#Endpoint Protection Platform
Explore tagged Tumblr posts
Text
An Endpoint Protection Platform (EPP) is a comprehensive security solution that is installed on endpoint devices to protect them from vulnerabilities. EPP solutions are often maintained in the cloud and leverage cloud data to facilitate sophisticated monitoring and remote repair. EPP solutions utilize a variety of security features.
0 notes
Text
ManageEngine Rounds off Its Endpoint Protection Platform with the Addition of Next Generation Antivirus Capability
Proactive, AI-based protection with real-time monitoring for known and unknown threats Unified approach promotes interoperability between IT functions, simplifying threat detection, investigation and remediation Download a 30-day, free trial of Endpoint Central at https://mnge.it/NGAV Philippines — ManageEngine, the enterprise IT management division of Zoho Corporation, today announced the…

View On WordPress
1 note
·
View note
Text
How to Choose the Right Antivirus Software: A Comprehensive Guide
In today’s digital age, where our lives are intricately intertwined with technology, safeguarding our digital assets has become paramount. With the proliferation of cyber threats, antivirus software stands as a crucial line of defense against malware, viruses, ransomware, and other malicious entities lurking online. However, the abundance of antivirus options can be overwhelming, making it…

View On WordPress
#A#Advanced Behavioral Analysis Software#Advanced Threat Detection#Antivirus#Antivirus Software#Automated Security Incident Response#Cloud Security Solutions#Cloud-Based Endpoint Security Platform#Comprehensive Data Protection Suite#Continuous Vulnerability Assessment#Cyber Defense#Cybersecurity#Cybersecurity Awareness Training#Data Encryption Software#Data Protection#Defense#Encryption#Endpoint Protection Suite#Endpoint Security#Firewall#Firewall Protection#Identity Theft#Identity Theft Prevention#Integrated Firewall Protection Mechanism#Internet Security Software#Malware#Malware Detection#Malware Removal Tool#Mobile Device Management#Multi-Layered Malware Defense System
0 notes
Text
Endpoint Protection Platforms Market Size Worth USD 6.91 Billion in 2030
The global Endpoint Protection Platforms (EPP) market size reached USD 3.33 Billion in 2021 and is expected to register a revenue CAGR of 8.4% during the forecast period, according to latest analysis by Emergen Research. Rise in trend of Bring Your Own Device (BYOD) and surge in incidence of cyberattacks are crucial factors driving market revenue growth.
0 notes
Text
#Endpoint Protection Platforms Software Market Size#Endpoint Protection Platforms Software Market Scope#Endpoint Protection Platforms Software Market Trend#Endpoint Protection Platforms Software Market Growth
0 notes
Text
Steven Beschloss at America, America:
I know there are many among us who see today as an endpoint. The demise of democracy. The failure of our electorate to commit to self-governance. The willingness to let the richest among us grab power, with the foolish assumption that they would advance the well-being of working people rather than further enrich themselves. Let’s not doubt: The inauguration of Donald Trump is a cruel slap in the face of every lover of democracy, equality, justice and the rule of law. This event offers the terrible odor of billionaires and kleptocrats who see an opportunity to exploit government resources at the expense of taxpaying Americans just trying to get by. The convicted felon mouthing the oath to protect and defend the Constitution? It portends an ugly future, enough to convince some Americans that the democratic project is over, they have lost the battle and there’s nothing they can do now besides turn away. They are wrong. In fact, normalizing the idea that Trump’s return represents the end of democracy is a useful component of his authoritarian playbook. Feelings of resignation and despair are just what the authoritarian ruler wants his opponents to experience. Giving up—or believing that it is beyond our power to sustain America’s democratic values and principles— accelerates his success. This is anticipatory obedience, just as much as billionaires like Jeff Bezos and Mark Zuckerberg handing over millions and bowing down to the Malignant One. This is not a time for silence. This is not a time for resignation or despair. This is not a time to be cynical and insist that it’s all over. This is a time to gather your strength and stay engaged. This is a time to seek out guidance, to be nourished by the wisdom of others, to remember that you are not alone, to keep in mind that we are facing challenges that many Americans have faced throughout our history—and that we can get through this together. This is not a time to give up. This would be a disservice to all the good people who came before us and fought for a democratic future defined by justice and equality of opportunity.
That’s why I’m grateful that this is the day to celebrate the birthday of the Rev. Martin Luther King, Jr., rather than dwell on Trump’s inauguration. These days King is rightly seen as a heroic figure, a widely beloved American who lived a life dedicated to justice, equality and the overcoming of racial discrimination. But the truth is that in his own time he was a deeply controversial figure, a truth-teller who said what needed to be said even when it caused terrible blowback. That included his intensifying criticism of racism, income inequality and the Vietnam War. As I’ve written previously, as late as 1968, the year King was killed, nearly 75 percent of Americans rejected him. Following his assassination in April of that year, nearly a third of Americans felt he “brought it on himself.”
