#cloud computing network
Explore tagged Tumblr posts
Text

Computer data Download/watch the looping video here: https://bit.ly/circuitBoard
#gif#animated gif#gif animation#motion graphics#mograph#circuit#computer#data#technology#web#internet#digital#digital data#computer network#networking#cloud computing#the cloud#motherboard#cpu
49 notes
·
View notes
Text
hey guys did you know IT is actually kinda neat
#i say as ive been in this IT course for less than one week#and i definitely wont regret this statement once we get into networks and cloud computing#delete later/
2 notes
·
View notes
Text
Open-Source Platform Cuts Costs for Running AI - Technology Org
New Post has been published on https://thedigitalinsider.com/open-source-platform-cuts-costs-for-running-ai-technology-org/
Open-Source Platform Cuts Costs for Running AI - Technology Org
Cornell researchers have released a new, open-source platform called Cascade that can run artificial intelligence (AI) models in a way that slashes expenses and energy costs while dramatically improving performance.
Artificial intelligence hardware – artistic interpretation. Image credit: Alius Noreika, created with AI Image Creator
Cascade is designed for settings like smart traffic intersections, medical diagnostics, equipment servicing using augmented reality, digital agriculture, smart power grids and automatic product inspection during manufacturing – situations where AI models must react within a fraction of a second. It is already in use by College of Veterinary Medicine researchers monitoring cows for risk of mastitis.
With the rise of AI, many companies are eager to leverage new capabilities but worried about the associated computing costs and the risks of sharing private data with AI companies or sending sensitive information into the cloud – far-off servers accessed through the internet.
Also, today’s AI models are slow, limiting their use in settings where data must be transferred back and forth or the model is controlling an automated system.
A team led by Ken Birman, professor of computer science in the Cornell Ann S. Bowers College of Computing and Information Science, combined several innovations to address these concerns.
Birman partnered with Weijia Song, a senior research associate, to develop an edge computing system they named Cascade. Edge computing is an approach that places the computation and data storage closer to the sources of data, protecting sensitive information. Song’s “zero copy” edge computing design minimizes data movement.
The AI models don’t have to wait to fetch data when reacting to an event, which enables faster responses, the researchers said.
“Cascade enables users to put machine learning and data fusion really close to the edge of the internet, so artificially intelligent actions can occur instantly,” Birman said. “This contrasts with standard cloud computing approaches, where the frequent movement of data from machine to machine forces those same AIs to wait, resulting in long delays perceptible to the user.”
Cascade is giving impressive results, with most programs running two to 10 times faster than cloud-based applications, and some computer vision tasks speeding up by factors of 20 or more. Larger AI models see the most benefit.
Moreover, the approach is easy to use: “Cascade often requires no changes at all to the AI software,” Birman said.
Alicia Yang, a doctoral student in the field of computer science, was one of several student researchers in the effort. She developed Navigator, a memory manager and task scheduler for AI workflows that further boosts performance.
“Navigator really pays off when a number of applications need to share expensive hardware,” Yang said. “Compared to cloud-based approaches, Navigator accomplishes the same work in less time and uses the hardware far more efficiently.”
In CVM, Parminder Basran, associate research professor of medical oncology in the Department of Clinical Sciences, and Matthias Wieland, Ph.D. ’21, assistant professor in the Department of Population Medicine and Diagnostic Sciences, are using Cascade to monitor dairy cows for signs of increased mastitis – a common infection in the mammary gland that reduces milk production.
By imaging the udders of thousands of cows during each milking session and comparing the new photos to those from past milkings, an AI model running on Cascade identifies dry skin, open lesions, rough teat ends and other changes that may signal disease. If early symptoms are detected, cows could be subjected to a medicinal rinse at the milking station to potentially head off a full-blown infection.
Thiago Garrett, a visiting researcher from the University of Oslo, used Cascade to build a prototype “smart traffic intersection.”
His solution tracks crowded settings packed with people, cars, bicycles and other objects, anticipates possible collisions and warns of risks – within milliseconds after images are captured. When he ran the same AI model on a cloud computing infrastructure, it took seconds to sense possible accidents, far too late to sound a warning.
With the new open-source release, Birman’s group hopes other researchers will explore possible uses for Cascade, making AI applications more widely accessible.
