#Rest API explained
Explore tagged Tumblr posts
Text

A RESTful API (Representational State Transfer) is a web service architecture that follows a set of principles and constraints, aiming to simplify communication between systems. RESTful APIs use standard HTTP methods (GET, POST, PUT, DELETE) to perform operations on resources, which are identified by unique URIs (Uniform Resource Identifiers).
0 notes
Text
Why to Use Graphql Explained with Example for API Developers
Full Video Link - https://youtube.com/shorts/hO2vbzF4cNk Hi, a new #video on #graphql usage for #microservice #api #developers is published on #codeonedigest #youtube channel. @java #java #awscloud @awscloud #aws @AWSCloudIndia #Cloud #CloudComp
GraphQL is a syntax for requesting data. It’s a query language for APIs. It lets you specify exactly what is needed, and then it fetches just that — nothing more, nothing less. GraphQL is the solutions to common REST issues like over fetching and multiple network request. REST is an API design architecture that has become the norm for implementing web services. It uses HTTP to get data and…

View On WordPress
#graphql#graphql api#graphql api calls#graphql api developers#graphql api java#graphql api platform#graphql api project#graphql developer#graphql example#graphql example api#graphql example java#graphql example spring boot#graphql example tutorial#graphql explained#graphql explained in 100 seconds#graphql tutorial#graphql use#graphql vs rest#rest api limitations#use graphql in nodejs#use graphql in postman#why graphql
0 notes
Text
What is Gender Anyway?
Okay, I'm gonna be an essay blogger now. In this essay, I will talk about my experience with gender. This is gonna be very rambling, with little structure.
Upfront, I want to say that this is only my personal experience. If you agree with me, great; if not, that's fine.
I'm gonna start by saying something controversial and then explain what I mean: I don't understand trans people.
That's not to say I don't support them (because I do support them), but the idea of caring enough about your gender to make that kind of effort is foreign to me. I just don't understand.
To me, gender isn't something you are. It's not a core part of who I am. It doesn't define me. It doesn't really matter.
To put it simply, gender isn't something I am, it's just something I have.
Gender is just a label that, if I tell you, leads you to make assumptions about me; enough of those assumptions are accurate that the label has value for communication, but that's it. If it lacked that value, I would likely just discard it.
I truly don't care what people think about my presentation. In person, I'm obviously a guy, but if someone messed it up, I'd just be confused.
Now, storytime: I was sitting in that mental space for a while. I've sat on the periphery of the LGBTA+ community for a long while, mostly hanging out in aspec spaces, but i would try and keep up with the broader community, even if I didn't quite fit in.
I had an easy enough time finding labels for the rest of my identity: I'm aroace, more specifically aegosexual.
But I didn't really have a good label for my understanding of gender, so it just went unmentioned. I considered the agender label for a while, but it didn't fit. I had a gender, it just didn't matter.

I found the label cassgender by chance. I was reading a wiki, doing some research for a story, when that moment of "oh crap, that me" struck. Next thing I knew, I was looking for a cassgender subreddit (my social media of choice was reddit at the time; I left during the API situation)... and that felt right.
So, that's my story. To me, gender is basically just a sign that I can hold up that says a few things about me. That's it.
I genuinely don't understand having stronger feelings on the matter. For those who do, more power to you, but I personally just don't care.
In summary: What is gender anyway? A miserable pile of ideas! But enough talk, HAVE AT YOU!
12 notes
·
View notes
Note
sorry if this is too personal and pls ignore if you want to, i remember you said you work as a writer before. do you mind explaining what kind of writing you do and how you got into it?
i work as a technical writer. more specifically i work as a technical writer for a software company. right now i'm writing client-facing stuff but previously (at my last company) i worked on aws and rest api documentation for engineers
as for how i got into it, my degree is in something completely unrelated. but i went to a prestigious (relative to where i live) school with an extremely good internship program, and because the program wasn't restricted to only jobs related to your degree, i was able to get jobs in technical writing despite the zero correlation. i was really lucky to have my first few internships be with massive companies which helped build my resume for after i graduated
this is of course not the most representative experience. from what i can tell most technical writers are either a) people who majored in something like english and then took online certifications in coding, or b) people who majored in computer science, engineering, etc. who happen to be good writers
having an above average understanding of any coding language but especially javascript (typescript), go, python, and java helps a lot in landing jobs in tech. at my old job my coworker (who had the same responsibilities as me) really struggled with the workload that i found very easy, mainly because he didn't know any coding languages and so it took him a lot longer to parse the information we were given
5 notes
·
View notes
Note
I actually got it in my dream yesterday XD (lol I do dream strange things don’t I?)
So I thought of a little continuation on your AU when Cahaya was almost dying in Petir’s hands but he survived! Not actually well they took him to the hospital and doctors managed to make his condition stable but they also said something… lemme just show you this au
Petir was walking down in the corridor of Tempur A Medic Hall. His face was cold as ever sending shivers down to all those nurses, aliens and hospital wards who saw him. He would careless about it as his mind was still processing on the event that happened yesterday, where his youngest brother’s BP fluctuated and he almost lost his life if Daun would have not visited him on time.
flashback:
THE PATIENT’S BODY IS COLD!
GET THE STABALIZER!
Doctor he almost went flatline!
“Your brother is stable for now” said the Doctor with a heavy voice, “The impact on his body was quite big, his back bone, nerve cord, and lower hemisphere of brain is injured, let’s not mention about his fractured neck and hands, he will be with oxygen tank until and unless his lungs get habitual with normal breathing rate” explained the doctor in much more simpler language than possible, “Also-“ and he stops there.
“Also?” asked Air as he noticed none of his brothers in a condition to ask anything while handling a stressful Api
“We don’t know for how long he’ll be in coma”
Those words were like a sword which pierced the remaining pieces of heart for the siblings
flashback ends
Petir sighs as he remembered the incident that happened two weeks back. He had arrived in front of the certain room he was walking to. He slowly opens the door and sounds of machine beeping welcomes him. As he walks inside he notices his younger brother with brown cap looking at his youngest brother expressionless. He keeps his hand on his brother’s shoulder who turns and looks back at him.
He (Tanah) gives Petir a painful smile, turns back at Cahaya once more, gets up and leaves from there
Petir looks at the door which his brother had closed as he walked away. He takes a seat next to Cahaya and looks at him carefully remembering the events that happened from past two weeks.
Tanah avoids everyone, he rarely prefer speaking to anyone else rather than his brothers but he had become over protective towards them. He constantly blames himself for Cahaya’s condition as he was the one who allowed him to take part in this mission.
Api is always angry and stressful. His nightmares aren’t helping him either which has returned after years. If Air or Angin don’t calm him down time to time, Tempur A will become just like their destroyed Tapops station.
Air calms down Api and shows that he is unaffected but him eating very less than his usual appetite and sleeping more than he usually does is concerning.
Daun usually locks himself up in Cahaya’s room or lab. He talks to himself most of the time and tells himself the weird facts he read from textbooks not really understanding any of their meanings.