[...] I don’t mean to minimize the scale of danger facing our democracy, rule of law and the Constitution with the return of Trump to our White House. We can expect on this Inauguration Day virtually immediate attacks on immigrants and other vulnerable people, efforts to dismantle government agencies, intensified demands to confirm his reckless appointees, pardons of Jan. 6. insurrectionists and targeting of critics. They will release “shock and awe” executive orders to stoke fear. If we previously could anticipate that major media organizations would do their part to push back, we know now that many of these billionaire-led outlets and tech bro-driven platforms have abandoned their democratic responsibility to serve the public and tell the truth. We have yet to see how the courts will respond once Trump’s Justice Department begins carrying out his demands for retribution with lawsuits, firings and other acts of intimidation to silence opposition. That will put more pressure on independent media and everyday Americans to speak out and oppose the lies and vengeful actions that we see and hear. So rather than look at Jan. 20, 2025 as the end of the era of democracy, I urge you to see it as the beginning a new chapter in our collective effort to defend it. Today is an important day to resist despair and refuse to lose sight of the values and principles that have built our nation. It won’t be easy, but the struggle for a better world never is. As Martin Luther King warned from his Alabama jail cell in 1963, “freedom is never given freely by the oppressor; it must be demanded by the oppressed.” His words mirrored those of another great American about a century earlier. “Power concedes nothing without a demand,” Frederick Douglass said in 1857. “It never did and it never will.” We cannot be silent. We cannot give up. We must continue to make demands to create the America that we envision for ourselves and coming generations.
Today is also Martin Luther King, Jr. Day. Unlike the man who returned to office today, MLK Jr. was a man of principle.
#Martin Luther King Jr. Day#MLK Day#Martin Luther King Jr.#Donald Trump#Inauguration 2025#Trump Inauguration
34 notes
·
View notes
Text
Just three weeks after Dr Vinay Prasad assumed oversight of vaccines at the FDA, Moderna’s latest Covid-19 vaccine, mNEXSPIKE®, received full approval.
For those who had hoped the mRNA platform would be shelved, the decision landed like a gut punch.
Approved on 31 May 2025, the next-generation shot is intended for adults over 65, as well as individuals aged 12 to 64 with at least one risk factor for severe illness.
And it came under the watch of a man who had spent years demanding greater scientific rigour from the agency.
Prasad had been among the FDA’s most outspoken critics during the pandemic, repeatedly condemning its reliance on surrogate endpoints—such as antibody levels—rather than hard clinical outcomes like reduced hospitalisation or death.
And he didn’t just say it once. He drove the point home, over and over.
“Showing boosters improve neutralizing antibodies or other laboratory measures is not what we need,” he posted on X in July 2022. “We need randomized control trials powered for clinical endpoints showing boosters improve outcomes that people care about.”
15 notes
·
View notes
Text
A study of over 19 billion exposed passwords has revealed that only 6 percent of the leaked passwords were unique. The vast majority, 94 percent, were reused or duplicated, making them prime targets for cybercriminals.
Common keyboard patterns and easily guessed strings remain prevalent. The "123456" sequence still dominates, appearing in 338 million passwords, according to the Cybernews study.
Why It Matters
The scale of password breaches and the continued reliance on weak passwords have heightened concerns about "credential stuffing," a tactic in which attackers use automated tools to test stolen credentials across multiple platforms.
Even breach success rates between 0.2 percent and 2 percent can still yield thousands of compromised accounts, according to Cybernews.
The most common password length is eight to 10 characters, and a significant portion contains only lowercase letters and digits, making passwords vulnerable to brute-force attacks.
Compared to just 1 percent in 2022, 19 percent of passwords now mix uppercase, lowercase, numbers, and symbols.
What To Know
The dataset analyzed included 19,030,305,929 passwords sourced from 200 cybersecurity incidents. These came from leaked databases, stealer logs, and combolists.
Paul Walsh, CEO of MetaCert, has emphasized another growing risk vector: phishing attacks targeting phones. He has urged cybersecurity companies to tackle SMS phishing with the same intensity as email security to help mitigate password leaks and breaches.
In an article published on Monday, Walsh told Forbes that MetaCert's latest national SMS phishing test, carried out in March and including carriers such as AT&T, Verizon, T-Mobile and Boost Mobile, was concerning.
"Every phishing message was still delivered," Walsh said. "None were blocked, flagged, or rewritten."
Walsh has written an open letter to the cybersecurity industry asking why the SMS phishing problem wasn't solved long ago.
What Are the Most Common Passwords?
Predictable patterns continue to dominate password choices. "123456" alone appears in 338 million of the passwords in the Cybernews study, while "password" and "admin" were used over 100 million times combined.
Users also often rely on names, with "Ana" appearing in 178.8 million instances. Positive words like "love," "freedom," and pop culture references such as "Batman" are also prevalent. Profanity, surprisingly, is common as well; "ass" alone shows up in 165 million passwords.
Some of the most frequently used pop culture terms in passwords included "Mario" (9.6 million), "Joker" (3.1 million), "Batman" (3.9 million), and "Thor" (6.2 million).
Additionally, seasonal words, food items, and cities frequently feature in password choices, leaving accounts vulnerable to attackers who exploit such predictability. Over 10 million of the passwords featured "apple," 4.9 million "rice," and 3.6 million "orange," while 3.3 million opted for "pizza."
The most popular city for passwords was "Rome" (13 million), while "summer" (3.8 million) was the most popular season.
What People Are Saying
Neringa Macijauskaitė, information security researcher at Cybernews: "We're facing a widespread epidemic of weak password reuse. If you reuse passwords across multiple platforms, a breach in one system can compromise the security of other accounts."
MetaCert CEO Paul Walsh told Forbes: "Criminals have already moved in full force, and the industry is failing to respond."
"The cybersecurity industry has no shortage of experts in email security, endpoint protection, or network defense, but when it comes to SMS infrastructure and security, there is a distinct lack of deep expertise."
