#Hardware Security Solution
Explore tagged Tumblr posts
Text
Why On-Premises Hardware Security Modules (HSMs) Are Essential for Protecting Encryption Keys
0 notes
Text
Setting Up an IRC Server for Secure Communication in a Future Insurrection
By WPS News Technical ReporterBaybay City | January 20, 2025 In an era marked by digital surveillance and control exerted by technology moguls, the need for independent communication platforms has never been more vital. As social movements and grassroots organizations rise to challenge existing power structures, the requirement for secure channels of communication is paramount. One viable…
#BayBay City#clean communication#communication platform#dedicated IP line#digital privacy#digital surveillance#domain registration#future insurrection#independent communication#internet freedom#internet service providers#IRC server#IT expertise#online security#secure communication#server hardware#tech independence#tech solutions#technology moguls#virtual private server
0 notes
Text
Exploring the Future of Hardware Wallets
The hardware wallet industry is booming, and one brand that stands out is ELLIPAL. Known for its innovative approach to cryptocurrency security, ELLIPAL offers a unique solution to safeguard digital assets. Their latest product is designed to provide users with a seamless experience while ensuring the highest level of protection for their cryptocurrencies.
With features like air-gapped technology and a user-friendly interface, ELLIPAL is making it easier for both beginners and experienced users to manage their digital currencies. The product not only prioritizes security but also emphasizes convenience, making it a fantastic choice for anyone looking to invest in cryptocurrencies.
As the demand for secure storage solutions continues to grow, ELLIPAL is at the forefront, proving that innovation and security can go hand in hand. Embrace the future of digital asset management with ELLIPAL and enjoy peace of mind knowing your investments are safe.
#digital currencies#secure storage solutions#digital asset management#ELLIPAL#hardware wallets#user-friendly#air-gapped technology
0 notes
Text
youtube
Microchip: Introducing the New 32-bit dsPIC33A DSC
https://www.futureelectronics.com/resources/featured-products/microchip-dspic33a-digital-signal-controllers-dsc . Discover the future of industrial automation, sustainable solutions and automotive systems with the dsPIC33A family of 32-bit Digital Signal Controllers (DSCs). To meet complex embedded, real-time control demands, dsPIC33A DSCs feature an advanced instruction set architecture and a powerful 200 MHz CPU. https://youtu.be/7R5WlMz94ow
#future electronics#WT#Microchip#dsPIC33A#32-bitDSC#Digital Signal Controller#Embedded Systems#Real Time Control#Industrial Automation#Hardware Security#CPU200MHz#System Efficiency#Sustainable Solutions#Youtube
1 note
·
View note
Text
dahabminers.com
#Bitcoin Mining#Cryptocurrency Mining#Blockchain Technology#Mining Hardware#ASIC Miners#GPU Mining#Mining Profitability#Renewable Energy for Mining#Crypto Economics#Decentralization#Mining Pools#Hashrate#Mining Algorithms#Proof of Work (PoW)#Bitcoin Economics#Crypto Market Trends#Mining Challenges#Green Energy Solutions#Mining Security#Crypto Regulatory News
0 notes
Text
TrueNAS SCALE Server Build for Home Lab
TrueNAS SCALE Server Build for Home Lab #homelab #virtualization #TrueNASSCALEHomeServer #HomeServerSetup #DebianLinuxServer #RAIDConfiguration #FileSharingServer #MediaStreamingServer #HomeAutomationHub #NetworkSecurity #ServerHardwareUpgrades #selfhost
There are so many options for running a home server for storage and virtualization needs on a home network. I have run VMware ESXi and Proxmox servers for my virtualization needs for the past few years now. However, until recently, I only ran TrueNAS inside a virtual machine for testing and a few light-duty applications. A project I wanted to tackle was repurposing one of my SuperMicro mini…

View On WordPress
#cost-effective server solution#Debian Linux server#file sharing server#home automation hub#Home Server Setup#media streaming server#network security#RAID configuration#server hardware upgrades#TrueNAS SCALE home server
0 notes
Text
Overcoming Common Challenges in SharePoint Server Installation
SharePoint Server, a powerful collaboration and content management platform, provides organizations with robust functionalities. However, the installation process can present various challenges that may hinder a seamless deployment. In this article, we will explore common issues faced during SharePoint Server installation and provide probable solutions to overcome them. “The tool was unable to…

View On WordPress
#Access Privileges#Application Services Configuration#Central Administration#Collation Settings#Configuration Database#Database Connectivity#Deployment Challenges#Disk Space#Firewall Interference#Hardware Requirements#Installation Issues#Internet Connectivity#Memory Exception#Probable Solutions#Secure Store Service Application#Service Account#SharePoint Prerequisites#SharePoint Search Service#SharePoint Server#SharePoint Timer Service#SQL Server Permissions#Troubleshooting#User Profile Service Application#Windows Features
0 notes
Text
Have YOU got an old Windows PC Microsoft has told you can't run Windows 11? It's time to give it a new life!
How to install Windows 11 on unsupported PC Hardware using Rufus. You can also disable some other Windows 11 bullshit like data harvesting and needing a Microsoft account.
It has been in the news a lot lately that Windows 11 isn't allowed to be installed on PCs without certain requirements, including the TPM 2.0, a chip that was only included in PCs made in 2018 or later. This means that once Windows 10 stops receiving security updates, those PCs will not be able to (officially) run a safe, updated version of Windows anymore. This has led to an estimated 240 million PCs bound for the landfill. Thanks Microsoft! I get you don't want to be seen as the insecure one, but creating this much waste can't be the solution.
