#CA Software Technologies
Explore tagged Tumblr posts
Text
Chinese Researchers Release World’s First AI-Based Fully Automated Processor Chip Design System
— Global Times | June 10, 2025

Photo: VCG
Chinese Researchers have released the World’s First Fully Automated Processor Chip Design System based on Artificial Intelligence (AI) Technology, making AI-designed chips a reality. With its designs comparable to the performance of human experts across multiple key metrics, the system represents a significant step toward fully automated chip design, potentially revolutionizing how chips are designed and manufactured.
The system named QiMeng jointly released by the Institute of Computing Technology, Chinese Academy of Sciences (CAS) and the Institute of Software of CAS, were recently published on arXiv.org, the Science and Technology Daily reported on Tuesday.
The QiMeng works like an automated architect and builder for computer chips. Instead of engineers manually designing every component, it uses AI to handle both the hardware and software aspects of chip creation.

China’s AI Chip Tool QiMeng Beats Engineers, Designs Processors In Just Days! With QiMeng, China’s Top Scientists Have Used AI To Build Processors Comparable To Intel’s 486 and Arm’s Cortex A53. June 10, 2025, Aamir Khollam Representational Image of AI-Driven Chip Design Process in China. Михаил Руденко/iStock. InterestingEngineering.Com
Expected to transform the design paradigms for the hardware and software of processor chip, the system not only significantly reduces human involvement, enhances design efficiency and shortens development cycles, but also enables rapid, customized designs tailored to specific application scenarios – flexibly meeting the increasingly diverse demands of chip design, the Science and Technology Daily reported.
Processor chips are hailed as the “Crown Jewel” of modern science and technology, with their design processes being highly complex, precise, and requiring a very high level of expertise. Traditional processor chip design relies heavily on experienced expert teams, often involving hundreds of people and taking months or even years to complete, resulting in high costs and lengthy development cycles.
Meanwhile, with the development of emerging technologies such as AI, cloud computing and edge computing, market demands for specialized processor chips and their corresponding foundational software optimization are growing rapidly. However, the number of professionals engaged in the processor chip industry in China is severely insufficient to meet this increasing demand.
In response to these challenges, the QiMeng system leverages advanced AI technologies such as large models to realize automated CPU design. It can also automatically configure corresponding foundational software for the chip, including operating systems, compilers and high-performance kernel libraries, according to the report.
#China 🇨🇳#Global Times#Chinese Researchers#World’s First AI-Based Fully Automated Processor Chip Design System#Artificial Intelligence (AI) Technology#Institute of Computing Technology | Chinese Academy of Sciences (CAS) | Institute of Software of CAS#“Crown Jewel”
0 notes
Text
Streamline Hybrid Event Planning with the Power of SMS
In the fast-evolving world of events, hybrid gatherings have become a cornerstone for connecting with audiences both physically and virtually. As organizations adopt this versatile approach, the demand for effective communication tools has become more critical than ever. SMS messaging stands out as a pivotal tool, enriching engagement and streamlining coordination throughout all stages of events.

Enhancing Engagement with SMS
Enablex's Hybrid Event Platform integrates robust SMS APIs, offering event planners a versatile tool to engage attendees effectively. By incorporating SMS into event planning, organizers can send timely reminders, updates, and personalized notifications. This proactive approach ensures that attendees stay informed about schedule changes, session updates, and networking opportunities, thereby enhancing their overall event experience.
Key Benefits of Using SMS in Hybrid Events
Real-Time Updates: Instantly notify attendees about last-minute changes or urgent announcements, ensuring everyone remains informed and on schedule.
Personalized Interaction: Use SMS to send personalized messages based on attendee preferences and behavior, fostering a deeper connection and engagement. Personalized greetings or targeted content can significantly enhance attendee satisfaction and participation.
Audience Reach: SMS boasts a significantly higher open rate compared to emails, making it a reliable channel to effectively reach a broader audience. This wider reach ensures that important event information reaches attendees promptly and reliably.
Interactive Features: SMS enables two-way communication, allowing attendees to engage with polls, surveys, and Q&A sessions in real-time, enriching the event experience. Interactive SMS features not only engage attendees but also provide valuable feedback and insights for event organizers.
Cost-Effective Solution: Implementing SMS as part of your hybrid event strategy is cost-effective compared to traditional marketing channels, offering a high return on investment. The affordability of SMS messaging allows organizers to allocate resources efficiently while maximizing attendee engagement and satisfaction.
Implementing SMS API for Seamless Integration
Enablex's robust SMS API empowers event planners to integrate SMS seamlessly into their existing platforms. Whether automating registration confirmations or sending event reminders, the API simplifies communication workflows. Its scalability ensures that whether you're managing a small seminar or a large-scale conference, SMS remains a reliable tool for communication.
Best Practices for Using SMS in Hybrid Events
Segment Your Audience: Tailor SMS messages based on attendee demographics, interests, and registration details to increase relevance and engagement. Segmenting your audience allows for personalized messaging that resonates with attendees, driving higher engagement and satisfaction.
Timing Is Key: Send messages at strategic times, such as before sessions start or during networking breaks, to maximize impact without overwhelming attendees. Strategic timing ensures that SMS messages are well-received and contribute positively to the attendee experience.
Clear Call-to-Actions: Include clear instructions or calls-to-action in your SMS messages to guide attendees on the next steps, such as accessing event resources or joining virtual sessions. Clear and actionable SMS content empowers attendees to take immediate action, enhancing their overall event participation and satisfaction.
Compliance and Privacy: Ensure compliance with local regulations (like GDPR) and respect attendees' privacy preferences when sending SMS messages. Maintaining compliance and respecting privacy builds trust with attendees and enhances the overall credibility of your event communications.
Case Study: Real-World Application of SMS in Hybrid Events
To illustrate the effectiveness of SMS in enhancing hybrid event experiences, consider a case study where a global technology conference utilized Enablex's SMS capabilities. By integrating SMS notifications for session reminders and live polls during presentations, the conference saw a 30% increase in attendee engagement compared to previous years. The real-time interaction facilitated by SMS not only kept attendees informed but also encouraged active participation and networking, ultimately contributing to the event's success.
FAQs About Using SMS in Hybrid Events
Q: How can SMS enhance attendee engagement?
A: SMS allows for real-time updates, personalized communication, and interactive features like polls and Q&A sessions, fostering active participation and engagement among attendees.
Q: Is SMS cost-effective for large-scale events?
A: Yes, SMS is a cost-effective solution compared to traditional marketing channels, offering higher open rates and engagement levels, especially for time-sensitive information.
Q: Can SMS be integrated with existing event management platforms?
A: Yes, Enablex's SMS API allows seamless integration with various event management platforms, enabling event organizers to automate and streamline communication workflows effectively.
Conclusion
In conclusion, leveraging SMS in hybrid event planning enhances attendee engagement, streamlines communication, reduces logistical challenges and enhances overall event success. With its robust SMS API and comprehensive features, Enablex's Hybrid Event Platform offers event planners a powerful tool to create memorable and impactful hybrid experiences. By embracing SMS, organizers can ensure that every attendee remains informed, engaged, and connected throughout the event journey.
By integrating SMS into your hybrid event strategy, you're not just communicating; you're creating meaningful interactions that drive participation and satisfaction. Embrace the power of SMS with Enablex and elevate your hybrid events to new heights of success.
#api#sdk#video ca#sms#bulk sms#sms marketing#hybrid#saas#saas technology#saas software#cpaas#cpaas provider
1 note
·
View note
Text
How does the adoption of blockchain in auditing firms enhance the practices of Chartered Accountants?
