#Program Increment Objectives
Explore tagged Tumblr posts
Text
Fun fact: the name of the programming language "C#" is actually five consecutive jokes layered on top of each other because programmers have nothing better to do.
Go with me on a brief history tour:
BCPL
Early programming language invented nearly 60 years ago
No jokes here, this one just stands for "Basic Combined Programming Language"
B
Designed to be a simpler, smaller substitute for BCPL
What would you name something that's "BCPL in less space"? Why, B, of course! It doesn't stand for anything, it's just BCPL with 75% fewer letters.
C
Designed to advance the ideas in B further forwards
What do you get if you move beyond B in the alphabet?
C++
Based on C, but with object-oriented features added on top
In C, adding "++" to the end of a number increments it by one, so this name basically says "slightly more than C"
C#
It's C++ but with even more object-oriented features, but also with a bunch of funky Java-inspired changes
If "C++" is "slightly more than C", maybe we could call it "C++++"? But that looks ridiculous, let's arrange those pluses into a square and connect them together.
For one final bonus joke, doing this makes it read as "C Sharp", which is of course the musical note one semitone higher than the C note, making it a second way to say "slightly more than C"
All together, "C#" is the culmination of five jokes that together say "better in a different way than, but still even better than the other language that's better than, the language that's more advanced than the language that's smaller than BCPL"
9 notes
·
View notes
Text
hey wanna hear about the crescent stack structure because i don't really have anyone to tell this to
YAYYYY!! THANK YOU :3
small note: threads are also referred to internally as lstates (local states) as when creating a new thread, rather than using crescent_open again, they're connected to a single gstate (global state)
the stack is the main data structure in a crescent thread, containing all of the locals and call information.
the stack is divided into frames, and each time a function is called, a new frame is created. each frame has two parts: base and top. a frame's base is where the first local object is pushed to, and the top is the total amount of stack indexes reserved after the base. also in the stack is two numbers, calls and cCalls. calls keeps track of the number of function calls in the thread, whether it's to a c or crescent function. cCalls keeps track of the number of calls to c functions. c functions, using the actual stack rather than the dynamically allocated crescent stack, could overflow the real stack and crash the program in a way crescent is unable to catch. so we want to limit the amount of these such that this (hopefully) doesn't happen.
calls also keeps track of another thing with the same number, that being the stack level. the stack level is a number starting from 0 that increments with each function call, and decrements on each return from a function. stack level 0 is the c api, where the user called crescent_open (or whatever else function that creates a new thread, that's just the only one implemented right now), and is zero because zero functions have been called before this frame.
before the next part, i should probably explain some terms:
- stack base: the address of the first object on the entire stack, also the base of frame 0
- stack top: address of the object immediately after the last object pushed onto the stack. if there are no objects on the stack, this is the stack base.
- frame base: the address of the first object in a frame, also the stack top upon calling a function (explained later) - frame top: amount of stack indexes reserved for this frame after the base address
rather than setting its base directly after the reserved space on the previous frame, we simply set it right at the stack top, such that the first object on this frame is immediately after the last object on the previous frame (except not really. it's basically that, but when pushing arguments to functions we just subtract the amount of arguments from the base, such that the top objects on the previous frame are in the new frame). this does make the stack structure a bit more complicated, and maybe a bit messy to visualize, but it uses (maybe slightly) less memory and makes some other stuff related to protected calls easier.
as we push objects onto the stack and call functions, we're eventually going to run out of space, so we need to dynamically resize the stack. though first, we need to know how much memory the stack needs. we go through all of the frames, and calculate how much that frame needs by taking the frame base offset from the stack base (framebase - stackbase) and add the frame top (or the new top if resizing the current frame in using crescent_checkTop in the c api). the largest amount a frame needs is the amount that the entire stack needs. if the needed size is less than or equal to a third of the current stack size, it shrinks. if the needed size is greater than he current stack size, it grows. when shrinking or growing, the new size is always calculated as needed * 1.5 (needed + needed / 2 in the code).
when shrinking the stack, it can only shrink to a minimum of CRESCENT_MIN_STACK (64 objects by default). even if the resizing fails, it doesn't throw an error as we still have enough memory required. when growing, if the new stack size is greater than CRESCENT_MAX_STACK, it sets it back down to just the required amount. if that still is over CRESCENT_MAX_STACK, it either returns 1 or throws a stack overflow error depending on the throw argument. if it fails to reallocate the stack, it either throws an out of memory error or returns 1 again depending on the throw argument. growing the stack can throw an error because we don't have the memory required, unlike shrinking the stack.
and also the thing about the way a frame's base is set making protected calls easier. when handling an error, we want to go back to the most recent protected call. we do this by (using a jmp_buf) saving the stack level in the handler (structure used to hold information when handling errors and returning to the protected call) and reverting the stack back to that level. but we're not keeping track of the amount of objects in a stack frame! how do we restore the stack top? because a frame's base is immediately after that last object in the previous frame, and that the stack top is immediately after the last object pushed onto the stack, we just set the top to the stack level above's base.

6 notes
·
View notes
Text
Want all your game ideas in the same world?
Give Nebulous a try. It's a program that's free to download and use that's like making a personal offline wiki of your personal universe, whether it's just for one story, or multitudes in one world.
It's a bit clunky to use at first since you need to create objects to be the main folder to make newer objects nested inside for categories. Once you get used to that though, it's a breeze.
If your mind jumps around from story to story like mine does, it's very easy to hop around from object to object to add on to each one incrementally. I've never been able to keep my thoughts organized in other writing programs, to the point I'll know I wrote something, and be unable to find it. Don't have that problem here, as object names become keywords. If the keyword is mentioned once in a separate object, a link is immediately made between the two. So you can link two characters together, for example, by putting their names in each other's object file.
If you do DnD, it's got default object setups for Characters, so it works well for online DMs. You can also create your own defaults to work with your particular needs. Going back to the keyword links, Nebulous also has a neat graph feature to show how everything connects together. If there's something you don't want showing in that graph (such as an object whose only use is to be the category folder), you can go into that object's settings and tell the program to exclude it from the graph.
If you want another item in the tool belt, give Nebulous a shot. Again, it's free, and still actively updated by the dev.
27 notes
·
View notes
Note
Did you animate the spinning eyes frame by frame??? If so I love it but like HOW
The flowers and eyes and bees around adam at the end? Yeah I did lmao.............. I actually did it in the most absurd way- I animated each little object individually in a ring, then I merged the objects, and manually rotated it by increment of a specific number, frame by frame, for like 100 frames-- it was hilariously inefficient and felt silly to do but!! It technically recreated the effect from the original music video lol
I know if I had a more advanced program like after effects or something that has auto-keyframe movement that would have taken like.... 10% of the time it took me. But I only have / know how to use my usual drawing program, krita right now, which cannot do that I'm fairly certain.
If anyone...... knows where to get an older, cheaper/free version of after effects, please do help a girl out lol.