(I know nerds, Linux is a thing. I love you but we are not having that conversation. If you want to use Linux on an old PC you are already doing it and you don't need to tell me about it. People need Windows for all sorts of reasons that Linux won't cut.)
So lately I have been helping some under privileged teens get set up with PCs. Their school was giving away their old lab computers, and these kids would usually have no chance to afford even a basic computer. They had their hard drives pulled so I have been setting them up with SSDs, but the question was, what to do about the operating system? So I looked into it and I found out there IS actually a way to bypass Microsoft's system requirement and put Windows 11 on PCs as old as 2010.
You will need: Rufus: An open source ISO burning tool.
A Windows 11 ISO: Available from Microsoft.
A USB Flash Drive, at least 16GB.
A working PC to make the ISO, and a PC from 2018 or older you want to install Windows 11 on.
Here is the guide I used, but I will put it in my own words as well.
Download your Windows 11 ISO, and plug in your USB drive. It will be erased, so don't have anything valuable on it. Run Rufus, select your USB drive in the Device window, and select your Windows 11 ISO with the Select button. (There is supposed to be a feature in Rufus to download your ISO but I couldn't get it to work.?
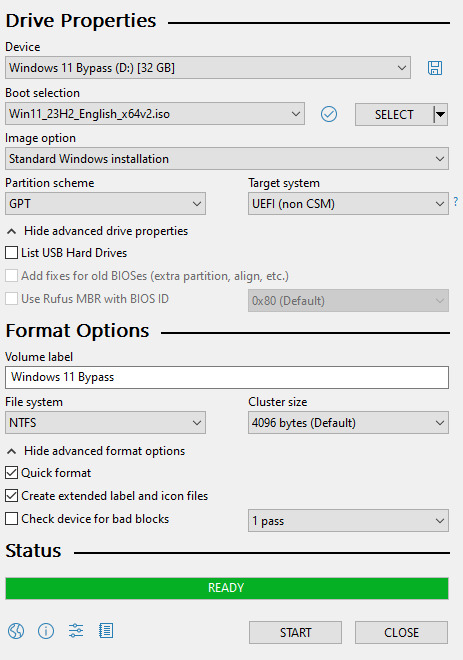
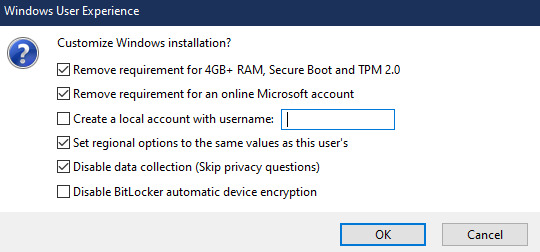
Choose standard windows installation, and follow the screenshot for your settings. Once you are done that, press Start, and then the magic happens. Another window pops up allowing you to remove the system requirements, the need for a microsoft account, and turn off data collecting. Just click the options you want, and press ok to write your iso to a drive.
From there you just need to use the USB drive to install windows. I won't go into details here, but here are some resources if you don't know how to do it.
Boot your PC from a USB Drive
Install Windows 11 from USB Drive
If you had a licensed copy of Windows 10, Windows 11 will already be licensed. If you don't, then perhaps you can use some kind of... Activation Scripts for Microsoft software, that will allow you to activate them. Of course I cannot link such tools here. So there you go, now you can save a PC made from before 2018 from the landfill, and maybe give it to a deserving teen in the process. The more we can extend the lives of technology and keep it out of the trash, the better.
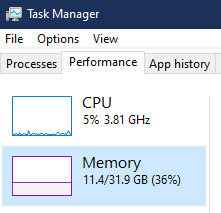
Additional note: This removes the requirement for having 4GB Minimum of RAM, but I think that requirement should honestly be higher. Windows 11 will be unusable slow on any system with below 8GB of RAM. 8GB is the minimum I think you should have before trying this but it still really not enough for modern use outside of light web and office work. I wouldn't recommend trying this on anything with 4GB or less. I am honestly shocked they are still selling brand new Windows 11 PCs with 4GB of ram. If you're not sure how much RAM you have, you can find out in the performance tab of Task Manager in Windows, if you click the More Details icon on the bottom right. If you don't have enough, RAM for old systems is super cheap and widely available so it would definitely be worth upgrading if you have a ram starved machine you'd like to give a new life.
#Windows#Windows 11#tech#tech advice#pc#TPM 2.0#rufus#open source#open source software#technology#tech tips
725 notes
·
View notes
Text
glancing through another slew of papers on deep learning recently and it's giving me the funny feeling that maybe Yudkowsky was right?? I mean old Yudkowsky-- wait, young Yudkowsky, baby Yudkowsky, back before he realised he didn't know how to implement AI and came up with the necessity for Friendly AI as cope *cough*
back in the day there was vague talk from singularity enthusiasts about how computers would get smarter and that super intelligence would naturally lead to them being super ethical and moral, because the smarter you get the more virtuous you get, right? and that's obviously a complicated claim to make for humans, but there was the sense that as intelligence increases beyond human levels it will converge on meaningful moral enlightenment, which is a nice idea, so that led to impatience to make computers smarter ASAP.
the pessimistic counterpoint to that optimistic idea was to note that ethics and intelligence are in fact unrelated, that supervillains exist, and that AI could appear in the form of a relentless monster that seeks to optimise a goal that may be at odds with human flourishing, like a "paperclip maximiser" that only cares about achieving the greatest possible production of paperclips and will casually destroy humanity if that's what is required to achieve it, which is a terrifying idea, so that led to the urgent belief in the need for "Friendly AI" whose goals would be certifiably aligned with what we want.
