#Access-Control-Policy-Template
Explore tagged Tumblr posts
Text
Comprehensive Policy Template for Secure Permissions Management
Sath, Inc. provides a comprehensive access control policy template, empowering organizations to establish precise guidelines for managing user access. Contact them today for a seamless access management journey!
https://sath.com/access-control-policy-template
0 notes
Text
It's time we start demanding answers! Here's an email template to send to those in our local, state, and US government that holds accountability.
Dear [Their Name]
I am writing to demand accountability regarding recent executive actions that erase, criminalize, and deny rights to transgender and intersex people. These actions are not just discriminatory—they are designed to strip legal recognition, restrict medical access, and criminalize existence itself. This is authoritarianism in action, and I need to understand if and why you support or tolerate it.
1. Do you support Trump’s executive order erasing transgender and intersex people from legal recognition? This is not just policy—it is government-mandated erasure of real people. Stripping legal recognition means denying basic rights, protections, and dignity.
2. Do you support the use of government power to control identity and erase marginalized communities? History is clear: every authoritarian regime begins by targeting vulnerable groups, stripping them of rights, and forcing them out of public life. We have seen this playbook before in Nazi Germany and Putin’s Russia. Why are you endorsing that path?
3. Do you support Trump’s decision to pardon violent insurrectionists while criminalizing trans people, doctors, and parents seeking medical care? This is not law and order—it is political persecution. The message is clear: those who attack democracy receive clemency, while those seeking basic healthcare face prosecution.
These policies directly threaten my rights and my future. As my government leader, I expect you to either defend democracy and human rights or publicly justify why you stand with those who seek to dismantle them. Silence is complicity. I demand real answers, not deflections.
I look forward to your response.
Sincerely,
[Your Name]
[Your Contact Info]
#luigi mangione#anti capitalism#protest#politics#donald trump#trump tariffs#fuck trump#trans community#trans positivity#transgender#intersex#trump
104 notes
·
View notes
Text
How to Disable Copilot on Windows 11
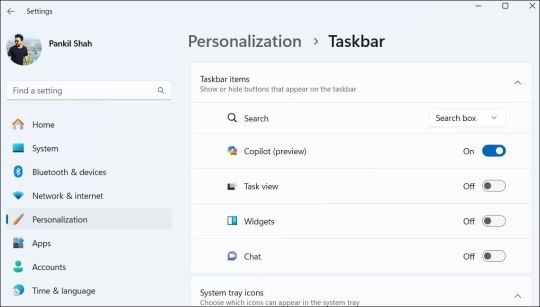
Windows Copilot, Microsoft's new AI assistant, can assist you with a variety of tasks, such as answering questions, changing system settings, and creating AI images. However, if you're not a fan of Copilot or simply don't need it, you can remove its taskbar icon or disable it entirely on your Windows 11 PC. Here, we'll show you how.
How to Remove the Copilot Icon From the Windows 11 Taskbar
By default, the Copilot icon appears in the Windows 11 taskbar. However, if you prefer not to have it there but still want to use it occasionally, it's easy to hide the Copilot icon. Simply right-click anywhere on an empty spot on your taskbar and select Taskbar settings. In the Settings window that appears, turn off the toggle next to Copilot.

This should remove the Copilot icon from the taskbar. You can still access Copilot by pressing the Win + C keyboard shortcut in Windows 11.
How to Completely Disable Copilot via Group Policy Settings
Although hiding the Copilot is quite easy, it does not turn it off completely, and you might inadvertently access it. Fortunately, you can turn off Copilot completely via the Local Group Policy Editor on PCs running the Professional, Education, or Enterprise edition of Windows 11. - Press Win + S to access the search menu. - Type gpedit.msc in the search box and select the first result that appears. - Select Yes when the User Account Control (UAC) prompt appears. - Use the left pane to navigate to User Configuration > Administrative Templates > Windows Components > Windows Copilot. - Double-click the Turn off Windows Copilot policy on your right. - Select the Enabled option. - Hit Apply followed by OK.
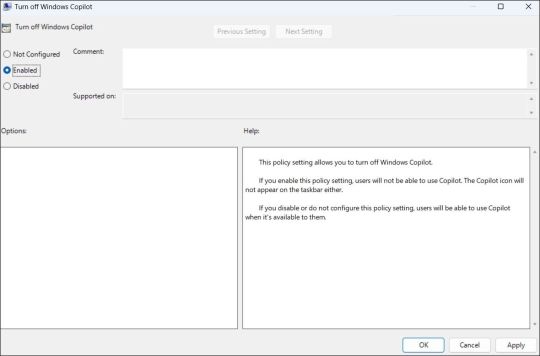
Once you complete the above steps, Copilot will be disabled on your Windows 11 PC and you won't be able to access it even with the keyboard shortcut. If you want to re-enable Copilot later, repeat the above steps and set the Turn off Windows Copilot policy to Not configured or Disabled.
How to Completely Disable Copilot by Modifying Registry Files
Another way to disable Copilot on Windows 11 involves modifying registry files. However, since editing the registry can be risky, you should follow the steps carefully. Also, be sure to back up all the registry files or create a restore point. This will allow you to restore the registry files in case something goes wrong. Once you’ve done that, here’s what you need to do to disable Copilot via the Registry Editor: - Press Win + R to open the Run dialog. - Type regedit in the text box and press Enter to open the Registry Editor. - Select Yes when the User Account Control (UAC) prompt appears. - Use the left pane to navigate to HKEY_CURRENT_USER > Software > Policies > Microsoft > Windows. - Right-click the Windows key and select New > Key. Name it WindowsCopilot. - Right-click on the WindowsCopilot DWORD, go to New, and select DWORD (32-bit) Value from the submenu. Name the DWORD TurnOffWindowsCopilot. - Double-click the TurnOffWindowsCopilot DWORD, type 1 in the text field, and click OK. - Restart your PC for the changes to take effect.
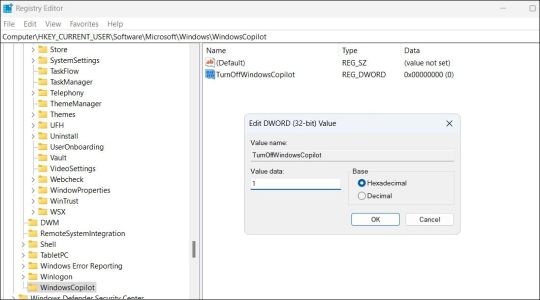
And that’s about it. Windows Copilot will be disabled on your PC. To re-enable it in the future, repeat the above steps and set the TurnOffWindowsCopilot DWORD value to 0. You can also delete the TurnOffWindowsCopilot DWORD instead.
Get Rid of Copilot on Windows 11
While Windows Copilot is a powerful tool, not everyone may want to use it. Fortunately, it’s possible to get rid of it. The above steps will help you achieve your goal, whether you want to keep Copilot out of sight or turn it off entirely. source Read the full article
3 notes
·
View notes
Text
Here's a email template I wrote up for any of y'all with republican reps that might hopefully work, remember, write for your audience:
Dear [REP LAST NAME],
I am writing to express my strong opposition to the RESTRICT Act (S.686), a bill that falsely claims to protect national security while in reality granting the federal government sweeping powers to censor information, control online platforms, and restrict Americans’ access to the global internet. This legislation is a thinly disguised attempt to isolate the American people, restricting our ability to communicate with the world under the pretense of combating foreign threats.
