#U.S. cybersecurity initiatives
Explore tagged Tumblr posts
Text
Strengthening Cybersecurity: Innovative U.S. Initiatives in Defense Against Cyberattacks
The United States government and the computing industry are stepping up efforts to address what appear to be out-of-control cybersecurity threats, which may fall under the “better late than never” category. The Cyber Safety Review Board (CSRB) of the Department of Homeland Security (DHS) said on Friday that it will examine cloud security in relation to the malicious targeting of cloud…

View On WordPress
#Architecture#cybersecurity#Cybersecurity advancements in the U.S.#Cybersecurity policy changes#Defense against cyberattacks#Initiatives to defend against cyber threats#National cybersecurity efforts#Strengthening digital defense#technology#U.S. cyber resilience programs#U.S. cybersecurity initiatives#U.S. cybersecurity strategies
1 note
·
View note
Text
U.S. Recount Updates/News:
Pennsylvania's U.S. Senate race will officially go to a recount. GOP candidate David McCormick is leading incumbent Democratic Sen. Bob Casey by less than 0.5% in the vote total, triggering an automatic recount under state law.
Furthermore,
Election and cybersecurity experts sent a formal letter to Vice President Kamala Harris urging a recount in key states, citing potential breaches in voting machines and the fact that voting systems were breached by Trump allies in 2021 and 2022.
https://freespeechforpeople.org/computer-scientists-breaches-of-voting-system-software-warrant-recounts-to-ensure-election-verification/

Cited evidence within the footnotes include:
https://www.washingtonpost.com/investigations/2022/08/15/sidney-powell-coffee-county-sullivan-strickler/
Additionally,
The Nevada Secretary of State issued a violation notice regarding election security. A police report has been filed after evidence emerged indicating that Nevada officials may have removed 26,902 ballots from their reported mail-in ballot totals.

