#aws s3 monitoring
Explore tagged Tumblr posts
Text
Amazon S3 Bucket Feature Tutorial Part2 | Explained S3 Bucket Features for Cloud Developer
Full Video Link Part1 - https://youtube.com/shorts/a5Hioj5AJOU Full Video Link Part2 - https://youtube.com/shorts/vkRdJBwhWjE Hi, a new #video on #aws #s3bucket #features #cloudstorage is published on #codeonedigest #youtube channel. @java #java #awsc
Amazon Simple Storage Service (Amazon S3) is an object storage service that offers industry-leading scalability, data availability, security, and performance. Customers of all sizes and industries can use Amazon S3 to store and protect any amount of data. Amazon S3 provides management features so that you can optimize, organize, and configure access to your data to meet your specific business,…

View On WordPress
#amazon s3 bucket features#amazon s3 features#amazon web services#aws#aws cloud#aws cloudtrail#aws cloudwatch#aws s3#aws s3 bucket#aws s3 bucket creation#aws s3 bucket features#aws s3 bucket tutorial#aws s3 classes#aws s3 features#aws s3 interview questions and answers#aws s3 monitoring#aws s3 tutorial#cloud computing#s3 consistency#s3 features#s3 inventory report#s3 storage lens#simple storage service (s3)#simple storage service features
0 notes
Note
any podcast recommendations for guys Going Through It. im a sucker for whump and i’ve already listened to TMA and Malevolent sooo
Fiction Podcasts: Characters Going Through It / Experiencing the Horrors
Gore warning for most, here's 15 to get you started:
I am in Eskew: (Horror) David Ward is arguably the Guy Going Through It. Stories from a man living in something that very much wants to be a city, and a private investigator who was, in her words, "hired to kill a ghost". Calmly recounted stories set to Eskew's own gentle, persistent rain. The audio quality's a bit naff but the writing is spectacular. If you like the writing, also check out The Silt Verses, which is a brilliant show by the same creators.
VAST Horizon: (Sci-Fi, Horror, Thriller/Suspense Elements) And Dr. Nolira Ek is arguably the Gal Going Through it. An agronomist wakes from cryo to discover the ship she's on is dead in the water, far from their destination, and seemingly empty, barring the ship's malfunctioning AI, and an unclear reading on the monitors. I think you'll like this one. Great sound design, amazing acting, neat worldbuilding, and plenty of awful situations.
Dining in the Void: (Horror, Sci-Fi) So, the initial pacing on this one is a little weird, but stick with it. A collection of notable people are invited to a dinner aboard a space station, and find not only are they trapped there, but they're on a timer until total station destruction: unless they can figure out who's responsible. And there's someone else aboard to run a few games, just to make things more interesting. The games are frequently torturous. If that wasn't clear.
The White Vault: (Horror) By the same creators as VAST Horizon, this one follows a group sent to a remote arctic research base to diagnose and repair a problem. Trapped inside by persistant snow and wind, they discover something very interesting below their feet. Really well made show. The going through it is more spread out but there's a lot of it happening.
Archive 81: (Horror, Weird Fiction, Mystery and Urban Fantasy Elements) A young archivist is commissioned to digitize a series of tapes containing strange housing records from the 1990s. He has an increasingly bad time. Each season is connected but a bit different, so if S1 (relatively short) doesn't catch your ear, hang in for S2. You've got isolation, degredation of relationships, dehumanisation, and a fair amount of gore. And body horror on a sympathetic character is so underdone.
The Harrowing of Minerva Damson: (Fantasy, Horror) In an alternate version of our own world with supernatural monsters and basic magic, an order of women knights dedicated to managing such problems has survived all the way to the world wars, and one of them is doing her best with what she's got in the middle of it all.
SAYER: (Horror, Sci-Fi) How would you like to be the guy going through it? A series of sophisticated AI guide you soothingly through an array of mundane and horrible tasks.
WOE.BEGONE: (Sci-Fi) I don't keep up with this one any more, but I think Mike Walters goes through enough to qualify it. Even if it's frequently his own fault. A guy gets immediately in over his head when he begins to play an augmented reality game of entirely different sort. Or, the time-travel murder game.
Janus Descending: (Sci-Fi, Horror, Tragedy) A xenobiologist and a xenoanthropologist visit a dead city on a distant world, and find something awful. You hear her logs first-to-last, and his last-to-first, which is interesting framing but also makes the whole thing more painful. The audio equivalent of having your heart pulled out and ditched at the nearest wall. Listen to the supercut.
The Blood Crow Stories: (Horror) A different story every season. S1 is aboard a doomed cruise ship set during WWII, S2 is a horror western, S3 is cyberpunk with demons, and S4 is golden age cinema with a ghostly influence.
Mabel: (Supernatural, Horror, Fantasy Elements) The caretaker of a dying woman attempts to contact her granddaughter, leaving a series of increasingly unhinged voicemails. Supernatural history transitioning to poetic fae lesbian body horror.
Jar of Rebuke: (Supernatural) An amnesiac researcher with difficulties staying dead investigates strange creatures, eats tasty food, and even makes a few friends while exploring the town they live in. A character who doesn't stay dead creates a lot of scenarios for dying in interesting ways
The Waystation: (Sci-Fi, Horror) A space station picks up an odd piece of space junk which begins to have a bizzare effect on some of the crew. The rest of it? Doesn't react so well to this spreading strangeness. Some great nailgun-related noises.
Station Blue: (Psychological Horror) A drifting man takes a job as a repair technician and maintenance guy for an antarctic research base, ahead of the staff's arrival. He recounts how he got there, as his time in the base and some bizzare details about it begin to get to him. People tend to either quite like this one or don't really get the point of it, but I found it a fascinating listen.
The Hotel: (Horror) Stories from a "Hotel" which kills people, and the strange entities that make it happen. It's better than I'm making it sound, well-made with creative deaths, great sound work, and a strange staff which suffer as much as the guests. Worth checking out.
223 notes
·
View notes
Text
so part of me wants to blame this entirely on wbd, right? bloys said he was cool with the show getting shopped around, so assuming he was telling the truth (not that im abt to start blindly trusting anything a CEO says lol), that means it’s not an hbo problem. and we already know wbd has an awful track record with refusing to sell their properties—altho unlike coyote v acme, s3 of ofmd isn’t a completed work and therefore there isn’t the same tax writeoff incentive to bury the thing. i just can’t see any reason to hold on to ofmd except for worrying about image, bc it would be embarrassing if they let this show go with such a devoted fanbase and recognizable celebrities and it went somewhere else and did really well (which it would undoubtedly do really well, we’ve long since proven that). it feels kinda tinfoil hat of me to making assumptions abt what’s going on in wbd behind the scenes, but i also feel like there are hints that i’m onto something w my suspicions: suddenly cracking down on fan merch on etsy doesn’t seem like something a studio looking to sell their property would bother with, and we know someone was paying to track the viewing stats on ofmd’s bbc airing, which isn’t finished yet, so i’d expect whoever is monitoring that to not make a decision abt buying ofmd until the s2 finale dropped.
but also i think part of me just wants there to be a clear villain in the situation. it’s kinda comforting to have a face to blame, a clear target to shake my fist at. but the truth is that the entire streaming industry is in the shitter. streaming is not pulling in the kind of profit that investors were promised, and we’re seeing the bubble that was propped up w investor money finally start to pop. studios aren’t leaving much room in their budgets for acquiring new properties, and they’re whittling down what they already have. especially w the strikes last year, they’re all penny pinching like hell. and that’s much a much harder thing to rage against than just one studio or one CEO being shitty. that’s disheartening in a way that’s much bigger and more frightening than if there was just one guy to blame.
my guess is that the truth of the situation is probably somewhere in the middle. wbd is following the same shitty pattern they’ve been following since the merger, and it’s just a hard time for anyone trying to get their story picked up by any studio. ofmd is just one of many shows that are unlucky enough to exist at this very unstable time for the tv/streaming industry.
when i think abt it that way, tho, i’m struck by how lucky we are that ofmd even got to exist at all. if the wbd merger had happened a year earlier, or if djenks and tw tried to pitch this show a year later, there’s no way this show would’ve been made. s1 was given the runtime and the creative freedom needed to tell the story the way the showrunners wanted to, and the final product benefited from it so much that it became a huge hit from sheer gay word of mouth. and for all the imperfections with s2—the shorter episode order, the hard 30 minute per episode limit, the last-minute script changes, the finale a butchered mess of the intended creative vision—the team behind ofmd managed to tell a beautiful story despite the uphill battle they undoubtedly were up against. they ended the season with the main characters in a happy place. ed and stede are together, and our last shot of ed isn’t of him sobbing uncontrollably (like i rlly can’t stress enough how much i would have never been able to acknowledge the existence of this show again if s1 was all we got)
like. y’all. we were this close to a world where ofmd never got to exist. for me, at least, the pain of an undue cancellation is worth getting to have this story at all. so rather than taking my comfort in the form of righteous anger at david zaslav or at wbd or at the entire streaming industry as a whole, i’m trying to focus on how lucky i am to get to have the show in the first place.
