#Network Firewall Security Management
Explore tagged Tumblr posts
Text

Network Firewall Security Management for Advanced Threat Protection
Protect your business with expert network firewall security management. We configure, monitor, and maintain firewalls to defend against cyber threats and ensure data safety. From rule updates to real-time alerts, our solutions keep your network secure and compliant. Get reliable protection tailored to your organization’s unique security needs.
0 notes
Text
The Benefits of Partnering with Radiant Info Solutions for Sophos XG Firewall Management
Discover the benefits of partnering with Radiant Info Solutions for Sophos XG Firewall management, ensuring robust security and efficient operations.

#Sophos XG Firewall management#Radiant Info Solutions#network security#firewall support#Sophos partner
0 notes
Text
How to Configure Azure Container Registry for a secure connection with Azure Container Apps
Ensuring container app resource security is important, and creating a private endpoint for security ensures it. This guide prioritizes actively configuring Azure Container Registry for secure connections with Azure Container Apps. Microsoft Azure empowers users with Azure Container Registry, enabling secure storage and management of Docker container images via Docker Hub technology. Azure…

View On WordPress
#AcrPull#Azure container Registry#Azure firewall#Azure Virtual Network#Container Apps#Private endpoint protection#Role Assignment#Self Assigned Managed Identity#User assigned Managed Identity#Workload security
0 notes
Text
1)Who is Ionix?
We are a full-service MSP (Managed Service Provider) based in Elk City, OK.
2)What does an MSP do?
If your school or business uses technology, we can help streamline your operations and protect you from security threats and equipment failure. We can do all of this for a fixed rate, so you don't have to worry about your system stability or your budget.
3)What can Ionix provide?
This is a hard question to answer because every business is different, and we customize our solutions to fit your needs. Small list of what we can provide:
Network Solutions: Firewall, Switches, Cabling and Wireless Access Points
Hardware for each user: Computer, Monitor, battery backup
Security Awareness Training
PCI Compliance/Consulting
Security Cameras
Data backup solutions
#WIRING#technology#Switch#smartboard#security cameras#network#MONITOR#Managed Services#laptop#firewall#desktop#cloud#cabling#backup
1 note
·
View note
Text
Top 20 Technical Support Interview Questions and Answers for Freshers in IT
When applying for a technical support role in the IT industry, preparation is key to success. To help freshers ace their technical support interviews, we’ve compiled a comprehensive list of 20 common interview questions along with sample answers. These questions cover a wide range of technical topics and soft skills necessary for excelling in a technical support role. What does technical support…

View On WordPress
#Antivirus#BIOS Update#Blue Screen of Death#DHCP#DNS#Firewall#Internet Connectivity#Interview questions#IP Address#IT Troubleshooting#Malware Protection#NAT#Network Security#Patch Management#Router#Subnetting#Switch#System Restore#Technical Support#Technology Trends#VPN
0 notes
Text
Firewall Friday: Network Security - Protecting Your Network from Threats
Welcome to Firewall Friday, where we dive into the exciting world of network security with a touch of humor and relatable analogies. In this edition, we’ll explore the importance of network security and how firewalls act as the guardians of your network, protecting it from potential threats. Get ready to embark on a hilarious and informative journey as we use common analogies, playful emojis, and…

View On WordPress
#access control#brute force attacks#data encryption#employee education#firewall#hackers#intruders#intrusion prevention#multi-layered defense#network protection#network security#packet inspection#patch management#security incident response#spoofing
0 notes
Text
I think we need more love for Ethernet cables around here. I TRULY think we do.
Come on, you can take both ends of a cable and jam them into both of the Ethernet ports a robot has and see her immediately get stuck in a network loop. Hear her fans start working three times as hard. Kick her off any wireless Internet she may have had, so she can't access any of her databases except what's installed. Even that's slow going, just because of how much energy the network loop is making.
Her firewalls and security measures would jam up and maybe even crash, from how much information it thinks it needs to scan. Immediate robot dumbification device, essentially.
This might not work very well on newer models, and you might get scolded on trying to make her networks loop like that, but on the models that don't have network management... you could really have some fun and wreak some havoc too.
#⚙️ | BOTPOSTING.py#��� | SUGGESTIVE.md#robophilia#technophilia#robot fucker#robotfucker#robofucker#robotgirl#robot girl#robot nsft
85 notes
·
View notes
Note
Hi Cyliph, can you tell something about Ar-Lo, he looks so interesting^^
I'm honored people like him :,)

