#biometric access control machine
Explore tagged Tumblr posts
Text

Biometric access, reinvented. Spintly brings a cloud-powered twist to traditional security - touch in, log smart, move freely: https://spintly.com/blog/biometrics-the-future-and-recent-trends-in-access-control/
#biometric access#biometric authentication#biometric attendance#biometric machine#wireless access#spintly#mobile access#access control system#access control solutions
0 notes
Text

Biometric Attendance Machine Mumbai
Contact Us Today and Enjoy Up to 10% Off!💥 Get the Best Biometric Attendance Machine for Attendance and access control at Unbeatable Prices! Don't miss out on this limited-time offer! Call Us: 7827942625 Visit:- https://www.securitysolutionindia.in/
#securitysolutionindia#biometric attendance#face recognition#Fingerprintbiometric#todayoffer#ordernow#biometric attendance machine#door lock access control
0 notes
Text
Find the Perfect GPS Tracker System for Your Needs in Gaya
In today's fast-paced world, GPS tracking systems have become an essential tool for both individuals and businesses. Whether you need to keep an eye on your fleet, ensure the safety of loved ones, or manage your assets, finding the right GPS tracker system is crucial. In Gaya, where transportation and logistics play a vital role, choosing the perfect GPS tracker can significantly enhance efficiency and security. This comprehensive guide will help you navigate the options and find the ideal GPS Tracker system In Gaya.
Understanding GPS Tracking Systems
What is a GPS Tracker?
A GPS tracker is a device that uses the Global Positioning System (GPS) to determine and track its precise location. This data is then transmitted to a remote server or device via cellular or satellite networks. GPS trackers are used in a variety of applications, from vehicle tracking to personal safety and asset management.
How Do GPS Trackers Work?
GPS trackers receive signals from a network of satellites orbiting the Earth. These signals contain time and location data, which the tracker uses to calculate its exact position. The device then transmits this information to a central server, where it can be accessed through a web-based platform or a mobile app. This real-time data allows users to monitor the location and movement of the tracker.
Types of GPS Trackers
Vehicle GPS Trackers
Vehicle GPS trackers are designed to be installed in cars, trucks, and other vehicles. Fire Alarm Shop In Gaya They provide real-time tracking, route history, and can even offer insights into driver behavior. These trackers are ideal for fleet management, ensuring that vehicles are used efficiently and safely.

Personal GPS Trackers
Personal GPS trackers are small, portable devices that can be carried by individuals. They are perfect for ensuring the safety of children, elderly family members, or those with special needs. These devices often come with features like emergency SOS buttons and geofencing, which alerts you if the person leaves a designated area.
Asset GPS Trackers
Asset GPS trackers are used to monitor valuable items, such as machinery, equipment, and cargo. These trackers help prevent theft and ensure that assets are used properly. They can be attached to almost anything, providing peace of mind and security.
Key Features to Look for in a GPS Tracker
Real-Time Tracking
One of the most crucial features of a GPS tracker is real-time tracking. Electronics Security And Surveillance In Gaya This allows you to see the exact location of the tracker at any given moment. Real-time tracking is essential for applications like fleet management, where knowing the precise location of each vehicle is vital.
Geofencing
Geofencing is a feature that lets you set virtual boundaries around a specific area. If the tracker enters or leaves this area, you receive an alert. This is particularly useful for personal trackers, ensuring that children or elderly family members stay within safe zones.
Battery Life
Battery life is a critical consideration when choosing a GPS tracker. Look for devices with long-lasting batteries, especially if you need continuous tracking over extended periods. Some trackers come with rechargeable batteries, while others use replaceable ones.
Durability and Waterproofing
For outdoor and rugged use, ensure that the GPS tracker is durable and waterproof. Electronic Security And Surveillance in Bihar This ensures the device can withstand harsh conditions and continue to function reliably.
Data Storage and History
Access to historical data can be extremely beneficial. Look for trackers that offer data storage and the ability to review past locations and movements. This feature is useful for analyzing routes and identifying patterns.
Top GPS Trackers Available in Gaya
TrakkingPro VT1000
The TrakkingPro VT1000 is a versatile vehicle GPS tracker ideal for fleet management. It offers real-time tracking, driver behavior monitoring, and route optimization. Its robust design ensures durability, and it comes with a user-friendly mobile app for easy access.
SafeGuard Mini GPS Tracker
The SafeGuard Mini GPS Tracker is perfect for personal use. Its compact size and long battery life make it ideal for keeping track of children or elderly family members. It features an SOS button, geofencing, and real-time tracking, ensuring safety and peace of mind.
AssetGuard AG300
The AssetGuard AG300 is designed for asset tracking. It’s rugged, waterproof, and provides real-time location data. Epabx and Intercom Store In Gaya This tracker is excellent for securing valuable assets like machinery and equipment. Its long battery life ensures continuous monitoring.
How to Choose the Right GPS Tracker
Assess Your Needs
Before choosing a GPS tracker, assess your specific needs. Are you looking for a device to track vehicles, individuals, or assets? Understanding your requirements will help you narrow down the options and select the most suitable tracker.
Consider the Coverage Area
Ensure that the GPS tracker you choose has reliable coverage in Gaya. Some trackers use cellular networks, while others rely on satellite communication. Choose a tracker that offers consistent coverage in your area of operation.
Check Reviews and Ratings
Research and read reviews of different GPS trackers. Look for devices with high ratings and positive feedback from users. This will give you an idea of the tracker’s performance and reliability.
Evaluate the Cost
Consider your budget when choosing a GPS tracker. CCTV Camera Store in Gaya While it’s important to find an affordable option, don’t compromise on essential features. Evaluate the cost of the device, subscription fees, and any additional charges.
Installation and Setup
Professional Installation vs. DIY
Some GPS trackers require professional installation, especially those designed for vehicles. Professional installation ensures that the device is correctly set up and functions properly. However, many personal and asset trackers are easy to install and can be set up by the user.
Setting Up Alerts and Notifications
Once your GPS tracker is installed, set up alerts and notifications based on your needs. This could include geofencing alerts, low battery warnings, or movement notifications. Properly configuring these settings ensures that you receive timely updates.
Maximizing the Benefits of GPS Tracking
Improving Fleet Management
For businesses in Gaya, using Camera Store In Gaya for fleet management can lead to significant improvements in efficiency and productivity. Trackers provide real-time data on vehicle locations, helping optimize routes, reduce fuel consumption, and enhance customer service.
Ensuring Personal Safety
Personal GPS trackers are invaluable for ensuring the safety of loved ones. Whether it’s keeping track of children on their way to school or monitoring elderly family members, these devices provide peace of mind and swift response in emergencies.
Securing Valuable Assets
For businesses and individuals with valuable assets, GPS trackers offer robust security solutions. Trackers help prevent theft, monitor usage, and provide real-time location data, ensuring that assets are always under surveillance.
Choosing the perfect GPS tracker system for your needs in Gaya involves careful consideration of your requirements, the features offered by different trackers, and their performance. Whether you need to manage a fleet, ensure personal safety, or secure valuable assets, a reliable GPS tracker can make a significant difference. By understanding the options and selecting a device that meets your specific needs, you can enhance efficiency, security, and peace of mind.
#GPS Tracker system In Gaya#Fire Alarm Shop In Gaya#Currency Counting Machine Shop In Gaya#Automatic School bell Store In Gaya#Epabx and Intercom Store In Gaya#Video Door Phone Store In Gaya#Fire Extinguisher Store In Gaya#Biometric Attendance and Access control In Gaya#Camera Store In Gaya#CCTV Camera Store in Gaya
0 notes
Text
The Advantages of Using VivencyGlobal’s Surveillance Solutions
Vivency Global is a leading provider of surveillance solutions that help organizations protect their assets, people, and operations. With over a decade of experience in designing, implementing, and managing complex security systems, Vivency Global has a proven track record of delivering high-quality solutions that meet the diverse needs of its clients. In this blog post, we will explore some of the advantages of using VivencyGlobal’s surveillance solutions and how they can benefit your business.
Comprehensive coverage
VivencyGlobal’s surveillance solutions offer comprehensive coverage of your premises, both indoors and outdoors. They use advanced technologies such as high-definition cameras, thermal imaging, facial recognition, license plate recognition, and analytics to detect and deter potential threats, identify suspicious behavior, and provide actionable intelligence to your security team. Whether you need to monitor your office building, warehouse, parking lot, or retail store, Vivency Global can design a customized solution that fits your needs and budget.
Real-time monitoring
VivencyGlobal’s surveillance solutions enable real-time monitoring of your premises from any location, using any device with an internet connection. This means you can stay connected to your security system 24/7 and receive alerts and notifications in case of any security breaches, unauthorized access, or other abnormal activities. You can also review live and recorded footage, manage access control, and communicate with your security team or law enforcement agencies using the same platform.
Scalability and flexibility
VivencyGlobal’s surveillance solutions are scalable and flexible, meaning they can adapt to your changing security requirements as your business grows or evolves. Whether you need to add more cameras, upgrade your software, integrate with other systems, or migrate to a cloud-based platform, Vivency Global can provide you with a seamless and cost-effective solution that minimizes disruption and maximizes value.
Expertise and support
VivencyGlobal’s surveillance solutions are backed by a team of experienced security professionals who understand the latest trends, technologies, and regulations in the industry. They can provide you with expert advice, training, and support throughout the lifecycle of your security system, from design to deployment to maintenance. They can also help you optimize your system’s performance, reduce false alarms, and minimize downtime, ensuring that your security system operates at peak efficiency.
Compliance and privacy
VivencyGlobal’s surveillance solutions are designed to comply with the highest standards of privacy and data protection. They use encryption, authentication, and access control mechanisms to secure your data and prevent unauthorized access, disclosure, or modification. They also adhere to local and international regulations such as GDPR, HIPAA, PCI-DSS, and SOX, ensuring that your security system meets the legal and ethical requirements of your industry and jurisdiction.
In conclusion, VivencyGlobal’s surveillance solutions offer many advantages that can help you enhance your security posture, reduce your risk exposure, and improve your operational efficiency. Whether you need to prevent theft, vandalism, or violence, or monitor compliance, productivity, or customer experience, Vivency Global can provide you with a customized solution that meets your needs and exceeds your expectations. To learn more about VivencyGlobal’s surveillance solutions, contact us today.
#Surveillance#Security#Monitoring#CCTV#Privacy#Technology#Data collection#Intelligence#Video analytics#Remote monitoring#Access control#Intrusion detection#Biometrics#Facial recognition#Network security#Smart cameras#Privacy concerns#Threat detection#Cybersecurity#Artificial intelligence (AI)#Machine learning#Sensor networks#Crime prevention#Homeland security#Public safety
1 note
·
View note
Text
ZKTeco iFace880 Plus Multi Biometric Time Attendance

