#Open-source intelligence (OSINT)
Explore tagged Tumblr posts
Text
استشارة: “أريد أن أتحرَّر، لديّ قدرة على التعلم السريع الحمد لله ولكنّي في حالة تَيه شديدة”
السلام عليكم، وبسم الله. وصلني عبر واتساب السؤال التالي: السلام عليكم ورحمة الله.أتمنى أن تكون بخير، أنا في حاجة لمساعدتك أستاذ يونس، سأحكي قصتي لتسطيع مساعدتي وأحاول أن أختصر عليك.منذ كنت أدرس في الثانوية العامة لظرف ما تأخرت عن زملائي ولم أدخل الامتحانات لمدة ثلات أعوام على التوالي، اصابني الإحباط شديدا لتأخري هذا، ومن ثم ألتحقت بكلية الآداب فاقدة الشغف تجاه كل شيء لأنها ما كانت رغبتي، تخطيت…
#Open-source intelligence (OSINT)#OSINT#قناة يونس بن عمارة#يوتيوب#الاستخبارات المفتوحة#استشارة#استشارة مجانية#جواب وسؤال#خطة حياة#علاج التوهان#علاج التيه
0 notes
Text
The Expanding Role of Open-Source Intelligence (OSINT) in Modern Cybersecurity
The digital age has revolutionized the way individuals, organizations, and governments access and share information. However, it has also introduced unprecedented risks. Cybercriminals exploit vulnerabilities with increasing sophistication, prompting security professionals to develop equally advanced defense strategies. One such powerful strategy is Open-Source Intelligence a practice that involves gathering and analyzing publicly available data to identify threats, assess risks, and inform decision-making.

Once considered the realm of state intelligence agencies, OSINT has now become an essential component of corporate and organizational cybersecurity frameworks. As cyberattacks grow more targeted and complex, OSINT offers a proactive, cost-effective, and legally sound method of defending assets, infrastructure, and reputation.
In this blog, we will delve into the foundational principles of OSINT, examine how it contributes to threat detection and response, and explore its broader role within modern cybersecurity architectures.
What is OSINT?
Open-Source Intelligence (OSINT) refers to the process of collecting, analyzing, and using information that is publicly available to identify and mitigate potential threats. This data can come from a wide range of sources, including:
News articles and public records
Social media platforms
Internet forums and blogs
Government reports and press releases
WHOIS databases and DNS records
Paste sites and code repositories
Dark web forums and marketplaces
Importantly, OSINT excludes data acquired through illicit or unauthorized means. It relies solely on legally accessible sources, making it an ethical and compliant method of intelligence gathering.
Organizations use OSINT to track cyber threats, monitor brand reputation, detect data breaches, and assess the digital footprint of their infrastructure. It serves as the foundation for informed risk assessment and strategic cybersecurity planning.
The Evolution of OSINT in Cybersecurity
OSINT was originally a military and national intelligence discipline, used to track political movements, enemy strategies, and global threats. Over time, the methods developed by national intelligence agencies trickled down into the private sector. The rise of cybercrime, hacktivism, insider threats, and state-sponsored cyber espionage has driven commercial enterprises to adopt OSINT practices.
With the democratization of information, cybersecurity analysts now have access to more data than ever before. Tools and platforms have evolved to aggregate and analyze data in real-time, offering insights that were once difficult, if not impossible, to obtain without significant manual effort.
Today, cybersecurity teams use OSINT to:
Identify leaked credentials and stolen data
Track phishing campaigns and malware infrastructure
Map adversaries’ digital behavior and communication patterns
Monitor insider threats and suspicious insider activity
Conduct vulnerability assessments on exposed infrastructure
Benefits of Leveraging OSINT
The value proposition of OSINT in cybersecurity is multifaceted. From preemptive threat detection to enhanced situational awareness, OSINT helps organizations become more resilient in a threat-laden digital landscape.

1. Cost Efficiency
Unlike proprietary data feeds or expensive cybersecurity platforms, most OSINT sources are free. This allows even smaller organizations to benefit from valuable threat intelligence without breaking their budgets.
