#Data Loss Prevention
Explore tagged Tumblr posts
Text
Data Loss Prevention (DLP) is a cybersecurity strategy that detects and prevents unauthorized access, sharing, or leakage of sensitive data. DLP solutions protect intellectual property, customer information, and confidential files across networks, endpoints, and cloud environments. Discover how DLP safeguards your business data effectively with advanced tools from Sangfor.
0 notes
Text
I'm having lunch at my mother's friend, the one who has stage 4 cancer. With my laptop. Because on top of everything I lost my mobile this morning while looking for things I needed to buy for her. I accidentally deleted all my data remotely via my Google account while in a panic. Then I called my number for the 4th time and finally the police responded. Some kind person had brought them my mobile. I should have just... waited. I lost all my data. 2 more years of my life completely deleted.
I'm... exhausted. Everything I held dear was on that phone. I knew I shouldn't have hoped. Somebody please tell me there's a way to recover my data. Please.
#text#personal#data recovery#Google apps#Google#Google account#phone issues#data loss prevention#data loss
0 notes
Text
Cloud Data Loss Prevention Features In Chrome Enterprise

Cloud Data Loss Prevention
Safeguarding confidential company information is now essential to the operation of the firm, not merely a recommended practice. Data breaches can have major effects in today’s society, ranging from operational problems and legal ramifications to monetary losses and harm to one’s reputation. To help businesses protect their sensitive data and stay compliant, Chrome Enterprise Premium, Google cloud cutting-edge secure corporate browser, now comes with an expanding range of Data Loss Prevention (DLP) features.
You now have even more precise control over the data in your business with some recent improvements made to Data Loss Prevention capabilities. From identifying possible risks and user behavior to managing data flow with strong security measures, looking into possible incidents with thorough reporting and analysis, and finally extending protection beyond desktops, this blog post will examine how these new capabilities support your organization’s entire Data Loss Prevention journey.
Discover and understand user behavior
The first step in avoiding data leaks is to understand how your users interact with your data. Chrome Enterprise offers strong features for observing user behavior and spotting possible dangers:
Chrome Security Insights
Through streamlined security monitoring, Chrome Security Insights enables Chrome Enterprise users to proactively detect possible attacks. With a few clicks, this functionality keeps an eye on 50 popular Data Loss Prevention detectors, security event logging, and important security setups.
With comprehensive reporting on users, domains, and sensitive data transfers, administrators may quickly identify and address security issues and obtain important insights into high-risk actions.
URL Filtering Audit Mode
The URL Filtering Audit Mode in Chrome Enterprise Premium is a useful tool for businesses looking to improve their online access guidelines. It gives administrators the ability to selectively turn on employee browser activity tracking without imposing limitations, giving them insight into user behavior and any security threats. IT and security professionals may effectively balance security and user productivity by using this data to drive their judgments about URL filtering policies.
Enforce DLP controls
It’s time to implement the appropriate controls to stop data leaks when you have a better understanding of your users’ behavior. A comprehensive suite of in-browser security features is provided by Chrome Enterprise.
Copy and paste protections
It’s critical to regulate user interaction with sensitive data. You may limit or prevent users from copying private information from websites or pasting it into unapproved apps or websites by using Chrome Enterprise Premium’s copy and paste safeguards. This fine-grained control lowers the risk of data breaches and aids in compliance with data protection laws by preventing data exfiltration and guaranteeing that private data remains inside specified bounds. Among the copy and paste safeguards are:
Stopping data from leaking into incognito mode: Are you worried that private information could be copied into incognito mode, where it might be able to evade security measures? You can now prevent or alert users when they try to copy data between incognito windows and regular browsing sessions with Chrome Enterprise Premium.
Managing data sharing between apps: Chrome Enterprise Premium now lets you block or alert users when they try to copy data from your web apps into external programs like Notepad, Microsoft Word, or other apps, which is useful for businesses trying to stop data leaks to other apps.
Data isolation across Chrome profiles: Users using several Chrome profiles or shared devices may increase the danger of data cross-contamination. You can now prevent or alert users when they try to transfer data between accounts using the new copy-paste controls in Chrome Enterprise Premium.
Protecting sensitive emails: Emails frequently include extremely private information that has to be protected. You may set up restrictions with Chrome Enterprise Premium, such preventing any copying from Gmail unless it’s being put back into Gmail.
