#WiFi Bandwidth Control Software
Explore tagged Tumblr posts
Text
Optimizing Internet Speed with WiFi Bandwidth Control Software
Discover how WiFi bandwidth control software boosts internet speed, manages network traffic, and delivers a faster, more reliable online experience.
0 notes
Text
ARMxy Industrial Computers BL330 for Water Treatment System Monitoring

Case Details
I. Advantages of ARMxy Industrial Computers BL330
Low Power Consumption
ARM architecture Cortex-A7 processors, consume significantly less power than x86 CPUs, ideal for 24/7 industrial operations.
Real-Time Performance
Supports real-time operating systems (RTOS) or Linux with real-time kernels, meeting time-sensitive data acquisition and control requirements.
Compact and Rugged Design
Compact size for space-constrained installations; operates in harsh environments (-40°C to 85°C) with resistance to dust, vibration, and humidity.
Rich Interfaces and Expandability
Equipped with industrial interfaces (RS-485, CAN, Ethernet, GPIO) to connect sensors (pH, turbidity, conductivity), PLCs, and actuators.
Cost-Effective
Lower hardware and maintenance costs compared to traditional industrial PCs, suitable for large-scale deployments.
II. Core Functions in Water Treatment Monitoring
Data Acquisition and Processing
Real-time collection of water quality parameters (COD, BOD, residual chlorine, dissolved oxygen) and equipment status (pump pressure, flow rate, valve position).
Communication via Modbus RTU/TCP, OPC UA protocols.
Edge Computing
Local data preprocessing (filtering, anomaly detection) to reduce cloud bandwidth usage.
Basic logic control (e.g., automatic chemical dosing based on pH levels).
Remote Monitoring and Visualization
Built-in web server or HMI for real-time data display and alarm management.
Data transmission to cloud platforms (SCADA, IoT Hub) via 4G/5G, Ethernet, WiFi.
Fault Diagnosis and Alerts
Predictive maintenance using historical data (e.g., membrane fouling, pump failure).
Trigger alarms or send notifications to operators via SMS/email.
III. Typical Applications
1. Online Water Quality Monitoring Stations
Function:
Deploy at water sources or treatment outlets to monitor turbidity, pH, heavy metals (e.g., arsenic, lead).
Hardware:
ARM computer + multi-parameter sensors + solar power (for remote areas).
2. PLC Replacement in Wastewater Treatment Plants
Function:
Replace traditional PLCs to control dissolved oxygen in aeration tanks, optimize sludge recycling, and adjust chemical dosing.
Solution:
ARM computer running Codesys soft PLC with PID algorithms, controlling devices via EtherCAT.
3. Distributed Rural Water Supply Monitoring
Function:
Monitor decentralized water purification systems (filter lifespan, flow anomalies) to ensure safe drinking water.
Architecture:
ARM edge gateway + sensor+ low-power design for unstable power supply scenarios.
IV. System Design Considerations
Environmental Adaptability
Use Industrial enclosures to protect against moisture and corrosive gases.
Communication Redundancy
Dual-network interfaces (wired + wireless) for reliable data transmission.
Software Architecture
Lightweight OS (Ubuntu, Linux) or RTOS (FreeRTOS) with MQTT/HTTP protocols.
Local storage (SQLite) or time-series databases (InfluxDB).
Cybersecurity
Enable firewalls, TLS/SSL encryption, and regular firmware updates.
V. Case Studies
Seawater Desalination Plant Monitoring
Hardware: ARM Cortex-A7 computer + pressure sensors + RO membrane modules.
Functions:
Monitor pressure differentials across RO membranes to predict fouling.
Automatically shut down high-pressure pumps during overloads.
OPC UA integration with central control systems.
Industrial Park Wastewater Station
Hardware: ARM edge gateway + AI cameras.
Functions:
AI-based foam thickness detection in aeration tanks to adjust blower speed.
Local TensorFlow Lite models for sludge settling ratio analysis.
VI. Challenges and Solutions
Sensor Data Drift
Regular calibration or machine learning-based compensation algorithms.
Long-Term Stability
Watchdog timers and industrial-grade eMMC storage.
Edge Deployment
Integrate lightweight frameworks (ONNX Runtime) for local water quality prediction.
VII. FAQs and Maintenance
Communication Failure: Check SIM signal strength or Ethernet connections.
Data Anomalies: Verify sensor power supply or grounding issues.
System Lag: Optimize software thread priorities.
ARM industrial computers enable cost-effective, intelligent monitoring for water treatment systems. For specific projects, consider
More low-cost industrial solutions:ARMxy SBC BL335
0 notes
Photo

TP-Link Archer AX20 AX1800 Dual Band Wifi 6 Router FEATURES: Dual-Band Wi-Fi 6: Equipped with the latest wireless technology, Wi-Fi 6, for faster speeds, greater capacity, and reduced network congestion Next-Gen 1.8Gbps Speeds: Enjoy smooth streaming, downloading, and gaming all without buffering with Wi-Fi speeds of 1.8Gbps Connect More Devices: Wi-Fi 6 technology communicates more data to more devices using revolutionary OFDMA technology while simultaneously reducing lag Quad-Core Processing: The 1.5GHz quad-core CPU ensures communications between your router and all connected devices are smooth Extensive Coverage: Beamforming, independent FEM, and four antennas combine to deliver focused reception to devices far away Increased Battery Life: Target Wake Time technology reduces your devices’ power consumption to extend their battery life USB Easy Sharing: A USB 2.0 Port enables easy file sharing within your network or building private Cloud Storage Easy Setup: Set up your router in minutes with the powerful TP-Link Tether App Backward Compatible: Supports all previous 802.11 standards and all Wi-Fi devices WIRELESS Standards Wi-Fi 6 IEEE 802.11ax/ac/n/a 5 GHz IEEE 802.11ax/n/b/g 2.4 GHz WiFi Speeds AX1800 5 GHz: 1201 Mbps (802.11ax) 2.4 GHz: 574 Mbps (802.11ax) WiFi Range 3 Bedroom Houses 4× Fixed High-Performance Antennas Multiple antennas form a signal-boosting array to cover more directions and large areas Beamforming Concentrates wireless signal strength towards clients to expand WiFi range High-Power FEM Improves transmission power to strengthen signal coverage WiFi Capacity High Dual-Band Allocate devices to different bands for optimal performance OFDMA Simultaneously communicates with multiple Wi-Fi 6 clients Airtime Fairness Improves network efficiency by limiting excessive occupation 4 Streams Connect your devices to more bandwidth Working Modes Router Mode Access Point Mode HARDWARE Processor 1.5 GHz Quad-Core CPU Ethernet Ports 1× Gigabit WAN Port 4× Gigabit LAN Ports USB Support 1× USB 2.0 Port Supported Partition Formats: NTFS, exFAT, HFS+, FAT32 Supported Functions: Apple Time Machine FTP Server Media Server Samba Server Buttons WPS/Wi-Fi Button Power On/Off Button LED On/Off Button Reset Button Power 12 V ⎓ 1.5 A SECURITY WiFi Encryption WPA WPA2 WPA3 WPA/WPA2-Enterprise (802.1x) Network Security SPI Firewall Access Control IP & MAC Binding Application Layer Gateway Guest Network 1× 5 GHz Guest Network 1× 2.4 GHz Guest Network VPN Server OpenVPN PPTP SOFTWARE Protocols IPv4 IPv6 Parental Controls URL Filtering Time Controls WAN Types Dynamic IP Static IP PPPoE PPTP L2TP Quality of Service QoS by Device Cloud Service Auto Firmware Upgrade OTA Firmware Upgrade TP-Link ID DDNS NAT Forwarding Port Forwarding Port Triggering DMZ UPnP IPTV IGMP Proxy IGMP Snooping Bridge Tag VLAN DHCP Address Reservation DHCP Client List Server DDNS TP-Link NO-IP DynDNS Management Tether App Webpage PHYSICAL Dimensions (W×D×H) 10.2 × 5.3 ×1.5 in (260.2 × 135.0 × 38.6 mm) Package Contents Wi-Fi Router Archer AX20 Power Adapter RJ45 Ethernet Cable Quick Installation Guide OTHER System Requirements Internet Explorer 11+, Firefox 12.0+, Chrome 20.0+, Safari 4.0+, or other JavaScript-enabled browser Cable or DSL Modem (if needed) Subscription with an internet service provider (for internet access) Certifications FCC, CE, RoHS Environment Operating Temperature: 0℃~40℃ (32℉ ~104℉) Storage Temperature: -40℃~70℃ (-40℉ ~158℉) Operating Humidity: 10%~90% non-condensing Storage Humidity: 5%~90% non-condensing TEST DATA WiFi Transmission Power CE:
0 notes
Text
Essentials of Setting up a Business Computer Network

Setting up a computer network for small-to-mid-sized businesses requires extensive planning. Business computer networks link two or more computers so that they can communicate with each other and share information.