The bill’s vague and overly broad language gives the executive branch unchecked authority to ban any platform, service, or technology it arbitrarily deems a “national security risk.” In doing so, it effectively hands the government the power to determine what information Americans can access, opening the door to mass censorship with no meaningful oversight or accountability.
The RESTRICT Act is not a cybersecurity measure, it is an authoritarian overreach that brings the United States disturbingly close to China’s Great Firewall, where the government dictates what its citizens can and cannot see online. This bill does not protect Americans; it isolates us, silences us, and strips us of our fundamental right to free and open communication.
This legislation is not just about foreign-owned apps like TikTok, it gives the government the ability to block any platform or service it disapproves of, without transparency or due process. This means that any online space where Americans freely exchange ideas, challenge government narratives, or connect with people worldwide could be targeted under the guise of “national security.”
The U.S. government has long criticized authoritarian regimes for restricting internet access and silencing dissent. How can we claim to stand for democracy and free speech if we are actively working to implement the same restrictive policies here at home?
I urge you to oppose the RESTRICT Act and vote against any attempt to strip Americans of their digital rights. We do not need a U.S. version of China’s Great Firewall, and we do not need a government that dictates which voices are allowed to be heard. The internet should remain a place of free and open communication, not a tool for state control.
Please take a stand against this blatant power grab and defend the freedoms of the people you were elected to represent. I look forward to your response and to seeing you reject this dangerous legislation.
Senate Bill 686 of the 118th Congress (The Restrict Act)
I’m honestly a bit disappointed here at Tumblr for not talking about this bill more, so I’m going to share what I’ve learned about it with you all
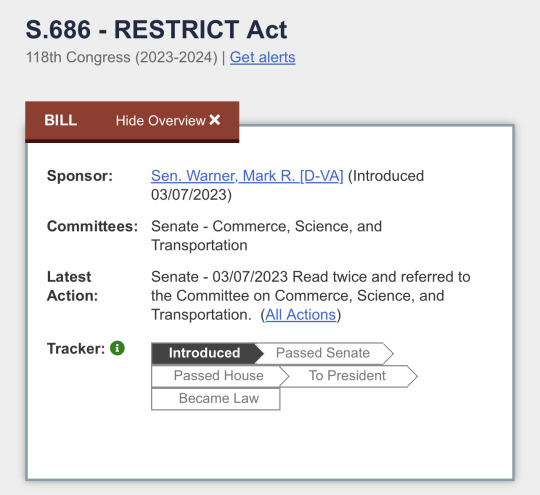
The link above goes to a pdf file going over the entire bill that has only been introduced atm as shown in the image just above from congress.gov.
Now, people only see this as a means to ban Tiktok, but that’s just the mask this truly cruel bill is hiding behind.
To boil it all down, this bill lets the Secretary of Commerce to have the power to ban…basically ANYTHING on the internet.
This includes hardware like video game consoles or Wifi networks as well as software and applications such as VPNs.
It also gives the government the power to monitor, basically everything you do online, private messages, posts on social media, streams, you name it, they can monitor it.
And the punishment for using, say, a VPN to access Tiktok, will result in 20 years in prison with a 1/4 million fine, a full million if you did it on purpose.
Now, I please ask you all to go to your representatives and tell them about how you don’t want this bill to be passed whatsoever. Heck, if you have to, (passively) threaten them with supporting their opponent in the next primary in any way they can. Just remember to be respectful and civil.
If you don’t want to do that, I respect that decision, and I understand that you wouldn’t want to deal with politics. But, I at least ask you to signal boost this post by reblogging it to your own followers and give any other thoughts about this that you might have in the tags or just normally.
I don’t want this lovable hellsite we all call home and made such good friends and memories on to be under the eyes of those pedophilic heathens who can’t seem to even know how to unlock a smartphone.
I thank you all for reading this, and I hope you all have a good day/night.
6K notes
·
View notes
Photo

Access Control and Authorization Policy Template https://fintechpolicies.com/product/access-control-and-authorization-policy-template/?utm_source=tumblr&utm_medium=social&utm_campaign=fintech+policies+templates
0 notes
Text
The Future of Fintech in Dallas: Why Managed IT Solutions Are No Longer Optional for Startups

Dallas: America's Emerging Fintech Frontier
Dallas has quietly transformed into a fintech powerhouse. With its pro-business policies, access to top-tier talent, and a lower cost of living than coastal cities, Dallas is rapidly becoming a strategic hub for startups building next-generation financial technologies. Since 2020, the number of fintech startups in Dallas has grown by over 33%, according to data from the Dallas Regional Chamber.
But while funding rounds and innovation headlines make the news, what often goes unnoticed is the crushing operational burden founders and CEOs face behind the scenes. Especially in small, non-technical teams, managing IT in Dallas, cybersecurity, and compliance alone becomes a silent stressor. As competition scales, so does risk—and without robust IT support, the very tech foundation of your fintech company becomes a liability instead of a growth lever.
When Innovation Outpaces Infrastructure in Fintech
In the pursuit of disrupting legacy financial systems, Dallas fintech startups often pour resources into product development. But here's the truth: your app or algorithm won't matter if your infrastructure can't keep up.
Behind most early-stage fintech lies:
Siloed tools with no integration.
Fragmented data spread across insecure storage.
Zero proactive monitoring, leading to downtime and data loss.
Cybersecurity gaps that leave companies exposed.
These issues do more than frustrate internal teams—they damage customer trust, trigger regulatory penalties, and repel investors. A study from the Ponemon Institute revealed that 59% of consumers would switch financial providers after a single data breach.
Cybersecurity Isn't Just IT for Fintech—It's Risk Management
Fintech deals in data. This means every line of code, every API call, and every user session is a potential attack surface. U.S. fintech startups are now 3x more likely to be targeted by cybercriminals due to unpatched systems and low IT maturity. (IBM Cost of Data Breach Report, 2023)
In 2023 alone:
A Dallas-based digital lending platform lost $4.6M in a ransomware attack.
A neobank fell victim to phishing that compromised 80,000 customer records.
Several startups failed their SOC 2 audits due to insufficient internal controls.
The financial sector remains the second-most targeted industry globally, and the average cost of a data breach in this space is $5.9 million.
What Managed IT Services Do for Fintech Startups?
Managed Service Providers (MSPs) go beyond "fixing laptops." For fintech startups, they offer a strategic partnership that replaces fragmented IT with an integrated, future-proof solution.
Key offerings include:
24/7 monitoring and threat detection to prevent breaches before they happen.
Automated backups and patch management to reduce human error.
Regulatory compliance templates and built-in documentation for audits.
Real-time dashboards for executives to track uptime, incidents, and data flows.
Instead of hiring a full internal IT team (which can cost over $300K/year for mid-tier talent), startups partner with local MSPs in Dallas for predictable monthly costs and fractional access to CTO-level expertise.
Compliance Isn't Optional—It's a Competitive Advantage for Fintech
From SOC 2 Type II to PCI-DSS and GLBA, compliance is no longer just about ticking boxes—it's about protecting your license to operate.
