#Windows 7 activation error
Text
The Haunting of Windows 7: "This Copy of Windows Is Not Genuine"
This Copy of Windows Is Not Genuine. Windows 7. The beloved operating system that powered our early internet stumbles, awkward teenage Facebook posts, and endless hours of Minecraft. But even seasoned veterans like Windows 7 can face their demons, and one particularly chilling specter is the dreaded “This Copy of Windows Is Not Genuine” message.
Continue reading Untitled

View On WordPress
#Microsoft support#pirated software#SLMGR -REARM#system damage#third-party tools#This Copy of Windows Is Not Genuine#windows 7#Windows 7 activation error#Windows 7 alternatives#Windows 7 genuine error#Windows 7 update#Windows Genuine Advantage Diagnostic Tool
0 notes
Text
Setting up AO3 Enhancements on a mobile browser
Hey there! Do you:
read fic primarily on your phone?
feel tired of having to punch in a lot of filter tags every time you browse for fics?
have an android device?
then I might be able to help you make fandom a cozier place! (and hopefully nip future drama in the bud, lol)
With this post, I'm gonna guide you through the process of installing the AO3 Enhancements browser extension, normally only available on desktop, on your mobile device. It works a charm, and I've been using it for months, and it's made the Undertale tag navigable again despite my utter disinterest in AU content.
Here's an archived version of the full post in case my dumbass accidentally deletes it for some reason
Let's get started!
UPDATE: For IOS users! You can download the browser app "Orion" which allows firefox extensions! No need to do this procedure, just install it and download the extension as you normally would from Firefox Add-ons
1) Download Firefox Nightly.
For those who are hearing of it for the first time, Firefox Nightly is a separate Firefox browser made specifically for developers. The name itself is due to the fact that it's patched and updated on a daily (er, nightly) basis. This makes it more prone to crashing and issues than the standard Firefox app, but I've switched over to nightly as my main browser months ago now, and if I ever encounter a problem, I just... download the latest update and I'm good to go.
What's crucial about Nightly, however, is that it gives the user access to various additional features. One of them being desktop extensions on mobile, which is what we're here for.
Here's the Google Play link.
2) Make a Firefox Account
This will be necessary to install the extension later
Once you've done that, go to the Firefox add-ons website and log into your account in the upper right (where it says "Biscia" in the screenshot below). Click on "View My Collections"
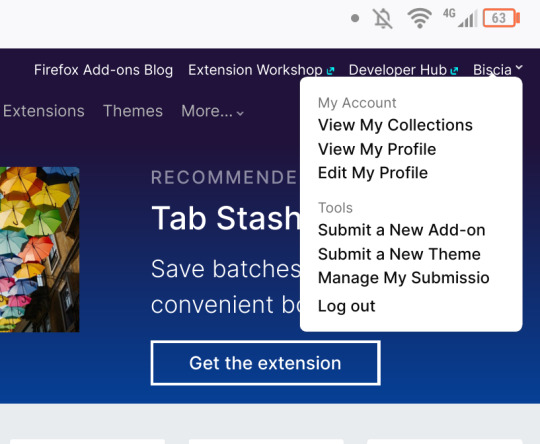
3) Making an add-on collection
Since browser extensions are technically blocked from being directly installed by the browser, Nightly offers a workaround.
Create a collection, and give it a name without spaces to avoid errors.
4) Adding the extension
Here is the link to ao3 enhancements (if it's not showing up, try reloading the page in desktop mode). Scroll down until you see the option "Add to a collection" and select the one you just created.
You can do it with any extension! Go nuts. There's lots of good stuff out there. Just remember that it's not guaranteed every one of them will work, since they aren't intended to be used on a mobile device.
5) Activating debug mode.
In your browser, tap the little sandwich menu in the bottom right, scroll down and click Settings. It should be under "Save to Collection".
Scroll down even more until you reach the "About" section, and click on "About Firefox Nightly"

Click on the firefox logo 5 times, and it should be done.
6) Activating your add-ons
Go to "View my profile" as seen in the screenshot in step 2. At the end of the link, there should be a string of numbers. Copy it.
After this, go back to the browser settings again, scroll down until you reach the add ons section and click on "custom add on collection". Paste the numbers you copied from your profile where it says "User ID", and the name of your collection EXACTLY as it appears in the link, where it says "Collection name". Mind, it's case sensitive.
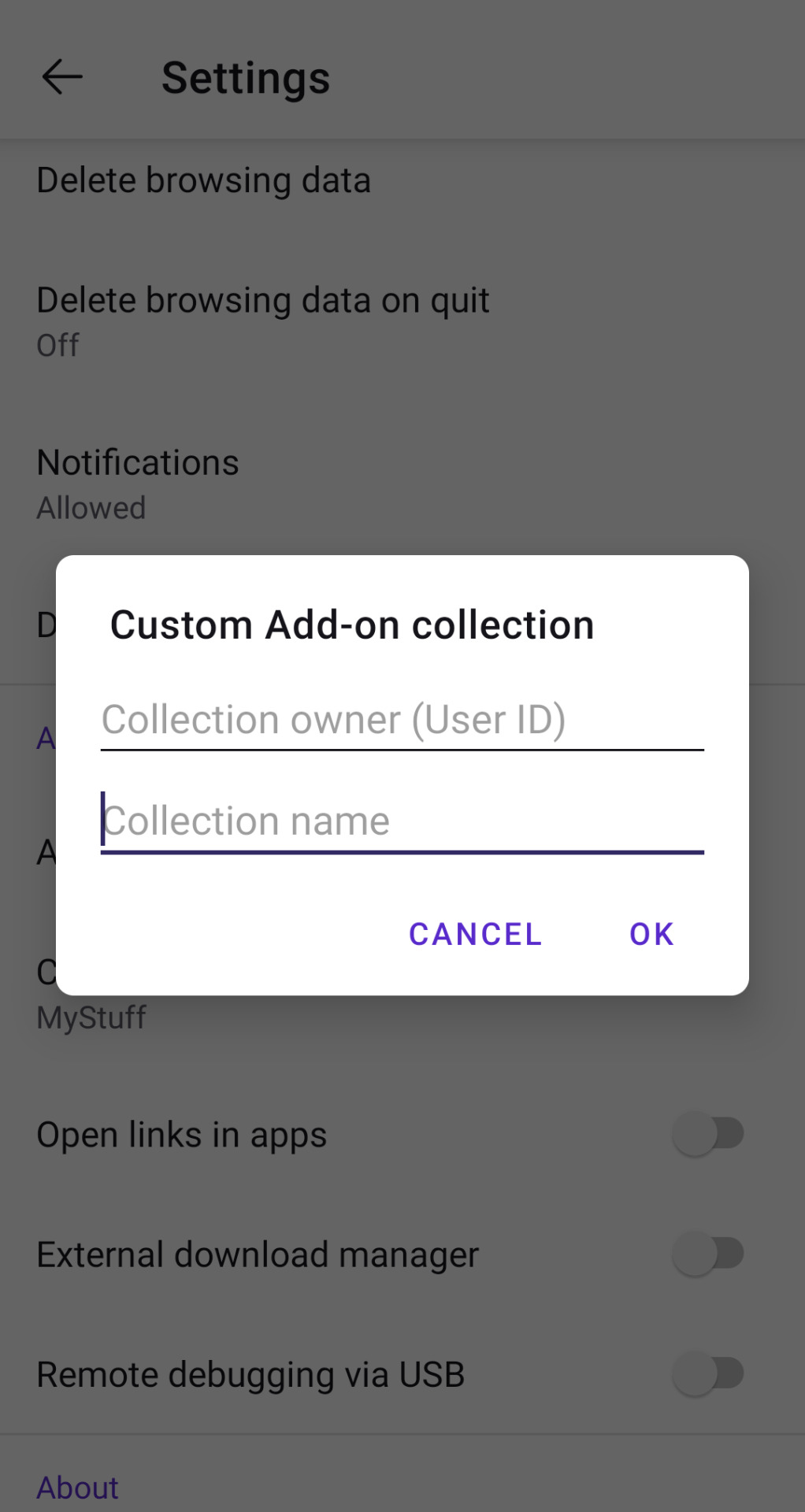
Press okay, and it should kick you out of the app. Open it again and, going in add-ons then add-ons manager, you should be able to add your extension.
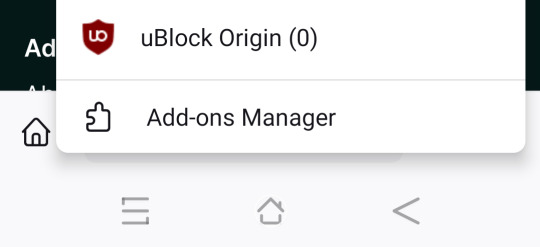
ATTENTION!! If you get the error message "failed to query add-ons" you either inputted the wrong user id or the wrong collection name
To avoid this type of issue, don't name your collection something that has spaces or punctuation in it, as it might mess with the link formatting.
7) Setting up your AO3 enhancements filters
If everything's worked out fine, you should be able to visit ao3 and see a new drop-down window.
Click on it, click on option, and it should open up a new window with all the settings available! Tweak them to your heart's content. Though mind, the background tag wrangling done by the ao3 volunteers doesn't work with this extension, so the extension is going to hide only the works tagged EXACTLY what you filtered. Character for character. This makes things a bit tricky when people aren't consistent with their tagging, but if it proves to be enough of a problem, you can just filter out the author name in full and be done with it.
You can choose to hide the fic behind a "show" button, or make it not show up at all. If you choose the latter option, and you blocked a tag that has lots of fics, it might look like certain pages of searches are almost empty, since all the fics were hidden.
And that's it! I sincerely hope this helps people avoid their triggers and other topics that make them uncomfortable. No more excuses fellas. You find a tag you haven't filtered yet? You add it to the list and move on. Easy peasy.
Hope I haven't missed anything. Let me know if you need any help!
2K notes
·
View notes
Text
marblehornets.com info masterpost
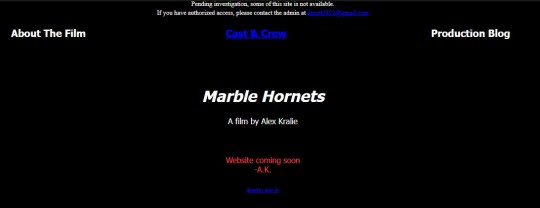
marblehornets.com was the in-universe production website for alex’s film. created for the short-lived clear lakes 44, it offered secret codes and additional info for the series.
it went down sometime ago, the url now defunct. thankfully, most of the site was archived via the wayback machine.
the purpose of this post is to compile every aspect of this site, especially it’s hidden ones, in one place. many newer fans may not be aware of the website, much less the additional secret pages and inaccessible blog posts that shed more light on alex’s character. this post will not go into detail regarding the codes or interpretations, just providing otherwise hard to find info.
if you posted about clear lakes during it’s short run or archived any of it’s pages, thank you from the bottom of my heart, because this post couldn’t have been made without you <3
main post under the cut
Main
archive of the site’s main page
the cast and crew list is accessible from there.
the email does not work.
While the site was active, the director sign-in link would open a window to input a username and passcode, which gave access to alex’s production blogs. due to the way the wayback machine archives sites, this feature was not preserved, and alex’s blogs seem inaccessible, the link leading to an error page. thankfully, I was able to find them in the form of screenshots across multiple tumblr blogs.
it should be noted that the site and some of it’s pages updated as the arg progressed. these changes can be viewed with the wayback machine.
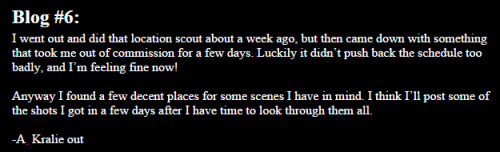
Alex’s Production Blogs


