#browser protection
Explore tagged Tumblr posts
Text

#genshin impact#genshin fanart#venti#fanart#ravidraws#look at my baby the new emote is so cute it gets me like#*gothic font* “I’ll protect you”#I fully expect the pic quality to be botched bc I’m uploading from my phone’s browser but I’ll fix it I swear#Also this is like the fourth thing I’ve drawn in basically two years I’m crying#Anyway his bday is in a less than a month and I have no idea on how can I possibly lock in and do another one of these in four weeks
110 notes
·
View notes
Text
Okay, look, they talk to a Google rep in some of the video clips, but I give it a pass because this FREE course is a good baseline for personal internet safety that so many people just do not seem to have anymore. It's done in short video clip and article format (the videos average about a minute and a half). This is some super basic stuff like "What is PII and why you shouldn't put it on your twitter" and "what is a phishing scam?" Or "what is the difference between HTTP and HTTPS and why do you care?"
It's worrying to me how many people I meet or see online who just do not know even these absolute basic things, who are at constant risk of being scammed or hacked and losing everything. People who barely know how to turn their own computers on because corporations have made everything a proprietary app or exclusive hardware option that you must pay constant fees just to use. Especially young, somewhat isolated people who have never known a different world and don't realize they are being conditioned to be metaphorical prey animals in the digital landscape.
Anyway, this isn't the best internet safety course but it's free and easy to access. Gotta start somewhere.
Here's another short, easy, free online course about personal cyber security (GCFGlobal.org Introduction to Internet Safety)
Bonus videos:
youtube
(Jul 13, 2023, runtime 15:29)
"He didn't have anything to hide, he didn't do anything wrong, anything illegal, and yet he was still punished."
youtube
(Apr 20, 2023; runtime 9:24 minutes)
"At least 60% use their name or date of birth as a password, and that's something you should never do."
youtube
(March 4, 2020, runtime 11:18 minutes)
"Crossing the road safely is a basic life skill that every parent teaches their kids. I believe that cyber skills are the 21st century equivalent of road safety in the 20th century."
#you need to protect yourself#internet literacy#computer literacy#internet safety#privacy#online#password managers#security questions#identity theft#Facebook#browser safety#google#tesla#clearwater ai#people get arrested when google makes a mistake#lives are ruined because your Ring is spying on you#they aren't just stealing they are screwing you over#your alexa is not a woman it's a bug#planted by a supervillain who smirks at you#as they sell that info to your manager#oh you have nothing to hide?#then what's your credit card number?#listen I'm in a mood about this right now#Youtube
189 notes
·
View notes
Text
In these shitty times I remind you to DITCH CHROME AND GOOGLE and use a reliable browser who won't sell you and your mom.
TL;DR. DuckDuckGo both search engine and browser is a good option for everybody and everyday purpose
I'd think duckduckgo both browser and search engine is a good
If you use iPhones and Mac Safari isn't the worst.
Tor is the best in terms of privacy, but it's run by volunteers so it's better if you don't use it to watch YouTube and download stuff, it's also very slow for socials.
Brave browser is slightly better then duckduckgo, but for average use it's almost the same. Also it has had a couple of controversies overtime.
I've recently found out that duckduckgo has it's own browser as well!!!!! AND it's available on both pc and android and I believe even ios and Mac.
Duckduckgo is (mainly) a search engine that doesn't try to sell you stuff like Google, gives you what you search for unfiltered, doesn't collect your data's, AND datas are filtered and bounced around multiple times to encrypt them better.
I know ecosia is appealing because of the trees, you can still use it, but be aware that there's basically no difference between that and Google. It's not secure nor you're guaranteed the results aren't filtered according to whatever strikes them at the moment
#browser#private#privacy#search engine#google#chrome#how about we put our actions where our mouths are and don’t keep using big capital shit#Also your privacy is actually important#And I don't say that just for shits and giggles#You actively trying to protect your privacy is a huge tool against totalitarian regimes#The thing that you agree to every cookie and shit because they're annoying and you have nothing to hide and you're a public person#Is shitty propaganda that benefits those with power and they did this consciously#Fight for your privacy
12 notes
·
View notes
Text
This is pure cinematographic masterpiece. It deserves an Oscar.