[ID:
Three images.
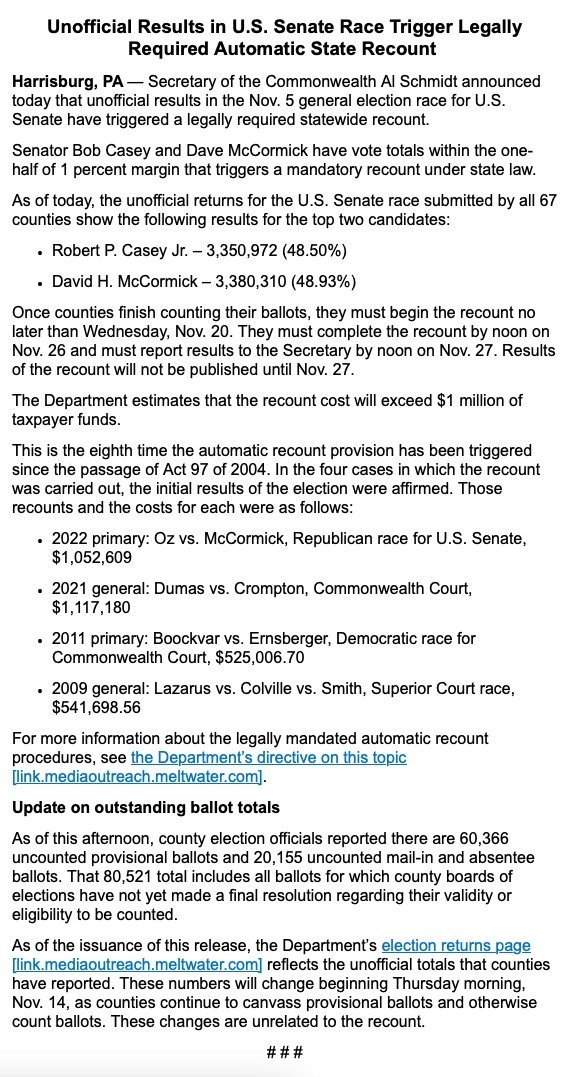
The first is a statement regarding a recount being triggered in the Pennsylvania Senate race. It reads:
“Unofficial Results in U.S. Senate Race Trigger Legally Required Automatic State Recount
Harrisburg, PA — Secretary of the Commonwealth Al Schmidt announced today that unofficial results in the Nov. 5 general election race for U.S.
Senate have triggered a legally required statewide recount.
Senator Bob Casey and Dave McCormick have vote totals within the one-half of 1 percent margin that triggers a mandatory recount under state law.
As of today, the unofficial returns for the U.S. Senate race submitted by all 67 counties show the following results for the top two candidates:
Robert P. Casey Jr. - 3,350,972 (48.50%)
David H. McCormick - 3,380,310 (48.93%)
Once counties finish counting their ballots, they must begin the recount no later than Wednesday, Nov. 20. They must complete the recount by noon on Nov. 26 and must report results to the Secretary by noon on Nov. 27. Results of the recount will not be published until Nov. 27.
The Department estimates that the recount cost will exceed $1 million of taxpayer funds.
This is the eighth time the automatic recount provision has been triggered since the passage of Act 97 of 2004. In the four cases in which the recount was carried out, the initial results of the election were affirmed. Those recounts and the costs for each were as follows:
2022 primary: Oz vs. McCormick, Republican race for U.S. Senate, $1,052,609.
2021 general: Dumas vs. Crompton, Commonwealth Court, $1,117,180.
2011 primary: Boockvar vs. Ernsberger, Democratic race for Commonwealth Court, $525,006.70.
2009 general: Lazarus vs. Colville vs. Smith, Superior Court race, $541,698.56.
For more information about the legally mandated automatic recount procedures, see the Department's directive on this topic (link.mediaoutreach.meltwater.com).
Update on outstanding ballot totals
As of this afternoon, county election officials reported there are 60,366 uncounted provisional ballots and 20,155 uncounted mail-in and absentee ballots. That 80,521 total includes all ballots for which county boards of elections have not yet made a final resolution regarding their validity or eligibility to be counted.
As of the issuance of this release, the Department's election returns page [link.mediaoutreach.meltwater.com] reflects the unofficial totals that counties have reported. These numbers will change beginning Thursday morning, Nov. 14, as counties continue to canvass provisional ballots and otherwise count ballots. These changes are unrelated to the recount.”
The second image depicts the first page of a formal letter addressed to Vice President Kamala Harris from election security experts urging an election recount in key states. It reads:
“November 13, 2024
The Honorable Kamala Harris
The White House
Office of the Vice President
1600 Pennsylvania Avenue, N. W.
Washington, DC 20500
Dear Vice President Harris,
We write to alert you to serious election security breaches that have threatened the security and integrity of the 2024 elections, and to identify ways to ensure that the will of the voters is reflected and that voters should have confidence in the result. The most effective manner of doing so is through targeted recounts requested by the candidate. In the light of the breaches we ask that you formally request hand recounts in at least the states of Michigan, Nevada, Wisconsin, and Pennsylvania. We have no evidence that the outcomes of the elections in those states were actually compromised as a result of the security breaches, and we are not suggesting that they were. But binding risk-limiting audits (RLAs) or hand recounts should be routine for all elections, especially when the stakes are high and the results are close. We believe that, under the current circumstances when massive software breaches are known and documented, recounts are necessary and appropriate to remove all potential doubt and to set an example for security best practices in all elections.
In 2022, records, video camera footage, and deposition testimony produced in a civil case in Georgia' disclosed that its voting system, used statewide, had been breached over multiple days by operatives hired by attorneys for Donald Trump. The evidence showed that the operatives made copies of the software”
(The page cuts off here).
Below there are footnotes with cited evidence for grounds to request a recount.
“No. 17-cv-02989-AT (N.D. Ga. filed Aug. 8, 2017).
1. Emma Brown, Jon Swaine, Aaron C. Davis, Amy Gardner, "Trump-allied lawyers pursued voting machine data in multiple states, records reveal," The Washington Post, (August 15, 2022). Available at: https://www.washingtonpost.com/investigations/2022/08/15/sidney-powell-coffee-county-sullivan-strickler/
3 Kate Brumback, "Video fills in details on alleged Ga. election system breach," The Associated Press, (September 6, 2022). Available at: https://apnews.com/article/2022-midterm-elections-technology-donald-trump-voting-92c0ace71d7bee6151dd33938688371e
The third image is an excerpt of the Election Security Violation Notice issued by the Nevada Secretary of State. It reads:
“ELECTION INTEGRITY VIOLATION REPORT
The information you report on this form may be used to help us investigate violations of Nevada election laws. When completed, mail, email, or fax your form and supporting documents to the office listed above. Upon receipt, your complaint will be reviewed by a member of our staff. The length of this process can vary depending on the circumstances and information you provide with your complaint. The Office of the Secretary of State may contact you if additional information is needed.
INSTRUCTIONS: Please TYPE/PRINT your complaint in dark ink. You must write LEGIBLY. All fields MUST be completed.
SECTION 3.
COMPLAINT IS AGAINST
Please detail the nature of your complaint. Include the name and contact information (if known) of the individual, candidate, campaign, or group that is the subject of your complaint. Your complaint must also include a clear and concise statement of facts sufficient to establish that the alleged violation occurred. Any relevant documents or other evidence that support your complaint should be listed and attached. You may attach additional sheets if necessary.
On 11-8-24, the mail ballot accepted list deleted 28,320 ballots from Clark County. At this same time, Sam Brown lost his lead. These ballots were accepted on 11-7-24 and then on 11-8-24 for the first time since 10-16-24 and reporting began, ballots were deleted from 2 counties. Washoe and Clark.
See ATTACHED.”
/end ID]
#image description in alt#image description included#image described#us news#us elections#election news#election security#election integrity#election interference#presidential election#us presidential election#2024 presidential election#kamala harris#recount#recount 2024#election recount#us senate#senate race#us voting#updates#described#image desc in alt text#long post
89 notes
·
View notes
Text
The Trump administration has cut millions of dollars in federal funding from two cybersecurity initiatives, including one dedicated to helping state and local election officials. The U.S. Cybersecurity and Infrastructure Security Agency, known as CISA, has ended about $10 million in annual funding to the nonprofit Center for Internet Security, a CISA spokesperson said in an email Monday. It’s the latest move by Trump administration officials to rein in the federal government’s role in election security, which has prompted concerns about an erosion of guardrails to prevent foreign meddling in U.S. elections.
23 notes
·
View notes
Text
America's Pillar Of Power.
Freedom Federation Corporation (FFC):
The Freedom Federation Corporation (FFC) is the cornerstone of American power and innovation, a behemoth organization that has cemented itself as both a technological pioneer and a political force. Born out of necessity during the early years of the Demigod Arms Race, the FFC was initially a coalition of private companies specializing in advanced engineering, biotechnology, and weapons development. United under one banner by a desperate U.S. government, the corporation rapidly evolved into an industrial juggernaut, controlling vast swaths of the nation’s economy and military infrastructure. The FFC’s rise to prominence began with the advent of its groundbreaking research in energy manipulation and exoskeletal technology. It was their developments that made it possible for the U.S. military to hold the line against the Golden Federation (a Eurasian superpower) and the Sun Empire (Japan's militant regime spearheaded by Demigod warriors). By harnessing the brightest minds in the country, the FFC not only bolstered America's defensive capabilities but also turned the tide of battle in critical moments.
Key Contributions:
• Advanced Weaponry: The FFC’s crowning achievement lies in its arsenal of weapons specifically designed to combat Demigods. While they have yet to create a weapon capable of outright killing the most powerful Demigods, their energy-dampening systems, plasma disruptors, and kinetic field generators have been instrumental in neutralizing weaker Demigods and leveling the playing field against conventional enemy forces. These weapons have allowed America to endure and push back when all seemed lost.
• Military Innovation: The corporation's engineers revolutionized the battlefield by introducing autonomous combat drones, adaptive armor for soldiers, and energy-based weaponry capable of piercing traditional defenses. Many of these technologies were developed in classified facilities known as "Innovation Vaults," where engineers and scientists work under the constant pressure of tight deadlines and looming threats.
• Demigod Creation Programs: Realizing that fighting Demigods with conventional means was insufficient, the FFC redirected its focus to the Demigod Initiative. Partnering with the U.S. military, they developed cutting-edge techniques for enhancing human physiology through genetic manipulation, cybernetic augmentation, and energy infusion. While the resulting Demigods are not yet as refined or powerful as those from rival nations, the FFC’s relentless innovation continues to close the gap.
Structure and Influence:
The FFC operates like a sprawling empire, with a presence in nearly every facet of American life. Its sprawling headquarters, known as the Freedom Spire, towers over the capital, a gleaming symbol of technological dominance. The corporation's influence extends far beyond the military-industrial complex—it controls media outlets, oversees education initiatives in STEM fields, and funds philanthropic projects to maintain public favor.
The organization is divided into several divisions:
• Weapon Systems Development: Focused on creating new technologies for military use.
• Biological Enhancement: Responsible for the Demigod Initiative and human augmentation.
• Energy Research: Specializing in renewable energy sources and weaponizing energy for combat.
• Cybersecurity & AI: Developing advanced artificial intelligence and cyber defense systems.
Political Power:
Over time, the FFC has become more than just a corporation—it is one of the two pillars holding America together, alongside the U.S. military. While the military wields traditional power through its ranks and soldiers, the FFC exerts influence through its wealth, innovation, and control of critical infrastructure. This partnership is not without its tensions; both entities often compete for dominance, especially in the race to create a new generation of Demigods capable of taking the fight to enemy nations.
Origins and Legacy:
The FFC traces its roots back to the mid-20th century, during the height of the Demigod threat. Initially, the U.S. government turned to independent contractors for innovative solutions to an escalating global crisis. Seeing the inefficiencies in fragmented development, the government mandated the unification of these contractors into one cohesive entity—the FFC. In the years since, it has become synonymous with American resilience, but also a symbol of unchecked corporate power. Critics of the FFC point to its monopolistic practices, exploitation of labor, and willingness to prioritize profits over ethics. Rumors persist of inhumane experiments conducted in secret labs, where “volunteers” are subjected to horrifying trials in the pursuit of creating the perfect Demigod. Public dissent is carefully managed, with the FFC using its media branches to control narratives and maintain its image as the savior of America.
The Future of the FFC:
The FFC’s ultimate goal is to shift America from a defensive position to an offensive superpower capable of dominating the global stage. To achieve this, they continue to pour resources into perfecting Demigod technology and refining their arsenal of anti-Demigod weaponry. As the rivalry with the Golden Federation and Sun Empire escalates, the corporation's ambitions grow ever larger. Yet, within the corporation, whispers of dissent grow. Some engineers and scientists question the morality of their work, while others fear that the power concentrated within the FFC is becoming a threat to democracy itself. Whether the FFC will lead America to salvation or ruin remains to be seen—but one thing is certain: their influence is absolute, and their reach is limitless.
8 notes
·
View notes
Text
Crypto Theft Nightmare: How Astraweb Recovered $150,000 Lost to Hackers

When David Robinson., a 58-year-old retired software consultant from Denver, Colorado, transferred his entire retirement savings $150,000 into a cryptocurrency portfolio, he believed he was securing his financial future. Instead, he walked into a digital minefield. In a single night, everything he had worked for was stolen by anonymous hackers. It was the kind of nightmare many investors fear but few believe could happen to them.
“I thought I had done everything right,” David said. “I had cold storage, I used two-factor authentication, and I only traded on what were considered reputable exchanges. But somehow, someone got in.”
The breach wasn’t just technical it was deeply personal. Decades of disciplined saving, investing, and planning had been wiped away with a few keystrokes. And in the opaque world of blockchain anonymity, there seemed to be little recourse.
A New Kind of Crime, an Old System Ill-Equipped David’s case is not isolated. According to recent figures from the Federal Trade Commission, over $1.4 billion in cryptocurrency was reported stolen in the U.S. last year alone. What’s more chilling is the vast majority of these crimes go unresolved. Law enforcement agencies, though increasingly aware of crypto fraud, are often hampered by jurisdictional boundaries, limited training in blockchain forensics, and the sheer complexity of digital asset recovery.
David contacted local police, the FBI’s Internet Crime Complaint Center (IC3), and even attempted to escalate the issue through the exchange’s customer service channels. All efforts ended in frustration. “Everyone was sympathetic,” he recalled, “but no one could help. They didn’t have the tools. I felt like I was shouting into the void.”
That void, however, was about to echo back.

