#ESXi Host Configuration
Explore tagged Tumblr posts
Text
Top VMware Home Lab Configurations in 2023
Top VMware Home Lab Configurations in 2023 @vexpert #vmwarecommunities #100daysofhomelab #VMwareHomeLabSetup #VMwareWorkstationHomeLab #ESXiHostConfiguration #NestedVirtualizationVMware #vSANClusterConfiguration #BestVMwareHomeLabConfigurations2023
In 2023, many great options exist for delving into a home lab. Many get into running a home server to learn more skills for their day job, or they like to tinker and play around with technology as a hobby. For many, it is a mix of both. VMware vSphere is the market leader hypervisor in the enterprise. It arguably provides the most features and capabilities of any hypervisor on the market. This…

View On WordPress
#Best VMware Home Lab Configurations 2023.#ESXi Host Configuration#Nested Virtualization VMware#vCenter Server Deployment#VMUG Advantage for Home Labs#VMware Home Lab Setup#VMware vs Open Source Hypervisors#VMware vSAN Explanation#VMware Workstation Home Lab#vSAN Cluster Configuration
0 notes
Text
How Do You Secure Your Server from Malicious ESX Scripts?
Securing your server from malicious ESX scripts is essential in ensuring the safety and integrity of your data and services. ESX (Elastic Sky X) is a virtualization platform often used in server environments, enabling multiple virtual machines to run on a single host. While ESX provides great flexibility and efficiency, it can also be vulnerable to attacks, particularly through malicious scripts. These scripts, if not properly managed, can compromise the security of your server, lead to data breaches, or disrupt the smooth operation of your virtualized environment.
Here’s a detailed guide on how to secure your server from malicious esx scripts:

Keep Your System Updated
The first and most crucial step in securing your server is to keep your ESX host and all its components up to date. VMware frequently releases patches and updates to address security vulnerabilities, performance improvements, and bug fixes. Regularly check for updates and ensure that all patches are applied promptly. Neglecting these updates can leave your server open to exploitation from attackers using known vulnerabilities.
Use Secure Configurations
Another key to securing your ESX environment is ensuring that your server is configured securely. This includes configuring the ESXi firewall, disabling unnecessary services, and following VMware’s security best practices. By turning off unnecessary services, you limit the number of potential attack vectors. VMware provides a comprehensive security guide that outlines recommended configurations for hardening your ESX installation. Follow these guidelines to ensure your system is as secure as possible.
Enable ESX Host Firewall
The ESX firewall acts as a barrier between your server and any potential intrusions from malicious actors. Ensure that the firewall is configured properly to block unnecessary ports and only allow trusted traffic. Additionally, you can configure the firewall to log suspicious activity, providing valuable information in case of a security breach. Regularly review firewall logs to spot any unusual activity.
Control User Access and Privileges
One of the most common ways attackers gain access to ESX servers is through compromised user accounts or excessive privileges. Implement the principle of least privilege (POLP) by ensuring that users and administrators only have access to the resources they need. Limit access to critical system components and ensure that users cannot execute scripts unless absolutely necessary. Use role-based access controls (RBAC) to assign permissions based on job responsibilities. Moreover, regularly audit user accounts and remove any unused or inactive accounts to minimize potential vulnerabilities.
Monitor and Analyze Logs
Effective logging and monitoring are essential for identifying and responding to malicious activity quickly. Set up centralized logging for all ESX hosts and monitor these logs regularly for signs of abnormal behavior, such as unauthorized access attempts, failed login attempts, or unusual script executions. VMware vRealize Log Insight can help you manage and analyze logs efficiently, enabling you to spot malicious activity in real-time. Promptly investigate and address any suspicious log entries.
Scan for Malicious Scripts
Malicious ESX scripts are often introduced by attackers who exploit vulnerabilities in your environment. To prevent such threats, regularly scan your ESX server for suspicious scripts or files. Automated malware detection tools and anti-virus software can help detect and quarantine malicious files before they can cause damage. Ensure that any scripts running on your server are from trusted sources, and review them periodically to ensure they haven’t been tampered with.
Use Secure Boot and Trusted Execution
Secure boot is an essential security feature that prevents unauthorized firmware, bootloaders, and other malicious code from loading during the boot process. Ensure that secure boot is enabled on your ESX host, as it helps protect against rootkits and boot-time malware. Additionally, using trusted execution environments such as Intel TXT (Trusted Execution Technology) or AMD SEV (Secure Encrypted Virtualization) can further protect the integrity of your ESX server and its virtual machines from malicious scripts.
Use Virtual Machine Isolation
In environments where multiple virtual machines (VMs) are running on the same ESX host, it is essential to ensure proper isolation between VMs. This minimizes the risk of an attacker gaining access to other VMs via a compromised script. Configuring virtual machine isolation settings, such as enabling virtual machine lockdown mode and using a separate network for sensitive VMs, will significantly reduce the chance of a malicious script spreading across your environment.
Backup Regularly
Even with all the security measures in place, it’s always a good practice to have a reliable backup strategy in case of a breach. Regularly back up your ESX server and its virtual machines to secure, offsite storage. This ensures that if a malicious script causes system corruption or data loss, you can quickly restore your system to its previous state. Automate your backups and perform regular tests to ensure data integrity.
Conclusion
Securing your ESX server from malicious scripts requires a comprehensive approach that involves proactive monitoring, secure configurations, and regular updates. By following these best practices and maintaining a vigilant stance against potential threats, you can safeguard your virtualized environment from the damaging effects of malicious ESX scripts. Regular auditing, user privilege management, and the use of advanced security features like secure boot and trusted execution environments will further strengthen your defenses and help you maintain a secure, stable ESX server environment.