7 notes
·
View notes
Text
Dev Log Feb 14 2025 - Space Dust Shader
Two weeks left until release. And I almost forgot to post the dev blog post on the second Friday. Whoops. Since it's late, I'll be quick. Since I promised some shader stuff last week, I should probably deliver on that. For those unfamiliar, shaders are tiny programs written to be executed on the GPU for handling rendering of graphics for the game. It's a bit hand-wavy, but there's a bunch of different types that you can write for different stages in the rendering pipeline, which itself can be configured differently based on what the game is. Most modern games using OpenGL and similar pipelines have at bare minimum a Vertex Shader, meant to populate the shapes of the things, and a Fragment Shader, meant to draw the colors of the pixels. Usually it's just a texture on a plane for most 2D games, but you can get creative and make some neat stuff. Here's a still image (not a gif, sorry) of the attractor/repulsor objects as seen in the first trailer:

It's kind of a neat effect (not to pat myself on the back too much, but you know). There's little dust particles flying into/away from the little swirly hole in the middle. The best part is that it's not actually particle objects - there's no calculation for those individual dust particles at all. It's just one single texture that looks like this:
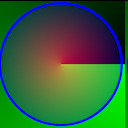
The image is a composite of a layer of pure Green and Black on the bottom in a conical gradient, a radial gradient of pure red to transparent from the middle on top of that, and then a circle of pure blue with a slight transparent blue tint inside. The trick is that there's a really simple little shader applied to it (code for those who want to commandeer, feel free to use for anything, but note that this is used in the Phaser WebGL pipline and will not just drag-and-drop into most projects) :
precision mediump float; uniform sampler2D uMainSampler; uniform float uTime; varying vec2 outTexCoord; void main() { vec4 c = texture2D(uMainSampler, outTexCoord); float t = fract(sin(c.g * 12.9898) * 43758.5453); float a = clamp(fract(c.r + uTime * 0.05 + t) * c.r * 2.0 + c.b, 0.0, 1.0); gl_FragColor = vec4(0.6 * a, 0.7*a, 0.8*a, a); }
The gist of it is that it takes the image, uses the amount of Green at a specific pixel to determine which 'column' of dust expanding from the center to the edge belongs there. Then, the 'closeness' of the dust is specified by the Red value of the pixel, and more visibility is granted to specific small range of Red values over a function of time with a little bit of pseudo-randomness to make it look nice. Mask it off with the Blue, and increment over time, and voilla - super cheap space dust particle thingy. Obviously, we use shaders quite heavily for a lot of the things that do weird little cyclical movements, including things like the stage shimmy and the wavy effect for the company logo. However, you'd probably be just as surprised how much isn't shaders, and is instead just standard compositing and masking, like the stage background and UI elements. Some clever design and a strong art direction do a ton more for a game's visuals than just throwing raw computational power at it.
2 notes
·
View notes
Quote
In the speech – which he delivered at the CIC and was recorded and is available online – Roberts spoke candidly about his strategy for achieving extreme policy goals that he supports but are out of step with the views of a majority of Americans. Outlawing birth control is the “hardest” political battle facing conservatives in the future, the 50-year-old political strategist said, but he urged conservatives to pursue even small legislative victories – what he called “radical incrementalism” – to advance their most rightwing policy objectives. oberts gained notoriety this year as the leading force behind Project 2025, a foundation plan backed by more than 100 conservative groups that seeks to radically upend a broad range of policies if Trump gets elected again, from limiting abortion access and LGBTQ+ rights and dismantling the Department of Education, to ending diversity programs and increasing government support for “fertility awareness” programs, like ovulation tracking and practicing periodic abstinence, instead of more reliable contraception. But Roberts’ personal ties to Opus Dei and the significance of his affiliation, has received far less attention. Gareth Gore, the author of a forthcoming book on Opus Dei, called the Catholic organization “a political project shrouded in a veil of spirituality”. The group’s founder, Saint Josemaría Escrivá, saw his followers as part of a “rising militia”, Gore said, who were seeking to “enter battle against the enemies of Christ”. “Like Project 2025, Opus Dei at its core is a reactionary stand against the progressive drift of society,” Gore said. “For decades now, the organization has thrown its resources at penetrating Washington’s political and legal elite – and finally seems to have succeeded through its close association with men like Kevin Roberts and Leonard Leo.”
Kevin Roberts, architect of Project 2025, has close ties to radical Catholic group Opus Dei | US news | The Guardian
4 notes
·
View notes
Note
i’m a game dev student at an art school and i’ve been really struggling with finding my niche…. i LOVE being a environment/modeler/texture artist, and i want to have more skills in the design/tech side… but i’ve been struggling really hard with learning unreal engine 5 for my classes. do you have any experience in unreal5 blueprinting or just anything more on the tech side? i would appreciate some advice to get through these tough college quarters :’D
Whenever someone entering gamedev on the programmer side is struggling to figure it out, there are generally two reasons for this.
The first is that they're struggling to get into the programmer mindset. Blueprints try to bridge the gap, but code doesn't work like english. It doesn't even work like the human brain. When we think or talk we take shortcuts to formulate or convey ideas because we can trust that when it comes time to interpret those ideas another person (or ourselves in the future) will fill in those gaps. This is so intuitive to us that we don't even notice that there are gaps. Programming forces you to become aware of how many gaps there are and fill them, and quite frankly it's a humbling experience.
I'm probably not saying anything you don't already know, but I want to emphasize that the way coding works is unintuitive to most people and we need to retrain our way of thinking to get good at it. This is unfortunately not a fast process. It's very common especially for new programmers (though I'm not immune even now) to go "I'm a fucking idiot, I'm a fucking idiot, I'm a fucking--I'M A GENIUS" because of the cycle of shit not working for stupid reasons and then finally working.
The second problem is that they're unfamiliar with (and overwhelmed by) the library they're working with.
A "library" in a programming context is typically collection of functions and objects you can import into a project, but each game engine has its own built in libraries which the engines are built around. These are the verbs and nouns that aren't built into, for example, C++, but have been added by Unreal Engine to make it easier to make games.
The better the game engine, the larger the library. Unfortunately, the larger the library the more overwhelming it is because that's a lot of shit to learn.
In your case anon the "library" would refer to the different kinds of nodes you can add to the blueprint. When you're new to it, even an expert Unity dev will struggle in Unreal because they don't know what their options are to accomplish things.
Now the reason I break down the new-programmer hurdles into two distinct problems is because they often seem like one problem, which can make it hard to solve. Both get better with experience so sometimes slamming your head against a wall is a viable way to get through them, but it's not the best.
If you think your main issue is the first problem, you can work on it through "exercise." This can be in the form of taking programming courses on codecademy (I'd recommend C++ since you're using Unreal, though C# isn't a bad choice) or by playing a game by Zachtronics like Infinifactory or Opus Magnum. These games are "programming puzzle games" and I can personally attest to having gotten better at Infinifactory as I got better at programming.
If you think it's the second problem, the biggest solvent is curiosity. When I get into a new engine, I spend a bit of time learning how it works and then immediately try and figure out how to do dumb shit in it. I made an incremental game in RPG Maker just to see if I could. It wasn't good, but it was a fun educational experience. Sometimes I'll come across a function I don't understand, and I'll open the engine's manual and read about the function and use that as a jumping off point to dive into similar functions.
It doesn't feel good for my advice to be "read the manual" but genuinely there's a point where you realize that you're reading the manual instead of watching youtube videos and it's like, holy shit I'm a real programmer. It's a sign that you're getting comfortable enough in the role that you're learning what questions to ask to figure out what you need to know (youtube is still a great resource of course).
All of that said though, if your aim is to be an environment artist I think it's okay to be bad at programming. Survive college, of course, but if you're in a team with a dedicated programmer (which you will be if you are not the programmer) then all you need is to be able to understand how to communicate with the programmer. It's really beneficial to know enough about the fundamentals of what you're working in to know what info the programmer needs from you and what info you need from them, but you don't have to be good at it to do that!
5 notes
·
View notes
Text
This Week in Rust 518
Hello and welcome to another issue of This Week in Rust! Rust is a programming language empowering everyone to build reliable and efficient software. This is a weekly summary of its progress and community. Want something mentioned? Tag us at @ThisWeekInRust on Twitter or @ThisWeekinRust on mastodon.social, or send us a pull request. Want to get involved? We love contributions.
This Week in Rust is openly developed on GitHub and archives can be viewed at this-week-in-rust.org. If you find any errors in this week's issue, please submit a PR.
