#Web Monitoring Software
Text

instagram: cheri.png
#pov I turn on my computer to work and upload on tumblr#I’ve been on a hardware roll#and I’m supposed to be software girl lol#crt monitor#windows xp#cybercore#old internet#old web#y2k#00s#cyber y2k#2000s#moodboard#tech#cyber core#old computers#retro tech#techcore#desk setup#tech blog#nostalgia#old windows#old microsoft#microsoft#nostalgiacore
345 notes
·
View notes
Text

Revolutionizing Project Management with the Project Monitoring Portal
In the dynamic world of project management, staying on top of every aspect of a project is crucial for success. The Project Monitoring Portal, powered by PPMS Software, offers a comprehensive solution for managing the entire project lifecycle with unparalleled efficiency and precision. From smarter planning to real-time progress tracking, this web-based application is designed to streamline project management processes, ensuring projects are completed on time and within budget.
https://www.cyberswift.com/in/products/csr-management-software
#it based project monitoring system#project monitoring system#progress monitoring system#work progress monitoring system#project progress monitoring system#web based project monitoring system#project monitoring software#best project tracking softask tracking system#engineering project tracking software#project tracking system#project management software with time tracking#construction project tracking software#tool tracking system for construction#time and project tracking software#simple project tracking software#project management tool with time tracking
0 notes
Text
Navigation Buoys GPS Tracking and Monitoring Solution
GPS tracking web application system for navigating, monitoring the location and data of marine buoys. The buoys have GPS trackers that are connected to the satellites to ensure real-time data monitoring.
Industry: Logistics and Transportation
Tech stack: Node.js, React.js
#nodejs#node.js#node js developers#node js development company#node#react app#react.js#react js#outsourcing#software development#custom software solutions#it staffing company#custom software development#staff augmentation#web development#it staff augmentation#it staff offshoring#custom software#monitoring software#monitoring systems#monitoring#data management
0 notes
Text
Aura: Our software actively monitors the Dark Web!
The FBI:

#yeah the fuck right fuck off lmao#I hate software that claims to monitor the dark web#That's like a business publicly offering to infiltrate local gangs to make sure they're not planning to rob your house
0 notes
Text
Empower Your Business with Avantao's Modern Web Development Services
Avantao Technologies is a cutting-edge software development company that specializes in providing advanced technology solutions for businesses. One of their core services is Modern Web Development, which focuses on creating high-quality, dynamic websites and web applications that meet the needs of modern businesses.
#MODERN WEB DEVELOPMENT#MOBILE APPS DEVELOPMENT SAAS BASED#SECURITY TESTING#ARTIFICIAL INTELLIGENCE#crm#crm services#Academios#customer service#employee monitoring software#iot
1 note
·
View note
Text
#Web server setup tips#Best practices for hosting websites#Choosing the right server for your website#Securing your server and website#Essential software and tools for website hosting#Step-by-step guide to hosting a website on your server#Common mistakes to avoid in website hosting#Monitoring and maintaining your server and website
0 notes
Text
An Introduction to Load Balancing: Improving Performance and Reliability for High-Traffic Websites and Applications
An Introduction to Load Balancing: Improving Performance and Reliability for High-Traffic Websites and Applications
Load balancing is a key aspect of any modern, high-traffic website or application. It allows for the distribution of incoming traffic across multiple servers, ensuring that no single server becomes overwhelmed and can provide a stable, fast experience for users. In this post, we’ll cover the basics of load balancing and how it can improve the performance of your website or application.
First,…
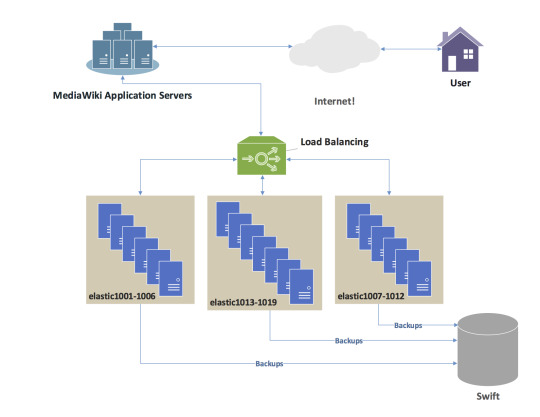
View On WordPress
#algorithms#Amazon Web Services#applications#cloud load balancers#Google Cloud Platform#hardware load balancers#layer 4#layer 7#Load balancing#Microsoft Azure#monitoring#performance#performance management#reliability#software load balancers#traffic#websites
0 notes
Text
Computer Network Monitoring
Computer Network Today it is virtually impossible for an organization not to have computers, whether it is a construction company or a high innovation firm. When an organization has greater than one computer system, they are generally linked with each other in a local area network. These networks may be basically sophisticated as well as for that reason basically pricey.Firms invest a lot (in…

View On WordPress
0 notes
Text
It was all downhill after the Cuecat

Sometime in 2001, I walked into a Radio Shack on San Francisco’s Market Street and asked for a Cuecat: a handheld barcode scanner that looked a bit like a cat and a bit like a sex toy. The clerk handed one over to me and I left, feeling a little giddy. I didn’t have to pay a cent.
The Cuecat was a good idea and a terrible idea. The good idea was to widely distribute barcode scanners to computer owners, along with software that could read and decode barcodes; the company’s marketing plan called for magazines and newspapers to print barcodes alongside ads and articles, so readers could scan them and be taken to the digital edition. To get the Cuecat into widespread use, the company raised millions in the capital markets, then mass-manufactured these things and gave them away for free at Radio Shacks around the country. Every Wired and Forbes subscriber got one in the mail!
That was the good idea (it’s basically a prototype for today’s QR-codes). The terrible idea was that this gadget would spy on you. Also, it would only work with special barcodes that had to be licensed from the manufacturer. Also, it would only work on Windows.
https://web.archive.org/web/20001017162623/http://www.businessweek.com/bwdaily/dnflash/sep2000/nf20000928_029.htm
But the manufacturer didn’t have the last word! Not at all. A couple of enterprising hardware hackers — Pierre-Philippe Coupard and Michael Rothwell — tore down a Cuecat, dumped its ROM, and produced their own driver for it — a surveillance-free driver that worked with any barcode. You could use it to scan the UPCs on your books or CDs or DVDs to create a catalog of your media; you could use it to scan UPCs on your groceries to make a shopping list. You could do any and every one of these things, because the Cuecat was yours.
Cuecat’s manufacturer, Digital Convergence, did not like this at all. They sent out legal demand letters and even shut down some of the repositories that were hosting alternative Cuecat firmware. They changed the license agreement that came with the Cuecat software CD to prohibit reverse-engineering.
http://www.cexx.org/cuecat.htm
It didn’t matter, both as a practical matter and as a matter of law. As a practical matter, the (ahem) cat was out of the bag: there were so many web-hosting companies back then, and people mirrored the code to so many of them, the company would have its hands full chasing them all down and intimidating them into removing the code.
