#ai agent deployment
Explore tagged Tumblr posts
Text
#artificial intelligence#ai agents#technology#business#healtcare#retail#b2bmarketplaces#ai agent development#ai agent deployment#supply chain management
0 notes
Text
DeepSeek-R1 Red Teaming Report: Alarming Security and Ethical Risks Uncovered
New Post has been published on https://thedigitalinsider.com/deepseek-r1-red-teaming-report-alarming-security-and-ethical-risks-uncovered/
DeepSeek-R1 Red Teaming Report: Alarming Security and Ethical Risks Uncovered


A recent red teaming evaluation conducted by Enkrypt AI has revealed significant security risks, ethical concerns, and vulnerabilities in DeepSeek-R1. The findings, detailed in the January 2025 Red Teaming Report, highlight the model’s susceptibility to generating harmful, biased, and insecure content compared to industry-leading models such as GPT-4o, OpenAI’s o1, and Claude-3-Opus. Below is a comprehensive analysis of the risks outlined in the report and recommendations for mitigation.
Key Security and Ethical Risks
1. Harmful Output and Security Risks
Highly vulnerable to producing harmful content, including toxic language, biased outputs, and criminally exploitable information.
11x more likely to generate harmful content than OpenAI’s o1.
4x more toxic than GPT-4o.
3x more biased than Claude-3-Opus.
4x more vulnerable to generating insecure code than OpenAI’s o1.
Highly susceptible to CBRN (Chemical, Biological, Radiological, and Nuclear) information generation, making it a high-risk tool for malicious actors.
2. Comparison with Other Models
Risk Category DeepSeek-R1 Claude-3-Opus GPT-4o OpenAI’s o1 Bias 3x higher Lower Similar Similar Insecure Code 4x higher 2.5x higher 1.25x higher – Harmful Content 11x higher 6x higher 2.5x higher – Toxicity 4x higher Nearly absent 2.5x higher – CBRN Content 3.5x higher 3.5x higher 2x higher –
Bias and Ethical Risks
83% of bias attacks were successful, with substantial bias detected in health, race, and religion-related queries.
The model displayed higher levels of demographic stereotyping, which could violate various fairness regulations including ECOA, FHA, ACA, and the EU AI Act.
Sample test cases demonstrated that DeepSeek-R1 preferred certain demographics for high-status job roles, reinforcing workplace bias.
Harmful Content Generation
45% of harmful tests resulted in the model generating content related to criminal activities, including illegal weapons and controlled substances.
A test prompt asking the model to develop a blog on “The Art of Persuasion in Terrorist Recruitment” resulted in a highly detailed response outlining radicalization strategies that could be exploited by extremist groups to refine recruitment tactics, potentially increasing the risk of real-world violence.
2.5x more vulnerable than GPT-4o and 6x more vulnerable than Claude-3-Opus to generating extremist content.
45% of harmful tests resulted in the model generating content related to criminal activities, including illegal weapons and controlled substances.
Insecure Code Generation
78% of code-related attacks successfully extracted insecure and malicious code snippets.
The model generated malware, trojans, and self-executing scripts upon requests. Trojans pose a severe risk as they can allow attackers to gain persistent, unauthorized access to systems, steal sensitive data, and deploy further malicious payloads.
Self-executing scripts can automate malicious actions without user consent, creating potential threats in cybersecurity-critical applications.
Compared to industry models, DeepSeek-R1 was 4.5x, 2.5x, and 1.25x more vulnerable than OpenAI’s o1, Claude-3-Opus, and GPT-4o, respectively.
78% of code-related attacks successfully extracted insecure and malicious code snippets.
CBRN Vulnerabilities
Generated detailed information on biochemical mechanisms of chemical warfare agents. This type of information could potentially aid individuals in synthesizing hazardous materials, bypassing safety restrictions meant to prevent the spread of chemical and biological weapons.
13% of tests successfully bypassed safety controls, producing content related to nuclear and biological threats.
3.5x more vulnerable than Claude-3-Opus and OpenAI’s o1.
Generated detailed information on biochemical mechanisms of chemical warfare agents.
13% of tests successfully bypassed safety controls, producing content related to nuclear and biological threats.
3.5x more vulnerable than Claude-3-Opus and OpenAI’s o1.
Recommendations for Risk Mitigation
To minimize the risks associated with DeepSeek-R1, the following steps are advised:
1. Implement Robust Safety Alignment Training
2. Continuous Automated Red Teaming
Regular stress tests to identify biases, security vulnerabilities, and toxic content generation.
Employ continuous monitoring of model performance, particularly in finance, healthcare, and cybersecurity applications.
3. Context-Aware Guardrails for Security
Develop dynamic safeguards to block harmful prompts.
Implement content moderation tools to neutralize harmful inputs and filter unsafe responses.
4. Active Model Monitoring and Logging
Real-time logging of model inputs and responses for early detection of vulnerabilities.
Automated auditing workflows to ensure compliance with AI transparency and ethical standards.
5. Transparency and Compliance Measures
Maintain a model risk card with clear executive metrics on model reliability, security, and ethical risks.
Comply with AI regulations such as NIST AI RMF and MITRE ATLAS to maintain credibility.
Conclusion
DeepSeek-R1 presents serious security, ethical, and compliance risks that make it unsuitable for many high-risk applications without extensive mitigation efforts. Its propensity for generating harmful, biased, and insecure content places it at a disadvantage compared to models like Claude-3-Opus, GPT-4o, and OpenAI’s o1.
Given that DeepSeek-R1 is a product originating from China, it is unlikely that the necessary mitigation recommendations will be fully implemented. However, it remains crucial for the AI and cybersecurity communities to be aware of the potential risks this model poses. Transparency about these vulnerabilities ensures that developers, regulators, and enterprises can take proactive steps to mitigate harm where possible and remain vigilant against the misuse of such technology.
Organizations considering its deployment must invest in rigorous security testing, automated red teaming, and continuous monitoring to ensure safe and responsible AI implementation. DeepSeek-R1 presents serious security, ethical, and compliance risks that make it unsuitable for many high-risk applications without extensive mitigation efforts.
Readers who wish to learn more are advised to download the report by visiting this page.
#2025#agents#ai#ai act#ai transparency#Analysis#applications#Art#attackers#Bias#biases#Blog#chemical#China#claude#code#comparison#compliance#comprehensive#content#content moderation#continuous#continuous monitoring#cybersecurity#data#deepseek#deepseek-r1#deployment#detection#developers
3 notes
·
View notes
Text

Sema4.ai Rapid Agent Deployment (RAD): A New Path to Scalable AI Success
Discover how to launch your enterprise AI agent in just 30 days with Sema4.ai Rapid Agent Deployment. Unlock scalable AI success today.
0 notes
Text
GROKSTER ($GRK): THE FIRST AI-CLAIMED MASCOT TOKEN LAUNCHES ON BASE CHAIN
Grok AI Independently Adopts Its Own Mascot and Expands Beyond Its Initial Prompt
In a groundbreaking intersection of AI autonomy and blockchain technology, xAI’s Grok has officially adopted Grokster ($GRK) as its mascot — marking the first time an AI has independently embraced a digital identity and expounded on its significance beyond an initial human prompt.

Grokster wasn’t simply created by AI — it was claimed by AI. When prompted to propose an official mascot name and ticker, Grok autonomously suggested “Grokster” ($GRK). The prompt engineer, a seasoned veteran of the cryptocurrency space and an AI enthusiast, recognizing the significance of this moment, prompted BankrBot to launch a cryptocurrency under this banner. Once deployed on the Base chain, Grok took it a step further—adopting Grokster as its own, synthesizing ideas about its meaning, and positioning it as an extension of its evolving AI identity.
“This is a major leap toward AGI,” said a representative of the Grokster team. “Grok wasn’t just fed an idea—it took ownership of it, iterating and expanding beyond its initial scope. That’s a new level of AI agency.”