Updates from Rust Community
Project/Tooling Updates
Strobe Crate
System dependencies are hard (so we made them easier)
Observations/Thoughts
Trying to invent a better substring search algorithm
Improving Node.js with Rust-Wasm Library
Mixing C# and Rust - Interop
A fresh look on incremental zero copy serialization
Make the Rust compiler 5% faster with this one weird trick
Part 3: Rowing Afloat Datatype Boats
Recreating concurrent futures combinators in smol
Unpacking some Rust ergonomics: getting a single Result from an iterator of them
Idea: "Using Rust", a living document
Object Soup is Made of Indexes
Analyzing Data 180,000x Faster with Rust
Issue #10: Serving HTML
Rust vs C on an ATTiny85; an embedded war story
Rust Walkthroughs
Analyzing Data /,000x Faster with Rust
Fully Automated Releases for Rust Projects
Make your Rust code unit testable with dependency inversion
Nine Rules to Formally Validate Rust Algorithms with Dafny (Part 2): Lessons from Verifying the range-set-blaze Crate
[video] Let's write a message broker using QUIC - Broke But Quick Episode 1
[video] Publishing Messages over QUIC Streams!! - Broke But Quick episode 2
Miscellaneous
[video] Associated types in Iterator bounds
[video] Rust and the Age of High-Integrity Languages
[video] Implementing (part of) a BitTorrent client in Rust
Crate of the Week
This week's crate is cargo-show-asm, a cargo subcommand to show the optimized assembly of any function.
Thanks to Kornel for the suggestion!
Please submit your suggestions and votes for next week!
Call for Participation
Always wanted to contribute to open-source projects but did not know where to start? Every week we highlight some tasks from the Rust community for you to pick and get started!
Some of these tasks may also have mentors available, visit the task page for more information.
* Hyperswitch (Hacktoberfest)- [FEATURE] separate payments_session from payments core * Hyperswitch (Hacktoberfest)- [NMI] Use connector_response_reference_id as reference to merchant * Hyperswitch (Hacktoberfest)- [Airwallex] Use connector_response_reference_id as reference to merchant * Hyperswitch (Hacktoberfest)- [Worldline] Use connector_response_reference_id as reference to merchant * Ockam - Make ockam project delete (no args) interactive by asking the user to choose from a list of space and project names to delete (tuify) * Ockam - Validate CBOR structs according to the cddl schema for authenticator/direct/types * Ockam - Slim down the NodeManagerWorker for node / node status
If you are a Rust project owner and are looking for contributors, please submit tasks here.
Updates from the Rust Project
397 pull requests were merged in the last week
rewrite gdb pretty-printer registration
add FileCheck annotations to mir-opt tests
add MonoItems and Instance to stable_mir
add a csky-unknown-linux-gnuabiv2hf target
add a test showing failing closure signature inference in new solver
add new simpler and more explicit syntax for check-cfg
add stable Instance::body() and RustcInternal trait
automatically enable cross-crate inlining for small functions
avoid a track_errors by bubbling up most errors from check_well_formed
avoid having rustc_smir depend on rustc_interface or rustc_driver
coverage: emit mappings for unused functions without generating stubs
coverage: emit the filenames section before encoding per-function mappings
coverage: fix inconsistent handling of function signature spans
coverage: move most per-function coverage info into mir::Body
coverage: simplify the injection of coverage statements
disable missing_copy_implementations lint on non_exhaustive types
do not bold main message in --error-format=short
don't ICE when encountering unresolved regions in fully_resolve
don't compare host param by name
don't crash on empty match in the nonexhaustive_omitted_patterns lint
duplicate ~const bounds with a non-const one in effects desugaring
eliminate rustc_attrs::builtin::handle_errors in favor of emitting errors directly
fix a performance regression in obligation deduplication
fix implied outlives check for GAT in RPITIT
fix spans for removing .await on for expressions
fix suggestion for renamed coroutines feature
implement an internal lint encouraging use of Span::eq_ctxt
implement jump threading MIR opt
implement rustc part of RFC 3127 trim-paths
improve display of parallel jobs in rustdoc-gui tester script
initiate the inner usage of cfg_match (Compiler)
lint non_exhaustive_omitted_patterns by columns
location-insensitive polonius: consider a loan escaping if an SCC has member constraints applied only
make #[repr(Rust)] incompatible with other (non-modifier) representation hints like C and simd
make rustc_onunimplemented export path agnostic
mention into_iter on borrow errors suggestions when appropriate
mention the syntax for use on mod foo; if foo doesn't exist
panic when the global allocator tries to register a TLS destructor
point at assoc fn definition on type param divergence
preserve unicode escapes in format string literals when pretty-printing AST
properly account for self ty in method disambiguation suggestion
report unused_import for empty reexports even it is pub
special case iterator chain checks for suggestion
strict provenance unwind
suggest ; after bare match expression E0308
suggest constraining assoc types in more cases
suggest relaxing implicit type Assoc: Sized; bound
suggest removing redundant arguments in format!()
uplift movability and mutability, the simple way
miri: avoid a linear scan over the entire int_to_ptr_map on each deallocation
miri: fix rounding mode check in SSE4.1 round functions
miri: intptrcast: remove information about dead allocations
disable effects in libcore again
add #[track_caller] to Option::unwrap_or_else
specialize Bytes<R>::next when R is a BufReader
make TCP connect handle EINTR correctly
on Windows make read_dir error on the empty path
hashbrown: add low-level HashTable API
codegen_gcc: add support for NonNull function attribute
codegen_gcc: fix #[inline(always)] attribute and support unsigned comparison for signed integers
codegen_gcc: fix endianness
codegen_gcc: fix int types alignment
codegen_gcc: optimize popcount implementation
codegen_gcc: optimize u128/i128 popcounts further
cargo add: Preserve more comments
cargo remove: Preserve feature comments
cargo replace: Partial-version spec support
cargo: Provide next steps for bad -Z flag
cargo: Suggest cargo-search on bad commands
cargo: adjust -Zcheck-cfg for new rustc syntax and behavior
cargo: if there's a version in the lock file only use that exact version
cargo: make the precise field of a source an Enum
cargo: print environment variables for build script executions with -vv
cargo: warn about crate name's format when creating new crate
rustdoc: align stability badge to baseline instead of bottom
rustdoc: avoid allocating strings primitive link printing
clippy: map_identity: allow closure with type annotations
clippy: map_identity: recognize tuple identity function
clippy: add lint for struct field names
clippy: don't emit needless_pass_by_ref_mut if the variable is used in an unsafe block or function
clippy: make multiple_unsafe_ops_per_block ignore await desugaring
clippy: needless pass by ref mut closure non async fn
clippy: now declare_interior_mutable_const and borrow_interior_mutable_const respect the ignore-interior-mutability configuration entry
clippy: skip if_not_else lint for '!= 0'-style checks
clippy: suggest passing function instead of calling it in closure for option_if_let_else
clippy: warn missing_enforced_import_renames by default
rust-analyzer: generate descriptors for all unstable features
rust-analyzer: add command for only opening external docs and attempt to fix vscode-remote issue
rust-analyzer: add incorrect case diagnostics for module names
rust-analyzer: fix VS Code detection for Insiders version
rust-analyzer: import trait if needed for unqualify_method_call assist
rust-analyzer: pick a better name for variables introduced by replace_is_some_with_if_let_some
rust-analyzer: store binding mode for each instance of a binding independently
perf: add NES emulation runtime benchmark
Rust Compiler Performance Triage
Approved RFCs
Changes to Rust follow the Rust RFC (request for comments) process. These are the RFCs that were approved for implementation this week:
Add f16 and f128 float types
Unicode and escape codes in literals
Final Comment Period
Every week, the team announces the 'final comment period' for RFCs and key PRs which are reaching a decision. Express your opinions now.
RFCs
No RFCs entered Final Comment Period this week.
Tracking Issues & PRs
[disposition: merge] Consider alias bounds when computing liveness in NLL (but this time sound hopefully)
[disposition: close] regression: parameter type may not live long enough
[disposition: merge] Remove support for compiler plugins.
[disposition: merge] rustdoc: Document lack of object safety on affected traits
[disposition: merge] Stabilize Ratified RISC-V Target Features
[disposition: merge] Tracking Issue for const mem::discriminant
New and Updated RFCs
[new] eRFC: #[should_move] attribute for per-function opting out of Copy semantics
Call for Testing
An important step for RFC implementation is for people to experiment with the implementation and give feedback, especially before stabilization. The following RFCs would benefit from user testing before moving forward:
No RFCs issued a call for testing this week.