bc really, even as i’m reeling in grief to know this is the end of the road for ofmd, a part of me still can’t quite wrap my head around that this show is real. a queer romcom about middle-aged men, a rejection of washboard abs and facetuned beauty standards, a masterful deconstruction and criticism of toxic masculinity, well-written female characters who get to shine despite being in a show that is primarily about manhood and masculinity, diverse characters whose stories never center around oppression and bigotry, a casually nonbinary character, violent revenge fantasies against oppressors that are cathartic but at the same time are not what brings the characters healing and joy, a queer found family, a strong theme of anti colonialism throughout the entire show. a diverse writers room that got to use their perspectives and experiences to inform the story. the fact that above all else, this show is about the love story between ed and stede, which means the character arcs, the thoughts, the feelings, the motivations, the backstories, and everything else that make up the characters of ed and stede are given the most focus and the most care.
bc there rlly aren’t a lot of shows where a character like stede—a flamboyant and overtly gay middle-aged man who abandoned his family to live his life authentically—gets to be the main character of a romcom, gets to be the hero who the show is rooting for.
and god, there definitely aren’t a lot of shows where a character like ed—a queer indigenous man who is famous, successful, hyper-competent, who feels trapped by rigid standards of toxic hypermasculinity, who yearns for softness and gentleness and genuine interpersonal connection and vulnerability, whose mental health struggles and suicidal intentions are given such a huge degree of attention and delicate care in their depiction, who messes up and hurts people when he’s in pain but who the show is still endlessly sympathetic towards—gets to exist at all, much less as the romantic lead and the second protagonist of the show.
so fuck the studios, fuck capitalism, fuck everything that brought the show to an end before the story was told all the way through. because the forces that are keeping s3 from being made are the same forces that would’ve seen the entire show canceled before it even began. s3 is canceled, and s2 suffered from studio meddling, but we still won. we got to have this show. we got to have these characters. there’s been so much working against this show from the very beginning but here we are, two years later, lives changed bc despite all odds, ofmd exists. they can’t take that away from us. they can’t make us stop talking abt or stop caring abt this show. i’m gonna be a fan of this show til the day i die, and the studios hate that. they hate that we care about things that don’t fit into their business strategy, they hate that not everyone will blindly consume endless IP reboots and spin-offs and cheap reality tv.
anyway i dont rlly have a neat way to end this post. sorta just rambling abt my feelings. idk, i know this sucks but im not rlly feeling like wallowing in it. i think my gratitude for the show is outweighing my grief and anger, at least for right now. most important thing tho is im not going anywhere. and my love for this show is certainly not fucking going anywhere.
#ofmd#our flag means death#save ofmd#s3 renewal hell#txt#mine#og#studio crit#edward teach#stede bonnet#gentlebeard
324 notes
·
View notes
Video
youtube
Complete Hands-On Guide: Upload, Download, and Delete Files in Amazon S3 Using EC2 IAM Roles
Are you looking for a secure and efficient way to manage files in Amazon S3 using an EC2 instance? This step-by-step tutorial will teach you how to upload, download, and delete files in Amazon S3 using IAM roles for secure access. Say goodbye to hardcoding AWS credentials and embrace best practices for security and scalability.
What You'll Learn in This Video:
1. Understanding IAM Roles for EC2: - What are IAM roles? - Why should you use IAM roles instead of hardcoding access keys? - How to create and attach an IAM role with S3 permissions to your EC2 instance.
2. Configuring the EC2 Instance for S3 Access: - Launching an EC2 instance and attaching the IAM role. - Setting up the AWS CLI on your EC2 instance.
3. Uploading Files to S3: - Step-by-step commands to upload files to an S3 bucket. - Use cases for uploading files, such as backups or log storage.
4. Downloading Files from S3: - Retrieving objects stored in your S3 bucket using AWS CLI. - How to test and verify successful downloads.
5. Deleting Files in S3: - Securely deleting files from an S3 bucket. - Use cases like removing outdated logs or freeing up storage.
6. Best Practices for S3 Operations: - Using least privilege policies in IAM roles. - Encrypting files in transit and at rest. - Monitoring and logging using AWS CloudTrail and S3 access logs.
Why IAM Roles Are Essential for S3 Operations: - Secure Access: IAM roles provide temporary credentials, eliminating the risk of hardcoding secrets in your scripts. - Automation-Friendly: Simplify file operations for DevOps workflows and automation scripts. - Centralized Management: Control and modify permissions from a single IAM role without touching your instance.
Real-World Applications of This Tutorial: - Automating log uploads from EC2 to S3 for centralized storage. - Downloading data files or software packages hosted in S3 for application use. - Removing outdated or unnecessary files to optimize your S3 bucket storage.
AWS Services and Tools Covered in This Tutorial: - Amazon S3: Scalable object storage for uploading, downloading, and deleting files. - Amazon EC2: Virtual servers in the cloud for running scripts and applications. - AWS IAM Roles: Secure and temporary permissions for accessing S3. - AWS CLI: Command-line tool for managing AWS services.
Hands-On Process: 1. Step 1: Create an S3 Bucket - Navigate to the S3 console and create a new bucket with a unique name. - Configure bucket permissions for private or public access as needed.
2. Step 2: Configure IAM Role - Create an IAM role with an S3 access policy. - Attach the role to your EC2 instance to avoid hardcoding credentials.
3. Step 3: Launch and Connect to an EC2 Instance - Launch an EC2 instance with the IAM role attached. - Connect to the instance using SSH.
4. Step 4: Install AWS CLI and Configure - Install AWS CLI on the EC2 instance if not pre-installed. - Verify access by running `aws s3 ls` to list available buckets.
5. Step 5: Perform File Operations - Upload files: Use `aws s3 cp` to upload a file from EC2 to S3. - Download files: Use `aws s3 cp` to download files from S3 to EC2. - Delete files: Use `aws s3 rm` to delete a file from the S3 bucket.
6. Step 6: Cleanup - Delete test files and terminate resources to avoid unnecessary charges.
Why Watch This Video? This tutorial is designed for AWS beginners and cloud engineers who want to master secure file management in the AWS cloud. Whether you're automating tasks, integrating EC2 and S3, or simply learning the basics, this guide has everything you need to get started.
Don’t forget to like, share, and subscribe to the channel for more AWS hands-on guides, cloud engineering tips, and DevOps tutorials.
#youtube#aws iamiam role awsawsaws permissionaws iam rolesaws cloudaws s3identity & access managementaws iam policyDownloadand Delete Files in Amazon#IAMrole#AWS#cloudolus#S3#EC2
2 notes
·
View notes
Text
Centralizing AWS Root access for AWS Organizations customers
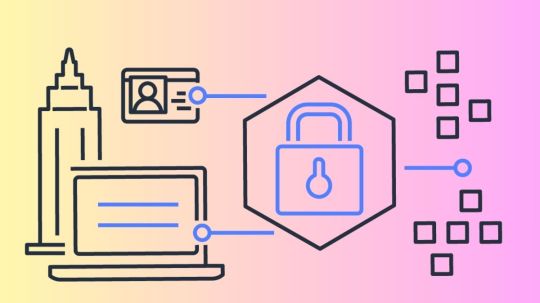
Security teams will be able to centrally manage AWS root access for member accounts in AWS Organizations with a new feature being introduced by AWS Identity and Access Management (IAM). Now, managing root credentials and carrying out highly privileged operations is simple.
Managing root user credentials at scale
Historically, accounts on Amazon Web Services (AWS) were created using root user credentials, which granted unfettered access to the account. Despite its strength, this AWS root access presented serious security vulnerabilities.
The root user of every AWS account needed to be protected by implementing additional security measures like multi-factor authentication (MFA). These root credentials had to be manually managed and secured by security teams. Credentials had to be stored safely, rotated on a regular basis, and checked to make sure they adhered to security guidelines.