Dallas MSPs with fintech specialization offer:
Pre-built compliance workflows that accelerate audit readiness.
Encryption standards and multi-layer authentication are baked into architecture.
Breach response playbooks with legal and technical alignment.
With the right partner, achieving compliance becomes an accelerator for fundraising, partnership approvals, and market expansion—not a blocker.
Cloud-First, Not Cloud-Only: Building Scalable Fintech Infrastructure
By 2026, 85% of all fintech platforms will be cloud-native (Gartner). Cloud computing allows startups to scale quickly, enable remote access, and reduce on-premise risk.
However, misconfigurations in the cloud can be catastrophic.
Managed IT providers specializing in cloud services offer:
Secure hybrid environments for transitioning slowly and safely.
Encryption at rest and in transit, plus zero-trust firewall setups.
Cloud sandboxing to test products before full-scale deployment.
Failover systems that guarantee uptime even during outages.
Why IT Outsourcing Is the Smartest Decision Fintech Startups in Dallas
Startups burn cash quickly. Every misstep costs time, money, and team morale. Hiring a full internal IT team might not just be expensive—it might be unnecessary.
Outsourcing IT services gives access to:
Top-tier cybersecurity experts, compliance consultants, and cloud engineers.
On-demand support without long-term payroll commitments.
Scalability from 10 to 100 users without restructuring.
One Dallas fintech reported a 40% reduction in IT costs after switching to an MSP within just 12 months—without sacrificing performance or compliance.
How to Choose the Right MSP for Your Fintech Company in Dallas
Before signing any contract, vet your MSP like you would a co-founder.
Here's your checklist:
Industry experience: Look for MSPs who've served financial services for 5+ years with clients that have passed SOC 2 or PCI-DSS audits.
Cybersecurity framework: They should support NIST CIS Controls and offer incident response SLAs in under 1 hour.
Compliance portfolio: Ensure support for SOC 2 Type II, GLBA, PCI-DSS, and FFIEC frameworks.
Transparent pricing: Dallas MSPs typically charge between $120 to $250 per user/month, depending on the services included.
Local presence: You need boots on the ground. Onsite support is critical when seconds matter.
Ask them:
How many fintech startups have you helped scale?
What's your average incident response time?
Do you provide audit documentation and testing?
Conclusion: You're Building the Future of Finance. Don't Build It on Fragile Infrastructure
As fintech startups in Dallas chase growth and innovation, they must also protect their foundation. Managed IT is no longer a support function—it's a strategic growth pillar.
By investing in proactive IT, you unlock:
Greater investor confidence.
Stronger regulatory positioning.
Lower operational risk and higher uptime.
Now is the time to align with a Dallas-based Managed IT Service Provider who understands the unique demands of fintech, from launch to scale.
#managed service provider#technology#cyber security services#msp#managed it services#msp services in texas#msp for fintech
0 notes
Text
you can also use Group Policy Editor to turn it off. access the Local Group Policy Editor by typing gpedit.msc in the command prompt, then press Enter
go to User Configuration > Administrative Templates > Windows Components > Windows Copilot. in the right pane, double-click the setting "Turn off Windows Copilot" to Enable the setting (which turns off the AI spyware)
if you read this in the future, there might be a new setting just for Recall, so look for it in this part of gpedit.msc - but this should do the trick now
in fact, Group Policy Editor (gpedit) is your best tool for configuring how every aspect of your machine works, but it's no longer included in Home Editions of Windows, so if it doesn't launch when you type that, you'll need to download it from a reputable source (I've been able to find safe distributions regularly, but don't want to link just in case - always do your research before downloading anything)
if you had to add it, you'll probably have to reinstall Group Policy Editor and remove some programs over and over after major updates, but at least these two give you control over your computer
(my creds: I used to work for those guys and literally wrote the early books on the Windows Registry and Group Policy!)
Literal definition of spyware:
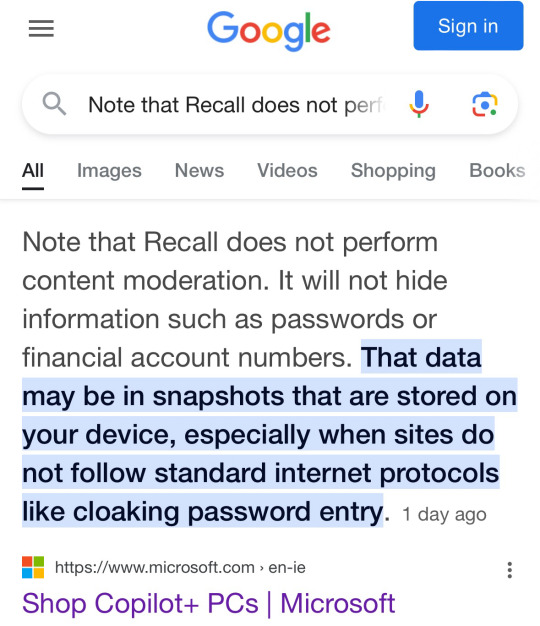
Also From Microsoft’s own FAQ: "Note that Recall does not perform content moderation. It will not hide information such as passwords or financial account numbers. 🤡
#privacy#surveillance#microsoft windows#windows recall#group policy#windows registry#won a few awards for those docs too!
