#avast software
Explore tagged Tumblr posts
Text
State of the Hill
SHORT VERSION: I will continue to write and post recaps to go with Ian's SH2 streams whether I can get my own video to work or not. We will get creative if necessary.
LONG VERSION: Things are not going great right now! The OBS recording software has decided that it hates me personally. I have been spending hours every day beating my head against this wall, sleeping on it overnight, coming back with some new approach, and hitting brick again.
It started as "the game's frame rate has become unplayable but OBS records that fine," and then I updated everything on earth, and the game looked great in person but the recordings were fucked. Shaky, jumpy. (Note: The cinematics record just fine. It's only the gameplay.)
At this point, I am working through my list of fix options. I have rolled back the NVIDIA drivers; despite NVIDIA fucking the game community over, that doesn't seem to be the problem. Downloading the Streamlabs plugin did not help; I only want to record, not stream, so I am going to uninstall Streamlabs (which seems very nice otherwise, but I don't need it), probably uninstall and reinstall an earlier version of OBS, and then, somewhere along the way, see if Avast Security is blocking something. Yes, I have enough storage. Yes, I have enough RAM. Yes, I have turned the computer off and on again. Yes, it is plugged in. I reinstalled a repair version of Windows at one point, so please believe I am trying everything I can think of. And when I run out of things to think of, I will look into other game + voice recording software, and we will start the troubleshooting cycle all over again (which is fitting, I guess).
(Actually, I tried repairing Windows because something happened to Microsoft Edge along the way--Microsoft Dot Com swears it's already installed, but every time I accidentally click some Windows news link I didn't want, it tells me there's no app to open an "edge link." Like, I didn't want or use Edge anyway, but it alarms me that I didn't choose for it to go away. But the OBS saga was happening before Edge went missing, so it's probably unrelated.)
Anyway, my point is, I am reducing my tech panic by telling myself that I will not have the fifth Silent Hill 2 video ready next week, and that this is okay, because you will have Ian's stream/upload if you want to see the full gameplay, and I will simply continue writing the recap as usual. I can still play the game, after all, and I have my muttered practice recordings from right before the frame rate got untenable. I know what I want to talk about for a recording that never actually happened. I can get any screenshots I want, and I can link to existing clips of the cutscenes.
The reason writing this is important to me, even if only three people read it, is because I have spent a lot of my life not finishing things. I am going to continue to look for any way possible to keep going with the means that I have (here's hoping I don't fall off a cliff, or my house sink into the sea) (I am nowhere near a sea) (that won't stop my luck). I am just giving myself over to radical acceptance of this bullshit situation--while I do continue trying to fix it, yes--so that any outcome is okay. I will sit and talk into Voice Memo on my phone like I am telling you a goddamn campfire story if there comes a time when that is all that remains to me. And then, of course, there's [gestures at everything] going on and maybe video games are not something we will care or worry about in the near future. My point is, I find that when I start putting a Plan B out into the universe, I find that Plan A often works itself out instead, and if it doesn't: I still have Plan B.
(Look where I was in the game. Look at it. I was so hype. If I weren't emotionally repressed I would cry. Universe, don't you want me to record this? Universe, pls.)

35 notes
·
View notes
Text
Anne Kustritz’s Identity, Community, and Sexuality in Slash Fan Fiction
Anne Kustritz’s new book, Identity, Community, and Sexuality in Slash Fan Fiction: Pocket Publics has just been released by Routledge (2024). You might know Kustritz, a scholar of fan cultures and transmedia storytelling, from her early essay “Slashing the Romance Narrative,” in the Journal of American Culture (2003) or maybe from some of her more recent work on transmedia and serial storytelling. But this new book is an exciting addition to the fan studies canon, and Fanhackers readers might be particularly interested, because the book “explores slash fan fiction communities during the pivotal years of the late 1990s and the early 2000s as the practice transitioned from print to digital circulation,”--which is the era that a lot of the fans involved in the creation of the OTW came from. As I noted in my book blurb, “While there has been an explosion of fan studies scholarship in the last two decades, we haven't had an ethnography of fan fiction communities since the early 1990s. Kustritz's Pocket Publics rectifies that, documenting the generation of slash fans who built much of fandom's infrastructure and many of its community spaces, both on and off the internet. This generation has had an outsized impact on contemporary fan cultures, and Kustritz shows how these fans created an alternative and subcultural public sphere: a world of their own.”