2. Timely Intelligence
OSINT provides real-time or near-real-time information. This immediacy enables organizations to respond quickly to emerging threats before they escalate into full-blown breaches.
3. Breadth and Depth of Data
The internet is a vast ocean of data. OSINT taps into this data from various angles—technical, strategic, social, and operational—offering a holistic view of the threat landscape.
4. Legal and Ethical Intelligence
Since OSINT only uses publicly available data, it does not violate privacy laws or corporate policies, making it a legally defensible intelligence-gathering method.
5. Customizability
Whether you are looking to protect customer data, monitor employee behavior, or assess vendor risk, OSINT can be tailored to meet specific organizational needs.
OSINT Collection Methods and Tools
To efficiently gather and analyze open-source data, cybersecurity professionals utilize a range of tools, techniques, and platforms. OSINT collection typically falls into two main categories:
1. Manual Techniques
These involve hands-on research using search engines, social media platforms, WHOIS lookup tools, and other freely accessible websites. Analysts may create fake accounts (sock puppets) to investigate adversaries or gather information from closed groups and forums.
2. Automated Tools
Automated OSINT tools can scrape, aggregate, and analyze data at scale, saving significant time and effort. Some popular tools include:
Maltego: A visual link analysis tool used for mapping relationships across digital entities
TheHarvester: A tool for gathering emails, subdomains, hosts, and employee names from public sources
SpiderFoot: An automation tool for collecting data on IPs, domains, emails, and more
Shodan: A search engine for finding internet-connected devices and identifying vulnerabilities
Recon-ng: A full-featured web reconnaissance framework
These tools often integrate with data APIs, making it possible to fuse OSINT with threat feeds, vulnerability databases, and incident response platforms.
The Role of OSINT in Threat Detection and Response
At the heart of cybersecurity is the ability to detect and respond to threats quickly and effectively. OSINT plays a pivotal role in enhancing this capability. Here’s how:
1. Early Warning System
OSINT can serve as an early warning system by identifying indicators of compromise (IOCs) such as domain spoofing, credential leaks, or planned cyberattacks. Security teams can investigate anomalies and neutralize threats before damage occurs.
2. Incident Enrichment
During incident response, OSINT can be used to enrich internal logs and telemetry data with external context. For example, correlating a suspicious IP with known threat actor infrastructure can improve attribution and incident classification.
3. Threat Attribution
By analyzing digital footprints and communication patterns, OSINT helps identify the actors behind cyberattacks. This is particularly useful in tracking hacktivist groups, state-sponsored actors, or organized cybercriminals.
4. Vulnerability Management
Security teams can use OSINT to find public disclosures of vulnerabilities in their technology stack. For instance, discovering a GitHub repository that mentions your product with an exploit can trigger a patch or mitigation workflow.
OSINT and the Threat Intelligence Ecosystem
While OSINT is powerful on its own, its true value is realized when integrated into a broader Threat Intelligence Platform. Such platforms aggregate data from internal telemetry, paid threat feeds, endpoint detection systems, and OSINT to form a centralized threat picture.
The synergy between OSINT and threat intelligence enables:
Faster identification of emerging threats
Better contextualization of security alerts
Smarter prioritization of response actions
More accurate risk assessments for decision-makers
When combined with automation and machine learning, OSINT can power predictive analytics, alert triaging, and dynamic threat scoring.
Challenges and Limitations of OSINT
Despite its numerous advantages, OSINT is not without its challenges. Organizations must be aware of the limitations to make the most of this intelligence discipline.

1. Volume and Noise
The sheer volume of publicly available data makes it difficult to separate signal from noise. Effective filtering and correlation mechanisms are essential.
2. False Positives
Not all public information is accurate. Misinformation, outdated content, and deliberate deception can lead to false conclusions.
3. Data Validation
OSINT must be cross-referenced with trusted sources to validate findings. Failure to do so may result in costly mistakes or misattribution.
