#Time Access Biometric Machine
Explore tagged Tumblr posts
Text
The Ultimate Guide to Choosing Attendance Management Software for Your Company
In today’s hybrid and dynamic work environments, attendance management software is no longer a nice-to-have but a strategic necessity. Managing employee attendance manually using spreadsheets or punch cards leads to inaccuracies, buddy punching, and administrative overhead, which can drain resources and impact productivity.
By adopting modern attendance management software, companies can automate attendance tracking, ensure policy compliance, reduce administrative workload, and gain actionable insights into employee productivity and engagement. It transforms a tedious HR task into a data-driven, strategic function that supports business goals.

This guide will walk you through why your company needs attendance management software, what features to look for, and how solutions like Spintly can support your business in creating efficient, seamless, and secure attendance workflows.
Why Companies Need Attendance Management Software
1. Automation Reduces Human Errors
Manual tracking can lead to missed entries, duplicate records, and inaccuracies in payroll. Attendance management software automates these processes, ensuring precision in time tracking, leave balances, and compliance.
2. Enhances Productivity
Automated attendance systems reduce administrative tasks, allowing HR teams to focus on employee engagement, talent management, and strategic HR initiatives.
3. Supports Hybrid and Flexible Work Models
With employees working from offices, home, or co-working spaces, attendance management software helps track attendance seamlessly across locations without compromising on accuracy.
4. Improves Compliance and Transparency
Organizations must comply with labor laws, working hour regulations, and overtime policies. Attendance management software ensures transparent record-keeping and easy retrieval of attendance data during audits.
Key Features to Look for in Attendance Management Software
When evaluating attendance management software for your company, ensure it aligns with your business model and workforce needs. Here are the essential features to prioritize:
1. Real-Time Attendance Tracking
Choose software that captures real-time check-in and check-out data, whether through biometric devices, mobile apps, or QR codes, reducing the chances of proxy attendance.
2. Integration with Payroll
Look for solutions that integrate seamlessly with your payroll system to automate salary calculations based on working hours, leaves, and overtime.
3. Leave Management
An effective attendance management software should include leave management capabilities, allowing employees to apply for leave and managers to approve or reject requests easily.
4. Mobile Accessibility
With the shift to hybrid work, mobile-friendly attendance management software allows employees to mark attendance, apply for leaves, and track hours remotely.
5. Biometric and Mobile Access Integration
Integrating with biometric devices and mobile-based access control systems enhances accuracy and security in attendance tracking.
6. Cloud-Based and Scalable
Cloud-based solutions enable you to access attendance data from anywhere while supporting scalability as your workforce grows.
7. Detailed Analytics and Reporting
Data-driven insights help HR teams analyze attendance patterns, late arrivals, absenteeism, and productivity trends to make informed workforce management decisions.
How Attendance Management Software Enhances Security and Efficiency
Modern attendance management software can integrate with access control systems to ensure that attendance tracking aligns with building security. For instance, integrating Spintly’s cloud-based, wireless access control with attendance management allows companies to:
Automate attendance as employees enter or exit specific zones.
Eliminate manual sign-ins, reducing physical touchpoints.
Monitor workplace occupancy for safety and compliance.
Restrict unauthorized access while capturing accurate attendance data.
Such integration not only ensures security but also streamlines HR workflows while enhancing employee experiences.
Steps to Choose the Best Attendance Management Software
1. Assess Your Business Requirements
Consider your company size, work policies (hybrid, remote, on-site), and workforce management needs to shortlist relevant features.
2. Evaluate Integration Needs
Check if the attendance management software integrates with your HRMS, payroll system, and existing access control solutions.
3. Consider User Experience
The software should be intuitive for HR teams and easy for employees to use, whether through biometric attendance, mobile apps, or web portals.
4. Review Security and Compliance
Choose a platform that offers secure data handling, compliance with privacy regulations, and audit-friendly records.
5. Check Vendor Support and Scalability
Look for a vendor with reliable support and a product that scales with your organization’s growth without requiring frequent system changes.
6. Pilot Testing
Before full-scale implementation, run a pilot program to identify gaps and ensure the software aligns with your operational workflows.
Why Choose Spintly for Attendance Management
Spintly offers a modern, cloud-based attendance management software that integrates seamlessly with its advanced wireless access control systems. By choosing Spintly, your business benefits from:
Contactless Attendance: Through mobile phones, QR codes, and biometric devices.
Cloud-Based Management: Manage attendance across multiple offices from a centralized dashboard.
Integration: Seamless integration with HRMS and payroll for automated workflows.
Scalable Solution: Suitable for startups, SMEs, and large enterprises.
Enhanced Security: Access control integration ensures only authorized personnel can mark attendance.
Spintly’s platform aligns with the hybrid work models of modern businesses while reducing administrative burdens and maintaining compliance.
Future Trends in Attendance Management Software
Adopting attendance management software today positions your business to benefit from emerging trends such as:
AI-Driven Insights: Predict absenteeism patterns and optimize staffing.
IoT Integration: Use sensors to track workspace occupancy for safety and efficiency.
Geofencing: For tracking attendance of field staff or remote teams based on location.
Mobile-First Solutions: Increasing use of smartphones for attendance and access control.
Sustainable Operations: Reducing paperwork and manual processing to align with green goals.
These trends will help transform attendance tracking into a strategic asset for your organization.
Future-Proof Your Workforce Management
Investing in attendance management software is a crucial step for businesses looking to streamline operations, improve employee accountability, and align workforce management with modern work practices. Whether you’re managing a small team or a large enterprise, the right solution will reduce administrative workload, enhance security, and support data-driven HR decisions.
Solutions like Spintly help companies move towards a seamless, contactless, and secure attendance management system while supporting scalable growth and future readiness.
#attendance management#time and attendance software#attendance machine#attendance management software#mobile access#spintly#smartacess#accesscontrol#access control solutions#access control system#visitor management system#biometrics#smartbuilding#biometric attendance
0 notes
Text
ZKTeco iFace880 Plus Multi Biometric Time Attendance

ZKTeco presents the iFace880 Plus multi-biometric time attendance and access control terminal which supports 3,000 palm templates, 4,000 fingerprint templates, and 10,000 cards (optional).
It is equipped with ZKTeco’s latest hardware platform and algorithm like 3-in-1 contactless palm recognition (palm shape, palm print, and palm vein).
This makes the terminal perform bio-authentication with the palm vein, palm print, and the shape of the palm when the sensor detects a hand that is presented.
The terminal’s touchless palm authentication method with a novel hand tracking technique allows angle tolerance as wide as +/- 60° in the roll axis.
With the advanced palm and face algorithm and multi-biometric verification technology, users can experience the terminal’s enhanced anti-spoofing ability and its significantly improved security level.
Features of ZKTeco iFace880 Plus
• 3,000 face, 3,000 palm, and 4,000 fingerprint templates • Multiple authentication methods: face/palm/fingerprint/card/password • Fast verification speed • Modern design and interactive UI • Chip encryption for firmware protection • Optional built-in backup battery providing approximately 4 hours of continuous operation
ZKTeco iFace880 Plus price in UAE
Cost To Cost provides the best price for the ZKTeco iFace880 access control
#zk#zkteco#dubai#uae#business#it support#time attendance machine#fingerprint time attendance and access control#access control systems#time attendance#biometric time attendance#ZKTeco iFace880 plus#costtocost#sharjah#biometric attendance system#fingerprint recognition
0 notes
Text
Parking Guidance System Saudi:-
Superior and advanced technology, The presence of a car parking management system certainly matters. The car owners get a comfortable parking experience. If the parking space is unavailable, the car owners come under stress. https://www.prologicfirstss.com/Car-Access.html

#parking management system saudi#types of rfid access cards in saudi#KIOSK for Attraction Saudi#qr code based parking saudi#car park access control systems#time access biometric machine saudi
0 notes
Text
Open Up Baby
Title: Open Up Baby Pairing: Tony Stark x Female Reader