Kustritz doesn’t just analyze and contextualize fandom, she also describes her own experiences as a participant-observer, and these might resonate with a lot of fans (especially Fanhackers-reading fans!) Early on in the book, Kustritz describes her how her own early interest in fandom blurred between the personal and the academic:
Because I began studying slash only a year after discovering fandom on-line, my interest has always been an intricate tangle of pleasure in the texts themselves, connection to brilliantly creative women, and fascination with intersections between fan activities and academic theory. I may now disclaim my academic identity as an interdisciplinary scholar with concentrations in media anthropology and cultural studies and begin to pinpoint my fan identity as a bifictional multifandom media fan; however, I only gradually became aware of and personally invested in these categories as I grew into them. This section defines the scope of the online observation period that preceded the active interview phase of this research. In so doing it also examines the messy interconnections between my academic and fannish interests and identities. Trying to pick apart what portion of my choices derived from fannish pleasure and which from academic interest helps to identify the basic internal tensions and categories that slash fan fiction communities relied upon to define themselves, the pressures exerted upon these systems by the digital migration, and complications in academic translation of fannish social structures.
Later in the book, Kustritz discusses how fans have organized and advocated for themselves as a public; in particular, there’s a fascinating chapter about the ways in which fandom has adopted and transformed the figure of the pirate to forge new ways of thinking about copyright and authorship. If the OTW was formed to argue that making fanworks is a legitimate activity, the figure of the pirate signifies a protest against the law and a refusal to be shamed by it:
[F]ans also use the figure of the pirate to make arguments that validate some fan activities and consign others to illegitimacy. At the urging of several friends involved with slash, I attended my first non-slash focused science fiction and fantasy convention in the summer of 2004. The program schedule announced a Sunday morning panel discussion provocatively titled “Avast, Matey: The Ethics of Pirating Movies, Music, and Software” with the subheading “Computers today can distribute [more] intellectual property than ever before--not always legally. Is it ever okay to copy, download, and/or distribute media? Sorry, ladies, none of us will be dressed as Captain Jack Sparrow.” The panel’s subheading, which obliquely warned away both lusty women and pirates, led a small contingent of slash fans to shake off Saturday night’s convention revelries unreasonably early and implement a plan of their own for Sunday’s panel. As many fan conventions encourage costumes, known as “cosplay,” one of my friends and research participants happened to have been dressed as Captain Jack Sparrow of Pirates of the Caribbean that weekend, so I entered the piracy panel with Captain Jack and a motley crew of slashers, some of them intent upon commandeering the discussion.
The clash that followed exemplifies a structural fault line between various types of fan communities regarding their shared norms and beliefs about copyright law, the relationship between fans and producers, and appropriate fan behavior.
If you want to find out how this clash played out–well, you’ll just have to read the book. 😀
–Francesca Coppa, Fanhackers volunteer
#fanhackers#author:francescacoppa#anne kustritz#early digital fandom#slash#piracy#fannish culture clashes
127 notes
·
View notes
Text
33 notes
·
View notes
Text
weekly reminder to update your software
i get it - it's annoying, it takes time and maybe there are changes (be it design or functionality... looking at you, discord) to the software you don't like. i get it. hell, these are things that annoy me too.
BUT it's also a security thing. old software and operating systems (windows or ios for example) is a safety risk. especially when you have it linked to accounts with your personal or financial information. cybercrime is no joke!! and your PC, laptop, smartphone or tablet can be virus-infected without you even noticing.
how can i be safe? i hear you asking. well, built-in security in operating systems is oftentimes enough - you don't need bloatware like avast or mcaffee or whatever they're called. they use unnecessary resources and can make older hardware slow.
but - and here is the catch - these built-in security measures (and even 3rd party software) are only safe when they're also kept UP TO DATE. windows defender needs to be updated with windows updates. so do them now, if you have been putting them up.
#ugh sorry. needed to get this out of my system#bc i talked to a friend a few days ago and they said their partner hates to update a software bc the developers changed the design and i -#- wanted to pull my own eyes out#i'm a IT specialist in training and i work at a place with high secruity levels#you have no idea how hard and labour intensive it is to keep data safe these days#it's ridiculous#addi.txt
5 notes
·
View notes
Text
Btw can anyone suggest me names for my future Hacker's memory team? I named everyone in my Cyber sleuth file bad internet/tech related things so on the other save i wanna name them good internet/tech related things. So far the only ideas i have are AntiVirus, Avast, BackupFile, FireWall, SystemReboot and Software.