Angin’s fake smiles and outgoing nature makes him sick. He bakes the cookies and eat them and tell about it’s flaws and nutrients to himself mimicking a certain septuplet.
Fang….he don’t know what’s going on with Fang? He rarely sees Fang on Tempur A. He just knows that Fang takes in from one mission to another whether they are small or big, he just occupies himself with work while he or his brother’s can’t do that as they are provided with a month of break from Commander due to Vargoba’s incident.
Petir comes out of his trance and looks at the time.
Ah! Visiting hours are almost over
He looks at the unconscious figure of his brother
He combs his hair and says with a soft voice, “You fought well”
“…………..You did a great job”
“Get well soon Haya”
Unknown to him a lone tear falls from his left eyes and he wipes it off roughly
“Sorry Haya”
Petir takes off his hand which was brushing Cahaya’s hair while roughly brushing off the rest of tears which managed to flow from his eyes
He wipes them and looks at Cahaya
“Sorry…..Your Abang was not able to protect you”
He bites his lips and calms himself down breathing slowly and steadily.
He closes his eyes and opens them bringing back his straight face showing he never expressed anything and walks away before any nurse could walk in telling him that he should leave now
AUGGHSHHHHHH THIS HIT ME
this is so wonderful, your choice of dialogue for the doctor is amazing and worded like that is so brutal because it adds in the injuries that arent seen visibly but has such a big impact to the human body. those types of injuries being fatal in one way or another
the way the brother's are affected in such different ways, either reverting back to their old mental state or having an opposite mental mindset to their original. Petir just being understanding and silent, trying to keep it together like tanah.
the way he just responds with little words but you can tell he cares and is very much affected especially since that near death experience happened on his hands, before his eyes
Api having nightmares, knowing both he and Petir was there firsthand at the scene, he and him saw they're brother get pounced, hurt, launched. they saw how he reached out to them last moment(yeah this is a thing i dont know if i mentioned in this au)
The rest, perhaps feeling lots of guilt because they werent there to support them in fighting and preventing all of that from happening
If this is based on my au's characterization of them then angin being the opposite of his mental mindset would make it worse knowing he's more freely expressive of himself, and him keeping it in shows how affected he is. like damn. love this
10 notes
·
View notes
Note
Oh hi me again lol
Egyxos AU ask!
What if in the ep "The Hidden Enemy" at the end Kefer and Exaton didn't managed to change their bodys back to normal. Having Exaton (still in Kefer's body) run back to the Dark Pyramid and leaving Kefer (in Exaton's body) trying to explain to the rest of the Golden Army what is going on.
The worst part is that Exaton would try to use this as an advabtage to ruin his brother reputation.
Leo would probably feel the most gulty of all because he was couldn't help his mentor and doesn't know how to help
hi
Hard question but it will probably go something like this.
(Egyxos) The hidden enemy, bad ending
Warnings! : angsty.
////////////////////
The warriors in gold stood silently, giving each other glances of confusion.
Leo and Kefer who is stuck in his brothers body try to explain and they only get more confused looks.
"Listen to me! Me and Neith went to the dark pyramid! This is one of Exatons tricks! You have to believe me!" The last Pharaoh explains to the warriors in his best ability.
"How can we trust you?! You could have easily betrayed us and joined Exatons army! " out of the crowd comes a sound. The voice belongs to Kha, who seems not to believe a word Leo says.
"He's right Leo, we can't trust you right now" The warrior bird Horus speaks trying to be as understanding as possible.
"You have to believe him! It's the truth" echoes through the halls and out comes the owner of the voice, Neith "I was there with him, he speaks the truth".
The golden warriors once again glance at each other. Could it really be that their Pharaoh is in Exatons body?
"How do we know you speak the truth?" "How is this possible? " "is that Neith!? Could they both be traitors?! " the throne room is filled with questions and Leo, Kefer, and Neith cannot answer all of them at once.
"My friends, this is a trick done by Exaton. He stole my body to be able to take over Egyxos" the voice belongs to Exaton but the way he speaks, it must have been Kefer.
"Pharaoh?! Could it really be?!" Horuses voice echoes.
"Yes it is me, I apologize for not being able to protect you all" the Pharaoh speaks.
"Wait! How can we tell, that you see not Exaton pretending to be Kefer?! " the harsh voice of Apis sounds.
"There must be a way! Hyksos! Don't you have a device to help with this? " Leo says clearly panicked.
"I.. I unfortunately do not" the creator warrior says sounding disappointed.
"We must take this to the council!" Apis exclaims.
Once the warriors explain or more like try to explain the situation to the council, the council makes their choice.
"Leo the council agrees that you and Neith are traitors and work for the dark army. Neith will be imprisoned and you Leo will be banished from Egyxos and as of Exaton you will be imprisoned and taken to no mans land! " The once soft voice of Iside is now loud and clear.
Leo's bracelet is taken from him by the council as Neith is being "escorted" rather harshly to her cell.
The last Pharaoh looks on last time at his mentor and apologizes for not being good enough, then he is sent back home.
Kefer, is also imprisoned, he on the other hand doesn't make a ruckus with the guards. He knows it's all over. Leo will never return and he has to live as Exaton for the rest of his life.
Leo P. O. V
I flop on my bed very upset and as much as I try I can't get my mind off Kefer. "What will he do now?" "Is he to live like this forever?" "What about Neith?" "Will she forever be seen as a traitor?"
My eyes close and I drift off...
///////////////
A. N
I hope this did not come out too angsty, and I really hope it is to your liking!
17 notes
·
View notes
Text
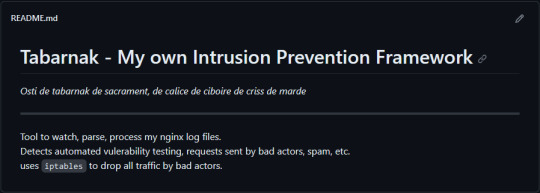
(this is a small story of how I came to write my own intrusion detection/prevention framework and why I'm really happy with that decision, don't mind me rambling)
Preface
About two weeks ago I was faced with a pretty annoying problem. Whilst I was going home by train I have noticed that my server at home had been running hot and slowed down a lot. This prompted me to check my nginx logs, the only service that is indirectly available to the public (more on that later), which made me realize that - due to poor access control - someone had been sending me hundreds of thousands of huge DNS requests to my server, most likely testing for vulnerabilities. I added an iptables rule to drop all traffic from the aforementioned source and redirected remaining traffic to a backup NextDNS instance that I set up previously with the same overrides and custom records that my DNS had to not get any downtime for the service but also allow my server to cool down. I stopped the DNS service on my server at home and then used the remaining train ride to think. How would I stop this from happening in the future? I pondered multiple possible solutions for this problem, whether to use fail2ban, whether to just add better access control, or to just stick with the NextDNS instance.
I ended up going with a completely different option: making a solution, that's perfectly fit for my server, myself.
My Server Structure
So, I should probably explain how I host and why only nginx is public despite me hosting a bunch of services under the hood.
