#6bones
Text

4/12/24
Mac Miller
I Love Life, Thank You
====
RIP. Always listen to Mac on 412 day. Music from a simpler time. The boom bap production is so simplistic, but it hits right. There are undoubtedly better Mac albums but this is one that I haven't spent as much time on.
6/10
#6bones#mac miller#album#spotify#albumreview#musicdiscovery#album review#albumoftheday#nowplaying#now listening#Music Review#Music Recommendation
10 notes
·
View notes
Text
0 notes
Text
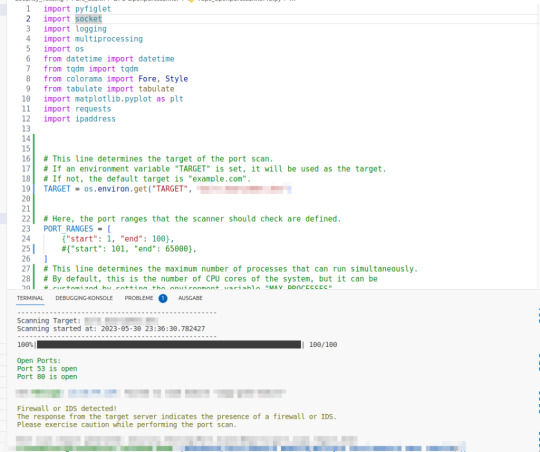
Python: Einfacher und flexibler Portscanner zum Schwachstellentesten (Version 0.1)

Klar man hätte auch einen der schon recht bekannten Port Scanner nutzten können, aber mich treibt es immer wieder zu einer Selbstentwicklung. Für mich ist es extrem wichtig hier Python zu nutzen, da ich es für extrem flexibel halte auch durch die Erweiterung in alle möglichen Richtungen da will ich mich schlichtweg nicht eingrenzen lassen.
Dieses Skript ist ein einfacher Port-Scanner in Python. Es scannt ein angegebenes Ziel (eine IP-Adresse oder einen Hostnamen) auf offene Ports innerhalb eines definierten Bereichs, protokolliert die Aktivitäten und erstellt einen Bericht über den Scan. Hier ist, was jeder Teil des Skripts macht:
- Konfiguration: Das Skript enthält verschiedene Konfigurationsvariablen, die entweder standardmäßig festgelegt sind oder über Umgebungsvariablen angepasst werden können. Diese Konfigurationen umfassen das Ziel des Portscans, die zu überprüfenden Portbereiche, die maximale Anzahl von Prozessen, die gleichzeitig ausgeführt werden können, die Timeout-Zeit für Socket-Operationen sowie die Namen und Pfade von Log- und Berichtsdateien.
- Logging-Konfiguration: Hier wird die Konfiguration für das Protokollieren von Ereignissen festgelegt. Es wird ein Protokollierungslevel festgelegt (standardmäßig INFO), ein Dateiname für das Protokoll (standardmäßig "port_scan.log") und ein Format für die Protokolleinträge.
- Hilfsfunktionen: Das Skript enthält mehrere Hilfsfunktionen, die für verschiedene Aufgaben verwendet werden, z. B. das Drucken eines ASCII-Banners, das Überprüfen der Gültigkeit einer IPv6-Adresse, das Überprüfen eines bestimmten Ports, das Abrufen der IP-Adresse eines Ziels, das Generieren eines Berichts und das Generieren eines Diagramms für die Portbereiche.
- Firewall-Erkennung: Es gibt eine Funktion zum Erkennen einer Firewall oder eines IDS (Intrusion Detection System) auf dem Zielhost. Es wird eine HTTP-Anfrage an den Zielserver gesendet, und basierend auf der Antwort wird überprüft, ob eine Firewall oder ein IDS vorhanden ist.