This is the Cyber sleuth team btw
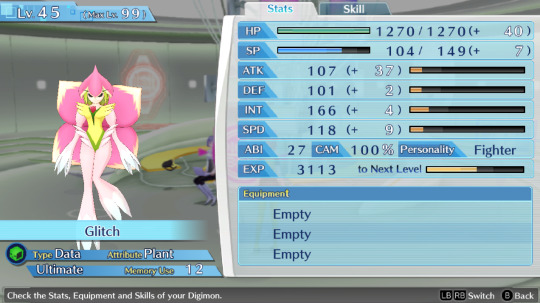
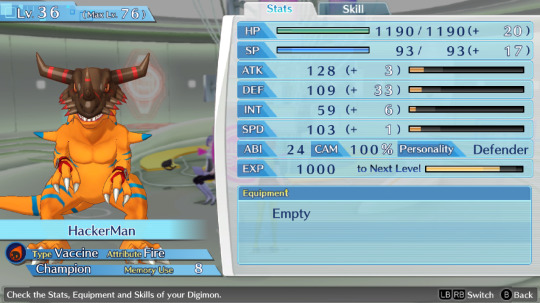
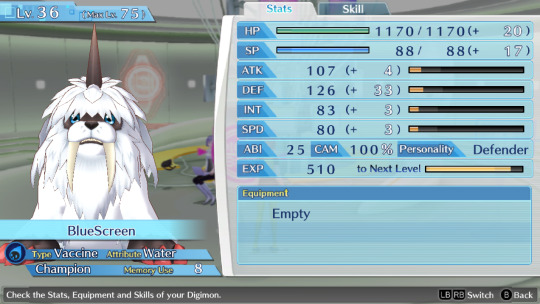

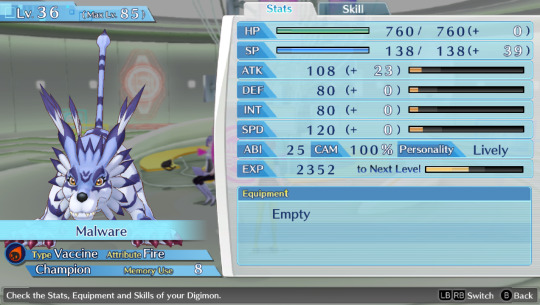
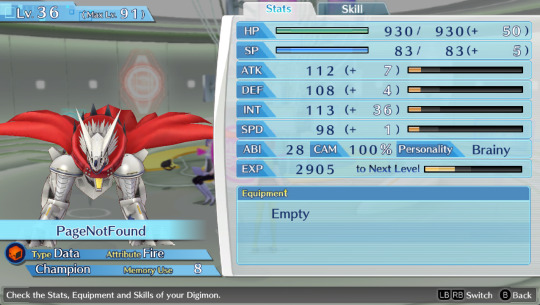
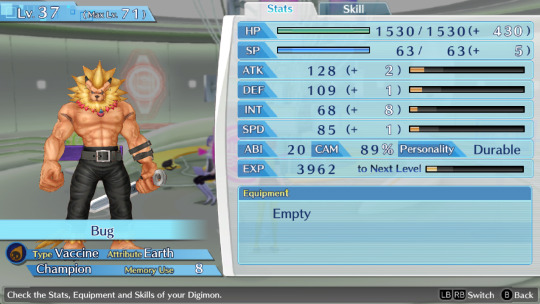
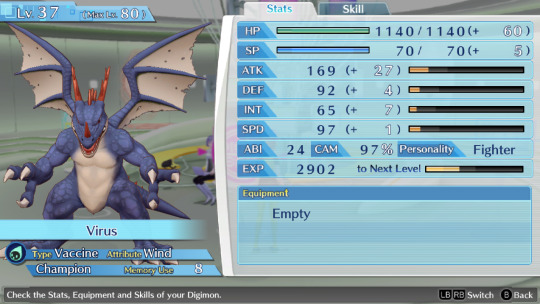


Honorable mention to these two, whom I've used for some time but didn't kept as permanent team members + BlueyBoy who breaks naming conventions because he's just BlueyBoy and i use him to grind levels on random digimons to evolve and fill out the encyclopedia.