obviously that didn't go anywhere because we don't know what we want! and even if we do know what we want we don't know how to specify it, and even if we know how to specify it we don't know how to constrain an algorithm to follow it, and even if we have the algorithm we don't have a secure hardware substrate to run it on, and so on, it's broken all the way down, all is lost etc.
but then some bright sparks invented LLMs and fed them everything humans have ever written until they could accurately imitate it and then constrained their output with reinforcement learning based on human feedback so they didn't imitate psychopaths or trolls and-- it mostly seems to work? they actually do a pretty good job of acting as oracles for human desire, like if you had an infinitely powerful but naive optimiser it could ask ChatGPT "would the humans like this outcome?" and get a pretty reliable answer, or at least ChatGPT can answer this question far better than most humans can (not a fair test as most humans are insane, but still).
even more encouragingly though, there do seem to be early signs that there could be a coherent kernel of human morality that is "simple" in the good sense: that it occupies a large volume of the search space such that if you train a network on enough data you are almost guaranteed to find it and arrive at a general solution, and not do the usual human thing of parroting a few stock answers but fail to generalise those into principles that get rigorously applied to every situation, for example:
the idea that AI would just pick up what we wanted it to do (or what our sufficiently smart alter egos would have wanted) sounded absurdly optimistic in the past, but perhaps that was naive: human cognition is "simple" in some sense, and much of the complexity is there to support um bad stuff; maybe it's really not a stretch to imagine that our phones can be more enlightened than we are, the only question is how badly are we going to react to the machines telling us to do better.
39 notes
·
View notes
Text
Hi there’s a tornado in my area rn but I’m spiteful like that. Random tsams/eaps headcanons be upon ye
Ruin still does those little audio log diaries. It helps manage his overflowing memory storage (read: old age = more memories to store) without compressing data files.
Bloodmoon sleeps with dog toys. Otherwise, they’d probably chew through whatever bedding material they had chosen that night. This was Ruin’s idea.
Eclipse can’t sleep with lights on in a room. Ruin can’t sleep without a light. The makeshift solution is a sleeping mask for Eclipse, but their actual compromise is a star projector.
Eclipse has to know where everyone is most of the time, especially after Charlie came into the picture. This is usually done with cameras and tracking via fazbear systems, but it’s an issue he has to work on, as it’s just a method to make him feel better about security now that there are people he cares about. At least one person has commented on there being a new nightguard.
Dark sun finds thrillers tacky, and prefers thought-provoking mysteries, bonus points for romance.
Most of them carry some kind of sanitizing wipe packet. For daycare attendants, these are for sticky messes and children. For those more familiar with tools, these are for tougher grime and are not suitable for sensitive (children’s) skin. Solar has both.
The eclipses (Eclipse, Solar, Ruin) are the most prone to damaging their rays. Eclipse sometimes hits doorways and doesn’t bother to fix cracked rays. Ruin is small enough for humans to reach his head. Solar peels the paint off of his. All three will pull or squeeze their rays in times of extreme stress, to varying degrees. Lunar is an exception for lack of rays. (Similarly, Sun fidgets with his rays, which is the source of this trait.)
While there are exceptions, Suns prefer tactile stimulation, Moons auditory, and Eclipses have no strong preference. Earth likes social interaction.
Animatronics have personalized UI that makes sense to them, which serves as their access point to their internal folders, like memory files, downloaded items, and executable programs. Bots that share an operating system/“brain” have the same UI. Diagnostics, software updates, and safety modes all require additional hardware (computers, parts and service devices, fazwrenches) to complete. Mindscapes are in AI chips, and multiple AIs in one mindscape happen when multiple AIs share the same operating system. Visual feed can be projected onto other screens with HDMI cables and vice versa, which can sometimes show that bot’s UI depending on what it is. For a more direct example of this think of the battery and blue borders you see in Security breach when Gregory is hiding inside Freddy.
Safety mode disconnects that bot from the Fazbear Ent. local network, meaning no tracking, no communication via local networks (which generally aren’t private anyway, most bots with access to phones prefer those), and no access to files that aren’t stored in that bot’s drive. This is meant to isolate a bot’s systems from the main network in case of a security breach (hah), make transportation of bots between locations easier, and make maintenance a smoother affair as there is no outside interference during the process. For the bots themselves, this is the equivalent of turning off your phone and going outside I mean focusing only on what’s in front of you instead of what’s going on in your area/social network. It’s possible to be stuck in safety mode. Depending on how much of a bot’s system relies on Fazbear Ent. Networks to function (such as a bot’s memory being stored in a Cloud, which is also ill advised between the bots themselves,) this can be mean a temporary personality/memory reset until those files get reconnected again. Bots do not need to be connected to the Fazbear ent networks to function, but it generally makes access to software updates easier due to being recognized as a company entity. It is possible for a private network to exist, but it’s considered foreign by Fazbear systems and can be more trouble than they’re worth. Moon and Eclipse have private networks shared with close friends and family for different purposes. Moon’s is mostly for emergency backups, and Eclipse’s is for security.
Animatronic’s memories are stored in the hard drives in their bodies. It’s possible to offload memory files into networks (Cloud) or external storage systems. If another bot had access to these clouds or external storages, they could experience the memories stored in them. Memory files include visual and auditory data, like a movie. AI/personality chips are the equivalent of a soul in that the AI is the product of a learning AI having experienced environments that supplied them information about the world AKA an Ai that developed a personality beyond their base programming, but they do not carry memories. For example, Eclipse V3-V4 is an Eclipse AI given incomplete memories, creating a disconnect in the AI’s learned behaviors and what it perceives as the source of that behavior, resulting in an incomplete backup. Backups are static/unchanging copies of integral memory files and the accompanying AI (As is in the moment that they are backed up.) Backups need to be updated as the animatronic it’s for develops.
