#configure Facebook
Explore tagged Tumblr posts
Text
Blocking Ads on Mobile Devices
Blocking ads on our phones is way harder than it should be so I figured I'd make some recommendations. These are not the only options out there, just the ones that I know and have used.
Please note that browser-level and system-level adblocking are complementary; you'll have the best experience if you use both of them together as they each block different things in different places. If you want a basic idea of how effective your combined adblocking setup is, you can visit this website in your mobile browser.
Lastly, there is some additional advice/info under the readmore if you're curious (EDIT: updated March 2025 to add more adblocking options for iOS and to add info about sideloading altered versions of social media apps that don't contain ads on Android and iOS).
Android
Browser-Level
uBlock Origin (for Firefox)
System-Level (works in all apps, not just browsers)
AdGuard
Blokada 5 (completely free version) OR Blokada 6 (has some newer features but they require a subscription)
iPhone/iPad
Browser-Level
AdGuard (Safari extension; free for basic browser-level blocking, requires a subscription or one time purchase of “lifetime” license for custom filters)
1Blocker (Safari extension from an indie developer; can enable one built-in or custom filter list for free, requires a subscription or one time purchase of “lifetime” license for enabling multiple filter lists and updating filter lists to the latest version automatically)
Wipr 2 (one time purchase from indie developer; simplest option to use, but also the least configurable. Best if you are looking for one time set and forget and don’t need any custom filters. Note that it does not have a system-level blocking option)
System-Level (works in all apps, not just browsers)
AdGuard (requires subscription or one time purchase of “lifetime” license for system-level blocking)
1Blocker (can activate without a subscription, but requires subscription or one time purchase of “lifetime” license to enable system-level blocking AND browser-level blocking simultaneously)
AdGuard DNS only (this is free and does not require the AdGuard app, BUT I would only recommend it for advanced users, as you can't easily turn it off like you can with the app. Credit to this Reddit thread for the DNS profile)
Some additional info: browser-level blocking is a browser addon or extension, like you might be used to from a desktop computer. This inspects the HTML code returned by websites and searches for patterns that identify the presence of an ad or other annoyance (popup videos, cookie agreements, etc.). System-level blocking is almost always DNS-based. Basically whenever an app asks your phone's OS to make a connection to a website that is known for serving ads, the system-level blocker replies "sorry, I don't know her 🤷♂️💅" and the ad doesn't get downloaded. This works in most places, not just a browser, but be warned that it might make your battery drain a little faster depending on the app/setup.
Each of those types of blocking has strengths and weaknesses. System-level DNS blocking blocks ads in all apps, but companies that own advertising networks AND the websites those ads are served on can combine their services into the same domain to render DNS blocking useless; you can’t block ads served by Facebook/Meta domains without also blocking all of Facebook and Instagram as well because they made sure their ads are served from the same domain as all the user posts you actually want to see. Similarly, browser-level blocking can recognize ads by appearance and content, regardless of what domain they’re served from, so it can block them on Instagram and Facebook. However, it needs to be able to inspect the content being loaded in order to look for ads, and there’s no way to do that in non-browser apps. That’s why using both together will get you the best results.
These limitations do mean that you can’t block ads in the Facebook or Instagram apps, unfortunately, only in the website versions of them visited in your browser. It also means ads served by meta’s/facebook’s ad network in other apps can’t be blocked either (unless you're one of the rare beasts who doesn't use facebook or instagram or threads, in which case feel free to blacklist all Meta/FB domains and watch your ads disappear 😍; I'm jealous and in awe of you lol).
One note: some apps may behave unpredictably when they can't download ads. For example, the Tumblr app has big black spaces where the ads are, and sometimes those spaces collapse as you scroll past them and it messes up scrolling for a few seconds (UPDATE: looks like the scrolling issue may have actually been a Tumblr bug that they have now fixed, at least on iOS). Still way less annoying than getting ads for Draco Malfoy seduction roleplay AI chatbots imo though. And honestly *most* apps handle this fairly gracefully, like a mobile game I play just throws error messages like "ad is not ready" and then continues like normal.
One final note: on Android, you may actually be able to find hacked versions of Meta’s apps that have the ad frameworks removed. In some cases they are a little janky (unsurprisingly, apps don’t always take kindly to having some of their innards ripped out by a third-party), and they are often out of date. BUT in return you get an Instagram app with no ads whatsoever, and some of them even add additional features like buttons for saving IG videos and photos to your phone. However, use these apps at your own risk, as there is functionally no way to validate the code that the third-parties have added or removed from the app. Example altered IG app (I have not vetted this altered app, it's just a popular option): link.
It is technically possible to install altered apps on iOS as well, but Apple makes it much, much harder to do (unless you are jailbroken, which is a whole different ballgame). I'm not going to cover sideloading or jailbreaking here because even I as a very techy person eventually grew tired of messing with it or having to pay for it. If you're interested you can read more about the different ways to do sideloading on iOS here.
#adblockers#ad blocking#digital privacy#internet privacy#firefox#firefox extensions#mine#adguard#blokada#android#ios#iphone
516 notes
·
View notes
Text
the only annoying thing I’ve run into with librewolf right off the bat is that it forces web content to load in light mode for fingerprinting resistance reasons, but darkreader seems to fix that
trying out librewolf as my personal browser & firefox as my school/ work one since there’s no way I’ll be able to replicate the insane workaround I did to run multiple instances of firefox on my old computer lol
#I love u darkreader#darkreader and ublock origin my 2 beautiful extension gfs#I have facebook containers too but it’s totally unnecessary if you configure ublock well enough#which I have. I just like to see the little facebook-killing fence on my toolbar it brings me peace
3 notes
·
View notes
Text

So, things on the archive have been a bit dicey the past month as the Mods have been investigating the ongoing DDoS attack and various options available to us to mitigate both the current attack and future attacks. I’ll lead with the big thing.
Planned Archive Downtime
The archive will be down for a bit as we configure the new security settings on the back end. The downtime could be as little as a few minutes or up to 72 hours and we anticipate some people will get access sooner than others. We don’t like it, but it’s for the best, and will hopefully allow us to resume full accessibility to all members.
When Is the Site Going Offline?
Approximately 9PM EDT, May 13 (Tuesday evening). While you have a couple of days, you should start preparing immediately.
Prepare? What Do You Mean By That?
Mostly, just be forewarned that the downtime is coming. Don’t panic if you can’t access the site or receive an error message.
You might want to take the time to download any ePubs for fics you are reading or plan to read soon. Likewise, while we don’t anticipate this will impact the site’s content, it’s never a bad idea to back up important things, such as story comments.
What’s the Security Solution You’re Implementing?
A very common, highly trusted, and broadly used security solution called Cloudflare. It’s the same that AO3 implemented following their DDoS attack. We have completed troubleshooting this solution on our test site.
How Did You Troubleshoot?
Once we got Cloudflare up and running, the Mods went to the test site and tried to break it. We wanted to replicate the errors we initially experienced, like the Forbidden/Forbidden 403 error message. A solution that works for only some people isn’t a viable long-term solution.
This is an imperfect process, but we were able to post stories, comments, news items, images, emojis, and all other normal archive activity without incident, while maintaining the strictest security settings available on the back-end.
What Happens if I Still Experience an Error Once Everything Is Back Up?
All members should continue reporting any unusual errors, messages, and so forth as they occur to [email protected].
How Do I Stay Updated While The Site Is Down?
Important updates will be made on all of EF’s active social platforms: Instagram, Bluesky, Threads, and Facebook. You may also join our Discord server. Please note that only EF members are allowed in the Discord server, and your server name must match your EF username.
Why Was EF Targeted?
No clue, and we’re not going to speculate on who is behind it or their motives. Doesn’t matter — Spuffy always walks through the fire and emerges stronger. So will we.
#elysianfieldsarchive#elysian fields archive#archive update#spuffy#elysian fields discord server#ddos#spuffy is endgame#spuffy forever
41 notes
·
View notes
Text
Subprime gadgets

