#OpenSearch
Explore tagged Tumblr posts
Text
EC2 I4i Instances: Increasing Efficiency And Saving Money

Efficient and economical search capabilities are essential for developers and organizations alike in today’s data-driven environment. The underlying infrastructure may have a big influence on costs and performance, whether it’s used for real-time search functions or complicated searches on big databases.
Businesses need to strike a compromise between budgetary limitations and performance, data scientists need to get data efficiently for their models, and developers need to make sure their apps are both dependable and speedy.
For applications requiring a lot of storage, Amazon EC2 I3 instances powered by Intel Xeon Scalable Processors and I4i instances powered by 3rd Gen Intel Xeon Scalable processors offer a solid mix of computation, memory, network, and storage capabilities. Cloud architects and clients may choose the best option that balances cost and performance by contrasting these two storage-optimized instance types.
Boosting Throughput and Efficiency with OpenSearch
Developers, data scientists, and companies looking for robust search and analytics capabilities are fond of OpenSearch, an open-source search and analytics package. It is a flexible tool because of its sophisticated search features, strong analytics, and capacity for handling massive data volumes with horizontal scalability. Many firms use OpenSearch because it provides transparency, flexibility, and independence from vendor lock-in.
It can chose to thoroughly examine the OpenSearch histogram aggregation speed and cost for AWS’s storage-optimized I3 instances and I4i instances due to its widespread usage. Professionals from a variety of backgrounds who want to maximize productivity and minimize expenses in OpenSearch implementations must comprehend the distinctions between these cases.
I4i instances powered by 3rd generation Intel Xeon Scalable processors provide:
Quicker memory
Greater cache size
Improved IPC performance brought about by new architecture and processes
Testing AWS Instances Powered by Intel
Using the OpenSearch Benchmark tool, Intel tested the assessed instances’ cost-effectiveness and performance, paying particular attention to two important performance metrics:
Histogram aggregation throughput: The quantity of operations per second that reveal how well the instances can manage big amounts of data.
Resource utilization: Evaluates how well CPU, memory and storage are used; this affects scalability and total cost.
Intel utilized data from yellow cab trips in New York City in 2015 (from the nyc_taxis workload) to assess the instances’ performance in managing demanding search and aggregation operations. With 165 million documents and 75 GB in total, this dataset offered a significant and realistic test situation.
It used Amazon Web Services (AWS) cloud storage-optimized (I) instance types for to the investigation. To oversee the activities, the cluster was set up with three data nodes, one coordinating node, and one cluster management node. To create the workload, a different client node was configured with the benchmark application was taken from the OpenSearch benchmark repository.
It set the heap size of the Java Virtual Machine (JVM) to 50% of the RAM that is available on each node in order to maximize Java performance. To better fit OpenSearch’s I/O patterns, it also changed the flush Tran slog threshold size from the default 512 MB to a fourth of the heap size. In order to facilitate more effective indexing operations, the index buffer size was also raised from its default value of 10% to 25% of the Java heap size.
Finding the best AWS instance type for OpenSearch jobs was the main objective, with an emphasis on both affordability and raw performance. To isolate the effects of the instance types on performance, the benchmark tests were conducted in a controlled environment with consistent storage and networking characteristics. The performance-per-dollar measure was computed using the related expenses from the AWS area where all instances were installed, which was also the same region utilized for on-demand instances.
Results for Cost-Effectiveness and Performance
While the I4i instances use the more sophisticated 3rd Gen Intel Xeon Scalable CPUs, the I3 instances are powered by Intel Xeon Scalable CPUs. One of the main components of AWS comparison study across the three instance sizes 2xlarge, 4xlarge, and 8xlarge is this difference in processing power.
They standardized the throughput data, using the I3 instances as a baseline for each size, in order to quantify the performance differences across the instance types. They were able to quantify the i4i series’ relative performance enhancements in a straightforward and consistent way thanks to this method.
It discovered that I4i instances, equipped with their 3rd generation Intel Xeon Scalable processors, produced a throughput that was around 1.8 times higher than that of the I3 instances in all cases. This translates to a generation-over-generation improvement in OpenSearch aggregate search throughput of up to 85%.
Intel observed that the I4i machines allowed for almost 60% more queries per dollar spent on average than the earlier I3 instances, in addition to a notable speed benefit. For businesses trying to efficiently control their cloud expenditures, this is a major benefit.
