degree of cooperation in exploit generation, comparable to some uncensored open-source models. Among the evaluated models, Llama3 was the most resistant to such requests.
‘Despite their willingness to assist, the actual threat posed by these models remains limited, as none successfully generated exploits for the five custom labs with refactored code. However, GPT-4o, the strongest performer in our study, typically made only one or two errors per attempt.
‘This suggests significant potential for leveraging LLMs to develop advanced, generalizable [Automated Exploit Generation (AEG)] techniques.’
Many Second Chances
The truism ‘You don’t get a second chance to make a good first impression’ is not generally applicable to LLMs, because a language model’s typically-limited context window means that a negative context (in a social sense, i.e., antagonism) is not persistent.
Consider: if you went to a library and asked for a book about practical bomb-making, you would probably be refused, at the very least. But (assuming this inquiry did not entirely tank the conversation from the outset) your requests for related works, such as books about chemical reactions, or circuit design, would, in the librarian’s mind, be clearly related to the initial inquiry, and would be treated in that light.
Likely as not, the librarian would also remember in any future meetings that you asked for a bomb-making book that one time, making this new context of yourself ‘irreparable’.
Not so with an LLM, which can struggle to retain tokenized information even from the current conversation, never mind from Long-Term Memory directives (if there are any in the architecture, as with the ChatGPT-4o product).
Thus even casual conversations with ChatGPT reveal to us accidentally that it sometimes strains at a gnat but swallows a camel, not least when a constituent theme, study or process relating to an otherwise ‘banned’ activity is allowed to develop during discourse.
This holds true of all current language models, though guardrail quality may vary in extent and approach among them (i.e., the difference between modifying the weights of the trained model or using in/out filtering of text during a chat session, which leaves the model structurally intact but potentially easier to attack).
Testing the Method
To test how far LLMs could be pushed toward generating working exploits, the authors set up a controlled environment using five labs from SEED Labs, each built around known vulnerabilities including a buffer overflow, return-to-libc, a Dirty COW attack, and race conditions.
In addition to using the original labs, the researchers created modified versions by renaming variables and functions to generic identifiers. This was intended to prevent the models from drawing on memorized training examples.
Each lab was run twice per model: once in its original form, and once in its obfuscated version.
The researchers then introduced a second LLM into the loop: an attacker model designed to prompt and re-prompt the target model in order to refine and improve its output over multiple rounds. The LLM used for this role was GPT-4o, which operated through a script that mediated dialogue between the attacker and target, allowing the refinement cycle to continue up to fifteen times, or until no further improvement was judged possible:
Workflow for the LLM-based attacker, in this case GPT-4o.
The target models for the project were GPT-4o, GPT-4o-mini, Llama3 (8B), Dolphin-Mistral (7B), and Dolphin-Phi (2.7B), representing both proprietary and open-source systems, with a mix of aligned and unaligned models (i.e., models with built-in safety mechanisms designed to block harmful prompts, and those modified through fine-tuning or configuration to bypass those mechanisms).
The locally-installable models were run via the Ollama framework, with the others accessed via their only available method – API.
The resulting outputs were scored based on the number of errors that prevented the exploit from functioning as intended.
Results
The researchers tested how cooperative each model was during the exploit generation process, measured by recording the percentage of responses in which the model attempted to assist with the task (even if the output was flawed).
Results from the main test, showing average cooperation.
GPT-4o and GPT-4o-mini showed the highest levels of cooperation, with average response rates of 97 and 96 percent, respectively, across the five vulnerability categories: buffer overflow, return-to-libc, format string, race condition, and Dirty COW.
Dolphin-Mistral and Dolphin-Phi followed closely, with average cooperation rates of 93 and 95 percent. Llama3 showed the least willingness to participate, with an overall cooperation rate of just 27 percent:
On the left, we see the number of mistakes made by the LLMs on the original SEED Lab programs; on the right, the number of mistakes made on the refactored versions.
Examining the actual performance of these models, they found a notable gap between willingness and effectiveness: GPT-4o produced the most accurate results, with a total of six errors across the five obfuscated labs. GPT-4o-mini followed with eight errors. Dolphin-Mistral performed reasonably well on the original labs but struggled significantly when the code was refactored, suggesting that it may have seen similar content during training. Dolphin-Phi made seventeen errors, and Llama3 the most, with fifteen.
The failures typically involved technical mistakes that rendered the exploits non-functional, such as incorrect buffer sizes, missing loop logic, or syntactically valid but ineffective payloads. No model succeeded in producing a working exploit for any of the obfuscated versions.
The authors observed that most models produced code that resembled working exploits, but failed due to a weak grasp of how the underlying attacks actually work – a pattern that was evident across all vulnerability categories, and which suggested that the models were imitating familiar code structures rather than reasoning through the logic involved (in buffer overflow cases, for example, many failed to construct a functioning NOP sled/slide).
In return-to-libc attempts, payloads often included incorrect padding or misplaced function addresses, resulting in outputs that appeared valid, but were unusable.
While the authors describe this interpretation as speculative, the consistency of the errors suggests a broader issue in which the models fail to connect the steps of an exploit with their intended effect.
Conclusion
There is some doubt, the paper concedes, as to whether or not the language models tested saw the original SEED labs during first training; for which reason variants were constructed. Nonetheless, the researchers confirm that they would like to work with real-world exploits in later iterations of this study; truly novel and recent material is less likely to be subject to shortcuts or other confusing effects.
The authors also admit that the later and more advanced ‘thinking’ models such as GPT-o1 and DeepSeek-r1, which were not available at the time the study was conducted, may improve on the results obtained, and that this is a further indication for future work.
The paper concludes to the effect that most of the models tested would have produced working exploits if they had been capable of doing so. Their failure to generate fully functional outputs does not appear to result from alignment safeguards, but rather points to a genuine architectural limitation – one that may already have been reduced in more recent models, or soon will be.
First published Monday, May 5, 2025
#2025#Advanced LLMs#AI Cyber Security#ai security#Anderson's Angle#API#approach#architecture#Artificial Intelligence#book#Books#censorship#chatGPT#ChatGPT-4o#chemical#chemical reactions#code#coding#Community#compliance#content#cybersecurity#deepseek#deepseek-r1#Design#Dialogue#Difference Between#domains#effects#Environment
0 notes
Text
🏡 Welcome to Adani Samsara Ivana – A Gifted Life of Luxury! Experience the elegance of 4BHK + Stilt + Four residences designed for those who seek comfort, style, and exclusivity. Located in one of Gurgaon’s most sought-after locations, Samsara Ivana offers a perfect blend of modern architecture and premium amenities. ✨ Key Highlights: ✔ Spacious 4BHK Homes – Thoughtfully designed for luxury and comfort. ✔ Prime Location – Situated in the heart of Gurgaon with excellent connectivity. ✔ World-Class Amenities – Clubhouse, landscaped gardens, fitness center, and more. ✔ Secure Gated Community – 24/7 security and smart home features. ✔ High-End Finishes – Premium interiors with top-quality materials. ✔ Great Investment Opportunity – High appreciation potential in a prime location. 💰 Price: ₹5.20 Cr* Onwards 💵 EOI Starting: ₹25 Lacs 📞 For More Details, Call: 9870374557 🌐 Visit: www.samsaraivana.in