[Potential small HDBS spoilers]]
Ar-Lo is old. Very old. Old enough to be considered somewhat of an cryptic figure among architects. He remembers a time when architects were not all One. Hundreds of thousands of years old. He was created as one of the first waves of expansion during a time when architects had just transferred to their biomechanical vessels. He's seen generations of vessels rise and fall out of use. One of the first ever born with no real parents or family or heritage.
A blank slate of an individual created to protect a colony world known as Juit-Eh from encroaching conflict (At least- that was the intention, the code recombination and manipulation technology was still new).
More below cut.
Who they were fighting, why, and for what has been lost to time. Ar-Lo himself remembers little of that bygone age and its politics. Its been lost to the network through information surges and wipes. What is known is that approximately 300,000 years ago Ar-Lo was functioning as a gladiator primarily based in Juit-Eh still. The indomitable vessel he used (barely modified-- not designed by him) was a real crowd pleaser to architects and non architects alike. It brought in loads of tourism-- and with it currency to the planet. The practice was considered too brutal by homeworld standards, and the end of his career was the annexation treaty that brought Juit-Eh back in to the protection of Oulinaean forces.
This annexation brought Juitian representation to the Tel Ju council. The representative brought a body guard with him, the most popular (former) gladiator known as Ar-Lo. The biggest 'fuck you' he could manage.
--
As it turns out, when you're primarily locked in the innermost sanctum of the most secure piece of architect territory you don't exactly get much valor. Not that Ar-Lo needed it. His pride was his strict loyalist views and sharp mind. He soon enough became versed enough in political talk that he could hold in own in any debate you threw at him. His trained body language and biolights (from years of existing as nothing but a background ornament) served him well in ensuring no other was able to get under his skin. His oratory skills only highlight his trained physical prowess and his rising influence on political matters made those in charge wary of him.
Ar-Lo proved his competency well enough that he was promoted over the course of years to supreme commander of the military. A scary job, and an isolating one. Not that it made a difference, by the time he reached the position anyone in networking distance already had a firewall up. He was already an unpleasant, paranoid, and a violent loyalist.
Though Ar-Lo had plans for every potential physical threat inside and out he was not prepared for the devastating plague that ripped through the architect colonies. Isolation barrier on isolation barrier proved useless, and with no cure in sight the council had to enact their most dire contingency plan. Ar-Lo was one such soul chosen to stay behind.
.
..
...

----
...
Cy fun facts:
Ar-lo was designed as the foil for Robin and Al-an in HDBS, he wasn't suppose to be likeable, but I'm grateful so many people want to know more about him. I cant reveal everything though.
He is brown because he needed to contrast the surrounding landscape, which was primarily green and dark turquoise.
Strange even among architects is that he does not experience dizzyness from vessel swapping no matter the size. Perhaps a remnant of his time as a gladiator, or maybe years of trained neural control.
Ar-lo might hold the record for oldest architect, especially post-kharaa.
His vessel is pretty standard bulky for guardsmen-- but he hasn't always used this vessel.
Before he became a political figure he was actually considered pretty handsome and likeable, like a celebrity. Even though his personality and skill didn't change.
He has never figured out how to properly integrate himself in architect society despite his age. This often leaves him frustrated and the only way he knows to take out that frustration is violence.
Ar-lo is only his current designation
Ar-lo likes art. Not realism, though. He likes art that makes you question things or appreciate the skill of the artist. The piece that represents him most closely is Josef Alber's Homage to the Square: Sentinel
Armor - Oulinaean (homeworld - left) - Jutian house (right) His thick hide serves as natural armor, anything else is just decorative, shows heritage, or is multitool storage.
Playlist:
PRE-KHARAA Seether - Words As Weapons Psychodelic Prn Crumpets - Found God in a Tomato Radiohead - Nude Five Finger Death Punch - Remember Everything Seether - Country Song System Of A Down - Spiders Puddle of Mudd - Blurry POST-KHARAA Soul Survivor - ORDER TotalDeadCenter - The Forgotten Soldier Skaen - Grief, Aftermath Mother Mother - Sleep Awake Vessel - Red Sex (Re-Strung) Vivivivivi - Reduced to Guts Pogo - Undone <- His theme song!
#i fucking love music <3#feb 2 was his birthday btw :)#subnautica#sbz#subnautica below zero#ask#architect oc#worldbuilding#ar lo#its funny that people ask the most about ar lo when i can say the least about him of any of my characters ;u;#hdbs#hdbs spoilers
62 notes
·
View notes
Text
Albert Gonzalez (born 1981) is an American computer hacker, computer criminal and police informer, who is accused of masterminding the combined credit card theft and subsequent reselling of more than 170 million card and ATMnumbers from 2005 to 2007, the biggest such fraud in history. Gonzalez and his accomplices used SQL injection to deploy backdoors on several corporate systems in order to launch packet sniffing (specifically, ARP spoofing) attacks which allowed him to steal computer data from internal corporate networks.
Gonzalez bought his first computer when he was 12, and by the time he was 14 managed to hack into NASA. He attended South Miami High School in Miami, Florida, where he was described as the "troubled" pack leader of computer nerds. In 2000, he moved to New York City, where he lived for three months before moving to Kearny, New Jersey.