Computer networks must remain robust and secure since they support wide-ranging equipment, devices, software, and applications that drive functions ranging from budgeting and inventory management to sales and marketing. The network spans laptops, phones, and printers and connects to internal or external servers that provide needed bandwidth for hosting and distributing data in real time.
Organizations can pick from two basic types of business networks: the local area network (LAN) and the vast area network (WAN). LAN networks use wifi or network cables. It connects devices within a limited geographic footprint, such as a building or office space, and relies on on-site servers. By contrast, WAN setups host network resources off-site and accessed on-demand via a cloud platform and provider that offers secure external hosting.
WAN and LAN networks connect devices using a router that links two or more via the Internet and applies to traditional wired and wireless setups. Professionals recommend using business-grade wifi routers since they contain features such as anti-virus software and firewall systems that filter out SPAM. They often allow for the installation of VPN servers that offer encryption capacities as data travels securely across a network. Encryption minimizes vulnerabilities to outside threats, such as hackers and malware. A quality router continues functioning seamlessly through events such as power outages. Organizations can configure them to optimize bandwidth through controlling and prioritizing usage.
Then, network switches support data flow across networks of computers and peripherals. They determine how a network allocates the bandwidth provided through an internet connection. Switches are programmable via web interface, CLI (command line interface), or SNMP (Simple Network Management Protocol).
Unmanaged switches apply to plug-and-play devices that communicate freely with each other in shared spaces that host personnel and visitors, such as conference rooms, and for shared equipment, such as fax and printing stations. Managed switches provide businesses with ways to control and limit access to data, defining how data flows across a network. They allow the setting of port bandwidths and the creation or modification of local area networks.
Physical cables apply to ports in management protocols. Service providers feature cloud-managed switches for wireless networking that enable remote network access control through a software interface. The wireless local area network (WLAN) defines wifi coverage. It has an access point, which serves as the gateway for users and devices that connect wirelessly to the network.
Business-grade access points have handling capacity designed to accommodate greater traffic flow. Alternatively, coverage range expands through range extenders - though these may slow network speeds and have a limited number of connectable devices.
Many small businesses utilize an underlying wired network to ensure stable connectivity that underpins their high-speed wireless network. The approach accommodates wired connections with stationary devices such as cameras and printers, which fees up wireless bandwidth for wireless-dependent devices such as phones and laptops. Therefore, organizations can use both instead of picking between cable and wireless network environments.
Lastly, pick the right cables. Cables provide sufficient bandwidth to access points and deliver a fast wireless network. Know current cable standards, as with CAT6 for LAN wiring, when picking cables. In addition, ensure that two cables running to each wireless access point have enough capacity. It will accommodate evolving industry standards and allow for extra wired bandwidth as the business grows.
1 note
·
View note
Text
Asus ROG Strix B660 A Gaming WIFI D4 Features: Intel LGA 1700 Socket: Ready for 12th Gen Intel Core, Pentium Gold and Celeron processors Optimal Power Solution: 12+1 power stages with ProCool power connectors, high-quality alloy chokes and durable capacitors to support multi-core processors Optimized Thermal Design: Integrated I/O cover, VRM heatsinks with high conductivity thermal pads, and three onboard M.2 heatsinks High-performance Networking: On-board Intel WiFi 6 (802.11ax) and Intel 2.5 Gb Ethernet with ASUS LANGuard Best Gaming Connectivity: Supports HDMI 2.1 and DisplayPort 1.4 output, three M.2 slots, as well as USB 3.2 Gen 2×2 Type-C Intelligent Control: ASUS-exclusive AI Cooling, AI Networking and Two-Way AI Noise Cancelation to simplify setup and improve performance DIY Friendly Design: M.2 Q-Latch, pre-mounted I/O shield, BIOS FlashBack button and Q-LED Unmatched Personalization: ASUS-exclusive Aura Sync RGB lighting, including one RGB header and three addressable Gen 2 headers Industry-leading Gaming Audio: ALC4080 with Savitech SV3H712 amplifier, along with DTS Sound Unbound and Sonic Studio III Renowned Software: Bundled 60-day free trial of AIDA64 Extreme, and an intuitive UEFI BIOS dashboard ROG Strix B660-A Gaming WiFi D4 offers premium power delivery and optimized cooling to unleash the full force of the latest 12th Gen Intel Core processors. Onboard PCIe 5.0, WiFi 6 and three PCIe 4.0 M.2 slots provide lightning-fast data transfers for an endless variety of scenarios, and ASUS-exclusive intelligent controls to help optimize PC settings. On top of all that, DIY-friendly innovations help simplify the PC building process to get to you up and running smoothly. TEAMED POWER STAGES 12+1 power stages combine high-side and low-side MOSFETS and drivers into a single package, delivering the power and efficiency that the latest Intel processors can take full advantage of. ALLOY CHOKES AND CAPACITORS High-end chokes and durable capacitors are engineered to resist extreme temperatures, enabling performance that exceeds industry standards. PROCOOL POWER CONNECTOR The ASUS ProCool socket is built to exacting specifications to ensure flush contact with the PSU power lines, enabling lower impedance and better heat dissipation. DIGI+ POWER CONTROL The Digi+ voltage regulator module (VRM) is one of the finest in the industry, ensuring ultra-smooth and clean power delivery to the CPU. SIX-LAYER PCB A multi-layered printed circuit board design quickly dissipates heat around the voltage regulators to improve overall system stability and provide the CPU with more overclocking headroom. Two-Way AI Noise Cancelation This powerful ASUS-exclusive utility leverages a massive deep-learning database to reduce background noise from the microphone* and incoming audio while preserving voices. Distracting keyboard clatter, mouse clicks and other ambient noises are removed so you can hear and be heard with perfect clarity while gaming or during calls. Asus ROG Strix B660 A Gaming WIFI D4 AI Cooling ASUS AI Cooling technology automatically manages and controls motherboard-connected fans to ensure optimal settings based on current system load and temperature. AI Networking The proprietary ROG GameFirst VI utility is designed to help all users beginners, experts, and everyone in between optimize network settings to ensure smooth online gameplay. New to this generation, GameFirst VI features AI-enhanced identification and boost technologies to ensure faster and smarter network optimization. Adaptive Intelligence GameFirst VI notes what you’re currently doing and adjusts bandwidth accordingly to ensure smooth online experiences, even when multitasking. OptiMem II OptiMem II technology offers higher clock speeds through trace layout optimizations that significantly reduce signal distance and crosstalk while enhancing memory stability and compatibility. ROG Strix B660-A Gaming WiFi D4 supports up to 128 GB of DDR4 memory across four slots.