This manual method became laborious and error-prone as clients’ AWS systems grew. For instance, it was difficult for big businesses with hundreds or thousands of member accounts to uniformly secure AWS root access for every account. In addition to adding operational overhead, the manual intervention delayed account provisioning, hindered complete automation, and raised security threats. Unauthorized access to critical resources and account takeovers may result from improperly secured root access.
Additionally, security teams had to collect and use root credentials if particular root actions were needed, like unlocking an Amazon Simple Storage Service (Amazon S3) bucket policy or an Amazon Simple Queue Service (Amazon SQS) resource policy. This only made the attack surface larger. Maintaining long-term root credentials exposed users to possible mismanagement, compliance issues, and human errors despite strict monitoring and robust security procedures.
Security teams started looking for a scalable, automated solution. They required a method to programmatically control AWS root access without requiring long-term credentials in the first place, in addition to centralizing the administration of root credentials.
Centrally manage root access
AWS solve the long-standing problem of managing root credentials across several accounts with the new capability to centrally control root access. Two crucial features are introduced by this new capability: central control over root credentials and root sessions. When combined, they provide security teams with a safe, scalable, and legal method of controlling AWS root access to all member accounts of AWS Organizations.
First, let’s talk about centrally managing root credentials. You can now centrally manage and safeguard privileged root credentials for all AWS Organizations accounts with this capability. Managing root credentials enables you to:
Eliminate long-term root credentials: To ensure that no long-term privileged credentials are left open to abuse, security teams can now programmatically delete root user credentials from member accounts.
Prevent credential recovery: In addition to deleting the credentials, it also stops them from being recovered, protecting against future unwanted or unauthorized AWS root access.
Establish secure accounts by default: Using extra security measures like MFA after account provisioning is no longer necessary because member accounts can now be created without root credentials right away. Because accounts are protected by default, long-term root access security issues are significantly reduced, and the provisioning process is made simpler overall.
Assist in maintaining compliance: By centrally identifying and tracking the state of root credentials for every member account, root credentials management enables security teams to show compliance. Meeting security rules and legal requirements is made simpler by this automated visibility, which verifies that there are no long-term root credentials.
Aid in maintaining compliance By systematically identifying and tracking the state of root credentials across all member accounts, root credentials management enables security teams to prove compliance. Meeting security rules and legal requirements is made simpler by this automated visibility, which verifies that there are no long-term root credentials. However, how can it ensure that certain root operations on the accounts can still be carried out? Root sessions are the second feature its introducing today. It provides a safe substitute for preserving permanent root access.
Security teams can now obtain temporary, task-scoped root access to member accounts, doing away with the need to manually retrieve root credentials anytime privileged activities are needed. Without requiring permanent root credentials, this feature ensures that operations like unlocking S3 bucket policies or SQS queue policies may be carried out safely.
Key advantages of root sessions include:
Task-scoped root access: In accordance with the best practices of least privilege, AWS permits temporary AWS root access for particular actions. This reduces potential dangers by limiting the breadth of what can be done and shortening the time of access.
Centralized management: Instead of logging into each member account separately, you may now execute privileged root operations from a central account. Security teams can concentrate on higher-level activities as a result of the process being streamlined and their operational burden being lessened.
Conformity to AWS best practices: Organizations that utilize short-term credentials are adhering to AWS security best practices, which prioritize the usage of short-term, temporary access whenever feasible and the principle of least privilege.
Full root access is not granted by this new feature. For carrying out one of these five particular acts, it offers temporary credentials. Central root account management enables the first three tasks. When root sessions are enabled, the final two appear.
Auditing root user credentials: examining root user data with read-only access
Reactivating account recovery without root credentials is known as “re-enabling account recovery.”
deleting the credentials for the root user Eliminating MFA devices, access keys, signing certificates, and console passwords
Modifying or removing an S3 bucket policy that rejects all principals is known as “unlocking” the policy.
Modifying or removing an Amazon SQS resource policy that rejects all principals is known as “unlocking a SQS queue policy.”
Accessibility
With the exception of AWS GovCloud (US) and AWS China Regions, which do not have root accounts, all AWS Regions offer free central management of root access. You can access root sessions anywhere.
It can be used via the AWS SDK, AWS CLI, or IAM console.
What is a root access?
The root user, who has full access to all AWS resources and services, is the first identity formed when you create an account with Amazon Web Services (AWS). By using the email address and password you used to establish the account, you can log in as the root user.
Read more on Govindhtech.com
#AWSRoot#AWSRootaccess#IAM#AmazonS3#AWSOrganizations#AmazonSQS#AWSSDK#News#Technews#Technology#Technologynews#Technologytrends#Govindhtech
2 notes
·
View notes
Text
How can you optimize the performance of machine learning models in the cloud?
Optimizing machine learning models in the cloud involves several strategies to enhance performance and efficiency. Here’s a detailed approach:

Choose the Right Cloud Services:
Managed ML Services:
Use managed services like AWS SageMaker, Google AI Platform, or Azure Machine Learning, which offer built-in tools for training, tuning, and deploying models.
Auto-scaling:
Enable auto-scaling features to adjust resources based on demand, which helps manage costs and performance.
Optimize Data Handling:
Data Storage:
Use scalable cloud storage solutions like Amazon S3, Google Cloud Storage, or Azure Blob Storage for storing large datasets efficiently.
Data Pipeline:
Implement efficient data pipelines with tools like Apache Kafka or AWS Glue to manage and process large volumes of data.
Select Appropriate Computational Resources:
Instance Types:
Choose the right instance types based on your model’s requirements. For example, use GPU or TPU instances for deep learning tasks to accelerate training.
Spot Instances:
Utilize spot instances or preemptible VMs to reduce costs for non-time-sensitive tasks.
Optimize Model Training:
Hyperparameter Tuning:
Use cloud-based hyperparameter tuning services to automate the search for optimal model parameters. Services like Google Cloud AI Platform’s HyperTune or AWS SageMaker’s Automatic Model Tuning can help.
Distributed Training:
Distribute model training across multiple instances or nodes to speed up the process. Frameworks like TensorFlow and PyTorch support distributed training and can take advantage of cloud resources.
Monitoring and Logging:
Monitoring Tools:
Implement monitoring tools to track performance metrics and resource usage. AWS CloudWatch, Google Cloud Monitoring, and Azure Monitor offer real-time insights.
Logging:
Maintain detailed logs for debugging and performance analysis, using tools like AWS CloudTrail or Google Cloud Logging.
Model Deployment:
Serverless Deployment:
Use serverless options to simplify scaling and reduce infrastructure management. Services like AWS Lambda or Google Cloud Functions can handle inference tasks without managing servers.
Model Optimization:
Optimize models by compressing them or using model distillation techniques to reduce inference time and improve latency.
Cost Management:
Cost Analysis:
Regularly analyze and optimize cloud costs to avoid overspending. Tools like AWS Cost Explorer, Google Cloud’s Cost Management, and Azure Cost Management can help monitor and manage expenses.
By carefully selecting cloud services, optimizing data handling and training processes, and monitoring performance, you can efficiently manage and improve machine learning models in the cloud.
2 notes
·
View notes
Text
The Accidental Unlocking: 6 Most Common Causes of Data Leaks

In the ongoing battle for digital security, we often hear about "data breaches" – images of malicious hackers breaking through firewalls. But there's a more subtle, yet equally damaging, threat lurking: data leaks.
While a data breach typically implies unauthorized access by a malicious actor (think someone kicking down the door), a data leak is the accidental or unintentional exposure of sensitive information to an unauthorized environment (more like leaving the door unlocked or a window open). Both lead to compromised data, but their causes and, sometimes, their detection and prevention strategies can differ.
Understanding the root causes of data leaks is the first critical step toward building a more robust defense. Here are the 6 most common culprits:
1. Cloud Misconfigurations
The rapid adoption of cloud services (AWS, Azure, GCP, SaaS platforms) has brought immense flexibility but also a significant security challenge. Misconfigured cloud settings are a leading cause of data leaks.
How it leads to a leak: Leaving storage buckets (like Amazon S3 buckets) publicly accessible, overly permissive access control lists (ACLs), misconfigured firewalls, or default settings that expose services to the internet can inadvertently expose vast amounts of sensitive data. Developers or administrators might not fully understand the implications of certain settings.
Example: A company's customer database stored in a cloud bucket is accidentally set to "public read" access, allowing anyone on the internet to view customer names, addresses, and even financial details.
Prevention Tip: Implement robust Cloud Security Posture Management (CSPM) tools and enforce Infrastructure as Code (IaC) to ensure secure baselines and continuous monitoring for misconfigurations.