- Portscan-Funktion: Die Hauptfunktion des Skripts ist die "scan_ports"-Funktion. Diese Funktion ruft die anderen Funktionen auf, um den Portscan durchzuführen. Sie erstellt ein ASCII-Banner, gibt Informationen zum Scan aus, erstellt eine Liste aller zu überprüfenden Ports, ruft die Funktion zum Überprüfen der Ports mithilfe von Multiprocessing auf, generiert einen Bericht, erstellt ein Diagramm für die Portbereiche und ruft die Firewall-Erkennungsfunktion auf. Der Bericht wird in einer HTML-Datei gespeichert.
Hauptprogramm: Der Code am Ende des Skripts überprüft, ob das Skript direkt ausgeführt wird (statt importiert zu werden). Wenn ja, wird die "scan_ports"-Funktion aufgerufen, um den Portscan durchzuführen.
Was in der Version 0.1 schon enthalten ist?
# Todo:
# 1. Add support for UDP ports
# 2. Add support for port ranges - Done
# 3. Add support for port lists - Done
# 4. Add support for CIDR notation - Done
# 5. Add support for hostnames - Done - Use socket.gethostbyname()
# 6. Add support for IPv6 - Done - Use socket.getaddrinfo()
# 7. Add support for IPv6 ranges - Done
# 8. Add support for IPv6 lists - Done
# 9. Add support for IPv6 CIDR notation - Done
# 10. Add support for IPv6 hostnames - Done
# 11. Add support for IPv6 link-local addresses - Done
# 12. Add support for IPv6 site-local addresses - Done
# 13. Add support for IPv6 multicast addresses - Done
# 14. Add support for IPv6 loopback addresses - Done
# 15. Add support for IPv6 unspecified addresses - Done
# 16. Add support for IPv6 IPv4-mapped addresses - Done
# 17. Add support for IPv6 IPv4-translated addresses - Done
# 18. Add support for IPv6 6to4 addresses
# 19. Add support for IPv6 Teredo addresses
# 20. Add support for IPv6 6bone addresses - Done
# 21. Add support for IPv6 documentation addresses - Testing
# 22. Add support for IPv6 global unicast addresses- Testing
# 23. Add support for IPv6 unique local addresses - Testing
# 24. Add support for IPv6 link-local unicast addresses - Testing
# 25. Add support for IPv6 site-local unicast addresses - Testing
# 26. Add support for IPv6 multicast addresses - Testing
# 27. Add support for IPv6 loopback addresses - Testing
# 28. Add support for IPv6 unspecified addresses
# 29. Add support for IPv6 addresses with zone indices
# 30. Add support for IPv6 addresses with scope IDs
# 31. Add support for IPv6 addresses with embedded IPv4 addresses
# 32. Add support for IPv6 addresses with embedded IPv4 addresses and zone indices
# 33. Add support for IPv6 addresses with embedded IPv4 addresses and scope IDs
# 34. Add support for IPv6 addresses with embedded IPv4-mapped addresses
# 35. Add support for IPv6 addresses with embedded IPv4-mapped addresses and zone indices - Done
# 36. Add support for IPv6 addresses with embedded IPv4-mapped addresses and scope IDs
# Done:
# 1. Add support for IPv6 addresses with embedded IPv4-mapped addresses and scope IDs
# 2. Add support for IPv6 addresses with embedded IPv4-mapped addresses and zone indices
# 3. Add support for IPv6 addresses with embedded IPv4 addresses and scope IDs
# 4. Add support for IPv6 addresses with embedded IPv4 addresses and zone indices
# 5. Add support for IPv6 addresses with zone indices
# 6. Add support for IPv6 unspecified addresses
# 7. Add support for IPv6 loopback addresses
# 8. Add support for IPv6 multicast addresses
# 9. Add support for IPv6 site-local unicast addresses
# 10. Add support for IPv6 link-local unicast addresses
Hier das komplette Skript