ZKTeco presents the iFace880 Plus multi-biometric time attendance and access control terminal which supports 3,000 palm templates, 4,000 fingerprint templates, and 10,000 cards (optional).
It is equipped with ZKTeco’s latest hardware platform and algorithm like 3-in-1 contactless palm recognition (palm shape, palm print, and palm vein).
This makes the terminal perform bio-authentication with the palm vein, palm print, and the shape of the palm when the sensor detects a hand that is presented.
The terminal’s touchless palm authentication method with a novel hand tracking technique allows angle tolerance as wide as +/- 60° in the roll axis.
With the advanced palm and face algorithm and multi-biometric verification technology, users can experience the terminal’s enhanced anti-spoofing ability and its significantly improved security level.
Features of ZKTeco iFace880 Plus
• 3,000 face, 3,000 palm, and 4,000 fingerprint templates • Multiple authentication methods: face/palm/fingerprint/card/password • Fast verification speed • Modern design and interactive UI • Chip encryption for firmware protection • Optional built-in backup battery providing approximately 4 hours of continuous operation
ZKTeco iFace880 Plus price in UAE
Cost To Cost provides the best price for the ZKTeco iFace880 access control
#zk#zkteco#dubai#uae#business#it support#time attendance machine#fingerprint time attendance and access control#access control systems#time attendance#biometric time attendance#ZKTeco iFace880 plus#costtocost#sharjah#biometric attendance system#fingerprint recognition
0 notes
Text
Why Biometric & Time Attendance Systems Matter
Time is money, and effective time management is essential for businesses to thrive. Traditional punch cards and paper registers have become obsolete and ineffective in modern workplaces. Biometric and time attendance systems have emerged as game-changers for businesses by offering the following benefits:
Accuracy: Biometric systems use unique human characteristics such as fingerprints, facial recognition, or iris scans, ensuring that employees cannot clock in or out for each other. This accuracy reduces payroll errors and saves money.
Elimination of Buddy Punching: With biometric systems, employees cannot clock in or out for their absent colleagues, preventing fraudulent practices and ensuring fair work hours.
Real-time Monitoring: Employers can monitor attendance in real time, providing instant insights into employee attendance patterns and helping with workforce planning.
Security: Biometric data is highly secure, reducing the risk of unauthorized access to sensitive areas within the organization.
Convenience: Employees can clock in and out quickly and conveniently, without the hassle of remembering passwords or carrying physical cards.
Tektronix Technologies: A Pioneer in Biometric & Time Attendance Systems
Tektronix Technologies has established itself as a trusted name in the field of biometric and time attendance systems in Dubai and Abu Dhabi. Here's why they are a preferred choice:
Cutting-Edge Technology: Tektronix Technologies stays at the forefront of technological advancements. Their systems utilize the latest biometric recognition methods, ensuring the highest level of accuracy and security.
Customized Solutions: They offer tailored solutions that fit the unique needs of each business, whether it's a small startup or a large enterprise.
User-Friendly Interfaces: Tektronix Technologies designs user-friendly interfaces that are easy to use for both employees and administrators.
Scalability: Their systems are scalable, meaning they can grow with your business, accommodating additional employees and locations.
Local Support: With a strong presence in Dubai and Abu Dhabi, Tektronix Technologies provides local support and maintenance, ensuring that your system runs smoothly at all times.
In a competitive business environment like Dubai and Abu Dhabi, efficient time and attendance management is critical for success. Tektronix Technologies offers cutting-edge biometric and time attendance systems that not only streamline attendance tracking but also enhance security and accuracy. Investing in these advanced systems is a strategic move that can lead to significant cost savings, improved productivity, and greater peace of mind for business owners and managers. With Tektronix Technologies, businesses in these dynamic cities are empowered to manage their workforce efficiently and effectively, paving the way for growth and success in the modern business landscape.
time attendance system dubai
time attendance system abu dhabi
biometric access control system
biometric access control system dubai
biometric access control system UAE
biometric access control system bur dubai
biometric access control system alain
biometric access control system
time attendance machine
time attendance machine Dubai
time attendance machine Abu Dhabi
time attendance machine uae
#timeattendancesystemabudhabi #timeattendancesystemdubai #timeattendancesystemabudhabi #timeattendancemachineuae #biometricmachinesupplierindubai #biometricmachinesupplierinuae #biometricaccesscontrolsystem #timeattendancemachineuae
#timeattendancesystemsoftware #imeattendancesystemsoftwareuae #timeattendancesystemsoftwaredubai
#timeattendancesystemsoftwareburdubai #fingerprintattendancesystemsoftwareuae
#biometric access control system#biometric access control system dubai#biometric access control system abu dhabi#biometric access control system in uae#biometric access control system in ajman#bio metric access control system in bur dubai#bio metric access control saudi arabia#time attendance system#time attendance system dubai#time attendance system uae#time attendance system abu dhabi#time attendance system in bur dubai#time attendance system in alain#time attendance system bur dubai#time attendance system in ajman#time attendance system sharjah#time attendance system dubai in alain#time attendance machine abu dhabi#time attendance solutions in bur dubai#time attendance machine in uae#time attendance machine in bur dubai#time attendance in bur dubai#time attendance bur dubai#time attendance machine in bur Dubai#biometric attendance machine uae#biometric attendance machine abu dhabi#biometric attendance machine in uae#biometric attendance machine bur dubai#biometric attendance machine in ajman#biometric attendance machine sharjah
0 notes
Text
#biometrics#biometric macine#Biometric Machine Company#Biometric System and Access Control Machine#Fingerprint Attendance System#Biometric Attendance System
0 notes
Text
01 - no good deed | just another player. (hwang in-ho x reader)