“Our goal is to see it used,” Birman said. “Our Cornell effort is supported by the government and many companies. This open-source release will allow the public to benefit from what we created.”
Source: Cornell University
You can offer your link to a page which is relevant to the topic of this post.
#A.I. & Neural Networks news#agriculture#ai#ai model#applications#approach#artificial#Artificial Intelligence#artificial intelligence (AI)#augmented reality#Bicycles#Cars#cascade#Cloud#cloud computing#cloud computing infrastructure#collisions#Companies#computation#computer#Computer Science#Computer vision#computing#dairy#data#data storage#Design#Developments#diagnostics#Disease
2 notes
·
View notes
Text
CBDC technology partner India
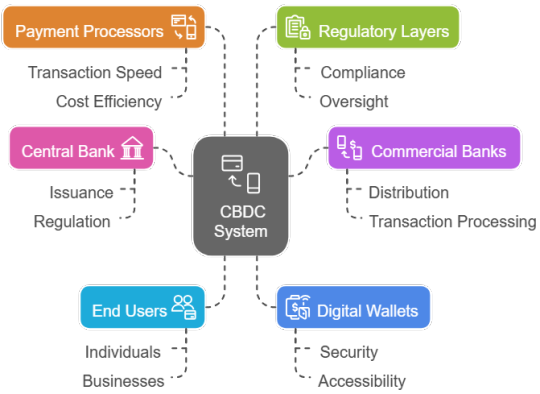
As CBDCs become a global reality, Prodevans equips banks with everything needed to enter the digital currency ecosystem. We provide full-spectrum CBDC implementation — including compliant architecture, token management, real-time reconciliation, secure wallet enablement, and 24/7 L1/L2 support. Trusted for our role in India’s national rollout, we help institutions go beyond pilots to scalable, production-ready platforms ensuring seamless end- user readiness. Our services ensure central bank compliance while delivering performance, observability, and rapid response to evolving regulatory needs. Whether you’re in the pilot phase or preparing for production rollout, Prodevans supports your CBDC journey at every step.
OUR ADDRESS
403, 4TH FLOOR, SAKET CALLIPOLIS, Rainbow Drive, Sarjapur Road, Varthurhobli East Taluk, Doddakannelli, Bengaluru Karnataka 560035
OUR CONTACTS
+91 97044 56015
#CBDC (Central Bank Digital Currency)#Cloud Computing & Cloud Services#Application Modernization#360° Monitoring (Server#Application#Database & Virtualization Monitoring)#Identity & Access Management (IAM)#Automation (incl. ML‑driven#Ansible#network/cloud automation)#DevOps Tools & Support#Infrastructure Management (IaaS/PaaS/SaaS#orchestration#orchestration tools)
0 notes
Text
Final Year Projects That Impress and Inspire
Stand out with smart, practical final year projects in tech, science, and engineering streams.
#cyber security projects for final year students#cyber security projects for final year#web development projects for final year#final year projects for cse#python projects for final year students#network security projects for final year students#cyber security final year project#data science final year projects#app development projects for final year#cloud computing projects for final year students#best web development projects for final year students#web development project for final year#final year project for cyber security#cloud computing final year project#aws projects for final year github#best computer science projects for final year#best computer science final year projects#best final year projects for it students#best major project for cse#best project for computer science final year#best projects for it final year#best python projects for final year students#cloud based final year projects#cloud computing based projects for final year#cloud computing projects final year#cloud projects for final year students
0 notes
Text
Industry 4.0: Powering the Next Industrial Revolution with Intelligence, Connectivity, and Automation
The world is undergoing a radical transformation. As we move deeper into the 21st century, the fusion of digital, physical, and biological systems is reshaping how we manufacture, operate, and innovate. This revolution has a name: Industry 4.0—the fourth industrial revolution. It represents a new era where smart technology, real-time data, automation, and interconnected networks converge to…
#5G Connectivity#Additive Manufacturing#advanced robotics#Artificial intelligence#Automation#Big Data Analytics#Blockchain#Cloud Computing#connected industry#Cyber-physical systems#data-driven operations#Digital Transformation#Digital twin#Edge computing#fourth industrial revolution#IIoT#Industrial Networking#Industry 4.0#intelligent systems#manufacturing innovation#next-gen industry#Predictive maintenance#Real-time analytics#Robotics#smart factory#Smart Grid#Smart logistics#Smart manufacturing#SolveForce#Supply Chain Visibility
0 notes
Text
The advantages of Computer Networks: Enhancing Connectivity & Efficiency
Computer networks form the backbone of modern communication, business operations, and data management, enabling seamless connectivity and resource sharing. Whether in workplaces, homes, or global enterprises, networking has transformed the way we exchange information. Here’s why computer networks are essential for efficiency, security, and collaboration. 1. Seamless Communication &…
#business connectivity#cloud storage solutions#computer networking benefits#digital collaboration#IT infrastructure efficiency#network performance optimization#secure data sharing
1 note
·
View note
Text
IoT in Action: Transforming Industries with Intelligent Connectivity

The Power of Connectivity
The Internet of Things (IoT) has become a cornerstone of innovation, as it reimagines industries and redefines the way business is conducted. In bridging the physical and digital worlds, IoT enables seamless connectivity, smarter decision-making, and unprecedented efficiency. Today, in the competitive landscape, intelligent connectivity is no longer just a technology advancement; for businesses wanting to be relevant and continue to thrive, it is now a strategic imperative.