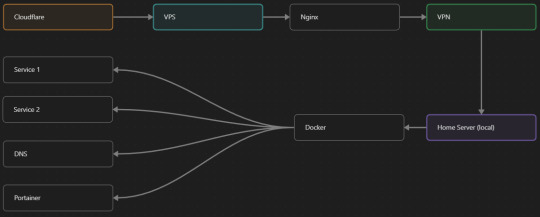
I have a public facing VPS that only allows traffic to nginx. That traffic then gets forwarded through a VPN connection to my home server so that I don't have to have any public facing ports on said home server. The VPS only really acts like the public interface for the home server with access control and logging sprinkled in throughout my configs to get more layers of security. Some Services can only be interacted with through the VPN or a local connection, such that not everything is actually forwarded - only what I need/want to be.
I actually do have fail2ban installed on both my VPS and home server, so why make another piece of software?
Tabarnak - Succeeding at Banning
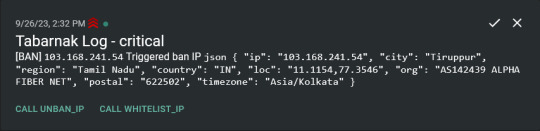
I had a few requirements for what I wanted to do:
Only allow HTTP(S) traffic through Cloudflare
Only allow DNS traffic from given sources; (location filtering, explicit white-/blacklisting);
Webhook support for logging
Should be interactive (e.g. POST /api/ban/{IP})
Detect automated vulnerability scanning
Integration with the AbuseIPDB (for checking and reporting)
As I started working on this, I realized that this would soon become more complex than I had thought at first.
Webhooks for logging This was probably the easiest requirement to check off my list, I just wrote my own log() function that would call a webhook. Sadly, the rest wouldn't be as easy.
Allowing only Cloudflare traffic This was still doable, I only needed to add a filter in my nginx config for my domain to only allow Cloudflare IP ranges and disallow the rest. I ended up doing something slightly different. I added a new default nginx config that would just return a 404 on every route and log access to a different file so that I could detect connection attempts that would be made without Cloudflare and handle them in Tabarnak myself.
Integration with AbuseIPDB Also not yet the hard part, just call AbuseIPDB with the parsed IP and if the abuse confidence score is within a configured threshold, flag the IP, when that happens I receive a notification that asks me whether to whitelist or to ban the IP - I can also do nothing and let everything proceed as it normally would. If the IP gets flagged a configured amount of times, ban the IP unless it has been whitelisted by then.
Location filtering + Whitelist + Blacklist This is where it starts to get interesting. I had to know where the request comes from due to similarities of location of all the real people that would actually connect to the DNS. I didn't want to outright ban everyone else, as there could be valid requests from other sources. So for every new IP that triggers a callback (this would only be triggered after a certain amount of either flags or requests), I now need to get the location. I do this by just calling the ipinfo api and checking the supplied location. To not send too many requests I cache results (even though ipinfo should never be called twice for the same IP - same) and save results to a database. I made my own class that bases from collections.UserDict which when accessed tries to find the entry in memory, if it can't it searches through the DB and returns results. This works for setting, deleting, adding and checking for records. Flags, AbuseIPDB results, whitelist entries and blacklist entries also get stored in the DB to achieve persistent state even when I restart.
Detection of automated vulnerability scanning For this, I went through my old nginx logs, looking to find the least amount of paths I need to block to catch the biggest amount of automated vulnerability scan requests. So I did some data science magic and wrote a route blacklist. It doesn't just end there. Since I know the routes of valid requests that I would be receiving (which are all mentioned in my nginx configs), I could just parse that and match the requested route against that. To achieve this I wrote some really simple regular expressions to extract all location blocks from an nginx config alongside whether that location is absolute (preceded by an =) or relative. After I get the locations I can test the requested route against the valid routes and get back whether the request was made to a valid URL (I can't just look for 404 return codes here, because there are some pages that actually do return a 404 and can return a 404 on purpose). I also parse the request method from the logs and match the received method against the HTTP standard request methods (which are all methods that services on my server use). That way I can easily catch requests like:
XX.YYY.ZZZ.AA - - [25/Sep/2023:14:52:43 +0200] "145.ll|'|'|SGFjS2VkX0Q0OTkwNjI3|'|'|WIN-JNAPIER0859|'|'|JNapier|'|'|19-02-01|'|'||'|'|Win 7 Professional SP1 x64|'|'|No|'|'|0.7d|'|'|..|'|'|AA==|'|'|112.inf|'|'|SGFjS2VkDQoxOTIuMTY4LjkyLjIyMjo1NTUyDQpEZXNrdG9wDQpjbGllbnRhLmV4ZQ0KRmFsc2UNCkZhbHNlDQpUcnVlDQpGYWxzZQ==12.act|'|'|AA==" 400 150 "-" "-"
I probably over complicated this - by a lot - but I can't go back in time to change what I did.
Interactivity As I showed and mentioned earlier, I can manually white-/blacklist an IP. This forced me to add threads to my previously single-threaded program. Since I was too stubborn to use websockets (I have a distaste for websockets), I opted for probably the worst option I could've taken. It works like this: I have a main thread, which does all the log parsing, processing and handling and a side thread which watches a FIFO-file that is created on startup. I can append commands to the FIFO-file which are mapped to the functions they are supposed to call. When the FIFO reader detects a new line, it looks through the map, gets the function and executes it on the supplied IP. Doing all of this manually would be way too tedious, so I made an API endpoint on my home server that would append the commands to the file on the VPS. That also means, that I had to secure that API endpoint so that I couldn't just be spammed with random requests. Now that I could interact with Tabarnak through an API, I needed to make this user friendly - even I don't like to curl and sign my requests manually. So I integrated logging to my self-hosted instance of https://ntfy.sh and added action buttons that would send the request for me. All of this just because I refused to use sockets.
First successes and why I'm happy about this After not too long, the bans were starting to happen. The traffic to my server decreased and I can finally breathe again. I may have over complicated this, but I don't mind. This was a really fun experience to write something new and learn more about log parsing and processing. Tabarnak probably won't last forever and I could replace it with solutions that are way easier to deploy and way more general. But what matters is, that I liked doing it. It was a really fun project - which is why I'm writing this - and I'm glad that I ended up doing this. Of course I could have just used fail2ban but I never would've been able to write all of the extras that I ended up making (I don't want to take the explanation ad absurdum so just imagine that I added cool stuff) and I never would've learned what I actually did.
So whenever you are faced with a dumb problem and could write something yourself, I think you should at least try. This was a really fun experience and it might be for you as well.
Post Scriptum
First of all, apologies for the English - I'm not a native speaker so I'm sorry if some parts were incorrect or anything like that. Secondly, I'm sure that there are simpler ways to accomplish what I did here, however this was more about the experience of creating something myself rather than using some pre-made tool that does everything I want to (maybe even better?). Third, if you actually read until here, thanks for reading - hope it wasn't too boring - have a nice day :)
10 notes
·
View notes
Text
Yeah, this is gonna be a long one so buckle up XD
Also sorry for the wait for this to come out, I've had it mostly done for so long, just didn't know how to finish it!
