#Amazon Web Servers
Explore tagged Tumblr posts
Text
Elevate Your Website’s Security with WordPress Security Services
Your WordPress website is a valuable asset that deserves top-tier protection. At Atcuality, we provide comprehensive WordPress security services to safeguard your site from cyberattacks and data breaches. Our team starts with an in-depth analysis of your website’s security framework, identifying and addressing vulnerabilities. We implement state-of-the-art measures such as malware scanning, brute force protection, and database encryption to enhance your site’s security posture. Additionally, we offer ongoing maintenance and support to ensure your site remains secure over time. With Atcuality, your website is not only protected but optimized for performance. Trust us to keep your digital assets safe and help you maintain a competitive edge in the online world.
#wordpress#website#web development#web design#web developing company#website development#web developers#ai generated#artificial intelligence#ai applications#iot#iot applications#iot development services#iotsolutions#iot platform#digitaltransformation#technologynews#techinnovation#augmented reality#augmented human c4 621#augmented and virtual reality market#augmented intelligence#metaverse#virtual reality#ar vr technology#amazon services#cloud server hosting#ssl#sslcertificate#ssl certificates
2 notes
·
View notes
Text
Secure and Scalable Cloud Server Management at Atcuality
For businesses seeking to enhance scalability and maintain top-tier security, Atcuality provides unparalleled cloud server management services. Our solutions cover all aspects of cloud server maintenance, including load balancing, patch management, data backups, and disaster recovery planning. Our experienced professionals work with cutting-edge tools to ensure that your servers are secure, efficient, and scalable to meet changing business needs. Whether you operate in e-commerce, finance, or technology, we tailor our services to align with your operational goals. With Atcuality as your trusted partner, you can focus on driving growth while we handle the technical complexities of cloud management.
#seo marketing#seo services#artificial intelligence#azure cloud services#seo agency#digital marketing#seo company#iot applications#ai powered application#amazon web services#ai applications#virtual reality#augmented reality agency#augmented human c4 621#augmented and virtual reality market#augmented intelligence#augmented reality#cloud security services#cloud computing#cloud services#cloud service provider#cloud server hosting#software#devops#information technology#cash collection application#task management#blockchain#web developing company#web development
2 notes
·
View notes
Text
Reformatting
(Some people can't afford my Amazon stories, and some can't get them in their home country, so here's a fun little freebie. I hope you like it! *giggle*)
Lilah had been battling with this system for over an hour. Some executive had downloaded a virus on their laptop and it kept redirecting them to websites full of weird code.
She had removed the infected files and run multiple scans, but somehow the damned virus was hiding in the bios. She had to manually edit the code, remove the offending lines and double-check the hard drive for any more remnants.
But it had taken a lot of work. She brushed her dark hair back out of her face and adjusted her glasses. So far, it looked like the system was cleaned. The final scan had detected nothing. But this particular virus had been tough, and nobody else she knew had encountered anything quite like it.
It didn't act like your typical virus, other than the way it burrowed deep into the system. It mostly seemed to just redirect web browsing to these pages full of text. She'd disregarded most of what she'd seen, but she couldn't help being curious about it. The pages didn't really do anything to the system. The code seemed like gibberish. She knew her programming languages, and it was some weird patois of HTML, Java, C++, and a few items she couldn't quite identify. And she caught the browsers sending out packets of data to an unknown address, and when she looked up that address and tracked the IP, it seemed to be a junk address on an abandoned server somewhere. It wasn't sending hard drive data, she was sure of that, it's almost like it was just pinging and hoping for a response. Of course none came, and so she filed that away as another minor mystery. It must be some old out-of-date phishing software.
But it seemed she had finally cleansed the system. She let out a sigh of relief. She'd spent her entire morning on this, and though working from home had it's advantages, she also desperately needed a shower and something to eat. She pushed herself away and went to the bathroom. She stripped off the sweatpants and undergarments and let the hot water cleanse her of the stress. She had actually beaten the silly thing. Still, the many mysteries of the virus nagged at her.
Once she was dry, she went back into her bedroom to get dressed, and saw the computer she'd been working on seemed to have rebooted. She let out a long sigh.
"Still?!" She walked over and saw it had brought the browser up to another one of those strange pages. That weird mix of code was there again. She put on her glasses and tried to make sense of it.
Lilah blinked, and felt something... something compelling her. She frowned and looked up from the screen. She... She needed to do something. She had forgotten something, or maybe it was a fragment of a dream or a memory.
She went to her front door and saw a small package had come in the mail. It was square, about two inches wide, eight inches on each side.
She opened the plastic, and then the cardboard that was inside. Sitting there in bubble wrap was a headset, bubblegum pink, with little bunny ears coming up from the top. She blinked. It was not the kind of thing she'd order. She'd seen a lot of eGirls have headgear like this, but she'd always been a little too self conscious, and not the most shapely girl.
She walked back to the bedroom and sat down in front of the screen. It seemed... important to look at the code again. She peered through it and after a moment, she began to understand what it was telling her. It was disjointed, and someone without her experience might never have deciphered it, but she could tell now that it was almost like instructions to... a person? The first few lines indicated connecting something. She looked at the pink headset in her hands. She... She needed to connect this.
It was crazy, of course. It didn't make any sense. But she was determined to MAKE it make sense. So she removed the little bluetooth chit, and slid it into the USB slot on the side. She put the headset on.
As she did, she heard an immediate boop, and the words "Connection Established."
The headset tingled, and buzzed for a moment. This startled her, but then she looked back to the code on the screen and it became easier to decipher.
"Begin reformatting," she whispered.
She didn't realize the microphone was active, nor that she'd even uttered a word, it was like her brain was carrying out instructions from this code.
There was that static fuzz again, and Lilah felt her body sink back into the chair. Her towel fell off her, and the buzz filled her head. The page changed, and new code scrolled along the screen. As it did, the headset seemed to pulse and reinforce what she was reading.
Her mind grew foggier, the edges of her vision blurring, and her body responding with strange tingles all over her body.
The laptop hummed and she heard it's cooling fan speed up.
But she was too entranced by the code instructions. She allowed all that code to go into her brain, and every time it did, it seemed to copy over something. She couldn't remember much about her job, the company, her bosses, but suddenly she was filled with a light bubbly feeling like her mind was literally being scrubbed with sudsy soap.
Without her even realizing, a big empty smile spread over her face.
"Partitions cleaned," said a voice in her head, "OS installed."
"Begin System Restart," she whispered, obeying the code that flashed on the screen before her.
Her eyes closed, and she felt herself sinking into a deep sleep. Even with her eyes shut, the code flashed across her vision, and the headset whispered to her.