4. Privacy and Ethics
While OSINT uses public data, ethical boundaries must be respected—especially when dealing with social media, forums, or employee information.
5. Tool Proficiency
Many OSINT tools require specialized knowledge. Organizations must invest in training and upskilling analysts to use these tools effectively.
Use Cases Across Industries
OSINT has found applications beyond cybersecurity. Its flexibility allows it to be adapted for use across diverse sectors, including:
1. Finance
Banks use OSINT to detect fraud, monitor geopolitical risk, and assess the digital exposure of high-net-worth clients.
2. Healthcare
Healthcare organizations monitor the dark web for leaked patient records, exposed medical devices, and phishing campaigns targeting staff.
3. Retail
Retailers leverage OSINT to track counterfeit goods, detect brand impersonation, and investigate supply chain threats.
4. Government
Government agencies use OSINT for law enforcement, border security, counterterrorism, and diplomatic risk assessment.
Integrating OSINT with Digital Risk Protection
A robust Digital Risk Protection strategy incorporates OSINT to monitor external digital environments for threats to brand, data, and infrastructure. This includes:
Scanning the dark web for stolen credentials
Monitoring social media for executive impersonation
Tracking data leaks in third-party vendor networks
Identifying malicious mobile apps or websites
By continuously scanning the surface, deep, and dark web, organizations can maintain visibility into their external threat surface and respond proactively to digital risks.
OSINT and Cyber Threat Analysis
OSINT is a foundational element of Cyber Threat Analysis. By enriching internal security data with external context, analysts can uncover the intent, tactics, techniques, and procedures (TTPs) of threat actors.
For example, correlating internal network anomalies with chatter from a hacker forum discussing a new exploit enables quicker and more targeted threat hunting. Similarly, mapping a phishing domain to known infrastructure can reveal broader attack campaigns.
OSINT feeds also help identify recurring patterns and attack timelines, supporting long-term security strategy development.
The Future of OSINT: AI, Automation, and Integration
The future of OSINT lies in deeper automation, smarter algorithms, and seamless integration with cybersecurity ecosystems. Advances in artificial intelligence and machine learning are enhancing OSINT's capabilities by:
Automatically detecting anomalies across vast data sets
Predicting potential attack vectors based on threat actor behavior
Categorizing and tagging OSINT findings for better decision-making
As organizations move toward zero-trust architectures and continuous threat monitoring, OSINT will become an indispensable part of their security arsenal.
Conclusion
Open-Source Intelligence (OSINT) has emerged as a crucial tool for detecting, analyzing, and mitigating cyber threats in an increasingly complex digital world. It provides organizations with a cost-effective, legally compliant, and real-time method of understanding their threat landscape. When combined with internal telemetry, automation, and broader threat intelligence efforts, OSINT can significantly enhance cybersecurity postures.
At DeXpose, we empower organizations to harness the full potential of OSINT and integrate it seamlessly with their broader threat detection and response strategies. With rising digital risks and cyber threats targeting every industry, adopting an OSINT-driven approach isn’t just a competitive advantage—it’s a necessity.
If you’d like to explore how OSINT and advanced threat intelligence can protect your organization, contact DeXpose today for a consultation and demo.