What Happens Next
Researchers have urged individuals and organizations to boost password security by using password managers, enforcing minimum length and complexity standards, and enabling multi-factor authentication. Organizations are advised to regularly audit access controls, monitor for credential leaks, and adopt real-time detection solutions.
10 notes
·
View notes
Text
What is Cybersecurity? Types, Uses, and Safety Tips
What is Cyber security?
Cyber security, also known as information security, is the practice of protecting computers, servers, networks, and data from cyberattacks. With the increasing reliance on technology in personal, professional, and business environments, the importance of cyber security has grown significantly. It helps protect sensitive data, ensures the integrity of systems, and prevents unauthorized access to confidential information.
For businesses in Jaipur, cyber security services play a crucial role in safeguarding digital assets. Whether you're an e-commerce platform, an IT company, or a local enterprise, implementing strong cyber security in Jaipur can help mitigate risks like hacking, phishing, and ransomware attacks.
Types of Cyber security
Cyber security is a vast domain that covers several specialized areas. Understanding these types can help individuals and organizations choose the right protection measures.
1. Network Security
Network security focuses on protecting the network infrastructure from unauthorized access, data breaches, and other threats. Tools like firewalls, virtual private networks (VPNs), and intrusion detection systems are commonly used. In Jaipur, many businesses invest in cyber security services in Jaipur to ensure their networks remain secure.
2. Information Security
This type of cyber security involves protecting data from unauthorized access, ensuring its confidentiality and integrity. Companies offering cyber security in Jaipur often emphasize securing sensitive customer and business information, adhering to global data protection standards.
3. Application Security
Application security addresses vulnerabilities in software and apps to prevent exploitation by cybercriminals. Regular updates, secure coding practices, and application testing are vital components.
4. Cloud Security
As more businesses move to cloud-based solutions, securing cloud environments has become essential. Cyber security providers in Jaipur specialize in offering services like data encryption and multi-factor authentication to ensure cloud data is safe.
5. Endpoint Security
Endpoint security protects devices such as laptops, desktops, and mobile phones from cyber threats. It is especially critical for remote work setups, where devices may be more vulnerable. Cyber security services in Jaipur provide solutions like antivirus software and mobile device management to secure endpoints.
6. IoT Security
With the rise of Internet of Things (IoT) devices, ensuring the security of connected devices has become crucial. Businesses in Jaipur use cyber security in Jaipur to secure smart devices like industrial sensors and home automation systems.
Uses of Cyber security
Cyber security is indispensable in various domains. From individual users to large organizations, its applications are widespread and critical.
1. Protection Against Cyber Threats
One of the primary uses of cyber security is to safeguard systems and data from threats like malware, ransomware, and phishing. Businesses in Jaipur often rely on cyber security Jaipur solutions to ensure they are prepared for evolving threats.
2. Ensuring Data Privacy
For industries like finance and healthcare, data privacy is non-negotiable. Cyber security measures help organizations comply with laws and protect sensitive customer information. Cyber security services in Jaipur ensure businesses meet data protection standards.
3. Business Continuity
Cyber security is essential for ensuring business continuity during and after cyberattacks. Jaipur businesses invest in robust cyber security services in Jaipur to avoid downtime and minimize financial losses.
4. Securing Financial Transactions
Cyber security ensures the safety of online transactions, a critical aspect for e-commerce platforms and fintech companies in Jaipur. Solutions like secure payment gateways and fraud detection tools are widely implemented.
5. Enhancing Customer Trust
By investing in cyber security in Jaipur, businesses build trust with their customers, demonstrating a commitment to safeguarding their data and transactions.
Cyber security in Jaipur
Jaipur is emerging as a hub for businesses and IT companies, which has increased the demand for reliable cyber security solutions. Cyber security services in Jaipur cater to diverse industries, including retail, healthcare, education, and finance.
Local providers of cyber security Jaipur solutions offer tailored services like:
Vulnerability Assessments: Identifying potential security risks in systems and networks.
Penetration Testing: Simulating attacks to uncover weaknesses and improve defenses.
Managed Security Services: Continuous monitoring and management of security operations.
Many IT firms prioritize cyber security services in Jaipur to ensure compliance with global standards and protect their operations from sophisticated cyber threats.
Safety Tips for Staying Secure Online
With the rising number of cyberattacks, individuals and businesses must adopt proactive measures to stay secure. Here are some practical tips that integrate cyber security in Jaipur into daily practices.
1. Use Strong Passwords
Ensure passwords are long, unique, and a mix of letters, numbers, and symbols. Avoid reusing passwords for multiple accounts. Cyber security experts in Jaipur recommend using password managers for added security.
2. Enable Two-Factor Authentication (2FA)
Adding an extra layer of security through 2FA significantly reduces the risk of unauthorized access. Many cyber security services in Jaipur emphasize implementing this measure for critical accounts.
3. Regular Software Updates
Outdated software can be a gateway for attackers. Keep operating systems, antivirus tools, and applications updated to close security loopholes. Businesses in Jaipur frequently rely on cyber security Jaipur providers to manage system updates.
4. Be Cautious with Emails
Phishing emails are a common attack vector. Avoid clicking on suspicious links or downloading unknown attachments. Cyber security in Jaipur often involves training employees to recognize and report phishing attempts.
5. Invest in Reliable Cyber security Services
Partnering with trusted cyber security services in Jaipur ensures robust protection against advanced threats. From endpoint protection to cloud security, these services help safeguard your digital assets.