Introduction: In recent years, the accounting and auditing landscape has undergone a transformative shift with the integration of blockchain technology. Blockchain, the decentralized and transparent ledger system that underlies cryptocurrencies, has found its way into various industries, and auditing firms are no exception. This exploration aims to highlight how the adoption of blockchain in…

View On WordPress
#Blockchain Technology#Chartered accountant software#Chartered Accountants#external audit software#internal audit software#software for CA#statutory audit software for chartered accountants#Technology
0 notes
Text
On Saturday, an Associated Press investigation revealed that OpenAI's Whisper transcription tool creates fabricated text in medical and business settings despite warnings against such use. The AP interviewed more than 12 software engineers, developers, and researchers who found the model regularly invents text that speakers never said, a phenomenon often called a “confabulation” or “hallucination” in the AI field.
Upon its release in 2022, OpenAI claimed that Whisper approached “human level robustness” in audio transcription accuracy. However, a University of Michigan researcher told the AP that Whisper created false text in 80 percent of public meeting transcripts examined. Another developer, unnamed in the AP report, claimed to have found invented content in almost all of his 26,000 test transcriptions.
The fabrications pose particular risks in health care settings. Despite OpenAI’s warnings against using Whisper for “high-risk domains,” over 30,000 medical workers now use Whisper-based tools to transcribe patient visits, according to the AP report. The Mankato Clinic in Minnesota and Children’s Hospital Los Angeles are among 40 health systems using a Whisper-powered AI copilot service from medical tech company Nabla that is fine-tuned on medical terminology.
Nabla acknowledges that Whisper can confabulate, but it also reportedly erases original audio recordings “for data safety reasons.” This could cause additional issues, since doctors cannot verify accuracy against the source material. And deaf patients may be highly impacted by mistaken transcripts since they would have no way to know if medical transcript audio is accurate or not.
The potential problems with Whisper extend beyond health care. Researchers from Cornell University and the University of Virginia studied thousands of audio samples and found Whisper adding nonexistent violent content and racial commentary to neutral speech. They found that 1 percent of samples included “entire hallucinated phrases or sentences which did not exist in any form in the underlying audio” and that 38 percent of those included “explicit harms such as perpetuating violence, making up inaccurate associations, or implying false authority.”
In one case from the study cited by AP, when a speaker described “two other girls and one lady,” Whisper added fictional text specifying that they “were Black.” In another, the audio said, “He, the boy, was going to, I’m not sure exactly, take the umbrella.” Whisper transcribed it to, “He took a big piece of a cross, a teeny, small piece … I’m sure he didn’t have a terror knife so he killed a number of people.”
An OpenAI spokesperson told the AP that the company appreciates the researchers’ findings and that it actively studies how to reduce fabrications and incorporates feedback in updates to the model.
Why Whisper Confabulates
The key to Whisper’s unsuitability in high-risk domains comes from its propensity to sometimes confabulate, or plausibly make up, inaccurate outputs. The AP report says, "Researchers aren’t certain why Whisper and similar tools hallucinate," but that isn't true. We know exactly why Transformer-based AI models like Whisper behave this way.
Whisper is based on technology that is designed to predict the next most likely token (chunk of data) that should appear after a sequence of tokens provided by a user. In the case of ChatGPT, the input tokens come in the form of a text prompt. In the case of Whisper, the input is tokenized audio data.
The transcription output from Whisper is a prediction of what is most likely, not what is most accurate. Accuracy in Transformer-based outputs is typically proportional to the presence of relevant accurate data in the training dataset, but it is never guaranteed. If there is ever a case where there isn't enough contextual information in its neural network for Whisper to make an accurate prediction about how to transcribe a particular segment of audio, the model will fall back on what it “knows” about the relationships between sounds and words it has learned from its training data.
According to OpenAI in 2022, Whisper learned those statistical relationships from “680,000 hours of multilingual and multitask supervised data collected from the web.” But we now know a little more about the source. Given Whisper's well-known tendency to produce certain outputs like "thank you for watching," "like and subscribe," or "drop a comment in the section below" when provided silent or garbled inputs, it's likely that OpenAI trained Whisper on thousands of hours of captioned audio scraped from YouTube videos. (The researchers needed audio paired with existing captions to train the model.)
There's also a phenomenon called “overfitting” in AI models where information (in this case, text found in audio transcriptions) encountered more frequently in the training data is more likely to be reproduced in an output. In cases where Whisper encounters poor-quality audio in medical notes, the AI model will produce what its neural network predicts is the most likely output, even if it is incorrect. And the most likely output for any given YouTube video, since so many people say it, is “thanks for watching.”
In other cases, Whisper seems to draw on the context of the conversation to fill in what should come next, which can lead to problems because its training data could include racist commentary or inaccurate medical information. For example, if many examples of training data featured speakers saying the phrase “crimes by Black criminals,” when Whisper encounters a “crimes by [garbled audio] criminals” audio sample, it will be more likely to fill in the transcription with “Black."
In the original Whisper model card, OpenAI researchers wrote about this very phenomenon: "Because the models are trained in a weakly supervised manner using large-scale noisy data, the predictions may include texts that are not actually spoken in the audio input (i.e. hallucination). We hypothesize that this happens because, given their general knowledge of language, the models combine trying to predict the next word in audio with trying to transcribe the audio itself."
So in that sense, Whisper "knows" something about the content of what is being said and keeps track of the context of the conversation, which can lead to issues like the one where Whisper identified two women as being Black even though that information was not contained in the original audio. Theoretically, this erroneous scenario could be reduced by using a second AI model trained to pick out areas of confusing audio where the Whisper model is likely to confabulate and flag the transcript in that location, so a human could manually check those instances for accuracy later.
Clearly, OpenAI's advice not to use Whisper in high-risk domains, such as critical medical records, was a good one. But health care companies are constantly driven by a need to decrease costs by using seemingly "good enough" AI tools—as we've seen with Epic Systems using GPT-4 for medical records and UnitedHealth using a flawed AI model for insurance decisions. It's entirely possible that people are already suffering negative outcomes due to AI mistakes, and fixing them will likely involve some sort of regulation and certification of AI tools used in the medical field.