1 note
·
View note
Text
on Various hypervisors are available in the market with each system presenting unique features. As such, selecting an appropriate hypervisor for the desired purpose is a strenuous task. Of late two hypervisors, the Microsoft Hyper-V and VMware have outshined others in the market. However, the contemporary concern seeks to understand which software provides a better package. This scrip, hence, addresses this challenge by providing a comparative examination of the Hyper-V and VMware. An Overview In the earlier years, Microsoft has unveiled various host-staged virtualization systems; the company ventured into the hypervisor market in 2010 with the release of the Hyper-V. Similarly, VMware supplies numerous virtualization systems that are mainly host based. In the hypervisor market, the developer mainly offers two somewhat similar softwares, the ESX and ESXi (Finn & Lownds 23). The ESX is the company’s customary release and it entails the hypervisor and a developed management operation while ESXi is the firm’s latest release, and it is a hypervisor-only version. Integration structure Both the Hyper-V and ESXi do not demand an OS accompaniment since they connect directly on the hardware; however, their integration structure varies. The VMware has a direct driver structure where the application’s lines install on hardware, hence, linking the hardware and virtual gadgets servicing the server. As such, the structure incorporates the hardware drivers in the hypervisor. Similarly, the Hyper-V installs on the hardware but a structured application that propels the Window Server, directs all functions and hardware’s access. Considering this connection structure, the Hyper-V system is regarded to have an indirect driver structure (Finn & Lownds 134). Ease of management The simpler the structure of a hypervisor, the easer is its management. Management entails adopting and structuring hardware, installing virtual accompaniments, configuring the network among others. Software that incorporates and adjusts to these demands comfortably is easier to manage. The Hyper-V and the VMware incorporate and associateswith these structures in varying ways. The Hyper-V control entirely depends on a root partition plan done through a central Hyper-V manager. This plan is somewhat similar to other Microsoft management applications and demands little skills to launch. This tool, hence, controls basic virtual functions associated with the hardware. Importantly, an operator can control some hardware setups in the root partition using ordinary OS tools. Indeed, the tool is manageable remotely from a Vista system (Finn & Lownds 35). Notably, the Hyper-V manager system is capable of managing all virtual servers in the system concurrently and in an efficient manner. Tactically, using basic Microsoft devices provides the Hyper-V software with high degrees of flexibilities, hence, easing its management. The ESXi management is principally dependent on remote tools. The VI client and the Remote Command Line Interface (RCLI) are the two methods commonly used while configuring an ESXi host. The VI client is best suited for graphical configuration while remote line connection is ideal for line-based and scripted authentication. Read the full article
0 notes
Text
When it comes time to deploy a platform for new projects, set up a CRM server, or build a data center fit for a standard hypervisor, every IT manager or storage administrator is faced with the question of which type of storage to use: traditional SAN appliance or virtual SAN? In this article, we'll take a look at two SAN solutions, distinguish between them, and give you an answer on which one to choose for your projects. Сontents What is the Storage Area Network (SAN)? When utilizing a typical SAN device? What are the usual costs of SAN appliances? What is a vSAN appliance? Use cases for virtual SAN (vSAN) devices When should you utilize a vSAN appliance? Cost of a virtual SAN (vSAN) device What is the difference between a regular SAN and vSAN? Which SAN to choose? Conclusion What is the Storage Area Network (SAN)? In essence, SANs are high-performance iSCSI or Fiber Channel block-mode physical datastores that may be used to host hypervisors, databases, and applications. Traditional Storage Area Network devices, which are generally available in a 4-bay tower to 36-bay rackmount configurations, offer high-performance storage space for structured applications using the iSCSI and/or Fiber Channel (FC) protocols. Structured workloads include the following: Databases: MySQL, Oracle, NoSQL, PostgreSQL, etc. Applications: SAP HANA or other major CRM or EHR software. Large deployments of standard hypervisors such as VMware ESX/ESXi, Microsoft Hyper-V, Windows Server Standard (or Datacenter) 2016/2019, KVM, Citrix (formerly XenServer), or StoneFly Persepolis For a better understanding of the difference between block storage and file storage, you can read this. When utilizing a typical SAN device? On-premises SAN systems are ideal for large deployments of critical applications with a low tolerance for delay. In addition to addressing latency problems, local SAN appliances offer you more control in terms of administration, operation, and security of physical devices, which is required by many regulating companies. With commensurate performance, SAN systems may scale from hundreds of gigabytes to petabytes of storage capacity. If your workloads have the ability to rise to this scale, on-premises SAN hardware is the superior alternative in terms of return on investment (ROI). That isn't to say that 4-bay towers or 6-bay devices aren't appropriate for SMB environments. It all comes down to the company budget, latency requirements, and the project(s) at hand. NetApp SAN, Voyager, Dell PowerVault, StoneFly ISC, and other on-premises SAN hardware are examples. What are the usual costs of SAN appliances? The level of cost of an on-premises SAN device is determined by the provider you choose, the OS you install, and, of course, the hardware specs you choose: system RAM, processor, network connections, RAID controller, hard drives, and other components are all important. Most vendors, including Dell, HPE, and NetApp, offer pre-configured products with limited customization options. As a consequence, you can find the price range on their web pages or in their catalogs. Other vendors let you customize your SAN hardware by selecting the characteristics that best meet your requirements. Before shipping you the plug-and-play appliance, they produce, test, and configure it. As a result, you could be given the qualities you desire within your budget. What is a vSAN appliance? Virtual SANs (vSANs) are iSCSI volumes that have been virtualized and installed on common hypervisors. Find out more here. The developer business VMware is responsible for popularizing the term vSAN in general. But VMware vSAN is not the only option provided. NetApp vSAN, StarWind vSAN, StoneFly vSAN, StorMagic vSAN, and others are examples of vSAN devices that are available. Use cases for virtual SAN (vSAN) devices Standard SAN and vSAN devices are similar in terms of use cases. The configuration is the sole variation between them. In other words,