0 notes
Text
#Open Source Intelligence (OSINT) Market report#Open Source Intelligence (OSINT) Market growth#Open Source Intelligence (OSINT) Market size
0 notes
Text
#Open-Source Intelligence (OSINT) Market#Open-Source Intelligence (OSINT) Market Scope#Open-Source Intelligence (OSINT) Market Analysis#Open-Source Intelligence (OSINT) Market Trends
0 notes
Text
Armchair military enthusiasts can only cause a nuclear cacophony
By N. C. Bipindra As a rookie in journalism three decades ago, the first lesson given to us by our seniors and editors was that ‘Dog bites man is not news, but man bites dog is, and that is a goldmine.’ Many of us, who have transitioned from print to electronic media and now social media journalism, have learned that such sensationalism may not always accrue benefits. While in the short term,…
#Arihant#Defence#Defense#Dhanush#FAS#India#Indian Navy#INS Subhadra#INS Suvarna#International Yoga Day#Maritime#Military#Missiles#Naval#Navy#Nuclear#Offshore Patrol Vessel#Open Source Intelligence#OPV#OPVs#OSINT#Seychelles#SSBN#SSBNs#Submarine#Yoga
0 notes
Text
The world of corporate intelligence has quietly ballooned into a market valued at over $20 billion. The Open Source Intelligence (OSINT) market alone, valued at around $9.81 billion in 2024. This exponential growth reflects an important shift: intelligence gathering, once the exclusive domain of nation-states, has been privatized and commodified. [...] The methods these firms employ have evolved into a sophisticated doctrine that combines centuries-old espionage techniques with new technology. Understanding their playbook is important to grasping how democracy itself is being undermined. [...] This practice is disturbingly widespread. A report by the Center for Corporate Policy titled “Spooky Business” estimated that as many as one in four activists in some campaigns may be corporate spies. The report documented how “a diverse array of nonprofits have been targeted by espionage, including environmental, anti-war, public interest, consumer, food safety, pesticide reform, nursing home reform, gun control, social justice, animal rights and arms control groups.” The psychological doctrine these firms follow was laid bare in leaked Stratfor documents. Their manual for neutralizing movements divides activists into four categories, each with specific tactics for neutralization: 1. Radicals: Those who see the system as fundamentally corrupt. The strategy is to isolate and discredit them through character assassination and false charges, making them appear extreme and irrational to potential supporters. 2. Idealists: Well-meaning individuals who can be swayed by data. The goal is to engage them with counter-information, confuse them about facts, and gradually pull them away from the radical camp toward more “realistic” positions. 3. Realists: Pragmatists willing to work within the system. Corporations are advised to bargain with them, offering small, symbolic concessions that allow them to claim victory while abandoning larger systemic changes. 4. Opportunists: Those involved for personal gain, status, or excitement. These are considered the easiest to neutralize, often bought off with jobs, consulting contracts, or other personal benefits. [...] Some firms have industrialized specific tactics into product offerings. According to industry sources, “pretexting” services — where operatives pose as someone else to extract information — run $500-$2,000 per successful operation. Trash collection from target residences (“dumpster diving” in industry parlance) is billed at $200-$500 per retrieval. Installing GPS trackers runs $1,000-$2,500 including equipment and monitoring. The most chilling aspect is how these costs compare to their impact. For less than a mid-level executive’s annual salary, a corporation can fund a year-long campaign to destroy a grassroots movement. For the price of a Super Bowl commercial, they can orchestrate sophisticated operations that neutralize threats to their business model. Democracy, it turns out, can be subverted for less than the cost of a good law firm.
67 notes
·
View notes
Text

Pentagon’s Pizza Index has accurately predicted 21 global crises since 1983
As tensions rise in the Middle East, a curious, crowd-driven theory known as the “Pentagon Pizza Index” has caught fire online.
On June 12 and 13, users on X (formerly Twitter) reported a sudden spike in pizza deliveries near the Pentagon and Department of Defense in Washington, D.C., sparking speculation that the United States may be quietly entering crisis mode behind closed doors.
The timing? Just hours before Israel reportedly struck targets in Iran in response to Tehran’s earlier drone and missile attacks. And once again, pizza orders were booming.
Cold war roots of the pizza theory. What began as a Soviet spy trick is now a digital-age meme
The idea isn’t new. During the Cold War, Soviet operatives observed pizza delivery activity in Washington, believing it signalled crisis preparation inside U.S. intelligence circles. They coined it “Pizzint” — short for pizza intelligence.
This tactic entered public lore on 1 August 1990, when Frank Meeks, a Domino’s franchisee in Washington, noticed a sudden surge in deliveries to CIA buildings. The next day, Iraq invaded Kuwait. Meeks later told the Los Angeles Times he saw a similar pattern in December 1998 during the impeachment hearings of President Bill Clinton.

