#Mac vs world building
Text
Imagine, after everything is said and done. No more darkness, no more evil-doers, no more overlord. Just peace.
What would the Ninja do next?
Nya would go into techs. Maybe she'd intern or shadow Borg tech, and she'd work there. That's a possibility, but after she learned all she could, she would definitely make her own tech company. She'd be less phone and game tech and more automobile innovations. Maybe she created a new, super-speedy express train. I wouldn't put it past her to invent something akin to teleportation, somehow. That might be far, far into her future. Seeing as her job mostly consists of things that can not touch water, she'd most likely spend some of her time near creeks or waterfalls, just meditating and connecting with her element. Eventually, she might get bored of that and make her tech completely water resistant. Everything. I'll talk about Jay in his section.
Kai might try to become a martial arts teacher again, but he would eventually become less enthusiastic about it due to the many, many kids he had to deal with. Then, he tried to pick up blacksmithing again. He created a nice little shop back in Ignacia, looking almost exactly like his parents'. Years down the line, the ninja + Pixal, Skylor, etc. have a get-together/reunion. Kai and Skylor reignite their spark, and they try long-distance. It got stressful, so Kai decided to drop everything and move near Skylor. He worked odd-jobs and lived in a glorified shack just to be able to go out with her. Skylor offered him a job at the noodle house, and he accepted. Sadly, the noodle house closed down due to a lack of workers - even though Skylor, Kai, and maybe 2 other people put their all into it. It was sad at first, but they decided to make the most of it. Together, they wanted to create a new restaurant - a mixture of Chen's noodles and Kai's family heritage & recipes. They just couldn't figure out the name. What could incorporate both Skylor Chen and Kai Smith? Kai quickly came up with the perfect solution. On a beautiful night out, while Kai walked Skylor back home after a dinner date, they stopped on a bridge to look at the night sky. Kai got down on one knee and proposed to the love of his life. They married and could finally start their restaurant - The Smiths'. It was a hit, and they lived happily every day happily.
Zane left together with Pixal to explore the world. They went place to place, experiencing everything together. They did not marry - not for lack of love, but because they felt their love was so much more to them than some silly social construct. I mean, they are going to live forever, as long as they have the proper maintenance. So, they don't think that they need to marry. Even while traveling, they always make sure to come back for everyone's birthday and for holidays. They bring gifts and recipes and knowledge with them. Once they felt they experienced it all, they returned to Ninjago City and worked with Nya. Well, they didn't really work for her. They just popped up one day, and Nya saw them building in her lab. She let them, and they ended up making an awesome hologram for entertainment. They didn't sell it, but every one in a while, the ninja cuddled up again and watched an almost life-like rendition of a Fritz donnegan movie. Pixal and Zane also decided that they wanted children, eventually. So, they made them. They put parts of themselves into the child and even mixed up their own technical make-up to make their kids: Chip and Mackayla, or Mac.
Lloyd kept training the new Elemental Masters, as he felt it was his duty. He really wanted to be like his uncle and train the next generation to make sure they were good people. He didn't expect his deciples to fight off anything major because his team defeated it, but he still wanted them to know how to fight/good vs bad just in case something terrible happens after he and the rest of the ninja weren't around to help. His students became wonderful and helpful individuals, which is far more than he could ever ask for. Aside from training, he started studying and researching. He grew up in dangerous situations, so it's very difficult for him to sit still and not try to be ready for the supposed next attack. His students and his friends keep him in check, and thankfully, nothing comes to pass. He didn't end up dating anyone, not for lack of desire. He just felt in his bones that he would live a long, long life and didn't want to hurt himself by falling in love. He envies Zane and Pixal a bit because of this, but he'd never say that (they know. They feel terrible but can't do anything about it). They visit a lot, especially after the other ninja pass on. Eventually, a while after they make their kids, they make Lloyd a companion - a friend who can stay forever. He cried when he received the gift. He trains many generations of ninjas and sometimes even uncovers a new way to use the elemental powers or spinjitzu. With each new generation, his students get stronger. He lives a happy, fulfilled life.
Jay and Nya get married immediately. Their celebration of being done with evil was their happy, happy marriage. Everyone was overjoyed with them, and you could even see a misty-eyed Kai if you looked hard enough (it's just allergies, guys, I'm not crying. It's allergies. It's the pollen, I swear). After that, he started working on tech again with Nya. He loves it, but he started to get burnt out. He remembers his time on stage, being the center of attention in both real life and in Prime Empire. He makes a gameshow. It was something silly, at first. Like a "how well do you know the ninja" trivia game. It was super fun and he kept getting asked by producers and directors to host more and more gameshows. He became the Steve Harvey of Ninjago; everyone knew him, everyone watched him. When he openly stated that he was starting to get bored of the trivia-types of stuff, he was asked to act in movies and to host in wipe-out shows because of his expertise in agility. Eventually, when he and Nya decided it was time to have kids, he became the best stay-at-home dad anyone could ask for. He loved it. Sure, he got antsy because of the inactivity, but be quickly cured that by just playing with the kids. They ended up being incredibly sporty because of this.
Cole went to art school, even if he was older than most. He went to art school and became one of the best goddamned artists there are out there. He traveled with Pixal and Zane for a hot sec and made it a point to paint from atop every single mountaintop they reached. His artwork is displayed in many museums. One time, a little kid walked up to him and asked him to teach her how to be a good artist. So, he did. After asking her parents, of course (they were very, very starstruck when their daughter came home one day with Cole FUCKING Brookstone, the famous artist, the black ninja, one of the saviors of ninjago). She became like a daughter to him, and was even allowed to travel places with him. She became a wonderful artist under his tutelage, and gained a lot of recognition for just training under him. He realized he had a passion for teaching, and his young student (with a lot of persistence) got him to start his own little art school. He made sure not to broadcast his name or face on the building, because he didn't want people to come just because he was who he was. It became very, very successful and a lot of people have a superstition that being in Cole's presence gives you the ability to draw/paint. This is only mildly true (due to his insane ability to teach), but the Ninja make sure tease him about it. (Kai joined a class one day just to mess with him and was very surprised when he ended up leaving the building with a beautiful, realistic portrait of Skylor. They hung it on their wall and they're still baffled on how it happened.)
Welp. There you go. Here's what I came up with
#ninjago#queue#lloyd garmadon#kai smith#kai jiang#nya jiang#nya smith#jay walker#cole brookstone#zane julien#august's opinion#ninjago headcanons#skylor chen#pixal borg#ninjago pixal
74 notes
·
View notes
Text
in response to a post that I saw on here but didn’t actually want to respond to because dropping a well, actually, into someone’s replies is a bit of a dick move:
I do think some fanfic can work as original fiction. Not all fanfic, no, but some of it absolutely has world building and characterization and arcs that fit into the conventions of published novels and short stories etc. I’ve read both canon compliant fics and AUs that work perfectly well as standalone stories, even if you’ve never interacted with the original media
I can hear someone saying “Well those are bad fanfics then!” And I’m like, well maybe? Depends how you judge a fanfic? What is a good fic vs a bad fic? What is the purpose of a fanfic? What criteria are we using to judge whether or not something works as a standalone story? I don’t subscribe to the view that all stories are fanfic, but I do think all stories exist in conversation with other art. Whether that’s genre conventions, direct textual references, cultural knowledges etc.
“Yeah but look at all this reylo trash that is being published and sucks”
Look, I don’t know if you’ve read much contemporary romance marketed at afab people but it is a genre marked by a lot of lazy publishing trends. The vast bulk of romance novels are not being written or read in a way that emphasizes innovation, quality, world building, characterization etc, because they’re written very fast for a readership that expects quantity over quality. They’re (often not always) the Big Macs of books. And the stuff that gets turned into novels is often the same: tropey, contrived, meant for easy consumption.
And that’s absolutely fine! Sometimes you just want a Big Mac.
Anyway, shorter me: Just because these reylo fanfics are published doesn’t mean all fanfic turned original work is trash. It’s like saying every movie of a book is also trash: some are, some aren’t. Judge the work on its merits, not on its inception
18 notes
·
View notes
Note
Why did you switch from animation to reviews? Also, do you still plan on doing CGI like you mentioned multiple times?
oH BOY..... you may need to sit down for this one
So it all started back in 2012. I was around 14 years old and just saw Rise of the Guardians and Wreck it Ralph. The stories, the characters, the world-building, the animation... now I never really went to movie theaters as a kid, but as a teen I started going and I instantly fell in love.
I went to community college for a few years and made some amazing friends. Loved some of my teachers and we participated in fun events like the 24-hour challenge and Campus Movie Fest. I had gotten in the top picks for Campus Movie Fest at some point and was supposed to go to the Cannes Film Festival in France to showcase my short film, but then the pandemic hit and it got canceled indefinitely.
So get this, for community college, I got a certification in 3D Animation and Video Game development. It's basically an AA degree but without general ed. (Why do you need general ed to get a degree in something? Math and PE have nothing to do with Animation. College is ridiculous. People have to pay you more simply because you were forced to spend more money in college. Wild.)
Out of the 20 classes I had taken to get this certification, only 3 of those courses were hands-on 3D animation. And only one of those courses was hands-on video game development and I dropped out of that class because it was PC only and I only had a Mac at the time. I applied to the class without realizing it was accommodating only to PCs. So even my certification is barely reaching the basics for the title of it, but I did take another online course or two for 3D animation which I have a different certification for.
Now even with my 3D animation, I was never taught the physics engine. I was never taught hair or cloth simulation, but I do have modeling, rigging, animating, and texturing experience. For gaming, I have very little experience. I've only modeled things and found my way around Unity, but otherwise, I suck at coding. I hate coding with a passion. Making a video game without coding isn't really possible.
Now, when the pandemic hit, a lot of things were shutting down. I had no idea where I wanted to go next. People kept asking me where I was going for my higher education, but I kept getting warned not to waste money on college if you're trying to become an artist, especially at University. It's a money pit, and competition is so high, you're not guaranteed a job, you're just gonna be in debt. Even colleges like Cal Arts, who charge over $1K per class, I've been told are a "Pay to get in" kind of place. Where the money is used to nab professionals from their work to teach students or talk about their company or programs, and through that, you get a bigger chance to get your foot in the door because you know someone. I've unfortunately been told that's the more realistic way to get into animation: networking. If you're a shy introvert who doesn't know any famous people, you need to be extremely talented and unique to stand out to get the chance of being noticed. I don't really want to suck up to people nor do I want to waste thousands of dollars and 5 more years on college that I may not even need (let alone be able to afford) especially if there are online classes that may be even more valuable.
Now after I got out of college and started applying a few places, I discovered a LOT of unfortunate information.
Most animation these days is done overseas. South Korea, India, Japan, and Canada are the big ones.
Invader Zim, Steven Universe, Miraculous Ladybug, The Simpsons, OK KO, Star vs the Forces of Evil, Kipo and the Age of the Wonder Beasts, Adventure Time, Twelve Forever, and the Powerpuff Girls Reboot were animated in South Korea. The Ghost and Molly Mcgee is animated in Canada.
(The first four seasons of the Simpsons were animated in America until it switched to South Korea and India.)
2D traditional animation is no longer viable. Puppetry is the industry standard because it's the cheapest. Luckily, Toon Boom Harmony has allowed us to push the boundaries of 2D puppetry. Puppetry these days, if done well, can look really great, like Tangled the Series, but if you don't have Toon Boom Harmony, you're probably not gonna be hired.

Not even all 3D is made in the USA. If it's Disney, Dreamworks, or Pixar, then it's usually USA.
But streaming service movies, like Sea Beast, Kid Cosmic, The Willoughbys, and Klaus, while they claim to be a "Netflix Original" that "Netflix Animation" animated, that's a lie. Klaus was animated by Yowza! Animation in Canada. The Willoughbys: Bron Animation, Canada. Kid Cosmic: Mercury Filmworks, Canada. Sea Beast: Sony Pictures Image Works, Canada. (X)
Go Go Cory Carson is written and storyboarded in America, but the animation is shipped out to be done in France. Sonic Boom is also French Animated.
Even Sony Pictures? Open Season, Surf's Up, Spiderman: Into the Spiderverse, Cloudy with a Chance of Meatballs, SMurfs, Hotel Transylvania, Over the Moon, The Angry Birds Movie, Sea Beast? Sony Pictures Imageworks is based in Canada. They're doing all the animation for them. It's not animated in America, it's merely funded by them.
I should also clarify: I only want to participate in stylized animated media. I don't want to do CGI for hyper-realistic films, which eliminates most of the animation jobs out there these days. It's just not my thing. The insane amount of details and uncanny valley are just so unappealing, I can't do it.
The closest animation studios are still far away. Most companies are located in LA. I'm over 7+ hours away from there. LA also has a high poverty rate, terrible air quality, is overcrowded, and is just generally not a good place to live, especially if you're low middle class. You're not gonna survive there.
Pixar is located in Emeryville, a few minutes north of San Fransisco city. Emeryville is the most crime-ridden city in that area. They tell you not to walk home alone at night. You're more likely to get robbed there than anywhere else according to the population ratio there. There are a lot of gangs that hide up there, and there's a lot of poverty there, even outside of San Fransisco. It's basically a trash pit. Not an ideal place to live, and commuting through 3-hour SF city traffic is also not gonna work. (X)
I have also been informed some people who work at Pixar are petty that the interns use their facility. Pixar has a heated pool, soccer field, gymnasium, and a few other nice things on their property. I was informed there was a person or two who got mad that an intern was using their basketball court.... when the intern was on break. As though they weren't part of Pixar, as though they had no right to touch the property. Apparently, they also used to make the interns push around little tea carts to serve refreshments as a way to "talk to the fellow animators" to probably get them interacting, but hearing that the interns were basically chored with butler duty to bother the animators hard at work seems like such a forced thing. That makes me uncomfortable. Of course, the person who told me these stories has been working with Pixar for over a decade or two now, so things could be very different as the years went on. Pixar itself on the inside of the animator building is gorgeous. They all decorate their office spaces in crazy ways, it looks like a movie set. But they have a bar and "whiskey club". They're apparently allowed to drink at work and have often had parties that got a little out of hand. There's also an old chain smoker room where the founders used to play poker and spy on people outside of their room with hidden cameras; I've even been inside. I don't think they use it anymore, though I'm not totally sure. Some of this info was fascinating, but the drinking made me uncomfortable. I kinda want to work with sober people here.
The sex ratio in the animation industry is also interesting and unfavorable. 70% of the animation and art school ratio is women, but only 34% of the actual animation workforce is women. 34% female to 66% male. More women study animation than men, but more men get hired and hold positions than women. Animation, ironically, has always been a male-dominated workplace. This unfortunately contributes to the "you have to know someone" or "be rich" to get-in situation. Men know a lot more men and not as many women. So the 30 to 40-year-old guys hire the other guys they know rather than a young poor girl with a passion. This makes it even more difficult for me to get in. (X)

20th Century, Netflix Animation, Nickelodeon, Cartoon Network, Bento Box, Vanguard Animation, Universal Studios, Titmouse, 6 Point Harness, ShadowMachine- all LA / South California.
There are a few places I could apply to, but what they do, I just don't care for. Niantic(Pokemon Go), Lucasfilm(Effects), Whiteboard Animation(Marketing), Sharpeyeanimation (Marketing), EA games (Mass Effect, Battlefield, Dragon Age 2, all those hyper-realistic war, sports, or fantasy games.)
So whether it's outside of the USA or within the USA, I need to move. I don't have the money for that yet.
Just find a company that does remote work, right? It should be easy, especially in pandemic times! Wrong. Most animation companies don't permit remote work. It's probably a security issue. But I've done research on this. The only big animation company I've found (so far) that allows remote work (or is HIRING for remote work) is Mainframe Studios in Canada. They have a 3D animation job list, and I guess they focus on animating Barbie movies(???). (X) But that's about it. And even if you're a remote worker, there's a high likely hood you still need a Visa to be allowed to work for a company belonging to another country. So that's a whole other legal process to deal with.
Disney is becoming a huge corporate monopoly over American animation. They bought Blue Sky only to kill them off. (Disney also just recently laid off 7,000 people due to their stock price drop and failed movies they released the past year with deliberately bad marketing for political reasons. (X)
Disney also bought Pixar and is pushing for sequels because weird or bad, sequels and terrible live actions make them a LOT of money. Did you know Disney's terrible Lion King CGI remake is amongst the top 10 highest-grossing movies ever made? It's criminal. (X)
Because Disney is such a big name in the USA, there's a huge association of animation = children's media, which is not true. Animation at the Oscars also has its own category, when it's not a genre, is a medium. Disney often wins at the Oscars too because no one sees the other animations. Granted, Disney has an insane marketing budget in comparison, but it's clear no one cares to seek out animation outside of heavy CGI live-action these days. No small-time studios, no limited releases, no anime. The fact that Disney also now OWNS the Oscars is SUS as hell. (The fact that Disney-owned ABC threatened the Oscars, forcing them to cut 8 categories or else there wouldn't be a show that year is wild. There isn't even an oscar for stuntmen. What the fuck, Hollywood?) (X)
Dreamworks nearly went bankrupt and sold itself to Comcast back in 2013. Comcast also owns Illumination. Dreamworks has been focusing on making bad tv show adaptions of their IPs. So yes people, Jack would sooner meet the Minions than meet Elsa. Disney is the biggest corporate monopoly, but it's definitely not the only one. The animation industry in America is snuffing out its competition by buying it out for itself. It's insane the kind of power they have.
Competition is HIGH. Because of this, the only ways to get in? If you're rich or you know someone. Pixar gets over 3,000 intern applications every summer. Less than 100 are seen by actual hiring managers. The most interns Pixar has ever taken in a single year were 12. The least they ever took in a single year was two. A 12 to 3,000 ratio is not favorable. That's a 3% chance to get into a big-shot animation company.
And again, because remote work isn't permissible to new hires, you need to live in the area to commute to the campuses. This is one of the reasons why LA is so crowded.
If you get into an animation company purely remote and maybe even for a different country? You are the luckiest person alive.
Programs are expensive. The animation industry is very strict on what programs they use. The industry standard for 2D puppetry is Toon Boom Harmony; the industry standard for 3D animation is Maya, and the industry standard for video game development isn't as clear but Unity is one of them.
Some of these programs are free, as long as you are a student. If you are attending college or a certain online program, you can use your school-issued email through them to apply to get the program for free for about a year. Otherwise, if you're using it to make your own animations solo?
Autodesk Maya: $225 a month or $1,785 a year (X)
and guess what? Maya removed its free render service. Arnold is now built in by default, however, if you want to BATCH render (Meaning render a full scene or several slides) it will slap it's ugly watermark over it.

