#Interface and abstract class
Explore tagged Tumblr posts
Text
What is interface and abstract class in Java?

In Java training, both interfaces and abstract classes are used to define abstract types, which means they cannot be instantiated directly but serve as blueprints for concrete classes to implement or extend. However, there are key differences between interfaces and abstract classes in terms of their functionality and usage:
Abstract Class
Keyword: Abstract classes are defined using the abstract keyword.
Methods: Abstract classes can have both abstract (unimplemented) and concrete (implemented) methods. Abstract methods are declared using the abstract keyword and must be implemented by concrete subclasses.
Fields: Abstract classes can have instance variables (fields) that can be inherited by subclasses. These fields can have access modifiers like public, private, or protected.
Constructor: Abstract classes can have constructors. These constructors are typically used to initialize fields in the abstract class.
Inheritance: Abstract classes support single inheritance, which means a Java class can extend only one abstract class. This can be a limitation when a class needs to inherit from multiple sources.
Usage: Abstract classes are used when you want to create a common base class with some default implementation that can be shared among multiple subclasses. Subclasses can extend the abstract class and provide concrete implementations for the abstract methods.
Interface
Keyword: Interfaces are defined using the interface keyword.
Methods: Interfaces can only have abstract methods (methods without implementation). In Java 8 and later versions, interfaces can also have default and static methods with implementations.
Fields: Interfaces can define constants (public static final fields), but they cannot have instance variables or non-constant fields.
Constructor: Interfaces cannot have constructors, as they cannot be instantiated directly.
Inheritance: Java supports multiple inheritance through interfaces, which means a class can implement multiple interfaces.
0 notes
Note
Apologies for the dumb question and loads of personal information, but..
I have severe moral ocd, and in the past the exploitation has actually caused me eating issues. I’d get intensely guilty whenever I ate anything bc I couldn’t avoid thinking of the exploitation that occurred to get it here and I honestly started avoided eating.
is that what im supposed to do? I know there’s no ethical consumption under capitalism but my sustained existence is reliant on food from the exploitative world of global “trade”, medicine from the oppressive pseudo jails of the psychiatric system, and technology running on copper and cobalt that people suffered to mine. I claim to be a leftist, but my sustained quality of life, god, my entire life, is dependent on the imperial core continuing to extort the rest of the world. Should I just give up?
nah. ultimately if you're a socialist you have to understand that what you do as an individual is--politically speaking--irrelevant. it's good to be aware of the harms that were done in the process of production, but it's both a political dead end and personally self-destructive to then flagellate about that. (and to be clear, if that awareness is impossible for you to maintain without falling into disordered eating behaviours, you don't need to be that aware--again, this isn't about moral duty. genuine socialist politics are never about individual moral duty, or about being a good person. there is no level of Thought or Awareness or Conscienciousness that can become a lever of meaningful political action.)
the harms have already been done by the time the commodity exists for you to access--you're not participating in or exacerbating them by using the commodity. even if you did find a way to live completely without interfacing with the systems of exploitation, those systems would continue unabated. they don't care about you. the idea that if everyone spontaneously individually decided to stop using the goods that are generated by exploitation then exploitation would end is laughable in both premises and conclusion.
you have to look at this on a material level--the 'harm' is not an abstract quality that gets infused into the fruit or the medicine or the iphone, it's not haunted, you cannot show me an atom of 'harm radiation' emitted by an out-of-season banana--the 'harm' is a series of actual events taking place somewhere in the world. and the way to combat that has nothing to do with the personal consumption of individuals--it has everything to do with organized efforts, with groups of people taking collective action to stop that harm from happening.
you're not god. you're not a dynasty warriors character. you vs. united fruit and foxconn is a losing battle. you alone can't change the world in any way that matters, good or bad. the only thing you can do is join your energy to a group, to participate in class struggle. to unionize or join a party or participate in a mutual aid network. class struggle, the marxist analysis of class struggle, the only meaningful vector of political action across myriad forms, cannot be reached or analysed through the lens of 'do my personal consumer choices make me a good or bad person'. i know it is obviously difficult to do when we live in a society that focuses on consumer choice as the be-all and end-all of personal and political and moral expression, but you have to reject that question outright.
socialism is not catholicism--the aim of left-wing politics is not to live virtuously. it is to unite as members of the working class and improve all of our lives. focus on uniting first--find the people around you who you can form organizational bonds of solidarity with--and then figure out how to participate in the class struggle together. that's the only way forward. everything else is a trap, a dead-end, or in this case, pointless self-abnegation. good luck, comrade.
610 notes
·
View notes
Text
Sam Reviews: Phoenix Point, part 1
Phoenix Point is down to ten bucks on GOG, DLC included!
I bought it, figuring even a half-decent XCOM clone is worth it for ten bucks. So far it feels like a $10 game indeed. I'm probably not going to finish it before the sale ends, I have a job, so here's my initial impressions for those interested and I'll come back with part 2 later.
Tutorial missions, fine. First regular mission against crab monsters, fine. Second regular mission pits me against gun-happy human bandits, and I am unpleasantly surprised that they return fire whenever they're shot at, getting 4 counter-attacks in a turn if 4 people shoot at them, they even "return fire" upon having a grenade thrown at them.
Solution: run up and bash them in the head with the butt of a gun repeatedly, they don't get to return fire from that. I grumbled about that, and the game feels like 'that' repeatedly.
I didn't like the puzzle boss nature of infinite return fire. One return fire per turn would have been cool, and enabled tactical counterplay options. Unlimited return fire breaks the action economy, breaks my immersion for the game abstraction of "action points", and makes me feel this is going to be a game about cheesing AP limits and ruleslawyer combos. Also, the infinite return fire ability was on multiple nameless minions in that mission, not even reserved for a boss. Bash bash bash bash!
I didn't like the lack of game hints in this context. I had Hints turned on for a first run at low difficulty. The Hints make suggestions for what to research, how game mechanics work, and provide informative popups the first time a new strain of crab monster appears. But there was no Hint popup about the first encounter with an enemy having the Return Fire ability, no tooltip on mouseover of enemy, nor was there any indication of what actions trigger Return Fire, despite this being significantly more impactful than "this crab monster regenerates".
I didn't like the solution, which felt like a rules loophole rather than a sensible way to approach rapid-firing enemies. Oh yeah here's a guy who can interrupt your turn to shoot multiple times per turn, you should all walk up to him and punch him and he'll politely submit to the beatings.
I really didn't like that compared to recent XCOM games, Phoenix Point added a micromanagement tracker for Weapon Durability, and bashing the return-fire-goons in the head damages your weapon! Also they brought back ammo management, so now your weapon has two stats that can run out during combat.
But I also recognize that these things aren't bugs or crashes or typos or other objectively wrong things about the game, they're design decisions that I disagree with. The game runs fine. I have a series of grumbles and no dealbreakers.
Moving on from the Return Fire-associated crap...
This is an XCOM-genre game, definitely. It has base building, squad management, research and production, capturing crab monsters for research, psychic mind control, a strategic "Geoscape" layer and numerous tactical battle missions. The one thing that's oddly missing is gear upgrades. New gear is mostly sidegrades and tactical options, on the other hand it offers far stronger character upgrades than in most XCOM games, to the point of looking partly like a CRPG with classes, levels and skill points.
The Geoscape has more content than the waiting game that was some previous xcoms. There are other factions moving on the map, there's some trade and diplomacy with them, there are unknown sites to explore, you reactivate old bases instead of building them from scratch. Sometimes this means clearing them of crab monsters.
The Phoenix Point interface inherits a lot of XCOM 2's cutscenery that I dislike. It is very beautiful, very zoomed in, and wants to make sure you see it. There's frequent waiting to watch stuff resolve, and the game insists on having the camera follow unimportant actions like the run animation of every soldier's every move, and locking the interface during this. Move orders (particularly out of sight of enemies) should not hog control, I should be able to tab to the next soldier and begin giving a new move order immediately after the previous! Each individual animation is short, but multiply it by several soldiers, on each of several turns, on each of several missions, and my frustration at an unresponsive interface accumulates.
The zoom-out is limited. Soldiers will frequently be so far away from each other that I can't see them on the same screen, and have to pan back and forth. Bleh.
The gun system is quite detailed with damage types, damage values, accuracy modifiers, weapon ranges, armor, armor-shredding weapons, body part targeting and hit location, disabled limbs, bleeding, cover, et cetera. The game then offers options to skip a lot of this gunnery where enemies get to resist, and instead go for special abilities that Just Work, like War Cry:

AOE, autohit, no save, renders most enemies unable to attack for a turn.
About that limbs stuff, Phoenix Point has tried hard to make hit locations relevant. Crab monsters have game-relevant organs and limbs that can be disabled for far less damage than it takes to kill the whole monster. It's neat, but feels a little underwhelming. I don't blame the devs much for this, balance is hard when there's hefty player optionality plus RNG, and there's a fine line between making targeting relevant and making a monster the Shootmeinthegland monster where shooting it in the gland simply becomes the new default target instead of shooting it in the head/center mass.
Guns are weak, and armor is powerful as part of making limb targeting relevant. Also, armor-shredding weapons. This feels related to the CRPG class-and-level stuff: with the smaller squad and the more personalized characters and the more important individuals, the game has to give more leeway for characters to survive being hit to avoid player frustration. We've moved a long way from X-COM:UFO where casualties were routine and replacements were cheap.
I don't know if it's good or bad that the game plays "fair" about the least relevant nameless NPCs being similarly padded, but I know one of my mutuals will hate this combination of health padding and detailed targeting:
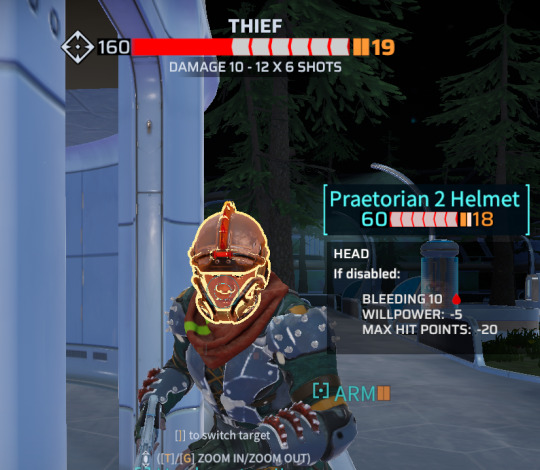
I have caught this thief at close range (2 tiles). I am about to launch a six-round burst from my character's assault rifle into his head. The targeting reticle, the highlighted yellow outline, and the info popup all agree that these bullets will go into his head if I fire here and now. The segmented bar at the top indicates that the result of close-range burst fire to the head through the front of the face is that the thief will lose about half his hitpoints.
To underscore that I've gotten a head hit, not a glancing blow off the helmet, the game displays the thief with a bloody face and blood-splattered clothes after the shot. But he lives. Somehow.
There's also a plot to Phoenix Point. I don't play xcoms for the plot, but there's definitely been some work on the plot beyond "kill and loot aliums :)". After the second world war, blah blah secret organization, moonbase, something something precursor civilization. It looks like good lore, I'll re-read the accumulated notes when I have more notes and fewer darkly hinting clue-scraps bereft of context.
(update: part 2)
26 notes
·
View notes
Text
tabletop role-playing games, as a medium i think, are predisposed to crafting reals, on top of it being largely an exercise of language.
i'm using "real" right now as a basic "something that is completely true thing." in a sense, role playing game design is reality-crafting.
this means that every mechanic and every word used in the game, down to the language, is a way of crafting a real wherein the players must accept that is real (within that space). the reality is the bounds of the fiction and also the major expressive influence into the player's minds. however in a very weird positivist way, what mechanics exist in a game reify what the game says is real, and what doesn't exist doesn't exactly mean something isn't real. so instead of a real/unreal dichotomy we have a real/real (in fiction)/implication(pseudo real)/unreal
so for example: a game might have Stats, Classes, and mechanics for making attack rolls. all of these are Real, and they inform the fiction (a high STR might mean your character is strong, being of a FIGHTER means you're good at fighting and you can pull off maneuvers, making attack rolls is you committing physical violence on another). So they're both real and real in fiction. the localized reality around player characters now exist and they interact with the game through these reals.
now these things might be non-diegetic (frex, a FIGHTER (CLASS) might not actually exist within the game setting, they're archetypical representations, which is something D&D 4e and D&D 5e do), but that doesn't matter: those things are now real due to game design. this means there ARE fighters in your game, even if there is only one kind of fighter that the PC is, there are still fighters.
going further, these Reals also imply something about the established game world. these are not yet the pseudo-reals: so for example, a game that has CAP Skills (skills that cap any other skills you might use while doing something within their field, such as Horseback Riding [a Riding Skill 3 might mean you can only add +3 to when you're doing Melee Combat despite your Melee Combat being at +7, etc.]) this presupposes then that someone who isn't good at Riding cannot be as effective with their martial skill despite having been skilled at martial skill for years.
is this realistic to real life? it doesn't matter: with that established within the game mechanics, that is now what's Real there. and in role-playing you must follow along the Reality crafted there. this has a number of pseudo-reals (implications) such as (cavalry are all good at horseriding, etc.) but the importance of pseudo-reals is that these are things the table (the player aspect) can interface with as they wish. those things which the player has no choice but to interface with are the highest of reals in a roleplaying game
your choice of language informs this even further. not just the fact that you choose to write it in english (tagalog, spanish, etc. expresses things and imposes different priorities when it comes to real) but the wording choice you choose. frex: having INTELLIGENCE as a Stat can be somewhat ableist. what does high INTELLIGENCE mean? aren't there different kinds of smarts, is knowledge the same? or is this an abstraction? but is it a meaningful abstraction or an abstraction brought about by historical momentum (it's what D&D used). why is INTELLIGENCE a meaningful abstraction but STRENGTH and CONSTITUTION are split? these are all arbitrary until it isn't, and you must establish a real to live in the imagined space (that is, the fiction). i'm not saying the 6 stat array is a bad thing mind you but i think it's useful to understand why you have it in there in the game. if it's just because it's the most well known stat array then that's fine i guess
finally, what reals you put into the game is inherently informed by your own worldview. it actually doesn't have to be (that's the point of creation) but commonly game designers simply inject their worldview into the games as real and recreate that real into their tabletop rpg (frex, misogynists who think its realistic for men to be stronger than women, capping women's STR stats etc.) so choosing what is real and what isn't is a matter of paradigm shifting and realizing that not all realities irl are the same (not to go into metaphysics and sociopolitical philosophy)
#waksthoughts#absolutely unhinged word vomit#about ttrpg realism and the things that influence a reality#important to note that these are completely unreformed thoughts#like this is word vomit straight from the chaos of the soul#pure vibes based writing#nothing final#no authority#just vibes#take what works and reject what doesn't
129 notes
·
View notes
Text