WiFi 6 (802.11 ax) Onboard WiFi 6 (802.11ax) supports ultrafast wireless-networking speeds, improved capacity and better performance in dense wireless environments, providing exceptional online gaming experiences. Pair your motherboard with ASUS WiFi 6 routers to fully experience the networking potential of WiFi 6. Intel 2.5 Gb Ethernet Onboard 2.5 Gb Ethernet gives your wired connection a boost, with up to a 2.5x improvement over standard Ethernet connections for faster file transfers, smoother lag-free gaming and high-res video streaming. SupremeFX ROG SupremeFX is a unique blend of hardware and software that provides superior audio. In ROG Strix B660-A Gaming WiFi D4, SupremeFX features the ALC4080 codec to increase playback resolution from 192 kHz to 384 kHz across all channels. The front-panel output is streamed through a highly integrated Savitech amplifier thatands capable of driving of a wide variety of gaming headsets and high-fidelity headphones. Undeniably ROG Strix The ROG Strix B660-A Gaming WiFi D4 will turn heads with a striking silver-white finish that contrasts with a bold Aura RGB-illuminated glitch-effect logo. Meanwhile, parallel strakes and dotted text on the aluminum I/O shroud, M.2 and PCH heatsinks tie the whole aesthetic together and underline the ROG Strix fundamentals of speed, diversity and attitude. M.2 Q-LATCH The innovative Q-Latch makes it easy to install or remove an M.2 SSD without the need for specific tools. The design employs a simple locking mechanism to secure the drive and neatly eliminate traditional screws. CERTIFIED COMPATIBILITY ROG Strix motherboards undergo an extensive certification program to ensure compatibility with the widest range of components and devices. Our Qualified Vendor List (QVL) provides a reference for identifying guaranteed-compatible components and memory. ASUS AIO coolers are also compatible with a wide variety of CPUs, up to and including 12th Gen Intel processors, giving you ultimate flexibility to cool the CPU that fits your needs. THE ROG STRIX ECOSYSTEM AWAITS Level up your game with ROG Strix. Enjoy complementary aesthetics, control and compatibility across AIO coolers, cases, peripherals, and much more. ROG offers more choices than any other brand. UEFI BIOS The renowned ROG UEFI (BIOS) provides everything you need to configure, tweak, and tune your rig. It offers intelligently simplified options for newcomers to PC DIY and more comprehensive features for seasoned veterans. Sonic Studio III ROG Sonic Studio supports HRTF-based (head-related transfer function*) virtual surround for VR headsets, casting an immersive aural landscape that draws you deeper into the action. The intuitive Sonic Studio interface also offers a range of EQ options and one-click presets, allowing you to tailor acoustics to suit personal preferences or the characteristics of your headset. DTS: Sound Unbound dts ROG Strix B660 motherboards are pre-loaded with the DTS Sound Unbound app that envelops you in audio as never before, conjuring whole new levels of immersion for extraordinary gaming and entertainment experiences. By leveraging Windows Sonic spatial technology, DTS Sound Unbound delivers audio in a virtual 3D space putting you right in the middle of the soundscape, where you can sense the location and direction of every gunshot, footstep or other sound in your virtual environment. Stereo Sound: Discrete left and right audio channels enable headphone or two-speaker setup. Surround Sound: Audio is split and served over multiple speaker channels e.g., 5.1 or 7.1 to create an enveloping experience on a single, logical plane. Spatial Sound: A virtual audio sphereand effect creates astonishing 360° immersion with you at the center, where sounds seem to travel in all directions. AIDA64 EXTREME ROG Strix B660 motherboards include an AIDA64 Extreme 60 days free trial. This industry-leading system information tool provides detailed information about installed hardware
and software, and it also provides benchmarks for measuring performance of the entire system or individual components. AIDA64 Extreme includes a monitoring and diagnostics feature to detect and prevent hardware issues. All vital system sensors can be tracked in real time, allowing voltage readings, fan speeds, and temperature information to be displayed on the desktop or sent to dedicated displays or to the OLED panels of ROG AIO liquid coolers*. Armoury Crate Armoury Crate is a software utility designed to give you centralized control of supported gaming products, making it easy to tune the look and feel of your system. From a single intuitive interface, Armoury Crate helps you customize RGB lighting and effects for compatible devices and synchronize them with Aura Sync to create a unified lighting scheme across your system. In addition, Armoury Crateands Fan Xpert4 tool provides comprehensive control over fans, water pumps and all-in-one (AIO) coolers. Asus ROG Strix B660 A Gaming WIFI D4
0 notes
Text
It's iPad Season Again, and Apple's New Tablets Promise Something Different

While we didn't get a new iPad Mini in today's Apple event (boo), the Cupertino tech giant nevertheless unleashed a new onslaught of portable computing goodness with its new iPad Pro and iPad Air models. Of course as with every new product launch, the new devices come with some significant upgrades in terms of overall performance, as well as changes to design. With that in mind, let's get started! New iPad Air First up is the new iPad Air, which comes in two sizes including an 11-inch and a new 13-inch model. As you can probably tell from the name, the iPad Air is designed to be portable, and comes with a new upgrade thanks to Apple's M2 chipset inside. The company also says that it's equipped the Air with a faster CPU and GPU, as well as a newer 16-core Neural Engine courtesy of the M2 chipset, which should prove to be a boost with the device's AI capabilities. Another change to the iPad Air is the front-facing ultra wide 12MP camera, which is now located horizontally making it more ideal for work calls and even just casual video chats; meanwhile, the rear of the tablet features a 12MP camera which supports 4K video, as well as 240-fps slow motion capture. For connectivity, Apple does offer the iPad Air in both Wifi and cellular models with 5G support for on-the-go connectivity. For pricing, the 11-inch iPad Air still starts at £599, while the 13-inch iPad Air is a bit more expensive coming in at £749. Folks looking to grab the new Air models can order them, with availability beginning on May 15. Going Pro For this year's iPad Pro models, Apple went all-in with performance thanks to the inclusion of the new M4 chip inside. It's a rare sight to see the company introduce a new and powerful SoC in a tablet launch, given that it highlights its M-series chipsets alongside its Mac device launches. With that said, the M4 does make for a very interesting package with the iPad Pro, although there's more to it than just a shiny new chip. CHECK OUT: Apple’s New M4 Chip Finally Makes its Debut Similar to the new iPad Air, the iPad Pro 2024 comes in two sizes at 11 inches and 13 inches, which both feature Apple's "Ultra Retina XDR" display technology, all wrapped in a design which the company claims is the thinnest to date. The company says that the M4 is tailor-made to be able to run the new display technology, providing users with a more immersive and visually-appealing user experience. Of course, this upgrade also extends to productivity - Apple has also launched a new Apple Pencil Pro with the iPad Pro, which packs a ton of tech inside, including support for haptic feedback, gesture controls, and improved usability. There's also a newly-redesigned Magic Keyboard, which is a bit slimmer than before. As with most other hardware manufacturers in the past couple of years, Apple is targeting AI-powered capabilities with the M4 chip - for one, the M4 features Apple's next-generation Neural Engine, which is able to perform an impressive 38 trillion operations per second (60x faster than the original A11 Bionic chip), and can work seamlessly in tandem with the CPU, GPU, and high-bandwidth memory for AI-powered tasks. During its presentation, the company was rather confident that power users after a productivity-focused device will find a lot to love about the iPad Pro, especially with support for apps such as Final Cut Pro, and other powerful video editing software. On the camera side of things, the iPad Pro features a 12MP back camera that comes with vibrant Smart HDR images and video - Apple claims this results in better-looking colours, texture, and even low-light details. There's also a new adaptive True Tone flash that makes document scanning on the new iPad Pro a bit easier, with improved visual quality as well - the camera can identify documents right in the Camera app, and if a shadow is in the way, it takes multiple photos with the adaptive flash, stitching the scan together for a better-looking image. In terms of pricing, the 11-inch iPad Pro starts at £999 for the Wi-Fi model, and £1,199 for the Wi-Fi + Cellular model. Meanwhile, the 13-inch iPad Pro starts at £1,299 for the Wi-Fi model, and £1,499 for the Wi-Fi + Cellular model. Read the full article
0 notes
Text
can't do secureline vpn from pro club wifi
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
can't do secureline vpn from pro club wifi
SecureLine VPN troubleshooting
SecureLine VPN troubleshooting may be necessary when you encounter connection issues, slow speeds, or other problems while using the service. To ensure a seamless experience with SecureLine VPN, follow these troubleshooting steps:
Check your internet connection: Before troubleshooting SecureLine VPN, make sure you have a stable internet connection. A weak or unreliable connection can impact the VPN's performance.
Restart SecureLine VPN: Sometimes, simply restarting the VPN application can resolve minor issues. Close the app completely and reopen it to see if this resolves the problem.
Select a different server: If you are experiencing slow speeds or connection issues, try connecting to a different server location. SecureLine VPN has servers worldwide, so choose one closer to your physical location for faster speeds.
Update SecureLine VPN: Ensure you are using the latest version of the VPN software. Updates often include bug fixes and performance improvements that can resolve common issues.
Disable any conflicting applications: Other VPN software or security programs running simultaneously can interfere with SecureLine VPN. Disable any conflicting applications and try connecting again.
Contact customer support: If you have tried the above steps and are still experiencing issues, reach out to SecureLine VPN customer support for further assistance. They can provide personalized troubleshooting tips based on your specific problem.
By following these troubleshooting tips, you can address common issues with SecureLine VPN and enjoy a secure and reliable connection for your online activities.
Pro Club WiFi restrictions
Pro Club WiFi restrictions are measures implemented by venues such as bars, cafes, and restaurants to manage and control the use of their WiFi network by patrons. These restrictions are imposed to ensure fair usage, network security, and overall customer satisfaction.
One common WiFi restriction at Pro Clubs is time limits. Patrons are often given a set amount of time to access the WiFi network before being automatically disconnected. This helps to prevent individuals from hogging the network and allows more customers to utilize the service.
Another restriction is bandwidth control. By limiting the amount of data that can be consumed by each user, Pro Clubs can prevent network congestion and ensure a smooth browsing experience for all customers. Bandwidth control also helps to optimize network performance during peak hours.
Some Pro Clubs also implement content filtering on their WiFi networks. This restriction blocks access to certain websites, such as adult content or gambling sites, to maintain a family-friendly environment and comply with local regulations.
Overall, Pro Club WiFi restrictions are in place to create a secure and enjoyable internet experience for all customers. By setting these limitations, Pro Clubs can better manage their network resources, prevent abuse, and enhance overall customer satisfaction.
VPN connection issues
Experiencing VPN connection issues can be frustrating, especially when you rely on a VPN for privacy, security, or accessing geo-restricted content. These problems can manifest in various forms, disrupting your online activities and potentially exposing your data to risks. Understanding common VPN connection issues and their solutions can help you troubleshoot and resolve them effectively.
One frequent issue is slow connection speeds. This can occur due to network congestion, server overload, or inadequate bandwidth. To address this, try connecting to a different server, preferably one closer to your physical location, or upgrading to a VPN plan with faster speeds.
Another common problem is intermittent connections or frequent disconnections. This could be caused by unstable internet connections, firewall settings, or outdated VPN software. To troubleshoot, ensure your internet connection is stable, adjust firewall settings to allow VPN traffic, and update your VPN client to the latest version.