|| masterlist ||
previous chapter | next chapter
----
The room was dark. Not the artificial, humming darkness of the dormitories. No flickering overhead lights, no sound of desperate breathing in the shadows.
This darkness was deeper, becoming quieter, then still.
Hwang In-ho bolts upright in his bed, breath caught in his throat, chest heaving beneath the black robe of the Front Man. Sweat clung to his skin like blood once did. The black mask sits abandoned on the table beside him, and for a moment, he remembers who he is.
Not Hwang In-ho.
The Front Man.
But the dream, kind of a memory, doesn’t let him go. He can still feel it — the warm pool of his blood beneath him, the shouts, the silence, and the pain.
And then, there was you.
Your gloved hands pressing down his wound with a whisper against the chaos, “If you live, don’t forget who you were.”
In-ho’s hands tremble as he reached for a glass of water beside him. He had forgotten, hadn’t he? Bit by bit, piece by piece, until all that remained was the mask, the control, the machine.
But that voice — your voice — it never left.
He brushes his hand through his damp hair, eyes burning as they stare at nothing. You were just a shadow then, a mask among other masks. A rule-breaker in a place where mercy was punishable by death.
He doesn’t even know your face or your name. Yet your presence lives in the cracks of his memory, in the fractured quiet of his mind that he never allowed himself to touch.
Except in his dreams.
Or nightmares.
He rose slowly, each movement deliberate. There’s something cold and restrained about him now, but the weight behind his eyes was unmistakable. He walked to the system terminal as the soft glow of the screens hummed to life, illuminating the sharp edges of his face, the shadow of grief still etched across his expression.
His fingers tapped on the keyboard as the screen flickered.
Pink Guard Personnel Records: 28th Squid Game
He shouldn’t do this.
He knew he shouldn’t. Everything about the games was built on anonymity, everything encrypted as if you were expected to forget, bury the past six feet beneath protocol and power.
But he couldn’t forget you.
His voice was low, hoarse, as he spoke into the silence. “Who were you?”
The system begins its search as the man behind the mask isn’t the Front Man tonight. Tonight, he’s a survivor… still trying to find the one person who made him feel human again.
Lines of data flicker across the screen — guard IDs, biometric logs, movement patterns, shift schedules. Thousands of entries. Most were clean, categorized, and controlled.
But one file stalls.
ID: P-132-20152745
In-ho narrowed his eyes as he noticed the file. He hovered his hand on his mouse as he clicked, only for the screen to shudder.
ERROR. FILE CORRUPTED. ACCESS DENIED.
He leaned closer as he squinted at the file number. He doesn’t recognize the number, but something about it pulls at him. The timestamp matches the night he was injured. That narrow window between the second and third round.
His fingers fly over the keys as he bypasses standard security. Firewalls resist him, but he wrote the protocols himself. He cracks through the surface code, digging deeper.
REDACTED ENTRY: UNAUTHORIZED INTERVENTION DETECTED.
P-132-20152745: Disciplinary Report - MISSING
Security Footage - DELETED
Status: UNKNOWN
He sits back slowly, the air tight in his lungs, realizing that someone had scrubbed the record.
Not just a name or a face. Just plain everything.
As if that guard never existed.
As if the system had tried to erase the very moment he clung to all these years.
His jaw tightened, rage pulsing beneath the surface. Not just for the system, but for himself for forgetting, surviving, and becoming the very thing he once feared.
Still, there’s a silver of data remaining. A slashed fragment of a voice file that was compressed and corrupted.
Yet, it was still playable.
The static nearly swallows the sound, but in the middle of the distortion, something cuts through.
“—wasn’t supposed to do this…”
“…remember who you are…” “—forgive me.”
In-ho’s eyes closed, his heart pulsing through his chest. Though it was comforting to feel that you were real, he couldn’t help but wonder what had happened to you.
As his thoughts almost swayed him, he immediately snapped out of his thoughts as he heard a heavy thud. Not from the room, but from the recording.
He sat up as a sharp intake of breath was heard, then another sound that seemed like a hit. Then, another sound that pierces through even the most distorted noise.
A soft, broken whimper. A woman’s voice.
“Please…” A muffled cry as another strike seemed to be done, and then, there was silence.
In-ho froze as his jaw clenched while the recording looped, replaying that single moment of helplessness. Something cold grips his chest, curling around his ribs like barbed wire.
Someone definitely made sure he wouldn’t remember it.
The file ends with one last, choked breath — one that doesn’t quite sound like fear, but grief.
“He wasn’t supposed to see me.”
The silence after felt suffocating. In-ho’s fingers curled into fists as the final realization sank in. This wasn’t just a disappearing act.
Someone silenced you, covered you up, and buried your existence under codes and protocols. In-ho scoffed, a smirk forming as if an idea shone all over his face.
They didn’t bury you well enough.
His eyes hardened as he locked the terminal.
You saved him once, now it was his turn.
——
The incinerator hisses as the body bag disappears into flame.
It was either buried or harvested for organs — you couldn’t care at all. In fact, you don’t flinch anymore. You haven’t, in a long time.
The stench of burnt cloth and blood clings to your mask, thick and stubborn, as if even the scent refuses to die here. You stand still, posture straight, hands clasped behind you just as protocol demands.
You were only a pink circle guard. Just another pair of obedient boots, another ghost in the machine.
Your boots echo softly down the corridor. Rhythm is everything here—footsteps measured, spine straight, eyes forward behind a mask that tells the world nothing. Now, you’re Guard 427.
You swipe your card at the checkpoint and enter the security control wing. The guards here don’t speak unless ordered. The walls hum with surveillance feeds, and one screen, larger than the rest, projects the black mask of the Front Man. You’ve worked hard to become invisible. You are precise in your tasks, silent in your duties, unremarkable in your movements. You erase yourself every day, bit by bit, in service of survival.
Still, you remember him. Not as the Front Man. But as Player 132.
He was bleeding when you found him, struggling beneath the weight of survival. You should’ve walked away. Left him to die like all the others. But something in his eyes that night — numb but furious, cracked but not yet broken made you stop.
You knelt. Whispered. Touched his bloodied chest with trembling fingers.
“If you live, don’t forget who you were before they made you fight.”
And now, he sits behind the glass of power, voice modulated, mask unshifting, his judgment absolute. You wondered if he dreams of you, if your voice ever slips into his nightmares. You wondered if, when he stares too long at the monitors, he's chasing something his mind won’t give him.
You kept your head down and your steps even. You cleaned blood off the walls. You followed orders. You pretend you’re not the one he’s unknowingly searching for.
Because if he ever does remember… If he ever sees through the perfect circle painted across your mask, what then?
Would he thank you? Punish you? Undo you?
You weren’t sure. In a place where mercy was a foreign concept, such a situation of his finding you would cause more complications.
The alarm blared. A low tone thrums through the walls, and every Circle in the hallway stops in unison.
“VIP arrival. Level Six. Escort detail.”
Your fellow pink guards peel off wordlessly, boots pivoting toward the service lift that leads to the opulent corridors you’re never meant to see. The ones draped in gold and smoke, the ones that reek of indulgence and blood.
But not you.
Your earpiece buzzes with a separate frequency.
“P-427, Report to Sub-Level Three. Clearance Sigma Red.”
Sigma Red.
You hesitate for half a breath before responding.
“Confirmed. On route.”
It wasn’t your first time.
You walked alone now, past the steel hallways, the flickering fluorescents, the guards who pretended not to see. You made your way towards the door marked only by a red triangle and the faint scent of disinfectant beneath it.
Inside the room was quiet, warmer, and cleaner. There was no briefing. No other guards. Just a room with a solitary mirror and a rack of clean clothing with soft fabric, unlike your uniform.
“Change. Protocol 09 is in effect,” the voice over the intercom says.
You obeyed, not needing to be told why.
You’ve done this before. You remember the way the Front Man had just taken the mask then. How his presence had loomed even before you could name it. The first time, you’d done what you were told because not doing so meant punishment.
You were a standard circle guard who was quiet, efficient, and obedient. Not until that night during the 28th Season where you chose mercy.
He was bleeding out during lights out where his eyes had pulled you in — the hollow ache of someone who wanted to die but was too proud to beg for it. You broke the rules, yet they let you live.
Only so they could strip you down slowly — the escort class.
The lowest, most degrading designation in the hierarchy of this twisted system. You are masked, dressed in thin civilian mimicry, and handed over to the VIPs—not for pleasure, necessarily. Sometimes just for company. Sometimes for cruelty. Always for obedience.
“Escort detail begins in thirty minutes. Await further instruction.”
The door clicks shut behind you. You sat and waited, listening to the hum of the walls as you wondered, what if this is the time he speaks to you? What if he looks at you a second too long? What if he asks your name? And what if you're too afraid to give it?
The walls here were too quiet. No screams, gunfire, and barking orders. Only silence — deliberate, echoing, and unnerving.
The mask stays on. It always stays on. It's the only part of yourself you're allowed to keep. As you sat, the intercom crackled again. A different voice this time. One you know. One you’ve heard before during your disciplinary hearing.
“Protocol 09 in effect,” the speaker hisses.
No acknowledgment required. They know you understand.
“You aided a player in the 28th Season. Unforgivable.”
A pause, long enough to let the weight settle. “You will not speak of it. Not to him. Not to anyone. The Front Man does not know. He must never know. Do you understand?”
You nod silently, because that’s all you're allowed to do now.
“VIPs arrive in thirty. Escort mode active.”
You fixed the mask over your face as you changed layer by layer, its garments feel like silk-wrapped shame.
You remember how, once, your hands shook as they held a bleeding man. The one who now runs the games, one who sits behind a mask of black steel, haunted by something he can’t quite name.
He lives because of you and now you serve because of him.
He must never know.
But you remember.
Every time.
——
The scent of cologne, alcohol, and smoke clung to the velvet of the VIP lounge. The lighting was warm, golden, and suffocating — designed to flatter the depraved. Laughter cuts the air like broken glass. Masks of beasts and emperors lounge across gilded sofas, their voices slurred, their gaze predatory.
One of the VIPs snaps his fingers lazily. You pour his drink, bow just enough, and say nothing — as trained. You don’t speak. You don’t blink too long. You don’t feel.
“You’re quiet,” the VIP, masked as a Minotaur, slurred, brushing his fingers against your mask. “That’s good. Quiet girls know their place.”
You don’t flinch. At least, not visibly.
He grabbed your wrist, pulling you slightly closer, examining you like a possession. “You’re prettier than the last one. I like the silent ones.”
You remain still and silent. Fighting the urge to pull away because if you did, they win. And if you speak, you lose more. Your hands rest on your knees as you lowered your gaze.
“You’re not new, are you?”
The question stung, but you didn’t flinch. You were burning inside, but you stayed silent.
“That means you know not to fight.”
A murmur of laughter from the others. One of them raises a toast. Another gestures toward you and makes a cruel joke about how easily the silent ones break.
But something shifts in the room. The air tightens. The laughter dulls into murmurs.
The door opened, revealing the Front Man.
Black mask. Black coat. His movements sharp and deliberate. Authority trails behind him like a shadow.
Your body reacts before your mind can catch up. You straightened your back, holding your breath as you felt your pulse surge. You kept your head bowed.
He shouldn't be here. Not during the lounge sessions. Not unless something’s wrong. Yet here he is.
He walked slowly through the room silently as if he were observing and calculating something. His presence stills the most obnoxious of the guests. Even the ones who believe they own this place lower their voices when he moves near.
From across the room, the Front Man’s visor tilts toward you. He seemed to see your… situation. But, he doesn’t stop it. He doesn’t speak.
He simply watches.
You don’t know what’s worse. The VIP’s hand curling around your waist…
…or the silence from the one man who might have stopped it.
The VIP’s hand had finally left your side—only because another escort had arrived, younger and easier to control. You’d bowed out with the grace expected of you, even though your fingers trembled behind your back.
“Go help the servers,” one of the Square guards said.
You obeyed.
It was almost a relief to stand by the bar cart again, serving champagne, bourbon, whiskey, gin. Anything they asked for. Anything to stop being seen.
“You,” the Square guard pointed at you. “Pour for the Front Man.”
The air around you dropped ten degrees, but your hands moved on instinct. The Front Man stood near the edge of the lounge, silent and still as the walls themselves. You could feel the room shift around him.
You approached with measured steps, a crystal decanter in hand.
He didn’t look at you when you poured, though you could smell his cologne even beneath your mask. As you were about to finish filling up the glass, he suddenly spoke.
“Stay.”
You froze. You expected to be dismissed. But instead, he stood there, drink in hand, and allowed you to remain beside him. One step behind. Within reach. Claimed without announcement.
“Careful with that one, Front Man!” a portly VIP calls out with a laugh, drink sloshing in his hand. “Keep her too close, and you might find yourself using her for more than just drinks!”
Laughter erupted from his circle as your breath hitched a bit. You didn’t move, and the Front Man didn’t say anything. You weren’t sure if he reacted beneath his mask, but he stayed still. There was no reaction and defense.
He sipped his drink slowly, his gaze never leaving the room. Not even a glance toward the man who joked. Not toward you. But then, you felt a sting inside you.
It wasn’t because of the VIP’s words — you’ve heard worse.
But because he didn’t stop it.
You stood at his side obediently, and he let the insult hang there, untouched. You forced the pain down like glass, straightening your spine. Somehow, his silence hurts more than the joke ever could.
By day, you sweep floors, distribute rations, check that the cameras are functioning. Your circle mask stares back at you from polished metal when you pass the infirmary door. You speak to no one. You salute when required. You blend in easily and invisibly.
You are not meant to be remembered. That, too, is part of the punishment.
At night, it changes. The suit comes off. The silk goes on. You trade your mask for another kind — faceless still, but far more exposed. An escort — a role no one envies.
No one asks how you ended up there. They already know.
It’s all because you interfered and saved someone you weren’t meant to. You’re not even sure he remembers. Or if he ever knew. Or if he’s simply chosen to forget because acknowledging what you did would mean acknowledging that even he was once weak enough to bleed.
And weakness isn’t allowed here.
Sometimes, when you stand beside his chair in the VIP lounge and pour his drink, you think about that moment in the dark, years ago. When he was gasping, wounded, barely clinging to life behind a player’s uniform soaked in blood. And you chose to help.
That was the night your position was stripped from you.
Because you weren’t always a circle.
Your hands remember how to hold a gun with authority. Your voice remembers how to give orders.
You were a square.
You remember the weight of command.
But mercy is a betrayal in this place, and your punishment is to be seen and not recognized. It is for you to serve quietly the man you once saved and to suffer silently each time he looks right past you.
----
A/N: We're back! This time, it's more of a slow burn type of fanfic so please bear with the story. What did you think of how you're a Pink Guard saving the Front Man back when he was still a player and him trying to find you in the crowd? This whole fic will be based on the events of Squid Game Season 1, as it would be like one of the first years of In-ho as the Front Man. :D
Don't forget to leave a comment in this chapter to be tagged on to the next chapter. :)
previous chapter | next chapter
|| masterlist ||
taglist: @roachco-k @goingmerry69
#hwang in ho#lee byung hun#player 001#squid game#the front man#oh young il#squid game netflix#001 squid game#001#in ho x reader#hwang inho#in ho#frontman x reader#frontman x you#inho x reader#inho x you#hwang inho x reader
56 notes
·
View notes
Text

