#SSL certificates SQL Server
Explore tagged Tumblr posts
Text
Implementing SSL Certificates on SQL Server Database Operations
When you’re planning to introduce an SSL certificate for securing connections to your SQL server, primarily for a new third-party application, it’s like making sure your home’s front door has a good lock. Just as the lock on the front door enhances security for the entire house without requiring new keys for every room, adding an SSL certificate focuses on securing the communication channels…
View On WordPress
#encrypting SQL communications#secure data transmission#SQL Server security#SSL certificates SQL Server#SSL implementation SQL Server
0 notes
Text
How to Choose the Right Security Stack for Your Business Website
In an age where cyberattacks are growing more frequent and sophisticated, a secure website isn’t just a best practice—it’s a business necessity. Whether you're running an eCommerce store, SaaS product, or a company website, your security stack plays a critical role in protecting sensitive data, maintaining customer trust, and ensuring compliance.
A professional Web Development Company will always prioritize building a tailored security framework that addresses both current risks and future vulnerabilities. But how do you decide which tools and layers should be part of your website's defense system?
Let’s break down what a “security stack” means and how to choose the right one for your business.
What Is a Website Security Stack?
A security stack is a layered approach to website protection. It combines various technologies and tools—each targeting a specific set of threats—to create a comprehensive shield around your web infrastructure.
Think of it like a multi-lock system for your home:
One layer protects your doors (authentication)
Another secures your windows (firewalls)
And another watches for unusual activity (monitoring tools)
When configured properly, these layers work together to identify, prevent, and respond to attacks—without compromising website speed or functionality.
1. Start With an SSL/TLS Certificate
This is the most basic, yet crucial, layer. An SSL/TLS certificate encrypts the data exchanged between your website and its users. It ensures that personal information, passwords, and payment details can't be intercepted by third parties.
Make sure:
Your certificate is issued by a trusted Certificate Authority (CA)
It’s renewed automatically
All pages (not just the login or checkout) are secured with HTTPS
Modern browsers now flag non-HTTPS sites as "Not Secure"—a red flag for users and search engines alike.
2. Use a Web Application Firewall (WAF)
A WAF monitors and filters HTTP traffic between your website and the internet. It blocks common threats like SQL injection, cross-site scripting (XSS), and brute-force attacks.
Choose a WAF that:
Offers customizable rules
Supports DDoS protection
Provides real-time traffic analytics
Popular WAFs include Cloudflare, Sucuri, and AWS WAF—each with varying levels of control and reporting. Your development agency can help configure the best fit based on your tech stack and risk exposure.
3. Implement Secure Authentication Protocols
Weak passwords and poorly managed login systems are among the top causes of data breaches. Strengthen this layer with:
Two-Factor Authentication (2FA)
OAuth2 or SSO integrations for enterprise-level users
Rate-limiting and lockout mechanisms for failed login attempts
Make sure admin panels, user dashboards, and CMS backends are protected with hardened authentication protocols—not just simple passwords.
4. Harden Your CMS and Framework
If you’re using platforms like WordPress, Webflow, or custom frameworks like Laravel or Django, security starts with how well the code and plugins are managed.
Best practices include:
Removing unused plugins and themes
Regularly updating core software
Using only trusted third-party packages
Applying role-based access controls
A Web Development Company will often audit your codebase and extensions for hidden vulnerabilities and outdated dependencies.
5. Monitor and Log Everything
Security isn’t static—it requires continuous monitoring. Use log management and monitoring tools to detect suspicious behavior in real time.
Your stack should include:
Application-level logging (failed logins, unusual traffic)
Server and file integrity monitoring
Alerts for changes in configuration or permissions
Tools like Sentry, Datadog, or even open-source solutions like Fail2Ban can help detect threats early before they escalate.
6. Secure Your Hosting Environment
Your server and hosting setup must be as secure as your code. Ensure:
Firewalls are configured at the OS level
SFTP (not FTP) is used for file transfers
Admin panels are IP-restricted or hidden behind VPNs
Automated daily backups are stored off-site
Many breaches happen at the server level due to misconfigured permissions or outdated software—especially on unmanaged VPS environments.
7. Regular Penetration Testing and Updates
Security isn’t a one-time setup. Schedule regular penetration testing and vulnerability scans to identify new risks. Ensure:
Your software dependencies are up-to-date
Security patches are applied immediately
Reports are reviewed and acted upon
This proactive approach protects your business from evolving threats and demonstrates compliance with security standards and regulations.
Conclusion
Choosing the right security stack is not just about installing tools—it's about building a customized, layered defense system that protects your website from every angle. From SSL certificates and firewalls to authentication protocols and monitoring tools, each element plays a role in safeguarding your digital assets.
To ensure nothing is overlooked, work with a Web Development Company that specializes in security-first development. With the right guidance and configuration, your website can stay protected, performant, and trusted—no matter how fast your business grows.
0 notes
Text
How Secure Is Your WordPress Website?

With over 40% of the web powered by WordPress, it’s no surprise that it's also a prime target for hackers and bots. While WordPress is a secure platform at its core, many websites become vulnerable due to poor practices, outdated plugins, or weak hosting setups. So, how secure is your WordPress website — really? Let’s dive into the key factors that affect WordPress security and how you can protect your site.
1. Are You Using Strong Login Credentials?
The easiest way for hackers to get in is through weak usernames and passwords. Avoid “admin” as a username and use a complex, unique password. Consider enabling two-factor authentication for an extra layer of protection.
2. Is Your WordPress Core Updated?
WordPress regularly releases updates that fix bugs and security vulnerabilities. If you're not updating your WordPress core, you're leaving the door open for attacks.
3. What About Plugins and Themes?
Outdated or poorly coded plugins are among the top reasons for WordPress site breaches. Always use plugins from trusted sources, update them regularly, and remove any that you’re not actively using.
4. Have You Installed a Security Plugin?
Tools like Wordfence, Sucuri, or iThemes Security can detect malware, block malicious IPs, and notify you of suspicious activity in real-time. These act as the first line of defense against threats.
5. Do You Have Regular Backups?
Backups won’t prevent attacks, but they can save your website in case one happens. Use plugins like UpdraftPlus or Jetpack Backup to schedule automated backups.
6. Is Your Hosting Provider Secure?
Not all hosting environments are equal. Choose a provider that offers SSL, firewall protection, malware scanning, and regular server updates.
7. Are You Using HTTPS?
If your website isn’t using an SSL certificate (HTTPS), both users and Google will flag it as untrustworthy. Most hosting providers now offer free SSL certificates — make sure yours is enabled.
8. File Permissions and Database Security
Set correct file permissions and secure your wp-config.php file. Also, regularly monitor your database and consider changing the default WordPress table prefix to make SQL injections harder.
9. Monitor User Activity
If multiple users access your dashboard, use a plugin to monitor and log activity. This helps you catch suspicious behavior before it becomes a serious issue.
10. Avoid Nulled Themes and Plugins
Tempted to download a premium plugin for free? Don’t. Nulled software often contains hidden malware that compromises your entire website.
Final Thoughts
Securing your WordPress website isn’t just about installing a few plugins — it’s about adopting a proactive, layered approach to safety. If you’re unsure whether your site is truly secure or need professional help hardening it, a WordPress Development Company in Udaipur can perform a full security audit and implement best practices tailored to your needs.
0 notes
Text
What Defines a Truly Secure Website?

