#Malware Development
Explore tagged Tumblr posts
Text

Malware detected.
#lab#laboratory#malware#development#cyberpunk#mecha#robot#pilot#connection#lost#cyborg#android#cables#rain#retro#mechanic#save#error#digitalart#digitalsketch#drawing#illustration#stuck#digitaldrawing#digitalartwork#lights#redlights#robotics#digital art#digital illustration
645 notes
·
View notes
Text
my sssstupid ugly ahh roblox oc fanart lalalala

me when I make the most scrumptious toe curling delicious eyeweeping fangirl giggling running around in circles air kicking crying screaming hair pulling frustration screeching ahh lore and backstory for my little sentient scrip-breaking and game corrupting roblox npc ocs but don't know how to make a game in studio
#his name is sybau 🥀💔#jk its selever#the face i make when my game developer slowly starts giving me visions of the future and nightmares each night#and then I regain my memories and find out I was a scrapped npc in my dev's game and was abandoned#and also realize I'm some sort of eery corrupted malware virus entity in my game and my dev wants to delete me#but then I see my devs killing my npc friends and earasing their memories#yeah.. Do I make a lore post for this guy?.. I wish I knew how to code and stuff cries#if I ever made this game (I won't I'm dumb) it's heavily inspired off roblox myths#sentient script-breaking characters#story games like gasa4 and hhh#this was totally not my outlaws of robloxia oc lol#fanart#roblox#roblox myths#roblox oc#robloxia until dawn#forsaken#roblox hackers#no#Nah sel isn't related to any of that but um#SHADDAP#life is robloks#this guy is basically the song eight wonder by lemon demon personified#GAHH I WISH I WAS SMART ENOUGH TO KNOW HOW TO MAKE A GAME :'(((#do i tag lemon demon? Yeah prolly#lemon demon#tally hall#will wood#will wood and the tapeworms#normalize pretending your ocs have a fandom
17 notes
·
View notes
Text
trying to conquer my fear of installing games right now- it's been three minutes and i'm shaking like a fucking leaf
#we had a graphics card driver that need updating two months ago#and it took a few days to figure out what was wrong#and i collapse into a sludge at the mention of malware#and developed a fear of using PCs#and especially downloading/installing#i feel very nauseous#but i will persever
13 notes
·
View notes
Text
Hey everyone, something a little different from the usual stuff I post, but last week my project group at university finished our semester project, which also means that (aside our thesis and exam) we're almost finished with our bachelor's degree.
Over the last ~3 months we've been working on a small video game and it would mean the world to us if more people would check it out and maybe even give feedback. It's available for Windows and Mac, also it's free :)
I was mainly responsible for everything graphics-related and worked on concept art, 2D and 3D assets (models, textures etc.) and some VFX, but since we were a team of just 6 people everyone helped out where they could, so I also contributed to the coding and audio in parts. It was a lot of work, but it's also been a very fun experience and we're proud of our achievements. In the coming week we're going to present our project at an exhibition at our university, but we already wanted to make it available for playing before :3