flyer shown in the link:
The text below “sides provided at audition and in advance” reads: (prior memorization not required)




the period after “A” in “A Kralie” is a link to a secret page containing a gif. the gif is titled “knockknockknock”
an audio file was found within the source code of the page. (volume warning)
the url in this blog
the url in this blog
massive thanks to the blogs linked below!!
#1 found here
#2 found here
#3 found here
#4 found here
#5 found here
#6 found here
#7 found here
#8 found here
Website Secrets
as the CL44 arg progressed, users on the thac and unfiction forums discovered secret pages containing codes on the site. these archived links are not in order of discovery.
there will be a linked thread at the end of this post that documents how these were found, along with further analysis.
marblehornets.com/werealwayswithyou
when the code is fully solved, it contains a url to this video. (flash warning)
marblehornets.com/iknowwhereyouare
marblehornets.com/welcome
marblehornets.com/donotanswer
marblehornets.com/therearefootsteps
marblehornets.com/alexarea
flash warning for this one
this “error” gif also showed up when you tried to access the cast and crew page before it was updated with their biographies.
marblehornets.com/lwtt
Extra
a video detailing CL44′s events up until august 5th 2015.
an archived THAC forums thread of the CL44 timeline up to september 11th 2015.
#if im missing anything or getting something wrong PLEASEE tell me#marblehornets.com#marble hornets#clear lakes 44#cl44#alex kralie#text#ref#over and out#edit March 2024: the website url no longer redirects to troy’s linktree and is defunct#just made a simple edit in the introduction to reflect that
467 notes
·
View notes
Text
Mods, Kisses, and Patch 4!
I posted this up on Mod Fixer's page on the Nexus...but I'll share it here as well!
Hi everybody! I'm just going to add what I did to get my mods working (and kisses!)(and Astarion kisses!)(no, Astarion's voice lines are still bugged - that's a Larian issue.). I can't say it will work for you. But it worked for me.
1 - I don't use script extender...so if you use it, sorry I can't help you.
2 - I use BG3 Mod Manager...so if you use Vortex...I'm not sure I can help you.
3 - I don't use any mods that change classes/skills or add classes/skills. I only use mods that add things like hair and faces and armor to the game.
4 - Yes, I use Basket Full of Equipment.
Ok...with that...what I did...
1 - Disable all mods. Move them to the right window in BG3MM. Leave Improved UI and ModFixer enabled on the bottom left of BG3MM. (The only way I could get my game to load at all with my mods disabled is to keep these two active).
2 - Export new version of load order from BG3MM (if you use BG3MM you should know what this means.)
3 - Load game. You will have all sorts of missing mod errors. But hopefully it will load.
4 - Save game. Exit game.
5 - Load game. No more errors because you've created a "clean" save. Your kisses should hopefully be working! If they are...YAY! Move to next step.
6 - Save game. Exit game.
7 - Start adding mods back in, moving them back to the active pane...but only add a couple at a time.
8 - Export new version of load order from BG3MM.
9 - Load game. Check to see if kisses still work.
At this point, it's basically trial and error. I was able to get all of my mods working again after creating a "clean" save and essentially starting over with mods. That includes Basket Full of Equipment! And I didn't have to unpack anything.
Like I said, I don't know if this will work for you...but it worked for me...so it's worth a shot! I have these mods enabled and it's working...
Honey's Hair Kitchen
Wyll's Demon Form
Vemperen's Other Heads
Rose Tattoo Fix
Minthara's Glittery Eyeshadow Restored
Darker Black Hair
Astarion's Earring
Purchasable Camp Clothes
Basket Full of Equipment SFW (this includes ModFixer...but I noticed I still need to have ModFixer enabled separately at the bottom...I have no idea but trial and error told me I do)
Improved UI (required)
ModFixer (required)
#bg3#bg3 modding#bg3 patch 4#astarion#astarion patch 4#baldur's gate 3 patch 4#baldur's gate 3 modding
19 notes
·
View notes
Text
The Arrangement (Part 1): The day I married someone else (a)

Books: The Royal Romance Book 3
Rating: M (Mature content and implied sexual activities)
Pairing: Liam & Jessica (MC)
The Arrangement - This is the story of how Liam Rys and Jessica Garcia enter a Cordonian arrangement. This is a 4 chapter story arc and fits into a story in between called the Promise which is in the Agent Phoenix A/U .
Detailed disclaimer
Triggers: Physical aggression
Chapter Summary: The walls close in on Liam as he is forced into marriage for the sake of his country.
A/N: This is an original chapter that I wrote to the arrangement which was first released in 2019/2020 under a previous blog name.
Song Inspiration: The Arrangement Playlist
Word Count: 2,000 *As always forgive my typo’s and grammatical errors*
Reading time: 7 minutes.