IoT is not simply about connecting devices; it’s about creating ecosystems that work collaboratively to drive value. With industries relying heavily on real-time data and actionable insights, IoT-powered connectivity has become the backbone of operational excellence and growth. Let’s explore how this transformative technology is revolutionizing key sectors, with a focus on how businesses can leverage it effectively.
Applications of IoT in Key Industries
1.Smart Manufacturing: Efficiency Through Connectivity
Manufacturing has embraced IoT as a tool to streamline operations and boost productivity. By embedding sensors in machinery and integrating real-time monitoring systems, manufacturers can:
Predict and Prevent Downtime: IoT-enabled predictive maintenance reduces unplanned outages, saving time and money.
Optimize Resource Allocation: Smart systems track inventory, raw materials, and energy consumption, ensuring optimal usage.
Enhance Quality Control: Real-time data from production lines helps identify defects early, maintaining high-quality standards.
Example: A global automotive manufacturer integrated IoT sensors into its assembly lines, reducing equipment downtime by 25% and improving production efficiency by 30%. The ability to monitor machinery health in real time transformed their operations, delivering significant cost savings.
2.Healthcare: Improve Patient Outcomes
In healthcare, IoT has been a game-changer in enabling connected medical devices and systems that enhance patient care and operational efficiency. The main applications include:
Remote Patient Monitoring: Devices track vital signs in real time, allowing healthcare providers to offer timely interventions.
Smart Hospital Systems: IoT-enabled equipment and sensors optimize resource utilization, from patient beds to medical supplies.
Data-Driven Decisions: IoT integrates patient data across systems, providing actionable insights for personalized treatment plans.
Example: A major hospital has put into operation IoT-enabled wearables for chronic disease management. This solution reduced the number of readmissions to hospitals by 20% and empowered patients to take an active role in their health.
3.Retail: Revolutionizing Customer Experiences
IoT is revolutionizing retail through increased customer interaction and streamlined operations. Connected devices and smart analytics allow retailers to:
Personalize Shopping Experiences: IoT systems track customer preferences, offering tailored recommendations in real time.
Improve Inventory Management: Smart shelves and sensors keep stock levels optimal, reducing wastage and improving availability.
Enable Smooth Transactions: IoT-driven payment systems make checkout easier and much faster, increasing customers’ convenience
Example: A retail chain leveraged IoT to integrate smart shelves that automatically update inventory data. This reduced out-of-stock situations by 40%, improving customer satisfaction and driving higher sales.
Role of Intelligent Connectivity in Business Transformation
Intelligent connectivity lies at the heart of IoT’s transformative potential. By connecting devices, systems, and processes, businesses can:
Accelerate Decision-Making: Real-time data sharing enables faster, more informed decisions, giving companies a competitive edge.
It increases collaboration by allowing smooth communication between departments and teams, making the entire system more efficient.
Adapt to Market Dynamics: IoT enables companies to respond quickly to changes in demand, supply chain disruptions, or operational challenges.
Intelligent connectivity is not just about technology; it’s about creating value by aligning IoT solutions with business objectives. This strategic approach guarantees that IoT investments will deliver measurable outcomes, from cost savings to improved customer loyalty.