─────────── ⌇ thoughts on Minh's Security Hacking
Minh doesn't really have a problem doing illegal acts, but there are certainly limitations. For example, he'd not use it for private matters to help anyone take revenge or some shit like that.
He also would not attempt to do any hacking of military or law enforcement security machines. The group he was in always focused on private persons or companies. He usually also moves in that realm now, but smaller.
Good examples of what he does probably be:
Surveillance Systems: e.g., CCTV, motion sensors
Access Control: e.g., keycard locks, biometric scanners (turning off warnings)
Banking Systems: e.g., ATMs, online banking platforms
Corporate Networks: e.g., firewalls, VPNs, email servers
Minh also avoids those where he knows their system is designed so that he would have the risk of leaving a trace.
He is not a hacker in the traditional sense that just gets into whatever device you hand him, he requires certain tools, programs and prepared devices.
7 notes
·
View notes
Text
Scan the online brochures of companies who sell workplace monitoring tech and you’d think the average American worker was a renegade poised to take their employer down at the next opportunity. “Nearly half of US employees admit to time theft!” “Biometric readers for enhanced accuracy!” “Offer staff benefits in a controlled way with Vending Machine Access!”
A new wave of return-to-office mandates has arrived since the New Year, including at JP Morgan Chase, leading advertising agency WPP, and Amazon—not to mention President Trump’s late January directive to the heads of federal agencies to “terminate remote work arrangements and require employees to return to work in-person … on a full-time basis.” Five years on from the pandemic, when the world showed how effectively many roles could be performed remotely or flexibly, what’s caused the sudden change of heart?
“There’s two things happening,” says global industry analyst Josh Bersin, who is based in California. “The economy is actually slowing down, so companies are hiring less. So there is a trend toward productivity in general, and then AI has forced virtually every company to reallocate resources toward AI projects.
“The expectation amongst CEOs is that’s going to eliminate a lot of jobs. A lot of these back-to-work mandates are due to frustration that both of those initiatives are hard to measure or hard to do when we don’t know what people are doing at home.”
The question is, what exactly are we returning to?
Take any consumer tech buzzword of the 21st century and chances are it’s already being widely used across the US to monitor time, attendance and, in some cases, the productivity of workers, in sectors such as manufacturing, retail, and fast food chains: RFID badges, GPS time clock apps, NFC apps, QR code clocking-in, Apple Watch badges, and palm, face, eye, voice, and finger scanners. Biometric scanners have long been sold to companies as a way to avoid hourly workers “buddy punching” for each other at the start and end of shifts—so-called “time theft.” A return-to-office mandate and its enforcement opens the door for similar scenarios for salaried staff.
Track and Trace
The latest, deluxe end point of these time and attendance tchotchkes and apps is something like Austin-headquartered HID’s OmniKey platform. Designed for factories, hospitals, universities and offices, this is essentially an all-encompassing RFID log-in and security system for employees, via smart cards, smartphone wallets, and wearables. These will not only monitor turnstile entrances, exits, and floor access by way of elevators but also parking, the use of meeting rooms, the cafeteria, printers, lockers, and yes, vending machine access.
These technologies, and more sophisticated worker location- and behavior-tracking systems, are expanding from blue-collar jobs to pink-collar industries and even white-collar office settings. Depending on the survey, approximately 70 to 80 percent of large US employers now use some form of employee monitoring, and the likes of PwC have explicitly told workers that managers will be tracking their location to enforce a three-day office week policy.
“Several of these earlier technologies, like RFID sensors and low-tech barcode scanners, have been used in manufacturing, in warehouses, or in other settings for some time,” says Wolfie Christl, a researcher of workplace surveillance for Cracked Labs, a nonprofit based in Vienna, Austria. “We’re moving toward the use of all kinds of sensor data, and this kind of technology is certainly now moving into the offices. However, I think for many of these, it’s questionable whether they really make sense there.”
What’s new, at least to the recent pandemic age of hybrid working, is the extent to which workers can now be tracked inside office buildings. Cracked Labs published a frankly terrifying 25-page case study report in November 2024 showing how systems of wireless networking, motion sensors, and Bluetooth beacons, whether intentionally or as a byproduct of their capabilities, can provide “behavioral monitoring and profiling” in office settings.
The project breaks the tech down into two categories: The first is technology that tracks desk presence and room occupancy, and the second monitors the indoor location, movement, and behavior of the people working inside the building.
To start with desk and room occupancy, Spacewell offers a mix of motion sensors installed under desks, in ceilings, and at doorways in “office spaces” and heat sensors and low-resolution visual sensors to show which desks and rooms are being used. Both real-time and trend data are available to managers via its “live data floorplan,” and the sensors also capture temperature, environmental, light intensity, and humidity data.
The Swiss-headquartered Locatee, meanwhile, uses existing badge and device data via Wi-Fi and LAN to continuously monitor clocking in and clocking out, time spent by workers at desks and on specific floors, and the number of hours and days spent by employees at the office per week. While the software displays aggregate rather than individual personal employee data to company executives, the Cracked Labs report points out that Locatee offers a segmented team analytics report which “reveals data on small groups.”
As more companies return to the office, the interest in this idea of “optimized” working spaces is growing fast. According to S&S Insider’s early 2025 analysis, the connected office was worth $43 billion in 2023 and will grow to $122.5 billion by 2032. Alongside this, IndustryARC predicts there will be a $4.5 billion employee-monitoring-technology market, mostly in North America, by 2026—the only issue being that the crossover between the two is blurry at best.
At the end of January, Logitech showed off its millimeter-wave radar Spot sensors, which are designed to allow employers to monitor whether rooms are being used and which rooms in the building are used the most. A Logitech rep told The Verge that the peel-and-stick devices, which also monitor VOCs, temperature, and humidity, could theoretically estimate the general placement of people in a meeting room.
As Christl explains, because of the functionality that these types of sensor-based systems offer, there is the very real possibility of a creep from legitimate applications, such as managing energy use, worker health and safety, and ensuring sufficient office resources into more intrusive purposes.
“For me, the main issue is that if companies use highly sensitive data like tracking the location of employees’ devices and smartphones indoors or even use motion detectors indoors,” he says, “then there must be totally reliable safeguards that this data is not being used for any other purposes.”
Big Brother Is Watching
This warning becomes even more pressing where workers’ indoor location, movement, and behavior are concerned. Cisco’s Spaces cloud platform has digitized 11 billion square feet of enterprise locations, producing 24.7 trillion location data points. The Spaces system is used by more than 8,800 businesses worldwide and is deployed by the likes of InterContinental Hotels Group, WeWork, the NHS Foundation, and San Jose State University, according to Cisco’s website.
While it has applications for retailers, restaurants, hotels, and event venues, many of its features are designed to function in office environments, including meeting room management and occupancy monitoring. Spaces is designed as a comprehensive, all-seeing eye into how employees (and customers and visitors, depending on the setting) and their connected devices, equipment, or “assets” move through physical spaces.
Cisco has achieved this by using its existing wireless infrastructure and combining data from Wi-Fi access points with Bluetooth tracking. Spaces offers employers both real-time views and historical data dashboards. The use cases? Everything from meeting-room scheduling and optimizing cleaning schedules to more invasive dashboards on employees’ entry and exit times, the duration of staff workdays, visit durations by floor, and other “behavior metrics.” This includes those related to performance, a feature pitched at manufacturing sites.
Some of these analytics use aggregate data, but Cracked Labs details how Spaces goes beyond this into personal data, with device usernames and identifiers that make it possible to single out individuals. While the ability to protect privacy by using MAC randomization is there, Cisco emphasizes that this makes indoor movement analytics “unreliable” and other applications impossible—leaving companies to make that decision themselves.
Management even has the ability to send employees nudge-style alerts based on their location in the building. An IBM application, based on Cisco’s underlying technology, offers to spot anomalies in occupancy patterns and send notifications to workers or their managers based on what it finds. Cisco’s Spaces can also incorporate video footage from Cisco security cameras and WebEx video conferencing hardware into the overall system of indoor movement monitoring; another example of function creep from security to employee tracking in the workplace.
“Cisco is simply everywhere. As soon as employers start to repurpose data that is being collected from networking or IT infrastructure, this quickly becomes very dangerous, from my perspective.” says Christl. “With this kind of indoor location tracking technology based on its Wi-Fi networks, I think that a vendor as major as Cisco has a responsibility to ensure it doesn’t suggest or market solutions that are really irresponsible to employers.
“I would consider any productivity and performance tracking very problematic when based on this kind of intrusive behavioral data.” WIRED approached Cisco for comment but didn’t receive a response before publication.
Cisco isn't alone in this, though. Similar to Spaces, Juniper’s Mist offers an indoor tracking system that uses both Wi-Fi networks and Bluetooth beacons to locate people, connected devices, and Bluetooth tagged badges on a real-time map, with the option of up to 13 months of historical data on worker behavior.
Juniper’s offering, for workplaces including offices, hospitals, manufacturing sites, and retailers, is so precise that it is able to provide records of employees’ device names, together with the exact enter and exit times and duration of visits between “zones” in offices—including one labeled “break area/kitchen” in a demo. Yikes.
For each of these systems, a range of different applications is functionally possible, and some which raise labor-law concerns. “A worst-case scenario would be that management wants to fire someone and then starts looking into historical records trying to find some misconduct,” says Christl. "If it’s necessary to investigate employees, then there should be a procedure where, for example, a worker representative is looking into the fine-grained behavioral data together with management. This would be another safeguard to prevent misuse.”
Above and Beyond?
If warehouse-style tracking has the potential for management overkill in office settings, it makes even less sense in service and health care jobs, and American unions are now pushing for more access to data and quotas used in disciplinary action. Elizabeth Anderson, professor of public philosophy at the University of Michigan and the author of Private Government: How Employers Rule Our Lives, describes how black-box algorithm-driven management and monitoring affects not just the day-to-day of nursing staff but also their sense of work and value.
“Surveillance and this idea of time theft, it’s all connected to this idea of wasting time,” she explains. “Essentially all relational work is considered inefficient. In a memory care unit, for example, the system will say how long to give a patient breakfast, how many minutes to get them dressed, and so forth.
“Maybe an Alzheimer’s patient is frightened, so a nurse has to spend some time calming them down, or perhaps they have lost some ability overnight. That’s not one of the discrete physical tasks that can be measured. Most of the job is helping that person cope with declining faculties; it takes time for that, for people to read your emotions and respond appropriately. What you get is massive moral injury with this notion of efficiency.”
This kind of monitoring extends to service workers, including servers in restaurants and cleaning staff, according to a 2023 Cracked Labs’ report into retail and hospitality. Software developed by Oracle is used to, among other applications, rate and rank servers based on speed, sales, timekeeping around breaks, and how many tips they receive. Similar Oracle software that monitors mobile workers such as housekeepers and cleaners in hotels uses a timer for app-based micromanagement—for instance, “you have two minutes for this room, and there are four tasks.”
As Christl explains, this simply doesn’t work in practice. “People have to struggle to combine what they really do with this kind of rigid, digital system. And it’s not easy to standardize work like talking to patients and other kinds of affective work, like how friendly you are as a waiter. This is a major problem. These systems cannot represent the work that is being done accurately.”
But can knowledge work done in offices ever be effectively measured and assessed either? In an episode of his podcast in January, host Ezra Klein battled his own feelings about having many of his best creative ideas at a café down the street from where he lives rather than in The New York Times’ Manhattan offices. Anderson agrees that creativity often has to find its own path.
“Say there’s a webcam tracking your eyes to make sure you’re looking at the screen,” she says. “We know that daydreaming a little can actually help people come up with creative ideas. Just letting your mind wander is incredibly useful for productivity overall, but that requires some time looking around or out the window. The software connected to your camera is saying you’re off-duty—that you’re wasting time. Nobody’s mind can keep concentrated for the whole work day, but you don’t even want that from a productivity point of view.”
Even for roles where it might make more methodological sense to track discrete physical tasks, there can be negative consequences of nonstop monitoring. Anderson points to a scene in Erik Gandini’s 2023 documentary After Work that shows an Amazon delivery driver who is monitored, via camera, for their driving, delivery quotas, and even getting dinged for using Spotify in the van.
“It’s very tightly regulated and super, super intrusive, and it’s all based on distrust as the starting point,” she says. “What these tech bros don’t understand is that if you install surveillance technology, which is all about distrusting the workers, there is a deep feature of human psychology that is reciprocity. If you don’t trust me, I’m not going to trust you. You think an employee who doesn’t trust the boss is going to be working with the same enthusiasm? I don’t think so.”
Trust Issues
The fixes, then, might be in the leadership itself, not more data dashboards. “Our research shows that excessive monitoring in the workplace can damage trust, have a negative impact on morale, and cause stress and anxiety,” says Hayfa Mohdzaini, senior policy and practice adviser for technology at the CIPD, the UK’s professional body for HR, learning, and development. “Employers might achieve better productivity by investing in line manager training and ensuring employees feel supported with reasonable expectations around office attendance and manageable workloads.”
A 2023 Pew Research study found that 56 percent of US workers were opposed to the use of AI to keep track of when employees were at their desks, and 61 percent were against tracking employees’ movements while they work.
This dropped to just 51 percent of workers who were opposed to recording work done on company computers, through the use of a kind of corporate “spyware” often accepted by staff in the private sector. As Josh Bersin puts it, “Yes, the company can read your emails” with platforms such as Teramind, even including “sentiment analysis” of employee messages.
Snooping on files, emails, and digital chats takes on new significance when it comes to government workers, though. New reporting from WIRED, based on conversations with employees at 13 federal agencies, reveals the extent to Elon Musk’s DOGE team’s surveillance: software including Google’s Gemini AI chatbot, a Dynatrace extension, and security tool Splunk have been added to government computers in recent weeks, and some people have felt they can’t speak freely on recorded and transcribed Microsoft Teams calls. Various agencies already use Everfox software and Dtex’s Intercept system, which generates individual risk scores for workers based on websites and files accessed.
Alongside mass layoffs and furloughs over the past four weeks, the so-called Department of Government Efficiency has also, according to CBS News and NPR reports, gone into multiple agencies in February with the theater and bombast of full X-ray security screenings replacing entry badges at Washington, DC, headquarters. That’s alongside managers telling staff that their logging in and out of devices, swiping in and out of workspaces, and all of their digital work chats will be “closely monitored” going forward.
“Maybe they’re trying to make a big deal out of it to scare people right now,” says Bersin. “The federal government is using back-to-work as an excuse to lay off a bunch of people.”
DOGE staff have reportedly even added keylogger software to government computers to track everything employees type, with staff concerned that anyone using keywords related to progressive thinking or "disloyalty” to Trump could be targeted—not to mention the security risks it introduces for those working on sensitive projects. As one worker told NPR, it feels “Soviet-style” and “Orwellian” with “nonstop monitoring.” Anderson describes the overall DOGE playbook as a series of “deeply intrusive invasions of privacy.”
Alternate Realities
But what protections are out there for employees? Certain states, such as New York and Illinois, do offer strong privacy protections against, for example, unnecessary biometric tracking in the private sector, and California’s Consumer Privacy Act covers workers as well as consumers. Overall, though, the lack of federal-level labor law in this area makes the US something of an alternate reality to what is legal in the UK and Europe.
The Electronic Communications Privacy Act in the US allows employee monitoring for legitimate business reasons and with the worker’s consent. In Europe, Algorithm Watch has made country analyses for workplace surveillance in the UK, Italy, Sweden, and Poland. To take one high-profile example of the stark difference: In early 2024, Serco was ordered by the UK's privacy watchdog, the Information Commissioner’s Office (ICO), to stop using face recognition and fingerprint scanning systems, designed by Shopworks, to track the time and attendance of 2,000 staff across 38 leisure centers around the country. This new guidance led to more companies reviewing or cutting the technology altogether, including Virgin Active, which pulled similar biometric employee monitoring systems from 30-plus sites.
Despite a lack of comprehensive privacy rights in the US, though, worker protest, union organizing, and media coverage can provide a firewall against some office surveillance schemes. Unions such as the Service Employees International Union are pushing for laws to protect workers from black-box algorithms dictating the pace of output.
In December, Boeing scrapped a pilot of employee monitoring at offices in Missouri and Washington, which was based on a system of infrared motion sensors and VuSensor cameras installed in ceilings, made by Ohio-based Avuity. The U-turn came after a Boeing employee leaked an internal PowerPoint presentation on the occupancy- and headcount-tracking technology to The Seattle Times. In a matter of weeks, Boeing confirmed that managers would remove all the sensors that had been installed to date.
Under-desk sensors, in particular, have received high-profile backlash, perhaps because they are such an obvious piece of surveillance hardware rather than simply software designed to record work done on company machines. In the fall of 2022, students at Northeastern University hacked and removed under-desk sensors produced by EnOcean, offering “presence detection” and “people counting,” that had been installed in the school’s Interdisciplinary Science & Engineering Complex. The university provost eventually informed students that the department had planned to use the sensors with the Spaceti platform to optimize desk usage.
OccupEye (now owned by FM: Systems), another type of under-desk heat and motion sensor, received a similar reaction from staff at Barclays Bank and The Telegraph newspaper in London, with employees protesting and, in some cases, physically removing the devices that tracked the time they spent away from their desks.
Despite the fallout, Barclays later faced a $1.1 billion fine from the ICO when it was found to have deployed Sapience’s employee monitoring software in its offices, with the ability to single out and track individual employees. Perhaps unsurprisingly in the current climate, that same software company now offers “lightweight device-level technology” to monitor return-to-office policy compliance, with a dashboard breaking employee location down by office versus remote for specific departments and teams.
According to Elizabeth Anderson’s latest book Hijacked, while workplace surveillance culture and the obsession with measuring employee efficiency might feel relatively new, it can actually be traced back to the invention of the “work ethic” by the Puritans in the 16th and 17th centuries.
“They thought you should be working super hard; you shouldn’t be idling around when you should be in work,” she says. “You can see some elements there that can be developed into a pretty hostile stance toward workers. The Puritans were obsessed with not wasting time. It was about gaining assurance of salvation through your behavior. With the Industrial Revolution, the ‘no wasting time’ became a profit-maximizing strategy. Now you’re at work 24/7 because they can get you on email.”
Some key components of the original work ethic, though, have been skewed or lost over time. The Puritans also had strict constraints on what duties employers had toward their workers: paying a living wage and providing safe and healthy working conditions.
“You couldn’t just rule them tyrannically, or so they said. You had to treat them as your fellow Christians, with dignity and respect. In many ways the original work ethic was an ethic which uplifted workers.”
6 notes
·
View notes
Text
How AI & Machine Learning Are Changing UI/UX Design