vSAN equipment may be utilized for structured workloads just like classic SAN appliances (examples listed above). When should you utilize a vSAN appliance? The deployment of vSAN technology is very adaptable. A vSAN appliance can be installed locally, in the cloud, or on a distant server. This offers up a variety of applications; nevertheless, the flexible deployment has a number of drawbacks, including administration, cost, availability, latency, and so on. vSAN, depending on the vendor, promises scalable performance and a high return on investment when placed on local hyper-converged infrastructure (HCI), according to the supplier chosen (VMware vSAN is usually costly). Latency is a factor when using public clouds or distant servers. If it's in a nearby location, latency may not be an issue - as many companies who run their workloads entirely in the cloud have discovered. Furthermore, several business clients have relocated to the cloud before returning to on-premises. The causes differ from one situation to the next. Just because vSAN isn't working for someone else doesn't imply it probably wouldn't work for you. However, just because something works for others does not guarantee that it will perform for you. So, once again, your projects, finance, and performance and latency needs will determine whether or not a vSAN appliance is the best option for you. Cost of a virtual SAN (vSAN) device The cost of vSAN appliances varies depending on the manufacturer, deployment, and assigned resources such as system memory, CPU, and storage capacity. If vSAN is installed in the cloud, the price of the cloud, the frequency with which vSAN is installed, and the frequency with which it is used are all factors to consider. The budget of the infrastructure and hypervisor influences the ROI if it is put on an on-premises HCI appliance. What is the difference between a regular SAN and vSAN? Aside from the obvious difference that one product is a physical object and the other is a virtual version, there are a few other significant differences: Conventional SAN: To assign storage capacity for structured workloads, outside network-attached storage (NAS), or data storage volumes are required. If migration is required, it is often complicated and error-prone. This is permanent machinery. You can't expand processor power or system ram, but you can add storage arrays to grow storage. With an internal SAN, you won't have to worry about outbound bandwidth costs, server security, or latency issues. Virtual SAN: Provides a storage pool with accessible storage resources for virtual machines to share (VMs). When necessary, migration is relatively simple. Volumes in vSAN are adaptable. You may quickly add extra CPU, memory modules, or storage to dedicated resources. In a totally server-less setup, vSAN may be implemented in public clouds. Which SAN to choose? There is no common solution to this issue. Some operations or requirements are better served by standard SAN, whereas others are better served by vSAN. So, how can you know which is right for you? The first step is to have a better grasp of your project, performance needs, and budget. Obtaining testing results might also be beneficial. Consulting with professionals is another approach to ensure you've made the appropriate selection. Request demonstrations to learn more about the capabilities of the product you're considering and the return on your investment. Conclusion The question isn't which is superior when it comes to vSAN vs SAN. It's more about your needs and which one is ideal for your projects. Both solutions offer benefits and drawbacks. Traditional SANs are best suited for large-scale deployments, whereas vSANs offer better flexibility and deployment options, making them suitable for a wide range of use cases, enterprises, and industries.
0 notes
Text
Beginners Guide - Using Nested ESXi Hosts for VCF 5.2.1 Home Lab
Attention: Using Nested ESXi (ESXi installed on ESXi) is not supported by VMware (or Broadcom). Use for your personal practices/learnings only. Not to be used for production environments. Part I – My Network Configuration Everyone’s network at home is different. See my configuration with my explanations hoping it will help you. On my physical ESXi Hosts, my VyOS router is running providing…

View On WordPress
0 notes
Text
Dell Unity Deploy D-UN-DY-23 Dumps Questions
If you're considering the D-UN-DY-23 Dell Unity Deploy 2023 Exam, you're in for a challenge that's both rigorous and rewarding. Having recently passed this exam, I want to share my experience and provide some tips that might help you on your journey. I found Certspots' Dell Unity Deploy D-UN-DY-23 dumps questions incredibly helpful. These dumps provide a realistic preview of the exam questions and scenarios you might encounter. Studying these Dell Unity Deploy D-UN-DY-23 Dumps Questions allowed me to familiarize myself with the exam format and question types, making it easier to tackle the actual test.
Why the Dell Unity Deploy 2023 Exam?
The D-UN-DY-23 exam is aimed at professionals involved in deploying Dell Unity systems, which are essential for contemporary data management and storage. It evaluates your knowledge and skills in areas such as installation, configuration, and management of these systems. Specifically, the Dell EMC Unity Deploy certification targets individuals looking to advance their careers in the Unity domain. The Dell EMC Unity Deploy 2023 (DCS-IE) exam confirms that candidates have the basic knowledge and demonstrated abilities required to manage Dell Unity storage systems in a production setting, aligning with business needs. It also covers configuration tasks that support ongoing management and basic integration topics.
Familiar with the D-UN-DY-23 Exam Topics
Dell Unity Platform Concepts, Features, and Architecture (10%)
● Describe the Dell Unity platform architecture, features, and functions
● Describe the Dell Unity VSA software defined storage solution
● Identify the Dell Unity XT hardware components
Dell Unity XT and UnityVSA Installation and Service (10%)
● Install and initialize a Dell Unity XT storage system
● Deploy and initialize a Dell UnityVSA system
● Perform key service tasks and identify related resources
● Describe the Dell Unity Platform service functions
Dell Unity XT and UnityVSA System Administration (5%)
● Identify and describe the user interfaces for monitoring and managing the Dell Unity family of storage systems
● Configure the Dell Unity XT support and basic system settings for system administration
Dell Unity XT and UnityVSA Storage Provisioning and Access (25%)
● Describe dynamic and traditional storage pools and how they are provisioned
● Describe dynamic pool expansion, considerations for mixing drive sizes and the rebuild process
● Provision block, file and VMware datastore storage
● Configure host access to block storage resources
● Configure NAS client access to SMB and NFS file storage resources
● Configure VMware ESXi hosts to access VMware datastore storage resources
Storage Efficiency, Scalability, and Performance Features (25%)
● Describe and configure FAST Cache
● Describe and configure File Level Retention
● Describe and configure Data Reduction
● Describe and configure FAST VP
Data Protection and Mobility (25%)
● Describe the Snapshots data protection feature and snapshot creation
● Descibe the Replication data protection feature
● Create synchronous and asynchronous replication sessions for storage resources
Preparation Tips for Dell Unity Deploy D-UN-DY-23 Exam
Study the Exam Objectives: Make sure you are well-versed in all the key topics listed in the exam objectives. The Dell Unity Deploy exam covers a range of topics including installation, configuration, and troubleshooting. Understanding these areas thoroughly is essential.