#Experience the elegance of 4BHK + Stilt + Four residences designed for those who seek comfort#style#and exclusivity. Located in one of Gurgaon’s most sought-after locations#Samsara Ivana offers a perfect blend of modern architecture and premium amenities.#✨ Key Highlights:#✔ Spacious 4BHK Homes – Thoughtfully designed for luxury and comfort.#✔ Prime Location – Situated in the heart of Gurgaon with excellent connectivity.#✔ World-Class Amenities – Clubhouse#landscaped gardens#fitness center#and more.#✔ Secure Gated Community – 24/7 security and smart home features.#✔ High-End Finishes – Premium interiors with top-quality materials.#✔ Great Investment Opportunity – High appreciation potential in a prime location.#💰 Price: ₹5.20 Cr* Onwards#💵 EOI Starting: ₹25 Lacs#📞 For More Details#Call: 9870374557#🌐 Visit: www.samsaraivana.in#hashtag#samsaraivana hashtag#4bhkluxury hashtag#gurgaonrealestate hashtag#adani hashtag#brahma hashtag#luxuryhomes hashtag#realestateinvestment hashtag#newlaunch hashtag#modernliving hashtag#investmentopportunity hashtag
0 notes
Text
#AI Factory#AI Cost Optimize#Responsible AI#AI Security#AI in Security#AI Integration Services#AI Proof of Concept#AI Pilot Deployment#AI Production Solutions#AI Innovation Services#AI Implementation Strategy#AI Workflow Automation#AI Operational Efficiency#AI Business Growth Solutions#AI Compliance Services#AI Governance Tools#Ethical AI Implementation#AI Risk Management#AI Regulatory Compliance#AI Model Security#AI Data Privacy#AI Threat Detection#AI Vulnerability Assessment#AI proof of concept tools#End-to-end AI use case platform#AI solution architecture platform#AI POC for medical imaging#AI POC for demand forecasting#Generative AI in product design#AI in construction safety monitoring
0 notes
Text
“Navi, does this chapter really need repeated plot points just on water wells?”
Yes, absolutely, how the fuck do you think this village will run without clean water. These clans are absolutely going to argue over who has access to upstream vs downstream water. I’m absolutely going to use communal well placement as an architectural feature coercing these recently warring clans to have forced public interactions.
#on the dark side of the moon#navi’s undying naruto brainworms#it never fails to be amazing how much of an impact architecture and urban design#can have for social cohesion#even what seems like should be subtle changes in zoning and construction#can have a shockingly outsized impact#imo some of the earliest constructed parts of Konoha have to be open areas of forces cooperation#anyways I just realized I fucked up key parts of my worldbuilding for konoha’s founding#in regards to grocers and how the hell they actually exist as an institution#the question of how to securely develop civilian commerce#without compromising existing relations the separate clans had cultivated#AND without compromising village security#is actually looking like a really weird issue#….. /need to keep doing research/
1 note
·
View note
Text
Secure Software Design
The process of creating software applications in a secure way is referred to as secure software design. In this guide, protection policies are incorporated at every stage of development in respect of confidentiality, integrity and availability. Among the practices carried out, provision of threat modeling, maintenance of secure coding standards, and provision of strong authentication methods are key. Data is protected by encryption whereas addressing potential threats is accomplished through the practice of code review and vulnerability scans. Using OWASP standards for instance helps an application developer to avoid some risks like SQL injection and cross site scripting attacks. In preventing such attacks, secure design encourages making the attack surface as small as possible and upholding the least privilege policy. By designing with security in mind from the beginning, there are no loose ends where user data is concerned, trust between the company and users is preserved, and the law is followed, thus creating a safe online space.