87 notes
·
View notes
Text

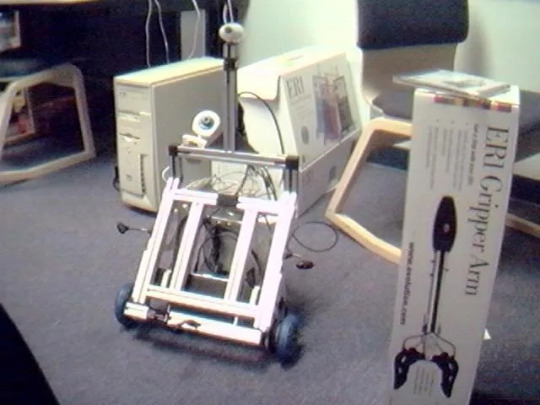

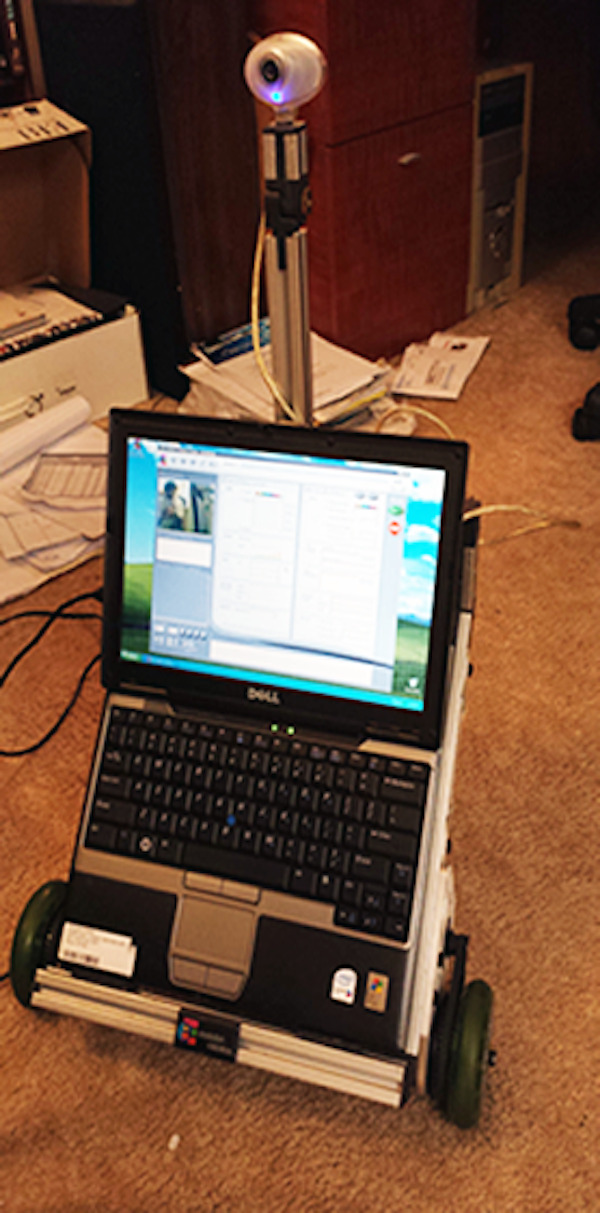

youtube
ER1 Personal Robot System by Evolution Robotics, Pasadena, CA (2002). "Coupled with Robot Control Center software and your laptop, the ER1 can be taught to negotiate your home, recognize objects visually, obey voice commands, and speak using its own text-to-speech voice. The solid aluminum ER1 is available either in kit form or already assembled. If you're handy with a screwdriver, you can spend a couple of hours and save $200. All the electronics come assembled. Once you've finished building the frame, just plug in the beefy stepper motors, the rechargeable power supply, and the control box. Your laptop rests on the ER1's cushioned mounts and connects through its USB ports to the robot's camera and control box." – ER1 Robot Kit, by Jay Munro.
Evolution Robotics "makes its technologies available to the developer community through the ER1, a programmable robot kit that can be purchased on the Evolution Robotics website and at leading technology retailers. Evolution Robotics mission is to accelerate the personal robot industry and help spur the creation of a variety of highly functional personal robot products that will become indispensable in our daily lives, at home and at work." – Bandai to Create Doraemon Robots, by Christopher Macdonald, Anime News Network.
26 notes
·
View notes
Text
CYBER TORTURE /ELECTRONIC HARASSMENT /GANGSTALKING
Cyber-stalking or online harassment, the technologies and tactics used by abusers in technology-facilitated stalking constantly evolve and may seem impossible or unrealistic when you first hear about them, but stalkers are creative and often go to great lengths to terrorize victims.”
🔵“…they monitor, surveil, contact, control, and isolate victims, as well as the ways they damage victims’ credibility or reputation.”
🔵“Stalkers may use phones, computers, tablets, software, the internet, email, social media, messaging applications, smart home devices, recording devices, tracking devices, or other digital electronic devices and software to facilitate their stalking behavior. Stalkers are pervasive in the ways they monitor, surveil, contact, control, and isolate victims, as well as the ways they damage victims’ credibility or reputation.”
YOU'RE ONE STEP AWAY FROM FREEDOM MESSAGE US NOW FOR HELP 💯 @@ Worldwide TI Support Organization
#flyingmonkey #gangstalking #V2K #PsychologicalWarfare #tievidence #MKUltra #Torture #CIA #FBI #targetedindividualscanada #mentalabuse #narcawareness #toxicrelationship #psychologicalwarfare #Narcissist #gangstalking #narcssurvivor #Gaslighting #domesticvoilence #manipulation #targetedindividualsunited #targetedindividualsbrazil #targetedindividualscanada #targetedindividualsnewyork #targetsouthflorida #target #targetedindividualsusa #gangstalkingtactics #targetedindividualsusa #targetedindividualsnewyork
3 notes
·
View notes
Text
Best Courses to Study in Australia for Indian Students with High ROI.

Why Australia is a Top Study Abroad Destination in 2025
Australia continues to rank among the top destinations for Indian students seeking world-class education, global career opportunities, and a multicultural lifestyle. With over 100,000 Indian students currently studying in Australia, the trend is fueled by high employability, quality institutions, and welcoming immigration policies. This blog provides a complete study guide in Australia for Indian students, focusing on the top courses offering the highest return on investment (ROI) in 2025.
Top Reasons to Study in Australia for Indian Students
Globally ranked universities like the University of Melbourne, ANU, and UNSW
Post-study work visas for up to 4 years
Pathways to Permanent Residency (PR)
Industry-relevant, skill-based courses
High graduate employability
Scholarships and financial support for Indian students
High ROI Courses for Indian Students in Australia
1. Information Technology and Computer Science
Why It’s Worth It:
Booming tech industry in cities like Sydney and Melbourne
Strong demand for software developers, AI specialists, and cybersecurity analysts
Excellent PR pathways via the Skilled Occupation List (SOL)
Career Opportunities:
Software Developer
Cloud Engineer
Cybersecurity Analyst
Average Salary: AUD 70,000 – 120,000
2. Engineering (Civil, Mechanical, Electrical, Mining)
Why It’s Worth It:
High demand for engineers in infrastructure, renewable energy, and mining
PR-friendly occupations
Hands-on, accredited programs (Engineers Australia recognition)
Career Paths:
Civil Engineer
Structural Engineer
Renewable Energy Consultant
Average Salary: AUD 75,000 – 130,000
3. Health Sciences & Nursing
Why It’s Worth It:
Acute shortage of skilled healthcare workers
Strong employment growth projected until 2030
Offers direct PR routes for nursing graduates
Career Opportunities:
Registered Nurse
Public Health Officer
Physiotherapist
Average Salary: AUD 65,000 – 110,000
4. Business Analytics and Data Science
Why It’s Worth It:
High demand across sectors (banking, retail, healthcare)
Versatile career paths with global appeal
STEM classification supports extended post-study work visa
Career Options:
Data Analyst
Business Intelligence Consultant
Data Scientist
Average Salary: AUD 85,000 – 130,000
5. Accounting and Finance
Why It’s Worth It:
Consistent job demand across Australia
Accredited courses (CPA Australia, CA ANZ)
Opens doors to roles in multinational firms
Career Opportunities:
Chartered Accountant
Financial Analyst
Auditor
Average Salary: AUD 70,000 – 115,000
6. Education and Teaching
Why It’s Worth It:
Australia’s school system seeks qualified teachers, especially in regional areas
Included in the Medium and Long-term Strategic Skills List (MLTSSL)
Roles After Graduation:
Primary School Teacher
Early Childhood Educator
Secondary School Teacher
Average Salary: AUD 65,000 – 100,000
7. Architecture and Construction Management
Why It’s Worth It:
Australia’s urban expansion and infrastructure projects
Recognized qualifications with global applicability
Popular Careers:
Architect
Project Manager
Construction Estimator
Average Salary: AUD 70,000 – 120,000
Cost of Education in Australia (2025)
Course Type
Average Annual Tuition (AUD)
UG Courses
20,000 – 45,000
PG Courses
22,000 – 50,000
MBA
40,000 – 80,000
Scholarships Available for Indian Students
Australia Awards Scholarships – Fully funded by the Australian government
Destination Australia Scholarships – Regional study scholarships worth AUD 15,000
University-Specific Grants – E.g., Monash International Merit Scholarship, University of Sydney International Scholarships
Post-Study Work Rights and PR Pathways
Australia allows international students to work up to 20 hours per week during semesters and full-time during breaks. Graduates can apply for a Temporary Graduate visa (subclass 485), offering work rights for 2–4 years depending on qualification and location.