Watermarking
Unauthorized data exchange is discouraged via watermarking. When critical corporate documents are read in Chrome Enterprise Premium, you may add visible watermarks that show details like the user’s email address, the date, or a personalized message. This makes it simpler to identify the source of any information that has been disclosed and deters data exfiltration.
Screenshot protections
Although screenshots are a handy tool to record information, there is a chance that they might leak data. You may stop users from capturing screenshots of critical material within the browser by using Chrome Enterprise Premium’s screenshot protection feature. This limits the possibility of illegal data gathering and gives your Data Loss Prevention approach an additional layer of security.
Together, these controls provide a thorough security plan that restricts the ways in which information may be stolen from your company.
Investigate potential data leaks
Being ready to look into possible security events is essential, even with the finest preventative measures in place. Chrome Enterprise offers the following resources to assist you in promptly recognizing and resolving threats:
Evidence Locker
The evidence locker offers a safe place to save documents and information that need to be looked at further by security personnel. For example, Chrome Enterprise Premium can prevent an employee from downloading a confidential financial report and keep a copy of the file in the evidence locker. IT and security teams receive a thorough report as a result, allowing them to do the necessary research and take corrective action. For additional details about Evidence Locker’s impending release, stay tuned.
Chrome Extension Telemetry in Google Security Operations
To provide you more insight into browser behavior, Chrome Enterprise Core connects with Google Security Operations, cloud-native security analytics platform. Detection and response teams could only examine static extension properties in the past. You may now establish dynamic rules that keep an eye on extension activity in your production environment, allowing you to proactively identify and address problems before they become threats. For instance, you can keep an eye on whether extensions are inadvertently accessing cookies or contacting distant servers. This improved visibility greatly lowers your organization’s susceptibility to malicious extensions by enabling your security team to identify and stop infrastructure threats and data theft in almost real-time.
Expand protection to other platforms
Chrome Enterprise is dedicated to expanding its desktop threat prevention features.
Mobile threat protections
Because more and more people are using mobile devices for work, it is crucial to secure the browser on these devices. Chrome Enterprise Core will now be able to safeguard Android devices that have download blocking. This capability will extend threat safeguards beyond desktops by enabling enterprises to implement policies that prohibit users from downloading dangerous files identified by Google Safe Browsing from the web onto their mobile devices. Additionally, organizations have the option to prohibit all Android downloads via controlled Chrome. Create an account with Chrome Enterprise Core now for free.
Chrome Enterprise Premium: Your partner in DLP
These features only scratch the surface of Chrome Enterprise’s extensive Data Loss Prevention capabilities. In order to assist businesses like yours prevent data loss, protect sensitive data at the crucial browser layer, and maintain compliance in the increasingly complicated digital world of today, it is constantly improving security capabilities.
For free, begin utilizing Chrome Enterprise Core now to acquire the fundamental security features.
What is data loss prevention?
Data Loss Prevention helps firms safeguard sensitive data from unauthorized access, transfer, or destruction. Protects on-premises, cloud, and endpoint data.
Organizations benefit from DLP
Comply with rules
HIPAA, GDPR, and CCPA compliance may be achieved via DLP.
Secure sensitive data
Organizations may safeguard credit card, identification, and medical data using DLP.
Detect data loss
Data loss prevention helps enterprises identify ransomware data loss.
DLP software detects and prevents data loss using several methods:
Network traffic analysis
DLP software may detect secret data leaks in network traffic.
Monitor endpoints
Laptops, servers, and mobile devices may be monitored using DLP software.
Stopping actions
DLP software can prevent moving business emails outside the company or transferring corporate files to consumer cloud storage.
Learning with machines
Data loss prevention software that employs machine learning and AI improves detection and blocking over time.
Read more on Govindhtech.com
#technews#technology#govindhtech#news#technologynews#technologytrends#googlecloud#dlp#machine learning#chrome enterprise#Chrome Enterprise Premium#data loss prevention
0 notes
Text

https://ukuzimanya.co.za/astutus-cyber-security-solutions/
Cyber Security is no longer a product that resolves attacks but a Solution that Investigates and Prevents an attack.
The world has evolved to a more hybrid working concept and with that Cyber Criminals have become more daring in the manner in which they attack and whom they attack.
1 note
·
View note
Text
5 Easy Ways To Improve Salesforce Data Backup Recovery Strategy
In today's data-driven world, businesses rely heavily on Customer Relationship Management (CRM) systems like Salesforce to manage their customer information, track sales, and drive growth. However, even the most robust platforms are not immune to data loss or system failures. That's why having a solid Salesforce data backup and recovery strategy is crucial for ensuring business continuity. In this blog post, we'll explore five easy ways to enhance your Salesforce data backup and recovery strategy.