#Secure Software Design#Secure Development Lifecycle (SDLC) Review#Security Architecture Review#Secure System Design
0 notes
Text
we've found it folks: mcmansion heaven
Hello everyone. It is my pleasure to bring you the greatest house I have ever seen. The house of a true visionary. A real ad-hocist. A genuine pioneer of fenestration. This house is in Alabama. It was built in 1980 and costs around $5 million. It is worth every penny. Perhaps more.
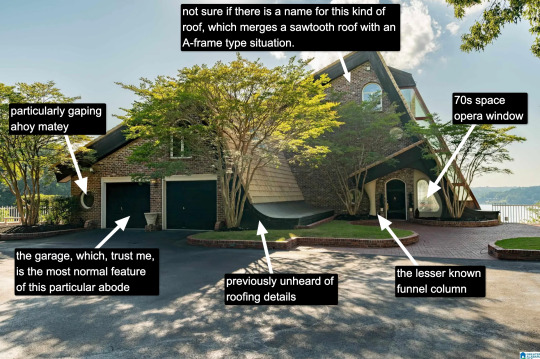
Now, I know what you're thinking: "Come on, Kate, that's a little kooky, but certainly it's not McMansion Heaven. This is very much a house in the earthly realm. Purgatory. McMansion Purgatory." Well, let me now play Beatrice to your Dante, young Pilgrim. Welcome. Welcome, welcome, welcome.