How Tudip Technologies Powers Intelligent Connectivity
Tudip Technologies specializes in designing and implementing IoT solutions that drive meaningful transformation for businesses. With a focus on innovation and collaboration, Tudip ensures that its clients achieve operational excellence through intelligent connectivity.
Tailored Solution for Every Business Industry
Tudip understands that no two businesses are alike. By customizing IoT strategies to address specific challenges, Tudip helps clients unlock the full potential of connectivity. Examples include:
Smart Supply Chains: Implementing IoT systems that provide real-time visibility into inventory and logistics, reducing delays and improving efficiency.
Energy Management: Developing IoT frameworks to monitor and optimize energy usage, driving sustainability and cost savings.
Healthcare Innovations: Designing networked medical devices that allow remote patient monitoring and data integration without a hitch.
The Future of Connected Systems
The demand for intelligent connectivity will keep increasing as the industries continue to evolve. Emerging trends in IoT include edge computing, 5G networks, and AI-powered analytics, which promise to redefine possibilities for connected ecosystems.
Businesses that embrace these advancements stand to gain:
Greater Resilience: IoT enables adaptive systems that can withstand market fluctuations and operational challenges.
Enhanced Innovation: Connected technologies open doors to new business models, revenue streams, and customer experiences.
Sustainable Growth: IoT optimizes resources and processes, contributing to long-term environmental and economic sustainability.
The future belongs to those who see connectivity not just as a technological tool but as a strategic enabler of transformation. The right partner will help businesses transform IoT from a concept into a competitive advantage.
Conclusion: Embracing Intelligent Connectivity with Tudip
IoT is not just changing the way businesses operate—it’s redefining what’s possible. From manufacturing and healthcare to retail and beyond, intelligent connectivity is driving innovation, efficiency, and growth across industries.
Tudip Technologies is at the forefront of this transformation, offering customized IoT solutions that deliver real results. By prioritizing collaboration, adaptability, and measurable outcomes, Tudip ensures that its clients stay ahead in an increasingly connected world.
Now is the time to embrace the power of IoT and unlock its potential for your business. With Tudip as your partner, the journey to intelligent connectivity is not just achievable—it’s inevitable.
Click the link below to learn more about the blog IoT in Action: Transforming Industries with Intelligent Connectivity https://tudip.com/blog-post/iot-in-action-transforming-industries-with-intelligent-connectivity/
#Tudip#IoT#intelligent connectivity#real-time data#predictive maintenance#smart manufacturing#remote patient monitoring#healthcare IoT#retail IoT#smart shelves#supply chain optimization#edge computing#AI-powered analytics#5G networks#industrial IoT#connected devices#digital transformation#operational efficiency#business intelligence#automation#data-driven decision-making#IoT solutions#smart systems#enterprise IoT#IoT-powered connectivity#sustainable growth#technology innovation#machine learning#cloud computing#smart sensors
0 notes
Text
AWS Network Firewall: Flow-Based Control Improves Security

AWS Network Firewall
Using AWS Network Firewall for Flow Management Improves Network Security
AWS Network Firewall manages stateful network firewalls and intrusion detection and prevention. It lets you apply security rules to VPC network traffic for better control. This blog article describes flow capture and flow flush, new AWS Network Firewall technologies that increase network visibility and security policy enforcement. While flow flush selectively terminates some or all flows, flow capture provides complete access into current network flows for monitoring and troubleshooting. These features help with network monitoring, troubleshooting, policy changes, and security circumstances that need isolating infected computers quickly.
Traffic flow is permanent if the firewall allows it. For compliance with your revised security needs, you may want to analyse and re-apply the new policy on existing flows after changing firewall rules, such as switching from a broader to a more targeted firewall policy.
This is especially beneficial in fast-paced security scenarios or dynamic cloud settings with changing security rules. These new features allow users better insight and control over this crucial firewall activity by natively recognising active flows and selectively flushing their connection data from the firewall's inspection engine. You may maintain network policy enforcement during scheduled security upgrades or security events by flushing dubious network traffic flows.
The AWS Network Firewall API and AWS Management Console offer these features.
Before AWS starts employing these new functionalities, let's examine some new terminology.
Terminology comprehension:
AWS Network Firewall's active flow is a monitored network connection with a uniquely identified source IP, destination IP, source port, destination port, and protocol. Flow capture and flush characteristics refer to active network flows as non-closed. This includes TCP sessions in the NEW or ESTABLISHED stage.