#This took me wayyy too long to learn how to screen record protected videos lmao#yall better enjoy it#carlos sainz jr#f1#singapore gp 2024#asdfs dvsd#omg ive just learned that you can now edit tags on browser????#the weird tag before was a test lol
24 notes
·
View notes
Text
lmao @ mozilla putting telemetry in firefox, then saying they will "anonymize it" and "not sell it to third parties"... and then a month later they acquire an advertising broker and send your data to that, which technically means it's a first party and their little "promise" isn't broken, while still attempting to send you directed ads based on your browsing data & profit from it
#firefox really only has mv2 extension support separating them from the other major browsers#went back to ungoogled chromium until the mv2 ban kicks in and then i don't know what i'm going to do#librewolf is an option but there are some streaming websites that don't play nice with it#hopefully mv3 data protection apps improve a bit more - the ad blockers are working pretty well but they aren't as privacy-protecting yet
9 notes
·
View notes
Text
I think Drag just. Enjoys the treatment and attention (and lack of) that not talking brings about.
Say nothing, and people start subconsciously ignoring you, people are often much more interested in what is said (by others). People inadvertently let you get away with things and slip through their fingers. If you're being mute on purpose, this isn't being ignored, it's probably what you wanted, and Drag probably loves it.
But inversely, when you choose not to speak, people are also attentive to your presence. They will wonder what you want because everyone else makes their needs known and you're now an exception and an enigma- people will be drawn to solving it.
In Dragunov's case, he's a well trained soldier that stands over 6'. You'd want to guess right and make him pleased because he looks like, and absolutely could seriously injure or straight up kill you.
I don't think Sergei goes around disobeying his orders or crushing people's limbs unless absolutely necessary, but I can see it delighting him inside to know and see that his silence commands the room (and lets him slip away for some alone time or whatever else he wants to do.)
But lastly, choose not to speak and it only gets easier to remain mute as time goes on. Any intelligible word you may choose to say will be heavily analyzed, repeated, remembered. Again, people cling quite tightly to what is said. I gotta wonder if Dragunov doesn't speak because of this too sometimes.
#.dragu#as someone who's known for pulling a Dragunov often. for over a week on occasion. And more#like lmao ask me about it i could unironically talk about it a lot#just another reason i like this character#sometimes I know the kind of person who is looking for words to twist and either don't talk or it's the bare minimum#It's not the silent treatment. as much as it is just silence is great protection#and though Drag has become an incredibly strong fighter physically and can defend himself think it's protection for him too still#protecting who he is and what he loves from his job and war and oh yeah the ninjas that belong in a shonen who will use those against him#it's pretty anime tropey itself but I think a lot of his power comes from the very human will to survive#Lol I love Drag for being the Badass Normal trope tbh#bruh the ui update made tumblr so hard to use in the mobile browser so sorry if i can't fucking type and make sense
3 notes
·
View notes
Text
thank you for tagging me in the wip challenge @fenharael
Rules: In a new post, post the names of all the files in your WIP folder regardless of how non descriptive or ridiculous. Let people send you an ask with the titles that most intrigue them and then post a little snippet or tell us about them. Tag as many folk as you have WIPs.
i wish i could participate properly in the wip challenge but my wips are called “beep” “e” “jesus fucking christ” “e” “jesus fucking christ 2” “he” “e” “e” “jail”
…
that said if you wanted to participate for real … please say i tagged you……


#i write in icloud notes because i’m insane but you can password protect notes + easy access on both phone and browser#no one suspects icloud notes.#however i put all of my wips in one note and eventually it stopped opening on pc because icloud notes is buggy. so i had to split it into 2#hencse jesus fucking christ 1+2….. a beautiful name for twin sisters….#its always a surprise to click into each note. as you can imagine.#you can ask about wips if you’re curious but.#i’m sorry my shift ends in 5 minites i’m barely concous…
3 notes
·
View notes
Text
was watching a rando one piece video essay theory, the dude randomly quipped that he hates yamato, and ive never clicked off and erased my browser history of a person so fast
#the reason i erased my browser history is bc im behind 15 layers of spyware protection#so youtube doesnt let me unrecommend/block channels anymore lol. its an invasive pop up option
12 notes
·
View notes
Text
Deepfake misuse & deepfake detection (before it’s too late) - CyberTalk
New Post has been published on https://thedigitalinsider.com/deepfake-misuse-deepfake-detection-before-its-too-late-cybertalk/
Deepfake misuse & deepfake detection (before it’s too late) - CyberTalk


Micki Boland is a global cyber security warrior and evangelist with Check Point’s Office of the CTO. Micki has over 20 years in ICT, cyber security, emerging technology, and innovation. Micki’s focus is helping customers, system integrators, and service providers reduce risk through the adoption of emerging cyber security technologies. Micki is an ISC2 CISSP and holds a Master of Science in Technology Commercialization from the University of Texas at Austin, and an MBA with a global security concentration from East Carolina University.