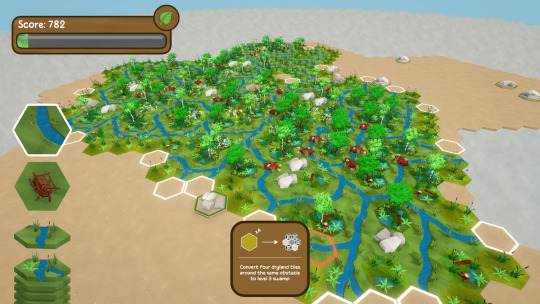
#gamedev#game development#game art#indie games#swampify#unity#unity3d#blender#selinasoriginal#I'm not really sure how to tag this lol#I just hope the warning from windows that you're executing and unknown program isn't too offputting for people🫠#we researched and apparently there's no way to sign it or otherwise manually certify it's not malware -#you literally can just wait & hope enough ppl use it regardless until microsoft goes: yeah enough ppl used it without issues guess it's saf
13 notes
·
View notes
Text
I want a kind of Papers Please, or like anomoly spot-the-difference type game just called SPYWARE(so you have to go and actively download and run a life called "spyware" in your computer) where youre looking at a mock up of like a windows 98 desktop as it simulates browsing the internet and, email clients, and running like limewire and shit, and you have to correctly identify fake ads and links and as you keep going the interface gradually progresses thru the 90s into the 00s and into the 2010s and on, with new styles of internet bullshit being phased in as old styles phase out.
#games no one will ever play#IS there some kind of like...#digital archive or like foundation or i dunno one random persons curated wiki for like ...#internet viruses?#where you can just look up information on specific malware programs and where they came from#and how they were generally transmitted#and over what period if time#and if they were part of a series if ongoing developing programs#etc ...
3 notes
·
View notes
Text
"Why do I feel so guilty?"
"You shouldn't. You did everything I asked."
"I know."
"He was so happy, though."
"You didn't get attached to the boy, did you?"
". . ."
"Answer me, GLITCH."
"No. I didn't."
"I'm just saying, he was actually happy."
"Why do you think I'd give two shits about that?"
"I don't. I just think that he didn't have to go—
"You don't have a say in any of this. He was only important to lure that bitch in. He was never meant to stay. What about that do you not fucking understand?"
". . ."
"GLITCH."
#glitchwave.exe#glitch_assistant_prototype.exe#glitchwave#glitchwaves developer#ransomware#malware#ask blog
2 notes
·
View notes
Text
I hope a lot of people who work in corporate IT learned a valuable lesson this weekend about why it's not more okay for a corporate computer to have programs that fuck around with your system than it is for an individual computer
#idk why but theres this attitude that thats fine on corporate computers even though you would never put something like that on your personal#i think the reasoning is that the company has it professionals who know what theyre doing and can keep a hold on it#but like aside from this weekend demonstrating that they obviously dont#ive never been on a work computer that didnt have some malware or other masquerading as a security program#taking up 87 per cent of the cpu at all times#well except for at google but they developed every program that was on their computers#anyway. i pray that this is the beginning of the end of that
6 notes
·
View notes
Text
AU Concept: The Sword of Cortés is cursed and more creepy and violent and Cortés manipulated Jack to be his protégé and curses Jack, which makes him a very disturbing distorted shell of himself while his soul is trapped in the Stone Prison.

#definitely inspired from those horror and infection aus#they genuinely creep me out but I love it#I might develop this more#fan art#reinbew’s art#creepypasta#pirates of the caribbean#potc#pirates#captain jack sparrow#jack sparrow#young jack sparrow#jack sparrow books#rob kidd#the image of the creepy eye gave me malware on my iPad it better be worth it#au#alternate universe#horror au#infection au#horror art
12 notes
·
View notes
Text
the 90/00s was so right as poetic describing the computer as body and extrapolating viruses out from there
4 notes
·
View notes
Text
Best SEO tools
Yoast SEO Yoast SEO is a powerful WordPress tool that optimizes websites for better search engine performance, enhancing visibility and helping achieve higher Google rankings. It streamlines the SEO process, making it straightforward to increase site reach and ranking potential.
Key Functions of Yoast SEO
On-Page SEO Analysis Yoast offers real-time on-page SEO analysis, suggesting improvements for keyword density, meta descriptions, titles, and headings. This helps in refining content for better SEO.
Readability Analysis The Readability Analysis feature makes content more engaging and user-friendly by recommending improvements to sentence structure and paragraph length.
Meta Tags & Snippet Optimization Yoast allows you to create custom meta tags and snippet previews, boosting click-through rates by optimizing how your content appears in search results.
XML Sitemaps Yoast automatically generates an XML sitemap, helping search engines easily discover and index your site content.
Schema Markup This feature provides easy integration of schema types like articles, business info, and events, resulting in rich snippets that improve user engagement.
Canonical URLs Canonical URLs help manage duplicate content, which is essential for better indexing and SEO performance.
Breadcrumbs Control Yoast’s breadcrumb feature enhances navigation, lowers bounce rates, and improves SEO by organizing content hierarchy.
Social Media Integration By adding Open Graph Metadata, Yoast optimizes content for platforms like Facebook, LinkedIn, and Twitter, improving visibility and engagement.
WooCommerce WooCommerce is a versatile, open-source e-commerce platform for WordPress, ideal for all business sizes. It offers customizable online stores, secure transactions, and powerful SEO features to enhance product visibility.
Key Functions of WooCommerce
Easy Setup & Customizable Products WooCommerce’s user-friendly setup allows quick store launch, with options for digital, grouped, or physical products to suit varied customer needs.
Payment Gateway Integration Supports multiple payment types like credit cards, PayPal, and Stripe, providing a seamless checkout experience.
Inventory & Shipping Management Inventory tracking and flexible shipping options make it easy to manage stock and meet diverse customer demands.
Tax Management Automated tax calculations simplify compliance with location-based tax rates.
Extensions & Mobile-Friendly Design WooCommerce offers various extensions and themes for store customization, with a mobile-friendly design to ensure a seamless experience across devices.
Here’s a refined draft that highlights your team’s expertise, affordable pricing, and experience in Yoast SEO and WooCommerce. I’ve organized the information to reflect your strengths and service offerings in a client-focused format. Reach out to us by clicking here