Then there was the law: how could you impose license terms on a gift? How could someone be bound by license terms on a CD that they simply threw away without ever opening it, much less putting it in their computer?
https://slashdot.org/story/00/09/18/1129226/digital-convergence-changes-eula-and-gets-cracked
In the end, Cuecat folded and sold off its remaining inventory. The early 2000s were not a good time to be a tech company, much less a tech company whose business model required millions of people to meekly accept a bad bargain.
Back then, tech users didn’t feel any obligation to please tech companies’ shareholders: if they backed a stupid business, that was their problem, not ours. Venture capitalists were capitalists — if they wanted us give to them according to their need and take from them according to their ability, they should be venture communists.
Last August, philosopher and Centre for Technomoral Futures director Shannon Vallor tweeted, “The saddest thing for me about modern tech’s long spiral into user manipulation and surveillance is how it has just slowly killed off the joy that people like me used to feel about new tech. Every product Meta or Amazon announces makes the future seem bleaker and grayer.”
https://twitter.com/ShannonVallor/status/1559659655097376768
She went on: “I don’t think it’s just my nostalgia, is it? There’s no longer anything being promised to us by tech companies that we actually need or asked for. Just more monitoring, more nudging, more draining of our data, our time, our joy.”
https://twitter.com/ShannonVallor/status/1559663985821106177
Today on Tumblr, @wilwheaton responded: “[T]here is very much no longer a feeling of ‘How can this change/improve my life?’ and a constant dread of ‘How will this complicate things as I try to maintain privacy and sanity in a world that demands I have this thing to operate.’”
https://wilwheaton.tumblr.com/post/698603648058556416/cory-doctorow-if-you-see-this-and-have-thoughts
Wil finished with, “Cory Doctorow, if you see this and have thoughts, I would LOVE to hear them.”
I’ve got thoughts. I think this all comes back to the Cuecat.
When the Cuecat launched, it was a mixed bag. That’s generally true of technology — or, indeed, any product or service. No matter how many variations a corporation offers, they can never anticipate all the ways that you will want or need to use their technology. This is especially true for the users the company values the least — poor people, people in the global south, women, sex workers, etc.
That’s what makes the phrase “So easy your mom can use it” particularly awful “Moms” are the kinds of people whose priorities and difficulties are absent from the room when tech designers gather to plan their next product. The needs of “moms” are mostly met by mastering, configuring and adapting technology, because tech doesn’t work out of the box for them:
https://pluralistic.net/2022/05/19/the-weakest-link/#moms-are-ninjas
(As an alternative, I advocate for “so easy your boss can use it,” because your boss gets to call up the IT department and shout, “I don’t care what it takes, just make it work!” Your boss can solve problems through raw exercise of authority, without recourse to ingenuity.)
Technology can’t be understood separately from technology users. This is the key insight in Donald Norman’s 2004 book Emotional Design, which argued that the ground state of all technology is broken, and the overarching task of tech users is to troubleshoot the things they use:
https://pluralistic.net/2020/04/29/banjo-nazis/#cuckoos-egg
Troubleshooting is both an art and a science: it requires both a methodical approach and creative leaps. The great crisis of troubleshooting is that the more frustrated and angry you are, the harder it is to be methodical or creative. Anger turns attention into a narrow tunnel of brittle movements and thinking.
In Emotional Design, Norman argues that technology should be beautiful and charming, because when you like a technology that has stopped working, you are able to troubleshoot it in an expansive, creative, way. Emotional Design was not merely remarkable for what it said, but for who said it.
Donald Norman, after all, was the author of the hugely influential 1998 classic The Design of Everyday Things, which counseled engineers and designers to put function over form — to design things that work well, even if that meant stripping away ornament and sidelining aesthetics.
https://www.basicbooks.com/titles/don-norman/the-design-of-everyday-things/9780465050659/
With Emotional Design, Norman argued that aesthetics were functional, because aesthetics primed users to fix the oversights and errors and blind spots of designers. It was a manifesto for competence and humility.
And yet, as digital technology has permeated deeper into our lives, it has grown less configurable, not more. Companies today succeed where Cuecat failed. Consolidation in the online world means that if you remove a link from one search engine and four social media sites, the material in question vanishes for 99% of internet users.
It’s even worse for apps: anyone who succeeds in removing an app from two app stores essentially banishes it from the world. One mobile platform uses technological and legal countermeasures to make it virtually impossible to sideload an app; the other one relies on strong-arm tactics and deceptive warnings to do so.
That means that when a modern Coupard and Rothwell decides to unfuck some piece of technology — to excise the surveillance and proprietary media requirements, leaving behind the welcome functionality — they can only do so with the sufferance of the manufacturer. If the manufacturer doesn’t like an add-on, mod, plug-in or overlay, they can use copyright takedowns, anticircumvention law, patent threats, trademark threats, cybersecurity law, contract law and other “IP” to simply banish the offending code:
https://locusmag.com/2020/09/cory-doctorow-ip/
Many of these laws carry dire penalties. For example, distributing a tool that bypasses an “access control” so that you can change the software on a gadget (say, to make your printer accept third-party ink) is a felony under Section 1201 of the DMCA, punishable by a $500k fine and a 5-year prison sentence.
If Cuecat’s manufacturers had simply skinned their firmware with a thin scrim of DRM, they could have threatened Coupard and Rothwell with prison sentences. The developments in “IP” over the two decades since the Cuecat have conjured up a new body of de facto law that Jay Freeman calls “felony contempt of business model.”
Once we gave companies the power to literally criminalize the reconfiguration of their products, everything changed. In the Cuecat era, a corporate meeting to plan a product that acted against its users’ interests had to ask, “How will we sweeten the pot and/or obfuscate our code so that our users don’t remove the anti-features we’re planning to harm them with?”
But in a world of Felony Contempt of Business Model, that discussion changes to “Given that we can literally imprison anyone who helps our users get more out of this product, how can we punish users who are disloyal enough to simply quit our service or switch away from our product?”
That is, “how can we raise the switching costs of our products so that users who are angry at us keep using our products?” When Facebook was planning its photos product, they deliberately designed it to tempt users into making it the sole repository of their family photos, in order to hold those photos ransom to keep Facebook users from quitting for G+:
https://www.eff.org/deeplinks/2021/08/facebooks-secret-war-switching-costs
Companies claim that their lock-in strategies are about protecting their users: “Move into our walled garden, for it is a fortress, whose battlements bristle with fearsome warriors who will defend you from the bandits who roam the countryside”:
https://locusmag.com/2021/01/cory-doctorow-neofeudalism-and-the-digital-manor/
But this “feudal security” offers a terrible temptation to the lords of these fortresses, because once you are inside those walls, the fortress can easily be converted to a prison: these companies can abuse you with impunity, for so long as the cost of the abuse is less than the cost of the things you must give up when you leave.