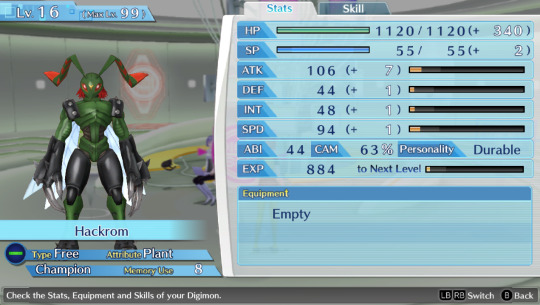
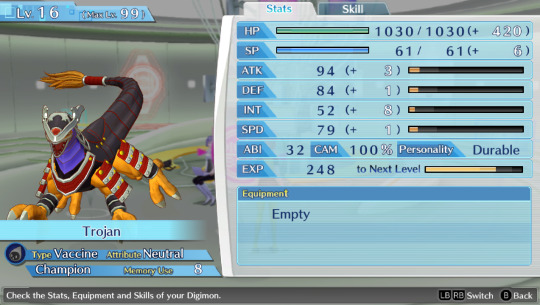
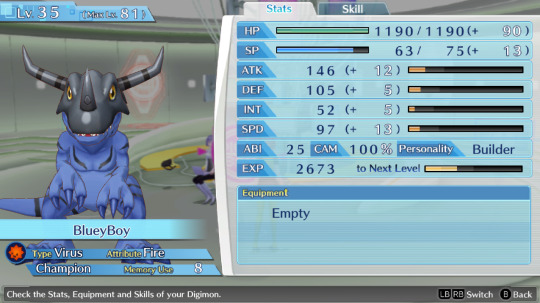
#Hackroom and Trojan are hella low level now because i evolved them into something random for completion reasons#and evolved them back into these forms#they used to be at level 26 and 29 respectively#also isn't it stupid how i have all the hacking names in the cyber sleuth team#and the nice tech names on the HACKER'S memory file? i love that honestly#hyena ramblings#digimon#digimon story cyber sleuth#Lilamon#GeoGreymon#Ikkakumon#Gaoamon#Garurumon#BaoHuckmon#Leomon#Coredramon#Lekismon#Raremon#ginryumon#stingmon#greymon blue
4 notes
·
View notes
Text
Avast was collecting users' browser information from 2014 to 2020, then selling it to more than 100 other companies through a since-shuttered entity known as Jumpshot, according to the Federal Trade Commission. Under a proposed recent FTC order (PDF), Avast must pay $16.5 million, which is "expected to be used to provide redress to consumers," according to the FTC.
If you were an Avast user between 2014 and 2020, you might get some cash. Also worth noting: Jumpshot was owned by Avast.
There's two ways to look at this:
Now that Avast is on the FTC's radar, they're gonna be on their best behavior (i.e. safe), or
Now that Avast has been revealed to be unscrupulous, why trust them ever again?
I personally stopped using Avast because their stuff is so freekin invasive and loud. Always popping up with false positives and/or needless "your system is clean!" messages in between ads to buy more Avast products & services. The final nail was when it tried to quarantine my software development tools.
What an aggravating product.
14 notes
·
View notes
Text
Full album in free download here https://archive.org/details/invisible-illusion-escaping-the-memory-hole

It's a little tribute to The Internet Archive. After being back next to October's hack, it was no more possible to download since the beginning of december. But it's fix now (perhaps not fully stable, one day or another the servers could be overloaded, but most of time it work perfectly) So I'll add the posts which were on internet archive and then the radio may continue to around mid of january... For those who do not know how to download on the internet archive it's not tricky just choice the format at right and click to on the spear to dwonload, alsothere is a link like this one https://archive.org/compress/invisible-illusion-escaping-the-memory-hole/formats=VBR%20MP3&file=/invisible-illusion-escaping-the-memory-hole.zip to do so on most of the netlabel releases. Last but not least Avast do many wrong detections these days, I've sent them several reports for audio file and JPG detected as malicious software !!! If anything like this happens don't worry there is no risk. I've been with avast free edition so many years but now with that kind of stuff I may change for AVG free version wich is as good and less intrusive.
Also still one day to take action as musician or fan "Over 600 musicians are speaking out to demand that major labels drop a lawsuit aimed to destroy the Internet Archive—and for their industry to take concrete actions to realign their actions with the interests of working artists. Sign their open letter now to show your support."
#free music#experimental#experimental music#creative commons#music#freeshare#tumblr music#music tumblr#electro#dark electro#dark wave#electronics#industrial music#witch house#weirdcore#noisecore#strange core#internet archive#the internet archive#internet radio#radio#free radio#underground music#trip hop#noise#copyleft#dark ambient#electropunk#synth punk
3 notes
·
View notes
Text
i mean re: ipad kids not actually learning how to use computers i think its a combination of 1) kids not being born knowing how to do stuff like i didn't know a lot of basic stuff abt computers until i started using mine to do enough things that i ended up with weird bugs i needed to fix, 2) software companies intentionally making their systems more opaque so the user has less and less obvious agency and things are more hidden, like the only reason i even know that you can clean the junk left over from installs beyond deleting the application is that i spent two days trying to figure it out after i installed avast on bad info, and 3) straight up misinformation from the most prominent people in the tech industry and new tech worshippers in general. like if you trust apple tech support you'll end up believing a lot of wrong things about how computers work but you won't realize that unless you happen to be told by someone or find a search result of people discussing the real mechanics. i do think the solution is better computer education but for the moment youre not gonna get that or even get that considered in schools, what you need to do is teach that 12 yr old how to use qbittorrent yourself.