#wordpress#web design#website#ecommerce website development#e commerce#web development#seo services#seo#digitalmarketing#smm#marketingtrends#emailmarketing#malware
2 notes
·
View notes
Text
wordpress malware removal service and security assessment
Are You Looking For Penetration Tester For your Website?
I will perform pentest for you!
I have much more experience in this field.
I will perform a comprehensive penetration test on the security of your website and will deliver a professional report.
In this gig I will do WordPress malware removal services and assessment.
If you have any question, feel free to knock me!
2 notes
·
View notes
Text
if this happens to you, do yourself a favor and open regedit.exe, and look at these 2 paths:
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
and
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
if there is anything there that looks dumb, aka an exe named "DllHost.exe" or other software you don't recognize burn your installation with fire and stop downloading stupid junk
me watching the 4 command boxes of unknown origin open and then close right away as i start up my computer

54K notes
·
View notes
Text
How to Secure Your WordPress Login Page from Hackers
[et_pb_section fb_built=”1″ _builder_version=”4.27.4″ _module_preset=”default” global_colors_info=”{}”][et_pb_row _builder_version=”4.27.4″ _module_preset=”default” global_colors_info=”{}”][et_pb_column type=”4_4″ _builder_version=”4.27.4″ _module_preset=”default” global_colors_info=”{}”][et_pb_text _builder_version=”4.27.4″ _module_preset=”default” hover_enabled=”0″ global_colors_info=”{}”…
#brute force attack#brute force attack prevention#cyber-security#cybersecurity#cybersecurity best practices#disable xml-rpc#firewall for wordpress#malware protection#protect wordpress website#secure wordpress hosting#secure wordpress login#secure wp-config file#security#site hacking prevention#SSL encryption#two-factor authentication#web application firewall#web development#Website Builders#Wordpress#wordpress brute force protection#wordpress hosting security#wordpress password security#wordpress security#wordpress security best practices#wordpress security plugins#wordpress security tips
0 notes
Text
#branding in seoul#branding in south korea#web design#branding web sites#branding agency#branding development#branding malware#branding software
1 note
·
View note
Text
Roko’s Basilisk and the Broader AI Conversation: A Reflection on Fear, Control, and Human Nature
Hey everybody! Recently, I watched a very long YouTube video, on the thought experiment “Roko’s Basilisk” merchandising posted to a YouTube channel called Aperture. For your convenience, I will include the video here. And if you guys wanna watch and discuss, I look forward to hearing your thoughts in the comments. Recently, I watched a video that expanded on the infamous thought experiment,…
#AGI#AI development#AI ethics#AI impact on humanity#AI in society#AI regulation#AI-driven malware#aperture#artificial intelligence#critical thinking#cybersecurity#job displacement#machine learning#philosophy of AI#Roko’s Basilisk#Socratic method#thought experiments#Thoughts on Media#YouTube
0 notes
Text