In today's digital landscape, a website is often the front door to a business, a personal brand, or vital information. With cyber threats constantly evolving, the question isn't just "Is my website online?" but "Is my website truly secure?" Many users look for the padlock icon and "HTTPS" in the address bar and breathe a sigh of relief. While essential, that green lock is merely the beginning of true website security.
HTTPS signifies that the connection between your browser and the website's server is encrypted, protecting data in transit. But a truly secure website goes far beyond encrypting data between two points. It's built on a multi-layered defense strategy, addressing vulnerabilities at every level of the application and infrastructure.
So, what are the characteristics of a website you can genuinely trust?
1. Always Uses HTTPS with Strong TLS Protocols
This is the foundational layer, but its proper implementation is crucial.
What it is: HTTPS (Hypertext Transfer Protocol Secure) encrypts the communication between the user's browser and the website's server using TLS (Transport Layer Security, the modern successor to SSL) certificates.
Why it's essential: It prevents eavesdropping, tampering, and message forgery, ensuring that the data you send (like login credentials or credit card numbers) and receive remains private and integral. Modern browsers flag sites without HTTPS as "Not Secure." Crucially, truly secure websites use strong, up-to-date TLS versions (like TLS 1.2 or 1.3), not older, vulnerable ones.
2. Robust Input Validation and Output Encoding
These are fundamental defenses against some of the most common web attacks.
Input Validation: Every piece of data a user submits (forms, search queries, URLs) must be strictly validated before the server processes it. This prevents attackers from injecting malicious code (e.g., SQL Injection, Command Injection) that could manipulate the database or execute commands on the server.
Output Encoding: Any data retrieved from a database or user input that is displayed back on the website must be properly encoded. This prevents Cross-Site Scripting (XSS) attacks, where malicious scripts could be executed in a user's browser, stealing cookies or defacing the site.
3. Strong Authentication & Authorization Mechanisms
Security starts with knowing who is accessing your site and what they are allowed to do.
Authentication:
Strong Password Policies: Enforce minimum length, complexity (mix of characters), and disallow common or previously breached passwords.
Multi-Factor Authentication (MFA): Offer and ideally mandate MFA for all user accounts, especially administrative ones. This adds a critical layer of security beyond just a password.
Secure Session Management: Use secure, short-lived session tokens, implement proper session timeouts, and regenerate session IDs upon privilege escalation to prevent session hijacking.
Authorization: Implement the principle of least privilege. Users should only have access to the data and functionalities strictly necessary for their role. Role-Based Access Control (RBAC) is key here, ensuring a customer can't access admin features, for instance.
4. Regular Security Updates & Patch Management
Software is complex, and vulnerabilities are constantly discovered.
Continuous Patching: The website's underlying operating system, web server software (e.g., Apache, Nginx), Content Management System (CMS) like WordPress or Drupal, plugins, themes, and all third-party libraries must be kept up-to-date with the latest security patches.
Why it's essential: Unpatched vulnerabilities are a common entry point for attackers. A truly secure website has a rigorous system for identifying and applying updates swiftly.
5. Comprehensive Error Handling & Logging
What happens when things go wrong, or suspicious activity occurs?
Generic Error Messages: Error messages should be generic and not reveal sensitive system information (e.g., database connection strings, file paths, or specific error codes) that attackers could use to map your system.
Robust Logging: All security-relevant events – failed login attempts, successful logins, administrative actions, suspicious requests, and critical system events – should be logged. These logs should be stored securely, centrally, and monitored in real-time by a Security Information and Event Management (SIEM) system for anomalies and potential attacks.
6. Secure Development Practices (SDL)
Security isn't an afterthought; it's built in from the ground up.
Security by Design: A truly secure website is born from a development process where security considerations are embedded at every stage – from initial design and architecture to coding, testing, and deployment. This is known as a Secure Development Lifecycle (SDL).
Code Reviews & Testing: Regular security code reviews, static application security testing (SAST), and dynamic application security testing (DAST) are performed to identify and fix vulnerabilities before the code ever goes live.
7. Web Application Firewall (WAF)
A WAF acts as a protective shield for your website.
What it does: It monitors and filters HTTP traffic between the web application and the internet. It can detect and block common web-based attacks (like SQL injection, XSS, DDoS, brute-force attempts) before they reach the application.
Why it helps: It provides an additional layer of defense, especially useful for mitigating new threats before a patch is available or for protecting against known vulnerabilities.
8. Data Encryption at Rest
While HTTPS encrypts data in transit, data stored on servers needs protection too.
Sensitive Data Encryption: Databases, file systems, and backups containing sensitive user information (passwords, PII, financial data) should be encrypted.
Why it's important: Even if an attacker manages to breach your server and access the underlying storage, the data remains unreadable without the encryption key, significantly mitigating the impact of a breach.
9. Regular Security Audits & Penetration Testing
Proactive testing is key to finding weaknesses before malicious actors do.
Vulnerability Scanning: Automated tools scan your website for known vulnerabilities.
Penetration Testing (Pen-Testing): Ethical hackers simulate real-world attacks to exploit vulnerabilities, test your defenses, and assess your overall security posture. These should be conducted regularly and after significant changes to the website.
10. Clear Privacy Policy & Data Handling Transparency
While not a strictly technical security feature, transparency builds user trust and demonstrates responsible data stewardship.
What it includes: A clear, easily accessible privacy policy explaining what data is collected, why it's collected, how it's used, how it's protected, and who it's shared with.
Why it matters: It shows commitment to data security and respects user privacy, a fundamental aspect of a truly trustworthy online presence.
A truly secure website is not a static state achieved by checking a few boxes. It's a continuous commitment to vigilance, proactive measures, and a deep understanding that security is an ongoing process involving people, technology, and robust policies. In a world where digital trust is paramount, building and maintaining a genuinely secure website is an investment that pays dividends in reputation, customer loyalty, and business continuity.
0 notes
Text
Web Security 101: Protecting Against Common Threats
In today’s digital world, websites serve as the face of businesses, educational institutions, and organisations. As online interactions grow, so do the threats targeting web applications. From malware attacks to phishing schemes, cyber threats are more sophisticated and frequent than ever. Whether you’re a business owner, developer, or tech enthusiast, understanding the fundamentals of web security is essential to ensure your digital presence remains safe and resilient.
In this article, we’ll cover the essentials of web security, outline common web threats, and discuss best practices to protect against them. For students and professionals pursuing technology careers, especially those enrolled in programs like the Full Stack Developer Course in Bangalore, mastering these security concepts is not just beneficial—it’s essential.
What is Web Security?
Web security, also known as cybersecurity for web applications, is the protective measure taken to safeguard websites and online services against unauthorised access, misuse, modification, or destruction. These protections help maintain the confidentiality, integrity, and availability (CIA) of information and services online.
With the increasing digitisation of services, web applications are a common target for attackers due to the valuable data they often store, such as user credentials, personal information, and payment details.
Common Web Security Threats
Here are some of the most common threats that web applications face today:
1. SQL Injection (SQLi)
SQLi a type of attack where malicious SQL queries are inserted into input fields to manipulate databases. If input validation is not properly handled, attackers can retrieve, alter, or delete sensitive data from the database.
2. Cross-Site Scripting (XSS)
XSS attacks occur when attackers inject malicious scripts into web pages viewed by other users. This can give rise to data theft, session hijacking, and the spreading of malware.
3. Cross-Site Request Forgery (CSRF)
In a CSRF attack, a malicious website tricks a user into performing actions on a different site where they’re authenticated. This can result in unauthorised fund transfers, password changes, and more.
4. Man-in-the-Middle (MITM) Attacks
These attacks happen when an attacker intercepts communication between two parties. They can steal or manipulate data without either party being aware.
5. Denial of Service (DoS) and Distributed DoS (DDoS)
These attacks flood a website with traffic, turning it slow or entirely unavailable to legitimate users. DDoS attacks can cripple even robust web infrastructures if not mitigated properly.
6. Zero-Day Exploits
Zero-day attacks exploit unknown or unpatched vulnerabilities in software. These are particularly dangerous because there’s often no fix available when the attack occurs.
Best Practices to Protect Against Web Threats
1. Use HTTPS
Securing your website with HTTPS encrypts data transferred between users and your server. It also ensures that data isn't altered during transmission. SSL/TLS certificates are now a basic requirement for modern websites.
2. Input Validation and Sanitisation
Never trust user input. Validate and sanitise all inputs on both client and server sides. This helps in preventing SQL injections, XSS, and other injection-based attacks.
3. Implement Proper Authentication and Session Management
Strong passwords, multi-factor authentication (MFA), and secure session management are crucial. Implement session expiration and automatic logout features to reduce unauthorised access risks.
4. Regularly Update Software and Libraries
Web frameworks, plugins, and server software should be regularly updated to patch known vulnerabilities. Automated tools can help identify outdated components in your tech stack.
5. Use Web Application Firewalls (WAF)
WAFs protect web applications by filtering and monitoring HTTP traffic. They can prevent many common attacks before they reach your server.
6. Data Encryption
Sensitive data—both at rest and in transit—should be encrypted. This reduces the damage caused by data breaches.
7. Conduct Regular Security Audits
Perform vulnerability assessments and penetration testing regularly to identify and fix security flaws in your applications.
8. Security Awareness Training
Educate employees and developers on security best practices. Social engineering attacks often target human error, so awareness is a strong line of defence.
Role of Developers in Web Security
Security isn't just the job of cybersecurity specialists. Developers play a critical role in implementing secure code and architecture. Understanding the OWASP Top 10—an industry-standard list of the most critical web application security risks—is a must for anyone writing backend or frontend code.
This is why modern tech education emphasises security fundamentals. At ExcelR, we integrate security concepts across our tech courses, including our Full Stack Developer Course in Bangalore. We believe that a well-rounded developer isn’t just one who can build efficient applications—but one who can build secure ones too.
Real-World Impact of Poor Web Security
Neglecting web security can have severe consequences. Major data breaches have cost companies millions in losses, legal penalties, and reputation damage. In extreme cases, companies have shut down operations permanently after suffering massive cyberattacks.
Even smaller websites are not immune. Bots and automated scripts scan thousands of websites daily for vulnerabilities, often targeting outdated CMS platforms or poorly configured servers.
Final Thoughts
Web security is not a one-time task—it’s an ongoing process of identifying risks, updating systems, and educating users and developers. With the evolution of cyber threats, staying informed and proactive is the best defense.
Whether you’re running a personal blog or developing enterprise-level web applications, implementing strong security measures can save you from irreversible damage. And if you're aspiring to become a tech professional, enrolling in a comprehensive program like the Full Stack Developer Course in Bangalore from ExcelR can give you both the technical and security skills required to thrive in today’s digital landscape.
For more details, visit us:
Name: Full Stack Developer Course In Bangalore
Address: No 9, Sri Krishna Akshaya, 1st Floor, 27th Main, 100 Feet Ring Rd, 1st Phase, BTM Layout, Bengaluru, Karnataka 560068
Phone: 9513446548
0 notes
Text

