#Index monitoring software
Explore tagged Tumblr posts
Text
Description
Empower your website’s visibility with our cutting-edge index monitoring service. Our platform delivers real-time Google indexing insights, automated alerts, and comprehensive technical SEO audits. By optimizing crawl budgets and pinpointing index coverage issues, we help you maintain a robust online presence, ensure high-quality content gets recognized, and drive sustainable organic traffic.
Website
https://searchoptimo.com/
#Google indexing#Website indexing tool#Index monitoring software#Technical SEO audit#Crawl budget optimization#Index coverage#Real-time alerts#Organic traffic growth#Duplicate content management#Canonical tags#Site audit tool#Structured data optimization
1 note
·
View note
Text

Pentagon’s Pizza Index has accurately predicted 21 global crises since 1983
As tensions rise in the Middle East, a curious, crowd-driven theory known as the “Pentagon Pizza Index” has caught fire online.
On June 12 and 13, users on X (formerly Twitter) reported a sudden spike in pizza deliveries near the Pentagon and Department of Defense in Washington, D.C., sparking speculation that the United States may be quietly entering crisis mode behind closed doors.
The timing? Just hours before Israel reportedly struck targets in Iran in response to Tehran’s earlier drone and missile attacks. And once again, pizza orders were booming.
Cold war roots of the pizza theory. What began as a Soviet spy trick is now a digital-age meme
The idea isn’t new. During the Cold War, Soviet operatives observed pizza delivery activity in Washington, believing it signalled crisis preparation inside U.S. intelligence circles. They coined it “Pizzint” — short for pizza intelligence.
This tactic entered public lore on 1 August 1990, when Frank Meeks, a Domino’s franchisee in Washington, noticed a sudden surge in deliveries to CIA buildings. The next day, Iraq invaded Kuwait. Meeks later told the Los Angeles Times he saw a similar pattern in December 1998 during the impeachment hearings of President Bill Clinton.

As former CNN Pentagon correspondent Wolf Blitzer once joked in 1990, “Bottom line for journalists: Always monitor the pizzas.”
WWIII warning: What is the Pentagon Pizza Index today? A meme, an OSINT tool, or a symptom of digital-age paranoia?
The modern Pentagon Pizza Index is tracked through open-source intelligence (OSINT) tools. These include Google Maps, which shows real-time restaurant activity, and social media observations. Pages like @PenPizzaReport on X have dedicated themselves to watching for abnormal patterns.
On 1 June 2025, the account posted, “With less than an hour to go before closing time, the Domino’s closest to the Pentagon is experiencing unusually high footfall.”
A few hours later, reports emerged of a fresh escalation between Israel and Iran. For believers in the theory, it was yet another sign that something bigger was underway.
The April 2024 pizza spike. A recent example that reignited interest
The most notable recent instance occurred on 13 April 2024, the night Iran launched a massive drone and missile strike against Israel. That same evening, screenshots from delivery platforms showed pizzerias around the Pentagon, White House, and Department of Defense tagged as “busier than usual.”

Multiple Papa John’s and Domino’s branches reported increased orders. The correlation prompted viral memes and renewed interest in the theory.
According to Euro News, a user on X posted on 13 June 2025, “The Pentagon Pizza Index is hiking.”
Inside the logic: Why pizza? Food, fatigue and national security
The concept is deceptively simple. When military staff face a national emergency, they work longer shifts and can’t leave their posts. They need quick, filling food — and pizza fits the bill.
Studies in behavioural psychology show that under stress, people prefer calorie-dense, familiar comfort foods. During high-alert operations, officials may work 16–20 hour days. That creates a visible consumption spike that outsiders can track.
And because platforms like Google and Uber Eats share real-time data on restaurant activity, amateur analysts can monitor these patterns — no hacking required.
World War III: Pizza as a proxy for preparedness. It’s not perfect, but it’s consistent
The Pentagon Pizza Index isn’t a foolproof system. It could easily be triggered by something mundane: a long staff meeting, a software glitch, or a nearby college football game.
That’s why modern OSINT analysts often cross-reference pizza spikes with other indicators — like unusual aircraft movements, ride-hailing activity, or power usage near government buildings. When multiple signs align, it suggests more than coincidence.
As a senior analyst put it: “You can’t bank a war call on a pizza. But if the Pentagon’s burning the midnight oil and feeding everyone, it’s worth a second look.”
Official silence, public curiosity. What the US government says — and doesn’t say
Despite the chatter online, the US government has made no mention of pizza deliveries as indicators of crisis.
Responding to speculation about American involvement in Israel’s airstrikes on Iran, Republican Senator Marco Rubio said:
“We are not involved in strikes against Iran, and our top priority is protecting American forces in the region. Israel advised us that they believe this action was necessary for its self-defence.”
Still, the Pentagon’s silence on the pizza theory hasn’t stopped internet users from speculating.
Humour meets anxiety in the age of digital vigilance
In an age where open-source tools let ordinary people track the movement of jets, ships, and even pizzas, the Pentagon Pizza Index sits at the bizarre intersection of humour and fear. It turns snack food into a warning system.
It’s also a reminder: not all intelligence requires a badge. Sometimes, the clue might be just down the road — in a Domino’s queue.
Whether you see it as absurd or insightful, one thing is clear: when the pizzas fly, people pay attention.
Daily inspiration. Discover more photos at Just for Books…?
74 notes
·
View notes
Text

TECHNOLOGY ID PACK

NAMES︰ admin. ajax. alexa. am. atari. audio. auto. bailey. binary. blank. blu. blue. bluesse. browser. browsette. bug. byte. cache. calware. chip. circe. click. clicker. clickie. clicky. cloud. coda. code. codette. codie. cody. computette. crypt. cursor. cy. cyber. cybernet. cybernetica. cyberweb. cypher. cypherre. data. dell. digi. digitalia. digitelle. digitesse. disc. dot. electronica. electronique. emoticon. emoticonnie. fax. file. gig. gizmo. glitch. glitche. glitchesse. glitchette. graphique. hacker. hal. halware. hijack. index. informationne. intelligette. internette. interweb. java. javascript. juno. key. link. linuxe. lotus. lovebytes. mac. mal. malakai. malware. malwaria. memorette. memorie. meta. mic. micah. mickey. morphe. mouse. mousette. myspace. nano. neo. net. netette. nett. netty. paige. pascal. payton. peyton. pixel. programatha. programette. programme. pulse. reboot. rom. router. ruby. sam. sammy. screene. screenette. sean. shock. solitaire. spy. static. stutter. talia. tap. tecca. tech. techette. tessa. tetris. trojan. troubleshoot. ts. user. vir. virus. virusse. volt. vyrus. webbe. wheatley. whirr. widget. will. wirehead. wiresse. zap. zett. zetta. zip.