As former CNN Pentagon correspondent Wolf Blitzer once joked in 1990, “Bottom line for journalists: Always monitor the pizzas.”
WWIII warning: What is the Pentagon Pizza Index today? A meme, an OSINT tool, or a symptom of digital-age paranoia?
The modern Pentagon Pizza Index is tracked through open-source intelligence (OSINT) tools. These include Google Maps, which shows real-time restaurant activity, and social media observations. Pages like @PenPizzaReport on X have dedicated themselves to watching for abnormal patterns.
On 1 June 2025, the account posted, “With less than an hour to go before closing time, the Domino’s closest to the Pentagon is experiencing unusually high footfall.”
A few hours later, reports emerged of a fresh escalation between Israel and Iran. For believers in the theory, it was yet another sign that something bigger was underway.
The April 2024 pizza spike. A recent example that reignited interest
The most notable recent instance occurred on 13 April 2024, the night Iran launched a massive drone and missile strike against Israel. That same evening, screenshots from delivery platforms showed pizzerias around the Pentagon, White House, and Department of Defense tagged as “busier than usual.”

Multiple Papa John’s and Domino’s branches reported increased orders. The correlation prompted viral memes and renewed interest in the theory.
According to Euro News, a user on X posted on 13 June 2025, “The Pentagon Pizza Index is hiking.”
Inside the logic: Why pizza? Food, fatigue and national security
The concept is deceptively simple. When military staff face a national emergency, they work longer shifts and can’t leave their posts. They need quick, filling food — and pizza fits the bill.
Studies in behavioural psychology show that under stress, people prefer calorie-dense, familiar comfort foods. During high-alert operations, officials may work 16–20 hour days. That creates a visible consumption spike that outsiders can track.
And because platforms like Google and Uber Eats share real-time data on restaurant activity, amateur analysts can monitor these patterns — no hacking required.
World War III: Pizza as a proxy for preparedness. It’s not perfect, but it’s consistent
The Pentagon Pizza Index isn’t a foolproof system. It could easily be triggered by something mundane: a long staff meeting, a software glitch, or a nearby college football game.
That’s why modern OSINT analysts often cross-reference pizza spikes with other indicators — like unusual aircraft movements, ride-hailing activity, or power usage near government buildings. When multiple signs align, it suggests more than coincidence.
As a senior analyst put it: “You can’t bank a war call on a pizza. But if the Pentagon’s burning the midnight oil and feeding everyone, it’s worth a second look.”
Official silence, public curiosity. What the US government says — and doesn’t say
Despite the chatter online, the US government has made no mention of pizza deliveries as indicators of crisis.
Responding to speculation about American involvement in Israel’s airstrikes on Iran, Republican Senator Marco Rubio said:
“We are not involved in strikes against Iran, and our top priority is protecting American forces in the region. Israel advised us that they believe this action was necessary for its self-defence.”
Still, the Pentagon’s silence on the pizza theory hasn’t stopped internet users from speculating.
Humour meets anxiety in the age of digital vigilance
In an age where open-source tools let ordinary people track the movement of jets, ships, and even pizzas, the Pentagon Pizza Index sits at the bizarre intersection of humour and fear. It turns snack food into a warning system.
It’s also a reminder: not all intelligence requires a badge. Sometimes, the clue might be just down the road — in a Domino’s queue.
Whether you see it as absurd or insightful, one thing is clear: when the pizzas fly, people pay attention.
Daily inspiration. Discover more photos at Just for Books…?
75 notes
·
View notes
Text
How does propaganda look like?
Let's take a look, this time at CCP propaganda.


Bloomberg and France 24 both published an article about the "success of Chinese jets used against India in the recent conflict between India and Pakistan".
Damien Symon, a globally recognized independent OSINT (Open-Source Intelligence) expert, used satellite imagery to dismantle propaganda from Pakistan and China. His findings revealed the destruction of Pakistani airbases, along with Chinese-made radars, air defense systems, and fighter jets stored in hangars, following India’s strikes.
links here and here
Maxar Technologies, a company that provides satellite imagery and data, has confirmed losses of Pakistani air assets guarded by Chinese radars and air defence.