2. Human Error / Accidental Exposure
Even with the best technology, people make mistakes. Human error is consistently cited as a top factor in data leaks.
How it leads to a leak: This can range from sending an email containing sensitive customer data to the wrong recipient, uploading confidential files to a public file-sharing service, losing an unencrypted laptop or USB drive, or simply discussing sensitive information in an insecure environment.
Example: An employee emails a spreadsheet with salary information to the entire company instead of just the HR department. Or, a developer accidentally pastes internal API keys into a public forum like Stack Overflow.
Prevention Tip: Implement comprehensive, ongoing security awareness training for all employees. Enforce strong data handling policies, promote the use of secure communication channels, and ensure devices are encrypted.
3. Weak or Stolen Credentials
Compromised login credentials are a golden ticket for attackers, leading directly to data access.
How it leads to a leak: This isn't always about a direct "hack." It could be due to:
Phishing: Employees falling for phishing emails that trick them into revealing usernames and passwords.
Weak Passwords: Easily guessable passwords or reusing passwords across multiple services, making them vulnerable to "credential stuffing" attacks if one service is breached.
Lack of MFA: Even if a password is stolen, Multi-Factor Authentication (MFA) adds a critical second layer of defense. Without it, stolen credentials lead directly to access.
Example: An attacker obtains an employee's reused password from a previous data breach and uses it to log into the company's internal file sharing system, exposing sensitive documents.
Prevention Tip: Enforce strong, unique passwords, mandate MFA for all accounts (especially privileged ones), and conduct regular phishing simulations to train employees.
4. Insider Threats (Negligent or Malicious)
Sometimes, the threat comes from within. Insider threats can be accidental or intentional, but both lead to data exposure.
How it leads to a leak:
Negligent Insiders: Employees who are careless with data (e.g., leaving a workstation unlocked, storing sensitive files on personal devices, bypassing security protocols for convenience).
Malicious Insiders: Disgruntled employees or those motivated by financial gain or espionage who intentionally steal, leak, or destroy data they have legitimate access to.
Example: A disgruntled employee downloads the company's entire customer list before resigning, or an employee stores client financial data on an unsecured personal cloud drive.
Prevention Tip: Implement robust access controls (least privilege), conduct regular audits of user activity, establish strong data loss prevention (DLP) policies, and foster a positive work environment to mitigate malicious intent.
5. Software Vulnerabilities & Unpatched Systems
Software is complex, and bugs happen. When these bugs are security vulnerabilities, they can be exploited to expose data.
How it leads to a leak: Unpatched software (operating systems, applications, network devices) contains known flaws that attackers can exploit to gain unauthorized access to systems, where they can then access and exfiltrate sensitive data. "Zero-day" vulnerabilities (unknown flaws) also pose a significant risk until they are discovered and patched.
Example: A critical vulnerability in a web server application allows an attacker to bypass authentication and access files stored on the server, leading to a leak of customer information.
Prevention Tip: Implement a rigorous patch management program, automate updates where possible, and regularly conduct vulnerability assessments and penetration tests to identify and remediate flaws before attackers can exploit them.
6. Third-Party / Supply Chain Risks
In today's interconnected business world, you're only as secure as your weakest link, which is often a third-party vendor or partner.
How it leads to a leak: Organizations share data with numerous vendors (SaaS providers, IT support, marketing agencies, payment processors). If a third-party vendor suffers a data leak due to their own vulnerabilities or misconfigurations, your data that they hold can be exposed.
Example: A marketing agency storing your customer contact list on their internal server gets breached, leading to the leak of your customer data.
Prevention Tip: Conduct thorough vendor risk assessments, ensure strong data protection clauses in contracts, and continuously monitor third-party access to your data. Consider implementing secure data sharing practices that minimize the amount of data shared.
The common thread among these causes is that many data leaks are preventable. By understanding these vulnerabilities and proactively implementing a multi-layered security strategy encompassing technology, processes, and people, organizations can significantly reduce their risk of becoming the next data leak headline.
0 notes
Text
🌐 DevOps with AWS – Learn from the Best! 🚀 Kickstart your tech journey with our hands-on DevOps with AWS training program led by expert Mr. Ram – starting 23rd June at 7:30 AM (IST). Whether you're an aspiring DevOps engineer or an IT enthusiast looking to upscale, this course is your gateway to mastering modern software delivery pipelines.
💡 Why DevOps with AWS? In today's tech-driven world, companies demand faster deployments, better scalability, and secure infrastructure. This course combines core DevOps practices with the powerful cloud platform AWS, giving you the edge in a competitive market.

📘 What You’ll Learn:
CI/CD Pipeline with Jenkins
Version Control using Git & GitHub
Docker & Kubernetes for containerization
Infrastructure as Code with Terraform
AWS services for DevOps: EC2, S3, IAM, Lambda & more
Real-time projects with monitoring & alerting tools
📌 Register here: https://tr.ee/3L50Dt
🔍 Explore More Free Courses: https://linktr.ee/ITcoursesFreeDemos
Be future-ready with Naresh i Technologies – where expert mentors and project-based learning meet career transformation. Don’t miss this opportunity to build smart, deploy faster, and grow your DevOps career.
#DevOps#AWS#DevOpsEngineer#NareshIT#CloudComputing#CI_CD#Jenkins#Docker#Kubernetes#Terraform#OnlineLearning#CareerGrowth
0 notes
Text
Unlock Your Future with DevOps AWS Courses in Hyderabad – IntelliQ IT

In today’s rapidly transforming IT industry, DevOps has emerged as a must-have skillset for professionals aiming to bridge the gap between development and operations. Hyderabad, being a top IT hub in India, is witnessing a growing demand for skilled DevOps professionals. If you're exploring top DevOps institutes in Hyderabad or looking to upskill with DevOps AWS courses in Hyderabad, you're on the right path to shaping a lucrative and future-proof career.
Why Choose DevOps?
DevOps is a culture and set of practices that bring development and operations teams together to shorten the development life cycle and deliver high-quality software continuously. By adopting DevOps, organizations improve productivity, enhance deployment frequency, and reduce the rate of failure for new releases.
Professionals skilled in DevOps tools like Docker, Kubernetes, Jenkins, Ansible, Terraform, and cloud platforms like AWS are in high demand across startups, MNCs, and tech giants.
The Rising Demand for DevOps and AWS Skills
With companies migrating their infrastructure to the cloud, AWS (Amazon Web Services) has become the leading cloud services provider. Integrating AWS with DevOps tools allows organizations to automate deployments, monitor systems, and scale applications effortlessly.
Learning DevOps with AWS is no longer a luxury—it’s a necessity. Hyderabad’s tech ecosystem demands certified professionals who can seamlessly integrate DevOps methodologies on AWS platforms.
DevOps Institutes in Hyderabad: What to Look For
When searching for DevOps institutes in Hyderabad, it’s essential to consider:
Comprehensive Curriculum: Ensure the course covers both foundational and advanced DevOps tools, cloud integration (especially AWS), CI/CD pipelines, and containerization technologies.
Hands-on Training: Practical exposure through real-time projects, labs, and case studies is critical for mastering DevOps.
Expert Trainers: Learn from certified trainers with industry experience in DevOps and AWS.
Placement Assistance: Institutes that offer resume building, mock interviews, and placement support can significantly boost your job prospects.
IntelliQ IT: A Trusted Name in DevOps AWS Training
Among the top DevOps institutes in Hyderabad, IntelliQ IT stands out for its dedication to delivering industry-relevant training. IntelliQ IT offers a well-structured DevOps AWS course in Hyderabad, designed for freshers, working professionals, and IT enthusiasts. The course not only covers key DevOps tools but also includes extensive AWS integration, ensuring you're job-ready from day one.
With a focus on real-time projects, practical labs, and expert mentorship, IntelliQ IT helps you build the confidence and skills required to crack interviews and succeed in the DevOps domain.
Key Features of IntelliQ IT's DevOps AWS Course:
In-depth coverage of AWS services like EC2, S3, IAM, CloudFormation, and more.
Practical training on CI/CD tools like Jenkins, Git, and Docker.
Live projects simulating real-world scenarios.
100% support in resume building and job placement.
Flexible batch timings including weekend and online classes.
Conclusion
If you are serious about your IT career, enrolling in DevOps AWS courses in Hyderabad is a smart investment. The synergy of DevOps and AWS is creating unmatched opportunities for tech professionals, and choosing the right institute is the first step toward success.
For quality-driven training with real-time exposure, IntelliQ IT is a name you can trust among the top DevOps institutes in Hyderabad. Take the leap today and power your career with cutting-edge skills in DevOps and AWS.
