#Protocol blockchain
Explore tagged Tumblr posts
Text
Mimblewimble – Protocol Blockchain axat pe Confidențialitate
IntroducereMimblewimble este un protocol blockchain conceput cu accent pe confidențialitate, securitate și scalabilitate. Inițial propus de un dezvoltator anonim, acest protocol revoluționează modul în care se efectuează tranzacțiile, asigurând anonimatul și protejând datele financiare ale utilizatorilor. În plus, Mimblewimble oferă o fungibilitate sporită, eliminând diferențele între monedele…
#blockchain#Scalabilitate#criptografie#confidentialitate#Zero-Knowledge Proofs#Mimblewimble#tranzacții sigure#Fungibilitate#Anonimitate#Protocol blockchain
0 notes
Text
Unlocking the Power of Kaspa (KAS): A Deep Dive into the Altcoin's Impressive Performance and Growth Potential
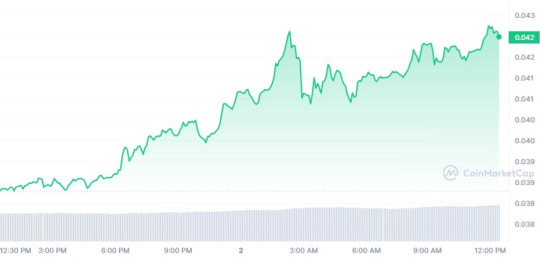
Kaspa (KAS) has been on an impressive bullish run, maintaining an upward trajectory for three consecutive days, positioning itself as one of the top-performing altcoins in July. At the time of this writing, Kaspa is trading at $0.04223, representing a notable 13.01% increase in the past 24 hours. This impressive uptrend has led to an astounding surge of over 80.52% in the trailing 30-day period.
Kaspa's Enigmatic Power in the Blockchain World
Kaspa stands out in the blockchain landscape as it operates on a Directed Acyclic Graph (DAG)-powered proof-of-work (PoW) platform. Its emergence coincided with the need for an Ethereum (ETH) alternative after the transition of Ethereum from PoW to proof-of-stake (PoS) last year. Growth Drivers for Kaspa - Diverse Community and Increased Adoption: Kaspa's native community has been a driving force behind its growth, accumulating and supporting the project consistently. Furthermore, the entry of buyers from other protocols, like Ethereum, has contributed to bolstering Kaspa's appeal across the entire crypto space. - Utility and Performance Focus: Unlike many competitors in the market, Kaspa is prioritizing utility and performance over mere hype. The platform boasts an impressive throughput rate, capable of processing up to 100 blocks per second, making it exceptionally suitable for enterprise adoption. - Developer Team and Functionality Upgrades: The dedicated team of developers working on Kaspa has been instrumental in continuously enhancing its functionalities. Recently, they introduced a new update, further fortifying the platform's capabilities. Climbing the Ranks Kaspa's recent impressive growth has propelled it up the rankings, currently standing at the 208th position. However, there is a prevailing perception that the coin is still undervalued. With a series of upgrades and dApps in the pipeline, Kaspa holds the potential for further uptrend before the end of Q3.
Conclusion
Kaspa (KAS) has exhibited remarkable bullish momentum, making it one of the standout performers among altcoins in July. Its Directed Acyclic Graph (DAG)-powered proof-of-work (PoW) platform sets it apart in the blockchain world, and with the support of a dedicated community and growing adoption, its appeal continues to expand. Focusing on utility and performance, Kaspa stands out as a strong contender for enterprise adoption. As the team of developers keeps upgrading the platform, the potential for further uptrend remains high, positioning Kaspa for a promising future in the crypto market. For more articles visit: Cryptotechnews24 Source: u.today
Related Posts
Read the full article
#altcoin#Blockchain#CryptoNews#DAG#DirectedAcyclicGraph#ETH#Ethereum#growthdrivers#KAS#kaspa#performance#PoW#proof-of-work#protocol#utility
2 notes
·
View notes
Text
Metaverse Marketing Services to Elevate Virtual Brands
Level up your project with Metaverse Marketing Services from The Kollab. We craft immersive campaigns that drive engagement, grow communities, and boost visibility across virtual platforms. Our Web3-native team connects you with metaverse influencers, gamers, and creators to power brand awareness. Discover how our strategies bring real impact in digital worlds.