Hands-On Practice: Practical experience is invaluable. If possible, get hands-on practice with Dell Unity systems. This could be through a lab environment or real-world experience. The more you work with the systems, the better you'll understand the intricacies of deployment and management.
Review Official Documentation: Dell's official documentation and guides are a goldmine of information. They provide in-depth details about the features and functionalities of Dell Unity systems. Reviewing these documents can give you a clearer understanding of what to expect in the exam.
Join Study Groups: Engaging with a study group or forum can provide additional insights and answer any questions you might have. Sharing knowledge and discussing topics with peers can enhance your understanding and provide different perspectives.
Final Thoughts
Passing the D-UN-DY-23 Dell Unity Deploy 2023 Exam was a rewarding achievement. The preparation process, particularly using Certspots D-UN-DY-23 dumps questions, made a significant difference in my study routine. If you're preparing for this exam, I strongly recommend using these resources to help you succeed. With dedicated study and hands-on practice, you can confidently approach and pass the exam.
Good luck on your journey to becoming a certified Dell Unity Deploy professional!
0 notes
Text
Expert IT Services for All Your Operating System and Hosting Needs
Whether you need help installing and configuring Linux, CentOS, Windows, ESXI, or setting up RDP, Linux, CentOS VMs, ESXI, Hyper-V, VPS, or any other operating system or hosting platform, I'm here to assist you. With my extensive experience and expertise, I can handle even the most complex IT tasks seamlessly.
0 notes
Text
Backup ESXi Host configuration
Enable SSH
vim-cmd hostsvc/firmware/sync_config
vim-cmd hostsvc/firmware/backup_config
Copy and paste the download link and replace the "*" with your host IP address.
0 notes
Text
How to fix ESXi Host Certificate Status
How to fix ESXi Host Certificate Status
Error is seen in vCenter: If you check in vCenter > host > Configure > System > Certificate You can see that my certificate has expired so I cannot renew it. You can fix this easily, need to move any running guest OS to another host, or shut them down. Once you have done that, you will need to disconnect the host from the vcenter server, restart, then reconnect it. Fix Expired Certificates…
View On WordPress
2 notes
·
View notes
Text
VMware Storage: Top 15 Tips in 2023
VMware Storage: Top 15 Tips in 2023 @vexpert #homelab #ESXiHostSettings #PowerManagementOptimization #StorageLatencyReduction #ServerHardwareAdjustments #BIOSPowerConfigurations #DeactivateC-states #ESXiPerformanceEnhancement
The storage layer is vital for having a high-performance, stable, and reliable virtualized environment. Specifically looking at VMware vSphere, there are specific storage best practices to note when architecting your storage for performance and reliability. If you are running VMware vSphere in production or your home lab, let’s consider the VMware storage top 15 tips 2023 for running your virtual…

View On WordPress
#BIOS power configurations#BIOS setting guide#deactivate C-states#energy consumption considerations#ESXi host settings#ESXi performance enhancement#Maximum performance policy#power management optimization#server hardware adjustments#storage latency reduction
0 notes
Text
Fortigate Vm Trial License Reset


Fortigate Vm Trial License Reset Download
Fortigate Vm License Download
So we recently started looking into Terminal Services and RemoteFX to power some of our admin users and move them off to thin clients instead of full blown desktops. As a trial I begun setting up RDS on one of our Dev machines. After going through the motions of enabling the Remote Desktop Features and setting up RemoteFX on a Virtual Machine for testing, I found that I couldn’t login via RDP to that machine. Going back to the RDS host I found the Licensing popup that informed me that the 128 day trial license had expired. Since this was a test I didn’t want to go using keys to activate or setup a licensing server (purely a PoC for us in IT at this stage).
Fortigate Vm Trial License Reset Download
Fortigate Vm License Download
To reset the grace period there is a registry key that we need to delete. As always when editing the registry, take a backup of the key/s you’re modifying. Navigate to the following location
HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlTerminal ServerRCMGracePeriod
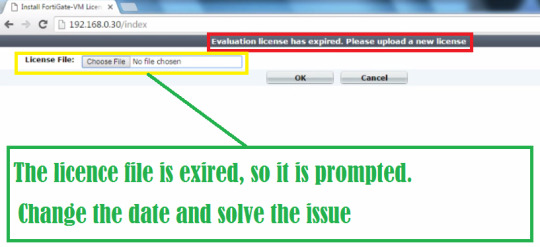
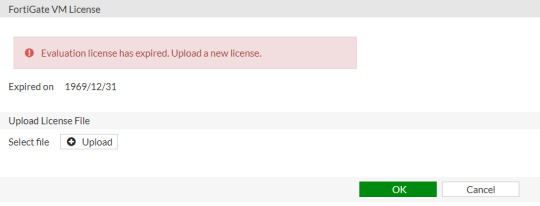
For testing, there was an integrated evaluation license for 15 days in each Fortigate VM. Since FortiOS 6.0.1 the evaluation license expires right from the first start of the virtual machine. In the GUI, there is the message 'Expired on 1970/01/01' with the possibility to upload a license file. Until FortiOS 6.0.0 it works as before. Well, you can reset the license and you can again use ESXi for next 60 days. And when the trial ends again, reset the license again.
Nov 02, 2015 Fortigate Firewall VM - Reset 14 days Trial Period without losing Configuration Fortigate Firewall VM - Reset 14 days Trial Period without losing Configuration Skip navigation. Fortigate vm license file crack. Igo primo 2 4 for android 480x800 download. FortiGate-VM FortiADC-VM.
