#InfoSecurity
Text
Person of Interest (2011-2016)
#person of interest#cyberpunk aesthetic#hacking#graphic design#surveillance#science fiction#surveillence state#hackers#cybersecurity#scifi#mobile hacker#code breaker#data manipulation#network security#infosecurity#10s#command line
76 notes
·
View notes
Text
[Media] Practical IoT Hacking
Practical IoT Hacking
A comprehensive guide to testing and exploiting IoT systems and devices. Written by expert security researchers, the book covers common threats and a threat modeling framework, security testing methodologies, and passive reconnaissance techniques.
Readers will learn how to assess security on all layers of an IoT system, perform VLAN hopping, crack MQTT authentication, abuse UPnP, craft WS-Discovery attacks, and tackle hardware and radio hacking.
The book also covers developing an NFC fuzzer, hacking a smart home, and more. The tools and devices used in the book are affordable and readily available, making it a valuable resource for security researchers, IT teams, and hobbyists.
Buy online:
🛒 https://amzn.to/3mzbqPG
#book #IoT

36 notes
·
View notes
Text
so a lot of people are panicking about the new data breach but like. its not even new data. the source was an incorrectly configured server for a search engine that allows you to check if you're in a data breach (painful painful irony)
your tumblr passwords are most likely safe (assuming you don't use the same password for other websites like twitter), but it can't hurt to change them now if you'd like.
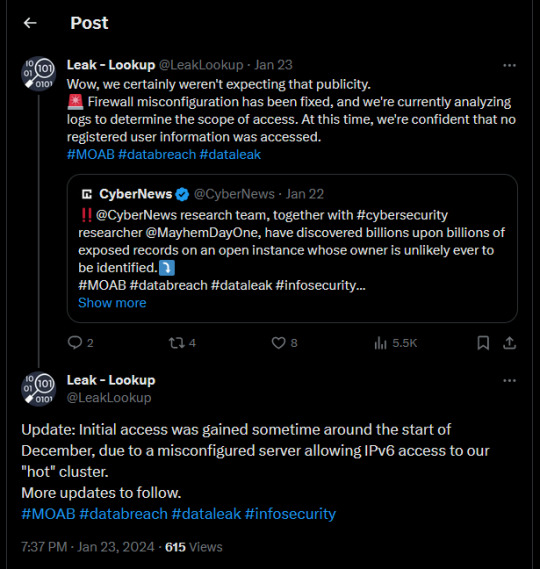
4 notes
·
View notes
Text
'Unpatchable' Vulnerability Found In Apple's Silicon #itnews #infosec
#vulnerability#apple music#apple#apple news#infosecurity#infosecawareness#infosec#infotech#information technology#it#i.t.#world news#breaking news#celebrity news#latest news#news#ausgov#politas#auspol#tasgov#taspol#australia#fuck neoliberals#neoliberal capitalism#anthony albanese#albanese government#mobilephone#mobile phones#phones#technology
2 notes
·
View notes
Text
Cyber Security Jobs UK

If your looking for the best cyber security jobs in the UK visit https://cybersecurityjobs.uk today which includes the best infosec jobs and cyber career opportunities online at the website for UK information security specialists
4 notes
·
View notes
Text
The Future Is Secure: Exploring the Top 10 Security Certifications for 2024
As technology continues to advance rapidly, cybersecurity remains a top concern for individuals and organizations alike. In an era where data breaches and cyber-attacks are becoming increasingly prevalent, investing in security certifications has never been more important. But with a wide range of certifications available, which ones are worth pursuing in 2024? In this article, we explore the top 10 security certifications that will dominate the industry shortly. These certifications are designed to equip professionals with the knowledge and skills needed to protect sensitive information, detect vulnerabilities, and respond to threats effectively. By acquiring these certifications, individuals can enhance their career prospects and demonstrate their expertise in a competitive job market. From the widely recognized Certified Information Systems Security Professional (CISSP) to the emerging Certified Cloud Security Professional (CCSP), we delve into each certification's key features and benefits. Whether you are an aspiring cybersecurity professional or a seasoned expert looking to stay ahead of the game, this article will provide valuable insights into the security certifications that will shape the future of the industry.
Top 10 Development Certifications to Enhance Your Career
1. Google Professional Cloud Security Engineer
Google Cloud has emerged as a significant player in the cloud services market, and securing these environments is a growing concern for businesses adopting Google Cloud services. This certification covers topics such as security best practices, regulatory compliance, and data protection. It is a valuable credential for professionals responsible for securing Google Cloud environments.
Why It is Important: As more companies migrate to Google Cloud, expertise in securing these environments is essential. This certification helps you build and maintain secure cloud solutions in one of the fastest-growing cloud platforms.