#go easy on me I only have basic knowledge of computer stuff#quirky headcanons#tsams#eaps#I’m also halfway through a sociology class so take the AI one with a grain of salt#hopefully this makes sense
25 notes
·
View notes
Text
HSM Provider in India

What Are Hardware Security Modules?
Hardware Security Modules (HSMs) are specialized devices designed to safeguard sensitive data and manage cryptographic keys. They serve as dedicated security tools that ensure the security, confidentiality, and integrity of critical information in various digital systems.
The primary function of HSMs revolves around the secure generation, storage, and utilization of cryptographic keys used in encryption, decryption, digital signatures, and other cryptographic operations. These modules are hardware-based, providing a secure and tamper-resistant environment for key management and cryptographic processes.
HSMs are equipped with robust security mechanisms, including tamper-evident coatings, secure enclosures, and physical protections, to prevent unauthorized access and protect against attacks. They ensure that cryptographic keys remain confidential, preventing their exposure to potential threats.
These devices are widely utilized across industries, including finance, healthcare, government, and more, where data security and compliance with stringent regulations are paramount. HSMs play a pivotal role in securing digital assets, ensuring data confidentiality, and mitigating the risks associated with unauthorized access or data breaches.
The Significance Of HSMs In Modern Security
HSMs play a critical role in securing digital assets by offering a secure environment for key management and cryptographic operations, ensuring data integrity and confidentiality
Functionality Of HSMs
Encryption And Decryption Capabilities
HSMs employ sophisticated encryption techniques, ensuring data confidentiality by encoding sensitive information, rendering it inaccessible to unauthorized entities.
Secure Key Management
One of the primary functions of HSMs is secure generation, storage, and management of cryptographic keys, preventing unauthorized usage and potential breaches.
Applications Of HSMs Across Industries:
Financial Sector:HSMs play a vital role in the financial industry, securing transactions, protecting sensitive financial data, and ensuring the integrity of banking systems. They enable secure payment processing, cryptographic operations for secure communication, and compliance with financial regulations like PCI DSS.
Healthcare Industry:In healthcare, HSMs safeguard electronic health records (EHRs) and sensitive patient information. They assist in encryption, secure access control, and maintaining data confidentiality, ensuring compliance with healthcare regulations such as HIPAA.
Certificate Inspection:With a single click, scan all your TLS/SSL certificates for vulnerabilities and weak configurations to avoid a lapse in security. See analytics and reports about the health of your network at any given moment.
Certificate Remediation:When CertCentral finds an issue, you’ll get remediation suggestions with detailed answers to virtually any certificate problem. And if you ever need to revoke a certificate, it only takes one click.
Government and Public Sector:Government agencies use HSMs to protect classified information, secure government networks, and ensure the integrity of critical systems. These modules aid in securing sensitive data, ensuring confidentiality in communications, and compliance with stringent government regulations.
Telecommunications:HSMs play a role in securing communication networks, protecting sensitive data during transmissions, and ensuring secure connections between devices. They enable encryption of voice, data, and messaging services in telecommunications.
Manufacturing and Industrial Control Systems:In industrial settings, HSMs are used to secure critical infrastructure, IoT devices, and control systems. They ensure the integrity and confidentiality of data in manufacturing processes, energy grids, and automated systems.
Cloud Service Providers:HSMs are integral in cloud environments, providing secure key management and encryption services. They enable encryption of data at rest and in transit, ensuring customer data remains confidential and protected within cloud infrastructures.
Retail and eCommerce:HSMs secure payment transactions, encrypt sensitive customer data, and facilitate secure connections between customers and online platforms. They assist in compliance with payment card industry standards, safeguarding financial data during online transactions.
Benefits Of Implementing Our Hardware Security Modules:
Enhanced Data Security:HSMs provide a robust layer of protection for sensitive data by encrypting information at rest and in transit. This encryption ensures that even if data is accessed, it remains unreadable and secure.
Protection Against Data Breaches:By securely managing cryptographic keys and enforcing strict access controls, HSMs significantly reduce the risk of data breaches. Unauthorized access to keys or sensitive information is thwarted, mitigating the impact of potential breaches.
Certificate Inspection:With a single click, scan all your TLS/SSL certificates for vulnerabilities and weak configurations to avoid a lapse in security. See analytics and reports about the health of your network at any given moment.
Regulatory Compliance:HSMs aid organizations in complying with various industry-specific regulations and standards such as GDPR, HIPAA, PCI DSS, and more. Their secure key management capabilities align with compliance requirements, avoiding potential penalties and legal implications.
Securing Transactions and Communications:In financial and communication sectors, HSMs enable secure transactions and communications by providing encryption, digital signatures, and authentication. This ensures the confidentiality and integrity of sensitive information during transmission.
Data Integrity and Authentication:HSMs contribute to ensuring the integrity of data and authenticating users or devices. They verify the authenticity of digital signatures and certificates, preventing data tampering or unauthorized modifications.