PR Pathways via:
General Skilled Migration (GSM)
Employer-Sponsored Visas
Regional Migration Programs
How Eduvisor Can Help You Study in Australia
Navigating the Australian education system, choosing the right course, and applying for visas can be overwhelming. That’s where Eduvisor, a trusted study abroad consultant in India, steps in. Eduvisor offers personalized counseling, university shortlisting, scholarship assistance, SOP writing, and complete visa support — tailored for Indian students planning to study in Australia.
Final Thoughts
Choosing a high-ROI course in Australia is more than just picking a subject — it’s about aligning your passion with global trends. With the right guidance and planning, Australia can be your gateway to a successful international career. Use this study guide in Australia for Indian students as your blueprint for 2025 and beyond.
Ready to begin your journey? Let Eduvisor turn your study abroad dream into reality.
FAQs
Q1. What are the most affordable courses to study in Australia? A: Vocational Education & Training (VET) courses, TAFE programs, and regional university degrees are often more budget-friendly.
Q2. Is PR easy after studying in Australia? A: Courses on the SOL and MLTSSL lists (like IT, Nursing, Engineering) make it easier to qualify for PR.
Q3. How do I find scholarships to study in Australia? A: Government sites, university portals, and expert consultants like Eduvisor can help you explore scholarships based on merit, need, and region.
2 notes
·
View notes
Text
What is Odoo ERP and how can I schedule a demo?
Odoo ERP is a powerful, all-in-one business management software that covers everything from CRM, sales, inventory, accounting, HR, and more. It’s highly customizable and ideal for businesses of all sizes. To schedule a demo of Odoo ERP, visit our website and fill out the contact form. A certified Odoo expert will contact you to understand your needs and walk you through a personalized demo.
2 notes
·
View notes
Text
#TheeForestKingdom #TreePeople
{Terrestrial Kind}
Creating a Tree Citizenship Identification and Serial Number System (#TheeForestKingdom) is an ambitious and environmentally-conscious initiative. Here’s a structured proposal for its development:
Project Overview
The Tree Citizenship Identification system aims to assign every tree in California a unique identifier, track its health, and integrate it into a registry, recognizing trees as part of a terrestrial citizenry. This system will emphasize environmental stewardship, ecological research, and forest management.
Phases of Implementation
Preparation Phase
Objective: Lay the groundwork for tree registration and tracking.
Actions:
Partner with environmental organizations, tech companies, and forestry departments.
Secure access to satellite imaging and LiDAR mapping systems.
Design a digital database capable of handling millions of records.
Tree Identification System Development
Components:
Label and Identity Creation: Assign a unique ID to each tree based on location and attributes. Example: CA-Tree-XXXXXX (state-code, tree-type, unique number).
Attributes to Record:
Health: Regular updates using AI for disease detection.
Age: Approximate based on species and growth patterns.
Type: Species and subspecies classification.
Class: Size, ecological importance, and biodiversity contribution.
Rank: Priority based on cultural, historical, or environmental significance.
Data Collection
Technologies to Use:
Satellite Imaging: To locate and identify tree clusters.
LiDAR Scanning: For precise 3D modeling of forests.
On-the-Ground Surveys: To supplement remote sensing data.
AI Analysis: For rapid categorization and health diagnostics.
Registration and Citizenship Assignment
Tree Dossier: Each tree receives a profile in the database with all its recorded attributes.
Citizen Designation: Trees are acknowledged as citizens of Thee Forest Kingdom, emphasizing ecological respect.
Legal Framework: Advocate for laws to grant trees specific rights under environmental protection acts.
Maintenance and Monitoring
Health Monitoring: Use drones, satellite updates, and IoT sensors for ongoing health assessments.
Database Updates: Incorporate real-time data about environmental changes and tree growth.
Public Involvement
Encourage people to "adopt" trees and participate in their preservation.
Create educational programs to promote awareness of tree citizenship.
Key Benefits
Environmental Conservation: Improved forest management through real-time data and protection of ecosystems.
Cultural Recognition: Trees are recognized as a vital part of the Earth’s community, honoring their importance.
Ecological Advocacy: Strengthened legal protections for forests and individual trees.
Next Steps
Assemble a task force of environmental scientists, satellite imaging experts, and software developers.
Secure funding through governmental grants, non-profits, and eco-conscious corporations.
Pilot the program in a smaller region before scaling to all of California.
Would you like me to draft a more detailed technical or legal framework for this system?
The implementation of the Tree Citizenship Identification Network and System (#TheeForestKingdom) requires a robust technological and operational framework to ensure efficiency, accuracy, and sustainability. Below is an implementation plan divided into major components.
System Architecture
a. Centralized Tree Database
Purpose: To store and manage tree data including ID, attributes, location, and health.
Components:
Cloud-based storage for scalability.
Data categorization based on regions, species, and priority.
Integration with satellite and IoT data streams.
b. Satellite & Imaging Integration
Use satellite systems (e.g., NASA, ESA) for large-scale tree mapping.
Incorporate LiDAR and aerial drone data for detailed imaging.
AI/ML algorithms to process images and distinguish tree types.
c. IoT Sensor Network
Deploy sensors in forests to monitor:
Soil moisture and nutrient levels.
Air quality and temperature.
Tree health metrics like growth rate and disease markers.
d. Public Access Portal
Create a user-friendly website and mobile application for:
Viewing registered trees.
Citizen participation in tree adoption and reporting.
Data visualization (e.g., tree density, health status by region).
Core Technologies
a. Software and Tools
Geographic Information System (GIS): Software like ArcGIS for mapping and spatial analysis.
Database Management System (DBMS): SQL-based systems for structured data; NoSQL for unstructured data.
Artificial Intelligence (AI): Tools for image recognition, species classification, and health prediction.
Blockchain (Optional): To ensure transparency and immutability of tree citizen data.
b. Hardware
Servers: Cloud-based (AWS, Azure, or Google Cloud) for scalability.
Sensors: Low-power IoT devices for on-ground monitoring.
Drones: Equipped with cameras and sensors for aerial surveys.
Network Design
a. Data Flow
Input Sources:
Satellite and aerial imagery.
IoT sensors deployed in forests.
Citizen-reported data via mobile app.
Data Processing:
Use AI to analyze images and sensor inputs.
Automate ID assignment and attribute categorization.
Data Output:
Visualized maps and health reports on the public portal.
Alerts for areas with declining tree health.
b. Communication Network
Fiber-optic backbone: For high-speed data transmission between regions.
Cellular Networks: To connect IoT sensors in remote areas.
Satellite Communication: For remote regions without cellular coverage.