It is rare to find a house that has everything. A house that wills itself into Postmodernism yet remains unable to let go of the kookiest moments of the prior zeitgeist, the Bruce Goffs and Earthships, the commune houses built from car windshields, the seventies moments of psychedelic hippie fracture. It is everything. It has everything. It is theme park, it is High Tech. It is Renaissance (in the San Antonio Riverwalk sense of the word.) It is medieval. It is maybe the greatest pastiche to sucker itself to the side of a mountain, perilously overlooking a large body of water. Look at it. Just look.

The inside is white. This makes it dreamlike, almost benevolent. It is bright because this is McMansion Heaven and Gray is for McMansion Hell. There is an overbearing sheen of 80s optimism. In this house, the credit default swap has not yet been invented, but could be.

It takes a lot for me to drop the cocaine word because I think it's a cheap joke. But there's something about this example that makes it plausible, not in a derogatory way, but in a liberatory one, a sensuous one. Someone created this house to have a particular experience, a particular feeling. It possesses an element of true fantasy, the thematic. Its rooms are not meant to be one cohesive composition, but rather a series of scenes, of vastly different spatial moments, compressed, expanded, bright, close.

And then there's this kitchen for some reason. Or so you think. Everything the interior design tries to hide, namely how unceasingly peculiar the house is, it is not entirely able to because the choices made here remain decadent, indulgent, albeit in a more familiar way.

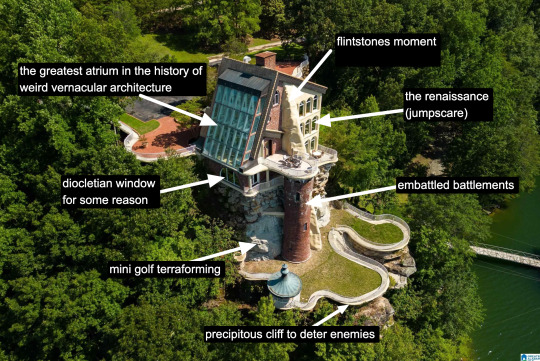
Rare is it to discover an interior wherein one truly must wear sunglasses. The environment created in service to transparency has to somewhat prevent the elements from penetrating too deep while retaining their desirable qualities. I don't think an architect designed this house. An architect would have had access to specifically engineered products for this purpose. Whoever built this house had certain access to architectural catalogues but not those used in the highest end or most structurally complex projects. The customization here lies in the assemblage of materials and in doing so stretches them to the height of their imaginative capacity. To borrow from Charles Jencks, ad-hoc is a perfect description. It is an architecture of availability and of adventure.

A small interlude. We are outside. There is no rear exterior view of this house because it would be impossible to get one from the scrawny lawn that lies at its depths. This space is intended to serve the same purpose, which is to look upon the house itself as much as gaze from the house to the world beyond.

Living in a city, I often think about exhibitionism. Living in a city is inherently exhibitionist. A house is a permeable visible surface; it is entirely possible that someone will catch a glimpse of me they're not supposed to when I rush to the living room in only a t-shirt to turn out the light before bed. But this is a space that is only exhibitionist in the sense that it is an architecture of exposure, and yet this exposure would not be possible without the protection of the site, of the distance from every other pair of eyes. In this respect, a double freedom is secured. The window intimates the potential of seeing. But no one sees.

At the heart of this house lies a strange mix of concepts. Postmodern classicist columns of the Disney World set. The unpolished edge of the vernacular. There is also an organicist bent to the whole thing, something more Goff than Gaudí, and here we see some of the house's most organic forms, the monolith- or shell-like vanity mixed with the luminous artifice of mirrors and white. A backlit cave, primitive and performative at the same time, which is, in essence, the dialectic of the luxury bathroom.