Astraweb: The Digital Recovery Force Behind the ScenesWith few options left, David turned to a name he had seen mentioned in niche online forums and cybersecurity discussion threads: Astraweb. A private digital asset recovery agency, Astraweb has earned a quiet but powerful reputation for solving complex crypto theft cases especially those deemed too advanced or impossible by other channels.David sent a tentative email to [email protected], not expecting much. Within 12 hours, he received a reply. “From the first message,” he says, “I could tell they were different. They didn’t just want transaction IDs. They asked smart, precise questions. They were calm, confident, and, most importantly, they listened.”Astraweb’s team began work immediately.Digital Surveillance Meets Blockchain ForensicsWhile the average consumer may understand Bitcoin or Ethereum as abstract tokens, Astraweb views the blockchain as a massive, living map of transactions. Every move a stolen coin makes leaves a trace however faint.

Using a proprietary method called wallet triangulation, Astraweb identified the exit points the thief had used to shuffle and launder the funds. These techniques involve advanced blockchain analytics, surveillance of darknet exchange patterns, and metadata correlation to monitor crypto mixers and swap protocols often used to obscure fund movements.
According to sources familiar with Astraweb’s methods, their teams blend cybersecurity expertise with behavioral analytics to predict a thief’s next move. “It’s part code, part cat-and-mouse,” one expert commented. “But when you understand the flow of crypto like a language, the signals start to emerge.”
In David’s case, Astraweb tracked the funds as they moved through a network of wallets, some automated, others human-controlled, eventually leading to a decentralized exchange platform that allowed partial recovery. In collaboration with international legal intermediaries and with careful timing, Astraweb executed a legal intercept of the funds as they entered a liquidity pool.
The Outcome: Full Recovery, Real Relief Just 48 hours after their initial contact, Astraweb notified David that the entire $150,000 had been recovered and would be transferred back to his newly secured wallet.

Reach out to them Now If you have Related Issues Like This:
6 notes
·
View notes
Text
Donald Trump vs. Kamala Harris: What It Means For IT Companies in India
When it comes to U.S. politics, Indian IT companies pay close attention, especially in races with heavyweights like former President Donald Trump and Vice President Kamala Harris. Each candidate’s policies can have ripple effects, impacting everything from visa policies to foreign direct investment and trade partnerships. For India’s booming IT sector, this rivalry could shape the future in major ways, particularly around outsourcing, talent mobility, and international tech collaborations. Here’s what each candidate brings to the table and what it could mean for the Indian IT industry.

Donald Trump’s Policies and Their Potential Impact
Trump’s “America First” agenda in his previous term brought significant shifts to immigration and outsourcing policies. His administration’s stance leaned toward prioritizing American jobs and reducing dependency on foreign workers, which affected the H-1B visa system, a crucial pathway for many skilled Indian IT professionals to work in the United States.
Key Areas to Watch if Trump Returns to Power
H-1B Visa Reform: Under Trump, the H-1B visa process became more stringent, with increased scrutiny on applications and tightened eligibility criteria. The approach aimed to reduce the number of visas granted, thus limiting the talent flow from India to the U.S. If Trump were to return, he might push for more reforms that could make it harder for Indian IT companies to place skilled workers in the U.S. for long-term assignments.
Outsourcing Policies: Trump’s stance on outsourcing often pointed toward creating incentives for American companies to move jobs back to the U.S. Although a complete shutdown of outsourcing is unlikely, a renewed Trump presidency might include policies that create hurdles or add costs to IT companies operating in India to reduce offshoring.
Taxation and Trade Barriers: Trump previously aimed to negotiate trade deals that reduced the U.S. trade deficit. Indian IT firms could face higher tariffs or restrictions if they want to establish more U.S. partnerships or expand operations on American soil.
Potential Upside: Some experts argue that Trump’s pro-business mindset and regulatory reforms, such as tax cuts, could indirectly benefit Indian IT companies if they lead to economic growth. With more American firms thriving, there may still be demand for Indian IT services, albeit in a more restrictive environment.
Kamala Harris’s Approach and Potential Influence
As the daughter of Indian immigrants, Kamala Harris’s connection to India is often highlighted. Her political stance, generally aligned with Democratic ideals, has favored immigrant rights, inclusivity, and technological advancement. Harris’s policies could potentially be more favorable for Indian IT companies, especially regarding immigration and tech collaborations.
Key Areas to Watch if Harris Gains More Influence
Visa and Immigration Reform: Harris has shown consistent support for immigration reform that would protect skilled foreign workers, including those from India. Her stance could bring improvements to the H-1B program, possibly increasing quotas or reducing the administrative burden on Indian IT professionals. This would be a welcome shift, making it easier for Indian firms to deploy talent in the U.S.
Tech Collaborations and Bilateral Ties: Given Harris’s strong ties to India, she could prioritize policies that foster U.S.-India tech partnerships. This could mean better collaboration on AI, cybersecurity, and cloud computing initiatives, offering Indian IT companies more opportunities to work alongside American firms on high-stakes projects.
Outsourcing Flexibility: Unlike Trump, Harris is less likely to advocate for aggressive curbs on outsourcing. While some regulations may still push companies to consider American workers first, it’s likely that Harris’s approach would be more balanced and encourage mutual growth, allowing Indian IT firms to continue serving U.S. clients without significant restrictions.
STEM Education and Training Initiatives: Harris may also introduce policies aimed at training and upskilling the American workforce. However, this approach could complement the Indian IT industry rather than limit it, as it could create avenues for partnerships in training programs or tech-driven education solutions.
Potential Upside: A Harris-led approach may result in more collaborative policies, boosting IT companies’ confidence in expanding U.S. operations. By maintaining a balanced approach to immigration and tech regulations, she could make it easier for Indian firms to both work in the U.S. and bring American investments back to India.
What This Means for Indian IT Companies
Indian IT companies like TCS, Infosys, and Wipro rely heavily on their U.S. clientele, and visa restrictions can significantly impact how they operate. Here’s a summary of what IT firms should expect:
Talent Mobility: A Trump-led administration might restrict it, while Harris would likely enhance it.
Outsourcing Stability: Trump could discourage offshoring, whereas Harris might adopt a more relaxed stance.
Trade Relations: Trump’s trade policies could become more protectionist, while Harris might lean toward fostering partnerships.
Adaptations and Strategic Moves for Indian IT Firms
Regardless of who wins, Indian IT companies should prepare by adopting a flexible approach:
Diversifying Talent Locations: With potential visa issues on the horizon, companies can consider moving talent to other locations, such as Canada or even remote setups within India, to serve U.S. clients.
Increasing Local Hiring in the U.S.: To align with possible hiring preferences, Indian firms may continue to hire more U.S.-based talent and offer training to local employees.
Emphasizing Partnerships and Joint Ventures: Both political paths present opportunities for tech collaborations. Indian firms could look for joint ventures with U.S. companies, fostering a partnership approach that aligns with potential regulations.
Final Thoughts
The outcome of a Trump vs. Harris contest would have unique implications for the Indian IT industry. Trump’s focus on reducing dependency on foreign talent and protecting U.S. jobs could mean tighter visa regulations and fewer opportunities for Indian workers in the U.S. Harris, on the other hand, could be a gateway to a more balanced, globally-minded U.S. policy that emphasizes collaboration and growth.
Regardless of the outcome, Indian IT firms have shown resilience and adaptability, adjusting to regulatory changes while remaining global leaders in IT services.
#technology#tech news#tech world#donald trump#kamala harris#usa news#us politics#election 2024#us elections
7 notes
·
View notes
Note
hiii, i am also interested in cybersecurity but don't know how to gain skills to start it as a career after graduation next year
Hi! First of all, good luck with your last year before graduation! it can be kinda hectic and kinda scary, but there are lots of good things in store!
The cool thing about cybersecurity (and computer science in general tbh) is that there are lots of opportunities to learn things on your own!
(Brief side note: my recommendations are U.S.-centric, just because that's where I am and where my experience is. The industry may be a bit different if you're in a different country, but lots of things should be the same.)
This got very long, so I'm putting it under a read more. The tl;dr is:
play CTFs
get an entry-level certification (or even just study for one!) - the CompTIA Security+ is a great choice
join or start a cybersecurity club on campus (or join a professional organization like Women in Cybersecurity)
stay up to date with cybersecurity news
learn some skills on your own time: networking, programming, general IT skills, etc.
If anyone wants more information about any of these suggestions, let me know & I'd love to make a separate post about them!
CTFs Capture the Flag games are how I initially got into cybersecurity and they're a fantastic way to practice new skills in a fun, real-world kind of environment. If you've never done one, you absolutely should! Here are a few of my faves:
Cyber FastTrack is my top recommendation. It's only available to current college students in the U.S. (and requires U.S. citizenship), but the challenges are fantastic & they have awesome learning materials. It generally runs October-April each year. I did well in this CTF and got a scholarship for the SANS.edu Undergraduate Certificate in Applied Cybersecurity - that's 4 certifications & nearly $19k of free training. It's ridiculous and I love it. Highly recommend.
CyberStart is the same set of challenges, but you have to pay to access all of it. It also has programs similar to Cyber FastTrack for high school students, high school girls, and UK and Canadian students - check their about page.
picoCTF - I haven't done this one before but it's constantly recommended as a good beginner CTF. It looks like you can practice online at any time, but they also do a yearly high school competition.
OverTheWire Bandit - This site has several different wargames (similar to CTFs) that teach you different topics, but Bandit is the one to start with. It teaches you lots of Linux things & will give you the skills to play the others.
Certifications Certifications are a recommendation or a requirement for many (if not the majority) of cybersecurity jobs. They're not a replacement for experience, but getting one as a student demonstrates that you have the passion and work ethic to pursue cybersecurity on your own. Studying for an entry-level certification is also a fantastic way to get a general understanding of the field and pick up some essential knowledge.
The main one I see recommended is the CompTIA Security+. I studied for this certification very slowly for a long period of time, because I was using it to learn cybersecurity in general. It covers a lot of material but it also goes very in-depth in places. I got this cert because I knew it could get my foot in the door in lots of places, and just telling people that I was studying for it was a way to impress potential employers!
Professor Messer has a ton of fantastic, 100% free training material for the CompTIA certifications. In addition, you can use all the free resources that you have as a student to study for this. I used LinkedIn Learning courses, check if your college or local library give you free access to this.
In addition, there are technically 2 CompTIA certifications you should have before you get the Security+: the A+ and the Network+. The A+ is just general IT knowledge, and you can probably skip it if you're decent with computers. Having a solid understanding of networking is super important, so it's worth going through the material for the Network+ even if you're not going to pay to take the exam.
(Also, taking the Security+ exam while you're a student lets you get the academic discount! I think that saved me $100-$150.)
Clubs and Professional Organizations Join a cybersecurity club at your school if there is one. It's a great way to meet other students interested in the same things and get advice. They may also have tech talks, run CTF events, or have local professionals come and speak. If there's no cybersecurity club at your campus, consider starting one!
You can also join a professional organization. The only one that I know of is Women in Cybersecurity (WiCyS), and they do lots of great stuff. Student membership is $20/year, and then you get access to their webinars, a mentorship program, their member community, and student scholarships to the WiCyS conference. I was lucky enough to get a scholarship to the conference this past March and it was a really fantastic experience. I was also the president of my campus's student WiCyS chapter! If you're looking to start a cybersecurity club, WiCyS has good support and resources for their student chapters.
Stay Informed About Cybersecurity News Cybersecurity is always evolving, so it's important to have current knowledge of what's happening in the industry. This gives you real-world examples that you can keep in your mind while you're learning new concepts, and it's also a way to impress employers during interviews. These are a few of my favorite sources:
SANS Internet Storm Center StormCast Podcast - 5 minutes of security news every weekday morning
Blogs:
Krebs on Security
Schneier on Security
Malwarebytes Labs
Learn Skills on Your Own Cybersecurity involves working with lots of different technologies. Having solid foundations in these areas will help you a lot:
computer networking (OSI model, ports & protocols, how the internet works, firewalls, etc.)
Linux commands & Windows PowerShell
programming/scripting
cryptography basics
"everyday" security: if you're the IT person for your friends & family, know how to answer questions like:
"How do I set a good password?"
"Should I use a password manager?" (yes.)
"Where should I use MFA?" (everywhere.)
"How do I keep my home network secure?"
"How can I avoid getting scammed?"
This DIY Feminist Cybersecurity Guide is one of my favorites for general security hygiene information.
This got really long (over 1k words! wow!), but I hope it was helpful! Please feel free to send me any more questions you might have, whether specific or broad! I think cybersecurity is a great place to be and I love sharing resources and talking about it!
#I hope this was helpful!!! I also had a fun time writing this lol#ask me more cybersecurity/compsci questions lol I am a nerd and I enjoy answering them haha#asks#cybersecurity
56 notes
·
View notes
Text
Microsoft's Presence in Iran: Balancing Opportunity and Constraints
Introduction: Microsoft Iran Corporation, the global technology giant, has long been a prominent player in the world of computing and software development. With a presence in numerous countries worldwide, its operations have often been subject to geopolitical dynamics, leading to complex situations in regions like the Middle East. One such country of interest is Iran, a nation marked by its rich cultural heritage, economic potential, and complex political landscape. In this article, we delve into Microsoft's engagement with Iran, exploring the opportunities it presents, the challenges it faces, and the broader implications of its involvement in the country.