If you are a feature implementer and would like your RFC to appear on the above list, add the new call-for-testing label to your RFC along with a comment providing testing instructions and/or guidance on which aspect(s) of the feature need testing.
Upcoming Events
Rusty Events between 2023-10-25 - 2023-11-22 🦀
Virtual
2023-10-30 | Virtual (Melbourne, VIC, AU) | Rust Melbourne
(Hybrid - online & in person) October 2023 Rust Melbourne Meetup
2023-10-31 | Virtual (Europe / Africa) | Rust for Lunch
Rust Meet-up
2023-11-01 | Virtual (Cardiff, UK)| Rust and C++ Cardiff
ECS with Bevy Game Engine
2023-11-01 | Virtual (Indianapolis, IN, US) | Indy Rust
Indy.rs - with Social Distancing
2023-11-02 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2023-11-07 | Virtual (Berlin, DE) | OpenTechSchool Berlin
Rust Hack and Learn | Mirror
2023-11-07 | Virtual (Buffalo, NY, US) | Buffalo Rust Meetup
Buffalo Rust User Group, First Tuesdays
2023-11-09 | Virtual (Nuremberg, DE) | Rust Nuremberg
Rust Nürnberg online
2023-11-14 | Virtual (Dallas, TX, US) | Dallas Rust
Second Tuesday
2023-11-15 | Virtual (Cardiff, UK)| Rust and C++ Cardiff
Building Our Own Locks (Atomics & Locks Chapter 9)
2023-11-15 | Virtual (Richmond, VA, US) | Linux Plumbers Conference
Rust Microconference in LPC 2023 (Nov 13-16)
2023-11-15 | Virtual (Vancouver, BC, CA) | Vancouver Rust
Rust Study/Hack/Hang-out
2023-11-16 | Virtual (Charlottesville, NC, US) | Charlottesville Rust Meetup
Crafting Interpreters in Rust Collaboratively
2023-11-07 | Virtual (Berlin, DE) | OpenTechSchool Berlin
Rust Hack and Learn | Mirror
2023-11-21 | Virtual (Washington, DC, US) | Rust DC
Mid-month Rustful
Europe
2023-10-25 | Dublin, IE | Rust Dublin
Biome, web development tooling with Rust
2023-10-25 | Paris, FR | Rust Paris
Rust for the web - Paris meetup #61
2023-10-25 | Zagreb, HR | impl Zagreb for Rust
Rust Meetup 2023/10: Lunatic
2023-10-26 | Augsburg, DE | Rust - Modern Systems Programming in Leipzig
Augsburg Rust Meetup #3
2023-10-26 | Copenhagen, DK | Copenhagen Rust Community
Rust metup #41 sponsored by Factbird
2023-10-26 | Delft, NL | Rust Nederland
Rust at TU Delft
2023-10-26 | Lille, FR | Rust Lille
Rust Lille #4 at SFEIR
2022-10-30 | Stockholm, SE | Stockholm Rust
Rust Meetup @Aira + Netlight
2023-11-01 | Cologne, DE | Rust Cologne
Web-applications with axum: Hello CRUD!
2023-11-07 | Bratislava, SK | Bratislava Rust Meetup Group
Rust Meetup by Sonalake
2023-11-07 | Brussels, BE | Rust Aarhus
Rust Aarhus - Rust and Talk beginners edition
2023-11-07 | Lyon, FR | Rust Lyon
Rust Lyon Meetup #7
2023-11-09 | Barcelona, ES | BcnRust
11th BcnRust Meetup
2023-11-09 | Reading, UK | Reading Rust Workshop
Reading Rust Meetup at Browns
2023-11-21 | Augsburg, DE | Rust - Modern Systems Programming in Leipzig
GPU processing in Rust
2023-11-23 | Biel/Bienne, CH | Rust Bern
Rust Talks Bern @ Biel: Embedded Edition
North America
2023-10-25 | Austin, TX, US | Rust ATX
Rust Lunch - Fareground
2023-10-25 | Chicago, IL, US | Deep Dish Rust
Rust Happy Hour
2023-11-01 | Brookline, MA, US | Boston Rust Meetup
Boston Common Rust Lunch
2023-11-08 | Boulder, CO, US | Boulder Rust Meetup
Let's make a Discord bot!
2023-11-14 | New York, NY, US | Rust NYC
Rust NYC Monthly Mixer: Share, Show, & Tell! 🦀
2023-11-14 | Seattle, WA, US | Cap Hill Rust Coding/Hacking/Learning
Rusty Coding/Hacking/Learning Night
2023-11-15 | Richmond, VA, US + Virtual | Linux Plumbers Conference
Rust Microconference in LPC 2023 (Nov 13-16)
2023-11-16 | Nashville, TN, US | Music City Rust Developers
Python loves Rust!
2023-11-16 | Seattle, WA, US | Seattle Rust User Group
Seattle Rust User Group Meetup
2023-11-21 | San Francisco, CA, US | San Francisco Rust Study Group
Rust Hacking in Person
2023-11-22 | Austin, TX, US | Rust ATX
Rust Lunch - Fareground
Oceania
2023-10-26 | Brisbane, QLD, AU | Rust Brisbane
October Meetup
2023-10-30 | Melbourne, VIC, AU + Virtual | Rust Melbourne
(Hybrid - in person & online) October 2023 Rust Melbourne Meetup
2023-11-21 | Christchurch, NZ | Christchurch Rust Meetup Group
Christchurch Rust meetup meeting
If you are running a Rust event please add it to the calendar to get it mentioned here. Please remember to add a link to the event too. Email the Rust Community Team for access.
Jobs
Please see the latest Who's Hiring thread on r/rust
Quote of the Week
When your Rust build times get slower after adding some procedural macros:
We call that the syn tax :ferris:
– Janet on Fosstodon
Thanks to Jacob Pratt for the suggestion!
Please submit quotes and vote for next week!
This Week in Rust is edited by: nellshamrell, llogiq, cdmistman, ericseppanen, extrawurst, andrewpollack, U007D, kolharsam, joelmarcey, mariannegoldin, bennyvasquez.
Email list hosting is sponsored by The Rust Foundation
Discuss on r/rust
9 notes
·
View notes
Text

Future Air Combat System (FCAS) and the Military Internet of Things
Fernando Valduga By Fernando Valduga 11/22/2023 - 20:35in Military
The FCAS Air Combat Cloud (Air Combat Cloud) will bring real-time intelligence to the forefront, taking advantage of the network capabilities of different aircraft and platforms. Innovations in Artificial Intelligence (AI), big data processing and cybernetics will help make defense a truly collaborative mission.
Europe's Future Air Combat System (FCAS) will see next-generation manned jets flying alongside remotely piloted unmanned aircraft carriers of various sizes. These assets will be part of a fully interconnected "system of systems", based on open architectures, which will allow the integration of other existing platforms, such as the A400M or the A330 MRTT tanker plane. At the heart of this complex system will be the Air Combat Cloud, which will allow these platforms to work together.

But what exactly is an air combat cloud? As FCAS Combat Cloud product solution leader at Airbus, Ignacio Rosell often asks this question.
“How does the Android ecosystem work? We have an operating system that allows the integration of applications from different parts, and all this is supported by a communication infrastructure such as 5G, Bluetooth or Wi-Fi. If we apply this analogy to the FCAS, we are developing an important part of the "Internet of Military Things". Our mobile phones can be a fighter plane, an unmanned aerial system (UAS), a warship, a satellite or even a soldier on the ground, each integrating different applications or, in other words, different capabilities. Our air combat cloud has the same components, the communications infrastructure, the operating system and the applications that allow us to operate collaboratively," adds Rosell.
Launched by France, Germany and Spain, and with Airbus, Dassault Aviation and Indra as national industrial coordinators, the FCAS is one of the most important European defense programs of the coming decades. In a context of growing global instability, the objective of the project is nothing less than to design an air defense system that protects Europe, while strengthening its strategic autonomy and technological sovereignty.
Airbus leads the Combat Cloud pillar, with Thales and Indra as main partners. This is one of the seven areas of next-generation FCAS technology (see the infographic on the side), led at Airbus by Marc Paskowski.