Flow filters match active network flows based on one or more parameters, such as source IP address, destination IP address, source port, destination port, or protocol. One flow filter matches several network flows that meet requirements.
This firewall function captures all active flows at a certain period using the supplied flow filter or filters. This functionality lets you see network traffic, security events, and flows before flushing. According to your flow filter(s), flow flush flushes a subset of active flows from the firewall flow table at a certain time. After flushing, packets are appraised as midstream flows based on stream exception criteria.
Summary: Flow capture and flush workflow
The open-source intrusion detection and prevention system Suricata is used by AWS Network Firewall for stateful inspection. When evaluating VPC traffic, the firewall stores detailed connection status data in a flow table. This means the firewall knows the full context of every network connection, not simply packets.
Depending on flow filter criteria like IP address, port, or protocol, you may need to flush flows to clear all active flows (during troubleshooting or maintenance) or selectively (during firewall rule updates, to flush long-running flows). Either flush flows directly using pre-specified filters or catch flows for examination before flushing. The firewall operation history lets you track and verify capture and flush actions.
Check out the flush and flow capture features:
These functions are accessible via console:
Enter the Amazon VPC console after login into AWS management.
Select Firewalls under Network Firewall in the navigation pane.
Firewalls: Select the firewall to collect or flush flows.
Firewall activities includes Configure flow capture and flush.
Capturing flow
Using full or partial 5-tuple filters to capture active flows is covered here. In the same VPC, AWS Network Firewall checks traffic on subnets 10.0.1.0/24 and 10.0.2.0/24. Find and flush active TCP port 80 traffic from 10.0.1.0/24 to 10.0.2.0/24.
Use the console to capture flow:
Select Configure Flow Capture to discover active flows. A new window appears.
Select Availability Zone.
The destination or source address must be entered.
Protocol (ICMP, TCP, UDP, IPv6-ICMP, or SCTP), Source Port, Destination Port, and Minimum Age of Flow are optional.
Select “Add filter.” Add up to 20 filters using entire or partial 5-tuple combinations.
Select “Start capture.”
Only one filter is needed to catch TCP port 80 traffic from subnet 10.0.1.0/24 to 10.0.2.0/24. Additional filters are shown to demonstrate filter choices. Specialised filters speed up operation.
After capture, the flow operation displays filter flows.
Flushing
Learn how to flush flows using a whole or partial 5-tuple in this section. Use the capture approach in the previous section to detect active flows before flushing. You may also specify new filters to flush certain active flows, starting a new flush operation.
Console-initiated flow flush:
Option 1: Record, erase
Select “Configure Flow.” Use the Configure flow capture process to cleanse flows that match the filters you previously defined.
Select Start flush in to flush.
Option 2: Direct flush
For firewall operations, choose “Set up flow flush”.
Set filter settings.
Start flushing.
You may inspect flushed flows after the flow flush using either option.
You can collect and flush flow to validate flushing again. Clients usually rejoin after flushing flows. The firewall's flow table and flow capture data reveal these retries. Minimum age can be used as a filter to reduce repeat flows in flow capture data.
For the stateful engine of your firewall, AWS Network Firewall flow logs show flushed flows. These entries show the flow's previous condition and the rationale field's flushed status.
Historical firewall operations
The Firewall operation history provides capture and flush actions from the preceding 12 hours using AZ-specific operation IDs. Any operation above 12 hours is immediately deleted. Click on a Flow operation ID to view capture or flush flow operation details.
What to know:
One flow capture or flush per AZ per firewall is allowed. If your firewall endpoints are in distinct AZs, you can capture or flush flows simultaneously.
Use Minimum age in Filter settings to identify or flush long-running flows. Only flows active for five minutes or longer are considered when the Minimum Age is 300 seconds.
The firewall policy's stream exception policy applies to packets that reach it after their flow state has been flushed. The reject stream exception policy is recommended for most applications.
Due to the distributed firewall technology, firewall hosts may perform flow capture and flush operations differently. The firewall distributes capture and flush actions instead than executing them in real time.
These traits support IPv4 and IPv6 flows.
For auditing, AWS CloudTrail logs flow capture and flush operations as management events.
