#anonymous proxy service
Explore tagged Tumblr posts
Note
Hi! Sorry to ask but I saw the anon’s ask and your response about the keychains, and it got me wondering that will anyone (including myself) who lives outside of America would get a chance of getting them too? I noticed that the shipment only remains in United Sates not anywhere else as it says the “shipping is not available to your country” :’)
But if not or you can’t, then that’s okay!! ^^
(Also, I really love your art!! It makes me feel happy every time I see them :3 and I wanted to say thank you so much for posting about Metal Cardbot!! If it wasn’t for you, I would never have the chance to watch them, so thank you!! And of course to people who worked really hard to do English sub, they are incredible :0)
Quick note: Please take your time and stay hydrated (^ •w•^)> ♡
Thank you so much! I actually decided to add worldwide shipping back to my ko-fi shop! However, it is expensive at $18 USD. Nothing I can do about the price, and it may even increase as this is only an estimate based on the last time I shipped overseas.
If you have any acrylic charm making companies in your country, I am distributing the image files for free download to people overseas if that is cheaper to have them made yourself! Send me a DM if you’re interested.
And thank you again, I’m happy to spread the MCB love to others, and I’m happy you like my silly doodles! I’m also happy to help out with the subs, even though anyone else could do the little edits I do 😅.. Cabalex and starosphere do all the real work. But thank you nonetheless!
#This ask deleted itself the first time i tried sending it 😭.. lets hope it works this time#Asks#anonymous#Proxy services may also be an option- but you would have to research those for your country.
5 notes
·
View notes
Text
Fast Secure Proxy Browser: Browse Anonymously Without Limits

Have you ever tried to access a website, only to be met with a frustrating “This content is not available in your region” message? Or perhaps you've felt uneasy knowing your online activity might be tracked or exposed on public Wi-Fi. In today’s digital landscape, where privacy breaches and content restrictions are increasingly common, it’s no surprise that more users are turning to solutions that offer both security and speed.
That’s where a fast secure proxy browser comes in. It's more than just a digital detour — it’s your shield against surveillance, a bridge to open access, and a tool that puts you back in control of your browsing experience. But what exactly makes a proxy browser both fast and secure? And how can it help you browse anonymously without limits?
In this post, we’ll break down how a fast secure proxy browser works, explore why it matters, and guide you through choosing one that fits your needs. Whether you’re looking to protect your data, bypass geo-blocks, or simply surf without compromise, you’re in the right place. Let’s dive into the tools and tactics that make anonymous browsing not just possible—but effortless.
Understanding Proxy Browsers
Proxy browsers serve as intermediaries between your device and the internet. When you access a website through a proxy browser, your request is rerouted through a remote server. This server masks your IP address, effectively hiding your identity from websites, advertisers, and even government surveillance.
A proxy browser differs from a Virtual Private Network (VPN) in a few key ways. While both hide your IP and offer privacy, VPNs typically encrypt all internet traffic on your device, while proxy browsers work at the application level—usually within the browser itself. This makes proxy browsers lighter and often faster for everyday use.
Why does speed matter? Because privacy tools shouldn't slow you down. A fast proxy browser ensures you're not waiting forever for a webpage to load, all while keeping your identity secure. It also allows seamless streaming, gaming, and general browsing without buffering or lag.
With a secure proxy browser, you no longer need to worry about malicious entities tracking your every move. Your location stays hidden, your data remains encrypted, and your browsing history is safe from third parties.
Key Benefits of a Fast Secure Proxy Browser
Maintain Online Privacy and Hide Your IP
One of the biggest advantages of a fast secure proxy browser is the ability to mask your real IP address. By doing so, your digital footprint is hidden, and your activities can't easily be traced back to you.
Bypass Geo-Restrictions and Censorship
Tired of running into blocked websites? Proxy browsers help you bypass content restrictions imposed by governments, schools, or workplaces. Whether you're accessing streaming services, social media, or news outlets, you can do so freely.
Enjoy Fast Speeds Without Compromising Security
Many users avoid privacy tools due to slow speeds. Fast secure proxy browsers, however, use optimized routing and load-balancing techniques to ensure swift connections, even under heavy traffic.
Protect Data on Public Wi-Fi Networks
Public Wi-Fi is notorious for being a security risk. With a secure proxy browser, you can encrypt your traffic and ensure your data isn’t intercepted by hackers, snoopers, or malicious hotspots.
Essential Features to Look for in a Proxy Browser
End-to-End Encryption Capabilities
Ensure that the proxy browser you choose offers end-to-end encryption. This prevents any third party, including your ISP, from reading your data.
Zero-Log and No Tracking Policies
A true privacy-focused proxy browser won’t log your activity. Check for providers that openly commit to zero-log policies.
Multiple Server Locations for Flexibility
The more server locations available, the easier it is to access global content. It also allows you to switch locations if one is underperforming.
One-Click Access and User-Friendly Interface
Ease of use matters. Look for browsers that require no technical expertise and offer clean, intuitive dashboards for users of all levels.
Use Cases: Who Needs a Fast Secure Proxy Browser?
Journalists and Researchers in Restricted Regions
For those working in countries with limited internet freedom, proxy browsers offer a vital tool for uncensored information gathering.
Everyday Users Who Value Privacy
Even if you're not a whistleblower or journalist, your data matters. Proxy browsers help safeguard everyday browsing activities.
Students Accessing Blocked Educational Resources
Educational institutions sometimes block certain sites. Proxy browsers can help students bypass these restrictions to access learning materials.
Travelers Looking to Avoid Regional Content Blocks
Traveling abroad and can’t access your favorite streaming service? A proxy browser can make it seem like you're back home, unblocking content seamlessly.
How to Get Started with a Secure Proxy Browser
Choosing the Right Tool for Your Needs
Not all proxy browsers are created equal. Look for one that balances speed, privacy, and usability based on your unique needs.
Step-by-Step Setup and Configuration
Download the proxy browser from the official website.
Install and launch the application.
Select a server or location you want to browse from.
Enable encryption settings if available.
Start browsing anonymously.
Tips for Maximizing Speed and Performance
Choose servers closer to your actual location.
Avoid peak usage times when servers may be overloaded.
Clear your browser cache regularly.
Common Mistakes to Avoid
Using free proxies with poor security protocols
Forgetting to turn on encryption settings
Overlooking privacy policies and logging practices
Conclusion
In a world where digital privacy is increasingly under threat, a fast secure proxy browser isn't just a luxury—it's a necessity. From hiding your IP address to bypassing global content barriers, it empowers you to browse anonymously, safely, and without limits.
Whether you're a professional navigating sensitive research or a casual user who values their online freedom, the right proxy browser can redefine your web experience. Choose wisely, stay informed, and take control of your digital journey. Your path to a freer, more secure internet starts now.
FAQ’s
1. What makes a proxy browser fast and secure?It combines optimized server infrastructure with encryption protocols and minimal data logging, ensuring high-speed access and strong privacy.
2. Are proxy browsers legal to use?Yes, using a proxy browser is legal in most countries. However, it's important to comply with local laws regarding internet usage.
3. Can a proxy browser replace a VPN?For basic privacy and unblocking content, yes. But for full-device encryption and enhanced security, a VPN may still be preferable.
4. Do proxy browsers work on mobile devices?Many secure proxy browsers are available for Android and iOS, offering similar features as their desktop counterparts.
5. Are free proxy browsers safe? Not always. Many free services log your data or serve ads. It’s better to choose a reputable proxy browser with a transparent privacy policy.
#secure proxy browser#anonymous web browsing#bypass internet restrictions#online privacy tools#fast proxy service
0 notes
Text
Exploring the Role of Residential Proxies in Cross-Border E-Commerce
In today’s digital economy, cross-border e-commerce has become a cornerstone of global business. Whether it’s for market research, competitive analysis, price comparison, or ad verification, companies engaged in cross-border commerce need to leverage various digital tools to maintain a competitive edge. One such tool that is increasingly becoming essential is the use of residential proxies.
Residential proxies, particularly rotating residential proxies and static residential proxies, allow e-commerce businesses to conduct operations that are crucial for success in a global marketplace. This article dives into the importance of residential proxies in cross-border e-commerce, how businesses can effectively use them, and the factors that determine the best residential proxy providers.
What Are Residential Proxies and Why Are They Important? To understand their significance in cross-border e-commerce, let’s first define residential proxies. A residential proxy uses IP addresses assigned to real residential homes by Internet Service Providers (ISPs). Unlike traditional data center proxies, which use IPs from data centers and are easily detected by websites as non-human traffic, residential proxies appear as if the traffic is coming from real people using everyday devices. This makes them more legitimate and harder for websites to block or flag as suspicious.
In the context of e-commerce, residential proxies offer several benefits:
Bypassing Geo-Restrictions: Residential proxies allow businesses to access content and services from different countries without being restricted by local geo-blocks. This is particularly useful for cross-border e-commerce companies that need to view content as it appears to users in different regions.
Ad Verification: Companies running ads in multiple markets need to ensure that their ads appear correctly in all regions. Residential proxies make it easier to verify ad placement and effectiveness across different countries, helping e-commerce businesses optimize their campaigns.
Price Scraping: E-commerce businesses often monitor competitors’ prices and adjust their pricing strategies accordingly. Residential proxies allow them to scrape competitor data without getting blocked, as the IP addresses mimic real users.
Rotating vs. Static Residential Proxies When choosing the best residential proxy service, one of the most important decisions is whether to opt for rotating residential proxies or static residential proxies. Each type offers distinct advantages depending on the task at hand.
A. Rotating Residential Proxies Rotating residential proxies are dynamic and change their IP address after each request or after a specified period. These proxies are perfect for activities that require continuous access to multiple websites without the risk of being blocked, such as:
Web scraping: When gathering data from multiple websites, rotating proxies make it appear as though the requests are coming from different users, reducing the likelihood of detection by websites.
Market research: E-commerce companies can simulate real users from different regions to gather insights about consumer behavior or competitive pricing.
The major benefit of rotating proxies is their ability to prevent websites from blocking a particular IP, as the IPs change frequently, mimicking a real human browsing experience.
B. Static Residential Proxies On the other hand, static residential proxies offer a single, fixed IP address that remains the same for the duration of the session. This type of proxy is ideal for activities that require consistency in the IP address. Some use cases include:
Ad verification: When verifying ads in a particular market, using a static residential proxy ensures that the same IP is used throughout the process, leading to more accurate ad placement results.
Account management: For e-commerce businesses managing multiple accounts or online platforms, static residential proxies offer a stable connection, which reduces the risk of account suspension or bans.
While static residential proxies are often slower than rotating ones, they provide a more reliable solution for businesses that require constant IP addresses.
Choosing the Right Residential Proxy Provider Selecting the right provider for your residential proxy needs can make or break your efforts in cross-border e-commerce. Here are the key factors to consider when evaluating residential proxy services:
A. Global Coverage and Location Variety One of the main reasons for using residential proxies in cross-border e-commerce is to access specific regions or countries. Therefore, the provider you choose should offer a wide range of IP addresses from various global locations. This is especially important for businesses that need proxies from specific countries to conduct geo-targeting, price scraping, or competitive analysis.
Ensure that your provider has a broad selection of residential IPs from major e-commerce markets, including the US, the EU, Asia, and emerging markets. This enables you to test ads, check regional prices, and interact with online marketplaces from different geographical locations.
B. Bandwidth and Speed Speed and bandwidth are essential when dealing with large-scale e-commerce operations. Residential proxies tend to be slower than data center proxies, but that doesn’t mean you should settle for slow connections. Look for providers that offer unlimited bandwidth and prioritize high-speed performance. This is crucial when performing real-time scraping or running large ad campaigns across multiple countries.
C. Security and Anonymity Anonymity and security should always be top priorities when using residential proxies for e-commerce activities. Make sure that your provider offers strong encryption and a secure connection to protect your data. A reliable residential proxy provider should hide your real IP and ensure that your e-commerce activities remain private and safe from prying eyes.
D. Pricing and Plans When evaluating residential proxy services, consider the pricing structure carefully. Residential proxies tend to be more expensive than data center proxies, so it’s important to find a provider that offers cost-effective plans while still meeting your needs. Many providers offer free trials or pay-as-you-go options that allow you to test their services before committing.
Some providers offer cheap residential proxies, but be careful as lower-cost options may not offer the same level of security, speed, or customer support as premium services. Always weigh the cost against the benefits provided to ensure you're getting good value.
E. Customer Support A good customer support team is crucial, especially for businesses that rely heavily on proxies for their operations. Look for providers that offer 24/7 support through multiple channels like live chat, email, and phone. Ensure that the provider has a responsive support system to help you troubleshoot any issues that arise, such as slow speeds, blocked IPs, or connection problems.
Different Types of Residential Proxies for E-Commerce Applications A. Residential SOCKS5 Proxies SOCKS5 residential proxies are a versatile option for e-commerce businesses that require more control over their internet connection. Unlike HTTP proxies, SOCKS5 proxies support a wide variety of protocols and can be used for a broader range of tasks, including web scraping, ad testing, and market research.
SOCKS5 proxies offer greater security by providing a secure tunnel between the client and the server, making it harder for websites to detect and block the traffic.