2. Cisco Certified CyberOps Professional
Cisco is a dominant player in networking and security solutions. The Cisco Certified CyberOps Professional certification is intended for professionals who work in security operations centers (SOCs) and focuses on incident detection and response. This certification covers advanced topics such as threat intelligence, security monitoring, and forensic analysis using Cisco security technologies. It is ideal for individuals looking to specialize in security operations.
Why It is Important: As cybersecurity operations become more sophisticated, having in-depth knowledge of security tools and incident response protocols is critical. Cisco’s strong presence in enterprise security makes this certification particularly valuable for SOC analysts and engineers.
More Information: Cisco CyberOps Professional Certification
3. AI CERT’s AI+ Security & AI+ Ethical Hacker
Overview: The AI+ Security and AI+ Ethical Hacker certifications from AI CERT’s focus on leveraging artificial intelligence (AI) in the realms of cybersecurity and ethical hacking.
AI+ Security emphasizes the application of AI technologies to enhance cybersecurity measures, including AI-driven threat detection, automated response systems, and machine learning for improved security. It is designed for professionals aiming to integrate AI into security practices.
AI+ Ethical Hacker highlights the use of AI in ethical hacking and penetration testing. This certification covers AI-powered tools for vulnerability assessment, threat modeling, and security testing, focusing on how AI can be used to identify and mitigate security risks effectively.
Ideal For:
AI+ Security: Security analysts, AI practitioners, and IT professionals interested in AI-driven security solutions.
AI+ Ethical Hacker: Ethical hackers, penetration testers, and cybersecurity professionals looking to incorporate AI into their security assessment practices.
Why They are Essential: Both certifications demonstrate advanced expertise in applying AI to enhance security and ethical hacking efforts, making you a valuable asset for organizations seeking to adopt innovative technologies for cybersecurity and risk management.
More Information:
AI+ Security
AI+ Ethical Hacker

Use the coupon code NEWCOURSE25 to get 25% OFF on AI CERT’s certifications. Visit this link to explore all the courses and enroll today.
4. Certified Information Security Manager (CISM)
Unlike other technical certifications, CISM focuses on the managerial aspects of security, such as risk management and aligning security initiatives with broader business goals. This certification is ideal for professionals looking to step into leadership roles, such as IT directors or security consultants.
Why It is Important: CISM is invaluable for professionals looking to bridge the gap between IT security and business leadership. It is a must-have for those seeking to manage security at a strategic level.
More Information: CISM Certification
5. Certified Cloud Security Professional (CCSP)
As cloud computing adoption accelerates, securing cloud environments has become a top priority for businesses. The Certified Cloud Security Professional (CCSP) certification, also offered by (ISC)², is tailored for professionals responsible for securing cloud infrastructures and services. CCSP covers crucial areas such as cloud architecture, governance, risk management, and compliance. With organizations increasingly shifting their workloads to the cloud, professionals with cloud security expertise are in high demand.
Why It is Important: Cloud security is becoming a critical part of overall cybersecurity strategies across industries. This certification is essential for those looking to secure cloud infrastructures and protect sensitive data in the cloud.
More Information: CCSP Certification
6. Microsoft Certified: Security, Compliance, and Identity Fundamentals
Microsoft remains a dominant player in enterprise IT infrastructure, and its security offerings are becoming increasingly critical as organizations move their operations to the cloud. The Microsoft Certified: Security, Compliance, and Identity Fundamentals certification is ideal for professionals working within Microsoft’s ecosystem. This certification focuses on the basics of security, compliance, and identity management using Microsoft Azure. It covers core concepts such as Azure security, Microsoft 365 compliance, and identity protection.
Why It is Important: As organizations continue to rely on Microsoft technologies, having expertise in securing these environments is a valuable asset. This certification provides foundational knowledge in securing Microsoft services, which are widely used across industries.