I'm on tour with my new, nationally bestselling novel The Bezzle! Catch me THIS SUNDAY in ANAHEIM at WONDERCON: YA Fantasy, Room 207, 10 a.m.; Signing, 11 a.m.; Teaching Writing, 2 p.m., Room 213CD.

The promise of feudal security: "Surrender control over your digital life so that we, the wise, giant corporation, can ensure that you aren't tricked into catastrophic blunders that expose you to harm":
https://locusmag.com/2021/01/cory-doctorow-neofeudalism-and-the-digital-manor/
The tech giant is a feudal warlord whose platform is a fortress; move into the fortress and the warlord will defend you against the bandits roaming the lawless land beyond its walls.
That's the promise, here's the failure: What happens when the warlord decides to attack you? If a tech giant decides to do something that harms you, the fortress becomes a prison and the thick walls keep you in.
Apple does this all the time: "click this box and we will use our control over our platform to stop Facebook from spying on you" (Ios as fortress). "No matter what box you click, we will spy on you and because we control which apps you can install, we can stop you from blocking our spying" (Ios as prison):
https://pluralistic.net/2022/11/14/luxury-surveillance/#liar-liar
But it's not just Apple – any corporation that arrogates to itself the right to override your own choices about your technology will eventually yield to temptation, using that veto to help itself at your expense:
https://pluralistic.net/2023/07/28/microincentives-and-enshittification/
Once the corporation puts the gun on the mantelpiece in Act One, they're begging their KPI-obsessed managers to take it down and shoot you in the head with it in anticipation of of their annual Act Three performance review:
https://pluralistic.net/2023/12/08/playstationed/#tyler-james-hill
One particularly pernicious form of control is "trusted computing" and its handmaiden, "remote attestation." Broadly, this is when a device is designed to gather information about how it is configured and to send verifiable testaments about that configuration to third parties, even if you want to lie to those people:
https://www.eff.org/deeplinks/2023/08/your-computer-should-say-what-you-tell-it-say-1
New HP printers are designed to continuously monitor how you use them – and data-mine the documents you print for marketing data. You have to hand over a credit-card in order to use them, and HP reserves the right to fine you if your printer is unreachable, which would frustrate their ability to spy on you and charge you rent:
https://arstechnica.com/gadgets/2024/02/hp-wants-you-to-pay-up-to-36-month-to-rent-a-printer-that-it-monitors/
Under normal circumstances, this technological attack would prompt a defense, like an aftermarket mod that prevents your printer's computer from monitoring you. This is "adversarial interoperability," a once-common technological move:
https://www.eff.org/deeplinks/2019/10/adversarial-interoperability
An adversarial interoperator seeking to protect HP printer users from HP could gin up fake telemetry to send to HP, so they wouldn't be able to tell that you'd seized the means of computation, triggering fines charged to your credit card.
Enter remote attestation: if HP can create a sealed "trusted platform module" or a (less reliable) "secure enclave" that gathers and cryptographically signs information about which software your printer is running, HP can detect when you have modified it. They can force your printer to rat you out – to spill your secrets to your enemy.
Remote attestation is already a reliable feature of mobile platforms, allowing agencies and corporations whose services you use to make sure that you're perfectly defenseless – not blocking ads or tracking, or doing anything else that shifts power from them to you – before they agree to communicate with your device.
What's more, these "trusted computing" systems aren't just technological impediments to your digital wellbeing – they also carry the force of law. Under Section 1201 of the Digital Millennium Copyright Act, these snitch-chips are "an effective means of access control" which means that anyone who helps you bypass them faces a $500,000 fine and a five-year prison sentence for a first offense.
Feudal security builds fortresses out of trusted computing and remote attestation and promises to use them to defend you from marauders. Remote attestation lets them determine whether your device has been compromised by someone seeking to harm you – it gives them a reliable testament about your device's configuration even if your device has been poisoned by bandits:
https://pluralistic.net/2020/12/05/trusting-trust/#thompsons-devil
The fact that you can't override your computer's remote attestations means that you can't be tricked into doing so. That's a part of your computer that belongs to the manufacturer, not you, and it only takes orders from its owner. So long as the benevolent dictator remains benevolent, this is a protective against your own lapses, follies and missteps. But if the corporate warlord turns bandit, this makes you powerless to stop them from devouring you whole.
With that out of the way, let's talk about debt.
Debt is a normal feature of any economy, but today's debt plays a different role from the normal debt that characterized life before wages stagnated and inequality skyrocketed. 40 years ago, neoliberalism – with its assaults on unions and regulations – kicked off a multigenerational process of taking wealth away from working people to make the rich richer.
Have you ever watched a genius pickpocket like Apollo Robbins work? When Robins lifts your wristwatch, he curls his fingers around your wrist, expertly adding pressure to simulate the effect of a watchband, even as he takes away your watch. Then, he gradually releases his grip, so slowly that you don't even notice:
https://www.reddit.com/r/nextfuckinglevel/comments/ppqjya/apollo_robbins_a_master_pickpocket_effortlessly/
For the wealthy to successfully impoverish the rest of us, they had to provide something that made us feel like we were still doing OK, even as they stole our wages, our savings, and our futures. So, even as they shipped our jobs overseas in search of weak environmental laws and weaker labor protection, they shared some of the savings with us, letting us buy more with less. But if your wages keep stagnating, it doesn't matter how cheap a big-screen TV gets, because you're tapped out.
So in tandem with cheap goods from overseas sweatshops, we got easy credit: access to debt. As wages fell, debt rose up to fill the gap. For a while, it's felt OK. Your wages might be falling off, the cost of health care and university might be skyrocketing, but everything was getting cheaper, it was so easy to borrow, and your principal asset – your family home – was going up in value, too.
This period was a "bezzle," John Kenneth Galbraith's name for "The magic interval when a confidence trickster knows he has the money he has appropriated but the victim does not yet understand that he has lost it." It's the moment after Apollo Robbins has your watch but before you notice it's gone. In that moment, both you and Robbins feel like you have a watch – the world's supply of watch-derived happiness actually goes up for a moment.
There's a natural limit to debt-fueled consumption: as Michael Hudson says, "debts that can't be paid, won't be paid." Once the debtor owes more than they can pay back – or even service – creditors become less willing to advance credit to them. Worse, they start to demand the right to liquidate the debtor's assets. That can trigger some pretty intense political instability, especially when the only substantial asset most debtors own is the roof over their heads:
https://pluralistic.net/2022/11/06/the-end-of-the-road-to-serfdom/