import pyfiglet
import socket
import logging
import multiprocessing
import os
from datetime import datetime
from tqdm import tqdm
from colorama import Fore, Style
from tabulate import tabulate
import matplotlib.pyplot as plt
import requests
import ipaddress
# This line determines the target of the port scan.
# If an environment variable "TARGET" is set, it will be used as the target.
# If not, the default target is "example.com".
TARGET = os.environ.get("TARGET", "example.com")
# Here, the port ranges that the scanner should check are defined.
PORT_RANGES =
# This line determines the maximum number of processes that can run simultaneously.
# By default, this is the number of CPU cores of the system, but it can be
# customized by setting the environment variable "MAX_PROCESSES".
MAX_PROCESSES = int(os.environ.get("MAX_PROCESSES", multiprocessing.cpu_count()))
# This sets the timeout for socket operations. The default timeout is one second,
# but it can be customized by setting the environment variable "SOCKET_TIMEOUT".
SOCKET_TIMEOUT = int(os.environ.get("SOCKET_TIMEOUT", 1))
# This determines the name of the log file. By default, it's "port_scan.log",
# but it can be changed by setting the environment variable "LOG_FILENAME".
LOG_FILENAME = os.environ.get("LOG_FILENAME", "port_scan.log")
# This determines the path and name of the report file. By default, it's "Security_Testing/Port_Scann/Reports/port_scan_report.html",
# but it can be changed by setting the environment variable "REPORT_FILENAME".
REPORT_FILENAME = os.environ.get("REPORT_FILENAME", "Security_Testing/Port_Scann/Reports/port_scan_report.html")
# This determines the directory where the report is saved.
REPORT_DIRECTORY = os.path.dirname(REPORT_FILENAME)
os.makedirs(REPORT_DIRECTORY, exist_ok=True)
# This creates the directory where the report is saved, if it doesn't already exist.
# The exist_ok=True parameter prevents an error if the directory already exists.
# Logging configuration
logging.basicConfig(filename=LOG_FILENAME, level=logging.INFO, format='%(asctime)s - %(levelname)s - %(message)s')
## filename=LOG_FILENAME: This specifies that the logs should be written to a file,
# and the name of the file is the value of the LOG_FILENAME variable.
## level=logging.INFO: This sets the root logger level to INFO. This means that only events of this level and above will be tracked,
# unless the logging package is configured differently elsewhere.
# Levels you can specify include DEBUG, INFO, WARNING, ERROR, and CRITICAL.
## format='%(asctime)s - %(levelname)s - %(message)s': This is a string that specifies the layout of the log entries.
# Each "%(name)s" is a placeholder that will be replaced with the corresponding "name" from each log record.
# In this case, asctime will be replaced with the time the log record was created, levelname will be replaced with the level
# name of the log record (INFO, ERROR, etc.), and message will be replaced with the log message.
def print_banner():
ascii_banner = pyfiglet.figlet_format("OPS - Open Port Scanner")
print(ascii_banner)
def print_scan_info():
print("-" * 50)
print("Scanning Target: " + TARGET)
global start_time
start_time = datetime.now()
print("Scanning started at: " + str(start_time))
print("-" * 50)
def validate_ipv6_address(ip):
"""Prüft, ob die gegebene IP-Adresse eine gültige IPv6-Adresse ist."""
