#Passwordless
Explore tagged Tumblr posts
Text

2 notes
·
View notes
Text
The password problem
Above: Illustration by nao701030455/DepositPhotos BitDepth#1506 for April 14, 2025 At the heart of most cybersecurity problems is a compromised password. A password that was guessed.A password unknowingly shared with a hacker in a phishing operation.A password found in a data breach that remained unchanged. It doesn’t matter how well something is locked down if the key can be easily found or…
#Cybersecurity#Data Breach#Facebook#Instagram#LastPass#Nordpass#Norton Lifelock#Password#Passwordless#YouTube
0 notes
Text
Passwordless Authentication: The Future of Secure Logins

In an era where cyber threats are evolving rapidly, traditional password-based authentication is proving to be a weak link in digital security. Passwords are often reused, forgotten, or easily compromised, making them an easy target for cybercriminals. Enter passwordless authentication—a revolutionary approach that enhances security while improving user experience. If you're keen on mastering cybersecurity trends like this, enrolling in a cybersecurity course can be your first step toward a secure digital future.
The Problem with Passwords
Despite the advancement in security technologies, passwords remain one of the most vulnerable aspects of authentication. Here’s why:
Weak Passwords: Many users create simple passwords for convenience, making them easy to crack.
Reused Credentials: People tend to reuse passwords across multiple platforms, increasing their risk.
Phishing Attacks: Cybercriminals use deceptive techniques to steal passwords.
Credential Stuffing: Attackers use leaked passwords to gain unauthorized access to multiple accounts.
These issues make it clear that passwords alone are no longer sufficient to secure online identities.
What is Passwordless Authentication?
Passwordless authentication eliminates the need for traditional passwords by leveraging more secure and user-friendly alternatives, such as:
Biometric Authentication – Uses fingerprints, facial recognition, or retina scans.
One-Time Passwords (OTP) – A temporary code sent via SMS, email, or authenticator apps.
Magic Links – Secure links sent to a user’s registered email or phone number for login.
Hardware Security Keys – USB or NFC-based security devices that authenticate users.
Mobile Authentication Apps – Apps like Google Authenticator or Microsoft Authenticator generate secure codes.
Benefits of Passwordless Authentication
1. Enhanced Security
By removing passwords, the risk of phishing, brute force attacks, and credential leaks is significantly reduced.
2. Improved User Experience
Users no longer need to remember complex passwords or go through tedious password recovery processes.
3. Reduced IT Costs
Organizations save on password-related support costs, such as resetting forgotten passwords.
4. Resistance to Phishing and Credential Theft
With authentication methods like biometrics and hardware security keys, cybercriminals have no credentials to steal.
How Passwordless Authentication is Reshaping Cybersecurity
Many organizations are adopting passwordless authentication to secure their digital ecosystems. Tech giants like Microsoft, Google, and Apple are already integrating passwordless solutions into their platforms. The FIDO (Fast Identity Online) Alliance is working towards widespread adoption of passwordless authentication standards.
Cybersecurity professionals must stay ahead of these advancements. If you're looking to build a career in this domain, taking a cybersecurity course can help you understand and implement modern authentication mechanisms effectively.
Challenges in Adopting Passwordless Authentication
While passwordless authentication is the future, it comes with challenges:
Initial Implementation Costs – Organizations must invest in infrastructure upgrades.
User Adaptation – Users need time to transition from traditional passwords.
Biometric Privacy Concerns – Storing biometric data securely is crucial to prevent misuse.
Conclusion
Passwordless authentication is not just a trend—it is the future of secure logins. It enhances security, improves user experience, and reduces the risks associated with password-based authentication. As cyber threats become more sophisticated, organizations and individuals must adopt modern authentication methods to stay protected.
Want to be at the forefront of these cybersecurity innovations? Consider enrolling in a cybersecurity course to gain hands-on expertise in advanced security solutions.
The future of authentication is passwordless—are you ready for it?
0 notes
Text
Weekly output: Boom Supersonic's XB-1, Comcast low latency, painstaking passkey progress
This has been a strange, sad and shocking week in the nation’s capital–first the mid-air collision outside National Airport Wednesday that left 67 people dead and ended a nearly 16-year streak without fatal crashes by U.S. airlines, then Elon Musk’s attempts to stage what I have to call a digital coup at the Treasury Department and the Agency for International Development. Patreon readers got an…
View On WordPress
#Andrew Shikiar#authentication#Boom Supersonic#Comcast#FIDO Alliance#infosec#low lag#low latency#Mach 1#passkeys#passwordless#supersonic#XB-1
0 notes
Text
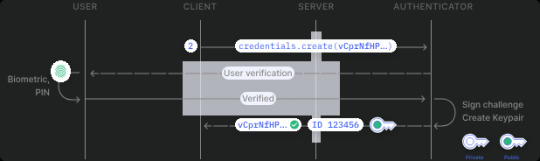
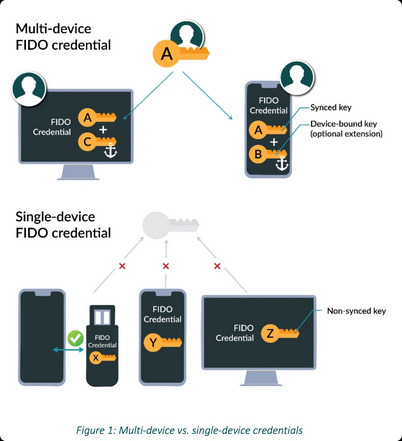
Passkeys: Secure, But Not User-Friendly? Holiday Tech Support Nightmare
Incoming With passkeys becoming more prevalent, concerns about their usability are rising just in time for the holiday season, when many people rely on tech support for assistance.