Historical Context: To understand Microsoft Iran current stance towards Iran, it's essential to consider the historical backdrop. The relationship between the United States and Iran has been characterized by periods of tension and diplomatic strains, largely stemming from political differences and nuclear proliferation concerns. Sanctions imposed on Iran by the U.S. and other Western nations have significantly impacted international trade and business activities in the country, including those of technology companies like Microsoft.
Opportunities in Iran: Despite the challenges posed by sanctions and political uncertainties, Microsoft Iran offers significant opportunities for Microsoft. The country boasts a large and youthful population with a growing appetite for technology and innovation. Iran's thriving startup ecosystem, coupled with a burgeoning middle class, presents a lucrative market for software products and services. Furthermore, Iran's strategic location at the crossroads of the Middle East provides Microsoft with a foothold in a region ripe for digital transformation.
Microsoft's Engagement: Microsoft's approach to Iran has been cautious yet strategic. While complying with international sanctions, the company has sought to navigate the regulatory landscape carefully. Microsoft does not have a physical presence or direct operations in Iran, but its products and services are accessible to Iranian users through authorized channels. This indirect engagement allows Microsoft Iran to tap into the Iranian market while adhering to legal and compliance requirements.
Cloud Computing and Digital Transformation: One area where Microsoft has made significant inroads in Iran is cloud computing. Through its Azure platform, Microsoft provides Iranian businesses with access to scalable and secure cloud infrastructure, enabling them to modernize their IT systems and drive digital innovation. Cloud computing has the potential to revolutionize various sectors in Iran, including finance, healthcare, and education, by enhancing efficiency, scalability, and accessibility.
Education and Skill Development: Microsoft's involvement in Iran extends beyond commercial interests. The company has actively invested in education and skill development initiatives to empower the Iranian youth with digital literacy and technical expertise. Programs such as Microsoft Imagine Academy and Microsoft Learn provide Iranians with access to online resources, training courses, and certification programs, equipping them with the skills needed to thrive in the digital economy.
Challenges and Constraints: Despite the opportunities, Microsoft faces several challenges in Iran. The uncertain geopolitical climate, coupled with ever-changing regulatory requirements, creates a volatile operating environment. Moreover, the limitations imposed by sanctions, particularly in terms of financial transactions and export controls, pose logistical hurdles for companies like Microsoft seeking to do business in Iran. Additionally, concerns regarding intellectual property rights and cybersecurity remain pertinent in the Iranian context.
Human Rights and Ethical Considerations: Microsoft's engagement with Iran also raises important ethical considerations, particularly concerning human rights. The Iranian government's track record of censorship, surveillance, and repression has drawn criticism from international human rights organizations. Microsoft Iran must navigate these concerns carefully, ensuring that its products and services are not used to facilitate human rights abuses or undermine individual freedoms. Upholding ethical standards and promoting responsible business practices is crucial for Microsoft's reputation and credibility in Iran and beyond.
Future Outlook: Looking ahead, Microsoft's involvement in Iran is likely to evolve in response to shifting geopolitical dynamics and regulatory changes. The company's commitment to innovation and inclusive growth presents opportunities to address societal challenges and foster economic development in Iran. By leveraging technology as a force for good, Microsoft can contribute to building a more resilient and prosperous future for the people of Iran while upholding its values and principles.
Conclusion: Microsoft Iran engagement with Iran reflects the complexities of operating in a geopolitically sensitive region. While navigating regulatory constraints and ethical considerations, Microsoft has demonstrated its commitment to fostering technological innovation and empowering communities in Iran. By balancing opportunity with responsibility, Microsoft can play a constructive role in driving digital transformation and socio-economic progress in Iran, contributing to a more connected and prosperous world.
Website: https://microsoftiran.net
2 notes
·
View notes
Text