Furthermore, some users encounter compatibility issues with their devices or operating systems. Certain VPN protocols may not be supported by all devices, leading to connectivity issues. In such cases, try switching to a different VPN protocol or updating your device's software.
Additionally, VPN blocking by network administrators or internet service providers (ISPs) can hinder connection attempts. Employing obfuscation techniques or using VPN servers that offer stealth capabilities can help bypass such restrictions.
Lastly, if all else fails, reaching out to your VPN provider's customer support can provide tailored assistance and troubleshooting guidance. They can offer insights into specific issues and recommend solutions based on your setup and circumstances.
By understanding and addressing these common VPN connection issues, you can ensure a smoother and more secure online experience. Regularly monitoring your VPN connection and staying informed about potential issues can help mitigate problems before they escalate.
Network security solutions
Network security solutions are vital components of any organization's digital infrastructure in today's increasingly interconnected world. As businesses continue to rely on technology for their operations, the need to protect sensitive data from cyber threats has become more critical than ever before.
One of the most common network security solutions is the implementation of firewalls. Firewalls act as a barrier between a trusted internal network and untrusted external networks, monitoring and controlling incoming and outgoing network traffic based on predetermined security rules. This helps prevent unauthorized access and potential cyber attacks.
Another essential network security solution is intrusion detection and prevention systems (IDPS). IDPS work by actively monitoring network traffic for signs of suspicious activity or known threats. When a potential threat is detected, the system can automatically take action to block the threat and protect the network from harm.
Virtual private networks (VPNs) are also popular network security solutions that enable secure remote access to a company's network. By encrypting data transmitted between the user and the network, VPNs help safeguard sensitive information from interception by unauthorized parties.
In conclusion, investing in robust network security solutions is crucial for safeguarding an organization's digital assets and maintaining the trust of customers and stakeholders. By implementing firewalls, IDPS, VPNs, and other security measures, businesses can mitigate the risks associated with cyber threats and operate in a secure and protected digital environment.
SecureLine VPN alternatives
In a world where privacy and security are paramount concerns, finding the right VPN (Virtual Private Network) service is essential. While SecureLine VPN by Avast is a popular choice for many users, there are several alternatives worth considering for those seeking robust protection and versatile features.
One notable alternative is ExpressVPN, renowned for its blazing-fast speeds and top-notch encryption. With servers in numerous countries and a user-friendly interface, ExpressVPN offers seamless access to geo-restricted content while ensuring your online activities remain private.
For users prioritizing affordability without compromising on security, NordVPN presents a compelling option. Boasting a vast server network and advanced security features like Double VPN and Onion over VPN, NordVPN is a favorite among budget-conscious individuals seeking reliable protection.
Another worthy contender is CyberGhost VPN, known for its intuitive interface and specialized servers optimized for streaming and torrenting. With strong encryption protocols and a strict no-logs policy, CyberGhost VPN provides peace of mind for users concerned about their digital footprint.
Those looking for a VPN tailored specifically for torrenting may find comfort in the features offered by Private Internet Access (PIA). With unlimited bandwidth and a SOCKS5 proxy included, PIA ensures fast and secure torrent downloads without sacrificing privacy.
Lastly, Surfshark stands out as an affordable yet feature-rich VPN solution. Offering unlimited simultaneous connections and a built-in ad blocker, Surfshark is ideal for households or individuals with multiple devices seeking comprehensive protection.
While SecureLine VPN remains a solid choice for many users, exploring these alternatives allows individuals to find the VPN service that best fits their specific needs and preferences, ensuring a safe and secure online experience.
0 notes
Text
Wisp Software: Empowering Efficiency and Collaboration through Innovative Solutions
In the ever-evolving landscape of technology, software plays a pivotal role in shaping industries and redefining business processes. One such innovative solution that has gained traction in recent years is Wisp software. Wisp, an acronym for Workflow Information Software Platform, has emerged as a game-changer in enhancing efficiency, collaboration, and transparency across various sectors. Its multifaceted capabilities have propelled it into the spotlight as a go-to choice for businesses seeking streamlined workflows and optimized operations.
The Essence of Wisp Software
At its core, Wisp software is designed to streamline workflows, simplify communication, and enhance project management. It acts as a centralized hub where teams can collaboratively plan, execute, and track projects, tasks, and resources. By seamlessly integrating various tools and functionalities, Wisp CRM software bridges the gap between project managers, team members, and stakeholders, fostering a holistic approach to project delivery.
Key Features and Functionalities
Centralized Project Management: Wisp offers a comprehensive project management dashboard that provides a bird’s-eye view of ongoing projects, milestones, and critical tasks. Project managers can allocate resources, assign tasks, and set deadlines, all within an intuitive and user-friendly interface.
Customizable Workflows: Every organization has unique workflows and processes. Wisp software allows users to create customized workflows that mirror their specific operational needs. This adaptability ensures that teams can seamlessly integrate the software into their existing processes.
Real-time Collaboration: One of Wisp’s standout features is its ability to facilitate real-time collaboration. Team members can communicate, share documents, and collaborate on tasks without the need to switch between different platforms or tools. This dynamic collaboration fosters improved communication and faster decision-making.
Resource Management: Efficient resource allocation is crucial for project success. Wisp bandwidth software provides tools for resource tracking, workload management, and resource optimization. This ensures that teams are operating at peak efficiency and that resources are utilized judiciously.
Document Management: Keeping track of documents and files can be challenging, especially in complex projects. Wisp offers robust document management capabilities, allowing users to store, organize, and access files with ease. Version control and access permissions further enhance data security and management.
Analytics and Reporting: Data-driven insights are invaluable for making informed decisions. Wisp’s analytics and reporting features provide visual representations of project progress, resource utilization, and other key performance indicators. This empowers stakeholders with actionable insights for continuous improvement.
Benefits for Businesses
Enhanced Efficiency: Wisp software streamlines workflows, minimizes manual tasks, and reduces bottlenecks. This results in faster project delivery and improved operational efficiency and helps in wifi solutions for university.
Improved Collaboration: By providing a unified platform for communication and collaboration, Wisp fosters teamwork and ensures that all stakeholders are on the same page.
Transparency: Transparent project management leads to better accountability and reduced misunderstandings. Wisp’s transparency ensures that everyone involved has visibility into project progress and status.
Scalability: Wisp software is designed to accommodate both small teams and large enterprises. Its scalability makes it a versatile solution that can grow alongside an organization’s needs. Visit for cloud hosted hospot management software.
Risk Mitigation: With real-time tracking and analytics, Wisp helps identify potential roadblocks or deviations from the plan, allowing for timely interventions and risk mitigation.
Real-world Applications
Wisp software finds applications in a wide range of industries. In architecture, engineering, and construction (AEC), it aids in project planning, document management, and collaboration among design and construction teams. In marketing and creative agencies, it assists in managing client projects, creative briefs, and campaign execution. Similarly, it benefits IT departments, manufacturing units, and healthcare institutions by optimizing their processes and enhancing collaboration.
The Road Ahead
As technology continues to evolve, so too will Wisp software. The future holds the promise of even more advanced features, such as AI-powered insights, predictive analytics, and enhanced integration capabilities. With the increasing demand for remote work solutions and efficient project management tools, Wisp is well-positioned to play a pivotal role in shaping the way businesses operate and collaborate. Read more about hotspot management software.
In conclusion, Wisp software stands as a testament to the power of innovation in addressing complex business challenges. Its ability to streamline workflows, enhance collaboration, and provide actionable insights sets it apart as a vital tool for modern organizations. By embracing Wisp software, businesses can navigate the intricacies of project management with confidence, efficiency, and success.
#wisp crm#wisp software#wifi bandwidth software#cloud hosted hospot management software#wifi solutions for university#hotspot management software
0 notes
Text
TP-Link TL-SG108-M2
Introduction
Introducing the TP-Link TL-SG108-M2, a cutting-edge 8-port Multi-Gigabit Unmanaged Network Switch that redefines connectivity and efficiency in your network setup. Designed with advanced features and unparalleled performance, this Ethernet splitter is a seamless blend of innovation and convenience. With its 2.5G bandwidth capabilities, the TL-SG108-M2 paves the way for lightning-fast data transfers, ensuring your network operates at the speed of modern demands.
Say goodbye to complicated installations – the TL-SG108-M2 boasts a hassle-free Plug & Play design that allows for instant integration into your network. Whether you’re a tech-savvy professional or a casual user, this switch simplifies the process, eliminating the need for complex configurations. Its versatile nature accommodates both desktop and wall-mount setups, giving you the flexibility to optimize your space.
Built to withstand the rigors of modern networking environments, the TL-SG108-M2 features a fanless metal design, ensuring reliable performance while remaining whisper-quiet. The durable construction enhances heat dissipation, contributing to the switch’s longevity and stability.