Liam woke up to the natural light of the sun shining through his windows; his eyes were red and puffy. It was hard to admit, but the Crown Prince spent his night in his room crying over her, knowing that there was no turning back. It was over.
Although his brother was his closest ally, his resentment boiled over today. He wanted to follow his heart and abdicate, giving the throne to his long-time friend Olivia Nevrakis. However, Jessica refused his offer, foolishly thinking that they could undo the wrong done to her. Had it not been for Leo’s abdication, he would at least be free to walk away from royal life and be with her. But on this day, he would need to say goodbye to the life he dreamed of, a life where the other side of the bed was warm with her beside him.
He walked into the bathroom and turned on the shower as he washed his hair; He let himself melt under the comfort of the warm water. His vulnerability came to the surface, and he found himself crying, thinking of her once more. The last time he saw her was three days ago at an adoption ceremony. She wore a light blue dress. At the Beaumont's, as she signed her name on the document that would tie her to them forever, she gave them a warm smile, something that he missed seeing and something that made his heart skip a beat each time he saw it. He tried to talk to her, but she avoided being alone with him, and she sent his calls to voicemail. The last time he made love to her was in Yu garden in Shanghai on a boat. He closed his eyes for a second to imagine that moment; for all he knew, standing in the shower, it was their last time. He could smell her scent of vanilla and lavender perfume. He could envision the way her red lace dress clung to the curves of her body in the most exquisite way and, when nothing else was on her body, the way the pearl bracelet glimmered in the moonlight. He sighed deeply and could feel her body on top of his as it expertly moved against his own. Each moment of intimacy was a gift of themselves to each other, and each time they fell deeper in love. He was losing that gift today.
To be with her now would put her in a category she didn’t belong. Liam hated the word ‘mistress’ because she would never be that to him. She would forever be the woman he loved. She wouldn’t be Jessica Rys or the other woman in the shadows. He told her Madeleine was his wife on paper, but emotionally, his heart was hers. His body was hers, and as he promised her, they were two bodies that shared the same heart and soul. A Cordonian arrangement was all they had. If she agreed, it would be the only way to be together. They tried to be friends during the engagement tour but couldn’t. They just couldn’t stay away from each other. With each wall she built up, Liam managed to break through. She struggled with it the entire engagement tour. Every time she saw him and his fiancée together, the dances that should have been theirs, the kisses and hand-holding, the moments of tenderness which were staged, but nonetheless, she knew that if it were her, it would be genuine. She never gave him an answer to what she wanted to do. After that, she decided to stay in New York, but something pulled her back to the court. It was her responsibility to the Beaumont's, but Liam hoped part of it was him in his heart.
After he showered, he walked to his closet and looked at his custom-made wedding regalia tailored for him. When he still believed there was a possibility of being together, on the inside of the jacket where his heart would rest, the monogram L&J. No one would notice it. Still, it was an essential detail to him that when they were alone, and he took off his jacket, he would show her that his heart was hers and he promised it before God and his people.
He traced the letter J and said, “Jessica” in barely a whisper. He hated that today it was designed for his wedding to her and would now be used in a ceremony where he would be promised to another.
He sat on his bed, took a deep breath, and looked at the clock. Any minute now, preparations for the wedding would begin. The bell in Cordonia square would toll, the people would line the streets waving Cordonian flags, and they would throw flowers and the official wedding coin with his image and that of the new Queen to be on the streets; a Cordonian tradition of good fortune. He didn’t want any of it. He wanted a swift ceremony and an even swiffer divorce. He hoped that nothing that was happening today would taint what he wanted Jessica to have if he could free himself. The laws made it clear it wasn’t a question if he could divorce, but it would be a question of grounds and how long he would need to wait as the Royal Council would need to approve of the dissolution of his coerced marriage. He combed his hands through his hair as he heard the dreaded sound. The sound that would set the day’s events into motion was the galloping of horses from their carriage. A messenger was sent to collect his signature and bring the instrument of intent to marry and ascend the throne to the Archbishop.
The door flung open with no warning. Constantine entered and said, “My boy, it is a joyous day. You will take over my throne.” He was followed by staff, who drew his curtains.
Liam looked at the floor as he responded. “There is nothing joyful about this day,” Liam said in a whisper. His throat was hoarse with grief and the strain of sobbing all night. His eyes were downcast, refusing to look at the man that ruined his life.
“It is time to do what you must and sign the instrument that promises Countess Madeleine lands and other rights owed to her as your wife.”
Liam scowled, “I refused to call her my wife.”
Constantine tsked, “No matter what, you call her in private. By law, she is your wife from this day forward. You will come around, son.”
The messenger was escorted to the room by the Royal Guard, holding a wooden box. “Your Majesty and, “Your Royal Highness,” the man said, bowing, “The Duchess of Krona and The Duke of Karlington have sent over the signed instrument. I am here to collect your signature so upon marriage, the Archbishop may place his seal.”
Liam looked at the document and took his pen, and with his left hand, he signed away his life for his people. Something that he was born to do in an arranged marriage his whole life but something that changed for him since meeting Jessica. He knew love, her love, and his heart wanted that more than anything. Marrying her would mean a marriage filled with love and tenderness.
The messenger said, “Your Royal Highness, is there anything you want to send the future Queen?”
Liam looked at him, puzzled, and said, “Excuse me, I am uncertain of what you mean?”
The man answered, “A gift.”
Liam looked at him and said, “Should she ask to tell her that she is allowed to live here although she is unwanted and she is allowed to be addressed as Queen. Although, she is undeserving of the title. Remind her that it will all be short-lived, and she is just a guest.”
Constantine sucked his teeth and said, “Please direct the messenger to Queen Regina’s quarters; she will provide you with a gift for the Bride, her niece, from her personal jewelry collection. Surely the Bride will be moved by such a gift from a Queen to a future Queen.”
Liam retorted and said, “Very well. I can’t stop you from giving her something. But I have given the messenger a directive, and he is to deliver that message. Should he ease up on the language, fine, but the message, whether in English, French, Italian, or whatever language the Countess knows, is the same at the core I despise her.” He turned to the messenger and said, “You are excused.”
With that, the messenger exited Liam’s quarters and was directed to Regina’s room to collect a hastily given bridal gift.
Liam allowed the royal servants to do whatever they wanted. Brush his hair, help him dress, put on Cologne. It all felt like he was no more than a rag doll being tossed around and dolled up while he just stared off into nothing.
Constantine watched the entire time, not caring about frivolous things such as privacy or respect for his youngest son.
“You look distasteful and weak with those red eyes. This will be broadcasted for the entire Nation to see. Something must be done to cover it.”
Liam snapped out of his trance, “Weak?” He huffed with a humorless chuckle. “It’s a strength and honor to my country to marry a woman who I can’t tolerate more than what social decorum dictates.”
Soon after came Regina and Leo after Liam was dressed. Leo smiled sadly at his younger brother.
“You look handsome as ever, Liam. I’m so proud of you.” Regina smiled softly.
Constantine said, “Proud? The boy looks like a sobbing child on a day when our reputation is on the line. The least he could do is be a man and handle his duty with pride.”
Liam snapped his head in his Father’s direction. All composure went out the window at the statement.
Leo closed his eyes and mumbled under his breath. “You couldn’t have stayed silent, could you?”
“A child, Father? You think I should be more stoic or manly on this day?” Liam released a bitter chuckle before kicking over a table.
“I apologize, Father! So sorry that my life has been ruined and my heart is being ripped into a million pieces, but I can’t act like I’m thrilled!! How dishonorable of me!”
Constantine huffed, “Well, you should know I sent Lady Jessica a letter by footman today about the doctrine Sex primis noctibus. I felt it necessary to remind her of her place should she become the other half of the Cordonian Arrangement.”
Liam glared at his Father and said, “You did what?!”
“You heard me. I reminded her of where you would be the first six nights of your marriage, unable to communicate with the outside world and bedding the Queen as tradition dictates.”
“I did not invoke that Cordonian clause! It is my right to invoke it, and I will not be trapped in this palace with Madeleine in close quarters to produce an heir!”
“That’s true, you didn’t invoke it, but I, as the King, have. It’s an order, so I’m sure she is devastated. Liam, do not forget the order of things. You convinced her to come here. Now she must deal with her new found status.”
Filled with anger at what his Father had done to further torment Jessica, he picked up a chair and threw it across the room.
Regina gasped, and Leo simply watched as Liam marched towards his Father, now towering over the older man.
Constantine glared, “What are you going to do, Liam, assault me? You had to taint today by stubbornly always keeping that woman in your thoughts.”
Liam yelled in his face. “Of course I fucking do! Because that woman is the only woman for me! Today was supposed to be her day, and you took that away from us both!!”
“I took nothing away.”
I’m being forced into a marriage of hate and lies, and you don’t even care!” Liam’s nostrils flared as he yelled, “You betrayed me, Father. You used me! You don’t give a damn about anyone but yourself!”
“Boy, calm yourself.”
Liam saw red at the order and, without thinking, shoved Constantine against a nearby wall. Regina clutched her mouth, and Leo calmly walked over as Liam screamed in his Father’s face. “I will not!! When do I get a say-so? When do I get to choose? I’ve been ripped back and forth, advised, and taken care of all my life. I am a grown man and can’t choose who I marry!”
Liam was inches from his Father’s face, hands on his collar as Constantine glared and dug his fingers into his son’s wrist.
“Come on, Li. The old man isn’t worth it.” Leo mumbled low while glaring at Constantine and forcibly dragged Liam off of him.
Constantine was red-faced as he got back up into Liam’s space as Leo held him back. “You ungrateful foul-mouthed BRAT! You’re being given a crown, all the power you could ask for, and reputation, and all you care about is not marrying some ordinary woman. I should have-”
Constantine stopped mid-sentence, coughing violently and hunching over. Regina rushed to him, placing a hand on his back.
“Liam, please! Can’t you see that your Father is ill?”
Liam relinquished himself of Leo’s grasp and threw a nearby vase at the wall. “OUT!! I want everyone out but my brother!”

My list is spilt between two blogs so if you if you would like to stay on the list please let me know and if you would like off the list please DM privately thank you for being on this writing journey with me. -J
#play choices#choices trr#choices fanfiction#Liam x Jessica#king liam#liam x mc#choices#the royal romance#mc x liam#choices app#Liam Rys#agent phoenix
55 notes
·
View notes
Text
Secret Crush on You Ep 9
-Was Toh seriously trying to practice sex noises? I think I blacked out for a second.
-Idk what's happening the jumbo condom box and the animal audios....wtf
- Toh very disappointed that by workout Nuea didn't mean workout 😏.
-Nuea, my guy, it's gonna be real hard (pun intended) for Toh to workout with you if you keep getting him worked up.
-Pouty Nuea...precious.

-Aww, surprise kiss picture. I love that shit. (I was raised on rom-coms, I'm very easy to please.)
-I can't believe he kissed the car window...that can't be sanitary.
-Poor Jao...he did not get the sex joke.
-But he did get a gallon Ziploc bag full of condoms... wtf Toh. But also, props for promoting safe sex.
-Sweet baby Jao has no idea how appealing he is.
-Sir Touch has returned....and gif spoilers tell me that Sir Daisy is gonna get some flirtation. ☺️☺️☺️
-Fucking Prao again 🙄
-Like...shoot your shot ladies (used ironically) but you all know these dudes are actively lusting after other people, so maybe stop being little bitches and find someone interested.
-We're gonna get drunk Toh again....aren't we....
-He just touched another man at the urinals...I don't have a penis but I know that's a faux pas.
-Jealous Nuea again. 😁😁
- Som is very vicious...I adore her.
-Aww... Daisy get your man.
-Sky...whatcha doin????😳😳😳

-Jao you goose, Sky considers you to be a friend too.
-Toh...got very aggressive with Sky...it's a little rude since anyone could see how Sky feels, but I love a protective friend.
-Fon and Kwan are like 'Bye Bitches' 😂😂😂
-I like Sky's fun printed shirt, this one is like a jazz band....very fun
- Sky's so cute. Awww ...the hug... so cute. Jao he really likes you babes. You gotta realize that.
-Drive Safe = I love you...we all know that.
-I do love drunk Toh I think. He's very bold and that's good sometimes.