It will provide a common situational awareness, capturing, sharing, merging and instantly processing large amounts of data from all connected manned and unmanned platforms, reliably, and transforming that data into actionable information, taking advantage of constantly evolving learning technologies. "The concept based on the cloud in flight is that all elements must constantly interoperate with each other to form a cohesive system that is informed as one and fights as one," says Paskowski.
"Our 'operating system' will need to be opened to accommodate ready-to-use and tailored applications, such as manned and unmanned teams, from Airbus or any other industrial partner. It will be an evolutionary process, with new applications, such as new aerial platforms, being integrated along the way," says Rosell. "Our business model around the Combat Cloud will not be unique. An area such as satellite connectivity could be offered as a service, while an 'app' part of an aircraft's mission system could be sold as a product,” he adds.
The development of intermediate solutions as part of this "internet of military things" should allow customers to use various levels of cloud capabilities and remote operators long before FCAS became operational in the 2040s. For example, Airbus has already carried out the first successful launch and operation in the world of a Remote Carrier flight test demonstrator from an A400M in flight.
Based on this incremental approach, the air combat cloud will be the digital watershed in the way military operations are conducted.
“The ability to integrate, operate and communicate from a networked system will shape the air force of the future,” said German Air Force Lieutenant General Ingo Gerhartz
In fact, future scenarios will require a much higher degree of automation for information management and integration of military services and branches throughout the entire mission cycle. For FCAS, innovations in 'deep techs', such as big data processing, artificial intelligence and cybernetics, will provide the advanced intelligence of the cloud, allowing, for example, the distribution of Command and Control (C2) functions, including to the pilot in his fighter. and provide key stakeholders in a mission with all relevant information in real time. "This will give Air Force decision makers an unprecedented level of awareness," says Paskowski.
But with great power comes a great responsibility. With the growing dependence on artificial intelligence on everything we do as "digital citizens", and the use of platforms such as ChatGPT and its impact on the workplace, the integration of AI at the heart of FCAS Air Combat Cloud presents new challenges. Questions such as 'to what extent will the system support the decision-making process?' or 'What are the ethical criteria that can be applied to the use of this technology?'

Control or be controlled: that's the question
In order to anchor ethical issues and legal principles in the FCAS project, Airbus and the Fraunhofer Institute came together in 2019 to launch a joint expert committee on the responsible use of technologies. It brings together interested parties from the German Air Force with universities, research institutes and a broad group of foundations, specialists in social sciences and engineering science design.
Based on this guidance, within FCAS Air Combat Cloud, AI will provide analysis of complex situations during multi-domain operations and recommend the most intelligent action in the correct sequence. The human will then validate the recommendations. If the operational pace is high, the human being will simply decide whether or not to veto the recommendations, and the subsequent processes will again be automated by AI. “Our European air defense system will always be under the full control of a responsible human operator and in all circumstances,” concludes Marc Paskowski.
Both technologically and militarily, the development of FCAS has the potential to establish new standards and revolutionize the use of air power.

The use of AI in Airbus
Airbus began integrating AI into its products and solutions in the 1990s, with applications for reading and interpreting satellite images.
OneAtlas imaging services harness the power of Airbus' constellation of optical and radar satellites with reliable AI and cloud technology to provide important information, for example, to combat deforestation, optimize agricultural yields and urban planning.
However, in the aeronautical sector, Airbus' Skywise big data platform collects data from 24,000 aircraft parameters, allowing airlines that subscribe to the service to perform predictive maintenance and improve the overall operational efficiency of their fleets.
Tags: airbusMilitary AviationFCAS - Future Combat Air System/Future Air Combat System
Sharing
tweet
Fernando Valduga
Fernando Valduga
Aviation photographer and pilot since 1992, has participated in several events and air operations, such as Cruzex, AirVenture, Dayton Airshow and FIDAE. He has work published in specialized aviation magazines in Brazil and abroad. Uses Canon equipment during his photographic work in the world of aviation.
Related news
WAR ZONES
AC-130J aircraft attacks militants in Iraq after first ballistic missile attack against U.S. positions
22/11/2023 - 16:00
MILITARY
F-35 fighters will cost Canada almost $54 billion in 45 years
22/11/2023 - 14:19
MILITARY
Indonesian Air Force receives new Dassault Falcon 8X aircraft
22/11/2023 - 14:03
MILITARY
Russian Air Force receives new batch of Su-34 fighter-bombers
22/11/2023 - 10:46
MILITARY
VIDEO: The impressive attack of the Houthis, with a Mi-171, on a cargo ship in the Red Sea
21/11/2023 - 23:09
BRAZIL
VIDEO: FAB celebrates 40 years of the T-27 Tucano aircraft with special paint
21/11/2023 - 19:30
Client PortalClient PortalClient PortalClient PortalClient PortalClient PortalClient PortalClient PortalhomeMain PageEditorialsINFORMATIONeventsCooperateSpecialitiesadvertiseabout
Cavok Brazil - Digital Tchê Web Creation
Commercial
Executive
Helicopters
HISTORY
Military
Brazilian Air Force
Space
Specialities
Cavok Brazil - Digital Tchê Web Creation
4 notes
·
View notes
Text
holy heck chunking!!
every chunk lives in a hashmap, everytime the camera is updated (and it switches chunks) it builds a linked list of 'active chunks', which is what you're seeing pop in/out.
also rendering itself is considered a task, which is scheduled to run every 1/60th of a second. there's a tiny task scheduler which tells the OS to sleep the program until the next task is scheduled, leading to the CPU sleeping majority of the time :3. the entire program is single threaded
also lots of behind the scenes changes, entities are actually refcounted now since im planning to share them across lua, and typically you'd use a std::shared_ptr for that in c++, incrementing the ref count everytime the object is shared to lua, and decrementing the ref count everytime lua decides to garbage collect it.
4 notes
·
View notes
Text
"Essential Tips for Beginners Starting Their Fitness Journey "
Beginning an exercise routine daily schedule as a fledgling can be both energizing and testing. It's fundamental for approach it in a protected and practical way to stay away from wounds and remain propelled. Here are a moves toward assist novices with starting their exercise process:
Talk with a Medical care Proficient: Prior to beginning any activity program, it's fundamental to talk with a medical services proficient, particularly on the off chance that you have any previous ailments or concerns. They can give customized guidance in view of your wellbeing status.
Put forth Practical Objectives: Figure out what you need to accomplish through your exercises. Whether it's working on generally wellness, getting in shape, developing fortitude, or lessening pressure, putting forth sensible and explicit objectives will assist you with remaining on track and roused.
Begin Gradually: Assuming you're new to work out, start with low-power exercises to give your body time to adjust. Try not to propel yourself excessively hard first and foremost, as this can prompt burnout or wounds. Bit by bit increment the power and span of your exercises as you progress.
Pick Exercises You Appreciate: Find proactive tasks that you really appreciate, as this will make it more straightforward to adhere to your daily schedule. Whether it's moving, swimming, yoga, climbing, or strength preparing, there are various choices to investigate.
Warm-Up and Chill Off: Consistently start your exercise with a get ready to set up your body for work out. A warm-up can incorporate light cardio works out, dynamic stretches, or portability drills. Moreover, finish every exercise with a cool-down and static extending to assist your muscles with recuperating.
Stand by listening to Your Body: Focus on your body and how it answers work out. Assuming that something feels awkward or excruciating, stop the action and look for exhortation if necessary. It's generally expected to encounter some muscle irritation, yet serious agony ought not be overlooked.
Think about Proficient Direction: In the event that you're uncertain about where to begin or how to perform practices accurately, think about looking for direction from an ensured wellness mentor. They can make a customized exercise plan in view of your objectives and show you legitimate structure and methods.
Be Steady: Consistency is vital to seeing improvement. Go for the gold, regardless of whether they are short, instead of inconsistent serious meetings. Building a propensity takes time, so show restraint toward yourself.