Now there should be a binary key value (like in the screenshot), you first need to have full access permissions to the folder (or take ownership) and then simply delete that value and reboot the server. Once back up your RDS Licensing should be back at the start of a 128 Day grace period. I wouldn’t do this if you have already obtained licensing and should definitely not be used in a production environment.

1 note
·
View note
Text
New Post has been published on VMware Virtualization Blog
New Post has been published on https://www.tayfundeger.com/vsan-capacity-reserve.html
vSAN Capacity Reserve
Merhaba,
vSAN Capacity Reserve isimli bu yazımda sizlere, vSAN’ın yeni özelliklerinden biri olan vSAN Capacity Reserve hakkında detaylı bilgi vereceğim. Daha önce yazmış olduğum vSAN makalelerine aşağıdaki linkten ulaşabilirsiniz.
https://www.tayfundeger.com/kat/VSAN
Daha önceki makalelerimde sürekli belirtmiştimdir. vSAN kullanıyorsanız doluluk oranlarına dikkat etmeniz gerekiyor. Kapasitenin %25 veya %30 ‘unu boş bırakmanız gerekiyor. Bunun sebebi aslında hem rebuild işlemleri hemde policy üzerinde yapacağınız bir değişiklikte free alan’ın azalmasına sebep olmasından kaynaklanıyor. vSAN rebuild, repair gibi işlemlerde free alanı kullanır. Hatta bu konu ile ilgili yazmış olduğum yazılara aşağıdaki linkten ulaşabilirsiniz.
VSAN – Resyncing Objects
SAN ve Arıza Senaryoları
VSAN – Advanced Options
vSAN Capacity Reserve
vSAN cluster’ında bir ESXi host’un down duruma gelmesi durumunda rebuild işlemi başlayacağı için bu free kapasite kullanılır. VSAN 7 U1’den önceki sürümlerde, önerilen free space’in takip edilmesi için vCenter Server alarm’larından veya vROPS gibi ürünlerden faydalanmak zorunda kalıyoruz. vSAN 7 U1 den itibaren artık bu free space’i özel olarak takip etmemize gerek bulunmuyor. vSAN ile birlikte gelen Reserved Capacity özelliği sayesinde, kapasitenin kritik değerleri aşmasını önlenmesine olanak sağlıyor.
Yukarıda da belirttiğim gibi rebuild ve repair işlemleri için free space kullanılırken, Storage Policy üzerinde değiştireceğiniz bir object konfigurasyonundan kaynaklı free space’i de kullanabilirsiniz. Örneğin disk kopyasını değiştirmeniz durumunda free space’de değişim olur. Çünkü var olan virtual machine’in disklerinin farklı bir diske senkronize olurken free space’in bir miktarını kullanır. Free space’i etkileyen bu şekilde etkenler bulunuyor iken, reserved capacity tam burada işimize yarıyor.
vSAN Capacity Reserve aktif etmenin 2 farklı yolu bulunuyor. İsterseniz vSAN cluster’ını seçip Configuration > vSAN Services Enable Capacity Reserve butonuna basabilirsiniz. İsterseniz de Monitor > Capacity bölümüne giriş yaptığınızda aşağıdaki bir ekran ile karşılaşırsınız.
vSAN Capacity Reserve
Burada, You can enable operations and host rebuild reserve yanında yer alan Configure butonuna basıyoruz.
Enable Capacity Reserve bölümüne giriş yaptığımızda karşımıza 2 adet seçenek çıkıyor.
Operations reserve: vSAN’ın cluster’daki internal işlemlerini yürütmek için ihtiyaç duyduğu alanı görüntüler . Kullanılan alan işlem eşiğini aşarsa, vSAN düzgün çalışmayabilir. Örneğin storage policy üzerinde bir ayar değiştirceksiniz ve bu değiştirdiğiniz ayar sonucunda vSAN cluster’ı içerisinde bulunan virtual machine dosyalarının senkronizasyon edilmesi gerekecek. Bu gibi durumlarda Operations reserve seçeneğini aktif durumda olur ise altyapımızı riske atmadan sorunsuz bir şekilde işlemlerimize devam edebiliriz.
Host rebuild reserve: Host rebuild reserve ise, bir ESXi host’un kapasitesine göre ayarlanmıştır. Bir vSAN Cluster’ında bir ESXi host arızalanırsa veya down olursa diyelim, böyle bir durumda üzerindeki diskleri kullanamaz ve bundan dolayı vSAN cluster’ındaki depolamaya katkıda bulunamaz. Bu gibi durumlar oluştuğunda cluster’da repair/rebuild işlemleri başlanır. Bu konu ile ilgili yazmış olduğum makalelere yukarıdaki linkten ulaşabilirsiniz. Rebuild/Repair işlemlerinin yapılabilmesi için bir kapasiteye ihtiyaç bulunmaktadır. Eğer bu kapasite bulunmaz ise rebuild/repair işlemleri başarısız olablir. Host rebuild reserve sayesinde bu gibi kapasite ihtiyaçlarını kontrol etme imkanına artık sahibiz. Bu özellik default olarak devre dışıdır. Özelliği aktif edebilmek için Operations reserve’i ilk olarak aktif etmeniz gerekmektedir.
Capacity Reserve’i aktif etmezseniz, kapasitenin tükenmesi durumunda virtual machine’lerin oluşturulmasını veya virtual machine’lerin çalışması engellenir. Capacity Reserver’i aktif ederseniz, vSAN eşik sınırlarına ulaştıktan sonra bile virtual machine’den gelen IO talepleri karşılanmaya devam eder. Capacity Reserve etkinleştirdikten sonra, cluster’daki disk alanı, sağlık uyarılarını ve kapasite kullanımını izlemeli ve kapasite kullanımını eşik sınırlarının altında tutmak için uygun eylemleri gerçekleştirmelisiniz.