Summary: Tony Stark straps you into a StarkTech-compatible bench for a private demonstration of his newest toys- complete with biometric feedback,
Word Count: 3.6k
Warnings: / Explicit Content /18+, Minors DNI, SMUT… BDSM/Restraints/Bondage, custom tech ball gag, toys (Egg vibe, anal beads, dildo) Overstimulation, Toy fucking/Machine-assisted thrusting, Filthy talk (Tony can't shut up), AI assists with data tracking, clinical observation, forced openness, Sensory overload
A/N: my entry for @avengers-assemble-bingo for April Kinky Bingo… Well this one turned into a whole thing.. Square: B2- Open Up Baby Card Number: KB003
You were already strapped to the bench- back arched, thighs spread wide in glossy chrome stirrups, wrists bound snug in Stark-grade cuffs that didn’t budge an inch. The synthetic leather beneath you was cool against your skin, but your body was already starting to heat with anticipation. The bench itself shifted slightly with every movement, like it was reading your tension, calibrating every twitch of your muscles into data Tony could access later.
You could hear the soft hum of the room’s ambient systems, the low mechanical whirrs, the faint electric pulse of tech running in standby, and underneath it all, Tony’s voice. He hummed absently as he moved around you, flicking through translucent holoscreens that floated in the air, readable only to him. Light glinted off his arc reactor through the thin black shirt he wore, sleeves rolled up to his elbows, veins flexing with every subtle flick of his fingers.
He looked like a scientist. Or a surgeon. No, a goddamn artist.
“You look tense,” he murmured, stepping in close, his fingers grazing your jaw with a feather-light touch. “That won’t do. We need to get a clean read. No clenched teeth, no locked jaws. Just you- open and…relaxed.”
He held up a sleek piece of tech. A mix of leather and metal. To you it looked like a ball gag. That wasn’t just a gag. It was his gag. Something custom. Personal. Laced with Stark Industry Tech.
“Open up, baby. Gotta install the biometric reader. It’s not science without a baseline.”
You hesitated, lips twitching. Just for a second. But he didn’t push. He just waited you out, smirk deepening, one brow arched like he had all the time in the world. That cocky, knowing gaze made you squirm even before anything touched you. Your breath hitched. And then you parted your lips.
“There we go,” he said, tone thick with approval as he slid the gag into place. It clicked against your teeth, snug and firm. A soft vibration flickered across your tongue as it locked in pushing the muscle down.
Friday’s voice chimed in overhead, calm and clinical.
“Gag calibration complete. Biometric sync active. Tracking vocal response, saliva levels, and tongue pressure.”
Tony leaned down, brushing his lips across your cheek in a whisper of a kiss. “Good girl. Now let’s get to work.”
He started with the egg.
Sleek. Silver. Pulsing faintly in his hand like it had a heartbeat of its own. The metal shimmered under the clinical lights, smooth and polished, shaped with the kind of precision that only Stark could deliver. He turned it over once, twice, like he was admiring a prized gadget- one that he was particularly proud of.
He showed it to you like a doctor unveiling a revolutionary new tool- calm, confident, deeply amused. Except this wasn’t a sterile exam room, and the look in his eyes wasn’t professional. His smirk told you he already knew what kind of mess this thing would reduce you to.
"This is your warm-up," he said, voice low and playful. "Phase One. Internal warming protocol. Testing receptivity. Calibration through heat and pulse response."
You whimpered into the gag. Of course you were excited- he’d been teasing you with this little 'demonstration' all week. Whispering promises in your ear, tapping out reminders on your thigh, dropping technical jargon laced with filth that left your core throbbing before he’d even touched you. Now that it was finally happening, your whole body was buzzing with need.
He didn't wait. He moved closer, one gloved hand parting your thighs a little further, the other settling between them. The bench adjusted beneath you, lifting your hips another inch to meet his touch perfectly. His fingers dipped between your folds- testing your wetness, teasing you just enough to make your body jerk in its bonds.
"Already responsive," he muttered, half to himself, half to Friday. "She’s going to be a dream to log."
He slid the egg in with two fingers, slow and deliberate. The cool metal kissed your entrance, making you flinch slightly- it was colder than you expected, stark contrast against your heated skin. Your walls instinctively tried to resist, clenching down, but his fingers were patient, coaxing you open, parting you around the sleek, unyielding toy.
The egg slid upward, heavy and smooth. As it moved deeper, your body yielded to it, the slow stretch making your breath catch. Its contours were designed to press into every sensitive spot, and you could feel your muscles fluttering around it, trying to accommodate the sudden fullness. As he pushed it deeper, you could feel every inch of it being swallowed by your body, your slick muscles tightening, fluttering around the intrusion.
He pushed the egg up high inside you, then paused, his finger still inside you too. "Squeeze for me," he ordered. You did, instinctively, your walls closing down as you used your pelvic floor, and Tony gave the platic string attached a soft tug.
The stretch, the resistance- it was delicious. The egg stayed locked in place. You couldn’t push it out if you tried. He smiled, clearly pleased.
"Perfect. Secure fit," he murmured. "Wouldn’t want it popping out mid-test."
It settled deep inside you, a sinful throb blooming in your core. Then it pulsed- just once, a quick flutter that made you jolt.
"There we go," he breathed, watching the screen light up with new data. "Didn’t even turn it on yet and she’s already going. Fuck, I love this job."
You were barely processing the first toy when he reached for the second.
Beads. Tapered, growing in size, each one gleamed under the soft blue lighting like tiny pieces of futuristic art. You squirmed, thighs pressing together, but it was no use- Stark had seen your reaction.
Tony laughed- low and delighted.
"Didn’t know we were going there, huh?" He nudged your knees apart again, voice dipping to a darker octave. "Come on, baby. I want you to open up for me. Let’s see what this one does..."
You shook your head slightly. Whimpered into the gag. Wide eyes watching him as you tried to protest around the ball gag in your mouth.
Tony turned to the tray beside him, selecting a small, frost-blue tube of gel. "Wouldn't be very considerate to skip prep," he muttered, more to himself than to you. He uncapped the tube and squeezed a slow, deliberate line of the slick, glistening substance along the length of the beads. The gel shimmered faintly under the light, warming as it reacted with the ambient temperature.
He coated each bead carefully, fingers moving with methodical ease, making sure the entire string was evenly slicked. "Lubricated. Body-safe. Custom formula," he said with a wink. "Slippery enough to slide in smooth- sticky enough to stay in place until I say otherwise."
Then he held the beads up for you to see, the string dangling between his fingers. You tensed instinctively.
"Oh no. You’re freezing up. Can’t test properly if you don’t behave. Legs. Open."
You didn’t.
Tony tsked, clicking his tongue in mock disappointment. Then he grabbed your chin, firm and steady, tilting your head so your eyes locked with his.
"Don't think so much. That’s not what good test subjects do."
Click.
The bench tilted beneath you without warning. Your hips rolled upward, knees falling further apart as the restraints auto-adjusted. You were fully exposed now- helpless. Wide open.
"You know I can override those restraints, right? I built them. Now be a good girl and show me everything."
He dipped his finger back into the gel and brought it to your ass, pressing a cool dollop directly to your tight, puckered entrance. The sudden chill made you flinch, but it was followed by the warm glide of his fingertip as he gently teased the gel in slow circles.
"You tense here, too," he said, amused. "Don't worry. This formula warms up just like you do."
He rubbed it in carefully, working the gel into your rim with delicate, coaxing pressure. The sensation tingled- both from the temperature shift and the way his finger circled and pressed until your body finally began to relent.
Then he lowered the beads between your cheeks and began to press them in- one at a time. The first slid in easily, the gel working its magic, cool and slick. The second made your breath stutter. The third had your whole body tensing as your hole stretched just enough to accommodate the new pressure.
Each one pulled a different, desperate noise from you- somewhere between a gasp and a whimper, caught in the back of your throat and forced through the gag in broken fragments.
By the time the third bead settled inside you, you felt full. Stretched in ways that left you panting, your back arching hard off the bench. Everything was working together- the deep pressure of the egg nestled high in your core, the hum beginning to buzz through your clit like a phantom, and now the slow, firm intrusion of the beads pressing against nerves that had you seeing stars. You struggled to catch your breath, the gag forcing each inhale to be short and choppy. Air hissed through your nose while your mouth flooded with saliva, spit slipping from the corners of your lips in thick strands that slid down your neck and onto your chest. The overwhelming heat of arousal and frustration tangled in your gut, building like steam with nowhere to escape. The restraint of it made the fire inside you burn hotter.
Your muscles clenched involuntarily, your hips rocking against the air, chasing friction that didn’t come. You couldn’t speak, couldn’t beg. Just drool, tremble, and take everything he gave you.
"Mmm. That moan? That was bead three. She likes that one, Friday."
"Confirmed," the AI replied. "Pelvic floor tension rising. Heart rate increasing."
"Good. Means it’s working."
The egg began to heat. The beads hummed in sync, and you felt everything shift- internally and externally- as pleasure bled into pressure, and pressure into overload. You were trembling now, thighs twitching again, trying to close- but the bench held you wide, utterly exposed.
"Heart rate’s spiking..." Tony’s voice was pure, filthy glee. "Oh, she’s gonna break soon. Look at her squirm."
You rutted against the air, clit untouched and screaming for attention. Your walls fluttered around the egg, your ass clenching down against the beads as the different pulses overlapped and collided. It was all too much and somehow not enough. You needed more and needed it to stop, all at once.
You tried to breathe, but the gag made it impossible to take anything but shallow, panting gasps. Each exhale was laced with a moan. Drool spilled freely down your chin, dripping warm across your face and neck. You were flushed, messy, wrecked- and he hadn’t even touched your clit.
Your back arched violently off the bench, cords of heat coiling through your belly and thighs. It felt like your body was unraveling, muscles tight and desperate, nerve endings screaming with pleasure.
Tony leaned in again, voice dark and syrup-smooth. "We’ve got her plugged, egged, and ready to combust. Think she can handle the next phase?"
Friday answered, "Orgasm build-up at 87%."
"Perfect." He tapped a command into the air. "Now let’s push her."
The egg pulsed deeper. The beads vibrated sharper. You cried out- moaning, writhing, the gag muffling it into raw, incoherent noise. You couldn’t form words. Couldn’t beg. Just sob through the pressure building to a breaking point.
"Baby, this is science. Filthy, beautiful science."
It hit you like a wave- white-hot and all-consuming. Your legs shook violently in the stirrups, muscles spasming as your body locked around the egg and beads pulsing inside you. Every nerve ending fired in chaotic pleasure, overwhelming your senses. You tried to scream, to sob, but the gag reduced it to a shattered, strangled cry that vibrated through the tech, each desperate noise dutifully logged.
Drool spilled in long, wet strands down your chin as your back bowed hard off the bench, your whole body trembling under the assault of pleasure. Your cunt clenched tight around the egg, milking it involuntarily, while your ass throbbed with each hum of the vibrating beads. Everything inside you was pulsing, moving, grinding you down into submission.
Tony watched, transfixed, his gaze locked on your ruined, shaking form. “There she goes - God, I should patent that moan.”
Your eyes rolled back. You could barely breathe. You could only tremble and leak and convulse as the orgasm tore through you. The bench beneath you vibrated subtly with your body’s response.
Friday: "Orgasm confirmed."
Tony waited until you were trembling, your breathing uneven, your thighs still twitching with aftershocks that rippled through your overstimulated body. Sweat slicked your skin in a thin, glistening sheen, catching the light as your chest heaved with broken gasps around the gag. Your limbs strained weakly against the restraints.
Then- slowly, methodically- he reached between your cheeks and took hold of the first bead. He didn’t rush. He eased it out one at a time, each slick orb dragging along your inner walls with a sticky, stretching glide. You shuddered at the sensation- the unbearable emptiness that bloomed in the wake of each removal. Your ass clenched reflexively around the loss, trying to hold onto what had filled you so completely. But he kept going.
The final bead popped free with a slick, obscene sound. Your hips jolted involuntarily, your back arching once more as your body spasmed again, clinging to the ghost of sensation.
Friday's voice crackled overhead. "Anal pressure reduced. Sphincter still contracting. She’s experiencing post-orgasmic muscle spasms."
Then came the egg.
He curled his fingers inside you, tugging the retrieval loop with a firm, practiced motion. The egg slipped free, wet and shiny, your cunt fluttering uselessly around the sudden void. The stretch, the drag, the warmth- it all left you aching. You cried into the gag, overwhelmed by the emptiness and the continued tremors in your muscles. Your thighs kicked slightly, your knees drawing in as far as the restraints would allow.
"Vaginal walls contracting. Core temperature still elevated. She's not done trembling yet," Friday observed, calm as ever.
Tony held both toys in one hand now- wet, warm, shining. He looked down at you with naked satisfaction.
"That’s some damn good tech," he said. "But we’re not done."
From the tray, he lifted his final piece.
A dildo- sleek, deep grey, Stark-stamped at the base. Modeled after him, and you knew it. Maybe a little bigger. Slightly wider at the base, with delicate ridges along the underside that hinted at something extra. Your breath caught just looking at it.
“This one’s special, baby. Built it from memory- well, from yours,” Tony said, rolling it in his hand. “Temperature regulated, pressure-sensitive, and the best part? The internal sensors sync to your contractions. It responds to you. The more you clench, the deeper it drives. A perfect loop.”
You whimpered around the gag, heart fluttering.
He moved between your spread legs and lined it up against your soaked, fluttering entrance. You were already sensitive- still trembling from the last orgasm- and when the wide tip pressed in, you nearly cried. It stretched you slowly, steadily, a little more than you were used to. Your slick walls resisted at first, clenching down instinctively, but Tony was patient, guiding it with precise control.
“There you go,” he coaxed, voice smooth but sharp-edged with amusement. “That’s it. Take all of it. Come on, baby- I know you can..”
His tone dipped into a purr. “There you go. Taking it like you need it. Bet you love being filled up with Stark-grade tech, huh?”
Your back bowed off the bench as he pushed it in, inch by inch, your pussy yielding to every contour, forced to accommodate the full shape of it. The fullness was delious, your body stretched taut around it. Your eyes rolled back as the final ridge slipped inside, the toy settling deep.
“There,” he said, watching your reactions with fascination. “Fills you out just right. And now... we see what she can really do.”
The base clicked into a pulse pattern, and the toy began to move inside you- slow at first, deliberate, like it was learning your shape. You could feel every textured ridge of the shaft as it rubbed against your inner walls, dragging across oversensitive flesh, sparking little detonations of pleasure with every pass.
Then it pulsed- long and low, a rhythmic thrum that radiated from base to tip, sending heat spiraling through your belly. With every thrust, the toy seemed to stretch you deeper, nudging a spot that made your toes curl and your thighs twitch against the restraints. Your pussy clenched around it reflexively, triggering the internal sensors Tony had mentioned. And just like that, the toy responded- pressing harder, thrusting deeper, faster.
It wasn’t just fucking you- it was reading you, syncing to the wild flutter of your muscles, pulsing in tandem with your arousal.
“Look at her,” Tony murmured, grinning as he watched the toy disappear again and again between your legs. “Every little squeeze makes it work harder. You’re doing this to yourself, baby. And I haven’t even touched your clit yet.”
You’d been so consumed by the thrusting inside you, by the stretch and pulse of the toy, that you hadn’t even noticed Tony move. But suddenly, he was there- looming over you, and the egg was pressed directly to your clit.
The sensation was immediate and brutal.
Your entire body jolted. The contact felt almost painful, your nerves raw and exposed, the stimulation electric. You tried to buck away, hips arching, thighs trembling, but you had nowhere to go.
Tony caught you effortlessly. One hand shoved the egg against your swollen clit, refusing to relent, while the other pressed down on your thigh to keep your knees from closing.
“Uh uh. None of that,” he said smoothly. “You don’t get to hide from this, baby. You earned it.”
You sobbed into the gag, thrashing your hips side to side, but the bench and Tony’s hands made escape impossible. Every attempt to squirm just sent the dildo thrusting deeper inside you, and the egg grinding cruelly over your clit.
“You’re not gonna break,” he whispered, teasing. “You’re gonna burn for me.”
"Don’t you dare run from it. look at me."
He was holding you still- one hand clamped over your thigh to keep your legs spread, the other pressing the egg mercilessly to your clit. You were trembling in his grasp, utterly helpless against the merciless pairing of his tech and his control.
"You’re gonna come again for me, sweetheart. Real data’s in the repeat response," he said, eyes locked on yours, voice both commanding and hungry.
The dildo thrust deep, the ridges grinding against your most sensitive spots as your walls clamped down. The egg buzzed brutally against your swollen clit, so overstimulated you couldn’t tell whether you were trying to run from it or chase it. Every jolt of pleasure lit your nerves like lightning- white-hot and impossible to hold back.
Your body jerked, hips spasming, thighs trembling violently as the sensations overloaded you. Your entire body was working against you- every clench, every twitch, every gasp just triggered the toy to go deeper, harder, faster. You weren’t riding it anymore- it was riding you, and Tony just watched with that devilish smirk, keeping you wide open.
“That's it. Shake for me. Scream into that gag. Show me what science can do.”
The climax tore through you without mercy- harder, deeper, a violent unraveling of every nerve as your body convulsed around the relentless rhythm of the tech inside you. You didn’t just come; you shattered, splintering open in a release so intense it blurred your vision, your mind, your ability to distinguish pleasure from pain. Your vision shattered into sparks, your scream muffled into a raw, hoarse noise behind the gag. Your body thrashed in the restraints, muscles locking as the orgasm ripped through you, longer and sharper than the last.
Friday: "Second orgasm confirmed. Neural spike significant. Subject approaching physical limit."
He slowed the toy, letting it ease to a stop deep inside you before withdrawing it carefully, letting you feel every last ridge dragging along your raw, overstimulated walls. Then, with a gentleness that almost contrasted the torment he’d just put you through, he removed the egg from your clit. The instant the contact broke, your whole body sagged in the restraints with relief and exhaustion. You were shaking, barely breathing- every inch of you buzzing, nerves fried and twitching from the overload.
You could taste salt on your lips- your own tears and spit, your jaw aching from clenching around the gag. You were drenched, body glistening with sweat, your skin flushed and hypersensitive to the air.
He removed the gag last. Your jaw fell slack with a wet, trembling gasp, strands of spit clinging to the corners of your mouth. You blinked up at him, vision hazy, lips wet and parted.
Tony gazed down at you, eyes gleaming with wicked satisfaction, his mouth tugging into a crooked grin that said told you so. He looked like a man admiring his finest creation- smug, yes, but also thoroughly entertained by the glorious, twitching mess sprawled out beneath him.
“You did good, baby. Fucking beautiful. But next time?”
He leaned close, brushing a kiss to your temple- slow, deliberate, his breath warm against your damp skin.
“Think I’ll need to design something that gets you to squirt. Can’t let a variable like that go untested. Wouldn’t be very Stark of me to stop now, would it?”
He turned with a little flourish, tapping the screen with a flick of his fingers, not bothering to look back.
“Friday, save this session. Label it: Successful. Prepare files for Phase Two.”
#avengersassemblebingo#marvel smut#Tony Stark fic#Tony Stark smut#Tony Stark x female reader#Tony Stark x reader#Tony Stark x you#Tony Stark imagine#Iron Man smut#Iron Man x female reader#Iron Man x reader#x female reader#smut#Tony Stark x fem!reader#TonyStark#Avengers assemble Bingo#Iron Man Fic#Iron Man Imagine#Dark!Tony Stark#Avengers Smut#aakinky#AAkinky
1K notes
·
View notes
Text
Why Biometric & Time Attendance Systems Matter
Time is money, and effective time management is essential for businesses to thrive. Traditional punch cards and paper registers have become obsolete and ineffective in modern workplaces. Biometric and time attendance systems have emerged as game-changers for businesses by offering the following benefits:
Accuracy: Biometric systems use unique human characteristics such as fingerprints, facial recognition, or iris scans, ensuring that employees cannot clock in or out for each other. This accuracy reduces payroll errors and saves money.
Elimination of Buddy Punching: With biometric systems, employees cannot clock in or out for their absent colleagues, preventing fraudulent practices and ensuring fair work hours.
Real-time Monitoring: Employers can monitor attendance in real time, providing instant insights into employee attendance patterns and helping with workforce planning.
Security: Biometric data is highly secure, reducing the risk of unauthorized access to sensitive areas within the organization.
Convenience: Employees can clock in and out quickly and conveniently, without the hassle of remembering passwords or carrying physical cards.
Tektronix Technologies: A Pioneer in Biometric & Time Attendance Systems
Tektronix Technologies has established itself as a trusted name in the field of biometric and time attendance systems in Dubai and Abu Dhabi. Here's why they are a preferred choice:
Cutting-Edge Technology: Tektronix Technologies stays at the forefront of technological advancements. Their systems utilize the latest biometric recognition methods, ensuring the highest level of accuracy and security.
Customized Solutions: They offer tailored solutions that fit the unique needs of each business, whether it's a small startup or a large enterprise.
User-Friendly Interfaces: Tektronix Technologies designs user-friendly interfaces that are easy to use for both employees and administrators.
Scalability: Their systems are scalable, meaning they can grow with your business, accommodating additional employees and locations.
Local Support: With a strong presence in Dubai and Abu Dhabi, Tektronix Technologies provides local support and maintenance, ensuring that your system runs smoothly at all times.
In a competitive business environment like Dubai and Abu Dhabi, efficient time and attendance management is critical for success. Tektronix Technologies offers cutting-edge biometric and time attendance systems that not only streamline attendance tracking but also enhance security and accuracy. Investing in these advanced systems is a strategic move that can lead to significant cost savings, improved productivity, and greater peace of mind for business owners and managers. With Tektronix Technologies, businesses in these dynamic cities are empowered to manage their workforce efficiently and effectively, paving the way for growth and success in the modern business landscape.
time attendance system dubai
time attendance system abu dhabi
biometric access control system
biometric access control system dubai
biometric access control system UAE
biometric access control system bur dubai
biometric access control system alain
biometric access control system
time attendance machine
time attendance machine Dubai
time attendance machine Abu Dhabi
time attendance machine uae
#timeattendancesystemabudhabi #timeattendancesystemdubai #timeattendancesystemabudhabi #timeattendancemachineuae #biometricmachinesupplierindubai #biometricmachinesupplierinuae #biometricaccesscontrolsystem #timeattendancemachineuae
#timeattendancesystemsoftware #imeattendancesystemsoftwareuae #timeattendancesystemsoftwaredubai
#timeattendancesystemsoftwareburdubai #fingerprintattendancesystemsoftwareuae
#biometric access control system#biometric access control system dubai#biometric access control system abu dhabi#biometric access control system in uae#biometric access control system in ajman#bio metric access control system in bur dubai#bio metric access control saudi arabia#time attendance system#time attendance system dubai#time attendance system uae#time attendance system abu dhabi#time attendance system in bur dubai#time attendance system in alain#time attendance system bur dubai#time attendance system in ajman#time attendance system sharjah#time attendance system dubai in alain#time attendance machine abu dhabi#time attendance solutions in bur dubai#time attendance machine in uae#time attendance machine in bur dubai#time attendance in bur dubai#time attendance bur dubai#time attendance machine in bur Dubai#biometric attendance machine uae#biometric attendance machine abu dhabi#biometric attendance machine in uae#biometric attendance machine bur dubai#biometric attendance machine in ajman#biometric attendance machine sharjah
0 notes
Text
CONFIDENTIAL LOGISTICS REPORT
DRC, Planning & Evaluation Office, Logistics & Infrastructure Division
Date: [REDACTED]
To: Director [REDACTED]
From: Administrator [REDACTED], Logistics & Infrastructure Division
Subject: Facility Expansion: New Paternity Compound Construction
Executive Summary
This report outlines the ongoing expansion of DRC-operated paternity compounds across several strategic locations nationwide. In response to increasing insemination rates and projected surrogacy demands, we have begun constructing new high-capacity compounds to accommodate more surrogates. These expansions will enable the DRC to streamline the conscription process, optimize surrogacy cycles, and ensure our ability to meet the population sustainability targets outlined for the next fiscal period.
The new compounds focus on enhanced security, specialized medical equipment, and increased surrogacy capacity.
I. Facility Expansion Overview
Strategic Locations and Site Selection
To ensure regional coverage and minimize travel time to detain and inseminated surrogates, the DRC has approved the construction of [REDACTED] new paternity compounds in FEMA Zones 4, 6, 7, and 8. These facilities will be situated in [REDACTED] areas, selected for their proximity to population centers, existing transport infrastructure, and relative isolation, ensuring operational security.
Zone 4: Atlanta, GA
Zone 6: Houston, TX
Zone 7: Omaha, NE
Zone 8: Denver, CO
Each compound is designed to accommodate [REDACTED] surrogates at any given time, with the ability to scale up to [REDACTED] in emergencies. Construction is scheduled for completion within the next [REDACTED] months, with the first inspections set to begin by [REDACTED] this year.
Paternity Compound Design Features:
High-Capacity Paternity Wards: Each compound contains specialized wards designed to manage surrogates carrying up to sedecatuplets (16), with private rooms for those at risk of premature labor.
Enhanced Monitoring Systems: Advanced surveillance and biometric monitoring ensure constant oversight and swift response to emergencies.
Security Enhancements: Reinforced containment protocols, secure access points, and patrol routes have been established to prevent unauthorized access and ensure surrogate compliance.
II. Specialized Equipment and Medical Support
Given the unique demands and expectations placed on surrogates, each paternity compound will be equipped with advanced medical infrastructure to ensure the safety and effective management of extreme weight gain, reduced mobility, and increased risks of organ stress.
Key Equipment and Infrastructure:
Reinforced Support Beds: Traditional hospital beds have proven insufficient for surrogates carrying high multiples, whose pregnancies can lead to total weight gains exceeding 200 lbs. Each ward will feature reinforced, adjustable support beds capable of accommodating extreme weights. These beds will be equipped with pressure-relief systems to minimize discomfort and reduce the risk of bedsores for near-immobile surrogates.
“I hate that I’m here! But… all I have is this bed! I can’t move, I can’t breathe half the time, but at least I have a fucking memory foam mattress!” - Surrogate S118-176-J, 27 days pregnant with decatuplets (10)
Automated Feeding & Hydration Systems: Automated systems will ensure continuous nutrition and hydration to support surrogates with reduced mobility. Given the caloric intake requirements for such pregnancies, these systems will monitor and adjust fluid and nutrient delivery, reducing the need for frequent staff intervention.
“I’m basically just a machine now, aren’t I? They hook me up, pump me full of these stupid protein shakes, and keep me breathing so I can keep carrying these bowling ball-sized kids. It’s disgusting!” - Surrogate S117-138-N, 18 days pregnant with quattuordecatuplets (14)
Custom Mobility Aids: Custom-designed lift systems and mobility aids will be integrated into each ward to facilitate the movement of surrogates. These devices will allow for safe repositioning, transfers to specialized birthing chairs, and support during transport.
“I don’t know how they expect us to move with this much weight on us. Even standing feels like my legs are going to snap. Those lifts? They’re humiliating... but without them, I wouldn’t be able to get out of bed at all.” - Surrogate S120-494-P, 30 days into a sedecatuplets (16) pregnancy
Advanced Fetal Monitoring: Each compound will have real-time ultrasound and biometric monitoring stations to track fetal development. Given the accelerated gestational period, these systems will continuously update fetal positioning, size, and viability, enabling rapid response to complications.
"It’s terrifying. Knowing how big they are, how many there are… they’re not coming out normal. When I finally pop them all out, they’ll get better care than I ever did!" - Surrogate S119-667-N, 22 days pregnant with hendecatuplets (14)
Dedicated Obstetrics & Neonatal Care Units: Immediate neonatal care is essential, and each compound will include state-of-the-art neonatal intensive care units (NICUs) to support newborns. Advanced incubators and respiratory support systems will ensure the survival of even the most premature babies.
"They always tell me how important it is to ensure the babies survive, even if I don’t. I get it, I do… but knowing there’s a whole team of people ready to take over the second I’m gone? It’s like they’ve already decided how this ends." - Surrogate S117-856-M, 8 days pregnant with tridecatuplets (13)
Pain Management and Sedation Systems: Surrogates will experience extreme discomfort and physical strain. Each paternity ward will be equipped with integrated IV pain management systems, allowing for both localized and systemic pain relief. Sedation protocols can be initiated remotely if a surrogate's distress becomes vocal, ensuring they can not incite civil disorder.
“I’m so big I can’t even see my dick, which is now buried under all these babies and fat. I’d be lying if I said the meds didn't help to blitz me out of my mind... a caring them I'm a gigantic incubator now.” - Surrogate S119-461-L, 11 days pregnant with dodecatuplets (12)
Future Equipment Developments: Research teams are exploring next-generation mobility aids, including exoskeleton support harnesses, to provide mobility assistance for late-term surrogates. These innovations aim to improve surrogate survival to deliver full-term pregnancies. Once available, prototypes will be tested in select compounds.
III. Expansion Strategy: Future Projections and Scaling
Projected Surrogacy Demand: With the increase in insemination rates, each compound is expected to handle up to [REDACTED] inseminations per month once fully operational. This translates to a need for approximately [REDACTED] newborns annually to meet population sustainability targets. Our current projections indicate that these numbers are achievable.
IV. Conclusion and Recommendations
The successful construction and operation of these new paternity compounds are critical to effectively maintaining the DRC’s ability to enforce surrogacy mandates. Our specialized equipment and infrastructure improvements will ensure we meet demands while preserving control over our surrogate.
Report submitted by: Administrator [REDACTED], Logistics & Infrastructure Division
----------------
Sending...
Sending...
Sending...
Read...
----------------
To: Administrator [REDACTED], Logistics & Infrastructure Division
From: Director [REDACTED], DRC
Subject: RE: Facility Expansion: New Paternity Compound Construction
Dear Mr. [REDACTED],
I’ve reviewed the latest progress report on the new Paternity Compounds, and I must commend your team on the impressive strides made thus far, even with the ambitious timeline we’ve set.
I have been particularly interested in the improvements to our birthing suites. As you are well aware, managing multiple pregnancies presents unique challenges.
We are entering a critical phase. I want to emphasize that these upcoming births will set a precedent for all future operations. The successful use of these new facilities will allow us to demonstrate that our methods ensure the next generation's survival and that we can handle the demands without sacrificing efficiency or outcomes.
I look forward to seeing the first results when the initial surrogates reach full term and the birthing suites are fully operational.
Keep up the excellent work, and do not hesitate to reach out if additional resources or support are needed to ensure success.
Regards, Director [REDACTED]
----------------
Click Here to return to DRC Report Archives