Key WooCommerce Security Tips for 2025
1. Use Strong Passwords and Enable Two-Factor Authentication (2FA)
A weak password is often the first point of vulnerability for any website. To protect your WooCommerce store, ensure that you and your team members use strong, unique passwords for all accounts related to your store. Additionally, enabling two-factor authentication (2FA) adds an extra layer of protection, requiring a second verification step when logging in.
While 2FA may seem like an added hassle, it is a powerful tool that prevents unauthorized access, even if someone obtains your password. Implementing 2FA will drastically reduce the likelihood of a security breach.
2. Keep WordPress, WooCommerce, and Plugins Updated
Regular updates to WordPress, the WooCommerce plugin, and any other installed plugins are critical for maintaining security. These updates often include security patches to fix newly discovered vulnerabilities. By updating your software regularly, you ensure that your store is protected against the latest threats.
If you don't have the time or expertise to handle updates yourself, consider seeking WooCommerce Development Services to keep your store secure and functioning smoothly. A professional team can handle the updates while ensuring no disruption to your store’s operations.
3. Implement SSL Encryption for Secure Transactions
SSL (Secure Socket Layer) certificates encrypt sensitive data that flows between the server and the user’s browser. This encryption ensures that your customers’ personal and financial details are protected. In 2025, having an SSL certificate isn’t just a security measure—it’s also essential for maintaining customer trust and improving your site’s SEO ranking.
If you're unsure how to integrate SSL encryption, a WooCommerce Developer can help set it up to ensure secure transactions and smooth customer experiences.
4. Install a Web Application Firewall (WAF)
A Web Application Firewall (WAF) acts as a barrier between your WooCommerce store and malicious traffic. It filters out harmful requests, preventing hackers from exploiting vulnerabilities in your site’s code. Implementing a WAF can block attacks such as SQL injection, cross-site scripting (XSS), and brute-force login attempts, which are common methods used by cybercriminals.
To configure the best WAF for your store, you can work with professionals who specialize in website security.
5. Backup Your Store Regularly
Data loss is one of the most detrimental effects of a cyberattack. If your store is compromised or experiences a system failure, having a recent backup ensures that you can restore your website with minimal downtime and data loss. Regular backups also give you peace of mind knowing that even in the worst-case scenario, you can recover your site quickly.
To streamline this process, WordPress Support Services often include backup solutions, providing continuous backups to keep your store secure and your data safe.
6. Limit Login Attempts
Brute force attacks involve hackers attempting to guess your login credentials by trying different combinations repeatedly. One effective way to prevent these attacks is by limiting the number of failed login attempts before temporarily locking out the user. This drastically reduces the chances of a hacker successfully gaining access to your store.
This is a simple yet effective security measure, and integrating it into your site can be done by a WooCommerce Developer who can ensure the right settings are in place to block these types of attacks.
Ongoing Maintenance and Monitoring for WooCommerce Security
Maintaining a secure WooCommerce store is an ongoing process. Regular security checks, audits, and proactive monitoring are essential to keep your site protected. Without routine maintenance, new vulnerabilities can arise, and hackers will always find new ways to exploit them.
By leveraging WordPress Website Maintenance Services, you can ensure that your store is continually monitored and updated, helping to safeguard it from emerging threats.
Conclusion
In 2025, the security of your WooCommerce store should be a top priority. By adopting strong passwords, implementing SSL certificates, enabling two-factor authentication, and keeping your software up to date, you can significantly reduce the risk of a breach.
For more advanced security measures and ongoing support, working with WooCommerce Development Services and WordPress Support Services ensures that your site remains secure, protected from the latest threats, and optimized for performance.
Let’s work together to make sure your WooCommerce store is as secure as possible in 2025 and beyond.
0 notes
Text
8 Common Techniques You Must Know to Create Secure Websites
Did you know that over 30,000 websites are hacked every day? In this era of digitization, website security is of utmost importance. The sophistication of cyberattacks is growing daily, and one incident can cause serious financial loss, legal consequences, and loss of brand reputation. Installing advanced security measures not only keeps your data secure but also builds trust among your customers. Let’s explore the 8 Common Techniques You Must Know to Create Secure Websites.
Enforce HTTPS using SSL/TLS Certificates
Switching from HTTP to HTTPS is a cornerstone of website security. HTTPS encrypts information passed between your site and any user’s browser, protecting it from interception and tampering. A certificate for SSL/TLS is necessary for this encryption, guaranteeing sensitive data, such as login credentials and financial information, stays private. In addition to security, HTTPS builds consumer trust. Browsers frequently symbolize this in a padlock icon, while also being beneficial in regard to your site’s ranking in search engines. Purchasing and installing an SSL certificate is now easier than ever, with various hosting services offering them for free or for minimal fees. Updating and renewing them periodically maintains constant protection.
Keep Software and Dependencies Up to Date
Outdated software is an easy mark for hackers. They take advantage of known vulnerabilities in content management systems (CMS), plug-ins, themes, and other website elements. Keeping them updated regularly ensures security fixes are deployed in a timely fashion, sealing potential holes for hackers. Even automation, when available, can simplify this for you and minimize human error. Be sure, however, to verify that upgrades won’t interfere with your current configuration. Case Study: The Equifax breach (2017) happened because of an unpatched vulnerability in Apache Struts, affecting 147 million people.
Implement Strict Password Guidelines and Two-Factor Authentication (2FA)
A Password is usually the first point of security against unauthorized use. Enforcing tight password policies requiring a combination of uppercase and lowercase letters, numbers, and special characters can discourage brute-force attacks. Instruct users against using easily guessable passwords and have them update them regularly. Reducing password use by supplementing it with Two-Factor Authentication (2FA) adds another layer of security. 2FA asks customers to identify themselves using a second process, for instance, a code sent to their mobile phone, which complicates unauthorized use tremendously.
Perform Regular Security Audits and Vulnerability Assessments
Taking the lead in finding and fixing security weaknesses is vital. Regular security audits mean carefully checking your website’s infrastructure, codebase, and configurations to spot any risks. Automated tools can help catch common problems, but a hands-on review gives you a clearer picture. Once you identify those risks, focus on the most critical ones and resolve them quickly. Doing these checks consistently not only boosts your website’s security but also shows users you’re serious about protecting their information.
Implement Web Application Firewalls (WAF)
A Web Application Firewall serves as a shield for your website against incoming traffic. It scans, filters, and blocks unwanted data packets from reaching your server. A WAF protects against an array of attacks, ranging from SQL injections to XSS and Distributed Denial of Service (DDoS) attacks. A WAF can identify and prevent suspicious activity in real time by monitoring HTTP requests. You can implement a WAF at the server level or through cloud services, depending on your website requirements. Example:��In 2020, GitHub survived a 1.3 Tbps DDoS attack thanks to its WAF and traffic filtering.
Backing Up Regularly
Data loss can be caused by different factors, such as hacking, hardware breakdowns, or user errors. Backing up your website at regular intervals guarantees that you can recover it in its last state in case data loss occurs. Use automatic backup solutions, which keep duplicates in safe, off-site locations. Periodically check your backups for integrity and validate that restoration works properly. A sturdy backup plan reduces downtime and data loss, safeguarding revenue and reputation.
Secure User Input and Prevent SQL Injection
Validate User Input and Prevent SQL Injection. Input forms, like contact forms or search bars, can also be used to inject harmful code if not properly secured. SQL injection is a common attack in which harmful SQL code is injected into input forms to modify your database. Prevent this by validating and sanitising user input. Use prepared statements and parameterized queries, which ensure user input is used as data and not as code. Including such measures secures your database against unauthorized use and data compromise.
Apply Content Security Policy (CSP)
A Content Security Policy is one of the security standards designed to thwart cross-site scripting (XSS) attacks by dictating which dynamic assets can load on your site. By setting trusted origins for scripts, style sheets, and other content, CSP prevents malicious scripts injected by attackers from running. Configuring your web server to include the right Content-Security-Policy HTTP header implements CSP. Periodically checking and revising your CSP affirms that it’s still effective against new threats.
Final Thoughts:
By integrating these eight practices in your website development and upkeep, its security stance is greatly improved. In addition to these, developing a culture of security among your staff and users further strengthens your defenses. Continual training of stakeholders in regard to possible threats and safe data handling creates an overall effort towards continuous security within an online setting. Website security is an evolving process, and vigilance, flexibility, and proactivity in anticipating upcoming threats in this respect are necessary.
0 notes
Text
Demonstrating Web Wizards' Comprehensive Solutions to Industry Challenges
In the dynamic world of web development, meeting and overcoming industry challenges is crucial for a business to thrive. At the forefront of this challenge-facing ethos is Web Wizards. Established in 2005, and incorporated in 2008, Web Wizards has grown to be a premier name in Website development Perth. With an 18-year legacy, this Cannington-based company exemplifies expertise in Web Development Cannington, and has been pivotal in transforming how businesses establish their digital presence. As the demands of the digital landscape continually evolve, Web Wizards offers cutting-edge, innovative solutions designed to overcome key industry hurdles. With a solid foundation in quality web design, digital marketing, and user-focused strategies, they demonstrate how practical expertise can drive business success. Below, we explore how Web Wizards tackles specific industry challenges and continually adapts to deliver exceptional outcomes.
Building Robust and Secure Websites
Cutting-edge Technologies
At the heart of Web Wizards' offerings is their use of advanced web technologies. They create bespoke websites utilizing HTML5, CSS3, JavaScript, and CMS platforms like WordPress. This expertise ensures that websites are not only visually appealing but also fast and search-engine optimized. Their commitment to non-outsourced work provides local businesses in Perth with reliable Website development services, directly addressing the industry's need for high-quality, affordable web design.
Emphasis on Security
Website security is paramount in today's digital environment. Web Wizards prioritizes secure web development practices by integrating SSL certificates, and implementing firewalls and security patches. Their thorough approach protects businesses against vulnerabilities, such as SQL injections and DDoS attacks, thereby maintaining their clients' trust. Through these robust measures, Web Wizards ensures every website is safe in the ever-evolving digital landscape. Understanding the importance of streamlined design and secure functionality, Web Wizards efficiently transitions their expertise to address performance enhancement challenges next.
Enhancing Website Performance
Speed Optimization Techniques
Recognizing Google's emphasis on page-speed as a ranking factor, Web Wizards implements comprehensive speed optimization strategies. Employing techniques like image compression, CSS/JS minification, and server-side improvements, they ensure websites load quickly and perform efficiently, boosting both user experience and SEO.
Local Hosting Services
Web Wizards also addresses the performance issue by providing local web server hosting in Perth. This strategic decision reduces loading times and enhances user experience significantly. The company's commitment to local service underscores its dedication to offering quality Website development Perth services that keep pace with customer needs. With performance challenges expertly tackled, Web Wizards turns its attention to solving user engagement issues.
Boosting User Engagement
Responsive Design
Website accessibility across diverse devices and platforms is crucial. Web Wizards excels in responsive design, ensuring websites adapt seamlessly to any screen size, from desktops to smartphones. This adaptability enhances user experience, encouraging longer site visits and engagement, which are critical for successful Web Development Cannington.
Progressive Web Apps (PWA)
To further boost engagement, Web Wizards offers Progressive Web App development, delivering web functionality similar to native mobile apps. PWAs increase user retention by providing offline access and push notifications, showcasing Web Wizards' ongoing commitment to top-tier Website development Perth. Overcomin
0 notes
Text
Securing Your Web Application: Key Strategies for Protection