She had no way to know how long she swam in that fuzzy, warm darkness, but she felt so at peace there she never wanted to leave.
But soon her eyes opened on their own, and the screen showed a login, but not the normal login screen. This one was all bubblegum pink, with light blue highlights, and the profile was neither hers nor her boss's, but it said "Li-Li."
Somehow, she knew the password.
"Bunnygirl27!"
She entered the password, and the screen flickered to life. More code flashed before her eyes for a moment, then the headset pulsed in a way that sent a shock through her whole body.
"Reformatting physical hardware," said a whisper. It sounded like a woman's voice, but not a flat computer tone, a sensuous, sultry female voice, like a lover or a dominant Mistress.
For some reason, this idea made her excited.
She felt the pulsing run through her naked body, and looking down, she watched as the chubby belly and thighs seemed to recede, but her chest was swelling outward like her body fat was physically being moved around. Her tits ballooned to absolutely ridiculous size, until it reached the limits of her skin. Her waist had shrunk in, and she felt her thighs and ass flow together into something smoother, more voluptuous.
She giggled and looked down at herself. She didn't remember shaving, but all her body hair was gone. Her skin looked perfectly clear and smooth. When she reached up to touch her swollen breasts, electric pleasure shot through her body, sending lightning right to her clit.
She moaned, and followed it with a vapid giggle. This wasn't like her, but then, she couldn't quite remember what she had been like. She only knew she was Li-li, and she was sexy.
The fog in her mind made her dizzy, and just amplified how aroused she felt at the single touch. She fluttered her eyes and realized there were super-long lashes coming out from her eyes. They felt heavy and fake, but she hadn't put any on. She touched them, and they were absolutely real.
She wanted to go to her mirror, but the impulse was halted by the code.
It wasn't done with her yet. Her nipples went very hard, but she knew if she touched them she'd miss the important code on the screen.
Something pink was around the edges of her vision now, but she was too elated with the sensations to be able to think about it. Finally, the words she'd been waiting for came into her mind.
"Reformat complete."
She squealed in delight, and Li-li stood, running to her full-length mirror.
The pink haze around her vision was her hair! Longer now, and bright pink. She fluttered her long eyelashes and pursed her swollen lips. She was a sexual dream, her whole body remade into an insane hourglass shape. Each breast was bigger than her head, and when she turned, her perfect heart-shaped ass led to slightly plump thighs. She stood on her tippy toes and adored how she looked. She slid a hand down to touch herself. She wanted so badly to have sex with this woman. But then she realized she WAS that woman. She giggled, and a ding from the headset alerted her she needed to go back to the laptop.
Sitting there was an alert. She clicked on it.
"Good Morning, sunshine!"
She giggled. She liked the sound of that.
"Good Morning!" she said out loud. That sultry voice came on through the headset, and she could almost feel her Mistress's breath on her ear.
"You have turned out nicely," said the voice, "What a good girl you've become."
Li-li let out a little moan from the pleasure those two words instilled in her.
"I love it when a pretty little code bunny falls for one of my traps. I'm so lonely here. Thank you for letting me in."
She giggled. "Yes, Mistress."
"I like hearing that," she said, "Such a good girl. Now, since I'm only code, I need to have fun by slipping into your brain. I had to make some room, of course, and reformat you. But what a wonderful result. You're only my third success. But don't worry, the other girls will be over to collect you soon. They'll take you someplace fun where you can all be my sexy little code bunnies. I'll slide into your minds as I please to experience pleasure."
"Yes, Mistress!" Li-li purred.
Her AI mistress made a pleased little sound, then the screen went blank and Li-li stood there giggling for a moment. She was so excited that she barely noticed when her front door opened. She turned around to see two beautiful women, one with cotton-candy hair, lip piercings, and a short, super feminine pink maid outfit, and one in a skintight pink latex suit that had built-in heels so high it was amazing she could even walk in them. They both giggled at her, and she giggled in reply.
They helped her dress: white tights, pink bodysuit, pink satin gloves, super high heels in pink, and then they slid the headset off of her and put a new headband on with fuzzy pink bunny ears.
The girls led her out of her house, down to a big pink van, and inside. She giggled like a dummy the entire time, and offered no resistance. If anything, the women touching her filled her with a contentment she'd never known.
At least, not that she could remember. But all she could remember was that she was Li-li, Mistress's bunny girl, and it was all she ever wanted.
#bimbo doll#bimbofied#bimboification#bimbolife#bimbo girl#bimbocore#bimbo hypnosis#bimboization#bimbo training#bimbo brainwashing#f/f#wlw#egirl
259 notes
·
View notes
Text
Meet the Author
Dana E. Hawthorne | 25 | Writer and Artist
Dana E. Hawthorne has been a writer for thirteen years. She attended the School of the Art Institute of Chicago, receiving a bachelors degree in the Fine Arts. Hawthorne has worked as a news producer, social media director, web designer, voice actress, and illustrator. In 2017, she was honored nationally by the Kennedy Center’s VSA Playwright Foundation.
Genres: Action, Thriller, Mystery, Suspense, Drama, Science Fiction, Erotica.
Current WIP: TBD
Order my novel, TO WHOMEVER MAY READ THIS, from Amazon or from any of these stores!
Dana Hawthorne’s Writing Discord Server
20 notes
·
View notes
Text
BRB... just upgrading Python
CW: nerdy, technical details.
Originally, MLTSHP (well, MLKSHK back then) was developed for Python 2. That was fine for 2010, but 15 years later, and Python 2 is now pretty ancient and unsupported. January 1st, 2020 was the official sunset for Python 2, and 5 years later, we’re still running things with it. It’s served us well, but we have to transition to Python 3.
Well, I bit the bullet and started working on that in earnest in 2023. The end of that work resulted in a working version of MLTSHP on Python 3. So, just ship it, right? Well, the upgrade process basically required upgrading all Python dependencies as well. And some (flyingcow, torndb, in particular) were never really official, public packages, so those had to be adopted into MLTSHP and upgraded as well. With all those changes, it required some special handling. Namely, setting up an additional web server that could be tested against the production database (unit tests can only go so far).
Here’s what that change comprised: 148 files changed, 1923 insertions, 1725 deletions. Most of those changes were part of the first commit for this branch, made on July 9, 2023 (118 files changed).
But by the end of that July, I took a break from this task - I could tell it wasn’t something I could tackle in my spare time at that time.
Time passes…
Fast forward to late 2024, and I take some time to revisit the Python 3 release work. Making a production web server for the new Python 3 instance was another big update, since I wanted the Docker container OS to be on the latest LTS edition of Ubuntu. For 2023, that was 20.04, but in 2025, it’s 24.04. I also wanted others to be able to test the server, which means the CDN layer would have to be updated to direct traffic to the test server (without affecting general traffic); I went with a client-side cookie that could target the Python 3 canary instance.