In conclusion
This post showed you how to utilise flow capture and flush to detect and clear out existing flows and test your security configurations, including stream exception policies, as needed. These new features allow organisations to monitor network traffic, respond quickly to security problems, and apply updated security policies consistently to all active connections. These features are enabled by default for new and current clients and are free.
#technology#technews#govindhtech#news#technologynews#cloud computing#AWS Network Firewall#Network Firewall#Flow capture and flow flush#Flow capture#flow flush
0 notes
Text
What If DNA Could Store All Human Knowledge 2025

What If DNA Could Store All Human Knowledge 2025
Imagine a future where the entire scope of human knowledge — every book, every film, every scientific discovery, and every moment of recorded history — could be encoded and stored inside something as small and essential as a strand of DNA. This idea is no longer purely science fiction. It is based on emerging scientific breakthroughs that combine the powers of biotechnology and information science. So, what would the world look like if DNA could really store all human knowledge? Let’s dive deep into the concept, its implications, and the possibilities it might unlock for the future of information, humanity, and even consciousness itself. Understanding DNA as a Data Storage Medium DNA, the molecule that carries genetic instructions in all living organisms, is incredibly dense when it comes to information storage. Just four nucleotide bases — adenine (A), thymine (T), cytosine (C), and guanine (G) — can be arranged in sequences that represent binary data (0s and 1s), much like the data stored on your phone or computer. In fact, researchers have already successfully encoded images, videos, entire books, and even operating systems into strands of synthetic DNA. For example, in a famous experiment, scientists encoded Shakespeare’s sonnets, an audio file of Martin Luther King Jr.'s “I Have a Dream” speech, and a JPEG image of the Mona Lisa into DNA and retrieved it back with nearly perfect accuracy. The Benefits of Using DNA to Store Human Knowledge Storing data in DNA comes with several major advantages over traditional digital storage systems: - 🧬 Extreme Density: DNA can store up to 215 petabytes (215 million gigabytes) per gram. - 🧬 Longevity: DNA can last for thousands of years if stored in a cool, dry place. Digital hard drives, in contrast, degrade after a few decades. - 🧬 Stability: Unlike magnetic tapes or SSDs that are prone to failure, DNA remains chemically stable for centuries. - 🧬 Universality: DNA is universal, meaning it can be read and copied by any biological system — making it a kind of "future-proof" data format. Now, imagine being able to store the entire internet inside a test tube. This is not a metaphor — it’s a real projection of future possibilities. How Would This Work in Practice? To make DNA storage practical on a global scale, a few technical challenges would need to be solved: - Encoding data into DNA involves converting binary code into sequences of A, T, C, and G. - Synthetic DNA is created using chemical processes that place these sequences in the desired order. - Reading the information back requires sequencing the DNA and decoding it into digital data. At present, this process is expensive and slow. However, rapid advances in biotechnology and AI-driven lab automation are reducing both cost and time. Within a few decades, we could see commercial DNA data storage systems as viable alternatives to cloud storage and hard drives.




Social and Scientific Implications If DNA becomes the ultimate storage device for human knowledge, it could change our society in numerous ways: 1. Revolutionizing Libraries and Archives Physical and digital libraries today consume vast amounts of space, energy, and maintenance. DNA-based libraries would require just a fraction of that space and could survive natural disasters, electromagnetic pulses, or even global internet blackouts. Imagine a tiny capsule carrying every piece of literature, every film, every academic journal — not on a server or in a vault, but in a genetic capsule you could carry in your pocket. 2. Personalized Knowledge Storage People might someday choose to carry personalized knowledge banks encoded in DNA. These could include medical records, learning materials, or even their entire family history. These capsules could be implanted subcutaneously or kept as heirlooms. 