239K notes
·
View notes
Photo

Alright, buckle up, buttercups, because we're about to dissect a truly delightful period: late medieval and early modern Europe. This was an epoch where asking to borrow a cup of sugar from your neighbor could just as easily get you a warm welcome as an accusation of consorting with Satan. In this pressure cooker of paranoia, "witchcraft" became the go-to explanation for everything from a bad harvest to a stubbed toe, especially when things got really weird with tales of cannibalism and perversions of the Eucharist. Merrall Llewelyn Price’s Consuming Passions isn't just a book; it's an autopsy of these intertwined terrors, revealing how accused witches weren't merely brewing herbal remedies but were also stirring society’s bubbling cauldron of collective anxieties. So, park your broom by the door, try not to look too shifty, and let’s wade through the muck of medieval fears. This isn't for the faint of heart; consider it a post-mortem on an entire era's sanity. THE MATERNAL BODY AND THE PRELINGUISTIC: A MOTHER’S LOVE… WITH FAVA BEANS? It seems the shrinks have a fancy term for everything. In this case, we’re dissecting the link between the maternal, the pre-verbal, and why, in the eyes of medieval hysterics, this sometimes translated into a mother with a rather… adventurouspalate. CANNIBALISM AND THE LACANIAN IMAGINARY: MOMMY DEAREST, OR DEMON DEAREST? Let’s start with the Freudian-adjacent babble: the Lacanian Imaginary. Sounds like a prog-rock album, but it’s essentially how our baby-brains first try to make sense of ourselves through Mom. In the upside-down logic of witch-panics, this primal mother-child bond got hideously twisted. Cannibalism and all manner of witchy depravity were thus projected onto this foundational relationship. Witches, you see, weren't just cackling old crones; they were seen as grotesque parodies of motherhood itself – the all-giving mother who also devours, the nurturer who secretly yearns to gnaw on your liver. It’s a delightful paradox: the source of life reimagined as the ultimate consumer. Family therapy clearly hadn't been invented yet. WITCHCRAFT AND MATERNAL POWER: WHEN "WOMAN'S WORK" INCLUDES HEXES Think your PTA meetings are rough? Try being a mother in medieval Europe when the witch-finders came calling. Women accused of witchcraft often found themselves in the stocks for allegedly using their maternal roles for nefarious ends – cursing their own children, or worse, using their unique biological knowledge for evil. Midwives were prime suspects. After all, who else had such intimate access to the miracle of birth, the blood, the afterbirth, the vulnerable newborn? If a baby died, or was born deformed, wasn't it easier to blame the woman who smelled faintly of herbs and knew a bit too much, than, say, poor sanitation or genetics? The fear of women wielding any control over reproduction, life, and death was so potent, it practically fueled the pyres. Witch hunts, in many ways, were just brutally effective HR policies for keeping women confined to their divinely ordained (and powerless) domestic sphere. BLOOD LIBEL AND SACRAMENTAL HERESY: A DEVILISH DUET OF DEFAMATION When societal paranoia seeks scapegoats, it rarely stops at one. The accusations against witches found a convenient, pre-existing template of horror in the antisemitic trope of blood libel, all wrapped up with a perverse bow of eucharistic anxiety. INTERCONNECTIONS WITH BLOOD LIBEL: SAME SCRIPT, DIFFERENT CAST Let’s add another rancid ingredient to this toxic stew: blood libel. This particularly nasty piece of antisemitic propaganda accused Jews of ritually murdering Christian children to use their blood in religious rites. Surprise, surprise! Witch-accusers, never ones to let a good horror story go to waste, simply copy-pasted these atrocities onto their new favorite scapegoat. Witches, they shrieked, were also stealing Christian babies for their midnight snacks and unholy rit
0 notes
Text
Why You Need an Integrated Document Management System in 2025

In an era where digital transformation is no longer a choice but a necessity, organizations must adopt technologies that not only streamline operations but also ensure compliance, security, and productivity. At the core of this evolution lies the Integrated Document Management System (IDMS) — a solution that is becoming indispensable for organizations striving for excellence in 2025.
Omnex Systems, a global leader in enterprise software solutions, is at the forefront of this digital revolution, offering a state-of-the-art Integrated Document Management System tailored to meet the demands of modern businesses.
What is an Integrated Document Management System?
An Integrated Document Management System is a centralized, digital solution that allows organizations to create, store, manage, and track electronic documents and records in a secure and efficient way. Unlike traditional document storage, an IDMS integrates with other enterprise systems such as Quality Management Systems (QMS), Enterprise Resource Planning (ERP), and Customer Relationship Management (CRM), creating a seamless workflow and data ecosystem.
Omnex Systems’ IDMS stands out by not only supporting robust document control but also ensuring version control, audit trails, electronic signatures, and compliance with global standards like ISO 9001, IATF 16949, and others.
Why 2025 Demands a Shift to Integrated Document Management
The year 2025 marks a pivotal moment in digital transformation. With increased data volumes, stricter compliance regulations, and the rise of hybrid work models, businesses must rethink how they manage information.
Here’s why transitioning to an Integrated Document Management System in 2025 is no longer optional:
1. Remote and Hybrid Work Enablement
The global shift to remote and hybrid work has made accessibility a priority. Employees must access documents anytime, anywhere, and from any device. Omnex Systems’ IDMS is cloud-enabled, ensuring secure, real-time access to documents for distributed teams. Collaboration becomes seamless, reducing bottlenecks and enhancing productivity.
2. Rising Compliance and Regulatory Pressures
Organizations today face increasingly complex regulations — from ISO standards to GDPR, HIPAA, and beyond. Non-compliance can result in hefty fines and reputational damage. An Integrated Document Management System from Omnex Systems automates compliance by providing:
Document version control
Automated retention and archival policies
Secure user access permissions
Audit-ready documentation
This makes audits faster and stress-free while ensuring continuous adherence to regulations.
3. Streamlined Workflows and Process Efficiency
Manual document management is slow, error-prone, and labor-intensive. With Omnex Systems’ IDMS, businesses can automate document approval workflows, route documents based on roles, and set reminders for key actions. These streamlined processes reduce administrative tasks and accelerate decision-making.
Key Features of Omnex Systems’ Integrated Document Management System
Omnex Systems has engineered its Integrated Document Management System with functionality tailored to regulated industries, global enterprises, and quality-driven organizations. Here are some standout features:
Automated Document Workflows: Manage approvals, reviews, and revisions with built-in automation.
Version Control and Audit Trails: Keep track of every change and ensure users are working on the latest version.
Compliance Integration: Pre-built templates and structures aligned with ISO and automotive standards.
Multi-Device Access: Access and manage documents from desktops, tablets, and smartphones.
Role-Based Security: Restrict access based on job role, department, or region for improved data protection.
Integration with QMS and Other Systems: Omnex’s IDMS is part of a larger quality ecosystem, linking document control directly with corrective actions, training, audits, and more.
Business Benefits of Adopting an IDMS in 2025
1. Improved Productivity
With faster document retrieval, automated workflows, and real-time access, employees spend less time managing documents and more time on core tasks. Teams can collaborate efficiently, no matter where they are.
2. Enhanced Data Security
Cybersecurity threats are evolving, and document security is a major concern. Omnex Systems’ Integrated Document Management System uses encryption, user authentication, and permission controls to ensure only authorized users access sensitive data.
3. Scalability
Whether you're a small enterprise or a multinational corporation, Omnex’s IDMS scales with your business. Add new users, departments, and geographies without losing performance or control.
4. Reduced Operational Costs
Eliminate the need for physical storage, paper, printing, and manual filing. Reduce errors and rework costs by ensuring every document is up-to-date and traceable.
5. Audit Readiness
Prepare for regulatory or internal audits with ease. With one click, you can generate audit trails, identify responsible parties, and provide documentation that meets quality standards.
Use Cases: Real-World Application of Omnex IDMS
Quality Management
Documenting procedures, work instructions, and SOPs is critical for quality assurance. Omnex Systems integrates IDMS with its eQCM Suite, enabling real-time updates and compliance with ISO standards.
Automotive Compliance
For IATF 16949 compliance, maintaining engineering changes, process flows, PFMEAs, and control plans is essential. Omnex IDMS links these documents across the APQP process, ensuring traceability and accuracy.
Training and HR
Employee training records, certifications, and performance documentation can be maintained and tracked efficiently, enabling HR to align with legal and corporate standards.
The Future of Document Management
Looking ahead, the role of an Integrated Document Management System will continue to evolve. With advancements in AI, machine learning, and predictive analytics, document systems will become smarter—automating not just management, but insights, risk mitigation, and strategic decision-making.
Omnex Systems is already investing in these technologies, ensuring its platform remains at the cutting edge of enterprise document management.
Conclusion: A Strategic Move for the Future
In 2025, the need for robust, intelligent, and scalable document control is undeniable. A fragmented approach to document management will no longer suffice. Organizations that adopt an Integrated Document Management System from Omnex Systems will not only meet today’s challenges but will be better prepared for tomorrow’s opportunities.
Whether you are aiming to boost compliance, drive efficiency, or enable a remote workforce, Omnex Systems offers a proven, secure, and enterprise-ready solution.