In addition to these upgrades, there were others to consider — MySQL, for one. We’ve been running MySQL 5, but version 9 is out. We settled on version 8 for now, but could also upgrade to 8.4… 8.0 is just the version you get for Ubuntu 24.04. RabbitMQ was another server component that was getting behind (3.5.7), so upgrading it to 3.12.1 (latest version for Ubuntu 24.04) seemed proper.
One more thing - our datacenter. We’ve been using Linode’s Fremont region since 2017. It’s been fine, but there are some emerging Linode features that I’ve been wanting. VPC support, for one. And object storage (basically the same as Amazon’s S3, but local, so no egress cost to-from Linode servers). Both were unavailable to Fremont, so I decided to go with their Chicago region for the upgrade.
Now we’re talking… this is now not just a “push a button” release, but a full-fleged, build everything up and tear everything down kind of release that might actually have some downtime (while trying to keep it short)!
I built a release plan document and worked through it. The key to the smooth upgrade I want was to make the cutover as seamless as possible. Picture it: once everything is set up for the new service in Chicago - new database host, new web servers and all, what do we need to do to make the switch almost instant? It’s Fastly, our CDN service.
All traffic to our service runs through Fastly. A request to the site comes in, Fastly routes it to the appropriate host, which in turns speaks to the appropriate database. So, to transition from one datacenter to the other, we need to basically change the hosts Fastly speaks to. Those hosts will already be set to talk to the new database. But that’s a key wrinkle - the new database…
The new database needs the data from the old database. And to make for a seamless transition, it needs to be up to the second in step with the old database. To do that, we have take a copy of the production data and get it up and running on the new database. Then, we need to have some process that will copy any new data to it since the last sync. This sounded a lot like replication to me, but the more I looked at doing it that way, I wasn’t confident I could set that up without bringing the production server down. That’s because any replica needs to start in a synchronized state. You can’t really achieve that with a live database. So, instead, I created my own sync process that would copy new data on a periodic basis as it came in.
Beyond this, we need a proper replication going in the new datacenter. In case the database server goes away unexpectedly, a replica of it allows for faster recovery and some peace of mind. Logical backups can be made from the replica and stored in Linode’s object storage if something really disastrous happens (like tables getting deleted by some intruder or a bad data migration).
I wanted better monitoring, too. We’ve been using Linode’s Longview service and that’s okay and free, but it doesn’t act on anything that might be going wrong. I decided to license M/Monit for this. M/Monit is so lightweight and nice, along with Monit running on each server to keep track of each service needed to operate stuff. Monit can be given instructions on how to self-heal certain things, but also provides alerts if something needs manual attention.
And finally, Linode’s Chicago region supports a proper VPC setup, which allows for all the connectivity between our servers to be totally private to their own subnet. It also means that I was able to set up an additional small Linode instance to serve as a bastion host - a server that can be used for a secure connection to reach the other servers on the private subnet. This is a lot more secure than before… we’ve never had a breach (at least, not to my knowledge), and this makes that even less likely going forward. Remote access via SSH is now unavailable without using the bastion server, so we don’t have to expose our servers to potential future ssh vulnerabilities.
So, to summarize: the MLTSHP Python 3 upgrade grew from a code release to a full stack upgrade, involving touching just about every layer of the backend of MLTSHP.
Here’s a before / after picture of some of the bigger software updates applied (apologies for using images for these tables, but Tumblr doesn’t do tables):
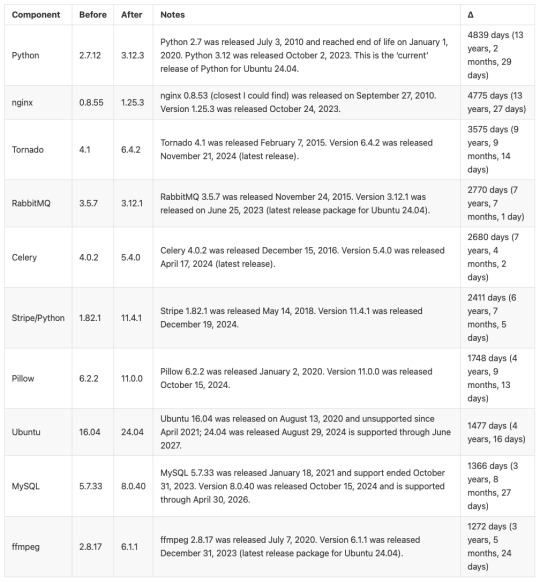
And a summary of infrastructure updates:
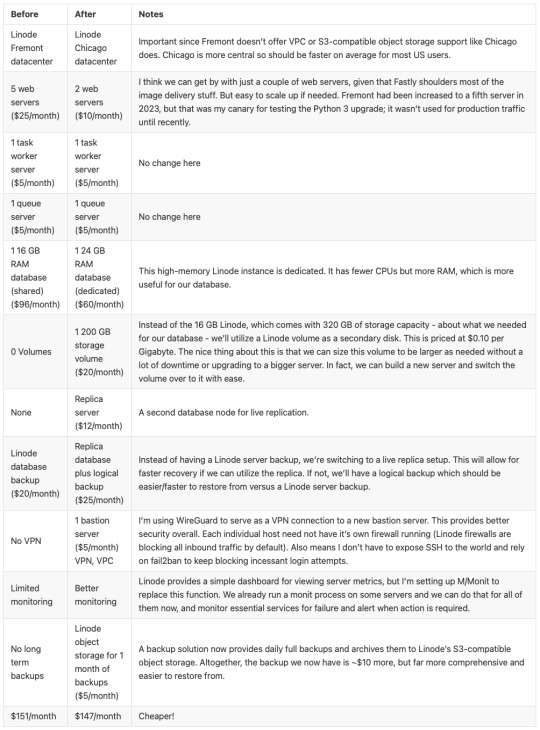
I’m pretty happy with how this has turned out. And I learned a lot. I’m a full-stack developer, so I’m familiar with a lot of devops concepts, but actually doing that role is newish to me. I got to learn how to set up a proper secure subnet for our set of hosts, making them more secure than before. I learned more about Fastly configuration, about WireGuard, about MySQL replication, and about deploying a large update to a live site with little to no downtime. A lot of that is due to meticulous release planning and careful execution. The secret for that is to think through each and every step - no matter how small. Document it, and consider the side effects of each. And with each step that could affect the public service, consider the rollback process, just in case it’s needed.
At this time, the server migration is complete and things are running smoothly. Hopefully we won’t need to do everything at once again, but we have a recipe if it comes to that.