In this dynamic and insightful interview, Check Point expert Micki Boland discusses how deepfakes are evolving, why that matters for organizations, and how organizations can take action to protect themselves. Discover on-point analyses that could reshape your decisions, improving cyber security and business outcomes. Don’t miss this.
Can you explain how deepfake technology works?
Deepfakes involve simulated video, audio, and images to be delivered as content via online news, mobile applications, and through social media platforms. Deepfake videos are created with Generative Adversarial Networks (GAN), a type of Artificial Neural Network that uses Deep Learning to create synthetic content.
GANs sound cool, but technical. Could you break down how they operate?
GAN are a class of machine learning systems that have two neural network models; a generator and discriminator which game each other. Training data in the form of video, still images, and audio is fed to the generator, which then seeks to recreate it. The discriminator then tries to discern the training data from the recreated data produced by the generator.
The two artificial intelligence engines repeatedly game each other, getting iteratively better. The result is convincing, high quality synthetic video, images, or audio. A good example of GAN at work is NVIDIA GAN. Navigate to the website https://thispersondoesnotexist.com/ and you will see a composite image of a human face that was created by the NVIDIA GAN using faces on the internet. Refreshing the internet browser yields a new synthetic image of a human that does not exist.
What are some notable examples of deepfake tech’s misuse?
Most people are not even aware of deepfake technologies, although these have now been infamously utilized to conduct major financial fraud. Politicians have also used the technology against their political adversaries. Early in the war between Russia and Ukraine, Russia created and disseminated a deepfake video of Ukrainian President Volodymyr Zelenskyy advising Ukrainian soldiers to “lay down their arms” and surrender to Russia.
How was the crisis involving the Zelenskyy deepfake video managed?
The deepfake quality was poor and it was immediately identified as a deepfake video attributable to Russia. However, the technology is becoming so convincing and so real that soon it will be impossible for the regular human being to discern GenAI at work. And detection technologies, while have a tremendous amount of funding and support by big technology corporations, are lagging way behind.
What are some lesser-known uses of deepfake technology and what risks do they pose to organizations, if any?
Hollywood is using deepfake technologies in motion picture creation to recreate actor personas. One such example is Bruce Willis, who sold his persona to be used in movies without his acting due to his debilitating health issues. Voicefake technology (another type of deepfake) enabled an autistic college valedictorian to address her class at her graduation.
Yet, deepfakes pose a significant threat. Deepfakes are used to lure people to “click bait” for launching malware (bots, ransomware, malware), and to conduct financial fraud through CEO and CFO impersonation. More recently, deepfakes have been used by nation-state adversaries to infiltrate organizations via impersonation or fake jobs interviews over Zoom.
How are law enforcement agencies addressing the challenges posed by deepfake technology?
Europol has really been a leader in identifying GenAI and deepfake as a major issue. Europol supports the global law enforcement community in the Europol Innovation Lab, which aims to develop innovative solutions for EU Member States’ operational work. Already in Europe, there are laws against deepfake usage for non-consensual pornography and cyber criminal gangs’ use of deepfakes in financial fraud.
What should organizations consider when adopting Generative AI technologies, as these technologies have such incredible power and potential?
Every organization is seeking to adopt GenAI to help improve customer satisfaction, deliver new and innovative services, reduce administrative overhead and costs, scale rapidly, do more with less and do it more efficiently. In consideration of adopting GenAI, organizations should first understand the risks, rewards, and tradeoffs associated with adopting this technology. Additionally, organizations must be concerned with privacy and data protection, as well as potential copyright challenges.
What role do frameworks and guidelines, such as those from NIST and OWASP, play in the responsible adoption of AI technologies?
On January 26th, 2023, NIST released its forty-two page Artificial Intelligence Risk Management Framework (AI RMF 1.0) and AI Risk Management Playbook (NIST 2023). For any organization, this is a good place to start.
The primary goal of the NIST AI Risk Management Framework is to help organizations create AI-focused risk management programs, leading to the responsible development and adoption of AI platforms and systems.
The NIST AI Risk Management Framework will help any organization align organizational goals for and use cases for AI. Most importantly, this risk management framework is human centered. It includes social responsibility information, sustainability information and helps organizations closely focus on the potential or unintended consequences and impact of AI use.
Another immense help for organizations that wish to further understand risk associated with GenAI Large Language Model adoption is the OWASP Top 10 LLM Risks list. OWASP released version 1.1 on October 16th, 2023. Through this list, organizations can better understand risks such as inject and data poisoning. These risks are especially critical to know about when bringing an LLM in house.