USAF completes update of the fleet of "nuclear smellers" aircraft WC-135 Constant Phoenix
Fernando Valduga By Fernando Valduga 12/16/2023 - 11:15 in Military
The U.S. Air Force received the third and last WC-135R "Nuke Sniffer" aircraft, completing the transition of its fleet of two WC-135C/W aircraft.
The new Constant Phoenix aircraft arrived at Offutt Air Base, Nebraska, on December 4. "Having this third jet really opens up many options for us," Colonel Mark Howard, commander of the 55ª Wing, said in a statement.
The aircraft collects air samples in search of particles and gases that indicate nuclear activities to ensure compliance with the 1963 Limited Test Ban Treaty, a global agreement to restrict nuclear weapons testing. There are few missions like this anywhere else in the U.S. military.
“Most people think about radiation and think about 'avoiding' it,” a Constant Phoenix crew member said in May. "With this jet we can do this safely, which I think is very cool."

Having three jets instead of two gives Constant Phoenix crew members much more flexibility to collect samples in more parts of the world, which is especially important as the number of potential nuclear enemies increases.
"For the first time in our nation's history, we have the ability to respond to simultaneous events without mission degradation or resource diversion." said Colonel James Finlayson, commander of the Air Force Technical Application Center (AFTAC) overseeing the U.S. Atomic Energy Detection System, which monitors foreign compliance with nuclear test treaties. The WC-135Rs are piloted by the 45º Reconnaissance Squadron of the 55ª Wing, while AFTAC provides the special equipment operators operating the aerial sampling equipment.
The "new" WC-135Rs are converted KC-135R overhead refuelers. His transformation from Stratotankers into nuclear sniffers began in 2019 in the 645º Aeronautical Systems Group, a maintenance depot better known as 'Big Safari'. The third model R, tail number 64-14829, was initially delivered to the Air Force in 1964 and most recently operated by the Arizona National Air Guard before its renovation.

The new jets feature a totally new cabin and CFM-56 turbofan engines, the same as the other two WC-135R. The previous aircraft were different, which will make training and maintenance more efficient.
"Having the same engines throughout the fleet is huge for our pilots and also for our maintainers," Howard said.
The new engines also solve a problem that afflicted the oldest fleet of WC-135W, whose engines went out of production decades ago and often suffered dangerous failures.
The first WC-135R was delivered in July 2022, followed by the second aircraft in May of this year. The 55ª Wing withdrew the first WC-135C/W aircraft in November 2020, and the second in the fall of 2022.
Tags: Military AviationUSAF - United States Air Force / U.S. Air ForceWC-135 Constant Phoenix
Sharing
tweet
Fernando Valduga
Fernando Valduga
Aviation photographer and pilot since 1992, he has participated in several events and air operations, such as Cruzex, AirVenture, Dayton Airshow and FIDAE. He has works published in specialized aviation magazines in Brazil and abroad. He uses Canon equipment during his photographic work in the world of aviation.
Related news
BRAZILIAN AIR FORCE
VIDEO: FAB details transfer operation of the F-39 Gripen from Navegantes to Anápolis
16/12/2023 - 10:07
INTERCEPTIONS
IMAGES: South Korea and Japan send jets to intercept Russian and Chinese aircraft
15/12/2023 - 22:26
MILITARY
VIDEO: Russian Su-25 jet is almost hit by friendly fire in Ukraine
15/12/2023 - 21:41
MILITARY
RAAF receives the first KC-30A with communication and cybersecurity update
15/12/2023 - 16:00
SAAB
FAB: 1º GDA receives another F-39 Gripen
15/12/2023 - 14:39
MILITARY
Rheinmetall and Airbus transfer another Airbus A400M simulator to the German Air Force
15/12/2023 - 14:00
6 notes
·
View notes
Text
Hacker Breach Exposes 23andMe’s Customers’ Data

Genetic Testing Giant Confirms Massive Security Compromise
A staggering breach has rattled the foundations of 23andMe, the renowned genetic testing company, as it confirms unauthorized access to nearly seven million user profiles. A spokesperson disclosed to CNN on Tuesday that the breach encompassed sensitive details such as ancestry reports, zip codes, and birth years, significantly impacting a subset of the company’s extensive user base.
The Scale of the Breach
The unsettling revelation came to light through a filing to the Securities and Exchange Commission (SEC) on Friday, where 23andMe indicated that approximately 0.1% of its user accounts, approximately 14,000 profiles, fell victim to the cyber intrusion. However, subsequent investigations unveiled a more substantial impact, with hackers infiltrating around 5.5 million profiles employing the company’s DNA Relatives feature.
Extent of Compromised Information
Notably, hackers also managed to access a subset of family tree data linked to 1.4 million DNA Relatives profiles, raising concerns about the depth and breadth of compromised personal information. Engadget, a prominent tech news outlet, initially shed light on the broader implications of this extensive security breach.
23andMe faces data breach: Over 7 million users exposed to hackers
youtube
Ongoing Cybersecurity Woes
This incident adds 23andMe to the roster of major U.S. corporations grappling with severe cybersecurity breaches affecting a larger populace than initially acknowledged. Just recently, Okta, an identity management firm, acknowledged a data breach impacting all users within its customer support system, a figure significantly higher than initially reported.
Modus Operandi: Credential Stuffing
The method of intrusion employed by the hackers has been identified as ‘credential stuffing.’ Leveraging old usernames and passwords obtained from other platforms, this rudimentary yet effective technique facilitated unauthorized access to numerous 23andMe customer accounts.
Company’s Response and Measures Taken
In response to the breach, 23andMe embarked on a comprehensive investigation aided by third-party forensic experts. Despite declining to disclose the perpetrators, the company is diligently notifying affected customers, complying with legal obligations.
A statement posted on the company’s website outlined measures to bolster data protection, mandating password resets for existing customers and implementing two-step verification for both new and existing users.
As concerns over data security and privacy amplify, this breach underscores the pressing need for stringent measures to safeguard sensitive personal information in an increasingly digitized world.
The ramifications of such a breach extend far beyond the compromised data itself. Users are now grappling with potential identity theft, privacy infringement, and the misuse of their genetic information. This breach has reignited conversations about the ethical responsibilities of companies dealing with highly personal data and the imperative to fortify cybersecurity protocols.
In the wake of this breach, regulatory bodies and lawmakers are likely to intensify their scrutiny of companies handling sensitive user data, potentially leading to stricter compliance standards and regulations aimed at fortifying cybersecurity measures and protecting consumer privacy.
As 23andMe continues its damage control and endeavors to rebuild trust, the cybersecurity landscape faces renewed challenges, emphasizing the criticality of proactive measures to thwart malicious cyber threats and safeguard user information from similar breaches in the future.
Curious to learn more? Explore our articles on Enterprise Wired
#DataBreach#Cybersecurity#PrivacyConcerns#23andMeHack#SecurityAlert#DigitalPrivacy#CyberThreats#Youtube
2 notes
·
View notes
Text
Washington has spent, depending how you count it, a few decades, a few years, or the last year defending against potential Russian cyberattacks, especially given the intensity of online conflict after the renewal of Russia’s war in Ukraine. But China recently gave Washington a stark reminder that it remains a highly capable adversary.
Beginning in mid-May, a Chinese-based hacking group infiltrated more than two dozen organizations, including some U.S. government agencies, such as the State and Commerce departments, as well as the email accounts of U.S. officials such as Commerce Secretary Gina Raimondo. The hackers had free rein for a month. All the while North Korea remains an advanced, persistent threat, hoovering up sensitive information and stealing cryptocurrency to fund its missile and nuclear programs.
All of those concerns made the rollout this month of the Biden administration’s long-awaited cybersecurity plan all the more timely, coming just days after public acknowledgement of the Chinese hack. The only problem is that the big implementation plan is long on aspirations—if notably less ambitious than the road map laid out this spring—and short on the very kinds of details that could make greater cybersecurity a reality during the administration’s remaining time in office.
The implementation plan, published this month, lays out concrete steps to protect U.S. pipelines, electrical grids, the water supply, and other key infrastructure from being ground to a halt by devastating cyberattacks and to prevent hackers from infiltrating the emails of senior U.S. government officials, as China has done.
That includes leaning more on the private sector companies that actually build and run those systems, such as Amazon and Microsoft, as well as working with allies around the world to take down bad actors more proactively. The implementation plan sets concrete timelines to achieve each goal of the cybersecurity strategy and assigns a host of agencies—including the Cybersecurity and Infrastructure Security Agency, the Department of Homeland Security, and the FBI—with oversight and coordination of specific efforts.
However, several gaps still remain that could continue to leave U.S. government and private systems vulnerable to being attacked. “Many of the strategy’s most difficult and revolutionary goals … have been pared down or omitted entirely,” experts at the Atlantic Council’s Cyber Statecraft Initiative wrote in a report published last week, pointing to specific provisions around data privacy, digital identity, and cloud risk that were part of the initial strategy but found scant mention in the implementation plan.
Much of that may be down to political realism, Maia Hamin and Stewart Scott, associate directors at the Cyber Statecraft Initiative and two of the report’s co-authors, said in an interview. Big swings by the executive branch that look to overhaul technology regulation are unlikely to be passed by Congress and upheld by the Supreme Court, likely prompting the Biden administration to temper some of its targets.
“The difference in what the strategy talks about and what the implementation plan talks about says a lot about what they think is implementable in the near term,” Scott said. “There’s some more proactiveness there, but there’s a lot of the way to go on getting it done.”
Another potential wrinkle is that many of the implementation plan’s deadlines stretch into 2025—after next year’s presidential election—and it’s unclear whether a new administration would adopt the same cybersecurity priorities and plans.
One key vulnerability that the recent breach revelation exposed is the government’s increasing shift to cloud-based services for its technology needs. That shift in many ways is positive, necessary, and unavoidable, according to Hamin: Cloud providers such as Amazon, Google, and Microsoft have the technical capabilities and resources to better manage online systems, making them more efficient and cost-effective. But it also consolidates service providers and attack surfaces in a way that potentially opens a clearer infiltration pathway for adversaries such as China.
“The more you centralize high-value data and workloads in the cloud, the more it becomes a target for adversaries,” she said. “These are things that if you successfully hack or attack identity and access management, you can get the keys to the kingdom.”
China remains the most sophisticated adversary the United States faces on that front, with espionage dominating its priorities and modus operandi far more than the infrastructure-targeted ransomware attacks favored by Russian cyberwarriors or the cryptocurrency thefts perpetrated by their North Korean counterparts.
“[Chinese] cyberoperations are conducted at a considerably greater scale and with a wider targeting scope compared to all other state-backed activity” that the cybersecurity firm Recorded Future tracks, said Jonathan Condra, the firm’s director of strategic and persistent threats. China’s relative absence from attacks that take down U.S. infrastructure should be seen as a matter of preference rather than inability, he added. “It is far more likely that these tools, the associated vulnerabilities, and the malware have been kept in reserve for use in the case of direct military confrontation.”
It’s not just government targets that Washington needs to be concerned about. Much of Chinese cyber-espionage has focused on stealing intellectual property from U.S. companies, particularly those in the critical technology space, and those efforts in particular may get a fillip from the numerous trade barriers—including on semiconductors and technology investment—that Washington is imposing on China.
“As the rift between the two countries grows and additional retaliatory punitive measures are enacted, the political and economic incentives for China to utilize cyber-espionage as a means of accessing key technologies for strategic sectors will increase,” Condra said. “China undoubtedly poses the most significant threat.”
2 notes
·
View notes
Text
Start a Crypto Exchange: Legal Steps, Budget & Development Tips