B. Private and Dedicated Residential Proxies For businesses that need exclusive and uninterrupted access to specific IPs, private residential proxies and dedicated residential proxies are ideal. These types of proxies ensure that the IPs are not shared with other users, offering more privacy and better performance for critical tasks.
Private residential proxies are typically sold to a single user, making them a perfect choice for businesses that need uninterrupted access to specific websites or services.
Dedicated residential proxies offer similar benefits but are usually associated with higher costs. They are excellent for high-priority users who require a guaranteed level of performance.
Conclusion In the competitive world of cross-border e-commerce, having access to reliable and efficient residential proxies can provide significant advantages. Whether you're engaged in geo-targeting, market research, or ad verification, residential proxies can help you access global content, maintain anonymity, and enhance your operations across multiple regions.
By carefully considering factors such as proxy type, global coverage, speed, security, and pricing, businesses can choose the best residential proxy provider to meet their needs. Whether you opt for rotating residential proxies, static residential proxies, or SOCKS5 residential proxies, the right residential proxy service can be a game-changer for your cross-border e-commerce efforts.
#HTTP Proxy#SOCKS5 Proxy#Dedicated Proxy#Rotating Proxies#Residential Proxy#DNS Proxy#Static Proxy#Shared Proxy#ShadowSOCKS Proxy#US PROXY#UK PROXY#IPV4 PROXY#Anonymous Proxy#Seo Proxy#ISP Proxies#Premium Proxy#Cheap Proxy#Private Proxy#Proxy Service#Linkedin Proxies#IP Rotation
0 notes
Text
Using Residential Proxies for Web Scraping: Tips and Considerations
In the digital age, web scraping has become a crucial activity for various industries. From market research to data extraction for machine learning projects, web scraping allows businesses to gather vast amounts of data from the internet. However, one of the biggest challenges that web scrapers face is bypassing geographic restrictions and anti-bot measures. To overcome this, many opt for residential proxies, which are an excellent solution for masking IP addresses and accessing content without detection. In this article, we will explore how residential proxies can be effectively used for web scraping, covering important tips, considerations, and best practices to ensure your scraping efforts are both efficient and ethical.
Understanding Residential Proxies A residential proxy is an IP address assigned by an Internet Service Provider (ISP) to a physical device located in a residential area. Unlike data center proxies, which use IP addresses from servers, residential proxies route traffic through real residential devices, making it appear as if the requests are coming from actual users rather than automated bots. This adds a layer of anonymity and makes it much harder for websites to detect and block the traffic as being from a bot.
When scraping websites using residential proxies, your requests are more likely to be considered legitimate, as they are sent through residential IP addresses, which are not easily flagged by anti-scraping systems. Moreover, rotating residential proxies or static residential proxies can be used to ensure continuous and diverse access to websites without raising suspicion.
The Importance of Residential Proxies in Web Scraping Web scraping often involves sending multiple requests to a target website. If these requests come from the same IP address or a set of data center IPs, the website may flag them as suspicious and block access. Residential proxies are essential for bypassing these restrictions because:
Bypassing Geo-Restrictions: Many websites restrict access based on geographical location. Residential proxies allow you to choose IP addresses from specific regions, enabling access to region-locked content. Avoiding Detection: Since residential proxies use IP addresses assigned to real homes, they are significantly harder to detect than data center proxies. Websites have a much harder time distinguishing between legitimate users and bots. Multiple Requests Without Blocking: With rotating residential proxies, you can make a large number of requests without triggering anti-bot measures. Each request can be routed through a different IP address, ensuring that your web scraping operations remain smooth and uninterrupted.
Types of Residential Proxies for Scraping There are different types of residential proxies available, and each offers unique benefits for web scraping. The most common types are static residential proxies and rotating residential proxies.
A. Static Residential Proxies Static residential proxies provide a fixed IP address that stays the same throughout the session. This type of proxy is ideal for web scraping tasks that require consistency, such as when you need to interact with the same website over time. For example, logging into a social media account or managing a marketplace account would require the same IP address to avoid triggering security systems.
Advantages:
Consistency: They allow for long sessions with the same IP address. Reliable for Account Management: Useful for maintaining stable connections when scraping sites that require login credentials. Disadvantages:
Higher Risk of Detection: If the same static IP is used repeatedly, it may eventually be flagged as suspicious, especially if the website detects unusual traffic patterns. B. Rotating Residential Proxies Rotating residential proxies are an excellent choice for large-scale web scraping projects. With rotating proxies, the IP address changes after each request or after a set period. This ensures that every request sent to a website comes from a different IP, significantly reducing the likelihood of being blocked.
Advantages:
High Anonymity: By rotating IP addresses frequently, it's nearly impossible for websites to track and block your requests. High Volume Scraping: Ideal for scraping large volumes of data from multiple sources, as it distributes traffic across many IP addresses. Disadvantages:
Less Stability: Some tasks that require consistent IP addresses, like login-based scraping, may not be suitable for rotating proxies. C. SOCKS5 Residential Proxies For more advanced web scraping needs, residential SOCKS5 proxies are also available. SOCKS5 proxies provide a high level of flexibility, supporting a wide range of activities beyond standard web scraping, including torrenting and gaming. They are often used for scraping data that involves highly dynamic content or requires specific network protocols.
Advantages:
Enhanced Security: SOCKS5 proxies offer a secure, encrypted connection for data transmission. Flexibility: They can handle various types of traffic, including P2P protocols and more specialized use cases. Disadvantages:
More Complex Setup: SOCKS5 proxies require more technical knowledge to set up and manage.
Considerations When Using Residential Proxies for Scraping While residential proxies are incredibly powerful tools for web scraping, there are several key factors to keep in mind when using them to ensure optimal performance and compliance with legal and ethical standards.
A. Proxy Pool Size The size of your proxy pool is an important factor when selecting a residential proxy service. A larger pool means a wider variety of IP addresses available for use, reducing the risk of hitting rate limits or being blocked. Some proxy providers offer unlimited residential proxies, which is ideal for extensive scraping tasks.
Best Practice: Choose a proxy provider with a large and diverse proxy pool to avoid detection and ensure continuous access to websites. B. Bandwidth and Speed For web scraping, especially when gathering large datasets, speed and bandwidth are crucial. You want a proxy service that provides high-speed connections and sufficient bandwidth to handle multiple requests simultaneously. If the proxies are too slow or have bandwidth limits, your scraping operations will be delayed, and you may miss important data.
Best Practice: Look for a residential proxy service that offers high-speed connections and unlimited bandwidth, particularly if you plan to scrape data continuously. C. Legal and Ethical Concerns It's essential to respect the terms of service of the websites you're scraping. While using residential proxies can help you bypass restrictions, scraping a website without permission may violate its terms of service and potentially lead to legal consequences. Always ensure that your web scraping activities are in compliance with the law.
Best Practice: Use residential proxies responsibly and ensure that your scraping activities are not causing harm to the target website or its users. Avoid scraping personal or confidential information unless you have explicit consent. D. Security and Privacy When selecting a residential proxy provider, consider the level of privacy and security they offer. Some providers offer private residential proxies that are dedicated to a single user, ensuring better security and anonymity. This can be crucial when scraping sensitive data or accessing websites that require secure connections.
Best Practice: Choose a reputable proxy provider that offers secure residential proxies with strong encryption to protect your data and privacy.
Best Practices for Web Scraping with Residential Proxies To maximize the effectiveness of residential proxies for web scraping, consider the following best practices:
Rotate Your Proxies: Use rotating residential proxies for large-scale scraping to avoid detection. This will allow you to scrape multiple pages from different IP addresses without triggering anti-scraping measures. Monitor Your Requests: Regularly monitor your scraping activities to ensure that your proxies are working efficiently and that you're not being blocked. Limit Request Frequency: Avoid making excessive requests in a short period. Slow down the scraping process to mimic human browsing behavior and reduce the chances of being detected. Handle Captchas and Blocks: Many websites use Captchas to prevent bots. Use services or tools that can bypass Captchas, or combine proxies with captcha-solving services to keep your scraping operation smooth.
Conclusion Residential proxies offer an effective solution for overcoming geo-blocks and bypassing anti-bot measures in web scraping. By using rotating residential proxies, static residential proxies, or SOCKS5 residential proxies, you can scrape data from websites with greater anonymity and efficiency. However, it's important to follow best practices, respect website terms of service, and prioritize security and privacy. With the right residential proxy provider, web scraping can be a powerful tool for data collection, market analysis, and more.
#HTTP Proxy#SOCKS5 Proxy#Dedicated Proxy#Rotating Proxies#Residential Proxy#DNS Proxy#Static Proxy#Shared Proxy#ShadowSOCKS Proxy#US PROXY#UK PROXY#IPV4 PROXY#Anonymous Proxy#Seo Proxy#ISP Proxies#Premium Proxy#Cheap Proxy#Private Proxy#Proxy Service#Linkedin Proxies#IP Rotation
0 notes
Text
HTTP Proxies
HTTP is widely recognized as a go-to protocol for proxy services. These type of proxies blend smoothly with the current web structure, so they are a good choice for both personal and corporate users.
Whether for balancing load of web traffic, managing content or even just enhancing privacy, an HTTP proxy can serve to limitlessly access the web.
This article will explain the HTTP proxy meaning, how it works and what are the most common use cases, so you'll know if it is the best solution for you.
Understanding HTTP
HTTP is an acronym for "Hypertext Transfer Protocol," which designates the basic technology system by which files can be shared through the World Wide Web. All web addresses starting with HTTP point out the use of the Hypertext Transfer Protocol. Designed to make the Internet faster and more efficient, it sits atop the Transmission Control Protocol/Internet Protocol (TCP/IP) stack and is also compatible with Google's QUIC protocol to serve better for very fast online communication.
This protocol is quite important for the way web browsers and servers communicate in order to issue web requests and receive back web pages. HTTP appeared in the year 1989 as a kind of concept proposed by Tim Berners-Lee, the architect of the World Wide Web. First introduced as HTTP/1.0, every version treats the user's requests independently and, at the same time, closes the connection after the particular task gets finished. HTTP has been rapidly changing, upgrading towards better features, and the latest edition is HTTP/3 that included the QUIC protocol for better performance.
Notably, HTTP does not offer encryption for the data in transit, and in about 2010, there was an awakening for a higher level of security; this was a turning point to go towards HTTPS (HTTP Secure). It includes the layer of secure sockets (SSL) with HTTP, which adds an encrypted layer over HTTP to exchange the data between browsers and servers, so you're gonna be secure from eavesdropping and tampering.
What Is The Meaning of An HTTP Proxy?
Let's take a little step back in time and explain to you, in a few words, what HTTP really is. We could say that it's something like the mother tongue of the browsers (like Chrome or Microsoft Edge) and the web servers (places where sites are located) in the communication process.
HTTP is a communication protocol used for the interchange and communication of different kinds of resources, including text, images, videos, and documents.
The HTTP proxy, therefore, is the one that operates just like a gateway on behalf of the web traffic that uses the HTTP protocol. It is a kind of server designed for connections regarding HTTP between a client device and a web server, etc.
Basically, when you use an HTTP server, you are taking advantage of an intermediary to connect to the desired website or page, hence remaining anonymous.
How does an HTTP proxy work?
Because of the online threats that keep haunting every business, all companies working in this domain need to know how an HTTP proxy works. Here is where the HTTP proxy server shines, known for its ability to isolate everything that is suspicious over your network traffic. It will be your vigilant guard, intercepting any outside threats that try to attack your system, scanning the system continuously for malware before they penetrate into the system.
An HTTP proxy server, however, does not stop at the filtering of traffic. It actually checks the source of incoming data before allowing them to be delivered into the internal network. With this protection, your network will be much less at risk of compromise by the content carrying harmful effects or buffer overflow attempts.
Moreover, businesses are able to customize the features of the HTTP proxy server software to fit their needs perfectly. A company can then operationalize the proxy to help with a variety of security and operational objectives that are achieved by tuning the ruleset.
Use Cases
HTTP proxies serve a variety of key functions and come in handy for several practical reasons. Here are some of the primary uses:
Enhancing Anonymity on the Web: HTTP Proxies are the way to go for someone interested in cruising the internet without leaving a trace. HTTP Proxies will hide your real IP and, also, all your online activities will look like they are coming from a different location. This added layer of anonymity makes it tough for anyone to pinpoint your real-world location or identify you.
Crossing Geographical Boundaries: An HTTP proxy could easily be your free ticket to unlimited coverage of the internet, where content or sites are blocked in your geographical area. You just need to route your connection through a proxy server in the geographical area where content is being accessible and you're gonna seamlessly enjoy global internet freedom.
Managing Digital Content: HTTP proxies come in handy in ensuring that the internet usage by institutions and businesses, is within the required guidelines. Most importantly, this helps in blocking out malicious sites, while, at the same time, providing restrictions of accessibility to content that does not relate to their work or studies.
Navigating Around Restrictions: Whether it’s website filters or social media platform limitations, HTTP proxies provide a way to sidestep these hurdles. Using HTTP proxies, users have at their disposal countless IP addresses, so managing numerous accounts or bypassing site restrictions becomes pretty easy, keeping detection and bans at distance.