The tale that companies block you from overriding their decisions is for your own good was always dubious, because companies simply can’t anticipate all the ways their products will fail you. No design team knows as much about your moment-to-moment struggles as you do.
But even where companies are sincere in their desire to be the most benevolent of dictators, the gun on the mantelpiece in Act I is destined to go off by Act III: eventually, the temptation to profit by hurting you will overpower whatever “corporate ethics” once stayed the hand of the techno-feudalist who rules over your fortress. Under feudal security, you are one lapse in corporate leadership from your protector turning into your tormentor.
When Apple launched the Ipad 12 years ago, I published an editorial entitled “Why I won’t buy an iPad (and think you shouldn’t, either),” in which I predicted that app stores would inevitable be turned against users:
https://memex.craphound.com/2010/04/01/why-i-wont-buy-an-ipad-and-think-you-shouldnt-either/
Today, Apple bans apps if they “use…a third-party service” unless they “are specifically permitted to do so under the service’s terms of use.” In other words, Apple specifically prohibits developers from offering tools that displease other companies’ shareholders, no matter whether this pleases Apple customers:
https://developer.apple.com/app-store/review/guidelines/#intellectual-property
Note that clause 5.2.2 of Apple’s developer agreement doesn’t say “You mustn’t violate a legally enforceable term of service.” It just says, “Thou shalt not violate a EULA.” EULAs are garbage-novellas of impenetrable legalese, larded with unenforceable and unconscionable terms.
Apple sometimes will displease other companies on your behalf. For example, it instituted a one-click anti-tracking setting for Ios that cost Facebook $10 billion in a matter of months:
https://www.cnbc.com/2022/02/02/facebook-says-apple-ios-privacy-change-will-cost-10-billion-this-year.html
But Apple also has big plans to expand its margins by growing its own advertising network. When Apple customers choose ad-blockers that block Apple’s ads, will Apple permit it?
https://www.wired.com/story/apple-is-an-ad-company-now/
The problem with app stores isn’t whether your computing experience is “curated” — that is, whether entities you trust can produce collections of software they vouch for. The problem is when you can’t choose someone else — when leaving a platform involves high switching costs, whether that’s having to replace hardware, buy new media, or say goodbye to your friends, customers, community or family.
When a company can leverage its claims to protecting you to protect itself from you — from choices you might make that ultimately undermine its shareholders interests, even if they protect your own interests — it would be pretty goddamned naive to expect it to do otherwise.
More and more of our tools are now digital tools, whether we’re talking about social media or cars, tractors or games consoles, toothbrushes or ovens:
https://www.hln.be/economie/gentse-foodboxleverancier-mealhero-failliet-klanten-weten-van-niets~a3139f52/
And more and more, those digital tools look more like apps than Cuecats, with companies leveraging “IP” to let them control who can compete with them — and how. Indeed, browsers are becoming more app-like, rather than the other way around.
Back in 2017, the W3C took the unprecedented step of publishing a DRM standard despite this standard not having anything like the consensus that is the norm for W3C publications, and the W3C rejected a proposal to protect people who reverse-engineered that standard to add accessibility features or correct privacy defects:
https://www.eff.org/deeplinks/2017/09/open-letter-w3c-director-ceo-team-and-membership
And while we’re seeing remarkable progress on Right to Repair and other policies that allow the users of technology to override the choices of vendors, there’s another strong regulatory current that embraces companies’ ability to control their users, in the hopes that these big companies will police their users to prevent bad stuff, from controversial measures like filtering for copyright infringement to more widely supported ideas like blocking child sex abuse material (CSAM, AKA “child porn”).
There are two problems with this. First, if we tell companies they must control their users (that is, block them from running plugins, mods, skins, filters, etc) then we can’t tell them that they must not control their users. It comes down to whether you want to make Mark Zuckerberg better at his job, or whether you want to abolish the job of “Mark Zuckerberg.”
https://doctorow.medium.com/unspeakable-8c7bbd4974bc
Then there’s the other problem — the gun on the mantelpiece problem. If we give big companies the power to control their users, they will face enormous internal pressure to abuse that power. This isn’t a hypothetical risk: Facebook’s top executives stand accused of accepting bribes from Onlyfans in exchange for adding performers who left Onlyfans to a terrorist watchlist, which meant they couldn’t use other platforms:
https://gizmodo.com/clegg-meta-executives-identified-in-onlyfans-bribery-su-1849649270
I’m not a fan of terrorist watchlists, for obvious reasons. But letting Facebook manage the terrorist watchlist was clearly a mistake. But Facebook’s status as a “trusted reporter” grows directly out of Facebook’s good work on moderation. The lesson is the same as the one with Apple and the ads — just because the company sometimes acts in our interests, it doesn’t follow that we should always trust them to do so.
Back to Shannon Vallor’s question about the origins of “modern tech’s long spiral into user manipulation and surveillance” and how that “killed off the joy that people like me used to feel about new tech”; and Wil Wheaton’s “constant dread of ‘How will this complicate things as I try to maintain privacy and sanity.”
Tech leaders didn’t get stupider or crueler since those halcyon days. The tech industry was and is filled with people who made their bones building weapons of mass destruction for the military-industrial complex; IBM, the company that gave us the PC, built the tabulating machines for Nazi concentration camps:
https://en.wikipedia.org/wiki/IBM_and_the_Holocaust
We didn’t replace tech investors and leaders with worse people — we have the same kinds of people but we let them get away with more. We let them buy up all their competitors. We let them use the law to lock out competitors they couldn’t buy, including those who would offer their customers tools to lower their switching costs and block abusive anti-features.
We decided to create “Felony Contempt of Business Model,” and let the creators of the next Cuecat reach beyond the walls of their corporate headquarters and into the homes of their customers, the offices of their competitors, and the handful of giant tech sites that control our online discourse, to reach into those places and strangle anything that interfered with their commercial desires.
That’s why plans to impose interoperability on tech giants are so exciting — because the problem with Facebook isn’t “the people I want to speak to are all gathered in one convenient place,” no more than the problem with app stores isn’t “these companies generally have good judgment about which apps I want to use.”