While in Kearny, he was accused of being the mastermind of a group of hackers called the ShadowCrew group, which trafficked in 1.5 million stolen credit and ATM card numbers. Although considered the mastermind of the scheme (operating on the site under the screen name of "CumbaJohnny"), he was not indicted. According to the indictment, there were 4,000 people who registered with the Shadowcrew.com website. Once registered, they could buy stolen account numbers or counterfeit documents at auction, or read "Tutorials and How-To's" describing the use of cryptography in magnetic strips on credit cards, debit cards and ATM cards so that the numbers could be used. Moderators of the website punished members who did not abide by the site's rules, including providing refunds to buyers if the stolen card numbers proved invalid.
In addition to the card numbers, numerous other objects of identity theft were sold at auction, including counterfeit passports, drivers' licenses, Social Security cards, credit cards, debit cards, birth certificates, college student identification cards, and health insurance cards. One member sold 18 million e-mail accounts with associated usernames, passwords, dates of birth, and other personally identifying information. Most of those indicted were members who actually sold illicit items. Members who maintained or moderated the website itself were also indicted, including one who attempted to register the .cc domain name Shadowcrew.cc.
The Secret Service dubbed their investigation "Operation Firewall" and believed that up to $4.3 million was stolen, as ShadowCrew shared its information with other groups called Carderplanet and Darkprofits. The investigation involved units from the United States, Bulgaria, Belarus, Canada, Poland, Sweden, the Netherlands and Ukraine. Gonzalez was initially charged with possession of 15 fake credit and debit cards in Newark, New Jersey, though he avoided jail time by providing evidence to the United States Secret Service against his cohorts. 19 ShadowCrew members were indicted. Gonzalez then returned to Miami.
While cooperating with authorities, he was said to have masterminded the hacking of TJX Companies, in which 45.6 million credit and debit card numbers were stolen over an 18-month period ending in 2007, topping the 2005 breach of 40 million records at CardSystems Solutions. Gonzalez and 10 others sought targets while wardriving and seeking vulnerabilities in wireless networks along U.S. Route 1 in Miami. They compromised cards at BJ's Wholesale Club, DSW, Office Max, Boston Market, Barnes & Noble, Sports Authority and T.J. Maxx. The indictment referred to Gonzalez by the screen names "cumbajohny", "201679996", "soupnazi", "segvec", "kingchilli" and "stanozlolz." The hacking was an embarrassment to TJ Maxx, which discovered the breach in December 2006. The company initially believed the intrusion began in May 2006, but further investigation revealed breaches dating back to July 2005.
Gonzalez had multiple US co-defendants for the Dave & Buster's and TJX thefts. The main ones were charged and sentenced as follows:
Stephen Watt (Unix Terrorist, Jim Jones) was charged with providing a data theft tool in an identity theft case. He was sentenced to two years in prison and 3 years of supervised release. He was also ordered by the court to pay back $250,000 in restitution.
Damon Patrick Toey pleaded guilty to wire fraud, credit card fraud, and aggravated identity theft and received a five-year sentence.
Christopher Scott pleaded guilty to conspiracy, unauthorized access to computer systems, access device fraud and identity theft. He was sentenced to seven years.
Gonzalez was arrested on May 7, 2008, on charges stemming from hacking into the Dave & Buster's corporate network from a point of sale location at a restaurant in Islandia, New York. The incident occurred in September 2007. About 5,000 card numbers were stolen. Fraudulent transactions totaling $600,000 were reported on 675 of the cards.
Authorities became suspicious after the conspirators kept returning to the restaurant to reintroduce their hack, because it would not restart after the company computers shut down.
Gonzalez was arrested in room 1508 at the National Hotel in Miami Beach, Florida. In various related raids, authorities seized $1.6 million in cash (including $1.1 million buried in plastic bags in a three-foot drum in his parents' backyard), his laptops and a compact Glock pistol. Officials said that, at the time of his arrest, Gonzalez lived in a nondescript house in Miami. He was taken to the Metropolitan Detention Center in Brooklyn, where he was indicted in the Heartland attacks.
In August 2009, Gonzalez was indicted in Newark, New Jersey on charges dealing with hacking into the Heartland Payment Systems, Citibank-branded 7-Eleven ATM's and Hannaford Brothers computer systems. Heartland bore the brunt of the attack, in which 130 million card numbers were stolen. Hannaford had 4.6 million numbers stolen. Two other retailers were not disclosed in the indictment; however, Gonzalez's attorney told StorefrontBacktalk that two of the retailers were J.C. Penney and Target Corporation. Heartland reported that it had lost $12.6 million in the attack including legal fees. Gonzalez allegedly called the scheme "Operation Get Rich or Die Tryin."
According to the indictment, the attacks by Gonzalez and two unidentified hackers "in or near Russia" along with unindicted conspirator "P.T." from Miami, began on December 26, 2007, at Heartland Payment Systems, August 2007 against 7-Eleven, and in November 2007 against Hannaford Brothers and two other unidentified companies.
Gonzalez and his cohorts targeted large companies and studied their check out terminals and then attacked the companies from internet-connected computers in New Jersey, Illinois, Latvia, the Netherlands and Ukraine.
They covered their attacks over the Internet using more than one messaging screen name, storing data related to their attacks on multiple Hacking Platforms, disabling programs that logged inbound and outbound traffic over the Hacking Platforms, and disguising, through the use of proxies, the Internet Protocol addresses from which their attacks originated. The indictment said the hackers tested their program against 20 anti virus programs.
Rene Palomino Jr., attorney for Gonzalez, charged in a blog on The New York Times website that the indictment arose out of squabbling among U.S. Attorney offices in New York, Massachusetts and New Jersey. Palomino said that Gonzalez was in negotiations with New York and Massachusetts for a plea deal in connection with the T.J. Maxx case when New Jersey made its indictment. Palomino identified the unindicted conspirator "P.T." as Damon Patrick Toey, who had pleaded guilty in the T.J. Maxx case. Palomino said Toey, rather than Gonzalez, was the ring leader of the Heartland case. Palomino further said, "Mr. Toey has been cooperating since Day One. He was staying at (Gonzalez's) apartment. This whole creation was Mr. Toey's idea... It was his baby. This was not Albert Gonzalez. I know for a fact that he wasn't involved in all of the chains that were hacked from New Jersey."
Palomino said one of the unnamed Russian hackers in the Heartland case was Maksym Yastremskiy, who was also indicted in the T.J. Maxx incident but is now serving 30 years in a Turkish prison on a charge of hacking Turkish banks in a separate matter. Investigators said Yastremskiy and Gonzalez exchanged 600 messages and that Gonzalez paid him $400,000 through e-gold.
Yastremskiy was arrested in July 2007 in Turkey on charges of hacking into 12 banks in Turkey. The Secret Service investigation into him was used to build the case against Gonzalez including a sneak and peek covert review of Yastremskiy's laptop in Dubai in 2006 and a review of the disk image of the Latvia computer leased from Cronos IT and alleged to have been used in the attacks.
After the indictment, Heartland issued a statement saying that it does not know how many card numbers were stolen from the company nor how the U.S. government reached the 130 million number.
Gonzalez (inmate number: 25702-050) served his 20-year sentence at the FMC Lexington, a medical facility. He was released on September 19, 2023.
22 notes
·
View notes
Text
Demystifying cloud computing: the future of technology.