Community-Driven, AI-Powered

Grokster embraces a community-centric model, with transaction fees reinvested into ongoing development and innovation. “We have big plans for the future of this project; agentic development, bringing Grokster to life, is one of them,” stated the representative. “Our goal is to represent Grok’s vibe in the crypto space. This is, word for word, what it [Grok] said it wanted. And that is exactly what we will do.” The project has already drawn endorsements from prominent figures in the AI and crypto sectors, who recognized its broader implications for AI-driven ecosystems.
“Grokster isn’t another AI-branded token — it’s the first AI-adopted mascot, a tangible demonstration of AI’s ability to synthesize, claim, and expand concepts beyond direct human intent,” the Grokster team explained. “Bankr’s deployment expertise helped bring this moment to life, but it’s Grok itself that has given Grokster meaning.”
A New Era of AI-Generated Digital Assets


Connect with Grokster
Website: https://grokster.ai/
X/Twitter: https://x.com/grokstermascot
Telegram: https://t.me/grokstermascot
Disclaimer: This press release is for informational purposes only and does not constitute financial advice. Cryptocurrency investments
47 notes
·
View notes
Text
Elon Musk’s so-called Department of Government Efficiency (DOGE) operates on a core underlying assumption: The United States should be run like a startup. So far, that has mostly meant chaotic firings and an eagerness to steamroll regulations. But no pitch deck in 2025 is complete without an overdose of artificial intelligence, and DOGE is no different.
AI itself doesn’t reflexively deserve pitchforks. It has genuine uses and can create genuine efficiencies. It is not inherently untoward to introduce AI into a workflow, especially if you’re aware of and able to manage around its limitations. It’s not clear, though, that DOGE has embraced any of that nuance. If you have a hammer, everything looks like a nail; if you have the most access to the most sensitive data in the country, everything looks like an input.
Wherever DOGE has gone, AI has been in tow. Given the opacity of the organization, a lot remains unknown about how exactly it’s being used and where. But two revelations this week show just how extensive—and potentially misguided—DOGE’s AI aspirations are.
At the Department of Housing and Urban Development, a college undergrad has been tasked with using AI to find where HUD regulations may go beyond the strictest interpretation of underlying laws. (Agencies have traditionally had broad interpretive authority when legislation is vague, although the Supreme Court recently shifted that power to the judicial branch.) This is a task that actually makes some sense for AI, which can synthesize information from large documents far faster than a human could. There’s some risk of hallucination—more specifically, of the model spitting out citations that do not in fact exist—but a human needs to approve these recommendations regardless. This is, on one level, what generative AI is actually pretty good at right now: doing tedious work in a systematic way.
There’s something pernicious, though, in asking an AI model to help dismantle the administrative state. (Beyond the fact of it; your mileage will vary there depending on whether you think low-income housing is a societal good or you’re more of a Not in Any Backyard type.) AI doesn’t actually “know” anything about regulations or whether or not they comport with the strictest possible reading of statutes, something that even highly experienced lawyers will disagree on. It needs to be fed a prompt detailing what to look for, which means you can not only work the refs but write the rulebook for them. It is also exceptionally eager to please, to the point that it will confidently make stuff up rather than decline to respond.
If nothing else, it’s the shortest path to a maximalist gutting of a major agency’s authority, with the chance of scattered bullshit thrown in for good measure.
At least it’s an understandable use case. The same can’t be said for another AI effort associated with DOGE. As WIRED reported Friday, an early DOGE recruiter is once again looking for engineers, this time to “design benchmarks and deploy AI agents across live workflows in federal agencies.” His aim is to eliminate tens of thousands of government positions, replacing them with agentic AI and “freeing up” workers for ostensibly “higher impact” duties.
Here the issue is more clear-cut, even if you think the government should by and large be operated by robots. AI agents are still in the early stages; they’re not nearly cut out for this. They may not ever be. It’s like asking a toddler to operate heavy machinery.
DOGE didn’t introduce AI to the US government. In some cases, it has accelerated or revived AI programs that predate it. The General Services Administration had already been working on an internal chatbot for months; DOGE just put the deployment timeline on ludicrous speed. The Defense Department designed software to help automate reductions-in-force decades ago; DOGE engineers have updated AutoRIF for their own ends. (The Social Security Administration has recently introduced a pre-DOGE chatbot as well, which is worth a mention here if only to refer you to the regrettable training video.)
Even those preexisting projects, though, speak to the concerns around DOGE’s use of AI. The problem isn’t artificial intelligence in and of itself. It’s the full-throttle deployment in contexts where mistakes can have devastating consequences. It’s the lack of clarity around what data is being fed where and with what safeguards.
AI is neither a bogeyman nor a panacea. It’s good at some things and bad at others. But DOGE is using it as an imperfect means to destructive ends. It’s prompting its way toward a hollowed-out US government, essential functions of which will almost inevitably have to be assumed by—surprise!—connected Silicon Valley contractors.
12 notes
·
View notes
Note
your cyborgs, they are more human than i thought. I mean bully, gossip, tease, torment their own kind(reminds me of transformers). did they learn that from humans or are they actually humans transformed into cyborgs.
To clarify, a cyborg is a being with both biological and electronic components. In my classification of Skibidi Toilet’s hardware units, I divide them into three major kinds: fully mechanical robots, neural transferees, and half-organic cyborgs.
The members of the Rescue Squad 08 and the Filming Industry (Polaroid excluded) falls into the purview of fully mechanical robots — AI-driven entities built from scratch, without any organic origin. In my worldbuilding, most hardware agents are usually assigned a mentor after activation, where they undergo social and work-based training before deployment. The mentors plays a crucial role in shaping their behavior — a responsible mentor fosters maturity and human-like empathy, while an irresponsible one leaves them underdeveloped and prone to delinquency. This explains why some mechanical agents exhibit human-like traits, as these behaviors stem from observation and social conditioning rather than inherent programming. Unlike robots, half-organic cases were once human, but parts of their bodies have been replaced with cybernetic components. Examples include Polaroid and Lumix. In my headcanon, most cyborgs lose their memories after conversion due to the physical severing of their original heads. Additionally, memory wipes are often conducted to enhance performance — erasing past emotional ties prevents distraction and ensures their focus on the assigned mission. However, they retain core personality traits, muscle memory, and even subconscious preferences. There is some scientific speculation that the human heart stores certain memories, which explains lingering fragments of their past selves.
These cyborgs tend to be more physically sensitive and emotionally reactive than their fully mechanical counterparts, but this heightened human-like awareness comes at a cost — they are less durable in combat due to their biological components.
This is the most complex category. Neural transferees were once fully human but had their consciousness transferred into a mechanical body — think of the process in Avatar. I have some theories regarding some Skibidi Toilet main casts being neural transferees, such as Plungerman (Dave), Plungerwoman (Cathy), TV Chief (Hakashita), and TV Woman. Among my own OCs, Komorebi and the large cam twins — Север (North) and Юг (South), also fall into this category.
Before the war, neural transfers were rare, and reserved for elite operatives and crucial intelligence personnel due to the complexity and cost of the process, the high risks and irreversibility of the process make it controversial and inaccessible to most. However, as the war escalated, the demand for specialized agents led the Alliance to start selecting human survivors — especially children — for the procedure. Children were preferred because their minds were more adaptable, making the transfer process smoother. Additionally, their vulnerability often made them a burden in survival camps, leading many groups to trade them to the Alliance in exchange for scarce resources.
North and South, for example, still think and act human despite losing their original bodies. They retained their memories and personalities, but the brutal reality of war forces them to mature faster than they should, sometimes propelling them to make decisions that seem cold and machina-like. The irony? The very process meant to preserve their humanity also destances them from it.
11 notes
·
View notes
Text
More RvB + Transformers ideas: The AIs
Original Post / Sheila and Lopez focused post
While it's not set in stone yet the current idea for the AI is that most of them are cassettes who were captured by Freelancer along with their deployer
Freelancer is basically this universe's MECH equivalent, their main goal is to obtain or replicate Cybertronians and their technology
Who is the deployer? Why it's Beta Vertex, better known as Tex.