The problem is that when those companies don’t have your back, you have to pay a blisteringly high price to leave their walled gardens. That’s where interop comes in. Think of how an interoperable Facebook could let you leave behind Zuckerberg’s dominion without forswearing access to the people who matter to you:
https://www.eff.org/interoperablefacebook
Cuecats were cool. The people who made them were assholes. Interop meant that you could get the cool gadget and tell the assholes to fuck off. We have lost the ability to do so, little by little, for decades, and that’s why a new technology that seems cool no longer excites. That’s why we feel dread — because we know that a cool technology is just bait to lure us into a prison that masquerades as a fortress.
Image:
Jerry Whiting (modified)
https://en.wikipedia.org/wiki/File:CueCat_barcode_scanner.jpg
CC BY-SA 3.0:
https://creativecommons.org/licenses/by-sa/3.0/deed.en
[Image ID: A Cuecat scanner with a bundled cable and PS/2 adapter; it resembles a plastic cat and also, slightly, a sex toy. It is posed on a Matrix movie 'code waterfall' background and limned by a green 'supernova' light effect.]
7K notes
·
View notes
Text

TECHNOLOGY ID PACK

NAMES ⌇ admin. ajax. alexa. am. atari. audio. auto. bailey. binary. blank. blu. blue. bluesse. browser. browsette. bug. byte. cache. calware. chip. circe. click. clicker. clickie. clicky. cloud. coda. code. codette. codie. cody. computette. crypt. cursor. cy. cyber. cybernet. cybernetica. cyberweb. cypher. cypherre. data. dell. digi. digitalia. digitelle. digitesse. disc. dot. electronica. electronique. emoticon. emoticonnie. fax. file. gig. gizmo. glitch. glitche. glitchesse. glitchette. graphique. hacker. hal. halware. hijack. index. informationne. intelligette. internette. interweb. java. javascript. juno. key. link. linuxe. lotus. lovebytes. mac. mal. malakai. malware. malwaria. memorette. memorie. meta. mic. micah. mickey. morphe. mouse. mousette. myspace. nano. neo. net. netette. nett. netty. paige. pascal. payton. peyton. pixel. programatha. programette. programme. pulse. reboot. rom. router. ruby. sam. sammy. screene. screenette. sean. shock. solitaire. spy. static. stutter. talia. tap. tecca. tech. techette. tessa. tetris. trojan. troubleshoot. ts. user. vir. virus. virusse. volt. vyrus. webbe. wheatley. whirr. widget. will. wirehead. wiresse. zap. zett. zetta. zip.

PRONOUNS ⌇ :-)/:-D. ^^/^^. ai/ai. alt/alt. anti/antivirus. arc/archive. audio/audio. bat/battery. beep/beep. beep/boop. bit/bit. bit/byte. blue/blue. board/board. bright/bright. brow/browser. browser/browser. brr/brr. bu/bug. bug/bug. buzz/buzz. byt/byte. byte/byte. c/cpu. charge/charger. cir/circuit. cli/click. click/clack. click/click. click/scroll. co/code. code/code. color/color. com/com. com/computer. comp/computer. compute/computer. computer/computer. cor/corrupt. corrupt/corrupt. CPU/CPU. crash/crash. cre/creeper. crtl/crtl. cy/cyber. cyb/cyber. cyber/cyber. da/data. data/data. delete/delete. di/disk. dig/digital. digi/digi. digi/digital. digital/digital. dra/drag. e/exe. electronic/electronic. enter/enter. er/error. err/error. error/error. exe/exe. fi/file. file/file. gi/gif. gli/glitch. glit/glitch. glitch/glitch. graphic/graphic. hac/hacker. hack/hack. hard/hardware. head/phone. hij/hijacker. ho/home. info/info. information/information. int/internet. intelligent/intelligence. intelligent/intelligent. inter/net. internet/internet. it/it. jpg/jpg. key/board. key/cap. key/key. key/keyboard. key/keylogger. lag/lag. lap/laptop. ligh/light. linux/linux. load/load. log/login. main/mainframe. mal/malware. me/media. memory/memorie. mon/monitor. mou/mouse. nano/nano. net/net. net/network. o_o/>_>. org/org. over/overwrite. page/page. pix/pix. pix/pixel. pixel/pixel. plu/plug. png/png. pop/popup. port/port. pow/power. pro/program. program/program. ram/ram. ran/ransom. reboot/reboot. reload/reload. res/restore. ret/retro. route/router. sca/scan. scr/scroll. scre/screen. scre/screencap. scree/screen. screen/screen. scri/script. script/script. sentient/sentience. shift/shift. site/site. skip/skip. soft/software. spa/spam. space/space. spy/spyware. stop/stop. te/tech. tech/nology. tech/tech. technology/technology. tou/touchpad. txt/txt. typ/type. upload/upload. user/user. vi/viru. vi/virus. vir/virtual. web/page. web/web. whir/whir. wi/wire. win/dow. win/window. wire/wire. wire/wired. zip/zip . ⌨ . ☣ . ⚙ . ⚠ . 🎞 . 🎨 . 🎭 . 🎮 . 🎵 . 👀 . 👁 . 💔 . 💡 . 💢 . 💣 . 💳 . 💵 . 💻 . 💽 . 💾 . 💿 . 📀 . 📱 . 🔇 . 🔈 . 🔉 . 🔊 . 🔋 . 🔌 . 🔎 . 🖥 . 🖱 . 🗡 . 🗯 . 🛠 . 🧿 .

#⭐️lists#id pack#npt#name suggestions#name ideas#name list#pronoun suggestions#pronoun ideas#pronoun list#neopronouns#nounself#emojiself#techkin#robotkin#internetkin
271 notes
·
View notes
Text
So I don't know how people on this app feel about the shit-house that is TikTok but in the US right now the ban they're trying to implement on it is a complete red herring and it needs to be stopped.
They are quite literally trying to implement Patriot Act 2.0 with the RESTRICT Act and using TikTok and China to scare the American public into buying into it wholesale when this shit will change the face of the internet. Here are some excerpts from what the bill would cover on the Infrastructure side:
SEC. 5. Considerations.
