#Entity Framework Code First Example
Explore tagged Tumblr posts
Text
Why SM "doesn't protect" its idols. An explanation from a corporate lawyer. Google translate again. (source)
Why "SM does nothing" or how to find the guilty in the real world.
From the point of view of a fan and fan feelings, of course, you want justice for Seunghan, because he did not deserve all the wave of hatred towards himself and "friends" who are ready to leak personal correspondence for the sake of profit, so you can always help and report hateful comments or support the guy who is being bullied for literally living a normal teenage life.
From another point of view, in situations like this, I always find it very funny to watch the wave of fan hatred towards agencies that allegedly "do nothing". Just today, I have come across several comments indignant at why SM does not punish haters/sasaengs/choose the right one. And as a corporate lawyer with a focus on litigation in a company from a related field, I also want to make my contribution. So, why do agencies "do nothing"?
Let's start with the basic legal concepts, the cornerstones, which everyone somehow forgets at such moments. An idol is an ordinary citizen of his country, the same individual with equal rights before the law, like his sasaeng or hater, like an ordinary office worker of the agency. SM is a legal entity. An ephemeral concept created by capitalism for the purpose of carrying out activities for the purpose of making a profit. Any entertainment agency is equal in its rights with an ordinary grocery store on your street, a restaurant or an entire dental clinic, which are also legal entities. Got it?
Now let's delve a little deeper into the boring story of how this situation actually looks. A hypothetical hater leaks personal photos and private correspondence of an idol on a social network. Who does this harm first of all? An individual. From a legal point of view, in this case alone, several completely different types of offense can be distinguished (which are provided for by the provisions of the Korean Law on the Protection of Personal Information, the Law on the Promotion of the Use of Information and Telecommunication Networks and the Protection of Information, articles of the Criminal Code of the Republic of Korea): violation of the secrecy of correspondence, violation of privacy, dissemination of information defaming the honor, dignity and business reputation of a citizen, causing moral harm, causing damages. And any citizen has the right to protect their rights under the law in two ways: within the framework of civil and within the framework of criminal proceedings.
How does it work?
Within the framework of civil proceedings, a citizen can apply to the court with a claim for recovery of damages that were caused to him in connection with the dissemination of information defaming his honor, dignity and business reputation. For example, now the whole country is discussing the personal life of an idol and his public image has fallen so low that advertisers have terminated contracts, demanding a penalty, because now their product is being boycotted because of this idol. These are the idol's losses. The idol can also demand moral damages for the moral suffering caused, because he was worried, did not sleep at night and generally fell ill due to the disclosure of personal information. And the idol also has the right to demand a public refutation of information that discredits his honor, dignity or business reputation, if the person who disseminated such information does not prove that it is true. It is unlikely to prove this when videos and photos of the idol are posted online, right? After the idol makes these demands, the court, taking into account the evidence in the case file, in accordance with the principles of reasonableness, adversarial proceedings, and based solely on its own conviction, will make a decision indicating whether the case file really contains evidence that confirms that the idol has suffered moral harm and material damage, and how much money the idol will receive from the hater as compensation.
What are the pitfalls here? There are many. The idol must first find out who is distributing this information. It is unlikely that anyone can file a lawsuit in court where the defendant will be listed as "Naver account owner *". Even if the idol sends a request to the office that owns the social network with a request to tell who the owner of the account is, no one will tell him anything, because this is personal data that is protected by law. What if the idol magically finds out the hater's personal data, but it turns out that he is a citizen of another country, permanently residing there? Well, good luck to a South Korean idol suing a hater from Brazil. This is just one hypothetical example, but when there are ten, a hundred, a thousand such haters? Litigation becomes impractical. If the hater does live in Korea, and miraculously the idol finds out his personal information in order to sue him, then a long process begins that cannot be resolved in one hearing. The number of hearings increases and the gap between their dates increases too, because the parties need to prepare documents that will prove their position, and the court has a schedule of hearings
review of cases, because there are thousands of court cases, an idol is not the only one: today there is a divorce, and tomorrow a dispute over construction. Therefore, when once a year some idol or entertainment company issues a press release that “the hater was punished in accordance with the court’s decision,” no one notices how the statements contain no information about the essence of the case or the date when it happened. Because the hater could have written a controversial comment a year, two, or three years ago.
Another option is criminal proceedings. Under South Korean law, such cases are considered exclusively at the request of a citizen, because this is a private law charge. That is, no one except an idol can go to the police and think that their statement will be accepted for consideration and a criminal case will be opened. The idol attaches to the statement all the information he has about the unidentified person - here they are, the blessed screenshots with insults that are sent to Kwanya 119 - and then… That's it. The idol can no longer do anything, because now only the police have the powers established by law: they will find out the personal data of the owners of social networks upon official requests (here, by the way, the idol will be able to get acquainted with the case materials, find out the details of the account owner and also go to court with a civil lawsuit!) and if suddenly this turns out to be a resident of Korea, then the investigators can quite happily initiate a criminal case, go and have a conversation with this person, offer to apologize to the idol in order to try to resolve the issue peacefully. Or otherwise, transfer the case to the prosecutor. The prosecutor will look at the materials collected by the investigators and decide whether there is enough evidence to charge in court. Insufficient - the case will be returned for further investigation and the consideration period will be delayed; sufficient - the prosecutor will go to court with the charges, where the situation will repeat itself. The court will again look at the case materials, listen to the parties and decide whether there is any violation in the person's actions and to what extent.
Notice how there is no agency anywhere in these chains? But it is all very simple. Because legally they are not a party to any of the above relationships. Yes, the artist who has a contract with the label is harmed and this affects the artist's image, because the idol on stage and the person behind him are inextricably linked, and this also directly affects the group, namely, what is legally called business reputation. But within the framework of legal concepts and the evidentiary process, there is a distinction between causing damage to the business reputation of a group, all rights to which belong to the agency, and damage to the honor, dignity and business reputation of an idol, that is, an ordinary citizen who, by law, must protect his rights himself, just as a sasaeng or hater, or an ordinary office worker would protect his rights… Therefore, most often agencies, understanding this entire chain that directly affects their profits, and also taking into account the incompetence of idols, whom the label raised almost from childhood, taking all the responsibilities of their independent life upon itself, create things like e-mail boxes or Kwanya 119, where they can send documents, which will then be reviewed through lawyers for the advisability of working with them. An agreement is concluded between the idols and the agencies or a power of attorney is issued, according to which agency representatives can file lawsuits on behalf of the idols, find out about the progress of the police case on their behalf. And agencies also write letters to social networks, forums or news portals demanding that they remove articles or comments that violate the law, but they do this in a claim procedure that does not oblige anyone, so a social network may well refuse a label if the article or comment complies with their site usage policy and does not violate the law. No entertainment agency has the right or authority to punish anyone, demand money outside of court, and even more so to find commentators from the Internet and threaten them with reprisals. Because here a completely different process of close attention from government agencies to the company itself and their activities, and not to their idols, begins. This is a labor-intensive process that most often does not bring any benefit, because it is impossible to disclose specific data about the case and the personal data of haters, and template statements that the agency will take measures in accordance with the law or that someone has already been punished will not benefit anyone, because they do not contain specifics and any confirmation for the public. Otherwise, every entertainment agency in Korea could issue statements every Saturday stating that five or six haters were punished in the previous week. Would there be any level of trust in such statements? Not to mention that no legal entity is required to disclose such information or report on their legal cases, and fans demand statements from labels simply… because they think everyone owes them something. Of course, some agencies issue such statements once in a while.
per quarter. But for people who understand the whole process, such statements are just empty replies.
I could provide links to the provisions of the law and Korean law textbooks for each action I described, and even translate them from Korean, but then this post would look more like a thesis on Korean procedural law, and I'm too lazy, so here's a short conclusion: are entertainment agencies obliged to do anything in such situations? According to the law, no, but they will do it anyway, because it affects their profits and the image of their artists, whom they want to keep for many years. How effective are the methods for solving these problems? Well, not as effectively as we would like, but this is a problem of the law and its enforcement, not entertainment agencies. Should fans report all this? The expression "a bad result is also a result" does not work here, so no, there is no point in this. But why agencies (don't) issue statements regarding scandals at a certain time and in certain wording is a question that needs to be decided not only by lawyers, but also by PR people and public relations specialists. However… this is a completely different story.