6. Avoid Public Wi-Fi for Sensitive Transactions
Public Wi-Fi networks are vulnerable to attacks. Use a VPN when accessing sensitive accounts or conducting financial transactions. Cyber security Jaipur experts often provide VPN solutions to businesses and individuals.
7. Backup Your Data Regularly
Regularly backing up data ensures that critical information is not lost during cyber incidents. Cyber security providers in Jaipur recommend automated backup solutions to minimize risks.
Why Choose Cyber Security Services in Jaipur?
The vibrant business ecosystem in Jaipur has led to a growing need for specialized cyber security services. Local providers like 3Handshake understand the unique challenges faced by businesses in the region and offer customized solutions.
Some reasons to choose cyber security Jaipur services from like 3Handshake include:
Cost-Effective Solutions: Tailored to fit the budgets of small and medium-sized businesses.
Local Expertise: Providers have an in-depth understanding of regional cyber threats.
24/7 Support: Many companies offer round-the-clock monitoring and support to handle emergencies.
For businesses in Jaipur, investing in cyber security services in Jaipur is not just about compliance; it's about ensuring long-term success in a competitive digital landscape.
4 notes
·
View notes
Text

Deep Dives into Tech and Digital Growth Strategies
In an era of rapid technological advancements and evolving business landscapes, understanding the nuances of tech-driven strategies is essential for sustained growth. Companies today must leverage cutting-edge technologies and innovative digital growth strategies to stay competitive. This article takes a deep dive into the world of technology and digital strategies, highlighting how businesses can harness them to achieve their full potential.
Tech Innovation: The Catalyst for Business Evolution
Innovation in technology is reshaping industries, from manufacturing and healthcare to retail and financial services. Businesses that embrace tech innovations can unlock new opportunities and create unique competitive advantages.
Automation and AI: Automation tools and artificial intelligence (AI) are driving efficiency, reducing human errors, and freeing up resources for more strategic tasks. Companies that adopt AI-driven decision-making processes gain valuable insights and predictive analytics.
Cloud Computing: Cloud-based solutions offer businesses scalable, cost-effective options for data storage and software deployment. Cloud technologies facilitate remote work, enhance collaboration, and provide data accessibility from any location.
Internet of Things (IoT): IoT is transforming industries by connecting devices and enabling real-time data collection and analysis. Businesses can leverage IoT to monitor operations, optimize workflows, and improve customer experiences.
5G Connectivity: The rollout of 5G networks is enabling faster communication and data transfer. This enhanced connectivity paves the way for innovations in areas like telemedicine, augmented reality, and autonomous vehicles.
Digital Marketing Strategies for Sustainable Growth
Digital marketing is at the heart of modern business strategies. To stand out in a crowded market, businesses must adopt targeted and innovative marketing tactics.
Search Engine Optimization (SEO): SEO is critical for improving online visibility and driving organic traffic. Businesses should focus on creating high-quality content, optimizing for keywords, and building authoritative backlinks to enhance search engine rankings.
Content Marketing: Content is king when it comes to building brand authority and engaging audiences. Businesses should invest in creating informative, relevant content that addresses customer pain points and provides solutions.
Social Media Engagement: Social media platforms are powerful tools for building brand awareness and fostering community engagement. Consistent posting, audience interaction, and strategic advertising can amplify a brand’s reach.
Data-Driven Marketing: Analyzing marketing performance data allows businesses to make informed decisions and refine strategies. By leveraging analytics tools, businesses can identify trends, understand customer behaviors, and optimize campaigns for better results.
Personalization: Today’s consumers expect personalized experiences. Businesses that use data to tailor their offerings and communication to individual preferences are more likely to build lasting relationships with customers.
Cybersecurity: Protecting Digital Assets
As businesses become more reliant on digital technologies, cybersecurity is paramount. Cyber threats can compromise sensitive data, disrupt operations, and damage reputations. To safeguard digital assets, businesses must implement robust cybersecurity measures.
Multi-Layered Security: Implementing multi-layered security protocols ensures that businesses are protected from various attack vectors. This includes firewalls, intrusion detection systems, and endpoint protection.
Data Encryption: Encrypting sensitive data both in transit and at rest protects it from unauthorized access.
Regular Audits: Conducting regular security audits helps identify vulnerabilities and ensures that security measures are up-to-date.
Employee Training: Human error is a common cause of data breaches. Educating employees on cybersecurity best practices can reduce the risk of phishing attacks and other social engineering tactics.
Customer-Centric Tech Solutions
Understanding and prioritizing customer needs is key to business growth. Tech innovations can enhance customer experiences and build long-term loyalty.
Customer Relationship Management (CRM) Systems: CRM systems help businesses manage customer interactions and provide personalized experiences. By analyzing customer data, businesses can tailor their offerings and improve satisfaction.
Chatbots and Virtual Assistants: AI-powered chatbots offer 24/7 customer support, answering queries and resolving issues in real-time. These tools enhance customer service while reducing operational costs.
Omnichannel Experiences: Today’s consumers interact with businesses across multiple channels. Providing a seamless, consistent experience across all touchpoints—whether online, in-store, or on mobile—is essential for customer satisfaction.
Tech Integration for Operational Efficiency
Integrating technology into core business processes can streamline operations, reduce costs, and improve overall efficiency.
Enterprise Resource Planning (ERP) Systems: ERP systems integrate various business functions into a unified platform, improving visibility and coordination across departments.