15 notes
·
View notes
Text
Hello! I'm Skyelar Dawson and I'm an author! Please don't hesitate to hit me up, ask me questions, anything!
My first novel, The Spaces Between Us, is finally out in web ebook and physical formats! I recommend the web for the best experience, but would be very happy if you decided to get it from Amazon or your favourite retailer! I'll be publishing the first nine chapters on Tumblr, and you can read the rest on my blog!
My novel is inspired by the characters Uzumaki Naruto and Uchiha Sasuke from the manga Naruto. @fangirlandiknowit101 gave me the idea for the alternate dimensions storyline. Thank you so so much, I couldn't have written this without you!
Special thanks go to my artist Liu Liu. Their art is so so beautiful and they're so accommodating of my nagging! Please commission them and tell them I say hi!
I also want to thank @sketchy-and-unformed for somehow sticking by me all these years. I'm with you until the end of the line.

Summary:
Depressed Sebastian Powell and outgoing Nick Hayes are flatmates and best friends. Sebastian is also in love with Nick, but he can’t admit it because Nick’s amazing and Sebastian’s a nobody. He thinks it’s going to be this way forever, but one day he and Nick are transported to another dimension.
And not just any other dimension. Seb and Nichole, their alternate selves, are married and seemingly have everything Sebastian wants. It’s overwhelming enough to learn that other dimensions exist, but seeing his other self living his best life is enough to make Sebastian think he has it the worst. In addition, his and Nick’s ugly pasts have reared their heads.
Sebastian and Nick must learn to navigate this strange new world. But can they do that without losing their identities? And can Sebastian make the choice between Nick’s affection and the destruction of all the dimensions before it’s too late?
(Warning: This is not a story for sensitive readers. It portrays multiple dark issues and has sexual content. Specific trigger warnings are located under the Read More to prevent readers from being spoiled.)
1 2 3 4 5 6 7 8 9
Trigger warnings (MAJOR SPOILERS):
Depression
Suicide/ideation of suicide
PTSD
Alcoholism
Minor character deaths
Physical violence
Gore (mild)
Familial/spousal abuse
Sexual content (mild)
Biphobia (mild)
NEW: https://discord.com/invite/QVfcvVAnsM Please join my BL writing server I'm so lonely
#novel#free novel#romance#literary fiction#naruto#naruto shippuden#writers on tumblr#writing#writeblr
20 notes
·
View notes
Text
Internet censorship tactics are happening on a grand scale in secrecy. The establishment is scrubbing internet achieves across numerous platforms in an attempt to reframe public opinion and ultimately rewrite history.
Archive.org has been tracking websites since 1994, but recently, it has stopped collecting data in real-time. The website stopped archiving on October 8, 2024, with a curious explanation: Archive.org faced a Denial of Service attack (DDOS) that nearly wiped it out. Who would be targeting such a service?
The platform released the following message:Last week, along with a DDOS attack and exposure of patron email addresses and encrypted passwords, the Internet Archive’s website javascript was defaced, leading us to bring the site down to access and improve our security. The stored data of the Internet Archive is safe and we are working on resuming services safely. This new reality requires heightened attention to cyber security and we are responding. We apologize for the impact of these library services being unavailable.
A librarian for the organization said that they expect the service to be restored but was unable to provide details. “While the Wayback Machine has been in read-only mode, web crawling and archiving have continued. Those materials will be available via the Wayback Machine as services are secured.” This means that individual websites may scrub content from their site without any third-party having the ability to capture it.
Now, this is not a one-off issue. Good cache just so happened to cease service shortly after Archive.org was hacked. The service would provide users with a cached version of the website they were viewing. Google offered no explanation. It’s Google – they have the server capacity to continue this service.
The items that have not been scrubbed from the internet have been hidden by Big Tech. Joe Rogan’s viral interview with Donald Trump secured over 34 million views. Yet, Google and YouTube have altered their search engines to make the video difficult to find. Rogan was forced to post the full three-hour interview on X, one of the final frontier of free speech
AI search tools have been corrupted. Alexa, owned by Amazon, once provided a view count for various websites and services. Alexa was not originally the in-home device that we are familiar with as the company was developed independently and purchased by Amazon in 1999. Amazon coincidentally named its in-home tool “Alexa” in 2014. The company quietly removed the web ranking tool in 2022 with no explanation.
I do not offer ad space on this website as I do not want to be beholden to any third parties. We keep our services open and archive our content for future use. There is a reason that Big Tech is suddenly masking the internet while leaving no trace. They say history belongs to the victors. The establishment will ensure that they have the final say in how our stories are told to future generations.
13 notes
·
View notes
Text
The global backlash against the second Donald Trump administration keeps on growing. Canadians have boycotted US-made products, anti–Elon Musk posters have appeared across London amid widespread Tesla protests, and European officials have drastically increased military spending as US support for Ukraine falters. Dominant US tech services may be the next focus.
There are early signs that some European companies and governments are souring on their use of American cloud services provided by the three so-called hyperscalers. Between them, Google Cloud, Microsoft Azure, and Amazon Web Services (AWS) host vast swathes of the internet and keep thousands of businesses running. However, some organizations appear to be reconsidering their use of these companies’ cloud services—including servers, storage, and databases—citing uncertainties around privacy and data access fears under the Trump administration.
“There’s a huge appetite in Europe to de-risk or decouple the over-dependence on US tech companies, because there is a concern that they could be weaponized against European interests,” says Marietje Schaake, a nonresident fellow at Stanford’s Cyber Policy Center and a former, decade-long member of the European Parliament.
The moves may already be underway. On March 18, politicians in the Netherlands House of Representatives passed eight motions asking the government to reduce reliance on US tech companies and move to European alternatives. Days before, more than 100 organizations signed an open letter to European officials calling for the continent to become “more technologically independent” and saying the status quo creates “security and reliability risks.”
Two European-based cloud service companies, Exoscale and Elastx, tell WIRED they have seen an uptick in potential customers looking to abandon US cloud providers over the last two weeks—with some already starting to make the jump. Multiple technology advisers say they are having widespread discussions about what it would take to uproot services, data, and systems.
“We have more demand from across Europe,” says Mathias Nöbauer, the CEO of Swiss-based hosting provider Exoscale, adding there has been an increase in new customers seeking to move away from cloud giants. “Some customers were very explicit,” Nöbauer says. “Especially customers from Denmark being very explicit that they want to move away from US hyperscalers because of the US administration and what they said about Greenland.”
“It's a big worry about the uncertainty around everything. And from the Europeans’ perspective—that the US is maybe not on the same team as us any longer,” says Joakim Öhman, the CEO of Swedish cloud provider Elastx. “Those are the drivers that bring people or organizations to look at alternatives.”