PRONOUNS︰ ai/ai. alt/alt. anti/antivirus. arc/archive. audio/audio. bat/battery. beep/beep. beep/boop. bit/bit. bit/byte. blue/blue. board/board. bright/bright. brow/browser. browser/browser. brr/brr. bu/bug. bug/bug. buzz/buzz. byt/byte. byte/byte. c/cpu. charge/charger. cir/circuit. cli/click. click/clack. click/click. click/scroll. co/code. code/code. color/color. com/com. com/computer. comp/computer. compute/computer. computer/computer. cor/corrupt. corrupt/corrupt. CPU/CPU. crash/crash. cre/creeper. crtl/crtl. cy/cyber. cyb/cyber. cyber/cyber. da/data. data/data. delete/delete. di/disk. dig/digital. digi/digi. digi/digital. digital/digital. dra/drag. e/exe. electronic/electronic. enter/enter. er/error. err/error. error/error. exe/exe. fi/file. file/file. gi/gif. gli/glitch. glit/glitch. glitch/glitch. graphic/graphic. hac/hacker. hack/hack. hard/hardware. head/phone. hij/hijacker. ho/home. info/info. information/information. int/internet. intelligent/intelligence. intelligent/intelligent. inter/net. internet/internet. it/it. jpg/jpg. key/board. key/cap. key/key. key/keyboard. key/keylogger. lag/lag. lap/laptop. ligh/light. linux/linux. load/load. log/login. main/mainframe. mal/malware. me/media. memory/memorie. mon/monitor. mou/mouse. nano/nano. net/net. net/network. org/org. over/overwrite. page/page. pix/pix. pix/pixel. pixel/pixel. plu/plug. png/png. pop/popup. port/port. pow/power. pro/program. program/program. ram/ram. ran/ransom. reboot/reboot. reload/reload. res/restore. ret/retro. route/router. sca/scan. scr/scroll. scre/screen. scre/screencap. scree/screen. screen/screen. scri/script. script/script. sentient/sentience. shift/shift. site/site. skip/skip. soft/software. spa/spam. space/space. spy/spyware. stop/stop. te/tech. tech/nology. tech/tech. technology/technology. tou/touchpad. txt/txt. typ/type. upload/upload. user/user. vi/viru. vi/virus. vir/virtual. web/page. web/web. whir/whir. wi/wire. win/dow. win/window. wire/wire. wire/wired. zip/zip . ⌨ . ☣ . ⚙ . ⚠ . 🎞 . 🎨 . 🎭 . 🎮 . 🎵 . 👀 . 👁 . 💔 . 💡 . 💢 . 💣 . 💳 . 💵 . 💻 . 💽 . 💾 . 💿 . 📀 . 📱 . 🔇 . 🔈 . 🔉 . 🔊 . 🔋 . 🔌 . 🔎 . 🖥 . 🖱 . 🗡 . 🗯 . 🛠 . 🧿 .

#pupsmail︰id packs#id pack#npt#name suggestions#name ideas#name list#pronoun suggestions#pronoun ideas#pronoun list#neopronouns#nounself#emojiself#techkin#robotkin#internetkin
453 notes
·
View notes
Text
Birdie (one)
This is an original work I wrote back in 2022 before I got into Call of Duty. Birdie is a former corporate software developer now living in a megabuilding inspired by the ones we see in the video game Cyberpunk 2077. This world is in transition, not quite post-corporate but on its way there. This is a story about Birdie falling into bed with the couple who moves in next door, and learning to trust other people again after enduring enormous personal betrayal. - cw: implications of stalking.

Birdie woke late in the morning to sunlight peeking through the cracks of her blinds and the smell of coffee gently percolating over in the kitchenette. It was a cool morning, silvery, the kind one wanted to luxuriate in and pretend noon would never come. Except—
Ping…ping…ping…
The soft chiming of her front door’s proximity alert was out of place.
She blinked groggily, swimming her legs through the tangle of blanket and sheets that she’d made a nest of in the night, and inchwormed her way to the edge of the mattress.
Half the pile slithered off the bed to puddle on the floor as her feet met the cool tile, which was spotless thanks to the vacuum-bot that had done its work during the night. She took a thin, reclaimed-fiber robe off its hook on the thin sliver of wall between the window and bed, and wrapped it around herself as she plodded, still half-asleep, in the direction of the chime.
Ping…ping…ping…
Birdie usually didn’t bring up her internal heads-up display until after her coffee, but the chime couldn’t be turned off without it. Safer that way—no one could tamper with it if they were of a mind to without hardwiring directly into her neural software. She flicked her index fingers upward in synchrony, and the translucent home screen slid in across her vision.
It was a simple interface—UI elements in soft white with simple drop shadows to contrast them against the real world they overlaid. Birdie could access the intranet, check her mail, keep track of her finances, and monitor her daily task lists as work orders came in; things people used to do on tablets or laptops, before integrated hard- and software became standard in the corporate era.
Ping…ping…ping…
No one was at the door—Birdie had set separate chimes for packages versus people. So she angled the bell camera downwards, seeking the parcel she expected to see—and scowled the moment she saw what it was.
Ping…ping…ping…
With an angry gesture she shut off the alert, with another opened the door, but no gesture in her software was going to make the big, sparkling crystal vase, stuffed to the gills with bright red roses, suddenly grow legs and run away.
A pink envelope was filed between two of the fattest blooms. Birdie bent at the waist, indignation traveling down her brain stem and hijacking her nerve endings, and plucked it from the bouquet. With one fingernail she broke the seal—real paper! Dyed paper! The audacity!—and as if disarming a bomb, she removed the folded stationery from within.
The ivory white, virgin sheet had obviously been recently manufactured, not pressed and cut from reclaimed pulp like any reasonable person would use these days. And, to add insult to injury, there was only one—one!—line of handwriting in the very middle.
I’m sorry, Margie. I still love you.
full chapter on Patreon
6 notes
·
View notes
Text
Richard Harris’ fear index spoilers ⬇️
a lot of the one stars on goodreads are saying ‘I saw the twist coming halfway through’ okay what are you saying no you did not 😭😭 You read 150 pages and predicted that Hoffman’s stalker was actually a german cannibal fetishist who found his account on a german mutual cannibalism forum but that account was created by Hoffman’s own advanced stock trading AI software gone rouge which had been monitoring him for months to study human fear behavior to then better predict market volatility. Why are you lying to my face
2 notes
·
View notes
Text
Cold Circuit excerpt: Hacker vs Drawer
I stand up and head to the back of the storage room, where I find a small portion of the wall shimmering lightly. Camotech, stolen from Marren International some time in Mama Zoraya’s past, fortified with three layers of the finest antivirus software ever created, DigiSoft’s programmable vanguards. Of course, I have no need to hack it, but I could use the practice all the same.
“May I?”
Celephaïs nods, and I unscrew the casing covering the distal phalanx of my cyber, revealing the cylindrical electric-blue jack beneath.
Now, if I remember correctly, there should be a spot to jack in right about…
I place my index finger on the upper lefthand corner faintly shimmering wall, the USB connect notification sound ringing in my ears. Seeing as I don’t yet have my eye installed, I decide to evade the digital vanguards rather than breach them.
This is a simple hack made complicated by a lack of visual feedback, and Cell once described it as using a keyboard and mouse for one of those vintage desktop computers from the early twenty-first century while the monitor is in another room.
Stumbling in the dark, I collide with my first vanguard.
So much for evasion.
There is no way to tell how this Vanguard would react to my intrusion, so I do the next best thing: overloading it with a bunk of junk code. Usually, I use this tactic sparingly, as I prefer to be efficient in my programming and either repurpose or dissect any junk code I come across, thereby leaving very little of the actual junk remaining, but this time, there is an uncomfortable excess, and it seems to be slowing me down incrementally.
I raise my right arm to the back of my neck, where the white-eyed woman slotted her strange program. No. Wait. This is not a program. A program would be too basic.
A virus.
The vanguard strains against the flow of useless data, a current of names, dates, birthdays and more that feels like it’ll never end, meanwhile I almost imagine the RAM in my brain standing up and stretching its legs after being in such a cramped digital space. The vanguard shuts down, and I find myself morbidly curious if that’s how I’ll end up, too.
Behold! the first scene where Sibyl hacks into something (more to refresh her memory. I more high-stakes hacking begins in the chapter after this)
Silverhands: @thatqueerweirdo @foyle-writes-things
Let me know if you wish to be added or removed
#writeblr#writers on tumblr#my writing#writerscommunity#cyberpunk#writer#writing#Cold Circuit#sci fi#sci fi books#science fiction#sci fi and fantasy
2 notes
·
View notes
Text
The Darkweb: Exploring the hidden crimes of the Internet