3. Integration with Human DNA (A Controversial Twist) The idea of integrating human knowledge directly into a person’s DNA is extremely controversial. But in theory, synthetic sequences could be inserted into non-coding (junk) DNA regions in human cells. This would not impact biological function but could allow for a permanent, inheritable archive of information. While this would raise significant ethical, biological, and privacy concerns, it opens the door to profound possibilities — like transmitting encyclopedic knowledge through generations. Ethical, Legal, and Privacy Concerns This kind of transformative technology doesn’t come without questions: - Who owns the DNA containing human knowledge? - Could it be hacked, corrupted, or stolen? - What if someone stores harmful, illegal, or misleading data? - Should human genomes be used as storage at all? Just like the internet needed laws, standards, and security protocols, DNA data storage will need ethical guidelines and regulatory oversight. Philosophical Questions The concept touches on deep philosophical questions as well: - What is the essence of human knowledge? - If DNA can carry all knowledge, does it bring us closer to a form of digital immortality? - Could one eventually upload parts of their consciousness, memories, or identity using DNA as a carrier? While those questions may remain speculative for now, they are no longer just the musings of science fiction writers — they are becoming real issues that future generations might confront. Potential Drawbacks and Limitations Despite the promise, several barriers still exist: - High Cost: Encoding data into DNA remains expensive and slow. - Read/Write Speeds: Accessing DNA-based data is slower than with digital drives. - Data Mutability: DNA is very stable, but in biological systems, it can mutate. This might be a concern if synthetic DNA interacts with living organisms. However, given the pace of innovation in biotechnology, machine learning, and nanotechnology, these issues may become solvable sooner than we expect. Final Thoughts Storing all human knowledge in DNA is not only feasible — it may become essential. As digital data creation continues to grow exponentially, we’re quickly reaching the physical and economic limits of traditional storage systems. DNA offers a biologically inspired solution with unmatched density, durability, and universality. So, what if DNA could store all human knowledge? The answer might be this: it would change everything — from how we preserve our past to how we shape our future. We would no longer be limited by hard drives or server farms. Instead, we could embed the legacy of humanity into the very fabric of life. And perhaps, one day, a strand of DNA floating in a glass vial could contain the entire story of civilization — all within a few microscopic coils. 📚 Explore our other futuristic topics: - What If Dreams Could Be Recorded and Played Back 2025 https://www.edgythoughts.com/what-if-dreams-could-be-recorded-and-played-back-2025 - What If Humans Could Communicate via Brain-to-Brain Networks 2025 https://www.edgythoughts.com/what-if-humans-could-communicate-via-brain-to-brain-networks-2025 🌐 For more context, visit the Wikipedia page on DNA digital data storage: https://en.wikipedia.org/wiki/DNA_digital_data_storage Read the full article
#1#2#2025-01-01t00:00:00.000+00:00#2025https://www.edgythoughts.com/what-if-dreams-could-be-recorded-and-played-back-2025#2025https://www.edgythoughts.com/what-if-humans-could-communicate-via-brain-to-brain-networks-2025#215#215000000#3#academicjournal#adenine#archive#automation#binarycode#binarydata#biologicalsystem#biotechnology#byte#capsule(fruit)#cell(biology)#chemicalprocess#chemicalsubstance#civilization#cloud#cloudstorage#communicationprotocol#computer#computerdatastorage#concept#consciousness#cost
0 notes
Text
🌐 The cloud didn’t vanish. It rained. And something new began to grow. Explore The Last Server Farm, a story of endings, beginnings, and the quiet revolution of decentralized networks. Read now: https://wp.me/p19z04-Oc #DecentralizedInternet #DigitalSovereignty #PeerToPeer #TheLastServerFarm
#cloud collapse#data centers#decentralized infrastructure#decentralized internet#digital resilience#digital sovereignty#edge computing#Keiran#mesh networks#peer-to-peer networks#post-cloud era#sustainable technology#The Last Server Farm#voice of the vortex#web3
0 notes
Text
Empower Your Business with Dedicated IT Resources from Quarec Resources Pvt. Ltd.

At Quarec Resources Pvt. Ltd., we provide top-tier Dedicated IT Resources to propel your business forward. Our skilled IT professionals seamlessly integrate with your team, offering expertise in software development, system administration, network management, and more. By choosing our dedicated resources, you gain flexibility, cost-efficiency, and the ability to swiftly adapt to evolving technological demands. Partner with Quarec to ensure your IT operations are robust, scalable, and aligned with your strategic goals.