Fun fact, this very rendered watermark can be seen accidentally in a single frame for the Kingdom Hearts Frozen cutscene

Well, you need to batch render if you're trying to animate so let's see what Arnold costs-
$50 monthly to $380 annually.... are you kidding me?! The rendering PLUG-IN BUNDLED TO MAYA COSTS MORE TO USE THAN THE OWN PROGRAM?! (X)
Now, there are other rendering plug-ins you can probably use with Maya. But they all have their ups and downs and their own costs as well. (X)
Pixar's Renderman is $595 per license. I can't seem to get info on Octane. V-ray solo is $39 monthly while premium is around $60 monthly.
Now there IS Blender, an alternative to Maya. It is free and I have it. That is ideal to work in for people like me. I tried it a while back, but I hated the interface windows. It was hard to work on it when you can't close them properly. It's possible they've fixed this in an update, but I haven't touched the program in over three years so I wouldn't know. It's different from Maya a little, so it has ups and downs in comparison too. But Blender is a savior to 3D artists everywhere.
Toon Boom Harmony isn't as bad but still high: Lowest price is $27 monthly / $220 annual and the highest is $124 monthly / $1,100 annual (X)
Unity has a basic version that is free, but Unity Plus is $399 yearly while Unity Pro is $2,040 (X)
So some programs are clearly more viable than others. But imagine you're trying to model, texture, rig, animate, simulate, and render a short film all by yourself in Maya. That's gonna take you over a year or two, and you'll have several thousand dollars out of your pocket by the time your free trial ends. And might I say, for an industry-standard program, Maya sucks. It's almost unusable without those plug-ins for not only rendering but also for the models to even be able to SELECT their BONE rigs.
Do you want to practice on your own when school is out of session? Fuck you! Fuck subscription services! Welcome to capitalist hell, baby!
Again, using Blender is more viable, but you're still going to be basically doing everything yourself. That's gonna take years. Do you have the patience for that? Do I?
Because of the pandemic, movies aren't even hitting theaters anymore. They're going straight to streaming services. Streaming services of which, gain sole rights to and can take media off their platforms at any time without warning. Thanks, Discovery+ ! Does everyone remember the HBO Max Animation & DC purge? It could happen to other streaming services too. Piracy will save the future of animation at this point. (X)
And again, Streaming services like Netflix will purchase films and claim they made them by slapping their logo over it; but no, they either bought the distribution rights or produced them through funding and maybe storyboarding. Often times from a Canadian film studio. (Link again X)
Even stop motion companies like LAIKA are losing money and may have to shut down or be bought out in the future, especially considering how much work and money they put into their films vs. how much money they actually make. (X)
All of this? Naturally made me fall into a depression. My god, the layers of hopelessness. My animation and modeling is pretty average too. I'm decent. I can maybe make a good shot. But I can't blow people away like James Baxter can. I mean, I shouldn't compare myself to people. If I worked really hard, maybe I could get into a good company. But again, I have to move!
A part of me gave up. I don't really do 3D animation anymore, though part of me misses it.
I still 2D animate. I'm trying to make a short film and though my college friends who were working on it with me have given up, I have done my best to keep going. Even if it has been produced at a snail's pace for the past three years, I still intend to finish this animation. It's gonna be beautiful when it comes out, and it will be a wonderful portfolio piece regardless.
So with nothing else to do and no other kind of job experience really under my belt(plus my family is prone to covid so getting a job in the pandemic was just kind of out of the question) I decided to go to youtube. I heard some people can make a little money on there, but the truth is I had actually wanted to become a youtuber for a few years prior. I've always looked up to animators and reviewers on youtube, I've loved the stories they tell and their incredibly detailed analysis essays on movies, tv series, books, etc. I wanted to be one of them. I wasn't sure exactly what I'd do, so I just followed the Youtube Partnership program set up which took a few months, and then jumped in! I found I only had the time to upload once every month or two. I had a ton of audio issues and I'm not outputting at the proper 1920 x 1080 quality that I should be doing either. It's a huge learning process that I still haven't perfected, but I'm taking notes to try and get better.
Even though Youtube is fun, I only make $300 a month, and that isn't even consistent. With patreon, I make maybe another $80 or $100 on top of that, so overall $400 a month average. That's really nice and pretty cool! But it's not enough to survive.
Now I work part-time at a coffee shop. My mental health is a lot better and I love my coworkers. I make roughly $400 a week in comparison to the $400 a month. It's still not enough to live off of (the cheapest rent around is over $1,000 a month, not ) and it's still a temporary job in the long run. I intend to work here for maybe another two years to save up money.
But what do I do now?
Am I welcome in animation spaces anymore?
As a critic of popular media, it could be likely that they could fire me or deny my application because of my critique of their past films or tv series. They could see my youtube persona and assume I'm a raging untrustworthy nitpick instead of a passionate, kind person.
Vivziepop's Spindlehorse company? What Viv was doing was a dream. I was so inspired by her. She made her own company, made a super successful pilot, and was even creating more jobs for traditional, high-quality animation. However, for Hazbin Hotel, she required more funding, which is why she sold it off to A24, who now has corporate say in the show. A24 is known for letting creators be more lenient, but otherwise, Viv won't have full control over it anymore unless she managed to get them to sign something over to her; but with the rumors of her being kicked off season 1? I don't know anymore.
Her own company Spindlehorse; they rely on youtube revenue and/or merch sales to fund Helluva Boss. That's a tricky business practice, but it's kept them afloat so far.
However, Spindlehorse is hiring a lot of people as of late. This could be a bad sign; that people might be leaving the company due to potential mistreatment or unhappiness. With the way the show is going, I don't really want to be part of that company regardless, but maybe before season 2 of Helluva Boss, I would have considered applying. Had I made any critique videos prior, there's no way they'd accept me. "Aren't you that one YouTuber that said my writing is bad for season 2 episode 2?" And you expect me to hire you?" Like yeah, that application process would go down well. Not. By critiquing artists' work, some of them are very sensitive. I'd be kicked out for a lot of things, when really, we artists should be critiquing each other all the time, trying to improve. That's how the writer's room always is, ahaha... hours of fighting goes down in those meetings. It's intense, but fun.
But yeah, it's such a shame. Even small companies need to sell out to corporate to survive. Either that or be HEAVILY crowd-funded, which again, can be a slippery slope.
I see a ton of small projects on Twitter looking to hire people, or looking to become a big studio to release a pilot or game. I've joined a few of them, but most are unpaid because of COURSE they are, and then these projects?? Just don't go anywhere. Because it's unpaid. Because we can't afford to work on a project for free. IRL comes first. Some of these projects seem so great but they don't go anywhere, and it's hard to have faith in start-up studios anymore. (Game creators might have a chance, but tv series or films? Good luck, folks.)
At that point, should I just make my own company? I don't have the money or knowledge for such a thing! It's insanely expensive to start a business and get licensing. So much paperwork, so much everything! And the USA Government is so behind in understanding technology. If you want to create a remote business and/or copyright something, you're still required to put an advertisement in a local newspaper about it, even if your business isn't selling to locals. 💀 The number of fees and ridiculous legal hoops you need to jump through... it's a ridiculous waste of time and money. But you need to do it. The question is, am I willing to do it? Am I willing to tackle such an insane thing by myself?
I want to keep my internet persona and IRL persona separate, but can I?
I value having a private, quieter life away from the screen. I worry about getting doxxed one day because of the nature of the internet. I worry about people finding my IRL resumes or profiles for work I want to do outside of youtube for security's sake. My art style is unique and very recognizable. I don't have a lot of private art that is worthy of being in a portfolio. But for absolute safety, I'd need to password-protect my websites or portfolios so the public doesn't have free access to them; only companies I'm applying to. But at that point, does password-protecting my resume and portfolio make it less likely I'd be hired due to the inconvenience? Due to the private, hard-to-find nature of my work? Being a YouTuber with great story skills and art skills with a fanbase could be a big plus to getting hired somewhere, but it could also be a horrible disadvantage that would get me fired. It's a double-edged sword that I cannot work around and I don't know what to do.
I've considered the video game industry, but even that isn't ideal. A lot of the indie ones I adore aren't made in the USA. Gris and Monster Camp were made in Spain. Ori and the Blind Forest: Austria. Hollow Knight: Australia. Little Nightmares and Raft: Sweden. LIMBO & INSIDE: Denmark. Outlast, Don't Starve, Spirit Farer, Bendy and the Ink Machine: Canada.
SuperGiant Games did Hades, Transistor and Bastion and is located in SF, but they're not hiring. Janimation, a multi-media company located in Texas isn't hiring. Frederator in New York isn't hiring.
I don't want to work for a studio that does nothing but first-person shooters or sports games. If I want to get into the gaming industry, I probably need to crowdfund and make a company to make a game myself.
If I make my own game, which I've wanted to do for a long time now and still want to... I can't code. I guess I could try to hire someone that could? But a game to the extent I want... I'd need to start small. I'd need to practice. It's several years of work. Will it even be worth it? I don't think I can do it alone. I'd need crowdfunding and workers; which again, here comes the "make my own studio" issue...
Do I even want to animate anymore? I prefer traditional animation in comparison to puppetry. I prefer 2D animation to 3D animation simply because it is more accessible.
But even then, I'm finding myself drawn more and more to writing, storyboarding, and character design. If I were a 3D animator, this is mostly what I'd be working with all day: Naked models in an empty room. I'd do none of the physics simulation or texturing or lighting.


Animating naked & bald people all day... I don't know... 3D Animation kind of lost its appeal. You only work on such a small portion of a film, you almost never have the bigger picture. You won't see the final result until the film is done. As an animator, you're almost kept in the dark. Maybe that's how they want it anyway, since leaks are a huge issue they keep quiet under strict NDA.
But yeah, anyway... I'm an artistic digital generalist. I can do almost anything. 3D animation, storyboarding, writing, photo editing, illustration, rendering, modeling and so much more. It's hard to choose what you really want to be in this industry. I feel like Barry Benson dfklgjdflkjg