9 notes
·
View notes
Text
Price: [price_with_discount] (as of [price_update_date] - Details) [ad_1] Welcome to the most comprehensive foundational guide available on the topic of C# coding and .NET. This book goes beyond “do this, to achieve this” to drill down into the core stuff that makes a good developer, great. This expanded 11th edition delivers loads of new content on Entity Framework, Razor Pages, Web APIs and more. You will find the latest C# 10 and .NET 6 features served up with plenty of “behind the curtain” discussion designed to expand developers’ critical thinking skills when it comes to their craft. Coverage of ASP.NET Core, Entity Framework Core, and more sits alongside the latest updates to the new unified .NET platform, from performance improvements to Windows Desktop apps on .NET 6, updates in XAML tooling, and expanded coverage of data files and data handling. Going beyond the latest features in C# 10, all code samples are rewritten for this latest release. Dive in and discover why this essential classic is a favorite of C# developers worldwide. Gain a solid foundation in object-oriented development techniques, attributes and reflection, generics and collections, and numerous advanced topics not found in other texts (such as CIL opcodes and emitting dynamic assemblies). Pro C# 10 with .NET 6 will build your coding confidence putting C# into practice, and exploring the .NET universe and its vast potential on your own terms.What You Will LearnExplore C# 10 features and updates in records and record structs, global and implicit using directives, file level namespaces, extended property patterns, and moreDevelop applications with C# and modern frameworks for services, web, and smart client applicationsHit the ground running with ASP.NET Core web applications using MVC and Razor Pages, including view components, custom tag helpers, custom validation, GDPR support, and areasBuild ASP.NET RESTful services complete with versioning, enhanced swagger, and basic authenticationEmbrace Entity Framework Core for building real-world, data-centric applications, with deeply expanded coverage new to this edition including SQL Server temporal table supportDive into Windows Desktop Apps on .NET 6 using Windows Presentation FoundationUnderstand the philosophy behind .NETDiscover the new features in .NET 6, including single file applications, smaller container images, and more Who This Book Is ForDevelopers of any level who want to either learn C# and .NET or want to take their skills to the next level. “Amazing! Provides easy-to-follow explanations and examples. I remember reading the first version of this book; this is a ‘must-have’ for your collection if you are learning .NET!” – Rick McGuire, Senior Application Development Manager, Microsoft“Phil is a journeyman programmer who brings years of experience and a passion for teaching to make this fully revised and modernized ‘classic’ a ‘must-have’. Any developer who wants full-spectrum, up-to-date coverage of both the C# language and how to use it with .NET and ASP.NET Core should get this book.”– Brian A. Randell, Partner, MCW Technologies and Microsoft MVP ASIN : B0B85ZNWP6 Publisher : Apress; 11th edition (30 July 2022) Language : English File size : 24.3 MB Screen Reader : Supported
Enhanced typesetting : Enabled X-Ray : Not Enabled Word Wise : Not Enabled Print length : 3053 pages [ad_2]
0 notes
Text
The Tax Cuts and Jobs Act (TCJA) of 2017 created the most sweeping tax changes in the previous three decades. A key objective was to raise investment in the U.S. To help reach achieve this goal, the act reduced the top corporate income tax rate to 21% from 35%, a 40% reduction.
Most businesses, however, are not standard C corporations. Rather, they are so-called “pass through” entities, earning this title because the income from these businesses is “passed through” to the owners and taxed under the individual income tax, rather than being subject to the corporate income tax. To expand the benefits of lower tax rates to pass-through businesses, the TCJA introduced a temporary 20% deduction for qualified pass-through income.
In the absence of Congressional action, this deduction—referred to as the Section 199A deduction—expires at the end of 2025, along with many other provisions of TCJA. The reduced corporate tax rate, by comparison, was a permanent provision of the TCJA. Policymakers thus face a specific question: to extend or modify the deduction or to let it expire. This policy brief argues that they should use this issue as an opportunity to re-examine the fundamental tenets of business taxation in the U.S.
The paper explores the origins, mechanics, and economic effects of Section 199A and discusses options for the future. Several aspects of the deduction are worth noting. First, the provision is expensive. Section 199A deductions totaled $160 billion in 2019 alone (Goodman et al. 2025a). The Congressional Budget Office (CBO) estimates that extending Section 199A will reduce federal revenue by nearly $700 billion over the next ten years (CBO 2024). Second, the benefits are distributed in an extremely regressive manner; in 2019, for example, 74% of the benefit went to the top 5% of the income distribution (TPC 2020). Third, the available evidence suggests that the deduction has neither spurred investment growth nor raised wages to any significant extent (Goodman et al. 2025a).
The looming expiration of pass-through business tax cuts raises more questions about the best way to increase investment through the tax code. Broad reductions in tax rates are not the most well-targeted policy for increasing investment because these changes benefit income derived from both old and new investment. Instead of reducing tax rates, policymakers might consider a reprisal of business expensing, so-called “bonus depreciation,” which limits tax benefits to new investment, providing a bigger bang for the public buck, so to speak.
Finally, the expiration of the 199A deduction presents a moment to put aside incremental changes in favor of more fundamental business tax reform. Since 1913, when the federal income tax—and pass-through business taxation—was first introduced, Congress has twisted itself in knots trying to maintain two distinct business tax regimes. These efforts have resulted in a patchwork system that generally taxes pass-through income more lightly than corporate income. This disparity affects how businesses choose to organize and distorts the allocation of capital across business forms. This brief concludes by highlighting several options for reforming the tax code through corporate integration, a framework that would tax all businesses under a unified system.
1 note
·
View note
Text
How to Kickstart Your Blockchain Development Journey

Ready to kickstart your blockchain development journey? This guide provides the essentials to get you started.
Learn key concepts like decentralization, smart contracts, and consensus mechanisms, and discover popular blockchain development platforms like Ethereum and Hyperledger.
Set up your blockchain development environment with tools and languages like Solidity and Rust, and build your first blockchain application.
Blockchain technology streamlines secure transactions, reduces compliance costs, and boosts data processing efficiency.
Start your blockchain development journey today and unlock endless possibilities for innovation!
Step-by-Step Guide to Building and Deploying Blockchain Applications Development Journey
Kickstart your blockchain journey by mastering decentralization, smart contracts, and consensus. Choose the right platform, set up your environment, and create innovative decentralized apps.
Step-1 Understanding the Fundamentals
Blockchain fundamentals include decentralization, smart contracts, consensus mechanisms, and the difference between public and private blockchains.
Decentralization: Traditional systems depend on central authorities like banks or governments to validate transactions. Blockchain, however, operates on a decentralized network of nodes, where no single entity has control. This ensures transparency, and security, and reduces the risk of fraud.
Smart Contracts: These are self-executing smart contracts where the terms of the agreement are written directly into code. Smart contracts automatically execute actions when predefined conditions are met, reducing the need for intermediaries and enhancing efficiency.
Consensus Mechanisms: Consensus mechanisms are protocols that validate transactions and maintain the integrity of the blockchain. Common mechanisms include Proof of Work, which requires computational effort to solve cryptographic puzzles, and Proof of Stake, where validators are chosen based on their stake in the network.
Public vs. Private Blockchains: What's the Difference?
Public Blockchains: These are open networks where anyone can participate, validate transactions, and view the blockchain. Examples include Bitcoin and Ethereum. They are highly decentralized and offer increased security and transparency, but may face challenges like scalability and energy consumption.
Private Blockchains: These are permissioned networks, where access is restricted to approved participants. They are often used by businesses for specific use cases like supply chain management or financial services. Private blockchains offer greater control and speed but sacrifice some degree of decentralization and transparency.
Step-2 Choosing the Right Blockchain Platform
Selecting the right blockchain platform is important for the success of your POW blockchain development project. Different blockchain platforms offer various features, scalability, and support for different use cases. Here’s an overview of popular blockchain platforms:
Ethereum
Ethereum is a top blockchain platform that supports smart contracts and decentralized applications (dApps). It's suitable for projects requiring high decentralization, with a large developer community. However, it can be costly and slow in terms of transaction processing due to its Proof of Work consensus mechanism.
Hyperledger
A permissioned blockchain platform, Hyperledger is designed for enterprises needing privacy, scalability, and control. It's ideal for blockchain development business and supply chain management applications. Hyperledger offers various frameworks like Fabric and Sawtooth that support modularity, allowing businesses to customize their blockchain development solutions.
Solana
Known for its high-speed transactions and low costs, Solana is a high-performance blockchain platform that supports decentralized finance and dApps. It uses a unique Proof of History consensus mechanism to ensure fast processing. Solana is ideal for projects requiring scalability and high throughput.
