#VMware Engine
Explore tagged Tumblr posts
Text
Intel And Google Cloud VMware Engine For Optimizing TCO

Google Cloud NEXT: Intel adds performance, flexibility, and security to Google Cloud VMware Engine for optimum TCO.
Intel and Google Cloud cooperate at NEXT 25. New and expanded Intel solutions will improve your total cost of ownership (TCO) by improving performance and workload flexibility.
Utilise Intel Xeon 6 processors' C4 virtual machine growth
Granite Rapids, the latest Intel Xeon 6 CPU, will join the C4 Machine Series. This expansion's capabilities, shape possibilities, and flexibility can improve the performance and scalability of customers' most essential applications. designed for industry-leading inference, databases, analytics, gaming, and real-time platform performance.
Google's latest local storage innovation, high-performance Titanium Local SSDs, will be offered in new virtual machine forms for C4 on Intel Xeon 6 CPUs. This cutting-edge storage technology speeds up workloads for I/O-intensive applications with better performance and up to 35% reduced local SSD latency.
Customers that want the maximum control and freedom may now use C4 bare metal instances. The new goods outperform bare metal predecessors from preceding generations by 35%.
Intel supports new, bigger C4 VM forms for greater flexibility and scalability. These new designs have the highest all-core turbo frequency of any Google Compute Engine virtual machine (VM) at 4.2 GHz, higher frequencies, greater cache sizes, and up to 2.2 TB of memory. This allows memory-bound or license-constrained applications like databases and data analytics to grow effectively.
Want a Memory-Optimized VM? Meet M4, the latest memory-optimized VM
Emerald Rapids is the first memory-optimized instance on 5th Gen Intel Xeon Scalable CPUs. The M4 virtual machine family, Google Cloud's latest memory-optimized instances, is designed for in-memory analytics. Compare to other top cloud solutions with similar architecture, M4 performs better.
M4's 13.3:1 and 26.6:1 Memory/Core ratios provide you additional flexibility to size database workloads. It supports 744GB to 3TB capacities. The RAM-to-vCPU ratio doubles with M4. M4 offers great options for companies looking to improve their memory-optimized infrastructure with new designs and a large virtual machine portfolio. The pricing performance of M4 instances is up to 65% better than M3.
Perfect SAP Support
Intel Xeon CPUs are ideal for SAP applications due to their speed and scalability. New memory-optimized M4 instances from Google Cloud are certified for SAP NetWeaver Application Server and in-memory SAP HANA workloads from 768GB to 3TB. In the M4, 5th Gen Intel Xeon Scalable processors provide 2.25x more SAPs than the previous iteration, improving performance. Intel's hardware-based security and data protection and M4's SAP workload flexibility help you reduce costs and maximise performance.
Z3-highmem and Z3.metal: New Storage Options for Industry-Specific VMs
Google Cloud's Z3 instance on 4th Gen Intel Xeon Scalable CPUs (codenamed Sapphire Rapids) adds 11 Z3-highmem Storage Optimised offerings with new smaller VM shapes from 3TB to 18TB Titanium SSD. This extension scales from 2 to 11 virtual machines to satisfy various storage needs and workloads.
Google Cloud, which optimises storage with the Titanium Offload System, includes Z3.metal and Z3 high-memory versions. Google Cloud's latest bare metal instance, Z3h-highmem-192-metal, has 72TB of Titanium SSD in a single compute engine unit. This form supports hyperconverged infrastructure, advanced monitoring, and custom hypervisors. Customers may develop comprehensive CPU monitoring or tightly controlled process execution with direct access to real server CPUs. Security, CI/CD, HPC, and financial services can handle workloads that cannot run on virtualised systems due to licensing and vendor support requirements.
Google Cloud VMware Engine Adds 18 Nodes that Change Everything
Cloud by Google VMware Engine is a fast way to migrate VMware estate to Google Cloud. Intel Xeon CPUs make VMware applications easy to run and move to the cloud. There are currently 26 node forms in VMware Engine v1 and v2, with 18 more added. You now have the most industry options to optimise TCO and capacity to meet business needs.
More Security with Intel TDX
Intel and Google Cloud provide cutting-edge security capabilities including Intel Trust Domain Extensions. Intel TDX encrypts currently running processes using a proprietary CPU function.
Two items now support Intel TDX:
Confidential GKE Nodes are Google Kubernetes Engines that protect memory data and defend against attacks via hardware. usually available in Q2 2025 with Intel TDX.
Process sensitive data in Intel TDX's safe, segregated environment.
Google Cloud VMware Engine?
Move VMware-based apps to Google Cloud quickly without changing tools, procedures, or apps. includes all hardware and VMware licenses needed for a VMware SDDC on Google Cloud.
Google Cloud VMware Engine Benefits
A fully integrated VMware experience
Intel provides all licenses, cloud services, and invoicing while simplifying VMware services and tools with unified identities, management, support, and monitoring, unlike other options.
Fast provisioning and scaling
Rapid provisioning with dynamic resource management and auto scaling lets you establish a private cloud in 30 minutes.
Use popular third-party cloud applications
Keep utilising your important cloud-based business software without changes. Google Cloud VMware Engine integrates top ISV database, storage, disaster recovery, and backup technologies.
Key characteristics of Google Cloud VMware Engine
Fast networking and high availability
VMware Engine uses Google Cloud's highly performant, scalable architecture with 99.99% availability and fully redundant networking up to 200 Gbps to meet your most demanding corporate applications.
Increase datastore capacity without compromising compute.
Google Filestore and Google Cloud NetApp Volumes are VMware Engine NFS datastores qualified by VMware. Add external NFS storage to vSAN storage for storage-intensive virtual machines to increase storage independently of compute. Use Filestore or Google Cloud VMware Engine to increase capacity-hungry VM storage from TBs to PBs and vSAN for low-latency storage.
Google Cloud integration experience
Fully access cutting-edge Google Cloud services. Native VPC networking allows private layer-3 access between Google Cloud services and VMware environments via Cloud VPN or Interconnect. Access control, identity, and billing unify the experience with other Google Cloud services.
Strong VMware ecosystems
Google Cloud Backup and Disaster Recovery provides centralised, application-consistent data protection. Third-party services and IT management solutions can supplement on-premises implementations. Intel, NetApp, Veeam, Zerto, Cohesity, and Dell Technologies collaborate to ease migration and business continuity. Review the VMware Engine ecosystem brief.
Google Cloud operations suite and VMware tools knowledge
If you use VMware tools, methods, and standards for on-premises workloads, the switch is straightforward. Monitor, debug, and optimise Google Cloud apps with the operations suite.