#ai mpreg#male pregnancy#mpreg#mpreg kink#mpreg belly#pregnant man#mpreg morph#mpreg caption#mpregbelly#mpregstory#mpreg birth#mpreg art#mpreg story#mpregnancy#mpreg roleplay#male pregnant#caucasianmpreg
213 notes
·
View notes
Note
So recently I got back into PnF and have been marathoning it (to catch up for the revival), and I finally rewatched at2d again. I have no idea if anyone else has talked about it, but how did Perry create the necklace key, the homing device inside it that led to his lair, as well as that replication machine that replicated all of Phin's and Ferb's inventions?
Like, if Perry really is monitored nearly at all times, how was this possible? How did he get the technology? When could he have even gotten it installed? Could it be possible that maybe he got insider help from someone in OWCA (Carl maybe?) or... Just maybe... Perry could have gotten help from Heinz? The amnesia-inator is a thing after all, so he could have mind wiped whoever helped him just to ensure that no one knew about all of this. (Because clearly if Monogram knew about it, he'd instantly have it all shut down and potentially relocate Perry immediately if not jail him like other rogue agents).
Anyway, I hope you don't mind me dropping this on you! I was just curious to see what others might think!
Nonnie, I do not mind at ALL, and i always love love love listening about AT2D and lore theories.
Dwampy is a fan of handwaving lore implications in the show.
HOWEVER. The replication machine WAS mentioned, i think, at the beginning of the movie. The analyser is in Perry's (and likely every other active field agent's) hats. Monogram says they use it to replicate and reverse engineer evil inventions, both for their own use (see the re-modded "Amnesia-Inator"), and also analyse if any of Doof's inventions get smarter ("jury's still out").
But consider; being able to FIT a 3D analyser that works with such terrifying efficiency in a collapsible fedora implies that invention is small, durable and practically unnoticeable. So theoretically? If Perry could get his hand on the analyser, he DOESN'T have to be in the backyard. At the end of every work day he STILL gets to see whatever it was the boys worked on, and keep those plans in a personal archive (probably the same archive he uses to store the edited BFF photos with Doof and the AT2D photos with the boys) for what if situations.
The replication machine is probably accessible to ANY agent with the right kind of security clearance. As we know, from "Where's Perry," and "OWCA files" Perry's security clearance is PRETTY GODDAMN HIGH, since his biometrics are the only ones registered as a backup to un-initiate Doomsday lockdown protocols. He's probably what we call a gold access card for Danville's OWCA division: what Perry wants in his lair, he gets.
He doesn't have to be at home to see what the boys get up to in the backyard. The Flynn-Fletcher house is DROWNING in OWCA cameras and speakers. A security measure both for family's safety, as well as a precautionary measure against Phineas and Ferb's evil potential. Like we KNOW the genius scares OWCA, low key. (See Carl Undercover). I know the movie wants you to think Perry's secretly there all the time for sentimental reason, but like. Yeah that doesnt make logistical sense.
So yeah, Perry can't logically be there all the time for every invention what with how they work him to the bone, but he DOES see every adventure, collect every invention, and he DOES have access to OWCA's replication machine.
The homing device as a spare key to the lair AND the secret data archive is exactly what Phineas says it is: a blatant show of trust. It is absolutely impossible to think of it as anything other than Perry having SPECIFICALLY anticipated an emergency scenario where he CAN'T be there for the boys, one way or another, because of OWCA or some other evil thing. At this point, Perry's been hunted, captured, relocated and almost KILLED both by OWCA and other villains. His worst nightmare is of his family taken hostage. After the events of Carl Undercover he knows he can't trust his employers, not completely. And while he loves and trusts Heinz to not endanger the boys so long as he is kept oblivious to some CRUCIAL information, that's still too high of a risk.
That key, and everything the boys see, was Perry saying, "I do. I trust you. I was there in spirit for every adventure you've ever been on, and no matter what, I have your back. I TRUST that you have mine. I TRUST that you know the right thing."
And to make that key the locket on his collar, with a picture of his boys? It's saying "I trust you because you mean as much to me as I do to you. I trust you because you are family."
Nonnie, I'm sure you don't need me to tell you how absolutely HUGE that is. Perry has very valid abandonment and control issues, and he is NOT easily impressed. I choke up, watching that scene. I still do.
TLDR; there IS a rational explanation to the replication machine that is Perry-going-behind-OWCA's-back related, and sadly not Perryshmirtz related. Honestly using the amnesia machine is possible but probably not too well thought out, which would be uncharacteristic. Perry loves and trusts his boys a LOT, and also hes an overthinker. Valid. What's new?
#perry the platypus#phineas and ferb#Phineas flynn#Ferb Fletcher#At2d#Across the Second dimension#fuck i love this movie so much#THANKS FOR THE DISTRACTION NONNIE#choice of asks#choice of meta#pnf
46 notes
·
View notes
Text
Scan the online brochures of companies who sell workplace monitoring tech and you’d think the average American worker was a renegade poised to take their employer down at the next opportunity. “Nearly half of US employees admit to time theft!” “Biometric readers for enhanced accuracy!” “Offer staff benefits in a controlled way with Vending Machine Access!”
A new wave of return-to-office mandates has arrived since the New Year, including at JP Morgan Chase, leading advertising agency WPP, and Amazon—not to mention President Trump’s late January directive to the heads of federal agencies to “terminate remote work arrangements and require employees to return to work in-person … on a full-time basis.” Five years on from the pandemic, when the world showed how effectively many roles could be performed remotely or flexibly, what’s caused the sudden change of heart?
“There’s two things happening,” says global industry analyst Josh Bersin, who is based in California. “The economy is actually slowing down, so companies are hiring less. So there is a trend toward productivity in general, and then AI has forced virtually every company to reallocate resources toward AI projects.
“The expectation amongst CEOs is that’s going to eliminate a lot of jobs. A lot of these back-to-work mandates are due to frustration that both of those initiatives are hard to measure or hard to do when we don’t know what people are doing at home.”
The question is, what exactly are we returning to?
Take any consumer tech buzzword of the 21st century and chances are it’s already being widely used across the US to monitor time, attendance and, in some cases, the productivity of workers, in sectors such as manufacturing, retail, and fast food chains: RFID badges, GPS time clock apps, NFC apps, QR code clocking-in, Apple Watch badges, and palm, face, eye, voice, and finger scanners. Biometric scanners have long been sold to companies as a way to avoid hourly workers “buddy punching” for each other at the start and end of shifts—so-called “time theft.” A return-to-office mandate and its enforcement opens the door for similar scenarios for salaried staff.
Track and Trace
The latest, deluxe end point of these time and attendance tchotchkes and apps is something like Austin-headquartered HID’s OmniKey platform. Designed for factories, hospitals, universities and offices, this is essentially an all-encompassing RFID log-in and security system for employees, via smart cards, smartphone wallets, and wearables. These will not only monitor turnstile entrances, exits, and floor access by way of elevators but also parking, the use of meeting rooms, the cafeteria, printers, lockers, and yes, vending machine access.
These technologies, and more sophisticated worker location- and behavior-tracking systems, are expanding from blue-collar jobs to pink-collar industries and even white-collar office settings. Depending on the survey, approximately 70 to 80 percent of large US employers now use some form of employee monitoring, and the likes of PwC have explicitly told workers that managers will be tracking their location to enforce a three-day office week policy.
“Several of these earlier technologies, like RFID sensors and low-tech barcode scanners, have been used in manufacturing, in warehouses, or in other settings for some time,” says Wolfie Christl, a researcher of workplace surveillance for Cracked Labs, a nonprofit based in Vienna, Austria. “We’re moving toward the use of all kinds of sensor data, and this kind of technology is certainly now moving into the offices. However, I think for many of these, it’s questionable whether they really make sense there.”
What’s new, at least to the recent pandemic age of hybrid working, is the extent to which workers can now be tracked inside office buildings. Cracked Labs published a frankly terrifying 25-page case study report in November 2024 showing how systems of wireless networking, motion sensors, and Bluetooth beacons, whether intentionally or as a byproduct of their capabilities, can provide “behavioral monitoring and profiling” in office settings.
The project breaks the tech down into two categories: The first is technology that tracks desk presence and room occupancy, and the second monitors the indoor location, movement, and behavior of the people working inside the building.
To start with desk and room occupancy, Spacewell offers a mix of motion sensors installed under desks, in ceilings, and at doorways in “office spaces” and heat sensors and low-resolution visual sensors to show which desks and rooms are being used. Both real-time and trend data are available to managers via its “live data floorplan,” and the sensors also capture temperature, environmental, light intensity, and humidity data.
The Swiss-headquartered Locatee, meanwhile, uses existing badge and device data via Wi-Fi and LAN to continuously monitor clocking in and clocking out, time spent by workers at desks and on specific floors, and the number of hours and days spent by employees at the office per week. While the software displays aggregate rather than individual personal employee data to company executives, the Cracked Labs report points out that Locatee offers a segmented team analytics report which “reveals data on small groups.”
As more companies return to the office, the interest in this idea of “optimized” working spaces is growing fast. According to S&S Insider’s early 2025 analysis, the connected office was worth $43 billion in 2023 and will grow to $122.5 billion by 2032. Alongside this, IndustryARC predicts there will be a $4.5 billion employee-monitoring-technology market, mostly in North America, by 2026—the only issue being that the crossover between the two is blurry at best.
At the end of January, Logitech showed off its millimeter-wave radar Spot sensors, which are designed to allow employers to monitor whether rooms are being used and which rooms in the building are used the most. A Logitech rep told The Verge that the peel-and-stick devices, which also monitor VOCs, temperature, and humidity, could theoretically estimate the general placement of people in a meeting room.
As Christl explains, because of the functionality that these types of sensor-based systems offer, there is the very real possibility of a creep from legitimate applications, such as managing energy use, worker health and safety, and ensuring sufficient office resources into more intrusive purposes.
“For me, the main issue is that if companies use highly sensitive data like tracking the location of employees’ devices and smartphones indoors or even use motion detectors indoors,” he says, “then there must be totally reliable safeguards that this data is not being used for any other purposes.”
Big Brother Is Watching
This warning becomes even more pressing where workers’ indoor location, movement, and behavior are concerned. Cisco’s Spaces cloud platform has digitized 11 billion square feet of enterprise locations, producing 24.7 trillion location data points. The Spaces system is used by more than 8,800 businesses worldwide and is deployed by the likes of InterContinental Hotels Group, WeWork, the NHS Foundation, and San Jose State University, according to Cisco’s website.
While it has applications for retailers, restaurants, hotels, and event venues, many of its features are designed to function in office environments, including meeting room management and occupancy monitoring. Spaces is designed as a comprehensive, all-seeing eye into how employees (and customers and visitors, depending on the setting) and their connected devices, equipment, or “assets” move through physical spaces.
Cisco has achieved this by using its existing wireless infrastructure and combining data from Wi-Fi access points with Bluetooth tracking. Spaces offers employers both real-time views and historical data dashboards. The use cases? Everything from meeting-room scheduling and optimizing cleaning schedules to more invasive dashboards on employees’ entry and exit times, the duration of staff workdays, visit durations by floor, and other “behavior metrics.” This includes those related to performance, a feature pitched at manufacturing sites.
Some of these analytics use aggregate data, but Cracked Labs details how Spaces goes beyond this into personal data, with device usernames and identifiers that make it possible to single out individuals. While the ability to protect privacy by using MAC randomization is there, Cisco emphasizes that this makes indoor movement analytics “unreliable” and other applications impossible—leaving companies to make that decision themselves.
Management even has the ability to send employees nudge-style alerts based on their location in the building. An IBM application, based on Cisco’s underlying technology, offers to spot anomalies in occupancy patterns and send notifications to workers or their managers based on what it finds. Cisco’s Spaces can also incorporate video footage from Cisco security cameras and WebEx video conferencing hardware into the overall system of indoor movement monitoring; another example of function creep from security to employee tracking in the workplace.
“Cisco is simply everywhere. As soon as employers start to repurpose data that is being collected from networking or IT infrastructure, this quickly becomes very dangerous, from my perspective.” says Christl. “With this kind of indoor location tracking technology based on its Wi-Fi networks, I think that a vendor as major as Cisco has a responsibility to ensure it doesn’t suggest or market solutions that are really irresponsible to employers.
“I would consider any productivity and performance tracking very problematic when based on this kind of intrusive behavioral data.” WIRED approached Cisco for comment but didn’t receive a response before publication.
Cisco isn't alone in this, though. Similar to Spaces, Juniper’s Mist offers an indoor tracking system that uses both Wi-Fi networks and Bluetooth beacons to locate people, connected devices, and Bluetooth tagged badges on a real-time map, with the option of up to 13 months of historical data on worker behavior.
Juniper’s offering, for workplaces including offices, hospitals, manufacturing sites, and retailers, is so precise that it is able to provide records of employees’ device names, together with the exact enter and exit times and duration of visits between “zones” in offices—including one labeled “break area/kitchen” in a demo. Yikes.
For each of these systems, a range of different applications is functionally possible, and some which raise labor-law concerns. “A worst-case scenario would be that management wants to fire someone and then starts looking into historical records trying to find some misconduct,” says Christl. "If it’s necessary to investigate employees, then there should be a procedure where, for example, a worker representative is looking into the fine-grained behavioral data together with management. This would be another safeguard to prevent misuse.”
Above and Beyond?
If warehouse-style tracking has the potential for management overkill in office settings, it makes even less sense in service and health care jobs, and American unions are now pushing for more access to data and quotas used in disciplinary action. Elizabeth Anderson, professor of public philosophy at the University of Michigan and the author of Private Government: How Employers Rule Our Lives, describes how black-box algorithm-driven management and monitoring affects not just the day-to-day of nursing staff but also their sense of work and value.
“Surveillance and this idea of time theft, it’s all connected to this idea of wasting time,” she explains. “Essentially all relational work is considered inefficient. In a memory care unit, for example, the system will say how long to give a patient breakfast, how many minutes to get them dressed, and so forth.
“Maybe an Alzheimer’s patient is frightened, so a nurse has to spend some time calming them down, or perhaps they have lost some ability overnight. That’s not one of the discrete physical tasks that can be measured. Most of the job is helping that person cope with declining faculties; it takes time for that, for people to read your emotions and respond appropriately. What you get is massive moral injury with this notion of efficiency.”
This kind of monitoring extends to service workers, including servers in restaurants and cleaning staff, according to a 2023 Cracked Labs’ report into retail and hospitality. Software developed by Oracle is used to, among other applications, rate and rank servers based on speed, sales, timekeeping around breaks, and how many tips they receive. Similar Oracle software that monitors mobile workers such as housekeepers and cleaners in hotels uses a timer for app-based micromanagement—for instance, “you have two minutes for this room, and there are four tasks.”
As Christl explains, this simply doesn’t work in practice. “People have to struggle to combine what they really do with this kind of rigid, digital system. And it’s not easy to standardize work like talking to patients and other kinds of affective work, like how friendly you are as a waiter. This is a major problem. These systems cannot represent the work that is being done accurately.”
But can knowledge work done in offices ever be effectively measured and assessed either? In an episode of his podcast in January, host Ezra Klein battled his own feelings about having many of his best creative ideas at a café down the street from where he lives rather than in The New York Times’ Manhattan offices. Anderson agrees that creativity often has to find its own path.
“Say there’s a webcam tracking your eyes to make sure you’re looking at the screen,” she says. “We know that daydreaming a little can actually help people come up with creative ideas. Just letting your mind wander is incredibly useful for productivity overall, but that requires some time looking around or out the window. The software connected to your camera is saying you’re off-duty—that you’re wasting time. Nobody’s mind can keep concentrated for the whole work day, but you don’t even want that from a productivity point of view.”
Even for roles where it might make more methodological sense to track discrete physical tasks, there can be negative consequences of nonstop monitoring. Anderson points to a scene in Erik Gandini’s 2023 documentary After Work that shows an Amazon delivery driver who is monitored, via camera, for their driving, delivery quotas, and even getting dinged for using Spotify in the van.
“It’s very tightly regulated and super, super intrusive, and it’s all based on distrust as the starting point,” she says. “What these tech bros don’t understand is that if you install surveillance technology, which is all about distrusting the workers, there is a deep feature of human psychology that is reciprocity. If you don’t trust me, I’m not going to trust you. You think an employee who doesn’t trust the boss is going to be working with the same enthusiasm? I don’t think so.”
Trust Issues
The fixes, then, might be in the leadership itself, not more data dashboards. “Our research shows that excessive monitoring in the workplace can damage trust, have a negative impact on morale, and cause stress and anxiety,” says Hayfa Mohdzaini, senior policy and practice adviser for technology at the CIPD, the UK’s professional body for HR, learning, and development. “Employers might achieve better productivity by investing in line manager training and ensuring employees feel supported with reasonable expectations around office attendance and manageable workloads.”
A 2023 Pew Research study found that 56 percent of US workers were opposed to the use of AI to keep track of when employees were at their desks, and 61 percent were against tracking employees’ movements while they work.
This dropped to just 51 percent of workers who were opposed to recording work done on company computers, through the use of a kind of corporate “spyware” often accepted by staff in the private sector. As Josh Bersin puts it, “Yes, the company can read your emails” with platforms such as Teramind, even including “sentiment analysis” of employee messages.
Snooping on files, emails, and digital chats takes on new significance when it comes to government workers, though. New reporting from WIRED, based on conversations with employees at 13 federal agencies, reveals the extent to Elon Musk’s DOGE team’s surveillance: software including Google’s Gemini AI chatbot, a Dynatrace extension, and security tool Splunk have been added to government computers in recent weeks, and some people have felt they can’t speak freely on recorded and transcribed Microsoft Teams calls. Various agencies already use Everfox software and Dtex’s Intercept system, which generates individual risk scores for workers based on websites and files accessed.
Alongside mass layoffs and furloughs over the past four weeks, the so-called Department of Government Efficiency has also, according to CBS News and NPR reports, gone into multiple agencies in February with the theater and bombast of full X-ray security screenings replacing entry badges at Washington, DC, headquarters. That’s alongside managers telling staff that their logging in and out of devices, swiping in and out of workspaces, and all of their digital work chats will be “closely monitored” going forward.
“Maybe they’re trying to make a big deal out of it to scare people right now,” says Bersin. “The federal government is using back-to-work as an excuse to lay off a bunch of people.”
DOGE staff have reportedly even added keylogger software to government computers to track everything employees type, with staff concerned that anyone using keywords related to progressive thinking or "disloyalty” to Trump could be targeted—not to mention the security risks it introduces for those working on sensitive projects. As one worker told NPR, it feels “Soviet-style” and “Orwellian” with “nonstop monitoring.” Anderson describes the overall DOGE playbook as a series of “deeply intrusive invasions of privacy.”
Alternate Realities
But what protections are out there for employees? Certain states, such as New York and Illinois, do offer strong privacy protections against, for example, unnecessary biometric tracking in the private sector, and California’s Consumer Privacy Act covers workers as well as consumers. Overall, though, the lack of federal-level labor law in this area makes the US something of an alternate reality to what is legal in the UK and Europe.
The Electronic Communications Privacy Act in the US allows employee monitoring for legitimate business reasons and with the worker’s consent. In Europe, Algorithm Watch has made country analyses for workplace surveillance in the UK, Italy, Sweden, and Poland. To take one high-profile example of the stark difference: In early 2024, Serco was ordered by the UK's privacy watchdog, the Information Commissioner’s Office (ICO), to stop using face recognition and fingerprint scanning systems, designed by Shopworks, to track the time and attendance of 2,000 staff across 38 leisure centers around the country. This new guidance led to more companies reviewing or cutting the technology altogether, including Virgin Active, which pulled similar biometric employee monitoring systems from 30-plus sites.
Despite a lack of comprehensive privacy rights in the US, though, worker protest, union organizing, and media coverage can provide a firewall against some office surveillance schemes. Unions such as the Service Employees International Union are pushing for laws to protect workers from black-box algorithms dictating the pace of output.
In December, Boeing scrapped a pilot of employee monitoring at offices in Missouri and Washington, which was based on a system of infrared motion sensors and VuSensor cameras installed in ceilings, made by Ohio-based Avuity. The U-turn came after a Boeing employee leaked an internal PowerPoint presentation on the occupancy- and headcount-tracking technology to The Seattle Times. In a matter of weeks, Boeing confirmed that managers would remove all the sensors that had been installed to date.
Under-desk sensors, in particular, have received high-profile backlash, perhaps because they are such an obvious piece of surveillance hardware rather than simply software designed to record work done on company machines. In the fall of 2022, students at Northeastern University hacked and removed under-desk sensors produced by EnOcean, offering “presence detection” and “people counting,” that had been installed in the school’s Interdisciplinary Science & Engineering Complex. The university provost eventually informed students that the department had planned to use the sensors with the Spaceti platform to optimize desk usage.
OccupEye (now owned by FM: Systems), another type of under-desk heat and motion sensor, received a similar reaction from staff at Barclays Bank and The Telegraph newspaper in London, with employees protesting and, in some cases, physically removing the devices that tracked the time they spent away from their desks.
Despite the fallout, Barclays later faced a $1.1 billion fine from the ICO when it was found to have deployed Sapience’s employee monitoring software in its offices, with the ability to single out and track individual employees. Perhaps unsurprisingly in the current climate, that same software company now offers “lightweight device-level technology” to monitor return-to-office policy compliance, with a dashboard breaking employee location down by office versus remote for specific departments and teams.
According to Elizabeth Anderson’s latest book Hijacked, while workplace surveillance culture and the obsession with measuring employee efficiency might feel relatively new, it can actually be traced back to the invention of the “work ethic” by the Puritans in the 16th and 17th centuries.
“They thought you should be working super hard; you shouldn’t be idling around when you should be in work,” she says. “You can see some elements there that can be developed into a pretty hostile stance toward workers. The Puritans were obsessed with not wasting time. It was about gaining assurance of salvation through your behavior. With the Industrial Revolution, the ‘no wasting time’ became a profit-maximizing strategy. Now you’re at work 24/7 because they can get you on email.”
Some key components of the original work ethic, though, have been skewed or lost over time. The Puritans also had strict constraints on what duties employers had toward their workers: paying a living wage and providing safe and healthy working conditions.
“You couldn’t just rule them tyrannically, or so they said. You had to treat them as your fellow Christians, with dignity and respect. In many ways the original work ethic was an ethic which uplifted workers.”
6 notes
·
View notes
Text