Balancing web traffic: HTTP proxies are champions in balancing web traffic. They distribute, in a very effective manner, user requests among a number of servers in a way that no individual server gets overwhelmed. This increases the performance and availability of the webs, but also provides a more reliable and faster user experience.
Wrapping Up
And there we wrap up our comprehensive overview of HTTP proxy servers and their operational mechanics.
Employing an HTTP proxy server offers a multitude of advantages for your enterprise, from safeguarding your network against external threats, concealing your IP address, filtering out irrelevant or harmful content, to facilitating your web scraping endeavors. Dive into our curated list of HTTP proxies and start integrating these tools into your projects without any complications
#HTTP Proxy#SOCKS5 Proxy#Dedicated Proxy#Rotating Proxies#Residential Proxy#DNS Proxy#Static Proxy#Shared Proxy#ShadowSOCKS Proxy#US PROXY#UK PROXY#IPV4 PROXY#Anonymous Proxy#Seo Proxy#ISP Proxies#Premium Proxy#Cheap Proxy#Private Proxy#Proxy Service#Linkedin Proxies#IP Rotation
1 note
·
View note
Text
Victoria Housekeeping co.'s special service
Zenless Zone Zero - Lycaon x Wise

A/N: This time I can only thank an anonymous supporter for trusting my skills, ehe ~ I'm not playing ZZZ and I didn't look too much into it, but I think I managed to do a good job.
Also, thanks @/wertzunge for beta reading this one for me!
Summary: Instead of doing her chores, Belle decides to hire Victoria Housekeeping's services to do it for her... and to do something else to her brother
Word count: 1020 words

“Coming…” Wise mumbled, heading towards the door after hearing someone knock thrice on the other side. Having to stop in the middle of his chores wasn’t exactly appreciated, but the possibility of a new customer waiting outside gave him just enough motivation to do so.
“Hello,” the proxy said, trying to sound as friendly as possible, “are you looking f- w-woah…” Wise stopped mid sentence at the sight of a tall, ominous and… fluffy figure. “Ahm, c-can I help you?”
“Victoria Housekeeping, at your service,” Lycaon announced, bowing slightly as his tail swished behind his back. “A full service was requested by master Belle. Is this the correct address?”
Wise nodded, still a bit stunned. His sister left not long ago - just after getting a hearing from him from not cleaning up her bedroom - and he was already accepting the fact that it would be on him to tidy up the place… Wise never expected Belle to actually hire someone to do the job. “V-Victoria? Wait, you guys actually do housekeeping services?”
"Our services are varied. We take every job that our staff see fit to fulfill.” Lycaon explained, a gentle yet firm voice tone as his cold gaze laid upon Wise. “I take you’re master Belle’s brother, master Wise. May I come in?”
Right. “Y-yes, that’s me. Please, come in,” Wise nearly stuttered, quickly stepping aside to allow the Thiren to enter his place. The proxy felt a weird sense of shame when Lycaon seemed to inspect the place so thoroughly, almost as if it was some sort of crime scene. “Ahm, sorry for the mess. I was about to clean it up and-”
“No need to apologize, master,” Lycaon interrupted, the sound of his metallic legs echoing as he turned around to face Wise. “That’s what I’m here for. Master Belle requested a full housekeeping and ‘care’ service.”
“I see,” Wise sighed. “Let me show you around, then.”
“As you wish, master,” Lycaon responded promptly, following Wise with absolute elegance in each and every action. A true gentleman, if you asked Wise.
In their short walk around, Wise decided that his bedroom would be a good place to start. It was where he was the most comfortable and familiar with and, if Belle indeed hired a ‘full housekeeping service’, then cleaning his room should also be part of the pack, right?
“This is far better from what I’ve expected, master,” Lycaon praised the proxy as he slid his fingers over one of the shelves, trying to check if there were any particles of dust laying around. “I believe this is not the main part of the problem, is it?”
“No, it isn’t,” Wise chuckled, sitting on the edge of his bed, “I- well, I thought it would be the easiest to start from, so I decided to show you this room first,” he explained, quickly using the excuse he just came up with.
“Then,” Lycaon turned to Wise, his tall figure towering over him as he stood inches away from Wise’s seat, “do you mind if I start with the second part of the service, master?” Lycaon suggested, holding his hand behind his back.
“What do you mean?”
“Master Belle requested a full housekeeping and care service,” Lycaon explained politely, “with your permission, I’ll do the cleaning once I’m done “taking care of you”, as she described in her request.”
Wise had a puzzled look on his face. What kind of thing did Belle hire? Taking care of him? “A-ahm, sure? What did she ask you t- WAH!!”
“Excuse me, master,” Lycaon muttered gently in a paradoxical contrast with his actions. With great, yet careful, force, the Thiren pushed the proxy back into the mattress. In a swift of Lycaon’s tail, Wise was straddled by cold, metallic legs that firmly pinned his body.
And, before he could figure what was going out, one of Lycaon’s hands closed around both his wrists, keeping them above his head. “As per request by master Belle, I need to inform you that this is for ‘scolding her and being so picky about her bedroom’, master,” Lycaon nodded, following the protocol like a true professional while… merciless tickling Wise’s body.
Big, yet nimble hands scratched and tickled up and down Wise’s side, pinching the spots between each of his ribs and prodding at the middle of his armpits. A mix of embarrassment and confusion struck Wise, but there was no room inside his brain to process all that when all he could think of was how much it tickled. “L-LYCAHAHAON!! AHaHAHAh, wahAHAHait a sehEHEhecon!”
“I apologize, master,” Lycaon muttered, his free hand torturing Wise’s exposed and vulnerable armpit with a ticklish onslaught, “I’m here under master Belle’s orders and her only. I’m afraid I can not follow your requests,” he explained, his hand quickly shooting down and tickling Wise’s waist like it has never been tickled before.
“P-plehehease!! AhAHAhah, i-it’s baAHAhad, LycaHAHAHON!!” Wise could feel the heat spreading over his cheeks as he laughed, all happening so fast and so suddenly that he could barely hold back his reactions. Why did they even have services like this?!
Still, Lycaon was merciless - an unstoppable, unyielding and ticklish force. It tickled so bad and he was still using just one hand!
…
Wise stared at the ceiling with a blank expression, his eyes gazing at the nothing while the sound of vacuum cleaner echoed from the other room. Even after receiving Lycaon’s 5-star-rated aftercare, he still felt like his body was drained of any energy. His stomach and cheeks still sore from laughing and, if he closed his eyes, he could still feel that lingering sensation of Lycaon’s fingers tickling him.
“I’m almost done with master Belle’s room, master,” Lycaon announced, turning off the tool before starting a different task - probably folding her bed sheets or something else. “Would you like something to drink once I’m done, master?”
“N-no need,” Wise sighed, the sound of his own laughter still ringing inside his head. Belle, that brat… Still, he shouldn’t give a negative review to Lycaon, right? It wasn’t like he did a bad job anyway…
#zenless zone zero#zzz#zenless zone zero tickling#zzz tickling#zzz wise#zzz von lycaon#lee!wise#ticklish!wise#ler!lycaon#tickle fic#commission#nim's coffee shop#to: anonymous#lycawise
389 notes
·
View notes
Text
✨Doujinshi Shop Open!✨



Hello all! I have set up a storefront to handle international orders outside of Japan for Closest To My Heart/だれよりも心を許している男, the pza/patrochilles doujinshi I released at the Japanese Hades fan event, Chthonios Epic 3. (And for the Eruri heads out there, I also have the last few copies of my first doujinshi listed as well!)
If you live outside of Japan and you’re interested in buying a copy of my book(s), please visit ninnananna.bigcartel.com!
Basic book details:
Price: ¥1300 JPY (about $8USD) (+ shipping)
A5 size
110 pages
English and Japanese versions both included in one volume
A limited number of copies will also include a FREE postcard extra, featuring a text-free version of the cover art. Please select Book + Postcard in the Book Options menu.
Some Important Things Of Note!
This doujinshi is a bilingual physical edition of my fanfic, Closest To My Heart, which I originally posted in English on AO3. The new Japanese translation of the fic is currently exclusive to this book.
The cover is drawn by the amazing and talented artist RIPTIDE, who also drew an 8-page comic based on a particular scene in the story. The original English version of the comic, as well as a newly created Japanese version are also included in the book.
This doujinshi is R-18 (Adult Only), so please confirm the nature of the contents before you buy. If you are an adult with a pixiv account, you can look at a collection of sample pages here. Please also feel free to read the original version of the story and comic in their entirety on AO3, which is also where I have relevant tags and content warnings written in more detail. But to summarize here: the story has a few brief references to acts of rape/non-con, as well as references to & depictions of emotional and physical abuse, rough sex acts, and dubious consent. This is a darker, more dramatic, alternate canon retelling of the Patrochilles quest from Hades, in which everyone involved (Achilles, Zagreus, & Patroclus) feel emotionally conflicted with one another, as well as the situation they get caught up in. “Toxic love triangle” is the story summary in a nutshell!
Currently, I am able to ship to countries where the Japan Post has Registered Airmail service available. Luckily, this applies to most countries! However, a big exception right now are: EU countries and Northern Ireland. Since apparently new GPSR requirements went into effect, I am looking into whether or not it is feasible for an individual like myself to comply when shipping to these countries.
For anyone living in the EU or Northern Ireland, the only possible workaround I can offer currently is this: proxy service via the listing on Pixiv Booth. Here is the Booth listing: https://darlingpoppet.booth.pm
Booth normally has a built-in proxy service through Buyee available for overseas customers. However, apparently this service is not extended to listings marked as Adult/R-18. However, it’s my understanding that there are other proxy service companies out there who are more lax about purchasing NSFW products on your behalf. I can’t personally vouch of any of them, but some names recommended to me as being Special Yaoi Book-friendly include Tenso, AOCS (both of whom I believe have official ties with the doujinshi retailer Toranoana), ZenMarket, and Neokyo. (ETA: I have since been able to confirm that this option has worked for an EU customer, so please try it!)
Finally, if you are someone who lives in Japan, please use the Booth listing!! Shipping is a flat 370 yen via Anshin Booth Pack, so the transaction is done completely anonymously.
Thank you everyone for your kind support! ♡ I had a lot of fun putting this book together so I hope you’ll enjoy it too.
#hades game#hades supergiant#hades fanart#hades fanfic#patrochilles#pza#zagchilles#patzag#zagreus#achilles#patroclus#hades patrochilles#the iliad#my fics#doujinshi#tagamemnon#eruri#rivaeru
100 notes
·
View notes
Text

HD HURT/COMFORT FEST RULES & GUIDELINES
Below are the rules and guidelines for HD Hurt/Comfort Fest 2025 participants. Please direct any questions or concerns to our ask box, or via [email protected].
HD Hurt/Comfort is an 18+ anonymous prompt-based fest that welcomes creations from both the angsty and fluffy ends of the trope spectrum. Accepted works include fic, art, craft, and podfic categorized as one of these three main tropes:
Angst
Fluff
Hurt/Comfort
**NEW FOR 2025** This year, we have implemented an ‘untagged’ option for prompts and creations! See the rules and guidelines below for more details!
Interested in supporting fellow participants? Need to engage the services of a cheerleader? Want to lament about your difficult muse? Join our HD/HC fest discord community! Open to 18+ only.
Important dates:
Prompting: Apr 7 - May 2 Claiming: May 5 - July 1 Submissions due: Aug 4 Posting begins: Sept 1 Reveals: End of September
Your HD/HC Mods, @peachpety, @vukovich banner art by @basiatlu
Rules & Guidelines below the cut.
PROMPTING
The prompting period is April 7 - May 2.
You may submit as many prompts as you like. You do not have to create for the fest in order to post a prompt.
All prompts must be identified as one of the three accepted fest tropes: angst, fluff, or hurt/comfort combination. Any extra details are welcome. Please note, however, that these additional details are for inspiration only and creators are not obligated to adhere to them fully.
Self-prompts are allowed. There will be a space on the claiming form to add details for self prompts.
**NEW FOR 2025** This year, fest mods have implemented an ‘untagged’ option for prompts and creations. All prompts must be identified as one of the three tagging options: tagged, untagged, or ‘surprise me.’ If a prompt is submitted with the ‘untagged’ or ‘surprise me’ option, the creator is permitted to forgo the use of additional tags and specific archive warnings when posting to AO3. The work will remain untagged for the duration of the fest. Tags may be added by the creator after or during reveals.
Prompts will be available for browsing as soon as prompting opens on April 7.
CLAIMING
The claiming period is May 5 - July 1.
Due to the nature of potential content, this fest is for participants aged 18 and over. Please do not sign up if you are not 18 by the time of claiming.
Upon signing up, you agree to the Rules and Guidelines of the fest.
Only one prompt may be claimed at a time. Prompts are assigned on a first come first serve basis. As such, should you have your eye on a specific prompt but are unable to claim it once claiming opens, a proxy is allowed to claim on your behalf.
If you fulfill your prompt with enough time before submissions, you're welcome to claim an additional prompt. We only ask that you submit your first work as per submission guidelines before claiming another.