In today's rapidly evolving digital world, cloud computing is not just a technology trend-cloud computing is the foundation of today's IT infrastructure. from streaming your favourite Netflix show to collaborating on Google Docs.
what is cloud computing?

Cloud computing is the provision of computing services including the servers, databases, storage, networking, software, analytics, and intelligence over the internet to offer faster innovation, flexible resources, and economies of scale.
Types of cloud services.
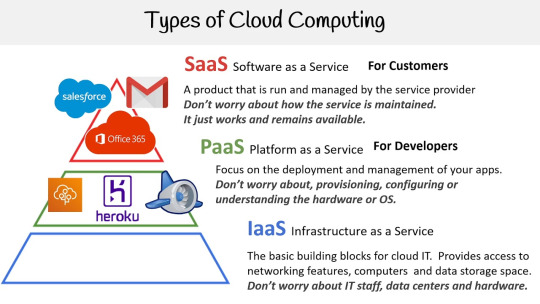
Security in the cloud.
Security is the top priority. cloud vendors employ encryption, firewalls, multi-factor authentication, and periodic audits to secure data. Organizations must, however, set up and manage secure access.
The future of cloud computing.

The future of cloud computing is being defined by a number of ground breaking trends that are changing the way data and applications are processed. Edge computing is moving computation near data sources to decrease latency and improve real-time processing for IoT and mobile applications.
7 notes
·
View notes
Text
CatNap stays calm as the Syndicate enforcer steps into the room, his augmented senses scanning the area. Without hesitation, CatNap activates his cloaking module, blending into the shadows. The enforcer glances around suspiciously but fails to spot him.
Carefully, CatNap moves back to the central control console. His fingers fly across the interface as he begins hacking into the system. The console's security protocols are tight, but nothing CatNap hasn't dealt with before. He bypasses the firewalls and begins accessing the prototype control network.
The enforcer, still on alert, moves closer to the console, scanning the area with laser focus. Time is running out, but CatNap manages to locate the shutdown failsafe that Dr. Bubbaphant mentioned. He quickly inputs the command, but the system requests the override code—Dr. Bubbaphant’s code.
Knowing the enforcer could detect him at any second, CatNap opens a secure communication channel to the doctor. “Doc, I’m in. I need the override code now.”
Dr. Bubbaphant, still at the safehouse, responds quickly. “The code is Omega-73Delta9... You have to hurry; they might have noticed by now.”
CatNap inputs the code, and the system begins initiating the shutdown sequence. All across Neon City, the prototypes are being disabled one by one, their control signals severed.
Just as the final confirmation flashes on the screen, the enforcer gets too close. His enhanced hearing picks up a faint noise from the console. “Who’s there?” he growls, drawing a plasma blade from his side.
CatNap remains cloaked but knows he needs to move fast.
6 notes
·
View notes
Text
What is the difference between network support and IT support?
Network Support Services