Regularly Scheduled Backups:
The foundation of any effective data recovery strategy is regular data backups. Salesforce provides a built-in data export tool that allows you to export data in a structured format, such as CSV or Excel. Set up a routine schedule for these exports to ensure that your data is backed up consistently. Depending on your organization's needs, you may choose to perform daily, weekly, or monthly backups.
Automate Your Backups:
Manually exporting data can be time-consuming and prone to errors. To streamline the process, consider automating your Salesforce data backups using third-party backup solutions. These tools can schedule and execute backups automatically, ensuring that your data is consistently and reliably backed up without manual intervention.
Store Backups Securely:
Backing up your Salesforce data is only half the battle. Equally important is where you store those backups. Utilize secure and redundant storage solutions, such as cloud storage platforms like Amazon S3 or Google Cloud Storage. Implement encryption and access controls to safeguard your backups from unauthorized access.
Test Your Recovery Process:
Having backups is essential, but they're only as good as your ability to recover data from them. Regularly test your data recovery process to ensure that it works as expected. Document the steps, and make sure that your team is familiar with the recovery procedures. Conducting mock recovery drills can help identify and address any potential issues before they become critical.
Monitor and Alerting:
Proactive monitoring is key to identifying data backup and recovery issues early. Implement monitoring and alerting systems that notify you of any backup failures or anomalies. This way, you can take immediate action to rectify issues and minimize data loss in case of a failure.
Consider Salesforce Data Archiving:
As your Salesforce database grows, it can become challenging to manage large volumes of data efficiently. Salesforce offers data archiving solutions that allow you to move older or less frequently accessed data to a separate storage location. This can help reduce storage costs and improve system performance, making your data recovery strategy more manageable.
In conclusion, enhancing your Salesforce data backup and recovery strategy doesn't have to be complicated. By implementing these five easy steps, you can significantly improve your organization's ability to recover critical data in the event of data loss or system failures. Remember that data is the lifeblood of your business, and a robust backup and recovery strategy is your insurance policy against unforeseen disasters.
#Salesforce best practices#Data loss prevention#Backup automation#Data retention policies#Data encryption#Salesforce customization#Data recovery testing#Backup monitoring#Data recovery procedures#Data backup optimization#Salesforce data protection#Backup reliability#Data restoration#Backup storage solutions#Data backup documentation#Salesforce metadata backup#Data backup strategy evaluation#Data backup policies#Salesforce data backup best practices
0 notes
Text
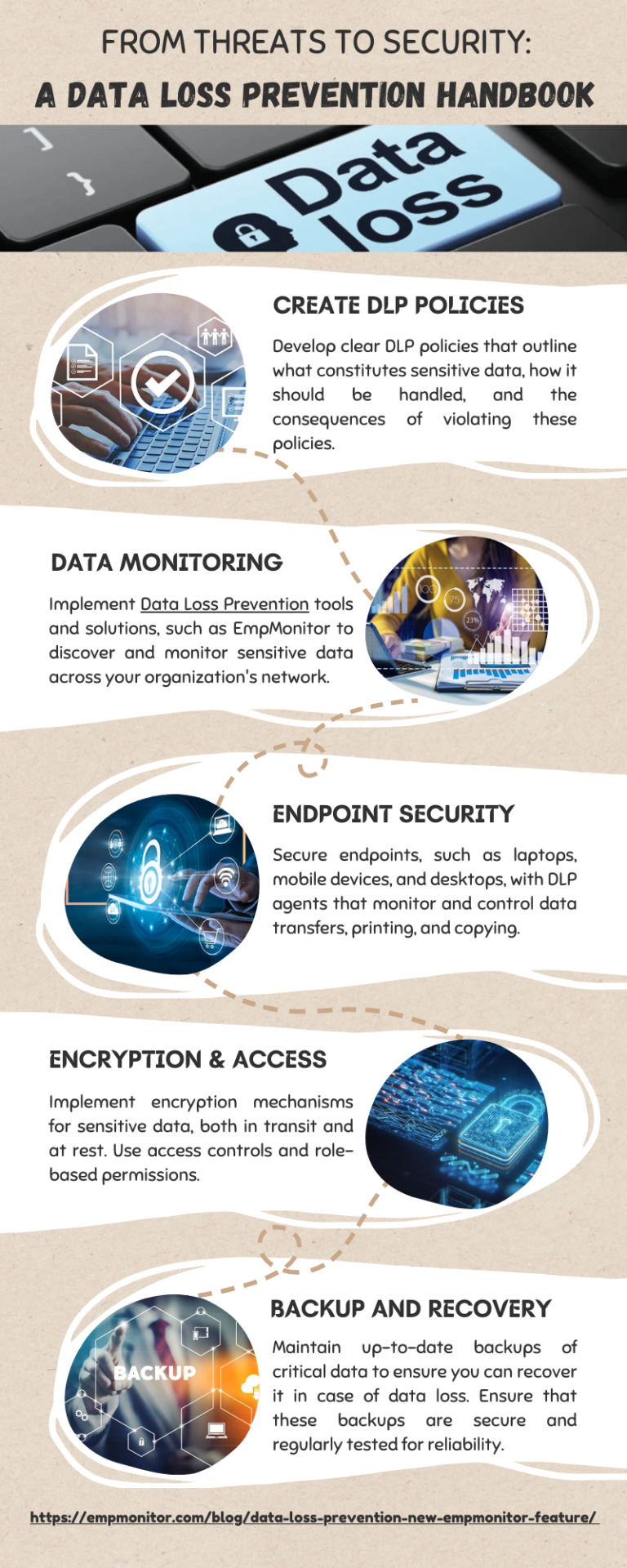
DLP is a set of strategies and technologies designed to protect sensitive information from being accessed. In this infographic, you will get to know about data loss prevention.