Features
BrandTP-LinkNumber of Ports8Included ComponentsTL-SG108-M2, Power Adapter, Installation Guide, Rubber FeetColor8 Port, 2,5GCompatible DevicesDesktop
Additional Details
【Eight 2.5Gbps Ports for Super-Fast Connections】8× 2.5-Gigabit ports unlock the highest performance with Multi-Gig bandwidth and provide up to 40 Gbps of switching capacity.
【Auto-Negotiation】Auto-negotiation intelligently senses the link speeds and adjusts between 3-speeds (100Mb/1G/2.5G) for compatibility and optimal performance for all your devices, including 2.5G WiFi 6 AP, 2.5G NAS, 2.5G PCIe Adapter, 2.5G Server, gaming computer, 4K video, and more.
【Hassle-Free Cabling】Instantly upgrade to 2.5 Gbps performance without the need to upgrade to Cat6 wiring, reducing wiring costs and hassle.
【Reliable and Quiet】IEEE 802.3X flow control provides reliable data transfer and a fanless design ensures quiet operation.
【Plug and Play】Easy setup with no software installation or configuration needed.
【Sturdy Metal Case】Durable metal casing and desktop/wall-mounting design are well-suited for different environments.
Read More>>

0 notes
Text
Capgemini is hiring freshers as WiFi Developers in Bangalore | Placement Officer
Capgemini is hiring freshers as WiFi Developers in Bangalore | Placement Officer

Capgemini is currently hiring freshers for the role of WiFi Developers in Bangalore. Join our team and contribute to the development of software for WiFi products, including Access Points and Wireless LAN Controllers. This role requires working knowledge of HostAP Daemon software, understanding of WiFi protocols and security, and basic IP data networking skills. Experience with SRS and Design documents, field debugging of WiFi issues, and managing a small team of engineers are highly valued. Strong programming skills in C and familiarity with the 802.11n/ac standard are essential. Secondary skills include familiarity with WiFi chipset SDKs and the Linux wifi stack. At Capgemini, we are a global leader in technology solutions, dedicated to unleashing human energy through technology for a sustainable future. Join us and shape the future you want. Apply now!
About the job
Job Description· Development of software for WiFi products such as Access Points and Wireless LAN Controllers.
Working knowledge of HostAP Daemon software and its interfaces· Working knowledge of 11ax a plus, if not at least theoretical understanding of 11ax.
Deep understanding of the 802.11 management plane (protocols), WiFi security (WPA2/3), beam forming, band steering, MIMO, Channel Bandwidth, MCS rates etc.
Basic IP data networking.
Contribution towards SRS and Design documents, and is mandatory.
Field debugging of WiFi issues an added plus.
Should have managed at least a small team of engineers. Primary Skills· Very strong in C programming· Working knowledge of the 802.11n/ac standard. Read More
#CapgeminiJobs#WiFiDevelopers#FreshersHiring#BangaloreJobs#TechnologyCareers#SoftwareDevelopment#NetworkingSkills#CProgramming#LinuxProgramming#WirelessTechnology#FutureofTechnology#CapgeminiCulture#TransformingBusinesses#InnovationandTechnology#GlobalLeader#UnleashHumanEnergy#ShapeYourFuture
0 notes
Text
What is NDI HX3? - Videoguys
New Post has been published on https://thedigitalinsider.com/what-is-ndi-hx3-videoguys/
What is NDI HX3? - Videoguys


On this week’s Videoguys Live, James is exploring the world of NDI HX3! This technology enhances video streaming with low latency and high-quality visuals, all while using minimal bandwidth. NDI is perfect to use for live events, remote production, and more.
Watch the full video below:
youtube
In Today’s Show We Will Discuss:
What is NDI?
How Do My NDI Devices Communicate?
Full bandwidth NDI
NDI HX – 2&3
Benefits of using HX3
Workflow examples of technology using HX3
What is NDI?
NDI Stands for “Network Device Interface”
NDI is used to transmit high quality, low latency video and audio signals over a local area network (LAN)
Paired with a Network switch NDI Allows users to send video, control and Power to an NDI Device through a standard Cat6 Ethernet cable.
It is widely used in broadcast systems, live streaming, video conferencing, and digital signage, among other applications.
How Do My NDI Devices Communicate?
NETGEAR M4250 Pro AV Switches
The M4250 Line of switches are designed specifically for AV over IP with NDI and Dante Presets available. Some switches even support ST 2110!
Netgear’s Engage software makes changing profiles a breeze.
Designed with Video in mind. They are rack mountable and quiet.
The M4250 acts like a hub for all of your NDI Devices to communicate to each other
NETGEAR is committed to AV over IP
Full Bandwidth NDI
Full bandwidth NDI is the original version of NDI. It provides High Quality, low latency, frame accurate video and audio over IP.
Pros
Cons
High Quality – Closest to SDI quality
High bandwidth required
Low Latency – 16ms
(1 frame)
Can require more advanced network infrastructure
Frame accurate syncing of Audio and Video
NDI HX2
Unlike Full bandwidth, HX2 uses H.264 compression to minimize the use of bandwidth on the network while still being able to send video over the network
Pros
Cons
Uses the least amount of Bandwidth possible
Compressed video can add more latency
Low latency 1-3 frames
Compressing the video can lower quality
Frame accurate syncing of Audio and Video
NDI HX3
NDI HX3 Is the middle ground between Full Bandwidth and NDI HX3. It offer compressed video using HEVC allowing for lower bandwidth usage than full bandwidth, while offering better image quality than NDI HX2
Pros
Cons
Less Bandwidth required than Full Bandwidth NDI
Compressed video can add more latency
Low latency 1-2 frames
Compressing the video can lower quality
Better image quality than NDI HX2
When Should I Use Full Bandwidth, HX2 or HX3?
Use Full bandwidth when quality and lowest latency is of utmost importance. Just keep in mind that this does require more Bandwidth
Use NDI HX2 When you do not have high bandwidth and want multiple cameras on the network. Just keep in mind this will have lower quality/ more latency
Use NDI HX3 as a middle ground, when you have some restrictions on bandwidth, but still want to have good Image Quality.
What are some products that use NDI HX3?
Vizrt PTZ3 PLUS and PTZ3 UHD PLUS Cameras
BirdDog MAKI Ultra, X1, and X1 Ultra Cameras
4K/60p
12X & 20X available
Compact
Super-fast Auto Focus
HDMI/SDI/USB/IP
NDI HX3
On-board buttons
1080/60p
20X Zoom
Tally Light
AI Auto Focus tracking
HDMI/USB/IP
NDI HX3
WiFi Connection
E-ink Label
Integrated NDI HX decoder
4K/30p
12X Zoom
Tally Light
AI Auto Focus tracking
HDMI/USB/IP
NDI HX3
WiFi Connection
E-ink Label
Integrated NDI HX decoder
JVC KY-PZ510N (NDIHX3 with free firmware update) and KY-PZ540N
PTZOptics Move 4K
NDI|HX3 Native
SONY Optics deliver up to 4Kp60
Total Connectivity:
HDMI, 3G-SDI, USB & IP Output. Plus POE!
Built-In Auto-Tracking
Available in gray or white
Kiloview
4K 12G-SDI to NDI Bi-Directional Converter 4K HDMI to NDI Bi-Directional Converter Now with special of free 1TB SSD!