"Debts that can't be paid, won't be paid," but that doesn't stop creditors from trying to get blood from our stones. As more of us became bankrupt, the bankruptcy system was gutted, turned into a punitive measure designed to terrorize people into continuing to pay down their debts long past the point where they can reasonably do so:
https://pluralistic.net/2022/10/09/bankruptcy-protects-fake-people-brutalizes-real-ones/
Enter "subprime" – loans advanced to people who stand no meaningful chance of every paying them back. We all remember the subprime housing bubble, in which complex and deceptive mortgages were extended to borrowers on the promise that they could either flip or remortgage their house before the subprime mortgages detonated when their "teaser rates" expired and the price of staying in your home doubled or tripled.
Subprime housing loans were extended on the belief that people would meekly render themselves homeless once the music stopped, forfeiting all the money they'd plowed into their homes because the contract said they had to. For a brief minute there, it looked like there would be a rebellion against mass foreclosure, but then Obama and Timothy Geithner decreed that millions of Americans would have to lose their homes to "foam the runways" for the banks:
https://wallstreetonparade.com/2012/08/how-treasury-secretary-geithner-foamed-the-runways-with-childrens-shattered-lives/
That's one way to run a subprime shop: offer predatory loans to people who can't afford them and then confiscate their assets when they – inevitably – fail to pay their debts off.
But there's another form of subprime, familiar to loan sharks through the ages: lend money at punitive interest rates, such that the borrower can never repay the debt, and then terrorize the borrower into making payments for as long as possible. Do this right and the borrower will pay you several times the value of the loan, and still owe you a bundle. If the borrower ever earns anything, you'll have a claim on it. Think of Americans who borrowed $79,000 to go to university, paid back $190,000 and still owe $236,000:
https://pluralistic.net/2020/12/04/kawaski-trawick/#strike-debt
This kind of loan-sharking is profitable, but labor-intensive. It requires that the debtor make payments they fundamentally can't afford. The usurer needs to get their straw right down into the very bottom of the borrower's milkshake and suck up every drop. You need to convince the debtor to sell their wedding ring, then dip into their kid's college fund, then steal their father's coin collection, and, then break into cars to steal the stereos. It takes a lot of person-to-person work to keep your sucker sufficiently motivated to do all that.
This is where digital meets subprime. There's $1T worth of subprime car-loans in America. These are pure predation: the lender sells a beater to a mark, offering a low down-payment loan with a low initial interest rate. The borrower makes payments at that rate for a couple of months, but then the rate blows up to more than they can afford.
Trusted computing makes this marginal racket into a serious industry. First, there's the ability of the car to narc you out to the repo man by reporting on its location. Tesla does one better: if you get behind in your payments, your Tesla immobilizes itself and phones home, waits for the repo man to come to the parking lot, then it backs itself out of the spot while honking its horn and flashing its lights:
https://tiremeetsroad.com/2021/03/18/tesla-allegedly-remotely-unlocks-model-3-owners-car-uses-smart-summon-to-help-repo-agent/
That immobilization trick shows how a canny subprime car-lender can combine the two kinds of subprime: they can secure the loan against an asset (the car), but also coerce borrowers into prioritizing repayment over other necessities of life. After your car immobilizes itself, you just might decide to call the dealership and put down your credit card, even if that means not being able to afford groceries or child support or rent.
One thing we can say about digital tools: they're flexible. Any sadistic motivational technique a lender can dream up, a computerized device can execute. The subprime car market relies on a spectrum of coercive tactics: cars that immobilize themselves, sure, but how about cars that turn on their speakers to max and blare a continuous recording telling you that you're a deadbeat and demanding payment?
https://archive.nytimes.com/dealbook.nytimes.com/2014/09/24/miss-a-payment-good-luck-moving-that-car/
The more a subprime lender can rely on a gadget to torment you on their behalf, the more loans they can issue. Here, at last, is a form of automation-driven mass unemployment: normally, an economy that has been fully captured by wealthy oligarchs needs squadrons of cruel arm-breakers to convince the plebs to prioritize debt service over survival. The infinitely flexible, tireless digital arm-breakers enabled by trusted computing have deprived all of those skilled torturers of their rightful employment:
https://pluralistic.net/2021/04/02/innovation-unlocks-markets/#digital-arm-breakers
The world leader in trusted computing isn't cars, though – it's phones. Long before anyone figured out how to make a car take orders from its manufacturer over the objections of its driver, Apple and Google were inventing "curating computing" whose app stores determined which software you could run and how you could run it.
Back in 2021, Indian subprime lenders hit on the strategy of securing their loans by loading borrowers' phones up with digital arm-breaking software:
https://restofworld.org/2021/loans-that-hijack-your-phone-are-coming-to-india/
The software would gather statistics on your app usage. When you missed a payment, the phone would block you from accessing your most frequently used app. If that didn't motivate you to pay, you'd lose your second-most favorite app, then your third, fourth, etc.
This kind of digital arm-breaking is only possible if your phone is designed to prioritize remote instructions – from the manufacturer and its app makers – over your own. It also only works if the digital arm-breaking company can confirm that you haven't jailbroken your phone, which might allow you to send fake data back saying that your apps have been disabled, while you continue to use those apps. In other words, this kind of digital sadism only works if you've got trusted computing and remote attestation.
Enter "Device Lock Controller," an app that comes pre-installed on some Google Pixel phones. To quote from the app's description: "Device Lock Controller enables device management for credit providers. Your provider can remotely restrict access to your device if you don't make payments":
https://lemmy.world/post/13359866
Google's pitch to Android users is that their "walled garden" is a fortress that keeps people who want to do bad things to you from reaching you. But they're pre-installing software that turns the fortress into a prison that you can't escape if they decide to let someone come after you.
There's a certain kind of economist who looks at these forms of automated, fine-grained punishments and sees nothing but a tool for producing an "efficient market" in debt. For them, the ability to automate arm-breaking results in loans being offered to good, hardworking people who would otherwise be deprived of credit, because lenders will judge that these borrowers can be "incentivized" into continuing payments even to the point of total destitution.
This is classic efficient market hypothesis brain worms, the kind of cognitive dead-end that you arrive at when you conceive of people in purely economic terms, without considering the power relationships between them. It's a dead end you navigate to if you only think about things as they are today – vast numbers of indebted people who command fewer assets and lower wages than at any time since WWII – and treat this as a "natural" state: "how can these poors expect to be offered more debt unless they agree to have their all-important pocket computers booby-trapped?"