Journalist Yalda Hakim and her Sky News team investigated terror camps in Muridke, Pakistan, uncovering evidence of their existence through social media posts linked to groups like Lashkar-e-Taiba. Their report exposed Pakistani officials’ evasive responses and lack of proof to counter claims of supporting terrorism.


The authors of the Bloomberg article changed after an update. What was the purpose of adding an Indian sounding name to the Bloomberg article when the content of the actual article didn't change?
Let's take a look at the France24 article, which claimed that Chinese jets beat French jets. It was written by reporter Leela Jacinto (who, according to France24, has won awards for her reportage)


Leela Jacinto wrote an article where she entirely dismisses the systematic, state sponsored attacks against the Hindu minority in Bangladesh after ex-PM Hasina's abdication. after having a closer look at her portfolio, it all starts making sense. 


India (and world), are you awake? The CCP has bought journalists and traditional media to parrot their propaganda. Do you understand how dangerous this is? we live in a post–truth world where fake news sell like hot cakes. it is obvious that Pakistan would never admit their defeat. They hardly admitted that they lost when East-Pakistan (Bangladesh) seceded. However, what horse in the race does the western media have in this? The west, that claims that it strives to uphold journalistic integrity, has easily sold itself to the lies of CCP. Lies which may even cost human lives. 
If you read all the way to the end, thank you so much. If you liked this blog about the Indo-Pak conflict, then I would recommend you to take a look at this and this too! 🙏🏼
#desiblr#india#hindublr#pakistan#india pakistan conflict#india pakistan#india pakistan war#operation sindoor#bunyanul marsoos#pakistani propaganda#ccp propaganda#geopolitics#propaganda war#propaganda#agitprop#journalism#5gw#desi tumblr#desi tag#desi#news#indo pak#indo pak war#osint
33 notes
·
View notes
Text
IN THE WAKE of Hamas’ deadly attacks on Israel this weekend—and the Israeli military’s response—journalists, researchers, open source intelligence (OSINT) experts, and fact-checkers rushed to verify the deluge of raw video footage and images being shared online by people on the ground. But users of X (formerly Twitter) seeking information on the conflict faced a flood of disinformation.
While all major world events are now accompanied almost instantly by a deluge of disinformation aimed at controlling the narrative, the scale and speed at which disinformation was being seeded about the Israel-Hamas conflict is unprecedented—particularly on X.
“For many reasons, this is the hardest time I’ve ever had covering a crisis on here,” Justin Peden, an OSINT researcher from Alabama known online as the Intel Crab, posted on X. “Credible links are now photos. On the ground news outlets struggle to reach audiences without an expensive blue check mark. Xenophobic goons are boosted by the platform’s CEO. End times, folks.”
Rather than being shown verified and fact-checked information, X users were presented with video game footage passed off as footage of a Hamas attack and images of firework celebrations in Algeria presented as Israeli strikes on Hamas. There were faked pictures of soccer superstar Ronaldo holding the Palestinian flag, while a three-year-old video from the Syrian civil war repurposed to look like it was taken this weekend.
As a result, Peden says that he and his fellow OSINT researchers have to spend their time debunking years-old content rather than verifying and sharing real footage from the conflict.
Many of these videos and images racked up hundreds of thousands of views and engagements. While some later featured a note from X’s decimated community fact-checking system, many more remained untouched. And as Elon Musk has repeatedly done in recent incidents, the platform’s CEO made the situation much worse.