Yuki, young girl with light brown and pink hair accompanied by heavy eye makeup, threw her bag at the roof fence, slumping down against it before giving a long and exaggerated sigh. "Ugh! I can't believe that Hayate got suspended again! He's such an ass!"
"Let me guess, another fight of his escalated?" Asked Minako, a pale girl who's purple eyes were highlighted by her bright grey hair and dark cardigan. The purple eyed middle schooler handed the other a bottle of water and watched as she gulped it all down, sighing with delight as she finished the water.
"Ahhh, that's good shit. Thanks, sugar!" The mentioned girl blushed at the nickname as her eyes softened, just then did she notice something. "Wait, where's Saki? She isn't usually this late." "You're right, where is she?" Yuki said and not a moment later, the doors to the roof were pushed open by their friend.
Saki stopped in front of the two girls and clutched her chest, catching her breath before apologising. "Sorry that I'm so late! I was taking the new kid to the nurses office."
This sparked Minako's attention, a new student in the middle of the year? "Huh, why'd he have to go?" The gyaru said. "He didn't tell me, but he looked ill." Saki said, it was obvious that she was worried about him despite just meeting him.
"I'm sorry if I'm interrupting you two, but who is this new student? I've never heard about him." Minako asked, gaining an answer from Yuki.
"His name is Apis Subaru! Well, at least I think it is, he didn't really tell me when I was showing him around. He didn't talk alot when I met him, I think he's an introvert? Eh, who knows, that guy's a mystery." Yuki explains, constantly moving her hands whilst doing so. "He seems nice enough, but I don't think the poor guy has any friends! And he has heterochromia as well, I'm not sure if it's a contact lense or not but it totally rocks!"
"If he doesn't seem to have any friends, then why don't we try being his friends?" Minako suggested, gaining a nod of the head from the other two. "I guess that could work! Okay, tomorrow, I'll invite him to have break and lunch with us." Saki decided,
The next day, Saki waited for the break to start before she walked her way over to Apis, noticing how he had a scar across his eye, that must've been what Yuki was talking about.
He looked at Saki and closed his eyes, giving her a small smile. "... Thank you… for yesterday… I really do appreciate it."
"Aren't you gonna go anywhere for break?" Saki asked the boy, causing him to simply shake his head, his hair swaying as he did. "No…. I don't really know anybody here… and I don't want to cause a distraction for anyone else by following them.."
Saki was filled with sympathy for him, it was clear that he didn't have a very good opinion of himself. In a way, she could see her younger self in him, and this only made her more determined to be his friend.
She smiled before offering him a hand. "Well if you don't have anyone to hang out with, why don't you come with me? It'll stop you from being lonely." "Are you sure? I.. don't want you to feel like you have to be my friend just because you pity me." Apis said before his classmate grabbed his hand, pulling him out of his seat and guiding him to the roof.
Saki was so much different from him, she was confident and didn't seem to care what people thought about her, he wished he could be like her.
By the time the two middle schoolers had got to the roof, Apis was already a bit out of breath, he wasn't yet used to running that quick yet.
"You really weren't kidding on your stubbornness to get him here, huh?" Yuki laughed, watching as the two sat down. "Nah, you know me, I never go back on a promise." Apis felt strange to be around the three girls on the roof, it reminded him far too much of the time Yuma and the rest of the Numbers club spent having lunch on the roof.
He was pulled out of his thoughts by Yuki complimenting him. "Oh my god, you wear elf ears to school? That's so rad! Kinda cute as well, where'd you get them?" "Uhmm, thank.. you? I'm sorry, I'm not sure what you mean.." He mumbled, said ears moved down as he tried to edge away from the girl questioning him.
She dramatically gasps, eyes widening as she covers her mouth. "They fucking move as well?! That's hella sick! You know what? You got a nice aesthetic going on right now and I'm digging it!" Apis didn't know how to respond, he didn't remember the last time he was complimented in such a way. All he could do was sit there.
As Yuki was gushing about nothing in particular to him, she noticed something quite worrying. "Wait, have you had any food yet? You look starving!" "Huh? Oh, I must've forgotten my food this morning." Apis replied, he had completely forgotten about eating and left the lunch that his dad had made for him at home, this happened yesterday and was the reason he went to the nurses office before fainting from hunger.
"um." Finally after watching Apis and getting a bit jealous over her girlfriend giving more attention to him, Minako speaks, offering her food to him. "I always have a tendency to pack too much food for myself, so you can have some of mine if you want, it'll stop you being hungry."
Apis was filled with a strange feeling in his heart for the rest of the day, it reminded him of the warmth and comfort that he felt with Yuma and the others.
He was going to feel very safe in this new town, he just knew it.
5 notes
·
View notes
Text
Understanding AI Architectures: A Guide by an AI Development Company in UAE

In a world where screens rule our day, Artificial Intelligence (AI) quietly drives most of the online tools we now take for granted. Whether it's Netflix recommending the next film, a smartphone assistant setting reminders, or stores guessing what shirt you might buy next, the trick behind the curtain is the framework-the architecture.
Knowing how that framework works matters to more than just coders and CTOs; it matters to any leader who dreams of putting AI to work. As a top AI company based in the UAE, we think it is time to untangle the idea of AI architecture, explain why it is important, and show how companies here can win by picking the right setup for their projects.
What Is AI Architecture?
AI architecture is simply the plan that lines up all the parts of an AI system and shows how they talk to one another. Think of it as the blueprint for a house; once the beams are in place, the system knows where to read data, learn trends, decide on an action, and respond to people or other software.
A solid architecture brings four quick wins:
speed: data is processed fast
growth: the platform scales when new tasks arrive
trust: sensitive details are kept safe
harmony: it plugs into tools the business already uses
Because goals, data amounts, and launch settings vary, every model-whether machine learning, deep learning, NLP or something else-needs its own twist on that blueprint.
Core Layers of AI Architecture
Whether you're putting together a chatbot, a movie recommender, or a smart analytics dashboard, most projects rest on four basic layers.
1. Data Layer Every AI starts with data, so this layer is ground zero. It handles:
Input sources, both structured tables and messy text
Storage options, from classic databases to modern data lakes
Cleaning tools that tidy and sort raw bits into useable sets
In the UAE, firms juggle Arabic, English, and several dialects across fields like finance and tourism, so keeping fast, local data clean can make-or-break a project.
2. Modelling Layer Next up, the brains of the operation live here. Data scientists and engineers use this stage to craft, teach, and test their models.
Major pieces include:
Machine-learning algorithms, such as SVMs, random forests, or gradient boosting
Deep-learning networks, like CNNs for images or Transformers for text
Training platforms, with tools from TensorFlow, Keras, or PyTorch
An AI shop in Dubai or Abu Dhabi tunes this layer to local patterns, legal rules, and industry demands-whether that's AML flags for banks, fast scans for hospitals, or fair-value estimates for buyers.