Bu özelliği kullanabilmeniz için bazı gereksinimleri karşılamanız gerekiyor. Capacity Reserve’i; Stretched Cluster, fault domain, ROBO Cluster ve vSAN Cluster’ı 4 node’dan az ise bu özelliği kullanamazsınız. Ayrıca vSAN Cluster’ında eşik değerinden yüksek bir kapasiteye sahipse zaten Capacity Reserve’i aktif edemezsiniz.
vSAN ‘ın yeni sürümleri ile birlikte sürekli yeni özellikler gelmeye devam ediyor. Capacity Reserve özelliğide vSAN ortamımı hem güvenli bir şekilde yönetmemize hemde operasyonel işlemler için gerekli tahmini boş kapasitenin dinamik olarak hesaplanmasını sağlıyor. Ayrıca cluster’ın kritik kapasite koşullarını aşmasını önlemeye yardımcı olduğu gibi güvenlik ve sağlık kontrollerinide kullanılmasına olanak tanıyor. vCenter Server üzerinden kritik kapasite koşullarını aşmasını önlemeye yardımcı olması oldukça güzel bir özellik. Çünkü yukarıda belirtmiş olduğum gibi ESXi host’un down olması durumunda gerekli olan rebuild işlemlerinde kullanılacak kapasiteyi hesaplaması önemli. Manuel olarak hesaplamak isteseniz farklı parametreleri toplamanız gerekir.
Bu özelliğin default olarak devre dışı geldiğini tekrar belirtmek isterim. Eğer free kapasitesiniz yeterli seviyede ise, yani %90 kullanım oranı bulunmuyor ise bu özellikleri aktif hale getirebilirsiniz.
Umarım faydalı olmuştur.
İyi çalışmalar.
1 note
·
View note
Text
An Introduction to Windows 2008 Hyper V

Well the closing model of this MS solution has been produced, people today have been downloading it considering that late 2008. Regrettably we are not chatting about the new avatar process for MS's prosperous console program the 360. No, we are speaking about Windows Server 2008 Hyper V. Late last year, I went to a technet server keynote in London town, MS CEO Steve Ballmer gave a speech regarding the merchandise of MS hyper v server 2008 to a group of seven hundred in addition IT market pro's. In case you have any kind of questions with regards to wherever and also the best way to employ esxi vs hyper-v, you can contact us on our internet site. We managed to get a preview of the characteristics of hyper v. Things this kind of as migration and memory distributions were covered. I need to say virtualization is a groundbreaking technology that has been all over, humorous plenty of for about forty several years! Now I know that this might not audio so thrilling to some of you, extra so considering that as far as virtualization of running techniques is anxious, VMware has very substantially dominated the market place for a selection of yrs, but I recommend that you delve further into the know-how and study extra about the several features and main improvements Hyper-V now presents. Virtualization it is an all-environmentally friendly remedy that enables you to help save not only on electrical power charges for powering and cooling your servers, but also on hardware, overhead and all round operational expenses by consolidating your servers and community storage. Another explanation why you may well want to search into virtualization is hardware underutilisation. Logs of IT overall performance reveal the average server utilisation of CPU is roughly 7 percent. But when you operate a few digital servers you seamlessly maximise useful resource outage without having neglecting overall performance. This is the circumstance with a ratio of 1:ten, in other phrases you run ten virtual servers on a solitary actual physical server. A different new and enjoyable product introduced by Microsoft is devoid of a doubt Server Main. This is a fairly bare operating method which is stripped of the .Web framework and hence can only operate certain roles that do not count on the framework this kind of as Domain Name System (DNS), Dynamic Host Configuration Protocol (DHCP), Community Load Balancing (NLB) and other standard roles. At the stop of the day it is nonetheless a really potent operating technique that can normally be maintained and configured by the command line interface applying MS PowerShell. I am assured IT administrators will always obtain this total electricity valuable for their day by day duties. If hyper v is anything you would contemplate practical for your self or your organization then it wise to research the a lot of hyper v education courses out there to display you the ropes.
1 note
·
View note
Text
Bryan Strauch is an Information Technology specialist in Morrisville, NC
Resume: Bryan Strauch
[email protected] 919.820.0552(cell)
Skills Summary
VMWare: vCenter/vSphere, ESXi, Site Recovery Manager (disaster recovery), Update Manager (patching), vRealize, vCenter Operations Manager, auto deploy, security hardening, install, configure, operate, monitor, optimize multiple enterprise virtualization environments
Compute: Cisco UCS and other major bladecenter brands - design, rack, configure, operate, upgrade, patch, secure multiple enterprise compute environments.
Storage: EMC, Dell, Hitachi, NetApp, and other major brands - connect, zone, configure, present, monitor, optimize, patch, secure, migrate multiple enterprise storage environments.
Windows/Linux: Windows Server 2003-2016, templates, install, configure, maintain, optimize, troubleshoot, security harden, monitor, all varieties of Windows Server related issues in large enterprise environments. RedHat Enterprise Linux and Ubuntu Operating Systems including heavy command line administration and scripting.