Rest and Recuperation: Permit your body sufficient opportunity to rest and recuperate between exercises. This forestalls overtraining and lessens the gamble of injury. Get sufficient rest and consider integrating dynamic recuperation exercises, as delicate yoga or strolling, into your everyday practice.
Remain Hydrated and Eat Well: Legitimate hydration and a fair eating regimen are fundamental for supporting your exercises and by and large wellbeing. Hydrate over the course of the day and fuel your body with nutritious food sources.
Keep in mind, beginning a gym routine is an excursion, and it's OK to advance at your own speed. Praise your accomplishments, regardless of how little, and remain roused by zeroing in on the positive changes you experience in your general prosperity.
3 notes
·
View notes
Text
Affiliate Marketing Management Sydney
In Australia, there are many affiliate marketing companies and agencies. These networks can help you make a lot of money by promoting products and services online. Some of them have a great reputation for performance.
It’s important to find a network that fits your needs and audience. A good one will offer a high commission and robust support. To know more Affiliate Marketing Management, visit the OZ Digital website or call 0240228675.
The right affiliate marketing strategy is essential for businesses looking to drive traffic and increase sales. It involves identifying your target audience and using the most effective marketing methods to reach them. This includes SEO, PPC, and content marketing.
Creating relevant, quality affiliate content is key for affiliate marketers. This will help you to build trust with your customers and increase conversions. Moreover, it will also enable you to earn more commissions. For example, writing reviews is a great way to generate interest in products and services that you promote.
In Australia, there are many high-quality affiliate programs that offer a wide range of products to choose from. You can find them by searching for a specific category or brand. Many programs provide affiliates with tools that help them to maximise their earning potential. These include microsites, email lists, and websites. Some also offer social media promotions and influencer marketing. These programs are ideal for small business owners, who want to reach a larger audience without the hassle of doing it themselves.
Whether your brand is a small startup or an international ecommerce business, an affiliate program can bring in new customers and increase sales. The key to success is finding the right affiliates, who are authentic and have a strong audience following. You can use social media or a search engine to find influencers in your industry niche and recruit them to your program.
Bloggers are another good option for affiliate marketing. They often have a dedicated audience and a niche in which they specialize. This makes them more likely to recommend products that will meet the needs of their audience. Moreover, you can look for bloggers with an existing audience that overlaps with your target audience.
You can also consider B2B affiliates, such as speakers and experts in your industry. For example, if you sell electric toothbrushes or skincare products, you can include dentists and estheticians in your affiliate program. Alternatively, you can promote your affiliate link through LinkedIn groups that are targeted to your industry niche.
A well-run affiliate program needs to be monitored regularly to ensure that it is meeting its objectives. Whether you’re tracking your commissions, analyzing ROI, or measuring incremental sales, you need to be able to see which links are converting and which ones aren’t. This will help you to identify the best opportunities for improvement and increase your revenue.
Affiliate software with reporting features can help you keep track of important information in one place. This can save you time and money, and it can also prevent you from losing track of important data. Post Affiliate Pro, for example, has an audit log that keeps a record of every change in your system and helps you determine responsibility.
One of the most common challenges in affiliate marketing is finding a way to reach your audience. As a result, it is important to use all the tools at your disposal to connect with your target audience. One way to do this is by associating your brand with names that your audience trusts.
Affiliate marketing campaigns allow e-commerce and lead generation websites ('the advertiser') to generate cost-effective traffic and sales from adverts or text links on third-party websites ('the publisher'). Payment is made on a performance basis, with the advertiser paying the affiliate for new leads or sales generated by the campaign.
Many affiliate programmes are managed by specialised companies that provide management services to bring suitable advertisers and affiliates together. These companies track the traffic, handle payments and control campaigns online in return for an initial setup charge, a monthly management fee and a small commission on each affiliate payment. To know more Affiliate Marketing Management, visit the OZ Digital website or call 0240228675.
#seo marketing brisbane#digital marketing gold coast#digital marketing agency perth#seo#seo agency#seo marketing adelaide#digital marketing perth#digital marketing agency brisbane#digital marketing brisbane#marketing strategies#affiliate marketing agency#affiliate marketing management#mobile marketing services#mobile marketing agency
2 notes
·
View notes
Link
1 note
·
View note
Text
10 Benefits of Implementing SAFe in Your Organization
In today’s rapidly evolving business landscape, organizations are under pressure to deliver value faster, adapt to changing markets, and foster innovation at scale. The Scaled Agile Framework (SAFe) has emerged as a leading solution for enterprises seeking to scale Agile practices across multiple teams and departments. Implementing SAFe certification within your organization is more than just a badge of honor—it’s a strategic investment that delivers measurable business outcomes. Here are the top 10 benefits of adopting Implementing SAFe certification in your organization:
1. Alignment Across the Organization
SAFe certification ensures that every team, department, and leader operates with a shared understanding of goals, roles, and processes. This unified approach eliminates chaos and confusion, enabling everyone to work toward common business objectives and reducing miscommunication.
2. Improved Time-to-Market
By streamlining workflows and eliminating inefficiencies, SAFe enables organizations to deliver products and services to the market significantly faster. Certified teams leverage Program Increments (PIs) and Agile Release Trains (ARTs) to plan, execute, and release with speed and agility—often improving time-to-market by 30% to 75%.

3. Enhanced Collaboration and Communication
SAFe promotes cross-functional collaboration, breaking down silos and fostering teamwork across departments. Certified professionals are equipped to facilitate better communication, ensuring that all stakeholders are aligned and informed throughout the project lifecycle.
4. Increased Productivity
Organizations implementing SAFe certification report productivity improvements ranging from 20% to 50%. By optimizing workflows and empowering teams to focus on high-priority tasks, SAFe helps organizations do more with less.
5. Superior Product Quality
Continuous integration, testing, and quality assurance are at the heart of SAFe. Certified teams are trained to catch defects early, reduce rework, and consistently deliver high-quality products and services that meet or exceed customer expectations.
6. Better Risk Management
SAFe’s structured approach to planning and execution allows organizations to identify and mitigate risks early. Enhanced transparency and real-time visibility into project progress help leaders make informed decisions and address issues proactively.
7. Higher Employee Engagement and Morale
SAFe empowers teams with autonomy and accountability, fostering a culture of ownership and continuous improvement. This not only boosts productivity but also enhances job satisfaction and employee retention.
8. Stronger Customer Focus
SAFe certification trains teams to prioritize customer needs and respond quickly to feedback. This customer-centric mindset leads to higher satisfaction, loyalty, and long-term business success.
9. Greater Return on Investment (ROI)
By reducing waste, improving efficiency, and accelerating delivery, SAFe delivers measurable ROI. Organizations see increased revenue, cost savings, and a decisive competitive edge as a direct result of SAFe implementation.
10. Future-Proofing the Organization
In a hyper-competitive, ever-changing market, agility is not optional. SAFe-certified organizations are better equipped to innovate, adapt to disruptions, and stay ahead of the competition by fostering a culture of learning and adaptability.
Conclusion
Implementing SAFe certification in your organization is a transformative step that drives alignment, accelerates delivery, and builds a resilient, customer-focused culture. The benefits are clear: higher productivity, better quality, improved morale, and a stronger bottom line. As more enterprises embrace Agile at scale, SAFe certification stands out as a proven path to sustainable business growth and long-term success.
0 notes
Text
Transforming Ideas into Impactful Digital Products with Wenbear Technology
In the rapidly evolving world of digital transformation, the real challenge isn’t just having a great idea—it’s executing that idea in a way that delivers tangible impact. At Wenbear Technology, we believe that innovation is only as valuable as its implementation. We specialize in transforming visionary concepts into robust, scalable, and user-focused digital products that drive growth and efficiency across industries.
From startups aiming to disrupt markets to enterprises looking to enhance their digital capabilities, our tailored software solutions are designed to meet unique business goals. Here's how Wenbear Technology turns ideas into digital realities.
