#7. How to set switch port security
Text
youtube
#Hi friends in this video tutorial I’m going to practically show you cisco switch configuration step by step from basic to advance#I use Cisco catalyst 9200l 48port switch to make the video. In this video#I will show you#1. How to set hostname#2. How to Set username and password (enable#console#ssh)#3. How to assign IP in vlan 1 and disable vlan#4. How to crerate vlan and assign IP#5. How to enable inter vlan routing#6. How to configure trunk port#7. How to set switch port security#Aafter complete this video you can easily configure any cisco switch and can manage small and medium network.#This Video is two Part#• One-part configuration on switch#• 2nd part-after configuration I will connect my Two Laptop in Two different VLAN on the switch and I will assign static IP to their inter#Youtube
0 notes
Text
Logos and Pathos (AOS Edition) Chapter Sixteen
AOS! Spock x Empath! Reader
Chapter Sixteen: Hidden Intentions
Summary: (Y/N), Kirk, and Khan make a risky move to board the Vengeance, and Spock is separated from (Y/N). That doesn't mean he's going to stop trying to help them, though.
“You want to do what?” hissed Scotty across the communicator.
“We’re coming over there,” said Kirk as he, (Y/N), Khan, and the security guards walked through the ship. “Sulu’s maneuvering the Enterprise into position as we speak.”
“To this ship? How?” asked Scotty.
“There’s a cargo door, Hangar 7, access port 101A,” said Khan. “You need to find the manual override to open that airlock.”
“Are you crazy?” cried Scotty. “Whoever you are.”
“Just listen to him, Scotty. It’s gonna be alright,” said Kirk.
“It is not gonna be alright. You want me to open an airlock into space, whereupon I will freeze, die, and explode!” said Scotty.
l
Spock paced the Bridge, reviewing his options. He paused and turned to Uhura.
“Lieutenant, from our current position, is it possible to establish contact with New Vulcan?”
Uhura frowned in confusion but nodded. “I’ll do my best.”
“Thank you,” said Spock, sitting down in the captain’s chair. “Mr. Sulu, what’s the status of the other ship?”
“Their systems are still offline,” reported Sulu. “I’m aligning our ship now.”
Spock nodded and stared at the viewscreen. Hopefully, his call would go through.
l
Belowdecks, (Y/N), Khan, and Kirk had suited up to be shot through literal space towards the airlock Scotty needed to open.
“Scotty, how we doing over there?” asked Kirk, in position.
“Captain, I wish I had better news,” said Scotty over the comms. “They’ve locked out access to the ship’s computer. They’ll have full weapons in three minutes. That means next I won’t be able to stop them from destroying the Enterprise. Stand by.”
“We’ll need to move quickly, then,” said (Y/N), frowning.
“Captain, (Y/N), the ships are aligned,” reported Spock.
“Copy that,” said Kirk. “Scotty!”
“I’m in the hangar. Give me a minute,” said Scotty. A moment passed. “Whoa, whoa, whoa, hold on, now, Captain. This door is very wee. I mean, you know, small. It’s four square meters, tops. It’s gonna be like jumping out of a moving car, off a bridge, into your shot glass.”
“It’s okay. I’ve done it before,” said Kirk.
(Y/N) and Khan looked at him in confusion.
“It was vertical,” he said. “We jumped onto a…It was a…” He trailed off, not bothering to explain.
“Did you find the manual override?” asked Khan.
“Right, the manual override, Scotty,” said Kirk.
“Not yet, not yet,” said Scotty.
“Captain, (Y/N), before you launch, you should be aware there is a considerable debris field between our ships,” reported Spock, which was even more reason for him to want (Y/N) safe by his side.
“Spock, not now,” said Kirk. “Scotty, you good?”
“It’s not easy!” replied Scotty.
“You’re the best we have. You can do it,” said (Y/N) encouragingly, still calm.
“How are you so calm?” whispered Kirk, turning off his comms.
“We either die out there in space or here on the Enterprise if it goes wrong,” said (Y/N). They crossed their arms. “And if I die, I’m doing it trying to take down Marcus.”
Kirk blinked, and Khan cocked his head as he regarded them curiously.
“Okay, Captain, stand by!” said Scotty finally. “Yes! Okay, okay! I’m set to open the door.”
“You ready?” asked Kirk.
“Are you?” said Khan coolly.
“As we can be,” said (Y/N). The screen of their helmet switched on.
“Spock, pull the trigger,” said Kirk.
“Yes, Captain,” came the measured response that concealed all of Spock’s misgivings about what they were about to attempt. “Launching activation sequence in three, two, one.”
The doors snapped open, and the suction of space tossed Khan, Kirk, and (Y/N) out into space. They shot through the “air”, trying to follow the path calculated by their helmets. As they flew, the group approached the debris field and braced for evasive maneuvers.
“Captain, there’s debris in your course,” said Spock.
“Got it,” said Kirk, activating small boosters and flying off to the side. His veering threw him greatly off course, and he had to begin getting back on course, difficult with the various pieces of metal.
“(Y/N), you’re approaching debris,” warned Spock.
“I see it,” said (Y/N), adjusting their course to dodge.
“Damn it!” cursed Kirk.
“Captain, what is it?” asked Spock.
“My helmet was hit,” said Kirk. “Uhura, tell me you have Mr. Scott back.”
“His communicator is working. I don’t know why he isn’t responding,” said Uhura.
“Khan, use evasive action,” cautioned Spock. “There is directly ahead.”
“I see it,” said Khan, dodging the first bit but hitting the next and going flying.
“Was Khan hit?” asked (Y/N).
“We are trying to find him now,” confirmed Spock.
“Captain, you need to adjust your target destination to 183 by 473 degrees,” said Sulu.
“Spock, my display’s dead. I’m flying blind,” said Kirk.
“Hitting your target destination is mathematically impossible,” said Spock, furrowing his brow.
“Spock, if I get back, we really need to talk about your bedside manner,” said Kirk, sighing.
“Captain,” said (Y/N). “My display is working.”
“As is mine.” Out of nowhere, Khan appeared behind and above (Y/N), right over their shoulder.
“Kirk, you’re two hundred meters ahead,” said (Y/N). “At about one o’clock.”
“Follow me,” said Khan.
Kirk managed to veer closer, and they all sped towards the airlock door—still shut tight.
“Scotty, we’re getting close. We need a warm welcome,” said Kirk. “Do you copy? Do you copy?”
“Scotty?” called (Y/N).
“If you can hear us, Mr. Scott, open the door in ten, nine—” began Spock.
“Scotty!” shouted Kirk. The closed door was approaching quickly.
“Eight. Seven.”
“Come on, come on, Scotty!”
“Six, five. Four. Three. Two. Mr. Scott, now!” Spock’s voice rose.
At the last moment, the airlock snapped open, and Khan, Kirk, and (Y/N) sailed into the ship. A man’s body shot out behind them, but they were just focused on the fact that they were still flying.
The airlock shut, and the pressure left. Khan, Kirk, and (Y/N) fell to the ground, rolling to a rough stop. They groaned and lifted their head to look at Scotty, who had tied himself to the lever to avoid being sucked into space.
“Welcome aboard,” he said, staring at them.
“It’s good to see you, Scotty,” said Kirk.
“You did great,” said (Y/N), catching their breath and giving a faint thumbs-up.
“Who is that?” asked Scotty, looking at Khan.
“Khan, Scotty. Scotty, Khan,” said Kirk, waving a hand.
“Hello,” said Scotty, confused but nodding.
“They’ll know we’re here,” said Khan, all business. “I know the best way to the Bridge.”
Kirk and (Y/N) nodded, and all three took off their suits and picked up their phasers—locked to stun.