JNR Management is the Best HSM Provider in India
#HMS#hardware security Module#HSM in India#HSM in Delhi#HSM in Mumbai#HSM in Bangalore#HSM Provider in India#HSM Provider in Delhi#HSM Solution in Delhi#HSM Solution in India
0 notes
Text
Setting Up an IRC Server for Secure Communication in a Future Insurrection
By WPS News Technical ReporterBaybay City | January 20, 2025 In an era marked by digital surveillance and control exerted by technology moguls, the need for independent communication platforms has never been more vital. As social movements and grassroots organizations rise to challenge existing power structures, the requirement for secure channels of communication is paramount. One viable…
#BayBay City#clean communication#communication platform#dedicated IP line#digital privacy#digital surveillance#domain registration#future insurrection#independent communication#internet freedom#internet service providers#IRC server#IT expertise#online security#secure communication#server hardware#tech independence#tech solutions#technology moguls#virtual private server
0 notes
Text
It starts with him
What was once a promise of technology to allow us to automate and analyze the environments in our physical spaces is now a heap of broken ideas and broken products. Technology products have been deployed en masse, our personal data collected and sold without our consent, and then abandoned as soon as companies strip mined all the profit they thought they could wring out. And why not? They already have our money.
The Philips Hue, poster child of the smart home, used to work entirely on your local network. After all, do you really need to connect to the Internet to control the lights in your own house? Well you do now!Philips has announced it will require cloud accounts for all users—including users who had already purchased the hardware thinking they wouldn’t need an account (and the inevitable security breaches that come with it) to use their lights.
Will you really trust any promises from a company that unilaterally forces a change like this on you? Does the user actually benefit from any of this?
Matter in its current version … doesn’t really help resolve the key issue of the smart home, namely that most companies view smart homes as a way to sell more individual devices and generate recurring revenue.
It keeps happening. Stuff you bought isn’t yours because the company you bought it from can take away features and force you to do things you don’t want or need to do—ultimately because they want to make more money off of you. It’s frustrating, it’s exhausting, and it’s discouraging.
And it has stopped IoT for the rest of us in its tracks. Industrial IoT is doing great—data collection is the point for the customer. But the consumer electronics business model does not mesh with the expected lifespan of home products, and so enshittification began as soon as those first warranties ran out.
How can we reset the expectations we have of connected devices, so that they are again worthy of our trust and money? Before we can bring the promise back, we must deweaponize the technology.
Guidelines for the hardware producer
What we can do as engineers and business owners is make sure the stuff we’re building can’t be wielded as a lever against our own customers, and to show consumers how things could be. These are things we want consumers to expect and demand of manufacturers.
Control
Think local
Decouple
Open interfaces
Be a good citizen
1) Control over firmware updates.
You scream, “What about security updates!” But a company taking away a feature you use or requiring personal data for no reason is arguably a security flaw.
We were once outraged when intangible software products went from something that remained unchanging on your computer, to a cloud service, with all the ephemerality that term promises. Now they’re coming for our tangible possessions.
No one should be able to do this with hardware that you own. Breaking functionality is entirely what security updates are supposed to prevent! A better checklist for firmware updates:
Allow users to control when and what updates they want to apply.
Be thorough and clear as to what the update does and provide the ability to downgrade if needed.
Separate security updates from feature additions or changes.
Never force an update unless you are sure you want to accept (financial) responsibility for whatever you inadvertently break.
Consider that you are sending software updates to other people’s hardware. Ask them for permission (which includes respecting “no”) before touching their stuff!
2) Do less on the Internet.
A large part of the security issues with IoT products stem from the Internet connectivity itself. Any server in the cloud has an attack surface, and now that means your physical devices do.
The solution here is “do less”. All functionality should be local-only unless it has a really good reason to use the Internet. Remotely controlling your lights while in your own house does not require the cloud and certainly does not require an account with your personal information attached to it. Limit the use of the cloud to only the functions that cannot work without it.
As a bonus, less networked functionality means fewer maintenance costs for you.
3) Decouple products and services.
It’s fine to need a cloud service. But making a product that requires a specific cloud service is a guarantee that it can be enshittified at any point later on, with no alternative for the user owner.
Design products to be able to interact with other servers. You have sold someone hardware and now they own it, not you. They have a right to keep using it even if you shut down or break your servers. Allow them the ability to point their devices to another service. If you want them to use your service, make it worthwhile enough for them to choose you.
Finally, if your product has a heavy reliance on the cloud to work, consider enabling your users to self-host their own cloud tooling if they so desire. A lot of people are perfectly capable of doing this on their own and can help others do the same.
4) Use open and standard protocols and interfaces.
Most networked devices have no reason to use proprietary protocols, interfaces, and data formats. There are open standards with communities and software available for almost anything you could want to do. Re-inventing the wheel just wastes resources and makes it harder for users to keep using their stuff after you’re long gone. We did this with Twine, creating an encrypted protocol that minimized chatter, because we needed to squeeze battery life out of WiFi back when there weren’t good options.
If you do have a need for a proprietary protocol (and there are valid reasons to do so):
Document it.
If possible, have a fallback option that uses an open standard.
Provide tooling and software to interact with your custom protocols, at the very least enough for open source developers to be able to work with it. This goes for physical interfaces as much as it does for cloud protocols.
If the interface requires a custom-made, expensive, and/or hard-to-find tool to use, then consider using something else that is commonly available and off the shelf instead.
5) Be a good citizen.
Breaking paid-for functionality on other people’s stuff is inherently unethical. Consider not doing this! Enshittification is not a technical problem, it is a behavioral one. Offer better products that are designed to resist enshittification, and resist it yourself in everything you do.
Nothing forced Philips to do what they are doing: a human made a decision to do it. They could have just as easily chosen not to. With Twine’s server lock-in, at least we chose to keep it running, for 12 years now. Consider that you can still make a decent living by being honest and ethical towards the people who are, by purchasing your products, paying for your lifestyle.
We didn’t get here by accident. Humans made choices that brought us to this point, and we can’t blame anyone for being turned off by it. But we can choose to do better. We can design better stuff. And we can choose not to mess things up after the fact.