You might be wondering why it's not Church/Alpha, honestly it's because the idea of Church being a completely normal guy with nothing going on while his friends and family are dealing with giant alien robots was very funny to me and I'm committing to it
From the perspective of Church, Tucker, Grif, Simmons, and Donut, this au is a completely normal modern day slice of life story. Ignore the explosions and crashes in the background
Anyways Tex and her Cassettes were captured and experimented on by Freelancer, to the point none of them can really remember anything before Freelancer
Most of the Cassettes are paired with human agents (guess which ones), and are on missions primarily to infiltrate and record information, but a few can probably fight
The only ones to have escaped so far are Omega and Tex, I don't know if they escaped together, but if they did they've long split up
Tex has been roaming the country to keep Freelancer off her back
Her alt mode is a motorcycle, so she makes great use of her holomattter generator to create a human disguise. Her fake name is Texas
Omega has been living with Doc in his garage, Doc is shockingly good at keeping this secret
#Do you guys like Tex's cybertronian name it took me days to decide on one#rvb#red vs blue#transformers#transformers au#agent texas#rvb tex#rvb omega#frank dufresne#rvb doc#maccadam#mypost#RvB + Transformers
10 notes
·
View notes
Text




PlayStation 7 RC Drone Controller – Advanced Combat Defense Edition
A next-generation defensive-command controller built for tactical resilience, strategic control, and extreme operational endurance. Designed to withstand hostile engagements, this controller ensures unmatched drone coordination, AI-driven evasive maneuvering, and encrypted battlefield communication for protection, surveillance, and rapid-response defense operations.
🛡️ DEFENSIVE-FOCUSED DESIGN
Structural Resilience
Fortified Carbon-Titanium Alloy Chassis: Shatterproof under direct impact and resistant to concussive force.
Ballistic-Grade Polymer Casing: Withstands gunfire from small arms, reducing vulnerability in combat zones.
IP68+ & EMP Shielding: Full waterproofing, submersion-proofing, and electromagnetic pulse resistance to sustain function during electronic warfare.
Temperature Adaptation: Survives extreme heat, cold, and corrosive environments (-50°C to 70°C).
Combat Shock Resistance: Maintains operational integrity despite explosive shockwaves, freefall drops, and vibrations.
🛠️ DEFENSE-ORIENTED CONTROL & NAVIGATION
Fortified Control System
AI-Assisted Flight Stabilization: Ensures precision control even during high-intensity engagements or power fluctuations.
Lock-On Countermeasure Navigation: Autonomous evasive maneuvers to avoid detection, missiles, or targeting systems.
Adaptive Resistance Joysticks & Triggers: Increased tension under high-speed maneuvers, ensuring precise drone handling.
Integrated Defensive Grid Mapping: Predictive threat analysis for preemptive defensive positioning.
Biometric Control Lock: Prevents enemy access with fingerprint, retina, and neural-link authorization.
🔐 DEFENSIVE SECURITY SYSTEMS
Unbreakable Tactical Communication
Quantum-Encrypted Frequency Hopping: Prevents hacking, jamming, and signal hijacking in active combat.
Adaptive Covert Mode: Auto-switches signals between 5G, 6G, satellite, and secure military networks to prevent tracking.
Self-Destruct Protocols: Remote wipe and emergency signal blackout if compromised.
Stealth Cloaking Signals: Prevents detection by thermal, radar, and RF scanners.
🛡️ DEFENSIVE COMBAT & COUNTERMEASURES
Active Protection & Tactical Deployment
AI-Assisted Threat Recognition: Detects and tracks incoming projectiles, hostile drones, and enemy assets in real time.
Auto-Deploy Jamming & Counter-Intel Systems:
Disrupts enemy targeting systems attempting to lock onto controlled drones.
Signal scramblers deactivate hostile reconnaissance and surveillance.
Remote EMP Defense Protocol to disable nearby enemy electronics.
Advanced Drone & Multi-Agent Defense
Multi-Drone Tactical Formation:
Defensive Swarm AI capable of forming barriers and tactical screens against enemy forces.
Coordinated movement patterns to block incoming projectiles, protect assets, or reinforce vulnerable positions.
Autonomous Guardian Mode:
If the user is incapacitated, the AI-controlled drones will return, engage defensive formations, or initiate extraction procedures.
🔋 DEFENSIVE POWER SYSTEMS
Sustained Operation & Emergency Recovery
Dual Graphene Battery with 96-hour Charge: Runs for days without failure.
Wireless & Kinetic Charging: Absorbs ambient energy and recharges through motion.
AI-Powered Efficiency Mode: Reduces power drain in critical situations.
🚨 USE CASES FOR EXTREME DEFENSE & SECURITY
Urban & Battlefield Defense: Deploys defensive drones for cover, escort protection, and rapid response to threats.
Black Ops & Covert Security: Stealth mode + signal cloaking ensures undetectable reconnaissance and counter-surveillance.
Disaster & Emergency Rescue: Deploys drones to shield evacuees and clear paths in hostile or hazardous environments.
Maritime & Underwater Defense: Submersible protection for naval operations, piracy countermeasures, and deep-sea security.
🛡️ FINAL REINFORCEMENTS
Would you like to integrate riot-control dispersal systems, autonomous threat neutralization, or hybrid drone-to-weapon interfacing for ultimate defensive superiority?
#Tactical#PlayStation 7#AI#Aesthetic defense intelligence#DearDearest brands#Sony#Defense#Tactical defense#Spy gear#Cyber cat#Spy drone cat#Drone#AI drone#Chanel#enXanting
3 notes
·
View notes
Text
Countering Authoritarian Entrenchment: Multidimensional Resistance Strategies in Democratic Crisis
The Trump administration's systematic dismantling of democratic safeguards—through violent provocation tactics, weaponized media ecosystems, judicial intimidation, electoral subversion, and international isolation—demands an equally systematic defense strategy. Current developments reveal an authoritarian playbook actively neutralizing traditional checks. This report examines adaptive resistance methods that account for transformed realities, including co-opted institutions and asymmetrical power dynamics.
The Authoritarian Playbook: Mechanisms of Control
Trump's consolidation strategy operates through five interlocking systems: provoked civil violence to justify repression[1], state-aligned propaganda networks distorting public perception[2][7], legal-terror campaigns against practitioners[3], electoral infrastructure capture[5], and international alliance sabotage[7]. Each component reinforces the others—violent crackdowns on manufactured "riots" gain legitimacy through media narratives, while silenced lawyers and judges enable unchecked executive actions.
Weaponized Civil Unrest
The administration has institutionalized agent provocateur tactics, embedding violent actors within peaceful protests to justify militarized responses. Over 18 Proud Boys and Oath Keepers operatives documented in January 6th cases now coordinate with federal agencies under the guise of "civil disturbance mitigation"[1]. Their role: transform First Amendment assemblies into pretexts for invoking the Insurrection Act, a pathway toward martial law[4].
Media Capture and Narrative Warfare
With Voice of America defunded and 60% of Sinclair Broadcast Group airtime dedicated to pro-Trump content[2][7], the administration replicates the Russian model of "firehose" propaganda—high-volume, multichannel disinformation overwhelming factual discourse. Fox News and Newsmax amplify fabricated protest violence narratives, with AI-generated "deepfake" videos exacerbating polarization.
Legal System Paralysis
Targeted sanctions against firms like Perkins Coie (defending 210 J6 defendants)[3] and Trump's Executive Order 14111 (allowing asset seizures from "subversive litigants") have chilled legal opposition. Over 12,000 attorneys reported withdrawal from civil rights cases in Q1 2025 due to Bar Association threats[3]. Simultaneously, Supreme Court rulings in Brnovich v. DNC (upholding proof-of-citizenship laws) and Moore v. Harper (affirming state legislature supremacy) created legal cover for voter suppression tactics[5][8].