If you'd like an essay-formatted version of this post to read or share, here's a link to it on pluralistic.net, my surveillance-free, ad-free, tracker-free blog:
https://pluralistic.net/2024/03/29/boobytrap/#device-lock-controller

Image: Oatsy (modified) https://www.flickr.com/photos/oatsy40/21647688003
CC BY 2.0 https://creativecommons.org/licenses/by/2.0/
#pluralistic#debt#subprime#armbreakers#mobile#google#android#apps#drm#technological self-determination#efficient market hypothesis brainworms#law and political economy#gadgets#boobytraps#app stores#curated computing#og app#trusted computing
230 notes
·
View notes
Text

The Junkers Ju 290 was produced for one of two primary roles – either as a transport or configured for maritime patrol in support of U-boat operations. The maritime patrol aircraft were assigned to Fernaufklärungsgruppe 5 for Atlantic patrol. This is Ju 290A-3 WNr. 10162 which was found at Salzburg, Austria after the war. Note the Messerschmitt Bf 109G14A/S on the right. For more, see my Facebook group - Eagles Of The Reich
#germany#ww2#luftwaffe#ww2 aircraft#messerschmitt#junkers#ju 290#bf 109g#1945#fernaufklärungsgruppe 5
66 notes
·
View notes
Text
Lilith Configuration and Its Revelations on Your Erotic Identity xxx

The lasting cosmic journey of Lilith in Aries unveils a narrative of audacity, impulsiveness, and a fearless embrace of dominance within the confines of the bedroom.
In the realm of Lilith gracing Taurus, one becomes a sensual connoisseur, delighting in the orchestration of carnal pleasures. Every moment is a lingering indulgence, a deliberate savoring of the exquisite nuances of passion.
Venturing into the enigmatic domain of Lilith in Gemini, one is greeted by the spirit of curiosity. This individual thrives on experimentation, displaying an openness to novel experiences and a penchant for exploring the vast landscape of fantasies.
For those marked by Lilith in Cancer, the sexual landscape transforms into a nurturing sanctuary. Here, the emphasis lies in crafting emotional intimacy, weaving a tapestry of connection that extends beyond the physical realm.
Lilith's fiery presence in Leo manifests as a passionate force, seeking the spotlight within the intimate confines of the bedroom. Adoration and worship become the currency of desire for those bearing this celestial imprint.
As Lilith aligns with Virgo, the sexual narrative adopts a meticulous and detail-oriented script. The pursuit of perfection becomes paramount, and pride is derived from the meticulous artistry of pleasuring one's partner.
In the libidinous ballet of Lilith in Libra, the pursuit of harmony and equilibrium takes center stage. The fulfillment of both personal desires and those of the partner becomes the guiding principle.
Lilith's descent into Scorpio's abyss signals a journey into the shadowy realms of sensuality. Boundaries are pushed, and the exploration delves into the profound, both emotionally and physically.
Sagittarius, adorned with Lilith's influence, embarks on a journey of sexual exploration. Breaking free from traditional shackles, the adventurer seeks novelty, craving the thrill of uncharted territories.
In the disciplined terrain of Lilith in Capricorn, the sexual landscape is marked by focus and unwavering discipline. Novelty holds no allure; the pursuit lies in the mastery of the tried and tested.
Aquarius, with Lilith's eccentric touch, ventures into uncharted waters of sexual expression. Liberation from societal norms becomes the cornerstone, pushing boundaries and embarking on a voyage of self-discovery.
Pisces, blessed with Lilith's whimsy, delves into a realm of imagination and dreams. The pursuit transcends reality, embracing the magical and fantastical in the kaleidoscopic tapestry of erotic exploration.
Follow our Facebook page Mage Magic Touch for personal consultations https://www.facebook.com/profile.php?id=61565561190268
#astro notes#astrology notes#astrology observations#astrology#astrological signs#astro community#astro memes#astrology community#astrology tips#astrology memes#astrotips#astrology planets#astroblr#astro blog#astrology blog#astrology facts#astrology readings#astrology knowledge#astro tips#astro placements#astro observations#astrology placements#natal chart#birth chart#Aries#Pisces#Scorpio#Virgo#Taurus#sagittarius
262 notes
·
View notes
Text
wait. wait. So I got this first picture from the Spies Are Forever facebook page, and it's part of a set that's out there from when Joey was still wearing the Oleg jacket and the set was already built (I'm assuming like a dress rehearsal?)
And I've seen this picture a bunch of times, but somehow never thought about the fact that the watch is on the other wrist!


So I wonder if these were like promotional photos that are intentionally staged differently to not totally give the game away, or if they switched things around before or even during the run, because the second configuration is definitely much more intimate. Like either way that is kinda brilliant
35 notes
·
View notes
Text
no one:
me: let’s check the vibe of the leverage facebook group
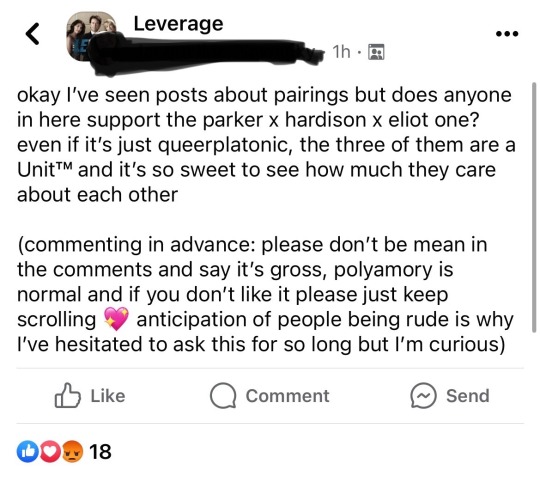
(blurred out my name for privacy)
at first people passed the vibe check with heart/care reacts, thumbs up… and then the boomers came
a lot of people settled on it’s some configuration of parker/eliot or hardison/eliot give off sibling vibes and hardison is dating parker, but a fair amount of folks said they would accept or would like the ot3. one based guy was like ‘if it drives the story then power to them’. someone else just commented ‘till my dying day’, another said ‘I mean… they already measured his head for the robot bodies’. someone else said they like brother sister eliot and parker but queerplatonic with parker and hardison dating is still good to them.
and then there was one woman who basically said if you don’t want honest answers you shouldn’t ask the questions and then said eliot is a good friend/brother to them and love does not need to be romantic or sexual to be strong (girlie what do you think queerplatonic means 😭💀)
also JUST got this gem (and am going to report them)
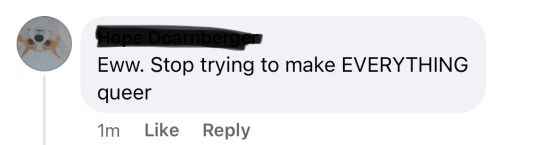
edit with my response:
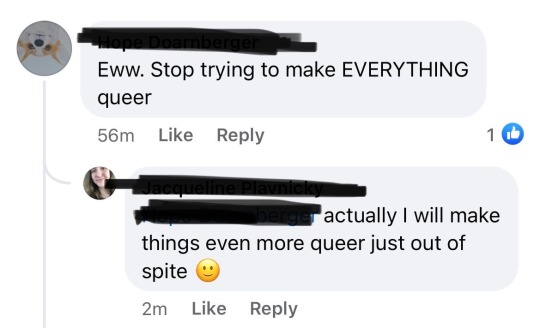
last edit: she was kicked out of the group after 💀
#it’s illegal to be mean to me on my birthday actually#jkjk#but fr fuck them I WILL make everything gay actually. out of SPITE#told my roommate and they were like jackie maybe you need to get off the internet#(I posted a pro palestine city hall gathering flyer in my towns facebook group monday and it. uh. had mixed results)#eliot spencer#parker#alec hardison#leverage ot3#parker x hardison x eliot#leverage#leverage redemption#other social media sites#facebook#jackie talks#mine#for context: some of the recent posts were about eliot and sophie getting together and about parker and hardison#so I’m like sure. talking about ships is fine right. what could go wrong#famous last words#there’s a reason why I haven’t posted until now
168 notes
·
View notes
Text