"The Price of Remembering"
HexguardHeart
Chapter 8: Perfect Sync
They met again days later to process everything that had been unfolding.
The Memory Den's makeshift war room was a chaos of holograms and possibility. Vi sat cross-legged on the old ring's canvas, while Caitlyn paced between floating screens of security protocols and building schematics.
"The authentication override requires board-level access," Caitlyn muttered, manipulating data with practiced grace. "But the secondary systems..."
"Run on a separate network," Vi finished, making Caitlyn turn. "Underground cables. Old tech. Harder to hack but-"
"Also harder to monitor." Caitlyn's eyes lit up. "How did you know that?"
"Found the blueprints when we..." Vi frowned, implant buzzing. "Viktor, when did we find those?"
"Last month's server raid," he supplied from his workbench. "The one where you stopped to help that kid and nearly got us caught because you couldn't resist punching that vending machine for him."
"Hey, that thing ate his lunch money!" Vi protested with a grin. "Besides, it was a very therapeutic punch."
Caitlyn moved closer, sitting on the canvas beside her. "The authentication protocols are designed to flag any unusual memory patterns during extraction. But." She pulled up new data. "If we introduced a specific type of feedback loop..."
"It would look like routine maintenance." Vi leaned in, their shoulders brushing. "And if we time it with the weekly system purge..."
"Every memory seller could keep a copy without setting off alerts." Caitlyn turned, finding Vi's face inches from hers. "How do you understand these systems so well?"
"I don't. Not really. But I understand people. How they think. How they hide things." Vi tapped her implant. "When you can't trust your memory, you learn to read everything else."
Their eyes held. Something electric passed between them.
"Here." Caitlyn pulled up the central processing hub's layout. "This is where they store the enhancement protocols. But the security..."
"Is focused on the main entrance." Vi pointed to a maintenance shaft. "They never watch the small things. Too busy guarding the front door to check the windows."
"And I have access to the quarterly maintenance schedule." Caitlyn's fingers danced through data. "We could..."
"Slip in during shift change." Vi nodded. "When the day crew's tired and the night crew's not fully alert."
They worked like this for hours, finishing each other's thoughts, seeing patterns the other missed. Vi knew the streets, the blind spots, the human weaknesses. Caitlyn knew the corporate architecture, the digital vulnerabilities, the procedural gaps.
"It's perfect," Ekko admitted finally, watching them work. "The princess knows exactly how they think they're protected, and Vi knows exactly how they're not. It's like watching a cop show where the cop and the criminal finish each other's-"
"Sentences?" Vi and Caitlyn said simultaneously.
"See? That's exactly what I mean!" Ekko laughed. "You two are like an old married couple, except one's a cop and the other keeps forgetting where she put her keys."
"Very funny, time boy," Vi rolled her eyes, but smiled. "At least I remember where I put my sense of humor."
Caitlyn looked up from a particularly complex security schematic. "There's just one problem. The final override needs physical authentication. Biometric. From a board member."
"Your mother," Vi said.
"My mother." Caitlyn's jaw tightened. "Who will definitely notice if I try to access her credentials."
Vi stood, offering Caitlyn her hand. "Then we don't access them. We make her give them to us."
Caitlyn took her hand, letting Vi pull her up. They stood close, energy humming between them.
"How?"
"By showing her exactly what she's afraid of losing." Vi's smile was sharp. "Her reputation. Her legacy. Her perfect daughter."
"You want me to threaten my own mother with exposure?"
"No." Vi touched Caitlyn's cheek, gentle despite her fading memories. "I want you to offer her a choice. The same choice she never gave any of us."
Caitlyn leaned into the touch. "The data crystal. The evidence."
"All of it. Released to every news outlet, every regulatory board, every competitor."
"Unless?"
"Unless she helps us make it right."
Their faces were very close now, plans and possibilities spinning around them in glowing light.
"It could work but she’ll hate me," Caitlyn whispered.
"It will work." Vi's voice was certain. "Because you'll remember the plan even when I can't. And I'll remember why it matters even when you doubt."
Caitlyn's hand found Vi's face, mirroring her touch. "How do you do that?"
"Do what?"
"Trust so completely? Even knowing you'll forget?"
Vi smiled, soft and real. "Some things you don't need to remember to know. Like how terrible Ekko's jokes are, or how Viktor secretly names all his machines."
"I do not!" Viktor protested from his corner.
"Really? So that's not Margaret the Memory Scanner over there?" Vi teased, making Caitlyn laugh despite the tension.
#caitvi fanfiction#arcane#caitvi#lovestory#arcane fanfiction#caitlyn kiramman#heatedfanfiction#caitlyn arcane#heat#fanfiction
4 notes
·
View notes
Text
🛡️ Cybersecurity and Fraud Prevention in Finance: How to Protect Your Financial Systems in 2025
In today’s digital-first financial world, cybersecurity and fraud prevention in finance are more critical than ever. With the rise of online banking, mobile payments, and digital assets, financial institutions face increasingly sophisticated cyber threats and fraud tactics.