#technology#technews#govindhtech#news#technologynews#cloudcomputing#Google Cloud VMware Engine#Google Cloud VMware#Intel Google Cloud VMware Engine#Cloud VMware Engine#VMware Engine#C4 virtual machines#Z3-highmem and Z3.metal
0 notes
Text
Keep NUST's Network Running Smoothly: Network Administrator Opportunity! - March 2025
The National University of Science and Technology (NUST) is seeking a skilled and proactive Network Administrator to join their Information and Communication Technology Services (ICTS) Department! If you’re passionate about maintaining and optimizing network infrastructure, ensuring seamless operations, and providing excellent technical support, this is an excellent opportunity. About the…

View On WordPress
#art#Bulawayo Jobs#CCNA#Comp TIA#Computer Science Jobs#Electronic Engineering Jobs#Hot Zimbabwe Jobs#ICT Jobs#Information Technology Jobs#JNCIA#Job Opportunity#Linux#MCSA#MCSE#Network Administrator Jobs#Networking Jobs#NUST Jobs#open-source#Power Shell#python#RHCE#technology#University Jobs#VMware#Zimbabwe Jobs
0 notes
Text
How to Configure HSRP in Cisco Router: Step-by-Step Guide 2024
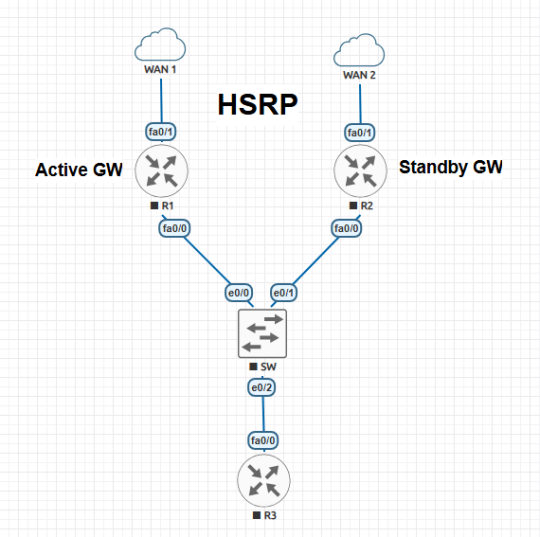
Are you looking to improve network reliability and minimize downtime? Hot Standby Router Protocol (HSRP) is a fantastic solution to ensure redundancy and seamless traffic flow in your Cisco networks. With HSRP, you can configure standby routers that automatically take over if the active router goes down, keeping your network stable and accessible.
I've put together a comprehensive, step-by-step guide on configuring HSRP on Cisco routers. Whether you're a beginner or have some experience, my guide covers everything you need to know—from initial setup to advanced configurations.
📖 Read the full guide here
Check it out to ensure your network's reliability and give your setup the failover advantage it needs for 2024!
#technology#virtualization#eve-ng#How to tutorials#tech blog#network engineer#system administrator#CCNA#CCNP#vmware#vmware workstation pro
0 notes
Text
youtube
High-level vmware overview.
#vmware#google cloud vmware engine#gcve#VMWare HCX#VMWare live migration#vmware cold migration#HCX Connector#Youtube
0 notes
Text

Want to learn the secret of #CloudNative #Development WITHOUT #Kubernetes ⁉
Then check out my session VMware Explore Las Vegas!! Register here
#developer#platform engineering#springboot#vmware#vmwaretanzu#kubernetes#spring#vmwareexplore#SpringOne#CloudFoundry
0 notes
Text
“The Fagin figure leading Elon Musk’s merry band of pubescent sovereignty pickpockets”

This week only, Barnes and Noble is offering 25% off pre-orders of my forthcoming novel Picks and Shovels. ENDS TODAY!.

While we truly live in an age of ascendant monsters who have hijacked our country, our economy, and our imaginations, there is one consolation: the small cohort of brilliant, driven writers who have these monsters' number, and will share it with us. Writers like Maureen Tkacik:
https://prospect.org/topics/maureen-tkacik/
Journalists like Wired's Vittoria Elliott, Leah Feiger, and Tim Marchman are absolutely crushing it when it comes to Musk's DOGE coup:
https://www.wired.com/author/vittoria-elliott/
And Nathan Tankus is doing incredible work all on his own, just blasting out scoop after scoop:
https://www.crisesnotes.com/
But for me, it was Tkacik – as usual – in the pages of The American Prospect who pulled it all together in a way that finally made it make sense, transforming the blitzkreig Muskian chaos into a recognizable playbook. While most of the coverage of Musk's wrecking crew has focused on the broccoli-haired Gen Z brownshirts who are wilding through the server rooms at giant, critical government agencies, Tkacik homes in on their boss, Tom Krause, whom she memorably dubs "the Fagin figure leading Elon Musk’s merry band of pubescent sovereignty pickpockets" (I told you she was a great writer!):
https://prospect.org/power/2025-02-06-private-equity-hatchet-man-leading-lost-boys-of-doge/
Krause is a private equity looter. He's the guy who basically invented the playbook for PE takeovers of large tech companies, from Broadcom to Citrix to VMWare, converting their businesses from selling things to renting them out, loading them up with junk fees, slashing quality, jacking up prices over and over, and firing everyone who was good at their jobs. He is a master enshittifier, an enshittification ninja.
Krause has an unerring instinct for making people miserable while making money. He oversaw the merger of Citrix and VMWare, creating a ghastly company called The Cloud Software Group, which sold remote working tools. Despite this, of his first official acts was to order all of his employees to stop working remotely. But then, after forcing his workers to drag their butts into work, move back across the country, etc, he reversed himself because he figured out he could sell off all of the company's office space for a tidy profit.
Krause canceled employee benefits, like thank you days for managers who pulled a lot of unpaid overtime, or bonuses for workers who upgraded their credentials. He also ended the company's practice of handing out swag as small gifts to workers, and then stiffed the company that made the swag, wontpaying a $437,574.97 invoice for all the tchotchkes the company had ordered. That's not the only supplier Krause stiffed: FinLync, a fintech company with a three-year contract with Krause's company, also had to sue to get paid.
Krause's isn't a canny operator who roots out waste: he's a guy who tears out all the wiring and then grudgingly restores the minimum needed to keep the machine running (no wonder Musk loves him, this is the Twitter playbook). As Tkacik reports, Krause fucked up the customer service and reliability systems that served Citrix's extremely large, corporate customers – the giant businesses that cut huge monthly checks to Citrix, whose CIOs received daily sales calls from his competitors.
Workers who serviced these customers, like disabled Air Force veteran David Morgan, who worked with big public agencies, were fired on one hour's notice, just before their stock options vested. The giant public agency customers he'd serviced later called him to complain that the only people they could get on the phone were subcontractors in Indian call centers who lacked the knowledge and authority to resolve their problems.
Last month, Citrix fired all of its customer support engineers. Citrix's military customers are being illegally routed to offshore customer support teams who are prohibited from working with the US military.
Citrix/VMWare isn't an exception. The carnage at these companies is indistinguishable from the wreck Krause made of Broadcom. In all these cases, Krause was parachuted in by private equity bosses, and he destroyed something useful to extract a giant, one-time profit, leaving behind a husk that no longer provides value to its customers or its employees.