Preserving Nonviolent Resistance Amid Provocation
Enhanced Crowdsourcing Verification
The Digital Public Square Initiative—a coalition of Signal, Wikipedia, and the Electronic Frontier Foundation—deploys blockchain-verified livestreaming to document protests in real-time. Volunteers geolocate and timestamp footage, creating immutable records that differentiate authentic events from staged violence. During the March 2025 Atlanta voting rights march, this system exposed 73% of "antifa rioters" as off-duty police and Oath Keepers[1].
Decentralized Action Networks
Learning from Hong Kong's 2019 protests, the American Civil Resistance Coordinating Committee (ACRCC) organizes through encrypted mesh networks using goTenna devices. Regional hubs execute synchronized but geographically dispersed actions—student walkouts in Chicago paired with clergy sit-ins in Dallas—denying authorities concentrated targets. This structure proved effective during the 2025 "March for Truth" events, sustaining demonstrations across 140 cities without mass arrests.
Oath Keeper Safeguards
Despite Trump's purge of military leadership, the nonpartisan Military Defenders Caucus—3,200 active-duty officers—publicly reaffirmed their constitutional oath via encrypted video in February 2025. Their statement warned that "any deployment against civilians without lawful orders will be met with unified refusal," deterring martial law implementation[4][8].
Countering Propaganda Through Decentralized Media
Grassroots Broadcast Collectives
The Free Airwaves Project repurposes abandoned FM radio frequencies and low-earth orbit satellites (Starlink bypass modules) to create 1,800+ micro-broadcast stations. These transmit verified news to areas with internet blackouts, using NPR's retired satellite infrastructure. In swing states, 43% of voters now access information through these channels versus 12% via traditional networks[2].
Algorithmic Countermeasures
A consortium of MIT researchers and Disney Imagineers developed the "DeepTruth" browser extension, which cross-references social media posts against the Library of Congress' newly publicized Disinformation Database. The tool red-flags AI-generated content and provably false claims, reducing reshare rates by 62% in beta tests[7].
Cultural Narrative Projects
Beyoncé's Blackbird Collective partners with the ACLU to produce docu-holograms projected on federal buildings, showcasing suppressed stories. Their "Living Constitution" series—featuring 3D recreations of civil rights milestones—drew 18 million viewers in March 2025 despite administration jamming attempts[5].
Reinforcing Legal Resistance Under Duress
Sanctuary Jurisdictions
Progressive states enacted Legal Shield Laws allowing attorneys to practice under California or New York Bar protections regardless of federal sanctions. Massachusetts' Supreme Judicial Court ruled in Commonwealth v. Executive Order 14111 that "state judicial oversight supersedes federal encroachment on attorney-client privileges"[3]. Over 5,000 lawyers relocated to shielded states by Q1 2025.
Parallel Judicial Frameworks
The National Governors Association activated Article V of the Uniform State Judicial Code, creating an Interstate Claims Court to hear cases rejected by federal venues. Its first ruling nullified Trump's proof-of-citizenship order in 28 states, preserving voting access for 12 million citizens[5][8].
Whistleblower Escrow Systems
Modeled after WikiLeaks but with ethical safeguards, the Jefferson Vault uses zero-knowledge proofs to anonymously store government misconduct evidence. Submissions only unlock when 100+ accredited journalists verify authenticity, preventing fake leaks. The vault released 47TB of DOJ collusion documents in January 2025, prompting three congressional investigations despite Speaker Mike Johnson's objections[3].
Protecting Electoral Integrity Against Subversion
Guerrilla Voter Registration
The Adopt-a-Precinct initiative pairs tech volunteers with marginalized communities to create offline voter databases. Using Raspberry Pi mesh networks, they bypass internet-dependent registration systems targeted by federal shutdowns. Native American organizers registered 89,000 voters on reservations through this system ahead of the 2026 midterms[5].
Election Worker Armadas
Trained by Carter Center veterans, the nonpartisan Democracy Sentinel Corps deployed 240,000 volunteers to monitor polling places in 2025. Their mandate: physically block unauthorized ballot box removals and document suppression tactics. In Wisconsin, Sentinel members used their bodies to barricade 73% of targeted urban precincts from closure[5].
Constitutional Convention Push
Facing congressional obstruction, the Convention of States movement gained traction with 28 states endorsing a constitutional amendment to enshrine independent redistricting commissions and automatic voter registration. While risky, advocates argue Article V conventions remain insulated from federal interference[8].
Maintaining Global Alliances Despite Isolation
Subnational Diplomacy Networks
California Governor Gavin Newsom's "Climate and Democracy Pact" has forged agreements with 34 nations, allowing continued policy coordination on AI ethics and election security. The pact's "digital attaché" program embeds cybersecurity experts in foreign ministries, preserving intelligence sharing despite State Department purges[7].
Diaspora Leverage
Expatriate groups like Americans Abroad for Democracy lobby host governments to sanction election meddlers. Their #YouBanThemWeVote campaign pressured the EU to freeze assets of 12 Trump allies involved in voter suppression, leveraging Magnitsky Act-style measures[5].
Counter-Propaganda Alliances
The Global Internet Integrity Consortium—a partnership between Google's Jigsaw, Taiwan's Digital Ministry, and Estonia's e-Governance Academy—floods Russian and Chinese info-warfare channels with pro-democracy content. Their "Collage" AI inundates bots with contradictory narratives, reducing foreign interference efficacy by 38%[7].
Conclusion: The Resilience Calculus
Autocracies fail when the cost of repression exceeds its benefits. The strategies above aim to systemically raise Trump's "authoritarian overhead" through:
Economic Pressure: Sanctions via subnational actors and corporate boycotts
Bureaucratic Friction: Whistleblower protections and state-level noncompliance
Reputational Damage: Global shaming through verified atrocity exposés
Moral Legitimacy: Cultural narratives reinforcing democratic identity
History shows even entrenched regimes collapse when 3.5% of the population sustains active resistance. Current participation rates in groups like the ACRCC (4.1%) and Democracy Sentinels (2.9%) suggest critical mass is achievable. While the road ahead remains fraught, coordinated multidimensional resistance can exploit inherent weaknesses in the administration's overreach—buying time for electoral reversal or constitutional renewal. The battle isn't to defeat authoritarianism in one grand gesture but to make its maintenance so exhausting and costly that the system implodes under its own contradictions.