-Yes Touch, be the gentleman for 'Daisy in Distress'.
-Props to Som for being the opposite of a cockblock...a cock enabler???
-Daisy's so fuckin cute...and Touch totally tricked him into a date. Good job babes.
-I have no idea what just happened with the noodle seller...that was wild. But I support their peaceful protest of whatever they're protesting.

-Daisy.exe error 😂😂😂

-I do need a behind the scenes for how those berets stay on...is it just hair pins???
-Toh's like

-Toh is going hard on Nuea's chest 😂😂😂 horny babe.
-Ooh another Phys Ed session for Toh, lucky bastard.
Honestly, this ep might be a 10/10. Lots of sweet corniness (and horniness) which I love.
7/10 for embarrassment, but we're definitely gonna have a moment the next time Nuea gets into Toh's apartment....I'm worried about it.
4 notes
·
View notes
Photo

How to fix We’re Having Trouble Activating Office 365 Error in Windows 7 👉 Read the article: https://bonguides.com/how-to-fix-were-having-trouble-activating-office-365-error-in-windows-7/?feed_id=555&_unique_id=667155f97f265
0 notes
Text
8 Common Kitchen Renovation Mistakes That Make Interior Designers Cringe
Embarking on a kitchen renovation can be thrilling, but the excitement often leads to hasty decisions and overlooked details. Kitchen interior designers in Bangalore frequently encounter mistakes that could have been easily avoided with a bit of foresight and professional guidance. Here are eight common errors that make interior designers cringe—and how to avoid them.
1. Neglecting the Work Triangle
The kitchen work triangle—the relationship between the stove, refrigerator, and sink—is crucial for a functional kitchen design. Ignoring this principle can result in an inefficient kitchen that's difficult to use.
Solution: Ensure your kitchen layout allows for easy movement between the stove, sink, and refrigerator. The ideal work triangle has each leg between 4 to 9 feet. Use design software or consult a professional to visualize the layout before making final decisions.
2. Insufficient Lighting
Lighting is often an afterthought, but it plays a crucial role in both functionality and ambiance. Poor lighting can make cooking tasks difficult and create an uninviting atmosphere.
Solution: Incorporate a mix of task, ambient, and accent lighting. Use under-cabinet lights for countertops, pendant lights over islands, and recessed ceiling lights for even illumination. Dimmer switches can also help adjust the lighting for different times of day and activities.
3. Overlooking Storage Needs
A lack of adequate storage can turn a beautiful kitchen into a cluttered mess. Not planning for enough storage leads to frustration and detracts from both functionality and aesthetics.
Solution: Consider various storage solutions, including cabinets, drawers, and pantry spaces. Use vertical space with tall cabinets and incorporate pull-out shelves, lazy Susans, and organizers. Custom cabinetry can also be designed to fit specific storage needs for appliances, spices, or cookware.
4. Choosing Style Over Function
Prioritizing aesthetics over practicality can lead to a kitchen that's difficult to work in. High-maintenance materials may result in more time spent cleaning than cooking.
Solution: Balance style with function by choosing durable, easy-to-clean materials. Opt for quartz countertops instead of marble for a low-maintenance yet stylish option. Professional designers can help you find beautiful yet functional choices that suit your lifestyle.
5. Skimping on Quality
Cutting corners to save money often backfires. Low-quality materials and appliances may need to be replaced sooner, leading to higher long-term costs.
Solution: Invest in high-quality materials and appliances, especially for items that see the most use like countertops, cabinets, and cooking appliances. Look for reputable brands and materials known for durability, and consult professionals to choose products offering the best value.
6. Ignoring Ventilation
Good ventilation is crucial to remove cooking odors, smoke, and excess moisture. Poor ventilation can lead to an uncomfortable and potentially unhealthy environment, contributing to mold growth and surface damage.
Solution: Install a quality range hood that vents to the outside, ensuring it’s powerful enough for your kitchen size and cooking habits. Consider strategic window placement to promote natural ventilation.
7. Poor Planning for Electrical Outlets
Not having enough electrical outlets or placing them in inconvenient locations can be a significant annoyance. Modern kitchens require more outlets for various gadgets and appliances.
Solution: Plan your kitchen layout to include ample electrical outlets. Consider appliance placement, charging stations, and other electrical needs. Install outlets along the backsplash, on island sides, and inside cabinets to keep cords out of sight but accessible. Consulting an electrician during planning helps meet all electrical needs.
8. Forgetting About Garbage Disposal
Not planning for waste disposal disrupts the kitchen’s flow and functionality. Poorly placed trash bins or lack of recycling space leads to clutter and inconvenience.
Solution: Incorporate built-in trash and recycling bins into your cabinet design, positioning them near the sink and prep areas for easy access. Use pull-out drawers or dedicated cabinets for waste and recycling, keeping these items hidden yet accessible. Consider composting solutions for an environmentally conscious approach.
Renovating your kitchen is an exciting endeavor, but avoiding these common mistakes is crucial for a successful outcome. Consulting with experienced kitchen interior designers in Bangalore provides the guidance and expertise needed to create a beautiful, functional, and efficient kitchen space. By paying attention to these details, you can transform your kitchen into the heart of your home without the pitfalls that make designers cringe.
0 notes
Text
Gamma Crusis: Prelude
The saintly star fell upon the cluster of orbitals. The looming sun of the red giant Gamma Crusis. Imposing its light on the minuscule speck where over a billion beings have chosen to reside in the face of that vast, dying star. It was a typical time cycle for the local inhabitant known as Noa, who levitated towards the panels monitoring the current flare activity. “No disturbances detected” it read. A typical cycle indeed.
Noa continued to advance in their activities, the tight and highly vertical corridors of the monitoring array built with the eventual construction of a solar mirror in mind. The project has had considerable delays due to infighting with the local asteroid harvesting communes who have Continued questions about the mirror and its intention. Much of which is due to the faction of harvesters who believe solar lifting tech is just around the corner and questioning the usefulness of a massive telescope situated at Gamma Crusis of all stars.
The shaft had finally been navigated to the proper location which Noa had sought as the final location of interest. A view at the mirror itself in construction. Noa peered out of the window, out there all one sees is a vast plain of glass with the pitch black sky only punctured by the lights of ships working on the mirror. It is a very serene sight on the whole, the gaze of Gamma Crusis is not present due to it being the “night” side of the mirror.
It was at that point Noa had been contacted by a local integrity monitor. Noa’s relief was near instantaneously punctured by one simple line-
“Noa. We have a complication.”
The frustration grew as the nature of the complication was further expressed in the form of a drone malfunction. A minor error from the stack of protocols followed by the construction drone led to it crashing into one of the support beams.
“I’ll take care of it directly.” Noa replied, knowing the task that now will absorb the whole cycle. Sending another drone is simply too ill advised. A generalized agent like themself exists to handle the convoluted tedium after all. Noa set out immediately, pulling themselves towards the airlock and donning the technician’s apparatus.
In the void, the scale of the mirror became ever clearer. The horizon was a glass horizon. The support structure the drone hit was over 7 kilometers from their location. Which was not a terribly long distance to travel using the apparatus. The journey was only half an hour.
After drifting for that half hour on the matched velocity Noa didn’t even need their sensors to see the impact. It was worse than merely a support structure beam getting mangled. The drone smashed into the damn mirror. Noa set to work immediately trying to salvage the situation.
The drone could not be salvaged.
The mirror for the whole sector was cracked, the chips and pieces kept Noa on edge as they were sharp enough to even puncture the apparatus should they be careless. Noa dodged around the large shards, never changing velocity too much and making touch down even as a sharp jagged tooth of a glass piece floated above them.
Noa got to work on the support beam itself, mending it with the graphene strand gel in short order and enameling it further with an adhesive. It was not optimal, but the alternative of disassembling hundreds of meters of mirror was simply not viable. Noa just wanted out of here. The glass shards drifting above making it clear the incident was going to need more than one mechanic with adhesives and gels. Using gels on the glass would further complicate their trajectories and be too much a liability. Noa only wanted to get back to the vertical corridors of the center monitoring tower and call in the heavy duty assistance.
But first, Noah had to take the broken beyond repair drone with them. Dislodging it was simple and the lack of gravity made it less difficult to carry in tow with the cables then it could have been.
Ascending the broken glass was all they had to do now.
The drift of the glass and timing it, navigated away from a large piece of glass that appeared to be headed towards them. The drift was anxiety inducing all the same as it glanced ever so close, this sharp broken crystal which was meant to power civilizations. Now a hazard for their own survival. Noa felt the smaller bits of glass regardless, tearing a bit on the suit. Mercifully, they managed to get out of the worst of it… the plains of solar panel blending into an indistinct bluish hue as they drift ever further upwards with the drone. The light of the recover craft illuminating behind them.
“Finally here?” Noa asked it, “I have the drone.”
Noa’s apparatus linked with the vehicle, the drone clutched in their hands. Noa would watch as they were rapidly flown back to the main control center, the simmering glimmer of the panels ever so distant now. The heat of the thrusters could be felt, but Noa didn’t hear them beyond the loose hum and vibration of the craft they are latched upon. It was strangely serene, as they watched the central tower of the power station come into view, a tower amid the ocean of solar panel below.
They finally got back to the station, drone in tow.
“Any new information?” Noa inquired.
“Nothing outside the repair crew being officially dispatched. Pending drone analysis.” the monitor replied.
The whole situation reeked of an absence. The repairs according the look up system were estimated to take 77 hours. Yet that estimate seemed painfully optimistic. The damage witnessed, the large shards floating over the sea of solar panels and the dust itself all pointed to an operation far more intensive than a mere glue operation.
Something simply didn’t make any sense.
Noa took the drone to the mechanical bay and got to work analyzing it. The drone was dead, as expected, but other strange anomalies were present. The navigation system seemed off-kilter. Which shouldn’t be possible, as these were drones specifically designed to keep the radiating heat of Gamma Crusis and its solar winds from perturbing the navigation system. Even the primitive probes the first space faring humans constructed didn’t run into that problem. Something else is tampering with it.
But what?
“The harvesters wouldn’t dare.” Noa stated out loud.
0 notes
Text
Python for Automation Testing