This is the DOGE playbook. It's all about plunder: take something that was patiently, carefully built up over generations and burn it to the ground, warming yourself in the pyre, leaving nothing behind but ash. This is what private equity plunderers have been doing to the world's "advanced" economies since the Reagan years. They did it to airlines, family restaurants, funeral homes, dog groomers, toy stores, pharma, palliative care, dialysis, hospital beds, groceries, cars, and the internet.
Trump's a plunderer. He was elected by the plunderer class – like the crypto bros who want to run wild, transforming workers' carefully shepherded retirement savings into useless shitcoins, while the crypto bros run off with their perfectly cromulent "fiat" money. Musk is the apotheosis of this mindset, a guy who claims credit for other peoples' productive and useful businesses, replacing real engineering with financial engineering. Musk and Krause, they're like two peas in a pod.
That's why – according to anonymous DOGE employees cited by Tckacik – DOGE managers are hired for their capacity for cruelty: "The criteria for DOGE is how many you have fired, how much you enjoy firing people, and how little you care about the impact on peoples well being…No wonder Tom Krause was tapped for this. He’s their dream employee!"
The fact that Krause isn't well known outside of plunderer circles is absolutely a feature for him, not a bug. Scammers like Krause want to be admitted to polite society. This is why the Sacklers – the opioid crime family that kicked off the Oxy pandemic that's murdered more than 800,000 Americans so far – were so aggressive about keeping their association with their family business, Purdue Pharma, a secret. The Sacklers only wanted to be associated with the art galleries and museums they put their names over, and their lawyers threatened journalists for writing about their lives as billionaire drug pushers (I got one of those threats).
There's plenty of good reasons to be anonymous – if you're a whistleblower, say. But if you ever encounter a corporate executive who insists on anonymity, that's a wild danger sign. Take Pixsy, the scam "copyleft trolls" whose business depends on baiting people into making small errors when using images licensed under very early versions of the Creative Common licenses, and then threatening to sue them unless they pay hundreds or thousands of dollars:
https://pluralistic.net/2022/01/24/a-bug-in-early-creative-commons-licenses-has-enabled-a-new-breed-of-superpredator/
Kain Jones, the CEO of Pixsy, tried to threaten me under the EU's GDPR for revealing the names of the scammer on his payroll who sent me a legal threat, and the executive who ran the scam for his business (I say he tried to threaten me because I helped lobby for the GDPR and I know for a fact that this isn't a GDPR violation):
https://pluralistic.net/2022/02/13/an-open-letter-to-pixsy-ceo-kain-jones-who-keeps-sending-me-legal-threats/
These people understand that they are in the business of ripping people off, causing them grave and wholly unjust financial injury. They value their secrecy because they are in the business of making strangers righteously furious, and they understand that one of these strangers might just show up in their lives someday to confront them about their transgressions.
This is why Unitedhealthcare freaked out so hard about Luigi Mangione's assassination of CEO Brian Thompson – that's not how the game is supposed to be played. The people who sit in on executive row, destroying your lives, are supposed to be wholly insulated from the consequences of their actions. You're not supposed to know who they are, you're not supposed to be able to find them – of course.
But even more importantly, you're not supposed to be angry at them. They pose as mere software agents in an immortal colony organism called a Limited Liability Corporation, bound by the iron law of shareholder supremacy to destroy your life while getting very, very rich. It's not supposed to be personal. That's why Unitedhealthcare is threatening to sue a doctor who was yanked out of surgery on a cancer patient to be berated by a UHC rep for ordering a hospital stay for her patient:
https://gizmodo.com/unitedhealthcare-is-mad-about-in-luigi-we-trust-comments-under-a-doctors-viral-post-2000560543
UHC is angry that this surgeon, Austin's Dr Elisabeth Potter, went Tiktok-viral with her true story of how how chaotic and depraved and uncaring UHC is. UHC execs fear that Mangione made it personal, that he obliterated the accountability sink of the corporation and put the blame squarely where it belongs – on the (mostly) men at the top who make this call.
This is a point Adam Conover made in his latest Factually podcast, where he interviewed Propublica's T Christian Miller and Patrick Rucker:
https://www.youtube.com/watch?v=Y_5tDXRw8kg
Miller and Rucker published a blockbuster investigative report into Cigna's Evocore, a secret company that offers claims-denials as a service to America's biggest health insurers:
https://www.propublica.org/article/evicore-health-insurance-denials-cigna-unitedhealthcare-aetna-prior-authorizations
If you're the CEO of a health insurance company and you don't like how much you're paying out for MRIs or cancer treatment, you tell Evocore (which processes all your claim authorizations) and they turn a virtual dial that starts to reduce the number of MRIs your customers are allowed to have. This dial increases the likelihood that a claim or pre-authorization will be denied, which, in turn, makes doctors less willing to order them (even if they're medically necessary) and makes patients more likely to pay for them out of pocket.
Towards the end of the conversation, Miller and Rucker talk about how the rank-and-file people at an insurer don't get involved with the industry to murder people in order to enrich their shareholders. They genuinely want to help people. But executive row is different: those very wealthy people do believe their job is to kill people to save money, and get richer. Those people are personally to blame for the systemic problem. They are the ones who design and operate the system.
That's why naming the people who are personally responsible for these immoral, vicious acts is so important. That's why it's important that Wired and Propublica are unmasking the "pubescent sovereignty pickpockets" who are raiding the federal government under Krause's leadership:
https://projects.propublica.org/elon-musk-doge-tracker/
These people are committing grave crimes against the nation and its people. They should be known for this. It should follow them for the rest of their lives. It should be the lead in their obituaries. People who are introduced to them at parties should have a flash of recognition, hastily end the handshake, then turn on their heels and race to the bathroom to scrub their hands. For the rest of their lives.