#c.paradisi#which has kinda always been how it worked? i had computer classes in school and they were not comprehensive#my main education was as stated 1) figuring out how to fix my computer when i fucked it up and 2) people telling me i could do X if i did#ALSO the majority of people arent that tech savvy. they know how to send emails and download files but thats about it#they have for generations this isnt new and as stated tech companies have a vested interest in keeping it that way
10 notes
·
View notes
Text
Sims 4 CC Finds + Resources (Newbie Friendly!)

(Disclosure: This blog contains affiliate links. As an Amazon Associate I earn from qualifying purchases.)
To be able to open links in a new tab, you can view this post on my website: https://desireluxe.com/sims-4-cc-finds-and-resources/ | Tumblr didn't give me the option to do that.
CC Newbie? Check out "Sims 4 CC + Mods Installation Tutorial Zoom Replay | How to Download CC": https://youtu.be/L_9f_Uwe1_Q
Places to find CC:
Tumblr:
https://desireccfinds.tumblr.com/
https://emilyccfinds.tumblr.com/
https://public-ccfinds.tumblr.com/
https://mmfinds.tumblr.com/
Pinterest:
https://www.pinterest.com/DesireLuxe/sims-4-cc-more/
https://www.pinterest.com/nintensims/cc-finds/
Websites:
https://www.thesimsresource.com/
https://sims4.aroundthesims3.com/index.shtml
https://www.simsfinds.com/
Websites with CC finds, news, and mod updates:
https://snootysims.com/
https://simscommunity.info/
Reshade + Gshade Presets:
https://desireccfinds.tumblr.com/tagged/gshade-preset
https://desireccfinds.tumblr.com/
https://www.pinterest.com/DesireLuxe/sims-4-cc-more/gshadereshade-presets/
Other Places:
Search "Sims 4 CC Finds" on Twitter and TikTok
Important Chrome Extensions:
AdBlock (use the one with the hand inside the stop sign): https://chromewebstore.google.com/detail/adblock-%E2%80%94-best-ad-blocker/gighmmpiobklfepjocnamgkkbiglidom?utm_source=ext_app_menu
You only need the next two if the link is behind ad*fly:
Ad*fly Skipper: https://chromewebstore.google.com/detail/adfly-skipper/obnfifcganohemahpomajbhocfkdgmjb?utm_source=ext_app_menu
FastForward (previously Universal Bypass: https://fastforward.team/
Important Software:
Avast Antivirus: https://www.avast.com/index#pc
WinRar (necessary for unzipping RAR files; it's actually forever free, you only have to buy it if you want to make a donation): https://www.win-rar.com/start.html?&L=0
7zip (makes it easier to unzip zip files): https://www.7-zip.org/
If you'd like your website/blog added, you can message me! You can also tag me in your CC posts to be re-blogged. I only reblog free CC; so if it's still in early access, I will wait until it's public to reblog it.
My Gaming PC Specs: I have 100 GB of CC and all packs minus some of the kits.
Prebuilt PC brand: CyberPowerPC Graphics Card: NVIDIA GeForce RTX 3070 Processor: Intel Core i7-11700KF RAM: 32 GB
Recommended Gaming PCs on Amazon
Pink Gaming Setup Essentials on Amazon
View more stuff on my Amazon storefront (pink finds, home finds, etc)
9 notes
·
View notes
Text
“For years, the antivirus software company harvested information from users’ web browsers without their consent.
“Avast, the cybersecurity software company, is facing a $16.5 million fine after it was caught storing and selling customer information without their consent. The Federal Trade Commission (FTC) announced the fine on Thursday and said that it’s banning Avast from selling user data for advertising purposes.
“From at least 2014 to 2020, Avast harvested user web browsing information through its antivirus software and browser extension, according to the FTC’s complaint. This allowed it to collect data on religious beliefs, health concerns, political views, locations, and financial status. The company then stored this information “indefinitely” and sold it to over 100 third parties without the knowledge of customers, the complaint says.”