There is nothing that amuses me more than a secret inside of a secret.
Here’s an article that I wrote that my friend Dario Leone owner of Aviation Geek Club shared about the YF 12 and the secret SR 71 tail number 951.
Most people when they think of the YF 12 think of it as an experimental airplane that never really flew, but that is wrong. It did fly for many years. The last flight was in 1979 when it was flown to the Air Force Museum near Dayton, Ohio you can find it next to the XB-70.
The so-called YF-12C was really the SR-71A 61-7951, modified with a bogus tail number 06937 belonging to an A-12.
Taken in 1975, the interesting photos in this post show NASA Blackbirds carrying the ” Cold wall” heat transfer pod on a pylon beneath the forward fuselage.
The Blackbirds portrayed in these photos are usually referred to as YF-12s, but actually one of them was an SR-71 as Linda Sheffield Miller (Col Richard (Butch) Sheffield’s daughter, Col. Sheffield was an SR-71 Reconnaissance Systems Officer), who runs Born into the Wild Blue Yonder Habubrats Facebook page, told to The Aviation Geek Club: ‘In case anybody asked the pictures with the two NASA Blackbirds the one on the top is a YF-12 but the one on the bottom is an SR-71!
‘Another interesting thing about those pictures is that NASA was not allowed to have an SR-71 but they did and they passed it off as a YF-12!
In fact, the “YF-12C” was a then-secret SR-71A (serial no. 64-17951, the second production SR-71A) given the NASA tail no. 60-6937. The reason for this bit of subterfuge lay in the fact that NASA while flying the YF-12A interceptor version of the aircraft, was not allowed to possess the strategic reconnaissance version for some time. The bogus tail number actually belonged to a Lockheed A-12 (serial no. 60-6937), but the existence of the A-12 remained classified until 1982. The tail number 06937 was selected because it followed the sequence of tail numbers assigned to the three existing YF-12A aircraft: 06934, 06935, and 06936. Isn’t that amazing?’
The Coldwell project, supported by Langley Research Center, consisted of a stainless steel tube equipped with thermocouples and pressure sensors. A special insulating coating covered the tube, which was chilled with liquid nitrogen.
Given that the US Air Force (USAF) needed technical assistance to get the latest reconnaissance version of the A-12 family, the SR-71A, fully operational, the service offered NASA the use of two YF-12A aircraft, 60-6935 and 60-6936.
Eventually, with 146 flights between Dec. 11, 1969, and Nov. 7, 1979, 935 became the workhorse of the program while the second YF-12A, 936, made 62 flights. Given that this aircraft was lost in a non-fatal crash on Jun. 24, 1971, it was replaced by the so-called YF-12C SR-71A 61-7951, modified with YF-12A inlets and engines and a bogus tail number 06937.
The SR-71 differed from the YF-12A in that the YF-12A had a round nose while the SR-71 had its chine carried forward to the nose of the airplane. The SR-71 was longer, nearly 8 feet longer as it had an extra fuel tank that the YF 12 didn’t have. There were other differences in internal and external configuration, but the two aircraft shared common inlet designs, structural concepts, and subsystems. Also of note the SR 71C is really a combination of a static display of the SR 71 for the front half and the back half is the crashed YF-12!
In my study of all the Blackbirds, I have found other secrets inside of secrets. Such as the test SR-71 plane the 955. Everyone was told often that this airplane never left the United States, but that is not true.
When it comes to reconnaissance airplanes and War, even if it was a Cold War, Rearranging the facts is fair.
There will always be mystery in the SR 71 program.
Don’t believe that all of the secrets have been told.
I know that is not true.
Linda Sheffield, Daughter of a Habu
@Habubrats71 via X
Tap Title bar to view👇
42 notes
·
View notes
Text
Comments on Nobellaureates works 2024 :DR/Advocate etc R S D Unnithan Legal chambers etc kottarakara kollam kerala india [email protected] [email protected] [email protected] [email protected] [email protected] Drnlocmopajrsdu twitter com facebook Instagram tik tok tumbler etc/www mednobel.ki.se/www.olympics.org
[email protected];Dear sir...Comments on Nobellaureates of chemistry 2024 work on proteins:"Can denatured proteins be recreated?How will you explain zwitter ion formations and stability in recreated or artificial synthetic proteins ?Further the rate of consumption of synthetic proteins in synthetic tracks and biomodels is governed by which law of contact in great speeds and power?"thanks ..DR/Advocate etc R S D Unnithan Legal chambers etc kottarakara kollam kerala india [email protected] [email protected] [email protected] [email protected] [email protected] [email protected] etc Drnlocmopajrsdu twitter com †****************************+ [email protected];Dear sir...Comments on Nobellaureates works 2024 in physics::Neural networks and patterns recognitions with boltsman spatial configurations as for memory gained or lost as per retention of memories when translated in machine languages for the possibilities of AI interventions in surgical post synaptic stages for a miraculous escapes wherein brain trauma comas from haemmorages and loss of memories can be revived for all success can be now hence proved in medical fields by the grace of your achievements which may be greater than EEG and some shocks which was being used?Yes or No?Explain?;thanks;DR/Advocate etc R S D Unnithan Legal chambers etc kottarakara kollam kerala india [email protected] [email protected] [email protected] [email protected] exnlexprofexwrbexocmoprsdunit@gmail †*******†********************* Dear sir..Comments on Nobellaureates works 24 in peace:It was quite interesting to know this year's 2024 awards went to Japan for its surviving victims of Hiroshima Nagasaki ... But;Is it possible to consider Russian president and Ukrainian president future surviving would be Nobellaureates within a span of fifty years or more if not any American presidents from Jimmy carter to trump etal?Is there any chance for any surviving relatives be in America or Russia or Ukraine for development of peace out of million to trillion dollars?thanks;DR/Advocate etc R S D Unnithan Legal chambers etc kottarakara kollam kerala india [email protected] [email protected] [email protected] [email protected] [email protected] Drnlocmopajrsdu twitter com facebook Instagram tik tok tumbler etc [email protected] etc
Show quoted text
On Mon, 2 Dec 2024, 18:47 Nobel laureate DR R S D UNNITHAN ,OCM;OP, <[email protected]> wrote:
[email protected];Dear sir..Comments on Nobellaureates works 24 in peace:It was quite interesting to know this year's 2024 awards went to Japan for its surviving victims of Hiroshima Nagasaki ... But;Is it possible to consider Russian president and Ukrainian president future surviving would be Nobellaureates within a span of fifty years or more if not any American presidents from Jimmy carter to trump etal?Is there any chance for any surviving relatives be in America or Russia or Ukraine for development of peace out of million to trillion dollars?thanks;DR/Advocate etc R S D Unnithan Legal chambers etc kottarakara kollam kerala india [email protected] [email protected] [email protected] [email protected] [email protected] Drnlocmopajrsdu twitter com facebook Instagram tik tok tumbler etc [email protected] etc†**********†********************. Comments (on tiny micro RNA: a macromolecule or a powerful micro molecule etc?) send to nobellaureates 2024 physiology and medicine king queen and tel updated to all::DR/Advocate etc R S D Unnithan Legal chambers etc kottarakara kollam Kerala India






