As the digital landscape continues to evolve, securing web applications has become more important than ever. With the increasing prevalence of cyberattacks, data breaches, and security vulnerabilities, ensuring your web application is protected should be a top priority. Whether you're building a new application or maintaining an existing one, it's critical to take proactive steps to safeguard user data and ensure the security of your platform. For businesses looking to create secure applications, enlisting web application development services can provide the expertise needed to implement the best security practices from the ground up.
Here, we’ll explore some key strategies to help secure your web application and protect it from potential threats.
1. Use HTTPS for Secure Communication
One of the most fundamental steps in securing your web application is ensuring that all communications between users and your servers are encrypted. This is achieved by implementing HTTPS (Hypertext Transfer Protocol Secure). HTTPS uses SSL/TLS certificates to encrypt data, preventing hackers from intercepting sensitive information, such as login credentials, personal data, or payment details.
Without HTTPS, data is transmitted in plain text, making it vulnerable to man-in-the-middle attacks. Make sure that every page of your web application, especially login, registration, and payment pages, uses HTTPS to safeguard your users' information.
2. Implement Strong Authentication and Authorization
Authentication and authorization are essential for verifying user identities and controlling access to your web application’s resources. It’s crucial to implement multi-factor authentication (MFA), which requires users to provide multiple forms of identity verification before granting access.
Additionally, ensure your application follows the principle of least privilege (PoLP) — only allowing users to access resources they absolutely need. This limits the impact of a potential security breach, as even if a hacker gains access to one part of the application, they won’t be able to access all user data or resources.
3. Sanitize Input to Prevent SQL Injection
SQL injection remains one of the most common security vulnerabilities in web applications. This occurs when an attacker manipulates input fields to inject malicious SQL code into your application’s database. To prevent this, always sanitize and validate user input, using parameterized queries and prepared statements when interacting with your database.
Additionally, use input validation libraries and frameworks that automatically escape malicious characters. Never trust user input, and treat all inputs as potentially harmful.
4. Keep Your Software Up to Date
One of the simplest yet most effective ways to secure your web application is by keeping all software up to date. This includes your web application framework, libraries, plugins, and any third-party services you use. Software vendors often release patches and updates to fix security vulnerabilities, so it’s essential to install these updates promptly.
Neglecting to update your software can leave your application open to known exploits that attackers could easily take advantage of. Setting up automated update systems or regularly reviewing available updates can help ensure your application stays secure.
5. Implement Proper Session Management
Session management is another crucial element in securing your web application. Ensure that user sessions are securely managed and expired after a reasonable period of inactivity. Use secure session tokens, which are harder to predict, and store them in a secure location, such as HTTP-only cookies, to reduce the risk of session hijacking.
You should also consider implementing session logging and monitoring to detect unusual activity, such as multiple failed login attempts or sessions accessed from unusual locations. This allows you to act quickly and prevent unauthorized access.
6. Protect Against Cross-Site Scripting (XSS)
Cross-site scripting (XSS) is another common vulnerability in web applications, where attackers inject malicious scripts into web pages viewed by other users. These scripts can steal session cookies, perform actions on behalf of users, or redirect them to malicious websites.
To protect your application from XSS attacks, ensure you sanitize and escape any user-generated content before displaying it. This includes using Content Security Policy (CSP) headers to prevent untrusted scripts from executing and implementing strict input validation to block dangerous scripts.
7. Utilize Web Application Firewalls (WAFs)
A Web Application Firewall (WAF) is a security system that monitors and filters HTTP requests to and from a web application. WAFs can help protect your application from a variety of threats, including SQL injection, XSS, and Distributed Denial of Service (DDoS) attacks.
WAFs work by examining incoming traffic and blocking malicious requests based on predefined security rules. They can also help reduce the risk of zero-day attacks, as they provide an additional layer of protection that may catch unknown vulnerabilities.
8. Regularly Backup Your Data
Even with the best security measures in place, data loss can still happen. Ransomware attacks, hardware failures, and other unforeseen issues can lead to the loss of critical application data. To mitigate this risk, make regular backups of your application data and store them securely.
Test your backups regularly to ensure they can be restored quickly in the event of an attack. Having a solid backup and disaster recovery plan can help you recover your application and minimize downtime in case of a security breach.
9. Conduct Security Audits and Penetration Testing
To ensure that your web application is secure, it’s important to perform regular security audits and penetration testing. A security audit will assess the overall security posture of your application, including code reviews, infrastructure assessments, and configuration checks.
Penetration testing, or ethical hacking, involves simulating an attack to identify vulnerabilities before malicious hackers can exploit them. By conducting these tests regularly, you can identify weaknesses and patch them before they become a problem.
Conclusion
Securing your web application is an ongoing process that requires vigilance, expertise, and the adoption of best practices. By implementing strong authentication, keeping software up to date, sanitizing input, and using tools like WAFs and encryption, you can protect your application from a variety of threats and ensure a safe experience for your users.
If you're looking to create a secure and robust web application, partnering with a web application development company can help ensure that security is embedded into your application from the start. Their expertise in building secure, scalable solutions can help you avoid common pitfalls and provide the protection your users expect.
0 notes
Text
Slingshots for a Spider
I recently finished (didn't take the test, I was just stumbling through the course, open mouthed and scared) the ineffable WEB-300: Advanced Web Attacks and Exploitation, from the magnanimous OffSec, which is the preparation course for the Offensive Security Web Expert certification (OSWE). The image is a very cool digital black widow spider, which makes sense, because the course is teaching you how to be an attacker on 'the web'.