#Dedicated IT Resources#IT Staff Augmentation#Dedicated IT#Software Development Team#System Administration Services#Network Management Solutions#IT Outsourcing#Remote IT Support#IT Consulting#Cloud Computing Services#Cybersecurity Solutions#Data Analytics Services#IT Project Management#Technical Support Services#IT Infrastructure Management
0 notes
Text

Inspired by a vision to bridge technological gaps and foster growth, our journey as a black minority-owned business began eight years ago. Over this time, we've honed our expertise in IT consulting, Cyber Security, Web/Software development, strategic sourcing, and staff augmentation, serving a wide spectrum of industries with dedication and innovation. From county and city governments to healthcare, insurance, and beyond, we've navigated challenges, forged partnerships, and delivered impactful solutions that drive progress. Our commitment to excellence, diversity, and community empowerment fuels every project we undertake, making us a trusted ally in your journey towards digital transformation. As we continue to evolve and innovate, we invite you to join hands with us and unlock new possibilities for your organization. Contact us today, and let's build a brighter future together!
0 notes
Text
New AI noise-canceling headphone technology lets wearers pick which sounds they hear - Technology Org
New Post has been published on https://thedigitalinsider.com/new-ai-noise-canceling-headphone-technology-lets-wearers-pick-which-sounds-they-hear-technology-org/
New AI noise-canceling headphone technology lets wearers pick which sounds they hear - Technology Org
Most anyone who’s used noise-canceling headphones knows that hearing the right noise at the right time can be vital. Someone might want to erase car horns when working indoors but not when walking along busy streets. Yet people can’t choose what sounds their headphones cancel.
A team led by researchers at the University of Washington has developed deep-learning algorithms that let users pick which sounds filter through their headphones in real time. Pictured is co-author Malek Itani demonstrating the system. Image credit: University of Washington
Now, a team led by researchers at the University of Washington has developed deep-learning algorithms that let users pick which sounds filter through their headphones in real time. The team is calling the system “semantic hearing.” Headphones stream captured audio to a connected smartphone, which cancels all environmental sounds. Through voice commands or a smartphone app, headphone wearers can select which sounds they want to include from 20 classes, such as sirens, baby cries, speech, vacuum cleaners and bird chirps. Only the selected sounds will be played through the headphones.
The team presented its findings at UIST ’23 in San Francisco. In the future, the researchers plan to release a commercial version of the system.
[embedded content]
“Understanding what a bird sounds like and extracting it from all other sounds in an environment requires real-time intelligence that today’s noise canceling headphones haven’t achieved,” said senior author Shyam Gollakota, a UW professor in the Paul G. Allen School of Computer Science & Engineering. “The challenge is that the sounds headphone wearers hear need to sync with their visual senses. You can’t be hearing someone’s voice two seconds after they talk to you. This means the neural algorithms must process sounds in under a hundredth of a second.”
Because of this time crunch, the semantic hearing system must process sounds on a device such as a connected smartphone, instead of on more robust cloud servers. Additionally, because sounds from different directions arrive in people’s ears at different times, the system must preserve these delays and other spatial cues so people can still meaningfully perceive sounds in their environment.
Tested in environments such as offices, streets and parks, the system was able to extract sirens, bird chirps, alarms and other target sounds, while removing all other real-world noise. When 22 participants rated the system’s audio output for the target sound, they said that on average the quality improved compared to the original recording.
In some cases, the system struggled to distinguish between sounds that share many properties, such as vocal music and human speech. The researchers note that training the models on more real-world data might improve these outcomes.
Source: University of Washington
You can offer your link to a page which is relevant to the topic of this post.
#A.I. & Neural Networks news#ai#Algorithms#amp#app#artificial intelligence (AI)#audio#baby#challenge#classes#Cloud#computer#Computer Science#data#ears#engineering#Environment#Environmental#filter#Future#Hardware & gadgets#headphone#headphones#hearing#human#intelligence#it#learning#LED#Link
2 notes
·
View notes
Text
Trending Final Year Projects for 2025
Choose from the latest and most in-demand project topics across engineering and technology domains.
#cyber security projects for final year students#cyber security projects for final year#web development projects for final year#final year projects for cse#python projects for final year students#network security projects for final year students#cyber security final year project#data science final year projects#app development projects for final year#cloud computing projects for final year students#best web development projects for final year students#web development project for final year#final year project for cyber security#cloud computing final year project#aws projects for final year github#best computer science projects for final year#best computer science final year projects#best final year projects for it students#best major project for cse#best project for computer science final year#best projects for it final year#best python projects for final year students#cloud based final year projects#cloud computing based projects for final year#cloud computing projects final year#cloud projects for final year students
0 notes
Text
Something to think about.
1 note
·
View note