try:
ipaddress.IPv6Address(ip)
return True
except ipaddress.AddressValueError:
return False
def check_port(port_info):
ip, port = port_info
try:
if validate_ipv6_address(ip):
with socket.socket(socket.AF_INET6, socket.SOCK_STREAM) as s:
s.settimeout(SOCKET_TIMEOUT)
# Add the scope id if it is a link-local address
if ipaddress.IPv6Address(ip).is_link_local:
s.connect((ip, port, 0, YOUR_NETWORK_INTERFACE_INDEX))
else:
s.connect((ip, port))
else:
with socket.socket(socket.AF_INET, socket.SOCK_STREAM) as s:
s.settimeout(SOCKET_TIMEOUT)
result = s.connect_ex((ip, port))
except OSError:
return {"port": port, "status": "error"}
if result == 0:
logging.info("Port {} is open".format(port))
return {"port": port, "status": "open"}
else:
return {"port": port, "status": "closed"}
def get_ip_address(target):
addresses = socket.getaddrinfo(target, None)
for address in addresses:
if address == socket.AF_INET6:
# Detect if it's an IPv4-mapped IPv6 address
ip = ipaddress.IPv6Address(address)
if ip.ipv4_mapped:
return str(ip.ipv4_mapped)
else:
return address
return addresses
def generate_report(results):
headers =
data = , port) for port in results]
table = tabulate(data, headers=headers, tablefmt="pretty")
report = f'''
Port Scan Report
Port Scan Report
Target: {TARGET}
Scan started at: {str(start_time)}
Scan finished at: {str(datetime.now())}
Time taken: {str(datetime.now() - start_time)}
Ports:
{table}
'''
return report
def generate_port_range_chart(results):
open_ports = len( == "open"])
closed_ports = len( == "closed"])
labels =
values =
colors =
explode = (0.1, 0)
plt.pie(values, explode=explode, labels=labels, colors=colors, autopct='%1.1f%%', startangle=90)
plt.axis('equal')
plt.title("Port Range Chart")
plt.show()
def detect_firewall(target):
try:
response = requests.get(f"http://{target}")
if response.status_code == 200:
print(Fore.YELLOW + "nFirewall or IDS detected!")
print("The response from the target server indicates the presence of a firewall or IDS.")
print("Please exercise caution while performing the port scan.")
print(Style.RESET_ALL)
logging.warning("Firewall or IDS detected")
except requests.exceptions.RequestException as e:
print(Fore.YELLOW + "nWarning: " + str(e))
print(Style.RESET_ALL)
logging.warning(str(e))
raise e
def scan_ports():
print_banner()
print_scan_info()
try:
port_ranges = , range_info) for range_info in PORT_RANGES]
all_ports =
for start, end in port_ranges:
all_ports.extend(range(start, end + 1))
if '/' in TARGET:
if ':' in TARGET:
ip_network = ipaddress.IPv6Network(TARGET, strict=False)
else:
ip_network = ipaddress.IPv4Network(TARGET, strict=False)
target_ips =
elif ',' in TARGET:
target_ips =
else:
target_ips = ]
'''Finally, you will need to adjust your code to handle IPv6 link-local addresses correctly when you are resolving the TARGET:
In this line, I have changed socket.AF_UNSPEC to socket.AF_INET6 to ensure that it will resolve to an IPv6 address.'''
#else:
#target_ips = ]
with multiprocessing.Pool(processes=MAX_PROCESSES) as pool:
total_ports = len(all_ports) * len(target_ips)
results = list(tqdm(pool.imap(check_port, ), total=total_ports, ncols=80, bar_format='{l_bar}{bar}| {n_fmt}/{total_fmt}'))
open_ports = for port in results if port == "open"]
if open_ports:
print(Fore.GREEN + "nOpen Ports:")
for port in open_ports:
print("Port {} is open".format(port))
print(Style.RESET_ALL)
logging.info("Open ports: {}".format(open_ports))
else:
print(Fore.RED + "nNo open ports found." + Style.RESET_ALL)
logging.info("No open ports found.")
report = generate_report(results)
with open(REPORT_FILENAME, 'w') as report_file:
report_file.write(report)
generate_port_range_chart(results)
detect_firewall(TARGET)
print("Port scan report generated: {}".format(REPORT_FILENAME))
except KeyboardInterrupt:
print("nExiting Program !!!!")
logging.info("Program interrupted by the user")
except socket.error as e:
print("nServer not responding !!!!")
print(Fore.RED + "nError: " + str(e))
logging.error(str(e))
raise e
except requests.exceptions.RequestException as e:
print(Fore.YELLOW + "nWarning: " + str(e))
logging.warning(str(e))
raise e
if __name__ == '__main__':
scan_ports()
Read the full article
0 notes
Note
The void: it slammed 6bones on the ground near Error


6 notes
·
View notes
Text
aliensnipe replied to your post: “Okay, been up since around noon… got distracted by YouTube. Finished...” :
!! You know 6bones? Do you follow Zarla's other stuff??