(a) Priority information and communications technology areas.—In carrying out sections 3 and 4, the Secretary shall prioritize evaluation of—
(1) information and communications technology products or services used by a party to a covered transaction in a sector designated as critical infrastructure in Policy Directive 21 (February 12, 2013; relating to critical infrastructure security and resilience);
(2) software, hardware, or any other product or service integral to telecommunications products and services, including—
(A) wireless local area networks;
(B) mobile networks;
(C) satellite payloads;
(D) satellite operations and control;
(E) cable access points;
(F) wireline access points;
(G) core networking systems;
(H) long-, short-, and back-haul networks; or
(I) edge computer platforms;
(3) any software, hardware, or any other product or service integral to data hosting or computing service that uses, processes, or retains, or is expected to use, process, or retain, sensitive personal data with respect to greater than 1,000,000 persons in the United States at any point during the year period preceding the date on which the covered transaction is referred to the Secretary for review or the Secretary initiates review of the covered transaction, including—
(A) internet hosting services;
(B) cloud-based or distributed computing and data storage;
(C) machine learning, predictive analytics, and data science products and services, including those involving the provision of services to assist a party utilize, manage, or maintain open-source software;
(D) managed services; and
(E) content delivery services;
(4) internet- or network-enabled sensors, webcams, end-point surveillance or monitoring devices, modems and home networking devices if greater than 1,000,000 units have been sold to persons in the United States at any point during the year period preceding the date on which the covered transaction is referred to the Secretary for review or the Secretary initiates review of the covered transaction;
(5) unmanned vehicles, including drones and other aerials systems, autonomous or semi-autonomous vehicles, or any other product or service integral to the provision, maintenance, or management of such products or services;
(6) software designed or used primarily for connecting with and communicating via the internet that is in use by greater than 1,000,000 persons in the United States at any point during the year period preceding the date on which the covered transaction is referred to the Secretary for review or the Secretary initiates review of the covered transaction, including—
(A) desktop applications;
(B) mobile applications;
(C) gaming applications;
(D) payment applications; or
(E) web-based applications; or
(7) information and communications technology products and services integral to—
(A) artificial intelligence and machine learning;
(B) quantum key distribution;
(C) quantum communications;
(D) quantum computing;
(E) post-quantum cryptography;
(F) autonomous systems;
(G) advanced robotics;
(H) biotechnology;
(I) synthetic biology;
(J) computational biology; and
(K) e-commerce technology and services, including any electronic techniques for accomplishing business transactions, online retail, internet-enabled logistics, internet-enabled payment technology, and online marketplaces.
(b) Considerations relating to undue and unacceptable risks.—In determining whether a covered transaction poses an undue or unacceptable risk under section 3(a) or 4(a), the Secretary—
(1) shall, as the Secretary determines appropriate and in consultation with appropriate agency heads, consider, where available—
(A) any removal or exclusion order issued by the Secretary of Homeland Security, the Secretary of Defense, or the Director of National Intelligence pursuant to recommendations of the Federal Acquisition Security Council pursuant to section 1323 of title 41, United States Code;
(B) any order or license revocation issued by the Federal Communications Commission with respect to a transacting party, or any consent decree imposed by the Federal Trade Commission with respect to a transacting party;
(C) any relevant provision of the Defense Federal Acquisition Regulation and the Federal Acquisition Regulation, and the respective supplements to those regulations;
(D) any actual or potential threats to the execution of a national critical function identified by the Director of the Cybersecurity and Infrastructure Security Agency;
(E) the nature, degree, and likelihood of consequence to the public and private sectors of the United States that would occur if vulnerabilities of the information and communications technologies services supply chain were to be exploited; and
(F) any other source of information that the Secretary determines appropriate; and
(2) may consider, where available, any relevant threat assessment or report prepared by the Director of National Intelligence completed or conducted at the request of the Secretary.

Look at that, does that look like it just covers the one app? NO! This would cover EVERYTHING that so much as LOOKS at the internet from the point this bill goes live.
It gets worse though, you wanna see what the penalties are?

(b) Civil penalties.—The Secretary may impose the following civil penalties on a person for each violation by that person of this Act or any regulation, order, direction, mitigation measure, prohibition, or other authorization issued under this Act:
(1) A fine of not more than $250,000 or an amount that is twice the value of the transaction that is the basis of the violation with respect to which the penalty is imposed, whichever is greater.
(2) Revocation of any mitigation measure or authorization issued under this Act to the person.
(c) Criminal penalties.—
(1) IN GENERAL.—A person who willfully commits, willfully attempts to commit, or willfully conspires to commit, or aids or abets in the commission of an unlawful act described in subsection (a) shall, upon conviction, be fined not more than $1,000,000, or if a natural person, may be imprisoned for not more than 20 years, or both.
(2) CIVIL FORFEITURE.—
(A) FORFEITURE.—
(i) IN GENERAL.—Any property, real or personal, tangible or intangible, used or intended to be used, in any manner, to commit or facilitate a violation or attempted violation described in paragraph (1) shall be subject to forfeiture to the United States.
(ii) PROCEEDS.—Any property, real or personal, tangible or intangible, constituting or traceable to the gross proceeds taken, obtained, or retained, in connection with or as a result of a violation or attempted violation described in paragraph (1) shall be subject to forfeiture to the United States.
(B) PROCEDURE.—Seizures and forfeitures under this subsection shall be governed by the provisions of chapter 46 of title 18, United States Code, relating to civil forfeitures, except that such duties as are imposed on the Secretary of Treasury under the customs laws described in section 981(d) of title 18, United States Code, shall be performed by such officers, agents, and other persons as may be designated for that purpose by the Secretary of Homeland Security or the Attorney General.
(3) CRIMINAL FORFEITURE.—
(A) FORFEITURE.—Any person who is convicted under paragraph (1) shall, in addition to any other penalty, forfeit to the United States—
(i) any property, real or personal, tangible or intangible, used or intended to be used, in any manner, to commit or facilitate the violation or attempted violation of paragraph (1); and
(ii) any property, real or personal, tangible or intangible, constituting or traceable to the gross proceeds taken, obtained, or retained, in connection with or as a result of the violation.
(B) PROCEDURE.—The criminal forfeiture of property under this paragraph, including any seizure and disposition of the property, and any related judicial proceeding, shall be governed by the provisions of section 413 of the Controlled Substances Act (21 U.S.C. 853), except subsections (a) and (d) of that section.
You read that right, you could be fined up to A MILLION FUCKING DOLLARS for knowingly violating the restrict act, so all those people telling you to "just use a VPN" to keep using TikTok? Guess what? That falls under the criminal guidelines of this bill and they're giving you some horrible fucking advice.
Also, VPN's as a whole, if this bill passes, will take a goddamn nose dive in this country because they are another thing that will be covered in this bill.
They chose the perfect name for it, RESTRICT, because that's what it's going to do to our freedoms in this so called "land of the free".
Please, if you are a United States citizen of voting age reach out to your legislature and tell them you do not want this to pass and you will vote against them in the next primary if it does. This is a make or break moment for you if you're younger. Do not allow your generation to suffer a second Patriot Act like those of us that unfortunately allowed for the first one to happen.
And if you support this, I can only assume you're delusional or a paid shill, either way I hope you rot in whatever hell you believe in.
