#EndPointSecurity
Explore tagged Tumblr posts
Text
𝐓𝐨𝐩 10 𝐀𝐧𝐭𝐢𝐯𝐢𝐫𝐮𝐬 𝐒𝐨𝐟𝐭𝐰𝐚𝐫𝐞 𝐭𝐨 𝐂𝐨𝐧𝐬𝐢𝐝𝐞𝐫 𝐢𝐧 2025 𝐟𝐨𝐫 𝐔𝐥𝐭𝐢𝐦𝐚𝐭𝐞 𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲
Cybersecurity isn't just an IT checkbox anymore it's a core part of operating in a digital-first, AI-powered world.
At Fraoula, where we build AI tools for smarter automation and workflow management, we know how critical it is to secure every layer of your work environment. From startup teams to scaling businesses, protecting your data, systems, and devices is foundational.
In this post, we break down the top 10 antivirus solutions to consider in 2025not just based on detection rates, but on real-world usability, zero-day protection, endpoint security, and cross-platform coverage.
If you're re-evaluating your security stack, this is the place to start.
Read the full post: https://www.fraoula.co/post/top-10-antivirus-software-to-consider-in-2025-for-ultimate-cybersecurity
#Fraoula#Cybersecurity2025#EndpointSecurity#AntivirusReview#StartupSecurity#AIandSecurity#DataProtection#WorkplaceSecurity#SaaSTools#ITOps
0 notes
Text
instagram
🔐 One Partner. Total Protection. Complete Connectivity. 🌐
At Preemptive Technofield, we bring together best-in-class cybersecurity 🛡️ and advanced networking solutions 🚀 — all under one roof, built for today’s digital-first enterprises 💼.
From endpoint security 🖥️, DLP 📂, and data backup 💾 to network access control 🔗, secure switching 🔒, and cloud protection ☁️ — we’re powering India’s businesses with future-ready IT infrastructure that’s secure, scalable, and smart. ⚙️📈
#Cybersecurity#NetworkingSolutions#DigitalTransformation#DataProtection#CloudSecurity#EndpointSecurity#ITInfrastructure#SmartIT#ScalableSolutions#BusinessContinuity#FutureReady#TechForBusiness#PreemptiveTechnofield#Instagram
0 notes
Text

#CyberSecurity#InfoSec#DataProtection#NetworkSecurity#CyberThreats#CyberAware#RansomwareProtection#DigitalSecurity#OnlineSafety#AIinCybersecurity#CloudSecurity#CyberAttack#MFA (Multi-Factor Authentication)#ZeroTrust#SecurityFirst#ThreatDetection#SecureYourBusiness#ITSecurity#CyberResilience#EndpointSecurity
0 notes
Text
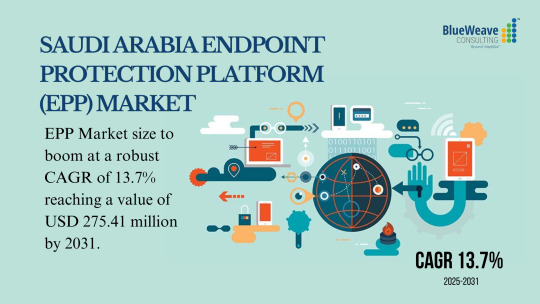
Saudi Arabia Endpoint Protection Platform (EPP) Market size by value at USD 112.11 million in 2024. During the forecast period between 2025 and 2031, BlueWeave expects Saudi Arabia Endpoint Protection Platform (EPP) Market size to boom at a robust CAGR of 13.7% reaching a value of USD 275.41 million by 2031. The Endpoint Protection Platform (EPP) Market in Saudi Arabia is propelled by the escalating frequency and complexity of cyber threats. Organizations are prioritizing the protection of diverse endpoints, including computers, laptops, and smartphones, through the implementation of advanced EPP solutions. Key features such as device control, data loss prevention, and patch management are critical components of these deployments. The adoption of cloud-based EPP solutions is further accelerating market expansion, offering scalability, flexibility, and cost-efficiency compared to traditional on-premises models. The documented surge in cyberattack incidents, exemplified by the Cybersecurity and Infrastructure Security Agency's (CISA) report of over 800 million attacks in 2021, reinforces the necessity for robust endpoint security measures and underscores the pivotal role of EPP in mitigating organizational risk.