#4K#ADD#ai#amp#applications#audio#bi#board#buttons#Cameras#compression#connectivity#decoder#devices#Digital Signage#Events#firmware#focus#Full#hdmi#how#Infrastructure#Ink#IP#it#lan#latency#LESS#Light#local area network
0 notes
Photo

TP-Link Archer AX20 AX1800 Dual Band Wifi 6 Router FEATURES: Dual-Band Wi-Fi 6: Equipped with the latest wireless technology, Wi-Fi 6, for faster speeds, greater capacity, and reduced network congestion Next-Gen 1.8Gbps Speeds: Enjoy smooth streaming, downloading, and gaming all without buffering with Wi-Fi speeds of 1.8Gbps Connect More Devices: Wi-Fi 6 technology communicates more data to more devices using revolutionary OFDMA technology while simultaneously reducing lag Quad-Core Processing: The 1.5GHz quad-core CPU ensures communications between your router and all connected devices are smooth Extensive Coverage: Beamforming, independent FEM, and four antennas combine to deliver focused reception to devices far away Increased Battery Life: Target Wake Time technology reduces your devices’ power consumption to extend their battery life USB Easy Sharing: A USB 2.0 Port enables easy file sharing within your network or building private Cloud Storage Easy Setup: Set up your router in minutes with the powerful TP-Link Tether App Backward Compatible: Supports all previous 802.11 standards and all Wi-Fi devices WIRELESS Standards Wi-Fi 6 IEEE 802.11ax/ac/n/a 5 GHz IEEE 802.11ax/n/b/g 2.4 GHz WiFi Speeds AX1800 5 GHz: 1201 Mbps (802.11ax) 2.4 GHz: 574 Mbps (802.11ax) WiFi Range 3 Bedroom Houses 4× Fixed High-Performance Antennas Multiple antennas form a signal-boosting array to cover more directions and large areas Beamforming Concentrates wireless signal strength towards clients to expand WiFi range High-Power FEM Improves transmission power to strengthen signal coverage WiFi Capacity High Dual-Band Allocate devices to different bands for optimal performance OFDMA Simultaneously communicates with multiple Wi-Fi 6 clients Airtime Fairness Improves network efficiency by limiting excessive occupation 4 Streams Connect your devices to more bandwidth Working Modes Router Mode Access Point Mode HARDWARE Processor 1.5 GHz Quad-Core CPU Ethernet Ports 1× Gigabit WAN Port 4× Gigabit LAN Ports USB Support 1× USB 2.0 Port Supported Partition Formats: NTFS, exFAT, HFS+, FAT32 Supported Functions: Apple Time Machine FTP Server Media Server Samba Server Buttons WPS/Wi-Fi Button Power On/Off Button LED On/Off Button Reset Button Power 12 V ⎓ 1.5 A SECURITY WiFi Encryption WPA WPA2 WPA3 WPA/WPA2-Enterprise (802.1x) Network Security SPI Firewall Access Control IP & MAC Binding Application Layer Gateway Guest Network 1× 5 GHz Guest Network 1× 2.4 GHz Guest Network VPN Server OpenVPN PPTP SOFTWARE Protocols IPv4 IPv6 Parental Controls URL Filtering Time Controls WAN Types Dynamic IP Static IP PPPoE PPTP L2TP Quality of Service QoS by Device Cloud Service Auto Firmware Upgrade OTA Firmware Upgrade TP-Link ID DDNS NAT Forwarding Port Forwarding Port Triggering DMZ UPnP IPTV IGMP Proxy IGMP Snooping Bridge Tag VLAN DHCP Address Reservation DHCP Client List Server DDNS TP-Link NO-IP DynDNS Management Tether App Webpage PHYSICAL Dimensions (W×D×H) 10.2 × 5.3 ×1.5 in (260.2 × 135.0 × 38.6 mm) Package Contents Wi-Fi Router Archer AX20 Power Adapter RJ45 Ethernet Cable Quick Installation Guide OTHER System Requirements Internet Explorer 11+, Firefox 12.0+, Chrome 20.0+, Safari 4.0+, or other JavaScript-enabled browser Cable or DSL Modem (if needed) Subscription with an internet service provider (for internet access) Certifications FCC, CE, RoHS Environment Operating Temperature: 0℃~40℃ (32℉ ~104℉) Storage Temperature: -40℃~70℃ (-40℉ ~158℉) Operating Humidity: 10%~90% non-condensing Storage Humidity: 5%~90% non-condensing TEST DATA WiFi Transmission Power CE:
0 notes
Text
In this era of interconnected devices, it's essential to ensure the security of our Wi-Fi networks. One aspect of this security is monitoring the devices connected to our network to detect any unauthorized access or potential threats. In this blog post, we will explore how you can keep an eye on devices connected to your Wi-Fi network and maintain control over your network's security. Let's dive in. 1. Accessing Your Router's Admin Panel: To monitor devices connected to your Wi-Fi network, you need to access your router's administrative panel. Open a web browser and type in the default gateway IP address, which is typically mentioned on the router's back or in the user manual. Enter the login credentials to access the admin panel. 2. Viewing the Device List: Once you've accessed the router's admin panel, look for a section or tab labeled "Device List" or "Connected Devices." This section displays a list of all the devices currently connected to your Wi-Fi network. You should be able to see the device names, IP addresses, and MAC addresses associated with each device. Read also: How to Make Wifi Antenna for Android Phone 3. Recognizing Known Devices: Identify the devices you are already familiar with, such as your smartphones, laptops, tablets, and smart home devices. Make a note of their IP and MAC addresses for reference. This way, it becomes easier to identify any unknown or suspicious devices on your network. 4. Identifying Unknown or Suspicious Devices: While reviewing the connected device list, keep an eye out for any unfamiliar devices. Unknown devices may indicate unauthorized access to your Wi-Fi network. Look for unfamiliar device names or MAC addresses that you cannot attribute to any known devices in your home or office. 5. Changing Wi-Fi Password: If you suspect unauthorized access or believe your network's security has been compromised, it is advisable to change your Wi-Fi password immediately. By doing so, you'll force all connected devices to reauthenticate with the new password, effectively disconnecting any unauthorized users. 6. MAC Address Filtering: Many routers offer a feature called MAC address filtering. By enabling this feature, you can specify which devices are allowed to connect to your network based on their MAC addresses. This adds an extra layer of security and prevents unknown devices from connecting to your network, even if they have the correct password. 7. Monitoring Network Traffic: To get a deeper understanding of the devices connected to your Wi-Fi network, you can monitor network traffic using third-party software or network monitoring tools. These tools provide detailed insights into the traffic generated by each device, helping you identify potential security risks or bandwidth hogs. 8. Using Network Security Apps: Several mobile apps can assist you in monitoring your Wi-Fi network. These apps provide real-time notifications about new devices connecting to your network and allow you to block or disconnect devices remotely. Some popular options include Fing, NetCut, and Wi-Fi Analyzer. 9. Updating Firmware and Security Patches: Regularly updating your router's firmware is crucial for maintaining network security. Router manufacturers often release firmware updates to fix vulnerabilities and enhance security. Check your router manufacturer's website for the latest firmware version and follow their instructions to update it. 10. Utilizing Guest Networks: If your router supports guest networks, consider enabling this feature. Guest networks provide a separate Wi-Fi network for visitors, keeping them isolated from your main network. This way, even if someone gains access to the guest network, they won't be able to access your primary network or connected devices. Conclusion: Keeping an eye on devices connected to your Wi-Fi network is an essential step in maintaining network security. By monitoring the device list, identifying unknown devices, changing passwords, enabling
MAC address filtering, monitoring network traffic, and utilizing security apps, you can ensure that only authorized
0 notes
Text
Asus Prime Z690 P WIFI D4 Intel Z690 (LGA 1700) ATX motherboard with PCIe 5.0, three M.2 slots, 14+1 DrMOS, DDR4, HDMI , DisplayPort , Intel WiFi 6, 2.5 Gb Ethernet, USB 3.2 Gen 2×2 Type-C , front USB 3.2 Gen 1 Type-C , Thunderbolt 4 support and Aura Sync RGB lighting Intel LGA 1700 socket: Ready for 12th gen Intel processors Enhanced power solution: 14+1 DrMOS, 8+4 pin ProCool connector, alloy chokes and durable capacitors for stable power delivery Comprehensive cooling: Large VRM heatsinks, M.2 heatsink, PCH heatsink, hybrid fan headers and Fan Xpert 4 ASUS OptiMem II: Careful routing of traces and vias, plus ground layer optimizations to preserve signal integrity for improved memory overclocking Next-gen connectivity: Intel WiFi 6, DDR4, PCIe 5.0, 2.5 Gb Ethernet, USB 3.2 Gen 2×2 Type-C , front panel USB 3.2 Gen 1 Type-C , Thunderbolt 4 header support PRIME Z690-P WIFI D4 ASUS Prime series motherboards are expertly engineered to unleash the full potential of 12th Generation Intel processors. Boasting a robust power design, comprehensive cooling solutions and intelligent tuning options, Prime Z690-P WIFI D4 provides users and PC DIY builders a range of performance tuning options via intuitive software and firmware features. FLEXIBILITY Comprehensive controls form the foundation of the ASUS Prime series. The Prime Z690 motherboard packs flexible tools to tune every aspect of your system, enabling performance tweaks to perfectly match the way you work to maximize productivity. Flexible Air- and Liquid-Cooling Controls ASUS Fan Xpert 4 software provides comprehensive control over fans and all-in-one (AiO) cooler. Whether cooling with air or water, an Auto-Tuning mode intelligently configures all parameters with a single click. There €™s also an Extreme Quiet mode that reduces all fan speeds to below the default minimum to keep your system whisper-quiet when performing light tasks. Fans and AiO cooler can also be controlled via the UEFI BIOS. Advanced Tuning for Serious Tweakers An intuitive Advanced mode offered via the UEFI lets you take complete control. A built-in search feature makes it easy to find options, and various advanced functions let you intelligently make nuanced adjustments so you can dial in performance just the way you want. Search Function Quickly and easily find the option or setting you need. ASUS User Profile Port configuration settings between different BIOS versions or share them with friends. Asus Prime Z690 P WIFI D4 PERFORMANCE Prime Z690 series is built to handle the additional cores and increased bandwidth of 12th Generation Intel processors. ASUS Z690 motherboards provide all the fundamentals to boost daily productivity, so your system will be ready for action with stable power, intuitive cooling and flexible transfer options. Power Design Stable power is essential to extract every last bit of performance out of 12th Generation Intel processors. Prime Z690-P WiFi D4 is geared to cater to the demands of these high-core-count CPUs Asus Prime Z690 P WIFI D4
0 notes
Text
Maximizing Efficiency and Connectivity: Unveiling the Benefits of WISP CRM, WISP Software, and Cloud-Hosted Hotspot Management Solutions
Introduction
In today's digitally driven world, effective customer relationship management, streamlined software solutions, and reliable Wi-Fi connectivity are paramount for businesses and institutions. Among the cutting-edge technologies that empower organizations, WISP CRM, WISP software, cloud-hosted hotspot management software, and Wi-Fi solutions tailored for universities play a pivotal role. This blog explores the myriad benefits of these innovative tools, highlighting how they enhance efficiency, optimize operations, and create seamless experiences for customers and end-users alike.