3. Serving Layer After the models finish training, they must be put into action and made available to users or business tools. This step includes:
APIs that let other software talk to the model
Places to run the model (on-site, in the cloud, or a mix)
Speed tweaks so answers come back fast
In a fast-moving market like the UAE, especially in Dubai and Abu Dhabi, a slow reply can turn customers away. That makes this layer so important.
4. Feedback and Monitoring Layer AI systems are not plug-and-play for life; they learn, drift, and need care. This layer keeps things fresh with:
Watching how the model performs
Collecting feedback from real-world results
Re-training and rolling out new versions
Without that routine check-up, models can grow stale, skewed, or just plain useless.
Popular AI Architectures in Practice:
Lets highlight a few AI setups that companies across the UAE already count on.
1. Client-Server AI Architecture Perfect for small and mid-sized firms. The model sits on a server, and the client zips data back and forth through an API.
Use Case: Retail chains analyze shopper behavior to better place stock.
2. Cloud-Native AI Architecture Built straight into big clouds such as AWS, Azure, or Google Cloud. It scales up easily and can be deployed with a few clicks.
Use Case: Fintech firms sifting through millions of records to spot fraud and score loans.
3. Edge AI Architecture Edge AI moves brainpower right onto the gadget itself instead of sending every bit of data to faraway cloud servers. This design works well when speed is vital or when sensitive info cant leave the device.
Use Case: Think of smart cameras scanning mall hallways or airport lounges in the UAE, spotting unusual behavior while keeping footage onsite.
4. Hybrid AI Architecture Hybrid AI blends edge smarts with cloud muscle, letting apps react quickly on a device but tap the cloud for heavy lifting when needed.
Use Case: A medical app that checks your heart rate and ECG in real time but uploads that data so doctors can run big-pattern analysis later.
Challenges to Consider While Designing AI Architectures
Building a solid AI backbone is not as simple as plug-and-play. Here are key hurdles firms in the UAE often encounter.
Data Privacy Regulations
With the UAE tightening digital-security rules, models must meet the Personal Data Protection Law or face fines.
Infrastructure Costs
Top-notch GPUs, fast storage, and chilled racks add up fast. A skilled UAE partner will size the setup wisely.
Localization and Multilingual Support
Arabic-English chatbots have to handle dialects and culture cues, which means fresh, on-the-ground training, not off-the-shelf data.
Talent Availability
Brilliant models need more than code; they rely on data engineers, AI researchers, DevOps pros, and industry insiders speaking the same language.
How UAE Businesses Can Profit from Custom AI Setups?
Across the UAE, artificial intelligence is spreading quickly-from online government services to real-estate apps and tourism chatbots. Picking or creating a custom AI setup delivers:
Faster decisions thanks to real-time data analysis
Better customer support through smart, automated replies
Lower costs via predictive maintenance and lean processes
Higher revenue by personalizing each users journey
Partnering with a seasoned local AI firm gives you technical skill, market know-how, rule-following advice, and lasting help as your project grows.
0 notes
Text
Master the Code: How Java, Python, and Web Development Tutoring on MentorForHire Can Supercharge Your Tech Career
In a world powered by software, coding is no longer just a niche skill—it's a core competency. Whether you're looking to break into tech, ace a coding bootcamp, land your first junior developer job, or scale your expertise as a senior engineer, personalized mentoring makes a dramatic difference. That’s where MentorForHire.com comes in—a platform that connects you with industry professionals for hands-on Java Tutoring, Python Tutoring, and Web Development Tutoring.
Here’s how specialized tutoring in these key areas can accelerate your learning journey and help you achieve your software development goals.
Why One-on-One Coding Tutoring Beats Generic Online Courses
Self-paced tutorials and free courses are great for dipping your toes in—but when you're serious about growth, they often fall short. Why?
You don’t know what you don’t know.
Debugging can become a time-wasting nightmare.
Without accountability, progress slows down.
You’re not getting job-ready feedback from a real developer.
MentorForHire solves all of these problems by connecting you with real mentors who’ve worked in tech and know what it takes to succeed. Whether you're working on a class assignment, preparing for interviews, or building a full-stack project, you'll get tailored support.
Java Tutoring: Build Enterprise-Grade Skills from the Ground Up
Java isn’t just for beginners—it powers billions of devices, from Android apps to massive backend systems used in finance, healthcare, and e-commerce. If you're serious about software engineering, Java Tutoring offers a rock-solid foundation.
With a mentor, you can:
Understand core concepts like classes, inheritance, interfaces, and exception handling.
Master data structures and algorithms for whiteboard interviews.
Build scalable applications using Java frameworks like Spring and Hibernate.
Get help with unit testing, debugging, and version control.
Prepare for certifications like Oracle Certified Associate (OCA) and Oracle Certified Professional (OCP).
A mentor will not only explain the "how" of Java development but also the "why"—turning you from a coder into a software architect-in-training.
Python Tutoring: The Most Versatile Language in Tech
Python has become the go-to language for beginners and professionals alike because of its simplicity and power. Whether you want to get into automation, data science, machine learning, or back-end web development, Python Tutoring gives you the skills you need to thrive.
On MentorForHire.com, Python mentors can help you:
Write clean, efficient, and maintainable code.
Understand essential concepts like functions, loops, list comprehensions, and file I/O.
Use libraries like NumPy, pandas, Matplotlib, and scikit-learn for data analysis.
Build web apps with Flask or Django from scratch.
Automate tasks using Python scripts or integrate with APIs.
Whether you're solving LeetCode challenges or working on a startup prototype, personalized tutoring can take your Python skills to the next level.
Web Development Tutoring: Learn to Build the Web, Not Just Consume It
Today’s digital economy is built on the web—and web developers are in high demand across every industry. But with so many tools and frameworks, it’s easy to get overwhelmed. That’s where Web Development Tutoring comes in.
From front-end to back-end to full-stack, tutors on MentorForHire.com can guide you step-by-step:
Front-End Skills:
HTML, CSS, and JavaScript fundamentals
Responsive design using Flexbox and Grid
JavaScript frameworks like React, Angular, or Vue
Version control with Git and GitHub
Back-End Skills:
Node.js with Express or Java with Spring Boot
REST APIs and database integration (MySQL, MongoDB)
Authentication systems (OAuth, JWT)
DevOps basics: deploying apps with Heroku or AWS
You’ll work on actual projects like to-do lists, dashboards, or e-commerce stores—and get expert feedback every step of the way.
How MentorForHire Makes Learning Easier and Smarter
MentorForHire.com isn't just about hiring a tutor—it's about mentorship. The platform matches you with experienced developers who offer:
Flexible scheduling – Learn when it suits your life.
Customized roadmaps – No more cookie-cutter syllabi.
Real-world projects – Build apps that solve actual problems.
Code reviews & interview prep – Gain confidence before job applications.
Ongoing support – Whether it’s bugs, burnout, or breakthroughs.
This isn’t a YouTube tutorial or a lecture—it’s a partnership. Whether you're 16 or 60, learning to code becomes faster and more meaningful when you have someone guiding you in real time.