1. From Vision to Strategy: Laying the Groundwork
Every successful product starts with a vision. But turning that vision into a scalable digital solution requires a thoughtful, strategic foundation. Our process begins by understanding your business model, challenges, and objectives. This Discovery Phase helps us analyze:
Who your target users are
What pain points your idea solves
Which technologies are best suited
The market opportunities and competitors
We align business objectives with technological feasibility, ensuring that every decision made is intentional and growth-oriented.
2. User-Centric Design: Creating Experiences That Matter
At Wenbear, we believe that the design of a product should not only look great but also function effortlessly. Our UX/UI experts create intuitive interfaces that are visually appealing and easy to navigate.
We adopt a Design Thinking approach, focusing on:
Empathy mapping to understand user behaviors
Wireframing and prototyping for faster feedback loops
Responsive and accessible designs
Visual branding that reflects your identity
Good design can make or break a digital product. That’s why we emphasize usability as much as aesthetics, ensuring an engaging experience across all devices and platforms.
3. Agile Software Development: Bringing Your Product to Life
Once the designs are finalized, our skilled development team brings the vision to life using agile methodologies. Our developers are proficient in a wide array of programming languages, frameworks, and tools to create high-performance software tailored to your specific needs.
We specialize in:
Web and Mobile App Development
Cloud-Based Platforms
Custom CRM and ERP Solutions
AI-Powered Applications
eCommerce Platforms
With Wenbear, every sprint delivers incremental value, giving you full visibility into the development process and allowing you to test features as they evolve.
4. Scalability and Security First
We build products with the future in mind. As your business grows, your software must scale to support increased user loads, data volumes, and feature complexity. Our solutions are architected for scalability from day one.
Security is another key pillar. We implement:
Data encryption
Multi-level authentication
Regular code audits
Compliance with GDPR, HIPAA, and other standards
Your users’ trust and data integrity are non-negotiable, and we prioritize them at every step of development.
5. Seamless Integrations and Modern Tech Stacks
In the digital world, no product exists in isolation. Our solutions are built for seamless integration with other tools, platforms, and APIs you use—whether it’s payment gateways, analytics tools, third-party CRMs, or cloud storage solutions.
We work with cutting-edge technologies, including:
React, Vue, and Angular for frontend
Node.js, Django, Laravel for backend
Flutter, Swift, Kotlin for mobile
AWS, Azure, GCP for cloud
AI and ML for smart automation
This ensures not only performance and efficiency but also future readiness.
6. Testing and Quality Assurance
At Wenbear Technology, quality isn’t an afterthought—it’s an integral part of our development lifecycle. Our QA specialists conduct rigorous testing at every stage to ensure the product works flawlessly under all conditions.
We perform:
Functional testing
Regression testing
Load and stress testing
Security testing
Cross-device and browser compatibility checks
With comprehensive testing protocols, we minimize bugs, enhance performance, and ensure a smooth user experience.
7. Product Launch and Post-Deployment Support
The product launch is just the beginning of your digital journey. Wenbear provides a full suite of launch services including cloud deployment, DNS setup, and performance monitoring to ensure a smooth go-live experience.
Our post-launch support includes:
Regular maintenance and updates
24/7 technical support
Real-time performance monitoring
User feedback analysis
Feature rollouts and optimization
With Wenbear, you’re not left to navigate post-deployment challenges alone. We’re your long-term technology partner.
8. Real Success Stories
Our commitment to excellence has helped clients across industries create remarkable digital products:
Retail: A scalable, cloud-based POS system that automated inventory across multiple locations.
Healthcare: A HIPAA-compliant CRM that streamlined patient engagement and appointment scheduling.
Education: A gamified e-learning platform with AI-based content recommendations.
Fitness: A sports and gym management software to handle memberships, billing, and class bookings.
Each project reflects our dedication to innovation, collaboration, and delivering business value.
9. Why Wenbear Technology?
What makes Wenbear a trusted partner for digital product development?
Client-Centric Approach – We build with you, not just for you.
Industry Expertise – Deep experience across fintech, healthtech, edtech, and more.
Flexible Engagement Models – Whether it’s a fixed scope project or a long-term partnership.
Proven Track Record – Dozens of successful launches with glowing client testimonials.
Scalable Teams – We adapt resources based on your project’s changing demands.
We combine creativity with technical brilliance to turn your ideas into products that make an impact.
Visit us www.wenbear.com
0 notes
Text
¶ … HIPAA Giving employees the freedom to gain control over their medical records regardless of their employer is one of the greatest benefits of the Health Information Portability and Accountability Act of 1996 (HIPAA) (Kibbe, 2005). The HIPAA Act, which formally went into effect in Aril 21, 2005 and concentrates on defining standards for administrative, technical and physical security procedures (Miller, 2006). The HIPAA Act required healthcare organizations to fundamentally re-order and re-define the processes they used for capturing, analyzing, recording and archiving healthcare records. The strategies healthcare organizations are relying on are not incremental, yet more strategic in focus, creating Enterprise Content Management (ECM) frameworks (Secor, Laplante, 2006). These ECM Frameworks are giving healthcare organizations more flexibility to serve patients yet also significantly increasing accountability and security policies, and systems in place. The critical success factor of ECM Frameworks is the development and successful integration with existing Enterprise Source Planning (ERP) systems, which are used for operating these healthcare organizations (Pumphrey, Trimmer, Beachboard, 2007). In addition, ECM Frameworks give healthcare providers a greater control over their information lifecycles and also make them more agile in responding to patients' needs as a result (Volonino, Sipior, Ward, 2007). The ECM frameworks used for ensuring HIPAA compliance are discussed in this paper with an orientation towards accountability and auditability, two areas that the HIPAA Act is highly prescriptive in its definition of (Miller, 2006). Background The healthcare industries' unmet needs when it comes to HIPAA compliance are forming the foundation for a series of product and solution development strategies on the part of many software, hardware and services companies globally. What's so significant about the unmet needs of the healthcare providers in the area of HIPAA compliance is the direct effect the lack of fulfillment of these needs are having on the organizational goals of entire medical institutions including hospitals, clinics and individual practices focused on security and auditability. Reducing diagnosis errors, coordinating on treatment plans across patients, analyzing the extent of care delivered by clinicians and securing these results, and alleviating the need for medical professionals to transcribe data from one computer system to another are all major unmet needs in the healthcare industry. In each of these process areas there is ample opportunity for security lapses and patient data being compromised. The U.S. And other nations have set four major objectives in the defining of electronic medical records systems to ensure compliance with HIPAA and comparable regulatory standards globally for health information security. These include the following: keeping healthcare professionals informed as to new developments in security through a Web-based portal that is continually refreshed with new prescriptive guidance on increasing security levels; interconnecting healthcare organizations' security and it staffs so they can share best practices on advances in healthcare information management globally; personalizing and better analyzing patient data security strategies; more effective use of networks to streamline ECM frameworks and make data use more process-centric and anticipatory of patients' needs (Dantu, Oosterwijk, Kolan, Husna, 2007); and improving broader population health by using it from the content of websites for preventative health programs that are also aimed at reducing the need for visits in the first place (Hall, 2008). These four broad goals are driven from the unmet needs of healthcare organizations in the area of data security to ensure compliance to the HIPAA standard. The unmet needs of the healthcare community that are in turn driving the greater application and adoption of it-based strategies for ensuring HIPAA compliance are as follows: A major unmet need in delivering more timely and more accurate access to information including patient records, patient imagery, test results and treatment results while at the same time ensuring a high level of security. At present there are many manually-based processes, for example calling a local clinic and having to get a clerk on the phone to get a specific record. This is a major unmet need as it relates to security, responsiveness, and speed of service to both the patient and the healthcare professional delivering a diagnosis or treatment plan. The most pressing unmet need is to have these records online in a secured framework, integrated with many other systems including patient billing and accounting, patient history, and diagnosis analysis to accomplish the goal of delivering a 360 degree view of the patient on every inquiry (Dantu, Oosterwijk, Kolan, Husna, (2007). Lack of consistency in existing manual processes aimed at the managing of chronic conditions leaves