#politics#restrict bill#tiktok#tiktok ban#s.686#us politics#tiktok senate hearing#land of the free i guess#patriot act#patriot act 2.0
896 notes
·
View notes
Text
Surveillance developments of the 21st century have replaced the traditional gaze of the supervisor on the industrial factory floor with an automated, digital one that continuously collects real-time data on living, breathing people. Even unionized workers do not have an explicit legal right to bargain over surveillance technologies; when it comes to the right to privacy, unions have an uphill battle to fight.
We now live in a world where employees are stuck in a web of participatory surveillance because they consent to be monitored as a condition of employment. Today’s workplace surveillance practices, as in the case of Amazon, have become invasive and almost limitless. Technology has allowed employers an unprecedented ability to surveil workers. Management can minutely track and persistently push workers toward greater productivity at the risk of exacerbating harms to workers’ physical health, as the high rates of injury in Amazon warehouses show. And the growing business of selling workplace surveillance software has allowed for massive amounts of data to be collected on working people: when and who they talk to, how quickly they complete tasks, what they search for on their computers, how often they use the toilet, and even the state of their current health and moods.
93 notes
·
View notes
Text
hi @hypertextdog followers and friends. it's that time again
the process of elimination (tpoe) <- play here
this is my interactive ergodic web fiction project, the process of elimination !!! ↴↴↴


it features six endings, a robust original soundtrack (by myself), and a number of visual artworks, including the banners visible above and the tpoe ost's album cover, by @notwerewolf. other information (including many content warnings) can be found on my homepage.
if that piques your interest at all, feel free 2 join the discord here!!
more info on it below ↴↴↴
tpoe is an exploration of isolation, control, surveillance, and early 2020's-era internet culture. you play as harry arsigne, a 14-year-old cat artist living ~alone with his overbearing father, scott, in a decommissioned lighthouse in the shoreline town of conder, connecticut.
making choices through personality test responses, you'll balance your two hobbies: exchanging personal histories with and seeking questionable guidance from the set of five eccentric criminals scott keeps in his d.i.y. prison cell in the lighthouse basement, and using his surveillance software to monitor the online activity of one wren wayer*, a rather pretentious local high school sophomore and twice attempted gamedev with whom you have an at times overwhelming obsession.
* that says "wren wayer" sorry dark mode users
it is a whole queer ordeal with honest deconstructions of modern online teenager-hood, including fandom and forum drama, gay parasocial love, e-childlabor, and destructive codependent ldr's. it's also a crime drama about a father whose overprotective affection manifests itself as a sort of religious zeal pertaining to disease, water purity, and fucked up architecture.
it is really good and i worked hard on it dudeee. play ittt join the serverrr thanks for reading👍👍
#rbs appreciated as always :]#the process of elimination#tpoe#interactive fiction#internet fiction#ergodic fiction#indie game#indiedev#gamedev#interactive story#hypertext fiction#hypertext novel#if#lgbt#lgbt fiction#gay#gay fiction#things i think tpoe enjoyers would enjoy! ->#homestuck#17776#17776 football#nitw#night in the woods#omori#oxenfree#house of leaves#myhouse.wad#hol
365 notes
·
View notes
Text
Please share tips for managing windows on an ultrawide computer display
I recently upgraded from a 27" 14-year-old Apple Cinema Display to a 34" Dell ultrawide.
Until now, I’ve always run a simple windowing setup: Most of the time, I’m using one app, and it’s maximized to fill the whole screen. When I want to switch apps, I Cmd-Tab between them (that’s equivalent to Alt-Tab on Windows). But that strategy is not going to work for me on a 34" display because the individual app becomes too big to take in. I think at first that if I’m working on just one application, I’ll have it centered, full height, 2/3 or 3/4 of the width of the screen. But what goes on either edge?
How do you manage your ultrawide lifestyle?
I use the computer for basic productivity, the web and social media. I’m not a gamer and I don’t generally watch videos or listen to music on my desktop.
I already use Raycast for window management, so I don’t need pointers to software such as Raycast, Moom, or Magnet. On the other hand, if there are particular applications you love for window management on ultrawide displays, please let me know.
By the way, I searched the Internet for tips on making the transition and found reddit.com/r/ultrawidemasterrace, where people share tips and photos of their ultrawide setups. 34" seems huge to me, but it barely qualifies for that sub. For example, check this out: a 49" display with another monitor mounted above it.
23 notes
·
View notes
Text
For more than three weeks, Gaza has faced an almost total internet blackout. The cables, cell towers, and infrastructure needed to keep people online have been damaged or destroyed as Israel launched thousands of missiles in response to Hamas attacking Israel and taking hundreds of hostages on October 7. Then, this evening, amid reports of heavy bombing in Gaza, some of the last remaining connectivity disappeared.
In the days after October 7, people living in Gaza have been unable to communicate with family or friends, leaving them unsure whether loved ones are alive. Finding reliable news about events has become harder. Rescue workers have not been able to connect to mobile networks, hampering recovery efforts. And information flowing out of Gaza, showing the conditions on the ground, has been stymied.
As the Israel Defense Forces said it was expanding its ground operations in Gaza this evening, internet connectivity fell further. Paltel, the main Palestinian communications company, has been able to keep some of its services online during Israel’s military response to Hamas’ attack. However, at around 7:30 pm local time today, internet monitoring firm NetBlocks confirmed a “collapse” in connectivity in the Gaza Strip, mostly impacting remaining Paltel services.
“We regret to announce a complete interruption of all communications and internet services within the Gaza Strip,” Paltel posted in a post on its Facebook page. The company claimed that bombing had “caused the destruction of all remaining international routes.” An identical post was made on the Facebook page of Jawwal, the region’s biggest mobile provider, which is owned by Paltel. Separately, Palestinian Red Crescent, a humanitarian organization, said on X (formerly Twitter) that it had lost contact with its operation room in Gaza and is “deeply concerned” about its ability to keep caring for people, with landline, cell, and internet connections being inaccessible.
“This is a terrifying development,” Marwa Fatafta, a policy manager focusing on the Middle East and North Africa at the digital rights group Access Now, tells WIRED. “Taking Gaza completely off the grid while launching an unprecedented bombardment campaign only means something atrocious is about to happen.”
A WIRED review of internet analysis data, social media posts, and Palestinian internet and telecom company statements shows how connectivity in the Gaza Strip drastically plummeted after October 7 and how some buildings linked to internet firms have been damaged in attacks. Photos and videos show sites that house various internet and telecom firms have been damaged, while reports from official organizations, including the United Nations, describe the impact of people being offline.
Damaged Lines
Around the world, the internet and telecoms networks that typically give web users access to international video calls, online banking, and endless social media are a complicated, sprawling mix of hardware and software. Networks of networks, combining data centers, servers, switches, and reams of cables, communicate with each other and send data globally. Local internet access is provided by a mix of companies with no clear public documentation of their infrastructure, making it difficult to monitor the overall status of the system as a whole. In Gaza, experts say, internet connectivity is heavily reliant on Israeli infrastructure to connect to the outside world.