Sample Request: https://www.blueweaveconsulting.com/report/saudi-arabia-endpoint-protection-platform-market/report-sample
#BlueWeave#Consulting#Marketforecast#Marketresearch#Cybersecurity#EndpointProtection#EndpointSecurity#ThreatIntelligence#MarketResearchReport#GrowthOpportunities#CybersecuritySolutions#EPPMarket
0 notes
Text

5 Key Facts About Endpoint Security You Need to Know
Did you know that 68% of businesses face end-to-end attacks every year? Find out how endpoint security protects your devices and helps reduce cyber risk by 75%.
Stay ahead of cyber threats—learn more here.
0 notes
Link
Managed antivirus works similarly to the traditional one. But with greater efficiency and control. It can effectively remove malware from your device by the following measures...
#virus#technology#cybersecurity#antivirus#virusprotection#managedantivirus#endpointsecurity#networkprotection#antivirusprotection
1 note
·
View note
Text
#CyberSecurity#FirewallProtection#Cryptography#DataSecurity#NetworkSecurity#Encryption#CyberDefense#ITSecurity#InfoSec#DataProtection#SecuritySolutions#SecureNetwork#CyberThreats#RansomwareProtection#EndPointSecurity
1 note
·
View note
Link
https://bit.ly/3TDVHwq - 🔒 Netskope Threat Labs has identified a sophisticated Azorult malware campaign leveraging advanced evasion techniques for data theft. This campaign uses HTML smuggling through Google Sites for payload delivery and employs various methods to evade detection, including reflective code loading and AMSI bypass, targeting sensitive information such as credentials and crypto wallet data. #CyberSecurity #DataTheft 🌐 The Azorult information stealer, first spotted in 2016, has been increasingly targeting the healthcare industry. This malware steals user credentials, browser info, and crypto wallet data, showcasing the growing threat to personal and sensitive data online. #HealthcareCybersecurity #Malware 🛡️ The campaign utilizes HTML smuggling with a unique twist by embedding the payload in a separate JSON file, enhancing its evasiveness. This technique allows the malware to bypass traditional security measures, demonstrating the sophistication of modern cyber threats. #CyberDefense #ThreatIntelligence 🔑 A notable aspect of this campaign is the use of a CAPTCHA as an additional evasion layer, making the malicious payload more difficult for security scanners to detect. This highlights the evolving tactics cybercriminals use to outmaneuver cybersecurity defenses. #CybersecurityAwareness #InfoSec 📁 The execution phase involves a fileless approach, where the Azorult malware operates directly in memory to minimize detection. Such stealthy tactics challenge existing security frameworks, underscoring the need for advanced threat detection and response strategies. #DigitalForensics #EndpointSecurity 💼 The campaign targets a wide array of sensitive data, including 137 crypto wallets, demonstrating the high stakes involved in protecting digital assets against sophisticated cyber threats. The use of legitimate-looking domains further complicates the challenge for users and defenders alike. #CryptoSecurity #DigitalAssetsProtection 🚨 Netskope Threat Labs' analysis underscores the importance of vigilance and advanced security measures in the face of evolving cyber threats. The use of comprehensive defense strategies is crucial to safeguard sensitive information against sophisticated malware campaigns like Azorult.
#CyberSecurity#DataTheft#HealthcareCybersecurity#Malware#CyberDefense#ThreatIntelligence#CybersecurityAwareness#InfoSec#DigitalForensics#EndpointSecurity#CryptoSecurity#DigitalAssetsProtection#CyberAware#ProtectYourData#sensitiveinformation#datatheft#healthcareindustry#labs#data#theft#html#sites#durablegoods#cybersecurity
1 note
·
View note
Text
#ITInfrastructure#CloudServices#Cybersecurity#CloudSecurity#DataProtection#BusinessContinuity#EndpointSecurity#DataEncryption#BackupandRecovery#CloudBackup#CyberThreats#CloudSolutions#InformationSecurity#NetworkSecurity#ITSecurity#CloudComputing#DigitalTransformation#ITManagement#DataPrivacy#CloudMigration#ITStrategy#ITConsulting#TechSolutions
0 notes
Text
Fortifying Cyber Resilience: Unveiling the Power of Network Detection and Response (NDR) Solutions
The landscape of cybersecurity has transformed significantly with the emergence of Network Detection and Response (NDR) technology, driven by the imperative to combat threats that traditional security measures often miss. This necessity has been underscored by the seismic shifts in work dynamics spurred by the COVID-19 pandemic, particularly the surge in remote work arrangements. With this surge comes a proliferation of non-secure devices tethering to organizational networks, rendering them susceptible to a gamut of cyber threats, from insidious malware to crippling ransomware assaults. In response, NDR solutions have emerged as indispensable allies, furnishing organizational Security Operations Center (SOC) teams with the arsenal needed for real-time threat management, detection, and mitigation.