Who Is This For?
Students who want to stand out in their CS classes
Career changers entering tech from another field
Bootcamp grads who need more 1:1 help
Junior developers looking to climb the ladder
Entrepreneurs building their own software products
If you’ve got a goal and a laptop, MentorForHire.com has a mentor ready to help you reach it.
Final Thoughts: The Future Belongs to Lifelong Learners
The best investment you can make is in yourself. Whether you're learning Java, diving into Python, or building full-stack web apps, tutoring turns passive learning into active progress.
MentorForHire.com helps unlock your potential by giving you access to mentors who’ve been where you are—and know how to help you level up.
So why wait? Start your personalized tutoring journey today. Visit MentorForHire and connect with a mentor who can help you write your success story in code.
0 notes
Text
How Secure Are ChatGPT Integration Services for Enterprise Use?
As enterprises continue to adopt AI-powered tools to streamline operations, improve customer service, and enhance productivity, one question is at the forefront of IT and compliance discussions: How secure are ChatGPT integration services for enterprise use?

With concerns around data privacy, intellectual property, and regulatory compliance, it’s critical to evaluate the security posture of any AI service—especially those powered by large language models like ChatGPT. In this blog, we’ll explore the key security considerations, current safeguards provided by OpenAI, and best practices for enterprises leveraging ChatGPT integration services.
Understanding ChatGPT Integration Services
ChatGPT integration services refer to embedding OpenAI’s GPT-based language models into enterprise applications, workflows, or digital experiences. This can take the form of:
Custom GPTs integrated via APIs
In-app AI assistants
Enterprise ChatGPT (ChatGPT for business use)
Plugins and extensions for CRMs, ERPs, and other tools
These integrations often involve handling proprietary business data, making security and privacy a top priority.
Core Security Features Offered by OpenAI
OpenAI offers several enterprise-grade security measures for its ChatGPT services, especially under its ChatGPT Enterprise and API platform offerings:
1. Data Encryption (At Rest and In Transit)
All communications between clients and OpenAI’s servers are encrypted using HTTPS/TLS.
Data stored on OpenAI’s servers is encrypted using strong encryption standards such as AES-256.
2. No Data Usage for Training
For ChatGPT Enterprise and ChatGPT API users, OpenAI does not use your data to train its models. This is a significant safeguard for enterprises worried about data leakage or intellectual property exposure.
3. SOC 2 Type II Compliance
OpenAI has achieved SOC 2 Type II compliance, which demonstrates its commitment to meeting stringent requirements for security, availability, and confidentiality.
4. Role-Based Access Control (RBAC)
Admins have control over how users within the organization access and use the AI tools.
Integration with SSO (Single Sign-On) providers ensures secure authentication and account management.
5. Audit Logs & Monitoring
Enterprises using ChatGPT Enterprise have access to audit logs, enabling oversight of who is accessing the system and how it’s being used.
Key Enterprise Security Considerations
Even with robust security features in place, enterprises must be mindful of additional risk factors:
A. Sensitive Data Input
If employees or systems feed highly sensitive or regulated data into the model (e.g., PII, PHI, financial records), there’s a risk—even if data isn’t used for training. Consider implementing:
Data redaction or minimization tools before inputs
Custom guardrails to filter or flag sensitive content
Clear usage policies for staff using ChatGPT
B. Model Hallucination and Output Control
Although ChatGPT is powerful, it can sometimes "hallucinate" (generate false or misleading information). For enterprise apps, this can pose legal or reputational risks. Mitigation strategies include:
Human-in-the-loop reviews
Fine-tuned models or custom GPTs with domain-specific guardrails
Embedding verification logic to cross-check model outputs
C. Third-party Integrations
When ChatGPT is integrated with external apps or services, the security of the entire stack must be considered. Verify:
API key management practices
Permission scopes granted to the model
Data flow paths across integrated systems
Regulatory Compliance & Industry Use Cases
Enterprises in regulated industries—like healthcare, finance, or legal—must consider:
GDPR, HIPAA, and CCPA compliance
Data residency and localization laws
Auditability and explainability of AI decisions
OpenAI’s enterprise services are designed with these challenges in mind, but organizations are still responsible for end-to-end compliance.
Best Practices for Secure Enterprise Integration
To ensure secure and compliant use of ChatGPT, enterprises should:
Use ChatGPT Enterprise or the API platform — Avoid consumer-grade versions for internal business use.
Implement strict access control policies — Utilize SSO, MFA, and user role segmentation.
Set clear internal AI usage guidelines — Educate employees on what data can and cannot be shared.
Use logging and monitoring tools — Track API usage and user behavior to detect anomalies.
Conduct periodic security assessments — Evaluate model behavior, data flow, and integration security.
Conclusion
ChatGPT integration services offer a secure and scalable way for enterprises to leverage AI—when implemented thoughtfully. OpenAI has made significant strides to provide a robust security foundation, from SOC 2 compliance to data privacy guarantees for enterprise customers.
However, ultimate security also depends on how organizations configure, monitor, and govern these integrations. With the right strategies, ChatGPT can be a powerful, secure tool in your enterprise AI stack.
0 notes
Text
Why Java Is Still the King in 2025—and How Cyberinfomines Makes You Job-Ready with It

1. Java in 2025: Still Relevant, Still Dominating Despite the rise of new languages like Python, Go, and Rust, Java is far from dead—it’s actually thriving.
In 2025, Java powers:
40%+ of enterprise backend systems
90% of Android apps
Global banking & fintech infrastructures
E-commerce giants like Amazon, Flipkart & Alibaba
Microservices and cloud-native platforms using Spring Boot
Java is reliable, scalable, and highly in demand. But just learning syntax won’t get you hired. You need hands-on experience, framework expertise, and the ability to solve real-world problems.
That’s exactly what Cyberinfomines delivers.
2. The Problem: Why Most Java Learners Don’t Get Jobs Many students learn Java but still fail to land jobs. Why?
❌ They focus only on theory ❌ They memorize code, don’t build projects ❌ No real understanding of frameworks like Spring Boot ❌ Can’t explain their code in interviews ❌ Lack of problem-solving or debugging skills
That’s where Cyberinfomines’ Training changes the game—we teach Java like it’s used in real companies.
3. How Cyberinfomines Bridges the Gap At Cyberinfomines, we:
✅ Teach Core + Advanced Java with daily coding tasks ✅ Use real-world problem statements (not academic ones) ✅ Give exposure to tools like IntelliJ, Git, Maven ✅ Build full-stack projects using Spring Boot + MySQL ✅ Run mock interviews and HR prep ✅ Help you create a Java portfolio for recruiters
And yes—placement support is part of the package.