Python for Automation Testing
Introduction
Have you ever wondered how tech companies ensure their software works flawlessly across various platforms and devices? The answer lies in Software testing . And guess what? Python is one of the best languages to get the job done. Whether you're a newbie in the world of programming or a seasoned developer, Python for automation testing can make your life a whole lot easier. Let's dive into the fascinating world of automation testing with Python. Explore the power of Automation Testing with Python . Learn about tools, techniques, and best practices for effective automation testing with Python.
Table of Contents
Sr#
Headings
1
Introduction to Automation Testing
2
Why Choose Python for Automation Testing?
3
Setting Up Your Environment
4
Basic Python Concepts for Automation
5
Popular Python Libraries for Automation Testing
6
Writing Your First Test Script
7
Advanced Testing Techniques
8
Integrating with CI/CD Pipelines
9
Handling Test Reports and Logs
10
Best Practices in Automation Testing
11
Common Challenges and Solutions
12
Future of Automation Testing with Python
13
Case Studies
14
Conclusion
15
FAQs
Introduction to Automation Testing
python for automation testing is like having a tireless assistant who meticulously checks your software for errors, ensuring it functions perfectly every time. Instead of manually executing test cases, automation testing uses scripts to run tests, saving time and reducing human error.
Why Choose Python for Automation Testing?
So, why Python? Imagine trying to read a technical manual written in ancient hieroglyphs. Frustrating, right? Python, however, is like reading your favorite novel—easy, enjoyable, and intuitive. Its simplicity and readability make it an ideal choice for automation testing. Plus, Python boasts a rich ecosystem of libraries and frameworks that cater specifically to testing needs.
Simplicity and Readability
Python's syntax is clean and straightforward, which means you spend less time figuring out the language and more time writing tests.
Extensive Libraries
From Selenium for web applications to PyTest for simple yet powerful testing frameworks, Python has it all.
Community Support
Python has a massive community. If you ever get stuck, chances are someone else has faced the same issue and found a solution.
Setting Up Your Environment
Before diving into writing tests, you need to set up your environment. Here’s how:
Installing Python
First, download and install Python from the official website. Ensure you add Python to your system’s PATH.
Setting Up a Virtual Environment
A virtual environment keeps your project’s dependencies isolated. Use the following commands:
bash
Copy code
pip install virtualenv virtualenv myenv source myenv/bin/activate # On Windows use `myenv\Scripts\activate`
Installing Required Libraries
Next, install the libraries you need. For example, to install Selenium:
bash
Copy code
pip install selenium
Basic Python Concepts for Automation
Before you start writing tests, you need to understand some basic Python concepts.
Variables and Data Types
Variables store data, and Python supports various data types such as integers, strings, and lists.
Functions
Functions help you organize your code into reusable blocks. Here’s a simple function:
python
Copy code
def greet(name): return f"Hello, {name}!"
Loops and Conditionals
Loops and conditionals control the flow of your program. For example:
python
Copy code
for i in range(5): if i % 2 == 0: print(f"{i} is even") else: print(f"{i} is odd")
Popular Python Libraries for Automation Testing
automation testing in python offers numerous libraries tailored for different testing needs.
Selenium
selenium webdriver python is the go-to library for web application testing. It allows you to interact with web elements just like a real user would.
PyTest
PyTest is a versatile testing framework. It’s simple for beginners yet powerful enough for advanced users.
Unittest
Unittest is Python’s built-in testing framework. It’s similar to JUnit in Java and is great for structured test cases.
Requests
For API testing, the Requests library is invaluable. It simplifies sending HTTP requests and handling responses.
Writing Your First Test Script
Now, let’s write a simple test script using Selenium and PyTest.
Creating a Test Case
Here’s a basic test case that checks if Google’s homepage loads correctly:
python
Copy code
from selenium import webdriver def test_google_homepage(): driver = webdriver.Chrome() driver.get("https://www.google.com") assert "Google" in driver.title driver.quit()
Running the Test
Save your test script and run it using PyTest:
bash
Copy code
pytest test_google_homepage.py
Advanced Testing Techniques
Once you're comfortable with basic test scripts, it's time to explore advanced techniques.
Data-Driven Testing
Data-driven testing involves running the same test with different inputs. PyTest makes this easy with parameterization.
Parallel Testing
To speed up your test suite, you can run tests in parallel using tools like pytest-xdist.
Mocking
Mocking allows you to simulate parts of your system that are not under test, making your tests faster and more reliable.
Integrating with CI/CD Pipelines
Continuous Integration and Continuous Deployment (CI/CD) ensure your software is always in a releasable state.
Setting Up Jenkins
Jenkins is a popular CI/CD tool. You can configure it to run your test suite every time there’s a code change.
Using GitHub Actions
GitHub Actions is a powerful automation tool that integrates seamlessly with GitHub repositories. You can set up workflows to run tests automatically.
Handling Test Reports and Logs
Test reports and logs help you understand what went wrong when a test fails.
Generating Reports with Allure
Allure is a flexible reporting tool that integrates with PyTest, providing detailed and visually appealing reports.
Logging with Python’s Logging Module
Logging is crucial for debugging. Python’s logging module allows you to capture detailed logs during test execution.
Best Practices in Automation Testing
To get the most out of your automation efforts, follow these best practices.
Maintainability
Keep your test scripts clean and well-organized. Use functions and classes to avoid code duplication.
Readability
Write your tests as if they were documentation. Use meaningful names for your test cases and include comments where necessary.
Scalability
Ensure your test suite can scale with your application. Regularly review and refactor your tests to accommodate new features and changes.
Common Challenges and Solutions
Automation testing comes with its own set of challenges. Here’s how to tackle some common issues.
Flaky Tests
Flaky tests are tests that sometimes pass and sometimes fail. To avoid them, ensure your tests are independent and use waits appropriately.
Environment Issues
Different environments can cause tests to fail. Use Docker to create consistent environments for your tests.
Handling Dynamic Elements
Web applications often have dynamic elements that can be tricky to test. Use strategies like waiting for elements to be present and using unique identifiers.
Future of Automation Testing with Python
The future of automation testing is exciting, with advancements in AI and machine learning leading the way.
AI-Driven Testing
AI can help in creating smarter tests that adapt to changes in the application.
Self-Healing Tests
Self-healing tests automatically adjust to minor changes in the application, reducing the need for manual intervention.
Case Studies
Let’s look at some real-world examples of companies that successfully implemented Python for automation testing.
Example 1: A Leading E-commerce Platform
An e-commerce giant used Python and Selenium to automate their extensive suite of regression tests, significantly reducing their release cycle.
Example 2: A Financial Services Company
A financial services firm leveraged PyTest and Requests to automate API testing, ensuring their services were reliable and performant.
Conclusion
python in automation testing is a powerful combination that can streamline your testing efforts and improve software quality. With its simplicity, extensive libraries, and robust community support, Python makes automation testing accessible and efficient.
FAQs
1. What is automation testing with Python?
Automation with Python involves using Python scripts to automate the execution of test cases, saving time and reducing human error.
2. Which Python libraries are best for automation testing?
Popular libraries include Selenium for web testing, PyTest for general testing, Unittest for structured test cases, and Requests for API testing.
3. How do I start automation testing with Python?
Start by setting up your environment, installing necessary libraries, and writing simple test scripts. Gradually move to advanced techniques as you gain confidence.
4. What are the benefits of using Python for automation testing?
Python is easy to learn, has a vast array of libraries, and a strong community. It’s perfect for writing readable and maintainable test scripts.
5. Can I integrate Python test scripts with CI/CD pipelines?
Yes, you can integrate Python test scripts with CI/CD tools like Jenkins and GitHub Actions to automate test execution and ensure continuous delivery.
0 notes
Text
The importance of managed hosting security for your clients’ web security needs
Cyberattacks, data breaches, and other criminal activities are a constant concern in today's digital environment. One of your main duties as a best web hosting provider is to ensure that others' websites are always safe from these security concerns and attacks.
Regretfully, there are instances when it's simpler to say than achieve. It can be difficult to constantly maintain the best web hosting security, especially if you're a small web hosting provider managing several clients and websites. Furthermore, unless you work in online security, you may not be aware of the precise features or tools that your clients want for the highest level of safety.