When managing technology in a business, terms such as Network Support and IT support often arise. While they may sound similar, they cover different areas of technology services. Understanding the difference can help businesses select the most suitable support for their specific needs.
What Is IT Support?
IT support refers to general technical assistance that helps users and businesses maintain their computer systems and networks. As this includes and consists of setting up hardware and software resources, troubleshooting errors, installing applications, managing user accounts, and fixing computer-related issues. IT support is often the first line of help when there’s a problem with your PC, email, or printer.
In short, IT support focuses on helping users interact with technology smoothly on the front end—solving problems that affect individual devices and users.
What Is Network Support?
Network assistance, on the other hand or side, is more focused on maintaining and managing the backend infrastructure that connects all devices in a business with its observations. As this includes routers, switches, firewalls, servers and wireless access points in it. Network assistance assures that the entire system runs securely, efficiently, and without interruptions.
Everyday network support tasks include and consists of activities:
Monitoring the network performance and observations.
Preventing and responding towards the security threats and potential checks.
Managing the IP addresses and server uptime with its implementation into the system.
Ensuring smooth internal and external communication.
Troubleshooting internet connectivity and network failures.
In essence, Network assistance maintains the foundation of your digital environment and existing settings, keeping it strong and reliable for better outcomes and deliverables. Without a properly managed network, IT devices and software may fail to function correctly and may result in significant concerns.
How Do They Work Together?
Both IT support and Network Support are essential and a must for a complete tech ecosystem and acceptable outcomes. While IT supports and aids the individual users and their machines with its expertise, meanwhile network support keeps the systems update behind the scenes running smoothly. Together, they ensure that businesses can operate efficiently without technical disruptions. Many businesses rely upon and prefer to stay updated with trusted technology service providers, such as Suma Soft, IBM, and Cyntexa, which offer both IT and Network assistance and support tailored to meet the specific needs of modern organizations as per the business demand and objective concern. Selecting the optimal blend of both assures long-term performance, stability, and sustainable growth with its adaptation.
#it services#technology#saas#software#saas development company#saas technology#digital transformation
2 notes
·
View notes
Text
Preventative IT Maintenance: Keeping Your Business Running Smoothly