0 notes
Text
didn't save 12 hours worth of writing and editing, having a nervous breakdown and am ready to never write a single word again
#I'm literally the girl crying incoherent in German meme#and if anyone is going to come with well meant recovery file tips I'm going to end them#I've been through every recovery trick google has to offer#the audacity of those pages also to end their list of solutions with a “how to prevent data loss in the future” tips#writing
11 notes
·
View notes
Text
Stop Losing Money: How Revenue Management Systems Prevent Revenue Leakage
Revenue leakage is a silent profit killer that many businesses overlook, but it can cost companies up to 9% of their annual revenue. Whether you're in hospitality, travel, retail, or SaaS, even small pricing errors or missed invoices can lead to massive financial losses over time.
In a world where profit margins are thin and competition is fierce, preventing revenue leakage is not optional—it's essential.
This is where an AI-powered Revenue Management System (RMS) like ZettaPrice comes in. From dynamic pricing to automated invoicing, RMS software can seal the leaks and boost your bottom line. In this blog, we’ll explore how a robust revenue management solution can transform financial performance across industries.
✅ What Is Revenue Leakage?
Revenue leakage refers to the unnoticed loss of potential revenue due to inefficiencies, manual errors, or poor pricing strategies. Common causes include:
Incorrect or inconsistent pricing
Contract non-compliance
Billing inefficiencies or missed invoices
Mismanaged discounts and promotions
Poor data visibility and tracking
🔍 Revenue leakage affects 42% of companies—costing businesses an average of 9% of total sales annually. The worst part? It often goes undetected until the damage is done.
🧠 What Is a Revenue Management System (RMS)?
A Revenue Management System is a data-driven, AI-powered software solution that helps businesses:
Optimize pricing based on market demand and competition
Forecast demand and adjust inventory or services accordingly
Automate critical revenue processes (e.g., invoicing, contract compliance, and discount approvals)
Detect and plug revenue gaps before they escalate
Popular in hotels, airlines, retail, and subscription-based businesses, an RMS ensures you’re not leaving money on the table.
🔐 How to Prevent Revenue Leakage Using Revenue Management Software
Here’s how an advanced revenue optimization software like ZettaPrice RMS helps businesses detect, prevent, and eliminate revenue leakage:
1. AI-Powered Dynamic Pricing
Adjust prices in real time based on market trends, competitor pricing, and demand.
Prevent underpricing or over-discounting that erodes profit margins.
Maximize revenue during high-demand periods without sacrificing customer satisfaction.
2. Contract and Compliance Monitoring
Automatically track contract terms, service-level agreements, and payment cycles.
Flag discrepancies, missed invoices, or unapproved discounts.
Ensure full revenue recognition from every agreement.
3. Demand Forecasting and Inventory Optimization
Use predictive analytics to forecast customer demand with high accuracy.
Minimize stockouts and overstocking—both major causes of revenue loss.
Optimize resource allocation and reduce holding costs.