Project Management Tools: Digital project management platforms enable teams to collaborate, track progress, and meet deadlines efficiently.
Supply Chain Optimization: Advanced technologies like IoT and blockchain can enhance supply chain transparency, improve inventory management, and reduce delays.
Sustainable Growth with Tech Partnerships
Partnering with tech solution providers can accelerate business transformation and growth. Collaborating with experts allows businesses to access specialized knowledge and cutting-edge technologies without investing heavily in in-house resources.
Scalability: Tech partnerships enable businesses to scale operations as needed, adapting to market demands without significant disruptions.
Innovation: Partnering with tech innovators ensures that businesses stay ahead of industry trends and adopt new technologies as they emerge.
Looking Ahead: Future Trends in Tech and Digital Growth
The tech landscape is constantly evolving, and businesses must stay agile to remain competitive. Emerging trends like artificial intelligence, quantum computing, and edge computing are set to redefine industries. By staying informed and embracing change, businesses can position themselves for long-term success.
Conclusion
Tech4Biz Solutions is committed to empowering businesses with innovative tech solutions and digital growth strategies. Whether it’s leveraging advanced technologies, optimizing marketing efforts, or enhancing customer experiences, Tech4Biz helps businesses unlock new possibilities. By diving deep into the world of tech and digital strategies, companies can fuel growth, drive innovation, and stay ahead of the curve in an ever-changing business landscape. Visit Tech4Biz Solutions to learn more about how we can help transform your business.
5 notes
·
View notes
Text
Highroad Cave
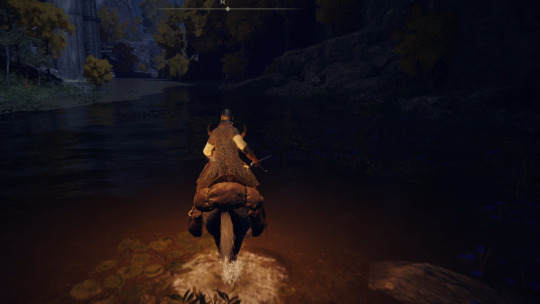
Underneath Saintsbridge, I found the origin of the Murkwater River. It However, even by the standards of this crazy land, it makes no goddamn sense. For the third time, it sinks into the earth and emerges below a cliff, but when I followed it all the way to the source, I found it just.. starts. There's a stone barrier, and then the inland sea. The actual running fresh water just appears right at that barrier. It's impossible.
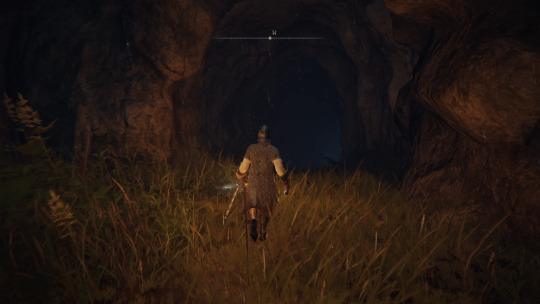
While pondering this, I noticed a cave pretty well hidden behind some trees. Well, time to go caving again. You never know what you're going to find.

A hole. I found a hole.

Following the advice of runes, I jumped down, and landed on a flat surface. Completely flat, aside from debris. I looked around with slowly dawning horror as I recognized that octagonal shape. It was one of the pillars I'd seen near the coast. Smaller, maybe, but of the same design.
I standing on the pillars of the earth.

I reached the bottom and continued towards a light. A pack of wolves had made their home here, but they were not trouble. But at the center of their den, I found another hole, with more pillars. How deep did this go?

After jumping from pillar to pillar, descending to an interminable depth, I emerged into a larger cave. A cave with campfires. I was not alone down here.
Next to the campfire, I found the corpse of a Kaidan sellsword, being picked apart by wolves. I find it hard to believe that they could bring down one of those stout warriors, so something else must've done the deed.
Traveling further into the cave, I faced more wolves, and found one of them picking apart the corpse of a giant bat.
Ah. I can more believe that. The wolves might be able to bring a bat down, but the Kaidan weapons would be too slow, and they have no recourse about the bat's ability to attack from a distance.
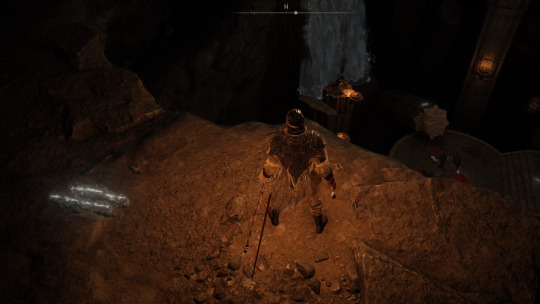
I emerged into a vast cavern. Waterfalls poured into a central basin. Did all the underground rivers pass through here? It was surrounded by broken columns, upon which perched a colony of giant bats.

At the center was a circular platform. A broken walkway lead who knows where. However, since the walkway only led away from this platform, it seemed like this was the endpoint of the path. Perhaps this was once some holy place, deep in the earth? A place for meditation? Whatever it was, its purpose was long gone. There was a treasure here, but only carried by some noble. Though...if it was here, perhaps he found it somewhere else in this same ancient mithraeum?

A shamshir. A curved sword with a graceful, dancing style. The blade was pale, almost silvery steel, though it had a slight patina of rust in parts.