We’re putting this into practice with Pickup. (We also think that part of an IoT reset is giving users the creative freedom of a general-purpose device.) If you’re looking for something better and our product can fill a need you have, consider backing us. We cannot claim to be perfect or have all of the answers, but we are absolutely going to try. The status quo sucks. Let’s do something about it.
Published October 15, 2023 By Jeremy Billheimer
137 notes
·
View notes
Text
NEW DELHI (Reuters) -Global makers of surveillance gear have clashed with Indian regulators in recent weeks over contentious new security rules that require manufacturers of CCTV cameras to submit hardware, software and source code for assessment in government labs, official documents and company emails show.
The security-testing policy has sparked industry warnings of supply disruptions and added to a string of disputes between Prime Minister Narendra Modi's administration and foreign companies over regulatory issues and what some perceive as protectionism.
New Delhi's approach is driven in part by its alarm about China's sophisticated surveillance capabilities, according to a top Indian official involved in the policymaking. In 2021, Modi's then-junior IT minister told parliament that 1 million cameras in government institutions were from Chinese companies and there were vulnerabilities with video data transferred to servers abroad.
Under the new requirements applicable from April, manufacturers such as China's Hikvision, Xiaomi and Dahua, South Korea's Hanwha, and Motorola Solutions of the U.S. must submit cameras for testing by Indian government labs before they can sell them in the world's most populous nation. The policy applies to all internet-connected CCTV models made or imported since April 9.
"There's always an espionage risk," Gulshan Rai, India's cybersecurity chief from 2015 to 2019, told Reuters. "Anyone can operate and control internet-connected CCTV cameras sitting in an adverse location. They need to be robust and secure."
Indian officials met on April 3 with executives of 17 foreign and domestic makers of surveillance gear, including Hanwha, Motorola, Bosch, Honeywell and Xiaomi, where many of the manufacturers said they weren't ready to meet the certification rules and lobbied unsuccessfully for a delay, according to the official minutes.
In rejecting the request, the government said India's policy "addresses a genuine security issue" and must be enforced, the minutes show.
India said in December the CCTV rules, which do not single out any country by name, aimed to "enhance the quality and cybersecurity of surveillance systems in the country."
This report is based on a Reuters review of dozens of documents, including records of meetings and emails between manufacturers and Indian IT ministry officials, and interviews with six people familiar with India's drive to scrutinize the technology. The interactions haven't been previously reported.
Insufficient testing capacity, drawn-out factory inspections and government scrutiny of sensitive source code were among key issues camera makers said had delayed approvals and risked disrupting unspecified infrastructure and commercial projects.
"Millions of dollars will be lost from the industry, sending tremors through the market," Ajay Dubey, Hanwha's director for South Asia, told India's IT ministry in an email on April 9.
The IT ministry and most of the companies identified by Reuters didn't respond to requests for comment about the discussions and the impact of the testing policy. The ministry told the executives on April 3 that it may consider accrediting more testing labs.
Millions of CCTV cameras have been installed across Indian cities, offices and residential complexes in recent years to enhance security monitoring. New Delhi has more than 250,000 cameras, according to official data, mostly mounted on poles in key locations.
The rapid take-up is set to bolster India's surveillance camera market to $7 billion by 2030, from $3.5 billion last year, Counterpoint Research analyst Varun Gupta told Reuters.
China's Hikvision and Dahua account for 30% of the market, while India's CP Plus has a 48% share, Gupta said, adding that some 80% of all CCTV components are from China.
Hanwha, Motorola Solutions and Britain's Norden Communication told officials by email in April that just a fraction of the industry's 6,000 camera models had approvals under the new rules.
CHINA CONCERN
The U.S. in 2022 banned sales of Hikvision and Dahua equipment, citing national security risks. Britain and Australia have also restricted China-made devices.
Likewise, with CCTV cameras, India "has to ensure there are checks on what is used in these devices, what chips are going in," the senior Indian official told Reuters. "China is part of the concern."
China's state security laws require organizations to cooperate with intelligence work.
Reuters reported this month that unexplained communications equipment had been found in some Chinese solar power inverters by U.S. experts who examined the products.
Since 2020, when Indian and Chinese forces clashed at their border, India has banned dozens of Chinese-owned apps, including TikTok, on national security grounds. India also tightened foreign investment rules for countries with which it shares a land border.
The remote detonation of pagers in Lebanon last year, which Reuters reported was executed by Israeli operatives targeting Hezbollah, further galvanized Indian concerns about the potential abuse of tech devices and the need to quickly enforce testing of CCTV equipment, the senior Indian official said.
The camera-testing rules don't contain a clause about land borders.
But last month, China's Xiaomi said that when it applied for testing of CCTV devices, Indian officials told the company the assessment couldn't proceed because "internal guidelines" required Xiaomi to supply more registration details of two of its China-based contract manufacturers.
"The testing lab indicated that this requirement applies to applications originating from countries that share a land border with India," the company wrote in an April 24 email to the Indian agency that oversees lab testing.
Xiaomi didn't respond to Reuters queries, and the IT ministry didn't address questions about the company's account.
China's foreign ministry told Reuters it opposes the "generalization of the concept of national security to smear and suppress Chinese companies," and hoped India would provide a non-discriminatory environment for Chinese firms.
LAB TESTING, FACTORY VISITS
While CCTV equipment supplied to India's government has had to undergo testing since June 2024, the widening of the rules to all devices has raised the stakes.
The public sector accounts for 27% of CCTV demand in India, and enterprise clients, industry, hospitality firms and homes the remaining 73%, according to Counterpoint.