Khan raised a brow. “Theirs won’t be,” he remarked.
“Try not to get shot,” said Kirk simply. He wasn’t risking giving Khan a gun capable of killing.
The four ran off into the belly of the Vengeance.
l
Aboard the Enterprise, Uhura turned towards Spock. “Commander, I have that transmission as requested.”
“On screen, pleased,” said Spock, inkling his head.
“Stand by.”
Two familiar faces appeared on the viewscreen.
“Mr. Spock,” greeted Spock Prime.
“Mr. Spock,” said Spock. “Mx. (Y/N).”
“Hello,” said (Y/N) Prime, smiling.
l
“They’re going to have full power and we’re walking?!” cried Scotty as he, Kirk, Khan, and (Y/N) ran through the halls of the Vengeance.
“The turbolifts can be tracked,” said (Y/N).
Khan nodded. “And then Marcus would have us trapped.” He paused by some computers. “This path runs adjacent to the engine room. They know they won’t be able to use their weapons here without destabilizing the warp core, which gives us the advantage.” He advanced through the ship.
“Where’d you find this guy?” wondered Scotty.
“It’s a long story,” said Kirk.
l
“I will be brief,” said Spock, addressing Spock Prime and (Y/N) Prime. “In your travels, did you ever encounter a man named Khan?”
He watched (Y/N) Prime stiffen and Spock Prime’s hand reach out to them. Clearly, they knew who Khan was.
“As you know, we have made a vow never to give you information that could potentially alter your destiny,” said Spock Prime. “Your path is yours to walk, and yours alone.”
Spock looked down, and Spock Prime and (Y/N) Prime exchanged looks.
“That being said,” continued (Y/N) Prime, and Spock looked back up. “Khan Noonien Singh is the most dangerous adversary the Enterprise ever faced.”
“He is brilliant, ruthless, and he will not hesitate to kill every single one of you,” said Spock Prime.
“He believes himself a ‘superior’ being, and he believes he deserves to control others because of it,” said (Y/N) Prime, leaning forward. “He will seize power by any means necessary.”
Spock Prime furrowed his brow slightly. “Did you defeat him?”
Again, (Y/N) Prime looked at Spock Prime worriedly and touched his hand. He looked solemnly at Spock.
“At great cost. Yes,” said Spock Prime.
“How?” asked Spock.
“We had to sacrifice a great deal,” said (Y/N) Prime, voice soft with emotion. Their past encounters with Khan had left a mark on them, one that would never be washed away.
“But you understand his danger now, and I assume he does not know your suspicions,” said Spock Prime.
Spock shook his head. “No. He is currently claiming to ‘work with us.’ ”
Spock Prime nodded. “Then use that to your advantage.”
Spock inclined his head in acknowledgement.
“Commander Spock,” said (Y/N) Prime, and he looked at them. “A final word of warning: do not let Khan near your (Y/N). His intentions with them can’t be trusted.” The communications shut off.
Spock stiffened, and Bones’s eyes widened in alarm.
“(Y/N) is on that ship with him,” breathed Bones, staring at Spock alertly.
Spock’s hand tensed around the arm of the captain’s chair. (Y/N) was with the most dangerous man Spock Prime and (Y/N) Prime had ever met, and, apparently, Khan was a threat to them even more than others.
And Spock couldn’t do anything to help them.
“Lieutenant Uhura,” said Spock. “Assemble all senior medical and engineering staff in the weapons bay.”
“Yes, Commander,” said Uhura, nodding and getting up, a bit confused.
“Good god, man, what about (Y/N) and Scotty and Jim?!” cried Bones.
“We must ensure Khan does not win,” said Spock. “That is the way to help them.”
“You actually are trying to protect them?” said Bones.
“Of course,” said Spock. It was obvious to him that he’d do everything in his power for the people he cared for—for the person he loved.
“Alright, then.” Bones crossed his arms. “What do you need?”
“You inadvertently activated a torpedo, Dr. McCoy,” said Spock. “Could you replicate the process?”
“Why the hell would I want to do that?” said Bones indignantly.
“Can you or can you not?” repeated Spock.
“Dammit, man, I’m a doctor not a torpedo technician!” said Bones.
“The fact that you are a doctor is precisely why I need you to listen very carefully,” said Spock. He had to make sure Khan didn’t have the power he needed to hurt the Enterprise, to hurt (Y/N). Spock had to handle Khan as soon as possible.
He had to protect (Y/N).
Taglist:
@a-ofzest
@grippleback-galaxy
@genderfluid-anime-goth
@groovy-lady
@im-making-an-effort
@unending-screaming
@h-l-vlovesvintage
@neenieweenie
@keylimeconstellation
@wormwig
@technikerin23
@ilyatan
@nthdarkqueen
@kyalov
@starlit-cass
#logos and pathos#x reader#gn reader#nb reader#x gn reader#x nb reader#empath reader#empath!reader#empath#commander spock#spock#mr spock#spock x reader#mister spock#star trek spock#spock aos#aos spock#aos#star trek aos#star trek#star trek alternate original series#star trek x reader#star trek aos x reader#aos spock x reader
18 notes
·
View notes
Text
I am the entire IT department of this place.
I am Help Desk.
I am Sysadmin.
I am executive management. Mainly because both of my actual bosses (On-site General Manager and remote corporate overlord) have no hard technical background. I was a software engineer for 7 years before this. And holy shit the whiplash.
My formal title is "IT Operations Manager", but I have nobody to manage. It's only me. I have complete authority over the IT infrastructure and am spending like 30% of my time doing help desk work. One minute I am setting top-level security policy, and the next, I am using a knife to pry an ethernet cable out of a laptop because apparently using the plastic tab to pull it out isn't intuitive for everyone.
I have learned a hell of a lot in the last few months.
But the thing that inspired this post, that I really want to talk about, but am struggling to find people to discuss with...
If I am walking across the facility to deal with an issue, there's like a 30% chance that someone will walk up to me with another issue that I need to deal with. I haven't implemented a help desk ticketing system yet. Haven't had the space.
But if I happen to be exhausted or in a bad mood when I respond to them, they will be hesitant to tell me when things break. This makes my job worse. I am not THEIR manager, but I'm still one of the Top Brass in this place. It doesn't matter how soft of a person I actually am, the workers here still don't want to upset me, and will swerve the hell away from me if they think they might be.
Even if I didn't care about being liked and was totally Machiavellian about how I treat people at work, this is bad.
I've read so much about the emotional labor of customer service.
Turns out, management has emotional labor, too. Except here, nobody will tell me when I'm being unapproachable. And it's also nobody else's problem.
If I can't be consistently friendly to the people around me, they will be disinclined to communicate with me. If cracks in the infrastructure appear, I won't know until something catches fire.
I cannot safely express my frustration or even exhaustion to *anyone* here, without making my job harder, regardless of how good of a rapport I may have with them.
I am the only computer professional in the building. Even the most well-meaning instance of "He is tired and overworked, let's not put more on his plate" could keep me ignorant of an impending disaster.
The entire intranet got completely fucked because someone plugged both ports of an IP phone into the same dumb switch, and I was up until 3AM trying to figure out what the fuck happened and I still haven't had the space to properly research how to overhaul this place's hackjob of a network out of the stone age. But they don't want to bother me with silly shit like helping people move cubicles when the job I was actually hired to do was implement automation into this manufacturing process.
My Corporate Overlords swear that they are working on hiring me help. But maybe I'm not squeaky enough of a wheel to get some grease.
/rant
2 notes
·
View notes
Text
How To Setup Elasticsearch 6.4 On RHEL/CentOS 6/7?
What is Elasticsearch?