Amid Israel’s intense bombing of Gaza, physical systems powering the internet have been destroyed. On October 10, the United Nations’ Office for the Coordination of Humanitarian Affairs (OCHA), which oversees emergency responses, said air strikes “targeted several telecommunication installations” and had destroyed two of the three main lines of communications going into Gaza.
Prior to tonight’s blackout, internet connectivity remained but was “extremely slow and limited,” Access Now’s Fatafta says. People she has spoken to from Gaza say it could take a day to upload and send a few photos. “They have to send like 20 messages in order for one to go through,” Fatafta says. “They are desperately—especially for Gazans that live outside—trying to get through to their families.”
“Every time I try to call someone from family or friends, I try to call between seven to 10 times,” says Ramadan Al-Agha, a digital marketer who lives in Khan Yunis, a city in the south of the Gaza Strip. “The call may be cut off two or three times,” he told WIRED in a WhatsApp message before the latest outages. “We cannot access news quickly and clearly.” People in the region have simultaneously faced electricity blackouts, dwindling supplies of fuel used to power generators, and a lack of clean water, food, and medical supplies. “It is a humanitarian disaster,” Al-Agha says.
Connectivity in Gaza started to drop not long after Israel responded to the October 7 Hamas attack. Rene Wilhelm, a senior R&D engineer at the nonprofit internet infrastructure organization Ripe Network Coordination Center, says based on an analysis of internet routing data it collects that 11 Palestinian networks, which may operate both in the West Bank and Gaza Strip, began to experience disruption after October 7. Eight of the networks were no longer visible to the global internet as of October 23, Wilhelm says. Ahead of this evening’s blackout, there was around 15 percent of normal connectivity, according to data from Georgia Tech’s Internet Outage Detection and Analysis project. That dropped to around 7 percent as reports of the blackout circulated.
One office belonging to Paltel in the Al Rimal neighborhood of Gaza City has been destroyed in the attacks, photos and videos show. Floors have been destroyed and windows blown away in the multistory building, and piles of rubble surround the entrances. (It is unclear what equipment the building housed or how many floors Paltel occupied.) Another internet provider, AlfaNet, is listed as being based in the Al-Watan Tower. The company posted to its Facebook page on October 8 that the tower had been destroyed and its services have stopped, with other online posts also saying the tower has been destroyed.
Multiple Palestinian internet and telecoms firms have said their services have been disrupted during the war, mostly posting to social media. Internet provider Fusion initially said its engineers were trying to repair its infrastructure, although it has since said this is not continuing. “The network was destroyed, and the cables and poles were badly damaged by the bombing,” it wrote on Facebook. JetNet said there had been a “sudden disruption” to access points. SpeedClick posted that the situation was out of its control. And HiNet posted that it has “no more to offer to ensure” people could stay online following “the attacks and destruction our internet servers have suffered.”
Across Paltel’s network on October 19, according to an update shared by the Office for the Coordination of Humanitarian Affairs, 83 percent of fixed line users had been disconnected, with 53 percent of sites providing fixed line connections also being offline. Half of the company’s fiber optic internet lines in Gaza weren’t operational, the update says. The connectivity disappeared this evening, according to Paltel’s Facebook post, which says there has been a “complete interruption” of all its services. Paltel, AlfaNet, Fusion, and SpeedClick could not be reached or did not respond to requests for comment.
Lost Connections
In recent years, governments and authoritarian regimes have frequently turned to shutting down the internet for millions of people in attempts to suppress protests and curtail free speech. Targeting the communications networks is common during conflicts. During Russia's war in Ukraine, its forces have decimated communications networks, tried to take over the internet, and set up new mobile companies to control information flows. When Hamas first attacked Israel on October 7, it used drones to bomb communications equipment at surveillance posts along the borders of the Gaza Strip.
Monika Gehner, the head of corporate communications at the International Telecommunication Union, says the body is always “alarmed” by damage inflicted on any telecommunications infrastructure during conflicts. The ITU, the United Nations’ primary internet governance body, believes “efficient telecommunication services” are crucial to peace and international cooperation, and its secretary-general has called for respecting infrastructure in the Middle East, Gehner says.
Officials in Israel have consistently claimed they are targeting Hamas militants within Gaza, not civilians, while responding to the Hamas attacks, which killed more than 1,400 people in Israel. The Hamas-run Health Ministry within Gaza has said more than 7,000 people have been killed there and released a list of names. A spokesperson for the Israel Defense Forces did not respond to WIRED’s questions about internet disruptions within Gaza.
Hanna Kreitem, a senior adviser for internet technology and development in the Middle East and North Africa at the Internet Society, an open internet advocacy nonprofit, says Palestinian firms have a “big reliance” on Israeli internet firms. “Palestinians are not controlling any of the ICT infrastructure,” says Mona Shtaya, a non-resident fellow at the Tahrir Institute for Middle East Policy. Mobile networks in the Gaza Strip rely on 2G technologies. Al-Agha, the digital marketer, shared a screenshot showing mobile internet speeds of 7.18 kilobytes per second; average mobile speeds in the US in 2022 were 24 megabits per second, according to mobile analytics firm Statista.
“The internet is vital in times of war in crises,” says Fatafta, the Access Now policy manager, who adds that there can be “terrible consequences” linked to connectivity blackouts. The UN’s OCHA said rescue workers have had a harder time “carrying out their mission” partly due to the “limited or no connection to mobile networks.” Al-Agha says he has lost some clients due to the disruptions. The lack of connectivity can obscure events that are happening on the ground, Fatafta says. News crews have told WIRED they have footage from the ground but are “losing the story because of the internet.”
Kreitem says that a lack of electricity and access to the equipment will have made an impact on top of any physical damage to communications networks. “We don't know how many of the people that actually operate these networks are still alive,” Kreitem says. “The network operators are part of the world there, there's no place for them to run. They are as affected as any other person.”
90 notes
·
View notes
Text
Common scams and you
Hello everyone!
I'm finally writing out the idea that has been floating around in my head for a while now, and I'm honestly surprised there's no videos on youtube (that I've found) that talk about the most common scams that are out there on the internet that you may encounter.
So! Let's start.
#1. Virus pop up scams.
These types of scams are based around inciting panic and fear in those that encounter them. They are generally encountered by mistyping a url in the search bar that then leads you to a web page containing a flashy visual alert (and sometimes audio alert) stating something like the following:
Your system is at risk! # Viruses found! Warning!
Your system has been compromised!
Viruses / Trojans found!