(continue reading)
171 notes
·
View notes
Text
The "Israel" X account tweeted on Tuesday night what it said was evidence of PIJ culpability in the attack, saying that “from the analysis of the operational systems of the IDF, an enemy rocket barrage was carried out towards Israel, which passed through the vicinity of the hospital when it was hit”. However, the original version of the post included a video of rockets fired from the vicinity of Gaza City. The video was later deleted by the account, while analysts noted that the first public mentions of the bombing were at 7.20pm local time, whereas the video shared by Israel as evidence was time-stamped at between 7.59 and 8pm local time. That same account shared audio on Wednesday from the Israeli army claiming to be a conversation between Hamas operatives, in which they discuss the destruction of the hospital and pin it on PIJ. But Muhammad Shehada, a Gaza-based civil rights activist who has reported on Hamas for a decade, posted that the quote had been mistranslated from "they're saying" to "we're saying". "He's describing a rumour, not evidence," Shehada wrote, before going on to list other reasons for believing the audio was part of a campaign of misinformation. Alex Thomson, a correspondent for Channel 4 News, said "several experts" had told him the "audio tape of 'Hamas' operatives talking about the missile malfunction is a fake. They say the tone, syntax, accent and idiom are absurd." "They shot it from the cemetary behind the hospital," one of them can be heard saying. Francesco Sebregondi, an architect and researcher currently with the investigative NGO Index, told Middle East Eye that Israel was keen to provide material quickly for analysts to pin their conclusions on. "By quickly providing a number of poorly substantiated 'evidence' in the form of, for example, drone footage of the site, the Israeli army may also be counting on the eagerness of some Open Source Intelligence (OSINT) actors to use any image/material/data to quickly publish new content, or 'analysis' and thereby more or less directly support its version of the events," he said.
223 notes
·
View notes
Text
In the hours after Iran announced its drone and missile attack on Israel on April 13, fake and misleading posts went viral almost immediately on X. The Institute for Strategic Dialogue (ISD), a nonprofit think tank, found a number of posts that claimed to reveal the strikes and their impact, but that instead used AI-generated videos, photos, and repurposed footage from other conflicts which showed rockets launching into the night, explosions, and even President Joe Biden in military fatigues.
Just 34 of these misleading posts received more than 37 million views, according to ISD. Many of the accounts posting the misinformation were also verified, meaning they have paid X $8 per month for the “blue tick” and that their content is amplified by the platform’s algorithm. ISD also found that several of the accounts claimed to be open source intelligence (OSINT) experts, which has, in recent years, become another way of lending legitimacy to their posts.
One X post claimed that “WW3 has officially started,” and included a video seeming to show rockets being shot into the night—except the video was actually from a YouTube video posted in 2021. Another post claimed to show the use of the Iron Dome, Israel's missile defense system, during the attack, but the video was actually from October 2023. Both these posts garnered hundreds of thousands of views in the hours after the strike was announced, and both originated from verified accounts. Iranian media also shared a video of the wildfires in Chile earlier this year, claiming it showed the aftermath of the attacks. This, too, began to circulate on X.
“The fact that so much mis- and disinformation is being spread by accounts looking for clout or financial benefit is giving cover to even more nefarious actors, including Iranian state media outlets who are passing off footage from the Chilean wildfires as damage from Iranian strikes on Israel to claim the operation as a military success,” says Isabelle Frances-Wright, director of technology and society at ISD. “The corrosion of the information landscape is undermining the ability of audiences to distinguish truth from falsehood on a terrible scale.”
X did not respond to a request for comment by time of publication.
Though misinformation around conflict and crises has long found a home on social media, X is often also used for vital real-time information. But under Elon Musk’s leadership, the company cut back on content moderation, and disinformation has thrived. In the days following the October 7 Hamas attack, X was flooded with disinformation, making it difficult for legitimate OSINT researchers to surface information. Under Musk, X has promoted a crowdsourced community notes function as a way to combat misinformation on the platform to varying results. Some of the content identified by ISD has since received community notes, though only two posts had by the time the organization published its findings.
“During times of crisis it seems to be a repeating pattern on platforms such as X where premium accounts are inherently tainting the information ecosystem with half-truths as well as falsehoods, either through misidentified media or blatantly false imagery suggesting that an event has been caused by a certain actor or state,” says Moustafa Ayad, ISD executive director for Asia, the Middle East, and Africa. “This continues to happen and will continue to happen in the future, making it even more difficult to know what is real and what is not.”