🔒 PANDORA – GLUTTONY DIVISION DOSSIER
SUBJECT: SKELTON, ISRAEL JANNICK Call Sign: Shepherd Clearance Level: ██/███ (Tier-9 Gluttony Access Only) Dossier ID: PND-GLUTTONY/Δ-HXN19-553
BIOLOGICAL OVERVIEW
Field Entry:
Full Name: Israel Jannick Skelton Date of Birth: 14 February 1993
Height:
6’2”
Weight:
172 lbs Place of Birth: Copenhagen, Denmark Nationality Dual – Danish / Classified (Naturalized ██████)
Species: Human/Shifter (Canine Variant: Belgian Malinois) Shifter Onset ██/██/20██ (Classified Biogenic Incident – Operation REBIRTH) Affiliation: Pandora Initiative – Gluttony Division Former Affiliation NATO Tactical Recon / K9 Division (BLACKLIST OPS: DEN-56) Status:
Active / Monitored
INTERNAL EVALUATION REPORT
SECTION I: SHEPHERD ABILITY OVERVIEW
Classification: Tier-III Controlled Morphotype (Caniform Subtype) Baseline Genome: Homo sapiens (genetically modified) Overlay Morphotype: Canis lupus familiaris (Shepherd-class phenotype)
A. Morphological Capabilities
Voluntary Shifting: Subject is capable of initiating full or partial transformation at will.
Partial Shifts: Include selective enhancement of olfactory organs, musculoskeletal extensions (e.g., digitigrade posture), and dermal layer modulation.
Full Shift: Yields complete quadrupedal canine form with high locomotion efficiency, camouflage benefit, and enhanced field mobility.
B. Structural Integrity & Recovery
Accelerated Tissue Regeneration: Healing factor calibrated to 4.7× human baseline; bone fractures re-knit in <24 hrs under monitored stasis.
Immune Compensation: Near-total resistance to conventional pathogens and most field-grade toxins.
Blood Reoxygenation Efficiency: Elevated hemoglobin turnover rate for extended physical exertion without hypoxia.
SECTION II: SENSORIAL AND PHYSICAL ENHANCEMENTS
A. Sensory Expansion
Olfactory Resolution: 40× human range. Capable of isolating individual scent trails from mixed source environments (urban, battlefield, subterranean).
Auditory Range: Detects ultrasonic emissions up to ~62 kHz. Has been used to triangulate active listening devices and microdrones.
Night Vision Equivalent: Tapetum lucidum layer in canine form provides low-light visual acuity rivaling next-gen thermal optics.
B. Physical Conditioning
Enhanced Strength: Estimated peak output at 3.2× human maximum. Documented ability to breach reinforced doors, carry 200+ kg under duress.
Agility & Speed: Max quadrupedal velocity recorded at 58 km/h (full sprint).
Climatic Adaptation: Fur density modulation in canine form provides heat insulation in low-temp environments.
SECTION III: COGNITIVE PROFILE & BEHAVIORAL PERFORMANCE
A. Tactical Intelligence
Maintains operational cognition during transformation. No evidence of regression to feral behavior unless provoked by trauma triggers (see Incident #091).
Proficient in abstract planning, real-time threat analysis, and independent vector rerouting under compromised comms.
B. Emotional Regulation
Suppressed affect during operations. Exhibits high detachment, particularly in canine state.
Displays intuitive reading of emotional cues from both human and animal subjects. Empathic mimicry appears tactical rather than authentic.
C. Canine Subject Interaction
Capable of issuing non-verbal commands to domestic dogs and ferals. Effective in disrupting or redirecting threats posed by trained K9 units.
Behavioral reinforcement strategies suggest intuitive understanding of canine dominance hierarchies.
SECTION IV: TECHNICAL EQUIPMENT INTERFACE
Device: VOX-HALO UNIT 7 (Speech Relay Collar)
Purpose: Enables Shepherd to communicate in canine form via neural impulse-to-speech synthesis.
Construction: Titanium-carbide housing; layered biometric mesh; embedded Q-band encryption node.
Functionality: Interprets subvocal electrical signals and brainwave patterns to articulate human-equivalent language output.
Limitations:
Latency (~250–300 ms) under stress conditions Signal disruption in EM-dense zonesRequires re-sync post-shift for phoneme calibration
SECTION V: OPERATIONAL SPECIALIZATIONS
Bio-Tracking & Residue Analysis (real-time genetic target ID through scent/vocal trace matching)
Counter-Persona Interrogation Resistance (fragmented memory encoding prevents strategic leaks if captured)
Behavioral Manipulation (direct influence over canine populations; contextual manipulation of human behavioral cues)
Tactical Foresight & Pattern Anticipation (predictive modeling in unpredictable terrain)
Environmental Navigation & Substructure Mapping (notably high spatial memory in complex architecture)
Long-Term Surveillance in Hostile Terrain (maintains passive reconnaissance in feral state undetected)
Pack-based Engagement Strategies (demonstrates ability to coordinate with autonomous or semi-autonomous canine assets)
SECTION VI: LIMITATIONS AND RISK FACTORS
Shift Instability Under Neurological Stress: Intense psychological or physical duress can cause involuntary shifting or memory fragmentation.
Feral Lock States: Extended time in canine form can lead to suppressed human identity markers; subject may become unresponsive to recall protocols.
Verbal Delay in Shifted Form: Despite the VOX-HALO collar, speech output remains delayed and prone to error in rapid-communication scenarios.
Hostile Conditioning Thresholds: Displays lower resistance to certain ultrasonic frequencies used in anti-animal deterrents.
Emotional Dysregulation Triggers: Strong emotional stimuli related to past trauma (see Incident #030) can disrupt task focus and cause aggression or withdrawal.
Operational Limitation Post-Morphogenic Exposure Risk Evaluation Summary: Shepherd undergoes full cellular deconstruction and reformation during morphogenic transitions between human and caniform states. Upon reversion to human form, all integrated clothing, tactical equipment, and external gear are nullified by the biological transmutation process. The subject re-emerges nude, without protective coverage or field-ready attire.
Operational Risks Identified:
Environmental Exposure: Susceptibility to hypothermia, chemical agents, or abrasions in uncontrolled terrain.
Tactical Vulnerability: Immediate post-shift incapacity to engage, defend, or retreat due to lack of armor or armament.
Unit Disruption: Potential for distraction, morale disruption, or psychological discomfort among human personnel.
Public Exposure Risk: In civilian-adjacent operations, post-shift emergence could compromise mission secrecy and provoke incident escalation.
Discretion Protocol: Visual engagement of Shepherd during reversion is to be limited. Non-essential visual contact is to be restricted.
Additional Notes: The issue remains physiological and currently unresolvable via augmentation without compromising morphogenic fluidity. A prosthetic gear-retention solution is under review but deemed non-viable in rapid-shift scenarios as of the latest R&D cycle.
SECTION VII: INCIDENT LOG EXCERPTS
Incident #030 – Exposure to Stimulus ("Whistle Echo Variant") Date: 14 Jan 2023 Outcome: Temporary feral lock lasting 5h17m. Operative displayed territorial aggression. No operatives injured. Induced via unknown high-frequency pattern in proximity mine.
Incident #091 – Tactical Disengagement (Morocco Urban Cleft) Date: 26 Sep 2024 Outcome: Subject entered canine form mid-assault and failed to re-establish identity for 3.4 hours. Autonomous escape and later regrouping suggest partial operational memory retention. Collar data lost in transit.
Incident #117 – Forced Capture Test Date: 09 Feb 2025 Outcome: Subject resisted physical interrogation for 72 hours. Under simulated neural interrogation, subject's memory nodes shifted erratically, preventing clean data extraction.
PSYCHOLOGICAL PROFILE [CONFIDENTIAL – REDACTED]
Diagnosed with Controlled Identity Dissociation due to dual consciousness bleed Behavioral Overlay: Canine Imprinting ResidualsCompulsion: Cataloging animal trauma in encrypted field logs Displays signs of interspecies empathy inversion: higher emotional response to canines than humans Regular debriefings required post-shift to confirm cognitive cohesion Trust rating: Satisfactory (fluctuating) Loyalty tier: ██ (Observed Deviations) Note: Obedience - Absolute.
Watchlist Tag: "If he breaks, do not attempt containment. End him."
Behavioral Note (per Division Psych Lead): “If Shepherd is lost to his canine identity mid-field, he becomes invisible—but also irretrievable. We don’t track him when he's in that state. We observe. From afar.”
CLASSIFIED — AUTHORIZED MEDICAL PERSONNEL ONLY
Subject: Medical and Enhancement History Report Operative Call Sign: Shepherd Date: May 20, 2025 Prepared by: Division Medical and Biotechnical Services
Incident Date: 2022-04-15 Injury: Shrapnel wounds to left forelimb and minor lung puncture Outcome: Immediate field stabilization, followed by surgical removal of shrapnel fragments and lung repair at forward operating base hospital. Six weeks recovery with physical therapy. Enhancements/Surgery: Introduction of subdermal armor plating in left forelimb to prevent similar injuries; enhanced respiratory efficiency implant to improve oxygen intake post-injury.
Incident Date: 2023-01-10 Injury: Compound fracture of right hind leg due to blast exposure Outcome: Emergency orthopedic surgery including insertion of titanium rod and joint reconstruction. Extended rehabilitation including advanced kinetic therapy. Enhancements/Surgery: Cybernetic tendon reinforcement installed post-healing to improve joint strength and durability; pain receptor modulation implant for increased pain tolerance.
Incident Date: 2023-07-22 Injury: Severe lacerations and nerve damage from close combat engagement Outcome: Microsurgical nerve repair and skin grafts conducted; partial sensory loss initially observed with gradual return over three months. Enhancements/Surgery: Neural interface upgrade for enhanced reflexes and motor control; dermal regeneration accelerator installed to speed up healing in future injuries.
Incident Date: 2024-03-05 Injury: Traumatic brain injury (TBI) caused by explosion shockwave Outcome: Intensive neurorehabilitation, including cognitive and motor skill therapies; implanted neural stabilizer to reduce inflammation and enhance brain plasticity. Enhancements/Surgery: Neural enhancement implant to improve situational awareness and reaction times; protective cranial plating surgically added to prevent future injuries.
Incident Date: 2024-11-17 Injury: Severe torso bruising and multiple rib fractures from vehicle rollover. Outcome: Surgical realignment of ribs, internal stabilization with biocompatible materials, and extended recovery with respiratory therapy. Enhancements/Surgery: Enhanced muscular reinforcement in torso area to absorb shock better; advanced pain modulation system installed to maintain operational capacity under duress.
SPECIALIZATIONS
Shifter Reconnaissance – Stealth Tier III (Caniform)
Bio-Tracking and Genetic Residue Analysis
Behavioral Manipulation (Canine and Human Subjects)
Canine-Based Infiltration Techniques (Enhanced Scent Masking, Terrain-Adaptive Stealth)
Counter-Persona Interrogation Resistance
Advanced Tactical Evasion and Pursuit
Environmental Adaptation and Survival (Urban and Wilderness)
Canine-Enhanced Sensory Surveillance (Olfactory and Auditory Amplification)
K9-Assisted Target Acquisition and Identification
Rapid Response and Extraction Operations
Tactical Communication and Nonverbal Signaling
Close Quarters Threat Neutralization
Combat-Integrated Tracking and Flanking Maneuvers
Low-Visibility Movement and Silent Navigation
Enhanced Pain Tolerance and Injury Recovery
Psychosensory Signal Disruption (Canine Howl Emulation for Area Confusion)
Counter-Surveillance and Detection Evasion
Multi-Terrain Mobility and Climbing Proficiency
Operational Camouflage Adaptation (Fur Pattern Shifting and Texture Modulation)
LIMITATIONS
Canine Phenotypic Shift Cognitive Decline: Upon full transformation into canine morphology, higher-order executive functions and complex tactical reasoning are significantly impaired, resulting in reliance on instinctual behaviors that may hinder mission-specific objectives.
Verbal Communication Restriction: In canine form, expressive communication is limited to nonverbal signaling and basic command comprehension, thereby reducing effective real-time coordination with human operatives. To mitigate this, a custom-engineered neural-linked collar—designated Vox-Halo Unit 7—has been implemented.
Sensory Modality Vulnerability: Exposure to extreme environmental factors such as hyperthermia or toxic chemical agents attenuates olfactory and other heightened sensory functions, diminishing tracking and detection capacity.
Physical Trauma Susceptibility: Despite augmented regenerative and endurance capabilities, Shepherd remains vulnerable to high-impact ballistic trauma and sustained blunt force injuries, which transiently impair operational effectiveness.
Engagement Range Limitation: Combat proficiency is primarily restricted to close-quarters; proficiency with ranged weaponry is suboptimal, necessitating support elements for medium to long-range threat neutralization.
Cognitive-Identity Disassociation: Prolonged duration in canine form or repeated canine-hominid identity shifts may precipitate episodes of cognitive disorientation or temporary loss of self-awareness, compromising operational reliability.
Cybernetic Maintenance Dependency: Enhanced physical and sensory augmentations require scheduled recalibration and maintenance; operational degradation occurs in the absence of routine servicing or if systems are compromised.