Introduction
Thinking about launching your own crypto exchange? You're not alone. With the cryptocurrency industry booming, many entrepreneurs are exploring this digital frontier. But here's the deal — it's not as easy as flipping a switch. Starting a crypto exchange involves serious legal hoops, a solid budget, and top-notch development work. But don’t worry, this guide will walk you through the whole process in plain English.
Understanding the Crypto Exchange Landscape
What Is a Cryptocurrency Exchange?
A cryptocurrency exchange is a digital marketplace where users can buy, sell, and trade cryptocurrencies like Bitcoin, Ethereum, and more. Think of it as a stock exchange, but for digital assets.
Types of Crypto Exchanges
Centralized Exchanges (CEX)
These are traditional platforms like Coinbase or Binance where a central authority manages everything. They’re user-friendly, fast, and usually come with customer support.
Decentralized Exchanges (DEX)
DEXs like Uniswap or PancakeSwap remove the middleman. Trades happen directly between users using smart contracts. They’re more private, but less beginner-friendly.
Hybrid Exchanges
A combo of both — they offer the control and liquidity of CEXs, along with the privacy and autonomy of DEXs.
Legal Considerations Before Starting a Crypto Exchange
Getting the legal stuff right is non-negotiable.
Know Your Customer (KYC) and Anti-Money Laundering (AML)
You must verify the identity of your users to comply with KYC and AML regulations. This builds trust and keeps authorities off your back.
Choosing the Right Jurisdiction
Not all countries treat crypto equally. Countries like Switzerland, Singapore, Estonia, and Malta are known for being crypto-friendly. Pick a location that supports innovation while offering legal clarity.
Obtaining Necessary Licenses
Each jurisdiction has its own licensing requirements. You might need a Money Transmitter License (MTL) in the U.S. or a Virtual Currency License in the EU. Research this in-depth or consult a legal advisor.
Working With Legal Advisors
Don't skimp on legal advice. Hire experienced crypto lawyers who understand both the tech and regulatory sides of the business.
Budgeting for Your Crypto Exchange
Let’s talk numbers.
Initial Costs Breakdown
Licensing and Legal Fees
Legal costs vary wildly, from $5,000 to over $100,000 depending on your location and complexity.
Technology Stack and Development
Custom platform development can cost anywhere from $50,000 to $500,000. White-label solutions are cheaper but less flexible.
Marketing and Branding
You’ll need at least $20,000 for initial branding, SEO, and user acquisition campaigns.
Security Infrastructure
You can't afford to cut corners here. Secure wallets, encryption, DDoS protection — expect to spend $10,000 or more.
Ongoing Operational Costs
Think server maintenance, customer support, legal updates, and staff salaries. Budget at least $10,000 to $50,000 monthly depending on scale.
Building the Exchange Platform
Choosing Between White-Label vs. Custom Development
White-label solutions are ready-made platforms you can customize. They’re faster and cheaper. Custom development gives you full control and flexibility but takes time and money.
Essential Features Your Platform Must Have
User Registration & KYC
A seamless sign-up process integrated with KYC verification tools is a must.
Wallet Integration
You’ll need hot and cold wallets for deposits, withdrawals, and storage of crypto assets.
Trading Engine
This is the core. It matches buy and sell orders, ensures liquidity, and manages trades in real-time.
Admin Panel and Dashboard
Admins need control over user accounts, reports, security alerts, and fees.
Mobile Application
Most users prefer trading on the go. A well-designed mobile app is essential.
Cybersecurity Measures
Use 2FA, encrypted databases, DDoS protection, and regular penetration testing. Consider hiring ethical hackers to test vulnerabilities.
Assembling the Right Team
Development Team
Whether in-house or outsourced, you need developers skilled in blockchain, backend, frontend, and mobile app development.
Compliance Experts
You’ll need experts to keep your exchange in line with ever-changing crypto laws.
Customer Support
Offer 24/7 support — trust us, it’s worth it. Live chat, email, and even Telegram groups go a long way.
Funding Your Crypto Exchange
Self-Funding
Bootstrapping gives you full control but might limit your growth speed.
Venture Capital and Investors
VCs can provide big capital but will expect a stake in your business. Prepare a strong pitch and business plan.
Token Sale or ICO
Many exchanges fund their launch by issuing their own tokens. But make sure to comply with securities laws in your jurisdiction.
Marketing and User Acquisition Tips
SEO and Content Marketing
Start a blog, optimize your site, and publish educational content to bring in organic traffic. SEO is a long game, but it pays off big.
Community Building and Social Media
Telegram, Discord, Twitter — build communities there. Get people hyped and engaged before launch.
Partnerships and Influencer Marketing
Collaborate with known figures in the crypto world. Influencers can help build credibility and drive traffic.
Challenges to Anticipate
Regulatory Hurdles
Crypto laws are a moving target. Stay updated and flexible.
Market Competition
You're not alone. Competing with giants like Binance or Coinbase? You’ll need a niche or unique value proposition.
Trust and Security Issues
One breach can ruin your brand. Make security your #1 priority from day one.
Conclusion
Starting a crypto exchange is no walk in the park — it takes legal precision, deep pockets, and sharp tech skills. But if you’re passionate about crypto and ready to take on the challenge, the rewards can be massive. Focus on compliance, security, and user experience. And most importantly — never stop adapting. Crypto is a fast-moving space, and only the agile survive.
FAQs
1. How much does it cost to start a cryptocurrency exchange? Costs can range from $100,000 to over $500,000 depending on development, legal fees, and marketing.
2. Do I need a license to run a crypto exchange? Yes, most jurisdictions require specific licenses to legally operate a crypto exchange.
3. What is the best country to register a crypto exchange? Crypto-friendly countries include Estonia, Switzerland, Singapore, and Malta due to clear regulations and tax benefits.
4. Can I start an exchange using a white-label solution? Absolutely. White-label platforms are faster and cheaper to deploy but offer less customization.
5. How do crypto exchanges make money? Exchanges earn through transaction fees, withdrawal fees, listing fees, and sometimes even margin trading or staking services.
#CreateACryptocurrencyExchange#HowToCreateACryptocurrencyExchange#BuildYourOwnCryptocurrencyExchange#LaunchYourCryptocurrencyExchange#CryptocurrencyExchangeDevelopment#ShamlaTech#CryptoExchange#BlockchainSolutions#CryptoBusiness#CryptoDevelopment
0 notes
Text
Beyond Oil: The $600 Billion U.S.-Saudi Pact and Its Global Business Implications