The majority of which then provide a phone number that scam victims would call to get the issue 'resolved.' Those who fall for this scam contact the call center seeking help, and those there- the scammers, lull their victims into a false sense of security that they'll solve the issue. They then have their victims download remote access software such as AnyDesk and UltraViewer.
These programs allow a user who connects complete and TOTAL CONTROL of your computer. They can view your screen, track what you type or click, not to mention they can lock it, and they can change the password, holding it at ransom. They can do pretty much ANYTHING as long as the software is installed. It runs in the background and they can monitor everything you do.
They will tell you that to get rid of the virus/'hack', you must pay a certain amount (usually between $300-$1k or more) for them to clean your computer and 'add an antivirus'.
They will tell you that you need to go to walmart/wallgreens to get gift cards. Or they will ask you to provide banking details so that they can steal your banking/login information to transfer money via zelle or other methods while under the control of the remote access application.
If you or anyone you know has made it to the installation part of this scam, make sure to disconnect the internet immediately and uninstall the program that they installed upon the computer.
This scam can ALSO happen to people on mobile. There are websites and apps configured to show that you've got a virus, and much like above, it will tell you that you need to call a phone number or download an app to get it resolved.
Clicking off the page / notification gets rid of it. There was never any virus to worry about. So don't worry too much if you see something like this while browsing the internet. Just try and be safe!
#2. E-Mail scams.
The most notorious of all of e-mail scams that I've encountered over the years are as follows:
Your <brand> anti-virus has expired. Click here to re-new!
You have been charged <huge amount> for <brand> anti-virus. If this is a mistake please call <phone number> to get this resolved.
You have received a PayPal invoice from <scammer name/brand> for <huge amount> please call <phone number>.
Much like the virus pop up scam, these scams follow a similar path when it comes to the end result. You call them, they have you install a remote access application, they tell you to pay x amount of money so they can install their 'anti-virus', and/or they do a fake 'scan' in the console, and likely install a real virus that harvests your information.
All in all, best to avoid it/delete the e-mail. No proper anti-virus is going to send you an e-mail telling you to call them. Nor are they going to charge you $300 for a 'renewal.'
As for the paypal invoice, just ignore it and check your actual paypal. If there's no invoice, there never was one in the first place. Flag it as trash and delete it.
#3 Phone scams.
These can be scary, especially if you've got a son, daughter, or relative who might live out of town.
Mom/Dad I lost my phone can you send me money for a new one?
Hey I'm with your kid and they're hurt/arrested/etc can you send me some money to pay the ambulance/bail/etc.
Your kid said I'd bring you these things and you'd pay me.
This is <name> from <fake business/tech support> on behalf of apple/microsoft to let you know your warranty has expired.
Sadly this means that your phone number has likely been leaked online somewhere, and scammers are now attempting to use it to get money from you. Best advice is to hang up and block the number immediately before calling your child/family member to make sure they're okay.
#4. Text Scams.
These are generally pretty easy to notice, and pretty easy to avoid, if you know what to look out for.
Any random number that texts you with something akin to the following, is a scam:
THIS IS <FAKE NAME> FROM THE UNITED STATES <FAKE COMPANY> TO INFORM YOU THAT YOU'VE WON <MILLIONS OF DOLLARS>. PLEASE FILL OUT THE FORM BELOW TO HAVE ACCESS TO YOUR WINNINGS.
Fedex has your package click this link to update your information.
UPS has failed to deliver your package. click this link to-
Hi <name that's not yours> are we set for our <event> next <day>?
<name not yours> I'm looking forward to <activity> next <day>. Are you going to be busy?
While links to scammy websites are easy to avoid, the last two might not be so easy to some people. Replying to them in any form puts you on a list of 'active numbers' for them to target. They will text you repeatedly with different prompts which all lead down the same line.
You say 'wrong number', they say 'this isn't <name>?' you say 'no' they say 'i'm so sorry i thought this was <name>' you say 'no problem' they say 'oh you're so kind want to be friends?' which then leads into 'i'm <fake name> from China/Singapore/<country> but I live in california/new york. I'm a fashion designer/investor/owner of a small company' and they send a fake picture of them which is likely stolen from somewhere online. They also ask for you to send them YOUR pictures. Don't do this.
End goal is for you to download WatsApp/Telegram to send them money and/or invest in fake crypto.
There are also text scams similar to those mentioned above where it's someone pretending to be a sugar mommy/daddy and they try to get you to spend time and hook up with them. They ask you to pay a 'fee' so they know you're 'legit' or something which, of course, is just a way to get you to send them money.
#5. Facebook Scams.
These are rather new, but once you know the signs, you'll know how to avoid them.
When buying/selling something on facebook, if someone says they can't pick it up but <brother/sister/cousin> can and they ask if you take cashapp, zelle, etc, it's a scam.
If you or someone you know who is older/elderly is contacted by someone who's in the military/ex-military/ex-cia/ex-fbi etc and they flood your DM's with affection and kindness and lots of love and attention in an effort to get you in a relationship with them, this is known as a romance scam.
They will ask for money to 'get a new phone' or 'to send pictures because my camera is broken.' or to 'buy a plane ticket to come see you'. It's a scam, a big scam, and a lot of elderly people have been scammed out of a lot of money because of it. They will call you and talk to you and say they love you and all that kissy kissy mwah junk just to build trust so they can try and get money.
It's not real. As sad as that is to say, all these people are after is money.
If you know anyone who might be in any of these situations, PLEASE try and talk some sense into them. Especially if they've sent large amounts of money to someone over the internet. Google is your best friend, and there is information out there for people who want to find it.
All in all, just make sure you're careful in who you trust.
#6. Discord/Steam Scams.
These can be less obvious to those who aren't tech savvy, but once you know the signs they're hard to miss.
Anyone who randomly DM's you about beta-testing their 'new game' is trying to get you to click a link that leads to a website containing an application that contains a virus. This will harvest your information and give the hacker access to everything on your computer.
Anyone who randomly DM's you saying that they found 'compromising photos/information of you online' most likely will try to get you to click a virus link that will infect your computer.
Anyone who randomly DM's you saying they 'reported you to the discord/steam admins' for something inappropriate/illegal will try to get you to contact their 'friend' who is a 'discord/steam admin' to get it resolved.
This will either involve them sending you a virus link or trying to get you to send them money/gift cards to get the issue 'resolved.' They will also sometimes send you to a legit looking steam page which is fake and will harvest your steam login data.
Again, these are easy to notice once you know the signs. Just note that sometimes your friends might send you messages like these or ask for money, which in that case their account was likely compromised/hacked. Make sure to report them so that discord/steam can help get the account back in the right hands.
I know I've likely forgotten some other types of scams but for now these are the most common that people should keep an eye out and look for.
Protect yourself and protect others!
37 notes
·
View notes