Networking: Layer 2/3 support (routing/switching), installation/maintenance of new network and SAN switches, including zoning SAN, VLAN, copper/fiber work, and other related tasks around core data center networking
Scripting/Programming: SQL, Powershell, PowerCLI, Perl, Bash/Korne shell scripting
Training/Documentation: Technical documentation, Visio diagramming, cut/punch sheets, implementation documentations, training documentations, and on site customer training of new deployments
Security: Alienvault, SIEM, penetration testing, reporting, auditing, mitigation, deployments
Disaster Recovery: Hot/warm/cold DR sites, SAN/NAS/vmware replication, recovery, testing
Other: Best practice health checks, future proofing, performance analysis/optimizations
Professional Work History
Senior Systems/Network Engineer; Security Engineer
September 2017 - Present
d-wise technologies
Morrisville, NC
Sole security engineer - designed, deployed, maintained, operated security SIEM and penetration testing, auditing, and mitigation reports, Alienvault, etc
responsibility for all the systems that comprise the organizations infrastructure and hosted environments
main point of contact for all high level technical requests for both corporate and hosted environments
Implement/maintain disaster recovery (DR) & business continuity plans
Management of network backbone including router, firewall, switch configuration, etc
Managing virtual environments (hosted servers, virtual machines and resources)
Internal and external storage management (cloud, iSCSI, NAS)
Create and support policies and procedures in line with best practices
Server/Network security management
Senior Storage and Virtualization Engineer; Datacenter Implementations Engineer; Data Analyst; Software Solutions Developer
October 2014 - September 2017
OSCEdge / Open SAN Consulting (Contractor)
US Army, US Navy, US Air Force installations across the United States (Multiple Locations)
Contract - Hurlburt Field, US Air Force:
Designed, racked, implemented, and configured new Cisco UCS blade center solution
Connected and zoned new NetApp storage solution to blades through old and new fabric switches
Implemented new network and SAN fabric switches
Network: Nexus C5672 switches
SAN Fabric: MDS9148S
Decommissioned old blade center environment, decommissioned old network and storage switches, decommissioned old SAN solution
Integrated new blades into VMWare environment and migrated entire virtual environment
Assessed and mitigated best practice concerns across entire environment
Upgraded entire environment (firmware and software versions)
Security hardened entire environment to Department of Defense STIG standards and security reporting
Created Visio diagrams and documentation for existing and new infrastructure pieces
Trained on site operational staff on new/existing equipment
Cable management and labeling of all new and existing solutions
Implemented VMWare auto deploy for rapid deployment of new VMWare hosts
Contract - NavAir, US Navy:
Upgraded and expanded an existing Cisco UCS environment
Cable management and labeling of all new and existing solutions
Created Visio diagrams and documentation for existing and new infrastructure pieces
Full health check of entire environment (blades, VMWare, storage, network)
Upgraded entire environment (firmware and software versions)
Assessed and mitigated best practice concerns across entire environment
Trained on site operational staff on new/existing equipment
Contract - Fort Bragg NEC, US Army:
Designed and implemented a virtualization solution for the US ARMY.
This technology refresh is designed to support the US ARMY's data center consolidation effort, by virtualizing and migrating hundreds of servers.
Designed, racked, implemented, and configured new Cisco UCS blade center solution
Implemented SAN fabric switches
SAN Fabric: Brocade Fabric Switches
Connected and zoned new EMC storage solution to blades
Specific technologies chosen for this solution include: VMware vSphere 5 for all server virtualization, Cisco UCS as the compute platform and EMC VNX for storage.
Decommissioned old SAN solution (HP)
Integrated new blades into VMWare environment and migrated entire environment
Physical to Virtual (P2V) conversions and migrations
Migration from legacy server hardware into virtual environment
Disaster Recovery solution implemented as a remote hot site.
VMware SRM and EMC Recoverpoint have been deployed to support this effort.
The enterprise backup solution is EMC Data Domain and Symantec NetBackup
Assessed and mitigated best practice concerns across entire environment
Upgraded entire environment (firmware and software versions)
Security hardened entire environment to Department of Defense STIG standards and security reporting
Created Visio diagrams and documentation for existing and new infrastructure pieces
Trained on site operational staff on new equipment
Cable management and labeling of all new solutions
Contract - 7th Signal Command, US Army:
Visited 71 different army bases collecting and analyzing compute, network, storage, metadata.
The data collected, analyzed, and reported will assist the US Army in determining the best solutions for data archiving and right sizing hardware for the primary and backup data centers.
Dynamically respond to business needs by developing and executing software solutions to solve mission reportable requirements on several business intelligence fronts
Design, architect, author, implement in house, patch, maintain, document, and support complex dynamic data analytics engine (T-SQL) to input, parse, and deliver reportable metrics from data collected as defined by mission requirements
From scratch in house BI engine development, 5000+ SQL lines (T-SQL)
Design, architect, author, implement to field, patch, maintain, document, and support large scale software tools for environmental data extraction to meet mission requirements
Large focus of data extraction tool creation in PowerShell (Windows, Active Directory) and PowerCLI (VMWare)
From scratch in house BI extraction tool development, 2000+ PowerShell/PowerCLI lines
Custom software development to extract data from other systems including storage systems (SANs), as required
Perl, awk, sed, and other languages/OSs, as required by operational environment
Amazon AWS Cloud (GovCloud), IBM SoftLayer Cloud, VMWare services, MS SQL engines
Full range of Microsoft Business Intelligence Tools used: SQL Server Analytics, Reporting, and Integration Services (SSAS, SSRS, SSIS)
Visual Studio operation, integration, and software design for functional reporting to SSRS frontend
Contract - US Army Reserves, US Army:
Operated and maintained Hitachi storage environment, to include:
Hitachi Universal Storage (HUS-VM enterprise)
Hitachi AMS 2xxx (modular)
Hitachi storage virtualization
Hitachi tuning manager, dynamic tiering manager, dynamic pool manager, storage navigator, storage navigator modular, command suite
EMC Data Domains
Storage and Virtualization Engineer, Engineering Team
February 2012 – October 2014
Network Enterprise Center, Fort Bragg, NC
NCI Information Systems, Inc. (Contractor)
Systems Engineer directly responsible for the design, engineering, maintenance, optimization, and automation of multiple VMWare virtual system infrastructures on Cisco/HP blades and EMC storage products.