Don’t wait for inefficiencies or compliance issues to become roadblocks. Make the smart move—integrate your documents, empower your teams, and transform your business with Omnex Systems.
For more info pls visit us +1 734-761-4940 (or) [email protected]
0 notes
Text
Secure and Compliant Healthcare Data Management with MediBest Hospital Management System Software
Healthcare now tops every industry for breach costs, averaging US $4.88 million per incident in 2024—a 15 % jump in just two years. At the same time, the U.S. Office for Civil Rights has logged more than 374,000 HIPAA complaints since 2003, underscoring regulators’ growing vigilance. A recent HIMSS survey found that 59 % of providers experienced a significant cybersecurity event in the past year, and most plan to increase budgets for data protection.

Modern hospitals therefore need more than firewalls; they require a fully integrated healthcare management system software that embeds security and compliance into every workflow.
How MediBest Builds a Defense-in-Depth Architecture
MediBest—an industry-trusted hospital software company—fortifies its cloud-native platform with multiple protective layers that work together to keep patient data safe.
End-to-end encryption (TLS 1.3 in transit, AES-256 at rest)
Zero-trust access controls with MFA and role-based privileges
Continuous threat monitoring powered by AI anomaly detection
Immutable audit logs for every clinical, financial, and admin action
Automated backups and geo-redundant disaster recovery
Because all modules share a single database, these safeguards apply consistently across EHR, billing, radiology, HR, and inventory—eliminating gaps common in bolt-on tools.
Compliance by Design: Meeting HIPAA, GDPR, and NABH
MediBest’s healthcare management system ships with pre-configured compliance templates and rule engines to streamline statutory reporting:
HIPAA & HITECH: automatic PHI tagging, breach-alert workflows, and encryption keys managed in certified data centers.
GDPR: data-subject-access request (DSAR) dashboards and right-to-erasure controls.
NABH & NABL: clinical quality and infection-control reports generated in one click.
Configurable policy packs let hospitals adapt settings to local regulations without costly code changes. Google my Business :
Business Benefits of Secure, Unified Data Governance
Reduced legal and financial risk: proactive safeguards lower the likelihood of fines and lawsuits.
Operational efficiency: single-source data eliminates duplicate entry, cutting admin time by up to 30 %.
Higher patient trust: visible security measures and transparent consent management improve satisfaction scores.
Stronger brand reputation: demonstrating best-practice cybersecurity differentiates your facility in competitive markets.
Fast, Low-Friction Implementation with MediBest
Assessment & gap analysis to map current vulnerabilities.
Phased rollout starting with high-risk modules such as billing and EHR.
Staff training on secure workflows and incident-response drills.
Quarterly security audits and penetration tests included in the support plan.
This structured approach lets hospitals deploy robust protection without disrupting day-to-day care. Click Here :
Frequently Asked Questions
1. What makes hospital management system software “secure”? It combines strong encryption, least-privilege access, continuous monitoring, and compliant audit trails inside one unified platform—protecting data at every step from admission to discharge.
2. Can cloud-based healthcare management systems meet HIPAA requirements? Yes. When hosted in certified data centers with encrypted storage, MFA, and documented BAAs, cloud systems can exceed on-premise security while providing better scalability and uptime.
3. How does MediBest simplify compliance reporting? Built-in templates for HIPAA, GDPR, and NABH pull real-time data from every module, auto-populate regulatory forms, and schedule submissions—cutting report prep from days to minutes.
MEDIBEST :- CONTANT NOW :- Corporate Office 303, IT Park Center, IT Park Sinhasa Indore, Madhya Pradesh, 452013 Call Now +91 79098 11515 +91 97139 01529 +91 91713 41515 Email [email protected] [email protected]
0 notes
Text
Top 5 Tools for Salesforce Data Migration in 2025

Data migration is a critical aspect of any Salesforce implementation or upgrade. Whether you’re transitioning from legacy systems, merging Salesforce orgs, or simply updating your current Salesforce instance, choosing the right tool can make or break the success of your migration. In 2025, the landscape of Salesforce data migration tools has evolved significantly, offering more automation, better user interfaces, and improved compatibility with complex datasets.
If you're a business looking to ensure a smooth migration process, working with an experienced Salesforce consultant in New York can help you identify the best tools and practices. Here's a detailed look at the top five Salesforce data migration tools in 2025 and how they can help your organization move data efficiently and accurately.
1. Salesforce Data Loader (Enhanced 2025 Edition)
Overview: The Salesforce Data Loader remains one of the most popular tools, especially for companies looking for a free, secure, and reliable way to manage data migration. The 2025 edition comes with a modernized UI, faster processing speeds, and enhanced error logging.
Why It’s Top in 2025:
Improved speed and performance
Enhanced error tracking and data validation
Seamless integration with external databases like Oracle, SQL Server, and PostgreSQL
Support for larger datasets (up to 10 million records)
Best For: Organizations with experienced admins or developers who are comfortable working with CSV files and need a high level of control over their data migration process.
Pro Tip: Engage a Salesforce developer in New York to write custom scripts for automating the loading and extraction processes. This will save significant time during large migrations.
2. Skyvia
Overview: Skyvia has emerged as a go-to cloud-based data integration tool that simplifies Salesforce data migration, especially for non-technical users. With drag-and-drop functionality and pre-built templates, it supports integration between Salesforce and over 100 other platforms.
Why It’s Top in 2025:
No coding required
Advanced transformation capabilities
Real-time sync between Salesforce and other cloud applications
Enhanced data governance features
Best For: Mid-sized businesses and enterprises that need a user-friendly platform with robust functionality and real-time synchronization.
Use Case: A retail company integrating Shopify, Salesforce, and NetSuite found Skyvia especially helpful in maintaining consistent product and customer data across platforms.
Expert Advice: Work with a Salesforce consulting partner in New York to set up your data models and design a migration path that aligns with your business processes.
3. Jitterbit Harmony
Overview: Jitterbit Harmony is a powerful data integration platform that enables users to design, run, and manage integration workflows. In 2025, it remains a favorite for enterprises due to its AI-powered suggestions and robust performance in complex scenarios.
Why It’s Top in 2025:
AI-enhanced mapping and transformation logic
Native Salesforce connector with bulk API support
Real-time data flow monitoring and alerts
Cross-platform compatibility (on-premise to cloud, cloud to cloud)
Best For: Large enterprises and organizations with complex IT ecosystems requiring high-throughput data migration and real-time integrations.
Tip from the Field: A Salesforce consulting firm in New York can help fine-tune your Jitterbit setup to ensure compliance with your industry regulations and data handling policies.
4. Informatica Cloud Data Wizard
Overview: Informatica is well-known in the enterprise data integration space. The Cloud Data Wizard is a lightweight, Salesforce-focused tool designed for business users. In 2025, its intuitive interface and automated field mapping make it a favorite for quick and simple migrations.
Why It’s Top in 2025:
Automatic schema detection and mapping
Pre-built Salesforce templates
Role-based access control for secure collaboration
Integration with Salesforce Flow for process automation
Best For: Companies needing quick, on-the-fly migrations with minimal IT involvement.
Case in Point: A nonprofit organization used Informatica Cloud Data Wizard for migrating donor information from spreadsheets into Salesforce Nonprofit Success Pack (NPSP) with minimal technical assistance.