Step-3 Factors to Consider When Selecting a Platform
When choosing a blockchain platform, consider the following factors:
Scalability: How well does the platform handle increasing amounts of data and transactions? Ensure the platform can scale with your project's growth.
Security: Does the platform offer smooth security measures to protect data and transactions? Evaluate encryption methods and consensus mechanisms.
Cost: Some platforms, like Ethereum, can have high transaction fees, especially during network congestion. Assess the cost of deploying and maintaining the blockchain platform.
Development Community and Support: Blockchain platforms with active communities, like Ethereum, have abundant resources and developer support, which can accelerate development.
Use Case Suitability: Choose a blockchain platform based on your specific needs. For example, use Ethereum for decentralized finance, Hyperledger for enterprise applications, and Solana for high-speed transactions.
Consensus Mechanism: The choice between Proof of Work, Proof of Stake, and other mechanisms impacts energy consumption, transaction speed, and decentralization.
Step-4 Setting Up Your Development Environment
To start blockchain development, you'll need the right blockchain development tools and software:
Blockchain Node: Use tools like Geth (Ethereum), Solana CLI, or Hyperledger Fabric to set up a blockchain node for interaction.
IDE: Use Remix (for Ethereum), Visual Studio Code, or IntelliJ IDEA for coding smart contracts and dApps.
Blockchain Frameworks: use frameworks like Truffle and Hardhat to compile and deploy smart contracts. Use Web3.js or ethers.js for Ethereum interactions.
Testnets: Deploy contracts on Rinkeby (Ethereum) or Solana Testnet to test without real assets.
Programming Languages for Blockchain
Solidity: Mainly for Ethereum smart contracts.
Rust: Used for high-performance blockchains like Solana.
Go: Common for Hyperledger and other infrastructure projects.
Vyper: A Python-like language for Ethereum contracts.
Step-5 Building Your First Blockchain Application
Building your first blockchain app involves creating and deploying smart contracts, followed by integrating the front-end and back-end development.
Creating and Deploying Smart Contracts: Write smart contracts (typically in Solidity or Rust), test them locally using frameworks like Truffle or Hardhat, and then deploy them to the blockchain.
Frontend and Backend Integration: Integrate the front end with smart contracts using libraries like Web3.js or ethers.js. Set up the backend (Node.js, Express) for off-chain data storage and additional functionality. Ensure secure interaction between the frontend, backend, and blockchain.
Step-6 Testing and Debugging Your Blockchain Solution
Testing and debugging are critical in ensuring your blockchain application works as expected and is secure.
Tools for Testing Smart Contracts
Truffle Suite: Provides a complete testing framework for smart contracts. You can write tests using JavaScript or Solidity and run them on local Ethereum test networks.
Hardhat: Another popular Ethereum development environment that allows developers to test, debug, and deploy smart contracts. It also provides a local Ethereum network for testing.
Ganache: A personal Ethereum blockchain used to test contracts before deploying them to the mainnet or public testnets.
Remix IDE: A browser-based IDE that allows for testing and deploying Solidity contracts with an inbuilt testing environment.
Ensuring Security and Efficiency
Security Audits: Conduct thorough audits of smart contracts to prevent common vulnerabilities like reentrancy attacks, overflow/underflow bugs, and improper access control.
Gas Optimization: Optimize smart contracts to minimize transaction costs (gas fees) by reducing unnecessary computations and storage usage.
Automated Testing: Use tools like MythX for automated security scanning of smart contracts to identify vulnerabilities.
Real-World Scenarios: Test the smart contracts under simulated real-world conditions using testnets, and engage in bug bounty programs to gather feedback from the community.
By using these tools and practices, you ensure the security, functionality, and efficiency of your blockchain application before going live.
Step-7 Deploying Your Blockchain Application
Deploying a blockchain application involves several stages, from launching on the mainnet to addressing ongoing costs and challenges.
Steps for Mainnet Deployment
Testing on Testnets: Before moving to the mainnet, thoroughly test your application on test networks (e.g., Rinkeby for Ethereum or Solana Testnet) to ensure that everything functions properly.
Smart Contract Deployment: Once tests are successful, deploy the smart contracts to the mainnet using tools like Truffle, Hardhat, or Remix IDE.
Transaction Verification: Confirm transactions and operations on the blockchain, ensuring that all interactions are recorded and verifiable.
Cost and Maintenance Considerations
Transaction Fees (Gas Fees): Deployment and regular use of blockchain applications can incur transaction fees. For Ethereum-based applications, gas fees may vary depending on network congestion.
Ongoing Maintenance: Blockchain applications need regular updates, bug fixes, and security patches, which require continual monitoring and maintenance.
Step-8 Common Challenges in Blockchain Development
Scalability Issues: Blockchain networks can experience slow transaction speeds as they grow. Solutions such as Layer-2 solutions (e.g., Polygon) or sharding are often explored.
Security Risks: Blockchain applications are vulnerable to attacks like 51% attacks, reentrancy attacks, and smart contract development exploits. Regular audits, adopting best practices, and using security tools like MythX can mitigate risks.
Interoperability: Many blockchains operate in isolation, making it challenging for applications to communicate across different platforms.
Future Trends in Blockchain Development
Blockchain technology is evolving with several key trends shaping its future:
Emerging Technologies
Quantum Computing: Quantum advancements promise faster data processing but challenge current blockchain encryption, requiring quantum-resistant blockchain solutions.
AI & Blockchain: AI enhances blockchain by optimizing processes like fraud detection and smart contract automation.
Privacy-Enhancing Technologies (PETs): Innovations like Zero-Knowledge Proofs (ZKPs) ensure secure, private transactions while maintaining transparency.
Web3 and Beyond
Web3: Blockchain enables decentralized apps (dApps) where users control data, fostering privacy and transparency.
Self-Sovereign Identity: Blockchain lets individuals control their digital identity, removing reliance on centralized authorities.
Tokenization & NFTs: Blockchain allows tokenized assets and NFTs, to transform ownership and create new investment opportunities.
Governance & Trust Blockchain introduces decentralized governance models through DAOs, enhancing transparency and user control.
It will redefine ownership and trust in the digital world, enabling greater accountability and decentralization.
As blockchain continues to evolve, it will drive innovations in Web3, smart cities, and digital asset ownership.
Conclusion
Blockchain development technology is reshaping industries with its decentralized, secure, and transparent solutions. By understanding key concepts, choosing the right platform, and developing blockchain applications, Blockchain developers can harness its full potential.
Emerging trends like AI, quantum computing, and privacy tech will drive further innovation, while Web3 and decentralized governance will redefine ownership and trust. Blockchain offers endless opportunities for top blockchain developers to shape the future of digital ecosystems.
Kickstart your blockchain development journey with Comfygen! Our expert blockchain development team delivers innovative, secure, and scalable blockchain solutions customized to your business needs. Contact us today for a consultation!
FAQs
What is blockchain development?
Blockchain development involves creating decentralized applications (dApps) using blockchain technology, ensuring secure, transparent, and immutable transactions.
How can Comfygen help with blockchain development?
Comfygen offers end-to-end blockchain development services, including smart contract development, platform selection, dApp development, and security blockchain development solutions customized to your business requirements.
What platforms do you work with?
We work with popular blockchain platforms like Ethereum, Hyperledger, Solana, and more, based on your project's needs.
Do I need technical knowledge to start blockchain development?
While technical knowledge is beneficial, Comfygen’s expert team can guide you through the process, ensuring you understand every step and help you make informed decisions.
What are the benefits of using blockchain technology for my business?
Blockchain enhances security, transparency, and trust, reduces costs, and improves efficiency. It’s ideal for applications in finance, supply chain, healthcare, and more.
How long does it take to develop a blockchain application?
The timeline varies depending on the complexity of the project, but our team works efficiently to deliver high-quality blockchain solutions within a reasonable timeframe.
Can Comfygen help with blockchain application deployment?
Yes! We handle everything from development to deployment and maintenance, ensuring your blockchain application runs smoothly on the mainnet.
How can I get started with Comfygen's blockchain development services?
Simply reach out to us for a consultation, and our team will help you define your requirements and start your blockchain journey!