Elasticsearch is a search engine based on Lucene. It is useful in a distributed environment and helps in a multitenant-capable full-text search engine. While you query something from Elasticsearch it will provide you with an HTTP web interface and schema-free JSON documents. it provides the ability for full-text search. Elasticsearch is developed in Java and is released as open-source under the terms of the Apache 2 license.
Scenario:
1. Server IP: 192.168.56.101
2. Elasticsearch: Version 6.4
3. OS: CentOS 7.5
4. RAM: 4 GB
Note: If you are a SUDO user then prefix every command with sudo, like #sudo ifconfig
With the help of this guide, you will be able to set up Elasticsearch single-node clusters on CentOS, Red Hat, and Fedora systems.
Step 1: Install and Verify Java
Java is the primary requirement for installing Elasticsearch. So, make sure you have Java installed on your system.
# java -version
openjdk version "1.8.0_181"
OpenJDK Runtime Environment (build 1.8.0_181-b13)
OpenJDK 64-Bit Server VM (build 25.181-b13, mixed mode)
If you don’t have Java installed on your system, then run the below command
# yum install java-1.8.0-openjdk
Step 2: Setup Elasticsearch
For this guide, I am downloading the latest Elasticsearch tar from its official website so follow the below step
# wget https://artifacts.elastic.co/downloads/elasticsearch/elasticsearch-6.4.2.tar.gz
# tar -xzf elasticsearch-6.4.2.tar.gz
# tar -xzf elasticsearch-6.4.2.tar.gz
# mv elasticsearch-6.4.2 /usr/local/elasticsearch
Step 5: Permission and User
We need a user for running elasticsearch (root is not recommended).
# useradd elasticsearch
# chown -R elasticsearch.elasticsearch /usr/local/elasticsearch/
Step 6: Setup Ulimits
Now to get a Running system we need to make some changes of ulimits else we will get an error like “max number of threads for user is too low, increase to at least ” so to overcome this issue make below changes you should run.
# ulimit -n 65536
# ulimit -u 2048
Or you may edit the file to make changes permanent
# vim /etc/security/limits.conf
elasticsearch - nofile 65536
elasticsearch soft nofile 64000
elasticsearch hard nofile 64000
elasticsearch hard nproc 4096
elasticsearch soft nproc 4096
Save files using :wq
Step 7: Configure Elasticsearch
Now make some configuration changes like cluster name or node name to make our single node cluster live.
# cd /usr/local/elasticsearch/
Now, look for the below keywords in the file and change according to you need
# vim conf/elasticsearch.yml
cluster.name: kapendra-cluster-1
node.name: kapendra-node-1
http.port: 9200
to set this value to your IP or make it 0.0.0.0 ID needs to be accessible from anywhere from the network. Else put your IP of localhost
network.host: 0.0.0.0
There is one more thing if you have any dedicated mount pint for data then change the value for
#path.data: /path/to/data to your mount point.
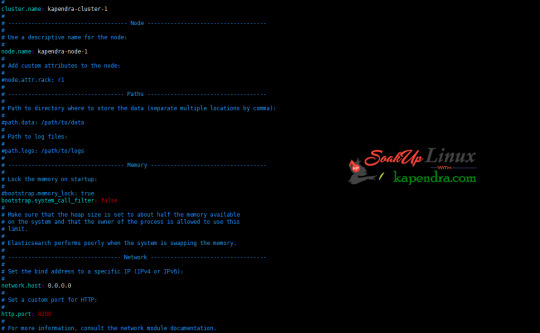
Your configuration should look like the above.
Step 8: Starting Elasticsearch Cluster
As the Elasticsearch setup is completed. Let the start Elasticsearch cluster with elastic search user so first switch to elastic search user and then run the cluster
# su - elasticsearch
$ /usr/local/elasticsearch/bin/elasticsearch
22278
Step 9: Verify Setup
You have all done it, just need to verify the setup. Elasticsearch works on port default port 9200, open your browser to point your server on port 9200, You will find something like the below output
http://localhost:9200 or http://192.168.56.101:9200
at the end of this article, you have successfully set up Elasticsearch single node cluster. In the next few articles, we will try to cover a few commands and their setup in the docker container for development environments on local machines.
Read the full article
2 notes
·
View notes
Text
Siemens Automation Products: The future of Industrial Automation
Siemens has emerged as a frontrunner in the constantly changing landscape of industrial automation, offering cutting-edge solutions that boost productivity, efficiency, and dependability. They provide a wide selection of automation goods for various industries, ranging from simple control functions to complicated production procedures. In this article, we will look at some of Siemens automation products and how they have shaped present-day industry.

SIMATIC Controllers
SIMATIC S7-1200 and S7-1500:
SIEMENS is known for their automation portfolio that has SIMATIC S7-1200 and S7-1500 series at its core. Due to their versatility, efficiency and user-friendliness, these controllers have gained a great name. The S7-1200 is compact and has an inbuilt input/output ports making it suitable for small applications. On the other hand, S7-1500 is suitable for high-end performance when it comes to complicated tasks because it has sophisticated diagnostic systems, built-in security features as well as wide-ranging communication facilities.
SIMATIC S7-200 SMART:
S7-200 SMART has been purposed for minor automation undertakings that represent a value for money while also being very strong. It can be used in numerous cases; it has either a functional format or embedded communication facilities hence making it flexible enough to serve various functions like controlling machines and organizing buildings.
HMI (Human-Machine Interface) Systems
SIMATIC HMI Panels:
Siemens' HMI panels provide operators with a user-friendly and intuitive interface for surveillance and control of industry processes. The panels go from simple text-to-speech displays to sophisticated touch screen displays with high resolution graphics. It can be easily integrated with the SIMATIC controllers, meaning that data is exchanged effectively, and timely monitoring done continuously.
SCADA Systems
SIMATIC WinCC:
SCADA (Supervisory Control and Data Acquisition) system is a highly efficient system made by Siemens and its name is WinCC (Windows Control Center). It has been fitted to work by providing solutions in the field of monitoring and control for industries. Databasing, allowing for real time viewing of data as well as offering of advanced analytical tools are some of these features found in WinCC that help businesses to improve their performance thus keeping them abreast about what is going on within their operations.
Industrial Communication
PROFINET and PROFIBUS:
Siemens has strong industrial communication offerings with PROFINET and PROFIBUS standards. PROFINET is an Ethernet-based protocol designed for high-speed, deterministic communication; this makes it ideal for real-time systems. On the other hand, PROFIBUS is a fieldbus protocol that guarantees reliable communication in difficult industrial settings.
Industrial Ethernet Switches:
Siemens’ Industrial Ethernet switch allows for quick and safe communication among devices in an industrial network. This kind of switch is made to survive difficult situations, which guarantees consistent transfer of information even in tough conditions.
Drives and Motion Control
SINAMICS Drives:
Siemens’ sacramental SINAMICS lifts cover everything from basic frequency converters to high-end servo drives. These drives ensure precise motor control, and high energy efficiency while at the same time helping to optimize processes. They are utilized in a variety of applications including conveyor belts, pumps, fans and machine tools.
SIMOTION:
Siemens’ SIMOTION is its motion control system that offers highly efficient solutions for complicated motion tasks. It brings together motion control, logic control and technology functions at one site, thus ensuring machines and processes are controlled with precision and effectiveness.
Process Automation
SIMATIC PCS 7:
Siemens’ PCS 7 is an advanced process control system for large-scale industrial processes. It has features like integrated engineering, scalable architecture and advanced control functions. As a result, it is commonly used in the chemical, pharmaceutical and oil & gas sectors where precision and reliability in process control are vital.