7. AWS Certified Security – Specialty
Amazon Web Services (AWS) is the leader in cloud services, and securing AWS environments is crucial for businesses that rely on the platform. The AWS Certified Security – Specialty certification is designed for individuals with deep knowledge of AWS security best practices. It covers topics such as encryption, incident response, identity, and access management (IAM), and compliance. This certification validates your ability to secure AWS workloads, making it a key credential for professionals working with AWS.
Why It is Important: As AWS continues to dominate the cloud services market, this certification equips you with the skills needed to protect critical data and systems hosted on AWS, ensuring security and compliance.
More Information: AWS Security Certification
8. Certified Information Systems Security Professional (CISSP)
The Certified Information Systems Security Professional (CISSP) is considered the de facto certification for experienced cybersecurity professionals. Managed by (ISC)², this globally recognized certification covers a wide range of security topics, including risk management, software development security, and cryptography. CISSP is aimed at professionals who design, implement, and manage security programs to protect organizations from complex cyber threats. With a rigorous exam and the requirement of five years of work experience in at least two domains, CISSP signifies an elevated level of expertise.
Why It is Important: CISSP is a highly sought-after certification for leadership roles such as Chief Information Security Officer (CISO) or security consultant. It is recognized as a benchmark of excellence across various industries.
More Information: CISSP Certification
9. Certified Ethical Hacker (CEH)
The Certified Ethical Hacker (CEH) certification from the EC-Council stands out as a crucial credential for professionals in ethical hacking and penetration testing. It trains security professionals to think like malicious hackers by identifying vulnerabilities in systems and networks before they can be exploited. Ethical hackers play a vital role in helping organizations shore up their defenses by proactively testing and securing their IT infrastructure. This certification covers a wide array of topics, from social engineering to malware threats and web application security.
Why It is Important: As cyber threats grow in complexity, ethical hacking has become a critical part of organizations’ cybersecurity strategies. CEH validates your skills in identifying vulnerabilities and defending against real-world cyberattacks.
More Information: CEH Certification
10. CompTIA Security+
The CompTIA Security+ certification is one of the most widely recognized entry-level certifications in the cybersecurity field. It provides a broad introduction to cybersecurity concepts such as network security, threat management, and cryptography. Security+ is vendor-neutral, meaning it covers a wide range of technologies and is often seen as a gateway certification for those starting in cybersecurity. It is also widely recognized by employers, making it a solid choice for professionals looking to launch their careers in security.
Why It is Important: CompTIA Security+ offers a solid foundation in cybersecurity and is often a prerequisite for more advanced certifications. It is an excellent starting point for individuals new to the field.
More Information: CompTIA Security+
Conclusion
The world of cybersecurity is ever-changing, and staying ahead of the curve requires continuous learning and adaptation. These certifications are not just badges of honor but also critical assets that equip professionals to protect organizations against a growing array of cyber threats. Whether you are focused on cloud security, AI security, or network protection, earning one or more of these certifications will give you the tools and knowledge to thrive in the cybersecurity landscape of 2024 and beyond. By investing in these certifications, you are not only advancing your career but also contributing to a safer, more secure digital world. Whether you are starting with foundational certifications like CompTIA Security+ or diving into specialized areas
#CyberSecurity#InfoSec#DataSecurity#SecurityCertifications#TechCareers#ITSecurity#EthicalHacking#NetworkSecurity#SecureFuture#2024Certifications#TechTrends2024#CareerDevelopment#TechLearning#CertificationGoals#CyberDefense#TechSecurity#CloudSecurity#SecurityCareers#DigitalSecurity#InfoSecurity#SecureYourFuture#HackerSkills#DataProtection#SecurityExperts#CareerInSecurity#ProtectYourData#TechCertifications#InfoSecPros#2024Security
0 notes
Text
Technical debt is the topic nobody wants to talk about. Is the emergence of AI an opportunity or a threat as it relates to this problem? How does your technical debt impact your growth and innovation?
Key Takeaways:
Technical debt, accumulating from outdated systems and quick fixes, poses significant security risks and stifles innovation.
The cost to address technical debt is estimated at $1.52 trillion, with broader impacts costing the U.S. $2.41 trillion annually.
The emergence of AI in software development might worsen technical debt by encouraging rapid, less optimized coding practices.
Strategies to mitigate technical debt include prioritizing system maintenance over new developments and employing AI for code analysis and updates.
Addressing technical debt is crucial for both economic efficiency and national security.
https://on.wsj.com/3QUZtQl
0 notes
Text

Messe Masters is a top-notch exhibition stand design company that has been serving exhibitors for years with the best and most affordable exhibition stands and services. So, if you are planning to exhibit at Infosecurity, connect with us at https://www.messemasters.com/ for the best exhibiting experience.
#infosecurity#INFOSECURITY2024#Infosecurityexpo#exhibition#exhibitionstand#exhibitionbooth#exhibitionbuilder
0 notes
Text