Artificial Intelligence (AI) and Machine Learning (ML) are revolutionizing UI/UX design by making digital experiences more intelligent, adaptive, and user-centric. From personalized interfaces to automated design processes, AI is reshaping how designers create and enhance user experiences. In this blog, we explore the key ways AI and ML are transforming UI/UX design and what the future holds.
For more UI/UX trends and insights, visit Pixelizes Blog.
AI-Driven Personalization
One of the biggest changes AI has brought to UI/UX design is hyper-personalization. By analyzing user behavior, AI can tailor content, recommendations, and layouts to individual preferences, creating a more engaging experience.
How It Works:
AI analyzes user interactions, including clicks, time spent, and preferences.
Dynamic UI adjustments ensure users see what’s most relevant to them.
Personalized recommendations, like Netflix suggesting shows or e-commerce platforms curating product lists.
Smart Chatbots & Conversational UI
AI-powered chatbots have revolutionized customer interactions by offering real-time, intelligent responses. They enhance UX by providing 24/7 support, answering FAQs, and guiding users seamlessly through applications or websites.
Examples:
Virtual assistants like Siri, Alexa, and Google Assistant.
AI chatbots in banking, e-commerce, and healthcare.
NLP-powered bots that understand user intent and sentiment.
Predictive UX: Anticipating User Needs
Predictive UX leverages ML algorithms to anticipate user actions before they happen, streamlining interactions and reducing friction.
Real-World Applications:
Smart search suggestions (e.g., Google, Amazon, Spotify).
AI-powered auto-fill forms that reduce typing effort.
Anticipatory design like Google Maps estimating destinations.
AI-Powered UI Design Automation
AI is streamlining design workflows by automating repetitive tasks, allowing designers to focus on creativity and innovation.
Key AI-Powered Tools:
Adobe Sensei: Automates image editing, tagging, and design suggestions.
Figma AI Plugins & Sketch: Generate elements based on user input.
UX Writing Assistants that enhance microcopy with NLP.
Voice & Gesture-Based Interactions
With AI advancements, voice and gesture control are becoming standard features in UI/UX design, offering more intuitive, hands-free interactions.
Examples:
Voice commands via Google Assistant, Siri, Alexa.
Gesture-based UI on smart TVs, AR/VR devices.
Facial recognition & biometric authentication for secure logins.
AI in Accessibility & Inclusive Design
AI is making digital products more accessible to users with disabilities by enabling assistive technologies and improving UX for all.
How AI Enhances Accessibility:
Voice-to-text and text-to-speech via Google Accessibility.
Alt-text generation for visually impaired users.
Automated color contrast adjustments for better readability.
Sentiment Analysis for Improved UX
AI-powered sentiment analysis tools track user emotions through feedback, reviews, and interactions, helping designers refine UX strategies.
Uses of Sentiment Analysis:
Detecting frustration points in customer feedback.
Optimizing UI elements based on emotional responses.
Enhancing A/B testing insights with AI-driven analytics.
Future of AI in UI/UX: What’s Next?
As AI and ML continue to evolve, UI/UX design will become more intuitive, adaptive, and human-centric. Future trends include:
AI-generated UI designs with minimal manual input.
Real-time, emotion-based UX adaptations.
Brain-computer interface (BCI) integrations for immersive experiences.
Final Thoughts
AI and ML are not replacing designers—they are empowering them to deliver smarter, faster, and more engaging experiences. As we move into a future dominated by intelligent interfaces, UI/UX designers must embrace AI-powered design methodologies to create more personalized, accessible, and user-friendly digital products.
Explore more at Pixelizes.com for cutting-edge design insights, AI tools, and UX trends.
#AI in UX Design#Machine Learning UX#UX Personalization#Conversational UI#Predictive UX#AI Chatbots#Smart UX Tools#UI Automation#Voice UI Design#Inclusive UX Design#Sentiment Analysis in UX#Future of UX#AI UX Trends 2025#Figma AI Plugins#Accessibility with AI#Adaptive UI Design#UX Innovation#Human-Centered AI#Pixelizes Blog#UX Strategy
2 notes
·
View notes
Text
Top Biometric Machine Brands in India for Attendance Tracking
In today’s fast-paced work environment, ensuring accurate employee attendance is more critical than ever. From streamlining payroll processes to reducing instances of time theft, businesses are investing heavily in biometric attendance systems to manage their workforce more effectively. As India embraces digitization across sectors, the demand for efficient and touchless attendance solutions is soaring.