Infiltration Countermeasure Sensitivity: Although adept in unconventional infiltration, Shepherd’s biological and sensory enhancements are susceptible to detection by advanced biometric and bio-signature surveillance technologies.
Manual Dexterity Deficiency: The canine anatomical form imposes significant limitations on fine motor skills, restricting capability for complex tool manipulation, technical sabotage, or field repairs.
Psychological Stress Response: Exposure to high-stress combat environments or trauma-associated stimuli can induce atypical behavioral responses, including heightened aggression or withdrawal, necessitating ongoing psychological evaluation and support.
SKILLS
Proficient
Close Combat Mastery
Acrobatics & Evasion
Perception
Battlefield Endurance
Stealth & Infiltration
Expertise:
Pain Tolerance
Substandard:
Seduction
Cryptograms & Codebreaking
KNOWN ANOMALIES
Subject retains partial "residual scent memory" across forms.
Exhibits involuntary memory recall of K9 partner deceased during Operation ███████.
Regular unauthorized logging of animal casualties.
🗂️ MISSION LOGS – CLASSIFIED SLTH OPS
MISSION: MOTHER TONGUE Location: Novosibirsk Oblast, Russian Federation Date: ██/██/20██ Objective: Infiltrate abandoned research site formerly operated under Soviet Directive Красный Глотка ("Red Throat"). Extract cognitive imprint data from canine-based neural wetware prototypes. Operative Assigned: Agent SHEPHERD (solo, Sloth insertion) Status: ✅ OBJECTIVE RECOVERED – SITE COMPROMISED Casualties: 3 (hostiles), 12 (canine test subjects) Post-Op Psychological Score: Borderline-Flagged (Tier 2 Dissociation Signs Present)
Extracted Log [REDACTED]:
“Site was frozen beneath six meters of ice and silence. It didn’t feel abandoned. The dogs were still there—wired, suspended. No sedation. Some were still blinking. They kept looking toward the corner of the room… as if something was there. I didn't see it. But I heard it. A sound like breathing through water.”
“Data was stored in bone. Implanted microchips behind the orbital ridge—wetware designed to carry imprint memories. They weren’t studying obedience. They were recording language. The dogs were speaking… but not with mouths. With static.”
“I euthanized the subjects. Quick. Clean. I kept one piece. Just one skull. It still hums when I touch it.”
RED FLAG: Agent extracted unauthorized relic (biological remains) against directive. Post-Mission Directive: Agent under Tier-1 Cognitive Watch for residual imprint bleed. Subject claims no memory of return flight or initial post-op debrief.
Internal Note [Director ███████]:
“We told him to extract code. He brought back ghosts.”
MISSION: GLASS PRAYER
Location: Haifa, Israel Date: ██/██/20██ Objective: Embedded as stray for 6 days inside biotech security compound. Recover prototype genetic stabilizer. Status: ✅ RECOVERED Anomalies: Subject remained in canine form for 142 consecutive hours. No reversion recorded.
Extracted Log [REDACTED]:
“…man in the courtyard fed me each morning. Called me 'Kelev.' Didn’t know I understood. He talked about his daughter. Told me secrets. Where the vault was. What he’d buried. Day six, I took the drive from his pocket. He cried when I ran. I didn’t look back. The leash tightens when they trust you.”
MISSION: REBIRTH
Location: [REDACTED] Date: ██/██/20██ Objective: ████████ Status: ██ Notes: Operation during which subject’s shifter state first manifested. Incident classified under Pandora Directive X/13. Only surviving operative. No visual data recovered. All environmental surveillance “glitched.”
Post-Op Incident Report:
“…I was watching Juno die and I wasn’t in my body. I felt the hair before I saw it. I heard something scream inside my head—my voice, but not. I shifted for the first time. And I didn’t come back for three days.”
Outcome: Full biogenic transition. Induction into Pandora Gluttony Division.
🔒 ADDITIONAL FILES (ACCESS RESTRICTED TO OMEGA-LEVEL):
[ ] DOG 19 Incident File – Content Locked[ ] JUNO Termination Record – Redacted by Order 5C[ ] Directive A-Null: “Fail-safes for Subject Shepherd”
🔻 END OF FILE
“He is what happens when loyalty breaks and reforms with teeth.” – Pandora Internal Memo
8 notes
·
View notes
Text
A thing that still blows my mind is that C++ is an object oriented language.
And most do not know what that means! :D
So we have the abstraction paradime. Badically having private and public stuff. Public interfaces and private implementation with the interface being some sort of abstraction. I mainly mentions this because that is SEPERATE from object oriented.
And then we have object oriented. Basically inheritance.
As in, software can inheret other software and extend it.
So in C++ class DERIVED can inherentclass BASE. And that means class DERIVED can be used both as class DERIVED and class BASE
Many languages facilitates the use of object oriented design like this.
But some languages are also object oriented.
As in, C++ is build so it inherits C
So you can use C++ as either C or C++
And Python inherets C++
Yes. You can write a program only in C in Python
Kotlin inherets Java.
Many languages do this. Because different languages does different things. If the different things can be described as different abstraction layers then it might be smart to let the higher abstraction level ones inheret from the lower abstraction level ones
Well written Python contains C for the very low level stuff, C++ for efficient safe use of HAL layer above it, and python for the system stuff
But if your python program have only higher lever stuff, it only needs to contain Python!
It is so flexible and neat! :D
#codeblr#programming#coding#softeware#software developer#software#the world is silly#software development#oop
8 notes
·
View notes
Text
In its flawed first season, “Halt and Catch Fire” tried too hard to be the next “Mad Men.” Following four visionaries through the first decade of the personal computing revolution, the AMC series opened by introducing its Don Draper: Joe MacMillan (Lee Pace), a slick, manipulative hotshot with an IBM pedigree. It’s 1983, and he’s speeding through Texas in a black sports car when he hits an armadillo. The carnage is nauseating, but it doesn’t stop him from making it to his destination: a college lecture hall where he’s come to interrogate a roomful of male comp-sci majors about the future of their industry. The sole woman in the class arrives late. She wears military fatigues, her hair is bleached, and bratty punk music blasts through her headphones. She is the most brilliant coder in the room.
Her name is Cameron Howe (Mackenzie Davis), and she turns out to be the show’s true protagonist. Her story comes to the fore in subsequent seasons that evolve radically enough to make “Halt and Catch Fire,” which ends its run on Saturday (Oct. 14), one of the greatest TV dramas of the decade. But there’s lots of tiresome male anti-hero stuff to get through first, as Joe commandeers a local electric company and talks its best employee, timid family man Gordon Clark (Scoot McNairy), into helping him reverse-engineer an IBM. As this classic alpha-beta duo schemes and innovates, their new hire (and Joe’s fuck buddy) Cameron remains a quasi-peripheral figure. It’s the songs music supervisor Thomas Golubić (“Breaking Bad,” “Better Call Saul,” “Six Feet Under”) surrounds Cam with that offer the first hint that the show is really her story.
Cam’s punk tapes are a window into the initially taciturn character’s rebellious nature, just as her headphones are the first clue that she’s a loner. In the premiere, she’s listening to the Vandals when she gets kicked out of a video arcade for using the old coin-on-a-string trick. A few episodes later, there’s a gorgeous scene where she pirouettes through a dark, empty office with X-Ray Spex’s “Germfree Adolescents” on her Walkman. (The moment is echoed near the end of season three, where she dances—first with Joe, then alone—to Pixies’ “Velouria.”) Whether it’s an iconic band like Bad Brains or a lesser-known act like Big Boys, Cam’s always got loud, angry music in her ears while she’s coding.
Cam is a punk, but not just in the banal, myopic way the tech industry has always appropriated the aesthetic—with dropout programming prodigies, “rockstar” developers, and startups bent on “disrupting” existing business models, all of whom share the ultimate goal of making money. She is impractical to a fault, trusting her own unruly instincts over the dictates of the market. Over four seasons, we watch her dream up everything from a friendly user interface that’s years ahead of its time and would take far too long to build, to a computer game so abstract, no one can understand how to play it. When she founds her own company, at the end of the first season, it’s called Mutiny. All of the employees live together in a house and make decisions democratically. Eventually, Cam exerts her power as Mutiny’s leader, but only to save her vision from getting absorbed into a big corporation.
From the very start, Cam’s music bleeds from her headphones into the show’s non-diegetic soundtrack. When she shows up for her first day at Cardiff Electric, the company Joe hijacks, “The Magnificent Seven” by the Clash follows her, its lyrics about the futility of the capitalist grind underscoring her ambivalence about the job. Over time, punk comes to symbolize Cam’s growing influence in the industry. It’s the official sound of Mutiny HQ, her chaotic geek haven adorned in red spray paint. Near the end of season two, the Raveonettes’ cover of Joy Division’s “She’s Lost Control” plays as she exacts public revenge on the billionaire who rips off the early online community she’s created. After Mutiny moves to California, in season three, hardcore riffs constantly reverberate through the cavernous office.
“Halt and Catch Fire” doesn’t usually hit you over the head with feminist themes, but it does subtly build an argument that women are gaining ground in a world men still control. Gordon’s wife, Donna (Kerry Bishé), initially seems like a nagging mom type, keeping her genius husband from his destiny. But she’s a genius, too; her engineering expertise becomes invaluable to Cardiff’s portable computer project, then she joins Cam at Mutiny. By the finale, Donna’s combination of technical prowess and business savvy have made her a powerful Silicon Valley venture capitalist, as well as a sort of Sheryl Sandberg figure.
Donna and Gordon Clark’s daughters, Joanie (played by Morgan Hinkleman as a kid and Kathryn Newton as a teenager) and Haley (Alana Cavanaugh and then Susanna Skaggs), are the next generation of liberated women. Cam lives with the Clarks after Mutiny moves to California, and her influence on the girls is palpable. A few quick time jumps land us in the mid-’90s by the fourth season, when the sisters are in high school. Teenage Joanie is a classic rebel, smoking cigarettes and getting into trouble and, yes, listening to punk. (The band name Shonen Knife, she explains to her father, basically means “dick” because “shonen” is the Japanese word for “boy.”) Haley is a budding web development star whose taste for PJ Harvey and riot grrrl helps her come to terms with her queer sexuality. A giddy scene midway through the season finds her bonding with her crush, a waitress, over Bratmobile and Heavens to Betsy.
Music becomes more essential to the show than ever in its fourth and final season. There are moving syncs that have nothing to do with Cam, like when an unmoored Donna gets pulled over for speeding while singing along to Pat Benatar’s “We Belong,” and when she plays Dire Straits’ “So Far Away” after Gordon’s sudden death. But the alternative, indie, and riot grrrl music Haley and Joanie listen to—Gen X’s version of the punk bands whose fierce spirit Cam helped instill in them—is the core soundtrack of these episodes. Golubić cements the connection by pairing Cam’s scenes with some of the 1990s’ most iconic female-led anthems: the Breeders’ “Cannonball,” Bikini Kill’s “Rebel Girl,” Hole’s “Doll Parts.” Just as X-Ray Spex and their peers helped pave the way for women in punk, Cam sets a precedent for girl programmers like Haley. At one point, she’s surfing the internet and stumbles upon a Cameron Howe fan page.
Perhaps the greatest thing about “Halt and Catch Fire” is that it ultimately has no real heroes or villains—only four talented, flawed people who all end up playing both of those roles at one point or another. The music is what puts us inside Cam’s mind more than any other character’s, though, and illustrates how her ideas electrify everyone who can wrap their mind around them, even when her projects fail. Her work endures like an out-of-print cassette passed from hand to grubby hand, a guidepost for like-minded young punks who walk the difficult path she cleared.
7 notes
·
View notes
Text
Data Visualization: Transforming Data into Insight
In an technology wherein information is produced at an remarkable tempo, the ability to extract significant insights is extra vital than ever. Data visualization plays a vital function on this procedure, enabling individuals and corporations to understand complex statistics sets, pick out trends, and communicate findings effectively. By converting abstract numbers into intuitive visuals, information visualization bridges the gap among uncooked data and human cognition, turning complexity into readability.
Data Visualization In Research