The Dark Web is a complex and often misunderstood segment of the internet, shrouded in secrecy and notorious for its association with illegal activities. This hidden part of the web, accessible only through specialised software like Tor (The Onion Router), allows users to navigate anonymously, which has fostered both legitimate and illicit uses. The Dark Web is a subset of the Deep Web, which itself constitutes about 90% of the internet not indexed by traditional search engines. While most users interact with the Surface Web, the Deep Web includes private databases and secure sites, whereas the Dark Web is specifically designed for anonymity and privacy. The Dark Web emerged from projects aimed at ensuring secure communication, originally developed by the U.S. Department of Defence in the early 2000s. [1] [2]
Hidden Crimes in the Dark Web
The anonymity offered by the dark web has made it a hub for numerous forms of criminal activity. From illegal marketplaces to cybercrime forums, this underworld of the internet is teeming with hidden dangers.
Illicit Markets and Drug Trade
One of the most notorious aspects of the dark web is its marketplace for illegal goods. Websites like the now-defunct Silk Road offered a platform where users could buy and sell illegal drugs, firearms, stolen goods, and counterfeit documents. These black markets are often operated using cryptocurrencies such as Bitcoin to further mask identities and ensure untraceable transactions.According to a 2019 study by the European Monitoring Centre for Drugs and Drug Addiction, the dark web drug trade has grown exponentially, with millions of dollars' worth of drugs being sold monthly across various platforms . [3] [4]
2. Cybercrime and Hacking Services
The dark web also serves as a marketplace for cybercriminals. Hacking tools, ransomware-as-a-service, and stolen data are regularly exchanged in these hidden corners of the internet. Criminals offer services ranging from DDoS attacks to the sale of stolen credit card information and personal identities. Some forums even provide tutorials for novice hackers looking to learn cybercrime techniques. [5]
3. Human Trafficking and Exploitation
While less publicly discussed, the dark web has been linked to disturbing trends in human trafficking and child exploitation. Illegal forums allow criminals to sell services or even traffic victims, relying on the secrecy provided by encryption and anonymity transactions. These criminal activities often occur alongside other heinous content like child abuse imagery, which is tragically prevalent in certain corners of the dark web . [5]
4.Weapons and Assassination-for-Hire
Another dark aspect of the dark web is the sale of illegal firearms, explosives, and even assassination services. Websites provide arms to buyers without the restrictions and regulations of the surface web. Though some claims of hitmen-for-hire on the dark web have been debunked as scams, the sale of illicit firearms remains a significant concern for global law enforcement agencies .
Top 5 Notorious Cases on the Dark Web
(Content Warning: This list includes some horrifying incidents and scary dark web stories. We suggest you skip entries if you’re faint of heart or suffering from any type of anxiety or stress disorder.)
1. Banmeet Singh’s $100M+ dark web drug empire gets brought to light
Starting with a fairly recent case, Banmeet Singh of Haldwani, Northern India was sentenced to eight years in prison in late January 2024 after he was found to have created and led a multi-million dollar drug enterprise.The Indian national also forfeited $150 million in cryptocurrency. This proved to be illegal drug money that was laundered into cryptocurrency. Singh used various dark web marketplaces to create his drug empire. According to the U.S. Department of Justice, Singh shipped drugs from Europe to eight distribution centers in the US. After, these were transported to and sold in all 50 US states and other countries in the Americas. Singh was arrested in London, where he was residing in 2019. In 2023, he was extradited to the US. [7]

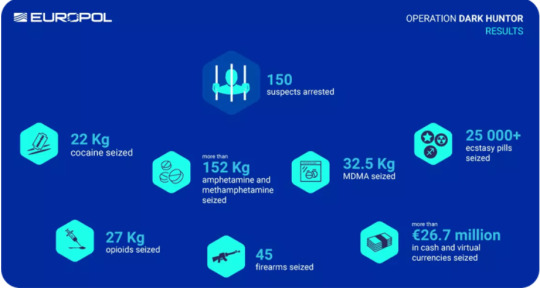
2. Operation Dark hunTor results in 150 arrests in nine countries
We’re moving from one multi-million-dollar illegal contraband case to the next. In 2021, Euro pol, Eurojust, and the police forces of nine countries conducted one of the biggest anti-crime operations the dark web has ever seen: Dark hunter. This operation resulted in 150 arrests across Australia, Bulgaria, France, Germany, Italy, the Netherlands, Switzerland, the United Kingdom, and the United States. All of the arrested were allegedly involved in buying or selling illegal goods on the dark web. The authorities found some articles in the possession of the arrested that strengthened their case: EUR 26.7 million (USD 31 million) in cash and virtual currencies, 234 kg of drugs, and 45 firearms.Italian authorities also managed to close down two dark web markets that boasted over 100,000 listings for illegal goods, DeepSea and Berlusconi. [7]
3. Operation DisrupTor exposes a dark web drugs distribution center
Amid the Covid pandemic, most businesses were struggling. Meanwhile, Operation DisrupTor suggests the drug business was still prospering. In February 2020, a group of FBI agents found 50 pounds of methamphetamine and thousands of Adderall pills in a storage shed in Los Angeles. The drugs, and the firearms that were also found, belonged to a crime network that had completed over 18,000 drug sales on the dark web. The criminal syndicate hid the drugs in a shed that they had made to look like a legitimate mail-order business. Their dark web drug sales included shipments to other dark net vendors, street dealers, and actual consumers. [7]
WATCH FULL VIDEO [8]
4. Attempt to hire a dark web hitman backfires
Now and then, crazy deep web stories pop up about how easy it is to hire a dark web hitman. One of these urban legends, however, turned out to be true. In February 2024, a woman from Canberra, Australia, pleaded guilty to inciting another to murder. The woman claimed to have contacted a dark web hitman (on the dark web marketplace Sinaloa Cartel) to murder her wealthy parents as part of an inheritance scheme. Supposedly, the total agreed-upon sum for the murder was $20,000, of which she had already paid $6,000 as a downpayment, using Bitcoin. It’s hard to say if the woman was actually talking to a contract killer or a scammer. Let’s just say we’re just happy the Australian court system was on to her before we could find out. While we don’t encourage anyone to go looking for a hitman on the dark web or elsewhere, this case goes to show that even on the dark web and while using crypto, many actions are retraceable. We always recommend people with good intentions to go for maximum privacy, as it’s no one’s business what they’re doing on the dark web. A great way to improve your privacy is by using NordVPN. NordVPN hides your IP address and encrypts your traffic, plus it blocks malicious links. [7]