Conclusion
Siemens automation products have drastically modified the industry scene in terms of increased efficiency, reliability and productivity. Industrial automation is still dominated by Siemens through strong controllers and intuitive human machine interfaces (HMIs) besides sophisticated SCADA systems and durable communication protocols. For businesses out there that want higher automation, reduced operational costs and remain competitive in a changing environment code these technologies in one code.
#siemens automation products#siemens dealers in ahmedabad#siemens industrial automation#siemens programmable logic controller#siemens controller#siemens#siemens plc controller#siemens hmi#siemens ac drive#siemens servo motor#Siemens SCADA
0 notes
Text
Best Golf Push Carts
Golf is a sport that offers not only a challenging physical activity but also a serene and enjoyable experience on beautifully manicured greens. To make the game even more enjoyable and convenient, golf enthusiasts have embraced the use of golf push carts. These innovative devices have revolutionized the way golfers transport their clubs and equipment around the course, replacing the traditional method of carrying or using motorized carts. In this article, we’ll explore the benefits and features of golf push carts and how they contribute to a more relaxed and efficient golfing experience.

Type of golf push carts?
Golf push carts come in a variety of types, each designed to cater to different preferences and needs of golfers. Here are some of the common types of golf push carts:
Three-Wheel Push Carts
These are the traditional style of golf push carts, featuring a single wheel at the front and two wheels at the back. They offer stability and are easy to maneuver, making them a popular choice among golfers. The single front wheel allows for easy swiveling, making navigation through the course smooth.
Four-Wheel Push Carts
Four-wheel push carts provide enhanced stability and balance due to the additional wheel. They are ideal for golfers who prefer a more secure and steady cart, especially on hilly or uneven terrain. Four-wheel carts often come with advanced features such as adjustable handles, extra storage space, and improved braking systems.
Electric Push Carts (Motorized Carts)
Electric push carts, also known as motorized carts or electric trolleys, are equipped with battery-powered motors that assist in propelling the cart. These carts eliminate the need for manual pushing, reducing physical strain on the golfer. Electric push carts come with various speed settings and often include additional features like distance tracking, remote control functionality, and USB charging ports.
Remote-Controlled Carts
These carts take convenience to the next level by allowing golfers to control the cart’s movement remotely. With a handheld remote, golfers can guide the cart to move forward, backward, left, or right, freeing them from the need to be near the cart at all times.
Collapsible Push Carts
Collapsible push carts are designed for easy storage and transport. They can be folded down to a compact size, making them convenient for golfers with limited storage space or those who frequently travel with their golf equipment.
Push-Pull Combo Carts
These versatile carts can be used as both push and pull carts, offering flexibility depending on the golfer’s preference. The handle and wheel arrangement can be adjusted to switch between pushing and pulling the cart.
Umbrella Holder Carts
Some push carts come equipped with an umbrella holder, providing a convenient way to shield yourself from the sun or rain while on the course. This feature is particularly useful in varying weather conditions.
Junior Golf Push Carts
Designed specifically for younger golfers, junior push carts are scaled-down versions of regular carts. They are lightweight, easy to handle, and help junior golfers build good habits early on.
These different types of golf push carts cater to a wide range of golfers, ensuring that everyone can find a cart that suits their playing style, preferences, and needs on the course. Whether you’re looking for a traditional three-wheel cart, an electric motorized cart, or something in between, there’s a push cart out there to enhance your golfing experience.
Top 10 Golf push Cart Reviews
In this section, we’ll talk about 10 most popular golf push carts with features, colors, pros, cons etc.
1. Bag Boy Nitron
2. Bag Boy Quad XL
3. CaddyTek Caddylite 15.3 V2
4. CaddyTel Explorer V8 SuperLite
5. Clicgear Rovic RV2L
6. SereneLife SLG3W
7. CaddyTek Caddylite 11.5 V3
8. Sun Mountain Pathfinder PX3 Black-Inferno
9. JEF WORLD of Golf Deluxe Steel
10. Jovial
Full Article here: Best Golf Push Carts
0 notes
Text
DIY Plumbing: Top 10 Common Issues and How to Fix Them
For the do-it-yourself enthusiast, tackling minor issues around the house can be both a pleasure and a challenge. Plumbing, in particular, has its fair share of problems that most homeowners face at some point. While major issues may necessitate professional services like Plumber Byford or Plumber Port Kennedy, many everyday plumbing concerns can be addressed with a bit of know-how and elbow grease. In this guide, we'll explore the top 10 common DIY plumbing issues and provide easy-to-follow steps to help you resolve them without calling in the pros.

1. Dripping Faucets Solution: Turn off the water supply to the faucet. Disassemble the faucet handle and inspect the washer. If worn out, replace it, reassemble the faucet, and turn the water supply back on.
2. Slow-Draining Sink Solution: Remove any visible obstructions from the drain. Use a plunger to create suction. If that fails, try a mixture of baking soda and vinegar followed by hot water to dissolve blockages.
3. Clogged Shower Drain Solution: Use a drain snake or a straightened wire hanger to pull out any hair or soap buildup. Flush with hot water.
4. Running Toilet Solution: Open the toilet tank and inspect the flapper. If it's not sealing properly, adjust its chain or replace it. Check the fill valve for any malfunctions and replace if necessary.
5. Leaky Pipes Solution: Turn off the water supply. Clean and dry the affected area. Use a patch kit or plumber’s tape to seal minor leaks.
6. Low Water Pressure Solution: Check if the low pressure is affecting all faucets. If it's only one faucet, clean the aerator by removing and rinsing it. If the whole house is affected, it might be best to consult a professional.
7. Jammed Garbage Disposal Solution: Turn off the power. Use an Allen wrench to manually turn the base of the garbage disposal, freeing any jams. Press the reset button and restore power.
8. Overflowing Toilet Solution: First, turn off the water supply. Use a plunger to clear any blockages. If it doesn't work, consider using a drain snake.
9. Water Heater Issues Solution: For insufficient heat, check the thermostat settings. Ensure the heating elements are working. If there's no hot water, the pilot light might have gone out. If you're unsure, it's best to consult a professional.
10. Frozen Pipes Solution: Open the faucet to let melted water flow out. Gradually apply heat using a hairdryer or a heating pad. Avoid using open flames. If a pipe bursts, turn off the main water supply and call a plumber immediately.
11. Noisy Pipes Solution: Noisy pipes can be caused by water hammer or loose pipe fittings. To address water hammer, you can install water hammer arrestors. For loose pipe fittings, try securing the pipes better with clamps or adding padding around them to prevent them from vibrating against the wall.
12. Bad Water Taste or Smell Solution: Regularly clean faucets and aerators. If the issue persists, consider installing a whole-house water filtration system. Sometimes, the water source might be responsible, so it's essential to consult with local water authorities.
13. Constantly Running Sump Pump Solution: Check for debris or clogs in the discharge line. Ensure the float switch is functional and not tangled. If issues persist, inspect the check valve; it might be installed backward.
14. Sewer System Backup Solution: This is a significant concern and may be a bit much for DIY. Initially, check for noticeable blockages in floor drains. If the problem is widespread, avoid using water in the house and call a professional immediately.
15. Slow Filling Toilet Tank Solution: Check the water shut-off valve; ensure it's fully open. Clean the toilet fill valve as accumulated dirt might slow down the water flow. If this doesn't solve the problem, consider replacing the fill valve.
In Conclusion: Empowerment Through Knowledge
Plumbing can seem complicated, but with a little patience and the right tools, homeowners can handle many minor issues. Empowering yourself with basic knowledge not only saves money but also offers immense satisfaction. However, it's essential to know when to call the professionals.