🔍 Why Cybersecurity Is Crucial in the Finance Industry
The financial sector is one of the most targeted industries by cybercriminals due to its vast access to sensitive personal data and high-value transactions. From phishing and ransomware to account takeover and insider threats, the risk landscape continues to evolve.
Google Keyword: financial cyber threats
💣 The Cost of Poor Financial Cybersecurity
Average cost of a financial data breach: $5.9 million
70% of consumers will switch banks or services after a breach
Identity theft and digital fraud rates are up 34% YoY
Trending Search Term: banking data breaches 2025
✅ Top Strategies for Cybersecurity and Fraud Prevention in Finance
1. Adopt Multi-Layered Security Protocols
Layered security (also called “defense in depth”) uses a combination of firewalls, encryption, anti-virus software, and secure authentication to prevent unauthorized access.
Related Term: secure financial transactions
2. Leverage AI and Machine Learning for Fraud Detection
Artificial intelligence plays a key role in identifying unusual patterns and suspicious behavior in real-time. AI-powered fraud detection systems can:
Flag fraudulent transactions instantly
Analyze thousands of data points in seconds
Continuously learn and adapt to new fraud tactics
Keyword: AI in cybersecurity
3. Implement Real-Time Transaction Monitoring
Real-time monitoring tools allow institutions to track and respond to threats instantly, reducing loss and minimizing damage.
Search Intent: fraud detection systems for financial services
4. Enhance Customer Authentication Protocols
Using multi-factor authentication (MFA), biometric verification, and one-time passwords (OTPs) helps protect accounts from unauthorized access.
Search Trigger: how to protect financial data from hackers
5. Train Employees and Clients on Cyber Hygiene
Human error remains one of the top causes of breaches. Train staff and customers on:
Recognizing phishing scams
Using secure passwords
Avoiding suspicious links and public Wi-Fi
Keyword Phrase: digital financial fraud prevention tips
🔐 Top Tools and Technologies for Financial Cybersecurity in 2025
Darktrace & Vectra AI: Behavioral threat detection
Splunk & IBM QRadar: Security Information and Event Management (SIEM)
Okta & Duo: Identity and access management
ThreatMetrix: Real-time fraud analytics
📉 Common Types of Financial Cyber Threats
Phishing Attacks
Credential Stuffing
Account Takeovers
Ransomware Attacks
Insider Threats
Synthetic Identity Fraud
Search Phrase: types of financial cyber fraud
🧠 Real-World Example
In 2024, a regional credit union prevented over $2 million in fraud losses using AI-based transaction monitoring and customer biometrics. This proactive cybersecurity investment boosted customer confidence and reduced fraud-related downtime by 75%.
🚀 The Future of Cybersecurity in Finance
In 2025 and beyond, expect to see:
Widespread use of zero-trust security models
Enhanced biometric authentication
Increased use of blockchain for transaction verification
AI-powered fraud prevention as the industry standard
Keyword Used: future of cybersecurity in banking
Need Personal Or Business Funding? Prestige Business Financial Services LLC offer over 30 Personal and Business Funding options to include good and bad credit options. Get Personal Loans up to $100K or 0% Business Lines of Credit Up To $250K. Also credit repair and passive income programs.
Book A Free Consult And We Can Help - https://prestigebusinessfinancialservices.com
Email - [email protected]
📌 Final Takeaway
As digital transactions continue to grow, so does the threat landscape. Prioritizing cybersecurity and fraud prevention in finance is no longer optional—it’s essential.
Businesses and institutions that invest in AI-driven security tools, real-time monitoring, and fraud prevention protocols will not only protect their assets but also build long-term customer trust and compliance.
Need Personal Or Business Funding? Prestige Business Financial Services LLC offer over 30 Personal and Business Funding options to include good and bad credit options. Get Personal Loans up to $100K or 0% Business Lines of Credit Up To $250K. Also credit repair and passive income programs.
Book A Free Consult And We Can Help - https://prestigebusinessfinancialservices.com
Email - [email protected]
Learn More!!
Prestige Business Financial Services LLC
"Your One Stop Shop To All Your Personal And Business Funding Needs"
Website- https://prestigebusinessfinancialservices.com
Email - [email protected]
Phone- 1-800-622-0453
#financial cyber threats#banking data breaches 2025#secure financial transactions#AI in cybersecurity#fraud detection systems for financial services#how to protect financial data from hackers
2 notes
·
View notes
Text
How AI & Machine Learning Are Changing UI/UX Design