#devops training in ameerpet#devops training hyderabad#devops in ameerpet#devops course in hyderabad#aws institute in ameerpet
1 note
·
View note
Text
Your Path to Cloud Certification Starts with AWS Training in Pune

In the era of digital transformation, cloud computing is no longer a luxury—it's a necessity. Whether you’re starting your career or aiming to upgrade your technical skill set, one certification stands out among the rest: AWS. And where better to start than with expert-led AWS Training in Pune at WebAsha Technologies?
Why AWS Certification Matters in Today’s IT Landscape
Amazon Web Services (AWS) dominates the cloud market with its reliable, scalable, and flexible platform, which is used by millions of businesses worldwide. Earning an AWS certification demonstrates your ability to design, deploy, and manage cloud-based solutions—a skill set that is increasingly sought after by top employers.
Benefits of Getting AWS Certified
Gain global recognition and credibility
Unlock higher-paying job opportunities
Strengthen your foundational and advanced cloud knowledge
Become eligible for roles like Cloud Architect, DevOps Engineer, and more
Stand out in interviews with verified cloud skills
Kickstart Your Journey with AWS Training in Pune
If you're in Pune—a rapidly growing IT and tech hub—there’s no better time or place to begin your cloud learning path. With AWS Training in Pune offered by WebAsha Technologies, you’ll learn directly from industry experts and gain hands-on experience that prepares you for real-world cloud environments.
Why Choose WebAsha Technologies?
At WebAsha Technologies, we don’t just teach cloud computing—we build cloud professionals. Our training goes beyond theory, providing you with the tools and confidence to earn your certification and succeed in the workforce.
What Makes Our AWS Training Unique?
Certified and experienced trainers
Real-time projects and lab sessions
Updated course content aligned with AWS exams
Interview preparation and placement support
Flexible batch timings for working professionals and students
What You Will Learn in Our AWS Training Program
Our structured curriculum ensures you’re not just exam-ready—but job-ready.
Core Modules Include:
Introduction to Cloud Computing and AWS Ecosystem
AWS Compute Services (EC2, Lambda)
Storage Solutions (S3, EBS, Glacier)
Networking and Security (VPC, IAM)
Database Management (RDS, DynamoDB)
Monitoring and Auto-Scaling
Deployment and CI/CD with AWS Tools
Hands-on Projects and Mock Certification Tests
Who Should Enroll in AWS Training in Pune?
Whether you’re a fresher or an experienced professional, our training is tailored for:
Aspiring Cloud Engineers and Architects
IT Professionals and Developers
DevOps Practitioners
Network and System Administrators
College Students Seeking Future-Proof Careers
Take the First Step Toward AWS Certification
At WebAsha Technologies, our goal is simple—empowering you with in-demand cloud skills through the best-in-class AWS Training in Pune. By the end of this course, you’ll be ready to clear your AWS certification exams and step confidently into the world of cloud computing.
0 notes
Text
Unlocking Agile Operations with the Power of Information Cloud

Introduction
In today’s rapidly changing digital landscape, agility is more than a competitive edge—it’s a business necessity. Organizations must be able to respond quickly to market demands, customer needs, and operational disruptions. This is where the Information Cloud comes in, serving as a dynamic foundation for enabling agile operations across all business functions.
The Information Cloud refers to an integrated, cloud-native environment that centralizes data, applications, and services to support fast, flexible, and scalable decision-making. Whether in manufacturing, logistics, finance, or customer service, an Information Cloud empowers teams with real-time insights, collaboration tools, and data-driven automation—transforming rigid processes into responsive, intelligent workflows.
What Is an Information Cloud?
An Information Cloud is a cloud-based infrastructure that brings together data storage, analytics, and communication platforms under one secure, accessible ecosystem. It supports:
Unified data access across departments
Real-time analytics and reporting
Scalable storage and compute power
Seamless integration with business applications
Intelligent automation and AI-driven decisions
Popular platforms enabling this capability include Microsoft Azure, AWS, Google Cloud, and hybrid solutions that blend private and public cloud environments.
Key Benefits of an Information Cloud for Agile Operations:
Real-Time Decision-Making Access to up-to-the-minute data enables faster, more informed decisions, especially during critical business events or disruptions.
Cross-Team Collaboration Cloud-based collaboration tools and shared data platforms help teams work in sync, regardless of location or department.
Operational Flexibility Agile workflows powered by cloud data ensure your business can pivot quickly—adapting to new demands without the need for infrastructure changes.
Cost Efficiency and Scalability Pay-as-you-go models and elastic scaling ensure you only use the resources you need, reducing operational overhead.
Business Continuity and Resilience Cloud-based backups, failovers, and remote access protect operations from on-premise system failures or disasters.
How to Build an Agile Operation with Information Cloud:
Centralize Data Repositories Unify siloed data sources into cloud platforms like Azure Data Lake, AWS S3, or Google BigQuery.
Adopt Cloud-Native Tools Leverage platforms like Power BI, Tableau, or Looker for real-time dashboards and analytics.
Automate Workflows Use services like Azure Logic Apps, AWS Lambda, or ServiceNow for intelligent process automation.
Enable Self-Service Analytics Empower employees with no-code/low-code tools to build their own reports and automate tasks.
Ensure Governance and Security Use built-in cloud controls to maintain compliance, monitor access, and enforce data privacy.
Real-World Use Cases:
Supply Chain Agility: Real-time tracking and predictive analytics enable proactive inventory management and logistics.
Finance and Accounting: Automated reporting and forecasting tools ensure quick insights into cash flow and profitability.
Healthcare Operations: Unified patient records and predictive care management enhance service delivery.
Smart Manufacturing: IoT sensors and cloud analytics optimize production schedules and machine maintenance.
Best Practices:
Start small with one or two cloud-enabled processes before scaling.
Regularly review data governance policies for security and compliance.
Train staff on cloud collaboration tools and agile methodologies.
Continuously monitor performance using integrated dashboards.
Conclusion:
An Information Cloud is more than just storage—it's the digital nervous system of an agile enterprise. By centralizing data, empowering teams with intelligent tools, and fostering cross-functional collaboration, it enables businesses to move faster, respond smarter, and operate more efficiently. Whether you're building smart factories, modernizing back-office functions, or enhancing customer experiences, the Information Cloud equips your organization to lead with agility in a digital-first world.
0 notes
Text
Mastering AWS DevOps Certification on the First Attempt: A Professional Blueprint
Embarking on the journey to AWS DevOps certification can be both challenging and rewarding. Drawing on insights from Fusion Institute’s guide, here’s a polished, professional article designed to help you pass the AWS Certified DevOps Engineer – Professional exam on your first try. Read this : AWS Certifications 1. Why AWS DevOps Certification Matters In today’s cloud-driven landscape, the AWS DevOps Professional certification stands as a prestigious validation of your skills in automation, continuous delivery, and agile operations. Successfully earning this credential on your first attempt positions you as a capable leader capable of handling real-world DevOps environments efficiently. 2. Solidify Your Foundation Before diving in, ensure you have: Associate-level AWS certifications (Solutions Architect, Developer, or SysOps) Hands-on experience with core AWS services such as EC2, S3, IAM, CloudFormation A working knowledge of DevOps practices like CI/CD, Infrastructure-as-Code, and Monitoring Start by reviewing key AWS services and reinforcing your familiarity with the terminology and core concepts. 3. Structured Study Path Follow this comprehensive roadmap: Domain Mastery Break down the certification domains and assign focused study sessions to cover concepts like CI/CD pipelines, logging & monitoring, security, deployment strategies, and fault-tolerant systems. Hands-on Practice Create and utilize play environments using CloudFormation, CodePipeline, CodeDeploy, CodeCommit, Jenkins, and Docker to learn by doing. Deep Dives Revisit intricate topics—particularly fault tolerance, blue/green deployments, and operational best practices—to build clarity and confidence. Mock Exams & Cheat Sheets Integrate Revision materials and timed practice tests from reliable sources. Address incorrect answers immediately to reinforce weak spots. Read This for More Info : Top DevOps Tools Conclusion Achieving the AWS DevOps Professional certification on your first attempt is ambitious—but eminently doable with: Strong foundational AWS knowledge Hands-on experimentation and lab work High-quality study resources and structured planning Strategic exam-day execution Fusion Institute’s guide articulates a clear, results-driven path to certification success—mirroring the approach shared by multiple first-time passers. With focused preparation and disciplined study, your AWS DevOps Professional badge is well within reach. Your AWS DevOps Success Starts Here! Join Fusion Institute’s comprehensive DevOps program and get the guidance, tools, and confidence you need to crack the certification on your first attempt. 📞 Call us at 9503397273/ 7498992609 or 📧 email: [email protected]
0 notes
Text
A Data Leak Detection Guide for the Tech Industry in 2025

For the tech industry, data is more than just information; it's the lifeblood of innovation, intellectual property, and customer trust. A data leak – the unauthorized exposure of sensitive information – can be an existential threat, far more insidious than a visible malware attack. Leaks can trickle out slowly, going unnoticed for months, or erupt in a sudden torrent, exposing source code, customer PII, design documents, or proprietary algorithms.