5 notes
·
View notes
Text
Malicious Actors Exploit YouTube for Phishing, Malware, and Scams

YouTube has emerged as a new battleground for cybercriminals to launch phishing attacks, distribute malware, and propagate fraudulent investment schemes, according to a report from security researchers at Avast. The report sheds light on the growing threat of malicious actors exploiting the popular video platform to target unsuspecting users. Deepfake Videos and Cryptocurrency Scams Researchers specifically highlighted using Lumma and RedLine malware for phishing, scam landing pages, and malicious software distribution. YouTube acts as a traffic distribution system, directing users to these malicious sites and pages, and supporting scams of varying severity. Moreover, the report uncovered a concerning rise in deepfake videos on the platform. These realistic but fake videos mislead viewers with fabricated people or events, spreading disinformation. Avast found multiple accounts with over 50 million subscribers each that were compromised and hijacked to spread cryptocurrency scams reliant on deepfake videos. These videos feature fake comments to deceive other viewers and contain malicious links. Exploitation Tactics on YouTube The researchers observed five different ways YouTube can be exploited by threat actors: - Personalized phishing emails to YouTube creators, proposing fake collaboration opportunities to gain trust before sending malicious links. - Compromised video descriptions containing malicious links, tricking users into downloading malware. - Hijacking YouTube channels and repurposing them to spread threats like cryptocurrency scams. - Exploitation of software brands and legitimate-looking domains with fraudulent websites loaded with malware. - Creating videos using social engineering techniques that guide users to allegedly helpful tools that are malware in disguise.
Protective Measures and Cybersecurity Awareness
Avast credits its scanning capabilities with protecting more than 4 million YouTube users in 2023 and approximately 500,000 users in the first quarter of this year from these threats. Trevor Collins, a WatchGuard Network security engineer, emphasizes the importance of companies and security leaders preparing their teams and organizations for these threats. "Regular education is essential. Make people aware that there are scammers out there doing this," Collins says. "In addition, train and reassure them that it's OK to notify either their security team or other people within the company if they've gotten an unusual request — for instance, to provide login credentials, move money, or go buy a bunch of gift cards — before acting on it." As cybercriminals continue to exploit popular platforms like YouTube, individuals and organizations must remain vigilant, prioritize cybersecurity awareness, and implement robust security measures to protect themselves from phishing, malware, and scams. Read the full article
3 notes
·
View notes
Text
first and last lines
Rules: Go through your last 5 completed works and share the first and last lines without context
Thanks for tagging me @ewelinakl! I'm breaking the rules and only doing my last fics that are over 500 words.
5. dreams of loneliness
OFMD, aromantic Izzy
First Line: “You’re jealous,” Ed accuses.
Last Line: “I don’t want to be left behind.”
4. if/else
OFMD, Izzy & Ed, modern software developer AU
First Line: Ed’s lying across his couch, limbs askew, when Izzy lets himself in.
Last Line: He takes a sip from his cup, fiddles with his ankle monitor, and says, “Did he show you the hidden marmalade room?”
3. Maybe We Should Try That
OFMD, Izzy & Ed, Night at the Museum AU
First Line: It was like waking up from a long nap.
Last Line: He had a second chance.
2. Holding Out For A Hero
OFMD, Stede/Ed & Izzy, superhero AU comedy
First Line: “Avast ye, villains! For it is I, the Gentleman Hero, here to—” he was cut off as he stumbled backwards, his cape caught in the door of the Revengemobile.
Last Line: And lo, reads the journal entry for that night, written by Stede’s long-suffering biographer Lucius, the Gentleman Hero, using only his wit and ingenuity, forever foiled the schemes of the dastardly yet handsome supervillain Blackbeard, and his unnamed, tiny flunky.
1. Blush
OFMD, Izzy & Stede, genderswap AU
First Line: Stede fucking Bonnet.
Last Line: Stede fucking Bonnet.