As scared as I am of spiders, I am enamored by this course. Enough to stare at it for two years then finally take it and complete it over one grueling year. It covers things like: Blind SQL Injection - setting things up in a program called Burpsuite, to repeatedly try sending various things, then clicking a button, and seeing how a website answers, whether it gives us info or errors (which is more info!)


Authentication Bypass Exploitation - skirting around the steps that websites use to make sure you are who you say you are, like taking a 'reset password' click of a button, knowing some admin's email, and getting a database to spit out the token so we can get to the website to reset the password before the admin.



and Server-Side Request Forgery - making a server (someone else's computer in charge of doing real work instead of messing around with a human) ask its connections and resources to get something for you.

Now I know what you're probably thinking: Holy cow, where to even start? If you're not thinking that, congratulations. If you are, I've the answer: Tools. No spider is eating flies without sensing, lurking, biting... this metaphor to say: No one's doing it by hand with no help.
So what tools are helpful? How do you know what's good, what's useful, what's a dime a dozen, what's only going to do part of what you want versus all of it...

Luckily the fan favorites are famous for a reason. Just about anything you'd need is already downloaded into Kali Linux, which is jam packed with much, much more than the average hacker even needs!
Tools are dependent on what you need to do. For this class we need to inspect web traffic, recover source code, analyze said code of source, and debug things remotely.
Inspecting web traffic covers SSL / TLS and HTTP. SSL is Secure Sockets Layer and TLS is Transport Layer Security. These are literally just protocols (rules! internet rules that really smart people spent a lot of time figuring out) that encrypts traffic (mixes and chops and surrounds your communication, to keep it safe and secure). HTTP is the hypertext transfer protocol, which is another set of rules that figures out how information is going to travel between devices, like computers, web servers, phones, etc.

But do you always follow the rules? Exactly. Even by accident, a lot can fall through the cracks or go wrong. Being able to see *exactly* what's happening is pivotal in *taking advantage* of what's not dotting the i's and crossing the t's.
Possibly the most famous tool for web hacking, and the obvious choice for inspecting web traffic, is Burp Suite. It gathers info, can pause in the middle of talking to websites and connections that usually happen behind the scenes in milliseconds, like manipulating HTTP requests. You can easily compare changes, decode, the list goes on.


Decompiling source code is the one where you could find a million things that all do very specific things. For example dnSpy can debug and edit .NET assemblies, like .exe or .dll files that usually *run*, and don't get cracked open and checked inside. At least not by a normal user. .NET binaries are easier to convert back to something readable because it uses runtime compiling, rather than compiling during assembly. All you have to do is de-compile. It's the difference between figuring out what's in a salad and what's in a baked loaf of bread. One's pretty easy to de-compile. The other, you'd probably not be able to guess, unless you already knew, that there are eggs in it! dnSpy decompiles assemblies so you can edit code, explore, and you can even add more features via dnSpy plugins.


Another type of code objects useful to analyze are Java ARchive or JAR files. Another decompiler that's good for JAR files is JD-GUI, which lets you inspect source code and Java class files so you can figure out how things work.


Analyzing source code is another act that can come with a lot of options. Data enters an application through a source. It's then used or it acts on its own in a 'sink'. We can either start at the sink (bottom-up approach) or with the sources (top-down approach). We could do a hybrid of these or even automate code analysis to snag low-hanging fruit and really balance between time, effort and quality. But when you have to just *look* at something with your *eyes*, most people choose VSCode. VSCode can download an incredible amount of plug ins, like remote ssh or kubernetes, it can push and pull to gitlab, examine hundreds of files with ease, search, search and replace... I could go on!

Last need is remote debugging, which really shows what an application is doing during runtime (when it's running!). Debugging can go step-by-step through huge amalgamations using breakpoints, which can continue through steps, step over a step, step INTO a step (because that step has a huge amalgamation of steps inside of it too, of course it does!), step out of that step, restart from the beginning or from a breakpoint, stop, or hot code replace. And the best part? VSCode does this too!

Remote debugging lets us debug a running process. All we need is access to the source code and debugger port on whatever remote system we happen to be working in.
Easy, right? Only a few tools and all the time in the world... WEB-300 was mostly whitebox application security, research, and learning chained attack methods. For example, you'd do three or seven steps, which incorporate two or four attacks, rather than just one. It's more realistic, as just one attack usually isn't enough to fell a giant. And here there be giants. Worry not: we've got some slingshots now.
The next step is seeing if we can get them to work!