Pro Insight: Partner with a Salesforce consultant in New York to evaluate whether the Cloud Data Wizard meets your scalability and security needs before committing.
5. Talend Data Fabric
Overview: Talend Data Fabric combines data integration, quality, and governance in one unified platform. In 2025, it leads the way in enterprise-grade data migration for Salesforce users who require deep customization, high security, and data lineage tracking.
Why It’s Top in 2025:
Full data quality and compliance toolset
AI-driven suggestions for data cleaning and transformation
End-to-end data lineage tracking
Integration with AWS, Azure, and Google Cloud
Best For: Industries with strict compliance needs like finance, healthcare, or government, where data accuracy and traceability are paramount.
Strategic Advantage: A Salesforce consulting partner in New York can help configure Talend’s governance tools to align with HIPAA, GDPR, or other regulatory requirements.
Why Choosing the Right Tool Matters
Data migration is more than just moving records from one system to another—it’s about preserving the integrity, security, and usability of your data. Choosing the right tool ensures:
Fewer errors and data loss
Faster deployment timelines
Higher end-user adoption
Better alignment with business goals
Partnering with Salesforce Experts in New York
Working with an experienced Salesforce consultant in New York can help you navigate the complexities of data migration. Local consultants understand both the technical and business landscapes and can offer personalized support throughout the migration journey.
Whether you're a startup looking for lean, cost-effective solutions or a large enterprise needing advanced governance, engaging with Salesforce consultants in New York ensures you make the most informed decisions.
These professionals can:
Conduct data audits and mapping
Recommend the best tool for your specific use case
Build custom scripts or integrations as needed
Ensure a smooth transition with minimal business disruption
Final Thoughts
In 2025, Salesforce data migration is no longer a cumbersome, manual task. With tools like Salesforce Data Loader, Skyvia, Jitterbit, Informatica, and Talend, businesses of all sizes can achieve fast, secure, and seamless migrations. The key lies in selecting the right tool based on your business size, technical capacity, and compliance needs.
Moreover, partnering with a knowledgeable Salesforce consulting partner in New York gives you access to tailored solutions and hands-on support, making your data migration journey smooth and successful.
Ready to migrate your data the right way? Consult with a trusted Salesforce consulting in New York expert and empower your business to scale with confidence.
#salesforce consultant in new york#salesforce consulting in new york#salesforce consulting partner in new york#salesforce consultants in new york#salesforce developer in new york#Top 5 Tools for Salesforce Data Migration in 2025
0 notes
Text
How Compliance Management Software Benefits the Healthcare Industry

In today’s complex regulatory landscape, Australian healthcare providers face unprecedented compliance challenges. From ever-evolving regulations to strict accreditation standards, maintaining compliance manually is no longer feasible.
Compliance management software offers a streamlined solution to these challenges, helping providers stay ahead of regulatory requirements while improving patient safety and operational outcomes.
Whether you’re managing a hospital, aged care facility, or small practice, implementing a digital compliance solution can transform your approach to regulatory adherence and risk management.
What is Compliance Management Software for Healthcare?
Compliance management software is a specialised digital solution designed to help healthcare organisations meet their regulatory, ethical, and operational obligations through automation and centralisation.
These platforms bring together various compliance elements into one unified system, replacing fragmented spreadsheets and paper-based processes with a structured approach.
At its core, compliance software enables healthcare providers to manage policies, track training, report incidents, assess risks, and prepare for audits, all from a single, accessible platform.
What are the Key Features for Australian Healthcare Compliance?
Modern compliance solutions offer features specifically designed for Australia’s healthcare regulatory environment, including:
Document control systems that maintain the latest clinical procedures and safety guidelines
Policy distribution tools that notify staff of critical updates and track acknowledgements
Training management modules that assign and monitor mandatory competencies
Incident reporting workflows that capture, investigate and resolve adverse events
Risk assessment templates aligned with Australian standards and regulations
Audit-ready reporting that generates evidence for accreditation bodies
These features are configured to support compliance with essential Australian healthcare frameworks, including the National Safety and Quality Health Service (NSQHS) Standards, Aged Care Quality Standards, and NDIS Practice Standards.
Why Is Compliance Management Critical in Australian Healthcare?
Australia’s healthcare sector operates within one of the most regulated environments, with multiple oversight bodies and frequently updated standards. Non-compliance can result in severe penalties, including legal action, loss of accreditation, funding cuts, and significant reputational damage that affects patient trust.
Healthcare providers must navigate this complex landscape whilst delivering quality care – a balancing act that becomes increasingly difficult without digital support systems.
Conclusion
In Australia’s highly regulated healthcare environment, compliance management software has transformed from a nice-to-have into an essential operational tool.
From policy control and workforce training to incident management and accreditation readiness, these platforms deliver efficiency, visibility, and risk reduction across all aspects of healthcare compliance.
By implementing a comprehensive compliance solution, healthcare organisations create not just a tick-box approach to regulations, but a culture of continuous improvement that ultimately benefits patients, staff, and the organisation itself.
Ready to Transform Your Healthcare Compliance with Sentrient?
Sentrient’s compliance management software is specifically designed for Australian healthcare providers, with features aligned to NSQHS Standards, Aged Care Quality Standards, and NDIS requirements.
Our platform helps you move beyond manual compliance management to a streamlined, digital approach that saves time, reduces risk, and improves governance.
Contact us today to arrange a demonstration tailored to your specific healthcare setting and compliance needs.
This given blog was originally published here: How Compliance Management Software Benefits the Healthcare Industry
#sentrient#compliance management system#hr management system#compliance system#compliance management#manual handling training course#grc software#performance management#performance management system#grc compliance software
0 notes
Text
For all EU-based people out there: go and tell the decision-makers what a horrible, bad, not good idea this legislation suggestion is.
In short:
They want to sanction unlicensed messaging apps, hosting services and websites that don't spy on users (and impose criminal penalties)
mandatory data retention, all your online activity must be tied to your identity
end of privacy friendly VPN’s and other services
cooperate with hardware manufacturers to ensure lawful access by design (backdoors for phones and computers)
all communication service providers are explicitly in scope no matter how small or open source
This would make us more authoritarian than both Russia and China, as well as introducing security risks (and thus effectively killing our own IT industry) in the way of backdoors, and is the not a limit I'm comfortable with limboing under.
Go and have your say here:
More information in the reddit discussion here:
A suggestion for feedback to send, based on u/demonya99's template to the commission (feel free to use):
At first glance, the proposed regulation might appear to be just another flawed attempt to balance security and privacy. But a closer look, especially at the High-Level Group (HLG) advice the EU cites as a foundational source, reveals something far more dangerous.
I understand the policy of keeping the High-Level Group anonymous (even though people involved in democratic decision-making should be known to all so we the public can see that all relevant interests have in fact been represented and that there's no conflict of interest). Therefore it is a problem when German MEP Patrick Breyer requested the names of the individuals behind the so-called High-Level Group that drafted this sweeping proposal, and the EU responded with a list where every single name was blacked out. A law that would introduce unprecedented surveillance powers across Europe is being built on recommendations from an anonymous and unaccountable group. In any democracy, this would be a scandal. In the European Union, this is an outright betrayal of public trust.