Presenting best managed hosting, a special service that strengthens your clients' websites with a complete, multi-layered security plan in addition to providing them with a web address.
Benefits of managed hosting security-
By relying on a managed web hosting provider for the technical and security needs of your clients' websites, you leverage specialized expertise and advanced tools aimed at defending against the latest cyber threats. Here are some features and benefits you can anticipate with best managed hosting security:
Attentive observation
Threats can arise at any time and without notice in an online environment.
Providers of managed hosting services are aware of this and are constantly alert. They monitor websites and servers for any odd or suspicious activities.
For instance, you will profit from having a fully staffed team and level 3 technicians at data centres monitoring your clients' servers and networks around the clock when you are a web hosting provider. This ensures that possible security risks are found early on and eliminated before they become more significant and cause harm.
This kind of attention to detail is usually absent from unmanaged hosting situations. Numerous risks may remain hidden until it's too late if proactive monitoring isn't done.
Security measures designed for a platform
The best web hosting provider adjusts security procedures and defences—like intrusion detection systems, firewalls, and DDoS protection—to the particular needs and weaknesses of any platform or website.
For instance, specific security settings that address known vulnerabilities in this content management system (CMS) will be applied to WordPress hosting websites.
Thus, you have a customized cybersecurity solution that is suited for your particular platform as opposed to a one-size-fits-all strategy that may leave security gaps.
Backups done automatically
A business owner never wants to have to start again after losing data, whether from a technical malfunction, user error, or hacker assault.
However, because most managed hosting security services include automated daily and on-demand backups, the risks of data loss are significantly reduced. These two functions serve as backups to guarantee that no important files, data, or projects belonging to you or your clients are ever lost.
Dedicated expert support
Dedicated professional support is just another exceptional advantage of managed hosting. The majority of service providers provide 24/7 customer support via a variety of channels, including live chat, email, and phone. To put it briefly, assistance is always just a button push away.
Additionally, the majority of managed web servers have support staff with training and experience in a variety of technical fields, such as operating systems like Windows and Linux and other content management systems like WordPress and Joomla.
Therefore, a skilled expert who is familiar with your particular ecosystem is prepared and glad to help, regardless of the platform or system powering your clients' websites.
Monitoring compliance
If your clients work in an industry or territory where compliance with privacy and security regulations is mandatory, you must ensure that your hosting environment complies with these rules. Managed hosting companies may assist in ensuring that your websites are compliant, as they typically have expertise in implementing these standards.
Cost Savings
The financial consequences of cyberattacks are extremely severe. For instance, IBM reports that the average cost of a data breach worldwide in 2023 was an astounding $4.45 million. In addition to immediate monetary losses, collateral damages may also occur, including damaged reputations, lost business, and even legal action.
By making an investment in managed hosting security, you and your clients are protected from a wide range of unanticipated costs, such as legal fees, post-breach clean-ups, and revenue losses due to downtime.
Furthermore, you won't need to engage a sizable in-house staff or contract out the work to a third party when your clients' security is being monitored and maintained by a specialized security team from the managed hosting provider. The money you save might be applied to other aspects of your company.
Peace of mind
You may lose focus on important business matters if you are preoccupied with concerns about your clients' websites' security all the time. You can relax knowing that your client's websites are in skilled and safe hands with managed to host security. You can refocus your energies on other crucial issues and redirect your energy with this peace of mind.
Threats against which managed hosting security works effectively-
Websites owned by your clients can be shielded from a variety of risks by using managed hosting security. Among them are:
Phishing attacks: Phishing is the practice of tricking targets into disclosing critical personal data, such as by building fake websites that mimic real ones. Although managed hosting cannot stop fraudsters or scammers from trying to deceive customers, it can provide SSL certificates, which enable users to verify a website's authenticity.
Brute force attacks: In these, attackers try different passwords, credentials, or other authentication details until they figure out the correct combination.
Distributed Denial of Service (DDoS) attacks: In a DDoS attack, a web server is overloaded with traffic, preventing authorized users from accessing it.
Malware attacks: Malicious software intended to breach, harm, or take over a network or website is known as malware. Outdated CMS and programs with documented security flaws that have been patched but not updated are common attack vectors. Ransomware, worms, trojans, malware, and viruses are a few examples. Managed hosting companies conduct routine malware scans to guarantee the early identification and elimination of these applications.
SQL injection: In this kind of attack, malicious SQL code is inserted into the input fields of the online application. The attacker might then be able to access, alter, or retrieve data from the website's database.
How to pick a highly secure managed hosting provider?
Selecting the best managed hosting provider for your requirements might be challenging with the wide range of options available.
Determine your clients' security needs
Every client has different security demands, and vice versa. Thus, the selection process of a managed hosting company begins by outlining its security requirements precisely. Consider the following inquiries for yourself:
What kinds and volumes of data do your customers manage?
Are there any compliance requirements that they must follow?
What volume of traffic do they usually receive?
Which threats are most relevant to their line of business?
By doing this, you can make sure that the provider you choose is exactly suited to the unique requirements of your client.
Compile a list of possible suppliers
After determining your clients' security requirements, you must now assemble a list of possible suppliers.
First, use your professional network. Industry colleagues and associates can provide priceless advice based on first-hand knowledge.
Next, explore internet resources, including tech groups, specialized blogs, and industry forums. These might assist you in locating respectable suppliers that are worthy of your consideration.
Perform preliminary investigation
The next thing to do is conduct some basic research after you have a list of potential providers.
Start by perusing consumer feedback and rankings on independent discussion boards. Evaluate the public's overall opinion or emotion regarding each supplier.
An indication of a provider's integrity and resilience might be found in how they have handled previous issues.
Look into transparency as well; it's important. Evaluate the transparency of each provider's infrastructure, security protocols, operational standards, and even pricing.
Finally, but just as importantly, compare and ascertain whether the suppliers on your list have security and compliance certifications. Certifications may strongly indicate a provider's dedication to security. Make sure to confirm that these certifications are legitimate.
Shortlist providers
Reduce the number of suppliers on your list to a select few who appear to match your main requirements based on the results of your investigation.
Generally speaking, the companies on your list have to have excellent ratings, a track record of successfully managing security problems, a wide range of service options, and a clear dedication to user protection.
Compare and analyze the features
Now that the list has been reduced, let's compare them in more detail. Examine the security offerings of each shortlisted provider in further detail.
What DDoS defense mechanisms and technologies do they provide? How thorough are their methods for defending against malware? Do they also offer SSL certificates, which are essential for guaranteeing your clients' data transit security? What about backups and firewall security? Examine these attributes carefully for every supplier and draw appropriate conclusions.
Remember that mishaps can still occur even with the best security. Having a committed support staff on hand can be really helpful in that situation.
Therefore, compare the technical support that each provider offers, including availability and the stated response time, in addition to the specific security features.
Compare pricing
Once you have a solid understanding of each provider's characteristics, you can examine their pricing structures.
Here are some things to think about asking:
Exist any undisclosed expenses or fees?
Are the listed costs within your means?
Is scalability implemented economically? Put differently, will the hosting package be able to grow with your clients' company without becoming too expensive?
Do the prices make sense, given the variety and complexity of security features available?
A crucial reminder is to consider more than just the statistics when evaluating costs. Low-cost plans may have features that are not necessary or security flaws. On the other hand, a high price does not guarantee an unbreakable security suite.
The idea of value needs to be highlighted: What are the rewards, both material and immaterial, that you are getting out of your investment? Make sure the solution you're paying for is complete and genuinely serves the interests of you and your clients rather than just a brand name or flashy features.
Decide and go on board
Now that all the required investigation, evaluation, and contrast have been completed, the stage is ready to make an informed decision. Select the managed hosting company that best meets your security requirements, financial constraints, and business objectives.
After that, you just need to get in touch with the supplier to start the onboarding procedure.
Conclusion-
Making the move from unmanaged to managed hosting could significantly impact your company.
It's an investment that not only provides the best level of protection for your clients' digital assets but also frees up important time and resources that you can use for your main company operations.