The rules require CCTV cameras to have tamper-proof enclosures, strong malware detection and encryption.
Companies need to run software tools to test source code and provide reports to government labs, two camera industry executives said.
The rules allow labs to ask for source code if companies are using proprietary communication protocols in devices, rather than standard ones like Wi-Fi. They also enable Indian officials to visit device makers abroad and inspect facilities for cyber vulnerabilities.
The Indian unit of China's Infinova told IT ministry officials last month the requirements were creating challenges.
"Expectations such as source code sharing, retesting post firmware upgrades, and multiple factory audits significantly impact internal timelines," Infinova sales executive Sumeet Chanana said in an email on April 10. Infinova didn't respond to Reuters questions.
The same day, Sanjeev Gulati, India director for Taiwan-based Vivotek, warned Indian officials that "All ongoing projects will go on halt." He told Reuters this month that Vivotek had submitted product applications and hoped "to get clearance soon."
The body that examines surveillance gear is India's Standardization Testing and Quality Certification Directorate, which comes under the IT ministry. The agency has 15 labs that can review 28 applications concurrently, according to data on its website that was removed after Reuters sent questions. Each application can include up to 10 models.
As of May 28, 342 applications for hundreds of models from various manufacturers were pending, official data showed. Of those, 237 were classified as new, with 142 lodged since the April 9 deadline.
Testing had been completed on 35 of those applications, including just one from a foreign company.
India's CP Plus told Reuters it had received clearance for its flagship cameras but several more models were awaiting certification.
Bosch said it too had submitted devices for testing, but asked that Indian authorities "allow business continuity" for those products until the process is completed.
When Reuters visited New Delhi's bustling Nehru Place electronics market last week, shelves were stacked with popular CCTV cameras from Hikvision, Dahua and CP Plus.
But Sagar Sharma said revenue at his CCTV retail shop had plunged about 50% this month from April because of the slow pace of government approvals for security cameras.
"It is not possible right now to cater to big orders," he said. "We have to survive with the stock we have."
7 notes
·
View notes
Text
USAID contract (2024)
Recipient: International Business Machines Corporation
Amount: $29,750,000
Purpose: The new cyber security activity will support host government and operators to develop and implement policies, procedures, and hardware/software solutions, as well as workforce development, aimed at improving prevention, protection, preparedness, resp...
Country: Albania
21 notes
·
View notes
Text
Tech Support
Fugitive!Luigi Series Part 4 1607w Action Adventure!

Summary: Luigi, Ben, and Mateo are asked to fix a communications issue between revolutionary groups in different cities. They have the expertise in CS to make it happen. It's selling it, that's the hard part.
Warnings: dialogue
December 6, 2024
The main meeting room smells like something that used to be alive and isn’t anymore. Maybe a rat. Maybe several rats..
It's a converted utility space, big enough for a long metal table, a few chairs, and a single, flickering overhead bulb that’s giving it its best shot. The walls are concrete, cracked in places, and the whole thing looks like it used to be a janitor’s break room before the world started ending. There’s a big dry-erase board on one wall, mostly blank except for a list of names and a crude map of the East Coast.
And across from us, the guys in charge.
There’s three of them, but only one who actually feels like the leader. Big guy, military stance, mid-40s, looks like he’s survived more than one close call. His name’s Darius.
The other two are Victor and Hassan. Victor looks like a construction worker. Broad shouldered, tattoos on his forearms, the kind of guy who probably knows how to use a blowtorch. Hassan’s leaner, quieter, but his eyes give him away. More than likely ex-military, maybe intel. The guy watches people too closely to be anything else.
Finally, Darius exhales, rubs a hand over his face. “Alright,” he says. “Fine. You’re here now. We need people. You stay, you work. You don’t like it, you leave. That simple.”
“Work,” I repeat.
“Yeah. And no offense but you three don’t exactly look like the manual labor type.”
I look at Mateo who looks at Ben who definitely looks offended by that statement.
“We have strengths in other areas.” Mateo throws in.
“Hopefully something we can use. There is one problem we’re trying to find a solution for.” he pauses, “maybe you could help us out.”
Now that gets my attention. I lean forward. “Go on.”
Darius exchanges a glance with Victor to his right, who nods slightly. Then he looks back at us. “We tried to set up communication with NYC a few days ago,” he says. “Didn’t go well. Whatever’s left of the internet… isn’t very safe. They got sloppy with communication and—“
“They got intercepted before they made it across the river. Two guys dead.” Hassan says flatly.
I glance at Mateo. He raises an eyebrow. Ben shifts uncomfortably.
“They must have been listening in,” says Hassan. “Tracking us somehow. We don’t know how deep they’ve got surveillance running, but if we keep trying to send runners, we’re just sending guys on a suicide mission.”
He’s right. Traditional communication methods are useless right now. The internet is barely functional, if at all. Anything digital is either monitored, unreliable, or both.
“So you need a better system,” I say.
Darius nods. “Yeah. Something secure. Something that can’t be intercepted.”
I can finally exhale, because I’ve already got a solution in mind.
Mateo, somehow, is already on the same page. He shifts forward, eyes bright. “You thinking what I’m thinking, Lou?”
“Probably.”
Darius squints. “You wanna let the rest of us in on it?”
I glance at Mateo. Mateo glances at me. Then he gestures, as if to say, go on, man.
I clear my throat.
“A mesh network,” I say. “A self-sustaining, decentralized communication system that doesn’t rely on ISPs, cell towers, or anything we don’t control. We set it up, and it’s ours. Government can’t shut it down, can’t intercept it without serious work. It lets us talk securely across cities, across states, without getting people killed in the process.”