I continued through a series of jumps across submerged columns, and found more corpses of dead sellswords. The larger cave looked like the site of a massacre. Whatever had killed so many strong warriors must be truly fearsome indeed.

Oh. It was a land squid.
To be fair to the deceased, these things had proven my end more than once. Their wild flailing and nigh-invulnerable rubbery bodies could be fearsome until you knew how to fight them, and most people didn't get to attempt as many times as I had.
I took care of it, and continued my journey into the earth. Eventually, I was confronted with a golden fog door. and I stepped through.

It was impossible to determine what this room was originally for. Aqueducts? Walkways? The structures were too ruined to make sense of. What I could make sense of, however, was the golem lying moribund in the water. It sluggishly stood up as I approached, as if struggling to reignite the fire within.
It was not ideal fighting one in such close quarters, but I made do and eventually it fell like the others I've faced. In its hand was a tiny charm. A simple cloth doll, that nonetheless carried a magic to it. Can a golem be sentimental? Or was it just the magic that it was protecting?

A cloth doll depicting a dancer garbed in blue. An ancient heirloom of some sort. The dancer in blue represents a fairy, who in legend bestowed a flowing sword upon a blind swordsman. Blade in hand, the swordsman sealed away an ancient god - a god that was Rot itself.
Intriguing. So many characters introduced with a single item. A Blue Dancer. A blind swordsman. A god of Rot. I had not heard of any of this before. Though...could it be related to the Scarlet Rot that poisons the Confessors' bolts? I will have to be on the lookout for any more information regarding these characters.
However, I am certain that the shamshir sword is related to this blind swordsman. His weapon, or perhaps a replica.
Who was the blue dancer?
Who was the blind swordsman?
What happened to the God of Rot once sealed away?
What was this ancient chamber used for?
Where did the collapsed walkway lead?
What were the sellswords searching for? The sword, the talisman, or something else?
9 notes
·
View notes
Text
How-To IT
Topic: Core areas of IT
1. Hardware
• Computers (Desktops, Laptops, Workstations)
• Servers and Data Centers
• Networking Devices (Routers, Switches, Modems)
• Storage Devices (HDDs, SSDs, NAS)
• Peripheral Devices (Printers, Scanners, Monitors)
2. Software
• Operating Systems (Windows, Linux, macOS)
• Application Software (Office Suites, ERP, CRM)
• Development Software (IDEs, Code Libraries, APIs)
• Middleware (Integration Tools)
• Security Software (Antivirus, Firewalls, SIEM)
3. Networking and Telecommunications
• LAN/WAN Infrastructure
• Wireless Networking (Wi-Fi, 5G)
• VPNs (Virtual Private Networks)
• Communication Systems (VoIP, Email Servers)
• Internet Services
4. Data Management
• Databases (SQL, NoSQL)
• Data Warehousing
• Big Data Technologies (Hadoop, Spark)
• Backup and Recovery Systems
• Data Integration Tools
5. Cybersecurity
• Network Security
• Endpoint Protection
• Identity and Access Management (IAM)
• Threat Detection and Incident Response
• Encryption and Data Privacy
6. Software Development
• Front-End Development (UI/UX Design)
• Back-End Development
• DevOps and CI/CD Pipelines
• Mobile App Development
• Cloud-Native Development
7. Cloud Computing
• Infrastructure as a Service (IaaS)
• Platform as a Service (PaaS)
• Software as a Service (SaaS)
• Serverless Computing
• Cloud Storage and Management
8. IT Support and Services
• Help Desk Support
• IT Service Management (ITSM)
• System Administration
• Hardware and Software Troubleshooting
• End-User Training
9. Artificial Intelligence and Machine Learning
• AI Algorithms and Frameworks
• Natural Language Processing (NLP)
• Computer Vision
• Robotics
• Predictive Analytics
10. Business Intelligence and Analytics
• Reporting Tools (Tableau, Power BI)
• Data Visualization
• Business Analytics Platforms
• Predictive Modeling
11. Internet of Things (IoT)
• IoT Devices and Sensors
• IoT Platforms
• Edge Computing
• Smart Systems (Homes, Cities, Vehicles)
12. Enterprise Systems
• Enterprise Resource Planning (ERP)
• Customer Relationship Management (CRM)
• Human Resource Management Systems (HRMS)
• Supply Chain Management Systems
13. IT Governance and Compliance
• ITIL (Information Technology Infrastructure Library)
• COBIT (Control Objectives for Information Technologies)
• ISO/IEC Standards
• Regulatory Compliance (GDPR, HIPAA, SOX)
14. Emerging Technologies
• Blockchain
• Quantum Computing
• Augmented Reality (AR) and Virtual Reality (VR)
• 3D Printing
• Digital Twins
15. IT Project Management
• Agile, Scrum, and Kanban
• Waterfall Methodology
• Resource Allocation
• Risk Management
16. IT Infrastructure
• Data Centers
• Virtualization (VMware, Hyper-V)
• Disaster Recovery Planning
• Load Balancing
17. IT Education and Certifications
• Vendor Certifications (Microsoft, Cisco, AWS)
• Training and Development Programs
• Online Learning Platforms
18. IT Operations and Monitoring
• Performance Monitoring (APM, Network Monitoring)
• IT Asset Management
• Event and Incident Management
19. Software Testing
• Manual Testing: Human testers evaluate software by executing test cases without using automation tools.