Biometric attendance systems use unique physical traits such as fingerprints, facial features, or iris patterns to authenticate users, making them a reliable and secure alternative to traditional punch cards or swipe systems. If you're looking to invest in a biometric solution for your organization, choosing the right brand is crucial. In this blog, we’ll look at some of the top biometric machine brands in India and the key features that make them stand out.
Why Indian Enterprises Are Shifting to Biometric Attendance Systems
The shift from manual registers and RFID cards to biometric attendance systems is driven by several factors:
Accuracy and Reliability: These systems eliminate human error and prevent buddy punching.
Integration: Modern biometric machines easily integrate with payroll and HR systems.
Security: They offer better access control by ensuring only authorized personnel can check-in or enter.
Touchless Convenience: Especially post-pandemic, facial recognition and mobile-enabled solutions offer safer options.
The result is a more accountable, productive, and secure workforce.
Key Features to Look for in a Biometric Attendance System
Before we dive into the top brands, it’s essential to know what makes a biometric attendance system effective:
Touchless operation (facial recognition or mobile check-in)
Cloud-based functionality for real-time data access
Integration with HRMS/payroll platforms
Customizable access control options
Scalability for growing enterprises
Top Biometric Machine Brands in India
Here are some of the leading brands offering advanced biometric attendance systems for Indian businesses:
1. Spintly
Spintly has emerged as a modern leader in the biometric and access control space. Known for its sleek, wireless infrastructure and mobile-first design, Spintly’s biometric attendance systems redefine how businesses manage entry and exit.
Key Features:
Cloud-based access control that eliminates the need for local servers
Touchless attendance using facial recognition or smartphone authentication
Seamless integration with payroll and HRMS
Ideal for co-working spaces, corporate offices, and enterprises
IoT-based infrastructure with Bluetooth and Wi-Fi compatibility
Spintly stands out for its ease of installation, scalability, and minimal hardware dependency - making it a top choice for tech-forward businesses across India.
2. Matrix Comsec
Matrix is a well-established Indian brand known for its advanced telecom and security solutions. It offers a wide range of biometric attendance systems, particularly suited for large enterprises.
Key Features:
Supports multiple biometric modalities like fingerprint, RFID, and face recognition
Offers real-time web-based monitoring
Comes with centralized software for attendance tracking across locations
Good for large-scale organizations needing extensive data control
Matrix is robust and customizable but may require more infrastructure and setup than newer cloud-native solutions.
3. ESSL Security
ESSL (Enterprise Software Solutions Lab) is a household name in India when it comes to biometric attendance. Their devices are widely used across schools, hospitals, and SMEs.
Key Features:
Affordable biometric machines for businesses of all sizes
Options include fingerprint, RFID, and facial recognition
Software support for basic reporting and data export
Localized customer service and availability
While not as cloud-focused as others, ESSL machines are popular for their reliability and cost-effectiveness.
4. Realtime Biometrics
Realtime is another India-based company offering a wide range of biometric attendance systems. Their devices are known for being budget-friendly and easy to deploy.
Key Features:
Focuses on small to mid-sized businesses
Supports multiple authentication methods
Basic software for time tracking and data backup
Good for quick implementation
Realtime offers good value for money, although enterprise-grade integrations may be limited compared to providers like Spintly.
5. ZKTeco India
ZKTeco is a global brand with a strong presence in India. Their biometric systems are feature-rich and cater to industries ranging from education to government institutions.
Key Features:
Extensive biometric portfolio (fingerprint, palm, face, iris)
Cloud-based software options
Integration with turnstiles and smart doors
Advanced encryption for data protection
ZKTeco systems are reliable and comprehensive but may come with a steeper learning curve and higher setup cost.
Why the Right Brand Matters
Choosing the right biometric brand isn’t just about features - it’s about support, adaptability, and long-term value. Brands like Spintly not only provide modern biometric solutions but also offer:
Remote configuration
Easy software updates
Advanced analytics
Local and global support
Zero-heavy cabling requirements
This makes them ideal partners for organizations looking to streamline operations without increasing IT complexity.
Conclusion
India’s adoption of biometric attendance systems is accelerating as businesses recognize the value of automation, accuracy, and accountability. While traditional brands still hold a significant presence, newer cloud-native solutions like Spintly are redefining the space with innovative, touchless, and mobile-first technology.
For businesses aiming to modernize attendance tracking without overhauling their infrastructure, choosing a future-ready brand is key. Whether you're running a coworking space, a corporate office, or a manufacturing unit, biometric systems offer the blend of security and simplicity every modern organization needs.
Ready to upgrade your attendance system? Start by exploring providers that bring the future of access control and biometric technology to your fingertips - like Spintly, a name at the forefront of smart workplace transformation in India.
#biometric access#biometric attendance#biometric machine#biometric authentication#spintly#access control system#mobile access#accesscontrol#access control solutions#biometrics#smartacess#visitor management system
0 notes
Text
By design, the details of how "freedom cities" would be established are laden with legalese like "federal enclaves with special economic and jurisdictional zones" or "interstate compacts." In practice, the plan is straightforward. Advocates want the federal government to set aside land to build cities exempt from federal and state laws. Instead, the cities would function as mini-dictatorships, where the CEO of each town runs everything, and the people who live and work there are subject to the boss's whims. It would be like being an employee of a controlling company, except you don't clock out at the end of the day or have a life — or rights — outside of what the boss allows you.
Along the way, DOGE also gained access to untold terabytes of data. Trump had given Musk and his operatives carte blanche to tap any unclassified system they pleased. One of their first stops: a database previously breached more than a decade ago by alleged Chinese cyberspies that contained investigative files on tens of millions of US government employees. Other storehouses thrown open to DOGE may have included federal workers’ tax records, biometric data, and private medical histories, such as treatment for drug and alcohol abuse; the cryptographic keys for restricted areas at federal facilities across the country; the personal testimonies of low-income-housing recipients; and granular detail on the locations of particularly vulnerable children.
What did DOGE want with this kind of information? None of it seemed relevant to Musk’s stated aim of identifying waste and fraud, multiple government finance, IT, and security specialists told WIRED. But in treating the US government itself as a giant dataset, the experts said, DOGE could help the Trump administration accomplish another goal: to gather much of what the government knows about a given individual, whether a civil servant or an undocumented immigrant, in one easily searchable place.
WIRED spoke with more than 150 current and former federal employees, experts, and Musk supporters across more than 20 agencies to expose the inner workings of DOGE. Many of these sources requested anonymity to speak candidly about what DOGE has done—and what it might do next.
-----
Excerpts under the cut:
Soon afterward, as WIRED first reported on February 4, a 25-year-old former X engineer named Marko Elez was granted the ability not only to read the code in the Treasury systems but also to write—or change—it. With that level of access, he (or anyone he reported to) could potentially have cut off congressionally authorized payments, effectively allowing Trump or Musk to exercise a line-item veto. More immediately ominous to people familiar with the systems was the possibility that, by tampering with the code, Elez could cause the systems, in whole or in part, to simply stop working. “It’s like knowing you have hackers on your network, but nobody lets you do anything about it,” a Treasury employee told WIRED.
. . .
Initially, Flick and officials from the CIO’s office determined that Bobba would be given anonymized, read-only access to records in the Numerical Identification System, which contains information on everyone who has ever applied for a Social Security number. On February 15, Bobba reported that there were issues with the dataset he’d been provided. Russo demanded that Bobba be given full access to “everything, including source code,” Flick recalled. This included the SSA’s Enterprise Data Warehouse, which contains the “names of spouses and dependents, work history, financial and banking information, immigration or citizenship status, and marital status,” according to Flick’s affidavit.
Later that day, the chief information officer for the whole federal government—a political appointee working out of the Office of Management and Budget—issued an opinion to Russo granting Bobba the access. Flick retired. In her affidavit, she expressed serious concerns about the potential for SSA records to be “inadvertently transferred to bad actors” and about “incredibly complex web of systems” being “broken by inadvertent user error.”
. . .
Later that month, DOGE imposed a $1 spending limit on federal employee credit cards. The move instantly roiled agencies from the National Park Service to the National Institutes of Health as employees scrambled to buy basic necessities to do their jobs. Yet again, DOGE’s move-fast ethos would put Americans’ personal data at risk.
At one SSA office, a manager confirmed to his staff that he could no longer pay the company that shreds sensitive documents. “We print a lot of shit daily,” one SSA employee told WIRED. “Stuff with people’s names, addresses, phone numbers, SSNs, bank accounts, you name it. We have giant locking trash bins we put it in, and we pay a shredding company to empty them every month.” With the new $1 limit, the employee said, a “stockpile” of sensitive data was growing, leaving workers with two options: “Shred it ourselves on regular office shredders—of which we have two, I think, and so it would take forever—or just sit on it while it piles up.”
2 notes
·
View notes
Text
Secure Your Business with CCTV Cameras in Gaya
In today's world, security is paramount, especially for businesses. Whether you run a small shop or a large enterprise, protecting your premises, assets, and employees should be a top priority. One of the most effective ways to enhance security is by installing Closed-Circuit Television (CCTV) cameras. CCTV cameras not only act as a deterrent to potential criminals but also provide valuable evidence in case of any untoward incidents. In Gaya, businesses are increasingly turning to CCTV cameras to safeguard their interests. Let's explore why CCTV cameras are essential for business security in Gaya and how you can benefit from them.