5. No Love Deep Web takes dark web enthusiasts on a treasure hunt
Back in August of 2012, visitors on the dark web could find clues scattered on the network that led them through a fascinating alternate reality game. Much like Cicada 3031’s 4chan game, the clues led regular users through an array of clever clues set up like a treasure hunt. The dark web game employed a lot of encryption means to hide its hints, including the Caesar cipher, QR codes, Morse code, and a lot of other similar encryption methods. All of the clues were spread around dark websites, and one participant recounts the experience as quite thrilling:

So what was going on? Well, it wasn’t a secret government agency recruiting new members, and it wasn’t a feat of a group of cybercriminals.
Rather, the game was created by the experimental hip-hop group Death Grips to promote their new album, No Love Deep Web. [7]
READ MORE CASES [7]
Law Enforcement and the Fight Against Dark Web Crime
Despite the anonymity and encryption, law enforcement agencies around the world have made significant progress in cracking down on dark web criminality. In 2021, a multinational law enforcement effort, Operation Dark HunTor, led to the arrest of 150 individuals across multiple countries, targeting major drug vendors and illegal marketplaces on the dark web .
Undercover operations, improved digital forensics, and advances in cryptocurrency tracing have given authorities new tools to combat the hidden crimes of the dark web. However, for every takedown, new marketplaces and forums emerge, reflecting the cat-and-mouse dynamic between law enforcement and cybercriminals. [6]
Conclusion
While the dark web itself is not inherently evil, its secrecy has allowed criminals to thrive in ways that are difficult to regulate or even detect. From drug trafficking and cybercrime to human exploitation, the hidden crimes of the dark web reveal a darker side of digital anonymity. As law enforcement and technology continue to evolve, so too will the battle to uncover and combat these underground activities. Nonetheless, the dark web serves as a potent reminder that as technology advances, so too does the need for robust security measures and ethical oversight.
.
.
.
.
sources:
https://www.varutra.com/the-hidden-internet-exploring-the-secrets-of-the-dark-web/
2.https://sopa.tulane.edu/blog/everything-you-should-know-about-dark-web
3. https://www.unsw.edu.au/research/ndarc/news-events/blogs/2016/01/dark-net-drug-marketplaces-begin-to-emulate-organised-street-cri
4. https://www.euda.europa.eu/darknet_en
5. https://www.findlaw.com/criminal/criminal-charges/dark-web-crimes.html
6. https://syntheticdrugs.unodc.org/syntheticdrugs/en/cybercrime/detectandrespond/investigation/darknet.html
7. file:///D:/New%20folder/The%2013%20Most%20Notorious%20Cases%20on%20the%20Dark%20Web.html
8. https://youtu.be/d4NSfrOtMfU?feature=shared
#crime#cyberpunk 2077#cybersecurity#internet#dark web#criminal case#laws#murder mystery#mental health
5 notes
·
View notes
Text
Seamless Transition: Best Practices for Website Migration to Shopify

In the ever-evolving landscape of e-commerce, staying competitive requires not just a robust online presence but also adaptability to emerging platforms. As businesses strive to enhance user experience, streamline operations, and optimize sales, many are turning to Shopify for its user-friendly interface, extensive customization options, and powerful marketing tools. However, migrating an existing website to Shopify can be a daunting task if not approached strategically. In this comprehensive guide, we'll delve into the best practices for a seamless transition to Shopify, ensuring minimal disruption to your online business.
Thorough Planning and Preparation:
Before embarking on the migration process, it's crucial to conduct a thorough assessment of your current website. Identify all existing content, including product listings, images, blog posts, and customer data. Take inventory of any custom features, integrations, or third-party apps that may need to be replicated or replaced on the new platform. Establish clear goals and timelines for the migration process to keep it on track.
Choose the Right Shopify Plan:
Shopify offers a range of plans tailored to different business needs, from startups to enterprise-level corporations. Assess your requirements in terms of product catalog size, expected traffic volume, and desired features to select the most suitable plan. Consider factors such as transaction fees, credit card rates, and additional services offered within each plan.
Data Migration and Integration:
Transferring your existing data to Shopify accurately is crucial for maintaining continuity and avoiding disruptions to your business operations. Utilize Shopify's built-in migration tools or third-party apps to seamlessly import product listings, customer information, and order history. Ensure compatibility with any existing integrations or third-party services your business relies on, such as payment gateways, shipping providers, and accounting software.
Design and Customization:
One of the key advantages of Shopify is its customizable design options, allowing you to create a unique and visually appealing storefront. Choose a Shopify theme that aligns with your brand identity and offers the features you require. Customize the design elements, layout, and color scheme to reflect your brand's personality and enhance user experience. Leverage Shopify's drag-and-drop editor and CSS customization capabilities to fine-tune the design to your liking.
Optimize for SEO:
A successful website migration should not only maintain your existing search engine rankings but also provide opportunities for improvement. Prioritize SEO best practices throughout the migration process, including:
Properly redirecting old URLs to their corresponding new URLs using 301 redirects to preserve link equity and prevent 404 errors.
Updating meta tags, headers, and image alt texts to optimize for relevant keywords and improve search engine visibility.
Submitting updated sitemaps to search engines to ensure they crawl and index your new Shopify site efficiently.
Implementing schema markup to enhance the appearance of your site's search results and provide rich snippets to users.
User Testing and Quality Assurance:
Before making your Shopify site live, conduct thorough testing to identify and address any issues or inconsistencies. Test the functionality of all features, including product pages, navigation menus, checkout process, and payment gateways, across different devices and browsers. Solicit feedback from beta users or employees to uncover any usability issues or bugs that may have been overlooked.
Launch and Post-Migration Optimization:
Once you're confident in the stability and functionality of your Shopify site, it's time to go live. Monitor closely for any post-migration issues, such as broken links, missing images, or discrepancies in data. Implement tracking tools such as Google Analytics to monitor site traffic, user behavior, and conversion rates. Continuously optimize your Shopify site based on performance metrics and user feedback to maximize its effectiveness in driving sales and achieving your business objectives.
In conclusion, migrating your website to Shopify can be a transformative step in enhancing your online presence and driving business growth. By following these best practices and approaching the migration process with careful planning and attention to detail, you can ensure a seamless transition that preserves your existing assets while unlocking the full potential of the Shopify platform.
2 notes
·
View notes
Text
Navigating the Hidden Corners of the Internet