According to digital rights organization EDRi, “The HLG has kept its work sessions closed, by strictly controlling which stakeholders got invited and effectively shutting down civil society participation.” In short, the process was deliberately closed off to public scrutiny, democratic debate, and expert dissent. Civil society was excluded while powerful lobbyists shaped one of the most consequential digital laws of our time behind closed doors.
A blunt overreach of state power:
1) Universal identification and data retention, every click, message, and connection must be logged under your legal name, turning the entire population into perpetual suspects. This is an overreach of our fundamental right to privacy.
2) Encryption smashed: providers must supply data “in an intelligible way” (Rec 27.iii), forcing them to weaken or bypass end-to-end encryption whenever asked. This introduces vulnerabilities which hostile powers as well as legitimate actors can use.
3) Backdoors by design: hardware and software makers are ordered to bake permanent law-enforcement access points into phones, laptops, cars, and IoT devices (Rec 22, 25, 26). This will weaken European digitalization efforts and our own IT industry.
4) Privacy shields outlawed: VPNs and other anonymity tools must start logging users or shut down. This is, yet again, an overreach of our fundamental right to privacy and would hamper business in the European Union as many central processes rely on secure connections and privacy shields.
5) Criminalized resistance: services or developers who refuse to spy on their users face fines, market bans, or prison (Rec 34). Again, a deliberate weakening of our own IT industry.
6) No one exempt: the rules cover every “electronic communication service”, from open-source chat servers to encrypted messengers to vehicle communications systems (Rec 17, 18, 27.ii). Again, a complete overreach, both regarding our right to privacy but also with whom this legislation affects.
A mass surveillance law, drafted in secrecy by unknown actors, with provisions that go beyond what we see in many authoritarian regimes. And yet, the European Commission is advancing it as if it’s routine policy work.
The European Commission must halt this process immediately. No law that enables this scale of surveillance, especially one built in the shadows, should ever be allowed to pass. Europe must not become a place where privacy dies quietly behind closed doors.
This threatens the fundamental rights of every citizen in the Union.
1 note
·
View note
Text
User-level Git secrets policy in EMR Studio Workspaces

Set up EMR Studio workplace collaboration. AWS Improves EMR Studio Security with Detailed IAM Permissions
Amazon Web Services (AWS) provides fine-grained control over user behaviours in Amazon EMR Studio, a big data analytics programming environment. New material covers AWS Identity and Access Management (IAM) user rights setup for controlling access to Amazon EMR clusters on EC2 or Amazon EKS. This comprehensive solution lets administrators set fine-grained permissions for user roles and authentication methods. It is important to note that this guide's permissions focus more on EMR Studio activity management than input dataset data access control. To manage dataset access, the Studio must directly establish cluster permissions. Foundational: User Roles and Permissions Permission architecture in EMR Studio emphasises user roles and access policies. IAM Identity Centre authentication requires an EMR Studio user role. This involves creating a role to grant permissions to an AWS service according to AWS procedures. This user position was built around trust relationship policy. This policy determines which service can perform the job. Acting like sts:Sts, AssumeRole:SetContext, EMR Studio's trust policy should allow elasticmapreduce.amazonaws.com to play the role. Standard trust policies look like this:
After creating the role, remove default policies and permissions. Before assigning users to Studios, this role is related with EMR Studio session policies.
Alternative authentication methods like direct IAM authentication or IAM federation with an external identity provider link permissions policies to IAM identities (users, groups, or roles). External IdP IAM jobs or roles are tied to IAM federation policies. Tiers of Permission Administrators can create IAM permissions policies to restrict Studio user access. Documentation includes basic, intermediate, and advanced policies. A careful analysis maps every Studio process to the minimum IAM activities. Permissions policies must include certain statements. Tagging Secrets Manager secrets with emr-studio-* requires permissions.
Example of Basic User Policy
Basic user policies allow most EMR Studio actions but restrict users from directly creating Amazon EMR clusters. It covers permissions to create, describe, list, start, stop, and delete Workspaces (elasticmapreduce: CreateEditor, DescribeEditor, ListEditors, DeleteEditor), view the Collaboration panel, access S3 for logs and bucket listings, attach and detach EC2 and EKS clusters, debug jobs using persistent and on-cluster user interfaces, and manage Git repositories. This policy includes tag-based access control (TBAC) requirements for EMR Studio service role compatibility. It can enumerate IAM roles (iam:ListRoles) and describe network objects (ec2:DescribeVpcs, DescribeSubnets, DescribeSecurityGroups). Direct IAM authentication requires the CreateStudioPresignedUrl permission, which the simple policy example lacks. Intermediate/Advanced Skills Intermediate user policy expands basic permissions. All basic EMR Studio actions work. Most crucially, it grants permissions for using cluster templates to create new Amazon EMR clusters. This covers CloudFormation:DescribeStackResources and Service Catalogue:SearchProducts, DescribeProduct, and ProvisionProduct. Intermediate users can attach and detach EMR Serverless apps. The enhanced user policy allows all EMR Studio functions for maximum access. In addition to the intermediate policy, elasticmapreduce:RunJobFlow can create new Amazon EMR clusters from templates or with a complete setup. The advanced policy also allows access to Amazon Athena SQL editor with Glue, KMS, and S3 permissions (athena:*, glue:*, kms:*, s3:* actions for data catalogue, queries, etc.), Amazon SageMaker AI Studio for Data Wrangler visual interface (sagemaker:* actions), and Amazon CodeWhisperer. The advanced policy requires CreateStudioPresignedUrl permission and TBAC requirements for IAM authentication users, like the basic and intermediate examples. The full table in the documentation shows how to add and remove Workspaces:
Workplace collaboration
Multiple users can cooperate in EMR Studio's workspace. You need certain rights to use the Collaboration panel in the Workspace UI: Elasticmapreduce:ListWorkspaceAccessIdentities, UpdateEditor, PutWorkspaceAccess, and DeleteWorkspaceAccess. The panel is accessible to authorised users. Limited collaboration can be achieved via tag-based access control. EMR Studio automatically applies a default tag with the key creatorUserId and the value the workspace creator's ID upon workspace creation. Manually tag older workspaces for TBAC, which applies to workspaces created after November 16, 2021. By using a policy variable like ${aws:userId}, users can enable collaboration only for their created Workspaces.
Policy variables like aws:userId enable request context-based policy evaluation. Managing Git Secret Permissions Integrating Git repositories with EMR Studio requires permissions to access AWS Secrets Manager Git credentials. EMR Studio automatically tags newly created Git secrets with for-use-with-amazon-emr-managed-user-policies for user-level access control. Users or services can set Git secret permissions. User-level management is implemented by adding tag-based permissions to the EMR Studio user role policy for the secretsmanager:GetSecretValue function. This policy utilises the tag ${aws:userId} for usage with Amazon EM R controlled user policies.
EMR Studio service role policy permissions for secretsmanager:GetSecretValue should be removed when moving to user-level rights. EMR Studio automatically applied the user-level tag on September 1, 2023. Secrets generated before this date must be tagged or recreated for user-level rights. Keeping GetSecretValue in the service role policy lets administrators use service-level access. For more precise secret access control, user-level permissions with tag-based access control are recommended. Last thoughts on EMR Studio permissions Businesses using Amazon EMR Studio must configure these IAM rights. Administrators can employ user roles, custom permission policies, and tag-based access control for Git secrets and Workspace collaboration to provide users the access they need to do their work. This enhances security and clarifies Studio user capabilities. These systems provide tight control over Studio activities, but restricting data access is also important for security.