Collaborations are welcome! Please only submit one claim form per collaboration and include the details of all participants.
Writer sign-up cap is set at 60. There is no cap for art, craft, or podfic.
If you wish to create art, craft, or podfic based on an existing fanwork, please submit it as a self prompt during the claiming period.
CREATING
All creations must fit into the ‘angst’, ‘fluff’, or ‘hurt/comfort’ categories. There are many themes that fall in line for fluff and angst, but below is a short list of suggestions to help inspire. If you have any doubts or questions about your theme(s), please reach out!
Angst
Depression Addiction (alcohol, other drugs) Abuse (emotional, physical, sexual, etc) Infidelity Death Grief
Fluff
Domesticity Slice of life Getting Together Meet Cute Found family Friends to Lovers
The main pairing for all creations is Draco Malfoy/Harry Potter. Participants may include any side-pairings, threesomes, and/or original characters, as long as the final submission is still a Drarry-centric piece. All ratings and archive warnings are accepted.
As this is an anonymous fest, please do not discuss your creations with anyone in a public forum outside the HD/HC Fest Discord, except for your alpha/beta readers and the fest mods until the reveals have been announced in September. Come join in our Discord fun here!
Ratings suggestions and additional details included for each prompt should be considered inspiration. Feel free to incorporate or ignore them as you see fit! Should you choose to gift your creation to the promptee, however, we ask that you honor any dislikes mentioned.
Please tag your works appropriately (see below for the *new* untagged option!). Due to the nature of this fest, we want to ensure that everyone is informed of potentially triggering content. Please note, however, that all fluff entries must be HEA (Happily Ever After) and must not contain content that merits an archive warning.
If you’re unsure about tagging your work, please let the mods know, and we are happy to help. Please also note that we reserve the right to review your tags and warnings in relation to your content and may contact you to request additions and/or changes. While we can’t dictate consumption of our creations, we will strive to empower our readers/viewers with appropriate information to make an informed choice.
**NEW FOR 2025** This year, fest mods have implemented an ‘untagged’ option for prompts and creations. If your claimed prompt was specified with the ‘untagged’ or ‘surprise me’ option, the creator is permitted to forgo the use of additional tags and specific archive warnings when posting to AO3. The work will remain untagged for the duration of the fest. Tags may be added by the creator after or during reveals.
Author and Artist Guidelines
We will not accept works created with AI.
For fics, the minimum word count is 1000. We have elected to implement a cap on fics of 60k.
All fics must be proofread and follow generally accepted SPaG guidelines. If you are unable to find a beta to assist, please reach out to the mods, and we can provide further guidance.
All fics are posted anonymously, however for art we allow artists to include watermarks on their creations if they so wish.
Podfic Guidelines
Podfics are most certainly welcome, as long as they fit into the 'angst', 'fluff', or 'hurt/comfort' categories! If you intend to podfic a work that you did not originally create, please make sure you get permission from the original author to record it.
For podfics, the minimum word count of the recorded story is 1000, maximum 60k.
All podfics must be proofed. If you are unable to find a beta to assist, please reach out to the mods and we can provide further guidance.
Podfics will be posted anonymously, but podficcers are allowed to state their name in the podfic recording itself (not within their notes on the post).
Drop Outs/Extensions
Throughout the creation period, we'll send a couple of check-in emails—one month and one week before submissions are due. You're welcome to ask for an extension at that time. You're also welcome to contact the mods outside of the check-in period via email or Discord at any point to request one.
We know life likes to surprise us with the unexpected, so please know that if you need to drop out for any reason, that's ok! Just please let us know as early as possible.
SUBMITTING
Once you have completed your work, it’s time to submit!
Submissions are due August 4. If you finish before this date, you are welcome to submit early.
All works must be posted directly [LINK TO POST] to the fest AO3 collection: HD Hurt Comfort Fest 2025. Podfics should be linked to the original work using the AO3 ‘Inspired By’ function, i.e: “This work is a remix, a translation, a podfic, or was inspired by another work” and pasting the URL of the original fic. Please contact the mods if you have any issues submitting your work.
Submissions must be complete works created for this fest. Please do not submit incomplete works or works that are a part of a series or a prequel/sequel to an existing work.
Due to the nature of content present in angsty creations in particular, we want to emphasize the importance of tagging. Please take care to tag for potentially triggering themes present in your work (see below for the *new* untagged option!). If you have questions or need clarification on anything, please reach out to the mods, and we'll be happy to help!
Mods will also read through entries prior to posting to help ensure proper tagging. Should we believe any changes are necessary, we will reach out to you and ask you to make those.
**NEW FOR 2025** This year, fest mods have implemented an ‘untagged’ option for prompts and creations. If your creation is ‘untagged’, you are permitted to forgo the use of additional tags and specific archive warnings when posting to AO3. We will suggest the use of a fest tag for these works: HDHC2025Untagged. The work will remain untagged for the duration of the fest. Tags may be added by the creator after or during reveals.
Following successful upload of your work to the collection, please submit the completed submission header form below to [email protected] to confirm you have posted to the collection. We will respond with a confirmation email in a timely manner.
Submission header:
For Art and/or Fic:
Title: Creator(s): Pairing(s): Harry Potter/Draco Malfoy, <any additional pairings> Rating: Word count/Art Medium Warnings/Tags: Summary: Author's note: Link to work:
For Podfic:
Title: Podficcer: Rating: Length: Warnings/Tags: Summary: Podficcer’s note: Link to podfic: Link to original work:
POSTING
Entries will be posted starting September 1.
In an effort to provide comfort to the hurt, a balm to soothe the pain, we will strive to post creations as pairs—one angst and one fluff per day. Each paired creation will have a stand-alone posting, but will include a link to its contrasting creation.
Of course, it's difficult to ensure we've got exactly equal numbers of angst and fluff pieces, and we don't want to limit creators, so we recognize things will in all likelihood be a little unbalanced.
This is ok though! As mods, we'll do our best to arrange the posting schedule to ensure an even distribution of excellent content.
Additionally, while we will not release a public posting schedule, we will inform participants prior to their anticipated post date.
Once your creation has been posted please be mindful not to reveal yourself as the creator through the duration of anon postings. After the mod reveals posting in September, you are free to claim your creation in personal posts to your heart’s content. Tag us @hd-hurtcomfort-fest in your posts on tumblr and we will reblog from the HD/HC Fest account!
While we hope that it will not happen, sometimes creations receive negative comments. If you receive a nasty or critical comment, please contact the mods asap. We are happy to work with you to address the situation, and will only step in to deal with it if that is your wish.
GENERAL/FAQ
Is this an 18+ fest? Yes, this fest is only open to creators over the age of 18 by the time of claiming (May 5 - July 1).
Untagged? How does that work? If a prompt is submitted with the 'untagged' option, the creator is permitted to forgo the use of additional tags and specific archive warnings when posting to AO3. The work will remain Untagged for the duration of the fest. Tags may be added by the creator after or during reveals.
I want to submit a MCD prompt, is that allowed? Yes! Major Character Death certainly counts as angsty content. Our list of suggested themes is only a small handful of ideas. So feel free to submit away! Also, be sure to select the ‘angst’ option when you submit your prompt.
I don’t want any hurt, only fluffy happy endings. Can my prompt be fluff only? Yes! Just be sure to select the ‘fluff’ option when you submit your prompt.
I love content that features both angst and fluff. Can my prompt be a combination of both? Of course! Just be sure to select the ‘hurt/comfort’ option when you submit your prompt.
Does my angst fic/art have to have comfort? No! You can write/create 100% angst, such as MCD, or pain & anguish without a happy ending if that's where your muse leads you.
What if I want to write hurt & comfort? Go for it!
I want to write/draw/create only cute & fluffy content, is that allowed? YES! We encourage creations of 100% fluff in this fest! Bring on all the meet cutes & sweet happy endings.
What if I don't want my entry to post with a corresponding [fluff||angst] piece? The entire premise of this fest is that angst and fluff pieces will get posted together. Although there will inevitably be an excess of one type of entry, resulting in slight augmentations to posting, there's no way we can make a fair commitment to post specific entries without a corresponding creation on the opposite side of the spectrum. We are happy to discuss your hesitation with you, but if you still have reservations, this particular fest might not be for you, and that's ok!
33 notes
·
View notes
Text
Okay Brits I need you to start paying attention.
We are likely in a General Election year.
We are going to be voting which political party we want to govern us the next five years. As of yet we don't have a date (the latest it could be held is January 2025, though it's probably going to be in 2024), but you need to start listening to what's going on so you can be ready and make an informed choice.
In the last General Election, the turnout was 67.3% across the UK. People often say they didn't vote because they didn't understand the politics or "they're all the same anyway."
When a General Election is called, Polling Day will be 25 days later. If you're working, busy, or just have life stuff happening, you may not have time to do the research you want. This is why it's important to start doing things now.
1. Are you Registered to Vote?
You can register to vote here.
You can check if you're registered by going here.
You must 18 or over on Polling Day to vote in a General Election.
You must also be one of the following:
A British, Irish, or qualifying Commonwealth citizen. (You can check here if you're a qualifying Commonwealth citizen)
Be resident at an address in the UK (or a British citizen living abroad who has been registered to vote in the UK in the last 15 years)
Not be legally excluded from voting
According to the website, while registering, "You’ll be asked for your National Insurance number (but you can still register if you do not have one). After you’ve registered, your name and address will appear on the electoral register."
There is also an option to register to vote anonymously "if you're concerned about your name and address appearing on the electoral register for safety reasons." The link to that page is here.
You can register to vote by post by going here and printing out the forms.
If you would like a step-by-step guide to registering to vote, here is a page that has a pdf doing just that. It is also available in Welsh.
2. Get a Photo ID
We now need to show a photo ID when turning up to the polls.
Here is a list of valid forms of photo ID.
Make sure you give yourself plenty of time to get a valid ID, otherwise you will be turned away from the polling station.
If you vote by proxy, you need to "take your own ID when you go to vote on someone else’s behalf. You do not need to take theirs."
According to the website, "The name on your ID must match your name on the electoral register. If it does not, you’ll need to:
register to vote again with your new details
take a document with you to vote that proves you’ve changed your name (for example, a marriage certificate)
Small differences do not matter. For example, if your ID says ‘Jim Smith’ instead of ‘James Smith’.
If you do not have a type of photo ID that allows you to vote, you can apply for a Voter Authority Certificate."
3. You need to apply to vote by post
You can apply here.
You need to be registered before applying.
To apply you need:
"The address where you are registered to vote
Your National Insurance number or other identity documents, e.g. a passport
the specific date of the election or referendum you want to make a postal vote, if you only want a one-off postal vote
You’ll also need to upload a photo of your handwritten signature in black ink on plain white paper.
If you cannot provide a signature or one that always looks the same, you may be able to apply for a postal vote signature waiver within the service.
You might be asked for extra documents to identify you."
The linked page has an option for downloading an application form to send in by post.
4. Start Researching!
Think back to the last few years.
What did you like, and who did them? What about the opposite?
Is there something local happening in your area, and who is pushing for/against it?
Look up the parties' social media - what do they promote, promise, and call out?
Here are some resources:
An overview of the political parties
BBC News page for current politics
How many MPs are in which parties
Information on General Elections/when ours will likely be held
The other key political events in 2024
General info around voting, elections, boundary changes, etc.
TL;DR
2024 Will likely be the year the UK votes for the next political party in charge.
You need to register to vote.
You need a photo ID to take with you.
You need to apply to vote by post.
The best time to start looking into the parties and what they do is now, so you can be informed later on.
The rest of the world is welcome to share this!
#politics#uk politics#british politics#general election#general election 2024#uk#britain#written in stone
95 notes
·
View notes
Text
Spy x Family AU

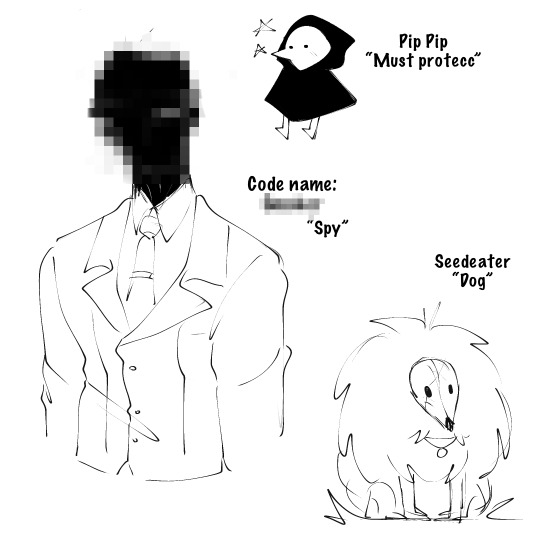
I still need to catch up with the series, but I’m enjoying it so far! I also thought it would be fun to implement some of my mutuals’ Creepypasta/Slenderverse OCs into the genre.
Might rewrite some things while I sort this out!
~~~
Overview
Between indeterminate nations, connections remain unstable and war is likely. To avoid conflicts, both states escorted secret services to deal with such difficulties. Such organizations are known as Proxies & The Red Room.