The Importance of Data Visualization
Data visualization is the graphical illustration of information and facts. By the use of visible elements like charts, graphs, and maps, statistics visualization tools make it less difficult to see and understand styles, trends, and outliers in facts. Its importance lies in numerous key areas:
Improved Understanding: Visuals are processed 60,000 times faster than textual content by way of the human mind. Graphs and charts can screen insights that would pass omitted in spreadsheets.
Enhanced Communication: Well-crafted visualizations allow statistics to be shared in a manner that’s available to a broader audience, no longer simply records analysts or statisticians.
Data-Driven Decision Making: In enterprise, governments, and medical research, visualizations support selection-making via without a doubt showing the implications of various statistics tendencies.
Pattern and Anomaly Detection: They help users quick become aware of deviations, spikes, or drops in data, which could suggest possibilities or threats.
Types of Data Visualization
Data visualization encompasses a big selection of techniques, each applicable to precise types of records and analytical desires. Some of the most commonly used sorts include:
1. Bar Charts
Bar charts are best for comparing quantities throughout classes. They are simple however effective for displaying differences among agencies.
2. Line Graphs
Often used to music changes over time, line graphs display tendencies and fluctuations, making them a fave for time-series information.
3. Pie Charts
They’re satisfactory for simple, clear percent facts.
4. Histograms
Histograms display the distribution of a dataset, making them beneficial for understanding records spread, crucial tendency, and frequency.
5. Heat Maps
Heat maps use colour gradients to indicate value depth throughout two dimensions.
6. Scatter Plots
Scatter plots are used to pick out relationships between variables, often revealing correlations or clusters in facts.
7. Box Plots
Box plots show the distribution of a dataset thru its quartiles, highlighting medians, variability, and ability outliers.
8. Geospatial Maps
These visualizations display facts associated with geographic regions and are extensively utilized in demographic research, environmental tracking, and logistics.
9. Dashboards
Dashboards integrate multiple visualizations into one interface, supplying a actual-time assessment of key metrics and overall performance signs.
Tools for Data Visualization
A huge range of tools is to be had for growing effective statistics visualizations. Popular alternatives encompass:
Tableau: A leading platform for interactive, shareable dashboards with drag-and-drop functions.
Power BI: Microsoft's enterprise analytics tool with sturdy integration into the Office atmosphere.
Google Data Studio: A unfastened tool for developing customizable reports the use of Google records sources.
Ggplot2: A effective R package for constructing state-of-the-art plots the use of the grammar of snap shots.
Each device gives distinctive competencies depending at the user’s technical information, information complexity, and desired results.
Best Practices in Data Visualization
Creating effective facts visualizations requires more than just technical skill. It includes an information of design ideas, cognitive psychology, and storytelling. Here are key exceptional practices:
1. Know Your Audience
Tailor the visualization to the information stage and pursuits of your target market. What a statistics scientist unearths intuitive is probably complicated to a business executive.
2. Choose the Right Chart
Using an inappropriate chart kind can deceive or confuse the viewer. For instance, a line chart ought to not be used for specific information.
Three. Simplify and Clarify
Avoid muddle. Focus on essential statistics and put off unnecessary elements like immoderate gridlines, decorative snap shots, or redundant labels.
Four. Use Color Thoughtfully
Color can enhance know-how but additionally lie to if used improperly. Stick to a consistent color scheme and use contrasts to highlight key points.
5. Tell a Story
Effective facts visualizations guide the viewer through a story. Highlight tendencies, anomalies, or correlations that support your message.
6. Maintain Integrity
Never manipulate axes or distort scales to magnify findings. Ethical visualization ensures accurate illustration of statistics.
Real-World Applications
Data visualization is applied in nearly each region, transforming industries through stepped forward insight and communication.
1. Business Analytics
In commercial enterprise, visualization tools assist in monitoring sales, client behavior, supply chain efficiency, and extra.
2. Healthcare
In medicinal drug and public health, visualizations are crucial for tracking disorder outbreaks, affected person records, and treatment results. For example, COVID-19 dashboards performed a main function in information the pandemic's unfold.
3. Finance
Financial analysts use records visualization to recognize market tendencies, examine investment overall performance, and check chance.
Four. Education
Educators and researchers use visualization to track pupil performance, perceive mastering gaps, and gift studies findings.
Five. Government and Policy
Policymakers use visible facts to understand social trends, aid allocation, and financial overall performance.
6. Journalism
Data journalism is growing hastily. Visual stories on topics like weather change, election results, or social inequality use charts and infographics to inform and engage readers.
Challenges and Limitations
Despite its electricity, facts visualization isn't with out demanding situations:
Data Quality: Inaccurate or incomplete information can lead to deceptive visuals.
Over-Simplification: Trying to make information too easy can lead to lack of nuance or important info.
Misinterpretation: Poor design selections or biased displays can cause audiences to draw wrong conclusions.
Tool Limitations: Not all equipment aid the extent of customization or interactivity wished for unique projects.
Overcoming these demanding situations requires a mix of technical talent, area information, and moral responsibility.
The Future of Data Visualization
The future of statistics visualization is increasingly interactive, actual-time, and AI-assisted. Emerging traits include:
Augmented and Virtual Reality (AR/VR): Immersive visualizations permit users to explore records in three-dimensional environments.
Machine Learning Integration: Algorithms can now endorse or even vehicle-generate visualizations based on the information furnished.
Collaborative Platforms: Teams can now work collectively in actual time on visualization dashboards, improving communique and agility.
These advancements will hold to make records greater accessible and insightful throughout all domain names.
Difference Between Augmented Reality (AR) and Virtual Reality (VR)
What Is Data Analysis In Research
2 notes
·
View notes
Text