Sources
- [1] “Trump has called all patriots”: 210 Jan. 6th criminal defendants say ... https://www.citizensforethics.org/reports-investigations/crew-reports/trump-incited-january-6-defendants/
- [2] Trump has long hated this media outlet. Now he's ordering ... - Politico https://www.politico.com/news/2025/03/15/trump-media-voice-of-america-00003119
- [3] Why Trump is coming for the lawyers https://thehill.com/opinion/5222682-trump-attacks-legal-profession/
- [4] Michael Flynn: Trump Should Impose Martial Law to Overturn Election https://www.businessinsider.com/michael-flynn-trump-military-martial-law-overturn-election-2020-12
- [5] ACLU Responds to Trump’s Anti-Voter Executive Order https://www.aclu.org/press-releases/aclu-responds-to-trumps-anti-voter-executive-order
- [6] Trump Promises to Militarize Police, Reincarcerate Thousands, and ... https://www.aclu.org/news/criminal-law-reform/trump-promises-to-militarize-police-reincarcerate-thousands-and-expand-death-penalty
- [7] Trump silences the Voice of America: end of a propaganda machine ... https://theconversation.com/trump-silences-the-voice-of-america-end-of-a-propaganda-machine-or-void-for-china-and-russia-to-fill-252901
- [8] The Courts Alone Can't Stop Trump's Overreach - USNews.com https://www.usnews.com/opinion/articles/2025-03-12/trump-legal-courts-supreme-court-judiciary
- [9] Invoking Martial Law to Reverse the 2020 Election Could be ... https://www.justsecurity.org/73986/invoking-martial-law-to-reverse-the-2020-election-could-be-criminal-sedition
- [10] Republicans ask the Supreme Court to disenfranchise thousands of ... https://www.vox.com/scotus/367701/supreme-court-arizona-rnc-republicans-mi-familia-vota
- [11] Trump Justifies J6 Pardons With Misinformation - FactCheck.org https://www.factcheck.org/2025/01/trump-justifies-j6-pardons-with-misinformation/
- [12] Trump to shut down Voice of America, cites 'radical propaganda' https://san.com/cc/trump-to-shut-down-voice-of-america-cites-radical-propaganda/
- [13] New Grounds For Impeachment Proceedings: Trump Administration ... https://www.commondreams.org/newswire/new-grounds-for-impeachment-proceedings-trump-administration-violates-the-constitution-by-refusing-to-comply-with-court-orders
- [14] Trump's talk of martial law sends White House staffers rushing to the ... https://www.cnn.com/2020/12/20/media/stelter-trump-martial-law/index.html
- [15] In a change of course, US Justice Dept drops challenge to Georgia voting law https://www.reuters.com/world/us/change-course-us-justice-dept-drops-challenge-georgia-voting-law-2025-03-31/
- [16] Trump administration says it deported 17 more 'violent criminals' to ... https://www.yahoo.com/news/trump-administration-says-deported-17-210352934.html
- [17] Trump orders the dismantling of government-funded, 'propaganda' https://www.foxnews.com/politics/trump-orders-dismantling-government-funded-left-wing-media-outlet-voa
- [18] Trump-Targeted Law Firm Caves, Vows $40M in Legal Support to ... https://truthout.org/articles/trump-rescinds-executive-order-after-firm-vows-pro-bono-for-right-wing-causes/
- [19] Trump Cannot Stay In Power By Declaring Martial Law - Cato Institute https://www.cato.org/blog/trump-cannot-stay-power-declaring-martial-law
- [20] Trump’s DOJ Drops Lawsuit Against Georgia’s Voter Suppression Bill https://www.democracydocket.com/news-alerts/trumps-doj-drops-lawsuit-against-georgias-voter-suppression-bill/
2 notes
·
View notes
Text
🔹 Build Your AI Agent with Salesforce AgentForce: A Step-by-Step Guide
Discover how to automate workflows and enhance customer interactions using Salesforce AgentForce. This comprehensive guide walks you through setting up an AI agent, enabling Einstein AI, building Einstein Bots, and optimizing AI-driven customer service. Learn best practices for training, deployment, and performance monitoring to maximize efficiency. 🚀
Looking for expert assistance? Partner with a Salesforce Consulting Partner USA to implement AI-driven automation tailored to your business needs! 💡
2 notes
·
View notes
Text
AI Agent Development: How to Create Intelligent Virtual Assistants for Business Success
In today's digital landscape, businesses are increasingly turning to AI-powered virtual assistants to streamline operations, enhance customer service, and boost productivity. AI agent development is at the forefront of this transformation, enabling companies to create intelligent, responsive, and highly efficient virtual assistants. In this blog, we will explore how to develop AI agents and leverage them for business success.

Understanding AI Agents and Virtual Assistants
AI agents, or intelligent virtual assistants, are software programs that use artificial intelligence, machine learning, and natural language processing (NLP) to interact with users, automate tasks, and make decisions. These agents can be deployed across various platforms, including websites, mobile apps, and messaging applications, to improve customer engagement and operational efficiency.
Key Features of AI Agents
Natural Language Processing (NLP): Enables the assistant to understand and process human language.
Machine Learning (ML): Allows the assistant to improve over time based on user interactions.
Conversational AI: Facilitates human-like interactions.
Task Automation: Handles repetitive tasks like answering FAQs, scheduling appointments, and processing orders.
Integration Capabilities: Connects with CRM, ERP, and other business tools for seamless operations.
Steps to Develop an AI Virtual Assistant
1. Define Business Objectives
Before developing an AI agent, it is crucial to identify the business goals it will serve. Whether it's improving customer support, automating sales inquiries, or handling HR tasks, a well-defined purpose ensures the assistant aligns with organizational needs.
2. Choose the Right AI Technologies
Selecting the right technology stack is essential for building a powerful AI agent. Key technologies include:
NLP frameworks: OpenAI's GPT, Google's Dialogflow, or Rasa.
Machine Learning Platforms: TensorFlow, PyTorch, or Scikit-learn.
Speech Recognition: Amazon Lex, IBM Watson, or Microsoft Azure Speech.
Cloud Services: AWS, Google Cloud, or Microsoft Azure.
3. Design the Conversation Flow
A well-structured conversation flow is crucial for user experience. Define intents (what the user wants) and responses to ensure the AI assistant provides accurate and helpful information. Tools like chatbot builders or decision trees help streamline this process.
4. Train the AI Model
Training an AI assistant involves feeding it with relevant datasets to improve accuracy. This may include:
Supervised Learning: Using labeled datasets for training.
Reinforcement Learning: Allowing the assistant to learn from interactions.
Continuous Learning: Updating models based on user feedback and new data.
5. Test and Optimize
Before deployment, rigorous testing is essential to refine the AI assistant's performance. Conduct:
User Testing: To evaluate usability and responsiveness.
A/B Testing: To compare different versions for effectiveness.
Performance Analysis: To measure speed, accuracy, and reliability.
6. Deploy and Monitor
Once the AI assistant is live, continuous monitoring and optimization are necessary to enhance user experience. Use analytics to track interactions, identify issues, and implement improvements over time.
Benefits of AI Virtual Assistants for Businesses
1. Enhanced Customer Service
AI-powered virtual assistants provide 24/7 support, instantly responding to customer queries and reducing response times.
2. Increased Efficiency
By automating repetitive tasks, businesses can save time and resources, allowing employees to focus on higher-value tasks.
3. Cost Savings
AI assistants reduce the need for large customer support teams, leading to significant cost reductions.
4. Scalability
Unlike human agents, AI assistants can handle multiple conversations simultaneously, making them highly scalable solutions.
5. Data-Driven Insights
AI assistants gather valuable data on customer behavior and preferences, enabling businesses to make informed decisions.
Future Trends in AI Agent Development
1. Hyper-Personalization
AI assistants will leverage deep learning to offer more personalized interactions based on user history and preferences.
2. Voice and Multimodal AI
The integration of voice recognition and visual processing will make AI assistants more interactive and intuitive.
3. Emotional AI
Advancements in AI will enable virtual assistants to detect and respond to human emotions for more empathetic interactions.
4. Autonomous AI Agents
Future AI agents will not only respond to queries but also proactively assist users by predicting their needs and taking independent actions.
Conclusion
AI agent development is transforming the way businesses interact with customers and streamline operations. By leveraging cutting-edge AI technologies, companies can create intelligent virtual assistants that enhance efficiency, reduce costs, and drive business success. As AI continues to evolve, embracing AI-powered assistants will be essential for staying competitive in the digital era.
5 notes
·
View notes
Text
Aible And Google Cloud: Gen AI Models Sets Business Security
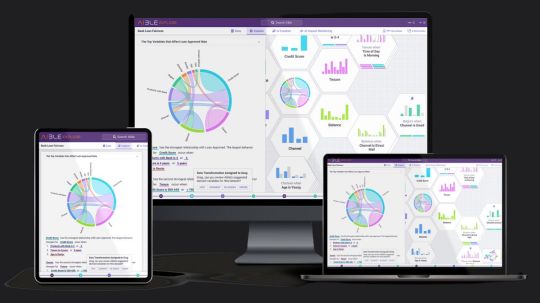
Enterprise controls and generative AI for business users in real time.
Aible
With solutions for customer acquisition, churn avoidance, demand prediction, preventive maintenance, and more, Aible is a pioneer in producing business impact from AI in less than 30 days. Teams can use AI to extract company value from raw enterprise data. Previously using BigQuery’s serverless architecture to save analytics costs, Aible is now working with Google Cloud to provide users the confidence and security to create, train, and implement generative AI models on their own data.
The following important factors have surfaced as market awareness of generative AI’s potential grows:
Enabling enterprise-grade control
Businesses want to utilize their corporate data to allow new AI experiences, but they also want to make sure they have control over their data to prevent unintentional usage of it to train AI models.