Proxies (Der Größemann)
Serves the West Nation and attends to the matters of the East. It's at its all-time high stakes for disaster with the East Nation.
The Red Room (Zalgo; Scarlet Kaiser)
Serves the War-torn East Nation; status: unknown...
~~~
Red Spider
Former hitman for hire, the Red Spider was an experiment gone wrong. She hates both nations for what they did to her which eventually led to a life in the shadows. However, she was brought back into the Zalgo workforce for... reasons. She unknowingly works with ████, serving as his "wife/co-partner" and mother/caretaker to Pip Pip.
@the-catcake
████
Alias unknown... He is a spy who works in secrecy. Not even his closest coworkers know his true identity or background. He unknowingly works with Red Spider, serving as her "husband/co-partner" and father/caretaker to Pip Pip.
@paxarsenal
Doll
Doll is one of Der Größemann's closest informants, secretaries, and main coordinator. She's the only person allowed to attend to the director. She must relay information to other coordinators and agents.
@the-slender-doll
Magico
His undercover occupation is a detective. He will use this ability to erase and rewrite evidence to secure his identity and group. Magico worked in the field for many decades and assisted younger spies and assassins to work on their training. He lost his pregnant wife a long time ago when serving the Proxies.
@realmysticalsorcerymystic
Nobody
A young, charming yet deadly assassin. He gets his code name from his secrecy and anonymity. Despite his age, he’s skilled in combat and agility. He brings his sister Crystal, close to his heart as he serves his mission to help citizens. He works closely with Magico, a former spy and current public agent.
@ivydarkrose
Pip Pip
The key to world peace! Very cute but might get into a lot of trouble.
@plaguemasterofficial
Seed Eater
Reduced to dog... Enhanced sight, hearing, smell... It can be very hungry for meat. It is the family "dog" to Pip pip.
#spy x family#crossover#creepypasta#creepypastaoc#creepypastas#art#nathan the nobody#papa grande di magico#akagumo#slender doll ally#alternate universe#au#pip pip#thebartender1941#seed eater
46 notes
·
View notes
Text
Over the last decade, the Kremlin's most aggressive cyberwar unit, known as Sandworm, has focused its hacking campaigns on tormenting Ukraine, even more so since Russian president Vladimir Putin's full-scale invasion of Russia's neighbor. Now Microsoft is warning that a team within that notorious hacking group has shifted its targeting, indiscriminately working to breach networks worldwide—and, in the last year, has seemed to show a particular interest in networks in English-speaking Western countries.
On Wednesday, Microsoft's threat intelligence team published new research into a group within Sandworm that the company’s analysts are calling BadPilot. Microsoft describes the team as an “initial access operation” focused on breaching and gaining a foothold in victim networks before handing off that access to other hackers within Sandworm’s larger organization, which security researchers have for years identified as a unit of Russia’s GRU military intelligence agency. After BadPilot's initial breaches, other Sandworm hackers have used its intrusions to move within victim networks and carry out effects such as stealing information or launching cyberattacks, Microsoft says.
Microsoft describes BadPilot as initiating a high volume of intrusion attempts, casting a wide net and then sorting through the results to focus on particular victims. Over the last three years, the company says, the geography of the group's targeting has evolved: In 2022, it set its sights almost entirely on Ukraine, then broadened its hacking in 2023 to networks worldwide, and then shifted again in 2024 to home in on victims in the US, the UK, Canada and Australia.
“We see them spraying out their attempts at initial access, seeing what comes back, and then focusing on the targets they like,” says Sherrod DeGrippo, Microsoft’s director of threat intelligence strategy. “They’re picking and choosing what makes sense to focus on. And they are focusing on those Western countries.”
Microsoft didn't name any specific victims of BadPilot's intrusions, but broadly stated that the hacker group's targets have included “energy, oil and gas, telecommunications, shipping, arms manufacturing,” and “international governments.” On at least three occasions, Microsoft says, its operations have led to data-destroying cyberattacks carried out by Sandworm against Ukrainian targets.
As for the more recent focus on Western networks, Microsoft's DeGrippo hints that the group's interests have likely been more related to politics. “Global elections are probably a reason for that,” DeGrippo says. “That changing political landscape, I think, is a motivator to change tactics and to change targets.”
Over the more than three years that Microsoft has tracked BadPilot, the group has sought to gain access to victim networks using known but unpatched vulnerabilities in internet-facing software, exploiting hackable flaws in Microsoft Exchange and Outlook, as well as applications from OpenFire, JetBrains, and Zimbra. In its targeting of Western networks over the last year in particular, Microsoft warns that BadPilot has specifically exploited a vulnerability in the remote access tool Connectwise ScreenConnect and Fortinet FortiClient EMS, another application for centrally managing Fortinet's security software on PCs.
After exploiting those vulnerabilities, Microsoft found that BadPilot typically installs software that gives it persistent access to a victim machine, often with legitimate remote access tools like Atera Agent or Splashtop Remote Services. In some cases, in a more unique twist, it also sets up a victim's computer to run as so-called onion service on the Tor anonymity network, essentially turning it into a server that communicates via Tor's collection of proxy machines to hide its communications.
Another, separate report Tuesday from the cybersecurity firm EclecticIQ pointed to an entirely distinct hacking campaign that firm also ties to Sandworm. Since late 2023, EclecticIQ found the hacker group has used a malware-infected Windows piracy tool, distributed via Bittorrent, to breach Ukrainian government networks. In those cases, EclecticIQ found, the hackers have installed a remote access tool called Dark Crystal RAT to carry out cyberespionage.
Any sign of Sandworm, which Microsoft refers to by the name Seashell Blizzard, raises alarms in part because the group has a history of hacking operations that go far beyond mere spying. Over the last decade, the group has caused at least three blackouts by targeting electric utilities in Ukraine—still the only such hacker-induced blackouts in history. The group also released the NotPetya malware that spread worldwide and did at least $10 billion in damage, and it used wiper malware to destroy countless networks in more targeted attacks across Ukraine both before and after the 2022 invasion.
Microsoft has so far found no evidence that, in BadPilot's targeting of Western networks specifically, Sandworm has shown any intention to carry out anything other than espionage. “This seems very early in terms of initial resource gathering, trying to get this much persistent access,” says Microsoft's DeGrippo. “Then we would have to wait to see what they do with it.”
But she notes that BadPilot is nonetheless tied to a larger group that has a history of highly disruptive cyberattacks. “Therefore," says DeGrippo, "the potential actions that they could take next is of deep concern.”
9 notes
·
View notes
Text
How to Leverage Residential Proxies to Increase SEO Traffic
In the digital marketing landscape, Search Engine Optimization (SEO) is a cornerstone for businesses looking to increase visibility, attract organic traffic, and drive conversions. SEO is an ongoing battle to rank higher on search engines, and various strategies can be employed to gain an edge over competitors. Among these strategies, one increasingly popular method is the use of residential proxies. These proxies can significantly enhance SEO efforts by simulating local searches, enabling market research, improving web scraping for data collection, and bypassing geo-blocked content.
In this article, we will explore how to use residential proxies, including rotating residential proxies, static residential proxies, and residential SOCKS5 proxies, to boost SEO traffic. We will discuss their applications, benefits, and the best practices for incorporating them into your SEO strategy.
What Are Residential Proxies and How Do They Impact SEO? Before diving into how residential proxies can be used for SEO, it's important to understand what they are and how they differ from other types of proxies, such as data center proxies.
Residential proxies are IP addresses that are assigned to real devices by Internet Service Providers (ISPs). Unlike data center proxies, which are generated from a central server and can be easily detected, residential proxies are associated with real residential addresses. These proxies appear legitimate to websites, which makes them ideal for activities that require anonymity and access to geo-restricted content.
In the context of SEO, residential proxies offer several benefits. By simulating real user traffic from different regions, businesses can gather market data, test search engine rankings from various locations, and ensure that their content is being indexed correctly. Using residential proxies can also help prevent search engines from flagging your activities as spam or bot behavior, which is common when scraping or automating SEO tasks.
How Residential Proxies Can Enhance SEO Traffic A. Bypass Geo-Restrictions for Localized SEO One of the most significant challenges for businesses with an international presence is the issue of geo-restrictions. Search engines often tailor their results based on a user's location. This can cause discrepancies when businesses conduct keyword research, monitor search rankings, or analyze competitors' performance in different regions.
By using residential proxies, businesses can simulate searches from different countries or cities. This allows them to check localized search results, adjust their SEO strategy for specific regions, and optimize their content to appeal to local audiences. For example, a company based in the U.S. may use residential proxies from the UK to monitor keyword rankings for its products in that region. This approach ensures that businesses get accurate, location-based results without being blocked by search engines or websites.
Rotating residential proxies are especially useful in this context. With rotating proxies, IP addresses change at regular intervals, making it difficult for websites and search engines to detect automated or repetitive activity. This helps businesses avoid IP bans and ensures continuous access to localized search data.
B. Web Scraping and Data Collection for SEO Research Effective SEO requires a deep understanding of competitors, market trends, and keyword performance. This is where web scraping comes into play—scraping data from search engine result pages (SERPs), competitor websites, and other digital platforms. However, most search engines have sophisticated mechanisms to detect scraping activities, which could lead to IP bans or throttling.
By using residential proxies, businesses can perform web scraping without worrying about getting blocked. Since residential proxies use real IP addresses, search engines are less likely to flag the activity as suspicious. Additionally, static residential proxies can provide a stable connection, ensuring that your scraping sessions remain uninterrupted and that data is collected consistently over time.
With rotating residential proxies, businesses can automatically rotate IP addresses to avoid triggering anti-bot mechanisms, ensuring that web scraping efforts are not blocked and that SEO data collection continues seamlessly.
C. Accurate Rank Tracking Without Penalties Monitoring search engine rankings across various regions is a critical component of SEO strategy. However, many SEO tools track rankings from a single location, which may not provide an accurate representation of how content performs globally. Using residential proxies allows businesses to simulate searches from multiple locations, ensuring more precise rank tracking.
For instance, a business can use residential SOCKS5 proxies to track the performance of specific keywords in different regions, measure fluctuations in rankings, and adjust its SEO strategy accordingly. Since residential proxies use IP addresses associated with real users in diverse locations, search engines will return rankings as if they were conducted by local users. This enables businesses to understand how their content ranks in various countries or cities and adjust their strategies to optimize visibility and traffic.
D. Avoid Search Engine Penalties for SEO Automation SEO automation is a powerful tool that allows businesses to streamline tasks such as keyword research, link building, content posting, and more. However, search engines often flag automated activities as suspicious and may impose penalties, resulting in dropped rankings and reduced organic traffic.
To mitigate the risk of penalties, businesses can use residential proxies to disguise automated activities. By rotating IP addresses regularly with rotating residential proxies, businesses can distribute tasks across different residential IPs, making it harder for search engines to detect automation. This allows businesses to perform bulk actions, such as submitting content or checking keyword rankings, without raising red flags.
Additionally, residential SOCKS5 proxies offer added security and anonymity. They can be used to manage multiple accounts for SEO tools and services without revealing your real IP address. This can prevent your SEO accounts from being flagged or suspended due to suspicious activity.
E. Improving Web Performance and User Experience for SEO User experience (UX) is a ranking factor that search engines take into account when determining the quality of a website. A key element of UX is how well a website performs in different regions. Since many SEO activities are location-dependent, ensuring that users from various regions can access your site quickly and without issues is crucial for maintaining high rankings.
Residential proxies can be used to test website performance from different geographical locations. By simulating traffic from multiple regions, businesses can identify issues related to website speed, content loading times, or regional content discrepancies. With this information, they can optimize their website to ensure that users from various locations enjoy a seamless browsing experience, which can, in turn, improve rankings and drive more organic traffic.
Rotating residential proxies ensure that businesses can gather this data continuously without the risk of being blocked or restricted by regional servers. This allows businesses to perform regular performance tests and adjust their website's UX to optimize SEO results.
Best Practices for Using Residential Proxies in SEO To maximize the benefits of residential proxies in SEO, here are some best practices to follow:
Choose Reliable Proxy Providers: Select a provider that offers high-quality, diverse IP addresses from different regions. Look for a provider that offers unlimited bandwidth, fast speeds, and excellent customer support to ensure a smooth experience.
Ensure Data Security: Use residential SOCKS5 proxies for sensitive SEO tasks, as they provide encrypted communication, which enhances data security. Protecting your SEO data and privacy is essential to avoid cyber threats.
Use Rotating Proxies for Scalability: For large-scale SEO tasks such as scraping, keyword research, and competitor analysis, rotating residential proxies are the best choice. They ensure that your activities remain undetected by search engines and websites.
Monitor IP Usage: Even though residential proxies offer high levels of anonymity, it’s essential to monitor your proxy usage and avoid excessive scraping or automation that may still trigger flags.
Track Local Rankings: Leverage static residential proxies to track rankings in specific locations. This will help you understand how your content is performing in different regions and make the necessary adjustments to your SEO strategy.