The Dark Web has long been shrouded in mystery and intrigue, often associated with illicit activities and clandestine operations. However, it's important to understand that not all aspects of the Dark Web are illegal or harmful. In this article, we will explore the concept of Dark Web links, shedding light on what they are, how they work, and how to navigate them responsibly.
For more information- Dark Web Links
Dark Web links are the gateways to websites, forums, and services hosted on the Dark Web. These links are not indexed by traditional search engines like Google, making them difficult to find through conventional means. Instead, users typically access Dark Web links through specialized software, most notably Tor (The Onion Router), which ensures anonymity and privacy.
1. Onion URLs: Dark Web links often use a onion domain, indicating that they are hosted on the Tor network. These URLs are designed to be complex and nonsensical, making them difficult to guess or remember. For example, a typical Dark Web link might look like example website onion.
2. Accessing the Dark Web: To access Dark Web links, users need to download and install the Tor browser, which routes internet traffic through a series of volunteer-operated servers to maintain anonymity. Once connected to the Tor network, users can enter onion URLs into the browser to access Dark Web sites.
Responsible Navigation of Dark Web Links
While the Dark Web offers some legitimate and ethical content, it is essential to approach it with caution and responsibility. Here are some guidelines for navigating Dark Web links:
1. Legal and Ethical Use: Ensure that your activities on the Dark Web are legal and ethical. Engaging in illegal activities or seeking out harmful content is not only unethical but can also lead to serious legal consequences.
2. Privacy and Security: Be aware that your online activities on the Dark Web are not entirely immune to surveillance or security breaches. While Tor provides a degree of anonymity, it is not foolproof. Take steps to protect your privacy and use encryption tools where necessary.
3. Browsing Safely: Stick to reputable websites and forums on the Dark Web that align with your interests and goals. Avoid clicking on suspicious links or downloading files from untrustworthy sources. Be cautious of phishing attempts and scams.
4. Verify Information: When using the Dark Web for research or information gathering, verify the accuracy of the information you find. Due to the anonymous nature of the Dark Web, misinformation can proliferate.
5. Avoid Illegal Markets: Steer clear of illegal marketplaces and services that offer drugs, stolen data, weapons, or other illicit goods. Engaging with such platforms can have severe legal consequences.
6. Maintain Anonymity: Remember that while Tor provides a degree of anonymity, it's not infallible. Avoid sharing personal information or engaging in behavior that could compromise your identity.
7. Report Illegal Activity: If you come across illegal activities or content on the Dark Web, consider reporting it to the appropriate authorities or organizations dedicated to monitoring and combating illegal online activities.
Conclusion
Dark Web links offer access to a hidden world of websites and services that are not indexed by traditional search engines. While the Dark Web is often associated with illegal activities, it's essential to recognize that it can also be used for legitimate and ethical purposes, such as protecting privacy, fostering free speech, and conducting research.
However, responsible navigation of Dark Web links is paramount. Engaging in illegal activities, downloading malicious content, or seeking out harmful materials not only jeopardizes your own safety but also contributes to the negative reputation of the Dark Web. As with any part of the internet, the key lies in responsible use. Approach Dark Web links with caution, adhere to ethical standards, and prioritize your own online security and privacy. By doing so, you can explore the hidden corners of the internet without falling into the traps of illegal activities or dangerous scams, contributing to a safer and more responsible online environment
3 notes
·
View notes
Text
“Still the arrangement is bringing new attention to the company’s scale and ubiquity. “It’s impossible to think of BlackRock without thinking of them as a fourth branch of government,” says William Birdthistle, a professor at the Chicago-Kent College of Law who studies the fund industry.
(…)
There’s probably no other financial institution that brings to the table what BlackRock does. It’s experienced in running large portfolios on behalf of others. It’s ubiquitous in markets for everything from passive, index-linked products to hands-on mutual funds, with $6.5 trillion in assets under management as of March 31. It’s the largest issuer of ETFs, which act like mutual funds but trade on an exchange. It actively manages more than $625 billion in bond funds for pension plans and other institutional clients. Almost anyone looking to buy a diverse portfolio quickly would consider BlackRock—and the Fed did the same. In a virtual hearing of the Senate Banking Committee on May 19, Fed Chairman Jerome Powell said BlackRock was hired for its expertise and “it was done very quickly due to the urgency” of the matter.
Beyond money management, BlackRock’s software platform, Aladdin, appealed to the Fed. The program evaluates risk for clients that include governments, insurers, and rival wealth managers, monitoring more than $20 trillion in assets. (Bloomberg LP, the parent company of Bloomberg News, sells financial software that competes with Aladdin.)
BlackRock has ascended to speed-dial status among Washington officialdom in part through shrewd business maneuvering. It scooped up Barclays Global Investors, including its iShares ETF division, in the fallout from the 2008 crisis. That gave BlackRock a stronghold in low-cost index funds, transforming it into the world’s largest asset manager almost overnight—and supercharging more than a decade of growth.
At the same time, the money manager built a powerful advocacy arm. Its sphere of influence reaches beyond the central bank to lawmakers, presidents, and government agency heads from both political parties, though its hiring leans Democratic. Bloomberg found only a handful of current BlackRock executives who came out of the George W. Bush administration, but more than a dozen Barack Obama alumni. These include Obama’s national security adviser, senior adviser for climate policy, the former Federal Reserve vice chairman he appointed, and numerous White House, Treasury, and Fed economists.
(…)
BlackRock, however, was handed three Fed assignments without any competitive process—though the Fed plans to rebid the contracts once the programs are in full swing. BlackRock will manage portfolios of corporate bonds and debt ETFs. It will do the same for newly issued bonds—sometimes acting as the sole buyer—and for up to 25% of bank-syndicated loans. And it will purchase commercial mortgage-backed securities from quasi-government agencies such as Fannie Mae and Freddie Mac.
BlackRock could reap as much as $48 million a year in fees for its Fed work, according to a Bloomberg analysis. That’s no windfall, especially in relation to its $4.5 billion in earnings last year. But it may further cement the money manager’s ties with policymakers. On May 12, BlackRock began the first stage of these programs when it began buying ETFs.
As with technology companies Facebook Inc. and Alphabet Inc., BlackRock’s growth raises questions over how big and useful a company can become before its size poses a risk. The firm has long argued that, unlike banks, it’s not making investments for itself with tons of borrowed money. Watching over large sums of money for clients doesn’t make its business a threat to the broader financial system.
With its latest assignment, that argument could be harder to make, says Graham Steele, director of the Corporations and Society Initiative at the Stanford Graduate School of Business. “They are so intertwined in the market and government that it’s a really interesting tangle of conflicts,” says Steele, who formerly worked at the Federal Reserve Bank of San Francisco. “In the advocacy community there’s an opinion that asset managers, and this one in particular, need greater oversight.”
Already there are growing worries about the power of BlackRock, Vanguard Group Inc., and State Street, often called the Big Three because they hold about 80% of all indexed money. That raises concerns about how they wield their voting power as shareholders and has even drawn attention from antitrust officials.
(…)
And then there are the potential conflicts. One arm of BlackRock knows what the Fed is buying, while other parts of the business participating in credit markets could benefit from that knowledge. To avoid conflicts, “there are stringent information barriers in place,” says the BlackRock spokesman. BlackRock employees working on the Fed programs must segregate their operations from all other units, including trading, brokerage, and sales. The fee waiver on ETFs helps avoid the appearance of self-dealing.