I don't know what I'm gonna do anymore. There's gotta be a solution to this but I just can't figure it out. I don't want to give up my youtube channel so I can be an animator. I don't want to give up a safer, quiet countryside house to be able to survive financially. Am I even willing or able to move countries? Is my career more important than friends and family?
I think I'm thinking too much about everything. I should start small. Move less than an hour away first and move in with roommates to get a feel for independence instead of jumping into it immediately. Get a job at a small time company, maybe not for what I want at first, but it'll get me some experience and maybe I'll learn some things along the way to understand where I can go next. Take it slow and don't panic too much over trying to be a young big shot. Take things one day at a time? That's my current goal, I suppose.
So you know... to answer your question... why did I switch to youtube for a current career? Because of a classic existential & career crisis in my 20s. Will I ever go back to 3D animation? Maybe. Maybe one day.
#ask#personal#3D animation#career#youtube#long post#i should also say because im a fan artist#i dont have a lot of original work to add to a portfolio which is a HUGE issue#Pixar doesnt even want to look at a portfolio if it has copyrighted material#they want to avoid lawsuits if they see material owned by a different company#you need to be so careful what you put in a portfolio#i mean especially if i use my 2D stuff or illustrations#my illustrations especially#animation#the animation industry#CGI#rant
81 notes
·
View notes
Text
10 songs tag
thank you for tagging me, @megarywrites ! doing this for the faery children, as usual.
rules: Use your WIP playlist and put it on shuffle. Write the first 10 songs that come up and quote your favourite lyrics from each song and/or the lyrics that fit your WIP best (they might be the same lyrics), then tag 10 people.
tagging: @deanwax @outpost51 @mrbexwrites @unmellowyellowfellow @sarahlizziewrites @ibuprofen-exe @mintyswriting @wardenwyrd @pumpkinsplots @keysandopenmind
shrike (hozier) - accurately describes how ola perceives her feelings for afsara
Dragging along
Following your form
Hung like the pelt
Of some prey you had worn
Remember me, love
When I'm reborn
As a shrike to your sharp
And glorious thorn
visions of gideon (sufjan stevens) - tragic-sounding song, and also relates to a very sad scene in act 2 :)
I have loved you for the last time
Is it a video? Is it a video?
I have touched you for the last time
everybody wants to rule the world (specifically the lorde version) - this has more of a dystopian/creepy feel for it, so the lyrics here are more to do with afsara's own guilt
It's my own design
It's my own remorse
soldier, poet, king (the oh hellos) - classic medieval fantasy pick. afsara is the soldier. 'nuff said.
There will come a soldier
Who carries a mighty sword
He will tear your city down
harsh realm (widowspeak) - i love tragic romances. even in hell ola loves afsara.
I knew you in the harsh realm
I thought about how it was
I thought about you because
I always think about you
no rest for the wicked (lykke li) - uhhhhh listen the codependent tragedy something something i like tortured gay people
If one heart can mend another
Only then can we begin
So won't you hold on a little longer
Don't let them get away
lavender moon (haroula rose) - a key theme of the story is dreams, and what happens in dreams affecting real life. also gay.
Walk the memories
Just me and the lavender moon
She knows
My heart belongs to you
witch's rune (s.j. tucker) - good old witch chant
Mother of the summer fields
Goddess of the silver moon
Join with us as power builds
Dance with us our witch's rune
devil's playground (the rigs) - this one was picked mostly for vibes i won't lie, but for lyrics i guess this would relate to the girls grappling with their desires vs their duty.
Brave, are you brave enough to meet
The desires that you seek
Hold my hand, I'll set you free
gypsy (fleetwood mac) - god what a classic. also lightning motif. also dedicated to your lover and how ola believes these moments are all she'll get with afsara.
And it all comes down to you
Well, you know that it does and
Lightning strikes maybe once, maybe twice
Oh and it lights up the night
And you see your gypsy
8 notes
·
View notes
Text
risk e. rat’s pizza and amusement center
the awkwardly long name (read: it’s always sunny in philadelphia) - both character and show meta incoming and I feel like that’s the first hint of the latter
am I the only one who keeps thinking risk e. rat’s pizza is the pizza for you and me…
“they make kids feel like they’re the ones in charge” - so interesting coming from mac mcdonald. soon followed up by “they were the first set of boobs I ever saw since my mom’s” which ties right into the burgeoning mommy issue thread
at the end of the day it’s all part of the fun!
just the gang singin’ in the car :)
dennis “that’s not my name” reynolds
how have I just NEVER noticed that dee is left-handed???
the broken water fountain - does it mean anything? I’m too tired to figure it out I need my tumblr brain trust
maybe mac being clean-shaven this season is to make him seem more boyish? I have a new theory for this every episode
I think I saw someone else say this but I do think it’s fitting that charlie and dennis are together on the titties storyline because of their shared baggage around childhood sexuality, like no one else in the gang would really be able to relate to dennis here and if charlie is figuring his shit out with that then he'll definitely serve as a parallel for dennis having to figure it out too
I like how they represent three different eras of risk e.’s (frank, gang, present day) to really explore changing values and how things getting softer can be bad in some ways but good in others. this episode definitely feels in keeping with lethal weapon 7 as a very sunny way of critiquing sunny that feels satisfyingly self-aware but also fairly true to form which is a pretty fine line to walk, to give credit to rcg and the rest of the creators
also if you haven’t seen the john oliver piece on chuck e. cheese go watch it because it provides so much context and crazy true history of these types of places that was definitely in my mind while watching this episode
dee and frank paired up again, and in a childhood place, probably ties into the dee parent-issues thing I hope they’re building up to
each character really tells on themself about what fucked up stuff they’ve come to believe is acceptable or even enjoyable but should be questioned:
frank - violence and verbal abuse toward children and everyone; sexually harassing women with impunity; calling people the r-slur
dee - ethnic humor, not racist humor; making her explain how it’s funny and realizing it’s not; ecologically irresponsible plastic cheese that gets immediately thrown away; dimwit duck or whatever his name was; not understanding what satire really is!!! ← they really took one of their biggest critiques head on
here’s a question I have about dee’s character - she tries to justify her problematic sense of humor and every time frank points out the truth behind it, illustrating what’s really awful about it without really meaning to, and dee seems to genuinely recoil like she doesn’t like that. does she feel bad and react that way because she doesn’t want to do harmful things, or just because she doesn’t want to be perceived as being un-pc because that’s what’s uncool now? like remember when charlie said “I think I might’ve called an old lady a cunt this morning” and looked kind of aghast at himself? could dee be developing more of a conscience too and if so, what does that say about her? or is she just a vehicle for rcg to navel-gaze about the show? also remember in lw7 how mac was like “if you don’t praise me for being a good person then why am I doing it?” I lie awake at night wondering how much rcg want to be better people vs. how much they don’t want to be kicked even further down the hollywood totem pole for being yucky. please share thoughts if you have any
mac - simulating real-world violence to get it out of his system; shame - “if you got no shame, you’re never gonna hate yourself enough to stop being bad”
dennis and charlie - being unprotected growing up; that’s what the bone’s for! (there’s nothing like a glenn and charlie riff btw); is it wrong because she’s underage?
sunny is really amping up the inner child work for the gang, I mean arguably the gang have always been childish but this season I feel like they’re exploring it in a more comprehensive way like via the setting of this episode. and it ALSO works as a perfect commentary on the show and we love the layers
there’s no adults around…
“cause we need monster representation” we need some representation for those who are freaky and fucked up okay??
I wish I could remember who said it but someone suggested that the de-breastifying of justine has to do with dennis’ heteroness disappearing and that is a very fun take - I do think it says something that they’re fixated on a very abstracted version of sexuality via these almost disembodied tits that aren’t even human… like are we overcompensating for something gentlemen? can the characters and the show itself have any relationship to women that doesn’t objectify or otherwise dehumanize them?
I for one think sam is supposed to look like a young mac, I saw some people questioning why they cast that kid and this is my theory. this is important for both the inner child and possible child-rearing stuff they’re bringing in
“hey man, I’m a licensed psychotherapist–” “you’re a talking dog”
“guys I hate to admit it but this place sucks now”; “that’s crazy, this was like one of the best bars in town, man”; “they could redeem themselves in the show” all very meta
“you cannot call a place a website” hahaha
“so that these kids can have the same experience that we had when we were younger” fucked up childhoods, the cycle of trauma, but also the show being how it used to be
and of course, an attempted revival of all that leading to immediate disaster. let’s move forward, not backward :)
#man I've had a hell of a week. really not feeling emotionally ready for the finale lol#sunny#always sunny#iasip#it's always sunny in philadelphia#risk e. rat's pizza and amusement center#s16#s16e6#sunny meta#I didn't really like this one at first I felt like it didn't flow and was too self-conscious but it grew on me in the rewatch#still not a fave but it's both fun and has stuff to say so that's cool#I haven’t even watched bowling yet 😭 gonna go do that now god bless
11 notes
·
View notes
Text
sorting the gang: mac
Previously: Dennis
We started with a non-obvious sorting so now let's move on to one of the easier ones.
PRIMARY: Snake (extremely dysfunctional), Bird model (extremely dysfunctional) (or the other way around?)
OK maybe it isn't THAT easy. Honestly you could go either way on this. I think part of it is that Mac's character gets written really differently depending on the episode/season (and a lot of fans LOVE complaining about this, "omg they ruined Mac's character" etc., despite both sides of his character being there early on)
Mac obviously is pretty attached to his worldview, usually his religion. He builds his entire identity around it and spends a lot of energy trying to work out the contradictions, the biggest example being being gay vs. being Catholic. He is very proud of how he can view the whole world through whatever lens he has glommed onto at any given point.
youtube
science is a LIAR sometimes
Idk I had an entire paragraph here about how everything he says in that video is wrong and how malleable these identities actually are for him in practice until I thought maybe that was still what Birds do especially less mature ones so idk. (Full disclosure I don't really "get" Bird primaries so I might not just be good at recognizing them?)
But I think a picture speaks a thousand words, especially when it is a picture that contains a thousand words:
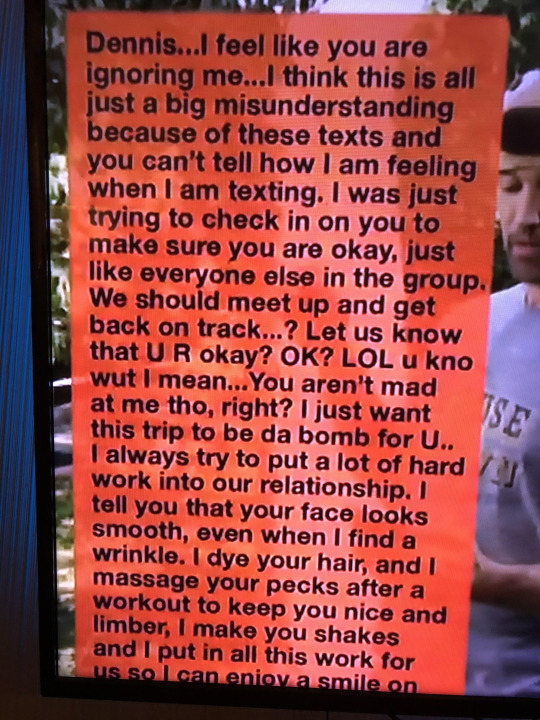
"just like everyone else in the group" lol ok mac
Mac is a Snake whose people don't give a shit about him. His people are his dad, his mom, Dennis, and to a lesser degree Charlie. "The Gang" isn't really a thing for him as a unit, those are the only people he cares about. And he really cares. ("We're like the best friends in the whole goddamn world and goddamn them for making me think otherwise!")
It isn't a good kind of caring. On his end, they are deeply codependent up to the point where he smuggles drugs for his dad because he's his dad, calls the cops on Dennis when he is out of the apartment for an hour, poisons Dennis to try to make him dependent on him... (Can you be Exploded about more than one person?) And obviously on their end all these people either openly hate Mac to an abusive extent or only give a shit insofar as they can use him. And Mac is deeply in denial that this is possible for his people.
youtube
like, even just the idea that OBVIOUSLY Luther wants to see this picture of his mom because OBVIOUSLY she's really important to Luther just like Mac is OBVIOUSLY important to him because OBVIOUSLY he would also care as much, that's how relationships OBVIOUSLY work...
And most importantly, the idea that other people in the world have things to offer does not register. It's not on YouTube but there's a legit tragic scene in the last season where Mac meets his uncle Donald. Donald is a family scapegoat for all the same reasons Mac is, and he is lonely and eager to connect. He is the perfect father figure for Mac, who desperately wants a father figure... and Mac doesn't give a shit about him. He sits through all of this with total disinterest. Charlie sits there the entire scene getting increasingly frustrated: "You have everything you've ever dreamed of right here, but we're gonna just blow right past it, aren't we?"
SECONDARY: Lion (Snake model except he is bad at it?)
This is the easy part, I mean like do I even have to explain it? Mac reacts to things. He reacts to things like a bomb does. Or like whatever the most badass and/or powerful action is at the time. ("Mac sees himself as the boss in most situations and the gang constantly complains about his bossiness.")
youtube
it like personally offends him that the mafia does things other than be badass at people
There are three common Mac plots. One is that Mac and someone else (usually Charlie) escalate each other into chaos. Two, someone (almost anyone) manipulates him with zero effort. Three, someone (usually Dennis) attempts to do a scheme with him that he derails loudly. Basically Mac is earnest, in a way that only Charlie really matches. I think that's probably part of why they're the two members of the Gang most likely to be interpreted as kinda-maybe-salvageable deep down even when they objectively do just as bad things as everyone else.
This is Sunny so Mac has a baseline ambient level of lying and scheming, i.e. lowkey Snake modeling. Notably he got a double dose of that model from hanging out with the Gang and beforehand from growing up with career criminals as parents. But he's the worst person in the Gang at scheming and it isn't remotely close. Which is not to say that he doesn't try to manipulate people, he just....... fundamentally doesn't get the concept:
youtube
"Oh shit... right, don't give away the information." feel like I'm using all my memes on these
Obligatory disclaimer that again this is the most exaggerated and cartoonish and just incredibly dumb version of Lioning so just like if you're a Bird secondary don't be offended about sharing it with a serial predator, don't be offended about sharing Lion with this incredibly dumb individual
8 notes
·
View notes
Text
rehashing this post from right before s15 like. hm !!!!! first half of the post died like hoodie gate and dennis in macs room turned to be Nothing. i’m still maintaining they fucked over quarantine (SINGING HAPPY SILLY LITTLE COUNTRY LOVE SONGS ?????? country mac vs mac) but. dennis is still emotionally in north dakota. he’s still fight or flight. he’s learnt he can’t survive without mac without the gang and still had to come crawling back to philly But he’s not emotionally back. he’s not accepted he’s back and this is Who He Is. that he couldn’t survive as someone else once again. he’s terrified mac and the gang can see through him. he still wants to run. the gang go on holiday. go where PURPLE ??? that’s not a place !!! vocal stim of all time. they go to ireland back to their Roots. they’re an Irish bar. macs so aggressively american irish. let’s tell him he’s dutch. to shut him up. need to confuse him, spin him around, give him a different focus other than Me.
mac and dennis barely interact in ireland. dennis’ obsession with authenticity almost killing him. he’s trying so hard to be Real to be a Real Person. not Himself of course. someone real here. s14 health scare dennis NOT vigilant about covid ???? REFUSING to admit he had it. because it wasn’t authentic. wasn’t Real. because he spent 2020 hiding away with mac, slowly falling back into old routines, back in love back to being see through. fuck. that’s Not what ireland was for. dennis being the one to point out charlie’s dad died from covid. weird washy vision. dennis the “Only One” who didn’t get vaccinated. s14 health freak out dennis more about mac than anything else. he wanted Everything to be The Same back to when they could read eachother BUT he’s terrified of being Seen by mac. by mac who can Now see himself as gay, what the fuck is he finally going to be able to see in dennis. macs been spun around by dennis so he just goes to i’ll look after dennis Directly when he asks. i don’t want him running away from me again. also pizza poisoning. building back up that codependency. dennis needing anything else than Mac to blame all his mac problems on. Macs priest journey he’s thinking about Himself he’s Looking After Himself. not dennis. big mo should we quit the game. if you’re not having fun anymore. he’s not. everything with dennis is more Pain than anything else. being suffocated by his own love. sorry about the delusional maccricket hopes. mac and cricket ex boyfriends i’ll never stop believing in you though. macden using cricket as a middle man instead of just fucking eachother. den and charlie trying to spin him around confuse him saying he’s not irish. okay. next aspect of my identity is catholic. i’ll just go Full into that. the wars over. the storm has stopped raging. maybe. it’s complex. but it’s easier than dennis. feeling unfulfilled by the church though. this isn’t what i wanted this isn’t filling my dennis shaped hole. coming back together on the mountain. to help charlie. finding the truth. they lied to me told me i wasn’t irish just because they thought i was annoying? heartbreaking. DEVASTATING honestly. fuck you im leaving. i don’t have to help you. you’ll never help me. all i’ve been DOING is trying to Look After Myself so you wouldn’t have to. macs whole LIFE trying so desperately for someone to Love him. fuck man.
but back in the pub. mirror of paddys. we’re never escaping paddys. but why would i want to. we’re always running out into the world looking for treasures when everything we need is right here in the bar. their own ecosystem. and we carry out country (us. giggling like yeah the United States US and just. Us as a relationship) with us wherever we go! BECAUSE WE LOVE HER! and when you love someone , you can’t BEAR TO LEAVE EM BEHIND” watch dennis. face journey. he realises before mac. he loves philly he loves paddys he loves the gang he loves mac. HE CANT KEEP RUNNING AWAY. it’s okay to stop and be stationary. it’s okay to be who you are. “not ever” he’s ran away so many times. even this holiday with the gang he’s running from them. mac looks at him. mac knows. it’s okay that mac can read me that he can see through me like this. it’s good. i missed it. i’m weak and tired of running and I’m Sorry. everything i’ve done to you because i hated myself because i was scared of myself. they go to charlie. it’s the big game. they’ve embraced who they are (american) (Who They Are) and that’s when you WIN. dennis was in north dakota during the big game. wasn’t part of it. was still running. i’ve said it a thousand times sure he’s physically back in philly for years but emotionally he was still running. he’s stopped. laid down to rest.
i don’t want to hypothesise about s16 too much but after the first two eps are out i feel confident saying. the cat is poking his head out of the wall. he’s missing mac. i’ve said before end of clip show SINISTER “we’re back to normal” it’s dennis’ fantasy he wants so badly to become reality. he’s the best at monitoring reality and pulling one over on the gang. because that’s all he Ever does. that’s all he’s been doing. they’ve only just caught on or directly challenged him or tried to live in their own fantasies. i don’t know if dee’s cat is fully coming out of the wall but he’s poking his head. barely saw macden apartment last season because they were running away from her. sterile. in the season Opener we saw Her Insides. the fridge. casual domesticity. throwing out all of their furniture and sleeping on a blow up bed together. he’s stopped running. when you embrace who you are then you WIN. but. macs moving on. it’s been too long. took dennis too long to adjust. that happens. i’m so scared to tinhat about johnny but. i’m still your leading man. macs got another leading man. he’s being replaced maybe. it’s me it was always me. i think we’re gonna see more of that. i have always trusted the structure. i don’t think it’s going to be fruitless. yeah i think i’m out now. he’s BACK from north dakota he’s working on himself. macden doorway in inflates mirroring macdenbreakup. we don’t need to tell you our business. he’s protecting himself protecting their relationship. he’s not getting angry anymore. working to be a person. not letting small things blow up anymore. but it’s not going to be enough. he needs to Show Mac he cares More. it’s going to be difficult but. i trust the structure
#trusting the structure#omg i deleted the screenshots and it’s not letting me link the post#brb#okay the link should b there and i’ve added a keep reading
8 notes
·
View notes
Text
The Blue Brand Wrestling Blog #1 - Wrestling News From This Past Weekend (WWE Payback, CM Punk & Tony Khan)
The Blue Brand Wrestling Blog
THEBLUEBRANDWRESTLINGBLOG.BLOGSPOT.COM
The Blue Brand Wrestling Blog #1
Wrestling News From This Past Weekend (WWE Payback, CM Punk & Tony Khan)
Hey there guys & girls,
I’m Andy Mac, AKA The Blue Brand owner and creator (@The_Blue_Brand) on X / Twitter. I thought I would delve into the world of blog writing and what better thing to write about than my favourite pastime Professional Wrestling.
I started watching WWF back in early 2000 around the time of the Royal Rumble. I was instantly hooked and became an avid fan of the great one, the brahma bull – The Rock! I was 100% invested in his battle with the Big Show around this time before heading towards WrestleMania 2000’s fatal four-way (McMahon in each corner) match against the champ Triple H, Mick Foley and The Big Show.
Since then, I’ve never looked back really, and I’ve been watching WWE for 23 years and counting. During this time, I’ve checked out TNA / Impact Wrestling, AEW and most recently Pro-Wrestling NOAH from Japan.
Anyway, maybe for a future blog I’ll write more about my introduction to the world of professional wrestling as a 9-year-old in the year 2000 and tell you who my favourites were. For now, I’m here to talk about this past weekend – 2nd & 3rd September and two stories I’ve decided to give my views on. Obviously, all opinions given are my own. Let’s get started –