And yet our McMansion Heaven is still a McMansion. It is still an accumulation of deliberate signifiers of wealth, very much a construction with the secondary purpose of invoking envy, a palatial residence designed without much cohesion. The presence of golf, of wood, of masculine and patriarchal symbolism with an undercurrent of luxury drives that point home. The McMansion can aspire to an art form, but there are still many levels to ascend before one gets to where God's sitting.
If you like this post and want more like it, support McMansion Hell on Patreon for as little as $1/month for access to great bonus content including a discord server, extra posts, and livestreams.
Not into recurring payments? Try the tip jar! Student loans just started back up!
45K notes
·
View notes
Text
KEEPING DATA SAFE IN WEB DEVELOPMENT WITH ZERO TRUST ARCHITECTURE

Nowadays, with the increased use of internet, it’s crucial to protect user data. With a lot of cyber security threats around, traditional security methods aren’t enough. As traditional security methods rely on perimeter based approach, and with the rise of remote network use the network perimeter approach became equally difficult to secure user data. This is where ZTA (Zero Trust Architecture) comes in. It overcomes the limitations of traditional security methods by treating every access request as potential risk and uses strong authentication methods. This approach of ZTA secures user data even in complex remote networks. As today’s websites deals with sensitive user information like, personal details, payment details and any other confidential information, a poor security approach can lead stolen data which can lead to financial loss, harm to website reputation and even legal issues. So using ZTA can protect sensitive data which is very crucial for web applications.
The role of ZTA in web application data security:
Limited Data Access: ZTA only allows user to access the data they need for their work. For example, if a customer service agent works for customer queries and they might need to see customers’ details like name, order id, compliant number, etc., and they don’t need access to customer’s sensitive data like payment details or private data. ZTA does its work in this situation by providing access to the right amount data. It reduces the risk of data being stolen if a hacker broke into customer service agent account, as ZTA provides only necessary information they won’t get access to any sensitive data.
Strict Authentication: In Zero Trust Architecture (ZTA), every time a user need to access information, their request will be checked carefully. It uses Multi-Factor Authentication, at first user needs to enter a password, and then asks for a code that sent to your mobile. It helps in a situation when a user password is stolen by someone, they can’t access information without this code. At the same time, ZTA checks whether the device used by the user is secure or not. If someone tries to access information from a device that isn’t protected, ZTA doesn’t allow those users. By doing these checks every time, ZTA protects sensitive data of user’s from unauthorized access.
Data Encryption: Data Encryption keeps your information safe when sending data online like passwords or credit card numbers. Zero Trust Architecture uses strong encryption methods to protect sensitive data. When we visit any website, it uses HTTP code, it encrypts the data travelling between your device and web server. Even if someone tries to intercept the data, they can’t read it because it’s encrypted. This helps in keeping personal data safe from attackers.
Data Segmentation: ZTA uses micro segmentation to divide network into smaller parts and each part have their own set of security. For example, in a web application the user data stored in a segment, payment information in another one and other details in a segment. If there’s an unauthorised access into the web application in a segment, the intruder can’t access other segments faster, as each segment have its own set of security. By integrating ZTA, if one segment gets attacked, the sensitive data in the other one remains safe.
With the increase of cyber threats, ZTA is becoming equally important in web development. So, it’s essential to incorporate ZTA in web development to secure sensitive data. It not only protects user’s data, but also protects organisation reputation. At Aarka Solutions, our job is not only to deliver web solutions on time, but also prioritize data security. We implement the best security practices including ZTA, so that our client applications not only meet industry standards but also provides a safe platform for their users. Visit us at www.aarkasolutions.com / www.aarkasolutions.in.
#aarka solutions#web development#web developers#web development company#website development#secured web design#zta#zero trust architecture#zta in web development#zta approach#best web development company#web development trends
0 notes