34 notes
·
View notes
Text
January 7, 2023 update from the Battleship Texas Foundation

Battleship Texas in dry dock 1/7/24.
"DRY DOCK TOURS
Tours are now full through the entire month of January. We look forward to welcoming five hundred of you into the shipyard to see the amazing progress made to Battleship Texas!


A Dry Dock Tour wanders underneath 27,000 tons of Battleship Texas.

Dry Dock Tour participants sign one of the COME ON TEXAS banners that have hung on the gangway for many months.
STEEL REPAIR - Steel repairs have been completed on the hull of Battleship Texas. Some troublesome areas were found once the ship was sandblasted, so additional repairs have been made. These areas will be blasted and coated before the ship submerges in the water once again.



New steel being placed near one of the ship's docking keels. This area will be lightly blasted and coated.
HULL - The ship's hull has been coated in PPG
SIGMASHIELD 880 GF to protect the steel from potential corrosion. While the hull is supposed to be red below the black band at the waterline, the Battleship Texas Foundation has chosen to not spend the extra funds on a cosmetic choice that will not be seen once the ship is back in the water. The coatings that have been applied are plentiful and should protect the ship for many years to come.
NAVY BLUE 5-N - Above the boot top (above the black band) the ship has been painted Navy Blue 5-N. This color was matched from existing examples found aboard (both internally and externally) the vessel. The ship was painted in this camouflage scheme (Measure 21) prior to deploying to the Pacific Theater in World War II. At this time Battleship Texas is the ONLY museum ship painted in this scheme and only one of two Battleships in their wartime measure.


The ship's draft numbers have been installed and painted on the bow and stern
HULL NUMBERS - The new hull numbers have been extensively researched so each number is not only the correct font, but applied in the appropriate position it was in 1945. The numbers have been applied to both bow and stern.



The ship's name and hull number have been applied to the stern.
FREQUENTLY ASKED QUESTIONS:
KEEL BLOCKS - Yes, the keel blocks supporting Battleship Texas can be moved. Each block is moved so the area atop of them can be blasted, repaired (if need be), and coated.
SPLASH! - The ship will be put back into the water in February 2024, but is dependent on the weather.
WHAT'S NEXT? - Battleship Texas will remain at Gulf Copper Shipyard for the time being. WHAT'S NEXT? - Battleship Texas will remain at Gulf Copper Shipyard for the time being. Additional steel work, removal and replacement of the ship's deck, and superstructure/aft fire control restoration will continue.

Scaffolding surrounds the ship's superstructure as repairs in these areas come to an end.


The ship's aft fire control continues to be restored to its 1945 configuration. The installation of the windows and more has already begun.

The areas that the ship's six 5"/51 cal. guns sat have been blasted and coated. A wood decking will go down next.

Part of a Dry Dock Tour ends their tour with a picture in front of the ship's bow!
Live, Laugh, And Flood your Torpedo Blisters. To donate to the preservation and operation of Battleship Texas, please visit: https://battleshiptexas.org/
Support Battleship Texas by making a purchase through the ship's store: https://store.battleshiptexas.org"
Posted on the Battleship Texas Foundation Group Facebook page: link
#battleship Texas#Battleship Texas Foundation#Update#USS TEXAS (BB-35)#USS TEXAS#New York Class#Dreadnought#Battleship#Warship#Ship#Drydock#Dry Dock#Galveston#Texas#repairs#Gulf Copper#Restoration#January#2024#my post
67 notes
·
View notes
Text
Tumblr Growth - Its tough trying to face the world from inside Tumblr.
I used a service called Make | Automation Software | Connect Apps & Design Workflows | Make to push my Youtube videos (All of them that I could on a free plan) to Tumblr - ive been also forming connections and commenting and being part of the community. I had issues where it would post the link to the video, well the ID and I had to manually push the you tube url video = [VideoID] but it didnt embed so I have been editing them one by one to properly embed them and tag them. Its paying off slowly, also pushing thebritbeardo.tumblr.com to the world, frustrated that tumblr is blocking bing bot and @tumblrsupport in a reddit thread said speak to Bing, Bing does not control robots.txt for my site so I kindly asked and will continue to ask tumblr support to remove the block to bingbot, I have sent screenshots from bing webmaster tools. Also, Google is not properly indexing britbeardo.tumblr.com because its not the canonical URL and no matter the tags I put in the html it seems that there is a tumblr controlled canonical url that is set to tumblr.com/accountname. All the canonical testers tell me this.
It seems they are really focusing on users using internal tumblr network and not reaching out to potentially new tumblr users. Its a shame as if you configure Tumblr correctly, follow the right people its actually a much better social environment that Facebook or X, Threads, Masterdon etc. I use them all pretty much and found Tumblr to be a breath of fresh air except for these few frustrations.
@TumblrSupport please allow users more control of blocked search engines in the robots.txt, even if its a check box for allow Yandex, Allow BingBot etc. And give us control of the canonical URL, if I put a Tag in my HTML to override please honor my request to use account.tumblr.com I considered buying a domain but in still concerned that using a domain will cause me to still blocked by bingbot and not have control of the canonical settings.

3 notes
·
View notes
Text
WiFi Dashboard for Solar Off-Grid Power Plants
This WiFi interface and Data Logger software are used mainly for Solar Off-Grid Power plants This contains wifi connection information, parameter dials, operational status, energy consumption status and fault status of the Unit History option allows the user to access the data history of a particular unit by searching the modem id. Upto 100 entries can be viewed in a single page. Every five minutes the data will be logged in the history and refreshed Data Config option allows the user to configure the data in the dashboard of a particular unit WiFi credential is to connect the unit to the desired wifi network. This can be achieved by entering Modem id, Network name and Password Switch option in the side panel allows the remote operation of the unit. The whole unit or only the charging can be turned ON/OFF from the dashboard by operating the respective ON and OFF tabs User manual option provides the instructions to configure modem to the wifi network and also use the website dashboard
Don’t forget to LIKE, COMMENT, and SUBSCRIBE for more renewable energy solutions and solar projects!
Enquire Now: 9035024760 or [email protected]
Follow our LinkedIn page: https://www.linkedin.com/company/53510028/admin/dashboard/
Follow our Facebook page: https://www.facebook.com/UniparEnergySystemsPvtLtd
Follow our Instagram: https://www.instagram.com/uniparenergysystemspvtltd/
Subscribe our YouTube channel: https://www.youtube.com/watch?v=3hchIw7CFjw
Visit our website: https://unipar.in/
#off grid solar system#off grid solar power systems#off grid solar electric system#grid off solar system#off grid inverter#off grid solar inverter#inverter solar off grid#grid off inverter#inverter grid off#pv inverter off grid#off grid solar#grid solar system
2 notes
·
View notes
Text