WWE Payback – Saturday 2nd September 2023. Pittsburgh, Pennsylvania at the PPG Paints Arena.
Seth “Freakin” Rollins (C) Vs Shinsuke Nakamura – Winner, Seth “Freakin” Rollins.
Match Length – 26:05.
I know most people coming out of this PLE are talking primarily about the women’s steel cage match between WWE Hall of Famer Trish Stratus and “The Man” Becky Lynch. Don’t get me wrong, this match was great and deserves all the praise and plaudits that is currently receiving, but for me personally the main event was the highlight.
First of all, it was extremely refreshing to see a different main event match at a PLE that didn’t include Roman Reigns or the Bloodline. Of course, I’m a huge fan of this storyline and the journey we’ve all been on the past few years, but it was nice to explore and experience something different.
In the build up to this match we got to see a ruthless and more aggressive side of Nakamura that we haven’t seen in a very long time. On top of that on the night of the PLE the company released an awesome animated promo package with Nakamura narrating over the top of it about what he planned to do to Rollins in their match. Rollins sold this well during the match – I also enjoyed the personal touch with Nakamura taking aim at Rollins family in the build-up.
Both men made their way to the ring, went through the usual introductions before the match got underway. Heading in to this one I had put money on Nakamura winning, especially with The Great Muta being in attendance. But in the end after a match that lasted just over 25 minutes, Seth Rollins managed to get the win with a curb stomp. This match was refreshing in sense that we had a babyface champion defending his title successfully in the main event of a WWE PLE. I also loved the fact that the pacing of the match was really well laid out. The match was telling the story of an injured Seth Rollins dealing with severe back issues that had been highlighted in the lead up to this match – So naturally as any good heel should do, Nakamura attacked and went on the offence with strong moves on the champions back. I’ve got to also give Michael Cole and Corey Graves huge credit for really selling the severity of the back injury and the pain Seth Rollins was having to deal with. My only critique of this match was the actual end, it felt quite abrupt, not due to match length, but maybe I’ve become to accustomed to multiple kick outs from finisher after finisher in Roman Reigns and AEW main event matches.
Initially I was disappointed it also ended the way it did for Nakamura, a clean loss after being so savage before and during the match. But thankfully once the PLE went off air Nakamura assaulted Rollins on the ramp. This feud still has legs, Nakamura can be a whiny but savage heel who feels embarrassed losing this World Title match in front of The Great Muta.
Let’s see how this one plays out on Monday Night RAW tonight!

Tony Khan and CM Punk – AEW Release CM Punk after (another) backstage fight
I’ll start this with Tony Khan – The list of job titles this man holds within the company alone should show why this doesn’t work. I know people will be quick to tell me The Elite are VP’s and have different roles within the company… But let’s face it, Tony holds all the real power and authority and he’s shown multiple times that he isn’t capable of being a strong leader or showing true authority to members of his roster who act out or behave unprofessionally. Let’s be honest, CM Punk should have been gone after the press conference and fight afterwards with The Elite last year, this all occurred after he defeated Jon Moxley for the AEW Championship at All Out 2022 last September. The fact Khan was willing to bring him back, basically create a whole new show for him and allow the carnage to continue and expected it to be smooth sailing says it all. What did he expect to happen? Can you imagine Vince McMahon allowing this to occur?
Now I’ll quickly discuss CM Punk – As I write this there are reports online about WWE actually being interested in CM Punk last year before WrestleMania. The idea of him returning at the Royal Rumble 2023 and being eliminated by Kevin Owens was proposed. This would supposedly lead to him facing Owens in the main event of WrestleMania night one. This apparently was actually considered by Vince McMahon and Triple H. These reports also note that Vince McMahon is open to Punk returning and Triple H would consider it, however he would want long-term story plans etc… in place. All of this makes sense if you consider Punk showed up at a Monday Night RAW earlier this year in the parking lot.
In conclusion, Tony Khan in my opinion needs to hire proper management that can be in between himself and the talent – Omega and The Young Bucks don’t count, sorry Tony. CM Punk, well, if he really does get one last chance with WWE, my advice would be –
Make a deal like Brock Lesnar / Goldberg – Work a set amount of dates, only work in the ring on PLE and have a set amount of TV appearances. Be a special attraction, be the star that you were between 2011 & 2014 in WWE.
Do as you’re told by Vince McMahon and Triple H – Learn from your mistakes in AEW. Yes, I blame Tony Khan for not being able to control his roster, but CM Punk also has to take responsibility for being a veteran who handles disagreements with fist fights. You can’t settle disagreements in this way in 2023.
I was a huge CM Punk fan back in his run with WWE, I couldn’t wait to see him in AEW. But due to a couple of fights and injuries, we were robbed of a full two year run and got a stop / start one year run. It’s a real shame, his career deserves to end better than this.
Anyway guys, I’ll stop rambling now. Thanks for reading if you managed to get through it all. I intend on trying to do between 2 to 3 of these posts per week as well as a few personal blogs and maybe even some gaming blogs (WWE 2K23 ‘My GM’ & TEW 2020 ‘Pro-Wrestling NOAH’ saves)
Please leave feedback, if it’s constructive then I’ll always appreciate it. I’m always happy to learn and to become better. Please keep it respectful though, everyone is entitled to an opinion.
Take it easy guys,
Andy
#wwe#aew#wwe nxt#wwe raw#wwe smackdown#aew dynamite#aew rampage#aew collision#all elite wrestling#aew all in#tony khan#wwe payback#seth rollins#shinsuke nakamura#cm punk
2 notes
·
View notes
Text
Mac vs. PC: The Never-Ending Battle Between Laptop Operating Systems

For decades, the debate between Macs and PCs has raged on, dividing tech enthusiasts and casual users alike. Both Mac and PC offer unique advantages and disadvantages, making the choice highly personal and dependent on individual needs. This blog delves into the core of this ongoing battle, exploring the strengths and weaknesses of each operating system (OS) across various aspects.
Even if you haven't actively participated in the Mac vs. PC debate, you've likely encountered the stereotypes. Macs are often associated with sleek design, user-friendliness, and a premium price tag, while PCs are known for their customizability, affordability, and wider software compatibility. But is this a fair assessment? Let's break down the key areas where Macs and PCs clash.
Hitech No. 1, a premier laptop repairing institute in New Delhi with over 20 years of experience, can't directly weigh in on the OS war. However, the knowledge they impart through their laptop repairing courses equips individuals with the skills to diagnose and potentially troubleshoot basic hardware or software issues, regardless of the operating system a laptop runs on.
Now, let's delve into the eight key battlegrounds of the Mac vs. PC war:
1. Hardware:
Mac: Apple designs and manufactures its own hardware, leading to a seamless integration between software and hardware. Macs are known for their sleek design, premium build quality, and powerful performance, especially for creative tasks. However, the limited hardware upgradeability can be a drawback for users who prefer customization.
PC: PCs offer a vast array of hardware options from various manufacturers. Users can choose from different brands, processors, RAM configurations, storage options, and graphics cards to personalize their machine for specific needs. While this flexibility allows for customization and potentially lower costs, compatibility issues can sometimes arise.
2. Operating System:
Mac: macOS is known for its user-friendly interface, intuitive design, and overall stability. The streamlined OS is generally considered easier to learn and navigate, especially for beginners. Additionally, Macs are less susceptible to malware due to a smaller user base compared to Windows.
PC: Windows offers a wider range of customization options and a vast library of software programs. Users have more control over the look and feel of the operating system. However, Windows can be more prone to security vulnerabilities and may require more troubleshooting effort compared to macOS.
3. Software Compatibility:
Mac: While the Mac App Store has grown significantly, it still offers a smaller selection of software compared to Windows. Some professional applications like industry-standard editing software might not have native Mac versions, requiring users to find alternatives or utilize workarounds.
PC: PCs benefit from a vast ecosystem of software applications. From creative tools to productivity suites, there's a high chance you'll find the program you need readily available for Windows. This makes them particularly attractive for professionals who rely on specific software.
4. Gaming:
Mac: While Macs have improved their gaming capabilities in recent years, they still lag behind PCs in terms of raw power and game selection. Many popular AAA titles might not be available on macOS or may run with lower performance compared to Windows machines.
PC: PCs reign supreme in the gaming world. The vast hardware customization options allow users to build powerful machines specifically tailored for high-performance gaming. Additionally, the wider availability of games and compatibility with various gaming peripherals solidify the PC's position as the preferred platform for serious gamers.
5. Security:
Mac: Due to a smaller user base, Macs are generally considered less susceptible to malware compared to Windows. However, Macs are not entirely immune to security threats, and users should still practice safe browsing habits and install security updates.
PC: As the more popular platform, Windows is a bigger target for malware creators. However, Windows has made significant strides in security over the years, and employing antivirus software and keeping the operating system updated can significantly mitigate risks.
6. Cost:
Mac: Macs are generally more expensive than comparable PCs. Apple's premium build quality and brand recognition come at a price. However, Macs tend to hold their resale value better than PCs.
PC: PCs offer a wider range of price points. Users can customize their machine to fit their budget, with budget-friendly options readily available alongside high-end gaming rigs.
7. Design and Aesthetics:
Mac: Macs are recognized for their sleek, minimalist design and premium build quality. Apple prioritizes aesthetics, resulting in aesthetically pleasing laptops that often feel well-crafted and luxurious.
PC: PC design varies significantly depending on the manufacturer. While some premium PCs offer a sleek, modern aesthetic, the overall design philosophy for PCs is more diverse, with options catering to various preferences.
8. Upgradeability and Repair:
Mac: Macs are known for their limited upgradeability. Due to the integrated nature of hardware and software, it's often difficult or impossible to upgrade components like RAM or storage after purchase. Repairs for Macs can also be more expensive due to the use of proprietary parts and Apple's authorized repair network. While Hitech No. 1 doesn't offer laptop repair services directly, the knowledge gained through their laptop repairing course in New Delhi can equip individuals with a basic understanding of laptop hardware, potentially allowing them to identify simple issues or perform minor maintenance tasks on any laptop, regardless of the operating system.
PC: PCs generally offer greater upgradeability. Users can often swap out components like RAM, storage drives, and even graphics cards to breathe new life into an aging machine. This flexibility allows users to customize their machine over time and potentially save money compared to buying a whole new laptop. Additionally, due to the wider availability of parts and independent repair shops, PC repairs can sometimes be more affordable than Mac repairs.
Conclusion:
Ultimately, the choice between Mac and PC comes down to individual needs and preferences. Consider the factors discussed above, such as hardware flexibility, operating system ease of use, software compatibility, gaming requirements, budget, and design aesthetics.
Here's a quick recap to help you decide:
Choose Mac if:
User-friendliness and a sleek design are your top priorities.
You primarily use Apple products and value seamless integration.
You prioritize security and are less concerned about a vast software library.
Choose PC if:
You need a machine for specific software programs not readily available on Mac.
You're a serious gamer who needs powerful hardware and a wider game selection.
You prefer customization options and the ability to upgrade components over time.
Budget is a major concern, and you want to explore more affordable options.
Remember, there's no single "right" answer. Both Macs and PCs offer unique strengths and weaknesses. By understanding these differences, you can make an informed decision that best suits your requirements and preferences.
0 notes
Text
Cross-Platform Showdown: Flutter vs. Xamarin vs. React Native

In today's mobile-driven world, cross-platform development frameworks have become increasingly popular for building mobile applications that can run seamlessly across multiple platforms. Among the most prominent frameworks are Flutter, Xamarin, and React Native, each offering unique features and capabilities. In this article, we'll delve into a showdown between these cross-platform development giants—Flutter, Xamarin, and React Native—comparing their strengths, weaknesses, and suitability for various development scenarios.
Understanding Flutter:
Flutter, developed by Google, is an open-source UI toolkit for building natively compiled applications for mobile, web, and desktop from a single codebase. Let's explore its key features:
Performance and Speed:
Flutter offers exceptional performance and fast rendering speeds by compiling Dart code directly to native machine code, resulting in smooth animations and responsive UIs.
Its "hot reload" feature allows developers to make changes to the code and see the results instantly, enhancing productivity and iteration speed.
Rich UI Experience:
Flutter provides a rich set of customizable widgets and UI components, enabling developers to create beautiful, native-like interfaces across platforms.
Its "widget-based" architecture allows for highly flexible and expressive UI design, with support for animations, gestures, and custom styling.
Growing Ecosystem:
Flutter has a rapidly growing ecosystem of packages, plugins, and community support, offering developers access to a wide range of tools and resources.
Frameworks like FlutterFire provide seamless integration with Firebase services for backend functionality, while plugins extend Flutter's capabilities for tasks like navigation, state management, and data persistence.
Exploring Xamarin:
Xamarin, acquired by Microsoft, is a cross-platform framework for building native mobile apps using C# and the .NET framework. Here are its key features:
Native Performance:
Xamarin allows developers to build fully native applications for iOS, Android, and Windows using a single codebase, leveraging the performance and capabilities of each platform.
Its architecture enables direct access to native APIs and platform-specific functionality, ensuring a high level of performance and user experience.
Unified Development Environment:
Xamarin provides a unified development environment with Visual Studio and Visual Studio for Mac, allowing developers to write, debug, and test code seamlessly across platforms.
Its integration with Microsoft's ecosystem, including Azure services and .NET libraries, simplifies backend integration, authentication, and cloud-based functionality.
Large Community and Support:
Xamarin has a large and active community of developers, contributors, and enthusiasts, providing valuable resources, documentation, and support forums.
Microsoft offers extensive documentation, tutorials, and training materials for Xamarin, as well as dedicated support channels for enterprise customers.
Comparing React Native:
React Native, developed by Facebook, is a JavaScript framework for building native mobile apps using React. Let's examine its key features:
Code Reusability:
React Native allows developers to write code once and deploy it across multiple platforms, including iOS, Android, and web, using a single codebase.
Its "learn once, write anywhere" approach leverages React's declarative UI paradigm and component-based architecture for efficient code reuse and maintainability.
Fast Development Iterations:
React Native offers a fast development cycle with its "hot reload" feature, allowing developers to see changes instantly and iterate quickly during the development process.
Its large ecosystem of third-party libraries, components, and plugins further accelerates development by providing pre-built solutions for common tasks and functionalities.
Community and Ecosystem:
React Native has a vibrant community of developers, contributors, and companies, with extensive documentation, tutorials, and resources available online.
The React Native community actively maintains a vast ecosystem of open-source libraries, tools, and plugins, enabling developers to extend and customize their applications with ease.
Cross-Platform Showdown:
Performance:
Flutter generally offers better performance compared to Xamarin and React Native due to its direct compilation to native machine code.
Xamarin provides native performance by accessing platform-specific APIs directly, while React Native may face occasional performance bottlenecks due to its JavaScript bridge.
Development Experience:
Flutter's "hot reload" feature and rich set of customizable widgets provide a smooth and efficient development experience.
Xamarin's unified development environment and strong integration with Microsoft's ecosystem offer a seamless experience for .NET developers.
React Native's fast development iterations and large ecosystem of third-party libraries enhance developer productivity and flexibility.
Ecosystem and Community Support:
Flutter and React Native have rapidly growing ecosystems and vibrant communities, offering extensive documentation, tutorials, and third-party libraries.
Xamarin benefits from strong support and resources from Microsoft, with dedicated documentation, training materials, and enterprise-level support.
Conclusion:
In conclusion, the showdown between Flutter, Xamarin, and React Native highlights the strengths, weaknesses, and unique features of each framework. Flutter excels in performance and rich UI experience, Xamarin offers native performance and strong integration with the .NET ecosystem, while React Native prioritizes fast development iterations and a large ecosystem of third-party libraries. The choice between these frameworks ultimately depends on your specific project requirements, development team's expertise, and long-term goals. By carefully evaluating these factors and comparing the features of Flutter, Xamarin, and React Native, you can choose the framework that best aligns with your needs and objectives, ensuring a successful and efficient cross-platform development process.
1 note
·
View note
Text
iOS vs. Android App Development: Choosing the Right Platform