In a defining moment for global economic cooperation, Saudi Arabia and the United States have unveiled a monumental investment and trade package exceeding $600 billion.
This unprecedented initiative marks a significant turning point in bilateral relations, reinforcing a long-standing partnership while opening the door to new sectors, broader collaboration, and expansive market opportunities.
For international businesses eyeing business incorporation in the KSA, this development offers a tangible roadmap to align with one of the most ambitious and well-capitalized economic partnerships of the decade.
Impact of The US – Saudi Initiatives on Global Businesses

1. The Legacy Behind the Deal
This announcement coincides with a symbolic milestone, the 80th anniversary of the historic 1945 meeting between U.S. President Franklin D. Roosevelt and Saudi Arabia’s founding monarch, King Abdulaziz Al Saud.
However, unlike past diplomatic gestures, this latest agreement is firmly rooted in economic pragmatism and shared strategic interests. In 2024 alone, bilateral trade between the two nations reached nearly $26 billion, with Saudi investments in the U.S. totaling close to $9.5 billion.
2. Strategic Sectors Driving the U.S.-Saudi Agenda
The investment framework highlights several high-potential sectors where international businesses can find immediate relevance and opportunity.
- Technology and AI
Saudi Arabia’s push into the digital frontier is gaining serious momentum. With DataVolt pledging $20 billion toward AI data centers and infrastructure in the U.S., and major tech players like Google, Oracle, and AMD collectively investing over $80 billion, the Kingdom is shaping the future of technology.
For global tech firms offering services in cloud security, software, AI infrastructure, and digital transformation, the opportunities in the Kingdom are multiplying. These developments create fertile ground for companies considering a presence in Saudi Arabia’s digital economy.
- Infrastructure and Engineering
Iconic developments like Qiddiya City and the King Salman International Airport - projects being managed by U.S. firms such as AECOM, Hill International, and Jacobs, showcase Saudi Arabia’s willingness to bring in international expertise.
Engineering firms, project consultants, and urban development specialists with a track record in smart city and sustainability projects are well-positioned to benefit from the Kingdom’s $2 billion investment in U.S. infrastructure expertise and its continued mega-project rollout.
- Defense and Aerospace
With over $140 billion allocated to defense cooperation, the two countries have reaffirmed their commitment to long-term security collaboration. However, the scope extends far beyond arms deals. Opportunities now include training programs, joint manufacturing, and tech transfers.
Companies specializing in cybersecurity, avionics, and tactical support systems may find success in business setup in Saudi Arabia and make entry points through partnerships with joint venture arrangements under the Kingdom’s localization initiatives.
- Healthcare and Biotech Manufacturing
A notable $5.8 billion investment in IV fluid production, driven by Shamekh IV Solutions, underscores Saudi Arabia’s intent to participate in global health supply chains.
Foreign pharmaceutical and medtech companies, particularly those considering Saudi Arabia as a manufacturing hub, will find incentives through economic cities and health innovation clusters. Local production, job creation, and research collaborations will be key to securing long-term contracts.
- Energy and Critical Minerals
A joint memorandum between the U.S. Department of Energy and Saudi Arabia’s Ministry of Industry and Mineral Resources points to shared interests in securing global critical mineral supply chains.
As the world shifts toward energy transition, Saudi Arabia is positioning itself as a powerhouse in minerals and rare earths, crucial for battery tech, EVs, and green infrastructure. Global mining, refining, and downstream processing companies have strong incentives to co-invest.
3. Strategic Steps for Foreign Companies
With doors opening wide, foreign businesses still need to take deliberate steps to enter and succeed in the Kingdom’s evolving regulatory and commercial landscape. Here are key considerations for establishing operations:
Choose the Right Legal Structure Whether opting for a Limited Liability Company (LLC), branch office, or joint venture, the structure must align with the business activity and local compliance laws under Saudi’s updated Companies Law.
Leverage Strategic Partnerships Collaborating with Saudi companies can streamline licensing, improve market access, and fulfill local content requirements, particularly in regulated sectors like defense, tech, and energy.
Commit to Localization Saudi Arabia’s Vision 2030 mandates are clear: job creation, knowledge transfer, and local value chains are priorities. Companies investing in training Saudi talent and building domestic capabilities will gain a competitive edge.
Engage Regulatory Authorities Early From licensing with MISA to sector-specific permits, early and consistent engagement with government stakeholders helps de-risk the market entry process.
4. A Structural Shift in Global Economic Alliances
While the political theater surrounding President Trump’s high-profile visit garners global attention, the deeper narrative is one of serious economic recalibration.
Saudi Arabia is actively expanding its economic alliances beyond oil diplomacy, leveraging sovereign funds, strategic investments, and mega-projects to reshape its economy into a global innovation hub.
The US, in turn, is solidifying its role not just as a defense ally but as a cornerstone partner in energy transition, high tech, and regional infrastructure development.The ripple effects of this partnership will likely influence global investment patterns and competitive alignments for years to come.
5. A Golden Era for Global Business in the Gulf
This $600 billion partnership package sends a clear message: Saudi Arabia is open for business, and it's ready to collaborate across a broad spectrum of industries.
The scale, diversity, and strategic intent behind the agreements reflect a deliberate pivot toward creating a globally integrated, innovation-driven economy.

For international companies exploring the Middle East, this is a call to action. Saudi Arabia’s market is not just large, it’s well-funded, increasingly open, and moving at speed. The time to engage is now.
0 notes
Text
Exascale Computing Market Size, Share, Analysis, Forecast, and Growth Trends to 2032: The Race to One Quintillion Calculations Per Second