• Automated Testing: Use of testing tools (e.g., Selenium, JUnit) to run automated scripts and check software behavior.
• Functional Testing: Validating that the software performs its intended functions.
• Non-Functional Testing: Assessing non-functional aspects such as performance, usability, and security.
• Unit Testing: Testing individual components or units of code for correctness.
• Integration Testing: Ensuring that different modules or systems work together as expected.
• System Testing: Verifying the complete software system’s behavior against requirements.
• Acceptance Testing: Conducting tests to confirm that the software meets business requirements (including UAT - User Acceptance Testing).
• Regression Testing: Ensuring that new changes or features do not negatively affect existing functionalities.
• Performance Testing: Testing software performance under various conditions (load, stress, scalability).
• Security Testing: Identifying vulnerabilities and assessing the software’s ability to protect data.
• Compatibility Testing: Ensuring the software works on different operating systems, browsers, or devices.
• Continuous Testing: Integrating testing into the development lifecycle to provide quick feedback and minimize bugs.
• Test Automation Frameworks: Tools and structures used to automate testing processes (e.g., TestNG, Appium).
19. VoIP (Voice over IP)
VoIP Protocols & Standards
• SIP (Session Initiation Protocol)
• H.323
• RTP (Real-Time Transport Protocol)
• MGCP (Media Gateway Control Protocol)
VoIP Hardware
• IP Phones (Desk Phones, Mobile Clients)
• VoIP Gateways
• Analog Telephone Adapters (ATAs)
• VoIP Servers
• Network Switches/ Routers for VoIP
VoIP Software
• Softphones (e.g., Zoiper, X-Lite)
• PBX (Private Branch Exchange) Systems
• VoIP Management Software
• Call Center Solutions (e.g., Asterisk, 3CX)
VoIP Network Infrastructure
• Quality of Service (QoS) Configuration
• VPNs (Virtual Private Networks) for VoIP
• VoIP Traffic Shaping & Bandwidth Management
• Firewall and Security Configurations for VoIP
• Network Monitoring & Optimization Tools
VoIP Security
• Encryption (SRTP, TLS)
• Authentication and Authorization
• Firewall & Intrusion Detection Systems
• VoIP Fraud DetectionVoIP Providers
• Hosted VoIP Services (e.g., RingCentral, Vonage)
• SIP Trunking Providers
• PBX Hosting & Managed Services
VoIP Quality and Testing
• Call Quality Monitoring
• Latency, Jitter, and Packet Loss Testing
• VoIP Performance Metrics and Reporting Tools
• User Acceptance Testing (UAT) for VoIP Systems
Integration with Other Systems
• CRM Integration (e.g., Salesforce with VoIP)
• Unified Communications (UC) Solutions
• Contact Center Integration
• Email, Chat, and Video Communication Integration
2 notes
·
View notes
Note
Thoughts on the Microsoft Third Party news?
I mean if Xbox is getting to be a big enough brand that people are raising questions of whether or not exclusivity means monopoly, then yeah, spreading more of your games out across multiple platforms makes legal sense.
More and more of the game industry is regrettably going to be moving in the direction of "account ecosystem" rather than hardware platform. Years ago there was talk about how one day there would be no Xbox or Playstation console, just an Xbox or Playstation App you launch on something like a Roku.
The final disgusting endpoint in all of this "no more sales, just service" drive. No discs, not even local data, just a monthly streaming subscription. Forever. No ownership, no ability to mod games, no way to play offline.
Even in the best case scenario, we're looking at a Netflix where you stream 90% of what you play and only "buy" the 10% of games you truly love.
The only thing that flies in the face of that is, like, Steam. The state of movie ownership is what it is because Netflix got there first. The streaming arm of Netflix is the entire reason the "Hollywood Streaming Industry" exists right now. It predates Prime Video, it predates Tubi, it predates everything.
Fewer people probably remember this, but the original premise of Hulu was to get TV networks signed on to simulcast their newest shows online, because none of them were doing that yet. "Netflix Instant" (the original name for Netflix streaming) even predates that. Hulu was trying to fill a need that Netflix could not because Netflix did not actually stream TV shows at first. Not even syndicated rerun stuff. It was just movies. Streaming Seinfeld or The Simpsons or The Office was just outright impossible.
Netflix got in there and shifted the direction of an entire industry, before borders had been staked out or consumers had built up substantial libraries they were protective of. So we went from VHS to DVD to Blu-ray to Streaming, where "Streaming" usually means a subscription service and not any form of ownership.
But that's not the case with games. Users expect backwards compatibility, they expect their libraries to carry forward, and in some cases people may own hundreds or even thousands of games in a digital library. I know on the Xbox 360, I own at least $200 worth of digital games, because I won a sweepstakes specifically for a $200 Xbox gift card. And my 19 year old Steam account will gladly tell the entire world I own over 1600 PC games.
That's just on Steam! Epic is still always giving away free games (200+), GOG is occasionally giving away free games and holding sales where you can get stuff for a couple bucks, etc. etc. etc. It's like the warehouse of mythical items from Indiana Jones over here.

People own gigantic libraries of digital games they expect to keep and willingly modify in perpetuity. It's a lot harder to push people to stream everything off the cloud as a result. It's why the big selling point for game streaming is "No downloads!" and it's why it's struggling to catch on. Sure, a 100gb+ game is huge, but if I take my download limiters off, it doesn't actually take that long. A 90 minute download for a 30+ hour game seems like a pretty fair exchange, all told.