7 notes
·
View notes
Quote
2月の月例セキュリティ更新でWindowsカーネルの脆弱性「CVE-2024-21338」が修正された。当初マイクロソフトは悪用は確認されていないとしていたが、北朝鮮の攻撃グループ「Lazarus」がゼロデイ攻撃に悪用していたことがわかった。 「CVE-2024-21338」は、「AppLockerドライバ」に判明した権限昇格の脆弱性。共通脆弱性評価システム「CVSSv3.1」のベーススコアは「7.8」、重要度は4段階中上から2番目にあたる「重要(Important)」とレーティングされている。 現地時間2月13日に公開した月例セキュリティ更新で修正した。公開当初、悪用は確認されていないとしていたが、同脆弱性を2023年8月に報告したというAvast Softwareは、脆弱性の詳細について説明し、ゼロデイ攻撃に悪用されていたことを明らかにした。 Avastは、北朝鮮が関与するとされる攻撃グループ「Lazarus」が悪用していたと指摘���同グループが展開するルートキット「FudModule」のあらたなバージョンに悪用コードが実装されていた。 同マルウェアは、セキュリティ対策ソフトウェアである「Microsoft Defender」「CrowdStrike Falcon」「HitmanPro」など保護されたプロセスを停止しようとしていたという。また一連の攻撃において、リモートよりアクセスを行うためのあらたな「RAT」なども確認されている。
【セキュリティ ニュース】2月修正のWindows脆弱性、北朝鮮グループがゼロデイ攻撃に悪用(1ページ目 / 全2ページ):Security NEXT
2 notes
·
View notes
Note
Cybersecurity related
After uninstalling Avast because it was frying up my pc , I instead installed a not so CPU consuming antivirus called Bitdefender , but recently I found out that Advanced System Care has also been eating all of my CPU
Do you consider it safe to uninstall it since I already have an antivirus and CCleaner?
This is not really my field of expertise, and somebody who is like a security consultant would know best. But it sounds like "advanced system care" is more of an optimization tool than a cybersecurity thing, so I can't imagine it would pose a risk in that regard to get rid of it.
But again, maybe I'm missing something here, because I don't use that software and have never worked in cybersecurity. My studies weren't particularly practical in that sense.
2 notes
·
View notes
Text
Parental Control Software Market Size, Share, Trends, Growth Opportunities and Competitive Outlook
Global Parental Control Software Market - Size, Share, Demand, Industry Trends and Opportunities
Global Parental Control Software Market, By Device Type (Smart Phones, Computers, and Video Games, Tablets, Digital Television, and Others), Deployment (On-Premise, and Cloud), Pricing (Free, Basic, Premium, and Others), Function (Time Management, Gaming, App Management, Web Access, Program-Specific Controls, Cyber Security, and Others), Operating System (Android, IOS, Windows, Linux, macOS, and Others), End User (Educational Institutes, Residential, and Commercial) – Industry Trends
Access Full 350 Pages PDF Report @
**Segments**
- On the basis of type, the global parental control software market can be segmented into traditional parental control software and smartphone parental control software. The traditional parental control software includes solutions that offer monitoring and filtering features for desktops and laptops, while smartphone parental control software caters to the monitoring and control of activities on mobile devices.
- Based on deployment mode, the market can be divided into cloud-based and on-premises parental control software. Cloud-based solutions offer flexibility and scalability, allowing users to access the software from anywhere, while on-premises options provide more control over data and customization.
- In terms of application, the parental control software market can be categorized into educational institutes, residential, and commercial sectors. Educational institutes use these tools to protect students from exposure to harmful online content, while residential and commercial users utilize parental control software to safeguard family members or employees from inappropriate material.
**Market Players**
- Some of the key players in the global parental control software market are NortonLifeLock Inc., Net Nanny, McAfee, Qustodio LLC, Kaspersky Lab, Mobicip, LLC, Symantec Corporation, Verizon Communications Inc., Avast Software s.r.o., and AVG Technologies. These companies offer a range of parental control solutions with features such as content filtering, screen time management, app blocking, and geofencing to address the diverse needs of users in the market.
The global parental control software market is witnessing significant growth as the awareness of online safety and the need for monitoring children's digital activities continue to rise. With the proliferation of digital devices and the increasing presence of children online, parents and guardians are turning to parental control software to ensure a safer online experience. The market is also being driven by regulatory compliance requirements in educational settings and the growing demand for effective monitoring solutions in households and businesses.
Cloud-based parental control software is gaining traction due to its convenience and accessibility, allowing users to manage settings remotely and across multiple devices. On-premisesThe global parental control software market is experiencing a surge in demand driven by the increasing awareness of online safety and the growing need for monitoring children's digital activities. As more children access digital devices and spend time online, parents and guardians are recognizing the importance of implementing parental control software to keep their children safe from harmful content and activities. The market is also benefiting from regulatory requirements in educational settings, where the protection of students from online threats is of paramount importance.
One of the key trends in the parental control software market is the shift towards cloud-based solutions. Cloud-based parental control software offers users greater flexibility and convenience by allowing them to access and manage settings from anywhere, using any device with an internet connection. This not only simplifies the management of parental controls but also ensures that parents can monitor their children's activities in real-time, even when they are away from home. The scalability of cloud-based solutions also makes them suitable for households with multiple devices and users, further driving their adoption in the market.