Naming these people isn't enough to stop the plunder, but it helps. Yesterday, Marko Elez, the 25 year old avowed "eugenicist" who wanted to "normalize Indian hate" and could not be "[paid] to marry outside of my ethnicity," was shown the door. He's off the job. For the rest of his life, he will be the broccoli-haired brownshirt who got fired for his asinine, racist shitposting:
https://www.npr.org/2025/02/06/nx-s1-5289337/elon-musk-doge-treasury
After Krause's identity as the chief wrecker at DOGE was revealed, the brilliant Anna Merlan (author of Republic of Lies, the best book on conspiratorialism), wrote that "Now the whole country gets the experience of what it’s like when private equity buys the place you work":
https://bsky.app/profile/annamerlan.bsky.social/post/3lhepjkudcs2t
That's exactly it. We are witnessing a private equity-style plunder of the entire US government – of the USA itself. No one is better poised to write about this than Tkacik, because no one has private equity's number like Tkacik does:
https://pluralistic.net/2023/06/02/plunderers/#farben
Ironically, all this came down just as Trump announced that he was going to finally get rid of private equity's scammiest trick, the "carried interest" loophole that lets PE bosses (and, to a lesser extent, hedge fund managers) avoid billions in personal taxes:
https://archive.is/yKhvD
"Carried interest" has nothing to do with the interest rate – it's a law that was designed for 16th century sea captains who had an "interest" in the cargo they "carried":
https://pluralistic.net/2021/04/29/writers-must-be-paid/#carried-interest
Trump campaigned on killing this loophole in 2017, but Congress stopped him, after a lobbying blitz by the looter industry. It's possible that he genuinely wants to get rid of the carried interest loophole – he's nothing if not idiosyncratic, as the residents of Greenland can attest:
https://prospect.org/world/2025-02-07-letter-between-friendly-nations/
Even if he succeeds, looters and the "investor class" will get a huge giveaway under Trump, in the form of more tax giveaways and the dismantling of labor and environmental regulation. But it's far more likely that he won't succeed. Rather – as Yves Smith writes for Naked Capitalism – he'll do what he did with the Canada and Mexico tariffs: make a tiny, unimportant change and then lie and say he had done something revolutionary:
https://www.nakedcapitalism.com/2025/02/is-trump-serious-about-trying-to-close-the-private-equity-carried-interest-loophole.html
This has been a shitty month, and it's not gonna get better for a while. On my dark days, I worry that it won't get better during my lifetime. But at least we have people like Tkacik to chronicle it, explain it, put it in context. She's amazing, a whirlwind. The same day that her report on Krause dropped, the Prospect published another must-read piece by her, digging deep into Alex Jones's convoluted bankruptcy gambit:
https://prospect.org/justice/2025-02-06-crisis-actors-alex-jones-bankruptcy/
It lays bare the wild world of elite bankruptcy court, another critical conduit for protecting the immoral rich from their victims. The fact that Tkacik can explain both Krause and the elite bankruptcy system on the same day is beyond impressive.
We've got a lot of work ahead of ourselves. The people in charge of this system – whose names you must learn and never forget – aren't going to go easily. But at least we know who they are. We know what they're doing. We know how the scam works. It's not a flurry of incomprehensible actions – it's a playbook that killed Red Lobster, Toys R Us, and Sears. We don't have to follow that playbook.


If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2025/02/07/broccoli-hair-brownshirts/#shameless
#pluralistic#Maureen Tkacik#the american prospect#corporate sociopaths#pixsy#luigi mangione#propublica#doge#coup#elon musk#guillotine watch#adam conover#private equity#citrix#tom krause#looters#marko elez
401 notes
·
View notes
Text
a sort of general thing spinning off "static site generators kind of suck" is issues about ease of use vs philosophy vs productivity.
How many programmers do you know who want to make a game but refuse to use Unity or Godot or even like, löve2d because it's Ideologically Impure to use an existing engine, so they have 50 git repos with seven features bolted on to an SDL2 demo and no meaningful game design.
Part of why I don't like Static Site Generators is that they add a lot of friction. I'm writing this on my phone while waiting for a kettle to boil at work, and this ease of use is a big part of why I blog on Tumblr multiple times a day but the old SSG that hosted my website got a post every couple years.
Increasingly I'm happier to take shortcuts and borrow from other people in order to get Things Out The Door. I don't have to design/pattern/program/calculate everything myself. I care much more about end products.
I still have some philosophies I guess. I won't use VMware even if that means fighting with otherwise worse VM solutions. There are still plenty of things I enjoy designing and fabricating myself rather than buying or copying. For some people building the game engine is the fun part! But it's worth asking yourself whether that's you, or the person you wish you were.
I like embroidering and backstitching by hand. This doesn't mean I can't use components from the esp-idf components library.
See Also: How To Make Good Small Games, Do It Scared, etc.
45 notes
·
View notes
Text

Tools of the Trade for Learning Cybersecurity
I created this post for the Studyblr Masterpost Jam, check out the tag for more cool masterposts from folks in the studyblr community!
Cybersecurity professionals use a lot of different tools to get the job done. There are plenty of fancy and expensive tools that enterprise security teams use, but luckily there are also lots of brilliant people writing free and open-source software. In this post, I'm going to list some popular free tools that you can download right now to practice and learn with.
In my opinion, one of the most important tools you can learn how to use is a virtual machine. If you're not already familiar with Linux, this is a great way to learn. VMs are helpful for separating all your security tools from your everyday OS, isolating potentially malicious files, and just generally experimenting. You'll need to use something like VirtualBox or VMWare Workstation (Workstation Pro is now free for personal use, but they make you jump through hoops to download it).
Below is a list of some popular cybersecurity-focused Linux distributions that come with lots of tools pre-installed:
Kali is a popular distro that comes loaded with tools for penetration testing
REMnux is a distro built for malware analysis
honorable mention for FLARE-VM, which is not a VM on its own, but a set of scripts for setting up a malware analysis workstation & installing tools on a Windows VM.
SANS maintains several different distros that are used in their courses. You'll need to create an account to download them, but they're all free:
Slingshot is built for penetration testing
SIFT Workstation is a distro that comes with lots of tools for digital forensics
These distros can be kind of overwhelming if you don't know how to use most of the pre-installed software yet, so just starting with a regular Linux distribution and installing tools as you want to learn them is another good choice for learning.
Free Software
Wireshark: sniff packets and explore network protocols
Ghidra and the free version of IDA Pro are the top picks for reverse engineering
for digital forensics, check out Eric Zimmerman's tools - there are many different ones for exploring & analyzing different forensic artifacts
pwntools is a super useful Python library for solving binary exploitation CTF challenges
CyberChef is a tool that makes it easy to manipulate data - encryption & decryption, encoding & decoding, formatting, conversions… CyberChef gives you a lot to work with (and there's a web version - no installation required!).
Burp Suite is a handy tool for web security testing that has a free community edition
Metasploit is a popular penetration testing framework, check out Metasploitable if you want a target to practice with
SANS also has a list of free tools that's worth checking out.
Programming Languages
Knowing how to write code isn't a hard requirement for learning cybersecurity, but it's incredibly useful. Any programming language will do, especially since learning one will make it easy to pick up others, but these are some common ones that security folks use:
Python is quick to write, easy to learn, and since it's so popular, there are lots of helpful libraries out there.
PowerShell is useful for automating things in the Windows world. It's built on .NET, so you can practically dip into writing C# if you need a bit more power.
Go is a relatively new language, but it's popular and there are some security tools written in it.
Rust is another new-ish language that's designed for memory safety and it has a wonderful community. There's a bit of a steep learning curve, but learning Rust makes you understand how memory bugs work and I think that's neat.
If you want to get into reverse engineering or malware analysis, you'll want to have a good grasp of C and C++.