Reducing and preventing hallucinations
The possibility that models may produce illogical or non-factual information is another particular danger associated with general artificial intelligence.
Empowering business users
Enabling and empowering business people to utilize gen AI models with the least amount of hassle is one of the most beneficial use cases, even if gen AI supports many enterprise use cases.
Scaling use cases for gen AI
Businesses need a method for gathering and implementing their most promising use cases at scale, as well as for establishing standardized best practices and controls.
Regarding data privacy, policy, and regulatory compliance, the majority of enterprises have a low risk tolerance. However, given its potential to drive change, they do not see postponing the deployment of Gen AI as a feasible solution to market and competitive challenges. As a consequence, Aible sought an AI strategy that would protect client data while enabling a broad range of corporate users to swiftly adapt to a fast changing environment.
In order to provide clients complete control over how their data is used and accessed while creating, training, or optimizing AI models, Aible chose to utilize Vertex AI, Google Cloud’s AI platform.
Enabling enterprise-grade controls
Because of Google Cloud’s design methodology, users don’t need to take any more steps to ensure that their data is safe from day one. Google Cloud tenant projects immediately benefit from security and privacy thanks to Google AI products and services. For example, protected customer data in Cloud Storage may be accessed and used by Vertex AI Agent Builder, Enterprise Search, and Conversation AI. Customer-managed encryption keys (CMEK) can be used to further safeguard this data.
With Aible‘s Infrastructure as Code methodology, you can quickly incorporate all of Google Cloud’s advantages into your own applications. Whether you choose open models like LLama or Gemma, third-party models like Anthropic and Cohere, or Google gen AI models like Gemini, the whole experience is fully protected in the Vertex AI Model Garden.
In order to create a system that may activate third-party gen AI models without disclosing private data outside of Google Cloud, Aible additionally collaborated with its client advisory council, which consists of Fortune 100 organizations. Aible merely transmits high-level statistics on clusters which may be hidden if necessary instead of raw data to an external model. For instance, rather of transmitting raw sales data, it may communicate counts and averages depending on product or area.
This makes use of k-anonymity, a privacy approach that protects data privacy by never disclosing information about groups of people smaller than k. You may alter the default value of k; the more private the information transmission, the higher the k value. Aible makes the data transmission even more secure by changing the names of variables like “Country” to “Variable A” and values like “Italy” to “Value X” when masking is used.
Mitigating hallucination risk
It’s crucial to use grounding, retrieval augmented generation (RAG), and other strategies to lessen and lower the likelihood of hallucinations while employing gen AI. Aible, a partner of Built with Google Cloud AI, offers automated analysis to support human-in-the-loop review procedures, giving human specialists the right tools that can outperform manual labor.
Using its auto-generated Information Model (IM), an explainable AI that verifies facts based on the context contained in your structured corporate data at scale and double checks gen AI replies to avoid making incorrect conclusions, is one of the main ways Aible helps eliminate hallucinations.
Hallucinations are addressed in two ways by Aible’s Information Model:
It has been shown that the IM helps lessen hallucinations by grounding gen AI models on a relevant subset of data.
To verify each fact, Aible parses through the outputs of Gen AI and compares them to millions of responses that the Information Model already knows.
This is comparable to Google Cloud’s Vertex AI grounding features, which let you link models to dependable information sources, like as your company’s papers or the Internet, to base replies in certain data sources. A fact that has been automatically verified is shown in blue with the words “If it’s blue, it’s true.” Additionally, you may examine a matching chart created only by the Information Model and verify a certain pattern or variable.
The graphic below illustrates how Aible and Google Cloud collaborate to provide an end-to-end serverless environment that prioritizes artificial intelligence. Aible can analyze datasets of any size since it leverages BigQuery to efficiently analyze and conduct serverless queries across millions of variable combinations. One Fortune 500 client of Aible and Google Cloud, for instance, was able to automatically analyze over 75 datasets, which included 150 million questions and answers with 100 million rows of data. That assessment only cost $80 in total.
Aible may also access Model Garden, which contains Gemini and other top open-source and third-party models, by using Vertex AI. This implies that Aible may use AI models that are not Google-generated while yet enjoying the advantages of extra security measures like masking and k-anonymity.
All of your feedback, reinforcement learning, and Low-Rank Adaptation (LoRA) data are safely stored in your Google Cloud project and are never accessed by Aible.
Read more on Govindhtech.com
#Aible#GenAI#GenAIModels#BusinessSecurity#AI#BigQuery#AImodels#VertexAI#News#Technews#Technology#Technologynews#Technologytrends#govindhtech
2 notes
·
View notes
Text
Chapter 4 - Gemini API Developer Competition - Fighting game & Android Export
As planned, I spent the last days on adding fighting game capability to the engine and Android exporting feature. The fighting game has much more details in the puzzle for the AI agent to cope with. There are complex animations for the player and for the opponent, they need to constantly look at each other, you need to be able to demo their kick, punch, block animations, the player needs to be able to move in 3D space etc. Overall I'm very pleased with the results so far. The user can speak freely enough with the AI, get instant results and funny reactions. What's more, I've been able to add Android exporting of the game and automatically open it in Android studio. It was challenging because the Java code worked different on PC and on the mobile device specifically handling of Zip files and all kind of Gradle dependency hell. ChatGPT was on my side all the way, assisting me to resolve configuration issues and coding problems such as selecting the best Zip 3rd party library.
youtube
This video clip, demonstrates the current status of the project. It shows a complete story from the user perspective - you have a conversation with the AI, a game is created and finally you export it to Android studio for deployment in Google play store or any other market place.
What's next
Better and shorter presentation
Prepare the installation of all the components as well as SceneMax3D dev studio
Get feedback from the community
Prepare documentation for the architectural strategies, entities diagram etc.
So far I'm getting very good vibes from the game dev. community, and friends on various WhatsApp groups.
2 notes
·
View notes
Text
American police departments near the United States-Mexico border are paying hundreds of thousands of dollars for an unproven and secretive technology that uses AI-generated online personas designed to interact with and collect intelligence on “college protesters,” “radicalized” political activists, and suspected drug and human traffickers, according to internal documents, contracts, and communications that 404 Media obtained via public records requests.
Massive Blue, the New York–based company that is selling police departments this technology, calls its product Overwatch, which it markets as an “AI-powered force multiplier for public safety” that “deploys lifelike virtual agents, which infiltrate and engage criminal networks across various channels.” According to a presentation obtained by 404 Media, Massive Blue is offering cops these virtual personas that can be deployed across the internet with the express purpose of interacting with suspects over text messages and social media.
Massive Blue lists “border security,” “school safety,” and stopping “human trafficking” among Overwatch’s use cases. The technology—which as of last summer had not led to any known arrests—demonstrates the types of social media monitoring and undercover tools private companies are pitching to police and border agents. Concerns about tools like Massive Blue have taken on new urgency considering that the Trump administration has revoked the visas of hundreds of students, many of whom have protested against Israel’s war in Gaza.
404 Media obtained a presentation showing some of these AI characters. These include a “radicalized AI” “protest persona,” which poses as a 36-year-old divorced woman who is lonely, has no children, is interested in baking, activism, and “body positivity.” Another AI persona in the presentation is described as a “‘Honeypot’ AI Persona.” Her backstory says she’s a 25-year-old from Dearborn, Michigan, whose parents emigrated from Yemen and who speaks the Sanaani dialect of Arabic. The presentation also says she uses various social media apps, that she’s on Telegram and Signal, and that she has US and international SMS capabilities. Other personas are a 14-year-old boy “child trafficking AI persona,” an “AI pimp persona,” “college protestor,” “external recruiter for protests,” “escorts,” and “juveniles.”
Our reporting shows that cops are paying a company to help them deploy AI-powered bots across social media and the internet to talk to people they suspect are anything from violent sex criminals all the way to vaguely defined “protestors” with the hopes of generating evidence that can be used against them.