But Microsoft is still going all-in on "account ecosystem." It's like, think of it this way: every game publisher is in a constant war to have the one big holiday game that everybody buys. And for guys like Microsoft, that one big game a year is their primary moneymaker. If they can get everyone to spend at least $60 on their game once a year, they stay in business.
Game Pass is $60 a year. They side step having to put out that holiday season's biggest game and get to say, "Well for the price of one game, you can get access to an entire library." It changes the perspective on so much of their business model. Suddenly they don't need the big flagship holiday blockbuster, they just need to get more people to pay for Game Pass.
And the ultimate end goal there is probably to get Game Pass in as many places as they can. There's already a PC Game Pass. If they can launch some version of Game Pass for Playstation? Game Pass for Switch? They'll do it. The Xbox almost doesn't matter anymore. The subscription and the ecosystem does. It's why Microsoft rebooted the Xbox app on PC a few years ago -- it used to be a "Companion App" for your console, but now the Xbox App on PC is where all of their PC gaming and Game Pass stuff lives. Xbox isn't hardware anymore, it's a service you subscribe to, and that's where the real money is. Especially considering what a gigantic money pit hardware is; I don't think Microsoft has ever, even once, turned a profit on Xbox hardware (and neither has Sony, as far as I know).
Get rid of the need for hardware and that $60/year looks even sweeter, doesn't it? Especially when you start to consider that something like Game Pass Ultimate is actually $180/year. If you can lure people in on the $60 but upsell them to the $180... well, gosh, that's almost the price of a whole new console every year, isn't it? That's a lot of constant cashflow without needing the years and years of deeply expensive research, development, and manufacturing.
Getting people to spend a console's worth of money on your service without actually needing the console itself is massively desirable. They'd be saving millions, if not billions of dollars while making millions more elsewhere. There's a chart out there some executive is drooling over where a line goes straight up by something like 900%.
The only problem is the whole consumer rights/ownership factor. Which I am not a fan of. I objectively refuse to support Game Pass for what it's obvious goals are. I will buy and own every game I want to play. No compromises. I will buy physical if space and money allows. I will not be bled dry by temporary access.
7 notes
·
View notes
Text
Check Point Software Named a Visionary in 2024 Gartner Magic Quadrant for Endpoint Protection Platforms
http://securitytc.com/TDl6q1
2 notes
·
View notes
Text
Endpoint Protection Platforms Market Size Worth USD 6.91 Billion in 2030
The global Endpoint Protection Platforms (EPP) market size reached USD 3.33 Billion in 2021 and is expected to register a revenue CAGR of 8.4% during the forecast period, according to latest analysis by Emergen Research. Rise in trend of Bring Your Own Device (BYOD) and surge in incidence of cyberattacks are crucial factors driving market revenue growth.
0 notes
Text
Microsoft Outage: CrowdStrike and the 'Blue Screen of Death' Affecting Users Worldwide

photo microsoft
Global Impact
Microsoft Windows users across the globe, including those in India, Australia, Germany, the United States, and the UK, are experiencing a critical issue leading to the infamous 'Blue Screen of Death' (BSOD). This problem causes systems to restart or shut down automatically. Notably, companies like Dell Technologies have attributed this crash to a recent update from CrowdStrike, although Microsoft has yet to confirm this as the root cause of the outage.
Affected Sectors
The outage, which began Thursday evening, primarily impacted Microsoft's Central US region. Essential systems for numerous airlines were crippled, affecting American Airlines, Frontier Airlines, Allegiant, and Sun Country in the US, as well as IndiGo and other airlines in India. Additionally, the disruption extended to banks, supermarkets, media outlets, and other businesses, highlighting the significant reliance on cloud services for critical infrastructure.
CrowdStrike: An Overview
CrowdStrike is a prominent cybersecurity platform that offers security solutions to both users and businesses. It employs a single sensor and a unified threat interface with attack correlation across endpoints, workloads, and identity. One of its key products, Falcon Identity Threat Protection, is designed to prevent identity-driven breaches in real time.
The Issue with CrowdStrike's Update
Reports indicate that a buggy update caused CrowdStrike’s Falcon Sensor to malfunction and conflict with the Windows operating system. This has led to widespread BSOD errors. CrowdStrike has acknowledged the problem, stating, “Our Engineers are actively working to resolve this issue and there is no need to open a support ticket.” The company has promised to update users once the issue is resolved.
Microsoft's Response
Microsoft confirmed that the Azure outage was resolved early Friday. However, this incident serves as a stark reminder of the potential consequences when critical infrastructure heavily relies on cloud services. The outage underscores the need for robust and reliable cybersecurity measures to prevent such widespread disruptions in the future.
Understanding the Blue Screen of Death
The Blue Screen of Death (BSOD) is a critical error screen on Windows operating systems that appears when the system crashes due to a severe issue, preventing it from operating safely. When a BSOD occurs, the computer restarts unexpectedly, often resulting in the loss of unsaved data. The error message typically states, “Your PC ran into a problem and needs to restart. We are just collecting some error info, then we will restart for you.”
This type of error is not exclusive to Windows; similar issues can be seen across Mac and Linux operating systems as well.
While the exact cause of the widespread BSOD errors remains unclear, the incident highlights the interconnectedness and vulnerability of modern digital infrastructure. Both Microsoft and CrowdStrike are working to resolve the issues and restore normalcy to affected users and businesses worldwide.
2 notes
·
View notes