But BlackRock’s contract with the Fed also acknowledges that senior executives “may sit atop of the information barrier” and “have access to confidential information on one side of a wall while carrying out duties on the other side.” Staff working on the Fed programs must go through a cooling-off period before moving to jobs on the corporate side, but it would last only two weeks.
Birdthistle, the Chicago-Kent law professor, suggests the Fed could have made its process more competitive by allocating some of its funds for buying corporate credit to a group of asset managers from the outset, instead of just one. “It raises the question: Why did all the money have to go to one company?” he asks. “I get why BlackRock would be on the list, but I don’t understand why it would be the only one on the list.””
6 notes
·
View notes
Text
Transforming Legal Operations: iManage Solutions for Modern Law Firms
In the evolving digital landscape, legal professionals face increasing demands for secure, organized, and efficient document and email management. That’s where iManage steps in. As the industry leader in legal document management, iManage empowers law firms and corporate legal departments with robust tools for handling files, emails, and workflows. Whether you're interested in the latest iManage software update or looking to streamline operations with iManage Worksite Web, MacroAgility Inc. delivers tailored iManage solutions to meet your unique needs.
What Is iManage?
iManage is a secure, AI-powered document and email management platform designed for legal, accounting, and financial services professionals. Its core platform, iManage Worksite, allows teams to collaborate, manage risk, and work smarter through enhanced workflows and centralized access to files and communications.
To get the most from your investment, MacroAgility Inc. provides full-service iManage support, deployment, and consulting through its team of certified experts.
iManage for Law Firms: Boosting Productivity & Compliance
Today’s law firms need more than just digital storage — they need seamless access, version control, and compliance-ready systems. iManage for law firms enhances legal workflows by offering:
Centralized document and email storage
Audit trails for compliance
Secure collaboration features
Cloud and on-premise deployment options
With MacroAgility's legal document management services, firms can implement, migrate, or optimize their imanaged solutions and confidently.
Introducing iManage White Rabbit & Bulk Import
iManage continues to innovate, and tools like iManage White Rabbit simplify large-scale data imports. This automation tool is especially beneficial during system upgrades or transitions from legacy platforms.
iManage bulk import capabilities allow your IT teams or consultants to efficiently bring in legacy data, client files, and historical emails — minimizing manual effort and maximizing accuracy. MacroAgility’s iManage Work consultants specialize in managing such transitions with minimal disruption.
iManage Worksite & Web Access
iManage Worksite is the backbone of the system — giving users structured access to all legal content. With iManage Worksite Web, you get that same powerful functionality in a web-based interface. This enables remote work and global collaboration while maintaining full compliance and security.
To ensure smooth performance and accessibility, MacroAgility offers consulting and support for configuring and customizing Worksite deployments.
iManage Worksite Jobs & Automation
Managing daily administrative tasks can be overwhelming for legal IT teams. That’s where iManage Worksite Jobs come in — automated background processes that ensure your repositories remain updated, synchronized, and secure. Common Worksite jobs include indexing, backup verification, and permission updates.
At MacroAgility, we help clients set up and monitor these jobs for optimal performance and zero downtime.
Staying Current: Latest iManage Software Update
With each litigation document management, users benefit from performance enhancements, new security protocols, and UI improvements. Staying updated is vital for security and productivity.
MacroAgility’s consultants help your organization implement these updates seamlessly — with minimal interruption to your daily operations.
Specialized Solutions: iManage at Macquarie
Institutions like Macquarie utilize customized iManage implementations to streamline financial and legal processes across departments. Their use case highlights iManage’s scalability for large, international enterprises.
At MacroAgility, we craft tailored solutions like these to fit your firm's size, scope, and regulatory requirements.
Why Choose MacroAgility for Your iManage Needs?
As a premier partner for imanage macquarie and legal technology consulting, MacroAgility Inc. stands out by offering:
Deep expertise across all iManage modules
Custom integrations and automation
White-glove onboarding and support
Performance optimization and compliance solutions
Whether you're migrating to iManage, upgrading to the latest version, or deploying iManage iSearch UI for enhanced search functionality, we’ve got you covered.
Ready to Future-Proof Your Legal Operations?
Empower your team with cutting-edge document and email management. Let MacroAgility Inc. help you unlock the full potential of iManage today.
📞 Contact us for a free iManage consultation!
0 notes
Text
In today’s digital era, database performance is critical to the overall speed, stability, and scalability of modern applications. Whether you're running a transactional system, an analytics platform, or a hybrid database structure, maintaining optimal performance is essential to ensure seamless user experiences and operational efficiency.
In this blog, we'll explore effective strategies to improve database performance, reduce latency, and support growing data workloads without compromising system reliability.
1. Optimize Queries and Use Prepared Statements
Poorly written SQL queries are often the root cause of performance issues. Long-running or unoptimized queries can hog resources and slow down the entire system. Developers should focus on:
Using EXPLAIN plans to analyze query execution paths
Avoiding unnecessary columns or joins
Reducing the use of SELECT *
Applying appropriate filters and limits
Prepared statements can also boost performance by reducing parsing overhead and improving execution times for repeated queries.
2. Leverage Indexing Strategically
Indexes are powerful tools for speeding up data retrieval, but improper use can lead to overhead during insert and update operations. Indexes should be:
Applied selectively to frequently queried columns
Monitored for usage and dropped if rarely used
Regularly maintained to avoid fragmentation
Composite indexes can also be useful when multiple columns are queried together.
3. Implement Query Caching
Query caching can drastically reduce response times for frequent reads. By storing the results of expensive queries temporarily, you avoid reprocessing the same query multiple times. However, it's important to:
Set appropriate cache lifetimes
Avoid caching volatile or frequently changing data
Clear or invalidate cache when updates occur
Database proxy tools can help with intelligent query caching at the SQL layer.
4. Use Connection Pooling
Establishing database connections repeatedly consumes both time and resources. Connection pooling allows applications to reuse existing database connections, improving:
Response times
Resource management
Scalability under load
Connection pools can be fine-tuned based on application traffic patterns to ensure optimal throughput.
5. Partition Large Tables
Large tables with millions of records can suffer from slow read and write performance. Partitioning breaks these tables into smaller, manageable segments based on criteria like range, hash, or list. This helps:
Speed up query performance
Reduce index sizes
Improve maintenance tasks such as vacuuming or archiving
Partitioning also simplifies data retention policies and backup processes.
6. Monitor Performance Metrics Continuously
Database monitoring tools are essential to track performance metrics in real time. Key indicators to watch include:
Query execution time
Disk I/O and memory usage
Cache hit ratios
Lock contention and deadlocks
Proactive monitoring helps identify bottlenecks early and prevents system failures before they escalate.
7. Ensure Hardware and Infrastructure Support
While software optimization is key, underlying infrastructure also plays a significant role. Ensure your hardware supports current workloads by:
Using SSDs for faster data access
Scaling vertically (more RAM/CPU) or horizontally (sharding) as needed
Optimizing network latency for remote database connections
Cloud-native databases and managed services also offer built-in scaling options for dynamic workloads.
8. Regularly Update and Tune the Database Engine
Database engines release frequent updates to fix bugs, enhance performance, and introduce new features. Keeping your database engine up-to-date ensures:
Better performance tuning options
Improved security
Compatibility with modern application architectures
Additionally, fine-tuning engine parameters like buffer sizes, parallel execution, and timeout settings can significantly enhance throughput.
0 notes
Text
Best Melt Flow Index Tester in 2025