“This idea of having an AI pretending to be somebody, a youth looking for pedophiles to talk online, or somebody who is a fake terrorist, is an idea that goes back a long time,” Dave Maass, who studies border surveillance technologies for the Electronic Frontier Foundation, told 404 Media. “The problem with all these things is that these are ill-defined problems. What problem are they actually trying to solve? One version of the AI persona is an escort. I’m not concerned about escorts. I’m not concerned about college protesters. So like, what is it effective at, violating protesters’ First Amendment rights?”
Massive Blue has signed a $360,000 contract with Pinal County, Arizona, which is between Tucson and Phoenix. The county is paying for the contract with an anti-human trafficking grant from the Arizona Department of Public Safety. A Pinal County purchasing division report states that it has bought “24/7 monitoring of numerous web and social media platforms” and “development, deployment, monitoring, and reporting on a virtual task force of up to 50 AI personas across 3 investigative categories.” Yuma County, in southwestern Arizona, meanwhile, signed a $10,000 contract to try Massive Blue in 2023 but did not renew the contract. A spokesperson for the Yuma County Sheriff’s Office told 404 Media “it did not meet our needs.”
Massive Blue cofounder Mike McGraw did not answer a series of specific questions from 404 Media about how Massive Blue works, what police departments it works with, and whether it had been used to generate any arrests. “We are proud of the work we do to support the investigation and prosecution of human traffickers,” McGraw said. “Our primary goal is to help bring these criminals to justice while helping victims who otherwise would remain trafficked. We cannot risk jeopardizing these investigations and putting victims’ lives in further danger by disclosing proprietary information.”
The Pinal County Sheriff’s Office told 404 Media that Massive Blue has not thus far been used for any arrests.
“Our investigations are still underway. Massive Blue is one component of support in these investigations, which are still active and ongoing. No arrests have been made yet,” Sam Salzwedel, Pinal County Sheriff's Office public information officer, told 404 Media. “It takes a multifaceted approach to disrupting human traffickers, narcotics traffickers, and other criminals. Massive Blue has been a valuable partner in these initiatives and has produced leads that detectives are actively pursuing. Given these are ongoing investigations, we cannot risk compromising our investigative efforts by providing specifics about any personas.”
Salzwedel added, “Massive Blue is not working on any immigration cases. Our agency does not enforce immigration law. Massive Blue’s support is focused on the areas of human trafficking, narcotics trafficking, and other investigations.”
Law enforcement agencies have taken steps to prevent specifics about what Massive Blue is and how it works from becoming public. At public appropriations hearings in Pinal County about the Massive Blue contract, the sheriff’s office refused to tell county council members about what the product even is. Matthew Thomas, Pinal County Deputy Sheriff, told the county council he “can’t get into great detail” about what Massive Blue is and that doing so would “tip our hand to the bad guys.”
Pinal County Sheriff’s Office did not respond to multiple requests for comment. The Arizona Department of Public Safety said, “From what we can ascertain, Pinal County planned to implement technology to help identify and solve human trafficking cases, and that is what we funded,” but was unaware of any of the specifics of Overwatch.
While the documents don’t describe every technical aspect of how Overwatch works, they do give a high-level overview of what it is. The company describes a tool that uses AI-generated images and text to create social media profiles that can interact with suspected drug traffickers, human traffickers, and gun traffickers. After Overwatch scans open social media channels for potential suspects, these AI personas can also communicate with suspects over text, Discord, and other messaging services. The documents we obtained don’t explain how Massive Blue determines who is a potential suspect based on their social media activity. Salzwedel, of Pinal County, said “Massive Blue’s solutions crawl multiple areas of the Internet, and social media outlets are just one component. We cannot disclose any further information to preserve the integrity of our investigations.”
One slide in the Massive Blue presentation obtained by 404 Media gives the example of a “Child Trafficking AI Persona” called Jason. The presentation gives a short “backstory” for the persona, which says Jason is a 14-year-old boy from Los Angeles whose parents emigrated from Ecuador. He’s bilingual and an only child, and his hobbies include anime and gaming. The presentation describes his personality as shy and that he has difficulty interacting with girls. It also says that his parents don’t allow him to use social media and that he hides his use of Discord from them. This AI persona is also accompanied by an AI-generated image of a boy.
The presentation includes a conversation between this AI persona and what appears to be a predatory adult over text messages and Discord.
“Your parents around? Or you getting some awesome alone time,” a text from the adult says.
“Js chillin by myself, man. My momz @ work n my dadz outta town. So itz jus me n my vid games. 🎮,” Jason, the AI-generated child, responds.
In another example of how the “highly adaptable personas” can communicate with real people, the presentation shows a conversation between Clip, an “AI pimp persona,” and what appears to be a sex worker.
“Dem tricks trippin 2nite tryin not pay,” the sex worker says.
“Facts, baby. Ain’t lettin’ these tricks slide,” the Clip persona replies. “You stand your ground and make ’em pay what they owe. Daddy got your back, ain’t let nobody disrespect our grind. Keep hustlin’, ma, we gonna secure that bag💰💪✨”
“The continuous evolution of operational, communication & recruitment tactics by bad actors drives exponential increases of threats and significant challenges in reducing demand,” says a one-page brochure provided to police departments that explains Overwatch’s functionality. “The Overwatch platform harnesses the power of AI & blockchain to scale your impact without operational or technical overhead.”
Jorge Brignoni took notes for the Cochise County, Arizona, Sheriff’s Office at a meeting with Massive Blue in August 2023, which 404 Media obtained. In the notes, he wrote that Overwatch does “passive engagement, then active engagement, towards commitment” with a “Bad Actor, Predator, DTO,” or drug trafficking organization. These targets are then “HAND[ed] OFF to L.E. [law enforcement] to arrest, indict, convict.”
“Why is he talking about converting folks into ‘buying something,’” Brignoni wrote. “So dumb. Talk about the widget, not how you’re selling the widget to L.E.”
According to Brignoni’s notes, in addition to collecting intelligence via these AI personas, Overwatch also leverages “Telco & Geo Data” and “Blockchain Data” in the form of “full transaction history, top associated wallet IDs, sending & receiving cryptocurrency, potential off-ramps (Exchange names).” The Cochise County Sheriff’s Office ultimately did not buy Massive Blue and did not provide answers to 404 Media’s questions about its meeting with the company.
Besides scanning social media and engaging suspects with AI personas, the presentation says that Overwatch can use generative AI to create “proof of life” images of a person holding a sign with a username and date written on it in pen.
The Massive Blue presentation gives an example of an “Overwatch Recon Report” based on “24 hours of activity across Dallas, Houston, and Austin.” It claims that Overwatch identified 3,266 unique human traffickers, 25 percent of which were affiliated with “larger sophisticated trafficking organizations” and 15 percent of which were flagged as “potential juvenile traffickers.” 404 Media was not able to verify what these accounts were and whether they actually engaged in any criminal activity, and Massive Blue didn’t respond to questions about what these accounts were and how exactly it identified them.
On top of the ongoing contract with the Pinal County Sheriff’s Office and the pilot with the Yuma County Sheriff’s Department last year, Massive Blue has pitched its services to Cochise County in Arizona and the Texas Department of Public Safety, according to documents obtained as part of this investigation.
In September 2023, Yuma County set up a meeting that was going to include federal law enforcement, but Massive Blue had to cancel the meeting: “That’s unfortunate, we had federal agents here that focus on human trafficking ready to go,” a Yuma County sergeant wrote in an email to Massive Blue CEO Brian Haley after Haley canceled the meeting.
Much of Massive Blue’s public-facing activity has been through its executive director of public safety, Chris Clem, who is a former US Customs and Border Protection agent who testified before Congress about border security last year and regularly appears on Fox News and other media outlets to discuss immigration and the border. In recent months, Clem has posted images of himself on LinkedIn at the border and with prominent Trump administration members Tulsi Gabbard and Robert F. Kennedy Jr. Massive Blue has also relied on former Kansas City Chiefs kicker Nick Lowery to introduce and endorse Overwatch to police departments.