As organizations adopt GenAI, they need a solid framework through which to assess, monitor, and identify GenAI-centric attacks. MITRE has recently introduced ATLAS, a robust framework developed specifically for artificial intelligence and aligned to the MITRE ATT&CK framework.
For more of Check Point expert Micki Boland’s insights into deepfakes, please see CyberTalk.org’s past coverage. Lastly, to receive cyber security thought leadership articles, groundbreaking research and emerging threat analyses each week, subscribe to the CyberTalk.org newsletter.
#2023#adversaries#ai#AI platforms#amp#analyses#applications#Articles#artificial#Artificial Intelligence#audio#bots#browser#Business#CEO#CFO#Check Point#CISSP#college#Community#content#copyright#CTO#cyber#cyber attacks#cyber security#data#data poisoning#data protection#Deep Learning
2 notes
·
View notes
Text

wanted to see if I could watch scorpy's stream on my parents' bigass tv and now my nephew is judging me
#it's not great#there's no built in app so I'm just watching it on the browser#ignore the void beneath the tv i erased it to protect the innocent
13 notes
·
View notes
Text
Time for a new edition of my ongoing vendetta against Google fuckery!
Hey friends, did you know that Google is now using Google docs to train it's AI, whether you like it or not? (link goes to: zdnet.com, July 5, 2023). Oh and on Monday, Google updated it's privacy policy to say that it can train it's two AI (Bard and Cloud AI) on any data it scrapes from it's users, period. (link goes to: The Verge, 5 July 2023). Here is Digital Trends also mentioning this new policy change (link goes to: Digital Trends, 5 July 2023). There are a lot more, these are just the most succinct articles that might explain what's happening.
FURTHER REASONS GOOGLE AND GOOGLE CHROME SUCK TODAY:
Stop using Google Analytics, warns Sweden’s privacy watchdog, as it issues over $1M in fines (link goes to: TechCrunch, 3 July 2023) [TLDR: google got caught exporting european users' data to the US to be 'processed' by 'US government surveillance,' which is HELLA ILLEGAL. I'm not going into the Five Eyes, Fourteen Eyes, etc agreements, but you should read up on those to understand why the 'US government surveillance' people might ask Google to do this for countries that are not apart of the various Eyes agreements - and before anyone jumps in with "the US sucks!" YES but they are 100% not the only government buying foreign citizens' data, this is just the one the Swedes caught. Today.]
PwC Australia ties Google to tax leak scandal (link goes to: Reuters, 5 July 2023). [TLDR: a Russian accounting firm slipped Google "confidential information about the start date of a new tax law leaked from Australian government tax briefings." Gosh, why would Google want to spy on governments about tax laws? Can't think of any reason they would want to be able to clean house/change policy/update their user agreement to get around new restrictions before those restrictions or fines hit. Can you?
SO - here is a very detailed list of browsers, updated on 28 June, 2023 on slant.com, that are NOT based on Google Chrome (note: any browser that says 'Chromium-based' is just Google wearing a party mask. It means that Google AND that other party has access to all your data). This is an excellent list that shows pros and cons for each browser, including who the creator is and what kinds of policies they have (for example, one con for Pale Moon is that the creator doesn't like and thinks all websites should be hostile to Tor).
#you need to protect yourself#anti google#anti chrome#anti chromium#chromium based browsers#internet security#current events#i recommend firefox#but if you have beef with it#here are alternatives!#so called ai#anti artificial intelligence#anti chatgpt#anti bard#anti cloud ai#data scraping
103 notes
·
View notes
Text
does anyone else's tumblr dash glitch out and show them like. 3 sets of the same few posts in a row. because it happens to me literally like once every day. and idk why
#if it helps im on mobile browser which I understand is inherently wrong. but I can't download the app bc of parent protection on my phone#like girl I'm about to graduate tf you need parent locks on here for....