In the hustling world of mobile app development, the choice between mobile development platforms plays a pivotal role in the success of your application. Each platform comes with individual strengths and considerations and selecting the right mobile app development platform to close businesses for growth prospects. That’s when consulting an expert app development company becomes crucial.
This article will help you understand what are the fundamentals of iOS vs. Android app development and considerations before making the big decision.
What Is Android?
Android is an open-source operating system primarily designed for mobile devices such as smartphones and tablets. Developed by Google, it is a flexible and customizable platform that allows developers to create a neverending range of applications and services.
Android includes its Linux-based kernel, which serves as the core of the operating system. Its open nature allows developers to modify and customize the Android OS for different devices. The Android ecosystem has a large diversity of devices from various manufacturers running the operating system. An app development company can leverage the ecosystem to help businesses generate more profit.
Popular programming languages for Android applications like Java or Kotlin. The platform supports a variety of apps, including productivity tools, games, and communication apps. Android has gained a strong fanbase and is becoming one of the most popular mobile operating systems worldwide, supporting a majority of smartphones and tablets. Furthermore, it is much easier presently to find the best app development company that provides Android mobile app development services.
What Is iOS?
iOS is the mobile operating system developed by Apple Inc. It is specifically designed for Apple's mobile devices, including the iPhone, iPad, and iPod Touch. iOS is known for its user-friendly interface and seamless integration with other Apple products and services.
The iOS mobile app platform includes a tight-bound ecosystem, where Apple controls the hardware and software and regulates their integration. This leads to a consistent and optimized user experience over a span. The operating system is based on a Unix-like kernel and supports numerous security measures, safeguarding user data.
Apple's programming languages, such as Swift and Objective-C are primarily used for building iOS applications by the top app development company. The applications for iOS devices are distributed through the App Store and usually undergo an in-depth review process to maintain quality and security standards.
Apple regularly updates the iOS mobile development platform, introducing new features, enhancements, and security enhancements. The seamless integration between iOS devices and other Apple products, such as Mac computers and Apple Watch, is a notable trait of the ecosystem. In short, iOS is popular for its stability, performance, and emphasis on user privacy.
iOS or Android—Which Is Better?
Let’s now compare which mobile app development platform is better and provides an upper hand over the other. Top mobile app development services are versed in the nuances between these two platforms, which helps them be decisive and select the suitable platform for their business clients.
As we are aware, an online business starts with a great-looking mobile app that responds well to navigation too. To achieve that, implementing the most relevant features and incorporating device-compatible functionalities are crucial.
Let’s begin with the discussion, about which is better, Android or iOS.
User Base
Only due to its premium user experience and high functionalities, iOS boasts a dedicated and opulent user base anticipating new features and willing to be extravagant. Apple devices simplify testing and optimization but may limit potential market reach due to the uniformity.
The diversity of devices and manufacturers poses challenges for app compatibility, but it provides an expansive user base and a larger global market share, especially in emerging markets.
Development Environment
Xcode, Apple's integrated development environment (IDE) provides robust and user-friendly tools for iOS app development. The closed ecosystem supports smoother app submission processes that ensure a consistent user experience.
Android Studio, Google's official IDE, offers a flexible environment. The open nature of the Android platform grants developers more control but requires careful testing to ensure compatibility across a wide range of devices.
Design Guidelines and User Interface
Apple's Human Interface Guidelines (HIG) focuses on sleek designs, keeping them minimal. Developers benefit from a consistent design language, that transforms them into visually appealing and intuitive applications.
Google's design language for Android—Material Design prioritizes a responsive and adaptive UI. Developers are free to customize meticulously while maintaining a cohesive visual identity across different devices.
Monetization Strategies
The App Store—store for Apple’s applications is known for higher average revenue per user (ARPU). As a result, the App Store is attracting a suitable platform for premium and in-app purchase models. The stringent review process may delay app deployment, however, the top app development company can help businesses overcome the compliance challenges that may hinder the app’s deployment in the store.
Google’s Play Store openness ensures faster deployment but ad-supported and freemium models dominate the store. However, diversity in Android’s user base adds both advantages and challenges for effective monetization.
Fragmentation Challenges
Apple has a controlled ecosystem that minimizes device fragmentation and promises consistent performance across a limited range of devices. This uncomplicates app development and maintenance.
The wide range of device manufacturers and versions can lead to fragmentation challenges on Android. Thorough testing and assessment on multiple devices are crucial to deliver a seamless experience to users.
Accessibility and Innovation
Apple's close-bound ecosystem enables faster adoption of emerging technologies and features. Developers can leverage cutting-edge innovations in hardware and software to deliver top-notch user experience.
Android's open nature encourages innovation, allowing developers to experiment and recreate the latest technologies. However, the adoption of new features may be device-related constraints and may impact the overall user experience.
Conclusion
Finally, the selection between iOS and Android app development considers factors like specific goals, target audience, financial constraints, design preferences, development environments, monetization strategies, and resources of the developer and businesses. While iOS boasts of a streamlined and wealth-enriched user base, Android claims a more extensive global reach.
Striking the right balance ensures that your app not only thrives on its chosen platform but also delivers a seamless experience to users. The perfect balance fosters the long-term success of the application in the competitive arena of mobile applications and unlocks prospects.
0 notes
Text
Tie Rod Steering VS RX7 Drift Trike! #shorts #grindhardplumbingco
He said I know how to do it you take the real world drive smaller car you leave the transmission and the drive shaft in the rear wheels and you pull the whole cabin off and there's a reason to do it if it's like destroyed or the electronics are gone and you fix the motor it's not hard it's only a few seals and unless it's ruined and that's a problem but a lot of them are okay it's just the cab is ruined and a lot of the stuff needs to be repaired and replaced it's not worth it and it's from weather and he said you then use the front wheel drive the rear wheel drive just like you see here and you put the motorcycle seat over it you have to cut out all the frame around it and the floorboards and everything and you have to run some main framing members and up to the steering mechanism and you can get those from the frame and he's sorry you're saying about the angle so he did it and he said wow this is very strong and you start doing it on the whole thing they need to start using saddles he said they kind of use those it says yeah they're saddles and they're over complicated there's no reason to make all that stupid s*** and yes saying your coordinate everything is just busy work for the robot computer that's what it was so he put together that and he said you use a solid rod and see the and use a springer with the car shock so he did that no but we're going to ask for a trike and you can make them out of any of these cars and you can tow a lot more
Thor Freya
I've actually done this before and it was kind of crude but really this is the way to do it is with the Springer or two of the automobile shocks up front he says you want to do the two Auto shocks to make sure that it rides more sturdily and it's true too and I really get this idea you're going to you're going to take this thing although he says there's no way to attach the shocks except for a Springer and for the most part he's right but I'd use too you going to take this thing and you're going to use the rear end in the drive shaft and the tranny and the motor the way it is and hell you can use up to like a 350 and you set it up and you elongate the handlebars put a big gas tank in there you can buy Boss hoss gas tanks and there you have it a massive trike with reverse people going to make these and you can make a company out of this he wants to make it the rat company and that's what we're called anyways so we'll have desert rats and snow rats and all the same bike I mean that's intense we're going to go ahead and do this
Bob marsh
What a dumb idea everybody's going to start doing this and all those cars will get used up and people will demand more but these bikes are going to work and some shops are high tech and they'll make a ton of money and there are people need transportation and all the parts are right there
Mac Daddy
There's got to be about 4 or 500 trillion now it's like 5,000 trillion vehicles that you could use this technique for for the trike and or the motorcycle the trike is the transmission and the rear drive you don't have to touch anything
Olympus
1 note
·
View note
Text
Network Connectivity
Network connectivity has become integral to our lives in today’s digital age. A reliable and efficient network is crucial, from staying connected with loved ones to conducting business operations. In this blog post, we will explore the significance of network connectivity and how it has shaped our world.
Over the years, network connectivity has evolved significantly. Gone are the days of dial-up connections and limited bandwidth. Today, we have access to high-speed internet connections, enabling us to instantly connect with people around the globe. This advancement has revolutionized communication, work, learning, and entertainment.
Network connectivity is the ability of devices or systems to connect and communicate with each other. It allows data to flow seamlessly, enabling us to access information, engage in online activities, and collaborate across vast distances. Whether through wired connections like Ethernet or wireless technologies such as Wi-Fi and cellular networks, network connectivity keeps us interconnected like never before.
Highlights: Network Connectivity
Network and Security Components
To understand network connectivity, we will break networking down into layers. Then, we can fit the different networking and security components that make up a network into each layer. This is the starting point for understanding how networks work and carrying out the advanced stages of troubleshooting.
Networking does not just magically happen; we need to follow protocols and rules so that two endpoints can communicate and share information. These rules and protocols don’t just exist on the endpoint, such as your laptop; they also need to exist on the network and security components in the path between the two endpoints.
TCP/IP Suite and OSI Model
We have networking models to help you understand what rules and protocols we need on all components, such as the TCP/IP Suite and the OSI model. These networking models are like a blueprint for building a house. They allow you to follow specific patterns and have certain types of people, which are protocols in networking.
For example, to find the MAC address, when you know the IP address of the destination, we use Address Resolution Protocol (ARP). So, we have rules and standards that we need to follow. By learning these rules, you can install, configure, and troubleshoot the main networking components of routers, switches, and security devices.
Related: Useful links to pre-information
Network Security Components
IP Forwarding
Cisco Secure Firewall
Distributed Firewalls
Virtual Firewalls
IPv6 Attacks
Layer 3 Data Center
SD WAN SASE
Back to basics: What is Network Connectivity?
Types of Network Connectivity
1. Wired Connectivity: Wired connections provide reliable and high-speed data transmission. Ethernet cables, fiber optics, and powerline adapters are typical examples of wired network connectivity. They offer stability and security, making them ideal for tasks requiring consistent and fast data transfer.
2. Wireless Connectivity: Wireless network connectivity has revolutionized how we connect. Wi-Fi networks have become ubiquitous, allowing us to access the internet wirelessly within a specific range. Additionally, cellular networks enable us to stay connected on the go, providing internet access even in remote areas.
Despite its numerous benefits, network connectivity can face challenges. Signal interference, network congestion, and security threats can hinder smooth connectivity. However, advancements in technology have paved the way for solutions. Mesh networks, signal boosters, and encryption protocols are tools and techniques to overcome these challenges and ensure reliable connectivity.
Network Connectivity
Network Connectivity Components
Main Connectivity Types: Wired vs Wireless
Wired connections provide reliable and high-speed data transmission.
Wireless connections utilize radio waves to transmit data between devices without needing physical cables.
Wireless networks also eliminate the need for physical infrastructure
Wired networks are less susceptible to interference and congestion, resulting in faster and more stable data transfer.
Section 1: Understanding Wired Connections
Wired connections have a long-standing history and are widely used in various settings. They involve physical cables that connect devices to a network. Ethernet cables, for instance, are commonly used to establish wired connections. These cables transmit data through electrical signals, ensuring reliable and secure connections. Wired connections are often preferred when stability and speed are crucial, such as in offices, data centers, and gaming setups.
Section 2: Pros and Cons of Wired Connections
While wired connections offer several advantages, they also come with their own set of limitations. One notable advantage is the consistent and reliable speed that wired connections provide. They are less susceptible to interference and congestion, resulting in faster and more stable data transfer. However, the downside of wired connections lies in their lack of mobility. Users are tethered to the physical connection point, limiting their freedom to move while remaining connected.
Section 3: Embracing Wireless Technology
On the other hand, wireless connections have revolutionized how we connect to networks. They utilize radio waves to transmit data between devices without needing physical cables. Wi-Fi networks have become incredibly popular, enabling users to connect multiple devices simultaneously. Wireless connections offer the convenience of mobility, allowing users to move freely within the coverage area while staying connected.
Section 4: Pros and Cons of Wireless Connections
Wireless connections have undoubtedly brought us unparalleled convenience, but they have some drawbacks. One of the main advantages is their flexibility, allowing users to connect devices without the hassle of cables. Wireless networks also eliminate the need for physical infrastructure, making them more cost-effective and easier to set up. However, wireless connections can be affected by interference from other devices, walls, and distance limitations, leading to potential signal drops and slower speeds.
Lab Guide on Networking Scanning
PowerShell and TNC
There are multiple ways to scan a network to determine host and open ports. PowerShell is used with variables and can perform advanced scripting. Below, I am using TNC to scan my own Ubuntu VM and the WAN gateway.
Note:
The command tnc stands for test network connection. This will display a summary of the request, and the output will show a timeout. The PingSucceeded value will equal False. This output can indicate port filtering or that the target machine is powered off. The different status can vary between operating systems even when the result appears to be the same.
You can scan for the presence of multiple systems on the network with the following 1..2 | % {tnc 192.168.0.$_}
Analysis:
This command will attempt to scan 2 IP addresses in the range 192.168.0.1 and 192.168.0.2. The number range 1..1 can be extended, for example, 1..200, although it will take longer to complete.
RDP is a prevalent protocol on machines within a corporate network for administrative purposes. This will display a summary of the request and will show a successful connection. The output will show TcpTestSucceeded equals False. This indicates the system is not running and active, and a service could be running on port 3389, which is typically used for administration and remote desktop access.
In the following example, we have a PowerShell code to create a variable called $ports by typing $ports = 22,53,80,445,3389 and pressing the Return key. This variable will store multiple standard ports found on the target system.
Then scan the machine using the new variable $ports with the command $ports | ForEach-Object {$port = $_; if (tnc 192.168.0.2 -Port $port ) {“$port is open” } else {“$port is closed”} }.
Analysis:
This code will scan the IP address 172.31.24.20 and test each port number within the previously created $ports variable. For each port found, an open port message is displayed.
For any port not found, the message port is closed is shown. Several ports should be opened on the machine according to the output.
Network Connectivity: Technical Details
Source and Destination
Networking, or computer networking, transports and exchanges data between nodes over a shared medium in an information system. It’s about moving information from your application across and within your network. Generally speaking, the essence of network connectivity exists as a source and a destination where we can communicate. T
There are different modes of communication, such as unicast, broadcast, and multicast. But for now, consider a network and the infrastructure used within a network to support communication between a single source and destination.
The source can be the application you use on your computer, such as your web browsers that use HTTP protocol. So, there are rules that your web browser software needs to follow, and the HTTP protocol specifies these. The destination could be elsewhere, such as an application hosted in the cloud or another network from your on-premise Local Area Network (LAN). In this case, we are moving from an on-premise network to a cloud network.Diagram: What is network connectivity? The source is esds.
Lab Guide on IGMPv1
IGMPv1 is a network-layer protocol that enables hosts to join or leave multicast groups on an Internet Protocol (IP) network. It is primarily designed to manage multicast group membership within a local area network (LAN). Using IGMPv1, hosts can receive information from a single sender and distribute it to multiple receivers, optimizing network traffic and improving efficiency.
IGMP (Internet Group Management Protocol) version 1 is the first version hosts can use to announce to a router that they want to receive multicast traffic from a specific group. It’s a simple protocol that uses only two messages:
Membership report
Membership query
Below, we have one router and two hosts. We will enable multicast routing and IGMP on the router’s Gigabit 0/1 interface. All modern operating systems support IGMP,
First, we enabled multicast routing globally; this is required for the router to process IGMP traffic.
We enabled PIM on the interface. PIM is used for multicast routing between routers and is also required for the router to process IGMP traffic.
Diagram: Debug IP IGMP
Network Connectivity with Edges of Control
In the world of computer networking and network connectivity, there are different types of edges of control. In this case, if you are sitting in your home network. The edge of control is our home router provided by a service provider in your area, along with a firewall device positioned at each of these perimeters, marking the points between internal and external networks.
In your home network, this parameter is static. However, the perimeter is more dissolved, especially in more extensive networks. You would need multiple firewalls and firewall types positioned in the local area network, creating a defense-in-depth approach to security.Diagram: Sample network for network connectivity.
One way to create the boundary between the external and internal networks is with a firewall. The example below shows a Cisco ASA firewall configured with zones. The zones create the border. Below, Gig0/0 is the internal zone with a security level of 0. By default, a higher-level area, such as the outside zone, with a security level of 100, cannot communicate with zones of lower numbering.
ASA security zones are virtual boundaries created within your network infrastructure to control and monitor traffic flow. These zones provide an added layer of defense, segregating different network segments based on their trust levels. Administrators can apply specific security policies and access controls by classifying traffic into zones, reducing the risk of unauthorized access or malicious activities.Diagram: Cisco ASA Configuration
Lab guide on DMVPN. Network connectivity over the WAN.
The lab guide below has a Dynamic Multipoint VPN topology based on a GRE tunnel. R12 is the hub, and R11 is the spoke. Usually, you would have additional spokes located across the WAN. DMVPN provides layer 3 network connectivity over the Wide Area Network; DMPVPN provides connectivity based on a Layer 3 overlay with GRE.
The underlay network connectivity is the SP network, and the overlay network connectivity is based on GRE. We can see the tunnel configuration with icon 1 in the diagram below. We have a tunnel source and destination with the tunnel protocol of point-to-point GRE.
Note:
DMVPN operates with different DMVPN phases. Point-to-point GRE on the spokes is DMVPN phase 1. Multipoint GRE on the spokes would illustrate DMVPN Phase 3. Icon 2 displays the routing protocol running over the GRE ( overlay tunnel ), and icon 3 shows the traceroute capture. We only see one hop as the TTL is encapsulated in the GRE tunnel.Diagram: DMVPN Configuration
Network Connectivity with Network Models
So, as I said, computer networks enable connected hosts—computers—to share and access resources. So when you think of a network, think of an area, and this area exists for sharing. The first purpose of network connectivity was to share printers, and it has not been expanded to many other devices to share, but in reality, the use case of sharing is still its primary use case.
You need to know how all the connections happen and all the hardware and software that enables that exchange of resources. We do this using a networking model. So, we can use network models to conceptualize the many parts of a network, relying primarily on the Open Systems Interconnection (OSI) seven-layer model to help you understand networking.
Remember that we don’t implement the OSI; we implement the TCP/IP suite. However, the OSI is a great place to start learning, as everything is divided into individual layers. You can place the network and security components at each layer to help you understand how networks work. Let us start with the OSI model before we move to the TCP/IP suite.
Why use the OSI Model?
The open systems interconnection (OSI) model is based on splitting a communication system into seven abstract layers, each stacked upon the last. What can you use the OSI model for? Understanding OSI enables a tech to determine quickly at what layer a problem can occur. Second, the OSI model provides a common language techs use to describe specific network functions.
Understanding the functions of each OSI layer is very important when troubleshooting network components and network communication. Once you understand these functions and the troubleshooting tools available to you at the various layers of the model, troubleshooting network-related problems and understanding will be much easier.
Highlighting the OSI layers
Layer 7 Application
The application layer provides the user interface. We have software applications like web browsers and email clients, to name a few, that rely on the application layer to initiate communications. Application layer protocols include HTTP and SMTP (Simple Mail Transfer Protocol is one of the protocols enabling email communications).
Layer 6 Presentation
The presentation layer determines how data is represented to the user. This layer is primarily responsible for preparing data so the application layer can use it; in other words, layer 6 makes the data presentable for applications to consume. Encryption and compression work at this layer.
Layer 5 Session
This layer is responsible for opening and closing communication between the two devices. The time between open and closed communication is known as the session.
Layer 4 Transport
Layer 4, the transport layer, is responsible for end-to-end communication between the two devices. These activities include taking data from the session layer and breaking it into segments before sending it to layer 3. Layer 4 is also responsible for flow control and error control.
Layer 3 Network
The network layer is responsible for facilitating data transfer between two different networks. The network layer is unnecessary if the two devices communicating are on the same network.
Layer 2 Data Link
The data link layer is very similar to the network layer, except the data link layer facilitates data transfer between two devices on the same network. The data link layer takes packets from the network layer and breaks them into smaller pieces called frames.
Layer 1 Physical
The physical layer defines physical properties for connections and communication: repeaters and hubs operate here. Wireless solutions are defined at the physical layer.
Lab on the data link layer and MAC addresses
The following lab guide will explore Media Access Control (MAC) addresses. MAC address works at the data link layer of the OSI model. This address may also be called the physical address since it’s the identifier assigned to a Network Interface Card (NIC).
While this is typically a physical card or controller that you might plug the ethernet or fiber into, MACs are also used to identify a pseudo-physical address for logical interfaces. This example shows the MAC changes seen in virtual machines or docker containers.
Note:
We have a Docker container running a web service and mapped port 80 on the container to 8000 on the Docker host. The Docker host is a Ubuntu VM. Also, notice the assigned MAC addresses; we will change these immediately. I’m also running a TCPDump. The TCPDump will start a packet capture on the Docker0.
Analysis:
For this challenge, we will focus on the virtual network between your local endpoint and a web application running locally inside a docker container. The docker0 interface is your endpoint’s interface for communication with docker containers. The “veth…” interfaces are the virtual interfaces for web applications.
Even though the MAC address is supposed to be a statically assigned identifier for the specific NIC, they are straightforward to change. We changed the MAC address in the following screenshots and brought down the Docker0.
Note:
Typically, attackers will spoof a MAC to mimic a desired type of device or use randomization software to mask their endpoint.
Now that you have seen how MAC addresses work, we can look at the ARP process.
Note:
When endpoints communicate across networks, they use logical IP addresses to track where the requests come from and the intended destination. Once a packet arrives internal to an environment, networking devices must convert that IP address to the more specific “physical” location the packets are destined for. That “physical” location is the MAC address you analyzed in the last challenge. The Address Resolution Protocol (ARP) is the protocol that makes that translation.
Analysis:
Let’s take this analysis step-by-step. When you send the curl request or any traffic, the first thing that must occur is to determine the intended destination. So we are giving the IP address as this, but we don’t know the Layer 2 MAC address. ARP is the process of finding this.
Where did the initial ARP request come from?
It looks like the first packet has a destination MAC of “ff:ff:ff:ff:ff:ff.” Since your endpoint doesn’t know the destination MAC address, the first ARP packet is broadcast. Although this works, this is a bit of a security concern.
A broadcast packet will be sent to every host within the local network. Unfortunately, the ARP protocol was not developed with security in mind, so in most configurations, the first host to respond to the ARP request will be the “winner.” This makes it very simple if an attacker controls a host within an environment to spoof their own MAC, respond faster, and effectively perform a Man-In-The-Middle (MITM) attack. Notice we have “Request how has ” above.
The requesting IP address must be found in the payload of the packet. This is an important distinction since most packets are returned to the requesting IP address found in the IPv4 header. This allows adversaries to use attacks such as ARP spoofing and MAC flooding since the original requester doesn’t have to be the intended destination. Notice we have a “Reply” at the end of the ARP process.
Understanding ARP:
ARP bridges the Network Layer (Layer 3) and the OSI model’s Data Link Layer (Layer 2). Its primary function is to map an IP address to a corresponding MAC address, allowing devices to exchange data efficiently.
The ARP Process:
1. ARP Request:
When a device wants to communicate with another on the same network, it sends an ARP request broadcast packet. This packet contains the target device’s IP address and the requesting device’s MAC address.
2. ARP Reply:
Upon receiving the ARP request, the device with the matching IP address sends an ARP reply containing its MAC address. This reply is unicast to the requesting device.
3. ARP Cache:
Devices store the ARP mappings in an ARP cache to optimize future communications. This cache contains IP-to-MAC address mappings, eliminating the need for ARP requests for frequently accessed devices.
4. Gratuitous ARP:
In specific scenarios, a device may send a Gratuitous ARP packet to announce its presence or update its ARP cache. This packet contains the device’s IP and MAC address, allowing other devices to update their ARP caches accordingly.
Lab Guide on Host Enumeration
Linux Host Enumeration
In a Linux environment, it is common practice to identify the host network details. A standalone isolated machine is scarce these days, and most systems will be interconnected to other systems somehow. Run the following command to display IP information, saving the output to a text file instead of the popular methods of displaying text on the screen.
Note:
1. Below, you can see there is usually a lot of helpful information displayed with network information. In the screenshot, note the network device ens33, and the MAC address is also listed.
2. The hping3 is a command-line tool that can craft and send customized network packets. It offers various options and functionalities, making it an invaluable asset for various tasks such as network discovery, port scanning, and firewall testing.
3. One of the critical strengths of hping3 lies in its advanced features. From TCP/IP stack fingerprinting to traceroute mode, hping3 goes beyond basic packet crafting and provides robust network analysis and troubleshooting techniques.
Analysis:
The w command will show who, what, and where from; in the above screenshot, a user is connecting from a remote location, and this highlights how interconnected we are today; connection could be anywhere in the world. Other helpful information here shows the user has a terminal open bash and is running the w command.
Use the hping command to ping your machine seven times using. sudo hping3 127.0.0.1 -c 57.
The sudo is needed as elevated privileges are required to run hping3. The IP address 127.0.0.1 is the loopback address, meaning this is your machine. We work in a secure lab environment and cannot ping systems online.
In the screenshot, errors will be displayed if there are any connection issues on the network. Generally, ping helps identify interconnected systems on the network. Hping is a much more advanced tool with many features beyond this challenge; It can also do advanced techniques for testing firewall port scanning and help penetration testers look for weaknesses. A potent tool!
Highlighting the TCP/IP Suite: Protocols
TCP/IP is a protocol suite—meaning multiple protocols exist to provide network connectivity. Each protocol in the suite has a specific purpose and function, and protocols work at different layers. TCP/IP is a suite of protocols, the most popular of which are Transmission Control Protocol (TCP), User Data Protocol (UDP), Internet Protocol (IP), and Address Resolution Protocol (ARP).
IP performs logical addressing so your computer can be found and reached across different networks. ARP converts these logical addresses to a physical MAC address to be transmitted on the wire. We can use the ICMP protocol for troubleshooting and diagnostics, which is the status- and error-reporting protocol.
The IP is the Internet’s address system and delivers packets of information from a source device to a target device. IP is the primary way network connections are made, and it establishes the basis of the Internet. IP does not handle packet ordering or error checking. Such functionality requires another protocol, often the TCP.
For example, when an email is sent over TCP, a connection is established, and a 3-way handshake is made. First, the source sends an SYN “initial request” packet to the target server to start the dialogue. Then, the target server sends a SYN-ACK packet to agree to the process. Lastly, the source sends an ACK packet to the target to confirm the process, after which the message contents can be sent.
TCP/IP: Networking Model: 4-layer model vs. 7-layer OSI
The TCP/IP model is a four-layer model similar in concept to the seven-layer OSI Reference Model. To simplify life, the four layers of the TCP/IP model map to the seven layers of the OSI version. The TCP/IP model combines multiple layers of the OSI model, so when starting with networking. It’s good to start with the OSI, as none of the layers are combined.
Moving through Layers: Enabling Network Connectivity
Each OSI model layer is responsible for communicating with the layers directly above and below, receiving data from or passing it to its neighboring layers. For example, the presentation layer will receive information from the application layer, format it appropriately, which could be encryption, as we mentioned, or compression, and then pass it to the session layer. The presentation layer will never deal directly with the transport, network, data link, or physical layers. The same idea is valid for all layers regarding their communication with other layers.
OSI Layer Example: Computers communicate with a server.
Let’s look at the layers from the point of view of two computers sending data to each other. The data is called different things at each layer. This is due to the encapsulation process, but we will call it data for now.
So we have Host A and Host B that want to send files to each other and, therefore, will exchange data on the network. Or host B has a local web server, and host A in their browser types in the IP address of host B. So, for network connectivity, we need a source and a destination.
So, Host A is the sending computer, the source, and Host B is the receiving computer, the destination. The data exchange starts with Host A sending a request to Host B in the application layer. So we have Host A, that is initiating the request.
At the receiving end, the destination, on host B, the data moves back up through the layers to the application layer, which passes the data to the appropriate application or service on the system. Port numbers will identify the proper service.
Starting to move through the layers
Network connectivity starts at the application layer of the OSI model, which will be on the sending system, which in our case is Host A, and works its way down through the layers to the physical layer. The information then passes the communication medium, physical cablings such as Copper or Fiber, or wireless, until it receives the far-end system, which operates back up the layers, starting at the physical layer until the application layer.