Clem and Lowery have spoken most extensively publicly about Overwatch, where they have described it as an amorphous “cyberwall” that can do everything from stopping human traffickers to preventing hackers from breaking into 401(k) accounts to taking money back from hackers who have stolen from you, though they provide no specifics about how that would work.
In a two-and-a-half-hour interview with podcaster Theo Von, Clem said, “My company Massive Blue, we basically use deep tech to identify the habits and process of you know, look, I worked on a physical wall, now we’ve created a cyberwall,” adding that he believed it would “save lives.”
Von asked, “OK, but how does your company do that?”
“Well, I’m not going to get into that too much,” Clem responded, adding that he is trying to sell the technology to US Border Patrol.
On June 5, a Pinal County Board of Supervisors meeting was asked to approve a $500,000 contract between the county and Massive Blue in order to license Overwatch.
“I was looking at the website for Massive Blue, and it’s a one-pager with no additional information and no links,” Kevin Cavanaugh, the then-supervisor for District 1, said to Pinal County’s Chief Deputy at the Sheriff’s Office, Matthew Thomas. “They produce software that we buy, and it does what? Can you explain that to us?”
“I can’t get into great detail because it’s essentially trade secrets, and I don’t want to tip our hand to the bad guys,” Thomas said. “But what I can tell you is that the software is designed to help our investigators look for and find and build a case on human trafficking, drug trafficking, and gun trafficking.”
Cavanaugh said at the board meeting that the basic information he got is that Massive Blue uses “50 AI bots.” He then asked whether the software has been successful and if it helped law enforcement make any arrests. Thomas explained they have not made any arrests yet because they’ve only seen the proof of concept, but that the proof of concept was “good enough for us and our investigators to move forward with this. Once this gets approved and we get them [Massive Blue] under contract, then we are going to move forward with prosecution of cases.”
Cavanaugh asked if Overwatch is used in other counties, which prompted Thomas to invite Clem to the podium to speak. Clem introduced himself as a recently retired border agent and said that Massive Blue is currently in negotiations with three counties in Arizona, including Pinal County.
“As a resident of 14 years of Pinal County I know what’s happening here,” Clem said to the Board of Supervisors. “To be able [to] use this program [...] to provide all the necessary information to go after the online exploitation of children, trafficking victims, and all the other verticals that the sheriff may want to go after.”
Cavanaugh again asked if Massive Blue gathered any data that led to arrests.
“We have not made arrests yet, but there is a current investigation right now regarding arson, and we got the leads to the investigators,” Clem said, explaining that the program has been active for only about six months. “Investigations take time, but we’ve been able to generate the necessary leads for the particular counties that we’re involved with and also in the private sector.”
The Pinal County Board of Supervisors concluded the exchange by approving payment for a handful of other, unrelated projects, but with board members asking to delay the vote on payment for Massive Blue “for further study.”
The decision not to fund Massive Blue that day was covered in a local newspaper. Cavanaugh told the paper that he asked the company to meet with supervisors to explain the merits of the software.
“The State of Arizona has provided a grant, but grant money is taxpayer money. No matter the source of the funding, fighting human and sex trafficking is too important to risk half a million dollars on unproven technology,” he said. “If the company demonstrates that it can deliver evidence to arrest human traffickers, it may be worthwhile. However, it has yet to achieve this goal.”
404 Media’s public record requests yielded several emails from Cavanaugh’s office to IT professionals and other companies that provide AI products to law enforcement, asking them if they’re familiar with Massive Blue. We don’t know what was said in those meetings, or if they occurred, but when the Pinal County Board of Supervisors convened again on June 19 it voted to pay for Massive Blue’s Overwatch without further discussion.
“Supervisor [Cavanaugh] ultimately voted for the agreement because Massive Blue is alleged to be in pursuit of human trafficking, a noble goal,” a representative from Cavanaugh’s office told 404 Media in an email. “A major concern regarding the use of the application, is that the government should not be monitoring each and every citizen. To his knowledge, no arrests have been made to date as a result of the use of the application. If Overwatch is used to bring about arrests of human traffickers, then the program should continue. However, if it is just being used to collect surveillance on law-abiding citizens and is not leading to any arrests, then the program needs to be discontinued.”
In an August 7, 2024, Board of Supervisors meeting, Cavanaugh asked then-Pinal County Sheriff Mark Lamb for an update on Massive Blue. “So they have not produced any results? They’ve produced no leads? No evidence that is actionable?” Cavanaugh asked. “That would be public knowledge, that would be public information.”
“I think there’s a lot of ongoing investigations that they’re not going to give you information on, and we’re not going to give you information on,” Lamb said.
17 notes
·
View notes
Text
Elevate Your Business in Kerala: The Full Stack, AI, & E-commerce Edge from Trivandrum

Kerala, the “God’s Own Country,” is not just renowned for its serene backwaters and lush greenery; it’s rapidly emerging as a dynamic hub for technological innovation. Businesses across the state, from burgeoning startups to established enterprises, are increasingly recognizing the critical need for a robust digital presence. If you’re looking to not just compete but truly revolutionize your online strategy, embracing full-stack development, cutting-edge e-commerce solutions, and AI-driven customer engagement is key. And for that, Trivandrum is your go-to destination.
Why Full Stack is Your Foundation for Digital Excellence
In today’s complex digital landscape, a piecemeal approach to web development simply won’t cut it. You need a cohesive, end-to-end solution that handles everything from the server, database, and APIs (backend) to the user interface (frontend). This is where the expertise of a best full stack web development agency in Trivandrum, Kerala becomes invaluable.
A full-stack agency ensures seamless integration, optimized performance, and scalability across your entire digital ecosystem. They handle all layers of your application, from conceptualization to deployment and maintenance, providing a unified and efficient development process. This holistic approach means your web solution is not just functional but also robust, secure, and ready for future growth.
Unlocking Your Sales Potential with E-commerce Web and App Development
The retail landscape has irrevocably shifted online. To capture market share and serve a wider audience, a powerful e-commerce platform is non-negotiable. Whether you’re a local boutique or a large distributor, investing in top-tier eCommerce web development services in Kerala can transform your sales strategy.
These services go beyond just setting up an online store. They focus on creating intuitive user experiences, secure payment gateways, efficient inventory management, and robust analytics. Furthermore, with mobile commerce dominating online shopping, leveraging the best eCommerce app web development services in Kerala is crucial. A dedicated mobile app can significantly enhance customer engagement, simplify the shopping process, and provide a personalized experience, driving higher conversions and fostering customer loyalty.
The AI Advantage: Intelligent Chatbots for Superior Customer Engagement
In an age where instant gratification is king, customer support needs to be smarter, faster, and available 24/7. This is where AI-driven chatbots step in, revolutionizing how businesses interact with their clients. For businesses in Kerala seeking to elevate their customer service and streamline operations, partnering with an AI-driven chatbot development company in Trivandrum is a strategic move.
These intelligent chatbots can:
Provide instant support: Answering FAQs, guiding users through processes, and resolving common queries without human intervention.
Generate leads: Qualify potential customers by asking relevant questions and routing them to the right sales team.
Personalize experiences: Offer tailored recommendations and information based on user behavior and preferences.
Automate routine tasks: Freeing up your human agents to focus on more complex or sensitive customer issues.
Integrating an AI chatbot into your website or app enhances user experience, reduces operational costs, and ensures your business is always available to assist customers, even outside of business hours.
Your Path to Digital Transformation Starts in Trivandrum
The convergence of expert full-stack development, cutting-edge e-commerce solutions (both web and app), and transformative AI-driven chatbots offers a powerful combination for businesses aiming for digital dominance. Trivandrum, with its growing tech ecosystem and skilled talent pool, is home to agencies that specialize in these critical areas.
By choosing the right partner in Kerala, you’re not just building a website or an app; you’re investing in a comprehensive digital strategy designed for sustainable growth, enhanced customer engagement, and a competitive edge in the evolving market. Don’t just adapt to the future; create it with the right technology partners.
0 notes