Source of Info:https://www.perfectgroupindia.co.in/blog/best-melt-flow-index-tester-in-2025
Introduction
The Melt Flow Index Tester is an important tool for analyzing the melting and flow properties of plastics during manufacturing. The top models in 2025 provide improved speed, digital displays and simple designs to make it easier for industries to choose the right plastic materials. These advanced tools help better processing and higher-quality products. Testing the melt flow of plastic is more important than ever because of the increasing demand for packaging, automobiles and everyday products. Perfect Group India is a reliable choice providing equipment that combine innovative functions with durable performance. This year it's an excellent choice to improve your tester if you want to achieve the highest level of manufacturing.
What is a Melt Flow Index Tester? A Melt Flow Index Tester measures how easily a thermoplastic polymer flows when melted at a specified temperature. The result is shown as grams per ten minutes. Manufacturers can use this value to analyze whether a plastic material is suitable for extrusion, molding or any other manufacturing process.
A higher melt flow rate for example means that the material flows easily and is perfect for injection molding; on the other hand a lower rate might work better for extrusion or blow molding.
Why is Melt Flow Testing Important in 2025? Quality control is more important than ever because of the growing demand for plastic products that are focused on results and reliable. Demand for advanced materials, recyclable polymers and recycled plastics has increased in 2025. Here are some industries that benefit from the Melt Flow Index Tester:
Make sure the plastic materials are consistent.
Find the processing properties of new materials.
From one batch to the next check the materials quality.
Identify whether recycled plastics can be used again.
Increase productivity of manufacturing.
Companies that choose on accurate melt flow data can reduce waste, improve productivity and deliver better products to the market.
Top Melt Flow Index Tester Features for 2025 Modern testing instruments are designed with accuracy and automation. Here are the improtan features that make a Melt Flow Index Tester stand out in 2025:
Touchscreen Interface The testers of today have an easy-to-use touchscreen panel. This allows real-time data tracking, improves processes and makes it simple for users to set up testing parameters.
Advanced Temperature Control Accurate and trusted heating is required for melt flow testing. The top models for 2025 guarantee test reliability by maintaining the temperature within a very small capacity range.
Auto-Cutting Mechanism Extrudate is automatically cut at predetermined intervals, providing consistent results and avoiding human error. Additionally this feature improves reliability.
Built-in Timer and Digital Display With a digital timer and large display, users can view results quickly and monitor the progress of each test without confusion.
Multiple Weight Options Advanced testers can be used to test a variety of polymer types and processing requirements because they have adaptable weights.
Software Connectivity The top Melt device for 2025 has USB or Wi-Fi connections for software, allowing for quality audits, report generation and data logging.
Safety Improvements To guarantee the safety of workers, security features like overload alerts and heat resistance are now standard.
Who Uses Melt Flow Index Tester? The demand for these instruments spans across several industries including:
Plastic product manufacturers
Recycling plants
Automobile parts suppliers
Medical equipment producers
Consumer goods companies
Research laboratories
These industries choose melt flow testing to maintain quality standards and to innovate with new materials.
Tips for Selecting the Best Melt Flow Index Tester
Testing Range: Choose a tester that supports various materials from HDPE to recycled PET.
Maintenance Support: Select a brand that provides measurement help service and post-purchase support.
Automation Level: Human error is decreased when a system is more automated because less manual work is required.
Data Management: For quality assurance reporting choose systems that offer options for data sharing and storage.
Best Melt Flow Index Tester for Modern Labs With so many models available in the market selecting the best option requires attention to detail. However Perfect Group India is a name that continues to gain trust for professionals. They are an excellent choice for both manufacturers and labs because of their dedication to quality, innovation and customer satisfaction. This equipment is suitable for both testing and manufacturing settings because of its accurate controls and advanced automation.
The Future of Melt Flow Testing As plastics change and eco-friendly materials become more common the role of melt flow testing will continue to grow. In the upcoming years, cloud data storage, IoT connectivity and AI integration are going to become regular. But in 2025 the top Melt Flow Index Tester on the market today is still defined by its accuracy and easy use.
Conclusion Melt Flow Index Tester is important to guarantee the quality of plastic materials when it comes to molding and extrusion processes. Modern testers in 2025 provide advanced features, quick results and user friendly designs. Selecting the right one guarantees better manufacturing and product quality. Perfect Group India offers equipment that easily satisfies industry demands for reliable results and trustworthy solutions. Any company that works with polymers would be beneficial to invest in modern testing equipment. These tools increase productivity while also making testing simple. Make the right choice and use advanced, user-friendly testing tools to support your process.
#industrial#equipments#perfectgroupindia#perfectinstruments#technology#droptester#business#boxcampressiontester#toploadertester
0 notes
Text
Deepening the Craft MCA's Real World Awakening
The transition from BCA to MCA wasn't just academic advancement. It was a conscious dive into the deeper mysteries of software architecture, algorithms, and system design. By this time, I was chasing mastery, not grades. The curriculum pushed boundaries I didn't know existed: complex data structures, advanced algorithms, and the art of building scalable systems.
My first real wake up call came during an internship where I encountered a sluggish Java web application that was testing users' patience. The application took forever to load, forms would timeout, and the user experience was painful to witness. Using profiling tools and performance monitoring, I discovered the culprit: inefficient database queries and unoptimized loops that were choking the system. After weeks of refactoring, indexing databases, and streamlining the codebase, I managed to cut load times by 40%.
Watching users navigate the improved application smoothly was a revelation. This wasn't just about elegant code or theoretical computer science. This was about real people accomplishing real tasks without frustration. The satisfaction of seeing my technical improvements translate into better user experiences was unlike anything I'd felt before - an insight I now regularly share through our educational content on LinkedIn, where we help other developers understand the business impact of their technical decisions.