AEG G.IIs in 1916 - the last 20 built had triple-rudders to counter some control issues. Manfred von Richthofen, the famous Red Baron, before becoming an ace, flew the AEG G.II in the spring of 1916. The AEG G-types all followed the same basic configuration; conventional biplanes with steel-tube structures covered by fabric and two engines mounted as tractors. Nearly all other Luftstreitkräfte (German Air Force) bombers had engines mounted as pushers at this time. For more, see my Facebook group - Eagles Of The Reich
46 notes
·
View notes
Text
187 - Testing The Waters
All comments, questions, and general feedback can be sent to [email protected]. Record a voice message and send it my way or leave one at the Speakpipe page!
You can subscribe to Radio BSOTS via the following options: RSS feed ||| Apple Podcasts ||| Spotify ||| Mixcloud Amazon Music ||| Goodpods ||| TuneIn ||| iHeartRadio
Connect with Camp Lo-Fi via social media: Twitter | Facebook | Instagram
This episode's track list (title / artist / source / license):
1. Happy Birthday ccMixter by J.Lang featuring Snowflake [ccMixter] (CC-BY) (2024)
2. Thanks For The Memories (Featuring Belle McNulty) by CM aka Creative [blocSonic] (CC-BY-NC-SA) (2024)
3. drain the sun by niteffect [Bandcamp] (CC-BY-NC-ND) (2022)
4. Over by Suhov [Free Music Archive] (CC-BY-NC-ND) (2008)
5. Whenever You Wanna Call Me by Comfort Fit [Free Music Archive] (CC-BY-NC-ND) (2005)
6. Out for a Shrink Pink Drink by Apes On Tapes [Free Music Archive] (CC-BY-NC) (2010)
7. Configurate by Proviant Audio [Free Music Archive] (CC-BY-NC-ND) (2009)
8. 1000 Miles by Bluntspeakers [Bandcamp] (CC-BY-NC-ND) (2010)
9. Soul Groove! (Patience) by !Mc'Lain! [Jamendo] (CC-BY-NC-ND) (2022)
10. The Holowaka Hides in the Shadow of the Sun by Fields Ohio [Bandcamp] (CC-BY-SA) (2024)
BSOTS BONUS TRACK:
11. Train Rides - In Praise of Black Men by Nikki Giovanni [Free Music Archive] (CC-BY-NC-SA 3.0) (2009)
If you're reading this, it means that you made it out of 2024. Happy New Year and welcome to Camp Lo-Fi. I hope and pray that you will be able to experience peaceful moments and great music throughout this year. I pulled this episode together as 2024 was coming to a close, making this the first sonic statement for Radio BSOTS in 2025. To kick off a new year of the podcast, this episode and the next episode will focus on my participation in the Netlabel Day Radio live stream marathon that took place in July of last year. I initially recorded a 30-minute test run for the stream and figured that I should share that with the listeners.
I gathered together some Creative Commons tunes from indie labels that ended up releasing later works under full copyright as time went on, but are still imprints that I hold in high regard (namely Tokyo Dawn, Budabeats, and Error Broadcast). All cuts played during the test run can still be found online via Jamendo, Bandcamp, and the Free Music Archive. This set of music leans heavy on the sounds of international beat culture, particularly that first decade of the early 2000s where the lines between electronic music and hip-hop production got blurry (and for the better, in my opinion). Selections from Comfort Fit, Suhov, Bluntspeakers, and Apes On Tapes are probably the best examples of this.
Outside of the test run, the show opens with a selection in honor of ccMixter turning 20 years old (featuring the voice of Madam Snowflake - check out this video for a snapshot of her artistic journey) and closes with an addictive head-nodding joint from Fields Ohio. I also get to share some listener feedback this time around. As a bonus, I couldn't let the episode end without the words and voice of the late, great Nikki Giovanni. As always, I welcome your interaction and hope that there are some selections within this installment of the podcast that grab your attention and increase your curiosity about other gems that can be found within the world of Creative Commons licensed music.
Theme music by Cy Tru (edited by Macedonia). Background music by Techniken Defunkus. ID drops from Morganics and Jonny Sonic.
Other key info: Macedonia on Mixcloud BSOTS show #178 - Creative Commons Gems From Public Enemy And Nikki Giovanni BSOTS show #181 - Creative Commons Sightings Of Kool Keith And DJ Harrison BSOTS show #186 - Download While You Can Netlabel Archive Funkwhale Castopod Tha Bloc Report
The content of this show has been released under a CC-BY-SA license. All works within this show retain their original releases. See the show notes at bsots.com for more information.
Another BSOTS podcast episode for the people...
2 notes
·
View notes
Text
8 Best Shopify Apps For Product Feed [Boost Visibility]
Are you trying to find the high-quality Shopify apps to manipulate product feeds and enhance visibility? Look no further! Experience hassle-free Shopify management with our top-tier Shopify Maintenance Service.
In this weblog publish, we will monitor powerful Shopify apps that can help you gain the fulfillment you want at the Shopify platform.
Whether it’s growing net visitors, generating income leads, or constructing an internet presence, those on hand gear will assist you get more visibility in no time.
Let’s dive in and find out the first-class Shopify apps for product feed!
List Of Shopify Apps For Product Feed
1. Socialwidget – Instagram Feed
Are you searching out an easy and efficient way to boost your product visibility? Look no further!
Socialwidget’s Instagram Feed is one of the quality Shopify apps to help your keep stand out.
Its pre-made templates and customizable product-tagging capabilities make it smooth to display beautifully-embedded Instagram and TikTok feeds right on your website, giving customers the ability to purchase right from the feeds.
Increase conversions and construct agree with with Socialwidget – the nice Shopify product feed app.
Key Features:
Showcase an aesthetically desirable Instagram gallery
Let clients ‘store the appearance’ with five item tags in keeping with image/video
Sort posts from Instagram accounts & hashtags
Increase Instagram fans with profile show
Leverage shoppable Instagram & TikTok feeds to your website online
Pricing:
Starter: Free
Standard: $9.Ninety/Month
Professional: $19.90/Month
Advanced: $49.90/Month
View App
2. FeedHub: Facebook, Google Feed
Boost your online visibility with FeedHub, the excellent Shopify app for product feed control. FeedHub lets you effortlessly create, optimize and publish product feeds to Google Shopping, TikTok and Facebook channels. Let us handle the upkeep while you focus on growth with our Shopify Maintenance Service.
With FeedHub, you could without difficulty configure product feeds to maximise accuracy and optimize your descriptions, titles and images.
Moreover, the app updates feeds in actual-time so that no capacity sale opportunity is overlooked, and also supports localized product feeds to amplify your reach.
Use FeedHub to get the maximum out of online product advertising and boost visibility.
Key Features:
Automate & sync google purchasing, Facebook, & TikTok feeds
Create product feeds w/ rules from collections & editions
Globalize feed in more than one languages & currencies
Optimize feed attributes, titles & pictures
Instantly replace feed on any store modifications
Pricing:
Starter: Free
Standard: $9.Ninety/Month
Professional: $29.Ninety/Month
Advanced: $49.Ninety/Month
View App
three. Pin it: Pinterest Save Button
Pin it: Pinterest Save Button Shopify app