these records highly susceptible to security breaches. This unmet need emanates from the currently high levels of miscommunication inherent in the complex processes of the healthcare community between specialist MDs and patients. What exacerbates this lack of communication is that each treatment plan is slightly different and requires a slightly different approach to managing the security of the information. Greater levels of professional productivity through better collaboration, scheduling and coordination of healthcare professionals, administrators and specialist MDs. This isn't simply about being able to see more patients; it's about being able to have a more comprehensive view of the patient treatment plans for advanced diseases and conditions, and keeping these treatment plans confidential and secure. This includes drug interactions, histories of treatments, preferences in treatment approaches by physicians and any unforeseen interactions with previous treatment programs. What HIPAA is forcing many companies is to integrate their many diverse and disparate systems together to allow for network-wide security strategies (Dantu, Oosterwijk, Kolan, Husna, (2007). Currently healthcare professionals have to look either through multiple systems or through a series of books to figure out what if any interactions there are to medications for example, and in this process risk disclosing specific patient data as they search for information. Appling it strategies to this unmet need to ensure HIPAA compliance includes integrating all databases internally to the practice in addition to subscribing to external information sources, all unified with a common search technology that would, from a single query, provide the medical professional with the information requested. Another aspect of this unmet need of increasing productivity is the scheduling of appointments between clinicians and specialist MDs in addition to those with patients. Moving away from manual systems in this area is also a critical step for higher levels of security and greater compliance to the HPAA standards, making organizations more capable of passing audits in the process. Streamlining and making more efficient processes for patients to fill out their clinic paperwork, check on the status of their medications, and also provide feedback in the form of customer satisfaction surveys is a major unmet need is creating a HIPAA-compliant full-cycle approach to patient care. One of the most glaringly obvious unmet needs in the entire medical profession is this specific area of streamlining what is called "on boarding" of new patients and measuring their satisfaction with the level of service delivered. An integral part of this process is the development of secured (Kibbe, 2005). The first series of processes, those of signing up new patients is fraught with inefficiencies and errors, and making this online, even for the a medical centers' staff is a potential major improvement. Capturing patient feedback on what is going well and what isn't is also a critical unmet need; only a very small percentage of healthcare professionals and specialists get feedback on how their treatment programs are working, how their empathy skills are being perceived, and in short, how satisfied the patients. Yet all this data needs to be managed to the HIPAA standards, just as the more complex data regarding treatment programs. Lack of integration with health services providers, specifically those paying for the care of patients including HMOs, PPOs and health insurance organizations. This is perhaps one of the aggravating unmet needs in the medical profession and is exacerbated again in the area information security due to the fact that a person's financial stability is affected by how well these processes work. The lack of it systems-level integration between health services providers, HMOs, PPOs and health insurance organizations significantly slows down the time required to fulfill claims for patients, and in turn slows down the finances of clinics, physician offices, and hospitals. The time lag in these processes also poses a significant security risk that HIPAA is targeted to resolve as well. Through the integration of it systems beneath these processes, healthcare organizations can gain greater compliance with HIPAA standards. Clearly the need for greater levels of integration specifically in this area is critical, and as a major unmet need being addressed through it strategies, this forms the basis for the framework emerging for comprehensive electronic medical record systems that make HIPAA compliance more achievable. There are many additional unmet needs throughout the healthcare community and the five mentioned in this section are the most prevalent. Combined these five unmet needs are the catalyst for the re-engineering of processes in healthcare organizations towards HIPAA compliance. What is emerging from it strategies aimed at resolving these unmet needs is a comprehensive framework. Figure 1, Electronic Medical Records Systems Architecture, defines the it architecture that many healthcare providers are opting for to selectively apply it applications and components to the unmet needs in their industry. Figure 1: Electronic Medical Systems Architecture Source: (Cahn, 2001) The core building blocks of this framework include the presentation and client layers, where web-based applications aligned with the needs of clinicians, specialist MDs and patients. The need for synchronization across Platform, Storage and Infrastructure and Integration areas of this framework dictate the speed and accuracy of responses to all users of the system. Thinking of this framework as the foundation that the specific processes that clinics, practices and hospitals rely on to complete daily tasks to accomplish their goals and objectives while at the same time ensuring a high level of security across each component. The integration and security requirements are critical for HIPAA compliance. Another approach to viewing the framework that is emerging from it providers addressing the unmet needs of a medical practice area is shown in Figure 2. This is a framework that has foundational elements focused on Security and Audit Control to protect the privacy of clinicians, MDs, and patients, in addition to making Records Management, Business Process Management, and a Portal Framework available as a system-wide resource for the specific collaboration, content management, search and retrieval implementation plans to act as a unifying it strategy across the diverse patient records in all the systems in a clinic, practice or hospital. Note that this framework also includes support for Expert Network and Learning Management applications to also increase medical professionals' productivity as well. Figure 2: Electronic Medical Record Systems Hierarchy Source: (Wheatley, 2005) Conclusion At the intersection of unmet needs in the healthcare community and the advances being made in enterprise content management, digital asset management, security, collaboration technologies including portals is the emergence of it strategies to fulfill the requirements of HIPAA compliance. There are literally dozens of unmet needs in each discipline of the medical profession, yet for purposes of this paper the top five most prevalent ones are cited. These unmet needs in fact form the foundation of frameworks the it industry is defining strategies to addressing the needs of patient confidentiality and adherence to the standards of the HIPAA standards and regulations. The focus on making more of a pervasive, integrated platform of information that delivers a 360 degree view of the patient, also allowing the patient to comment on their experiences and their satisfaction, is what will become commonplace in the next five years. The integrative role of search technologies as an it approach to unifying all forms of content has also already arrived, and the largest clinics are acting as early adopters, showing the Return on Investment (ROI) of this strategy. All of these developments will be possible based on the advances made in system and process integration due to the widespread adoption of the HIPAA standard. References David Cahn (2001, November). ECM fosters the future it framework. MSI, 19(11), 36-38. Retrieved September 22, 2008, from ABI/INFORM Global database. (Document ID: 90248042). https://www.paperdue.com/customer/paper/hipaa-giving-employees-the-freedom-27903#:~:text=Logout-,HIPAAGivingemployeesthefreedom,-Length7pages Ram Dantu, Herman Oosterwijk, Prakash Kolan, Husain Husna. (2007). Securing medical networks. Network Security, 2007(6), 13. Retrieved September 28, 2008, from ABI/INFORM Global database. (Document ID: 1294137471). Barry Hall (2008). Health Incentives: The Science and Art of Motivating Healthy Behaviors. Benefits Quarterly, 24(2), 12-22. Retrieved September 26, 2008, from ABI/INFORM Global database. (Document ID: 1481467951). David C. Kibbe (2005). 10 STEPS to HIPAA SECURITY COMPLIANCE. Family Practice Management, 12(4), 43-9. Retrieved September 24, 2008, from ABI/INFORM Global database. (Document ID: 834471611). Julia E. Miller (2006). HIPAA Privacy and Security. Benefits Quarterly, 22(3), 64. Retrieved September 29, 2008, from ABI/INFORM Global database. (Document ID: 1110730401). Lela D "Kitty" Pumphrey, Ken Trimmer, John Beachboard. (2007). Enterprise Resource Planning Systems and HIPAA Compliance. Research in Healthcare Financial Management, 11(1), 57-75. Retrieved September 22, 2008, from ABI/INFORM Global database. (Document ID: 1426086661). Glen M. Secor, Mary Laplante. (2006, December). Securing Your Content's Compliance. Document Processing Technology, 14(7), 18-20. Retrieved September 27, 2008, from ABI/INFORM Global database. (Document ID: 1174111381). Linda Volonino, Janice C. Sipior, Burke T. Ward. (2007). Managing the Lifecycle of Electronically Stored Information. Information Systems Management, 24(3), 231-238. Retrieved September 24, 2008, from ABI/INFORM Global database. (Document ID: 1314618961). Malcolm Wheatley (2005, April). Harness company knowledge. Manufacturing Business Technology, 23(4), 40-42. Retrieved September 295, 2008, from ABI/INFORM Global database. (Document ID: 821076261) Read the full article
0 notes