On-premises parental control software, on the other hand, provides users with a greater sense of control over their data and customization options. Some users, especially those who are concerned about data privacy and security, prefer on-premises solutions as they keep all monitoring activities within their own network. While on-premises solutions may require more upfront investment and maintenance, they appeal to users who prioritize data sovereignty and customization capabilities.
The parental control software market is highly competitive, with a number of key players vying for market share. Companies such as NortonLifeLock Inc., Net Nanny, McAfee, and Kaspersky Lab offer a diverse range of parental control solutions with features such as content filtering, screen time management, app blocking, and geofencing. These companies are continuously innovating their products to meet the evolving needs of users and stay ahead in the competitive landscape.
In conclusion, the global parental control software market is expected to continue its growth trajectory as the importance of online safety and digital monitoring remains**Global Parental Control Software Market Analysis**
- **Global Parental Control Software Market, By Device Type (Smart Phones, Computers, and Video Games, Tablets, Digital Television, and Others)** The parental control software market is segmented by the type of device on which the software can be installed. This segmentation is crucial as different devices may require specific features and functionalities to ensure effective monitoring and control of online activities. With the increasing use of smartphones, tablets, computers, and other digital devices by children, the demand for parental control software across different devices is on the rise.
- **Deployment (On-Premise, and Cloud)** The deployment mode of parental control software plays a significant role in the market as it determines how users can access and manage the software. On-premise solutions offer a more localized approach to monitoring and control, while cloud-based solutions provide greater flexibility and accessibility. The choice of deployment mode depends on factors such as data privacy concerns, customization requirements, and the need for remote management capabilities.
- **Pricing (Free, Basic, Premium, and Others)** The pricing strategy of parental control software can influence its adoption and market penetration. Free versions may attract a larger user base but may lack advanced features, while premium packages offer a comprehensive set of functionalities for a higher cost. The pricing segmentation caters to different user preferences, from those looking for basic monitoring to users seeking advanced parental control features.
- **Function (Time Management, Gaming, App Management, Web Access,
TABLE OF CONTENTS
Part 01: Executive Summary
Part 02: Scope of the Report
Part 03: Research Methodology
Part 04: Market Landscape
Part 05: Pipeline Analysis
Part 06: Market Sizing
Part 07: Five Forces Analysis
Part 08: Market Segmentation
Part 09: Customer Landscape
Part 10: Regional Landscape
Part 11: Decision Framework
Part 12: Drivers and Challenges
Part 13: Market Trends
Part 14: Vendor Landscape
Part 15: Vendor Analysis
Part 16: Appendix
Core Objective of Parental Control Software Market:
Every firm in the Parental Control Software Market has objectives but this market research report focus on the crucial objectives, so you can analysis about competition, future market, new products, and informative data that can raise your sales volume exponentially.
Size of the Parental Control Software Market and growth rate factors.
Important changes in the future Parental Control Software Market.
Top worldwide competitors of the Market.
Scope and product outlook of Parental Control Software Market.
Developing regions with potential growth in the future.
Tough Challenges and risk faced in Market.
Global Parental Control Software top manufacturers profile and sales statistics.
Browse Trending Reports:
Digital Holographic Display Market Robotics End Effector Market Outboard Engines Market Connected Solutions for Oil and Gas Market Biotechnological Plant Breeding and CRISPR Plants Market Canned Tuna Market Zinc Methionie Chelates Market Watches Market Shoe Rack Market Capsule Hotel Market Chickpea Protein Market Weill-Marchesani Syndrome Market
About Data Bridge Market Research:
Data Bridge set forth itself as an unconventional and neoteric Market research and consulting firm with unparalleled level of resilience and integrated approaches. We are determined to unearth the best market opportunities and foster efficient information for your business to thrive in the market. Data Bridge endeavors to provide appropriate solutions to the complex business challenges and initiates an effortless decision-making process.
Contact Us:
Data Bridge Market Research
US: +1 614 591 3140
UK: +44 845 154 9652
APAC : +653 1251 975
Email: [email protected]
0 notes
Text
Sr Software Engineer - Mobile
We’re more than just a company; we’re a global leader in digital safety. With a strong commitment to ensuring that everyone can navigate the digital world securely, we unite the best minds and cutting-edge technology through our family of brands: Norton, Avast, LifeLock, Avira, AVG, ReputationDefender, and CCleaner. Together, we protect over 500 million people worldwide. Our workplace is built on…
0 notes