#NFT Services#NFT Marketing#Blockchain Services#Blockchain Technology#Blockchain Technology Services#Metaverse Marketing#Metaverse Marketing Agency#Crypto Marketing#Web3 Marketing#Web3 Marketing Strategies#Blockchain Protocol#Web3 Marketing Tips#DeFi Market Analysis#Crypto Social Media Management Services#Cryptocurrency Marketing Agency#NFT Marketing Services#Web3 Influencer Marketing#Crypto Influencer Marketing#Web3 Digital Marketing Agency#Best Web3 Marketing Agency#Crypto Digital Marketing Agency#Best Crypto Marketing Agency#Kol Management Agency
0 notes
Text
#BYDFi#crypto trading#decentralized finance#DeFi#cryptocurrency#blockchain#digital assets#trading platform#crypto exchange#BYDFi features#crypto investment#yield farming#staking#DeFi protocols#crypto trading tools.
0 notes
Text
DAO-Based Music Communities: The Future of Fan Engagement
Making a Scene Presents DAO-Based Music Communities: The Future of Fan Engagement How Decentralized Autonomous Organizations (DAOs) empower musicians and fans to work together, vote on decisions, and share profits within a community-driven music ecosystem The traditional music industry has always thrived on control—labels control releases, platforms control algorithms, and a handful of middlemen…
#Aragon DAO#blockchain music#blockchain music revolution#Catalog music NFTs#community-owned music#DAO music communities#DAO music ecosystem#DAO music platform#DAOhaus#decentralized fan engagement#decentralized music industry#Discord fan community#fan-powered music#Gnosis Safe treasury#Guild.xyz token gating#indie artist Web3#indie musician DAO#Juicebox music funding#Lens Protocol Web3 social#Mirror.xyz music crowdfunding#music DAO tools#Music NFTs#music token economy#NFT music drops#smart contracts music#Snapshot DAO voting#Sound.xyz music NFTs#Web3 for musicians#Zora NFT platform
0 notes
Text
The FUTURE of crypto is HERE 💡 Say goodbye to dead coins & hello to AI-powered profits! 🤖💰 Meet $UNSD, the game-changer of 2025! 🔥💎 Plus 3 hidden gems 💎 flying under the radar 🚨 Ready to earn while you SLEEP? 😴🧠 Tap in & secure your spot early 🕒 #Crypto #AI #Web3 #Altcoins #Unstaked #CryptoGains #BullRun2025 #PassiveIncome 💸👀 Don’t miss this wave
#$UNSD#AGIX#AI automation#AI blockchain#AI crypto#best altcoins#blockchain#crypto#crypto agents#crypto investment#Crypto news#crypto presale#cryptocurrency#DeFi#earn with crypto#FET#Fetch.ai#future of crypto#OCEAN#Ocean Protocol#passive income#Proof of Intelligence#SingularityNET#smart crypto#top crypto 2025#trending coins#Unstaked#viral crypto#Web3
0 notes
Text
Cybercriminals are abusing Google’s infrastructure, creating emails that appear to come from Google in order to persuade people into handing over their Google account credentials. This attack, first flagged by Nick Johnson, the lead developer of the Ethereum Name Service (ENS), a blockchain equivalent of the popular internet naming convention known as the Domain Name System (DNS). Nick received a very official looking security alert about a subpoena allegedly issued to Google by law enforcement to information contained in Nick’s Google account. A URL in the email pointed Nick to a sites.google.com page that looked like an exact copy of the official Google support portal.
As a computer savvy person, Nick spotted that the official site should have been hosted on accounts.google.com and not sites.google.com. The difference is that anyone with a Google account can create a website on sites.google.com. And that is exactly what the cybercriminals did. Attackers increasingly use Google Sites to host phishing pages because the domain appears trustworthy to most users and can bypass many security filters. One of those filters is DKIM (DomainKeys Identified Mail), an email authentication protocol that allows the sending server to attach a digital signature to an email. If the target clicked either “Upload additional documents” or “View case”, they were redirected to an exact copy of the Google sign-in page designed to steal their login credentials. Your Google credentials are coveted prey, because they give access to core Google services like Gmail, Google Drive, Google Photos, Google Calendar, Google Contacts, Google Maps, Google Play, and YouTube, but also any third-party apps and services you have chosen to log in with your Google account. The signs to recognize this scam are the pages hosted at sites.google.com which should have been support.google.com and accounts.google.com and the sender address in the email header. Although it was signed by accounts.google.com, it was emailed by another address. If a person had all these accounts compromised in one go, this could easily lead to identity theft.
How to avoid scams like this
Don’t follow links in unsolicited emails or on unexpected websites.
Carefully look at the email headers when you receive an unexpected mail.
Verify the legitimacy of such emails through another, independent method.
Don’t use your Google account (or Facebook for that matter) to log in at other sites and services. Instead create an account on the service itself.