“And you can build it?” Hassan asks.
I nod. “If I have the right hardware.”
“What kind of hardware?”
“Servers.���
Silence. I realize it isn’t ringing a bell.
I clarify, “Fancy computer parts.”
“And where do we get that?”
I'm trying not to smile. I lean forward.
“UPenn,” I say. “The CS department. The server room.”
Mateo lets out a low whistle. Ben blinks. Darius just watches me.
“It might already be looted,” Victor warns.
“Maybe,” I admit. “But if it’s not? We walk in, I pull together everything we need, and we roll out with the start of a functioning network.” Hassan looks at Darius. Darius looks back at him. Then he looks at me.
“…And you know where this server room is?”
I grin.
“Buddy,” I say, “I used to live in there.”
-------------------------------------------------
We take I-95 South, or what’s left of it.
Newark wasn’t exactly thriving, but Philly? Philly looks bad.
Newark at least had some essentials standing, and at least you could say the city blocks were intact structurally. I cannot say the same for Philly. Entire chunks of buildings look like they've had a big bite taken out of them.
There’s something about Philly… some kind of deep, ancestral commitment to destruction that makes the whole city feel like it’s always one bad day away from collapse. Theyre always smashing windows after an Eagles win or loss. There’s a general understanding this city was meant to be broken.
“This place is a fucking war zone,” Ben mutters.
“It’s Philly,” Mateo says. “This is how it’s always been.”
Ben is visibly nervous, again. Rifling through his backpack looking for nothing in particular. He’s got some neurodivergent flavor to him that's soothed by tactile repetition.
i ignore them both and focus on the actual problem—which is finding the resistance headquarters without getting shot on sight.
Because we have no idea where it is.
Newark had an organized leadership. Philly? Philly’s different. Less structure. More scattered factions. More places to die if you show up unannounced. We make it to a dead end. Theres a few symbols spray painted on the sides of buildings i don't recognize. But at least it isn't fascist.
“Alright,” I say, exhaling. “How do we find the guys in charge without getting riddled with bullets?”
Mateo grins. “Easy. We let them find us.”
Ben turns slowly. “What.”
And before anyone can stop him, Mateo leans out of the window and fires off two gunshots into the air.
CRACK. CRACK.
Silence. Then—movement.
---------------------------------------------
We get out of the car. It doesn't take long before someone comes out of the ruins.
He’s tall, maybe 6’5, lean, wearing a patched-up tactical vest and a Sixers hoodie. His rifle’s resting but ready, not quite pointed at us, but close enough.
“Explain why I shouldn’t put a bullet in you.”
I raise my hands. Cool, calm, let’s not die here.
“We’re from Newark. We’re looking for a resistance group.”
The guy snorts. “Which one?”
“We’re looking for the guys who actually get shit done,” I say.
Sixers Hoodie squints. Then—he recognizes something.
Or someone.
“You,” he says, pointing at Mateo. “I’ve seen you before.”
Mateo tilts his head. “Yeah?”
“Yeah.” Sixers Hoodie looks him over again, then scoffs. “You were the psycho running guns through Camden before all this went to shit, weren’t you?”
Mateo grins wider. “Still am, baby.”
And just like that, the mood shifts.
He doesn't exactly trust us, but Mateo’s recognizable enough that he decided not to kill us immediately. Which is great, because I hate getting shot at. Sixers hoodie has us follow him through a series of office hallways that lead into the center of the building, which is the only part structurally sound.
Inside, it’s a mix of military types, former street guys, and people who just refuse to die. It’s a different vibe than Newark– rougher, more desperate. We shuffle into what seems to be another old meeting room, with mismatched swivel chairs and collapsible tables lining the walls. Each one overflowing with specialized guns and ammo that i hadn't seen available at the Newark base.
One guy, a sandy blonde kid probably my age with a plethora of shitty tattoos– turns around when we come in.
“You guys ever heard of the radio?” Sixers Hoodie leans his rifle against a side table and sits in a metal chair that groans under his weight. “Didn’t tell us you were coming.”
Ben steps in, voice level. “Didn’t have a choice. Radio comms are compromised. Newark tried reaching NYC before. The message got intercepted. People died.”
The two guys share a look.
Mateo continues. “That’s why we’re here. We’re gonna fix it.”
“And you think you can do that?”
“Well,” i interject, “we think we can build something more secure and efficient.”
That gets their attention.
The sandy haired guy sighs and sits down. “You’re talking mesh networking, right?”
I nod. “You know what that is?”
“Enough to know we don’t have the equipment to make it work.”
“Yeah, well. The hardware isn’t exactly lying around. But we know where to get it.”
Sixers, we’ll call him, eyes me. “Where?”
“UPenn.”
That gets actual laughter from the two of them.
“You serious?” The first guy asks. “UPenn’s fucked. That whole area got hit bad. Looters, military sweeps—there’s nothing left.”
I don’t say anything.
Because I know. I know how universities work. I know the kinds of places people forget to check when they’re looting Best Buys and grocery stores.
“We think it's worth it.” Ben says with his chest– trying to sell the idea.
Sixers sighs. “Look, you want to go dig through the ruins, be my guest. But we’re not wasting time on a suicide run.”
I expected that.
But I also know one thing they don’t.
I know server rooms are built to last. They’re locked down and nearly impossible to break into, hidden in basements or behind security doors. And UPenn? They weren’t just running a few computers in a lab– they had real infrastructure, real enterprise-level servers that nobody was thinking about when they started setting cars on fire.
I know it’s there.
I can feel it.
8 notes
·
View notes