Useful links:
(PortSwigger Ltd., 2020), https://portswigger.net/burp/documentation
(DNN Corp., 2020), https://www.dnnsoftware.com/
(0xd4d, 2020), https://github.com/0xd4d/dnSpy
(ICSharpCode , 2020), https://github.com/icsharpcode/ILSpy
(MicroSoft, 2021), https://docs.microsoft.com/en-us/dotnet/csharp/language-reference/compiler-options/command-line-building-with-csc-exe
(Wikipedia, 2021), https://en.wikipedia.org/wiki/Cross-reference
(Wikipedia, 2019), https://en.wikipedia.org/wiki/Breakpoint
(Oracle, 2020), https://docs.oracle.com/javase/tutorial/deployment/jar/manifestindex.html
(Wikipedia, 2021), https://en.wikipedia.org/wiki/Integrated_development_environment
(Microsoft, 2022), https://code.visualstudio.com/(Wikipedia, 2021), https://en.wikipedia.org/wiki/False_positives_and_false_negatives
(Oracle, 2021), https://docs.oracle.com/javase/8/docs/technotes/guides/jpda/conninv.html#Invocation
0 notes
Text
Resolving The certificate chain was issued by an authority that is not trusted.
The error message you’re seeing indicates a problem with the SSL/TLS certificate used by the SQL Server. This typically happens when the server uses a self-signed certificate or a certificate issued by a Certification Authority (CA) that is not recognized by the client system. To resolve this issue, you have a few options: Install the Certificate as a Trusted Root on the Client: Import the…
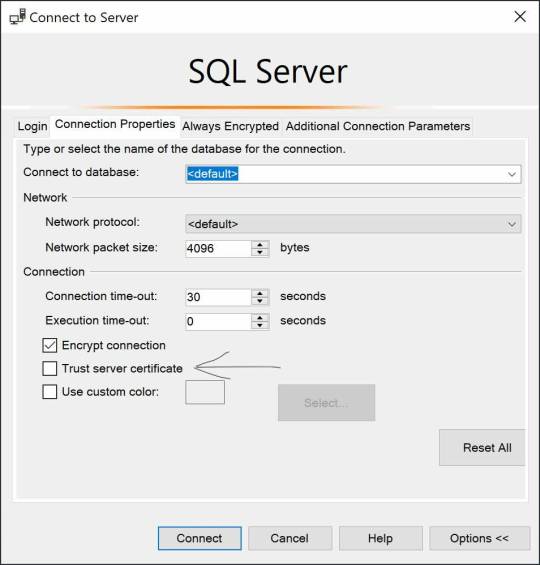
View On WordPress
#SQL Server certificate install#SQL Server security configuration#SQL Server SSL error#Trusted Root Certification Authorities#TrustServerCertificate
0 notes
Text
The Art and Science of Website Development: Crafting Digital Experiences in the Modern Era
In the digital age, websites have become the cornerstone of online presence for businesses, organizations, and individuals alike. The process of website development is a complex interplay of design, functionality, and technology, requiring a deep understanding of both user needs and technical capabilities. From frontend design to backend infrastructure, every aspect of website development plays a crucial role in creating a seamless and engaging user experience. As the internet continues to evolve, so too do the tools and techniques used by developers to build websites that are not only visually appealing but also fast, secure, and scalable.
At the heart of website development lies the frontend, the part of the website that users interact with directly. This is where HTML, CSS, and JavaScript come into play, forming the building blocks of modern web design. HTML provides the structure of the page, CSS adds style and visual appeal, and JavaScript brings interactivity and dynamic content. Frameworks like React, Angular, and Vue.js have revolutionized frontend development, enabling developers to create complex, responsive, and highly interactive user interfaces. These frameworks leverage the concept of components, reusable pieces of code that can be combined to build intricate layouts and features. Additionally, responsive design ensures that websites look and function well on a variety of devices, from desktops to smartphones, using techniques like media queries and flexbox.
While the frontend is what users see, the backend is the engine that powers the website. This is where server-side logic, databases, and application programming interfaces (APIs) come into play. Backend development often involves languages like Python, Ruby, PHP, and Node.js, each offering its own set of advantages and use cases. For instance, Node.js is particularly well-suited for real-time applications, while Python is favored for its simplicity and versatility. Databases, such as MySQL, PostgreSQL, and MongoDB, store and manage the data that fuels the website, from user profiles to product catalogs. APIs, on the other hand, enable communication between the frontend and backend, as well as integration with third-party services like payment gateways and social media platforms.
One of the most critical aspects of website development is performance optimization. Users expect websites to load quickly and run smoothly, and even a few seconds of delay can lead to higher bounce rates and lost revenue. Techniques like caching, minification, and lazy loading are commonly used to improve performance. Content Delivery Networks (CDNs) distribute website content across multiple servers worldwide, reducing latency and ensuring fast load times for users regardless of their location. Additionally, image optimization and code splitting help reduce the size of assets and JavaScript bundles, further enhancing performance. Tools like Google Lighthouse and WebPageTest provide valuable insights into website performance, helping developers identify and address bottlenecks.
Security is another paramount concern in website development. With cyber threats on the rise, developers must implement robust security measures to protect user data and maintain trust. HTTPS is now a standard requirement, encrypting data transmitted between the user’s browser and the server. Web Application Firewalls (WAFs) and SSL/TLS certificates add an extra layer of protection, safeguarding against attacks like Cross-Site Scripting (XSS) and SQL injection. Regular security audits and penetration testing are essential for identifying vulnerabilities and ensuring compliance with regulations like GDPR and PCI DSS. Furthermore, two-factor authentication (2FA) and secure password policies help protect user accounts from unauthorized access.
The rise of headless CMS and static site generators has introduced new possibilities for website development. A headless CMS separates the content management system from the frontend, allowing developers to use any technology stack to build the user interface. This approach offers greater flexibility and scalability, making it ideal for complex websites with diverse content needs. Static site generators like Gatsby and Jekyll pre-render pages at build time, resulting in faster load times and improved security. These tools are particularly well-suited for blogs, documentation sites, and other content-heavy websites.
In conclusion, website development is a multifaceted discipline that combines creativity, technical expertise, and strategic thinking. From frontend design and backend infrastructure to performance optimization and security, every aspect of the process plays a crucial role in creating a successful website. As the digital landscape continues to evolve, developers must stay abreast of emerging trends and technologies, from headless CMS to progressive web apps (PWAs), to deliver cutting-edge solutions that meet the needs of modern users. By mastering the art and science of website development, developers can create digital experiences that are not only visually stunning but also fast, secure, and scalable, ensuring their place at the forefront of the digital revolution.
Make order from us: @Heldcbm
Our portfolio: https://www.linkedin.com/company/chimeraflow
0 notes
Text
How to Build a Fast, Secure, and Scalable Website
In today’s digital age, having a website that is fast, secure, and scalable is essential for businesses and developers alike. Whether you are building a personal blog, an e-commerce platform, or an enterprise-level application, ensuring optimal performance, security, and scalability should be a priority. A well-optimized website enhances user experience, improves search engine rankings, and ensures seamless operation even during traffic surges. In this blog, we’ll explore best practices to help you build a website that meets these critical criteria and supports business growth effectively.
1. Optimize for Speed
Website speed plays a crucial role in user experience and search engine rankings. Here are some key strategies to enhance website performance:
Use a Fast Hosting Provider
Choosing the right hosting provider can significantly impact your website's speed and reliability. Opt for a service that offers high-speed performance, such as cloud hosting or dedicated servers. Popular hosting providers like AWS, Google Cloud, and DigitalOcean offer scalable and high-performance solutions tailored to different business needs.
Leverage Content Delivery Networks (CDNs)
CDNs store copies of your website’s static assets across multiple global servers, reducing latency and load times for users in different locations. Using a CDN ensures your website loads quickly, even for visitors accessing it from distant geographic locations.
Optimize Images and Media Files
Large image files can slow down your website significantly. Use tools like TinyPNG or WebP format to compress images without sacrificing quality. Additionally, consider using responsive image formats that adjust dynamically based on device resolution and screen size.
Minify CSS, JavaScript, and HTML
Reducing the size of your code by minifying CSS, JS, and HTML files can significantly improve loading times. Tools like UglifyJS, CSSNano, and HTMLMinifier can help streamline your code while maintaining its functionality.
Implement Lazy Loading
Lazy loading ensures that images, videos, and other heavy resources load only when needed, improving initial page load speed. This technique reduces the amount of data that needs to be loaded immediately when a user lands on your page.
Use Browser Caching
By enabling caching, browsers can store copies of static resources, reducing the need to reload them each time a user visits the website. This helps in significantly improving return visits and reducing server load.
2. Enhance Security Measures
With cyber threats on the rise, securing your website is non-negotiable. Here’s how to protect your site effectively:
Use HTTPS and SSL Certificates
Securing your website with HTTPS by installing an SSL certificate encrypts data between users and your site, preventing cyber-attacks like man-in-the-middle attacks and data breaches.
Regularly Update Software and Plugins
Keep your CMS, themes, and plugins updated to prevent vulnerabilities that hackers may exploit. Outdated software is one of the primary security risks leading to data theft and unauthorized access.
Implement Web Application Firewall (WAF)
A WAF helps filter and monitor HTTP traffic between a web application and the Internet, blocking malicious attacks. It acts as a shield against threats such as SQL injection and cross-site scripting (XSS).