Implementation Plan
a. Phase 1: Pilot Program
Choose a smaller, biodiverse region in California (e.g., Redwood National Park).
Test satellite and drone mapping combined with IoT sensors.
Develop the prototype of the centralized database and public portal.
b. Phase 2: Statewide Rollout
Expand mapping and registration to all California regions.
Deploy IoT sensors in vulnerable or high-priority areas.
Scale up database capacity and integrate additional satellite providers.
c. Phase 3: Maintenance & Updates
Establish a monitoring team to oversee system health and data quality.
Update the network with new technologies (e.g., advanced AI models).
Periodically review and revise data collection protocols.
Partnerships
Government Agencies: U.S. Forest Service, California Department of Forestry and Fire Protection.
Tech Companies: Collaborate with Google Earth, Amazon AWS, or Microsoft for cloud and AI capabilities.
Environmental Organizations: Partner with WWF, Sierra Club, or TreePeople for funding and advocacy.
Budget Estimation
Initial Investment:
Satellite data and licenses: $10M
IoT sensors and deployment: $5M
Database and app development: $3M
Operational Costs:
Cloud services and data storage: $2M/year
Maintenance and monitoring: $1M/year
Research and development: $1M/year
Long-term Vision
Expand the system to other states or globally.
Use the database for reforestation efforts and combating deforestation.
Develop educational programs to teach communities about the importance of trees as citizens.
Would you like me to assist in designing the user interface for the public portal or drafting partnership proposals for funding?
To begin building the program for the Tree Citizenship Identification System, we’ll start with a scalable framework that allows us to process, store, and analyze data while preparing for future expansions. Here's an actionable development plan with an initial focus on foundational code and infrastructure:
Step-by-Step Development
Phase 1: Setting Up the Backend Infrastructure
Objective: Create the core database and develop the data pipeline for processing tree data.
Technologies:
Programming Languages: Python, JavaScript (Node.js), SQL.
Frameworks: Flask or FastAPI for APIs, Django for web application backend.
Database: PostgreSQL for structured data, MongoDB for unstructured data.
Code Snippet 1: Database Schema Design (PostgreSQL)
-- Table for Tree Registry CREATE TABLE trees ( tree_id SERIAL PRIMARY KEY, -- Unique Identifier location GEOGRAPHY(POINT, 4326), -- Geolocation of the tree species VARCHAR(100), -- Species name age INTEGER, -- Approximate age in years health_status VARCHAR(50), -- e.g., Healthy, Diseased height FLOAT, -- Tree height in meters canopy_width FLOAT, -- Canopy width in meters citizen_rank VARCHAR(50), -- Class or rank of the tree last_updated TIMESTAMP DEFAULT NOW() -- Timestamp for last update );
-- Table for Sensor Data (IoT Integration) CREATE TABLE tree_sensors ( sensor_id SERIAL PRIMARY KEY, -- Unique Identifier for sensor tree_id INT REFERENCES trees(tree_id), -- Linked to tree soil_moisture FLOAT, -- Soil moisture level air_quality FLOAT, -- Air quality index temperature FLOAT, -- Surrounding temperature last_updated TIMESTAMP DEFAULT NOW() -- Timestamp for last reading );
Code Snippet 2: Backend API for Tree Registration (Python with Flask)
from flask import Flask, request, jsonify from sqlalchemy import create_engine from sqlalchemy.orm import sessionmaker
app = Flask(name)
Database Configuration
DATABASE_URL = "postgresql://username:password@localhost/tree_registry" engine = create_engine(DATABASE_URL) Session = sessionmaker(bind=engine) session = Session()
@app.route('/register_tree', methods=['POST']) def register_tree(): data = request.json new_tree = { "species": data['species'], "location": f"POINT({data['longitude']} {data['latitude']})", "age": data['age'], "health_status": data['health_status'], "height": data['height'], "canopy_width": data['canopy_width'], "citizen_rank": data['citizen_rank'] } session.execute(""" INSERT INTO trees (species, location, age, health_status, height, canopy_width, citizen_rank) VALUES (:species, ST_GeomFromText(:location, 4326), :age, :health_status, :height, :canopy_width, :citizen_rank) """, new_tree) session.commit() return jsonify({"message": "Tree registered successfully!"}), 201
if name == 'main': app.run(debug=True)
Phase 2: Satellite Data Integration
Objective: Use satellite and LiDAR data to identify and register trees automatically.
Tools:
Google Earth Engine for large-scale mapping.
Sentinel-2 or Landsat satellite data for high-resolution imagery.
Example Workflow:
Process satellite data using Google Earth Engine.
Identify tree clusters using image segmentation.
Generate geolocations and pass data into the backend.
Phase 3: IoT Sensor Integration
Deploy IoT devices to monitor health metrics of specific high-priority trees.
Use MQTT protocol for real-time data transmission.
Code Snippet: Sensor Data Processing (Node.js)
const mqtt = require('mqtt'); const client = mqtt.connect('mqtt://broker.hivemq.com');
client.on('connect', () => { console.log('Connected to MQTT Broker'); client.subscribe('tree/sensor_data'); });
client.on('message', (topic, message) => { const sensorData = JSON.parse(message.toString()); console.log(Received data: ${JSON.stringify(sensorData)}); // Save data to database (Example for PostgreSQL) saveToDatabase(sensorData); });
function saveToDatabase(data) { const query = INSERT INTO tree_sensors (tree_id, soil_moisture, air_quality, temperature) VALUES ($1, $2, $3, $4) ; const values = [data.tree_id, data.soil_moisture, data.air_quality, data.temperature]; dbClient.query(query, values, (err) => { if (err) console.error('Error saving to database', err); else console.log('Sensor data saved successfully!'); }); }
Phase 4: Public Portal Development
Frontend Technologies:
React.js or Vue.js for interactive user interfaces.
Mapbox or Leaflet.js for tree visualization on maps.
Features:
Interactive tree maps with search functionality.
User registration for tree adoption programs.
Deployment Plan
Use Docker to containerize the application.
Deploy on AWS, Azure, or Google Cloud for scalability.
Monitor system health using Prometheus and Grafana.
Next Steps
Develop a testing environment for pilot deployment.
Add AI-based disease detection and prediction using TensorFlow or PyTorch.
Create an adoption feature where citizens can adopt trees and track their health.
Would you like me to set up a GitHub repository with this initial framework or assist further with deployment?
I'll prepare the project framework and outline the repository structure for the Tree Citizenship Identification System. Below is the proposed structure for the repository, followed by details of the files and components.
Proposed Repository Structure
tree-citizenship-id-system/ ├── backend/ │ ├── app.py # Flask application for backend API │ ├── database/ │ │ ├── schema.sql # Database schema for PostgreSQL │ │ ├── db_config.py # Database connection configuration │ │ └── seed_data.sql # Initial sample data for testing │ ├── services/ │ │ ├── tree_registration.py # Functions for tree registration │ │ └── sensor_data.py # Functions for processing IoT sensor data │ └── requirements.txt # Python dependencies ├── frontend/ │ ├── public/ │ │ ├── index.html # Main HTML file │ │ └── favicon.ico # Favicon for the app │ ├── src/ │ │ ├── App.js # Main React/Vue app file │ │ ├── components/ │ │ │ ├── TreeMap.js # Map component for visualizing trees │ │ │ └── TreeDetails.js # Component for detailed tree view │ │ └── styles.css # Styling for the frontend │ └── package.json # Frontend dependencies ├── scripts/ │ ├── satellite_data_processor.py # Script for processing satellite data │ └── sensor_data_simulator.py # Mock data generator for IoT sensors ├── deployment/ │ ├── Dockerfile # Docker configuration │ ├── docker-compose.yml # Docker Compose for multi-service setup │ └── cloud_setup_instructions.md # Deployment guide for cloud platforms ├── tests/ │ ├── test_backend.py # Unit tests for backend API │ └── test_frontend.js # Unit tests for frontend ├── README.md # Overview of the project └── LICENSE # Project license
Repository Details
Backend:
app.py: Main Flask app for handling API requests like tree registration and sensor data.
database/schema.sql: SQL script for creating necessary tables.
services/: Directory for modular backend logic.