4. Identifying Revenue Gaps and Errors
Real-time dashboards highlight where revenue is leaking and why.
Actionable insights help you fix issues proactively instead of reacting later.
Improve financial reporting and transparency.
🚀 Benefits of Implementing a Revenue Management System
1. Increased Profitability
With smart pricing strategies, businesses can ensure they’re charging the right price at the right time. This boosts revenue without alienating customers.
📌 Example: Hotels using RMS increase RevPAR (Revenue per Available Room) by adjusting room prices during peak and off-peak seasons.
2. Improved Operational Efficiency
Manual revenue tracking and billing are prone to errors. Automation through RMS helps:
Save time and reduce human errors
Standardize pricing and billing processes
Ensure regulatory compliance
📌 Example: Airlines use RMS to automate fare updates, reducing fare leakage due to outdated pricing.
3. Enhanced Customer Experience
Personalize pricing and promotions using customer data.
Improve conversion rates and brand loyalty.
Deliver better value to different customer segments.
📌 Example: E-commerce retailers apply dynamic discounts based on browsing behavior and purchase history.
4. Competitive Advantage
Stay one step ahead by responding to market changes in real time. With RMS:
React instantly to competitor pricing
Maintain market share without sacrificing margin
Improve price transparency and customer trust
5. Smarter, Data-Driven Decisions
Access to real-time analytics empowers your teams to:
Identify new revenue opportunities
Predict churn in subscription models
Avoid pricing blind spots and inefficiencies
📌 Example: SaaS platforms use RMS data to prevent downgrades and maximize lifetime customer value.
🧩 Why Choose ZettaPrice RMS to Prevent Revenue Leakage?
ZettaPrice Revenue Management System is a cutting-edge solution designed to plug revenue gaps and increase profitability. It helps your business:
✅ Dynamically optimize pricing using AI & machine learning ✅ Eliminate revenue loss from underpricing or outdated rates ✅ Automate invoicing, billing, and discount tracking ✅ Monitor contracts and ensure compliance ✅ Uncover hidden revenue opportunities using data analytics
ZettaPrice RMS is ideal for industries like:
Hotels and Resorts
Online Travel Agencies (OTAs)
Retail Chains & E-commerce
SaaS and Subscription Services
With ZettaPrice, you don’t just stop revenue leakage—you unlock long-term financial stability and growth.
🏁 Conclusion: Seal the Leaks Before It’s Too Late
Revenue leakage is preventable—but only if you have the right tools. In today’s data-driven world, investing in a revenue management system is no longer a luxury but a necessity. With AI-powered software like ZettaPrice RMS, you can:
Prevent revenue losses
Improve operational efficiency
Gain a competitive advantage
Maximize profitability
Don’t wait until your profits vanish through cracks you can’t see.
👉 Start your journey to leak-free revenue with ZettaPrice RMS today!
#Revenue leakage#Revenue management system (RMS)#Dynamic pricing software#Prevent revenue loss#AI pricing tool#Hotel revenue management#SaaS pricing optimization#E-commerce revenue software#Data-driven pricing strategies#Automate invoicing and billing#Contract compliance tracking#Retail pricing automation#Optimize demand forecasting#Revenue analytics software#ZettaPrice RMS
0 notes
Text

Best Employee Monitoring Solution | Kriptone | Kntrol
#best employee time tracking software#Real-time monitoring software#it security services company#Data loss prevention solutions#Endpoint security#IT cyber security services#Data loss protection#Web Tracking
1 note
·
View note
Text

Lost Data? Get It Back Now with DRD 💾 Fast, Reliable Hard Drive Recovery 👉 Supporting all brands: Seagate, WD, Toshiba & more! 90% Success Rate Affordable Prices Free Diagnosis Located in the heart of Dubai 💡 Act Fast to Save Your Data! 📞 Call us: +971542669600🌐 Visit: www.drd.ae
0 notes
Text
Ahmedabad's Digital Guardians: Top Data Loss Prevention Companies

Ahmedabad, a hub for business and innovation, thrives on the secure flow of information. But with this digital growth comes a rising concern: data loss. Sensitive information can be accidentally leaked, stolen by malicious actors, or even lost due to technical glitches. This is where Data Loss Prevention companies step in, acting as your digital shield.
DLP solutions go beyond basic antivirus software. They proactively identify, classify, and protect sensitive data across your network, devices, and cloud environments. Here's a look at some of Ahmedabad's leading DLP providers:
Comprehensive Protection:
SecureU: A national leader in data security, SecureU offers a robust suite of DLP solutions tailored to businesses of all sizes. Their advanced features include data discovery and classification, endpoint encryption, and content filtering to prevent unauthorized data transfers.