Dollar2host
Dollar2host.com
We provide expert Webhosting services for your desired needs
Facebook Twitter Instagram YouTube
0 notes
Text
Welcome to my tutorial on how to install Kali Linux on Windows 11 with a GUI using the Windows Subsystem for Linux (WSL). Kali Linux is a popular operating system used by security professionals and enthusiasts for penetration testing and ethical hacking.
With the WSL feature on Windows 11, you can install and run a Linux environment without the need for a virtual machine or dual booting.
In this tutorial, I will guide you through the step-by-step process of installing Kali Linux using WSL and setting up the desktop environment for a graphical user interface. So, let's get started!
1Step 1: Enable Windows Subsystem for Linux2Step 2: Install Kali Linux from the Microsoft Store3Step 3: Set WSL 2 as the Default Version4Step 4: Launch Kali Linux5Step 5: Update Kali Linux6Step 6: Install the Win-Kex Desktop Environment7Step 7: Launch the Win-Kex Desktop Environment
Step 1: Enable Windows Subsystem for Linux
To get started, you'll need to enable the Windows Subsystem for Linux on your Windows 11 computer. Here's how:
Open the Windows Features settings by searching for "Turn Windows features on or off" in the Start menu. Or you can go to the “Control Panel” and then navigate to “Programs and Features”. On the sidebar, you can open Windows feature settings.
Scroll down to find “Virtual Machine Platform” and "Windows Subsystem for Linux," then check the boxes.
Click the "OK" button, and it will enable the Windows Subsystem for Linux. After that, you have to restart your computer when prompted.
Step 2: Install Kali Linux from the Microsoft Store
Once the Windows Subsystem for Linux is enabled, you can install Kali Linux from the Microsoft Store app on your Windows 11 computer. Here's how:
Open the Microsoft Store app on your Windows 11 computer. Then simply search for "Kali Linux" and select the Kali Linux app.
Click the "Get" button to install Kali Linux on your computer. This will take some time to install, depending on your internet connection. I will skip the installation part.
Sometimes you will get this error message during the installation.
WslRegistertionDistribution failed with Error: 0x80370102
Then you have to install Kali Linux manually from a downloaded package. You can download it here. (Manual installation of WSL-2)
You can download the Linux kernel update package from the above link. Then run this package; it will install the Linux kernel and resolve the error.
Step 3: Set WSL 2 as the Default Version
Next, you have to set Windows Subsystem for Linux Version 2 as the default version. Search for “Windows Power Shell” and run it as an administrator.
Then you have to enter this command. Ok, now WSL 2 is activated.
wsl --set-default-version 2
Step 4: Launch Kali Linux
With Kali Linux installed, you can launch the app to set it up for the first time. Here's how:
Open the Start menu and find the Kali Linux app. Then run it as an administrator, and it will launch the app to set up Kali Linux for the first time. It will ask you to choose a username and password when prompted.
You can enter any username and password, then verify them. You can see that Kali Linux is now running on your machine. Let's see how to set up the graphical user interface for this Kali Linux OS.
Step 5: Update Kali Linux
Now that Kali Linux is installed and launched, you'll want to update it to the latest version before installing the GUI. You just need to run a few small commands. Just copy and paste them below.
First, run this command to update the package list.
sudo apt update
It asks you to enter the root password that you set. This will take some time to update all the packages.
Step 6: Install the Win-Kex Desktop Environment
To use Kali Linux with a graphical user interface, you'll need to install the Win-Kex desktop environment. Win-KeX provides a Kali Desktop Experience for the Windows Subsystem for Linux with several features.
For that, you just have to enter this command, and it will begin the installation. Wait until it is finished.
sudo apt install -y kali-win-kex
Step 7: Launch the Win-Kex Desktop Environment
With the Win-Kex desktop environment installed, you can launch it in window mode, enhanced session mode, and seamless mode.
Win-Kex Modes
Window Mode
Enhanced Session Mode
Seamless Mode
You can use any of them. I am going to run in seamless mode. You need to enter this command to run Kali Linux in seamless mode.
kex --sl -s
It will ask for some firewall permissions, but you can allow them safely. You can try other modes also check this article for more information.
Now it is running on your computer.
To enter the Kali Linux GUI, open the Kali Linux terminal using the app. Then type “kex” and enter. When you enter it for the first time, it asks you to enter a password. You can enter whatever you want.
Then ask if you want this to be set as the view-only password, so type “N” here; otherwise, you didn’t be able to use the Kali Linux GUI.
Congratulations! You've successfully installed Kali Linux on Windows 11 using the Windows Subsystem for Linux and set up the graphical user interface! With Kali Linux installed, you can now use it for penetration testing and ethical hacking on your Windows 11 computer.
If you have any issues regarding this tutorial, feel free to contact us through the Minex Tuts tech forum. Thanks for watching/ reading, and don't forget to subscribe for more tutorials!
Ask Questions
0 notes
Text
Troubleshooting Guide: Sage 50 Won't Open After the Update

Sage 50 is a robust accounting software trusted by many businesses for managing their finances efficiently. However, encountering issues like the software not opening after an update can be frustrating and disruptive to your workflow. In this blog post, we'll explore some common reasons why Sage 50 may fail to open after an update and provide troubleshooting steps to resolve the issue Sage 50 Wont Open after the Update.
1. Check System Requirements:
Before delving into troubleshooting, ensure that your system meets the minimum requirements for running Sage 50. Make sure your computer has sufficient disk space, RAM, and processor speed to support the software. Also, verify that you are using a compatible operating system version.
2. Restart Your Computer:
Sometimes, a simple restart can fix software glitches and errors. Close all applications, restart your computer, and then try opening Sage 50 again to see if the issue persists.
3. Verify Internet Connection:
Sage 50 may require an active internet connection, especially after an update, to validate the license or perform other tasks. Check your internet connection and ensure that it is stable. If you're using a firewall or antivirus software, make sure it's not blocking Sage 50 from accessing the internet.
4. Run as Administrator:
Try running Sage 50 as an administrator to see if it resolves the issue. Right-click on the Sage 50 shortcut or executable file and select "Run as administrator" from the context menu. This grants the software elevated privileges and may help bypass any permission-related issues.
5. Disable Compatibility Mode:
If Sage 50 is set to run in compatibility mode for an older version of Windows, it may encounter compatibility issues with the latest updates. Right-click on the Sage 50 shortcut, go to Properties, navigate to the Compatibility tab, and uncheck the box that says "Run this program in compatibility mode for." Click Apply and then OK to save the changes.
6. Repair Sage 50 Installation:
Corrupted installation files can prevent Sage 50 from opening properly. To repair the installation, navigate to the Control Panel, go to Programs > Programs and Features, find Sage 50 in the list of installed programs, right-click on it, and select Repair. Follow the on-screen instructions to complete the repair process.
7. Reinstall Sage 50:
If none of the above steps resolve the issue, consider reinstalling Sage 50. Uninstall the software from your computer, download the latest version from the official Sage website, and reinstall it. Be sure to backup your company data before uninstalling to prevent any data loss.
Conclusion:
Encountering issues with Sage 50 not opening after an update can be frustrating, but with the right troubleshooting steps, you can resolve the issue and get back to managing your finances seamlessly. By following the tips outlined in this guide, you can diagnose the problem and implement the necessary fixes to ensure Sage 50 runs smoothly on your system.
0 notes
Text
TOWG
When did (GTA) Grand Theft Auto Come Out?
How to Disconnect Jumper Cables?
What is Adult Friend Finder?
How to Invest in Quantum AI
How does Steam Deck OLED work?
The Best Horror Games on PC
How to Get Free Money on Grand Theft Auto 5?
How to Play Grand Theft Auto 5 Online on Xbox 360?
How to Play The Legend of Zelda?
What is League of Legends?
How to Clear Opera Cache on PC & Smartphone?
How to Activate NFC on Android & iPhone?
How To Post GIFs on Instagram?
GameShark PS2 ISO (Latest Version)
Action Replay Max PS2 ISO
Xploder PS2 ISO
Top of the Best Cooperative Games on Nintendo Switch
Best Nintendo Switch Pokemon Games
Top of the Best Game Boy Advance Games
The Best Nintendo Switch Games for Kids
BEST GBA EMULATORS ON ANDROID
Best Nintendo Switch Emulators for PC and Android
What is the Top PSP Emulators for Android?
What Are the Best PSP Emulators for Windows PC or Mac?
The Best Nintendo Switch Games for 7-year Old’s
How to Play Nintendo Switch Games on Android?
HOW TO CONFIGURE YUZU EMULATOR ON PC?
How Do I Fix a Software Error on My Switch?
How to Charge Nintendo Switch?
How to Connect Nintendo Switch to TV?
How to Reset Bluetooth Headphones?
How to Connect Bluetooth Headphones to Mac?
How to Connect Bluetooth Headphones to PS4?
How to Connect Bluetooth Headphones to PC?
How to Connect Bluetooth Headphones to Xbox One?
How to Refund a Game on Steam?
Best Instagram Story Saver Download APK
How to Repair a Bow in Minecraft?
How to Download YouTube Videos Online-Offline?
How to Turn Off VPN? Do Your Turn VPN Off
How to Download Movies on iphone?
How to Pay with PayPal on Amazon without Card?
How to Buy Quality Essay from Expert Writers?
How to See WhatsApp Status Without Being Seen?
How to Send Automatically Disappearing Message on WhatsApp?
How To Make Money Online With Instagram Reels?
How to Deactivate Instagram Account?
How to Earn Money Online on Instagram?
How to Clear Memory on a Mac?| How to Free up RAM on Mac?
How To Change your MacBook Name?| How can I Rename my Mac?
How to Upload Photo on Google | Add Image to Google Search
What is Social Bookmarking? How to do Social Bookmarking?
What is Google Web Stories? Enable Web Stories on Google
How to Delete & Clear Internet Search History Online?
How to Increase Followers On Instagram?
0 notes
Text
FEATURES OF SAS PROGRAMMING