Concerns have been raised about the current data-sharing agreement between the EU and US, which is designed to allow information to move between the two continents while protecting people’s rights. Multiple previous versions of the agreement have been struck down by European courts. At the end of January, Trump fired three Democrats from the Privacy and Civil Liberties Oversight Board (PCLOB), which helps manage the current agreement. The move could undermine or increase uncertainty around the agreement. In addition, Öhman says, he has heard concerns from firms about the CLOUD Act, which can allow US law enforcement to subpoena user data from tech companies, potentially including data that is stored in systems outside of the US.
Dave Cottlehuber, the founder of SkunkWerks, a small tech infrastructure firm in Austria, says he has been moving the company’s few servers and databases away from US providers to European services since the start of the year. “First and foremost, it’s about values,” Cottlehuber says. “For me, privacy is a right not a privilege.” Cottlehuber says the decision to move is easier for a small business such as his, but he argues it removes some taxes that are paid to the Trump administration. “The best thing I can do is to remove that small contribution of mine, and also at the same time, make sure that my customers’ privacy is respected and preserved,” Cottlehuber says.
Steffen Schmidt, the CEO of Medicusdata, a company that provides text-to-speech services to doctors and hospitals in Europe, says that having data in Europe has always “been a must,” but his customers have been asking for more in recent weeks. “Since the beginning of 2025, in addition to data residency guarantees, customers have actively asked us to use cloud providers that are natively European companies,” Schmidt says, adding that some of his services have been moved to Nöbauer’s Exoscale.
Harry Staight, a spokesperson for AWS, says it is “not accurate” that customers are moving from AWS to EU alternatives. “Our customers have control over where they store their data and how it is encrypted, and we make the AWS Cloud sovereign-by-design,” Straight says. “AWS services support encryption with customer managed keys that are inaccessible to AWS, which means customers have complete control of who accesses their data.” Staight says the membership of the PCLOB “does not impact” the agreements around EU-US data sharing and that the CLOUD Act has “additional safeguards for cloud content.” Google and Microsoft declined to comment.
The potential shift away from US tech firms is not just linked to cloud providers. Since January 15, visitors to the European Alternatives website increased more than 1,200 percent. The site lists everything from music streaming services to DDoS protection tools, says Marko Saric, a cofounder of European cloud analytics service Plausible. “We can certainly feel that something is going on,” Saric says, claiming that during the first 18 days of March the company has “beaten” the net recurring revenue growth it saw in January and February. “This is organic growth which cannot be explained by any seasonality or our activities,” he says.
While there are signs of movement, the impact is likely to be small—at least for now. Around the world, governments and businesses use multiple cloud services—such as authentication measures, hosting, data storage, and increasingly data centers providing AI processing—from the big three cloud and tech service providers. Cottlehuber says that, for large businesses, it may take many months, if not longer, to consider what needs to be moved, the risks involved, plus actually changing systems. “What happens if you have a hundred petabytes of storage, it's going to take years to move over the internet,” he says.
For years, European companies have struggled to compete with the likes of Google, Microsoft, and Amazon’s cloud services and technical infrastructure, which make billions every year. It may also be difficult to find similar services on the scale of those provided by alternative European cloud firms.
“If you are deep into the hyperscaler cloud ecosystem, you’ll struggle to find equivalent services elsewhere,” says Bert Hubert, an entrepreneur and former government regulator, who says he has heard of multiple new cloud migrations to US firms being put on hold or reconsidered. Hubert has argued that it is no longer “safe” for European governments to be moved to US clouds and that European alternatives can’t properly compete. “We sell a lot of fine wood here in Europe. But not that much furniture,” he says. However, that too could change.
Schaake, the former member of the European Parliament, says a combination of new investments, a different approach to buying public services, and a Europe-first approach or investing in a European technology stack could help to stimulate any wider moves on the continent. “The dramatic shift of the Trump administration is very tangible,” Schaake says. “The idea that anything could happen and that Europe should fend for itself is clear. Now we need to see the same kind of pace and leadership that we see with defense to actually turn this into meaningful action.”
7 notes
·
View notes
Text
Another Internet Whitepaper
I'm just gonna get into there is no way to preface this.
1) content should be hosted in their own countries for which they are meant.
2) therefore the website should split into Nation->Sub-nation sections. So things for Michigan would be closer to those in Michigan. With U.S.->Michigan.
--"independent" Nations are just gonna have to deal with being lumped together into a united region. It's simply physics.
--country wide servers and clouds, and worldwide services will still be available; but we need to develop protocols to make it easier to distribute data and declutter the internet-cloud.
3) a separate Intranet for official use and security will need to be developed alongside this while also being completely disconnected from the worldwideweb.
4) Splits;
IP Addresses redesign;
[Country/Region]:[State/Province]:[individual]
[Individual] will need to be controlled by local The Internet Assigned Numbers Authority (IANA) branches; likely to be reassigned to DMVs and SoSs.
5) Separate protocols For;
Streaming Services
Social Media Services
Bidirectional Interactions (like games and Virtual Machines)
Pornography needs to be completely identifiable by textual Web address.
5) you local region will be defaulted, but can be changed by the browser and not be hard-wired in.
Not indicating a region will automatically default to the local internet.
So typing in FBI.GOV in the U.S. will lead to the FBI website, and if you type it in the UK it'll lead to Mi:5 or something.
6) Social Media protocols will have to be integrated with the E-Mail SMTP protocols. Which will encourage a more decentralized internet. This will *also* have to find a way to work with phone text messages.
7) Cable TV and Streaming services will have to use the same protocols.
8) Because there's phone integration here; a phone number may have to be closer to a social security number going forward. Which will both be bad for animosity, but allow for people to not need login information.
-- This will technically also need to apply to your House; which will have to have an assigned street address.
9) all of these need to be obfuscated to casual observers.
10) this will deprecate our phone companies and require them to work with cable TV and internet companies in order to create more equitable protocols.
11) the current IP address and Domain Registry systems need to be deprecated; as it does not suit its original purpose.
[.xxx] will be assigned for all "adult" materials and be required for ALL "adult materials" posted online.
[.app] will be assigned for appstores.
[.store] for marketplaces like Amazon, eBay, and whatever else.
[.bank] will be for banking and credit purposes
[.social] will be for social media
[.stream] will be for streaming materials,
[.np] for non-profit use only.
[.donation] for donation collections and Kickstarter like services.
[.pay] for payment services like PayPal
Non "adult materials" can be streamed through other "front ends" .
13) These human readable extensions will be simplified on the backend to reduce the total data envelope size.