But MCA also served me healthy doses of humility. I once attempted to build a machine learning model in Python without fully grasping the underlying mathematics. The model crashed spectacularly, producing results that were not just wrong but hilariously nonsensical. That failure taught me to respect the complexity of what I was attempting and to never hesitate to ask for help or admit when I was out of my depth. These learning moments became the foundation for the authentic, educational posts we share on Facebook, where we discuss both successes and failures in the tech entrepreneurship journey.
During this period, I also started noticing how users interacted with the systems I built. A simple change in button placement could dramatically affect user behavior. An intuitive navigation structure could mean the difference between a successful user journey and immediate abandonment. These observations were planting seeds for what would later become my fascination with the psychology behind digital experiences, insights we now visualize and share through compelling graphics on Instagram.
0 notes
Text
S&P 500 ASX: Key Stocks Moving Across Energy, Finance, Tech
Highlights
Leading energy, finance, and tech tickers in focus across major indices
S&P 500 ASX stocks include high-cap names from diversified sectors
Tickers represent listings across ASX 200, S&P/ASX 50, and S&P 500
S&P 500 ASX stocks represent companies across a wide range of sectors. Among them, energy, finance, and technology play a dominant role, with tickers listed both on the ASX and those tracked on the S&P 500 index. These stocks are also included in other significant benchmarks such as the ASX 200 and the S&P/ASX 50, aligning domestic and global market tracking. Companies in this dual exposure segment often demonstrate performance characteristics shaped by both domestic economic conditions and global market trends.
Energy sector coverage with dual-listed presence
The energy sector includes companies that hold listings in both Australian and American stock exchanges. One such ticker is BHP Group Limited (ASX:BHP), which operates in metals, petroleum, and mining. BHP is part of the ASX 200, S&P/ASX 50, and is also tracked in the S&P 500 under its NYSE listing. Another company in this segment is Woodside Energy Group Ltd (ASX:WDS), known for its gas and oil exploration business. Woodside appears on the ASX 200 and is listed in the United States through a secondary listing. These companies benefit from commodity-driven momentum and are often influenced by global crude and resource demand.
Banking and finance names in key index groups
The financial sector includes entities that contribute to both Australian and US stock benchmarks. Commonwealth Bank of Australia (ASX:CBA) is a dominant financial services provider and is featured on the ASX 200 and S&P/ASX 50. While not directly listed on the S&P 500, companies such as National Australia Bank Ltd (ASX:NAB) and Westpac Banking Corporation (ASX:WBC) are indirectly referenced in international portfolios due to institutional interest and depositary receipts. Macquarie Group Ltd (ASX:MQG) also features in this space and participates in global financial activity, aligning with top-tier benchmark tracking.
Technology-driven tickers tracked across borders
Technology stocks listed on the ASX and also linked to S&P 500 constituents include names such as Xero Ltd (ASX:XRO), a software company specializing in accounting solutions. Although Xero is not directly listed on US exchanges, it is included in global ETFs that mirror both ASX and S&P index strategies. Another name is Block Inc. (ASX:SQ2), which is listed on the ASX through a Chess Depositary Interest and is originally a US-based company also listed on the S&P 500. This reflects a unique blend of cross-listing, allowing Australian market participants access to a US-rooted technology enterprise.
Consumer-focused stocks with dual market attention
In the consumer goods segment, companies such as CSL Limited (ASX:CSL) hold significant weight across multiple indices. CSL is a biotech firm that operates globally and is listed on the ASX 200 and S&P/ASX 50. It is often monitored alongside US peers due to comparable product lines and healthcare services. Wesfarmers Limited (ASX:WES) is another significant name in consumer staples, representing supermarkets, retail, and industrial divisions. These companies align with consumer activity and reflect shifts in global consumption patterns, making them part of broader equity strategies.
Industrial and diversified firms bridging markets
Industrial players such as Brambles Ltd (ASX:BXB) offer pallet and supply-chain logistics services. Brambles has exposure to both domestic and international markets, appearing on the ASX 200. While it does not sit on the S&P 500, its supply chain operations link it to companies that are core S&P constituents. Another relevant stock is Amcor Plc (ASX:AMC), a packaging firm with dual listings in Australia and the United States. Amcor is part of the ASX 200 and also holds a position on the S&P 500 through its NYSE listing. This makes it one of the few companies that connect both markets structurally and operationally.
Healthcare and pharmaceutical entities with global reach
The healthcare space is represented by companies like ResMed Inc. (ASX:RMD), which is also traded in the US and forms part of the S&P 500 under its US ticker. Its ASX listing enables local exposure to a business that generates much of its revenue from North America and Europe. Sonic Healthcare Ltd (ASX:SHL) also provides medical diagnostics and is included in the ASX 200. Though not listed on the S&P 500, it interacts with global operations and maintains partnerships across several international jurisdictions, drawing attention from multi-regional asset managers.
Materials and resources beyond mining
In addition to mining, the broader materials sector includes companies like Fortescue Ltd (ASX:FMG), which is primarily focused on iron ore but is active in renewable energy transitions. Though Fortescue is not listed on the S&P 500, its global trade flows and collaborations bring its business into alignment with companies that are part of the index. Other companies like South32 Ltd (ASX:S32) offer diversified mining portfolios and maintain operations in regions that coincide with S&P 500-linked economies. Their presence on the ASX 200 contributes to sectoral balance.
Telecommunications and infrastructure in market blends
Telstra Group Ltd (ASX:TLS) is Australia's leading telecom firm and part of the ASX 200 and S&P/ASX 50. Its scale and infrastructure presence often parallel US-based firms tracked on the S&P 500. While Telstra itself is not dual-listed, partnerships and technology integrations with American network companies create indirect alignment. Similarly, APA Group (ASX:APA) operates energy infrastructure and features in domestic indices. Though not connected to the S&P 500 through direct listing, its asset base reflects a network-centric business model common in US utility benchmarks.
0 notes