The Blu Frog Plumbing Assurance
While these DIY fixes can handle minor plumbing issues, certain situations will always require the expertise and skill set of professionals. For residents in WA, Blu Frog Plumbing offers unmatched proficiency and dedication. Known for their reputation for excellence, the Blu Frog Plumbing team is fully licensed and insured to tackle any plumbing concern. But beyond their technical expertise lies a commitment to client satisfaction and a personal touch that sets them apart. They believe in maintaining an open dialogue, understanding their customers’ expectations, and delivering top-tier service with a human touch. Remember, DIY can get you far, but when you need expert intervention, Blu Frog Plumbing is the name to trust.
0 notes
Text
How to Protect Your Industrial Switches from Damage
Introduction: Industrial switches serve as the backbone of modern manufacturing and automation systems, facilitating efficient data communication and network management. Their reliable operation is essential for maintaining seamless processes and preventing costly downtime. In this in-depth guide, we'll delve into a range of comprehensive strategies to safeguard your industrial switches from damage, ensuring consistent performance and the longevity of your critical systems.

1. Optimal Environment Selection:
The foundation of switch protection starts with choosing the right installation environment. Avoid areas with extreme temperature fluctuations, high humidity levels, corrosive chemicals, and excessive dust. If your industrial setting cannot provide ideal conditions, consider utilizing climate-controlled enclosures to create a controlled environment that shields switches from external stressors.
2. Ruggedized Industrial Switches:
In environments prone to vibrations, shocks, and adverse conditions, investing in ruggedized industrial switches is a prudent choice. These switches are purpose-built to withstand the challenges of industrial settings, from manufacturing floors to outdoor installations. Ruggedized switches are constructed with reinforced casings and components, minimizing the risk of damage due to environmental factors.
3. Surge Protection and Power Conditioning:
Power surges and fluctuations can cause irreversible damage to industrial switches. Employ surge protection devices and uninterruptible power supplies (UPS) to safeguard switches against voltage spikes caused by lightning strikes or electrical grid irregularities. Power conditioning equipment ensures a stable power supply, reducing the risk of sudden voltage changes that could harm switches.
4. Comprehensive Cable Management:
Disorganized cables can lead to accidental disconnections or excessive strain on switch ports. Implement a meticulous cable management system that includes cable trays, labels, and cable ties. Organized cabling minimizes the risk of human error, preventing cable-related damage and maintaining efficient network connectivity.
5. Regular Maintenance Routine:
Scheduled maintenance is paramount to identifying potential issues before they escalate. Regularly inspect switches for signs of wear, corrosion, loose connections, or damaged components. Develop a comprehensive maintenance checklist that includes visual inspections, performance tests, and firmware updates.
6. Environmental Monitoring Systems:
Implement environmental monitoring systems that track factors such as temperature, humidity, and air quality around your switches. These systems provide real-time data and alerts if conditions deviate from optimal ranges. Swift responses to such alerts can help prevent damage caused by unfavorable environmental conditions.
7. Dust and Debris Protection:
Dust and debris accumulation can compromise switch performance over time. Install dust covers and enclosures to shield switches from airborne particles. Regularly clean and maintain enclosures to prevent the buildup of contaminants that could affect switch functionality.
8. EMI and RFI Shielding:
Electromagnetic interference (EMI) and radio-frequency interference (RFI) can disrupt switch operations. Incorporate effective shielding and grounding techniques to mitigate the impact of these interferences. Maintain proper separation between data cables and power cables to minimize cross-talk and interference.
9. Controlled Physical Access:
Limit access to switch cabinets and enclosures to authorized personnel only. Implement strict access controls, security protocols, and surveillance measures to prevent physical tampering or accidental damage to switches.
10. Redundancy and Backup Solutions:
Implement redundancy and backup systems to ensure minimal disruption in the event of switch failures. Redundant switches or network paths guarantee continuity even if a component malfunctions. Regularly test and update backup systems to ensure their reliability.
11. Training and Employee Awareness:
Educate your staff on the proper handling and maintenance of industrial switches. Provide training on cable management, correct installation procedures, and the significance of adhering to best practices. Well-informed employees play a critical role in preventing inadvertent damage.
12. Timely Firmware Updates:
Stay current with the latest firmware releases provided by switch manufacturers. Firmware updates often include bug fixes, security enhancements, and performance optimizations that contribute to the overall health and functionality of your switches.
Conclusion: Industrial switches are central to maintaining the efficiency and reliability of modern manufacturing and automation processes. By implementing a comprehensive array of protection strategies—from selecting appropriate environments and investing in ruggedized switches to deploying surge protection and fostering a culture of regular maintenance—you can significantly mitigate the risk of damage and ensure the sustained performance of your critical systems. Prioritizing the protection of industrial switches is an investment in the long-term success and productivity of your operations.
0 notes
Video
youtube
How to Resolve Bloomberg TV App Not Working on Samsung Smart TV ?
https://smarthomeapt.com/67-resolving-bloomberg-tv-app-not-working-on-samsung-smart-tv-try-these-fixes
Here are the 15 fixes explained in step by step process:
1. Restart your Samsung Smart TV: Press and hold the Power button on your Samsung TV remote to shut down the TV. Wait 30 seconds then press the Power button again to turn on your TV.
2. Check for software updates on TV: Go to Settings - Support - Software Update on your Samsung TV. Select "Update Now" and follow the on-screen prompts to install any available updates.
3. Update the Bloomberg TV app: Open the Bloomberg TV app on your Samsung TV and go to Settings or the Menu. Select "Check for Updates" or "Update App" and install any update available for the app.
4. Reinstall the Bloomberg TV app: Go to Settings - Apps - Bloomberg TV app - Delete app on your Samsung TV. Select "Delete" to confirm and uninstall the app. Go to the Samsung Apps Store and redownload the Bloomberg TV app. Follow prompts to install.
5. Restart your Wi-Fi router: Locate your Wi-Fi router and disconnect the power cable for a few minutes. Reconnect the power cable to turn the router back on.
6. Reset your router to factory default: Locate the "Reset" or "Restore Default" button on your Wi-Fi router. This may be a physical button or an option in the router menu. Press and hold the "Reset" button for 5-10 seconds until the router restarts to factory settings. Or select "Restore Default" in router menu and click "Yes" to confirm. Reconfigure your Wi-Fi name and password through the router menu and re-add the network on your Samsung TV.
7. Update router firmware: Log into your Wi-Fi router settings, usually by entering your router's IP address into a web browser. Select "Check for Updates" or "Firmware Update" and follow prompts to update your router firmware. Your router may restart during the update. Wait until fully restarted before using.
8. Change your Wi-Fi channel: Log into your Wi-Fi router settings, usually by entering your router's IP address into a web browser. Go to "Wireless" or "Wi-Fi" settings and select "Channel" or "Frequency". Choose an "Auto-select" option or manually change from the current channel to channel 6 or 11. Channels 6 and 11 are typically less congested. Click "Save" to change channels. Your router may temporarily restart Wi-Fi signal.
9. Check if service is down: If services are temporarily down, there is no need to troubleshoot. Just wait until services are restored to use the Bloomberg TV app.
10. Delete and re-add Wi-Fi network: Go to Settings - Network - Wi-Fi on your Samsung TV. Highlight your current Wi-Fi network and select "Delete". Confirm deletion. Go back and choose "Add network" to enter your network name (SSID) and password to re-add the Wi-Fi details. Select "Connect" and your TV will reboot. Try accessing the Bloomberg TV app again.
11. Restart your modem: Locate your internet modem (if separate from Wi-Fi router) and disconnect the power cable for a few minutes. Reconnect the power cable to turn the modem back on. Wait 2 minutes and check if Bloomberg TV app is working.