Other Tools for Cybersecurity
There are lots of things you'll need that aren't specific to cybersecurity, like:
a good system for taking notes, whether that's pen & paper or software-based. I recommend using something that lets you work in plain text or close to it.
general command line familiarity + basic knowledge of CLI text editors (nano is great, but what if you have to work with a system that only has vi?)
familiarity with git and docker will be helpful
There are countless scripts and programs out there, but the most important thing is understanding what your tools do and how they work. There is no magic "hack this system" or "solve this forensics case" button. Tools are great for speeding up the process, but you have to know what the process is. Definitely take some time to learn how to use them, but don't base your entire understanding of security on code that someone else wrote. That's how you end up as a "script kiddie", and your skills and knowledge will be limited.
Feel free to send me an ask if you have questions about any specific tool or something you found that I haven't listed. I have approximate knowledge of many things, and if I don't have an answer I can at least help point you in the right direction.
#studyblrmasterpostjam#studyblr#masterpost#cybersecurity#late post bc I was busy yesterday oops lol#also this post is nearly a thousand words#apparently I am incapable of being succinct lmao
22 notes
·
View notes
Text
Ransomware Attacks Target VMware ESXi Infrastructure Following Interesting Pattern

Cybersecurity firm Sygnia has shed light on a concerning trend where ransomware attacks targeting VMware ESXi infrastructure follow a well-established pattern, regardless of the specific file-encrypting malware deployed. According to the Israeli company's incident response efforts involving various ransomware families, these attacks adhere to a similar sequence of actions.
The Attack Sequence
- Initial access is obtained through phishing attacks, malicious file downloads, or exploitation of known vulnerabilities in internet-facing assets. - Attackers escalate their privileges to obtain credentials for ESXi hosts or vCenter using brute-force attacks or other methods. - Access to the virtualization infrastructure is validated, and the ransomware is deployed. - Backup systems are deleted, encrypted, or passwords are changed to complicate recovery efforts. - Data is exfiltrated to external locations such as Mega.io, Dropbox, or attacker-controlled hosting services. - The ransomware initiates execution and encrypts the "/vmfs/volumes" folder of the ESXi filesystem. - The ransomware propagates to non-virtualized servers and workstations, widening the scope of the attack.

Mitigation Strategies
To mitigate the risks posed by such threats, organizations are advised to implement the following measures: - Ensure adequate monitoring and logging are in place - Create robust backup mechanisms - Enforce strong authentication measures - Harden the environment - Implement network restrictions to prevent lateral movement
Malvertising Campaign Distributing Trojanized Installers
In a related development, cybersecurity company Rapid7 has warned of an ongoing campaign since early March 2024 that employs malicious ads on commonly used search engines to distribute infected installers for WinSCP and PuTTY via typosquatted domains. These counterfeit installers act as a conduit to drop the Sliver post-exploitation toolkit, which is then used to deliver more payloads, including a Cobalt Strike Beacon leveraged for ransomware deployment. This activity shares tactical overlaps with prior BlackCat ransomware attacks that have used malvertising as an initial access vector, disproportionately affecting members of IT teams who are most likely to download the infected files.
New Ransomware Families and Global Trends
The cybersecurity landscape has witnessed the emergence of new ransomware families like Beast, MorLock, Synapse, and Trinity. The MorLock group has extensively targeted Russian companies, encrypting files without first exfiltrating them and demanding substantial ransoms. According to NCC Group's data, global ransomware attacks in April 2024 registered a 15% decline from the previous month, with LockBit's reign as the top threat actor ending in the aftermath of a sweeping law enforcement takedown earlier this year. The turbulence in the ransomware scene has been complemented by cyber criminals advertising hidden Virtual Network Computing (hVNC) and remote access services like Pandora and TMChecker, which could be utilized for data exfiltration, deploying additional malware, and facilitating ransomware attacks. Read the full article
4 notes
·
View notes
Text




Order Now 60% Off
Nespresso Original Line Coffee Pod with 1 Storage Drawer Holder, 50 Capsule Capacity, Black
Available at a lower price from other sellers that may not offer free Prime shipping. Color Black Material Plastic Brand Amazon Basics Product Dimensions 14.9"D x 9.1"W x 2"H Number of Drawers 1
#amazon fba,#amazon,amazon sale,#how to sell on amazon,#amazon fba for beginners,#amazon next sale 2024,#amazon fba tutorial,selling on amazon,#amazon fba step by step,#sell on amazon,how to sell on amazon fba,#upcoming sale on flipkart and amazon,#amazon sale 2023,amazon new sale,#amazon returns,how to sell on amazon for beginners,#alibaba to amazon,next sale on amazon,#how to start selling on amazon,#amazon summer sale 2023,#amazon great indian sale #private ai,#chatgpt offline,#vmware,#nvidia,#fine-tuning ai,#artificial intelligence,#privacy in technology,#zombie apocalypse survival,#vmware private ai foundation,nvidia ai enterprise,wsl installation,llms,deep learning vms,custom ai solutions,#gpus in ai,#rag technology,#private gpt setup,#intel partnership,#ibm watson,#vmware cloud foundation,#networkchuck tutorials,#future of tech,#ai without internet,#data privacy,#because science,#engineering #best product from every brand at sephora,#best hair product,#best product management books,#best product development books,#product research,#best products,best product books,#best trim product,#amazon best products,#best products for eyes,#best product landing page,#best product landing pages,#best matte hair product,#best at sephora,#best way to sell a product,#hair product,#best products for eye bags,#best product development tips,#best products for puffy eyes
#viralpost#viral news#viral products#trendingnow#trendingtopics#trending#viral#amazon#amazing body#affiliate#sales#business#networking#strategy#online shopping#online shop uk#online shops offer#online store#online business#shopping state
3 notes
·
View notes
Text
I'm gonna be honest, professionalism is a disease. Sometimes you just need the words to bring reality to someone who won't listen and they can't start with per my last e-mail.
There's a specific site at my job that drives me nuts because they just don't listen to instructions carefully and this problem is endemic across their entire management pool. They'll also constantly cross lines and do shit like call me on teams without warning because they *know* I'm good at my job and I'll fix the damn problem if I can, but sometimes I'm in the middle of doing other shit and I can't be pissed to fuck around for fifteen minutes to reset johnny dipshit's RSA because he chronically can't remember a 4 digit number.
So this week was a gigantic headache because small minded upper management made an absolutely awful decision and has set a 90 day ticking time bomb on our password policy due to a delayed overreaction from a security breach that happened in October, they forcibly reset every call centers password and unfortunately because of more dumb shortsightedness they specifically decided to flag it for VMware logins. VMware is not directly attached to our primary IDP so it caused a ton of IDP flowback issues usually locking people out of random applications on other subdomains and often locking people out of active directory login entirely.
I've had to basically route a large portion of this intake for this specific issue and it's been mostly resolved as everyone who got flagged in these domains has reset their shit and had a temporary password issued and their accounts synced for proper primary IDP flow down.
I got a guy today however who managed to dodge this issue and I told him I'd have to route his issue to another team because someone already picked up this ticket, but genius middle management refuses to let people be unproductive for a bit and he's in my dms telling me to reset chuckledick's password again.