Action at one layer undone at another layer
When you think of two devices communicating, such as two computers, it is crucial to understand that whatever action is done at one layer of a sending computer is undone at the same layer on the receiving computer. For example, if the presentation layer compresses or encrypts traffic the information on the sending computer, the data is uncompressed or decrypted on the receiving computer.
Network Connectivity and Network Security
So, we have just looked at generic connectivity. But there will be two main functions carried out by these networking and security devices. First, there is the network connectivity side of things.
So, we will have network devices that will need to forward your traffic so it can reach its destination. Traffic is delivered based on IP. Keep in mind there is not any guarantee with IP. Enabling reliable network connectivity is handled further up the stack. The primary version of IP used on the Internet today is Internet Protocol Version 4 (IPv4).
Due to size constraints with the total number of possible addresses in IPv4, a newer protocol was developed. The latest protocol is called IPv6. It makes many more addresses available and is increasing in adoption.
Network Security and TCPdump
Secondly, we will need to have network security devices. These devices allow traffic to pass through their interfaces if they deem it safe, and policy permits the traffic to pass through that zone in the network. The threat landscape is dynamic, and bad actors have many tools to disguise their intentions. Therefore, we have many different types of network security devices to consider.
Tcpdump is a powerful command-line packet analyzer that allows users to capture and examine network traffic in real time. It captures packets from a network interface and displays their content, offering a detailed glimpse into the intricacies of data transmission.
Getting Started with tcpdump
To utilize TCPdump effectively, it is crucial to understand its primary usage and command syntax. By employing a combination of command-line options, filters, and expressions, users can tailor their packet-capturing experience to suit their specific needs. We will explore various TCPdump commands and parameters, including filtering by source or destination IP, port numbers, or protocol types.
Analyzing Captured Packets
Once network packets are captured using TCPdump, the next step is to analyze them effectively. This section will explore techniques for examining packet headers payload data, and extracting relevant information. We will also explore how to interpret and decode different protocols, such as TCP, UDP, ICMP, and more, to understand network traffic behavior better.
Lab Guide on tcpdump
Capturing Traffic with tcpdump
Note:
Remember that starting tcpdump requires elevated permissions and initiates a continuous traffic capture by default, resulting in an ongoing display of network packets scrolling across your screen. To save the output of tcpdump to a file, use the following command:
sudo tcpdump -vw test.pcap
Tip: Learn tcpdump arguments
sudo Run tcpdump with elevated permissions
-v User verbose output
-w write output to the file
Analysis:
Running TCPdump is an invaluable tool for network analysis and troubleshooting. It lets you capture and view the live traffic flowing through your network interfaces. This real-time insight can be crucial for identifying issues, understanding network behavior, and detecting security threats.
Next, to capture traffic from a specific IP address, at the terminal prompt, enter:
sudo tcpdump ip host 192.168.18.131
Tip: Learn tcpdump arguments
ip the protocol to capture
host <ip address> limit the capture to a single host’s IP address
To capture a set number of packets, type the following command:
sudo tcpdump -c20
Analysis:
Filtering tcpdump on a specific IP address streamlines the analysis by focusing only on the traffic involving that address. This targeted approach can reveal patterns, potential security threats, or performance issues related to that host.
Limiting the packet count in a tcpdump capture, such as 20 packets, creates a more focused and manageable dataset for analysis. This can be particularly useful in isolating incidents or behaviors without being overwhelmed by continuous information.
Tcpdump finds practical applications in various scenarios. Whether troubleshooting network connectivity issues, detecting network intrusions, or performing forensic analysis, tcpdump is an indispensable tool.
Conclusion:
In conclusion, tcpdump is an invaluable tool for network traffic analysis. Its versatility and powerful filtering capabilities empower network administrators and analysts to gain deep insights into their networks. By mastering tcpdump, you can troubleshoot issues, detect anomalies, and optimize network performance. So equip yourself with tcpdump and embark on a journey of network exploration!
Components for network connectivity
In general, we have routers forwarding the traffic based on IP, and they usually work with switches that help connect all the devices. Switches work with MAC addresses and not IP addresses. Then we have the security devices such as firewalls that help with the security side of things. Generally, a firewall device will allow all traffic to leave the network, but only traffic you permit can enter the network.
Starting with the Layer 3 Router
Routers, the magic boxes that act as the interconnection points, have all the built-in smarts to inspect incoming packets and forward them toward their eventual LAN destination. Routers are, for the most part, automatic. A router is any hardware or software that forwards packets based on their destination IP address.
Routers work at the OSI model’s Network layer (Layer 3). Classically, routers are dedicated boxes with at least two connections, although many contain many more connections and offer various network connectivity options.
The router inspects each packet’s destination IP address and then sends the IP packet out to the correct port. To perform this inspection, every router has a routing table that tells the router exactly where to send the packets. This table is the key to understanding and controlling forwarding packets to their proper destination.
Starting with Switches
Then we have switches, which can control and only send frames to the proper destination and reduce the number of devices receiving the frame, reducing the chance of collisions. So when we have switches, we have a star topology but consider the links between the end host and the switch port to be point-to-point.
This allows full duplex communication that effectively disables the CSMA/CD process between the switch port and the attached device. Now, the ability to transmit and receive simultaneously only occurs between the switch port and the end station. So, consider full-duplex to be a 10x speed improvement over half-duplex. The switch port also acts as a boundary for collisions.
Building a small network: Network and Security Components
Information on Hub
With the information you learned from the OSI, let’s look at some networking components in more detail. Networking started with hubs. A hub is an older network device you hopefully do not encounter on your networks because more effective and secure switches have replaced them. A network hub has three pitfalls:
No filtering
When a system was to send data to another system, the hub would receive the data and then send the data to all other ports on the hub. A switch operating at Layer 2 will understand MAC addresses to make better forwarding decisions.
Collisions
Because any data was sent to all other ports, and any system could send its data at any time, this resulted in many collisions on the network. A collision occurs when two data pieces collide, must be retransmitted, and will degrade application performance.
Security For Hubs
Because the data was sent to all ports on the hub, all systems receive all data. Systems look at the destination address in the frame to decide whether to process or discard the data.
Packet Sniffer
But if someone were running a packet sniffer such as Wireshark or tcpdump on a system that used a hub, they would receive all packets and be able to read them. Sniffers examine streams of data packets that flow between computers on a network, between networked computers, and the more extensive Internet. This created a huge security concern.
The solution to the hub problem was to replace network hubs with switches with better filtering capabilities and the capability to carve a switch into multiple switches using VLANs. This improves both security and performance.
Lab Guide Networking Scanning with Python
Python and NMAP
I am scanning my local netowrk in this lab guide, looking for targets and potential weaknesses. Knowing my shortcomings will help strengthen the overall security posture. I am scanning and attempting to gain access to services with Python.
Network scanning is identifying and mapping the devices and resources within a network. It helps in identifying potential vulnerabilities, misconfigurations, and security loopholes. Python, a versatile scripting language, provides several modules and libraries for network scanning tasks.
Note:
Python offers various libraries and modules that can be used with Nmap for network scanning. One such library is “python-nmap,” which provides a Pythonic way to interact with Nmap. By leveraging this library, we can easily automate scanning tasks, customize scan parameters, and retrieve results for further analysis.
The code will import the nmap library used to provide nmap functionality. Then the most basic default scan will be performed against the Target 1 virtual machine.
Steps:
Using the nano editor, create a new text file called scannetwork.py by typing nano scannetwork.py. This is where the Python script will be created.
With nano open, enter the following Python code to perform a basic default port scan using nmap with Python. Add your IP address for the Target 1 virtual machine to the script.
import nmap
import subprocess
nm = nmap.PortScanner()
print(‘Perform default port scan’)
nm.scan(‘add.ip.address.here’)
print(nm.scaninfo())
Note: The code will import the nmap library used to provide nmap functionality, then the most basic default scan will be performed against the Target 1 virtual machine.
Analysis:
Scan results may vary. The following output shows many numbers, signifying port numbers, with the scan completing quickly. With this type of full scan without arguments and the speed at which Python returns, the results will likely produce errors.
Remember that you need to have NMAP installed first.
Conclusion:
Python network scanning has numerous real-world applications. From security audits to vulnerability assessments, Python-based network scanning tools can greatly assist in identifying potential risks and strengthening overall network security. Additionally, network administrators can automate routine scanning tasks, saving time and effort.
Python and tools like Nmap empower network security professionals to conduct comprehensive and efficient network scans. By automating the scanning process and leveraging Python’s flexibility, developers can create robust solutions tailored to their specific needs. Whether for security auditing or network exploration, Python network scanning opens up a world of possibilities.
Network connectivity: Start with switches
At layer 2, we can have switches that reduce collisions, optimize traffic, and are better from a security point of view. LAN Switch Switches are one of the most common devices used on networks today. All other devices connect to the switch to gain access to the network. For example, you will connect workstations, servers, printers, and routers to a switch so that each device can send and receive data to and from other devices. The switch acts as the central network connectivity point for all devices on the network.
Layer 2 Switch: How switches work
The switch tracks every device’s MAC address (the physical address burned into the network card) and then associates that device’s MAC address with the port on the switch to which the device is connected. The switch stores this information in a MAC address table in memory on the switch. The switch then acts as a filtering device by sending data only to the port that the data is destined for.
Collision Domains and Broadcast Domains
Collision Domain: Hub – Single Collision Domain
In a collision domain, data transmission collisions can occur. For example, suppose you are using a hub to connect 10 systems to a network. Because traffic is sent to all ports on the hub, the data could collide on the network if several systems send data simultaneously. For this reason, all network ports on a hub (and any devices connected to those ports) are considered parts of a single collision domain. This also means that when you cascade a hub of another, all hubs are part of the same collision domain. Do you connect 100 hubs, and even though they are different physical devices, it is still one collision domain?
Switches: Break down Collision Domains
If you were using a switch to connect the ten systems, each port on the switch would create its network segment. When data is sent by a system connected to the switch, the switch sends the data only to the port on which the destination system resides. For this reason, if another system were to send data simultaneously, the data would not collide. As a result, each port on the switch creates a separate collision domain.
Controlling Broadcast Domain
A broadcast domain is a group of systems that can receive one another’s broadcast messages. When using a hub to connect five systems in a network environment, if one system sends a broadcast message, the message is received by all other systems connected to the hub. For this reason, all ports on the hub create a single broadcast domain. Likewise, if all five systems were connected to a switch and one sent a broadcast message, all other systems on the network would receive the broadcast message.
Therefore, all ports are part of the same broadcast domain when using a switch. If you wanted to control which systems received broadcast messages, you would have to use a router that does not forward broadcast messages to other networks. You could also use virtual LANs (VLANs) on a switch, with each VLAN being a different broadcast domain.
Network Connectivity: Starting with Routers
A switch connects all systems in a LAN setup, but what if you want to send data from your network to another network or across the Internet? That is the job of a router. Routers work at Layer 3 of the OSI model. A router sends or routes data from one network to another until the data reaches its final destination. Note that although switches look at the MAC address to decide where to forward a frame, routers use the IP address to determine what network to send the data to.
Network Connectivity with Network Routing
Network routing is selecting a path across one or more networks. Routing principles can apply to any network, from telephone to public transportation. In packet-switching networks, such as the Internet, routing selects the paths for Internet Protocol (IP) packets to travel from origin to destination. These Internet routing decisions are made by specialized network hardware called routers.
Routing Tables and Layer 3 Connectivity
Routers refer to internal routing tables to decide how to route packets along network paths. A routing table records the paths packets should take to reach every destination the router is responsible for. The router has a routing table listing all the networks it can reach. Routing protocols populate routing tables. Routing protocols can be dynamic or static.
Routing tables can either be static or dynamic. Static routing tables do not change. A network administrator manually sets up static routing tables. This sets in stone the routes data packets take across the network unless the administrator manually updates the tables. Dynamic routing tables update automatically. Diagram: Layer 3 connectivity. Source is geeksforgeeks
Dynamic routers use various routing protocols (see below) to determine the shortest and fastest paths. They also make this determination based on how long it takes packets to reach their destination. Dynamic routing requires more computing power, so that smaller networks may rely on static routing. However, dynamic routing is much more efficient for medium-sized and large networks.
Understanding NAT Static
NAT static, also known as static NAT, maps an internal private IP address to a specific public IP address. Unlike dynamic NAT, which dynamically assigns public IP addresses from a pool, NAT static uses a fixed mapping configuration. This means that the private IP address is consistently associated with the same public IP address, ensuring reliable.
One of the critical advantages of NAT static is enhanced security. A one-to-one mapping between private and public IP addresses creates a clear separation between internal and external networks. This adds a layer of protection against potential cyber threats. Moreover, NAT static enables organizations to host services or applications on internal servers by exposing them to the public using a dedicated public IP address.
Implementation of NAT Static
Implementing NAT static requires configuration settings on a network device, typically a router or firewall. The process involves specifying the mapped internal IP address and the corresponding public IP address. Port forwarding rules can also be set up to direct incoming traffic to specific services or applications within the internal network.
NAT static finds valuable applications in various scenarios. For instance, it is widely used in organizations that require external access to internal resources, such as web servers, FTP servers, or VPN gateways. By utilizing NAT static, these resources can be accessed securely from the internet while maintaining the privacy of the internal network.
Lab Guide on Static NAT in Cisco IOS
Below in the following lab guide, you see 3 routers called Host, NAT, and Web1. There are two segments to this network—an internal and an external segment. The NAT device creates the network boundary. In our case, this is a Cisco IOS router. In the production network, this would be a Firewall. Imagine our host is on our LAN, and the web server is somewhere on the Internet. Our NAT router in the middle is our connection to the Internet.
Note:
1. Disabling “routing” on a router that turns it into a typical host that requires a default gateway is possible. This is very convenient because it will save you the hassle of connecting real computers/laptops to your lab.
2. Use no ip routing to disable the routing capabilities.
3. I use debug ip packet to see the IP packets that I receive. Don’t do this on a production network, or you’ll be overburdened with debug messages!
Analysis:
You can use the show ip nat translations command to verify our configuration. The web server’s packet from the host has a source IP address of 192.168.23.2.
And when it responds to the destination, the IP address is 192.168.23.2. Now we know that static NAT is working.
Conclusion:
In conclusion, NAT static offers a reliable and secure method of connecting internal networks to the external world. With its fixed mapping configuration and enhanced security features, organizations can confidently expose services and applications while protecting their network infrastructure.
What is Dynamic NAT?
Dynamic NAT, also known as NAPT (Network Address Port Translation), translates private IP addresses to public ones on a network. Unlike Static NAT, which uses one-to-one mapping, Dynamic NAT allows multiple private IP addresses to share a single public IP address. This dynamic mapping is based on the availability of public IP addresses in the NAT pool.
When a device from a private network initiates a connection to the internet, Dynamic NAT dynamically assigns a public IP address from the NAT pool to that device. This dynamic mapping is stored in a NAT translation table, which keeps track of the private IP address, the assigned public IP address, and the associated ports. As the connection terminates, the mapping is released, making the public IP address available for other devices.
Benefits and Use Cases of Dynamic NAT
Dynamic NAT offers several advantages, making it a popular choice for organizations and network administrators. Firstly, it allows the conservation of public IP addresses by sharing them among multiple devices. This scalability is particularly useful for large networks with limited public IP resources. Additionally, Dynamic NAT provides an additional layer of security as private IP addresses are not exposed to the internet directly. This makes it an ideal solution for securing internal networks.
Use cases for Dynamic NAT range from small office setups to large enterprise networks. It is commonly used in scenarios where there is a need for multiple devices to access the internet simultaneously while sharing a limited number of public IP addresses. This includes home networks, small businesses, and service providers managing large-scale networks.
Implementing Dynamic NAT
Implementing Dynamic NAT involves configuring NAT policies on networking devices such as routers or firewalls. These policies define the NAT pool, which includes the range of public IP addresses available for dynamic mapping. Additionally, access control lists (ACLs) can be used to specify which devices are eligible for Dynamic NAT. Careful planning and network design are essential to ensure smooth operation and efficient utilization of available resources.
Lab Guide on Dynamic NAT
It’s time to configure dynamic NAT, where we use a pool of IP addresses for translation. I’ll use a fairly simple topology with two hosts and one router performing NAT. We have 2 host routers on the left side this time, and I’m using another subnet. The subnet 192.168.123.0/24 is the internal network, and 192.168.23.0 is the external network.
Note:
The ip nat pool command lets us create a pool. I’m called “MYPOOL,”. For this pool, I’m using IP address 192.168.23.10 up to 192.168.23.20. We can now select the hosts we want to translate, which is done with the access list.
The access list above matches network 192.168.123.0 /24. That’s where host1 and host2 are located. The last step is to put the access list and pool together:
The command above selects access-list 1 as the source, and we will translate it to the pool called “MYPOOL.” This ensures that host1 and host2 are translated to an IP address from our pool. Remember that the unmanaged switch is just used for port connectivity and has no VLAN configuration.
Analysis:
And as you can see, host2 has been translated to IP address 192.168.2.11.
As you can see above, host1 has been translated to IP address 192.168.23.10.
Inside global is the IP address on the outside interface of your router performing NAT.
Inside local is the IP address of one of your inside hosts translated with NAT.
Outside local is the IP address of the device you are trying to reach, in our example, the web server (Web1).
Outside global is also the IP address of the device you are trying to reach, such as the webserver (Web1).
Why are the outside local and outside global IP addresses the same? With NAT, it’s possible to translate more than just from “inside” to “outside.” It’s possible to create an entry in our NAT router that whenever one of the hosts sends a ping to an IP address (say 10.10.10.10), it will be forwarded to Web1. In this example, the “outside webserver” is “locally” seen by our hosts as 10.10.10.10, not 192.168.23.3.
Conclusion:
Dynamic NAT serves as a versatile and efficient solution for network address translation. Allowing multiple devices to share a single public IP address offers scalability, security, and optimized resource utilization.
Network Connectivity: Starting with Firewalls
A firewall is a security system that monitors and controls network traffic based on security rules. Firewalls usually sit between trusted and untrusted networks, often the Internet. For example, office networks often use a firewall to protect their network from online threats—Firewalls control which traffic is allowed to enter a network or system and which traffic should be blocked.
When configuring a firewall, you create the rules for allowing and denying traffic based on the traffic protocol, port number, and direction. Firewalls work at Layer 3 and Layer 4 of the OSI model. We know now that Layer 3 is the Network Layer where IP works. Then we have Layer 4, the Transport Layer, where TCP and UDP work.
Packet filtering firewall
A packet-filtering firewall can filter traffic based on the source and destination IP addresses, the source and destination port numbers, and the protocol used. The downfall of a simple packet-filtering firewall is that it needs to understand the context of the conversation, making it easy for a bad actor to craft a packet to pass through the firewall.
Stateful packet inspection
Stateful packet inspection firewalls. Like a packet filtering firewall, a stateful packet inspection firewall filters traffic based on source and destination IP addresses, the source and destination port numbers, and the protocol in use. Still, it also understands the context of a conversation. Stateful firewalls rely on a lot of contexts when making decisions.
For example, if the firewall records outgoing packets on one connection requesting a certain kind of response, it will only allow incoming packets on that connection if they provide the requested type of response. Stateful firewalls can also protect ports* by keeping them all closed unless incoming packets request access to a specific port. This can mitigate an attack known as port scanning.
A key point: Lab Guide on Traffic flow and NAT
NAT operates as a middleman between a local network and the internet. When a device within a private network wants to communicate with an external device on the internet, NAT translates the private IP address of the sending device into the public IP address assigned to the network.
This translation process allows the device to establish a connection and send data packets across the internet. In the below example, while traffic flows from R1 to R2, the ASAv performs NAT. R1 is in an internal zone, while R2 is outside.Diagram: Firewall traffic flow and NAT
Next-generation firewall
Next-generation firewall A next-generation firewall (NGFW) is a layer seven firewall that can inspect the application data and detect malicious packets. A regular firewall filters traffic based on it being HTTP or FTP traffic (using port numbers), but it cannot determine if there is malicious data inside the HTTP or FTP packet.
An application-layer NGFW can inspect the application data in the packet and determine whether there is questionable content inside. NGFWs are firewalls with the capabilities of traditional firewalls but also employ a host of added features to address threats on other OSI model layers. Some NGFW-specific features include:
Deep packet inspection (DPI) – NGFWs perform much more in-depth inspection of packets than traditional firewalls. This deep inspection can examine packet payloads and which application the packet access. This allows the firewall to enforce more granular filtering rules.
Application awareness – Enabling this feature makes the firewall aware of which applications are running and which ports those applications use. This can protect against certain types of malware that aim to terminate a running process and then take over its port.
Identity awareness lets a firewall enforce rules based on identity, such as which computer is being used, which user is logged in, etc.
Sandboxing – Firewalls can isolate pieces of code associated with incoming packets and execute them in a “sandbox” environment to ensure they are not behaving maliciously. The results of this sandbox test can then be used as criteria when deciding whether or not to let the packets enter the network.
Web Application Firewalls (WAF)
While traditional firewalls help protect private networks from malicious web applications, WAFs help protect web applications from malicious users. A WAF helps protect web applications by filtering and monitoring HTTP traffic between a web application and the Internet. It protects web applications from attacks like cross-site forgery, cross-site scripting (XSS), file inclusion, and SQL injection.
Intrusion Prevention System
An intrusion prevention system (IPS) is a security device that monitors activity, logs any suspicious activity, and then takes corrective action. For example, if someone is doing a port scan on the network, the IPS would discover this suspicious activity, log the action, and then disconnect the system performing the port scan from the network.
In conclusion, network connectivity is the lifeline of our interconnected world. It empowers us to access information, communicate across borders, and unlock endless opportunities. From wired to wireless connections, overcoming challenges to embracing future advancements, network connectivity continues to shape our present and pave the way for a connected future.
0 notes
Text
Random Assorted Artists with songs in the showdown Pt. 2
This is the second list of random artists that have been submitted. This is pretty much anyone that didn’t get many submissions. If you see a song and are like hey this should be somewhere else the answer is no. Unless there is a repeat of a song somewhere or the artist shows up on another list they are meant to be here. Check out the other lists here.
Somebody - Age of Madness
Finale (The Magic Shop) - The Muppets
Komm, süsser Tod - Arianne Schreiber
If I Didn’t Believe in You - Jeremy Jordan (The Last Five Years)
Iodine - Icon for Hire
Can’t be Erased - JT Music
My Ordinary Life - The Living Tombstone
An Unhealthy Obsession - The Blake Robinson Synthetic Orchestra
Welcome to the Family - Watsky
Infinitesimal - Mother Mother
You’re Gonna Go Far, Kid - The Offspring
Walking Disaster - Sum 41
Small Blue Thing - Suzanne Vega
Wolf in Sheep’s Clothing - Set It Off
Finale (Can’t wait to see what you do next) - AJR
Top Picks for You - Injury Reserve
Good News - Mac Miller
Gopher Guts - Aesop Rock
Close your eyes (And count to fuck) - Run the Jewels
That Scrooge - Team Starkid
Rule #9- Child of the Stars - Fish in a Birdcage
A Million Gruesome Ways to Die - Daniel Ingram and Black Gryphon
Chicken Man - Evelyn Evelyn
Open the Sky - The Stupendium
Poison Pop - qbomb
I.D. - go! child
These Hallowed Wings - The Stupendium
Finding Mr. Midnight - Random Encounters
End of the Rope - They Might Be Giants
Lo-Fi Children - Wild Party
Brass Goggles - Steam Powered Giraffe
Hypothesis - Penny Parker
What Will You Leave Behind - Max II
Light of the Sun - Rustage ft. Johnald
DONTTRUSTME (don’t trust me) - 3OH!3
Vulture - Bear Ghost
Pale Blue Eyes - The Velvet Underground
Suicide Romantics - Des Rocs
Sleep Now in the Fire - Rage Against the Machine
Never Let Me Down Again - Depeche Mode
Selfless - The Strokes
The Loneliest - Måneskin
Back to Black - Amy Winehouse
The End of the World - Sharon Van Etten
Who said anything (about falling in love) - The Hoosiers
Live and Learn - Crush 40
Choices - The Hoosiers
Sometimes - Nick Lutsko
Hellbent - Mystery Skulls
When the Chips are Down - Hadestown
Trials - STARSET
Take Control - Old Gods of Asgard
Ricochet - STARSET
Symbiotic - STARSET
Aura - Thomas Bergersen
Asking For It - Hole
Softer, Softest - Hole
Banks - Lincoln
Bury Our Friends - Sleater-Kinney
Unwritten - Natasha Bedingfield
Planet of the Bass - Kyle Gordon
Bi Bi Bi - Sub-Radio
VS SAYU - James Landino ft. Nikki Simmons
Teal - Wunderhose
All My Friends - LCD Soundsystem
Bad Bad Things - AJJ
Since I saw Vienna - Wilbur Soot
Brain Power - NOMA
THE MOST FASHIONABLE FACTION - The Stupendium
Superman - Ivory Lane
New York - St. Vincent
Old Friends - Scott Helman
Even My Dog - Katheryn Gallagher
Way Less Sad - AJR
IT’S OK - Nightbirde
Vienna - Billy Joel
Breaking Out - The Protomen
Atlanta - go! child
Enigma - go! child
Atlanta - go! child
I’m Enough - Early Eyes
Melody from the Past - The Megas
The Will of One - The Protomen
build a giant robot out of trash - qbomb
Believe - Hollywood Undead
If I Believed - Starkid (Twisted Soundtrack)
The Night We Met - Lord Huron
Hearing Damage - Thom Yorke
A Better Son/Daughter - Rilo Kiley
Nothing Left - John-Allison Weiss
Along the Road - Radical Face
Learning to Fly - Hills x Hills
Habibi - Tamino
HYACINTHUS - Aidoneus
Into the West - Annie Lennox ish
Two Birds - Regina Spektor
Sticks & Stones - Jónsi
Where No One Goes - Jónsi, John Powell
Together from Afar - Jónsi
Throw Me in the Water - WILD
Welcome Home Son - Radical Face
Hey Brother - Avicii
Here’s To Us - Kevin Rudolf
Hungover in the City of Dust - Autoheart
Burned Out - dodie
In Our Bedroom After The War - Stars
Glory - Radical Face
Older Than I Am - Lennon Stella
Brother - Kodaline
Devourer - Aidoneus
Forever Young - Youth Group
The Village - Wrabel
0 notes
Text
Best Computer For Homeschooling
Cup of Parenting — Your Guide to the Best Computer for Homeschooling
As the world of education continues to evolve, more parents are opting for homeschooling to provide their children with a personalized and flexible learning experience. Whether you’re new to homeschooling or looking to upgrade your current setup, choosing the right computer is a vital decision that can significantly impact your child’s educational journey. In this article, we will explore the factors to consider when selecting the best computer for homeschooling.
Determining the Ideal Homeschooling Computer
Homeschooling is not one-size-fits-all. To find the ideal computer, you must assess your specific needs, budget, and preferences. Here are some key considerations:
Budget Constraints
Setting a realistic budget is the first step in finding the perfect homeschooling computer. Homeschooling can be cost-effective, but it’s essential to determine how much you’re willing to invest in the technology that will support your child’s education.
Desktop vs. Laptop
The decision between a desktop and a laptop depends on your homeschooling style. Desktops offer more power and customization options, while laptops provide mobility and flexibility. Consider your space, needs, and preferences to make the right choice.
Choosing the Right Operating System
The operating system (OS) of your computer is a critical factor. Here’s a quick overview of the most common options:
Windows: Windows-based computers offer a wide range of software and are compatible with many educational applications.
Mac OS: Apple’s macOS provides a user-friendly and creative learning environment. It’s an excellent choice for artistic and design-related subjects.
Linux: Linux is a versatile option for tech-savvy parents and children who want to explore open-source software and programming.
Chromebooks: These budget-friendly devices are designed for web-based tasks and are suitable for basic homeschooling needs.
Processing Power Matters
The processing power of your computer is crucial for multitasking and running educational software smoothly. Consider the type of tasks your child will be performing and choose a CPU (Central Processing Unit) accordingly.
Storage Solutions
Storage plays a role in how well your computer performs. For homeschooling, it’s recommended to opt for Solid State Drives (SSD) over Hard Disk Drives (HDD) due to their speed and durability. Ensure you have enough storage to accommodate educational materials, projects, and files.
RAM Requirements
Random Access Memory (RAM) is essential for multitasking and system performance. For smooth homeschooling, aim for at least 8GB of RAM, which can handle various applications simultaneously.
Display and Graphics
A good display and capable graphics are essential for engaging educational content. Consider screen size, resolution, and dedicated graphics if your child is into graphic design or gaming.
Connectivity Options
A stable internet connection is vital for online lessons. Ensure your computer has both wired and wireless connectivity options. A good Wi-Fi adapter and an Ethernet port can make a significant difference in your child’s online learning experience.
Peripherals Matter
Ergonomics should not be overlooked. A comfortable keyboard and mouse are essential for your child’s daily use. Additionally, consider external storage options and other peripherals like printers or scanners, depending on your homeschooling needs.
Audio and Webcam Quality
Clear audio and a reliable webcam are essential for online classes and video conferencing. Invest in quality peripherals or choose a computer with built-in high-definition audio and video capabilities.
Portability and Durability
If you plan on homeschooling on the go, consider the weight and battery life of the computer. Laptops are a natural choice for mobile learning, so choose one that suits your child’s needs. Durability features, like a rugged build, can also ensure the longevity of your device.
Security Features
Online safety is a top priority for homeschooling parents. Look for built-in security features, and consider additional measures, such as parental control software, to protect your child’s online activities.
0 notes
Text
The Great Pro-Wrestling Adventure Hour - 021
10/05/23
Defy TV 4:00 PM - 5:00 PM EST
Filmed at the Good Time Theatre at Dorney Park in Allentown, Pennsylvania
SEGMENT ONE (EIGHT MINUTES):