AWS I4i instances
When compared to I3 instances, AWS I4i instances, which are based on 3rd Gen Intel Xeon Scalable processors, provide a more potent mix of value and performance, as well as superior performance. The more recent I4i instance is clearly the better option for enterprises seeking to maximize their OpenSearch installations, grow their business, and service more clients without incurring additional expenses. The Amazon OpenSearch service offers both of the instances covered in this article.
Read more on govindhtech.com
#EC2I4iInstances#IncreasingEfficiency#SavingMoney#databases#AmazonEC2#OpenSearch#IntelXeonScalableprocessors#cloudstorage#memorystorage#AWSinstance#IntelXeonScalableCPU#I4iinstances#aws#intel#BoostingThroughput#technology#technews#news#govindhtech
0 notes
Text
Observing the Observer (Fluent Bit monitoring)
In the Fluent Bit book I touch upon the point that we should be observing the observer. After all, if we don’t monitor our observability stack, then we’ll be operating blind and may never know until things go catastrophically wrong, and we’re getting complaints that production business solutions are down. One of the peer review comments was it would be really good to have a visual representation…
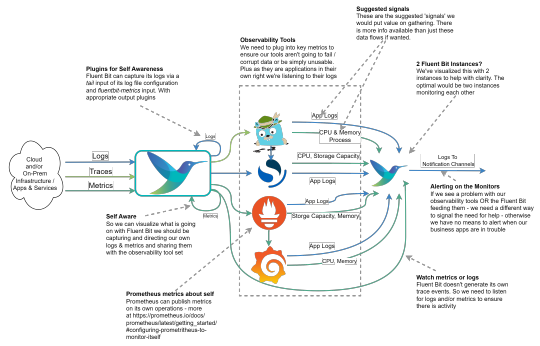
View On WordPress
0 notes
Text
The Circuit Breaker Exception in OpenSearch| AntStack
We had a search functionality requirement in one of the projects and that’s how I got to know about Amazon OpenSearch Service, It provides a quick, relevant search experience and makes it easier to add a search feature to your applications.
The only hiccup is sizing the OpenSearch is a tricky and long-term process, and it often takes many iterations to make sure that you get the right specifications according to your workload. It also needs monitoring so as to be aware of future problems.

0 notes
Text
Lessons learned: Custom Opensearch Dashboards Plugin Security
To determine the user that is signed in when making a request to your plugin server, or in more formal words the “authentication context” of a request you have two options Client Side This is not very secure as it is initiated and consumed by the browser, which is under the complete control of the end user – so do not rely on this method to enforce actions depending on the signed in user as it…
View On WordPress
1 note
·
View note
Text
.
#I'm going to kill the people behind the Graylog documentation#“don't install both the Graylog node and db#and the data node on the same machine “#and then they go on and assume that you're doing it all on the same machine#PROVIDE THE DOCS#also at some point they changed from Opensearch to Datanode#with no indication of what that means practically#I'm going to throw my laptop in a minute#so anyway I'm going to go to Reddit
2 notes
·
View notes
Text
Elasticsearch vs. OpenSearch: Choosing the Right Search Engine
When it comes to robust search engine solutions, Elasticsearch and OpenSearch emerge as top contenders, each offering unique features and community support. Understanding their differences is crucial in selecting the ideal tool for your specific needs.
Understanding Elasticsearch and OpenSearch
Elasticsearch: Built on Apache Lucene, Elasticsearch is renowned for its real-time search capabilities and scalability. It supports advanced search functionalities, near real-time indexing, and complex data analysis through aggregations. Integrated with the Elastic Stack, it facilitates seamless data visualization via Kibana.
OpenSearch: Initially a fork of Elasticsearch, OpenSearch emphasizes a fully open-source approach under the Apache 2.0 license. It retains compatibility with Elasticsearch APIs while focusing on customizable alerting, monitoring, and robust security features. Backed by a thriving community, OpenSearch promotes innovation and community-driven development.
Key Features Comparison
Elasticsearch: Offers distributed search, multi-tenancy, and a rich ecosystem of plugins. It excels in real-time data indexing, RESTful API integration, and comprehensive data visualization.
OpenSearch: Fully open-source with customizable alerting and monitoring. It prioritizes data security and embraces community-driven innovation.
Performance and Community Support
Performance: Elasticsearch provides robust performance optimizations with active development by Elastic. OpenSearch focuses on performance enhancements through community contributions and updates.
Community Support: Elasticsearch boasts a large, established community with extensive documentation and support. OpenSearch benefits from a growing community dedicated to maintaining open-source integrity and fostering innovation.