Provide support, integration, operation, and maintenance of various system management products, services and capabilities on both the unclassified and classified network
Coordinate with major commands, vendors, and consultants for critical support required at installation level to include trouble tickets, conference calls, request for information, etc
Ensure compliance with Army Regulations, Policies and Best Business Practices (BBP) and industry standards / best practices
Technical documentation and Visio diagramming
Products Supported:
EMC VNX 7500, VNX 5500, and VNXe 3000 Series
EMC FAST VP technology in Unisphere
Cisco 51xx Blade Servers
Cisco 6120 Fabric Interconnects
EMC RecoverPoint
VMWare 5.x enterprise
VMWare Site Recovery Manager 5.x
VMWare Update Manager 5.x
VMWare vMA, vCops, and PowerCLI scripting/automation
HP Bladesystem c7000 Series
Windows Server 2003, 2008, 2012
Red Hat Enterprise and Ubuntu Server
Harnett County Schools, Lillington, NC
Sr. Network/Systems Administrator, August 2008 – June 2011
Systems Administrator, September 2005 – August 2008
Top tier technical contact for a 20,000 student, 2,500 staff, 12,000 device environment District / network / datacenter level design, implementation, and maintenance of physical and virtual servers, routers, switches, and network appliances
Administered around 50 physical and virtual servers, including Netware 5.x/6.x, Netware OES, Windows Server 2000, 2003, 2008, Ubuntu/Linux, SUSE, and Apple OSX 10.4-10.6
Installed, configured, maintained, and monitored around 175 HP Procurve switches/routers Maintained web and database/SQL servers (Apache, Tomcat, IIS and MSSQL, MySQL) Monitored all network resources (servers, switches, routers, key workstations) using various monitoring applications (Solarwinds, Nagios, Cacti) to ensure 100% availability/efficiency Administered workstation group policies and user accounts via directory services
Deployed and managed applications at the network/server level
Authored and implemented scripting (batch, Unix) to perform needed tasks
Monitored server and network logs for anomalies and corrected as needed
Daily proactive maintenance and reactive assignments based on educational needs and priorities Administered district level Firewall/IPS/VPN, packet shapers, spam filters, and antivirus systems Administered district email server and accounts
Consulted with heads of all major departments (finance, payroll, testing, HR, child nutrition, transportation, maintenance, and the rest of the central staff) to address emergent and upcoming needs within their departments and resolve any critical issues in a timely and smooth manner Ensure data integrity and security throughout servers, network, and desktops
Monitored and corrected all data backup procedures/equipment for district and school level data
Project based work through all phases from design/concept through maintenance
Consulted with outside contractors, consultants, and vendors to integrate and maintain various information technologies in an educational environment, including bid contracts
Designed and implemented an in-house cloud computing infrastructure utilizing a HP Lefthand SAN solution, VMWare’s ESXi, and the existing Dell server infrastructure to take full advantage of existing technologies and to stretch the budget as well as provide redundancies
End user desktop and peripherals support, training, and consultation
Supported Superintendents, Directors, all central office staff/departments, school administration offices (Principals and staff) and classroom teachers and supplementary staff
Addressed escalations from other technical staff on complex and/or critical issues
Utilized work order tracking and reporting systems to track issues and problem trends
Attend technical conferences, including NCET, to further my exposure to new technologies
Worked in a highly independent environment and prioritized district needs and workload daily Coordinated with other network admin, our director, and technical staff to ensure smooth operations, implement long term goals and projects, and address critical needs
Performed various other tasks as assigned by the Director of Media and Technology and
Superintendents
Products Supported
Microsoft XP/Vista/7 and Server 2000/2003/2008, OSX Server 10.x, Unix/Linux
Sonicwall NSA E8500 Firewall/Content filter/GatewayAV/VPN/UTM Packeteer 7500 packet shaping / traffic management / network prioritization
180 HP Procurve L2/L3 switches and HP Procurve Management Software
Netware 6.x, Netware OES, SUSE Linux, eDirectory, Zenworks 7, Zenworks 10/11
HP Lefthand SAN, VMWare Server / ESXi / VSphere datacenter virtualization
Solarwinds Engineer Toolset 9/10 for Proactive/Reactive network flow monitoring
Barracuda archiving/SPAM filter/backup appliance, Groupwise 7/8 email server
Education
Bachelor of Science, Computer Science
Minor: Mathematics
UNC School System, Fayetteville State University, May 2004
GPA: 3
High Level Topics (300+):
Data Communication and Computer Networks
Software Tools
Programming Languages
Theory of Computation
Compiler Design Theory
Artificial Intelligence
Computer Architecture and Parallel Processing I
Computer Architecture and Parallel Processing II
Principles of Operating Systems
Principles of Database Design
Computer Graphics I
Computer Graphics II
Social, Ethical, and Professional Issues in Computer Science
Certifications/Licenses:
VMWare VCP 5 (Datacenter)
Windows Server 2008/2012
Windows 7/8
Security+, CompTIA
ITILv3, EXIN
Certified Novell Administrator, Novell
Apple Certified Systems Administrator, Apple
Network+ and A+ Certified Professional, CompTIA
Emergency Medical Technician, NC (P514819)
Training:
Hitachi HUS VM
Hitachi HCP
IBM SoftLayer
VMWare VCP (datacenter)
VMWare VCAP (datacenter)
EMC VNX in VMWare
VMWare VDI (virtual desktops)
Amazon Web Services (AWS)
Emergency Medical Technician - Basic, 2019
EMT - Paramedic (pending)
1 note
·
View note
Text
ESXi configstorecli enhancement in vSphere 8.0 Update 1
The ESXi configstorecli was introduced back in vSphere 7.0 Update 1 and provides access to the ESXi ConfigStore which responsible for centrally managing all configurations for an ESXi host instead of relying on different methods including a variety of configuration files, I highly recommend reviewing this refresher article HERE if you have not heard of the […]http://dlvr.it/SlckMG
View On WordPress
0 notes
Text
VMware: Add user and group access to only a single ESXi host
Follow the following steps to add specific user and group access to a single ESXi host: Configure a single group, be it AD (remote) or Local. Add user to the above group. Login to the VCSA (vSphere Client). Select the ESXi host. Click on the Permissions tab. Click on the + icon. You will be in the Add Permission | host01.domain.abc popup. Select the domain. Select the group. Start…
View On WordPress
0 notes