As the name says, INFOSECURITY EUROPE is an exhibition for information professionals, and if you are one of them or interested in presenting you are brand here, visit https://www.expostandservice.com/ for the best presence at the display ground.
#infosecurity#INFOSECURITY2024#Infosecurityexpo#exhibition#exhibitionstand#exhibitionbooth#exhibitionbuilder
0 notes
Text
Osintgram – An OSINT Tool on Instagram
🔍✨ Exciting News Alert! ✨🔍
Hey, fam! 👋 Just dropped a fresh new blog post on my site, and I'm pumped to share it with you all! 🚀 Today, we're diving into the world of OSINT (Open Source Intelligence) on Instagram with my latest article: "Osintgram – An OSINT Tool on Instagram" 📸💻
Ever wondered how to harness the power of Instagram for intel gathering? 🤔 Well, wonder no more! Osintgram is here to level up your OSINT game, providing insights and tools to navigate the vast sea of Instagram data. 🌊💡 From gathering valuable info for research to enhancing your investigative skills, this tool is a game-changer! 🕵️♂️🔍
Check out the full post here ➡️ Osintgram – An OSINT Tool on Instagram
And don't forget to spread the word! 📣 Share with your fellow info enthusiasts and let's explore the world of OSINT together! 🌐💬
#OSINT#Instagram#Osintgram#OpenSourceIntelligence#InfoSec#Investigation#DigitalForensics#TechTools#InfoSecurity#CyberSecurity#DataAnalysis#OnlineResearch#DigitalFootprint#TechBlog#NewPost#Blogging#MenofLetter 🔎📲
0 notes
Text
Infosecurity Exhibitor List 2024

Infosecurity 2024 is the largest information security professional conference in Europe. Connect with industry specialists with our Infosecurity Exhibitor List 2024!
0 notes
Text
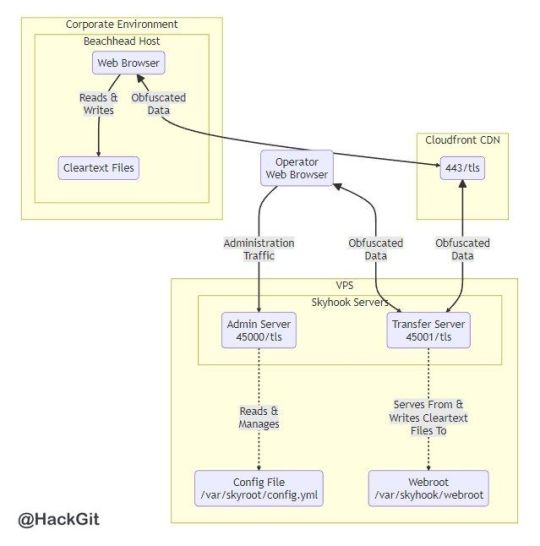
[Media] Skyhook
Skyhook
A REST-driven web application used to smuggle files into and out of networks defended by perimeter controls that inspect and act on traffic perceived to contain malicious content.
https://github.com/blackhillsinfosec/skyhook
#infosec #pentesting #redteam
9 notes
·
View notes
Text

arguing for people to write down and admit to what they own. #infosec #inventory #assets #cmdb
0 notes
Text
Insider Threats: Understanding, Mitigation, and Prevention Strategies
Explore the intricate world of insider threats in cybersecurity, uncovering their nature, motivations, and strategies for mitigation and prevention. Understand the risks and consequences posed by insiders, and learn how organizations can defend against these formidable challenges. Stay informed, stay secure, and prioritize proactive measures to safeguard sensitive data and assets.

Read More..
#InsiderThreats#Cybersecurity#Mitigation#Prevention#DataSecurity#RiskManagement#InfoSec#SecurityStrategies#InsiderRisk#DataProtection#CyberDefense#InfoSecurity#ITSecurity#RiskMitigation#SecurityAwareness
0 notes
Text

Are you ready to explore the advanced intricacies of persistence in networking and take your understanding to the next level? DC Lessons offers an enlightening course tailored for IT professionals, network administrators, and anyone eager to master the art of maintaining connections and ensuring uninterrupted network services. https://www.dclessons.com/persistence-advance-persistence-concepts
#Persistence#AdvancedPersistence#DClessons#CyberSecurity#InfoSec#SecurityTraining#CyberAware#LearnSecurity#ThreatDetection#SecurityEducation#PersistentThreats#IncidentResponse#CyberDefense#InfoSecurity#ThreatIntelligence
0 notes
Text
Velvyslanectví Ruska na Slovensku využívá Facebook pro informační operace
Velvyslanectví Ruské federace na Slovensku je prodlouženou rukou Kremlu. Jeho profil na Facebooku je nejaktivnější ze všech ruských a čínských velvyslanectví v Evropě. Od začátku války Ruska proti Ukrajině na něm bylo zveřejněno téměř 5 tisíc příspěvků.
International Republican Institute (IRI) spustil monitorování aktivit ruských a čínských velvyslanectví v Evropě na Facebooku. Nejaktivnější ambasádou působící v evropském státě je velvyslanectví Ruské federace na Slovensku. Od začátku války do 3. dubna 2023 zveřejnilo na svém facebookovém profilu až 4 972 příspěvků.
#hybridní válka#dezinformace#manipulace#fake news#konspirace#hoax#Rusko#Slovensko#Infosecurity#vlivové operace
0 notes