Section 1: WISP CRM
WISP CRM, short for Wireless Internet Service Provider Customer Relationship Management, is a comprehensive software solution that empowers internet service providers to manage their customer interactions and relationships seamlessly. By integrating customer data, billing, support, and marketing functionalities into a single platform, WISP CRM streamlines operations and enhances efficiency in several ways. First and foremost, WISP CRM centralizes customer information, providing a unified view of each customer's data, including service history, billing details, and support tickets. This holistic approach enables businesses to gain valuable insights into customer preferences and behavior, facilitating personalized interactions and targeted marketing campaigns.
Moreover, WISP CRM automates various manual tasks, such as generating invoices, tracking payments, and managing customer support requests. This automation not only reduces human errors but also saves valuable time and resources for the business. Furthermore, WISP CRM empowers ISPs with robust reporting and analytics capabilities. By analyzing data on customer behavior, service usage, and revenue trends, providers can make informed decisions, identify upselling opportunities, and enhance overall customer satisfaction.
Section 2: WISP Software and Wi-Fi Bandwidth Management
WISP software, specifically designed for Wireless Internet Service Providers (WISPs), offers a range of functionalities that optimize network management, including Wi-Fi bandwidth control and monitoring. One of the primary benefits of WISP software is its ability to ensure fair and efficient allocation of bandwidth resources among users. By implementing traffic shaping and bandwidth prioritization mechanisms, WISP software allows providers to optimize network performance, minimize congestion, and deliver a superior internet experience to customers.
Additionally, Wifi bandwidth software enables real-time monitoring of network performance and usage patterns, empowering providers to identify and resolve connectivity issues promptly. This proactive approach reduces downtime and enhances customer satisfaction. Furthermore, advanced WISP software often includes billing and provisioning features, automating the process of onboarding new customers, managing subscriptions, and generating invoices. These features streamline administrative tasks and reduce manual errors, enhancing operational efficiency.
Section 3: Cloud-Hosted Hotspot Management Software
Cloud-hosted hotspot management software is a powerful tool for businesses and institutions that provide Wi-Fi access to their customers or visitors. This software enables seamless management and control of Wi-Fi networks, ensuring a secure and reliable internet connection. One of the key advantages of cloud-hosted hotspot management software is its centralized administration. It allows businesses to manage multiple access points and locations from a single, user-friendly dashboard. Administrators can set up and customize Wi-Fi networks, control bandwidth allocation, and enforce security measures effortlessly.
Moreover, this software enables the creation of captive portals, where users must authenticate or agree to terms and conditions before accessing the Wi-Fi network. Captive portals offer businesses valuable opportunities for branding, data collection, and targeted marketing. Cloud-hosted hotspot management software also provides detailed analytics and reporting capabilities. Businesses can gain insights into user behavior, track network performance, and make data-driven decisions to optimize their Wi-Fi infrastructure.
Section 4: Wi-Fi Solutions for Universities
Universities and educational institutions have unique Wi-Fi requirements due to the large number of users and diverse network demands. Wi-Fi solutions tailored for universities address these challenges by providing robust connectivity, efficient network management, and seamless authentication. These solutions offer scalable Wi-Fi infrastructure capable of handling high user density and bandwidth-intensive activities such as online learning, video streaming, and research. With features like load balancing, roaming support, and quality of service (QoS) settings, Wi-Fi solutions ensure consistent and reliable connectivity across campus.
Moreover, Wi-Fi solutions for universities often incorporate hotspot management software, enabling administrators to control user access, manage bandwidth allocation, and enforce security policies. These features help maintain a secure and efficient network environment while ensuring a seamless user experience.
Conclusion
In conclusion, WISP CRM, WISP software, cloud-hosted hotspot management software, and Wi-Fi solutions tailored for universities bring numerous benefits to organizations and institutions. They streamline operations, enhance efficiency, optimize network performance, and improve customer satisfaction. By harnessing these cutting-edge technologies, businesses and educational institutions can stay ahead of the curve, delivering exceptional experiences to their customers and users. Embracing these solutions will undoubtedly pave the way for a connected and successful future.
#wisp crm#wisp software#wifi bandwidth software#cloud hosted hospot management software#wifi solutions for university#hotspot management software
0 notes
Text
What is Empowerment Technologies?
This blog, Empowerment Technologies, is an insight into what I have learned on our lessons about Empowerment Technologies: ICT for Professional Tracks, for 11th grade, under the teaching of Miss Shaira Denise Dela Cruz. The goal of this blog is to promote ICT and give you some insight into ICT

The first lesson that was discussed was, what is ICT? ICT is the abbreviation for Information and Communication Technologies. It refers to technologies that provide access to information through telecommunications such as mobile phones, wireless networks, telephones, and other communication mediums. The current state of ICT is WWW or World Wide Web.
The World Wide Web(WWW), commonly known as the Web, is an information system where documents and other web resources are identified by Uniform Resource Locators, which may be interlinked by hypertext, and are accessible over the Internet. It has three versions which are Web 1.0, Web 2.0, and Web 3.0. Web 1.0 is the first version and most web pages were static or “read-only web.”
The second and most used is Web 2.0, which allows users to interact and contribute with the page instead of just reading a page, the users are able to create a user account. Web 2.0 offers us five features: Folksonomy, Rich User Experience, Long Tail, User Participation, and software as a service.
The last is Web 3.0. Its aim is to have machines understand the user’s preference to be able to deliver web content specifically targeting the user. Web 3.0 hasn’t released yet as it still has some problems. Those problems are compatibility, security, vastness, vagueness, and logic.

Moving on to the next lesson which is all about ‘Online Saftey, security, ethics, and etiquette.’
The Internet consists of tens of thousands of interconnected networks run by service providers, individual companies, universities, and governments. It is defined as an information highway, which means anyone can access any information through the internet. That is why the internet is one of the most dangerous places, the reason why it is important how to keep yourself and your personal information safe. Some of the information that is in rick when spoiled on the internet are names of your immediate family, address, phone or home number, birthday, email address, your full name, and your previous and current school. It is important to keep this information top secret as cyber-creeps can use these to find you.
To keep yourself safe:
Be mindful of what you share online.
Do not just accept terms and conditions, read it.
Keep your passwords to yourself, and make sure your password is long, strong, and unique.
Do not talk or meet up with someone you don’t know.
Never post anything about a future vacation. This can signal some robbers about which date they can come and rob your house. It is better to post about your vacation when you got home already.
Add friends you know in real life, don’t accept someone you barely know or met.
Avoid visiting or downloading anything from an untrusted website, make sure to check the icon beside the search box. *picture* According to DigiCert Blog, “How to Know if a Website is Secure?”, Look at the URL of the website. If it begins with “https” instead of “http” it means the site is secured using an SSL certificate (the s stands for secure). SSL certificates secure all of your data as it is passed from your browser to the website’s server.
Make your home wifi private by adding a password.
Make sure to install and update antivirus software on your computer.
Do not reply or check links from suspicious emails as it can lead you to an untrusted site and can hack your laptop or social media.

To give you more information, here are some of the internet threats that we need to be aware of and try to avoid:
The Malware, stands for malicious software. It includes virus, worm, trojan, spyware, adware, and ransomware. The virus is the most common malware. It is a malicious program designed to replicate itself and transfer from one computer to another (internet, local networks, FDs, CDs,etc.). Worms is a standalone piece of malicious software that reproduces itself and spreads from computer to computer. The trojan is a malicious program that disguises as a useful program but once downloaded or installed, leaves your PC unprotected and allows hackers to get your information. Spyware is defined by Webroot Cybersecurity as "malware used for the purpose of secretly gathering data on an unsuspecting user." It is a program that runs in the background and spies your behavior as you are on your computer. Adware is malware that forces your browser to redirect to web advertisements, which often themselves seek to download further, even more, malicious software. Lastly, Ransomware, also known as scareware. This is a type of malicious software from cryptovirology that threatens to publish the victim’s data or perpetually block access to it unless a ransom is paid.
The Spam, this is any kind of unwanted, unsolicited digital communication, often an email, that gets sent out in bulk.
The Phishing, is a cybercrime in which a target/s are contacted by someone posing as a legitimate institution to lure individuals into providing sensitive data such as personally identifiable information, banking and credit card details, and passwords.