Actually I only just now discovered this.... character.
... I might look more into that person’s stuff in the future. But. Ow. Dat fanon.
#aliensnipe#replies#and dat aesthetic#undertale/#*keels over abt body horror shit again*#aaand now i'm also intrigued by that handplates au#aaaaaa - i need to workout and draw shit tonight#bUT
3 notes
·
View notes
Text
0 notes
Text
Warrm Blood
read it on the AO3 at https://ift.tt/2ZqZwX9
by 6bones
Raquel Darling's life is perfectly on track.
Enter Steve Rogers and the bullshit that follows him.
Words: 3, Chapters: 1/1, Language: English
Fandoms: Captain America - All Media Types
Rating: Explicit
Warnings: Graphic Depictions Of Violence
Categories: F/M, M/M
Characters: Steve Rogers, James "Bucky" Barnes, Original Female Character(s) of Color, the gangs all here - Character
Relationships: James "Bucky" Barnes/Steve Rogers/Original Female Character(s), Steve Rogers/Original Female Character(s), James "Bucky" Barnes/Original Female Character(s), James "Bucky" Barnes/Steve Rogers
Additional Tags: Slow Burn, Forced Pregnancy, Children, Depression, mentions of classissm, Racism, Smut, Blowjobs, Choking, Dom/sub Undertones
read it on the AO3 at https://ift.tt/2ZqZwX9
0 notes
Text
Why long-term IPv6/IPv4 dual stack technology coexists
IPv6 is unlikely to replace IPv4 immediately, so IPv4 and IPv6 will coexist in an environment for quite some time. To provide a smooth conversion process that has little impact on existing users, a good conversion mechanism is required. This topic is the main goal of the IETF ngtrans working group. Many conversion mechanisms have been proposed and some have been used on 6Bone. The IETF recommends conversion mechanisms such as dual stacks, tunneling techniques, and network address translation:
I. IPv6/IPv4 dual stack technology
The dual stack mechanism is to make the IPv6 network node have an IPv4 stack and an IPv6 stack, and support both IPv4 and IPv6 protocols. IPv6 and IPv4 are network layer protocols with similar functions. Both are applied to the same physical platform and carry the same transport layer protocol TCP or UDP. If a host supports both IPv6 and IPv4 protocols, the host can and only Host communication supporting IPv4 or IPv6 protocols. ccie dc written and lab dumps
Second, tunnel technology
The tunneling mechanism is a mechanism for encapsulating IPv6 packets as data in IPv4 packets when necessary, so that IPv6 packets can be transmitted over existing IPv4 infrastructure (mainly IPv4 routers). With the development of IPv6, some local IPv6 networks isolated by the backbone network running IPv4 have emerged. In order to realize communication between these IPv6 networks, tunnel technology must be adopted. The tunnel is transparent to the source site and the destination site. At the entrance of the tunnel, the router encapsulates the IPv6 data packet in IPv4. The source and destination addresses of the IPv4 packet are the IPv4 address of the tunnel entry and exit respectively, at the tunnel exit. Then, the IPv6 packet is taken out and forwarded to the destination site. The advantage of the tunneling technology is the transparency of the tunnel. The communication between the IPv6 hosts can ignore the existence of the tunnel, and the tunnel only functions as a physical channel. Tunnel technology has been widely used in the initial stage of IPv4 to IPv6 evolution. However, tunneling technology cannot implement communication between IPv4 hosts and IPv6 hosts.
Third, network address translation technology
The Network Address Translator (NAT) technology treats an IPv4 address and an IPv6 address as internal and global addresses, respectively, or vice versa. For example, when an internal IPv4 host communicates with an external IPv6 host, the IPv4 address (equivalent to an internal address) is converted into an IPv6 address (equivalent to a global address) in the NAT server, and the server maintains a mapping table of IPv4 and IPv6 addresses. Conversely, when an internal IPv6 host communicates with an external IPv4 host, the IPv6 host is mapped to an internal address, and the IPv4 host is mapped to a global address. NAT technology can solve the problem of interworking between IPv4 hosts and IPv6 hosts.