Deterrence of Criminal Activities
CCTV Camera Store in Gaya are an excellent deterrent against criminal activities such as theft, vandalism, and burglary. The mere presence of cameras can discourage potential criminals from targeting your business. Knowing that their actions are being recorded and monitored makes individuals think twice before committing a crime, thereby reducing the likelihood of incidents occurring on your premises.
Enhanced Monitoring and Surveillance
With CCTV cameras installed, you can monitor your business premises in real-time. This allows you to keep an eye on activities inside and outside your establishment, even when you're not physically present. Modern CCTV systems offer remote viewing capabilities, allowing you to access live footage from your smartphone or computer. This feature is particularly useful for business owners who travel frequently or have multiple locations.
Protection of Assets and Inventory
For businesses that deal with valuable assets or inventory, Camera Store In Gaya provide an added layer of protection. In the event of theft or damage, CCTV footage can serve as crucial evidence for insurance claims or police investigations. Additionally, by monitoring your inventory, you can prevent internal theft and ensure that your assets are secure at all times.
Employee Safety and Productivity
CCTV cameras can also contribute to the safety and productivity of your employees. By providing a secure work environment, you can boost employee morale and reduce the risk of workplace accidents or conflicts. Fire Extinguisher Store In Gaya can also help in monitoring employee performance and adherence to company policies, ensuring that everyone is on the same page.
Compliance with Regulations
In many jurisdictions, businesses are required to maintain a certain level of security, including the use of GPS Tracker system In Gaya. By installing CCTV cameras, you can ensure that your business complies with relevant regulations and avoid potential fines or penalties for non-compliance.
Cost-Effective Security Solution
Compared to other security measures, such as hiring security personnel, CCTV cameras offer a cost-effective solution for businesses of all sizes. Once installed, Automatic School bell Store In Gaya require minimal maintenance and can provide round-the-clock surveillance without the need for human intervention.
CCTV cameras are an indispensable tool for enhancing the security of your business in Gaya. By deterring criminal activities, monitoring your premises, protecting your assets, and ensuring employee safety, CCTV cameras offer a comprehensive security solution for businesses of all sizes. If you haven't already installed CCTV cameras in your establishment, now is the time to do so and secure your business against potential threats.
#Top CCTV Installation Services in Gaya#Camera Store In Gaya#CCTV Camera Store in Gaya#GPS Tracker system In Gaya#Fire Alarm Shop In Gaya#Note Currency Counting Machine Shop In Gaya#Automatic School bell Store In Gaya#Epabx and Intercom Store In Gaya#Video Door Phone Store In Gaya#Fire Extinguisher Store In Gaya#Biometric Attendance and Access control In Gaya#cctvinstallation#cctv camera#cctv
1 note
·
View note
Text
G Witch Onscreen Text: Episode 2
This is part 3 in an ongoing series where I try and document and discuss all of the text that appears on screens and monitors throughout the show! Just because I can!
<<Click here to go back to Episode 1!
(Once I have a masterpost set up I will link it here!) Let us Begin! Below the Cut!

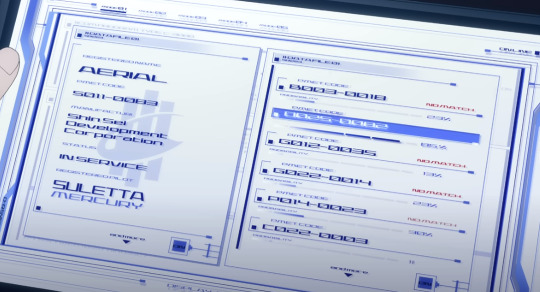
TEXT: (Lefthand side) Registered Name: AERIAL PMET CODE: 5011-0083 MANUFACTUR(ER): SHIN-SEI DEVELOPMENT CORPORATION STATUS: IN SERVICE REGISTERED PILOT: SULETTA MERCURY
At the beginning of the episode, Rouji has Haro run a program that compares Aerial's permet code and registered statistics against other registered Mobile Suits to try and find a match, and measures the probability of the two being the same type of MS. There is no direct match to any other MS by Permet Code, but the system states there's an 85% probability that it's a match for a Mobile Suit with permet code 0025-0082.
We never see the specific name of this MS, but considering that Shaddiq names "Ochs Earth" as the company that made it and proceeds to call Aerial, "...the Witch's Mobile Suit," I think it's reasonable to assume that 0025-0082 was the Permet Code for Lfrith-03.

TEXT: ALERT ACCESS CONTROL [???] [----OF ENTRY A---]
Unfortunately due to the small text of the Alert message, the fact that it scrolls, and it's brief time onscreen, its hard to make out specifically what it says. My best assumption from what we have is that it's a warning currently barring anyone from entry into the 13th Tactical Testing Sector.