With technology moving forward so fast, your business can’t operate without it. Computers, servers, cloud systems and software platforms have to be running smoothly to keep your team productive, defend confidential information and make sure customers receive a good experience.
Unfortunately, IT systems don’t manage themselves without attention.
This is why we need preventative IT maintenance. Regular car servicing makes sure your car avoids breakdowns and preventative IT support does the same for your systems. Here at Image IT, we know that companies who focus on IT before issues arise benefit a lot. We’ll now look at what preventative maintenance means and understand why it helps your business run smoothly.
What Does Preventative IT Maintenance Mean?
Taking care of your IT infrastructure ahead of time is called preventative maintenance. With preventative maintenance, you take action to make sure your systems are in good shape all the time, so you don’t have to rush to solve emergencies.
Such tasks refer to:
Tracking how the system is running
Putting security patches and new versions of the software into use
Regularly using antivirus and malware software
Testing the use of backup options
Updating both your device’s drivers and firmware
Checking the configurations for firewalls and networks
Exchanging ageing equipment to prevent any breakdowns
At Image IT, we set up specialized maintenance services that guarantee your technology remains in top condition and reduces the chance of risks and downtime.
Why Taking Care of Problems in Advance Is Crucial for Companies in Ireland
1. Minimize any time when your business is not working effectively.
Problems with your IT systems such as servers failing, networks breaking or bugs in software, may bring your work to a halt and cost you in both time and money. Doing preventative maintenance lets you catch and manage issues early and this means your business avoids the stress of dealing with major problems.
If a server begins to overheat, it’s possible to handle the issue before it crashes, so you won’t have to deal with expensive downtime and loss of data.
2. Prevent or Stop Cyber Attacks
More and more, businesses in Ireland are facing cyberattacks, most often small and medium-sized companies. Many attackers use old software, unpatched versions and networks that have not been properly set up.
Ongoing upkeep of security tools such as firewalls, antivirus software and system updates, makes it much less likely for your system to become a victim of ransomware, phishing or a data breach.
3. Increase the Lifespan of IT Assets
Just as changing the oil in your car lengthens its engine’s lifespan, looking after your IT equipment in the same way will help it work longer. Regularly taking care of computers stops them from wearing out and prevents too many replacements.
4. Raise the effectiveness of your staff.
This kind of slow work is frustrating and influences how your team feels about their work. If technology runs smoothly, your team won’t have to worry about systems or spend time finding IT solutions.
5. With time, the cost of IT will decrease.
Though it might feel like a pricey addition, upfront maintenance helps save money and prevents serious IT problems. One data breach, meeting replacement or lasting period of downtime can often be more expensive than all your ISP’s services put together.
Important Parts of a Well-Made IT Maintenance Plan
We create preventative maintenance strategies for your business that fit its individual requirements at Image IT. The method we use is:
We watch your systems around the clock.
We watch over your systems around the clock, spotting problems early and fixing them so they don’t impact your work.
Timely Updates and Patch Upgrades
We make sure your operating systems, applications and antivirus are always running on the latest versions.
Test the backup and recovery of your data.
We ensure your backups are properly configured and we regularly perform tests to see how fast you can recover data.
You can do a Network Health Check here.
We examine your network for good speed, serious security flaws and technology issues to confirm your system operates safely and properly.
Managing Assets and Deciding on Their Life
We watch over your equipment and make sure you can update your technology before it starts causing issues.
Support from the users and helpdesk
If your team has any IT questions or concerns, our friendly team is there to lend a non-technical helping hand.
Why Is Image IT a Great Solution?
Operating out of North Dublin, Image IT has been supporting company’s in Ireland for about 15 years. Our knowledgable team delivers helpful, consistent and friendly IT assistance to the companies here in New Zealand.
We are dedicated to forming long-term relationships with clients so we can do more than just address issues; we can help avoid them.
You will gain the following benefits when you work with us:
Transparent pricing
A quick response from the team
Customized maintenance services
Expert opinions offered in a personal way
If you have just a few devices or a complex IT structure, our solutions are designed to match your requirements and your budget.
Benefits You Can See in Life: An Example
There were many issues at one of our clients, a small financial services firm in Dublin, involving downtime in the network and software that was past its update. Following their sign up for our preventative maintenance, we set up a monitoring system, cleaned their network and ran scheduled updates.
The result? A 90% drop in IT issues reported by staff, faster systems, and peace of mind for their management team knowing their data and systems were protected.
Your Next Step: Secure Your Business with Preventative IT Support
Don’t wait for a system failure, data breach, or productivity drop to remind you of your IT vulnerabilities. Preventative maintenance is one of the smartest investments you can make in your business.
Let Image IT take the stress out of managing your technology — so you can focus on what you do best.
2 notes
·
View notes
Text
What is Cybersecurity? Types, Uses, and Safety Tips
What is Cyber security?
Cyber security, also known as information security, is the practice of protecting computers, servers, networks, and data from cyberattacks. With the increasing reliance on technology in personal, professional, and business environments, the importance of cyber security has grown significantly. It helps protect sensitive data, ensures the integrity of systems, and prevents unauthorized access to confidential information.
For businesses in Jaipur, cyber security services play a crucial role in safeguarding digital assets. Whether you're an e-commerce platform, an IT company, or a local enterprise, implementing strong cyber security in Jaipur can help mitigate risks like hacking, phishing, and ransomware attacks.
Types of Cyber security
Cyber security is a vast domain that covers several specialized areas. Understanding these types can help individuals and organizations choose the right protection measures.
1. Network Security