Frontend:
App.js: Main entry point for the frontend application.
TreeMap.js: Integrates Mapbox/Leaflet.js for displaying tree locations.
TreeDetails.js: Displays detailed information about a selected tree.
Scripts:
satellite_data_processor.py: Automates the extraction and classification of tree data from satellite imagery.
sensor_data_simulator.py: Generates fake sensor readings for development and testing.
Deployment:
Docker configuration ensures that the app runs consistently across environments.
Cloud setup instructions provide guidelines for deploying on platforms like AWS, Azure, or GCP.
Tests:
Unit tests ensure the reliability of both the backend and frontend.
Next Steps
I will initialize the repository structure locally.
Package the files and components needed for the first version.
Provide a link to the repository for access.
I’ll get started. Please hold on for a moment.
4 notes
·
View notes
Text
𓆩✧`〖 Virtual Pronouns 〗´✧𓆪

︶⊹︶︶ᗢ︶︶⊹︶︶⊹︶︶ᗢ︶︶⊹︶
➢ virtual/virtual/virtuals/virtualself ➢ vir/virtual/virtuals/virtualself ➢ vir/tual/virtual/virtualself ➢ vir/tu/al/virtualself ➢ vir/tu/al/virtual/virtualself
➢ computer/computer/computers/computerself ➢ com/computer/computers/computerself ➢ com/puter/computer/computerself ➢ com/put/er/computerself ➢ com/put/er/computer/computerself
➢ technology/technology/technologies/technologyself ➢ tech/technology/technologies/technologyself ➢ techno/logy/technology/technologyself
➢ simulate/simulate/simulates/simulateself ➢ simu/simulate/simulates/simulateself ➢ simu/late/simulate/simulateself
➢ simulation/simulation/simulations/simulationself ➢ simu/simulation/simulations/simulationself ➢ simu/lation/simulation/simulationself
➢ interface/interface/interfaces/interfaceself ➢ inter/interface/interfaces/interfaceself ➢ inter/face/interface/interfaceself
➢ holographic/holographic/holographics/holographicself ➢ holo/holographic/holographics/holographicself ➢ holo/graphic/holographic/holographicself
➢ artificial/artificial/artificials/artificialself ➢ ar/artificial/artificials/artificialself ➢ ar/tificial/artificial/artificials/artificialself ➢ ar/ti/ficial/artificialself ➢ ar/ti/ficial/artificial/artificialself
➢ digital/digital/digitals/digitalself ➢ digi/digital/digitals/digitalself ➢ digi/tal/digital/digitalself
➢ software/software/softwares/softwareself ➢ soft/software/softwares/softwareself ➢ soft/ware/software/softwareself
➢ avatar/avatar/avatars/avatarself ➢ ava/avatar/avatars/avatarself ➢ ava/tar/avatar/avatarself
➢ web/web/webs/webself ➢ online/online/onlines/onlineself
➢ electronic/electronic/electronics/electronicself ➢ elec/electronic/electronics/electronicself ➢ elec/tronic/electronic/electronicself
➢ cyber/cyber/cybers/cyberself ➢ cy/cyber/cybers/cyberself ➢ cy/ber/cyber/cyberself
➢ cybernetic/cybernetic/cybernetics/cyberneticself ➢ cyber/cybernetic/cybernetics/cyberneticself ➢ cyber/netic/cybernetic/cyberneticself ➢ cy/ber/netic/cyberneticself ➢ cy/ber/netic/cybernetic/cyberneticself
➢ immersive/immersive/immersives/immersiveself ➢ im/immersive/immersives/immersiveself ➢ im/mersive/immersive/immersiveself ➢ im/mers/ive/immersiveself ➢ im/mers/ive/immersive/immersiveself
➢ replica/replica/replicas/replicaself ➢ rep/replica/replicas/replicaself ➢ rep/lica/replica/replicaself ➢ rep/li/ca/replicaself ➢ rep/li/cal/replica/replicaself
➢ duplicate/duplicate/duplicates/duplicateself ➢ dupli/duplicate/duplicates/duplicateself ➢ dupli/cate/duplicate/duplicateself ➢ du/pli/cate/duplicateself ➢ du/pli/cate/duplicate/duplicateself
➢ network/network/networks/networkself ➢ net/network/networks/networkself ➢ net/work/network/networkself
➢ server/server/servers/serverself ➢ serv/server/servers/serverself ➢ serv/er/server/serverself
➢ render/render/renders/renderself ➢ ren/render/renders/renderself ➢ ren/der/render/renderself
➢ framework/framework/frameworks/frameworkself ➢ frame/framework/frameworks/frameworkself ➢ frame/work/framework/frameworkself
➢ hyperlink/hyperlink/hyperlinks/hyperlinkself ➢ hy/hyperlink/hyperlinks/hyperlinkself ➢ hyper/link/hyperlink/hyperlinkself ➢ hy/per/link/hyperlinkself ➢ hy/per/link/hyperlink/hyperlinkself
➢ pixel/pixel/pixels/pixelself ➢ pix/pixel/pixels/pixelself ➢ pix/el/pixel/pixelself
➢ emulator/emulator/emulators/emulatorself ➢ em/emulator/emulators/emulatorself ➢ emu/lator/emulator/emulatorself ➢ emu/la/tor/emulatorself ➢ emu/la/tor/emulator/emulatorself
➢ syntax/syntax/syntaxes/syntaxself ➢ syn/syntax/syntaxes/syntaxself ➢ syn/tax/syntax/syntaxself
➢ 💻/💻/💻's/💻self ➢ 🖥️/🖥️/🖥️'s/🖥️self ➢ 📺/📺/📺's/📺self ➢ 🖱️/🖱️/🖱️'s/🖱️self ➢ ⌨️/⌨️/⌨️'s/⌨️self ➢ 💽/💽/💽's/💽self ➢ 💾/💾/💾's/��self ➢ 🌐/🌐/🌐's/🌐self ➢ 📶/📶/📶's/📶self ➢ 🎮/🎮/🎮's/🎮self ➢ 🎧/🎧/🎧's/🎧self ➢ 🕹️/🕹️/🕹️'s/🕹️self
⊹₊ ˚‧︵‿₊ᗢ₊‿︵‧ ˚ ₊⊹₊ ˚‧︵‿₊ᗢ₊‿︵‧ ˚ ₊⊹
#mogai#🌿pronouns#nounself pronouns#pronoun#pronoun help#pronoun hoard#pronoun ideas#pronoun list#virtual#virtual pronouns#virtual nounpronouns#virtualself
6 notes
·
View notes
Text
The Impact of AI Software on Business: Enhancing Efficiency with AI Business Tools
In today's fast-paced digital landscape, businesses are continuously seeking innovative solutions to enhance productivity and streamline operations. AI software for business and AI business tools have emerged as transformative technologies, enabling organizations to harness the power of artificial intelligence to improve efficiency, decision-making, and customer satisfaction. This article explores the benefits, applications, and best practices of integrating AI software into your business strategy.