Adit Microsys:
This company focuses on providing secure DLP solutions for both enterprises and mid-sized businesses. Their offerings include real-time data monitoring, customizable policies, and integration with existing IT infrastructure, ensuring comprehensive data protection.
0 notes
Text
Unlock the secrets to safeguarding your data! Dive into our latest blog on Secure Your Data: Tips For Implementing Data Loss Prevention (DLP) and keep your valuable information safe.
1 note
·
View note
Text
Proofpoint to Buy Tessian to Infuse Email Protection With AI
Data Loss Prevention (DLP) , Email Security & Protection , Email Threat Protection Acquiring Tessian Will Help Proofpoint Thwart Misdirected Emails, Misattached Files Michael Novinson (MichaelNovinson) • October 30, 2023 Proofpoint has agreed to purchase a cloud email security provider founded by HSBC, RBS, Santander and UBS alumni to apply artificial intelligence to evolving threats. See…

View On WordPress
0 notes
Text
#Data Loss Prevention Market Size#Data Loss Prevention Market Scope#Data Loss Prevention Market Trend#Data Loss Prevention Market Growth
0 notes
Text
What is SharePoint Syntex? 6 SharePoint Syntex Use Cases
SharePoint Syntex offers a range of powerful features that enable organizations to automate content processing, enhance information management, and improve productivity within SharePoint. Let's explore some of the key features of SharePoint Syntex:
Content Understanding: SharePoint Syntex utilizes AI-powered models to understand and extract valuable information from unstructured content. It can analyze documents, images, and audio files to identify entities, key phrases, and relationships. This feature enables organizations to gain insights from their content and make informed decisions based on the extracted knowledge.
Document Understanding Models: SharePoint Syntex provides pre-built and trainable document understanding models. These models can be customized to match the specific needs and terminology of an organization. They can automatically classify documents, extract specific information, and apply metadata tags based on the content. The ability to train models empowers organizations to tailor SharePoint Syntex to their unique business requirements.
Form Processing:SharePoint Syntex simplifies the extraction of data from forms, whether they are physical or digital. It can automatically capture data fields, validate inputs, and store the extracted information in SharePoint lists or other systems. This feature reduces manual data entry, minimises errors, and accelerates data processing workflows.
Integration with Power Automate:SharePoint Syntex seamlessly integrates with Power Automate (formerly Microsoft Flow). This integration enables the creation of powerful workflows and automation scenarios. For example, when a document is classified or a form is processed, SharePoint Syntex can trigger actions such as sending notifications, updating databases, or initiating approval processes, streamlining business operations.
Managed Metadata and Taxonomy:SharePoint Syntex enhances information management by leveraging managed metadata and taxonomy capabilities. It can automatically apply metadata tags to documents based on their content, ensuring consistency and improving searchability. This feature enables organisations to establish a structured and organised information architecture, facilitating efficient content management and discovery.
Information Extraction and Classification:SharePoint Syntex can extract information from structured and unstructured documents. It can identify key entities, extract data fields, and classify documents based on their content. This feature streamlines document processing, reduces manual effort, and enables faster search and retrieval of information.
Data Loss Prevention (DLP) and Compliance:SharePoint Syntex supports data loss prevention and compliance efforts. It can automatically detect sensitive information, such as personally identifiable information (PII) or financial data, within documents. SharePoint Syntex can enforce information governance policies by applying retention labels, ensuring compliance with regulations, and protecting sensitive data.
Search and Discovery:SharePoint Syntex improves search and discovery within SharePoint. By automatically applying metadata tags and extracting valuable information, it enhances search results and enables users to find relevant content more efficiently. This feature improves the overall user experience and productivity within SharePoint environments.
Customization and Extensibility: SharePoint Syntex provides customization options to tailor the solution to specific organizational needs. It offers a flexible framework that allows organizations to build their own AI models, train them using their data, and integrate them into SharePoint Syntex. This customization and extensibility enable organizations to address unique business requirements and achieve greater value from SharePoint Syntex.
Visit us: https://www.perfectiongeeks.com/custom-business-card-design-services
#Data Loss Prevention (DLP) and Compliance#ios app development#website development company#best iphone app development#ui and ux design service#perfectiongeeks#app development#blockchain application development#SharePoint Syntex
1 note
·
View note