Network security focuses on protecting the network infrastructure from unauthorized access, data breaches, and other threats. Tools like firewalls, virtual private networks (VPNs), and intrusion detection systems are commonly used. In Jaipur, many businesses invest in cyber security services in Jaipur to ensure their networks remain secure.
2. Information Security
This type of cyber security involves protecting data from unauthorized access, ensuring its confidentiality and integrity. Companies offering cyber security in Jaipur often emphasize securing sensitive customer and business information, adhering to global data protection standards.
3. Application Security
Application security addresses vulnerabilities in software and apps to prevent exploitation by cybercriminals. Regular updates, secure coding practices, and application testing are vital components.
4. Cloud Security
As more businesses move to cloud-based solutions, securing cloud environments has become essential. Cyber security providers in Jaipur specialize in offering services like data encryption and multi-factor authentication to ensure cloud data is safe.
5. Endpoint Security
Endpoint security protects devices such as laptops, desktops, and mobile phones from cyber threats. It is especially critical for remote work setups, where devices may be more vulnerable. Cyber security services in Jaipur provide solutions like antivirus software and mobile device management to secure endpoints.
6. IoT Security
With the rise of Internet of Things (IoT) devices, ensuring the security of connected devices has become crucial. Businesses in Jaipur use cyber security in Jaipur to secure smart devices like industrial sensors and home automation systems.
Uses of Cyber security
Cyber security is indispensable in various domains. From individual users to large organizations, its applications are widespread and critical.
1. Protection Against Cyber Threats
One of the primary uses of cyber security is to safeguard systems and data from threats like malware, ransomware, and phishing. Businesses in Jaipur often rely on cyber security Jaipur solutions to ensure they are prepared for evolving threats.
2. Ensuring Data Privacy
For industries like finance and healthcare, data privacy is non-negotiable. Cyber security measures help organizations comply with laws and protect sensitive customer information. Cyber security services in Jaipur ensure businesses meet data protection standards.
3. Business Continuity
Cyber security is essential for ensuring business continuity during and after cyberattacks. Jaipur businesses invest in robust cyber security services in Jaipur to avoid downtime and minimize financial losses.
4. Securing Financial Transactions
Cyber security ensures the safety of online transactions, a critical aspect for e-commerce platforms and fintech companies in Jaipur. Solutions like secure payment gateways and fraud detection tools are widely implemented.
5. Enhancing Customer Trust
By investing in cyber security in Jaipur, businesses build trust with their customers, demonstrating a commitment to safeguarding their data and transactions.
Cyber security in Jaipur
Jaipur is emerging as a hub for businesses and IT companies, which has increased the demand for reliable cyber security solutions. Cyber security services in Jaipur cater to diverse industries, including retail, healthcare, education, and finance.
Local providers of cyber security Jaipur solutions offer tailored services like:
Vulnerability Assessments: Identifying potential security risks in systems and networks.
Penetration Testing: Simulating attacks to uncover weaknesses and improve defenses.
Managed Security Services: Continuous monitoring and management of security operations.
Many IT firms prioritize cyber security services in Jaipur to ensure compliance with global standards and protect their operations from sophisticated cyber threats.
Safety Tips for Staying Secure Online
With the rising number of cyberattacks, individuals and businesses must adopt proactive measures to stay secure. Here are some practical tips that integrate cyber security in Jaipur into daily practices.
1. Use Strong Passwords
Ensure passwords are long, unique, and a mix of letters, numbers, and symbols. Avoid reusing passwords for multiple accounts. Cyber security experts in Jaipur recommend using password managers for added security.
2. Enable Two-Factor Authentication (2FA)
Adding an extra layer of security through 2FA significantly reduces the risk of unauthorized access. Many cyber security services in Jaipur emphasize implementing this measure for critical accounts.
3. Regular Software Updates
Outdated software can be a gateway for attackers. Keep operating systems, antivirus tools, and applications updated to close security loopholes. Businesses in Jaipur frequently rely on cyber security Jaipur providers to manage system updates.
4. Be Cautious with Emails
Phishing emails are a common attack vector. Avoid clicking on suspicious links or downloading unknown attachments. Cyber security in Jaipur often involves training employees to recognize and report phishing attempts.
5. Invest in Reliable Cyber security Services
Partnering with trusted cyber security services in Jaipur ensures robust protection against advanced threats. From endpoint protection to cloud security, these services help safeguard your digital assets.
6. Avoid Public Wi-Fi for Sensitive Transactions
Public Wi-Fi networks are vulnerable to attacks. Use a VPN when accessing sensitive accounts or conducting financial transactions. Cyber security Jaipur experts often provide VPN solutions to businesses and individuals.
7. Backup Your Data Regularly
Regularly backing up data ensures that critical information is not lost during cyber incidents. Cyber security providers in Jaipur recommend automated backup solutions to minimize risks.
Why Choose Cyber Security Services in Jaipur?
The vibrant business ecosystem in Jaipur has led to a growing need for specialized cyber security services. Local providers like 3Handshake understand the unique challenges faced by businesses in the region and offer customized solutions.
Some reasons to choose cyber security Jaipur services from like 3Handshake include:
Cost-Effective Solutions: Tailored to fit the budgets of small and medium-sized businesses.
Local Expertise: Providers have an in-depth understanding of regional cyber threats.
24/7 Support: Many companies offer round-the-clock monitoring and support to handle emergencies.
For businesses in Jaipur, investing in cyber security services in Jaipur is not just about compliance; it's about ensuring long-term success in a competitive digital landscape.
4 notes
·
View notes
Text
Building Your Own Operating System: A Beginner’s Guide
An operating system (OS) is an essential component of computer systems, serving as an interface between hardware and software. It manages system resources, provides services to users and applications, and ensures efficient execution of processes. Without an OS, users would have to manually manage hardware resources, making computing impractical for everyday use.