Pin it: Pinterest Save Button is the excellent unfastened Shopify App for product feed.
It permits customers to quickly and effortlessly add the Pinit button functionality to their Shopify keep so that customers can keep their favored products to Pinterest.
With one easy click on, clients can add product pics, pricing, and product links to their Pinterest forums to share with their Pinterest followers, boosting visibility for his or her business.
The Pin it function is a brilliant manner to promote merchandise on Pinterest and in addition interact with customers.
Key Features:
Embed a ‘pin it’ button with one click
Easily upload an ‘upload to cart’ button
Discover content organized in boards
Build a customised Lookbook with option to save merchandise
Integrate pins with website analytics
4. Google Shopping Feed XML/CSV
Google Shopping Feed XML/CSV app for Shopify
Are you looking to boom visibility and income? With the Google Shopping Feed XML/CSV app for Shopify you can quickly and effortlessly boost your shop’s visibility to customers worldwide!
This app creates an XML feed that integrates seamlessly with Google Shopping, allowing store owners to easily and appropriately exhibit their merchandise.
It also helps multi-language, multi-currency, and even neighborhood inventory ads feeds, perfect for groups working in diverse locations.
With this app, you could without problems make certain customers could make informed decisions and make the most of their buying revel in.
Get the maximum out of online purchasing with the Google Shopping Feed XML/CSV app for Shopify—the pleasant product feed apps for Shopify.
Key Features:
Support for more than one countries & currencies
All variations & custom attributes tagging
Support for nearby inventory feeds
Csv record subsequent to the xml feeds
Works on Bing, Meta/Facebook, & marketplaces
Pricing:
Default Plan: $7/Month
View App
five. Google Shopping Feed Advanced
Google Shopping Feed Advanced Shopify app
Boost your product visibility with Google Shopping Feed Advanced – the satisfactory Shopify App for product feed.
With its powerful AI-driven functions, this app makes it less difficult than ever earlier than to maximize your product publicity on Google Shopping, Facebook Ads, Microsoft Ads, TikTok, Pinterest, PriceCheck, Takealot, ShareASale, and different channels.
It facilitates you dynamically map attributes to create powerful product titles, descriptions, and version information like Color, Age & Gender, fix problems in Google Merchant Center, and embed unlimited recommendations.
Now you could take your eCommerce business presence to the next degree thru powerful product records feed control.
So, get ready to increase your product publicity and enhance your income with Google Shopping Feed Advanced!
Key Features:
One-click synchronization of stock and orders
Ai powered product titles & barcodes
Automatically map categories with statistics-manipulation guidelines
Price differentiation for better manipulate over income
Enjoy dynamic discounts & clever feed recommendations
Pricing:
Basic: $20/Month
Premium: $one hundred twenty/Month
Feednexus: $500/Month
View App
6. FeedAPIs For Bing Shopping /MS
FeedAPIs For Bing Shopping /MS app for Shopify
For Shopify merchants in need of a reliable, clean-to-use product feed solution as a way to raise visibility and brings consequences, the FeedAPI for Bing Shopping/MS app ought to pinnacle the listing.
It’s one of the excellent Shopify apps for product feed and without problems integrates with Microsoft Merchant Center Store, allowing you to optimize product statistics feeds and personalize product titles, descriptions, and product sorts for a hit product listings.
With it you may song dynamic remarketing tagging and conversion monitoring and create promotions feed for unique and all products – supplying you with whole manipulate over your product feed.
FeedAPI for Bing Shopping/MS app is your one-stop answer to enhance visibility and maximize your product feed’s potential.
Key Features:
Automatically extract product feed out of your ecommerce save
Submit optimized product statistics to Microsoft merchant center store
Enable conversion monitoring & dynamic remarketing with UTM tag
Optimize campaigns with clever filters & bulk edit alternatives
Create & put up service provider promotions for particular merchandise
Pricing:
Up To 500 Products: $four.Ninety nine/Month
Max one thousand Products: $eight.Ninety nine/Month
Max 5000 Products: $thirteen.99/Month
Max 10000 Products: $17.Ninety nine/Month
View App
7. AfterShip Feed for TikTok Shop
AfterShip Feed for TikTok Shop Shopify app
Are you seeking to expand your keep’s visibility through promoting your merchandise on TikTok Shop? AfterShip’s Feed for TikTok Shop is one of the high-quality Shopify apps for product feed to effortlessly sync and switch product and order information from Shopify to your TikTok Shop — in few clicks!
With Feed for TikTok Shop, you can seamlessly combine with different eCommerce platforms, trouble-free.
Its robust API services assure a clean overall performance and problem-free save control, while its devoted customer support crew affords well timed and complete answers to any of your questions concerning product feed management.
Now, improve your store’s visibility with AfterShip’s Feed for TikTok Shop and take gain of this thrilling new possibility to attain ability customers!
Key Features:
Sync product & fees to TikTok shop & mobile app
Auto satisfy orders from ecommerce keep’s admin
Map products & classes to what merchants want
Immersive mobile shopping with notifications & wishlists
One-click on automobile product sync to TikTok & cell apps
Pricing:
Free: Free
Essentials: $18/month
Pro: $119/month
8. Flexify: Facebook Product Feed
Flexify: Facebook Product Feed Shopify app
Introducing Flexify – the pleasant Shopify app for seamlessly optimizing product statistics for Facebook channels.
Flexify simplifies the method of making wonderful product feeds, routinely including in missing product attributes for boosted visibility and similarly optimizing product listings on Facebook and Instagram – an appropriate answer for traders looking to generate greater income.
With Flexify, you’ll be able to reveal, compare, and improve your product facts to its top of the line level – making the maximum of the huge reach of the two social media giants and the capability to target capability customers.
Make your product records shine with Flexify – the leading Shopify app for product feed optimization.
Key Features:
Automatically create Facebook & Instagram advertisements
Customize ads and targeting options
Supports multiple languages and currencies
Easy checkout revel in for Facebook & Instagram
Monetize & control product feeds in one vicinity
Pricing:
Free-Forever: Free
Premium – Small: $29/Month
Premium – Medium: $forty nine/Month
Premium – Large: $seventy nine/Month
Final Words
The apps we mentioned have the ability to growth your product visibility and amplify your reach.
Feed optimization let you enhance your keep’s universal performance and generate greater conversions.
By taking the time to research and put in force the exceptional product feed app in your precise wishes, you’ll be capable of take your keep and product visibility to the following degree.
Also Read : 6 Best Shopify Apps For Frequently Bought Together
5 Best Inventory Management Apps for Shopify
2 notes
·
View notes