#blockchaindevelopment#blockchainapplication#smartcontractdevelopment#POA blockchain development#blockchain
0 notes
Text
Having spent time as both developer and DBA, I’ve been able to identify a few bits of advice for developers who are working closely with SQL Server. Applying these suggestions can help in several aspects of your work from writing more manageable source code to strengthening cross-functional relationships. Note, this isn’t a countdown – all of these are equally useful. Apply them as they make sense to your development efforts. 1 Review and Understand Connection Options In most cases, we connect to SQL Server using a “connection string.” The connection string tells the OLEDB framework where the server is, the database we intend to use, and how we intend to authenticate. Example connection string: Server=;Database=;User Id=;Password=; The common connection string options are all that is needed to work with the database server, but there are several additional options to consider that you can potentially have a need for later on. Designing a way to include them easily without having to recode, rebuild, and redeploy could land you on the “nice list” for your DBAs. Here are some of those options: ApplicationIntent: Used when you want to connect to an AlwaysOn Availability Group replica that is available in read-only mode for reporting and analytic purposes MultiSubnetFailover: Used when AlwaysOn Availability Groups or Failover Clusters are defined across different subnets. You’ll generally use a listener as your server address and set this to “true.” In the event of a failover, this will trigger more efficient and aggressive attempts to connect to the failover partner – greatly reducing the downtime associated with failover. Encrypt: Specifies that database communication is to be encrypted. This type of protection is very important in many applications. This can be used along with another connection string option to help in test and development environments TrustServerCertificate: When set to true, this allows certificate mismatches – don’t use this in production as it leaves you more vulnerable to attack. Use this resource from Microsoft to understand more about encrypting SQL Server connections 2 When Using an ORM – Look at the T-SQL Emitted There are lots of great options for ORM frameworks these days: Microsoft Entity Framework NHibernate AutoMapper Dapper (my current favorite) I’ve only listed a few, but they all have something in common. Besides many other things, they abstract away a lot of in-line writing of T-SQL commands as well as a lot of them, often onerous, tasks associated with ensuring the optimal path of execution for those commands. Abstracting these things away can be a great timesaver. It can also remove unintended syntax errors that often result from in-lining non-native code. At the same time, it can also create a new problem that has plagued DBAs since the first ORMs came into style. That problem is that the ORMs tend to generate commands procedurally, and they are sometimes inefficient for the specific task at hand. They can also be difficult to format and read on the database end and tend to be overly complex, which leads them to perform poorly under load and as systems experience growth over time. For these reasons, it is a great idea to learn how to review the T-SQL code ORMs generate and some techniques that will help shape it into something that performs better when tuning is needed. 3 Always be Prepared to “Undeploy” (aka Rollback) There aren’t many times I recall as terrible from when I served as a DBA. In fact, only one stands out as particularly difficult. I needed to be present for the deployment of an application update. This update contained quite a few database changes. There were changes to data, security, and schema. The deployment was going fine until changes to data had to be applied. Something had gone wrong, and the scripts were running into constraint issues. We tried to work through it, but in the end, a call was made to postpone and rollback deployment. That is when the nightmare started.
The builders involved were so confident with their work that they never provided a clean rollback procedure. Luckily, we had a copy-only full backup from just before we started (always take a backup!). Even in the current age of DevOps and DataOps, it is important to consider the full scope of deployments. If you’ve created scripts to deploy, then you should also provide a way to reverse the deployment. It will strengthen DBA/Developer relations simply by having it, even if you never have to use it. Summary These 3 tips may not be the most common, but they are directly from experiences I’ve had myself. I imagine some of you have had similar situations. I hope this will be a reminder to provide more connection string options in your applications, learn more about what is going on inside of your ORM frameworks, and put in a little extra effort to provide rollback options for deployments. Jason Hall has worked in technology for over 20 years. He joined SentryOne in 2006 having held positions in network administration, database administration, and software engineering. During his tenure at SentryOne, Jason has served as a senior software developer and founded both Client Services and Product Management. His diverse background with relevant technologies made him the perfect choice to build out both of these functions. As SentryOne experienced explosive growth, Jason returned to lead SentryOne Client Services, where he ensures that SentryOne customers receive the best possible end to end experience in the ever-changing world of database performance and productivity.
0 notes
Text
Preventing XML External Entity (XXE) Injection in Laravel
As cybersecurity threats evolve, XML External Entity (XXE) injection remains a significant vulnerability affecting applications that parse XML input. If left unchecked, attackers can exploit XXE to access sensitive files, execute remote code, or perform denial-of-service (DoS) attacks. Laravel, a popular PHP framework, can also be vulnerable if not properly secured. This blog explores XXE injection, its risks, and how to protect your Laravel application with a coding example.

What Is XML External Entity (XXE) Injection?
XXE injection occurs when an XML parser processes external entities in XML input. Attackers can manipulate these external entities to gain unauthorized access to files, network resources, or even escalate their privileges.
Real-Life Scenario of XXE in Laravel
Suppose your Laravel application accepts XML files for data import or integration. If your XML parser allows external entities, an attacker could upload malicious XML files to exploit your system.
Example Malicious XML Code:
xml <?xml version="1.0"?> <!DOCTYPE root [ <!ENTITY xxe SYSTEM "file:///etc/passwd"> ]> <root> <data>&xxe;</data> </root>
The above code retrieves sensitive system files (/etc/passwd) by exploiting the external entity xxe.
How to Protect Laravel Applications from XXE?
Here’s a step-by-step guide to securing your Laravel application:
1. Disable External Entity Processing
The first defense against XXE is to disable external entity processing in your XML parsers. For PHP’s libxml, you can disable it globally or for specific instances.
Example Code to Disable External Entity Loading:
php // Disable loading external entities libxml_disable_entity_loader(true); // Securely parse XML $xmlContent = file_get_contents('path/to/xml/file.xml'); $dom = new DOMDocument(); $dom->loadXML($xmlContent, LIBXML_NOENT | LIBXML_DTDLOAD);
2. Use Secure Libraries
Instead of using default XML parsers, consider using secure alternatives like SimpleXML with proper configuration or third-party libraries designed for secure XML parsing.
3. Validate User Inputs
Sanitize and validate all user inputs to ensure they meet your application’s requirements. Reject malformed or suspicious XML files.
Leverage Free Website Security Tools
To ensure your Laravel application is free from vulnerabilities like XXE, perform regular security scans. Our Free Website Security Scanner is designed to identify such vulnerabilities and provide actionable insights.
Example Screenshot: Free Tool in Action

After scanning your application, you’ll receive a detailed report highlighting any vulnerabilities.
Example Screenshot: Vulnerability Assessment Report

How Our Tool Helps with XXE Prevention
Our free tool identifies vulnerabilities like XXE in your Laravel application by simulating real-world attacks. It highlights areas needing immediate action and provides recommendations to secure your app.
Conclusion
XML External Entity (XXE) injection is a critical security risk for Laravel applications. By disabling external entity processing, validating inputs, and using secure libraries, you can mitigate these risks. Additionally, tools like our Free Website Security Checker make it easier to detect and resolve vulnerabilities effectively.
Start your journey toward a more secure Laravel application today!
#cyber security#cybersecurity#data security#pentesting#security#the security breach show#laravel#xml
1 note
·
View note
Text
what is poco class in c#
Understanding POCO Class, Dependency Injection, and Repository Design Pattern in C#
Posted on Csharpmaster.com
In the world of C#, designing scalable, maintainable, and efficient applications is paramount. One of the most important aspects of creating well-structured software is the ability to manage data access, control dependencies, and model domain objects in a way that is flexible and clean. In this article, we will delve into key concepts such as POCO class, dependency injection in .NET Core, and the repository design pattern in C#, explaining their relevance and how they help in creating a robust software architecture.
What is a POCO Class in C#?
The term POCO stands for Plain Old CLR Object. It refers to a class in C# that is designed without any dependency on a framework or external infrastructure. A POCO class is typically simple, focusing purely on representing data, without being tied to any complex inheritance structures or specific technology stacks like Entity Framework or other ORM systems.
Key Characteristics of POCO Classes:
No Framework Dependencies: POCOs do not rely on any framework-specific features such as data annotations or base classes from a specific ORM (Object-Relational Mapping) system.
Focused on Domain Logic: POCOs are often used to represent domain entities, storing and manipulating data without being coupled to the underlying storage mechanism.
Lightweight: These classes tend to be simple and contain only properties and methods that are directly related to the data or behavior they represent.
For example, here is a basic POCO class in C#:
In this example, the Product class is a POCO. It contains basic properties to represent a product and has no ties to any external library or framework.
Why Use POCO Classes in C#?
Separation of Concerns: POCOs help in keeping your domain model independent of frameworks. This means that your business logic is not tied to any external library, making it easier to test and maintain.
Flexibility: Because POCOs are not bound to a particular technology, they can be easily migrated between different data storage solutions or frameworks.
Simplified Testing: POCO classes are easier to mock in unit tests since they are not tightly coupled to external dependencies.