Artificial Intelligence (AI) and Machine Learning (ML) are revolutionizing UI/UX design by making digital experiences more intelligent, adaptive, and user-centric. From personalized interfaces to automated design processes, AI is reshaping how designers create and enhance user experiences. In this blog, we explore the key ways AI and ML are transforming UI/UX design and what the future holds.
For more UI/UX trends and insights, visit Pixelizes Blog.
AI-Driven Personalization
One of the biggest changes AI has brought to UI/UX design is hyper-personalization. By analyzing user behavior, AI can tailor content, recommendations, and layouts to individual preferences, creating a more engaging experience.
How It Works:
AI analyzes user interactions, including clicks, time spent, and preferences.
Dynamic UI adjustments ensure users see what’s most relevant to them.
Personalized recommendations, like Netflix suggesting shows or e-commerce platforms curating product lists.
Smart Chatbots & Conversational UI
AI-powered chatbots have revolutionized customer interactions by offering real-time, intelligent responses. They enhance UX by providing 24/7 support, answering FAQs, and guiding users seamlessly through applications or websites.
Examples:
Virtual assistants like Siri, Alexa, and Google Assistant.
AI chatbots in banking, e-commerce, and healthcare.
NLP-powered bots that understand user intent and sentiment.
Predictive UX: Anticipating User Needs
Predictive UX leverages ML algorithms to anticipate user actions before they happen, streamlining interactions and reducing friction.
Real-World Applications:
Smart search suggestions (e.g., Google, Amazon, Spotify).
AI-powered auto-fill forms that reduce typing effort.
Anticipatory design like Google Maps estimating destinations.
AI-Powered UI Design Automation
AI is streamlining design workflows by automating repetitive tasks, allowing designers to focus on creativity and innovation.
Key AI-Powered Tools:
Adobe Sensei: Automates image editing, tagging, and design suggestions.
Figma AI Plugins & Sketch: Generate elements based on user input.
UX Writing Assistants that enhance microcopy with NLP.
Voice & Gesture-Based Interactions
With AI advancements, voice and gesture control are becoming standard features in UI/UX design, offering more intuitive, hands-free interactions.
Examples:
Voice commands via Google Assistant, Siri, Alexa.
Gesture-based UI on smart TVs, AR/VR devices.
Facial recognition & biometric authentication for secure logins.
AI in Accessibility & Inclusive Design
AI is making digital products more accessible to users with disabilities by enabling assistive technologies and improving UX for all.
How AI Enhances Accessibility:
Voice-to-text and text-to-speech via Google Accessibility.
Alt-text generation for visually impaired users.
Automated color contrast adjustments for better readability.
Sentiment Analysis for Improved UX
AI-powered sentiment analysis tools track user emotions through feedback, reviews, and interactions, helping designers refine UX strategies.
Uses of Sentiment Analysis:
Detecting frustration points in customer feedback.
Optimizing UI elements based on emotional responses.
Enhancing A/B testing insights with AI-driven analytics.
Future of AI in UI/UX: What’s Next?
As AI and ML continue to evolve, UI/UX design will become more intuitive, adaptive, and human-centric. Future trends include:
AI-generated UI designs with minimal manual input.
Real-time, emotion-based UX adaptations.
Brain-computer interface (BCI) integrations for immersive experiences.
Final Thoughts
AI and ML are not replacing designers—they are empowering them to deliver smarter, faster, and more engaging experiences. As we move into a future dominated by intelligent interfaces, UI/UX designers must embrace AI-powered design methodologies to create more personalized, accessible, and user-friendly digital products.
Explore more at Pixelizes.com for cutting-edge design insights, AI tools, and UX trends.
#AI in UX Design#Machine Learning UX#UX Personalization#Conversational UI#Predictive UX#AI Chatbots#Smart UX Tools#UI Automation#Voice UI Design#Inclusive UX Design#Sentiment Analysis in UX#Future of UX#AI UX Trends 2025#Figma AI Plugins#Accessibility with AI#Adaptive UI Design#UX Innovation#Human-Centered AI#Pixelizes Blog#UX Strategy
2 notes
·
View notes
Text
How Biometric Devices Improve Employee Time Tracking
In an era where organizations strive for efficiency, accuracy, and security, managing employee attendance has evolved from traditional punch cards and manual logbooks to high-tech solutions. Among the most transformative innovations is the biometric device, a software that has revolutionized how companies track and manage employee time.
Whether you're a small business or a large enterprise, ensuring accurate time tracking is essential for payroll, productivity, and workforce management. Biometric devices offer a modern solution by linking attendance to unique human characteristics such as fingerprints, facial recognition, or iris scans - making time fraud and buddy punching things of the past.