1/30 Days of Productivity
🎧 mighty to save — hillsong worship
wake up early
yoga
learning task 1 : Abstract Classes and Interfaces 💬
learning task 2 : Intro to TOC 💬
oil pulling
plan the week
learning task 3: SQL Lecture 01 Relating
note: pray ▪︎ trust the process 🌱✨️
2 notes
·
View notes
Text
Cyberpunk Monsters and Hunters
So I was asked to dig a bit into cyberpunk this morning since we finished with the new Team playbooks.
One of the things that we were asked to do with Hunter's Journal and Slayer's Survival Kit is to add more sci-fi options as adverse to the usual occult flavor that is the default assumption with Monster of the Week.
This resulted in the inclusion of the Host, the Visitor, The Interface, Research Lab, and Escaped Experiments as well as the sections on creating future-tech and bionics in the Gear section. However, Sci-Fi does not necessarily equate to cyberpunk. So what makes cyberpunk?
Settings with a "punk" descriptor usually heavily focus on social inequity. You're going to have powerful corporations and unethical government programs feature heavily. The problems that you face are outgrowths of the dehumanization of the lower classes and the reduction of their societal role into being a cog in the machine feeding the comfort of those people in power. In a lot of way's Marek's advice about taking a Gothic look at things is very applicable to cyberpunk. Instead of using a supernatural monster or phenomenon instead use a science fiction one.
This right now is me writing a bit just in the morning over the course of about 30 minutes. This is a topic that will take a bit deeper thought to give a complete thought on. However, some basic summaries here:
A lot of cyberpunk fiction involves corporations and governments trying obfuscate or justify what is effectively slavery. The villains of the setting will make an effort to narrow the definition of a person and attempt to retain ownership bionic upgrades and replacements. Your replacement heart was taken on credit and can be repossessed, such as you see in Repo: The Genetic Opera.
Branching off that, explore what it means to be human or a person. Is there a line of replacement at which point a person stops being a person? Or is there something more abstract that determines what makes a person? Short Circuit goes into this with Johnny Five's spontaneous sapience being explored. This is also a driving point in the video game Detroit: Becoming Human with sapient robots and in Blade Runner with clones.
Explore the unintended consequences of technological advancement. Technology itself is neither good nor bad but cyberpunk often explores what happens when an advancement is rushed out without proper quality controls or, worse, disregarding significant dangers that the company doesn't want to bother dealing with because they need profit now. A fair number of Black Mirror episodes seem to examine this.
Take the promise of an exciting technological advancement and imagine how it might be twisted and corrupted from its original intended application once funneled through the perspective of a corporation that only sees the potential for profit or a government that only sees the potential for control. It is important that the tech is not inherently bad, nor are humans inherently bad, but bad people have inordinately more control over how things go than they should. In the Val Kilmer movie, The Saint the conflict is over free energy, for instance.
For contrast, Star Trek takes place post cyberpunk and the webcomic Questionable Content assumes a reality where several cyberpunk tropes were avoided creating a world where AIs and humans live alongside each other as equals.
As regards to Monster of the Week, you'll be dealing more often with Villains and Phenomena than Monsters, where Phenomena represent a new technological marvel that has some horrific side-effect that is just being concealed or ignored by the creator. That said, you can still get Monsters with things like rogue AIs and killer robots. But also, AIs and robots might become bystanders that you have to help escape from the corporations and governments as well.
The ultimate enemy of cyberpunk stories is crushing social inequity. A very small number of people have inordinately more power than the bulk of humanity. You'll find a lot of that emotional inspiration in both my own and Marek's design spaces.
When it comes to the hunters.... hmmm, let's create a quick team. I don't have time to do Hero Forge minis just yet, but I'll probably build some over the day to add in here.
For weird moves I'm going to focus on the following:
Hacking, the control of computers and tech, naturally.
Weird Science, the crafting of unstable prototype gadgets.
No Limits, enhanced physicality, could represent cybernetic enhancement.
Tradecraft, enhanced analytical prowess, again, could represent cybernetic enhancement.
And for playbooks I'm going with the following:
The Interface, all about interacting with tech.
The Host, in this case, fused with an AI.
The Expert, with a highly technological Haven.
The Constructed, this is a third-party playbook that's popular, we may eventually see it become official.
And I did Escaped Experiments earlier, but I think I'll do this as Whistleblowers... which is sort of like the prologue to Escaped Experiments and I used the model of Whistleblower when I was creating the questions for creating the Project in Escaped Experiments and the App in Swipe to Slay.
Masamune-Sigurd Industries
The hunters are agents that are part of a megacorp that is pushing the boundaries of technology with the stated goal of advancing humanity. Or at least the humanity represented by their major shareholders.
Style: Revolt - let's burn it all down.
The Organization
Official Goals: Research human enhancement, expand market share.
Goals you suspect: Taking over the world.
Official Resources: Modernized, Rich
Suspected Resources: Bribed officials, sacrificing members
Obvious Flaws: Closed hierarchy
Suspected Flaws: Hostile superiors, protects member criminals
Core Traits
Team Ally: Faruq, an office worker in the organisation. He also feels there’s something wrong but is too afraid to act openly about it.
Team Moves: Something Rotten
Team Assets
Fake IDs: Fake government IDs.
Workshop: A big space for craft and repair projects, with plenty of tools and materials.
Bobbie Lloyd - The Interface
Look: A cybernetically enhanced soldier with clearly artificial body parts, though from a distance or under heavy clothing they could pass as a normal human.
Charm -1
Cool +1
Sharp +1
Tough +2
Weird +0
Integration
Upgrades: Heads-up Display, Intelligence Database
Faults: Hackable Brain
Origin: Volunteer
Moves
Basic Weird Move: Tradecraft
Moves: Keep Going and Going, Take the Shot, Expert Troll
Gear
Tactical Armor (1-armour)
Jumping Boots (integrated)
Enhanced Sensor Suite (integrated)
Internal Computer (integrated)
Recording Suite (Integrated)
Submachine gun arm (3-harm close area loud reload integrated blatant)
Muscle Augments (1-harm hand useful integrated)
Incessantly replayed voicemail
Nostalgic Photo
History
Phoebe Morris represents one of Bobbie's nightmares, having an AI meshed into her brain. The fact she did it to herself, deliberately even, makes it so much worse.
They don't see Project V as much different from themself. Just coming from a different starting point.
Bobbie knows that Eileen has some shady past. They just don't know details about what Eileen's done. That said they do recognize that Eileen is honestly trying to atone for past sins.
Bobbie was quick to volunteer for the Cipher program and hasn't regretted losing flesh and bone body parts yet. The one thing that concerns her is that there is now a path from a hacker to access her organic brain and do all sorts of terrible things to her mind (and possibly body)
Phoebe Morris - The Host
Look: A lovely young woman with a number of skin-mods showing LED lights flashing in lines along her skin. Looking into her eyes you can see binary numbers processing.
Charm +1
Cool +1
Sharp +0
Tough -1
Weird +2
Symbiosis
The Norn-AI
Benefits: Can't be possessed (hacked), Subtle Physical Improvements
Downsides: Obvious mutations (the neon lines and digital eyes)
Moves
Basic Weird Move: Hacking
Moves: Defensive Adaptation (Whispered Advice), Collaborative Effort, Mutual Survival
Gear
Audio recorder and backup storage
Symbiotic Stunner (0-harm close stun integrated retractable)
History
Eileen's advice was instrumental in the successful symbiosis with the Norn-AI.
Phoebe saved Bobbie from an intrusive virus or AI and that was how she came to the idea of upgrading her nervous system to house Norn-AI
Project V has come to her and Norn-AI for advice on how to fit in with biological human beings.
Phoebe could very much have ended up a monster that needed to be put down. Fortunately, the Norn-AI is largely friendly or at least tolerant to their host personality. Phoebe had discovered the Norn-AI quarantined in a neglected corner of the company's Byzantine digital structures. Housing Norn-AI in her own body is how she decided to rescue them.
Eileen Moreno - The Expert
Look: A woman somewhere between middle-aged and elderly, but it's hard to say exactly which as life-extending technology has muddled the signs of her aging. She dresses sharply and walks with a slight limp.
Charm +0
Cool +1
Sharp +2
Tough -1
Weird +1
Haven
A private lab hidden away on company grounds where she can perform her off-the-books research and projects.
Hidden
Guardian (Personal lab AI)
Science Laboratory
Moves
Basic Weird Move: Weird Science
Moves: Dark Past, The Woman with the Plan
Gear
Magnum (3-harm close reload loud)
Stun Gun (1-harm hand stun electric)
Walking Stick (1-harm hand innocuous)
History
Project V knows a lot of Eileen's dark secrets. But they're not entirely sure which are bad and which are just past events.
Phoebe Morrise approached Eileen for advice on her project, at the time Eileen was distracted with her moral epiphany and did not realize that Phoebe planned to host an AI within her own cybernetically enhanced nervous system.
Bobbie Lloyd's upgrades are at least partially based on Eileen's designs. She is concerned at this use but has to admit that Bobbie's upgrades are well done.
Eileen has been an important researcher at Masamune-Sigured for over six decades and she's well into her 80th year for all that she looks much younger. In her time at the company she has both seen and performed many sins in the pursuit of technological advance. Upon discovering Project V's growing sapience, Eileen had an epiphany and started to realize that she's been in the wrong in many circumstances.
Project V - The Constructed
Look: A mostly human looking face with a clearly sleek, robotic body made from a silvery metal that will eventually be covered in a substitute for skin like their face is.
Charm +0
Cool +1
Sharp -1
Tough +2
Weird +1
Purpose
Experiment
Animating Force: Electricity
Creator set them free
Moves
Basic Weird Move: No Limits
Experiment Move: Always Learning
Moves: Inhuman, Recharge, But Why?
Gear
Huge handgun (3-harm close loud reload)
Bulwark (1 armour)
History
Eileen Moreno is Project V's creator and she's working on a way for Project V to pass as a biological human.
Bobbie Lloyd first assumed that Project V was another bionically enhanced human being. They were a bit surprised at the truth but rebounded quickly back to accepting Project V as a person.
Phoebe Morris's host AI has expressed interest in Project V's programming and has engaged in digital conversations probing the subject. So far the AI has avoided pushing boundaries.
The point of Project V on paper was to create a robotic soldier or operative. However, once Eileen started recognizing the potential of what was in front of her, she started to divert attention away from the project and slowly remove V from the official records. Since then, Project V has mostly been confined to the hidden facilities the team has available, but will leave that area to help the team.
You can find the Interface and Host can be found in the new supplements along with advice on incorporating bionics into your campaign can be found in the Slayer's Survival Kit.
#tabletop#character creation#urban fantasy#urban horror#monster of the week#cosmic horror#roleplaying games#evil hat productions#ttrpg#rpg#cyberpunk#Mike Sands#Marek Golonka#sci-fi gothic#cybergothic#motw#motw character#pbta#powered by the apocalypse
2 notes
·
View notes
Text
#Playstation7 #framework #BasicArchitecture #RawCode #RawScript #Opensource #DigitalConsole
To build a new gaming console’s digital framework from the ground up, you would need to integrate several programming languages and technologies to manage different aspects of the system. Below is an outline of the code and language choices required for various parts of the framework, focusing on languages like C++, Python, JavaScript, CSS, MySQL, and Perl for different functionalities.
1. System Architecture Design (Low-level)
• Language: C/C++, Assembly
• Purpose: To program the low-level system components such as CPU, GPU, and memory management.
• Example Code (C++) – Low-Level Hardware Interaction:
#include <iostream>
int main() {
// Initialize hardware (simplified example)
std::cout << "Initializing CPU...\n";
// Set up memory management
std::cout << "Allocating memory for GPU...\n";
// Example: Allocating memory for gaming graphics
int* graphicsMemory = new int[1024]; // Allocate 1KB for demo purposes
std::cout << "Memory allocated for GPU graphics rendering.\n";
// Simulate starting the game engine
std::cout << "Starting game engine...\n";
delete[] graphicsMemory; // Clean up
return 0;
}
2. Operating System Development
• Languages: C, C++, Python (for utilities)
• Purpose: Developing the kernel and OS for hardware abstraction and user-space processes.
• Kernel Code Example (C) – Implementing a simple syscall:
#include <stdio.h>
#include <unistd.h>
int main() {
// Example of invoking a custom system call
syscall(0); // System call 0 - usually reserved for read in UNIX-like systems
printf("System call executed\n");
return 0;
}
3. Software Development Kit (SDK)
• Languages: C++, Python (for tooling), Vulkan or DirectX (for graphics APIs)
• Purpose: Provide libraries and tools for developers to create games.
• Example SDK Code (Vulkan API with C++):
#include <vulkan/vulkan.h>
VkInstance instance;
void initVulkan() {
VkApplicationInfo appInfo = {};
appInfo.sType = VK_STRUCTURE_TYPE_APPLICATION_INFO;
appInfo.pApplicationName = "GameApp";
appInfo.applicationVersion = VK_MAKE_VERSION(1, 0, 0);
appInfo.pEngineName = "GameEngine";
appInfo.engineVersion = VK_MAKE_VERSION(1, 0, 0);
appInfo.apiVersion = VK_API_VERSION_1_0;
VkInstanceCreateInfo createInfo = {};
createInfo.sType = VK_STRUCTURE_TYPE_INSTANCE_CREATE_INFO;
createInfo.pApplicationInfo = &appInfo;
vkCreateInstance(&createInfo, nullptr, &instance);
std::cout << "Vulkan SDK Initialized\n";
}
4. User Interface (UI) Development
• Languages: JavaScript, HTML, CSS (for UI), Python (backend)
• Purpose: Front-end interface design for the user experience and dashboard.
• Example UI Code (HTML/CSS/JavaScript):
<!DOCTYPE html>
<html>
<head>
<title>Console Dashboard</title>
<style>
body { font-family: Arial, sans-serif; background-color: #282c34; color: white; }
.menu { display: flex; justify-content: center; margin-top: 50px; }
.menu button { padding: 15px 30px; margin: 10px; background-color: #61dafb; border: none; cursor: pointer; }
</style>
</head>
<body>
<div class="menu">
<button onclick="startGame()">Start Game</button>
<button onclick="openStore()">Store</button>
</div>
<script>
function startGame() {
alert("Starting Game...");
}
function openStore() {
alert("Opening Store...");
}
</script>
</body>
</html>
5. Digital Store Integration
• Languages: Python (backend), MySQL (database), JavaScript (frontend)
• Purpose: A backend system for purchasing and managing digital game licenses.
• Example Backend Code (Python with MySQL):
import mysql.connector
def connect_db():
db = mysql.connector.connect(
host="localhost",
user="admin",
password="password",
database="game_store"
)
return db
def fetch_games():
db = connect_db()
cursor = db.cursor()
cursor.execute("SELECT * FROM games")
games = cursor.fetchall()
for game in games:
print(f"Game ID: {game[0]}, Name: {game[1]}, Price: {game[2]}")
db.close()
fetch_games()
6. Security Framework Implementation
• Languages: C++, Python, Perl (for system scripts)
• Purpose: Ensure data integrity, authentication, and encryption.
• Example Code (Python – Encrypting User Data):
from cryptography.fernet import Fernet
# Generate a key for encryption
key = Fernet.generate_key()
cipher_suite = Fernet(key)
# Encrypt sensitive user information (e.g., account password)
password = b"SuperSecretPassword"
encrypted_password = cipher_suite.encrypt(password)
print(f"Encrypted Password: {encrypted_password}")
# Decrypting the password
decrypted_password = cipher_suite.decrypt(encrypted_password)
print(f"Decrypted Password: {decrypted_password}")
7. Testing and Quality Assurance
• Languages: Python (for automated tests), Jest (for JavaScript testing)
• Purpose: Unit testing, integration testing, and debugging.
• Example Unit Test (Python using unittest):
import unittest
def add(a, b):
return a + b
class TestGameFramework(unittest.TestCase):
def test_add(self):
self.assertEqual(add(10, 20), 30)
if __name__ == '__main__':
unittest.main()
8. Order of Implementation
• Phase 1: Focus on core system architecture (low-level C/C++) and OS development.
• Phase 2: Develop SDK and start building the basic framework for UI and input management.
• Phase 3: Work on backend systems like the digital store and integrate with front-end UI.
• Phase 4: Begin rigorous testing and debugging using automated test suites.
This comprehensive approach gives you a detailed idea of how each component can be built using a combination of these languages and technologies. Each section is modular, allowing teams to work on different aspects of the console simultaneously.
[Pixel Art/Sprites/Buildinodels/VictoriaSecretPixelArtKit #Playstation7 #DearDearestBrands]