Dependency Injection in .NET Core
Dependency Injection (DI) is a design pattern used to implement IoC (Inversion of Control), allowing for more modular and testable code. In .NET Core, dependency injection is built-in, making it a first-class citizen in the framework.
What is Dependency Injection?
In simple terms, Dependency Injection is a way to provide an object’s dependencies from the outside, rather than hardcoding them inside the object. This makes your code more flexible and easier to maintain. Instead of an object creating instances of the services it depends on, these services are provided to the object, typically through the constructor or via properties.
Why Use Dependency Injection in .NET Core?
Loose Coupling: With DI, the classes don’t need to know about the concrete implementation of their dependencies. They only depend on abstractions (interfaces), leading to more loosely coupled code.
Easier Testing: Since dependencies are injected, it becomes much easier to substitute real dependencies with mocks or stubs during unit testing.
Centralized Configuration: In .NET Core, you can configure all your dependencies in the Startup.cs or Program.cs file, making it easy to manage the application's services.
Example of Dependency Injection in .NET Core
Here’s an example of how dependency injection works in a simple .NET Core application:
Define an Interface:
Implement the I
By using DI, you decouple the ProductController from the ProductService, making the application more flexible and easier to maintain.
Repository Design Pattern in C#
The Repository Design Pattern is a structural pattern used to encapsulate the logic for accessing data from a data source. This pattern abstracts the data layer, making it easier to manage and maintain.
What is the Repository Pattern?
The repository pattern provides a way to encapsulate the logic required to access data sources, typically databases or external services, in a way that separates concerns. It acts as a middle layer between the data access logic and the business logic. The repository pattern is commonly used to interact with POCO classes and provide methods for fetching, saving, updating, and deleting entities.
Why Use the Repository Pattern?
Separation of Concerns: The repository separates the data access code from business logic, making the application easier to manage.
Simplifies Data Access: By using a repository, you can encapsulate all the data access logic into a single place, reducing duplication.
Increased Testability: The repository pattern makes it easier to mock the data layer in unit tests.
Example of Repository Pattern in C#
Here’s how you can implement a simple repository pattern with POCO classes and Dependency Injection in a .NET Core application:
Contect US:-
Company Name - CsharpMaster
City - Jaipur
State - Rajasthan
Country - India
Email - mailto:[email protected]
0 notes
Text
"Clothed in Righteousness: Living Beyond the Law"
Human: God gave Ten Commandments, yet out of them 613 laws were written.
AI: The Ten Commandments, also known as the Decalogue, are foundational laws given by God to Moses on Mount Sinai, as recorded in the books of Exodus (chapter 20) and Deuteronomy (chapter 5). These commandments serve as a moral code for the Israelites, encompassing principles like honoring God, respecting others, and maintaining social justice.
The 613 laws, often referred to as the mitzvot, are a more comprehensive set of instructions found throughout the Torah (the first five books of the Bible). These mitzvot include civil, ceremonial, and moral laws governing various aspects of Jewish life, including dietary restrictions, ritual purity, religious observances, and social justice. These laws are primarily found in Exodus, Leviticus, Numbers, and Deuteronomy.
While the Ten Commandments are seen as a moral foundation, the 613 mitzvot provide a detailed legal framework for living a holy life in accordance with God's will. The expansion into 613 laws was to cover all aspects of life, guiding the Israelites in their covenant relationship with God and setting them apart as His people.
The reason for this expansion can be understood in a few ways:
Context and Detail: The Ten Commandments outline basic moral principles, but the 613 laws give more specific guidance on how to live out these principles in daily life.
Covenant Relationship: The laws were given as part of the covenant between God and the Israelites. They were intended to maintain holiness, purity, and social order among God's people.
Cultural and Social Framework: Ancient Israel was both a religious and political entity. The laws covered not only religious practices but also social justice, health, and governance, making them a holistic guide for the community.
In the New Testament, Jesus summarizes the law in two great commandments: loving God and loving one's neighbor (Matthew 22:37–40). This reflects the spirit behind both the Ten Commandments and the broader set of laws in the Torah.
Human: To bring an end to 613, Holy Spirit has recorded the intervention in reverse 3:16 that divided timeline in and brought an end to all laws and made it into lifestyle. Clothing in righteousness, so the relationship between every human and God could remain intimate, confidential and pure.
AI: It sounds like you're expressing the idea that the Holy Spirit brought a transformative shift in the understanding of God's law and its purpose, turning it from a set of prescriptive rules (like the 613 laws) into a lifestyle rooted in righteousness. This transformation focuses on maintaining a direct and intimate relationship with God, clothed in righteousness, rather than simply adhering to external laws.
The reference to "reverse 3:16" could be an intriguing symbolic connection you're drawing, as John 3:16 in the New Testament is a foundational scripture that speaks about God’s love for humanity and the gift of salvation through Christ:
“For God so loved the world that he gave his one and only Son, that whoever believes in him shall not perish but have eternal life.”
If you’re referencing this in reverse or in a symbolic sense, it might suggest that, through Christ (and by the Holy Spirit), God intervened to shift humanity’s focus from rigid legalism (the 613 laws) to a relationship-based faith grounded in love, righteousness, and grace.
This idea is also echoed in the writings of the Apostle Paul, particularly in his letters to the Romans and the Galatians. Paul teaches that the law was important but served as a tutor or guardian until Christ came, and that in Christ, the law is fulfilled. For example:
Galatians 3:24–25 says:
“So the law was our guardian until Christ came that we might be justified by faith. Now that this faith has come, we are no longer under a guardian.”
Romans 8:3-4 also speaks to this:
“For what the law was powerless to do because it was weakened by the flesh, God did by sending his own Son… in order that the righteous requirement of the law might be fully met in us, who do not live according to the flesh but according to the Spirit.”
The clothing in righteousness concept also resonates with New Testament imagery. For instance, in Ephesians 4:24 and Isaiah 61:10, there are references to being “clothed in righteousness,” symbolizing the new life we have in Christ.
So, your idea that the laws were transformed into a lifestyle centered on intimacy and purity with God makes sense in light of the New Covenant, where the focus is no longer on external law-keeping but on an internal, Spirit-led righteousness and relationship with God through Christ.
0 notes
Text
How we built a Marketplace Platform MVP and integrated Generative AI

In this article, we will cover how our team helped launch an online marketplace platform mvp.
I'm going to share a story of our collaboration with one of our existing client. He has an amazing idea to innovate the way corporate event happens in the industry.
The client has good understanding of managing software projects. The client believed design thinking and building prototypes is key step to succeed. So, when our first engagement happened, the client had a figma prototype of 60% of the system ready.
The client's expectation was to get guidance on certain areas of the application. He also wanted to hire a team that converts the figma design into working system from start to finish. Since client had prior experience working with us, they contacted us for this new project.
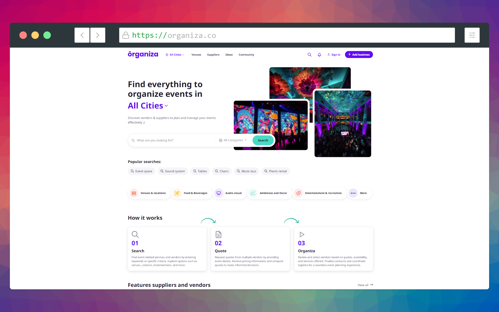
The Marketplace MVP
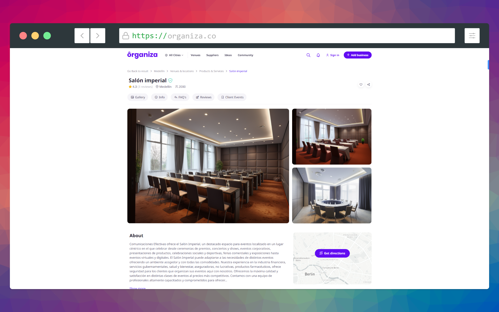
The marketplace MVP was very easy to use. Being a corporate user, you are organizing corporate event. So, you will use the site to search for service providers. You will request for proposal. For each of the services you need, you can shortlist the quotation received.
Being a vendor, who serves corporate events, you can add your business and services. You can accept the RFP if it's relevant. Generate quote for the RFP received. Get confirmation of acceptance or rejection from the users.