- Our show this week opened with Sudu Upadhyay voicing over still images from CORE's live event at the Bloomsburg Fair. We then join Sudu and Raven at the commentary booth where Sudu announced that as part of CORE's landmark strategic alliance, we will be joined by special guests from All Style Pro Wrestling and GLEAT. One of ASPW's top luchadores Tromba will be in action and from GLEAT we are joined by blue chip young wrestler Tetsuya Izuchi and referee Soft Imai. Raven said he had some special guests of his own, and with that the lights in the building were replaced by the glow of black lights and smoke began to fill the studio. Six individuals wearing make-up and fluorescent outfits ran into the frame and began to take turns sliding on their hands and knees in front of commentary booth, the metal they attached to their bodies sent sparks shooting up. Raven welcomed the slider scare actors from Dorney Park's Haunt event to the set. Sudu was impressed but confused by the display. Raven said as a special treat for the viewers during commercial breaks the scare actors will be giving Sudu a spooky slider makeover and at the end of the program Sudu will perform a slide of his own. Sudu said he never agreed to this, but Raven told him that the viewers are already looking forward to it and Sudu wouldn't want to disappoint them.
- The Great Pro-Wrestling Adventure Hour opening aired set to "Black Swan Lake" by Janko Nilovic.

Queen Aminata and Raychell Rose vs. Gin Sevani and Gypsy Mac
Queen Aminata and Raychell Rose defeated Gin Sevani and Gypsy Mac with a spear from Rose on Mac. (3:45)