At its core, an NDR solution harnesses a repertoire of non-signature-based techniques, prominently featuring machine learning (ML) and other sophisticated analytical methodologies, to ferret out nefarious and suspicious activities lurking within the enterprise network. These tools function as vigilant sentinels, continuously surveilling network traffic and sounding the alarm at the faintest whiff of aberrant behavior. Moreover, NDR solutions offer a twofold approach to threat response, seamlessly toggling between automated interventions and manual interventions tailored to the exigencies of the situation. These interventions encompass a spectrum of activities, ranging from proactive threat hunting to swift incident response, all underpinned by the relentless ingestion and correlation of copious volumes of network traffic and security events spanning disparate assets and network hops.
Central to the efficacy of an NDR solution is its provision of untrammeled visibility across the entirety of network infrastructure, encompassing every port and protocol in its purview. Through the judicious deployment of sensors strategically situated at key junctures—be it at the network gateway, within the organizational confines, in the ethereal realms of the cloud, or even ensconced within the bastions of email and web gateways—an Network Detection and Response solution casts its omniscient gaze over the labyrinthine labyrinth of network pathways. It is through this comprehensive surveillance apparatus that modern NDR solutions are endowed with the capacity to conduct real-time dissection of raw network packet traffic, affording invaluable context to discern the telltale signs of cyber malfeasance amidst the digital morass.
Moreover, the discerning eye of the NDR solution is honed by the sophisticated algorithms of machine learning and analytics, enabling it to distinguish the mundane from the malevolent with remarkable acumen. By scrutinizing network traffic through the prism of these analytical lenses, NDR solutions deftly identify anomalies that betray the presence of latent threats, while simultaneously furnishing an invaluable trove of metadata that facilitates retrospective detection and analysis, spanning back several months into the annals of network history.
Furthermore, the efficacy of NDR solutions extends to the seemingly impenetrable bastions of encrypted traffic, where it deftly profiles Transport Layer Security (TLS) encrypted data through meticulous analysis of metadata and certificates. Through this sleight of hand, it discerns between the footprints of human browsing and automated machine traffic, thereby unmasking hidden threats that might otherwise remain cloaked in the guise of benign activity.
In the realm of threat response, Network Detection and Response solutions serve as force multipliers, consolidating disparate alerts into cohesive narratives replete with contextual nuance and evidentiary weight. Armed with this holistic perspective, SOC teams are empowered to streamline their triage efforts, expediting the identification of actionable threats and automating response actions commensurate with the severity of the detected incursion. Whether deployed within the confines of an enterprise cloud server or ensconced within the tangible confines of an on-prem device, the efficacy of NDR solutions in fortifying the cyber ramparts of organizations against the ceaseless onslaught of digital adversaries is beyond dispute
#NDRSecurity#NDRSolutions#NetworkDetectionAndResponse#Cybersecurity#ThreatDetection#NetworkTraffic#CloudSecurity#EndpointSecurity#NDR#CyberResilience
0 notes
Text







#CybersecurityThreats#BusinessSecurity#CyberAttacks#DataBreach#Ransomware#Phishing#Malware#SocialEngineering#IoTSecurity#CloudSecurity#SupplyChainSecurity#AIinCybersecurity#ZeroDayExploits#CyberResilience#EndpointSecurity#CyberHygiene#InsiderThreats#CyberCrime#DataPrivacy#IdentityTheft#CyberInsurance#ThreatIntelligence#PatchManagement#BusinessContinuity#CyberSecurityAwareness#Encryption#MultiFactorAuthentication#CyberSecurityStrategy#Certera
0 notes
Text
An Endpoint Protection Platform (EPP) is a comprehensive security solution that is installed on endpoint devices to protect them from vulnerabilities. EPP solutions are often maintained in the cloud and leverage cloud data to facilitate sophisticated monitoring and remote repair. EPP solutions utilize a variety of security features.