In 2025's hyper-connected, cloud-centric, and API-driven world, detecting these leaks is a unique and paramount challenge. The sheer volume of data, the distributed nature of development, extensive third-party integrations, and the high value of intellectual property make tech companies prime targets. Proactive, multi-layered detection is no longer optional; it's essential for survival.
Here's a comprehensive guide to detecting data leaks in the tech industry in 2025:
1. Advanced Data Loss Prevention (DLP) & Cloud Security Posture Management (CSPM)
Gone are the days of basic keyword-based DLP. In 2025, DLP needs to be intelligent, context-aware, and integrated deeply with your cloud infrastructure.
Next-Gen DLP: Deploy DLP solutions that leverage AI and machine learning to understand the context of data, not just its content. This means identifying sensitive patterns (e.g., PII, PHI, financial data), source code fragments, and intellectual property across endpoints, networks, cloud storage, and collaboration tools. It can detect unusual file transfers, unauthorized sharing, or attempts to print/download sensitive data.
Integrated CSPM: For tech companies heavily invested in cloud, Cloud Security Posture Management (CSPM) is non-negotiable. It continuously monitors your cloud configurations (AWS, Azure, GCP) for misconfigurations that could expose data – like publicly accessible S3 buckets, overly permissive IAM roles, or unencrypted databases. A misconfigured cloud asset is a leak waiting to happen.
2. User and Entity Behavior Analytics (UEBA) Powered by AI
Data leaks often stem from compromised accounts or insider threats. UEBA helps you spot deviations from the norm.
Behavioral Baselines: UEBA tools use AI to learn the "normal" behavior patterns of every user (employees, contractors, customers) and entity (servers, applications) in your environment. This includes typical login times, locations, data access patterns, and resource usage.
Anomaly Detection: When behavior deviates significantly from the baseline – perhaps a developer suddenly downloading gigabytes of source code, an administrator accessing systems outside their routine hours, or a sales executive emailing large customer lists to a personal address – UEBA flags it as a high-risk anomaly, indicating a potential compromise or malicious insider activity.
Prioritized Alerts: UEBA helps cut through alert fatigue by assigning risk scores, allowing security teams to focus on the most critical threats that signify potential data exfiltration.
3. Network Traffic Analysis (NTA) with Deep Packet Inspection
Even if data bypasses endpoint or application controls, it still has to travel across the network. NTA is your eyes and ears for data exfiltration.
Real-time Monitoring: NTA (often part of Network Detection and Response - NDR) continuously monitors all network traffic – internal and external – using deep packet inspection and machine learning.
Exfiltration Signatures: It identifies suspicious patterns like unusually large outbound data transfers, communication with known command-and-control (C2) servers, attempts to tunnel data over non-standard ports, or encrypted traffic to unusual destinations.
Detecting Post-Compromise Movement: NTA is crucial for detecting lateral movement by attackers within your network and the final stages of data exfiltration, often providing the earliest warning of a breach in progress.
4. Specialized Source Code & Repository Monitoring
For the tech industry, source code is the crown jewel, and its accidental or malicious leakage can be catastrophic.
VCS Integration: Deploy solutions that deeply integrate with your Version Control Systems (Git, GitHub, GitLab, Bitbucket) and internal code repositories.
Credential/Secret Detection: These tools scan commits and push requests for hardcoded credentials, API keys, private keys, and other sensitive information that could be accidentally committed and exposed.
IP Leakage Prevention: They monitor for unauthorized pushes to public repositories, large-scale cloning or downloading of proprietary code, and suspicious activity within the development pipeline, acting as a crucial line of defense against intellectual property theft.
5. Dark Web & Open-Source Intelligence (OSINT) Monitoring
Sometimes, the first sign of a leak appears outside your perimeter.
Proactive Reconnaissance: Subscribe to specialized dark web monitoring services that scan illicit marketplaces, forums, paste sites (like Pastebin), and private channels for mentions of your company, leaked credentials (emails, passwords), customer data samples, or even fragments of proprietary code.
Public Repository Scans: Regularly scan public code repositories (like public GitHub, GitLab) for inadvertently exposed internal code or configuration files.
Early Warning System: These services provide crucial early warnings, allowing you to invalidate compromised credentials, assess the scope of a leak, and respond before widespread damage occurs.
6. API Security Monitoring
Modern tech stacks are heavily reliant on APIs. A compromised API can be a wide-open door for data exfiltration.
API Traffic Baselines: Establish baselines for normal API call volumes, types, and user access patterns.
Anomaly Detection: Monitor for unusual API call spikes, unauthorized access attempts (e.g., using stolen API keys), attempts to bypass authentication/authorization, or large data extractions via API calls that deviate from normal usage.
Automated Response: Integrate API security solutions with your WAFs and SIEMs to automatically block malicious API requests or revoke compromised keys.
Beyond Detection: The Response Imperative
Detecting a leak is only half the battle. A well-rehearsed incident response plan is critical. This includes clear steps for containment, investigation, eradication, recovery, and communication. Regular tabletop exercises and simulations are vital to ensure your team can act swiftly and decisively when a leak is detected.
In 2025, data leaks are an existential threat to the tech industry. By adopting a multi-faceted, AI-driven detection strategy, deeply integrated across your infrastructure and focused on both human and technical anomalies, you can significantly enhance your ability to spot and stop leaks before they spiral into full-blown crises, safeguarding your innovation and maintaining customer trust.
0 notes
Text
Defending the Digital Frontier: Key Skills Validated by a Cloud Security Certification
In 2025, the cloud isn't just a technology; it's the new digital frontier, powering everything from innovative startups in Shela, Gujarat, to the mission-critical operations of global enterprises. However, with unprecedented scalability and agility comes a unique and complex set of security challenges. Protecting these dynamic, distributed environments demands a specialized skillset – one that traditional cybersecurity alone often cannot fully address. This is why a cloud security certification has become the gold standard, not just for demonstrating knowledge, but for validating the precise cloud security skills essential for defending this crucial digital landscape.
For professionals looking to build a resilient cloud security career, understanding the core and emerging skills required is paramount. This guide will delve into the critical cloud security skills that are highly valued by employers, explain how a cloud security certification validates these competencies, and highlight why these credentials are indispensable for safeguarding data and applications in the cloud era.
Why Specialized Cloud Security Skills Are Paramount
The intricacies of cloud computing necessitate a distinct approach to security, setting it apart from traditional on-premise models. Here’s why possessing specialized cloud security skills is non-negotiable:
Shared Responsibility Model: Unlike on-premise where organizations control everything, the cloud operates on a shared responsibility model. Understanding this model and knowing whose responsibility it is to secure what (e.g., the cloud provider secures the infrastructure, the customer secures data and configurations) is foundational.
Dynamic and Ephemeral Resources: Cloud environments are highly agile. Virtual machines, containers, and serverless functions are spun up and down rapidly, often automated. Security needs to be integrated into this dynamic flow, requiring skills in automation, Infrastructure as Code (IaC) security, and continuous monitoring.
Distributed Nature: Cloud services are distributed across regions and availability zones. Securing this vast, interconnected network requires different network security paradigms compared to a centralized data center.
Cloud-Native Services and Tools: Each cloud provider (AWS, Azure, GCP) offers a unique suite of security services and tools (e.g., AWS Security Hub, Azure Sentinel, Google Security Command Center). Proficiency in these specific tools is crucial for effective cloud defense.
New Attack Vectors: Cloud environments introduce new attack surfaces, such as misconfigured S3 buckets, insecure APIs, or compromised cloud credentials. Specialized skills are needed to identify and mitigate these specific threats.
Compliance in the Cloud: Regulatory frameworks like India's DPDPA, GDPR, and HIPAA apply to cloud data. Implementing and proving compliance in a dynamic cloud environment requires specific expertise.