0 notes
Text

3/11/24
Make A Change...Kill Yourself
Oblivion Omitted
====
One Man Metal from Denmark. DSBM (Depressive Suicidal Black Metal). This is a perfect album for a working rainy day like today. Overall I have a tough time with the title or even DSBM in general because I'm worried that it promotes very destructive behavior both to oneself and potentially others. Setting aside that musically the piece is well done--it's very clear and deliberate beautiful black metal that is not what you would expect.
However, there is something that stops me from going deeper on this guy because of the promotion of sui****.
6/10
#6bones#dsbm#album#spotify#albumreview#musicdiscovery#album review#albumoftheday#nowplaying#now listening#Music Review#Music Recommendation#black metal#metal
8 notes
·
View notes
Text

11/21/23
Slowdive
everything is alive
====
Dreamwave, dream-pop, shoegaze Cali music. I've never really been into this music before, but it does have a charming sense about it. It's not meant for me, but I can certainly see a great lane for this group for great mass appeal.
6/10
#6bones#slowdive#album#spotify#tumblr#aesthetic#albumreview#musicdiscovery#album review#albumoftheday#nowplaying#musicislife#pitchfork#albumart
7 notes
·
View notes
Text

1/7/2022
The Weeknd
Dawn FM
====
Hard to really put my finger on if this is a coming to age tale of The Weeknd. Definitely hitting the poppy Tron, tech sounds meant for radio. But now feeling more like he's just becoming more of a figure than an artist. No more Wicked Games.
6/10
#6bones#the weeknd#album#spotify#tumblr#aesthetic#albumreview#musicdiscovery#album review#albumoftheday#nowplaying#musicislife#pitchfork#albumart
5 notes
·
View notes
Text

3/9/24
Mannequin Pussy
I Got Heaven
====
This album has been getting so much hype. They made one of these albums that is hard to hate--I think there is something for everyone in this piece. Rock, punk, alt rock with female vocals, it's a well produced piece of art, there is no doubt about that.
Overall, this album just isn't for me and I see them as a flash. They will do the festival circuits this year and be propped up by big blogs and labels a bit before they are thrown away. I'm not buying them.
6/10
#6bones#mannequin pussy#album#spotify#albumreview#musicdiscovery#album review#albumoftheday#nowplaying#now listening#Music Review#Music Recommendation#rock#alt rock#punk
2 notes
·
View notes
Text

3/8/24
Superheaven
Jar
====
Shoegaze from 2013. Sounds alot like Soundgarden with the songs feeling a bit depressing, yet hopeful. They haven't released an album since 2015, but the album, 'Jar' was a really nice introduction into them and back into shoegaze in general. The one thing that I would have wanted was some diversity, but it certainly has bangers like 'Youngest Daughter'.
6/10
#6bones#superheaven#shoegaze#album#spotify#albumreview#musicdiscovery#album review#albumoftheday#nowplaying#now listening#Music Review#Music Recommendation
4 notes
·
View notes
Text

9/28/23
Peeling Flesh
Human Pudding
====
Just like you would expect. I don't think they take themselves too seriousy either. That being said, this is a really solid deathcore. I'd throw this on at a party no doubt.
6/10
4 notes
·
View notes
Text

2/17/24
Depeche Mode
Ultra
====
Circa 1997. Pretty long album with traces of ambience, pop and down-tempo. Something to throw on in the background wile you work, which is exactly what I did. I know this is one of their most legendary albums, but I failed them with the lack of focus I have, not them. A very deep concept piece of work.
6/10
#6bones#depeche mode#album#spotify#albumreview#musicdiscovery#album review#albumoftheday#nowplaying#now listening#Music Review#Music Recommendation
2 notes
·
View notes