0 notes
Text

#Skylark Information Technologies, in collaboration with #crowdstrike , empowers your business resilience by delivering enhanced security for your Endpoints, Clouds, and Identities. Visit our website to know more. #skylarkinfo #cloudsecurity #endpointsecurity
0 notes
Text
Looking for a Fortinet Partner in Pakistan? Here’s What You Need to Know
Cybersecurity is evolving fast—and if your business in Pakistan isn’t adapting, you could be vulnerable. That’s where Ambsan Technologies, a certified Fortinet partner, steps in.
Whether you're a startup needing secure VPNs or a large enterprise seeking advanced firewall protection, Fortinet solutions can help defend against today’s complex threats. But it’s not just about buying a firewall—it’s about end-to-end strategy, integration, and ongoing support.
🔐 What we cover in the full blog: • How Fortinet’s NGFWs go beyond basic filtering • Why endpoint and cloud security matter more than ever • What makes Ambsan Technologies different from others • Our people-first approach to cybersecurity consulting
📲 Don’t leave your network exposed. ➡️ Read the full blog here Visit us at Ambsan Technologies
#FortinetPakistan #CyberSecurity #AmbsanTechnologies #NGFW #EndpointSecurity #PakistanBusiness #FortinetPartner #CloudSecurity
0 notes
Text
🛡️ Cybersecurity Gets Real — Extended Detection & Response market to hit $7.5B by 2034 (from $1.85B 😮), with a spicy 15% CAGR.
Extended Detection and Response (XDR) is reshaping the cybersecurity landscape by delivering a unified approach to threat detection, investigation, and response across multiple security layers. Unlike traditional solutions that operate in silos, XDR integrates data from endpoints, networks, servers, email, and cloud workloads into one cohesive platform. This holistic visibility enables security teams to detect complex attacks faster and respond more effectively with automated workflows and advanced analytics.
To Request Sample Report : https://www.globalinsightservices.com/request-sample/?id=GIS24377 &utm_source=SnehaPatil&utm_medium=Article
XDR solutions leverage machine learning, threat intelligence, and behavior analytics to reduce alert fatigue and uncover stealthy threats that often go unnoticed. As cyberattacks grow in sophistication, organizations are turning to XDR to bridge security gaps and streamline incident response. The ability to correlate signals across environments in real-time enhances threat hunting, reduces dwell time, and strengthens overall security posture. Designed for scalability and integration, XDR supports both on-premises and hybrid cloud infrastructures, offering flexibility for modern enterprises. In today’s digital-first world, XDR is not just a trend — it’s becoming a necessity for proactive, intelligent, and coordinated cybersecurity defense.
#xdr #cybersecurity #extendeddetectionandresponse #threatdetection #endpointsecurity #cloudsecurity #networksecurity #securityoperations #siem #soar #securityanalytics #threathunting #malwareprotection #infosec #zerotrust #securityautomation #cyberresilience #threatintelligence #dataprotection #securityplatform #digitaldefense #incidentresponse #cyberthreats #attackprevention #realtimesecurity #machinelearningsecurity #behavioranalytics #cyberdefense #hybridcloudsecurity #securitystrategy #securityvisibility #securityintegration #advancedthreatprotection #securitystack #securitymanagement #itsecurity
Research Scope:
· Estimates and forecast the overall market size for the total market, across type, application, and region
· Detailed information and key takeaways on qualitative and quantitative trends, dynamics, business framework, competitive landscape, and company profiling
· Identify factors influencing market growth and challenges, opportunities, drivers, and restraints
· Identify factors that could limit company participation in identified international markets to help properly calibrate market share expectations and growth rates
· Trace and evaluate key development strategies like acquisitions, product launches, mergers, collaborations, business expansions, agreements, partnerships, and R&D activities
About Us:
Global Insight Services (GIS) is a leading multi-industry market research firm headquartered in Delaware, US. We are committed to providing our clients with highest quality data, analysis, and tools to meet all their market research needs. With GIS, you can be assured of the quality of the deliverables, robust & transparent research methodology, and superior service.