12. Change Wi-Fi bandwidth: Log into your Wi-Fi router settings, usually by entering your router's IP address into a web browser. Go to "Wireless" or "Wi-Fi" settings and select "Bandwidth" or "Channel". Choose either the "2.4GHz" or "5GHz" option, whichever is currently unused. For best streaming, use 5GHz. Click "Save" and your Wi-Fi will switch channels. Reconnect your devices to the Wi-Fi.
13. Make sure HDMI cable is firmly plugged in: Locate the HDMI cable connecting your TV to the internet/router. Ensure both ends of the HDMI cable are plugged in securely to the TV and modem/router HDMI ports. Loose HDMI cables can disrupt the internet signal and cause issues with streaming apps.
14. Reset Bloomberg TV app login info: Open the Bloomberg TV app on your Samsung TV and go to "Settings" or Menu. Select "Logout" to sign out of the Bloomberg TV app. Next, select "Login" or "Sign In" and enter your email and password again to sign back into the Bloomberg TV app. Entering login credentials again can reset your connection and fix access issues.
15. Perform a power cycle: Press and hold the Power button on your Samsung TV, Wi-Fi router and modem to shut them down. Unplug the Samsung TV, router and modem from power for 5 minutes. Plug the devices back in and turn your TV on
0 notes
Text
Folks It’s New a Bullshit on the Block! Officials Believe Pro-Ukraine Group May Have Sabotaged Nord Stream – Reports
European and US agencies have obtained tentative intelligence relating to pipeline bombing, say reports
— Dan Sabbagh, Philip Oltermann and Lorenzo Tondo in Kyiv | Tuesday 7 March 2023 1

Gas leak at the Nord Stream 2 gas pipeline in September. Photograph: Danish Defence/AFP/Getty Images
European and US intelligence officials have obtained tentative intelligence to suggest a pro-Ukrainian saboteur group may have been behind the bombing of the Nord Stream gas pipelines last year, according to reports in the New York Times and German newspaper Die Zeit.
German investigators believe the attack on the pipelines was carried out by a team of six people, using a yacht that had been hired by a company registered in Poland and owned by two Ukrainian citizens, according to Die Zeit.
The information has been shared between European intelligence agencies in an effort to establish more information about those who carried out the undersea bombings in September, an attack that had left western governments perplexed.
Details about the intelligence remain sketchy and it is unclear what confidence the US intelligence community places in the theory, as well as who may have organised, funded and directed such a daring attack on the gas pipelines running between Russia and Germany. But it is suggested that the government of Kyiv did not direct the underwater strike.
Russia said it wanted an independent international inquiry to be set up in response to the report. Its deputy envoy to the UN said Moscow would call for a vote at the UN security council on whether to launch one.
A senior aide to Ukraine’s president, Volodymyr Zelenskiy, told the Guardian the government in Kyiv was “in no way involved in the attack”, which he said had no military impact on Russian forces.
“In the midst of a war … Ukraine and its allies would definitely not spend resources on something that would not bring us victory directly on the battlefield. It doesn’t make any sense. But it is extremely beneficial for Russia itself to try to switch attention from the war … and try to present itself as a kind of ‘victim’,” he said.
The attack took place in international waters in the Baltic Sea, near the Danish island of Bornholm, with large amounts of gas rising up from the sea floor.
youtube
Nord Stream pipeline damage captured in underwater footage – Video
The prevailing theory at the time of the attack was that the bombing was the work of Russia, seeking to blame the west, but there have been doubts about whether Moscow would want to destroy its own expensively built infrastructure, even if the flow of gas had been halted by the time of the attack.
While investigators had been able to largely reconstruct how the pipelines had been blown up, Die Zeit’s report said, they had not found any evidence as to who would have tasked the group to carry out an attack, with a “false flag” operation still a theoretical possibility.
Six people were involved in the operation to transport explosives to the site, including the yacht’s captain, two divers, two diving assistants and a doctor. All six were understood to have used professionally faked passports, said Die Zeit, with their real identities still unclear.
The yacht set sail from the German port city of Rostock on 6 September. The equipment for the secret operation was previously transported to the port in a delivery truck, according to Die Zeit. After its return, investigators found traces of explosives on one of the tables inside the hired vessel.
Russia has repeatedly denied carrying out the bombing, even at one point blaming the UK, although there is no evidence of British involvement. A month ago, the US investigative journalist Seymour Hersh wrote an article saying the US had blown up the pipes – a claim denied by the US.
Speculation about US involvement has lingered because, just before Putin invaded Ukraine, Joe Biden cryptically claimed “there will be no longer a Nord Stream 2” if war were to break out. “We will bring an end to it,” he said, adding: “I promise you we’ll be able to do it.”
The German government said its own investigation has not yet reached a conclusion. Sweden, Denmark and Germany informed the security council a few days ago that their investigations were continuing and that there were still no results, a German government spokesperson said.
Reactions in Germany to Tuesday’s unconfirmed reports were cautious
“My impression from previous conversations is that the German investigators do not yet have any results that they can or want to communicate, simply because the evidence is far too thin,” said Roderich Kiesewetter, of the conservative Christian Democratic Union (CDU).
“We have to continue to ask the question: who had an interest in the detonation, why were only three of the four strands detonated, and who is benefiting from the very uncertainty, speculation, an accusations?” he added.
White House spokesperson John Kirby said: “We need to let these investigations conclude and only then should we be looking at what follow-on actions might or may not be appropriate.”
The Nord Stream gas pipelines connected Russia and Germany and were long opposed by Ukraine as they would have let Moscow sell more gas to western Europe. Gazprom representatives did not immediately respond to a request for comment.
It is not the first time pro-Ukrainian groups have been suspected of carrying out a major attack. US intelligence has come to believe that the car bombing of Darya Dugina in Moscow last August was conducted by partisans working for “elements” of the government in Kyiv.
A former Russian MP described that attack as the work of a little-known group called the National Republican Army, which he said was composed of Russian partisans. Its primary target was believed to be not Dugina, but her father, the Russian nationalist Alexander Dugin, but he switched vehicle at the last moment.
— The Guardian USA
0 notes
Text
Convenient Connection with Wireless Network
Most of our connections today are done wirelessly because it's clean and convenient. It doesn't require any wired cable for your mobile devices to get connected and access the internet. The wireless network is a computer network that uses RF connections (radio frequency) between nodes in the network and is very popular among homes, businesses, and telecommunication networks. We now lived in a connected world and the number of connections increases every day as many businesses and industries today discover and switch the power of staying connected easier and faster. Most of us now as mobile devices like smartphones, laptop, and tablets that connect to the internet and uses this wireless network. As a result, you can find many places with this type of network like fast food chains, coffee shops, and public transport stations.
Benefits of Wireless Network
* It allows users to move around freely within the coverage of the network and get their mobile devices, handheld devices, etc to get connected to the internet.
* Its users can easily share files and other resources with other devices connected to the network without the need for a cable or port.
* You don't have to lay cables and put them on walls and can consider advantages in terms of time and expense.
* It's easier to add extra devices to the network with no cabling required.
* Its is accessible to customers where you can bring extra business and it provides convenience to them.
* It can handle numerous users because it doesn’t limit any specific number of connection ports.
* It provides instant transfer of information to social media much easier than uploading a photo and can be done as quickly as possible with wireless technology.
Certain Risks to your Wireless Network
1. Piggybacking - failing to secure your wireless network can open your internet connection to any unintended users and they may conduct illegal activity, monitor and capture your web traffic or even steal your data.
2. Wardriving - this is a specific kind of piggybacking where in wireless access point can make an internet connection available outside your home and even up to your street. Some savvy computers may drive along cities and neighborhoods to check for unsecured wireless networks.
3. Evil Twin Attacks - this is an adversary that gathers information about a public network access point and then set it up a system to impersonate. It uses a broadcast signal stronger than one generated by the legitimate access point.