0 notes
Text
ManageEngine Strengthens Its Identity-First Security Offerings With Passwordless, Phishing-Resistant Authentication
ManageEngine combats ransomware attacks and identity theft with its latest launch of FIDO2 authentication in its on-premises identity security solution The company also strengthens and protects network endpoints against unauthorized system actions by launching endpoint MFA in its cloud-native identity platform Try FIDO2 authentication and endpoint MFA for free…

View On WordPress
0 notes
Text
Passwordless Authentication System

Dive into the future of authentication with our latest blog! Discover everything you need to know about Passwordless Authentication and how it's revolutionizing security.
Read now: https://biocube.ai/blog/passwordless-authentication-system/
#passwordless authentication#passwordless#authentication#biometrics#technology#passwordless technology#authentication system#biometric authentication
0 notes
Text
Dashlane ditching master passwords

A top-tier password manager maker is ditching the use of master passwords and offering its users a totally passwordless experience. https://jpmellojr.blogspot.com/2023/12/dashlane-ditching-master-passwords.html
0 notes
Text
Have you ever wondered that someone meant by "Passwordless" entry to a website? This is a great explanation from Neal Fennimore.
0 notes
Text
How passkeys are changing the face of authentication - Help Net Security
As passwordless identity becomes mainstream, the term “passkey” is quickly becoming a new buzzword in cybersecurity. But what exactly is a passkey and why do we need them? A passkey is a digital credential that can only be used by the authorized user. This commonly requires unlocking a device with a biometric marker (such as facial or fingerprint scan) or a unique factor (e.g., a PIN).…

View On WordPress
0 notes
Text
(2023-06-14) Securing Or Attacking Your Active Directory With Azure AD Passwordless Authentication? That IS The Question!
Tonight I was reading Dirk-Jan’s post on how Cloud Kerberos Trust, in use by Azure AD Passwordless AuthN, could be used to attack the Active Directory. Very interesting read! For all the details, please see: Obtaining Domain Admin from Azure AD by abusing Cloud Kerberos Trust This is interesting as normally Active Directory is being used to attack Azure AD. Now it is the other way around, using…

View On WordPress
0 notes
Text
The Future of Passwords: Do We Really Need Them?
Passwords are one of the most common and widely used methods of authentication on the internet. They are supposed to protect our online accounts and data from unauthorised access and misuse. Passwords are increasingly becoming a source of frustration and insecurity for users and organisations alike. They are often easy to guess, hard to remember, and reused across multiple sites, making them…

View On WordPress
#2022 Data Breach Investigations Report#alternative authentication methods#biometrics#cybersecurity#Dashlane#Equifax#Google#IBM#LastPass#MFAs#passkeys#passwordless#Passwords#Verizon
0 notes
Text
Okay! For those who were wondering about alternatives to Google Docs, I think I found pretty much the perfect option: Ellipsus
Besides being online and collaborative like GDocs, a few things I've liked about it so far:
It has a drafts feature, which you can use to track and merge revisions to your doc OR you can use them as sub-documents to store things like your bible--character info, notes, scenes, whatever OR you can break down your story into chapters


Strictly anti-AI, and wanting you to own your writing 100%
Has a built in writing timer, and a focus mode (Strips away the UI)

Aaaaaand….!! What's that...?

Oh yeah, snippet sharing:

and a built in export to AO3

Their plans are to keep this version of the product free, and then create higher end paid versions with more features to maintain a sustainable model that'll keep the product viable. They seem really cool so far. Highly recommend checking them out, if you're in any way interested in degoogling.
#degoogle#writing tools#ellipsus#This is an organic recommendation nobody told me to share this#And it's passwordless login which is more secure in the longterm!
347 notes
·
View notes
Text
on the topic of people taking advantage of the genocide in Palestine to turn themselves a pretty profit, why does everyone else have to buy esims if they're a purely digital process? what's stopping companies from providing that shit out to the people in need exactly? and more importantly, how do we know the esims we donate even get to where we want them to go? what stops a company from just pretending or lying?
#ikildaman shut the fuck up#not saying to not donate or support anyone or anywhere. please keep helping where u can#but at what point does our goodwill actually cross that threshold of helping people. and at what point are we just being played#its too easy to drop some cash off on a link and move on with our timelines. are we Keeping Up with who we give to at all ?#im just very acutely aware that esim companies have got to be seeing profit margins rise exponentially lately. and thats all they want#but then i wonder how the process for it even Works. if internet infrastructure is out in palestine how tf is a digital sim card gna help#fucks it gonna Connect To ?#i Know the reason people gotta pay for it. i Know providing internet freely devalues most paid forms of it#but i still find our manufactured values of processes that are largely digital to be really. really fucking stupid#all it takes is like one hacker. one free-for-all passwordless hotspot. or something akin to these to Break the gate. what a joke
2 notes
·
View notes