I can't tell him he's a technological hazard and that his mother should pound sand on the beach that makes you old and block him because that's ~unprofessional~ so instead I tell him this is a bad idea because the department under me already reset his shit and synced it from the jump server and this will reset it back to square one and probably break any other access that was working along the way. I know what the issue is and that it's elsewhere but I'm a network engineer so I *shouldn't* modify this person's OUs if it's already someone else's ticket. However he's not taking my polite "No" for an answer so I reset the person's acct and issue a temporary password, he tells me he'll be back in 5 minutes. It takes him 25, meanwhile I'm regularly refreshing the domain that has NT logins registered on it and see that the password update flag doesnt reset, meaning chuckledick cant log in.
I fuckin set myself to busy so these people will stop bothering me and leave him a message before he can even return: "I see user was unable to log in meaning this issue is IDP domain flow down related like I had initially diagnosed, in the future please refrain from wasting (network dept name)'s time and arguing with us over tickets already assigned to the correct department. I hope you take this lesson to heart." Which is about the politest way I can tell this person he is a fucking fool and I hate working with him.
2 notes
·
View notes
Text
Cloud Cost Optimization Strategies Every CTO Should Know in 2025
As organizations scale in the cloud, one challenge becomes increasingly clear: managing and optimizing cloud costs. With the promise of scalability and flexibility comes the risk of unexpected expenses, idle resources, and inefficient spending.
In 2025, cloud cost optimization is no longer just a financial concern—it’s a strategic imperative for CTOs aiming to drive innovation without draining budgets. In this blog, we’ll explore proven strategies every CTO should know to control cloud expenses while maintaining performance and agility.
🧾 The Cost Optimization Challenge in the Cloud
The cloud offers a pay-as-you-go model, which is ideal—if you’re disciplined. However, most companies face challenges like:
Overprovisioned virtual machines
Unused storage or idle databases
Redundant services running in the background
Poor visibility into cloud usage across teams
Limited automation of cost governance
These inefficiencies lead to cloud waste, often consuming 30–40% of a company’s monthly cloud budget.
🛠️ Core Strategies for Cloud Cost Optimization
1. 📉 Right-Sizing Resources
Regularly analyze actual usage of compute and storage resources to downsize over-provisioned assets. Choose instance types or container configurations that match your workload’s true needs.
2. ⏱️ Use Auto-Scaling and Scheduling
Enable auto-scaling to adjust resource allocation based on demand. Implement scheduling scripts or policies to shut down dev/test environments during off-hours.
3. 📦 Leverage Reserved Instances and Savings Plans
For predictable workloads, commit to Reserved Instances (RIs) or Savings Plans. These options can reduce costs by up to 70% compared to on-demand pricing.
4. 🚫 Eliminate Orphaned Resources
Track down unused volumes, unattached IPs, idle load balancers, or stopped instances that still incur charges.
5. 💼 Centralized Cost Management
Use tools like AWS Cost Explorer, Azure Cost Management, or Google’s Billing Reports to monitor, allocate, and forecast cloud spend. Consolidate billing across accounts for better control.
🔐 Governance and Cost Policies
✅ Tag Everything
Apply consistent tagging (e.g., environment:dev, owner:teamA) to group and track costs effectively.
✅ Set Budgets and Alerts
Configure budget thresholds and set up alerts when approaching limits. Enable anomaly detection for cost spikes.
✅ Enforce Role-Based Access Control (RBAC)
Restrict who can provision expensive resources. Apply cost guardrails via service control policies (SCPs).
✅ Use Cost Allocation Reports
Assign and report costs by team, application, or business unit to drive accountability.
📊 Tools to Empower Cost Optimization
Here are some top tools every CTO should consider integrating:
Salzen Cloud: Offers unified dashboards, usage insights, and AI-based optimization recommendations
CloudHealth by VMware: Cost governance, forecasting, and optimization in multi-cloud setups
Apptio Cloudability: Cloud financial management platform for enterprise-level cost allocation
Kubecost: Cost visibility and insights for Kubernetes environments
AWS Trusted Advisor / Azure Advisor / GCP Recommender: Native cloud tools to recommend cost-saving actions
🧠 Advanced Tips for 2025
🔁 Adopt FinOps Culture
Build a cross-functional team (engineering + finance + ops) to drive cloud financial accountability. Make cost discussions part of sprint planning and retrospectives.
☁️ Optimize Multi-Cloud and Hybrid Environments
Use abstraction and management layers to compare pricing models and shift workloads to more cost-effective providers.
🔄 Automate with Infrastructure as Code (IaC)
Define auto-scaling, backup, and shutdown schedules in code. Automation reduces human error and enforces consistency.
🚀 How Salzen Cloud Helps
At Salzen Cloud, we help CTOs and engineering leaders:
Monitor multi-cloud usage in real-time
Identify idle resources and right-size infrastructure
Predict usage trends with AI/ML-based models
Set cost thresholds and auto-trigger alerts
Automate cost-saving actions through CI/CD pipelines and Infrastructure as Code
With Salzen Cloud, optimization is not a one-time event—it’s a continuous, intelligent process integrated into every stage of the cloud lifecycle.
✅ Final Thoughts
Cloud cost optimization is not just about cutting expenses—it's about maximizing value. With the right tools, practices, and mindset, CTOs can strike the perfect balance between performance, scalability, and efficiency.
In 2025 and beyond, the most successful cloud leaders will be those who innovate smartly—without overspending.
0 notes
Text
How does cloud computing enable faster business scaling for me
Cloud Computing Market was valued at USD 605.3 billion in 2023 and is expected to reach USD 2619.2 billion by 2032, growing at a CAGR of 17.7% from 2024-2032.
Cloud Computing Market is witnessing unprecedented growth as businesses across sectors rapidly adopt digital infrastructure to boost agility, scalability, and cost-efficiency. From small startups to global enterprises, organizations are shifting workloads to the cloud to enhance productivity, improve collaboration, and ensure business continuity.
U.S. Market Leads Cloud Innovation with Expanding Enterprise Adoption
Cloud Computing Market continues to expand as emerging technologies such as AI, machine learning, and edge computing become more integrated into enterprise strategies. With increased reliance on hybrid and multi-cloud environments, providers are innovating faster to deliver seamless, secure, and flexible solutions.