What Is a Biometric Device?
A biometric device is a piece of hardware used to identify individuals based on unique biological traits. In the context of workplace management, these devices are typically deployed for access control and attendance tracking. Unlike traditional systems that require ID cards or PINs, biometric systems ensure that only the actual individual can clock in or access a restricted area.
Biometric devices can come in various forms:
Fingerprint scanners
Facial recognition systems
Iris recognition devices
Voice recognition tools
The growing popularity of biometric technology is due to its speed, accuracy, and ease of integration with other HR and payroll systems.
Common Problems with Traditional Time Tracking Methods
Before diving into how biometric devices improve employee time tracking, it’s worth understanding the limitations of traditional systems:
Buddy punching: Employees clock in or out for each other, leading to time theft.
Manual errors: Human oversight when entering or correcting data can lead to payroll discrepancies.
Lost or stolen access cards: These can pose both a security and operational risk.
Lack of real-time data: Delayed updates make it difficult to monitor workforce performance.
These challenges not only impact payroll accuracy but also affect overall productivity and morale.
How Biometric Devices Transform Time Tracking
1. Accuracy and Reliability
Biometric devices are incredibly accurate. Because they rely on individual traits that cannot be duplicated or shared, they offer reliable verification each time an employee clocks in or out. This eliminates common issues like buddy punching or fraudulent time logging.
For instance, a facial recognition-based biometric device ensures that only the authorized individual can record attendance. This means more accurate payroll processing and fewer disputes between HR and employees.
2. Real-Time Attendance Monitoring
Biometric systems provide real-time data on employee attendance. This allows HR departments and team managers to monitor punctuality, break times, and absenteeism more effectively. Cloud-based biometric devices like those offered by Spintly offer real-time syncing across multiple locations, perfect for businesses with distributed teams or multiple branches.
This live data can be accessed through dashboards and reports, offering actionable insights that go beyond mere attendance tracking.
3. Integration with Payroll and HRMS
A modern biometric device does more than log time. Many advanced systems integrate seamlessly with Human Resource Management Systems (HRMS) and payroll software. This eliminates the need for manual data entry, ensuring timely and accurate salary processing, tax compliance, and leave management.
Solutions like Spintly’s biometric access control and attendance management platforms are built with open APIs, making it easy to integrate with third-party software - resulting in a streamlined workflow and reduced administrative burden.
4. Improved Compliance and Audit Trail
Maintaining proper records of working hours is essential to comply with labor laws and industry standards. Biometric devices automatically log every time an employee enters or exits the workplace, providing a secure and tamper-proof audit trail.
This data becomes especially useful during labor audits or legal disputes, ensuring organizations remain compliant without having to dig through manual records.
5. Contactless and Hygienic Options
In the post-pandemic world, hygiene has become a critical consideration in workplace technology. Modern biometric devices now offer touchless options, such as facial recognition and mobile-based check-ins, which minimize physical contact.
Cloud-enabled platforms like Spintly even offer mobile-based biometric attendance solutions, where employees can check in via their smartphones - reducing shared touchpoints while maintaining strict security protocols.
Industry Use Cases
1. Corporate Offices
Biometric time tracking helps monitor in-office attendance while integrating with access control systems to manage entry permissions.
2. Manufacturing & Industrial Units
These devices ensure workers clock in accurately despite working in high-volume shifts, often across different parts of the plant.
3. Healthcare Institutions
Hospitals benefit from biometric tracking to maintain 24/7 shift records and manage attendance in a critical-care environment where staffing is essential.
4. Educational Institutions
Schools and colleges use biometric devices to track faculty and staff attendance while maintaining secure access to restricted areas.
Advantages Over RFID and PIN Systems
While RFID cards and PINs offer basic functionality, they’re prone to misuse and loss. A biometric device offers a level of certainty and convenience that traditional systems can't match. Employees can’t forget or lose their fingerprint or face, making the system more dependable and reducing the cost and hassle of replacements.
Furthermore, combining biometric devices with access control solutions, such as those provided by Spintly, enhances building security. The system ensures that only verified individuals gain access to sensitive areas, creating a safer workplace.
Key Features to Look for in a Biometric Device
If you're considering investing in a biometric time tracking solution, keep the following features in mind:
Cloud connectivity for remote access and real-time syncing
Integration capabilities with HRMS and payroll systems
Touchless operation for post-COVID hygiene standards
Mobile authentication for flexible, remote check-ins
Data encryption to protect biometric data and ensure compliance
Providers like Spintly are paving the way for secure, scalable, and easy-to-deploy biometric solutions that fit businesses of all sizes.
Conclusion
In a digital-first world, managing your workforce with accuracy and efficiency isn’t just about technology - it’s about trust, compliance, and operational excellence. A biometric device simplifies employee time tracking while eliminating common pitfalls like buddy punching, manual errors, and data delays.
By integrating biometric attendance with access control and cloud-based dashboards, organizations get a holistic view of employee movement and performance. Solutions such as Spintly’s smart biometric access platform are leading this transformation by offering sleek, wireless systems that combine convenience with security.
Whether you're looking to tighten security, reduce administrative overhead, or simply improve the employee experience, adopting a biometric solution could be the smartest investment your business makes this year.
#biometric machine#biometric attendance#biometric access#mobile access#attendance management#time and attendance software#accesscontrol#spintly#smartacess#biometrics#smartbuilding#visitor management system#access control solutions
0 notes
Text
ZKTeco Horus E1-FP Time Attendance Machine

ZKTeco Horus E1FP is one of the most advanced Access Control & time and attendance terminals existing in the market, with an incredibly compact size (almost the same size as the iPhone XS max).
Powerful facial recognition technology offering up to 3 meters recognition distance, ±30 degrees pose angle tolerance, high anti-spoof ability, support on plentiful communication protocols (Wi-Fi, 3G, 4G, Bluetooth) and worldwide network setting, optional fingerprint and RFID card modules, up to 10,000 facial templates capacity.
It is compatible with the all-in-one security & time attendance platform ZKBioSecurity and BioTime.
Functions:
• New height of facial recognition template capacity up to 1: N-10,000 facial templates • Anti-spoofing algorithm against print attacks (laser, color, and B / W photos), video attacks, and 3D mask attack • Supports multiple communication protocols: 4G, Wi-Fi, Bluetooth, and USB • 5-inch smartphone-grade IPS touch LCD monitor • Extensive Fingerprint, RFID, and TCP / IP, modules available • Extra-large 2MP CMOS with WDR function • Various further development options: embedded GPS / A-GPS, microphone, and PIR sensor
Costtocost offers the best price for the ZKTeco Horus E1-FP Time Attendance Machine. Buy now with the best price!
#uae#dubai#it solutions#costtocost#electronics#best electronics and it supplier in uae#it support#it support in dubai#business#zk#zkteco#zkteco horus E1FP#Time Attendance Machine#time & attendance system#fingerprint time attendance machine#biometric time attendance#zkteco horus#onlineshopping#dubai shopping#deals#sale#black friday sale#access control systems
0 notes
Text
Thailand Visa Exemptions
Thailand's visa exemption system operates under:
Immigration Act B.E. 2522 (1979)
Ministerial Regulations No. 14 (B.E. 2535)
Bilateral agreements with 64 countries (as of 2024)
The policy is administered by the Thai Immigration Bureau with oversight from the Ministry of Foreign Affairs. Unlike true visa-free entry, exemptions are technically "visas on arrival" granted under Section 12 of the Immigration Act.
2. Current Exemption Scheme Structure (2024)
A. Standard Exemption (Tourism Purpose Only)
Duration: 30 days (land/sea entry) or 30-90 days (air entry)
Nationalities: 64 eligible countries
Entry Points: All international airports, 26 land borders
Key Distinctions:
Air vs. Land Entry:
Air arrivals receive 30 days (57 nationalities) or 90 days (7 nationalities)
Land arrivals strictly limited to 30 days (extendable once)
B. Special Bilateral Agreements
90-Day Exemption: Brazil, Chile, Peru, South Korea
60-Day Exemption: Russia (temporary measure until 2025)
30-Day Exemption: Most ASEAN members (extendable to 90)
3. Technical Entry Requirements
Documentation Standards
Passport Validity:
Minimum 6 months remaining
At least 2 blank pages
Machine-readable or biometric only (no handwritten passports accepted)
Proof of Onward Travel:
Confirmed ticket within exemption period
Airlines may require at check-in (IATA TIM regulation)
Acceptable formats:
Flight itinerary (PNR must verify)
E-ticket with 13-digit ticket number
Bus/train tickets for land border exits
Financial Proof:
Official requirement: 20,000 THB/person (40,000/family)
Enforcement protocol:
Random checks at discretion of Immigration Officer
Cash or traveler's checks only (bank statements not accepted)
New 2024 measure: Credit limit verification for card holders
4. Operational Procedures at Entry Points
A. Airport Processing
Automated Verification:
Advance Passenger Information (API) screening
Interpol database cross-check
Previous immigration history review
Secondary Inspection Triggers:
More than 3 exemptions in 12 months
Previous overstays (even if paid fine)
Suspected "visa run" patterns
B. Land Border Specifics
Daily Quotas:
Poipet (Cambodia): 300/day
Sadao (Malaysia): 500/day
Time Restrictions:
No crossings after 18:00 at most borders
Mandatory 6-hour minimum stay abroad for re-entry
5. Extension Mechanisms
Official Extension Process
Eligibility: One 30-day extension permitted
Requirements:
TM.7 form + 1,900 THB fee
Proof of residence (hotel receipt or lease)
4x6cm photo (specific biometric standards)
Processing Time: 45 minutes to 3 hours (varies by office)
De Facto Alternatives
Border Run Limitations:
Maximum 2 land border exemptions per calendar year
Automated tracking via TM6 departure cards
Visa Conversion Option:
Change to Non-Immigrant visa possible at some offices
Requires showing 200,000 THB in Thai bank account
6. Special Cases and Exceptions
A. Diplomatic/Official Passports
90-day exemption for 46 countries
Must present note verbale for official visits
B. APEC Business Travel Card Holders
90-day stay privilege
Fast-track lane access at major airports
C. Crew Members
30-day exemption with valid:
Crew ID
Operator's letter
Layover schedule
7. Compliance and Enforcement Trends
A. New Monitoring Systems
Biometric Facial Recognition: Rolled out at 32 entry points
Advanced Passenger Processing (APP): Pre-arrival screening
Overstay Blacklist: Automated 1-10 year bans
B. Recent Policy Changes
2023 Digital Nomad Measure:
Exemption holders can now apply for 5-year LTR visa without exiting
2024 Financial Verification:
Pilot program at BKK/Suvarnabhumi for cashless proof of funds
Border Run Restrictions:
Electronic TM6 system flags frequent exempt entries
8. Practical Considerations for Travelers
A. High-Risk Scenarios
Previous Overstays:
Even 1-day overstay may trigger secondary inspection
Frequent Exemptions:
More than 6 exemptions in 24 months risks denial
Suspected Employment:
Carrying work equipment without proper visa
B. Recommended Protocols
Document Preparation:
Printed hotel confirmations for first 7 days
Embassy contact details
Health insurance (increasingly requested)
Entry Point Strategy:
Airports generally more lenient than land borders
Avoid "visa run" border crossings (e.g., Poipet)
9. Future Policy Directions
Digital Nomad Visa Integration:
Planned merger with exemption system
ASEAN Harmonization:
Potential 60-day standard for ASEAN+6 countries
Blockchain Verification:
Pilot program for digital proof of onward travel
Dynamic Pricing Model:
Proposed fee structure based on nationality risk factors
This technical breakdown demonstrates Thailand's visa exemption system as a carefully managed balance between tourism facilitation and immigration control, with increasingly sophisticated compliance mechanisms. The system continues evolving with new technologies while maintaining its core accessibility for legitimate travelers.
#immigration#thailand#thai#visa#thaivisa#thailandvisa#visainthailand#thailandvisaexemptions#immigrationinthailand#thaiimmigration
2 notes
·
View notes
Text