Contact Us:
Global Insight Services LLC 16192, Coastal Highway, Lewes DE 19958 E-mail: [email protected] Phone: +1–833–761–1700 Website: https://www.globalinsightservices.com/
0 notes
Text
AI in Cybersecurity: $154.6B by 2034 – The War on Hackers Just Got Real!
AI in Cybersecurity market is revolutionizing threat detection, prevention, and response with machine learning, predictive analytics, and automated security solutions. As cyber threats evolve, AI-driven cybersecurity provides real-time defense mechanisms, ensuring data protection, network security, and endpoint resilience.
To Request Sample Report : https://www.globalinsightservices.com/request-sample/?id=GIS33021 &utm_source=SnehaPatil&utm_medium=Article
🌍 Market Overview & Key Trends
✅ Endpoint security dominates, reflecting the rising need to protect devices from sophisticated cyber threats. ✅ Network security follows closely, emphasizing data protection during transmission. ✅ AI-powered tools like antivirus, firewalls, and intrusion detection systems are transforming cyber defense strategies. ✅ Machine learning & behavioral analytics enhance anomaly detection, making AI a game-changer in cybersecurity.
📈 Regional Insights
🌎 North America leads, driven by technological advancements & high cybersecurity awareness. 🇪🇺 Europe ranks second, fueled by strict data protection laws (GDPR) & AI security investments. 🇺🇸 The U.S. dominates, with early adoption of AI-driven security solutions. 🇬🇧 The UK is emerging as a key player, supported by government initiatives & cybersecurity innovations.
🏆 Market Segmentation & Growth
🔹 Type: Network Security, Endpoint Security, Application Security, Cloud Security 🔹 Technology: Machine Learning, NLP, Context-Aware Computing 🔹 Deployment: On-Premises, Cloud-Based, Hybrid 🔹 End Users: BFSI, IT & Telecom, Healthcare, Government, Retail, Manufacturing 🔹 Key Players: IBM, Cisco, Palo Alto Networks
🚀 Future Outlook
The market, valued at $12B in 2023, is expected to skyrocket to $35B by 2033! Network security leads with 45% market share, followed by endpoint security (30%) and application security (25%). AI’s integration with big data & machine learning is set to redefine cybersecurity strategies, offering proactive protection against cyber threats!
#aiincybersecurity #cybersecuritysolutions #machinelearningsecurity #threatdetection #endpointsecurity #networkprotection #firewalltechnology #intrusiondetection #cloudsecurity #predictiveanalytics #dataprotection #gdprcompliance #automatedsecurity #cyberawareness #digitaldefense #securityintelligence #aicyberdefense #riskmanagement #identityprotection #realtimemonitoring #ethicalhacking #cyberthreats #frauddetection #securityautomation #nextgensecurity #cyberresilience #anomalydetection #cyberforensics #blockchainsecurity #securecloud #itsecuritytrends #zerotrustarchitecture #infosecurity #cyberattackprevention #bigdatasecurity
Research Scope:
· Estimates and forecast the overall market size for the total market, across type, application, and region
· Detailed information and key takeaways on qualitative and quantitative trends, dynamics, business framework, competitive landscape, and company profiling
· Identify factors influencing market growth and challenges, opportunities, drivers, and restraints
· Identify factors that could limit company participation in identified international markets to help properly calibrate market share expectations and growth rates
· Trace and evaluate key development strategies like acquisitions, product launches, mergers, collaborations, business expansions, agreements, partnerships, and R&D activities
About Us:
Global Insight Services (GIS) is a leading multi-industry market research firm headquartered in Delaware, US. We are committed to providing our clients with highest quality data, analysis, and tools to meet all their market research needs. With GIS, you can be assured of the quality of the deliverables, robust & transparent research methodology, and superior service.
Contact Us:
Global Insight Services LLC 16192, Coastal Highway, Lewes DE 19958 E-mail: [email protected] Phone: +1–833–761–1700 Website: https://www.globalinsightservices.com/
0 notes