TEXT: (Suletta's Asticassia ID) PILOTING DEPARTMENT ID No: LP-041 SULETTA MERCURY BIRTHPLACE: MERCURY HOUSE: NO DATA PC-CRIMINAL RECORD: NO DATA PC-BIOMETRIC SYSTEM: REGISTERED
(Below) WE ARE RESPONSIBLE UNDER COMPANY REGULATIONS FOR THE PROCESSING OF PERSONAL DATA
UNDER THESE REGULATIONS, WE ARE ALSO RESPONSIBLE FOR DATA HANDLING SUCH AS TRANSMISSION TO RECIPIENTS AND THIRD PARTIES.
PLEASE REFER TO THE FOLLOWING DOCUMENTS FOR DETAILS.
As Suletta is being questioned, we get a brief glimpse at the investigation report the interrogator was looking at before the screen cuts to black when it hits the table. Nothing super interesting here, but Suletta doesn't have a registered criminal record! Yippeeee!

TEXT: CAM: 05 MONITORING CAMERA FACILITY MANAGEMENT COMPANY
Not much to say here, this camera lets us know where Suletta is currently being held. (The Facility Management Company)
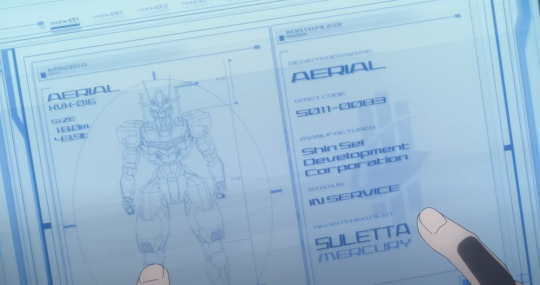
TEXT: (Lefthand Side) AERIAL XVX - 016 SIZE: 18.0m 48.9t
No point discussing the info on the right, we've already seen it, but this gives us a look at Aerial's height and weight.

TEXT: (Top Right) COM DELLING REMBRAN BENERIT GROUP
I only included this to point out that wow the display system devs made some poor choices with the UI here. Dark Blue text on Dark Backgrounds? You'd think the text would automatically lighten but I guess we'll have to wait for Ver 6.0 for that update.
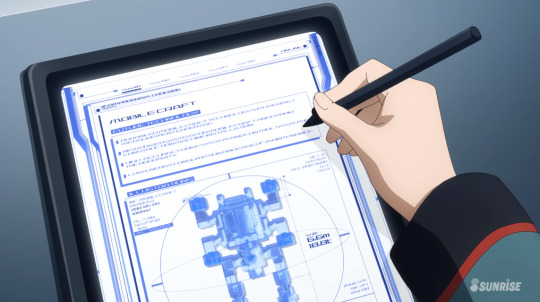
TEXT (Top half) MOBILE CRAFT FUTURE TECHNOLOGY
ADVANCED MOBILE CRAFT TECHNOLOGY WITH PERMET MEASUREMENT EXPERTISE NEW POWER SYSTEM FOR MOBILE CRAFT AND HYBRID CONSTRUCTION MACHINE INSTALLATION HIGH ACCURACY DRIVE SYSTEM AND CONTROL SYSTEM IN MICROGRAVITY LOW ENERGY CONSUMPTION AND EASE OF MAINTENNANCE
No need to discuss the bottom half, its just the height and weight of the MC which we already know. I think it's funny how many classes this school seems to have on the new and improved Mobile Craft from Future Technology. I should probably buy one too. I love you Mobile Craft.


TEXT: (Left Image) The Shin Sei Development Corporation was established in A.S. 89. Our business began with the development of integrated operating systems for mobile suits and medical devices. We have been involved in MS development and have supported welfare engineering throughout our company history.
(Right Image) Ranking: D Sales Ranking (within group companies): 151th (out of) Total 157 companies [Mobile Suit Development] Number of clients: Over 300 companies Yearly patents: Over 200
We get a lot of information about Shin Sei in this scene where Martin looks at the Company History tab on their official website. The most interesting thing being that they were founded in A.S. 89. The Vanadis Incident occured in A.S. 101, and the show proper takes place in A.S. 122, so at some point between 101 and 122, Prospera worked her way up through Shin Sei, eventually becoming its CEO.
Given that Suletta had to have been born around A.S. 105, and that in Cradle Planet, we learn that Prospera had been working within Shin Sei when Suletta was around 6, that places A.S. 111 as the earliest she was involved.
We also learn in Cradle Planet, that when Suletta is around 11, Prospera has recently been promoted within the company, and now has many people working under her. That would be around A.S. 116. When Suletta is 16, that's when Prospera tells her that she's going to school, which would be around A.S. 121, and I think it's safe to assume that she had already become president by then.
SO!! TL;DR!! It's most likely that Prospera became the president of Shin Sei at SOME point between A.S 116 and A.S 121. I'd put it somewhere in the middle, around A.S 119. (Can't wait to find out that they probably just outright state this somewhere and I did all this for nothing....)
ADDENDUM

GOD DAMNIT. I WATCHED ALL OF CRADLE PLANET TO MATH THAT SHIT OUT. WHATEVER. I CAME TO THE SAME CONCLUSION SO I WIN.

The text is too small to make out, but we DO get a small glimpse at the letter Delling sent to Miorine about unenrolling her from the school. It probably just literally says what the body guard reads out.
I think it says something that Delling doesn't even like, text his daughter. He sends an email through the official Benerit Group email account to her bodyguard who reads it for her. What a cowardly man.

TEXT: (Left) FLUSH (Right) EMERGENCY CALL UNLOCK LOCK
YES the toilet text is important to document stop fucking looking at me like that.

TEXT: NEXT STAGE TOUCH SCREEN TO CONTINUE
I'll leave the explanation of the symbolism of this scene as an exercise for the reader. [Sultry Wink]

TEXT (Above) THIS ELECTRONIC SIGNATURE IS PROOF THAT IT WAS SIGNED BY A REPRESENTATIVE OF THE BENERIT GROUP.
No way to tell what Delling is signing here, but we do get a brief look at his handwriting. It turns out his cursive is really bad, actually!
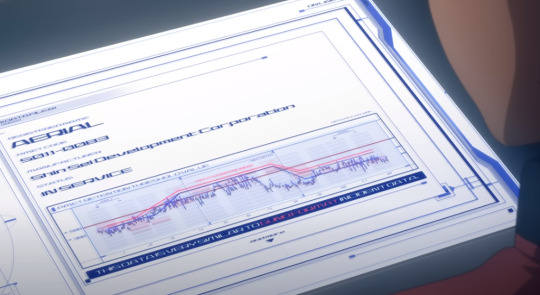
At the Shin Sei inquiry, Shaddiq shares this graph titled "PMET RETENTION THRESHOLD VALUE", stating that during the duel, Aerial's Permet Influx Values exceeded the standards set by Cathedra.
This graph can be tough to parse, so let me explain it as best I can. The blue line represents Aerial's Permet Retention during the duel. The solid dark line represents the permet retention limit imposed by cathedra on mobile suits. (At around 500) As we can see, while Aerial began the duel underneath that limit, it exceeded it for a moment (presumably when Suletta took over for Miorine and the GUND bits were activated.)
The red line above that is labelled DATA STORM INCIDENT, which is representative of the minimum Permet Retention a Gundam expresses when it is interfacing with a Data Storm. The text on the bottom reads, THIS DATA IS VERY SIMILAR TO GUND FORMAT INCIDENT DATA.
But the key thing to take note of here is that Aerial's chart just BARELY doesn't exceed the DATA STORM INCIDENT graph, meaning that, despite it exceeding Cathedra's standards, it CANNOT be directly proven that Aerial was interfacing with a Data Storm. This is actually what Prospera brings up as her main counterpoint to the accusation.

So the graph is entirely consistent with Prospera's main argument. While she can't prove that Aerial isn't a gundam, nobody else can prove that it is.
Huaaaahh!! Alright!! This one was very DENSE. If you made it all the way through, thank you very much!! As a reward, have some little gay people




[I sprinkle these stills on the ground like bird seed.]
There was definitely a lot of really interesting info in this episode, and while not a lot of it was particularly new, I think it's really a testament to the dedication of keeping things wholly consistent in this world, even for the smallest of things that no normal person watching would even bother noticing.
Also, on the Shin Sei Website, did you notice that they accidentally put 151th instead of 151st?
You can't win em all!
Click here to go to Episode 3! >>
Click here to go to the Masterpost!
36 notes
·
View notes
Text
ZKTeco Horus E1-FP Time Attendance Machine

ZKTeco Horus E1FP is one of the most advanced Access Control & time and attendance terminals existing in the market, with an incredibly compact size (almost the same size as the iPhone XS max).
Powerful facial recognition technology offering up to 3 meters recognition distance, ±30 degrees pose angle tolerance, high anti-spoof ability, support on plentiful communication protocols (Wi-Fi, 3G, 4G, Bluetooth) and worldwide network setting, optional fingerprint and RFID card modules, up to 10,000 facial templates capacity.
It is compatible with the all-in-one security & time attendance platform ZKBioSecurity and BioTime.
Functions:
• New height of facial recognition template capacity up to 1: N-10,000 facial templates • Anti-spoofing algorithm against print attacks (laser, color, and B / W photos), video attacks, and 3D mask attack • Supports multiple communication protocols: 4G, Wi-Fi, Bluetooth, and USB • 5-inch smartphone-grade IPS touch LCD monitor • Extensive Fingerprint, RFID, and TCP / IP, modules available • Extra-large 2MP CMOS with WDR function • Various further development options: embedded GPS / A-GPS, microphone, and PIR sensor
Costtocost offers the best price for the ZKTeco Horus E1-FP Time Attendance Machine. Buy now with the best price!
#uae#dubai#it solutions#costtocost#electronics#best electronics and it supplier in uae#it support#it support in dubai#business#zk#zkteco#zkteco horus E1FP#Time Attendance Machine#time & attendance system#fingerprint time attendance machine#biometric time attendance#zkteco horus#onlineshopping#dubai shopping#deals#sale#black friday sale#access control systems
0 notes