Enable Two-Factor Authentication (2FA)
Adding an extra layer of security, such as 2FA, ensures that only authorized users gain access to sensitive areas of your website. This significantly reduces the risk of unauthorized access due to password breaches.
Perform Regular Security Audits
Use tools like Sucuri or Qualys to conduct regular security scans and identify potential vulnerabilities before hackers do. Conducting periodic penetration testing also helps in strengthening website security.
Implement Secure Authentication and Data Encryption
Use strong passwords, encrypt stored data, and implement security headers to protect against threats like cross-site scripting (XSS) and SQL injection attacks. Keeping security policies updated helps in mitigating emerging cybersecurity risks.
3. Ensure Scalability
Scalability is essential to handle traffic spikes without compromising performance. Here’s how to design a scalable website:
Adopt a Microservices Architecture
Instead of a monolithic structure, use a microservices-based approach where different parts of the application can scale independently. This allows for easier updates and better fault isolation.
Use Load Balancing
Distribute traffic efficiently across multiple servers to prevent overload and downtime. Load balancers like Nginx or AWS Elastic Load Balancing can help maintain high availability even during peak traffic periods.
Leverage Cloud Infrastructure
Cloud platforms like AWS, Google Cloud, and Azure offer auto-scaling features that adjust resources based on traffic demands. This ensures that your website remains responsive even during unexpected traffic surges.
Optimize Database Performance
Use indexing, query optimization, and caching techniques (e.g., Redis or Memcached) to improve database efficiency and handle high loads. A well-optimized database enhances website performance and response time.
Use Asynchronous Processing
For tasks that do not require immediate execution, implement asynchronous processing using message queues (e.g., RabbitMQ, Apache Kafka) to enhance performance. This allows the website to handle multiple processes efficiently without performance lags.
Monitor and Scale Automatically
Set up monitoring tools like New Relic, Google Analytics, or AWS CloudWatch to track performance metrics and automate scaling decisions. Proactive monitoring helps in identifying performance bottlenecks and making necessary optimizations.
Conclusion
Building a fast, secure, and scalable website requires a strategic approach that balances performance optimization, security best practices, and scalable architecture. By implementing these techniques, you can create a website that provides a seamless experience for users while ensuring security and reliability as your business grows.
Need help with website development? At Chirpin, we specialize in building high-performance, secure, and scalable websites. As a digital marketing agency in Delhi, we also provide digital marketing services in Delhi NCR to help businesses enhance their online presence. Whether you are looking for the best digital marketing company in Delhi or need professional digital marketing services in Delhi NCR, Chirpin has you covered. Our expert team works with businesses of all sizes, helping them establish a strong online presence and drive more leads. If you are looking for the best digital marketing company in Delhi NCR that offers comprehensive web development and marketing solutions, contact us today to bring your digital vision to life!
exhibition stand builders in dubai exhibition stand contractors in dubai exhibition contractors in dubai exhibition stand builders dubai dubai exhibition stand contractor exhibition stand designers in dubai best exhibition stand contractor in dubai best exhibition stand builders dubai exhibition stand design company in dubai exhibition stand design dubai dubai exhibition stands exhibition company in dubai exhibition companies in dubai exhibition stand builder abu dhabi exhibition stand contractor in abu dhabi exhibition stand contractors abu dhabi exhibition stand companies in abu dhabi exhibition stand design company abu dhabi exhibition stand in abu dhabi
0 notes
Text
Maximize Your Control with Dedicated Windows Servers
When it comes to web hosting and managing digital resources, the need for control, reliability, and high performance is non-negotiable. This is where Dedicated Windows Servers step in, offering a premium solution for businesses, developers, and enterprises looking to elevate their web presence. Unlike shared hosting or virtual private servers (VPS), dedicated servers provide an exclusive environment, giving you full control over your resources and software configurations.
In this blog, we'll explore the benefits and reasons why dedicated Windows servers are the ideal choice for those seeking maximum control over their hosting environment.
What is a Dedicated Windows Server?
A Dedicated Windows Server refers to a physical server that is entirely dedicated to a single user or organization. This means that you don’t share resources like CPU, RAM, or bandwidth with other clients. Powered by the Windows operating system, these servers support a variety of enterprise-level applications, including SQL Server, Active Directory, and custom web hosting environments.
The Windows environment is known for its user-friendly interface and wide support for software, making it an excellent choice for businesses that rely on Microsoft-based applications and require a stable, familiar platform.
1. Full Control Over Your Server
One of the most significant advantages of using a dedicated Windows server is complete control. As the sole user of the server, you have administrative access to the entire machine. This means you can install and configure any software, change system settings, and implement custom solutions according to your needs.
With root access to the operating system, you can:
Install and update software without restrictions.
Set up complex configurations to meet business requirements.
Ensure maximum security by controlling firewall settings and access permissions.
Install custom scripts and tools that may not be available in shared hosting environments.
This level of flexibility is essential for businesses with specific software needs or those operating resource-intensive applications.
2. Enhanced Performance and Reliability
With a dedicated Windows server, performance is vastly improved compared to shared hosting or VPS. Since you're the only user, the server's resources are allocated entirely to your applications and websites, ensuring faster load times and better overall performance.
Key performance benefits include:
No Resource Sharing: Unlike shared hosting, where multiple users share the same server, a dedicated server's resources are all yours.
Better Uptime: Since the server is dedicated to your use, there's less likelihood of experiencing downtime caused by the actions of other users.
Scalability: Dedicated servers can be easily upgraded to accommodate growing needs, whether that involves adding more RAM, storage, or processing power.
This reliability is crucial for businesses that require constant uptime, such as e-commerce stores, large websites, and enterprise applications.
3. Improved Security and Customization
Security is one of the most critical factors for any business operating online. With a dedicated Windows server, you can take control of your security measures and implement custom security protocols. Unlike shared hosting, where security depends on the actions of other users, a dedicated server offers isolated resources, reducing the risk of cyber-attacks and data breaches.
You can customize security settings by:
Installing and configuring your own firewalls.
Using Windows Security features such as BitLocker and Windows Defender.
Creating isolated environments with virtual machines (VMs).
Enabling regular backups and disaster recovery plans.
Implementing SSL certificates for secure transactions.
These customizable options allow you to create a robust security framework suited to your business’s specific needs.
4. Dedicated Support and Expert Assistance
When you opt for a dedicated Windows server, you're not just paying for the hardware and software – you're also getting access to expert technical support. Most hosting providers offer 24/7 support with dedicated teams that understand the intricacies of Windows servers.
This means:
Quick Resolution of Issues: Any technical difficulties or issues are resolved faster with a team that understands your specific setup.
Proactive Monitoring: Many providers offer proactive server monitoring services to identify potential issues before they impact your operations.
Consultation and Optimization: Dedicated support staff can guide you through system optimization and help you get the most out of your server.
This hands-on support ensures you can maintain your server's performance, security, and stability with ease.
5. Cost-Effective for Large Operations
Although dedicated Windows servers are generally more expensive than shared hosting or VPS options, they can be incredibly cost-effective for larger operations or businesses with high resource demands. By consolidating multiple applications, websites, and services onto a single dedicated server, you can save money on multiple hosting solutions.
Additionally, with full control over your server, you can optimize costs by adjusting the configuration to your precise needs, avoiding unnecessary expenses for resources you don’t use.
Conclusion
A Dedicated Windows Server offers unmatched control, performance, and security, making it the ideal choice for businesses that require a customized, scalable, and reliable hosting environment. Whether you’re running mission-critical applications, handling sensitive data, or operating large-scale websites, the flexibility and power provided by a dedicated server can take your business to the next level.
If you’re ready to maximize your control and optimize your online presence, consider upgrading to a dedicated Windows server today. With the right configuration and support, you’ll experience an enhanced digital experience that positions your business for long-term success.
0 notes
Text
Regulatory Compliance & Security: Why Enterprises Migrate to Shopify