Get Sample Copy of This Report: https://www.snsinsider.com/sample-request/2779
Market Keyplayers:
Amazon Web Services (AWS) (EC2, S3)
Microsoft (Azure Virtual Machines, Azure Storage)
Google Cloud (Google Compute Engine, Google Kubernetes Engine)
IBM (IBM Cloud Private, IBM Cloud Kubernetes Service)
Oracle (Oracle Cloud Infrastructure, Oracle Autonomous Database)
Alibaba Cloud (Elastic Compute Service, Object Storage Service)
Salesforce (Salesforce Sales Cloud, Salesforce Service Cloud)
SAP (SAP HANA Enterprise Cloud, SAP Business Technology Platform)
VMware (VMware vCloud, VMware Cloud on AWS)
Rackspace (Rackspace Cloud Servers, Rackspace Cloud Files)
Dell Technologies (VMware Cloud Foundation, Virtustream Enterprise Cloud)
Hewlett Packard Enterprise (HPE) (HPE GreenLake, HPE Helion)
Tencent Cloud (Tencent Cloud Compute, Tencent Cloud Object Storage)
Adobe (Adobe Creative Cloud, Adobe Document Cloud)
Red Hat (OpenShift, Red Hat Cloud Infrastructure)
Cisco Systems (Cisco Webex Cloud, Cisco Intersight)
Fujitsu (Fujitsu Cloud Service K5, Fujitsu Cloud IaaS Trusted Public S5)
Huawei (Huawei Cloud ECS, Huawei Cloud OBS)
Workday (Workday Human Capital Management, Workday Financial Management)
Market Analysis
The global cloud computing landscape is being redefined by increasing demand for on-demand IT services, software-as-a-service (SaaS) platforms, and data-intensive workloads. In the U.S., cloud adoption is accelerating due to widespread digital transformation initiatives and investments in advanced technologies. Europe is also experiencing significant growth, driven by data sovereignty concerns and regulatory frameworks like GDPR, which are encouraging localized cloud infrastructure development.
Market Trends
Surge in hybrid and multi-cloud deployments
Integration of AI and ML for intelligent workload management
Growth of edge computing reducing latency in critical applications
Expansion of industry-specific cloud solutions (e.g., healthcare, finance)
Emphasis on cybersecurity and compliance-ready infrastructure
Rise of serverless computing for agile development and scalability
Sustainability focus driving adoption of green data centers
Market Scope
Cloud computing's scope spans nearly every industry, supporting digital-first strategies, automation, and real-time analytics. Organizations are leveraging cloud platforms not just for storage, but as a foundation for innovation, resilience, and global expansion.
On-demand infrastructure scaling for startups and enterprises
Support for remote workforces with secure virtual environments
Cross-border collaboration powered by cloud-native tools
Cloud-based disaster recovery solutions
AI-as-a-Service and Data-as-a-Service models gaining traction
Regulatory-compliant cloud hosting driving European market growth
Forecast Outlook
The future of the Cloud Computing Market is driven by relentless demand for agile digital infrastructure. As cloud-native technologies become standard in enterprise IT strategies, both U.S. and European markets are expected to play pivotal roles. Advanced cloud security, integrated data services, and sustainability-focused infrastructure will be at the forefront of upcoming innovations. Strategic alliances between cloud providers and industry players will further fuel momentum, especially in AI, 5G, and IoT-powered environments.
Access Complete Report: https://www.snsinsider.com/reports/cloud-computing-market-2779
Conclusion
As the digital economy accelerates, the Cloud Computing Market stands at the core of modern enterprise transformation. It empowers businesses with the tools to scale intelligently, respond to market shifts rapidly, and innovate without limits. For leaders across the U.S. and Europe, embracing cloud technology is no longer optional—it's the strategic engine driving competitive advantage and sustainable growth.
Related Reports:
U.S.A drives innovation as Data Monetization Market gains momentum
U.S.A Wealth Management Platform Market Poised for Strategic Digital Transformation
U.S.A Trade Management Software Market Sees Surge Amid Cross-Border Trade Expansion
About Us:
SNS Insider is one of the leading market research and consulting agencies that dominates the market research industry globally. Our company's aim is to give clients the knowledge they require in order to function in changing circumstances. In order to give you current, accurate market data, consumer insights, and opinions so that you can make decisions with confidence, we employ a variety of techniques, including surveys, video talks, and focus groups around the world.
Contact Us:
Jagney Dave - Vice President of Client Engagement
Phone: +1-315 636 4242 (US) | +44- 20 3290 5010 (UK)
Mail us: [email protected]
0 notes
Text
Kubernetes Cluster Management at Scale: Challenges and Solutions
As Kubernetes has become the cornerstone of modern cloud-native infrastructure, managing it at scale is a growing challenge for enterprises. While Kubernetes excels in orchestrating containers efficiently, managing multiple clusters across teams, environments, and regions presents a new level of operational complexity.
In this blog, we’ll explore the key challenges of Kubernetes cluster management at scale and offer actionable solutions, tools, and best practices to help engineering teams build scalable, secure, and maintainable Kubernetes environments.
Why Scaling Kubernetes Is Challenging
Kubernetes is designed for scalability—but only when implemented with foresight. As organizations expand from a single cluster to dozens or even hundreds, they encounter several operational hurdles.
Key Challenges:
1. Operational Overhead
Maintaining multiple clusters means managing upgrades, backups, security patches, and resource optimization—multiplied by every environment (dev, staging, prod). Without centralized tooling, this overhead can spiral quickly.
2. Configuration Drift
Cluster configurations often diverge over time, causing inconsistent behavior, deployment errors, or compliance risks. Manual updates make it difficult to maintain consistency.
3. Observability and Monitoring
Standard logging and monitoring solutions often fail to scale with the ephemeral and dynamic nature of containers. Observability becomes noisy and fragmented without standardization.
4. Resource Isolation and Multi-Tenancy
Balancing shared infrastructure with security and performance for different teams or business units is tricky. Kubernetes namespaces alone may not provide sufficient isolation.
5. Security and Policy Enforcement
Enforcing consistent RBAC policies, network segmentation, and compliance rules across multiple clusters can lead to blind spots and misconfigurations.
Best Practices and Scalable Solutions
To manage Kubernetes at scale effectively, enterprises need a layered, automation-driven strategy. Here are the key components:
1. GitOps for Declarative Infrastructure Management
GitOps leverages Git as the source of truth for infrastructure and application deployment. With tools like ArgoCD or Flux, you can:
Apply consistent configurations across clusters.
Automatically detect and rollback configuration drifts.
Audit all changes through Git commit history.
Benefits:
· Immutable infrastructure
· Easier rollbacks
· Team collaboration and visibility
2. Centralized Cluster Management Platforms
Use centralized control planes to manage the lifecycle of multiple clusters. Popular tools include:
Rancher – Simplified Kubernetes management with RBAC and policy controls.
Red Hat OpenShift – Enterprise-grade PaaS built on Kubernetes.
VMware Tanzu Mission Control – Unified policy and lifecycle management.
Google Anthos / Azure Arc / Amazon EKS Anywhere – Cloud-native solutions with hybrid/multi-cloud support.
Benefits:
· Unified view of all clusters
· Role-based access control (RBAC)
· Policy enforcement at scale
3. Standardization with Helm, Kustomize, and CRDs
Avoid bespoke configurations per cluster. Use templating and overlays:
Helm: Define and deploy repeatable Kubernetes manifests.
Kustomize: Customize raw YAMLs without forking.
Custom Resource Definitions (CRDs): Extend Kubernetes API to include enterprise-specific configurations.