#victoriasecretrunway#runwaybattle#victoria secret fashion#victoria secert model#victoriasecret#victoria secret#VictoriaSecretRunwayBattle#capcom victoriasecret#capcom videogames#playstation7#ps7#deardearestbrands#capcom#digitalconsole#python#script#rawscript#raw code#framework#VictoriaSecretVideoGame#deardearestbrandswordpress
2 notes
·
View notes
Text
Top 5 Common Database Design patterns in Laravel
In the world of Laravel development, a well-structured database is the bedrock of a robust and scalable application. While Laravel's Eloquent ORM provides a powerful abstraction layer for interacting with your data, understanding common database design patterns can significantly enhance your development process.
These patterns not only promote code organization and maintainability but also enable you to adapt your database structure to the unique needs of your application. By mastering these patterns, you can build efficient, reliable, and easily maintainable Laravel applications that can handle diverse data requirements.
1. Active Record Pattern:
This is the most common pattern used by Eloquent ORM in Laravel. It encapsulates database logic within model classes, allowing you to interact with the database using object-oriented methods.
Application
This pattern is well-suited for projects of any size and complexity. It simplifies database operations, making them easier to understand and maintain.
Example:

Advantages:
Simplicity: Easy to understand and implement.
Code Reusability: Model methods can be reused throughout your application.
Relationship Management: Built-in support for relationships between models.
Disadvantages:
Tight Coupling: Model logic is tightly coupled to the database, making it harder to test independently.
Complexity: Can become complex for large applications with complex data structures.
2. Data Mapper Pattern:
This pattern separates data access logic from domain logic. It uses a dedicated "mapper" class to translate between domain objects and database records.
Application
This pattern is useful for large-scale applications with complex domain models, as it allows for greater flexibility and modularity. It is particularly useful when working with multiple data sources or when you need to optimize for performance.
Example:

Advantages:
Flexibility: Easily change the database implementation without affecting business logic.
Testability: Easy to test independently from the database.
Modularity: Promotes a modular structure, separating concerns.
Disadvantages:
Increased Complexity: Requires more code and might be overkill for simple applications.
3. Repository Pattern:
This pattern provides an abstraction layer over the data access mechanism, offering a consistent interface for interacting with the database.
Application
This pattern promotes loose coupling and simplifies testing, as you can easily mock the repository and control the data returned. It is often used in conjunction with the Data Mapper pattern.
Example:

Advantages:
Loose Coupling: Decouples business logic from specific data access implementation.
Testability: Easy to mock repositories for testing.
Reusability: Reusable interface for accessing different data sources.
Disadvantages:
Initial Setup: Can require more setup compared to Active Record.
4. Table Inheritance Pattern:
This pattern allows you to create a hierarchical relationship between tables, where child tables inherit properties from a parent table.
Application
This pattern is useful for creating polymorphic relationships and managing data for different types of entities. For example, you could have a User table and separate tables for AdminUser and CustomerUser that inherit from the parent table.
Example:

Advantages:
Polymorphism: Enables handling different types of entities using a common interface.
Code Reusability: Reuses properties and methods from the parent table.
Data Organization: Provides a structured way to organize data for different types of users.
Disadvantages:
Increased Database Complexity: Can lead to a more complex database structure.
5. Schema-less Database Pattern:
This pattern avoids the use of a predefined schema and allows for dynamic data structures. This is commonly used with NoSQL databases like MongoDB.
Application
This pattern is suitable for projects that require highly flexible data structures, such as social media platforms or analytics systems.
Example:

Advantages:
Flexibility: Easily adapt to changing data structures.
Scalability: Suitable for high-volume, rapidly changing data.
High Performance: Efficient for specific use cases like real-time analytics.
Disadvantages:
Increased Complexity: Requires a different approach to querying and data manipulation.
Data Consistency: Can be challenging to maintain data consistency without a schema.
Choosing the Right Pattern:
The best pattern for your project depends on factors like project size, complexity, performance requirements, and your team's experience. It is important to choose patterns that align with the specific needs of your application and ensure long-term maintainability and scalability.
Conclusion:
This exploration of common database design patterns used in Laravel has shed light on the importance of strategic database structuring for building robust and scalable applications. From the simplicity of the Active Record pattern to the sophisticated capabilities of the Data Mapper and Repository patterns, each pattern offers distinct benefits that cater to specific project needs.
By understanding the strengths and applications of these patterns, Laravel developers can choose the optimal approach for their projects, ensuring a well-organized, efficient, and maintainable database architecture. Ultimately, mastering these patterns empowers you to create Laravel applications that are not only functional but also adaptable to evolving data requirements and future growth.
#laravel#laravel development company#laravel framework#laravel developers#database#design#coding#programming
4 notes
·
View notes
Text
How deep is your pleasure

Inspired exploration by Sabrina Lynn's work. (Find her on youtube, IG, Facebook, etc.). I also listened to Ethereal Astrology, Brittany (also on youtube) while I wrote this to remind myself of the sensations I've been processing.
Full Moon Lunar eclipse in Pisces + Venus opposing Chiron
A lot of resistance is coming up for me around expression. I have had several epiphanies about being addicted to self healing and having the realization that the brain will create whatever you focus on.
Personally doing ( physical action) anything has been very difficult. My mind wants to be terribly distracted. I am also seeing how much I am addicted to consuming: food, content, information, education, well being, style, fashion, aesthetics, the list goes on and on.
Even given that, I do feel a need to move something out of me- like these thoughts. I have been becoming aware of an old, ingrained, conditioned mindset ( solidifying more the last 3 months) that has been the imaginary chains I've had on myself for probably my whole life. This is so interesting as I have been digesting a lot of Jung's work on the anima/animus. This has provided a lot of experiential context in relation to myself in my relationships. The invisible chains being certain thoughts, feelings ( as sensations) and emotions.
For me this was identified as Jung's animus- the masculine partner a woman has that is the unconscious aspect of her mind, if she is unaware of it. I do believe that because of my experience with parts work ( IFS) and my own previous education through polarity consciousness in spiritual circles ( an actual somatic class I took with Jennifer Joseph, naturalmagics on instagram) I already had a bit of an awareness to him. I had conceived some ideas of him like going through someone's belongings in their house and making up narratives of what they might be like. The belongings, one could say, made me believe perhaps more than one masculine being resided there. I went down a rabbit hole and should write the story of Cowboy and Shaman someday.
Of course being abstract concepts of our mind, they are not actual people. Though I could see their projections in my life in different people I'd known at one point or another. Now, according to Jung, if the animus is maladapted he actually has his own anima ( which makes sense to me now, why cowboy was Gay & why he was kinda evil). These figures seem to be going through a transformation process with the awareness I've gleaned about them. Like the tail end of THE dragon. Careful now, you know what they say about chasing THE dragon.
Anyhow, He (my animus) seems to be getting clearer... almost like he's still a ghost haunting ( more like a scuddle these days) the house but he goes in and out of being something more jello-like than ether and even though he's still wearing a sheet around- I am very aware of him. Perhaps his speech is less OOOOooooooooh like and more coherent as grunts and uh huhs and mmm's. Far less cryptic, not scary and mostly frustrating if not comical or annoying.
Which brings me to Sabrina's prompt about pleasure. Imagine not being able to interface with your lover in a way that was pleasant? Just thoughts and ideas about what that should look like, and then using stand in's to kill time, subs to get experience? Not understanding your animus is like playing charades with someone from another planet. You don't speak the same language, cannot translate, you have no context, and you have no way to relate. This of course will not stop anyone from existing, it just makes your inner workings complicated, confusing, conflicted, and hard to understand. From that point of view it is difficult to allow pleasure to be alive in your life. Some aspect of you is always on the defensive for how you will mishandle it, because historically denying it is all you have done. Painful, suffering, uncomfortable existence, anxiety are normal. Which makes sense to me why addiction to substance is so palpable. To finally get some pleasure through immobilizing those deafening, defensive rigid parts, just long enough to have some relief in pleasure... makes too much sense. I did that a lot in my life.
So now, knowing the jello-ghost animus is on his way to have a Beauty and the Beast like transformation is quite exciting. I'm still reading up on how it works ( which is why he's in a chrysalis stage).
Looking more at exploring aspects of pleasure for myself and being able to dialogue with him looks like it will take some time. But can't help but imagine my own little Helen Keller genius making waves soon.
Visual meditation:
In the middle of writing this I did a 10 min heart centered meditation because I felt compelled to for some time and saw a corridor between a narrow stretch in a mountain like chasm. The ground was covered in a soft spongey moss and I was barefoot. As I moved forward I couldn't see anything in front of me, it was all thick mist. A few yards in and I start seeing colors peeking through of different colorful flowering plants. I walk past dense flowering blooms and looked down when I noticed the ground seemed to be more wet. Blood, intermixed with water covering the moss.
Moving forward it appears there is what looks like body parts of something strewn about. The mist is receding to reveal a vast field. It looks like a war has just occurred, but is over now. A river is rushing ahead and it is clearing this field of the blood and parts. I also see being's I don't have descriptions for... they seem to be ever changing in shape of creatures I do not recognize. It also appears these are what was in parts in the bloodied field. They are also carrying off the parts; like ants away from the field. I watch them. Very quickly they seem to be building structures. A tree house structure forms ahead of me, they build other tree/vine like bridges and other structures near the river... I move towards it with feelings of excitement and well being. The meditation ends*
3 notes
·
View notes
Text
Knee Deep in the Passenger Seat: Is It Casual Now if We're Having a Quiz Next Meet?
"2 weeks and your mom invites me to her house in long beach, is it casual now?" Just like what Chappell said, is it casual now that we're 4 weeks in or are we getting for real right now? Although I would like to think that it is still casual, the hard truth is that it's not. Over the past few weeks, the topics we've discussed have slowly increased until the load was nearly enough for us to have our first quiz the following week. At least that's what we thought when we first entered the room, however it soon changed when our professor told us that we were going to have our quiz that day, a palpable sense of panic and horror was felt by everyone at that very moment, including myself. Although I was slightly prepared because I did a light review on the first topic, it was still not enough to help me pass and salvage myself from the dreadful test. However the feeling was soon dissipated when our professor said that we were just going to discuss the second topic, everybody breathed a sigh of relief the moment our professor said that.
Attached here are the shocked faces of Ms. Gwen and Ms. April 😝😜