Technical details Analyzing the URL used in the attack on Nick, (https://sites.google.com[/]u/17918456/d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/edit) where /u/17918456/ is a user or account identifier and /d/1W4M_jFajsC8YKeRJn6tt_b1Ja9Puh6_v/ identifies the exact page, the /edit part stands out like a sore thumb. DKIM-signed messages keep the signature during replays as long as the body remains unchanged. So if a malicious actor gets access to a previously legitimate DKIM-signed email, they can resend that exact message at any time, and it will still pass authentication. So, what the cybercriminals did was: Set up a Gmail account starting with me@ so the visible email would look as if it was addressed to “me.” Register an OAuth app and set the app name to match the phishing link Grant the OAuth app access to their Google account which triggers a legitimate security warning from [email protected] This alert has a valid DKIM signature, with the content of the phishing email embedded in the body as the app name. Forward the message untouched which keeps the DKIM signature valid. Creating the application containing the entire text of the phishing message for its name, and preparing the landing page and fake login site may seem a lot of work. But once the criminals have completed the initial work, the procedure is easy enough to repeat once a page gets reported, which is not easy on sites.google.com. Nick submitted a bug report to Google about this. Google originally closed the report as ‘Working as Intended,’ but later Google got back to him and said it had reconsidered the matter and it will fix the OAuth bug.
11K notes
·
View notes
Text

NOSTR Snapback Hat @ 21rebel
#JOIN THE FEDIVERSE#web3#NOSTR#crypto#ethereum#cybersecurity#blockchain#decentralized#cryptocurrency#protocol#21rebel#fediverse#merch
1 note
·
View note
Text
Harnessing Zero-Knowledge Protocols for Modern Authentication and Privacy
Introduction Zero-knowledge protocols represent an intriguing paradox in the realm of cryptographic technologies: they enable one party (the prover) to demonstrate knowledge of a secret to another party (the verifier) without disclosing the secret itself. Originating from foundational work by Goldwasser, Micali, and Rackoff, these protocols have evolved into powerful tools for secure…
#blockchain#blockchain referendum#Blockchain Technology#blockchain voting#Digital Democracy#e-democracy#e-participation#e-voting#Secure Voting#zero knowledge#Zero knowledge proof#Zero Knowledge Protocols#ZKP
0 notes
Text
The Promising Future of DeFi Yields: Surpassing Traditional US Money Funds
In recent years, the Decentralized Finance (DeFi) sector has witnessed exponential growth. As a result, experts predict that DeFi yields could surpass traditional US money funds. These projections come at a time when the Federal Reserve is expected to cut interest rates, which could significantly boost the DeFi market. This article delves into the reasons behind these projections, providing key…
#Aave#Bernstein analysis#blockchain#blockchain finance#blockchain technology#crypto economy#Crypto Investments#crypto market#crypto markets#crypto staking#crypto wealth#crypto yields#decentralized applications#decentralized assets#decentralized banking#decentralized borrowing#decentralized economy#decentralized exchanges#decentralized finance#decentralized finance growth#decentralized finance risks#decentralized finance trends#decentralized governance#decentralized lending#decentralized networks#decentralized protocols#decentralized wealth#DeFi#DeFi adoption#DeFi ecosystem
0 notes
Text
Empowering Lives with HRRKOIN’s Job Mining Protocol: Fostering Social Impact

#HRRKOIN#BlockchainRevolution#CommunityDriven#Innovation#GetInvolved#BlockchainTechnology#futureofwork#blockchain#Web3#AI#decentralized#hrwithblockchain#hrrevolution#hrrcoin#linkingjobs#https://hrrkoin.org/empowering-lives-with-hrrkoins-job-mining-protocol-fostering-social-impact/
0 notes
Text
Zero-Knowledge Proofs în Bitcoin: Securitate și Confidențialitate Avansate
Introducere Bitcoin a revoluționat sistemele financiare prin introducerea unui mod descentralizat de a efectua tranzacții, bazat pe o tehnologie blockchain transparentă și securizată. Totuși, această transparență, deși esențială pentru integritatea rețelei, ridică probleme privind confidențialitatea tranzacțiilor și a datelor financiare. În acest context, dovezile cu cunoștințe zero…
#Bitcoin privacy#inovații cripto#protocoale descentralizate#Tehnologie disruptivă#interactivitate#securitate tranzacțională#securitate informațională#algoritmi de criptografie#protocoale criptografice#digital privacy#dovezi cu cunoștințe zero#zkSNARK#zkSTARK#proof of knowledge#ZKP Bitcoin#blockchain privacy#confidential transactions#Pedersen commitments#range proofs#Tapscript#securitatea rețelei#distribuție blockchain#zero-knowledge protocols#non-interactivitate#Goldwasser#Micali#Rackoff#proof systems#proof-of-concept#confidentialitate
1 note
·
View note
Text
Solv Protocol Brings Bitcoin Staking to Base with New Liquid Staking Options, Expanding Bitcoin’s Role in the Onchain Economy
New York, September 12, 2024 – Solv Protocol, a leading Bitcoin staking platform, has announced Bitcoin staking for cbBTC holders on Base, an Ethereum Layer 2 offering secure, low-cost, and builder-friendly onchain development. With the launch of cbBTC, a wrapped Bitcoin asset by Base, Solv Protocol allows cbBTC tokens to be minted into SolvBTC, which can further be converted into SolvBTC.BBN —a…
0 notes
Text
Web3 Influencer Agency for Scalable Growth – The KOLLAB
The KOLLAB is a top-tier Web3 Influencer Agency connecting blockchain, NFT, and DeFi brands with powerful KOLs. Our Web3 influencer agency drives real results through targeted campaigns, community engagement, and creator-led storytelling. Partner with The KOLLAB to grow your Web3 project with trusted voices and authentic digital influence.