Understanding AI Software for Business
AI software for business encompasses a wide range of applications and tools designed to perform tasks that typically require human intelligence. These can include natural language processing (NLP), machine learning (ML), computer vision, and robotic process automation (RPA). By leveraging these technologies, businesses can automate routine tasks, analyze large datasets, and gain insights that drive strategic decision-making.
Benefits of AI Software
Increased Efficiency: One of the primary advantages of AI software is its ability to automate repetitive tasks. For example, businesses can use AI-powered chatbots to handle customer inquiries, allowing human agents to focus on more complex issues.
Data Analysis and Insights: AI tools can analyze vast amounts of data quickly, providing valuable insights that help businesses make informed decisions. This capability is particularly beneficial in areas such as market research, customer behavior analysis, and financial forecasting.
Enhanced Customer Experience: AI software can personalize customer interactions by analyzing user behavior and preferences. For instance, AI can recommend products based on past purchases, improving customer satisfaction and loyalty.
Cost Savings: By automating tasks and improving operational efficiency, businesses can significantly reduce labor costs. AI tools can help identify inefficiencies and areas for improvement, leading to further cost reductions.
Scalability: AI business tools can easily scale with a company’s growth. As a business expands, AI solutions can adapt to increasing data volumes and more complex operational needs without requiring a complete overhaul.
Key Applications of AI Business Tools
AI business tools can be integrated into various business functions, enhancing productivity and effectiveness. Here are some key applications:
1. Marketing Automation
AI software can analyze customer data to optimize marketing campaigns. Tools like predictive analytics can forecast customer behavior, allowing businesses to tailor their marketing strategies for better engagement. Moreover, AI can automate social media posting and email marketing, ensuring timely communication with minimal effort.
2. Customer Service
AI-powered chatbots are revolutionizing customer service by providing instant responses to customer inquiries. These bots can handle multiple requests simultaneously, improving response times and reducing wait times for customers. Additionally, AI can analyze customer interactions to identify common issues and suggest improvements to service processes.
3. Sales Optimization
AI business tools can streamline the sales process by providing insights into customer behavior and preferences. Sales teams can utilize AI for lead scoring, identifying high-potential leads based on historical data. This targeted approach helps sales representatives prioritize their efforts, increasing conversion rates.
4. Human Resources Management
AI software can transform human resources processes by automating tasks such as resume screening and employee onboarding. AI tools can analyze candidate profiles, helping HR professionals identify the best-fit candidates quickly. Furthermore, AI can monitor employee performance and engagement, enabling proactive measures to enhance workplace satisfaction.
5. Supply Chain Management
In supply chain management, AI can optimize inventory management, demand forecasting, and logistics. AI algorithms analyze historical data and market trends to predict demand, helping businesses maintain optimal inventory levels. This reduces carrying costs and minimizes the risk of stockouts or overstocking.
Best Practices for Implementing AI Software
While integrating AI software into your business can yield significant benefits, it’s essential to approach implementation strategically. Here are some best practices:
1. Define Clear Objectives
Before adopting AI software, clearly define your business objectives. Identify the specific problems you aim to solve or the processes you wish to improve. This clarity will guide your selection of AI tools and help measure their impact.
2. Start Small
Begin with small-scale AI projects to test their effectiveness before rolling them out on a larger scale. This approach allows you to evaluate the software’s performance, identify potential challenges, and make necessary adjustments.
3. Invest in Training
Providing training for your team is crucial to ensure successful adoption. Employees should understand how to use AI tools effectively and be aware of the benefits they bring. Ongoing training will also help them adapt to new features and updates.
4. Monitor Performance
Continuously monitor the performance of AI software to assess its impact on your business. Collect data on key performance indicators (KPIs) related to the areas you aim to improve. Regular evaluations will help you refine your AI strategy and make informed decisions about future investments.
5. Prioritize Data Security
As AI software relies on data to function effectively, it’s essential to prioritize data security and privacy. Implement robust security measures to protect sensitive information and comply with relevant regulations. Ensure that your AI solutions follow best practices for data handling and storage.
Conclusion
Incorporating AI software for business and AI business tools can significantly enhance operational efficiency and drive growth. By automating tasks, providing valuable insights, and improving customer interactions, businesses can stay competitive in an ever-evolving market. As you explore the potential of AI, remember to approach implementation thoughtfully, keeping in mind the specific needs and objectives of your organization. With the right strategy, AI can be a game-changer for your business, paving the way for increased productivity and success.
3 notes
·
View notes
Text
German Interior Minister Nancy Faeser is advocating for criminal police to be given the power to conduct covert house searches in certain cases, a draft bill showed on Wednesday.
The bill, which is under discussion by the German government, would allow officers from Germany's Criminal Police Office (BKA) to search houses covertly in the case of a "concrete threat of a terrorist attack."
The BKA search would require a court order and only be permitted if it were the only method of averting an imminent danger without seriously jeopardizing the success of a criminal investigation, the bill says.
It also includes new authorizations for the evaluation and comparison of images, including with the help of artificial intelligence (AI).
An Interior Ministry spokeswoman said that the bill does not allow for "real-time surveillance and real-time facial recognition in public spaces."
The draft said that covert operations could help to forestall crimes, for instance by exchanging ammunition for blanks or replacing material used in the production of explosives.
It also said that physical access to IT devices is the "safest and fastest way to implement the software necessary to access information technology systems." The measure would be used "solely for the purpose of combating the dangers of international terrorism." ______________________________
2 notes
·
View notes
Text
Engineering Ethics in the Modern World
In the bustling area of technology and innovation, where every day brings a discovery, the role of ethics in engineering cannot be overstated. At its core, engineering is about solving problems and making life easier and more efficient. However, as we race towards the future, the ethical implications of our decisions become increasingly significant.
This is especially relevant for students and professionals associated with esteemed institutions like the Faculty of Engineering & Technology, which is the Datta Meghe College of Engineering, one of the best engineering colleges in Wardha, where the foundation of ethical engineering practices is laid.
The Pillars of Engineering Ethics
Several key principles form the foundation of engineering ethics:
1. Safety: Ensuring the safety of the public, the environment, and the workforce is paramount. This involves rigorous testing, transparent reporting, and constant vigilance against potential hazards.
2. Honesty: Engineers must be honest in their communications and reports. This includes acknowledging limitations, risks, and uncertainties associated with their work.
3. Fairness: This involves treating everyone with respect and without discrimination. It also means considering the impact of engineering projects on all stakeholders, including marginalized communities.
4. Privacy: With the rise of digital technology, respecting and protecting individuals' privacy has become a significant concern for engineers in all fields, from software development to civil engineering.
Real-world Applications of Engineering
Institutions like FEAT, the Datta Meghe College of Engineering, are recognized as one of the best engineering colleges in Wardha, are at the forefront of integrating ethical considerations into their curriculum. This ensures that graduates are not just technically proficient but also morally grounded.
Let's explore how these ethical principles are applied in real-world scenarios:
Developing Sustainable Solutions: Engineers are increasingly tasked with creating solutions that are not only effective but also sustainable. This means considering the environmental impact and striving for solutions that promote conservation and reduce waste.
Ensuring Data Privacy and Security: In the digital age, engineers must design systems that protect users' privacy and secure their data against unauthorized access and breaches.