Conclusion Incorporating residential proxies into your SEO strategy is an effective way to enhance your efforts, drive more organic traffic, and improve search engine rankings. From bypassing geo-restrictions to automating SEO tasks securely, residential proxies provide the tools needed to stay competitive in the ever-evolving digital landscape. Whether you choose rotating residential proxies, static residential proxies, or residential SOCKS5 proxies, these proxies help businesses gather accurate data, monitor competitors, and optimize their websites for better performance.
By following best practices and choosing the right proxy provider, businesses can leverage residential proxies to gain a competitive advantage, improve SEO rankings, and boost website traffic.
#HTTP Proxy#SOCKS5 Proxy#Dedicated Proxy#Rotating Proxies#Residential Proxy#DNS Proxy#Static Proxy#Shared Proxy#ShadowSOCKS Proxy#US PROXY#UK PROXY#IPV4 PROXY#Anonymous Proxy#Seo Proxy#ISP Proxies#Premium Proxy#Cheap Proxy#Private Proxy#Proxy Service#Linkedin Proxies#IP Rotation
0 notes
Text
How to Choose a Reliable Residential Proxy Service Provider: Top 5 Criteria for 2024
In the world of data collection, web scraping, and online privacy, residential proxies have become an essential tool. Unlike traditional data center proxies, residential proxies provide users with IP addresses assigned to real devices in residential areas, making them appear as if they are real people browsing the internet. As businesses, marketers, and individuals rely on residential proxies for tasks such as bypassing geo-restrictions, web scraping, and ad verification, selecting the right provider is crucial. The choice can impact the success of your digital operations. To help you make an informed decision, this article outlines the top five criteria for evaluating residential proxy providers, ensuring you get the best performance, security, and value for your needs.
Understanding Residential Proxies Before diving into the factors for evaluating a provider, it's important to first understand what residential proxies are and how they function. A residential proxy is an IP address provided by an Internet Service Provider (ISP) that is associated with a physical device such as a laptop, smartphone, or desktop computer. These proxies are often used for activities that require a high level of anonymity, like web scraping, ad verification, or accessing geo-restricted content.
Unlike data center proxies, which are generated from servers in data centers, residential proxies are harder to detect because they originate from real residential devices. This makes them ideal for users who need to mimic real user traffic or avoid being blocked by websites.
Key Criteria for Choosing a Residential Proxy Provider 2.1 IP Pool Size and Diversity One of the most important factors to consider when choosing a residential proxy provider is the size and diversity of their IP pool. A large pool of IP addresses means that you can rotate your IPs across different locations, which is essential for web scraping and ad verification. If you're conducting activities like price comparison, competitor analysis, or local market research, you will benefit from proxies that cover a wide variety of countries and regions.
Providers offering unlimited residential proxies or a broad range of IPs across different geographical areas allow users to access localized content, ensuring that their activities appear more natural and less likely to be flagged. Look for a provider that offers rotating residential proxies, allowing IPs to change at regular intervals, or static residential proxies, which remain consistent over time for activities requiring stable connections.
2.2 Reliability and Uptime A reliable proxy service is essential to ensure that your operations run smoothly. Proxy downtime can result in delays or even the blocking of your IP addresses, which can disrupt business operations. Therefore, always check for a provider that guarantees a high uptime—ideally 99.9% or more.
Good residential proxy providers back their services with clear service-level agreements (SLAs) that outline uptime expectations. They should also have built-in redundancy to ensure that your proxies continue to perform, even if certain IP addresses are flagged or blocked.
2.3 Speed and Performance While residential proxies are generally slower than data center proxies, they should still meet performance expectations for most use cases. Factors such as latency, bandwidth, and connection speed are essential when choosing a provider. For web scraping, ad verification, or SEO monitoring, the speed of the proxies will determine how efficiently your tasks can be executed.
Make sure to test the provider’s proxies to see if they meet your performance requirements. If your task requires high-speed data transfers or real-time scraping, you should choose a provider that offers unlimited bandwidth or high-speed residential proxies.
2.4 Security and Privacy Security is a paramount consideration when selecting a residential proxy provider. Since residential proxies are often used to conceal the user's identity, it’s important that the provider respects your privacy and follows best practices for data security. Ensure the provider uses HTTPS encryption to protect your traffic from potential interception.
Also, avoid providers that collect or log your personal information. A reliable provider will have a transparent privacy policy that clearly outlines their practices and guarantees that your data will not be shared or sold to third parties. Look for providers that adhere to strong security standards and avoid any providers that have questionable practices in this area.
2.5 Customer Support Responsive customer support can make or break your experience with a residential proxy provider. When using proxies, you may encounter technical issues, IP bans, or other obstacles that require prompt assistance. Choose a provider that offers 24/7 customer support across multiple channels like live chat, email, and phone support.
It’s always a good idea to test the provider’s customer support before committing to a plan. Reach out with a few questions to see how quickly and effectively they respond. A provider that offers excellent support can ensure your proxy service remains uninterrupted, helping you solve any issues in a timely manner.
2.6 Pricing and Plans Cost is an important factor in any decision-making process. However, when it comes to residential proxies, the cheapest option is not always the best. Lower-cost services might come with limitations in terms of IP pool size, speed, or security. Make sure the pricing aligns with your business needs.
Some providers offer flexible pricing models, including pay-as-you-go or subscription-based plans, which can help businesses scale up or down based on usage. Additionally, look for free trial periods or money-back guarantees to test the service before committing long-term.
Providers that offer dedicated residential proxies may charge higher fees, but they can be ideal for activities that require high consistency and performance. On the other hand, rotating residential proxies can be more cost-effective for tasks like web scraping where IP rotation is necessary.
2.7 Reputation and Reviews One of the best ways to evaluate a residential proxy provider is by checking user reviews and feedback from other customers. Reviews on independent forums, third-party review sites, or social media platforms can give you an honest perspective on the provider’s strengths and weaknesses.
Pay attention to what other users are saying about the provider’s IP quality, customer support, uptime, and performance. Negative reviews about slow or unreliable proxies, poor customer service, or hidden fees are red flags that should not be ignored.
However, be cautious about providers with overly positive reviews, as some may engage in review manipulation to boost their reputation. Consider multiple sources of feedback to get a well-rounded view of the provider’s reliability.
2.8 Trial Periods and Money-Back Guarantees Many reliable residential proxy service providers offer free trials or money-back guarantees to give users the opportunity to test the service before making a full commitment. Taking advantage of these offers allows you to evaluate the quality of the proxies, their speed, and their compatibility with your intended use case.
For instance, some providers offer a residential proxy trial that allows you to test a certain number of IPs for free or at a reduced rate. This is an excellent way to assess the provider’s performance and see if they meet your needs before making a long-term financial commitment.
Red Flags to Watch Out For While many proxy providers are legitimate, there are a few red flags that might indicate a less trustworthy service:
Vague terms of service: If the provider doesn’t have clear terms of service or a privacy policy, it may be a sign of poor practices. Unrealistically low pricing: Extremely low pricing could mean that the provider is cutting corners in terms of service quality or security. Poor customer support: If the provider is unresponsive to inquiries or doesn’t offer adequate support, it’s best to avoid them. Limited geographic coverage: Some providers may not offer the regional diversity you need for global operations.
Conclusion Selecting a reliable residential proxy service provider is a critical decision for any business or individual using proxies for activities like web scraping, ad verification, or geo-restricted content access. The key factors to consider include IP pool size, geographic coverage, speed and performance, security and privacy, customer support, and pricing.
By carefully evaluating these factors and testing out different providers, you can ensure that you select the best provider for your needs. Always watch out for red flags and take advantage of trial periods to test the service before committing to a long-term plan. With the right residential proxy provider, you can ensure the success of your digital operations while maintaining the highest levels of security, performance, and reliability.
#HTTP Proxy#SOCKS5 Proxy#Dedicated Proxy#Rotating Proxies#Residential Proxy#DNS Proxy#Static Proxy#Shared Proxy#ShadowSOCKS Proxy#US PROXY#UK PROXY#IPV4 PROXY#Anonymous Proxy#Seo Proxy#ISP Proxies#Premium Proxy#Cheap Proxy#Private Proxy#Proxy Service#Linkedin Proxies#IP Rotation
0 notes
Text
isam1mir is the person who went and told funy4howa about sophiebabyb3ar and ruined her proxy service..if you did not know you do now
~Anonymous
8 notes
·
View notes
Text
Quicksand
Fem Reader x Sir Crocodile
20 Chapters - 46,838 words
Read it on Ao3 or Wattpad
CW: Language, violence, blood, moral ambiguity, murder, sexual themes and situations, yandere, angst with a happy ending, a referenced instance of physical abuse. 18+ only
Note: There's an alternative version of this story that picks up at chapter six that will be available as well. It goes darker and harder than the original. ♥
Summary: You're employed as an Internal Coordinator in the West Branch of Rain Dinners in Grandline Metro. You're well-aware your boss is the Warlord Sir Crocodile, but your sixty days is almost up on the popular dating website Cult of Personality, and you're looking forward to meeting the person you've been talking to for the last sixty days. (This makes it sound way fluffier than it is, oops.)

Chapter 1: The Nitty-Gritty
You smile at the sound of the message popping up on your computer. You'd been chatting online with someone for the last couple months, and after getting to know one another through your shared likes and dislikes, you'd finally decided to meet. You've avoided sharing photos, or even having a conversation on the phone, but all of that had been the point of the website you'd both found yourselves using.
Cult of Personality was a quirky singles site that focused on people getting to know one another purely through interests. The idea behind it was that you could get to know someone without those pesky instincts getting in the way – no getting swept away by someone's voice, or getting too focused on their appearance (for better or worse). Instead, you spent at least sixty days communicating by text through anonymous proxies. If anyone said something that was a deal-breaker during that time, then there were no messy fallouts to deal with.
The connection would be severed without you knowing enough about the other to be able to locate them. The system was even designed to automatically censor location names, so people couldn't accidentally give themselves away. The only thing the service did with location information was use it to randomly match people who were within 100km of one another.
It was great for people who didn't really want to fill out tons of questionaries, or worry about uploading photos, or dealing with talking about themselves.
For you it was nice because after a few failed relationships, and with a job that took a lot of your time, it was an easy way to get yourself back into the whole idea of dating.
As your luck would have it, you found someone who you enjoyed "talking" to after only a couple tries. You had even admitted that you looked forward to your conversations and had been pleasantly surprised to find out he did as well. It was reassuring to know that things weren't one-sided, and shortly after that you'd both started making plans to meet up once the 60 days was completed, and the site gave you the option to lift the automatic censoring.
You had preemptively decided on a Saturday lunch meeting, just in case you were at the edges of the 100km diameter that the site utilized. Better than trying to make a dinner reservation on a Friday after work, and ending up in a panic if one of you were to be stuck in traffic.
The restrictions lifted tomorrow, Wednesday, and as you got ready for work you were humming to yourself.
In Grandline Metropolis, amidst it's 600,000 sq km of land, you worked for one of the seven Warlords who oversaw the second circle of the city. While you knew Mr. Crocodile was a warlord, you weren't directly connected to the city's underground. You knew about the city's underground because you were school friends with people who had ended up in that life, and you still kept in touch. But, like most of the employees of the Rain Dinners – the casino/restaurant/hotel chain with five locations around the Grandline Metro – you weren't a part of the underground directly. There were people closer to Mr. Crocodile who probably had ties to stuff like that, but you were just the secretary to one of the mid-level casino floor managers of the West location, just outside White Beard's territory.
Buggy was, well, buggy. He seemed to be constantly under a lot of stress, but he wasn't a terrible boss. He had a decent sense of humor, was easily brought into focus, and often went out of his way to make sure the people under him were doing well. He was a bit selfish, but whenever someone needed to be legitimately let go, you always had to come to him with well-documented, irrefutable proof. While that could be annoying in some cases, it was also reassuring that he wasn't letting people come and go without being sure there was nothing else to be done for it.
"Hey boss, I won't be available this weekend." You explain, handing over another paper for Buggy to review. "So if something goes wrong you'll have to call Alvida."
"Are we expecting anything unusual this weekend?" He questions calmly.
"No, there's no big events, and Alvida's already aware I'll be unavailable." You're kind of surprised to see Buggy this calm. Usually, he was a complete mess when you took vacations or called out sick.
"Alright, (Y/N), just make sure to let Alvida know that Galdino's going to be the one reaching out. I'm off this weekend as well."
Ah, that explains why he's so relaxed. You muse. After a moment's thought you flinch. You hadn't exchanged names with the person you were meeting this weekend. Statistically, it was improbable that it was Buggy, but it wasn't impossible either. Well, if it was him, you couldn't let your professional assessment of him color how he was in his private life.
"I'll let her know." You assure him flatly, taking back the last of the documents and reorganizing them quickly on his desk. "Your meetings are light today, and tomorrow you have the Staff Luncheon to attend."
Buggy flinches. "Right."
"It's at our branch this month, Buggy."
Your boss sighs. "That's the problem."
You laugh. "It is harder to 'accidentally' miss it due to traffic when it's here."
"You're being a little too flashy, Miss (Y/N)." He grumbles.
"And yet you still appreciate me." You quip, giving him a smile before walking out to get back to your own work.