4. Java Course Curriculum: Built for the Real World Core Java
Data types, loops, arrays, OOP principles
Exception handling, packages, constructors
File handling & multithreading
Classes vs Interfaces
String manipulation & memory management
Advanced Java
JDBC (Java Database Connectivity)
Servlet Lifecycle
JSP (Java Server Pages)
HTTP Requests & Responses
MVC Design Pattern
Spring Framework + Spring Boot
Dependency Injection & Beans
Spring Data JPA
RESTful API Creation
Security & authentication
Connecting with front-end apps (React/Angular)
Tools Covered
IntelliJ IDEA
Eclipse
Postman
Git & GitHub
MySQL & Hibernate
Live Projects
Library Management System
Employee Leave Tracker
E-Commerce REST API
Blog App with full CRUD
Interview Preparation
DSA using Java
Java-based coding problems
100+ mock interview questions
HR round preparation
Resume writing workshops
5. Who Should Learn Java in 2025? You should choose Java if you are:
A fresher who wants a strong foundation
A non-tech graduate looking to switch to IT
A teacher/trainer who wants to upskill
A professional aiming for backend roles
Someone interested in Android development
A student looking to crack placement drives or government IT jobs
6. Real Success Stories from Our Java Learners
Amit (BSc Graduate) – Now working as a Java backend developer at an IT firm in Pune. Built his confidence with live projects and mock tests.
Pooja (Mechanical Engineer) – Switched from core to IT after completing Cyberinfomines’ Java program. Cracked TCS with flying colors.
Rahul (Dropout) – Didn’t finish college but now works remotely as a freelance Spring Boot developer for a US-based startup.
Every story started with zero coding experience. They ended with real jobs.
7. Top Java Careers in 2025 & Salary Trends In-demand roles include:
Java Backend Developer
Full Stack Developer (Java + React)
Android Developer (Java)
Spring Boot Microservices Architect
QA Automation with Java + Selenium
API Developer (Spring + REST)
Starting salary: ₹4.5 – ₹8 LPA (for freshers with strong skills) Mid-level: ₹10 – ₹20 LPA Freelancers: ₹1,000 – ₹2,500/hour
Java is stable, scalable, and pays well.
8. Certifications, Tools & Practical Add-Ons After training, you’ll earn:
Cyberinfomines Java Developer Certificate
Portfolio with at least 3 GitHub-hosted projects
Proficiency in IntelliJ, Maven, Git, MySQL
Resume aligned with Java job descriptions
Interview recordings and performance feedback
9. What Makes Cyberinfomines Java Training Different
✔ Human mentorship, not just videos ✔ Doubt sessions + code reviews ✔ Classes in Hindi & English ✔ Live assignments + evaluation ✔ Placement-oriented approach ✔ No-nonsense teaching. Only what’s needed for jobs.
We focus on you becoming employable, not just completing a course.
10. Final Words: Code Your Future with Confidence Java in 2025 isn’t just relevant—it’s crucial.
And with Cyberinfomines, you don’t just learn Java.
You learn how to:
Solve real problems
Write clean, scalable code
Work like a developer
Get hired faster
Whether you’re starting fresh or switching paths, our Java course gives you the skills and confidence you need to build a future-proof career.
📞 Have questions? Want to get started?
Contact us today: 📧 [email protected] 📞 +91-8587000904-905, 9643424141 🌐 Visit: www.cyberinfomines.com
0 notes
Text
The Ultimate Guide to Hiring Django Developers in 2025
If you’re building a scalable, secure, and high-performing web application in 2025, Django remains one of the best frameworks to use. But to unlock its full potential, you need to hire Django developers who understand how to use this Python-based framework to meet your business goals.

Why Choose Django in 2025?
Django is still a top choice for web development in 2025 due to:
Rapid Development: Built-in admin panel, ORM, and modular architecture
Scalability: Used by companies like Instagram, Spotify, and NASA
Security: Protection against XSS, CSRF, and SQL injections
Community Support: A mature and well-documented ecosystem
When Should You Hire a Django Developer?
You should hire Django developers if:
You need to build a custom web application or CMS
You’re planning a secure eCommerce site
You require API development for mobile/web apps
You want a high-performance MVP or startup product
You need a secure backend for SaaS or enterprise software
Key Skills to Look For
Before hiring, make sure the Django developer is skilled in:
Python programming
Django framework (ORM, views, forms, templates)
REST APIs (DRF — Django REST Framework)
Front-end integration (HTML, CSS, JavaScript, React/Angular)
Database systems (PostgreSQL, MySQL, SQLite)
Version control (Git)
Deployment (Docker, AWS, CI/CD)
Hiring Options: Freelancer vs Agency
Option Pros ConsFreelancer Cost-effective, flexible Limited availability, may lack team supportAgency (like Oodles)Scalable, full-stack team, support & QASlightly higher cost
If you want a full-cycle development solution with guaranteed timelines and post-launch support, hiring through an agency is ideal.
Interview Questions to Ask
Here are a few practical questions you can ask during the interview:
What’s the difference between a Django model and a Django form?
How would you handle user authentication in Django?
Explain the role of middleware in Django.
What are signals in Django and when should you use them?
How do you optimize Django for performance?
How Much Does It Cost to Hire Django Developers in 2025?
Freelancers: $20 — $60/hour (based on location & experience)
Agencies: $25 — $100/hour (comes with project managers, QA, and design support)
Dedicated Developer (Full-Time): $2000 — $6000/month
Outsourcing to countries like India gives you access to highly skilled developers at lower cost without compromising quality.
Where to Find Django Developers?
Freelance Platforms: Upwork, Freelancer, Toptal
Developer Marketplaces: Turing, Arc, Gun.io
Agencies: Oodles — Hire Django Developer
Job Boards: StackOverflow, GitHub Jobs, Remote OK
✅ Final Thoughts
Hire Django developers in 2025 is about more than just technical skills. You need someone who understands your business vision, works well with your team, and builds secure, scalable web applications with future growth in mind.
Whether you’re launching a new product, upgrading your tech stack, or expanding your backend, make sure you hire a Django developer who brings value from day one.
Looking to hire Django experts? Partner with Oodles for experienced Django developers who deliver quality, speed, and security.
0 notes
Text
Magistral: Mistral AI challenges big tech with reasoning model
New Post has been published on https://thedigitalinsider.com/magistral-mistral-ai-challenges-big-tech-with-reasoning-model/
Magistral: Mistral AI challenges big tech with reasoning model
Mistral AI has pulled back the curtain on Magistral, their first model specifically built for reasoning tasks.
Magistral arrives in two flavours: a 24B parameter open-source version called Magistral Small that anyone can tinker with, and a beefier enterprise edition, Magistral Medium, aimed at commercial applications where advanced reasoning capabilities matter most.
“The best human thinking isn’t linear—it weaves through logic, insight, uncertainty, and discovery,” explains Mistral AI.
That’s a fair point, existing models often struggle with the messy, non-linear way humans actually think through problems. I’ve tested numerous reasoning models and they typically suffer from three key limitations: they lack depth in specialised domains, their thinking process is frustratingly opaque, and they perform inconsistently across different languages.
Mistral AI’s real-world reasoning for professionals
For professionals who’ve been hesitant to trust AI with complex tasks, Magistral might change some minds.