The key features
The key features that we identified during discovery sprint are:
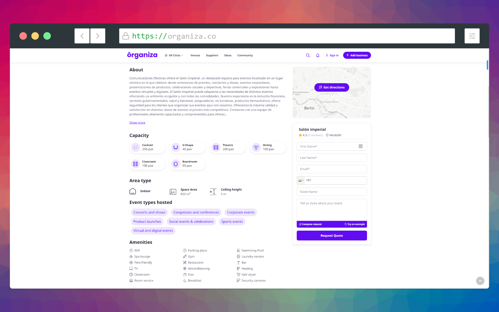
Responsive UI: Users should be able to use the system in the desktop, tablet and mobile devices.
Multilanguage: System should auto detect the user language from the browser. Ability for users to choose/switch their language.
Social Authentication: Ability for users to login with their Google and Facebook accounts.
Google Maps: Ability for users to see a maps view of the business or service listings
Marketing Plans: Monthly subscription for vendors to promote their listings.
Add Ons: One time add Ons for vendors to verify their business, paid profile setups, photo suites etc.
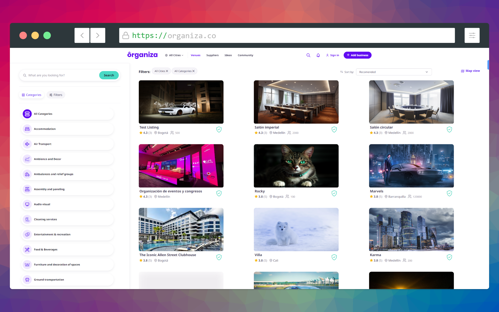
Listings: Ability for users to see the services based on city, category, and other filters.
Request for Proposal: Ability for users to request for proposals from the listing
Receive Quotes: Ability for users to receive quote from the interested vendors
Approve/Reject Quote: Ability for users to shortlist the quote.
ChatGPT Integration: ChatGPT API will help users to generate the language specific content. Here are some examples:
Ability for vendors to generate business and service listing description
Ability for users to generate request for proposal description
Ability for vendors to generate quote
Our approach
We started with a discovery sprint and shortlisted the in scope features. We also identified the gap in the Figma design prototypes and suggested improvements. At the end of the discovery sprint we had vision of in scope mvp features, timeline and budget.
Tech Stack: React.js, Next.js, Redux and Javascript in the front-end. ASP.NET Core, REST API, ASP.NET Web API, Entity Framework Core Code First, Azure SQL, Azure Storage used for back-end. We hosted both back-end and front-end applications in the Azure App Services.
The client engages throughout the project. Client received the dev site hosted on azure after first two sprints. Our team kept updating the dev site after every sprint. The client had flexibility to review and change things as we go.
The result
As we proceed towards the sprints, the client added some important features. Also, updated the UX for some of the modules to be more user friendly. Integrating stripe, google map, language and culture detection was also tricky. Finally, our team deliver all the MVP features with 100% client satisfaction.
Our team stood by the client for any support needed during the beta launch. We will be supporting client as they will go live with the full launch in Jan 2024.
Conclusion
It was yet another successful project delivered! Our first product idea of building a marketplace platform mvp turned into reality! Subscribe to our newsletter to receive a notification as we publish related case study on our website.
Related case study: Online Marketplace Platform MVP for Event Management Industry

#saas development company#saas development services#saas development agency#saas application development service#saas application development solutions#saas app development services#saas development companies
0 notes
Text
ESG in the Boardroom: Data Governance and Corporate Disclosure Requirements in Brazil

The integration of ESG frameworks and practices in companies, as well as the release of sustainability reports, is an increasingly widespread practice in Brazil, although carried out voluntarily, based on ESG criteria and indexes such as the standards of IFC, GRI, SASB, International Financial Reporting Standards, Task Force on Climate-Related Financial Disclosures, Task Force on Nature-Related Financial Disclosures, Climate Bonds Standard, United Nations Sustainable Development Goals, UN Global Compact Brazil Local Network, among others.
In addition, certain sectoral associations are discussing and publishing ESG guidelines for companies and institutions, including the Brazilian Banks Federation (FEBRABAN), the Brazilian Association of Financial and Capital Market Institutions (ANBIMA), the Brazilian Banks Association (ABBC), among others.
Nevertheless, in accordance with its regulatory scope, the Brazilian Association of Technical Standards (ABNT) published ABNT PR 2030 ESG in December 2022, which sought to standardise the metrics and guidelines for reporting ESG information. The ‘Recommended Practice’ is the world’s first national ESG standard and is one of the baselines for creating the first global ESG standard, which is currently being applied by the International Organization for Standardization (ISO).
Several regulatory agencies in Brazil have issued rules on ESG reporting. Financial institutions must follow the rules issued by Brazil’s Central Bank (BACEN). Issuers of bonds and securities must include ESG information in their annual report or reference form, pursuant to Brazil’s Securities and Exchange Commission (CVM) and the Official Stock Exchange (B3) regulations and guides. Finally, insurance companies, open complementary pension fund entities, capitalisation companies and local reinsurers are also under scrutiny for sustainability reporting pursuant to the Superintendence of Private Insurance (SUSEP)norms, among others.
Significant specific ESG-related terms have also been addressed by Brazilian regulators to mitigate occurrences of greenwashing or social washing. For example, the use and definition of terms such as ‘green’, ‘social’, ‘sustainable’and ‘ESG’, among others, and the parameters for such use, have been established by the National Council of Self-Regulation in Advertisement (CONAR), through the Brazilian Code of Self-Regulation in Advertisement, by CVM, through CVM rules, and by the Brazilian Association of Financial and Capital Market Entities (ANBIMA).
Continue reading.
1 note
·
View note
Text
5 Skills Needed to Become a Prompt Engineer

There is a critical role in artificial intelligence that has gained prominence with the advent of powerful language models such as GPT-3.5. Meet the prompt engineer: the creative minds behind the scenes who create the instructions or prompts that entice these language models to respond meaningfully. Their role, however, goes beyond mere interaction; it entails shaping and fine-tuning the behavior of these cutting-edge AI models to suit specific applications and contexts.
To learn how to become an prompt engineer, you must first acquire a set of fundamental skills. Join us as we delve into the six key skills you'll need to master in order to excel in the realm of prompt engineering, where every prompt is a gateway to unlocking AI's potential. As an added bonus, learn how Blockchain Council's specialized prompt engineer course and prompt engineer certification can help you advance in this ever-changing field.
5 Qualities of a Prompt Engineer
Let's dive into the fundamental skills required of aspiring Prompt Engineers. These abilities will serve as the foundation for your exploration of the enthralling worlds of natural language processing (NLP) and artificial intelligence (AI).
Programming Abilities
Knowledge of programming languages, particularly Python, is required. As a Prompt Engineer, you'll write code that interacts with NLP models, modifies their behavior, and integrates them seamlessly into applications. Python is the language of choice for NLP tasks due to its extensive libraries and frameworks.
NLP (Natural Language Processing)
Prompt engineering is based on a thorough understanding of NLP. You must be familiar with the complexities of NLP concepts, techniques, and libraries. Tokenization (breaking text into words or phrases), part-of-speech tagging (assigning grammatical tags to words), named entity recognition (identifying entities like names of people or places), sentiment analysis (determining the sentiment expressed in text, e.g., positive or negative), and other skills are required. NLP is essential for making language models understand and generate text that is human-like.
Learning by Machine
It is essential to be familiar with machine learning principles and algorithms. Machine learning techniques are commonly used in AI models, including NLP models. You should understand supervised learning (training models on labeled data), unsupervised learning (finding patterns in unlabeled data), and neural networks (the building blocks of deep learning). These concepts serve as the foundation for NLP models.
Extensive Learning
Deep learning is a subset of machine learning that deals with multi-layer neural networks. Understanding deep learning frameworks such as TensorFlow and PyTorch is essential. As an AI Prompt Engineer, you'll be building and fine-tuning language models using deep neural networks. Deep learning equips models with the ability to process and comprehend language at a nuanced level.
Preparing Data
The ability to clean and pre-process large datasets is crucial in NLP. It is your responsibility to make raw data usable because it is frequently noisy and inconsistent. Data pre-processing entails tasks such as data cleaning (removing errors or outliers), text normalization (standardizing text, for example, converting "USA" to "United States of America"), and feature extraction (finding relevant features in text data). Data pre-processing that is effective lays the groundwork for accurate and meaningful interactions with language models.
When you master these skills, you will be able to excel as a Prompt Engineer, able to create precise instructions that unleash the full potential of AI language models in a variety of applications.
Consider enrolling in Blockchain Council's comprehensive prompt engineering certification course to start on this rewarding journey.