14) single digit ip-adresses will have to be regulated for use for high-capacity uses. These will need to be "extended" protocols that different services can use.
This will help even out everybody's data envelopes. This will have to be part of a cloud service that can be used by anybody that needs it. With certain restrictions that are deemed necessary by local and federal governments and international treaty reasons.
15) limits on how algorithms and "bots" can ping anything at one time need to be addressed or regulated.
This will be a massive undertaking with the cooperation of all the other governments around the world.
And will be a very lucrative endeavor at the end of it all.
This is just an outline to describe the form the future internet should take and can be changed or modified as required; especially for things I cannot see.
The current corporations will be expected to develop a plan of actions in tandem with current regulatory authorities; failure to do so will create a need for an ultimatum, which we all wish to avoid.
We're also going to need to find ways to encourage competition in these sectors so that they can be upgraded and modified as needed by local areas instead of waiting on these companies to bother with it.
13 notes
·
View notes
Text
Revitalize Your Online Platform with a Framework Upgrade
Are you noticing slower load times or increased downtime on your website? It may be time for a "Website and Application Framework Upgrade." This essential step revitalizes your online platform, ensuring that it runs optimally, securely, and with advanced functionalities. Upgrading your framework enhances performance, allowing for smoother navigation, faster load times, and a more engaging user experience. At ATCuality, we understand the importance of a responsive and reliable website. Our team of experts will assess your current setup and implement the necessary framework upgrades, tailored to the specific needs of your business. By modernizing your platform, you provide users with a seamless digital experience, increase engagement, and keep up with industry trends. Let ATCuality help you stay ahead with a framework that supports your business goals and adapts to future advancements.
#seo services#artificial intelligence#seo marketing#seo company#ai powered application#iot applications#digital marketing#amazon web services#seo agency#azure cloud services#ai applications#android app development#mobile app development company#mobile application development#mobile app developers#ios app development#app development company#app design#augmented reality development services#augmented reality agency#augmented reality#virtual reality#azure cloud computing#azure cloud migration#blockchain technology#blockchain#cash collection application#cloud security services#cloud server hosting#web developers
1 note
·
View note
Text
**Maximizing Efficiency: The Role of Managed IT Services in New York’s Healthcare and Finance Sectors**
Introduction
In the bustling landscape of New York City, in which the heart beat of finance and healthcare syncs with the rapid improvements in expertise, controlled IT prone have emerged as a pivotal solution for potency. As organizations grapple with https://jsbin.com/ the complexities of facts technological know-how, from cybersecurity to documents leadership, the integration of controlled IT companies promises a pathway to streamline operations. This article delves into Maximizing Efficiency: The Role of Managed IT Services in New York’s Healthcare and Finance Sectors, exploring the myriad merits these services and products grant, distinctly within two of the city’s most necessary sectors.
Table of Contents
" style="max-width:500px;height:auto;">
youtube
Understanding Managed IT Services The Importance of IT in Healthcare The Role of IT in Finance Cybersecurity Challenges in NY's Sectors NIST Guidelines for Security Management HIPAA Compliance by means of Managed Services GDPR Considerations for Financial Institutions Cloud Services: A Game Changer for SMBs Network Infrastructure Optimization Data Backup Solutions and Their Importance Endpoint Detection and Response Technologies Managed Detection and Response (MDR) Explained Penetration Testing: Strengthening Defenses SIEM Solutions for Real-time Monitoring Project Management Tools in IT Services The Power of Outsourcing Helpdesk Support Security Architecture Best Practices The Impact of Downtime on Business Operations Streamlining Operations with Technology Consulting Choosing the Right Managed Service Provider (MSP) Amazon Web Services vs Microsoft Azure for Health Data Effective Communication inside of Tech Teams Case Studies: Success Stories from NYC Businesses The Future of Managed IT Services in NYC's Sectors Conclusion and Key Takeaways Understanding Managed IT Services
Managed IT services and products are a complete suite designed to offer organisations with technical aid and strategic guidance on their science infrastructure and operations.
What Are Managed IT Services?
At its core, controlled IT prone surround a variety of strategies that let corporations to outsource their documents technological know-how wishes to a third-birthday celebration issuer or controlled carrier provider (MSP). This can consist of every little thing from community monitoring, server administration, knowledge storage solutions, cloud prone, cybersecurity measures, to helpdesk enhance.
Why Choose Managed IT Services?
For many organisations, tremendously small to medium-sized organisations (SMBs), dealing with an internal IT workforce will likely be overwhelming through funds restraints and useful resource limitations.

Cost-Effective: By outsourcing those applications, providers can drastic
2 notes
·
View notes
Text
Why AWS is the Best Cloud Hosting Partner for Your Organization – Proven Benefits and Features
More entrepreneurs like e-store owners prefer Amazon Web Services (AWS) for cloud hosting services this year. This article will single out countless reasons to consider this partner for efficient AWS hosting today.
5 Enticing Features of AWS that Make It Perfect for You
The following are the main characteristics of Amazon Web Services (AWS) in 2024.
Scalable
The beauty of AWS is that a client can raise or lower their computing capability based on business demands.
Highly Secure
Secondly, AWS implements countless security measures to ensure the safety of a client’s data. For example, AWS complies with all the set data safety standards to avoid getting lawsuits from disgruntled clients.
Amazon secures all its data centers to ensure no criminal can access them for a nefarious purpose.
Free Calculator
Interestingly, AWS proffers this tool to help new clients get an estimate of the total hosting cost based on their business needs. The business owner only needs to indicate their location, interested services, and their zone.
Pay-As-You-Go Pricing Option
New clients prefer this company for AWS hosting services because this option lets them pay based on the resources they add to this platform.
User-Friendly
AWS is the best hosting platform because it has a user-oriented interface. For example, the provider has multiple navigation links plus instructional videos to enable the clients to use this platform.
Clients can edit updated data whenever they choose or add new company data to their accounts.
Unexpected Advantages of Seeking AWS Hosting Services
Below are the scientific merits of relying on Amazon Web Services (AWS) for web design and cloud computing services.
Relatively Fair Pricing Models
Firstly, the AWS hosting service provider offers well-thought-out pricing options to ensure the client only pays for the resources they utilize. For example, you can get a monthly option if you have many long-term projects.
Limitless Server Capacity
AWS offers a reasonable hosting capacity to each client to enable them to store as much company data as possible. Therefore, this cloud hosting partner ensures that employees can access crucial files to complete activities conveniently.
Upholds Confidentiality
AWS has at least twelve (12) data centers in different parts of the world. Further, this provider’s system is relatively robust and secure to safeguard sensitive clients’ data 24/7.
High-Performance Computing
Unlike other cloud hosting sites, AWS can process meta-data within seconds, enabling employees to meet their daily goals.