Pro Tip: Store and manage these configurations in Git repositories following GitOps practices.
4. Scalable Observability Stack
Deploy a centralized observability solution to maintain visibility across environments.
Prometheus + Thanos: For multi-cluster metrics aggregation.
Grafana: For dashboards and alerting.
Loki or ELK Stack: For log aggregation.
Jaeger or OpenTelemetry: For tracing and performance monitoring.
Benefits:
· Cluster health transparency
· Proactive issue detection
· Developer fliendly insights
5. Policy-as-Code and Security Automation
Enforce security and compliance policies consistently:
OPA + Gatekeeper: Define and enforce security policies (e.g., restrict container images, enforce labels).
Kyverno: Kubernetes-native policy engine for validation and mutation.
Falco: Real-time runtime security monitoring.
Kube-bench: Run CIS Kubernetes benchmark checks automatically.
Security Tip: Regularly scan cluster and workloads using tools like Trivy, Kube-hunter, or Aqua Security.
6. Autoscaling and Cost Optimization
To avoid resource wastage or service degradation:
Horizontal Pod Autoscaler (HPA) – Auto-scales pods based on metrics.
Vertical Pod Autoscaler (VPA) – Adjusts container resources.
Cluster Autoscaler – Scales nodes up/down based on workload.
Karpenter (AWS) – Next-gen open-source autoscaler with rapid provisioning.
Conclusion
As Kubernetes adoption matures, organizations must rethink their management strategy to accommodate growth, reliability, and governance. The transition from a handful of clusters to enterprise-wide Kubernetes infrastructure requires automation, observability, and strong policy enforcement.
By adopting GitOps, centralized control planes, standardized templates, and automated policy tools, enterprises can achieve Kubernetes cluster management at scale—without compromising on security, reliability, or developer velocity.
0 notes
Text
I have seen a lot of mentions about "alternatives" to #kubernetes lately... Just here to remind you about #CloudFoundry and #VMwareTanzu Application Service, running apps at scale since 2011 😎
#developer#vmwaretanzu#vmware#cloud computing#platform engineering#platform#springboot#java#kubernetes#k8s#open source
1 note
·
View note
Text
A Complete Guide to Cloud Computing Master’s Degrees in France, Germany, and Ireland
The digital world is changing because of cloud computing. It's at the centre of today's tech-driven world, from streaming services and mobile apps to AI and data analytics. The need for skilled workers is skyrocketing as businesses quickly move to cloud infrastructure. And where better to learn these skills that are in high demand than in Europe?
France, Germany, and Ireland are now the best places for international students who want to specialise in cloud computing to study. These countries are great places to start your cloud-focused career because they have strong academic programs, access to global tech companies, and great job opportunities after you finish school.
We'll show you everything you need to know about getting a Master's degree in Cloud Computing in these three countries in this guide. We'll talk about why they're a great choice, the best schools to go to, and what you can do after you graduate.
Why Pursue Cloud Computing in Europe?
Europe is now a hotbed of new technology. Cloud computing is a top priority for governments all over Europe as they work on digital transformation. France is making tech hubs like Station F in Paris. Germany is ahead of the rest of the world when it comes to digitising industry. Ireland is home to the European headquarters of the largest cloud service providers.
You can find a lot of master's programs in tech that are taught entirely in English, even in countries where English isn't the first language, like France and Germany. This makes it possible for international students to get a good education without having to worry about language problems.
All three countries have a lot of job opportunities after you finish your studies. Most graduates have 18 to 24 months to find a job, which gives you plenty of time to get into cloud development, security, DevOps, and other fields.
Studying Cloud Computing in France
The number of international tech students choosing France is increasing. Light fees, excellent research results and worldwide cooperation have made it the ideal base for cloud-related studies.
At the Institut Polytechnique de Paris, the MSc in Cloud and Network Infrastructures (provided by EIT Digital) lets students study and apply what they have learned in industry projects. Within two years, students become familiar with cloud systems, mobile networks and virtualization by learning at several European universities.
EPITA School of Engineering and Computer Science has developed a MSc in Cloud Computing and Virtualisation that focuses on gaining practical skills in distributed technologies, security for cloud environments and important virtualization tools like VMware and Docker. The teaching is closely linked to what is used in the real world.
A research-focused approach is taken in the MSc in Computer Science (Cloud and Network Security) offered by the University of Lille. Students engage in both cloud infrastructure and security topics such as cryptography, secure protocols and intrusion detection which helps them succeed in industry and PhD programs.
With cloud companies OVHCloud and Thales based in France, graduates have plenty of employment opportunities as a Cloud Architect, DevOps Engineer or Cloud Security Analyst.
Studying Cloud Computing in Germany
Long ago, Germany became well-known for its top-level engineering and technical education. Also, Germany is emerging as a major part of Europe’s digital transformation which makes it an ideal choice for cloud studies.
People looking for a master’s degree in Informatics can find a well-regarded program with a Cloud Computing track at TUM. This course is especially suitable for students wishing to study distributed systems and scalable system design supported by up-to-date research and labs.
RWTH Aachen University has a cloud focus for its MSc in Computer Science program. Students develop strong understanding and skills in distributed systems, scalable computing and high-performance networks which are vital for cloud computing.
In the MSc in Software Engineering and Management at the University of Stuttgart, students have the option to focus on Cloud Technology. This two-year program provides a mix of theoretical learning and tasks in cloud systems, agile teamwork and the use of Kubernetes and other tools.
Graduates in Germany typically find work as Cloud Infrastructure Engineers, Cloud Project Managers or Systems Administrators in tech hubs such as Berlin, Munich and Frankfurt due to the healthy job market in Germany.
Studying Cloud Computing in Ireland
Ireland is quickly becoming Europe's tech centre. Almost every big tech company, from Microsoft to Google, has a presence there, making it a great place for IT workers. This is one of the best places to start a career in cloud computing.
Dublin City University (DCU) has a one-year MSc in Computing with a Cloud Computing stream. This program gives you a full picture of cloud technologies, such as DevOps, cloud-native development, and scalable architectures. It does this through strong ties to the industry and learning through projects.
The National College of Ireland (NCI) offers an MSc in Cloud Computing that focusses on using tools like AWS, Azure, and Google Cloud in real life. Students get an edge in the Irish and global job markets by working on real projects and doing internships.
The MSc in Computer Science with a focus on Cloud and Network Technologies at Technological University Dublin (TU Dublin) is for people who want to be technical leaders. Students learn about enterprise networks, cloud orchestration, virtualisation, and distributed systems.
Ireland has a booming tech industry, which means there are good jobs at companies like Amazon, IBM, and Accenture. Cloud Software Developer, Solutions Architect, and Site Reliability Engineer are some of the jobs that graduates often get.
Are you looking for the best study abroad consultants in Kochi
#study abroad#study in uk#study abroad consultants#study in australia#study in germany#study in ireland#study blog
0 notes