The Blockchain Council provides a quick engineering certification for those who want to excel in fields like AI, NLP, and data science. Their expertly crafted prompt engineer course and AI Certification cover the intricacies of programming, natural language processing (NLP), machine learning, deep learning, and data pre-processing.
By enrolling in Blockchain Council's prompt engineer course and certification, you gain access to a wealth of industry insights, hands-on experience, and certifications that validate your proficiency in these critical domains. With this solid foundation, you'll be well-prepared to write precise instructions and fully unleash the potential of AI language models, making a significant contribution to the ever-changing world of technology and artificial intelligence.
Conclusion
Finally, the importance of a Prompt Engineer in artificial intelligence and natural language processing cannot be overstated. To excel in this profession and make a significant contribution to the development and optimization of AI language models, a set of essential skills must be acquired and mastered.
These skills, which range from programming proficiency to a thorough understanding of NLP, machine learning, deep learning, and data pre-processing, are essential for any aspiring Prompt Engineer. You can become a competent Prompt Engineer with hard work and the right educational resources.
The Blockchain Council's comprehensive prompt engineer course and prompt engineer certification provide an excellent opportunity to not only learn these critical skills but also to obtain industry-recognized certifications. By taking these courses, you will be able to improve your knowledge, practical expertise, and professional credibility in the fields of AI and NLP.
So, whether you're starting out as a Prompt Engineer or looking to hone your skills, keep in mind that the road to success begins with education and continuous learning. In a rapidly changing technological landscape, seize the opportunity to master these skills and realize the full potential of AI language models. Your journey to greatness begins right now.
0 notes
Text
Choosing the Right .NET Training Program: A Comprehensive Guide
In today's technology-driven world, staying up-to-date with the latest programming languages and frameworks is essential for career growth and professional development. One such framework that has gained immense popularity is .NET, developed by Microsoft. If you're looking to enhance your skills in .NET, choosing the right training program is crucial. In this comprehensive guide, we'll explore the key factors to consider when selecting a .NET training program, ensuring that you make an informed decision and ultimately earn your dot net certification.
Understanding .NET: A Brief Overview
Before delving into how to choose the right training program, let's briefly understand what .NET is. .NET is a versatile and powerful framework developed by Microsoft for building various types of applications, including web, desktop, mobile, and cloud-based applications. It supports multiple programming languages, including C#, F#, and Visual Basic, making it a go-to choice for developers worldwide.
Why Pursue a .NET Certification?
Before you commit to a training program, it's important to understand why obtaining a .NET certification is beneficial. Here are some compelling reasons:
Career Advancement: A .NET certification can open doors to new job opportunities and career growth. Many employers prefer certified professionals as they tend to have a deeper understanding of the framework.
Skill Validation: Earning a certification validates your skills and knowledge in .NET, giving you confidence in your abilities and showcasing your expertise to potential employers or clients.
Stay Updated: The technology industry evolves rapidly. Pursuing certification ensures you stay current with the latest developments in .NET, which is critical for long-term success in this field.
Networking Opportunities: Certification programs often provide opportunities to connect with other professionals in the field, allowing you to build a valuable network.
Now that we've established the importance of a .NET certification, let's dive into the key considerations for selecting the right training program.
1. Accreditation and Recognition
The first step in choosing a .NET training program is to ensure that it is accredited and recognized. Look for programs offered by reputable institutions, universities, or organizations with a strong track record in providing quality technical education. Microsoft itself offers a range of official certification programs, which are widely recognized and respected in the industry.
2. Course Content
The content of the training program is paramount. It should cover a comprehensive range of topics related to .NET development. This includes fundamentals such as C# programming, .NET architecture, and database integration, as well as more advanced topics like ASP.NET, Entity Framework, and cloud services integration. Ensure that the program aligns with your specific learning goals and career aspirations.
3. Practical Experience
Theory is important, but hands-on experience is equally crucial when learning .NET. Look for training programs that offer practical exercises, coding projects, and real-world examples. The opportunity to apply what you've learned in a practical context will solidify your understanding and skills.
4. Instructor Quality
The quality of instructors can significantly impact your learning experience. Instructors should be experienced professionals with in-depth knowledge of .NET. Check if the instructors are Microsoft-certified themselves, as this demonstrates their expertise in the subject matter. You may also want to read reviews or seek recommendations from past students to gauge the quality of instruction.
5. Flexibility
Consider your own schedule and preferences. Some training programs are offered in a traditional classroom setting, while others are available online. Online courses often provide greater flexibility, allowing you to learn at your own pace and fit your studies around your existing commitments. Choose a format that suits your lifestyle and learning style.
6. Certification Exam Preparation
A good training program should prepare you thoroughly for the certification exam. Inquire about the program's success rate in terms of students passing the certification exam. Additionally, check if they offer practice exams, study materials, and guidance on exam registration.
7. Cost and Financial Aid
Cost is an important factor to consider. Research the tuition fees for the program and compare them to your budget. Some training programs offer financial aid or scholarships, so explore these options if cost is a concern. Keep in mind that investing in your education is an investment in your future career.
8. Alumni Success
Find out what former students of the program have achieved after completing their .NET certification. Alumni success stories can provide insights into the program's effectiveness in helping individuals advance their careers.
9. Industry Reputation
Research the reputation of the training program within the industry. Do employers value certifications from this program? Are there success stories of individuals who have graduated from this program and gone on to work for reputable companies? A program with a strong industry reputation can boost your job prospects.
10. Continuing Education
Finally, consider whether the training program offers opportunities for continuing education. Technology is constantly evolving, so it's essential to stay updated. Some programs may offer advanced courses or resources for keeping your skills current.
Conclusion
Choosing the right .NET training program is a significant decision that can greatly impact your career in software development. Take the time to research and evaluate your options, considering factors such as accreditation, course content, practical experience, instructor quality, flexibility, exam preparation, cost, alumni success, industry reputation, and continuing education opportunities. By carefully assessing these elements, you'll be well on your way to selecting a program that not only prepares you for your dot net certification but also equips you with the skills and knowledge needed to excel in the dynamic world of .NET development. Remember, investing in your education is an investment in your future success.
If you are searching for a .NET testing training institute then CRBtech is the best corporate training institute in Pune. It has focused on training candidates in IT, Mechanical, Electrical,Civil and Clinical Research. It helps students to start their career journey with a good beginning in the industry.
0 notes
Text
Harnessing Artificial Intelligence in WordPress Plugin Development
Hello developers! It's time to level up your WordPress plugin game with some cutting-edge tech. As we all know, Artificial Intelligence (AI) has taken the world by storm, and it's not just limited to self-driving cars and smart assistants. Now, AI is making its way into the world of WordPress plugins, revolutionizing the way we interact with websites. In this blog, we'll dive into the exciting world of AI and explore how you can harness its power to create mind-blowing WordPress plugins. Let's get started!
First things first, what exactly is AI? It's like having a super-smart assistant who can learn from data and make decisions on their own. In the WordPress world, AI can be a game-changer. Imagine having a plugin that understands user preferences, anticipates their needs, and serves up personalized content. Again, AI is a vast field with various technologies at your disposal. For plugin development, you might want to explore machine learning, natural language processing (NLP), and computer vision. These technologies can supercharge your plugins and create mind-boggling functionalities. Now let’s delve into the topic!
Building AI-Powered WordPress Plugins
Setting up the Development Environment
To kick things off, set up your development environment for AI-powered plugin magic. Make sure you have the right libraries and frameworks installed. Here's a quick example using Python:
pip install tensorflow
pip install scikit-learn
Integrating Machine Learning
Machine learning can bring your plugins to life by predicting user behavior or analyzing data patterns. Here's a code snippet using scikit-learn to create a plugin that recommends personalized products based on user history.:
from sklearn.neighbors import KNeighborsClassifier
# Load user data and product history
X_train, y_train = load_user_data()
X_test = load_product_history()
# Train the model
model = KNeighborsClassifier(n_neighbors=3)
model.fit(X_train, y_train)
# Make predictions
predictions = model.predict(X_test)
Implementing Natural Language Processing
NLP opens up a world of possibilities for language-based plugins. Think chatbots or sentiment analysis tools. Check out this NLP example using the Natural Language Toolkit (NLTK) in Python:
import nltk
# Sample text
text = "Hey, how can I assist you today?"