#AmazonEMRStudio#Gitsecrets#EMRStudioservice#tagbasedaccesscontrol#AWSservice#Gitsecretspolicy#technology#technews#technologynews#news#govindhtech
0 notes
Text
Enhancing Document Management with SharePoint Document Libraries

In today’s hybrid workplace, managing documents effectively is a challenge many organizations continue to face. As businesses scale, so does the volume of digital content — making it critical to have a system in place that offers structured storage, secure access, and seamless collaboration. Enter SharePoint Document Libraries — a feature-rich, scalable, and secure solution that addresses these challenges with enterprise-grade precision.
What Makes SharePoint Document Libraries Stand Out?
At its core, a SharePoint Document Library is a centralized repository for storing files. However, it goes far beyond basic file storage. It integrates deeply with Microsoft 365 applications like Teams, Outlook, and OneDrive, enabling employees to collaborate in real-time without switching between platforms.
From an IT and information governance perspective, SharePoint provides granular permission controls, version history, and audit trails. Admins can define access at the library, folder, or even document level — ensuring sensitive data is only available to authorized users.
Key Features for Technical and Business Teams
1. Metadata and Content Organization
One of the most powerful features of SharePoint Document Libraries is metadata tagging. Rather than relying solely on folder hierarchies, documents can be categorized using custom columns and metadata filters. This makes search and retrieval far more efficient, especially in large libraries with thousands of files.
2. Versioning and Check-in/Check-out
Version control ensures that every edit is tracked and reversible. The check-in/check-out functionality prevents overwriting and maintains document integrity during collaborative editing.
3. Automation and Workflows
Integration with Power Automate allows organizations to build automated document workflows — from approval chains and review cycles to retention and archival policies. This eliminates manual steps and enhances compliance.
4. Co-authoring and Real-Time Collaboration
Multiple team members can work on the same document simultaneously using Word, Excel, or PowerPoint, with real-time updates and commenting. This accelerates teamwork and reduces reliance on email-based communication.
5. Security and Compliance
With support for Microsoft Purview, Information Rights Management (IRM), and DLP (Data Loss Prevention), SharePoint Document Libraries help enforce regulatory compliance and data security at every level.
Practical Use Cases Across Industries
Whether you're in healthcare managing patient records, in manufacturing handling technical documents, or in finance dealing with audit files, SharePoint Document Libraries can be tailored to your business needs. Document templates, content types, and workflow configurations can be customized to match internal processes — all while maintaining enterprise-grade scalability.
Final Thoughts
The SharePoint Document Library is more than just a file storage tool — it’s a strategic asset for businesses aiming to centralize knowledge, improve collaboration, and enforce document governance. As organizations continue to embrace digital transformation, leveraging SharePoint’s document management capabilities ensures teams stay connected, compliant, and efficient.
0 notes
Text
What are the steps to obtain GDPR certification in Malaysia?

GDPR Certification in Malaysia , With the rise of cross-border data flows, many Malaysian businesses–especially in IT, BPO, e-commerce, and cloud services–are expected to comply with the EU General Data Protection Regulation (GDPR). Although the GDPR accreditation is not required, it is a strong confidence signal and is an official proof of compliance for firms processing personal data of EU citizens.
Here is a step-by-step procedure to obtain the GDPR certificate within Malaysia.
Step 1: Understand GDPR Requirements
Begin by developing a thorough knowledge of the basic principles of GDPR. And its underlying principles, such as:
Legal, fair, and transparent processing
Limitation of purpose and minimization of data
Data subject rights (access, erasure, rectification, etc.)
Consent and accountability
Information about security and breach obligations
Malaysian companies must understand the difference between GDPR and the Malaysian Personal Data Protection Act (PDPA) and where additional compliance measures are required.
Step 2: Conduct a GDPR Gap Analysis
Before you can seek certification, conduct a gap analysis of the GDPR to:
Examine your current practices in the field of data processing
Find processes that are not in compliance
Map personal data flow (especially those involving EU individuals who are data subjects)
You might want to consider using data mapping tools or employing a GDPR consultant from Malaysia to make this process easier.
Step 3: Build or Update Your Data Protection Program
Update or develop your privacy policies and procedures to ensure they align with the GDPR. For example:
Privacy policy (in simple and clear language)
Assessment of the impact of data protection (DPIA) templates
Consent management procedures
Data breach response plan
Processing of requests for data subject rights
Documentation is crucial to prove accountability (Articles 5 and 24 in GDPR).
Step 4: Train Staff on GDPR Principles
Employee awareness is vital. Provide GDPR-related training sessions to:
Management
Cybersecurity and information technology teams
Marketing and customer service staff
All employees who handle personal data
The training must be based on the participant’s role and include examples relevant to Malaysian company operations.
Step 5: Strengthen Technical and Organizational Security Measures
To meet the GDPR Article 32 (Security of Processing), you’ll have to implement:
Controls of access and encryption
Secure transfer and storage protocols for data
A regular security assessment and vulnerability check
Response procedures and detection of incidents
ISO 27001 certification can support GDPR compliance efforts by improving information security governance.
Step 6: Appoint a Data Protection Officer (DPO) or Representative
If your Malaysian company frequently monitors or processes huge amounts of EU data, GDPR might be a requirement for you to:
Appoint a Data Protection Officer (DPO)
Designate the designation of a representative within the EU (Article 27) to serve as the point of contact for regulators and data subjects.
Your DPO may be internal or outsourced, but they must be knowledgeable about GDPR.
Step 7: Choose an Accredited GDPR Certification Body
A certified certification body must have issued GDPR certifications within the EU framework. While the EU accredits any Malaysian certification bodies, you can:
Partner in conjunction with a GDPR consultant in Malaysia who works with certification bodies that are EU-approved
Request Audits of GDPR compliance from companies that have experience in cross-border privacy regulations
Make preparations for the future EU-recognized certifications as soon as they are available in the region.
Check for certification schemes approved by the authorities under Articles 42 and 43 of GDPR..
Step 8: Undergo a GDPR Compliance Audit
After you have your guidelines, control, and procedures in place, your certification authority will
Review your documentation
Review your organization’s and technical security measures
Interview with the appropriate personnel
Check your breach response and the handling of the rights of data subjects
Successful audits are the basis for a GDPR certificate, usually valid for three years with annual monitoring audits.
Why choose Factocert for GDPR Certification in Malaysia?
Do you need a GDPR Consultant in Malaysia? Factocert has the top GDPR Consultant in Malaysia with global expertise for Malaysian businesses doing business with EU countries GDPR Compliance for Data Protection and Data Privacy. Our Consultant provides the best GDPR Certification in Malaysia; send us an inquiry to this mail id [email protected] with all the necessary information or visit our official website www.factocert.com so that one of our experienced Consultants will contact you at the initial to finely understand your requirements and provide a best available solution in market
For more information visit us : GDPR Certification in Malaysia
0 notes