4. Wireless Sniffing - many public access points are not secure which can put sensitive communication or transaction at risk and malicious users can sniff tools to obtain sensitive information like passwords or credit card numbers.
5. Unauthorized Computer Access - unsecured public wireless network with unsecured file sharing can allow a malicious user to access any directories and files unintentionally made available for sharing. It is best when file sharing is not used to disable it.
6. Shoulder surfing - malicious users can simply tap your shoulder and glance at what you're doing by simply watching they can steal information or sensitive data, so you need to be cognizant of your surroundings.
7. Theft of Mobile Devices - not everyone can gain access thru wireless but by physically stealing your device. Attackers can have unrestricted access to all your data and all connected cloud accounts.
How to minimize risk on your wireless network
- Change the default password on your network
- You need to restrict access
- You need to encrypt the data on your network
- You need to protect your service set identifier (SSID)
- You must install a firewall
- You must maintain antivirus software
- You can also use file sharing with caution
- You can keep your access point software patched and up to date
- You must check your internet provider's or router manufacturer's wireless security options
- You must connect using a Virtual Private network (VPN)
Though wireless network provides us convenience and flexibility, it is still best to always stay secure and protected since cyberattacks and malicious attackers are very popular nowadays. Since technology are now so high-tech many devices can be used to steal information and data from you. You need to know how to minimize the risk and keep your account and information safe wherever you go.
To know more just visit https://www.nextelle.com.au

0 notes
Text
Recently I’ve started adopting Ubiquiti’s UniFi networking equipment in my home in a journey to building home lab infrastructure. I appreciate how Ubiquiti has positioned UniFi as technology for businesses of various sizes – home lab builders, SMEs, to large organizations. UniFi’s set of products have become incredibly popular among the “prosumer” community.
Having not worked with UniFi devices before, and most commercial networking equipment for over 2 years. In retrospect, I can confirm the setup process was smoother than anticipated, once you’re able to connect to the devices. My goal with this article is guide you through the process of installing and using Network Application/Controller on macOS.
For installation of UniFi Network Application on Ubuntu / Debian, checkout link below:
Install UniFi Controller on Ubuntu 18.04 / Debian 9
For running in Docker Containers check out the guide below:
How To Run UniFi Controller in Docker Container
My current UniFi equipment (provided by Ubiquiti are:
1x UniFi 16-Port PoE Switch (US-16-150W)
In future I’ll consider adding:
1x UniFi Dream Machine Pro (UDM PRO)
1x UniFi Security Gateway (USG)
1x UniFi Cloud Key (UCK)
Extra AP – Ubiquiti Networks UniFi UAP-AC-PRO
If you have UniFi Cloud Key – A small device with UniFi controller software pre-installed, then you can skip this guide, as it connects directly to your UniFi devices via Ethernet networking.
What is UniFi Network Application/Controller?
The UniFi® Controller, now called Network Application, is a wireless network management software solution from Ubiquiti Networks™. It enables you to manage multiple UniFI networks devices using a web browser.
For you to install and run it you should meet the following system Requirements:
A DHCP-enabled network
Linux, Mac OS X, or Microsoft Windows 7/8 – Running controller software
Java Runtime Environment 8
Web Browser: Mozilla Firefox, Google Chrome, or Microsoft Internet Explorer 8 (or above)
Install UniFi Network Application/Controller on macOS
Refer to steps covered in this section to successfully install UniFi Network Application/Controller on macOS. Ensure your system has internet access and you have sudo privileges.
Step 1 – Install Java Runtime (Java 8)
Java 8 is required to run UniFi Network Application on macOS. I struggled for a while with Java 17 before I could figure out required version. Before you can continue check your current version of Java:
$ java -version
openjdk version "16.0.2" 2021-07-20
OpenJDK Runtime Environment Homebrew (build 16.0.2+0)
OpenJDK 64-Bit Server VM Homebrew (build 16.0.2+0, mixed mode, sharing)
I had to remove this version before installing Java 8.
cd /Library/Java/JavaVirtualMachines
sudo unlink openjdk.jdk
Then head over to Java Downloads Archive page and select Java 8 for macOS to download.
Login with your Oracle account details or create a new account to begin download.
Double click on the package to begin installation on your macOS.
Check Java version after installation:
$ java -version
java version "1.8.0_331"
Java(TM) SE Runtime Environment (build 1.8.0_331-b09)
Java HotSpot(TM) 64-Bit Server VM (build 25.331-b09, mixed mode)
Step 2 – Create account on UniFi cloud
In case you don’t have UniFi cloud account create one at unifi.ui.com.
If you don’t have an account hit “Create one” and input required user information.
Click on the email you received to verify your email address.
Step 3 – Install UniFi Network Application/Controller
Next we download the UniFi Controller software from the Ubiquiti Networks website.
Select latest release of UniFI Network Application for macOS to download it.
Step 4 – Install UniFi Network Application/Controller
Click on the software application downloaded to install it.
Go through screens to set destination, installation type.
Finally launch the application once it has been installed.
Step 5 – Using UniFi Network Application/Controller
The UniFi Network Application software startup will begin. Click Launch a Browser to Manage Wireless Network.
Ignore SSL security warning and proceed to UniFi Network application web interface.
Step 5 – Configure UniFi Network Application
Give a name to your network application.
Sign in with your Ubiquiti account – the once we created in step 2
Enable automatic backup of network configurations.
If your UniFi devices are plugged into the same network as your macOS workstation, they will be discovered automatically. Select the once you’ll like to configure.
Create your first WiFi network if this is a new configuration of UniFi network.
Finally review the configurations to complete the installation of UniFi Network Application on macOS system.
Configurations are applied in few seconds.
With all settings applied you’re presented with an intuitive browser-based interface of UniFi Network Application software for easy configuration and management of your Network devices.
In the articles to follow we’ll dig deeper into different management functions available on uniFi Network Application software. Keep visiting our website for newer updates. Enjoy your day!
0 notes
Text
Aol verizon mail convert pop to imap

#AOL VERIZON MAIL CONVERT POP TO IMAP PASSWORD#
#AOL VERIZON MAIL CONVERT POP TO IMAP FREE#
However, if you have a large number of contacts, you may want to try exporting them to a CSV file (comma-separated values), so you can import them to Gmail. If you only have a handful of contacts in your old e-mail account, you're probably OK to just enter them in manually in Gmail. If you're sure you want to delete it from Gmail, go back to Settings > Accounts, then under "Check mail from other accounts (using POP3)," click "delete" next to the account. It wouldn't hurt to leave it enabled, though, just in case you get new messages there in the future. Once you've verified that the import is done, you can remove the account from Gmail. Go back to Settings > Accounts, then under "Check mail from other accounts (using POP3)," click on "View history."ĭepending on how much old e-mail you have, the import process shouldn't take very long, and the mail fetch history should help you figure out if the process is complete. Step 7: Check your mail fetch history to make sure your messages are being imported. Click "No" if you don't want to set up the custom From address or want to come back to it later. Step 6: Click "Yes" if you want to set up a custom From address for the account you just added. Archiving incoming messages is probably a good idea so you don't fill up your Inbox with all your old e-mail.Using the default label of your old e-mail address might help you find older messages a little easier, but this is totally up to you. You can label incoming messages if you'd like.SSL is more secure and will help protect you when you're using Gmail in public Wi-Fi networks. We recommend using SSL to check for new messages.If you want to delete your old e-mail messages off of your old account provider's server after Gmail imports them, check the box.For example, AOL's POP server is "" and Comcast's is "." Gmail will enter the settings of known providers for you, but if you run into any problems, check with your provider to make sure the settings are correct.