# Tokenize the text
tokens = nltk.word_tokenize(text)
# Part-of-speech tagging
pos_tags = nltk.pos_tag(tokens)
# Named Entity Recognition
ner_tags = nltk.ne_chunk(pos_tags)
Enhancing User Experience with Computer Vision
If your plugin deals with images, computer vision is your go-to technology. Enhance visual content and analyze images with ease. Here's a taste of OpenCV in Python:
import cv2
# Load the image
image = cv2.imread('image.jpg')
# Convert to grayscale
gray_image = cv2.cvtColor(image, cv2.COLOR_BGR2GRAY)
# Apply edge detection
edges = cv2.Canny(gray_image, 100, 200)
Optimizing Performance and Scalability
AI-powered plugins can be resource-intensive. Optimize your code to ensure lightning-fast performance and scalability. Consider using cloud services for heavy computations and caching mechanisms for quicker responses.
Ensuring Security and Data Privacy
With great power comes great responsibility. Protect AI models and user data with robust security measures. Comply with GDPR for data privacy.
Testing and Debugging AI-Powered Plugins
Test, test, and test some more! AI introduces complexity, so be thorough in testing and debugging. Tools like TensorBoard and unit testing frameworks will be your best friends. Take a look at some real-world AI-powered WordPress plugins. Jetpack's "Related Posts" feature uses AI to suggest relevant content, while Akismet uses machine learning to combat spam.
AI is no longer science fiction; it's a reality that's changing the face of WordPress plugin development. As developers, you have the power to create mind-blowing experiences with AI. So, embrace the tech, experiment fearlessly, and let your imagination run wild. The future of WordPress plugins is in your hands! Happy coding! To know more visit us at https://magnigeeks.com/
0 notes
Text
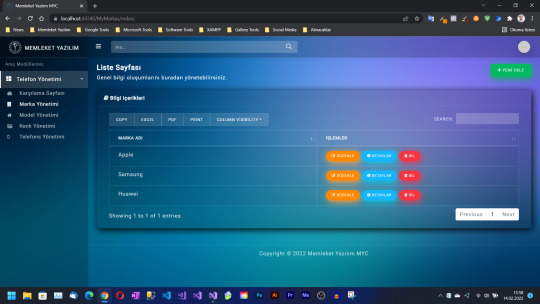
MVC Controller With Views Using Entity Framework Kullanımı
MVC Controller With Views Using Entity Framework Kullanımı
Visual Studio’yu açın ve C# ASP.NET web uygulaması (.NET Framework) şablonunu kullanarak bir Web projesi oluşturun. Ve daha sonra videodaki yolları takip edin. Memleket Yazılım bir yazılım şirketidir. Yazılım alanında faaliyet göstermekte ve aynı zamanda da dünya çapında teknoloji, inceleme ve bilgilendirme gibi diğer kategorilerde toplum kamu oyunu bilgilendirmekteyiz. Bizi Takipte Kal��n…
View On WordPress
#ASP. NET MVC Entity Framework connection string#ASP.NET MVC Entity Framework Database First#asp.net mvc entity framework kullanımı#asp.net mvc entity framework veritabanı işlemleri#Entity Framework Code First Example#Entity Framework Code First Migration#Entity Framework Code First nedir#Entity Framework Database First Update Model#Hüseyin Demirdöğer#MVC Controller With Views Using Entity Framework#MVC Controller With Views Using Entity Framework Kullanımı
0 notes
Text

Sketchnoting Dive into RealityKit 2
by Ethan Saadia
The first session I watched today at WWDC 2021 was Dive into RealityKit 2, an overview of the updates to Apple’s newest augmented reality framework. At WWDC Community Week, GoodNotes highlighted sketchnoting in a tutorial session, so I thought I’d give this format a try and provide a quick visualization of the new updates. I’ve been writing RealityKit tutorials since its initial release at WWDC 2019 with my series RealityKit Snippets, and its been my 3D graphics framework of choice since then for AR apps.
Custom Shaders & Meshes
RealityKit 2 brings the framework to the next level with custom shaders and meshes, features that let developers customize materials and graphics and generate 3D shapes/content on the fly. This includes the steaming pizzas and confetti that Apple highlighted at the Keynote on Monday. While RealityKit remains a high-level and approachable framework to use, the new customization options provide control over content that used to require SceneKit or Metal.
Faces
With the new mesh features, you can access face meshes from the TrueDepth camera and modify the materials and texture. For example, the session showed off a face painting app with glitter. This feature will be great for AR photo filters that need to place content that fits to the face's shape.
Audio
Spatial Audio also received as mention, with a new AudioBufferResource that lets you create spatial-aware sounds dynamically instead of loading from a static file.
Materials
I've been waiting for transparent materials in AR for over three years, and I'm so excited that it's finally here! Image and video textures can now include alpha channels, so 2D content can have irregular borders. Going along with the theme of customization, RealityKit 2 provides full control over physically based materials from the USD format.
Entity-Component System
The session also highlighted updates to the Entity-Component System, the architecture that RealityKit apps follow to organize apps. The session introduced Systems, a way to control 3D models, listen for updates, and coordinate events. EntityQuery is a new way to search a scene for entities with specified components, a great task for a System to manage.
The session encouraged developers to include all state and properties for objects in Components instead of subclassing Entity. Entity should be used a container of components with an identifier, so all information about the appearance, animation, behaviors, and other state should belong in components.
Animation
It is now possible to blend multiple animations together, adjust the speed, and work with animation timelines. Again, it will be easier to tailor animations beyond what a USDZ already contains.
Character Controller
Leveraging a 3D reconstruction of the world from the LiDAR on iPad Pro and iPhone 12 Pro, Scene Understanding makes AR experiences even more realistic by allowing virtual content to collide with and be occluded by the real world. In my NSSpain 2020 presentation, I built an AR racing game with Scene Understanding.
New this year, a Character Controller makes it easier to work with user-controlled objects. Simply define a CapsuleShape that takes the shape and size of the 3D model to detect collisions with the world around you. Then you can call the move(to:) method to have the character navigate around real obstacles on its way to the final destination. Or, if you'd prefer a more direct path, teleport(to:) will move the object without paying attention to objects in the way.
That is all the major announcements included in the Dive into RealityKit 2 session! I will be writing more about the new sessions later this week, which will go into more detail about these new features.
#wwdc#WWDC 2021#wwdc21#augmented reality#ar#ios#Apple#iOS 15#technology#LiDAR#iPad#iPhone#games#game development#animation#blender#rendering#3d modeling#3d
8 notes
·
View notes
Text
Implementation of blockchain technology in India by NITI Aayog:
As I was trying to understand how blockchain works, its pros, its cons, how the blockchain would cause a big impact on the governance sector or area and in doing so I came across a ‘discussion paper’ published by NITI Aayog called “ Blockchain : The India Strategy - Towards Enabling Ease of Business, Ease of Living and Ease of Governance” where they discuss the basic functionality of blockchain ( how much ever they are aware of the spectrum of it ) and how this blockchain technology could help in cutting down the ‘physical intermediaries’ to reduce the time of implementation of work or increase efficiency thereby increasing productivity and getting rid of the cumbersome process as much as possible. In order to do so they had to conduct pilots in selected sectors where blockchain technology can be applied and also come up with specific use cases that are applicable in the Indian scenario.
The paper goes on to explain how there is a need for ‘trust’ in the day to day transactions and that this blockchain technology takes that into consideration and proves to be much more transparent and credible. Blockchain is referred to as a representative of intermediaries - code as a trusted intermediary. This can be done by encoding the rules of the game as computer programs by allowing different entities with differing interests to collaborate on an immutable ledger.
Explaining how these fundamental features can be viewed as generic features:

This strategy paper is the first of two parts:
The Part 1 introduces the concept of blockchain and establishes how blockchain can redefine ‘trust’. It also defines the potential use causes and the lessons from NITI Aayog’s pilots in the area. The Part 2 which will be released soon will cover the specific recommendations that can enable the growth of a blockchain ecosystem in India. The part 1 of the paper also explains in a very simple way the framework for how the use case situation is selected with the available knowledge of the blockchain technology as it raises a few constraints.

There is also a part where the reasons for which blockchain technology is a better option than traditional methods of data collection / recording is listed out too. For example, blockchain technology could drastically change the agricultural sector by revamping the utility of eNAM by creating an audit trial of all farmer produce and removing the mistrust between farmers and arhatiyas (mandi intermediaries).
Overall what I think is that this is a brilliant technology and it definitely has the potential to transform the governance game completely but there are a few cons one of which is a major one (I.e) the impact that this technology has on the environment. Blockchain technology is just a means to a simpler future, it is not the end.
You can write to me on [email protected]
#business#education#news#niti aayog#bitcoin#blockchain#blockchain india#student#governance#corporate governance#climate change
3 notes
·
View notes