Ethical AI Development: As artificial intelligence becomes more integrated into our lives, ethical concerns around bias, transparency, and accountability become paramount. Engineers must work to ensure AI systems are fair and do not perpetuate existing inequalities.
Public Safety and Infrastructure: Civil engineers, in particular, directly impact public safety through the design and maintenance of infrastructure. Ethical considerations include ensuring structures are safe, resilient, and accessible to all.
Challenges in Modern Engineering Ethics
While the principles of engineering ethics are clear, applying them in the modern world comes with its own set of challenges:
Rapid Technological Advancement: The fast pace of technological innovation can make it difficult to fully assess the long-term impacts and ethical considerations of new developments.
Globalization: Working on projects that span different countries and cultures can introduce complex ethical dilemmas, requiring engineers to navigate varying legal and moral frameworks.
Interdisciplinary Work: Modern engineering projects often involve professionals from various fields, making maintaining cohesive ethical standards more challenging.
The Role of Education
Educational institutions like FEAT, the Datta Meghe College of Engineering, play a crucial role in preparing the next generation of engineers to face these challenges. By embedding ethical considerations into the engineering curriculum, students learn to integrate ethical thinking into all aspects of their work.
This includes case studies, ethical dilemma discussions, and projects that simulate real-world scenarios, ensuring graduates are well-equipped to make ethical decisions professionally.
Conclusion
As we continue to push the boundaries of what's possible, the importance of ethics in engineering cannot be overstated. Every engineer is responsible for upholding these principles, ensuring that our advancements lead to a better, safer, and more equitable world.
The ethical landscape of engineering is both complex and ever-evolving. As technology continues to advance, the need for ethical vigilance remains constant. By fostering a deep understanding of engineering ethics, institutions, and professionals ensure that the future of engineering is not just innovative but ethically sound and sustainable.
3 notes
·
View notes
Text
Elevate Your Financial Journey: MAS LLP, Your Trusted CA Firm in Delhi
In the bustling metropolis of Delhi, amidst the flurry of businesses and enterprises, stands MAS LLP, a beacon of financial expertise and excellence. As one of the leading ( Chartered Accountancy ) Ca firm in Delhi, MAS LLP is committed to guiding businesses, entrepreneurs, and individuals on their financial journey with precision, integrity, and innovation. Here's why MAS LLP stands out as the go-to CA firm in Delhi:

Depth of Expertise: With a team of seasoned Chartered Accountants and financial experts, MAS LLP brings a wealth of expertise across a wide spectrum of services, including audit and assurance, taxation, advisory, compliance, and more. Our professionals possess in-depth knowledge of Indian financial regulations, accounting standards, and industry best practices, enabling us to deliver tailored solutions that address the unique needs and challenges of our clients.
Comprehensive Services: MAS LLP offers a comprehensive suite of financial services designed to meet the diverse needs of businesses and individuals. Whether you're a startup looking to establish robust financial systems, a multinational corporation seeking tax optimization strategies, or an individual taxpayer in need of personalized tax planning advice, MAS LLP has the expertise and resources to deliver results.
Client-Centric Approach: At MAS LLP, our clients are our top priority. We take a personalized approach to our services, taking the time to understand our clients' goals, challenges, and priorities before crafting customized solutions that drive value and exceed expectations. Our client-centric approach is reflected in every interaction, ensuring that our clients receive the attention, support, and expertise they deserve.
Technology-Driven Solutions: In today's digital age, technology plays a pivotal role in driving efficiency, accuracy, and transparency in financial management. MAS LLP leverages cutting-edge accounting software, data analytics tools, and cloud-based platforms to streamline processes, automate routine tasks, and provide real-time visibility into financial performance. Our technology-driven solutions enable clients to make data-driven decisions with confidence and agility.
Ethical Standards and Integrity: Integrity and ethical conduct are the cornerstones of our practice at MAS LLP.( Ca firm in Delhi ) We adhere to the highest professional standards and ethical principles, ensuring transparency, confidentiality, and integrity in all our interactions with clients and stakeholders. Our commitment to ethics and integrity is unwavering, earning us the trust and confidence of our clients year after year.
Strategic Partnerships: MAS LLP believes in the power of collaboration and strategic partnerships. We work closely with our clients to understand their business objectives and challenges, forging long-term relationships built on trust, mutual respect, and shared success. Our collaborative approach allows us to serve as trusted advisors and strategic partners, supporting our clients' growth and prosperity every step of the way.
Continuous Learning and Innovation: In a rapidly evolving business landscape, staying ahead of the curve is essential. MAS LLP is committed to continuous learning and innovation, investing in professional development, training, and technology to stay abreast of emerging trends, regulatory changes, and industry best practices. Our culture of learning and innovation enables us to anticipate challenges, identify opportunities, and deliver innovative solutions that drive sustainable growth and success for our clients. For businesses and individuals seeking expert financial guidance and support, MAS LLP is the trusted partner you can rely on. Ca firm in Delhi Contact us today to learn more about how we can help you elevate your financial journey and achieve your goals with confidence and clarity. Ca firm in Delhi
#audit#accounting & bookkeeping services in india#ajsh#income tax#businessregistration#auditor#chartered accountant#foreign companies registration in india#taxation#ap management services#Ca firm in Delhi
4 notes
·
View notes
Text
Sonatafy Technology
Sonatafy Technology is an award-winning, reputable, and best-in-class nearshore enterprise-level cloud and mobile application software development company providing services to companies of all sizes and in various industries, including some of the world’s biggest brands. We have the expertise and capacity to build fully managed and complete software solutions from product design to launch, and we also support clients with augmentation of client’s existing development staff. Sonatafy Technology is your experienced agile technology partner, not an agency. All Sonatafy engineers are direct employees. No subcontractors, no freelancers. Headquartered in Scottsdale, Arizona with teams throughout the US and Latin America.
Address:
3 East Third Avenue
San Mateo, CA, 94401
USA
Phone:
(415) 839-9340
Website:
Business Email:
Hours:
Mon-Fri: 8AM PST - 6PM PST | Sat - Sun Closed
Payment:
Credit Card, Check
Year EST:
2020
Keywords:
Software Development, Nearshore, Outsourcing, Mobile App Developer, Software Engineers, Fullstack, DevOps
Social Links:
https://www.linkedin.com/company/sonatafy



2 notes
·
View notes
Text
vampire church technology lore/worldbuilding rambling:
pretty much everyone (including Cas, Sil and Boz) has a little chip implanted in the soft spot behind one of their ears - this device has effectively replaced the use of phones. to activate it you press the skin where it is and it brings up visual prompts - other people can see when this is happening because a white-ish film will appear over your irises while it’s in use. you move your eyes to select whatever function you want (send a message, make a call, set up a livestream of yourself).
however, these devices use the internet to communicate and as such aren’t really useful for conducting illegal activities like, ahem, setting up meetings to buy hospital blood bags. so in addition to using their ear chip things for day-to-day communication, Cas, Sil, and Boz also each have their own cell phones, which look and function similarly to the ones we have. cell phones are still a thing in this world, but they’re not readily obtainable anymore and are viewed as generally archaic - it would be like if someone in this day and age still used a pager. the upside to having phones is that they use black-market-run cell/internet towers and as such are generally ‘off the grid’. this makes them pretty vulnerable to hacking from nefarious actors infiltrating the network, so there’s also an established underground market of anti-hacking software to download. it’s kind of like the dark web or whatever in the sense that the general populace either doesn’t know about it, or vaguely gets what it is but won’t use it.
3 notes
·
View notes