Legal eagles, finance folks, healthcare professionals and government workers will appreciate the model’s ability to show its work. All conclusions can be traced back through logical steps—crucial when you’re operating in regulated environments where “because the AI said so” simply doesn’t cut it.
Software developers haven’t been forgotten either. Magistral claims to shine at the kind of structured thinking that makes for better project planning, architecture design, and data engineering. Having struggled with some models that produce plausible-sounding but flawed technical solutions, I’m keen to see if Magistral’s reasoning capabilities deliver on this front.
Mistral claims their reasoning model excels at creative tasks too. The company reports that Magistral is “an excellent creative companion” for writing and storytelling, capable of producing both coherent narratives and – when called for – more experimental content. This versatility suggests we’re moving beyond the era of having separate models for creative versus logical tasks.
What separates Magistral from the rest?
What separates Magistral from run-of-the-mill language models is transparency. Rather than simply spitting out answers from a black box, it reveals its thinking process in a way users can follow and verify.
This matters enormously in professional contexts. A lawyer doesn’t just want a contract clause suggestion; they need to understand the legal reasoning behind it. A doctor can’t blindly trust a diagnostic suggestion without seeing the clinical logic. By making its reasoning traceable, Magistral could help bridge the trust gap that’s held back AI adoption in high-stakes fields.
Having spoken with non-English AI developers, I’ve heard consistent frustration about how reasoning capabilities drop off dramatically outside English. Magistral appears to tackle this head-on with robust multilingual support, allowing professionals to reason in their preferred language without performance penalties.
This isn’t just about convenience; it’s about equity and access. As countries increasingly implement AI regulations requiring localised solutions, tools that reason effectively across languages will have a significant advantage over English-centric competitors.
[embedded content]
Getting your hands on Magistral
For those wanting to experiment, Magistral Small is available now under the Apache 2.0 licence via Hugging Face. Those interested in the more powerful Medium version can test a preview through Mistral’s Le Chat interface or via their API platform.
[embedded content]
Enterprise users looking for deployment options can find Magistral Medium on Amazon SageMaker, with IBM WatsonX, Azure, and Google Cloud Marketplace implementations coming soon.
As the initial excitement around general-purpose chatbots begins to wane, the market is hungry for specialised AI tools that excel at specific professional tasks. By focusing on transparent reasoning for domain experts, Mistral has carved out a potentially valuable niche.
Founded just last year by alumni from DeepMind and Meta AI, Mistral has moved at breakneck speed to establish itself as Europe’s AI champion. They’ve consistently punched above their weight, creating models that compete with offerings from companies many times their size.
As organisations increasingly demand AI that can explain itself – particularly in Europe where the AI Act will require transparency – Magistral’s focus on showing its reasoning process feels particularly timely.
(Image by Stephane)
See also: Tackling hallucinations: MIT spinout teaches AI to admit when it’s clueless
Want to learn more about AI and big data from industry leaders? Check out AI & Big Data Expo taking place in Amsterdam, California, and London. The comprehensive event is co-located with other leading events including Intelligent Automation Conference, BlockX, Digital Transformation Week, and Cyber Security & Cloud Expo.
Explore other upcoming enterprise technology events and webinars powered by TechForge here.
#adoption#ai#ai & big data expo#ai act#AI adoption#ai tools#Amazon#amp#Apache#API#applications#architecture#Artificial Intelligence#automation#azure#Big Data#BIG TECH#black box#box#bridge#california#change#chatbots#clinical#Cloud#Companies#comprehensive#conference#content#cyber
0 notes
Text
REST vs GraphQL in eCommerce Backend Systems
This blog compares REST and GraphQL in the context of eCommerce backend systems. It explains how both methods handle data requests, speed, and developer tasks for product listings, carts, and checkout flows.
The section on GraphQL vs REST API performance gives clear points on which works better in real-time store operations. Real-world examples help you understand which option may suit your online store better—without getting too technical or confusing.
0 notes
Text
AOSP Architecture Explained: A Practical Guide for Android Developers
In this blog, we delve into the architecture of the Android Open Source Project (AOSP), breaking down each layer of the software stack. From the Linux Kernel to Applications, we explore the functionalities and responsibilities of each component. Whether you're customizing ROMs or developing hardware-specific solutions, understanding the AOSP architecture is crucial.
The Android Open Source Project (AOSP) serves as the foundation for the Android operating system, offering a comprehensive software stack that enables developers to create a consistent user experience across various devices. Understanding the AOSP architecture is essential for developers aiming to build custom Android builds or integrate deeply with system components.
Overview of the AOSP Software Stack
The AOSP software stack is organized into several layers, each responsible for specific functionalities:
Linux Kernel: At the base, the Linux Kernel manages core system services such as process management, memory management, and hardware drivers. It acts as an abstraction layer between the hardware and the rest of the software stack.
Hardware Abstraction Layer (HAL): HAL provides standard interfaces that expose device hardware capabilities to the higher-level Java API framework. This allows Android to be agnostic about lower-level driver implementations.
System Services and Daemons: These are background processes that provide core system functionalities like power management, telephony, and media playback. They facilitate communication between the HAL and the Android Runtime.
Android Runtime (ART): ART is the managed runtime used by applications and some system services. It includes a set of core libraries and handles tasks like memory management, garbage collection, and bytecode execution.
System APIs: These APIs provide the necessary interfaces for applications to interact with the underlying hardware and system services, enabling functionalities like location services, telephony, and sensor management.
Android Framework: The framework offers a rich set of APIs that developers use to build applications. It includes components like Activity Manager, Window Manager, and Content Providers, which manage the user interface and application resources.
Applications: At the top layer, applications include both native apps provided by the device manufacturer and third-party apps installed by users. These apps interact with the Android Framework to perform their functions.
Importance for Developers
Understanding the AOSP architecture is vital for several reasons:
Customization: For developers building custom ROMs or tailoring Android for specific hardware, knowledge of each layer allows for effective customization and optimization.
Performance Optimization: Identifying and addressing performance bottlenecks requires a deep understanding of how different layers interact and where potential issues may arise.
Scalability: Proper utilization of the Android Framework and System APIs ensures that applications are scalable and maintain compatibility across various devices and Android versions.
Security: Awareness of the interactions between privileged and system-level components is crucial for developing secure applications and protecting user data.
Conclusion
The AOSP software stack is a meticulously designed architecture that harmonizes hardware and software components to deliver a seamless user experience. For developers, mastering this architecture is key to unlocking the full potential of Android, whether it's for application development, system customization, or hardware integration.
If you're looking to leverage AOSP for your projects, consider partnering with industry leaders like Silicon Signals. Recognized among the top 10 BSP and AOSP service companies, Silicon Signals offers expert services in Android BSP development, custom Android solutions, and more. Their team excels in delivering tailored solutions that meet the evolving demands of the industry. Silicon Signals
Ready to bring your Android project to life? Reach out to Silicon Signals at [email protected] for a free consultation.
#embeddedtechnology#embeddedsoftware#embeddedsystems#linux kernel#androidbsp#linuxdebugging#android#aosp#androidopensource
0 notes