Core Cloud Security Skills Validated by Certifications
Leading cloud security certifications are meticulously designed to validate a comprehensive array of cloud security skills that directly address the challenges above. These include:
Identity and Access Management (IAM): This is foundational. You'll master skills in managing user identities, defining roles and permissions, implementing multi-factor authentication (MFA), and ensuring the principle of least privilege across cloud resources. This includes understanding federated identity and integrating corporate directories with cloud IAM.
Network Security in the Cloud: Key skills include designing and securing Virtual Private Clouds (VPCs) or Virtual Networks (VNets), configuring network segmentation, implementing security groups and Network Access Control Lists (NACLs), setting up cloud-native Web Application Firewalls (WAFs), and securing connectivity via VPNs or direct connect services.
Data Protection and Encryption: Validated skills involve implementing encryption for data at rest (e.g., using Key Management Services like AWS KMS, Azure Key Vault, Google Cloud KMS) and in transit (e.g., TLS for API endpoints). Understanding data classification, data loss prevention (DLP) strategies, and secure data storage practices (e.g., secure S3 buckets) is paramount.
Logging, Monitoring, and Auditing: Proficiency in configuring cloud-native logging services (e.g., AWS CloudTrail, Azure Monitor, Google Cloud Logging), integrating with Security Information and Event Management (SIEM) systems, analyzing security logs, and setting up alerts for suspicious activity. Skills in continuous monitoring and threat detection are validated here.
Compliance and Governance: Cloud security certifications validate your ability to understand and implement security controls that meet various regulatory frameworks (like India's DPDPA, ISO 27001, SOC 2). This includes establishing security policies, conducting audits, and ensuring adherence to industry best practices and cloud security posture management (CSPM).
Incident Response and Forensics in the Cloud: Skills in detecting, analyzing, containing, eradicating, and recovering from cloud-specific security incidents. This involves understanding cloud-native forensic tools and processes for investigating breaches in a distributed cloud environment.
Application Security in the Cloud: Validated skills include securing cloud-native applications, understanding API security, securing serverless functions (e.g., AWS Lambda, Azure Functions), and implementing container security (e.g., Docker, Kubernetes).
Cloud Risk Management: Identifying cloud-specific risks, conducting threat modeling exercises for cloud deployments, and implementing appropriate mitigation strategies.
Beyond the Core: Emerging Cloud Security Skills Validated
As cloud technology rapidly evolves, so do the required security skills. Leading cloud security certifications increasingly incorporate and validate expertise in these emerging areas:
DevSecOps Automation: The ability to integrate security into every phase of the software development lifecycle (SDLC) within cloud environments. This includes skills in Infrastructure as Code (IaC) security, security automation tools (e.g., Terraform, CloudFormation), and embedding security into CI/CD pipelines.
Multi-Cloud and Hybrid Cloud Security: As organizations often use more than one cloud provider or integrate cloud with on-premise infrastructure, skills in securing diverse, heterogeneous cloud environments are critical.
AI/ML in Cloud Security: Understanding how Artificial Intelligence and Machine Learning are leveraged for advanced threat detection, anomaly analysis, and automating security operations within cloud platforms.
Serverless and Container Security: Specific expertise in securing these modern, highly scalable, and often ephemeral computing paradigms, which present unique security challenges compared to traditional virtual machines.
Cloud-Native Security Services: Deep proficiency in the rapidly expanding suite of security services offered by each major cloud provider (e.g., AWS WAF, Azure Firewall, Google Cloud Armor).
How Cloud Security Certifications Validate These Skills
A reputable cloud security certification serves as a robust validation mechanism for these essential cloud security skills through:
Rigorous Exam Blueprints: Certifications base their exams on meticulously defined blueprints that directly reflect industry-demanded skills and knowledge areas.
Performance-Based Assessments: Many advanced cloud security certification exams include hands-on labs or simulations, requiring candidates to demonstrate actual proficiency in configuring, troubleshooting, or deploying security controls in a live cloud environment. This is a critical differentiator.
Comprehensive Training Paths: Certification bodies and their authorized training partners offer structured cloud security training and cloud security courses designed to impart these skills, often including extensive lab work and real-world scenarios. EC-Council, for instance, emphasizes practical learning in their programs, such as the C|CSE (Certified Cloud Security Engineer), which includes significant lab components across multiple cloud providers.
Industry Recognition: When a cloud security certification is widely recognized, it means industry experts, employers, and recruiters trust that the certified individual possesses the validated skills to perform effectively.
Choosing the Right Cloud Security Certification to Validate Your Skills
Given the array of skills required, choosing the right cloud security certification is a strategic decision that depends on your current expertise and career aspirations. Whether you're aiming for a foundational understanding or deep specialization, there's a certification designed to validate specific competencies. For a comprehensive overview of the different credentials and their skill validations, exploring the ultimate guide to the best cloud security certifications in 2025 can provide invaluable insights, helping you to align your learning path with the most sought-after skills in the industry.
The Impact of Validated Skills on Your Cloud Security Career
Possessing validated cloud security skills through a cloud security certification has a profound impact on your career:
Increased Employability: You become a highly attractive candidate for roles where cloud security expertise is a prerequisite.
Higher Earning Potential: Employers are willing to pay a premium for certified professionals who can secure their critical cloud assets.
Ability to Tackle Complex Projects: Your validated skills enable you to confidently take on challenging cloud migration, deployment, and security projects.
Contribution to Organizational Resilience: You become a key player in defending your organization against sophisticated cloud-native threats, directly contributing to its business continuity and reputation.
Clear Career Trajectory: Certified skills provide a strong foundation for continuous learning and progression into more advanced and specialized roles within the cloud security career path.
Conclusion
In 2025, defending the digital frontier requires a specialized arsenal of cloud security skills. From mastering Identity and Access Management and network security in the cloud to understanding compliance and automating security controls, these competencies are vital for safeguarding modern digital infrastructure. A cloud security certification serves as the definitive validator of these crucial skills, proving to employers that you possess the practical abilities needed to excel. By strategically acquiring and validating these key cloud security skills, you position yourself at the forefront of a high-demand industry, ready to protect the most valuable assets in the digital age.
0 notes
Text
Is Your Cloud Really Secure? A CISOs Guide to Cloud Security Posture Management

Introduction: When “Cloud-First” Meets “Security-Last”
The cloud revolution has completely transformed how businesses operate—but it’s also brought with it an entirely new battleground. With the speed of cloud adoption far outpacing the speed of cloud security adaptation, many Chief Information Security Officers (CISOs) are left asking a critical question: Is our cloud truly secure?
It’s not a rhetorical query. As we move towards multi-cloud and hybrid environments, traditional security tools and mindsets fall short. What worked on-prem doesn’t necessarily scale—or protect—in the cloud. This is where Cloud Security Posture Management (CSPM) enters the picture. CSPM is no longer optional; it’s foundational.
This blog explores what CSPM is, why it matters, and how CISOs can lead with confidence in the face of complex cloud risks.
1. What Is Cloud Security Posture Management (CSPM)?
Cloud Security Posture Management (CSPM) is a framework, set of tools, and methodology designed to continuously monitor cloud environments to detect and fix security misconfigurations and compliance issues.
CSPM does three key things:
Identifies misconfigurations (like open S3 buckets or misassigned IAM roles)
Continuously assesses risk across accounts, services, and workloads
Enforces best practices for cloud governance, compliance, and security
Think of CSPM as your real-time cloud security radar—mapping the vulnerabilities before attackers do.
2. Why Traditional Security Tools Fall Short in the Cloud
CISOs often attempt to bolt on legacy security frameworks to modern cloud setups. But cloud infrastructure is dynamic. It changes fast, scales horizontally, and spans multiple regions and service providers.
Here’s why old tools don’t work:
No perimeter: The cloud blurs the traditional boundaries. There’s no “edge” to protect.
Complex configurations: Cloud security is mostly about “how” services are set up, not just “what” services are used.
Shadow IT and sprawl: Teams can spin up instances in seconds, often without central oversight.
Lack of visibility: Multi-cloud environments make it hard to see where risks lie without specialized tools.
CSPM is designed for the cloud security era—it brings visibility, automation, and continuous improvement together in one integrated approach.
3. Common Cloud Security Misconfigurations (That You Probably Have Right Now)
Even the most secure-looking cloud environments have hidden vulnerabilities. Misconfigurations are one of the top causes of cloud breaches.
Common culprits include:
Publicly exposed storage buckets
Overly permissive IAM policies
Unencrypted data at rest or in transit
Open management ports (SSH/RDP)
Lack of multi-factor authentication (MFA)
Default credentials or forgotten access keys
Disabled logging or monitoring
CSPM continuously scans for these issues and provides prioritized alerts and auto-remediation.