Lightweight operating system for old laptops
Functions of an Operating System
Operating systems perform several crucial functions to maintain system stability and usability. These functions include:
1. Process Management
The OS allocates resources to processes and ensures fair execution while preventing conflicts. It employs algorithms like First-Come-First-Serve (FCFS), Round Robin, and Shortest Job Next (SJN) to optimize CPU utilization and maintain system responsiveness.
2. Memory Management
The OS tracks memory usage and prevents memory leaks by implementing techniques such as paging, segmentation, and virtual memory. These mechanisms enable multitasking and improve overall system performance.
3. File System Management
It provides mechanisms for reading, writing, and deleting files while maintaining security through permissions and access control. File systems such as NTFS, FAT32, and ext4 are widely used across different operating systems.
4. Device Management
The OS provides device drivers to facilitate interaction with hardware components like printers, keyboards, and network adapters. It ensures smooth data exchange and resource allocation for input/output (I/O) operations.
5. Security and Access Control
It enforces authentication, authorization, and encryption mechanisms to protect user data and system integrity. Modern OSs incorporate features like firewalls, anti-malware tools, and secure boot processes to prevent unauthorized access and cyber threats.
6. User Interface
CLI-based systems, such as Linux terminals, provide direct access to system commands, while GUI-based systems, such as Windows and macOS, offer intuitive navigation through icons and menus.
Types of Operating Systems
Operating systems come in various forms, each designed to cater to specific computing needs. Some common types include:
1. Batch Operating System
These systems were widely used in early computing environments for tasks like payroll processing and scientific computations.
2. Multi-User Operating System
It ensures fair resource allocation and prevents conflicts between users. Examples include UNIX and Windows Server.
3. Real-Time Operating System (RTOS)
RTOS is designed for time-sensitive applications, where processing must occur within strict deadlines. It is used in embedded systems, medical devices, and industrial automation. Examples include VxWorks and FreeRTOS.
4 Mobile Operating System
Mobile OSs are tailored for smartphones and tablets, offering touchscreen interfaces and app ecosystems.
5 Distributed Operating System
Distributed OS manages multiple computers as a single system, enabling resource sharing and parallel processing. It is used in cloud computing and supercomputing environments. Examples include Google’s Fuchsia and Amoeba.
Popular Operating Systems
Several operating systems dominate the computing landscape, each catering to specific user needs and hardware platforms.
1. Microsoft Windows
It is popular among home users, businesses, and gamers. Windows 10 and 11 are the latest versions, offering improved performance, security, and compatibility.
2. macOS
macOS is Apple’s proprietary OS designed for Mac computers. It provides a seamless experience with Apple hardware and software, featuring robust security and high-end multimedia capabilities.
3. Linux
Linux is an open-source OS favored by developers, system administrators, and security professionals. It offers various distributions, including Ubuntu, Fedora, and Debian, each catering to different user preferences.
4. Android
It is based on the Linux kernel and supports a vast ecosystem of applications.
5. iOS
iOS is Apple’s mobile OS, known for its smooth performance, security, and exclusive app ecosystem. It powers iPhones and iPads, offering seamless integration with other Apple devices.
Future of Operating Systems
The future of operating systems is shaped by emerging technologies such as artificial intelligence (AI), cloud computing, and edge computing. Some key trends include:
1. AI-Driven OS Enhancements
AI-powered features, such as voice assistants and predictive automation, are becoming integral to modern OSs. AI helps optimize performance, enhance security, and personalize user experiences.
2. Cloud-Based Operating Systems
Cloud OSs enable users to access applications and data remotely. Chrome OS is an example of a cloud-centric OS that relies on internet connectivity for most functions.
3. Edge Computing Integration
With the rise of IoT devices, edge computing is gaining importance. Future OSs will focus on decentralized computing, reducing latency and improving real-time processing.
4. Increased Focus on Security
Cyber threats continue to evolve, prompting OS developers to implement advanced security measures such as zero-trust architectures, multi-factor authentication, and blockchain-based security.
3 notes
·
View notes
Text
**From PCI DSS to HIPAA: Ensuring Compliance with Robust IT Support in New York City**
Introduction
In contemporary digital world, organisations are a growing number of reliant on science for their operations. This dependence has caused a heightened focus on cybersecurity and compliance specifications, specifically in regulated industries like healthcare and finance. For services working in New York City, wisdom the nuances of compliance frameworks—specifically the Payment Card Industry Data Security Standard (PCI DSS) and the Health Insurance Portability and Accountability Act (HIPAA)—is quintessential. Navigating those policies requires potent IT give a boost to, which encompasses everything from community infrastructure to documents management.
With the rapid advancement of technological know-how, organizations ought to additionally remain abreast of high-quality practices in details technologies (IT) give a boost to. This article delves into how organizations can ensure that compliance with PCI DSS and HIPAA thru triumphant IT processes whilst leveraging materials from accurate providers like Microsoft, Google, Amazon, and others.
Understanding PCI DSS What is PCI DSS?
The https://brooksxaoj631.over.blog/2025/04/navigating-cybersecurity-in-the-big-apple-essential-it-support-solutions-for-new-york-businesses.html Payment Card Industry Data Security Standard (PCI DSS) is a group of safety principles designed to look after card tips all the way through and after a economic transaction. It was once proven by using significant credit card enterprises to fight growing times of fee fraud.
Why is PCI DSS Important?
Compliance with PCI DSS enables groups defend touchy economic recordsdata, thereby modifying visitor trust and slicing the possibility of info breaches. Non-compliance can bring about intense consequences, such as hefty fines or maybe being banned from processing credit score card transactions.

youtube
Key Requirements of PCI DSS Build and Maintain a Secure Network: This carries fitting a firewall to preserve cardholder knowledge. Protect Cardholder Data: Encrypt kept files and transmit it securely. Maintain a Vulnerability Management Program: Use antivirus utility and develop protect structures. Implement Strong Access Control Measures: Restrict entry to in basic terms people that want it. Regularly Monitor and Test Networks: Keep observe of all get admission to to networks and aas a rule look at various protection tactics. Maintain an Information Security Policy: Create insurance policies that cope with defense necessities. Exploring HIPAA Compliance What is HIPAA?
The Health Insurance Portability and Accountability Act (HIPAA) sets the ordinary for conserving sensitive sufferer know-how in the healthcare trade. Any entity that offers with blanketed well being know-how (PHI) have got to adjust to HIPAA regulations.
Importance of HIPAA Compliance
HIPAA compliance no longer handiest protects affected person privateness however also guarantees more suitable healthcare outcome with the aid of permitting maintain sharing of affected person data between permitted entities. Violations can cause titanic fines, prison results, and wreck to popularity.
" style="max-width:500px;height:auto;">

Core Components of HIPAA Compliance Privacy Rule: Establishes countr
2 notes
·
View notes