And for those that are part of X’s subscription model and ad revenue sharing model, going viral could potentially mean making money.
Though it’s not clear that any of the users spreading fake or misleading information identified by ISD were monetizing their content, a separate report released by the Center for Countering Digital Hate (CCDH) earlier this month found that between October 7 and February 7, 10 influencers, including far-right influencer Jackson Hinkle, were able to grow their followings by posting antisemitic and Islamophobic content about the conflict. Six of the accounts CCDH examined were part of X’s subscription program, and all 10 were verified users. The high-profile influencers who are part of X’s ad revenue sharing program receive a cut of advertising revenue based on ”organic impressions of ads displayed in replies” to their content, according to the company.
40 notes
·
View notes
Text
#Open Source Intelligence (OSINT) Market trends#Open Source Intelligence (OSINT) Market growth#Open Source Intelligence (OSINT) Market share
0 notes
Text
#Open-Source Intelligence (OSINT) Market#Open-Source Intelligence (OSINT) Market Analysis#Open-Source Intelligence (OSINT) Market Scope#Open-Source Intelligence (OSINT) Market Trends
0 notes
Text
https://www.globenewswire.com/news-release/2025/01/09/3007089/0/en/Open-Source-Intelligence-OSINT-Market-Poised-for-Explosive-Growth-of-USD-62-99-billion-by-2032-Driven-by-Cybersecurity-Demand-and-Advanced-Data-Analytics-Solutions-Research-By-SNS-.html
0 notes
Text
Claim: Did Mahmoud Khalil hire an "American-looking" woman to pose as his wife?
Veridct: False conspiracy theory bullshit. Obviously.
Weird racists, of both the Netanyahu & Trump supporter variety, are trying to discredit the outrage around Khalil by claiming that he hired a "fake wife" who looked "more American" to appear at a press conference.


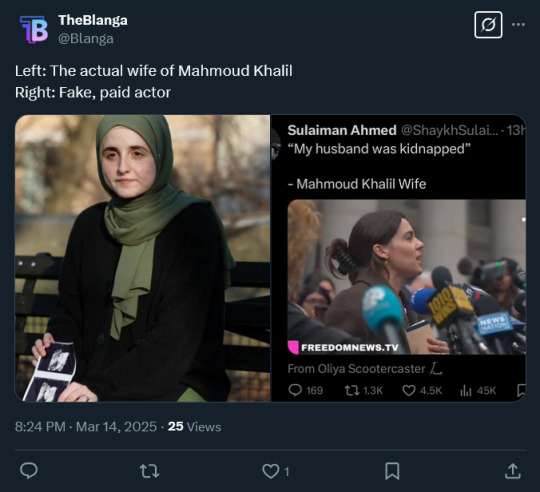
Obviously, this isn't true. Notably, every post about this uses exclusively images - even though the original tweet is a video. And if we watch the video...

...it's his lawyer. Of course it is. The entire framing is nonsense that only works if you're also a weird racist creep, bc what does "Western-looking" even mean?
Now, whoever first shared this knew that - they had to, in order to get the right screencap to lie about its contents. They seized on an admittedly poorly written tweet that included a quote from his wife over a video of his lawyer without making it clear it was the lawyer saying it, making it easy for them to spin a story to gullible conspiracy types about how it's a different woman (I looked up the original post's author, and he is a crypto & Epstein list guy, since that is the only type of guy left on Twitter no matter what else they support). His tweet was copied by "Open Source Intelligence" accounts (if you're only familiar with OSINT from outlets like Bellingcat, it's been a trend that social media platforms, from Twitter to Bluesky, are being flooded by "OSINT" accounts that...just share news videos they see) and spread further, and now it's the crux of the argument of some weird crisis actor conspiracy theory
But it takes about thirty seconds to look up this video & see the immediate caption explaining that she's a lawyer...you know, if you want to do anything but believe it unthinkingly, and hold up that it's Very Suspicious when multiple women stand adjacent to a man at different times, or when women refer to him in a press conference
7 notes
·
View notes