4. The Role of a CISO in CSPM Strategy
CSPM isn’t just a tool—it’s a mindset shift, and CISOs must lead that cultural and operational change.
The CISO must:
Define cloud security baselines across business units
Select the right CSPM solutions aligned with the organization’s needs
Establish cross-functional workflows between security, DevOps, and compliance teams
Foster accountability and ensure every developer knows they share responsibility for security
Embed security into CI/CD pipelines (shift-left approach)
It’s not about being the gatekeeper. It’s about being the enabler—giving teams the freedom to innovate with guardrails.
5. CSPM in Action: Real-World Breaches That Could Have Been Avoided
Let’s not speak in hypotheticals. Here are a few examples where lack of proper posture management led to real consequences.
Capital One (2019): A misconfigured web application firewall allowed an attacker to access over 100 million customer accounts hosted in AWS.
Accenture (2021): Left multiple cloud storage buckets unprotected, leaking sensitive information about internal operations.
US Department of Defense (2023): An exposed Azure Blob led to the leakage of internal training documents—due to a single misconfiguration.
In all cases, a CSPM solution would’ve flagged the issue—before it became front-page news.
6. What to Look for in a CSPM Solution
With dozens of CSPM tools on the market, how do you choose the right one?
Key features to prioritize:
Multi-cloud support (AWS, Azure, GCP, OCI, etc.)
Real-time visibility and alerts
Auto-remediation capabilities
Compliance mapping (ISO, PCI-DSS, HIPAA, etc.)
Risk prioritization dashboards
Integration with services like SIEM, SOAR, and DevOps tools
Asset inventory and tagging
User behavior monitoring and anomaly detection
You don’t need a tool with bells and whistles. You need one that speaks your language—security.
7. Building a Strong Cloud Security Posture: Step-by-Step
Asset Discovery Map every service, region, and account. If you can’t see it, you can’t secure it.
Risk Baseline Evaluate current misconfigurations, exposure, and compliance gaps.
Define Policies Establish benchmarks for secure configurations, access control, and logging.
Remediation Playbooks Build automation for fixing issues without manual intervention.
Continuous Monitoring Track changes in real time. The cloud doesn’t wait, so your tools shouldn’t either.
Educate and Empower Teams Your teams working on routing, switching, and network security��need to understand how their actions affect overall posture.
8. Integrating CSPM with Broader Cybersecurity Strategy
CSPM doesn’t exist in a vacuum. It’s one pillar in your overall defense architecture.
Combine it with:
SIEM for centralized log collection and threat correlation
SOAR for automated incident response
XDR to unify endpoint, application security, and network security
IAM governance to ensure least privilege access
Zero Trust to verify everything, every time
At EDSPL, we help businesses integrate these layers seamlessly through our managed and maintenance services, ensuring that posture management is part of a living, breathing cyber resilience strategy.
9. The Compliance Angle: CSPM as a Compliance Enabler
Cloud compliance is a moving target. Regulators demand proof that your cloud isn’t just configured—but configured correctly.
CSPM helps you:
Map controls to frameworks like NIST, CIS Benchmarks, SOC 2, PCI, GDPR
Generate real-time compliance reports
Maintain an audit-ready posture across systems such as compute, storage, and backup
10. Beyond Technology: The Human Side of Posture Management
Cloud security posture isn’t just about tech stacks—it’s about people and processes.
Cultural change is key. Teams must stop seeing security as “someone else’s job.”
DevSecOps must be real, not just a buzzword. Embed security in sprint planning, code review, and deployment.
Blameless retrospectives should be standard when posture gaps are found.
If your people don’t understand why posture matters, your cloud security tools won’t matter either.
11. Questions Every CISO Should Be Asking Right Now
Do we know our full cloud inventory—spanning mobility, data center switching, and compute nodes?
Are we alerted in real-time when misconfigurations happen?
Can we prove our compliance posture at any moment?
Is our cloud posture improving month-over-month?
If the answer is “no” to even one of these, CSPM needs to be on your 90-day action plan.
12. EDSPL’s Perspective: Securing the Cloud, One Posture at a Time
At EDSPL, we’ve worked with startups, mid-market leaders, and global enterprises to build bulletproof cloud environments.
Our expertise includes:
Baseline cloud audits and configuration reviews
24/7 monitoring and managed CSPM services
Custom security policy development
Remediation-as-a-Service (RaaS)
Network security, application security, and full-stack cloud protection
Our background vision is simple: empower organizations with scalable, secure, and smart digital infrastructure.
Conclusion: Posture Isn’t Optional Anymore
As a CISO, your mission is to secure the business and enable growth. Without clear visibility into your cloud environment, that mission becomes risky at best, impossible at worst.
CSPM transforms reactive defense into proactive confidence. It closes the loop between visibility, detection, and response—at cloud speed.
So, the next time someone asks, “Is our cloud secure?” — you’ll have more than a guess. You’ll have proof.
Secure Your Cloud with EDSPL Today
Call: +91-9873117177 Email: [email protected] Reach Us | Get In Touch Web: www.edspl.net
Please visit our website to know more about this blog https://edspl.net/blog/is-your-cloud-really-secure-a-ciso-s-guide-to-cloud-security-posture-management/
0 notes
Text
AWS Cloud Training in Pune: The Smartest Move for Tech Enthusiasts

The world is moving to the cloud, and so should your career. As organizations adopt digital-first strategies, the need for cloud computing experts—especially those skilled in Amazon Web Services (AWS)—is rising fast. If you’re in Pune and ready to step into the world of cloud technology, AWS Cloud Training in Pune with WebAsha Technologies is your best move toward a high-growth IT career.
What is AWS? And Why Should You Learn It?
Amazon Web Services (AWS) is the most widely used cloud computing platform globally, offering secure, scalable, and cost-efficient infrastructure. It powers businesses in every domain—from tech startups to government agencies—enabling them to deploy applications, store data, and manage services in real-time.
Why AWS Skills Are Career Gold:
AWS holds over 30% of the global cloud market share
More than 1 million active users globally
High-paying job roles across industries
Certifications that are recognized worldwide
Why Choose WebAsha Technologies for AWS Cloud Training in Pune?
At WebAsha Technologies, we go beyond textbooks. We deliver career-oriented training that helps you not only learn AWS but also implement it in real-world scenarios. Whether you're a student, a working professional, or someone seeking a career change, our program is tailored to meet your goals.
What Makes Our AWS Training Stand Out?
Certified Trainers with real-time cloud project experience
Hands-On Learning with labs and practical simulations
Live Projects to prepare for real-world deployments
Updated Curriculum
Interview Preparation & Job Support
Who Can Join AWS Cloud Training in Pune?
This course is designed for learners from various backgrounds. You don’t need prior cloud experience—just curiosity and dedication.
Ideal for:
IT Professionals looking to upskill
Freshers eager to start a career in cloud computing
System Admins and Network Engineers
Software Developers and DevOps Engineers
Business Owners or Startup Founders with technical goals
Course Highlights – What You’ll Learn
Our AWS Cloud Training in Pune focuses on building your knowledge from the ground up and preparing you for AWS certifications like Solutions Architect Associate.
Core Modules Include:
Introduction to Cloud & AWS Overview
EC2: Compute Services
S3: Cloud Storage Solutions
VPC: Virtual Private Network Setup
IAM: User and Permission Management
RDS & DynamoDB: Databases on AWS
Elastic Load Balancers & Auto Scaling
Cloud Monitoring with CloudWatch
AWS Lambda & Serverless Computing
Real-World Project Deployment
Career Path After AWS Training
Once you complete the course, you can aim for industry-recognized certifications such as:
AWS Certified Cloud Practitioner
AWS Certified Solutions Architect – Associate
AWS Certified Developer – Associate
AWS Certified SysOps Administrator
Why Pune is the Perfect Place to Learn AWS
As one of India’s top IT cities, Pune hosts numerous tech parks and multinational companies. Cloud computing roles are booming here, and employers actively seek AWS-certified professionals. By completing AWS Cloud Training in Pune, you position yourself for local and global job opportunities.
Final Words: Let the Cloud Power Your Future
With cloud computing becoming essential in every sector, there has never been a better time to learn AWS. Enroll in AWS Cloud Training in Pune at WebAsha Technologies and take your first step toward a high-paying, future-ready career. Learn from experts, get hands-on experience, and earn certifications that can open doors globally.
0 notes