What is SAS-
Statistical Analysis Systems is the complete form of SAS. SAS is a versatile language for programming. The language elements are called procedures. The processes perform different things, such as different forms of analysis, functions of data management, and generate various types of output for text-based and graphical presentation.
There are the following uses for the SAS language and its procedures:
•In both internal and external databases, access info.
•Using different methods to handle data editing, retrieval, encoding, and conversions.
•Tools such as forecasting & modelling, descriptive statistics, multivariate methods, and linear programming are used.
•Present the performance information in different formats, such as papers, statistical graphs, etc.
SAS Programming 's Top 7 Features-
Good expertise for data processing
The first SAS function is that, as discussed below, SAS Programming has a potential for strong data analysis.
• It's like a complete package for data analysis streams. The acumen of its analysis ranges from simple statistics to an advanced level. For example, to compute a correlation between complex SAS data sets, it plots bar graphs from the given data.
• The best thing about SAS is the libraries that are built-in. These provide all of the necessary packages necessary for data analysis and reporting.
Flexible Programming Language of 4 Generations (4GL)
The main feature of SAS is that it is a programming language with 4GL.
• Easy-to - learn SAS syntax. The code is like a declaration. Such declarations serve as simple and succinct guidelines for the systems.
• With its built-in libraries, SAS has reduced coding for popular applications. It offers an opportunity for our work to be modularized. For non- programming users, it is also user-friendly.
• SAS is a language that is interactive. The log window is like a mirror which continues to instruct the user. It includes error notices and markings.
• It also has DS2, which assists in the manipulation of data. At its position in the database, complex data may be tampered with.
SAS Studio
Among the SAS functions, SAS Studio is special.
• With any web browser, it is easily accessible from any laptop. No client installation is required. All the SAS software libraries and data files can be accessed through any web browser.
• In essence, it is rather instructive. The Autocomplete role prompts us to use different procedures as soon as you start typing. For further guidance, the pop-up syntax and parameter list are shown.
• It also helps to add and build individual snippets of code and add them to the library of snippets.
• We may point to the guides and press it; it directs us at different levels in the research process.
Various Types of Data Format for Support
Another feature of SAS is support for different data formats.
• The language of SAS has the ability to read data from any file type, from any format and even from missing data files.
• SAS offers SQL support. It has an immense character encoding database; the most commonly used languages are completely supported.
• It also preserves the singularity of code, so that SAS works in multiple languages with data.
Management
One of SAS's significant characteristics is SAS Management.
• The SAS environment manager warns, tracks and controls the environment for analytics.
• The extended Java Graphical user interface in the SAS Management Console administers SAS activities.
• One of the essential characteristics of SAS software is SAS management. It has an SAS Environmental Manager who warns, tracks and controls the ecosystem for analytics. In the SAS Management Console, the Expanded Java Graphical User Interface administers SAS functions.
• There are a number of functions in the XML engine, such as importing and exporting XML documents and generating XML maps.
• The Application Response Measurement interface tests different applications and checks for transaction availability.
Report Output Format
• SAS is able to view analytical findings and the number of options for reporting.
• In Base SAS 9.4, high-quality graphics are ODS statistical graphics, ODS Graphics Designer and Editor and so on.
• In a standard format like RTF, PowerPoint, and pdf, we can save and generate reports. They can also be saved as an ebook and an I-book. It offers us the privilege of analytic visuals.
• We can tailor performance according to the clients' hierarchy of needs. The production can be ported to different locations.
Algorithms for Data Encryption
SAS makes sure that the confidentiality of how we grant access remains immaterial. In SAS 9.4, SAS / SECURE is a safety feature. Via different algorithms, we can also encrypt SAS data on discs.
Summary
We have studied in this SAS function that SAS programming is a complete package for any kind of statistical work. It also offers service support on all but one of the channels. All those commonly required for review are included in the libraries in the SAS. Its encryption function makes it secure and portable for different devices.
About Rang Technologies:
Headquartered in New Jersey, Rang Technologies has dedicated over a decade delivering innovative solutions and best talent to help businesses get the most out of the latest technologies in their digital transformation journey. Read More...
0 notes
Text
does express vpn work on xp
🔒🌍✨ Get 3 Months FREE VPN - Secure & Private Internet Access Worldwide! Click Here ✨🌍🔒
does express vpn work on xp
Compatibility of ExpressVPN with Windows XP
ExpressVPN is a leading VPN service provider known for its user-friendly interface and robust security features. When it comes to the compatibility of ExpressVPN with Windows XP, users may encounter certain limitations due to the outdated operating system.
Windows XP was released by Microsoft in 2001 and stopped receiving official support and updates in 2014. As a result, many software developers, including VPN providers like ExpressVPN, have gradually phased out support for Windows XP due to security concerns and compatibility issues.
While ExpressVPN may have been compatible with Windows XP in the past, the latest versions of the VPN client may not be fully optimized to work seamlessly with the outdated operating system. Users attempting to install and run ExpressVPN on Windows XP may encounter errors, connectivity issues, or be unable to access certain features and server locations.
For users who are still using Windows XP and require VPN services, it is recommended to consider upgrading to a more recent and supported operating system, such as Windows 7, 8, or 10. These newer versions of Windows offer enhanced security features, better performance, and broader compatibility with the latest software, including VPN clients like ExpressVPN.
In conclusion, while ExpressVPN may have been compatible with Windows XP in the past, users should be aware of the potential limitations and risks of using an outdated operating system with a modern VPN service. Upgrading to a newer version of Windows will not only ensure better compatibility with ExpressVPN but also improve the overall security and performance of the system.
ExpressVPN functionality on Windows XP
ExpressVPN, a leading virtual private network (VPN) service provider, offers functionality on Windows XP, providing users with privacy, security, and unrestricted access to online content.
Despite Windows XP's outdated status, ExpressVPN remains compatible with this operating system, allowing users to safeguard their online activities. With ExpressVPN installed on Windows XP, users can encrypt their internet connection, shielding their data from potential threats such as hackers, ISPs, and government surveillance.
ExpressVPN's functionality on Windows XP extends beyond security to provide users with access to geo-restricted content. By connecting to servers located around the world, users can bypass censorship and access streaming services, social media platforms, and websites that may be blocked in their region.
Setting up ExpressVPN on Windows XP is straightforward, with user-friendly installation instructions provided by the service. Once installed, users can easily connect to their preferred servers with just a few clicks, ensuring a seamless browsing experience.
Moreover, ExpressVPN's Windows XP compatibility ensures that users can enjoy fast and reliable connections, enabling smooth streaming, gaming, and downloading experiences.
Despite Windows XP's lack of support from Microsoft, ExpressVPN continues to prioritize the security and privacy of its users on this platform. By offering functionality on Windows XP, ExpressVPN ensures that even users of older operating systems can benefit from the advantages of a VPN.
In conclusion, ExpressVPN's functionality on Windows XP provides users with essential security, privacy, and access to online content, making it a valuable tool for those still utilizing this operating system.
ExpressVPN support for Windows XP
ExpressVPN, a popular virtual private network service provider, offers versatile and reliable support for various operating systems, including Windows XP. Despite Microsoft ending support for Windows XP in 2014, there are still users who rely on this legacy operating system for various reasons.
ExpressVPN's commitment to user satisfaction is evident in their continued support for Windows XP users. By providing a dedicated client that is compatible with Windows XP, ExpressVPN ensures that even users of this outdated operating system can benefit from the security and privacy features that the VPN service offers.
With ExpressVPN's support for Windows XP, users can enjoy a secure browsing experience, safeguarding their sensitive information from potential cyber threats and surveillance. The VPN service encrypts internet traffic, making it virtually impossible for third parties to intercept or monitor online activities.
Additionally, ExpressVPN's global network of servers allows Windows XP users to access geo-restricted content and websites with ease. By connecting to servers in different locations, users can bypass censorship and access online content that may otherwise be unavailable in their region.
In conclusion, ExpressVPN's support for Windows XP underscores the company's dedication to inclusivity and user satisfaction. By offering a reliable VPN solution for users of this legacy operating system, ExpressVPN ensures that everyone can enjoy a secure and unrestricted internet experience, regardless of the platform they choose to use.
Using ExpressVPN with Windows XP
ExpressVPN is a popular VPN service that offers users a secure and private internet experience. While Windows XP is an outdated operating system that is no longer supported by Microsoft, it is still possible to use ExpressVPN with Windows XP with a few considerations.
Before attempting to use ExpressVPN with Windows XP, it's important to note that Microsoft no longer releases security updates for this operating system. This means that using Windows XP can expose your device to security vulnerabilities. However, if you still choose to proceed, here are some steps to use ExpressVPN with Windows XP:
Download the compatible version of ExpressVPN: Visit the official ExpressVPN website and download the version of the software that is compatible with Windows XP. Follow the on-screen instructions to complete the installation process.
Subscribe to ExpressVPN: Sign up for an ExpressVPN subscription if you haven't already. You will need a valid account to log in to the software.
Launch ExpressVPN: Open the ExpressVPN application on your Windows XP device. Enter your login credentials to access the dashboard.
Connect to a VPN server: Select a VPN server location from the list provided by ExpressVPN. Click on the "Connect" button to establish a secure connection.
Enjoy a secure internet experience: Once connected, your internet traffic will be encrypted, and your online activities will be protected from prying eyes.
It's essential to remember that using an outdated operating system like Windows XP poses security risks. Consider upgrading to a newer version of Windows to ensure better protection for your device and data.
ExpressVPN performance on Windows XP
ExpressVPN is a popular choice for users looking to enhance their online privacy and security. However, when it comes to performance on Windows XP, there are some factors to consider.
Windows XP, being an older operating system that is no longer supported by Microsoft, may present some challenges when running modern software like ExpressVPN. While ExpressVPN does offer support for older versions of Windows, the performance on Windows XP may vary compared to newer operating systems such as Windows 7 or Windows 10.
One of the key factors affecting the performance of ExpressVPN on Windows XP is the hardware capabilities of the system. Since Windows XP is an older operating system, it may not be able to fully utilize the advanced features of ExpressVPN, leading to potential performance issues such as slower connection speeds or higher CPU usage.
Additionally, since Windows XP is no longer receiving security updates from Microsoft, using a VPN like ExpressVPN can help enhance the security of the system by encrypting internet traffic and protecting sensitive data from potential cyber threats.
Overall, while ExpressVPN can still be installed and used on Windows XP, users may experience varying performance based on the system specifications and limitations of the operating system. It is recommended to ensure that the system meets the minimum requirements for running ExpressVPN to achieve optimal performance and security benefits.
0 notes