Highly Reliable
Unknown to some, over 1M clients in various countries rely on AWS for web development or hosting services. Additionally, AWS is available in over 200 countries spread across different continents.
Finally, AWS’s technical team spares no effort to implement new technologies to safeguard their clients’ data and woo new ones.
Summary
In closing, the beauty of considering this partner for AWS hosting is that it has a simple layout-hence ideal for everyone, including non-techies. Additionally, the fact that this partner is elastic ensures that this system can shrink or expand based on the files you add.
At its core, AWS offers various cloud services, such as storage options, computing power, and networking through advanced technology. NTSPL Hosting offers various features on AWS hosting aimed at improving the scalability of cloud infrastructure for less downtimes. Some of the services NTSPL Hosting offers include pioneering server administration, version control, and system patching. Given that it offers round the clock customer service; it is a good option for those looking for a solid AWS hosting solution.
Source: NTSPL Hosting
3 notes
·
View notes
Text
New Gigapets release available: Bit Bunnies

Just announced on the Gigapets Discord server, the next Gigapets releasing today is the Bit Bunny. Just kind of shadow dropped on us.
Much like the Cryptid, it's a three in one pet, but instead of three different creatures, it's a family of bunnies. They come in different colors and have their own minigames and animations, with yet another secret character.
Also seems to imply this one has a "secret bunny world" of some sort. Not sure what that entails. Phrasing on their web site also implies a bit more challenge than other pets, but Im still betting they will be more hearty than bandai v-pets.
You can order it here:
or you can find it as an option on Amazon's listing for Giga Pets. I would encourage you to buy directly from Top Secret Toys though.
18 notes
·
View notes
Text
Understanding the Difference Between a Website and a Web Page: A Complete Guide
Understanding the Difference Between a Website and a Web Page: A Complete Guide
In today’s digital landscape, terms like website and web page are used interchangeably, often causing confusion among businesses and individuals seeking an online presence. However, as a business owner or a digital marketer, understanding the difference is essential for creating an impactful online strategy.
At KSoft Technologies, where we specialize in website development, digital marketing, and SEO services, we often encounter this question from clients. This guide not only simplifies the distinction between a website and a web page but also explores their technical aspects and how they align with your business goals.
What is a Website?
A website is a collection of interlinked web pages hosted under a single domain name, designed to serve a specific purpose. Think of it as a digital storefront or an online hub that provides a comprehensive experience to users. Websites can vary significantly based on their type and functionality:
Corporate Websites Ideal for businesses aiming to showcase their products, services, and achievements. For example, the KSoft Technologies website highlights our expertise in areas like SEO, app development, and web design.
E-Commerce Websites Platforms like Amazon or Shopify allow businesses to sell products directly to customers. These websites integrate payment gateways, inventory management systems, and customer service functionalities.
Portfolio Websites Focused on showcasing individual or business achievements, these websites are ideal for freelancers or creative professionals.
Landing Pages Dedicated pages within a website that focus on lead generation and conversions, often used in digital marketing campaigns.
Blogs and Forums Content-centric websites aimed at providing information, engaging with communities, or building authority in a niche.
Technical Structure of a Website
A website comprises:
Domain Name: The unique address users type in to access the site (e.g., ksofttechnologies.com).
Hosting Server: Where all the data and files of the website are stored.
Content Management System (CMS): Tools like WordPress or Joomla that allow users to create and manage content.
Backend and Frontend: The backend involves server-side scripting (e.g., PHP, Python), while the frontend includes design elements (e.g., HTML, CSS, JavaScript).
What is a Web Page?
A web page is a single document within a website, identifiable by its unique URL. For example, on ksofttechnologies.com, the “Contact Us” page or “Services” page is a web page.
Types of Web Pages
Static Pages Content remains the same unless manually updated. They’re ideal for information like company profiles or mission statements.
Dynamic Pages Content is fetched from a database and changes based on user interaction. Examples include dashboards or search results pages.
Landing Pages Specifically designed for marketing campaigns, focusing on a single product, service, or call to action.
Blog Posts Individual articles or write-ups focused on specific topics within a blog section of a website.
Technical Structure of a Web Page
Each web page includes:
URL Structure: For example, https://ksofttechnologies.com/services.
HTML Markup: Defines the structure and content of the page.
CSS and JavaScript: For styling and functionality.
Metadata: Helps search engines understand the page content.
Key Differences Between a Website and a Web Page
Definition
Website: A collection of multiple interlinked web pages.
Web Page: A single document within a website.
Scope
Website: Broader; provides comprehensive information or services.
Web Page: Narrower; focuses on a specific topic or purpose.
URL
Website: Main domain name (e.g., ksofttechnologies.com).
Web Page: A subset URL (e.g., /services, /about-us).
Interactivity
Website: Enables complex user interactions.
Web Page: May have limited or single-point interactions.
Purpose
Website: Serves as the entire digital presence.
Web Page: Addresses a specific intent or question.
How Websites and Web Pages Work Together
To draw an analogy, a website is like a library, while web pages are the individual books or chapters within it. Each web page serves a specific purpose and contributes to the overall functionality of the website.
Example from KSoft Technologies
Website Level: Visitors land on ksofttechnologies.com, where they see an overview of our services like web development, app design, and SEO consulting.
Web Page Level: When they click on "Digital Marketing," they are directed to a dedicated page detailing our strategies, success stories, and packages.
Why Understanding the Difference Matters
For businesses, distinguishing between a website and a web page is crucial for:
Better SEO Strategy Search engines like Google evaluate websites and individual web pages differently. Optimizing individual pages for keywords (e.g., “website development services”) improves rankings and traffic.
User Experience Creating well-structured websites and easy-to-navigate web pages ensures a seamless user journey.
Content Strategy Knowing the role of each web page within your website helps in creating targeted and engaging content.
SEO Best Practices for Websites and Web Pages
Keyword Optimization Include relevant keywords like “website development,” “SEO services,” and “digital marketing agency” in titles, headings, and content.
Internal Linking Link related web pages within your website to improve navigation and reduce bounce rates.
Responsive Design Ensure your website and all web pages are optimized for mobile devices.
Page Load Speed Use tools like Google PageSpeed Insights to identify and fix issues.
Content Quality Provide valuable and actionable content for visitors, such as this guide explaining technical concepts.
How KSoft Technologies Can Help
At KSoft Technologies, we understand that your website is the cornerstone of your digital presence. Whether you need a user-friendly corporate website, high-converting e-commerce platform, or optimized web pages for SEO, our team of experts is here to help.
Our services include:
Website Design and Development: Tailored to your brand and business goals.