#KOL Partnerships#Social Media Management Services#Crypto PR#Crypto PR Agency#Crypto Public Relations#Earn Crypto Social Media#Crypto SEO#Crypto SEO Agency#Web3 Industries#Cryptocurrency Services#NFT Services#NFT Marketing#Blockchain Services#Blockchain Technology#Blockchain Technology Services#Metaverse Marketing#Metaverse Marketing Agency#Crypto Marketing#Web3 Marketing#Web3 Marketing Strategies#Blockchain Protocol#Web3 Marketing Tips#DeFi Market Analysis#Crypto Social Media Management Services#Cryptocurrency Marketing Agency#NFT Marketing Services#Web3 Influencer Marketing#Crypto Influencer Marketing#Web3 Digital Marketing Agency#Best Web3 Marketing Agency
0 notes
Text
Explore These Exciting DSU Micro Project Ideas
Explore These Exciting DSU Micro Project Ideas Are you a student looking for an interesting micro project to work on? Developing small, self-contained projects is a great way to build your skills and showcase your abilities. At the Distributed Systems University (DSU), we offer a wide range of micro project topics that cover a variety of domains. In this blog post, we’ll explore some exciting DSU…
#3D modeling#agricultural domain knowledge#Android#API design#AR frameworks (ARKit#ARCore)#backend development#best micro project topics#BLOCKCHAIN#Blockchain architecture#Blockchain development#cloud functions#cloud integration#Computer vision#Cryptocurrency protocols#CRYPTOGRAPHY#CSS#data analysis#Data Mining#Data preprocessing#data structure micro project topics#Data Visualization#database integration#decentralized applications (dApps)#decentralized identity protocols#DEEP LEARNING#dialogue management#Distributed systems architecture#distributed systems design#dsu in project management
0 notes
Text
Bitcoin Runes Protocol and Memecoins: A Look into 2024's Crypto Landscape

2024 has been a transformative year for cryptocurrencies. The Bitcoin halving in April and the emergence of the Bitcoin Runes protocol, developed by Casey Rodarmor (the creator of the Bitcoin Ordinals protocol) has significantly influenced the landscape of memecoins. This blog explores the impact of Bitcoin Runes and the resurgence of memecoins in the crypto market.
Limitations of BRC-20 Highlighting the Urgency of Better Solution
No Smart Contract Functionality: BRC-20 lacks support for smart contracts, limiting its application scope.
Limited Interoperability: Challenges in interoperability with other blockchains and wallets.
Limited Utility: Primarily for fungible assets, less suitable for complex token features.
Network Congestion: Contributes to slower transactions and higher fees due to Bitcoin blockchain limitations.
Bitcoin Runes - An Overview
Bitcoin Runes simplifies fungible token creation on the Bitcoin blockchain without relying on Bitcoin Ordinals. Utilizing OP_RETURN and UTXO models, the Bitcoin Runes protocol enhances efficiency and reduces network load.
Advantages of Bitcoin Runes:
Simplicity: Offers a simple way for token creation and management.
Increased Efficiency: Uses OP_RETURN for efficient and secure token transactions.
Broader Use Cases: Help crate helps various tokens, including stablecoins, tokenized assets, and more.
Improved Security: Secure token creation and transaction process.
Impact of Bitcoin Runes on MemeCoin Growth
The launch of the Bitcoin Runes protocol sparked the creation of numerous cryptocurrencies, particularly Bitcoin runes memecoins, leveraging enhanced functionality and security. Factors driving this surge include accessibility, innovation, and market dynamics.
Top 5 Memecoins on the Rise with Bitcoin Runes in 2024
KangaMoon (KANG)
Doge Killer’s (LEASH)
Book of Meme (BOME)
Shiba Inu (SHIB)
Coq Inu (COQ)
Final Words
Bitcoin Runes protocol promises to enhance Bitcoin’s utility and performance. Consulting blockchain experts like Antier can provide deeper insights into Bitcoin Runes memecoins, and related protocols, navigating the evolving landscape effectively.
0 notes