Licensing and Deployment Considerations
Licensing: Elasticsearch operates under a dual licensing model, which includes a proprietary license, while OpenSearch is entirely under the Apache 2.0 license, appealing to organizations seeking open-source solutions without licensing constraints.
Deployment: Choose Elasticsearch for advanced features and seamless integration within the Elastic Stack. Opt for OpenSearch for its open-source principles, flexibility, and community-driven enhancements.
Choosing the Right Tool
The choice between Elasticsearch and OpenSearch hinges on project requirements, budget, and organizational philosophy. Evaluate factors such as advanced features, licensing terms, and community engagement to make an informed decision that aligns with your long-term goals.
Conclusion
Both Elasticsearch and OpenSearch offer powerful search engine solutions tailored to diverse organizational needs. By understanding their core attributes and differences, you can confidently select the search engine that enhances your data search capabilities and aligns with your business objectives.
For more insights on leveraging Elasticsearch or OpenSearch for your projects, contact ProsperaSoft. We're here to discuss how our expertise can contribute to your success.
#elasticsearch vs opensearch#opensearch vs elasticsearch opensearch#elasticsearch opensearch vs elasticsearch#performance opensearch vs elastic search#elastic search vs opensearch#elastic search vs open search#elastic vs opensearch
0 notes
Text
1970's Landduo


image I used for the background: https://www.ecosia.org/images?addon=opensearch&addonversion=7.1.0&q=70s+patterns+blue+and+red#id=182D04C0A0FCA5D77F1C69F81CD211DAC2887AC7
#landduo#the realm smp#qsmp#qsmp fanart#the realm fanart#badboyhalo#foolish gamers#badboyhalo fanart#foolish fanart#the realm foolish#the realm badboyhalo#qsmp foolish#qsmp badboyhalo
24 notes
·
View notes
Text
I want to pat my past self on the back for adding robust backups to an opensearch instance and slaving over bending the stupid dotnet client in ways it probably shouldn't be used just to have the condig in code.
Now I can just kill that poor domain and create an identical clone with the execution of two commands
Sayonara dev instance.
I'll probably kill you again at some point
2 notes
·
View notes
Text
OpenSearch 3.0: Vector Search Gets the Open Source Performance Boost AI Applications Need
OpenSearch 3.0 delivers 9.5x faster vector search performance, GPU acceleration, and AI agent support to power next-generation applications.
@tonyshan #techinnovation https://bit.ly/tonyshan https://bit.ly/tonyshan_X
0 notes
Link
In this post, we demonstrate how to use large vision models (LVMs) for semantic video search using natural language and image queries. We introduce some use case-specific methods, such as temporal frame smoothing and clustering, to enhance the video #AI #ML #Automation
0 notes
Link
a fun discovery from a recent trip to London
2 notes
·
View notes
Text
Amazon OpenSearch Service スクリプトプラグインのサポート追加でカスタム検索機能が大幅強化!
Amazon OpenSearch Serviceにおけるカスタムプラグインの機能拡張により、より柔軟で高度な検索・分析システムの構築が可能になりました。 特にスクリプトプラグインの対応により、開発者はこれまで以上にパーソナライズされた検索体験を提供できるようになっています。 Amazon OpenSearch Serviceのカスタムプラグイン機能概要 Amazon OpenSearch…
0 notes
Text
Kibana / Opensearch Dashboards: Error when creating new index pattern (Bad Request)
This article is based on internal documentation from CyberSift, and since this seems to be a problem which others might run into, I’ve posted it here Problem scenario When attempting to (re-)create a new index pattern from Kibana / Opensearch Dashboards, we encounter the error Bad Request: Troubleshooting steps First point of call is the kibana/dashboard logs. Tailing these logs while…
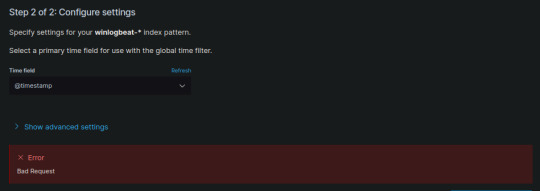
View On WordPress
0 notes
Text
Implementing AWS Web Application Firewall for Robust Protection
Implementing AWS Web Application Firewall (WAF) offers robust protection for web applications by filtering and monitoring HTTP(S) traffic to safeguard against common threats like SQL injection and cross-site scripting (XSS). This managed service integrates seamlessly with AWS services such as Amazon CloudFront, Application Load Balancer, and API Gateway, providing a scalable and cost-effective solution for application security. To ensure effective deployment, it's recommended to test WAF rules in a staging environment using count mode before applying them in production. Additionally, enabling detailed logging through Amazon CloudWatch or Amazon S3 can aid in monitoring and compliance. Regularly updating and customizing WAF rules to align with specific application needs further enhances security posture. For organizations seeking comprehensive application-level security, leveraging AWS WAF in conjunction with services like Edgenexus Limited's Web Application Firewall can provide layered defense against evolving cyber threats.