Why Self-Service Kiosks Are the Future of Hospitality and Retail !!
The retail and hospitality industries are constantly evolving to meet the demands of modern consumers. As businesses strive for efficiency, convenience and improved customer experience, self-service kiosks have emerged as a game-changing solution. From quick-service restaurants to retail stores and hotels, kiosks are revolutionizing how customers interact with businesses, making transactions smoother, reducing wait times and enhancing overall satisfaction.
The Growing Demand for Self-Service Solutions
With the rise of digital transformation, consumers now expect seamless, tech-driven interactions in every aspect of their lives. Self-service kiosks address this demand by providing :
Speed and Efficiency – Customers can place orders, check-in or make payments quickly without waiting in long lines.
Reduced Labor Costs – Businesses can optimize staff allocation, reducing operational expenses while maintaining quality service.
Enhanced Customer Experience – Customizable interfaces and multilingual support ensure a smooth and personalized experience for diverse audiences.
Improved Accuracy – Self-service kiosks eliminate human errors in order placement, payment processing, and service requests.
How Kiosks Are Transforming Retail Retailers are integrating self-service kiosks to streamline operations and improve shopping experiences. Some key benefits include:
Faster Checkout – Self-checkout kiosks minimize congestion at traditional cash registers, reducing wait times.
In-Store Navigation & Product Lookup – Customers can quickly locate products and access real-time stock availability.
Loyalty Program Integration – Kiosks enable customers to register for rewards programs, check points, and redeem offers effortlessly.
Seamless Omnichannel Experience – Integration with e-commerce platforms allows customers to order online and pick up in-store.
Upselling and Cross-Selling Opportunities – Kiosks can suggest complementary products or promotions based on customer preferences.
The Impact of Kiosks in Hospitality In the hospitality industry, self-service kiosks are redefining guest experiences by offering:
Faster Hotel Check-Ins and Check-Outs – Guests can skip front desk lines and access rooms with digital keys.
Self-Ordering at Restaurants – Quick-service and fast-casual restaurants use kiosks to enhance order accuracy and speed.
Automated Ticketing and Reservations – Kiosks streamline the process for theme parks, movie theaters and travel agencies.
Personalized Customer Interactions – AI-powered kiosks can recommend services, upgrades, or add-ons based on customer preferences.
Multi-Functionality – Kiosks can serve as concierge services, providing guests with local recommendations and travel assistance.
The Future of Self-Service Kiosks The future of self-service kiosks is driven by technological advancements, including:
AI and Machine Learning – Personalized recommendations and predictive analytics will enhance user engagement.
Contactless and Mobile Integration – NFC payments and mobile app connectivity will further simplify transactions.
Biometric Authentication – Facial recognition and fingerprint scanning will improve security and user convenience.
Sustainable and Eco-Friendly Kiosks – Digital receipts and energy-efficient designs will support environmental initiatives.
Cloud-Based Management – Remote monitoring and software updates will enable seamless kiosk operations.
Voice-Activated Interfaces – Enhancing accessibility for all users, including those with disabilities.
Conclusion Self-service kiosks are no longer a luxury but a necessity for businesses aiming to enhance efficiency, reduce costs and improve customer satisfaction. As the retail and hospitality industries continue to evolve, adopting kiosk technology will be key to staying competitive and meeting the ever-growing expectations of tech-savvy consumers.
What are your thoughts on the future of self-service kiosks? Share your insights in the comments below!
#PanashiKiosk#KioskDesign#TrendingDesign#InnovativeKiosks#RetailDesign#CustomerExperience#DigitalKiosks#UserFriendlyDesign#SmartRetail#DesignTrends#InteractiveKiosks#TechInRetail#KioskSolutions#ModernDesign#BrandExperience#RetailInnovation#DesignInspiration#FutureOfRetail#selfservicekiosk#businesssolution#kiosk#kioskmachine#bankingkiosk#insurancekiosk#telecomkiosk#vendingmachine#interactivetellermachine#QSRkiosk#restaurantkiosk#donationkiosk
2 notes
·
View notes
Text
G Witch Onscreen Text: Episode 2
This is part 3 in an ongoing series where I try and document and discuss all of the text that appears on screens and monitors throughout the show! Just because I can!
<<Click here to go back to Episode 1!
(Once I have a masterpost set up I will link it here!) Let us Begin! Below the Cut!

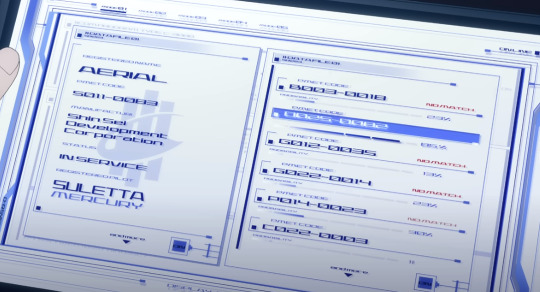
TEXT: (Lefthand side) Registered Name: AERIAL PMET CODE: 5011-0083 MANUFACTUR(ER): SHIN-SEI DEVELOPMENT CORPORATION STATUS: IN SERVICE REGISTERED PILOT: SULETTA MERCURY
At the beginning of the episode, Rouji has Haro run a program that compares Aerial's permet code and registered statistics against other registered Mobile Suits to try and find a match, and measures the probability of the two being the same type of MS. There is no direct match to any other MS by Permet Code, but the system states there's an 85% probability that it's a match for a Mobile Suit with permet code 0025-0082.
We never see the specific name of this MS, but considering that Shaddiq names "Ochs Earth" as the company that made it and proceeds to call Aerial, "...the Witch's Mobile Suit," I think it's reasonable to assume that 0025-0082 was the Permet Code for Lfrith-03.

TEXT: ALERT ACCESS CONTROL [???] [----OF ENTRY A---]
Unfortunately due to the small text of the Alert message, the fact that it scrolls, and it's brief time onscreen, its hard to make out specifically what it says. My best assumption from what we have is that it's a warning currently barring anyone from entry into the 13th Tactical Testing Sector.

TEXT: (Suletta's Asticassia ID) PILOTING DEPARTMENT ID No: LP-041 SULETTA MERCURY BIRTHPLACE: MERCURY HOUSE: NO DATA PC-CRIMINAL RECORD: NO DATA PC-BIOMETRIC SYSTEM: REGISTERED
(Below) WE ARE RESPONSIBLE UNDER COMPANY REGULATIONS FOR THE PROCESSING OF PERSONAL DATA
UNDER THESE REGULATIONS, WE ARE ALSO RESPONSIBLE FOR DATA HANDLING SUCH AS TRANSMISSION TO RECIPIENTS AND THIRD PARTIES.
PLEASE REFER TO THE FOLLOWING DOCUMENTS FOR DETAILS.
As Suletta is being questioned, we get a brief glimpse at the investigation report the interrogator was looking at before the screen cuts to black when it hits the table. Nothing super interesting here, but Suletta doesn't have a registered criminal record! Yippeeee!

TEXT: CAM: 05 MONITORING CAMERA FACILITY MANAGEMENT COMPANY
Not much to say here, this camera lets us know where Suletta is currently being held. (The Facility Management Company)
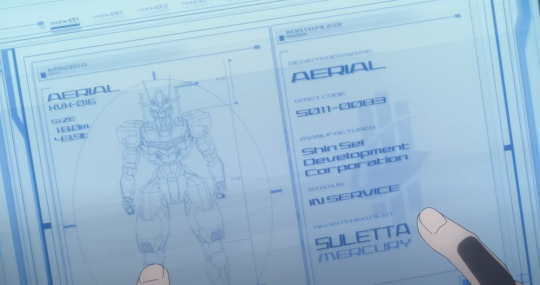
TEXT: (Lefthand Side) AERIAL XVX - 016 SIZE: 18.0m 48.9t
No point discussing the info on the right, we've already seen it, but this gives us a look at Aerial's height and weight.

TEXT: (Top Right) COM DELLING REMBRAN BENERIT GROUP
I only included this to point out that wow the display system devs made some poor choices with the UI here. Dark Blue text on Dark Backgrounds? You'd think the text would automatically lighten but I guess we'll have to wait for Ver 6.0 for that update.
TEXT (Top half) MOBILE CRAFT FUTURE TECHNOLOGY
ADVANCED MOBILE CRAFT TECHNOLOGY WITH PERMET MEASUREMENT EXPERTISE NEW POWER SYSTEM FOR MOBILE CRAFT AND HYBRID CONSTRUCTION MACHINE INSTALLATION HIGH ACCURACY DRIVE SYSTEM AND CONTROL SYSTEM IN MICROGRAVITY LOW ENERGY CONSUMPTION AND EASE OF MAINTENNANCE
No need to discuss the bottom half, its just the height and weight of the MC which we already know. I think it's funny how many classes this school seems to have on the new and improved Mobile Craft from Future Technology. I should probably buy one too. I love you Mobile Craft.


TEXT: (Left Image) The Shin Sei Development Corporation was established in A.S. 89. Our business began with the development of integrated operating systems for mobile suits and medical devices. We have been involved in MS development and have supported welfare engineering throughout our company history.
(Right Image) Ranking: D Sales Ranking (within group companies): 151th (out of) Total 157 companies [Mobile Suit Development] Number of clients: Over 300 companies Yearly patents: Over 200
We get a lot of information about Shin Sei in this scene where Martin looks at the Company History tab on their official website. The most interesting thing being that they were founded in A.S. 89. The Vanadis Incident occured in A.S. 101, and the show proper takes place in A.S. 122, so at some point between 101 and 122, Prospera worked her way up through Shin Sei, eventually becoming its CEO.
Given that Suletta had to have been born around A.S. 105, and that in Cradle Planet, we learn that Prospera had been working within Shin Sei when Suletta was around 6, that places A.S. 111 as the earliest she was involved.
We also learn in Cradle Planet, that when Suletta is around 11, Prospera has recently been promoted within the company, and now has many people working under her. That would be around A.S. 116. When Suletta is 16, that's when Prospera tells her that she's going to school, which would be around A.S. 121, and I think it's safe to assume that she had already become president by then.
SO!! TL;DR!! It's most likely that Prospera became the president of Shin Sei at SOME point between A.S 116 and A.S 121. I'd put it somewhere in the middle, around A.S 119. (Can't wait to find out that they probably just outright state this somewhere and I did all this for nothing....)
ADDENDUM

GOD DAMNIT. I WATCHED ALL OF CRADLE PLANET TO MATH THAT SHIT OUT. WHATEVER. I CAME TO THE SAME CONCLUSION SO I WIN.

The text is too small to make out, but we DO get a small glimpse at the letter Delling sent to Miorine about unenrolling her from the school. It probably just literally says what the body guard reads out.
I think it says something that Delling doesn't even like, text his daughter. He sends an email through the official Benerit Group email account to her bodyguard who reads it for her. What a cowardly man.

TEXT: (Left) FLUSH (Right) EMERGENCY CALL UNLOCK LOCK
YES the toilet text is important to document stop fucking looking at me like that.

TEXT: NEXT STAGE TOUCH SCREEN TO CONTINUE
I'll leave the explanation of the symbolism of this scene as an exercise for the reader. [Sultry Wink]

TEXT (Above) THIS ELECTRONIC SIGNATURE IS PROOF THAT IT WAS SIGNED BY A REPRESENTATIVE OF THE BENERIT GROUP.
No way to tell what Delling is signing here, but we do get a brief look at his handwriting. It turns out his cursive is really bad, actually!
At the Shin Sei inquiry, Shaddiq shares this graph titled "PMET RETENTION THRESHOLD VALUE", stating that during the duel, Aerial's Permet Influx Values exceeded the standards set by Cathedra.
This graph can be tough to parse, so let me explain it as best I can. The blue line represents Aerial's Permet Retention during the duel. The solid dark line represents the permet retention limit imposed by cathedra on mobile suits. (At around 500) As we can see, while Aerial began the duel underneath that limit, it exceeded it for a moment (presumably when Suletta took over for Miorine and the GUND bits were activated.)
The red line above that is labelled DATA STORM INCIDENT, which is representative of the minimum Permet Retention a Gundam expresses when it is interfacing with a Data Storm. The text on the bottom reads, THIS DATA IS VERY SIMILAR TO GUND FORMAT INCIDENT DATA.
But the key thing to take note of here is that Aerial's chart just BARELY doesn't exceed the DATA STORM INCIDENT graph, meaning that, despite it exceeding Cathedra's standards, it CANNOT be directly proven that Aerial was interfacing with a Data Storm. This is actually what Prospera brings up as her main counterpoint to the accusation.

So the graph is entirely consistent with Prospera's main argument. While she can't prove that Aerial isn't a gundam, nobody else can prove that it is.
Huaaaahh!! Alright!! This one was very DENSE. If you made it all the way through, thank you very much!! As a reward, have some little gay people




[I sprinkle these stills on the ground like bird seed.]
There was definitely a lot of really interesting info in this episode, and while not a lot of it was particularly new, I think it's really a testament to the dedication of keeping things wholly consistent in this world, even for the smallest of things that no normal person watching would even bother noticing.
Also, on the Shin Sei Website, did you notice that they accidentally put 151th instead of 151st?
You can't win em all!
Click here to go to Episode 3! >>
Click here to go to the Masterpost!
36 notes
·
View notes