Data breaches erode trust and damage reputations. Stringent regulations like GDPR and CCPA place immense pressure on e-commerce businesses to protect sensitive data. While platforms like Magento and WooCommerce offer powerful features, they often present significant security and compliance challenges. This blog post explores the complexities of e-commerce security and compliance, examines the difficulties enterprises face with Magento and WooCommerce, and highlights why Shopify has become a preferred solution for businesses prioritizing security and streamlined compliance.
The Evolving E-commerce Landscape: Compliance & Security
The e-commerce landscape is dynamic, demanding a proactive approach to compliance and security. It’s no longer enough to simply meet minimum requirements; businesses must cultivate a culture of security and prioritize data protection. Key regulations like GDPR, CCPA/CPRA, PCI DSS, and HIPAA impose strict rules for data handling, emphasizing:
Data Privacy: Protecting personal information from unauthorized access, use, or disclosure.
Security Standards: Implementing technical and organizational measures to safeguard data.
Transparency: Open communication with consumers about data practices.
Accountability: Taking responsibility for data protection and compliance.
However, e-commerce platforms are constantly targeted by cybercriminals. Common threats include:
SQL Injection: Exploiting vulnerabilities to manipulate databases.
Cross-Site Scripting (XSS): Injecting malicious scripts to steal data or redirect users.
Malware: Malicious software designed to damage systems or steal data.
DDoS Attacks: Overwhelming websites with traffic, causing downtime.
Phishing: Deceptive attempts to obtain sensitive information.
Ransomware: Encrypting data and demanding ransom for its release.
These attacks can lead to:
Financial Loss: Stolen data, lost sales, recovery costs, fines.
Reputational Damage: Loss of customer trust, negative brand perception.
Legal Penalties: Fines and sanctions for non-compliance and breaches.
Operational Disruption: Website downtime, order fulfillment delays.
The cost of non-compliance and security breaches is substantial, making robust security measures essential.
Challenges with Magento & WooCommerce
Magento, while powerful, can be complex for enterprises, particularly regarding security and compliance. Challenges include:
Complexity: Requires specialized technical expertise for security management.
Plugin Vulnerabilities: Reliance on third-party plugins, each a potential weakness.
Maintenance Burden: Ongoing updates and patching require dedicated resources.
Scalability Challenges: Security and compliance become more complex with growth.
WooCommerce, built on WordPress, faces similar challenges:
Plugin Issues: Inherits vulnerabilities from the WordPress plugin ecosystem.
Hosting & Server Management: Responsibility for self-hosting and server security.
Limited Enterprise Features: May lack features for complex compliance needs.
Shopify’s Advantages: A Secure & Streamlined Solution
Shopify offers a compelling alternative, simplifying compliance and enhancing security with:
Built-in Security Features: PCI DSS compliance, SSL certificates, fraud prevention, DDoS protection, regular updates.
Simplified Compliance Management: Data encryption, secure hosting, automated backups, compliance certifications.
Centralized Platform: Streamlined management, improved visibility, reduced costs.
Scalability and Reliability: Cloud-based infrastructure, high availability, global reach.
App Store Ecosystem (with caution): Extends functionality, but requires careful vetting of apps.
24/7 Support: Assistance with security and compliance issues.
Migrating to Shopify: Practical Considerations
Migrating to Shopify requires careful planning and execution:
Data Migration: Secure and accurate transfer of data, including customer information, product catalogs, and order history. This involves data audits, choosing a migration method, data mapping, testing, and a go-live migration.
SEO Best Practices: Maintaining search visibility through 301 redirects, similar URL structures, updated sitemaps, and rank monitoring.
Integration with Existing Systems: Connecting Shopify with ERP, CRM, and other business systems for seamless operations.
Choosing the Right Shopify Plan: Selecting a plan that meets specific business needs and budget.
Conclusion
Maintaining compliance and security on Magento and WooCommerce can be complex and resource-intensive. Shopify simplifies these processes with built-in features, a centralized platform, and a robust infrastructure. If you’re seeking a more secure and streamlined e-commerce solution, consider migrating to Shopify. Contact us for a free consultation or start your free Shopify trial today.
1 note
·
View note
Text
PHP Full-Stack Developer Certification Course
1. Introduction to Full-Stack Development
Understanding the full-stack ecosystem.
Role of PHP in modern web development.
Overview of front-end and back-end integration.
2. Frontend Development
HTML5 and CSS3: Building responsive and accessible web layouts.
JavaScript: Core concepts, DOM manipulation, and ES6 features.
Bootstrap: Designing responsive and mobile-first web pages.
React or Vue.js (Optional): Adding dynamic interactivity to your web apps.
3. Backend Development with PHP
PHP Basics: Syntax, variables, functions, and error handling.
Working with Databases: MySQL basics, CRUD operations, and PDO.
Advanced PHP Concepts: Object-Oriented Programming, sessions, and file handling.
Building APIs: RESTful APIs using PHP for dynamic data.
4. Full-Stack Integration
Combining front-end and back-end using PHP.
AJAX for seamless data exchange.
Creating and managing sessions for user authentication.
5. Database Design and Management
Normalization techniques for efficient databases.
SQL queries for complex data retrieval.
Using database management tools like phpMyAdmin.
6. Framework Mastery: Laravel
Setting up Laravel for rapid development.
Routing, controllers, and views.
Eloquent ORM for advanced database interactions.
Building scalable and secure applications.
7. Version Control with Git
Basics of Git and GitHub.
Managing code repositories and collaborating on projects.
8. Deployment and Hosting
Configuring web servers (Apache, Nginx).
Hosting on platforms like cPanel, AWS, or Heroku.
Managing domains and SSL certificates.
9. Capstone Project
Develop a complete full-stack application (e.g., an e-commerce site or blog platform).
Incorporate learned skills into a professional project.
10. Certification Exam
Online test to validate your knowledge.
Practical exam to demonstrate your development skills.
Who Should Enroll?
Aspiring full-stack developers.
Web designers aiming to enhance their back-end knowledge.
PHP developers seeking to expand their skill set.
Course Duration:
12–16 weeks (flexible learning pace).
Outcome:
Certification as a PHP Full-Stack Developer.
Portfolio of projects showcasing your skills.
Fullstack course in chennai
Fullstack developer course in chennai
Fullstack training in chennai

0 notes