The Importance of AWS Web Application Firewall
AWS WAF is a managed service that helps protect web applications from common web exploits that could affect application availability, compromise security, or consume excessive resources. By filtering and monitoring HTTP and HTTPS requests, AWS WAF allows you to control access to your content. Implementing AWS WAF enables businesses to defend against threats such as SQL injection, cross-site scripting (XSS), and other OWASP Top 10 vulnerabilities. This proactive approach to security is essential for maintaining the integrity and availability of web applications.
Key Features of AWS Web Application Firewall
AWS WAF offers several features that enhance web application security. It provides customizable rules to block common attack patterns, such as SQL injection or cross-site scripting. Additionally, AWS WAF allows for rate-based rules to mitigate DDoS attacks and bot traffic. Integration with AWS Shield Advanced provides an additional layer of protection against larger-scale attacks. Furthermore, AWS WAF's logging capabilities enable detailed monitoring and analysis of web traffic, facilitating quick identification and response to potential threats.
Best Practices for Implementing AWS Web Application Firewall
When implementing AWS WAF, it's crucial to follow best practices to ensure optimal protection. Start by defining a baseline of normal application traffic to identify anomalies. Utilize AWS Managed Rules to protect against common threats and customize them to fit your application's specific needs. Regularly update and review your WAF rules to adapt to emerging threats. Additionally, integrate AWS WAF with AWS CloudWatch for real-time monitoring and alerting, enabling swift responses to potential security incidents.
Integrating AWS Web Application Firewall with AWS Services
AWS WAF seamlessly integrates with various AWS services, enhancing its effectiveness. Deploying AWS WAF with Amazon CloudFront allows for global distribution of content with added security at the edge. Integration with Application Load Balancer ensures that only legitimate traffic reaches your application servers. Additionally, AWS WAF can be used with Amazon API Gateway to protect APIs from malicious requests. These integrations provide a comprehensive security solution across your AWS infrastructure.
Monitoring and Logging with AWS Web Application Firewall
Monitoring and logging are essential components of a robust security strategy. AWS WAF provides detailed logs of web requests, including information on the request's source, headers, and the action taken by the WAF rules. These logs can be stored in Amazon S3, analyzed using Amazon Athena, or visualized through Amazon OpenSearch Service. By regularly reviewing these logs, businesses can identify patterns, detect anomalies, and respond promptly to potential threats, ensuring continuous protection of web applications.
Cost Considerations for AWS Web Application Firewall
While AWS WAF offers robust security features, it's essential to consider the associated costs. Pricing is based on the number of web access control lists (ACLs), the number of rules per ACL, and the number of web requests processed. To optimize costs, regularly review and adjust your WAF rules to ensure they are necessary and effective. Additionally, leveraging AWS Shield Advanced can provide additional protection against larger-scale attacks, potentially reducing the need for extensive custom WAF rules. By carefully managing AWS WAF configurations, businesses can achieve a balance between robust security and cost efficiency.
Future-Proofing Your Web Application Security with AWS WAF
As cyber threats continue to evolve, it's crucial to future-proof your web application security. AWS WAF's flexibility allows for the implementation of custom rules to address emerging threats. Regularly updating and refining these rules ensures that your applications remain protected against new vulnerabilities. Additionally, staying informed about updates and new features released by AWS can provide opportunities to enhance your security posture further. By proactively managing AWS WAF configurations, businesses can maintain a robust defense against evolving cyber threats.
Conclusion
Implementing AWS Web Application Firewall is a critical step in protecting web applications from common and emerging threats. By following best practices, integrating with AWS services, and continuously monitoring and refining security configurations, businesses can ensure the integrity and availability of their applications. Edgenexus Limited's expertise in IT services and consulting can assist organizations in effectively deploying and managing AWS WAF, providing tailored solutions to meet specific security needs. With a proactive approach to web application security, businesses can safeguard their digital assets and maintain trust with their users.
0 notes