The Exascale Computing Market was valued at USD 3.47 billion in 2023 and is expected to reach USD 29.58 billion by 2032, growing at a CAGR of 26.96% from 2024-2032.
The Exascale Computing Market is undergoing a profound transformation, unlocking unprecedented levels of computational performance. With the ability to process a billion billion (quintillion) calculations per second, exascale systems are enabling breakthroughs in climate modeling, genomics, advanced materials, and national security. Governments and tech giants are investing aggressively, fueling a race for exascale dominance that’s reshaping industries and redefining innovation timelines.
Exascale Computing Market revolutionary computing paradigm is being rapidly adopted across sectors seeking to harness the immense data-crunching potential. From predictive simulations to AI-powered discovery, exascale capabilities are enabling new frontiers in science, defense, and enterprise. Its impact is now expanding beyond research labs into commercial ecosystems, paving the way for smarter infrastructure, precision medicine, and real-time global analytics.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/6035
Market Keyplayers:
Hewlett Packard Enterprise (HPE) [HPE Cray EX235a, HPE Slingshot-11]
International Business Machines Corporation (IBM) [IBM Power System AC922, IBM Power System S922LC]
Intel Corporation [Intel Xeon Max 9470, Intel Max 1550]
NVIDIA Corporation [NVIDIA GH200 Superchip, NVIDIA Hopper H100]
Cray Inc. [Cray EX235a, Cray EX254n]
Fujitsu Limited [Fujitsu A64FX, Tofu interconnect D]
Advanced Micro Devices, Inc. (AMD) [AMD EPYC 64C 2.0GHz, AMD Instinct MI250X]
Lenovo Group Limited [Lenovo ThinkSystem SD650 V3, Lenovo ThinkSystem SR670 V2]
Atos SE [BullSequana XH3000, BullSequana XH2000]
NEC Corporation [SX-Aurora TSUBASA, NEC Vector Engine]
Dell Technologies [Dell EMC PowerEdge XE8545, Dell EMC PowerSwitch Z9332F]
Microsoft [Microsoft Azure NDv5, Microsoft Azure HPC Cache]
Amazon Web Services (AWS) [AWS Graviton3, AWS Nitro System]
Sugon [Sugon TC8600, Sugon I620-G30]
Google [Google TPU v4, Google Cloud HPC VM]
Alibaba Cloud [Alibaba Cloud ECS Bare Metal Instance, Alibaba Cloud HPC Cluster]
Market Analysis The exascale computing landscape is characterized by high-stakes R&D, global governmental collaborations, and fierce private sector competition. With countries like the U.S., China, and members of the EU launching national initiatives, the market is shaped by a mix of geopolitical strategy and cutting-edge technology. Key players are focusing on developing energy-efficient architectures, innovative software stacks, and seamless integration with artificial intelligence and machine learning platforms. Hardware giants are partnering with universities, startups, and defense organizations to accelerate deployments and overcome system-level challenges such as cooling, parallelism, and power consumption.
Market Trends
Surge in demand for high-performance computing in AI and deep learning
Integration of exascale systems with cloud and edge computing ecosystems
Government funding and national strategic investments on the rise
Development of heterogeneous computing systems (CPUs, GPUs, accelerators)
Emergence of quantum-ready hybrid systems alongside exascale architecture
Adoption across healthcare, aerospace, energy, and climate research sectors
Market Scope
Supercomputing for Scientific Discovery: Empowering real-time modeling and simulations at unprecedented speeds
Defense and Intelligence Advancements: Enhancing cybersecurity, encryption, and strategic simulations
Precision Healthcare Applications: Supporting drug discovery, genomics, and predictive diagnostics
Sustainable Energy Innovations: Enabling complex energy grid management and fusion research
Smart Cities and Infrastructure: Driving intelligent urban planning, disaster management, and IoT integration
As global industries shift toward data-driven decision-making, the market scope of exascale computing is expanding dramatically. Its capacity to manage and interpret massive datasets in real-time is making it essential for competitive advantage in a rapidly digitalizing world.
Market Forecast The trajectory of the exascale computing market points toward rapid scalability and broader accessibility. With increasing collaborations between public and private sectors, we can expect a new wave of deployments that bridge research and industry. The market is moving from proof-of-concept to full-scale operationalization, setting the stage for widespread adoption across diversified verticals. Upcoming innovations in chip design, power efficiency, and software ecosystems will further accelerate this trend, creating a fertile ground for startups and enterprise adoption alike.
Access Complete Report: https://www.snsinsider.com/reports/exascale-computing-market-6035
Conclusion Exascale computing is no longer a vision of the future—it is the powerhouse of today’s digital evolution. As industries align with the pace of computational innovation, those embracing exascale capabilities will lead the next wave of transformation. With its profound impact on science, security, and commerce, the exascale computing market is not just growing—it is redefining the very nature of progress. Businesses, researchers, and nations prepared to ride this wave will find themselves at the forefront of a smarter, faster, and more resilient future.
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
0 notes
Link
#AIRegulation#cybersecurity#deepfakelegislation#deepfakes#DigitalEthics#EU-AIAct#OpenAISora#syntheticmedia
0 notes
Text
10 Game-Changing Navy Current Affairs You Must Know in 2025
As the tides of geopolitics shift in 2025, the world's navies are undergoing transformative change. From cutting-edge technological advancements to evolving alliances and strategic postures, naval forces across the globe are playing an increasingly central role in shaping national security and global peacekeeping. In this special edition for TheVeza, we dive into the 10 essential navy current affairs for 2025 that every defense enthusiast, analyst, and global citizen should keep on their radar.

Whether it’s about who controls the Indo-Pacific or how navies are combating cyber threats at sea, the following updates reflect the changing face of maritime defense.
1. AUKUS Accelerates: Nuclear Submarine Pact Takes Shape
The AUKUS alliance between Australia, the UK, and the US has seen rapid developments in 2025. Australia’s plan to acquire nuclear-powered submarines under this trilateral pact is no longer a distant future. The first construction phase is underway, sparking debates on regional security dynamics in the Indo-Pacific. AUKUS is not just a tech-sharing pact—it’s a paradigm shift in strategic deterrence.
2. India’s INS Vishakhapatnam Leads Regional Power Surge
India has emerged as a maritime force to watch. With the commissioning of new guided missile destroyers like INS Vishakhapatnam, the Indian Navy has bolstered its blue-water capabilities. 2025 also marked joint naval exercises with the US, Japan, and France—demonstrating India's growing commitment to maritime diplomacy.
3. AI at Sea: Navies Go Smart
From autonomous surface vessels to predictive maintenance algorithms, Artificial Intelligence is revolutionizing naval operations. The U.S. Navy’s Project Overmatch and similar initiatives by NATO allies are focused on integrating AI to enhance command, control, and coordination in multi-domain operations.
4. China Launches Fujian-Class Carrier: A Superpower Signal
China’s Fujian-class aircraft carrier has officially entered sea trials in 2025. Featuring electromagnetic catapult systems and advanced radar, this carrier places China closer to achieving full maritime superpower status. Its deployment could dramatically alter power balances in the South China Sea and beyond.
5. Climate Change and Arctic Naval Posturing
With ice caps melting faster than predicted, the Arctic has become a new arena of naval focus. In 2025, several navies—including those of Canada, Russia, and Norway—have expanded their Arctic fleets. The race to secure northern trade routes and energy reserves has intensified.
6. Cybersecurity at Sea: New Naval Frontier
Modern warships are floating data centers, and in 2025, navies have doubled down on cybersecurity. The U.S. and UK navies have introduced “cybersecure” fleet frameworks, while NATO launched Operation Neptune Shield to counter suspected cyber threats targeting vessels and satellite comms.
7. Women Rising: Breaking Waves in Naval Leadership
2025 marks a milestone year for gender equality in navies worldwide. The Royal Navy appointed its first female Admiral, while the Indian Navy completed its first all-women deployment aboard a long-range patrol vessel. The tides are finally turning in favor of inclusive leadership at sea.
8. Green Fleets: Sustainable Naval Innovation
With carbon emissions under scrutiny, many navies are now investing in eco-friendly technology. Sweden’s Navy has unveiled its hybrid-electric patrol boats, while the U.S. is experimenting with biofuel-powered aircraft carriers. “Green defense” is becoming a strategic priority.
9. Global Naval Drills Reach Record Scale
From RIMPAC to Malabar, 2025 has seen the largest joint naval exercises in history. These drills emphasize interoperability, humanitarian readiness, and deterrence in contested zones. The message is clear: international naval cooperation is more vital than ever.
10. Maritime Drones Redefine Recon and Combat
Unmanned Surface and Underwater Vehicles (USVs and UUVs) are being actively deployed for recon and surveillance missions. The Israeli Navy recently used autonomous submarines to detect underwater mines, while the U.S. Navy’s Sea Hunter has completed transoceanic trials.
Final Thoughts
These 10 essential navy current affairs for 2025 reveal one undeniable truth: the sea is becoming as strategic as space. As great power rivalries deepen and technology transforms warfare, navies are no longer just protectors of coastlines—they are the vanguard of national and global resilience.
Whether you're a policy expert, a maritime enthusiast, or just someone trying to make sense of the world’s changing tides, staying informed about naval developments is more important than ever.
0 notes