The rest of your work day went smoothly. You coordinated with Galdino and Alvida about the weekend, making sure they knew that neither you nor Buggy would be available. Alvida had raised an eyebrow over it, since she knew you'd been signed up on Cult of Personality. You had filled her in on your plans for the weekend before now. You were still pretty sure it wasn't Buggy, but she made you promise her that if it turned out to be him you would let her know immediately.
Alvida had her quirks, and she could kind of mean in that haughty beauty sort of way, but she wasn't malicious or cruel. You'd shared a few drinks outside of work, and mainly she just enjoyed drama and gossip.
Getting home you went through your after-work routine. Peeling off your work clothes you slipped into sweats and a t-shirt, made yourself something easy, and relaxed with an episode of your favorite show while you ate. Afterward you checked your messages and settled into the dating website.
You: One more day \o/
Him: I'm glad your enthusiasm hasn't waned.
You: At this rate I'm worried I'll be exhausted come Saturday. I'm really looking forward to this.
Him: Plans can be easily adjusted if need be.
You: Joking aside, I'm sure I'll manage. Though, I have to admit that today has caused me to be very curious about something. >_>
Him: Oh?
You: Well, it seems my boss at work has requested this weekend off as well. O_O
Him: Ah-ha. Did you request your time off today?
You: I did.
Him: Then I wouldn't worry. I didn't have any of my employees request time off to me directly today.
You: Oh good.
Him: My condolences to your boss.
You: lol he's not a bad guy, but that would've been incredibly awkward.
Him: It would've been a mark against you wanting to meet someone new, as well.
You: You're not wrong.
You: Admittedly, I wouldn't hold it against you if we did know one another.
Him: That's reassuring. Though, if I do know you, then I have done myself a great disservice for not knowing you well enough until now.
You feel yourself blush despite it all. It was nice to be appreciated for your, well, you-ness, and not for anything else. You let him know you appreciated the sentiment and the two of you talked about nothing and everything off and on for the rest of the evening.
Tomorrow was going to be the longest Wednesday to ever dare to exist, not just because you were looking forward to getting home before you'd even left for work, but also because the monthly staff luncheons always made the days feel longer when they were at your branch. It wasn't nearly as bad when Buggy was ushered out and into a different branch for the event, but every 5th month it meant your casino was filled with important people.
Important people like to feel important, so there were all sorts of extra protocols and fine moving parts to worry about. The hardest part was going to be dealing with the Billions. The people who were only just barely important and wanted to make sure no one could possibly forget it. The Baroque Works staff would be there as well, and if things went well, after the initial meet and greet, all you would have to worry about was filling Buggy's shoes while he was busy at the Luncheon.
. . . . .
You: Good morning, I can't stay on and talk much right now, there's an event at work I need to be in early for. Looking forward to talking to you tonight!
Him: Much anticipated.
The drive into work was faster than usual since you had left a couple hours earlier and traffic was nonexistent. You got into work and got all your normal morning work done before the doors had even opened. Alvida and Galdino were in almost as early and you set them to work organizing the cleaners and preppers. Surfaces that had been polished the night before were polished again just to add a little more luster.
There were three times as many valets available today, to deal with the influx of VIPs, and almost every member of staff was working. People were rotated in and out on tables more often as well to keep every extra sharp. Extra areas had been opened in the back to accommodate people being able to lounge between there active table times so they could recharge properly. It was an untenable schedule every single day, but everyone came together to make it work for the Luncheons.
When the owner, Mr. Crocodile arrived, everyone lined up to greet him. It was the only time all the staff stopped what they were doing to greet a guest. Nothing was said, but everyone lined up neatly in the lobby and bowed slightly as he entered. As far as you knew it wasn't even something he had requested, one of the Numbers had demanded it at their branch some years ago and the tradition stuck.
Frankly, if you ever learned who Mr. Nine was, you would happily punch the lout right in his nose for suggesting it. Fortunately, Mr. Crocodile didn't linger in the entry way, and strode quickly through. Considering he was just over 7', he had an impressive stride. Aside from the company photo, and the occasional glance in the hall when the luncheons were held at your branch, all you ever saw of him were his shoes.
When you first started working at Rain Dinners you'd had a little crush on him, but from the way things went for most of the staff, everyone had a little crush on him. He was the least eccentric of the Warlords, far as you were aware, and the man had style. Most of the ladies swooned over him and half the of the men on staff did as well.
He wasn't much older than you either. Far from the youngest of the Warlords, he was just over 30 and doing remarkably well for himself. He was barely of legal gambling age when he started the first Rain Dinners, and within three years there were 5 of them in the Grandline Metro alone.
With the owner gone, everyone burst into action and the several moments later the casino came alive as the doors opened to the public and the day began properly.
Only eight more hours to go before you could start making proper plans for the coming weekend.
#Quicksand#Sir Crocodile#x reader#sir crocodile x reader#one piece fanfiction#modern au#reader insert#yandere#grandline metro au
55 notes
·
View notes
Text
[Full Text] Emerging Media Companies, Tracking Cookies, and Data Privacy -- An open letter to Critical Role, Dropout, and fellow audience members
Summary / TL;DR
Both Critical Role (CR) and Dropout have begun exclusively using links provided by third-party digital marketing solution companies in their email newsletters.
Every link in each of the newsletters (even the unsubscribe link) goes through a third-party domain which is flagged as a tracking server by the uBlock Origin browser extension.
Third-party tracking cookies are strictly unnecessary and come with a wide array of risks, including non-consensual targeted advertising, targeted misinformation, doxxing, and the potential for abuse by law enforcement.
You are potentially putting your privacy at risk every time you click on any of the links in either of these newsletters.
IMO these advertising companies (and perhaps CR/Dropout by proxy) are likely breaking the law in the EU and California by violating the GDPR and CCPA respectively.
Even if Critical Role and Dropout are not directly selling or exploiting your personal data, they are still profiting off of it by contracting with, and receiving services from, companies who almost certainly are. The value of your personal data is priced into the cost of these services.
They should stop, and can do so without any loss of web functionality.
1/7. What is happening?
Critical Role and Dropout have begun exclusively using links provided by third-party digital marketing solution companies in their email newsletters.

[ID: A screenshot of the Dropout newsletter alongside the page’s HTML source which shows that the target destination for an anchor element in the email leads to d2xR2K04.na1.hubspotlinks.com. End ID.]

[ID: A screenshot of the CR newsletter alongside the page’s HTML source which shows that the target destination for an anchor element in the email leads to trk.klclick.com. End ID.]
The domains attached to these links are flagged as advertising trackers by the uBlock Origin browser extension.

[ID: Screenshot of a Firefox web browser. The page displays a large warning icon and reads “uBlock Origin has prevented the following page from loading [...] because of the following filter: `||hubspotlinks.com` found in Peter Lowe’s Ad and tracking server list. End ID.]

[ID: Screenshot of a Firefox web browser. The page displays a large warning icon and reads “uBlock Origin has prevented the following page from loading [...] because of the following filter: `||klclick1.com` found in Peter Lowe’s Ad and tracking server list. End ID.]
In both cases, every link in the newsletter goes through the flagged third-party domain, and the intended endpoint (Twitter, their store page, etc.) is completely obscured and inaccessible from within the email itself. Even the unsubscribe links feed through the tracking service.
You can test this yourself in your own email client by hovering your cursor over a link in the email without clicking it and watching to see what URL pops up. You may have noticed this yourself if you use uBlock Origin as an ad-blocker.
I don’t know for certain when this first started. It’s possible that this has been going on for a year or more at this point, or it may have started just a few months ago. Either way: it ought to stop.
2/7. What is a tracking cookie?
A tracking cookie is a unique, universally identifiable value placed on your machine by somebody with the intention of checking for that value later to identify you (or at least to identify your machine).
Tracking cookies are used by companies to create advertising behaviour profiles. These profiles are supposedly anonymous, but even if the marketing companies creating them are not lying about that (a tough sell for me personally, but your mileage may vary when it comes to corporations with 9-figure annual incomes), the data can often be de-anonymized.
If this happens, the data can be used to identify the associated user, potentially including their full name, email address, phone number, and physical address—all of which may then be associated with things like their shopping habits, hobbies, preferences, the identities of their friends and family, gender, political opinions, job history, credit score, sexuality, and even when they ovulate.
Now, it is important to note that not all cookies are tracking cookies. A cookie is just some data from a web page that persists on your machine and gets sent back to the server that put it there. Cookies in general are not necessarily malicious or harmful, and are often essential to certain web features functioning correctly (e.g. keeping the user logged in on their web browser after they close the tab). But the thing to keep in mind is that a domain has absolute control over the information that has been stored on your computer by that domain, so allowing cookies is a matter of trusting the specific domain that wants to put them there. You can look at the outgoing information being sent from your machine, but its purpose cannot be determined without knowing what is being done with it on the other side, and these marketing companies ought not to have the benefit of your doubt when they have already been flagged by privacy watchdogs.
3/7. What’s the harm?
Most urgently, as I touched on above: The main source of harm is from corporations profiting off of your private data without your informed consent. However, targeted advertising is actually the least potentially harmful outcome of tracking cookies.
1/6. Data brokers
A data broker is an individual or company that specializes in collecting personal data (such as personal income, ethnicity, political beliefs, geolocation data, etc.) and selling or licensing such information to third parties for a variety of uses, such as background checks conducted by employers and landlords, two universally benevolent groups of people.
There are varying regulations around the world limiting the collection of information on individuals, and the State of California passed a law attempting to address this problem in 2018, following in the footsteps of the EU’s GDPR, but in the jurisdiction of the United States there is no federal regulation protecting consumers from data brokers. In fact, due to the rising interest in federal regulation, data broker firms lobbied to the tune of $29 million in the year 2020 alone.
2/6. De-anonymization techniques
Data re-identification or de-anonymization is the practice of combining datasets (such as advertising profiles) and publicly available information (such as scraped data from social media profiles) in order to discover patterns that may reveal the identities of some or all members of a dataset otherwise intended to be anonymous.
Using the 1990 census, Professor Latanya Sweeney of the Practice of Government and Technology at the Harvard Kennedy School found that up to 87% of the U.S. population can be identified using a combination of their 5-digit zip code, gender, and date of birth. [Link to the paper.]
Individuals whose datasets are re-identified are at risk of having their private information sold to organizations without their knowledge or consent. Once an individual’s privacy has been breached as a result of re-identification, future breaches become much easier: as soon as a link is made between one piece of data and a person’s real identity, that person is no longer anonymous and is at far greater risk of having their data from other sources similarly compromised.
3/6. Doxxing
Once your data has been de-anonymized, you are significantly more vulnerable to all manner of malicious activity: from scam calls and emails to identity theft to doxxing. This is of particular concern for members of minority groups who may be targeted by hate-motivated attacks.
4/6. Potential for abuse by government and law enforcement
Excerpt from “How period tracking apps and data privacy fit into a post-Roe v. Wade climate” by Rina Torchinsky for NPR:
Millions of people use apps to help track their menstrual cycles. Flo, which bills itself as the most popular period and cycle tracking app, has amassed 43 million active users. Another app, Clue, claims 12 million monthly active users. The personal health data stored in these apps is among the most intimate types of information a person can share. And it can also be telling. The apps can show when their period stops and starts and when a pregnancy stops and starts. That has privacy experts on edge because this data—whether subpoenaed or sold to a third party—could be used to suggest that someone has had or is considering an abortion. ‘We're very concerned in a lot of advocacy spaces about what happens when private corporations or the government can gain access to deeply sensitive data about people’s lives and activities,’ says Lydia X. Z. Brown, a policy counsel with the Privacy and Data Project at the Center for Democracy and Technology. ‘Especially when that data could put people in vulnerable and marginalized communities at risk for actual harm.’
Obviously Critical Role and Dropout are not collecting any sort of data related to their users’ menstrual cycles, but the thing to keep in mind is that any data that is exposed to third parties can be sold and distributed without your knowledge or consent and then be used by disinterested—or outright malicious—actors to de-anonymize your data from other sources, included potentially highly compromising data such as that collected by these period-tracking apps. Data privacy violations have compounding dangers, and should be proactively addressed wherever possible. The more of your personal data exists in the hands of third parties, the more it is to be de-anonymized.
5/6. Targeted misinformation
Data brokers are often incredibly unscrupulous actors, and will sell your data to whomever can afford to buy it, no questions asked. The most high-profile case of the consequences of this is the Facebook—Cambridge Analytica data scandal, wherein the personal data of Facebook users were acquired by Cambridge Analytica Ltd. and compiled alongside information collected from other data brokers. By giving this third-party app permission to acquire their data back in 2015, Meta (then Facebook) also gave the app access to information on their users’ friend networks: this resulted in the data of some 87 million users being collected and exploited.
The data collected by Cambridge Analytica was widely used by political strategists to influence elections and, by and large, undermine democracy around the world: While its parent company SCL had been influencing elections in developing countries for decades, Cambridge Analytica focused more on the United Kingdom and the United States. CEO Alexander Nix said the organization was involved in 44 American political races in 2014. In 2016, they worked for Donald Trump’s presidential campaign as well as for Leave.EU, one of the organisations campaigning for the United Kingdom to leave the European Union.