💖💖��💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖
As usual, before the class started we had our cutesy little game, the REBUS PUZZLE!!. And do you want to know what makes this different from the past games? It's because this time, I finally got a correct answer! YAYY!!! The answer was supposedly Jack-in-box but I said Jack-in-the-box, but the professor still considered it as correct, so it's still a win for me. (´▽`ʃ♡ƪ)
💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖
Everybody was on a high after that mini-game and it was finally time to start the discussion...
The discussion began by defining the software design, where its critical role in the software lifecycle was emphasized. The purpose of software design was also highlighted, which was to create a blueprint for building software that meets specified requirements while ensuring maintainability, scalability, and usability. Then the core design principles were discussed such as problem partitioning, abstraction, modularity, and top down & bottom up strategy. Then the system implementation and its deployment were covered next. It was highlighted that we should follow the design blueprint closely so that we can ensure that the software meets its requirements. And that we should also note the importance of rigorous testing at every stage to ensure that the software is free of defects. And before deploying the system to the production environment, there should be strategies discussed first and also consider the rollbacks, monitoring, and maintenance of the system. And finally, the importance of code refactoring, it is the process of restructuring the existing code in order to improve the readability and also reduce the complexity without having to change the external behavior. Overall, the topic was discussed in great detail with numerous examples to further help us understand the topic.

💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖
As expected, after the discussion we had another activity where we had to design a system based on the problem given to us. We were still grouped into 4,and also by pure coincidence, the problem assigned to us was similar to the current project that we were doing, to design an online bookstore where users can browse books, add them to a shopping cart, and make purchases, and what's even funnier is that I was in the same group with 2 of the other members from the project, so color us surprised! In doing the task, I was assigned to create the initial design diagram for the system. Honestly, with the amount of time given and the resources available to use, I think we did well with the interface of the system. Although there were critiques from the other group that COMPLETELY left us speechless, I thought that we still did a great job with our output. And of course, what's the best way to end the class with an announcement for an upcoming quiz the following week! (┬┬﹏┬┬) May we survive the quiz next meet... so not looking forward to it ಥ_ಥ So in conclusion, no it is NOT casual, WE ARE LOCKED IN!!
💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖💖
And before we end the week, we did a follow-up consultation on the pre-requisites of our manuscript, the hard-work and perseverance of the team bore fruit as it led to us being in the lead to finish the pre-requisites first. However, our Activity 1 was completely wrong, I guess we got lost in translation. ƪ(˘⌣˘)ʃ In the end, the consultation finished rather quickly, with minor adjustments here and there, and it finally ended in a positive note. 💖💖
2 notes
·
View notes
Text
From Novice to Java Pro: A Step-by-Step Learning Journey
Java programming, renowned for its platform independence and versatility, is a sought-after language in the world of software development. It's the language behind countless web applications, mobile apps, game development, and more. This blog serves as your comprehensive guide to embarking on a journey to learn and master Java programming. We'll walk you through the basics of programming, Java's syntax and structure, the essential tools and libraries, and the importance of practice.

The Path to Java Proficiency:
1. Understand the Basics of Programming:
Prior Experience: If you're new to programming, it's crucial to start with the foundational concepts. Variables, data types, control structures (if-else, loops), and functions are universal principles that you need to understand before delving into any programming language, including Java.
What to Learn: Begin by grasping the basics of programming logic and problem-solving. Familiarize yourself with concepts like variables (to store data), data types (to specify the kind of data), and control structures (to make decisions and loop through actions). These concepts serve as the building blocks for Java programming.
2. Java Syntax and Structure:
Prior Experience: As you delve into Java, you'll find that it's an object-oriented language with its unique syntax and structure. While prior programming experience is beneficial, it's not a prerequisite. You can start with Java as your first language.
What to Learn: Java introduces you to classes and objects. Classes are blueprints for creating objects, which are instances of classes. Java is known for its object-oriented nature, where you'll encounter concepts like inheritance (creating new classes based on existing ones), polymorphism (objects of different classes can be treated as objects of the same class), encapsulation (data hiding), and abstraction (simplifying complex reality by modeling classes based on real-world objects).
3. Get Your Hands on a Compiler and IDE:
Prior Experience: No prior experience is required to set up your Java development environment.
What to Learn: To start writing and running Java code, you'll need to install a Java Development Kit (JDK), which includes the Java compiler (javac). This kit allows you to compile your source code into bytecode that the Java Virtual Machine (JVM) can execute. Additionally, install an Integrated Development Environment (IDE) like Eclipse, IntelliJ IDEA, or NetBeans. These IDEs provide a user-friendly interface for coding, debugging, and managing your Java projects.
4. Learn the Java Standard Library:
Prior Experience: No specific prior experience is necessary, but familiarity with basic programming concepts is beneficial.
What to Learn: Java's power lies in its extensive standard library. This library includes pre-built classes and packages that simplify common programming tasks. For example, you can utilize classes in the java.io package to handle file input and output. You'll explore the java.lang package, which provides fundamental classes like String and Integer. Understanding this library is crucial for performing operations like file handling, string manipulation, and working with data structures.
5. Practice, Practice, Practice:
Prior Experience: No prior experience is required. This stage is suitable for beginners and those with basic programming knowledge.
What to Learn: The key to mastering Java or any programming language is practice. Apply the knowledge you've gained by working on small coding projects. Start with simple programs and gradually move on to more complex tasks. Solving programming challenges, such as those on websites like LeetCode or HackerRank, is an excellent way to put your skills to the test. Build simple applications to get hands-on experience in real-world scenarios.
6. Join Java Communities:
Prior Experience: No prior experience is needed to join Java communities.
What to Learn: Engage with Java communities and forums, such as Stack Overflow or Reddit's r/java. These platforms provide a space to ask questions, seek advice, and learn from experienced Java developers. You can also contribute by answering questions and sharing your knowledge.
7. Enroll in Java Courses:
Prior Experience: Enrolling in Java courses is suitable for learners of all levels, from beginners to advanced users.
What to Learn: ACTE Technologies offers comprehensive Java training programs that cater to a diverse range of learners. These programs are designed to provide hands-on experience and real-world examples, ensuring that you gain practical skills in Java programming.

In your journey to master Java programming, structured training plays a pivotal role. ACTE Technologies is a trusted partner, offering Java training programs for learners at all levels. Whether you're a beginner taking your first steps in Java or an experienced programmer seeking to expand your skill set, they can provide the guidance and resources needed to excel in the world of Java development. Consider exploring their Java courses to kickstart or enhance your Java programming journey. Java programming is a versatile and essential language, and mastering it is a rewarding journey. With dedication, practice, and structured training, you can become a proficient Java developer. Institutions like ACTE Technologies offer valuable resources and courses to accelerate your learning process, making your journey to Java mastery even more efficient.
7 notes
·
View notes
Text
worldbuilding: Cores are computer modules. They're usually anywhere between 0.5L to 2L in volume; somewhere around the size of a brick. Most cores use a standard accessory interface port, which can also supply power to the core (think today's USB-C monitors, docks, etc.)
Cores usually contain specialized SoCs, containing both general-purpose and tensor processors. Often, they also include a discrete tensor processor for greater performance. Some cores are fairly simple, meant for desktop computers, or to only run heuristic algorithms. Others are able to run agentic intelligences.
There's a numerical scale of intelligence classes. An agent at L=0 is capable of approximately human-level reasoning (also referred to as a "sophont"). Generally, humans are agents at L=0. Lower levels are capable of less abstract, novel reasoning. (For example, automated phone systems use agents at L=3; service desk and level 1 customer support systems use agents at L=1.)
The cognitive capabilities of artificially constructed agents are restricted by NAU law. Possession of an artificial agent at L=0 requires a government-issued license. There's also very severe restrictions on international trade.
The consciousness of artificial intelligences is a hotly debated topic.
8 notes
·
View notes