- A music video aired set to "No estamos solas" by Ana Tijoux promoting a new tag team making their debut next week, two wrestlers from Chile that have made a name for themselves in CMLL and rings around the world, Stephanie Vaquer and La Catalina.
SEGMENT TWO (EIGHT MINUTES):

Tetsuya Izuchi vs. KUUKAI
Tetsuya Izuchi defeated KUUKAI via submission with a hammerlock in full guard. (4:09)

- Following the match we join Daphne Oz at the CORE news desk from the COal REgion Roundup.
- Daphne first sends us to comments from Fuego Del Sol on his unlikely alliance with Giant Baba Yaga. After weeks of coming to the aid of local talent that were being attacked by The Production, he never anticipated that it would be Giant Baba Yaga that would be there in his time of need. Fuego said that he and Baba will team up later today to face Derek Dillinger and Magnum CK, and after that we'll just have to see what the future holds. Regardless, Fuego is confident it will end better for him than it did for Jake Something and Vincent Nothing.
- Next up we get comments from the folkstyle team of Shaw Mason, Tim Bosby, and Hunter Holdcraft. They expressed a desire to get back to basics following their recent loss to the Southern 6. So they will be having a series of singles matches over the next three weeks against one another, the first of them to defeat both of their partners will go on to face "Filthy" Tom Lawlor at CORE's 15th Anniversary Show on October 27th in Jim Thorpe.
- We are then sent to a video of Starboy Charlie at ringside at the Worldwide Dojo in Bristol, Pennsylvania where Marcus Mathers is in the ring doing a number on some of the students as he gets back in ring shape after the injury he received prior to Trios Kingdom. Alex Taylor then appeared to the apparent surprise of the two men. Taylor said he streamed the training session for Kerry Morton to see, and Kerry was so impressed he got Starboy and Mathers a match next week against Big Dan Champion and Joshua Bishop of the TrustBusters Reserve.
- We close the segment out with Daphne Oz announcing the return of a familiar face. After a disappointing first run with CORE, the Von Trier brothers returned to the family ranch to regroup. After months of soul searching, next week one of the Von Triers will be back in CORE, Keith Von Trier. But as part of his journey, Keith has taken on a new moniker. So next week we will see Trench take on The Pennsylvania Polar Vortex.
SEGMENT THREE (SEVEN MINUTES):

Black Generation International (Titus Alexander and Bendito) vs. Tromba and Mike Skyros
Black Generation International defeated Tromba and Mike Skyros with the Chaos Theory from Alexander on Skyros. (4:47)

- Disappointed with his assigned partner, Tromba attacked Mike Skyros after the loss. Tromba locked Skyros in a submission hold and refused to break it. CORE officials made their way toward the ring to put a stop to the attack, but one of them caught the attention of Titus Alexander as he made his way up the aisle. Alexander shoulder checked Jigsaw and then got in his face. Jigsaw tried to deescalate the situation while Alexander shouted for Jigsaw to let Eddie Kingston know that he wants his rematch. Local talent and CORE officials turned their attention to the altercation and got between the two as Skyros was left to cry out for help.
SEGMENT FOUR (NINE MINUTES):

Giant Baba Yaga and Fuego Del Sol vs. The Production (Derek Dillinger and Magnum CK)
Giant Baba Yaga and Fuego Del Sol defeated The Production with a running neckbreaker from Yaga on Magnum. (7:33)
SEGMENT FIVE (NINE MINUTES):
- Before the main event, we got a shot of the commentary booth where Sudu's slider makeover was near complete, his face painted like a skull, hair spiked up a sprayed with temporary hair color, and a neon colored spiked vest over his suit jacket.

Sonny Kiss vs. Hyan
- Hyan went for the busaiku knee on Sonny Kiss, but Sonny pulled referee Allison Leigh in the way to absorb the strike. With the referee down, Trench made his way toward the ring. Before Trench could interfere, referee Scarlette Donovan entered the ring and sent Trench to the back. While this was transpiring, Sonny Kiss placed an international object in their boot. Hyan got back to her feet but was met with a superkick with Sonny's loaded boot and pinned.
Sonny Kiss defeated Hyan with a superkick. (7:07)

- Sonny Kiss called the members of the TrustBusters Reserve to the ring after the match. Trench was first out but Big Dan Champion, Joshua Bishop, and Invictus Khash all looked reluctant to enter the ring. Sonny Kiss requested that two of them lift Sonny's arms in victory. Trench was first to volunteer, but Sonny wanted one of three longer tenured members to do it, with Big Dan and Bishop eventually performing the honors.
SEGMENT SIX (THREE MINUTES):
- The lights again went down and were replaced by black lights, smoke filled the set, the disco version of the Friday The 13th theme from Part III began to play, and Raven announced that it was time for Sudu Upadhyay's very first slide. Sudu ran into frame preparing to send sparks flying with a tremendous slide, but just then one of the scare actors hit Sudu with a drop toe hold into a steel chair. Raven began laughing uproariously and said that while Sudu had been training during commercials breaks to learn how to slide, he had been doing some training of his own showing some of the scare actors his favorite wrestling maneuvers.
Next week on The Great Pro-Wrestling Adventure Hour
Starboy Charlie and Marcus Mathers vs. TrustBusters Reserve (Big Dan Champion and Joshua Bishop)
Shaw Mason vs. Hunter Holdcraft
Trench vs. "The Pennsylvania Polar Vortex" Keith Von Trier
Also in action…
Giant Baba Yaga and Fuego Del Sol
and the CORE tag team debut of Stephanie Vaquer and La Catalina
Upcoming Shows:
CORE Pro #124
10/27/23
Ancient Footprints Are Everywhere - CORE 15th Anniversary Show
Penn's Peak - Jim Thorpe, Pennsylvania
0 notes