#AOL VERIZON MAIL CONVERT POP TO IMAP PASSWORD#
Step 3: Enter the password for the e-mail account you're migrating, as well as your e-mail provider's POP server name and port number. Step 2: Enter the e-mail address of the account you want to migrate (your old e-mail address). Step 1: Go to Settings > Accounts, then under "Check mail from other accounts (using POP3)," click "Add a POP3 mail account you own." This way, you can store all of your old messages in Gmail for later reference, while receiving new messages at your new Gmail address. Your old e-mail messages can be imported into Gmail as long as you haven't deleted them from the mail server.
#AOL VERIZON MAIL CONVERT POP TO IMAP FREE#
So if you're ready to go ahead and migrate your old e-mail to Gmail, sign up for your free Gmail account, then come back to this tutorial and follow the steps below: Importing mail Migrating your old e-mail account to Gmail isn't that difficult and Gmail actually makes it pretty painless. And if you spend any time at all on a tablet or smartphone, the Gmail apps provide an unrivaled experience. In other words, it's secure, reliable, and convenient. Gmail offers a ton of storage (currently at 10GB and growing), spam filtering at the server-level, two-step verification, and access from any Web browser or mobile device. If you're still holding onto an old AOL e-mail account or using the one your ISP (Internet Service Provider) gave you, it might be time to consider switching to Gmail.

1 note
·
View note
Text
Comcast incoming mail server android password

#Comcast incoming mail server android password update#
#Comcast incoming mail server android password password#
The cookies is used to store the user consent for the cookies in the category "Necessary". This cookie is set by GDPR Cookie Consent plugin. The cookie is set by GDPR cookie consent to record the user consent for the cookies in the category "Functional". The cookie is used to store the user consent for the cookies in the category "Analytics". These cookies ensure basic functionalities and security features of the website, anonymously. Necessary cookies are absolutely essential for the website to function properly. Encryption: TLS (use SSL if TLS isn’t shown.).Outgoing Mail Server Port Number: 587 (SMTP) If Needed: 465 (SMTPS).Incoming Mail Server Port Number: 993 with SSL ON.4 Select Internet Email Addresses, click Next and enter the following data among user data: 3 Switch on Server Settings and click Next. Set up Outlook Comcast 1 Start Outlook, click the File tab and click in the category information Account Settings 2 Click in the tab Email on New. How do I set up my Comcast email with Outlook? Check that your modem or router are both connected properly. Perform some basic troubleshooting on your computer and network connections. To create the mail id, you need to go to the. And all the users can be managed from the My Account page of the Comcast website. You can create up to six email accounts per connection.
#Comcast incoming mail server android password password#
They will have a username and password in time of subscription. To Create a Comcast email account, one must be subscribed to XFINITY internet. It is also better if you have a poor internet connection and need to access your emails offline. POP3 works better if you are only using one device, but have a very large number of emails. IMAP is better if you are going to be accessing your email from multiple devices, such as a work computer and a smart phone. For outgoing mail server, type in as your host name, and type in both your user name and password again. Next, type in the incoming mail server host name - and your user name (the first part of your email address). Setup Your Account with Your Email Program Using IMAP (Comcast) SMTP Server Your email account will remain active as long as you access it at least once every nine months.Ĭ (Comcast) provides IMAP access to your (Comcast) account, so you can connect to your email from mobile devices and desktop email clients….Setup Your Account with Your Email Program Using IMAP. Does Comcast net still exist?Īs a former Xfinity customer, you can still use your email address if you logged into your account in the 90 days prior to disconnecting your service. Switching from a POP3 connection to IMAP can result in your existing email being deleted, so you should create a backup of your mailboxes to avoid losing anything important. Will I lose email if I switch from POP to IMAP? Incoming Mail Server Port Number: 995 (POP3 With SSL) or 110 (POP3 Without SSL) What should the incoming mail server be for Comcast?
#Comcast incoming mail server android password update#
You can update your Incoming Mail Server Port to 995 with SSL to continue to receive mail without any change to your experience. Port 995 with SSL is secure and is the recommended port for POP. Does Comcast still support POP3?Ĭan I still access my email through POP? Yes. POP can cause problems when checking your mail from more than one phone or computer because POP removes the mail from our server and delivers it to your device. We recommend using IMAP for your Comcast email.
7 How do I set up my Comcast email with Outlook?.
5 What is the host name for Comcast email?.
3 Will I lose email if I switch from POP to IMAP?.

0 notes
Text
Alternative hyperterm

#ALTERNATIVE HYPERTERM SERIAL#
#ALTERNATIVE HYPERTERM PORTABLE#
#ALTERNATIVE HYPERTERM WINDOWS#
StrMessage.Format(strFormat, theApp.GetString(_T( " SerialName"), _T( " COM1"))) ĬString strServerIP = theApp.GetString(_T( " ServerIP"), _T( " 127.0.0.1")) StrFormat.LoadString(IDS_SERIAL_PORT_OPENED) (CSerialPort::FlowControl) theApp.GetInt(_T( " FlowControl"), CSerialPort::NoFlowControl),ĪfxBeginThread(SerialPortThreadFunc, this) (CSerialPort::StopBits) theApp.GetInt(_T( " StopBits"), CSerialPort::OneStopBit), (BYTE)theApp.GetInt(_T( " DataBits"), 8), (CSerialPort::Parity) theApp.GetInt(_T( " Parity"), CSerialPort::NoParity), Switch (theApp.GetInt(_T( " Connection"), 0)) Please check the OnOpenSerialPort and OnCloseSerialPort functions for implementation details. Next, now you can connect/disconnect from your data source. Please check the CConfigureDlg class for implementation details.
#ALTERNATIVE HYPERTERM SERIAL#
How Do I Get Started?įirst, configure the MFC application to get logs from either serial port or TCP/UDP socket connection. Confirmation of the EFTPOS transaction is sent to the store and passed on to the customer in the form of a printed EFTPOS transaction record. Before the EFTPOS customer has had the goods put into a bag, the EFTPOS transaction will be complete. The EFTPOS transaction takes a matter of only a few seconds. Unless there is reason for the EFTPOS transaction not to be completed, the funds will then be transferred between the two accounts. A message is also sent to the customer's bank. When the EFTPOS customer confirms the purchase, either by signature or security PIN, the EFTPOS equipment contacts the store's bank electronically about the transaction. On making a purchase, the EFTPOS customer gives an EFTPOS card to the cashier who inserts it into an on-site EFTPOS machine. For those who do not know, EFTPOS is the method for paying for goods or services without needing to carry cash. The main purpose of this MFC application is to get logs via serial port or UDP socket from embedded systems, such as EFTPOS devices, and it is based on PJ Naughter's CSerialPort and CWSocket classes. You can use IntelliPort to perform the specific tasks described above, but do not attempt to use IntelliPort for more complex communication needs. IntelliPort is designed to be an easy-to-use tool and is not meant to replace other full-feature tools available on the market.
#ALTERNATIVE HYPERTERM PORTABLE#
You can use IntelliPort to transfer large files from a computer onto your portable computer using a serial port rather than going through the process of setting up your portable computer on a network. IntelliPort has scroll functionality that allows you to look at received text that has scrolled off the screen. To make sure that your modem is connected properly or to view your modem's settings, you can send commands through IntelliPort and check the results. Therefore, it can serve as a valuable troubleshooting tool when setting up and using your modem. IntelliPort records the messages passed to and from the computer on the other end of your connection. IntelliPort is a program that you can use to connect to other computers, using either your null modem cable or Ethernet connection.
#ALTERNATIVE HYPERTERM WINDOWS#
As you already know, Microsoft has dropped the development of HyperTerminal starting with Windows 7.

0 notes