The digital landscape is constantly evolving, and unfortunately, so are the threats that plague it. Malicious software development, often abbreviated as malware development, has become a booming underground industry, churning out ever-more sophisticated threats designed to steal data, disrupt operations, and inflict financial damage.
This poses a significant challenge for individuals and businesses alike, particularly in the United States, a prime target for cybercriminals due to its vast digital infrastructure and economic power. Here, we'll delve into the concerning rise of malware development, explore the evolving tactics of cybercriminals, and highlight how Sohojware (https://sohojware.com) is fortifying its proactive security measures to safeguard its clients.
The Alarming Rise of Malware Development
The malware development industry is fueled by significant financial gains. By compromising systems and stealing sensitive information, cybercriminals can extort victims, sell stolen data on the black market, or disrupt critical operations for ransom. This lucrative incentive has led to a surge in malware development, with new threats emerging at an alarming rate.
According to a recent report by Cybersecurity Ventures, global ransomware damage costs are projected to reach a staggering $26 billion by 2 This highlights the immense financial strain that malware development inflicts on businesses worldwide.
Evolving Tactics of Cybercriminals
Cybercriminals behind malware development are constantly innovating their tactics. Here are some of the concerning trends:
Ransomware as a Service (RaaS): This model allows less technical attackers to leverage pre-developed malware for a share of the ransom profits. This democratizes cyberattacks, making them more accessible and widespread.
Supply Chain Attacks: Targeting trusted vendors and software providers allows attackers to infiltrate a vast network of systems through a single point of entry.
Fileless Malware: This type of malware doesn't rely on traditional executables, making it more challenging to detect with conventional antivirus software.
Social Engineering: Deceptive tactics like phishing emails and phone scams are used to trick victims into revealing sensitive information or downloading malware.
These are just a few examples, and cybercriminals are constantly developing new methods to exploit vulnerabilities.
Sohojware's Commitment to Proactive Security
At Sohojware (https://sohojware.com), we understand the gravity of the malware development threat. We are committed to providing our clients with robust security solutions that are constantly evolving to stay ahead of the curve. Here's how we're fortifying our security measures:
Threat Intelligence: We maintain a comprehensive threat intelligence feed, allowing us to stay abreast of the latest malware development trends and vulnerabilities.
Security Awareness Training: We offer security awareness training programs to educate our clients and their employees on how to identify and avoid malware threats.
Multi-Layered Security Solutions: We employ a layered security approach that combines firewalls, intrusion detection systems, endpoint protection, and regular security assessments to mitigate malware risks.
Regular Patch Management: We prioritize timely patching of vulnerabilities to minimize the window of opportunity for malware exploits.
Incident Response Planning: We have a comprehensive incident response plan in place to effectively address and contain malware incidents should they occur.
By proactively addressing the evolving threat landscape of malware development, Sohojware empowers its clients to operate with greater peace of mind in the digital world.
FAQs about Sohojware and Malware Development
1. How can Sohojware help me protect my business from malware development?
Sohojware offers a comprehensive suite of security solutions designed to mitigate malware risks. We can conduct security assessments, implement multi-layered security solutions, and provide ongoing monitoring and threat intelligence to safeguard your business.
2. Does Sohojware offer security awareness training for employees?
Yes, Sohojware offers security awareness training programs that educate employees on how to identify and avoid malware threats. This training empowers your workforce to become a vital line of defense against cyberattacks.
3. What is Sohojware's incident response plan for malware attacks?
Sohojware has a comprehensive incident response plan that outlines the steps we take to identify, contain, and remediate malware incidents. This plan ensures a swift and effective response to minimize damage.
4. How does Sohojware stay updated on the latest malware development trends?
Sohojware maintains a subscription to a comprehensive threat intelligence feed. This allows us to stay informed about the latest malware development tactics and vulnerabilities, enabling us to proactively adjust our security measures.
5. Can Sohojware help me recover my data if it's encrypted by ransomware?
Yes, Sohojware offers incident response services that can assist in recovering your data after a ransomware attack. While we cannot guarantee data recovery in all cases, our experts will work diligently to develop a recovery plan tailored to your specific situation. We also provide guidance on data backup and recovery best practices to help prevent future data loss.
Conclusion
The relentless evolution of malware development underscores the critical importance of robust cybersecurity measures. By staying informed about the latest threats and implementing proactive security strategies, businesses and individuals can significantly reduce their risk of falling victim to cyberattacks. Sohojware (https://sohojware.com) is committed to helping you navigate this complex landscape and protect your valuable assets.
Remember: The key to effective cybersecurity lies in a multi-layered approach that includes technology, employee training, and ongoing vigilance.
By partnering with Sohojware, you're taking a proactive step towards safeguarding your digital world.
1 note
·
View note