Lastly, before we move to the next lesson it is important to know ‘The Core Rules of Netiquette’ are excerpted from the book Netiquette by Virginia Shea.
First, Remember the Human.When communicating online, practice the Golden rule: Do unto others as you would have others do unto you. Remember that your written works or messages are read by real people, therefore you should ask yourself, "Would I be okay with this if someone else had written it?" before sending it.
Second, Adhere to the same standards of behavior online that you follow in real life. It is a must that your best to act within the laws and ethical manners of society whenever you inhabit "cyberspace." Standards of behavior may be different in some areas of cyberspace, but they are not lower than in real life. Be ethical. Don't believe anyone who says, "The only ethics out there are what you can get away with."
Third, Know where you are in cyberspace. What's perfectly acceptable in one area may be dreadfully rude in another. And because Netiquette is different in different places, it's important to know where you are. Thus the next corollary: Lurk before you leap.
Fourth, Respect other people’s time and bandwidth. Online communication takes time: time to read and time in which to respond. Most people today lead busy lives, just like you do, and don't have time to read or respond to frivolous emails or discussion posts. It's your responsibility to ensure that the time they spend reading your posting isn't wasted.
Fifth, Make yourself look good online. One of the best things about the virtual world is the lack of judgment associated with your physical appearance, the sound of your voice, or the clothes you wear. However, you will be judged by the quality of your writing so keep in mind the following tips: (1)Always check for spelling and grammar errors, (2) Know what you're talking about and state it clearly
Sixth, Share expert knowledge. The reason for asking questions online works is that a lot of knowledgeable people are reading the questions. And if even a few of them offer intelligent answers, the sum total of world knowledge increases. The Internet itself was founded and grew because scientists wanted to share information. Gradually, the rest of us got in on the act. So do your part. Despite the long lists of no-no's in this book, you do have something to offer. Don't be afraid to share what you know.
Seventh, Help keep flame wars under control. "Flaming" is what people do when they express a strongly held opinion without holding back any emotion.g. While "flaming" is not necessarily forbidden in virtual communication, "flame wars," when two or three people exchange angry posts between one another, must be controlled or the camaraderie of the group could be compromised. Don't feed the flames; extinguish them by guiding the discussion back to a more productive direction.
Eighth, Respect other people’s privacy. Depending on what you are reading in the virtual world, be it an online class discussion forum, Facebook page, or an email, you may be exposed to some private or personal information that needs to be handled with care. Thus, Just as you expect others to respect your privacy, so should you respect the privacy of others. Be sure to err on the side of caution when deciding to discuss or not to discuss virtual communication.
Ninth, Don’t abuse your power. Some people in cyberspace have more power than others. There are wizards in MUDs (multi-user dungeons), experts in every office, and system administrators in every system. Knowing more than others, or having more power than they do, does not give you the right to take advantage of them. For example, sysadmins should never read private emails.
Tenth, Be forgiving of other people’s mistakes. Everyone was a network newbie once. So when someone makes a mistake, whether it's a spelling error or a spelling flame, a stupid question or an unnecessarily long answer, be kind about it. If you do decide to inform someone of a mistake, point it out politely, and preferably by private email rather than in public. Give people the benefit of the doubt; assume they just don't know any better.

The last lesson that was taught to us is ‘Advanced Word Processing Skill’. This lesson focuses on the software word processor the ‘Microsoft Word.’
A Word Processor is an electronic device or computer software application that performs the task of composing, editing, formatting, and printing of documents.
Microsoft Word is a word processor developed by Microsoft and the first released on October 25, 1983. Microsoft Word has features and functions which are not mostly known by others. These are the Auto-Correct, Grammar Checker, Read Aloud, Template, Thesaurus, Mail Merge, and Text Wrap.
Advance Features of Microsoft Word are discussed. Beginning with the kinds of Materials we can have in Microsoft Word.
The first is Pictures. Generally, these are electronic or digital pictures or photographs you have saved on any local storage device. There are three file formats that pictures have which are JPEG or Joint Photographic Expert Group, this can support 16.7 million colors so that it is suitable for use when working with full-color photographic images, GIF or Graphics Interchange Format, this is used for computer-generated images that support animation, can only support up to 256 colors., lastly, PNG or Portable Network Graphics, this is similar to GIF except it has smaller file size but does not support animation, it can display up to 16 million colors and allows the control of the transparency level or opacity of images.
The second material is Clip Art. This is generally a GIF type; line art drawings or images used as a generic representation for ideas and objects that you might want to integrate into your document.
The third is Shapes. These are printable objects or materials that you can integrate in your document to enhance its appearance or to allow you to have some tools to use for composing and representing ideas or messages. The fourth is Smart Art. Generally, these are predefined sets of different shapes grouped together to form ideas that are organizational or structural in nature.
The fifth is Chart. Another type of material that you can integrate into your Word document that allows you to represent data characteristics and trends.
The sixth is Screenshot. Sometimes, creating reports or manuals for training or procedure will require the integration of a more realistic image of what you are discussing on your report or manual.
Moving on to the most focused part of the lesson which is the Mail Merge. Mail Merge is a useful tool that allows you to produce multiple letters, labels, envelopes, name tags, and more using information stored in a list, database, or spreadsheet. When these two documents are combined (merged), each document includes the individual names and addresses you need to send it to. The two components of Mail Merge are the Form Document, this contains the main body of the message we want to convey or send., and the List or Data File, This is where the individual information or data that needs to be plugged in (merged) to our form document is placed and maintained.
It was demonstrated to us, how to use and make mail merge, and here’s mine:
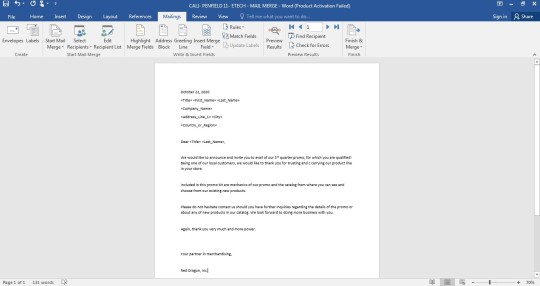

Before ending this blog, I would like to show you some of my modules for the subject Empowerment Technologies(ETech): ICT for Professional Track.
First, the open forum about the “How can you promote Netiquette?”
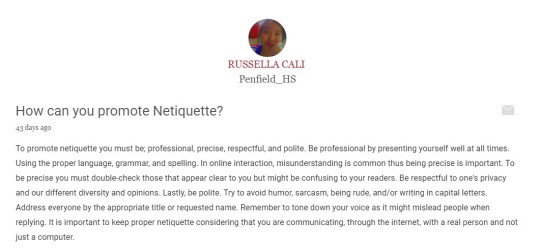
Second, an assignment about “Cyberspace: Share an experience that you have always tend to do but later did you discover that it is not a standard of ONLINE SAFETY, SECURITY, ETHICS, AND ETIQUETTE. “
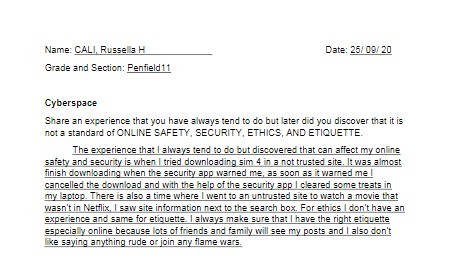
Third, another open forum about “What is the importance of Microsoft office in your education?”
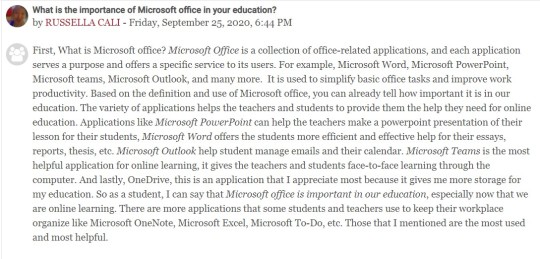
Lastly is another assignment, making an Infographic: Promoting your specific track/strand. My infographic is a promotion of my strand, STEM or Science, Technology, Engineering, and Mathematics.
Hope you learn a lot from this blog as I learn a lot from my subject teacher for Empowerment Technologies(ETech): ICT for Professional Track.
Let this day be filled with success in all the ventures you make today. Have a great day!
Photo Credits:
1
https://curatti.com/wp-content/uploads/2019/11/WWW-Image-1.jpg
2
https://go4customer.com/articleimages/1581925569Safety_Internet_Day.png
3
https://futureofsourcing.com/sites/default/files/articles/internet_attacks.jpg
4
https://i.pinimg.com/originals/fc/37/e1/fc37e162244d19115d88ab58e07ccc2b.png
5
https://cdn.guidingtech.com/imager/assets/2019/05/226896/Image-Best-Microsoft-Word-Online-Tips-and-Tricks 2_4d470f76dc99e18ad75087b1b8410ea9.png?1558678050
2 notes
·
View notes