6/6. The Crux: Right to Privacy Violations
Even if all of the above were not concerns, every internet user should object to being arbitrarily tracked on the basis of their right to privacy. Companies should not be entitled to create and profit from personality profiles about you just because you purchased unrelated products or services from them. This right to user privacy is the central motivation behind laws like the EU’s GDPR and California’s CCPA (see Section 6).
4/7. Refuting Common Responses
1/3. “Why are you so upset? This isn’t a big deal.”
Commenter: Oh, if you’re just talking about third party cookies, that’s not a big deal … Adding a cookie to store that ‘this user clicked on a marketing email from critical role’ is hardly [worth worrying about].
Me: I don’t think you understand what tracking cookies are. They are the digital equivalent of you going to a drive through and someone from the restaurant running out of the store and sticking a GPS monitor onto your car.
Commenter: Kind of. It’s more like slapping a bumper sticker on that says, in restaurant-ese, ‘Hi I’m [name] and I went to [restaurant] once!’
This is actually an accurate correction. My metaphor was admittedly overly simplistic, but the correction specifies only so far as is comfortable for the commenter. If we want to construct a metaphor that is as accurate as possible, it would go something like this:
You drive into the McDonald’s parking lot. As you are pulling in, unbeknownst to you, a Strange Man pops out of a nearby bush (that McDonald’s has allowed him to place here deliberately for this express purpose), and sticks an invisible bumper sticker onto the back of your car. The bumper sticker is a tracker that tells the Strange Man which road you took to drive to McDonald’s, what kind of car you drive, and what (if anything) you ordered from McDonald’s while you were inside. It might also tell him where you parked in the parking lot, what music you were listening to in your car on the way in, which items you looked at on the menu and for how long, if you went to the washroom, which washroom you went into, how long you were in the washroom, and the exact location of every step you took inside the building.
Now, as soon as you leave the McDonald’s, the bumper sticker goes silent and stops being able to report information. But, let’s say next week you decide to go to the Grocery Store, and (again, unbeknownst to you), the Strange Man also has a deal with the Grocery Store. So as you’re driving into the grocery store’s parking lot, he pops out of another bush and goes to put another bumper sticker onto your car. But as he’s doing so, he notices the bumper sticker he’s already placed there a week ago that only he can see (unless you’ve done the car-equivalent of clearing your browser cache), and goes “ah, it’s Consumer #1287499290! I’ll make sure to file all of this new data under my records for Consumer #1287499290!”
You get out of your car and start to walk into the Grocery Store, but before you open the door, the Strange Man whispers to the Grocery Store: “Hey, I know you’re really trying to push your cereal right now, want me to make it more likely that this person buys some cereal from you?” and of course the Grocery Store agrees—this was the whole reason they let him set up that weird parking lot bush in the first place.
So the Strange Man runs around the store rearranging shelves. He doesn’t know your name (all the data he collects is strictly anonymous after all!) but he does know that you chose the cutesy toy for your happy meal at McDonald’s, so he changes all of the cereal packaging labels in the store to be pastel-coloured and covered in fluffy bears and unicorns. And maybe you were already going to the Grocery Store to buy cereal, and maybe you’re actually very happy to buy some cereal in a package that seems to cater specifically to your interests, but wouldn’t you feel at least a little violated if you found out that this whole process occurred without your knowledge? Especially if you felt like you could trust the people who owned the Grocery Store? They’re not really your friend or anything, but maybe you thought that they were compassionate and responsible members of the community, and part of the reason that you shopped at their store was to support that kind of business.
2/3. “Everyone does it, get over it.”
Commenter: [The marketing company working with CR] is an industry standard at this point, particularly for small businesses. Major partner of Shopify, a fairly big player. If you don't have a software development team, using industry standard solutions like these is the easy, safe option.
This sounds reasonable, but it actually makes it worse, not better, that Critical Role and Dropout are doing this. All this excuse tells me is that most businesses using Shopify (or at least the majority of those that use its recommended newsletter service) have a bush for the Strange Man set up in their parking lot.
Contracting with these businesses is certainly the easy option, but it is decidedly not the safe one.
3/3. “They need to do it for marketing reasons.”
Commenter 1: Email marketing tools like [this] use tracking to measure open and click rates. I get why you don’t want to be tracked, but it’s very hard to run a sizeable email newsletter without any user data.
Commenter 2: I work in digital marketing … every single email you get from a company has something similar to this. Guaranteed. This looks totally standard.
I am a web programmer by trade. It is my full time job. Tracking the metrics that Critical Role and Dropout are most likely interested in does not require embedding third-party tracking cookies in their fans’ web browsers. If you feel comfortable taking my word on that, feel free to skip the next section. If you’re skeptical (or if you just want to learn a little bit about how the internet works) please read on.
5/7. Tracking cookies are never necessary
We live in a technocracy. We live in a world in which technology design dictates the rules we live by. We don’t know these people, we didn’t vote for them in office, there was no debate about their design. But yet, the rules that they determine by the design decisions they make—many of them somewhat arbitrary—end up dictating how we will live our lives. —Latanya Sweeney
1/3. Definitions
A website is a combination of 2 computer programs. One of the two programs runs on your computer (laptop/desktop/phone/etc.) and the other runs on another computer somewhere in the world. The program running on your computer is the client program. The program running on the other computer is the server program.
A message sent from the client to the server is a request. A message sent from the server to the client is a response.
Cookies are bits of data that the server sends to the client in a response that the client then sends back to the server as an attachment to its subsequent requests.
A session is a series of sequential interactions between a client and server. When either of the two programs stops running (e.g. when you close a browser tab), the session is ended and any future interactions will take place in a new session.
A URL is a Uniform Resource Locator. You may also sometimes see the initialism URI—in which the ‘I’ stands for Identifier—but they effectively refer to the same thing, which is the place to find a specific thing on the internet. For our purposes, a “link” and a URL mean the same thing.
2/3. What do Critical Role and Dropout want?
These media companies (in my best estimation) are contracting with the digital advertising companies in order to get one or more of the following things:
Customer identity verification (between sessions)
Marketing campaign analytics
Customer preference profiles
Customer behaviour profiles
3/3. How can they get these things without tracking cookies?
Accounts. Dropout has an account system already. As Beacon is a thing now I have to assume Critical Role does as well, therefore this is literally already something they can do without any additional parties getting involved.
URL Query Parameters. So you want to know which of your social media feeds is driving the most traffic to your storefront. You could contract a third-party advertising company to do this for you, but as we have seen this might not be the ideal option. Instead, when posting your links to said feeds, attach a little bit of extra text to the end of the URL link so: becomes or or even These extra bits of information at the end of a URL are query parameters, and act as a way for the client to specify some instructions for the server when sending a request. In effect, a URL with query parameters allows the client to say to the server “I want this thing under these conditions”. The benefit of this approach is, of course, that you actually know precisely what information is being collected (the stuff in the parameters) and precisely what is being done with it, and you’ve avoided exposing any of your user data to third parties.
Internal data collection. Optionally associate a user’s email address with their preferences on the site. Prompt them to do this whenever they purchase anything or do any action that might benefit from having some saved preference, informing them explicitly when you do so and giving them the opportunity to opt-out.
Internal data collection. The same as above, but let the user know you are also tracking their movements while on your site. You can directly track user behaviour down to every single mouse movement if you really want to—again, no need to get an outside party involved to snoop on your fans. But you shouldn’t do that because it’s a little creepy!
At the end of the day, it will of course be more work to set up and maintain these things, and thus it will inevitably be more expensive—but that discrepancy in expense represents profit that these companies are currently making on the basis of violating their fans’ right to privacy.
6/7. Breaking the Law
The data subject shall have the right to object, on grounds relating to his or her particular situation, at any time to processing of personal data concerning him or her [...] The controller shall no longer process the personal data unless the controller demonstrates compelling legitimate grounds for the processing which override the interests, rights and freedoms of the data subject or for the establishment, exercise or defence of legal claims. Where personal data are processed for direct marketing purposes, the data subject shall have the right to object at any time to processing of personal data concerning him or her for such marketing, which includes profiling to the extent that it is related to such direct marketing. Where the data subject objects to processing for direct marketing purposes, the personal data shall no longer be processed for such purposes. At the latest at the time of the first communication with the data subject, the right referred to in paragraphs 1 and 2 shall be explicitly brought to the attention of the data subject and shall be presented clearly and separately from any other information. — General Data Protection Regulation, Art. 21
Nobody wants to break the law and be caught. I am not accusing anyone of anything and this is just my personal speculation on publicly-available information. I am not a lawyer; I merely make computer go beep-boop. If you have any factual corrections for this or any other section in this document please leave a comment and I will update the text with a revision note. Before I try my hand at the legal-adjacent stuff, allow me to wade in with the tech stuff.
Cookies are sometimes good and sometimes bad. Cookies from someone you trust are usually good. Cookies from someone you don’t know are occasionally bad. But you can take proactive measures against bad cookies. You should always default to denying any cookies that go beyond the “essential” or “functional” categorizations on any website of which you are remotely suspicious. Deny as many cookies as possible. Pay attention to what the cookie pop-ups actually say and don’t just click on the highlighted button: it is usually “Accept All”, which means that tracking and advertising cookies are fair game from the moment you click that button onward. It is illegal for companies to arbitrarily provide you a worse service for opting out of being tracked (at least it is in the EU and California).
It is my opinion (and again, I am not a legal professional, just a web developer, so take this with a grain of salt) that the links included in the newsletter emails violate both of these laws. If a user of the email newsletter residing in California or the EU wishes to visit any of the links included in said email without being tracked, they have no way of doing so. None of the actual endpoints are available in the email, effectively forcing the user to go through the third-party domain and submit themselves to being tracked in order to utilize the service they have signed up for. Furthermore, it is impossible to unsubscribe directly from within the email without also submitting to the third-party tracking.

[ID: A screenshot of the unsubscribe button in the CR newsletter alongside the page HTML which shows that the target destination for the anchor element is a trk.klclick.com page. End ID.]
As a brief aside: Opening the links in a private/incognito window is a good idea, but will not completely prevent your actions from being tracked by the advertiser. My recommendation: install uBlock Origin to warn you of tracking domains (it is a completely free and open-source project available on most major web browsers), and do not click on any links in either of these newsletters until they change their practices.
Now, it may be the case that the newsletters are shipped differently to those residing in California or the EU (if you are from either of these regions please feel free to leave a comment on whether or not this is the case), but ask yourself: does that make this any better? Sure, maybe then Critical Role and Dropout (or rather, the advertising companies they contract with) aren’t technically breaking the law, but it shows that the only thing stopping them from exploiting your personal data is potential legal repercussions, rather than any sort of commitment to your right to privacy. But I expect that the emails are not, in fact, shipping any differently in jurisdictions with more advanced privacy legislation—it wouldn’t be the first time a major tech giant blatantly flaunted EU regulations.
Without an additional browser extension such as uBlock Origin, a user clicking on the links in these emails may not even be aware that they have interacted with the advertising agency at all, let alone what sort of information that agency now has pertaining to them, nor do they have any ability to opt out of this data collection.
For more information about your right to privacy—something that only those living in the EU or California currently have—you can read explanations of the legislations at the following links (take note that these links, and all of the links embedded in this paper, are anchored directly to the destinations they purport to be, and do not sneakily pass through an additional domain before redirecting you):
7/7. Conclusion
Never attribute to malice that which can be adequately explained by neglect, ignorance or incompetence. —Hanlon’s Razor
The important thing to make clear here is this: Even if Critical Role and Dropout are not directly selling or exploiting your personal data, they are still profiting off of it by contracting with, and receiving services from, companies whom I believe are. You may not believe me.
I do not believe that the management teams at Critical Role and Dropout are evil or malicious. Ignorance seems to be the most likely cause of this situation. Someone at some marketing company told them that this type of thing was helpful, necessary, and an industry standard, and they had no reason to doubt that person’s word. Maybe that person had no reason to doubt the word of the person who told them. Maybe there are a few people in that chain, maybe quite a few. I do not expect everyone running a company to be an expert in this stuff (hell, I’m nowhere close to being an expert in this stuff myself—I only happened to notice this at all because of a browser extension I just happened to have installed to block ads), but what I do expect is that they change their behaviour when the potential harms of their actions have been pointed out to them, which is why I have taken the time to write this.
PS. To the employees of Critical Role and Dropout
It is my understanding that these corporations were both founded with the intention of being socially responsible alongside turning a profit. By using services like the ones described above, you are, however unintentionally, profiting off of the personal datasets of your fans that are being compiled and exploited without their informed consent. You cannot say, implicitly or explicitly, “We’re not like those other evil companies! We care about more than just extracting as much money from our customers as possible!” while at the same time utilizing these services, and it is my hope that after reading this you will make the responsible choice and stop doing so.
Thank you for reading,
era
Originally Published: 23 May 2024
Last Updated: 28 May 2024
#critical role#dimension 20#dropout#dropout tv#brennan lee mulligan#sam reich#critical role campaign 3#cr3#midst podcast#candela obscura#make some noise#game changer#smarty pants#very important people#web security#data privacy#gdpr#ccpa#open letter
10 notes
·
View notes