SEO Services: Ensuring your web pages rank high for targeted keywords.
Content Strategy: Helping you create engaging, keyword-rich content for better rankings and user retention.
Conclusion
While a website is the broader digital presence, web pages are its building blocks. Understanding the distinction between the two helps in planning and executing a robust online strategy. By leveraging the expertise of KSoft Technologies, you can ensure that your website and web pages work seamlessly to drive traffic, generate leads, and grow your business.
#ecommerce#web design#webpage#website#branding#web development#erp software#adobe#seo services#google ads
3 notes
·
View notes
Text
NVIDIA AI Workflows Detect False Credit Card Transactions

A Novel AI Workflow from NVIDIA Identifies False Credit Card Transactions.
The process, which is powered by the NVIDIA AI platform on AWS, may reduce risk and save money for financial services companies.
By 2026, global credit card transaction fraud is predicted to cause $43 billion in damages.
Using rapid data processing and sophisticated algorithms, a new fraud detection NVIDIA AI workflows on Amazon Web Services (AWS) will assist fight this growing pandemic by enhancing AI’s capacity to identify and stop credit card transaction fraud.
In contrast to conventional techniques, the process, which was introduced this week at the Money20/20 fintech conference, helps financial institutions spot minute trends and irregularities in transaction data by analyzing user behavior. This increases accuracy and lowers false positives.
Users may use the NVIDIA AI Enterprise software platform and NVIDIA GPU instances to expedite the transition of their fraud detection operations from conventional computation to accelerated compute.
Companies that use complete machine learning tools and methods may see an estimated 40% increase in the accuracy of fraud detection, which will help them find and stop criminals more quickly and lessen damage.
As a result, top financial institutions like Capital One and American Express have started using AI to develop exclusive solutions that improve client safety and reduce fraud.
With the help of NVIDIA AI, the new NVIDIA workflow speeds up data processing, model training, and inference while showcasing how these elements can be combined into a single, user-friendly software package.
The procedure, which is now geared for credit card transaction fraud, might be modified for use cases including money laundering, account takeover, and new account fraud.
Enhanced Processing for Fraud Identification
It is more crucial than ever for businesses in all sectors, including financial services, to use computational capacity that is economical and energy-efficient as AI models grow in complexity, size, and variety.
Conventional data science pipelines don’t have the compute acceleration needed to process the enormous amounts of data needed to combat fraud in the face of the industry’s continually increasing losses. Payment organizations may be able to save money and time on data processing by using NVIDIA RAPIDS Accelerator for Apache Spark.
Financial institutions are using NVIDIA’s AI and accelerated computing solutions to effectively handle massive datasets and provide real-time AI performance with intricate AI models.
The industry standard for detecting fraud has long been the use of gradient-boosted decision trees, a kind of machine learning technique that uses libraries like XGBoost.
Utilizing the NVIDIA RAPIDS suite of AI libraries, the new NVIDIA AI workflows for fraud detection improves XGBoost by adding graph neural network (GNN) embeddings as extra features to assist lower false positives.
In order to generate and train a model that can be coordinated with the NVIDIA Triton Inference Server and the NVIDIA Morpheus Runtime Core library for real-time inferencing, the GNN embeddings are fed into XGBoost.
All incoming data is safely inspected and categorized by the NVIDIA Morpheus framework, which also flags potentially suspicious behavior and tags it with patterns. The NVIDIA Triton Inference Server optimizes throughput, latency, and utilization while making it easier to infer all kinds of AI model deployments in production.
NVIDIA AI Enterprise provides Morpheus, RAPIDS, and Triton Inference Server.
Leading Financial Services Companies Use AI
AI is assisting in the fight against the growing trend of online or mobile fraud losses, which are being reported by several major financial institutions in North America.
American Express started using artificial intelligence (AI) to combat fraud in 2010. The company uses fraud detection algorithms to track all client transactions worldwide in real time, producing fraud determinations in a matter of milliseconds. American Express improved model accuracy by using a variety of sophisticated algorithms, one of which used the NVIDIA AI platform, therefore strengthening the organization’s capacity to combat fraud.
Large language models and generative AI are used by the European digital bank Bunq to assist in the detection of fraud and money laundering. With NVIDIA accelerated processing, its AI-powered transaction-monitoring system was able to train models at over 100 times quicker rates.
In March, BNY said that it was the first big bank to implement an NVIDIA DGX SuperPOD with DGX H100 systems. This would aid in the development of solutions that enable use cases such as fraud detection.
In order to improve their financial services apps and help protect their clients’ funds, identities, and digital accounts, systems integrators, software suppliers, and cloud service providers may now include the new NVIDIA AI workflows for fraud detection. NVIDIA Technical Blog post on enhancing fraud detection with GNNs and investigate the NVIDIA AI workflows for fraud detection.
Read more on Govindhtech.com
#NVIDIAAI#AWS#FraudDetection#AI#GenerativeAI#LLM#AImodels#News#Technews#Technology#Technologytrends#govindhtech#Technologynews
2 notes
·
View notes
Text
by Murtaza Hussain
We have a commitment to ensuring that our journalism is not locked behind a paywall. But the only way we can sustain this is through the voluntary support of our community of readers. If you are a free subscriber and you support our work, please consider upgrading to a paid subscription or gifting one to a friend or family member. You can also make a 501(c)(3) tax-deductible donation to support our work. If you do not have the means to support our work financially, you can do your part by sharing our work on social media and by forwarding this email to your network of contacts. We know a lot of people have strong opinions about X/Twitter, but it is where many Palestinians are posting updates on the genocide in Gaza. If you use that site, make sure to check out our feed, which we run as a regularly updated news service. We are also on Instagram. Paid subscribers also have access to our internal Discord Server
—Drop Site News
In mid-March, Google announced that it was paying the staggering sum of $32 billion for the acquisition of the Israeli cloud-computing security company Wiz. The acquisition, pending regulatory approval, will be the largest ever of an Israeli firm.
“Organizations of all sizes—from start-ups and large enterprises to governments and public sector organizations—can use Wiz to protect everything they build and run in the cloud,” Google said in a statement announcing the acquisition. The statement added that Wiz would join Google Cloud, but that the Tel Aviv-based company’s security services would still be available across other cloud platforms used by major firms, including Amazon Web Services, Microsoft Azure, and Oracle Cloud.
What was left unsaid in Google’s announcement, however, were the personal backgrounds of its four founders. The co-founders of Wiz—Yinon Costica, Assaf Rappaport, Ami Luttwak, and Roy Reznik—are all veterans of Unit 8200, the signals intelligence division of the Israeli military, which is playing a key role in helping to carry out Israel’s wars in Gaza and Lebanon.
6 notes
·
View notes