2 notes
·
View notes
Text
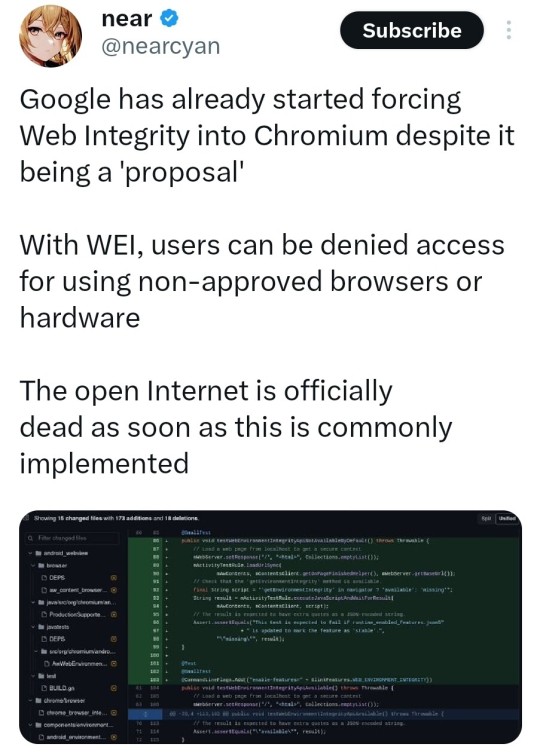
Switch to Firefox.
#google chrome#chrome#chromium#webintegrity#wei#firefox#internet#web browsers#browser#fyi#psa#google ads#billions of google users warned over dangerous ‘info email’ – don’t let your bank be emptied#google warns billions over ‘money transfer’ attack that empties your bank – how to spot dangerous message#google#google workspace#google warns billions of android users to switch on important setting that could spare you from bank raiding disaster#google warns android owners to hit ‘hidden blue button’ that stops bank draining app mistake – you’ll need to act fast#google warns billions of gmail users their account could be deleted at the end of the year – how to protect yours#google warns android owners to delete apps right now – they silently ‘steal’ from you#google emoji kitchen#google earth#google en passant#google eyes#ausgov#politas#auspol#tasgov#taspol#neoliberal capitalism
6 notes
·
View notes
Text
How to Modify the Browser Fingerprint?

So for users with special needs, how to modify the browser fingerprint information?
If you want to modify the specific fingerprint information of the fingerprint browser, you must pass some auxiliary tools, such as fingerprint browser. Fingerprint browser means a browser that can modify fingerprints and disguise fingerprints. There are many fingerprint browsers in the market, here choose an old and excellent reputation VMLogin fingerprint browser as an example:
1. First, download and install VMLogin, open the client, click “New Browser Profile” or “Create a New Profile”. You can also right-click on the created browser profile and select “Edit Profile” to continue to modify it.
2. Then enter the profile editing page, divided into the basic configuration and other configurations, users can customize or random configuration. The more detailed the modified fingerprint information, the better the anti-detection effect.
#software#incognito#protection#dataprotection#virtualbrowser#searchsafely#virtualplatform#browser#vmlogin#ecommercesuccess#ecommercemarketing#entrepreneur#branding#ecommerce#digitalmarketing#sales#marketing#youtube
5 notes
·
View notes
Text
hmm love reading a poast about computer hardware thats wrong and gonna get ppl to waste their money
#i dont wanna like start drama or shit#i5 is NOT equivalent to ryzen 7#8 gb of ram is barely enough with modern web browsers#im currently using 8.4 gb on firefox alone#you can fit most modern gpus in most modern matx cases#im running an matx case right in front of me that clearly has the room for a three fan shroud#as someone who has worked in computer hardware for 7+ years#the idea of being like “just buy a dell or hp” is absurd to me#do you even understand the concept of upgradability of desktops if you suggest them#DO YOU UNDERSTAND THE CONCEPT OF EWASTE#also most hard disks come with some sort of jostle protection#ive dropped my hard disks from my shoulder height and they boot fine#ough rant over i just needed to get that out#hashtage autism moment
5 notes
·
View notes
Text
okay i promise this is not an ad, and this is probably old news by now, but just in case there's other people like me who didn't know, there's this great tool called Relay made by our favourite web browser Firefox
basically it uses a masked email when you sign up for websites so companies don't have access to your real email, but you still get the notifications you want to receive. it stops businesses from buying your contact info too, as they only have the spoof email address provided by Relay
and best of all, you can use it totally free! you can have up to five email masks, use the Relay browser extension, and it removes email trackers too
or if you want you can pay $0.99 a month/$11.88 a year to get unlimited masks, a unique Relay email domain, and the ability to reply to emails anonymously
i believe they're also rolling out phone number protection, but i'm not sure when that's happening or if it's out already
anyway, please make use of this amazing tool to keep your data safe and private, and stop companies profiting off of you just a little bit more.
#i swear i am not being paid to say this im just autistic about firefox#firefox#firefox relay#web browsers#data privacy#data protection#fr i have only just discovered this exists even tho it came out like 3 years ago#and i thought it might be good to share it on the 'we love firefox' site#unless y'all have been lying about using firefox 🤨#either way this is a very good thing that more people should know about + use#mine#my post
3 notes
·
View notes