#ethical hacking classes
Explore tagged Tumblr posts
Text
Ethical Hacking Classes in Delhi – Advance Your Cyber Skills
Sharpen your cyber skills with Ethical Hacking Classes in Delhi at NEW DELHI YMCA IMSIT. These classes provide in-depth training on penetration testing, network defense, data protection, and ethical hacking tools. Learn from industry professionals in a hands-on environment and become proficient in identifying and neutralizing cyber threats. Whether you're a beginner or IT enthusiast, this course empowers you with the technical expertise to enter the cybersecurity field confidently. Gain certification and career opportunities in a high-demand industry.
0 notes
Text
0 notes
Text
Indian Institute of Computer Science (IICS) is Delhi's leading IT training institute, offering a wide range of affordable programs and courses to empower learners with essential technology skills. With expert instructors and practical training in areas like AI, programming, web development, and more, we aim to prepare students for thriving careers in the tech industry. Join us to build your future in IT!best software engineer courses in Delhi
#Graphic Designer Course in Delhi#Best ethical hacking institute in Delhi#best cyber security institute in delhi#Web Development Course in Delhi#Advanced computer institute Delhi#Multimedia and Animation Classes in Delhi#IT training institute in delhi#Computer Courses and Classes in Delhi#Best e-accounting institute in Delhi#computer course with placement#Best computer education institute in Delhi
0 notes
Text
0 notes
Text
IT Education Center is a dedicated and reputable supplier of solutions and training in the areas of networking, ethical hacking, and IT security. Delivering top-notch products and solutions to our clients is how we aim for excellence in everything we do. Our clients and students benefit greatly from our emphasis on practical, hands-on training, which helps them grow quickly and flourish in their chosen field(s). We specialize in addressing Black Hat level topics such as exploit development, reverse engineering, penetration testing, etc. and our primary activity is offering elite training in information security and networking, ethical hacking, and other related areas.
0 notes
Note
Hacking and coding isn’t that hard. This isn’t to discredit your worth ethic and accomplishments (I deeply admire you) it’s a PSA to your followers.
Is there an internet cat whose deeds you’d like to emulate?
Take a little time and learn how the tech you interact with every day works. You’d be surprised at how “simple” most machines are. How vulnerable you personally are.
People see the long streams of numbers and words and get psyched out. But really you just need to learn rules. Some coding classes are like 3 months long. It’s a learnable hobby in your own time like baking.
yeah! a big part of why i do the work i do (primarily as like a "science communicator" type girlie for hacking/activism rly) is that i am trying to show people they can do things like that and show that curiosity rly is everything :) that's why u try to keep my technical writing as accessible as possible as well
2K notes
·
View notes
Text
König X Reader (F) ~Nerdy Little Maus~ When the reader successfully gets into a Dark Web Forum and makes a name for herself, how unfortunate for her she's a little to trusting with her client. How fortunate for the client, König, though that she falls right into his trap for him to take his nerdy little maus, all for himself. (Daddy Issues, Sugar Daddy, Kidnapping, Corruption Kink, Size Kink, Female Reader) Ao3 Link No TW - Part 1

Life had not been kind to you when you were young. Your mother passed away tragically, leaving you to be cared for by your father, who took the bottle to cope with her death. You tried desperately to gain his favor by excelling in your studies, but sadly, his drinks kept all his attention.
You were taking a computer science class in high school and excelling at learning code. The teacher, Mr. Johnson, was impressed at your ability to pick up the new information so quickly. Mr. Johnson pulled you aside one day and handed you a flyer for an ethical hacking competition; he truly believed you had what it took to win. For a few weeks straight, you stayed after school studying with a small group of other students, learning everything Mr. Johnson knew to teach. On the Saturday of the competition, your father begrudgingly permitted you to go with Mr. Johnson, Mrs. Johnson, and a few other classmates as a group.
You won the competition that day and were awarded a $10,000 scholarship to the Massachusetts Institute of Technology (MIT). The joy you felt as you stood on stage accepting your scholarship brought tears of happiness to your eyes. It was a shame your father was too busy-(drunk) to see how you glowed with pride at the most significant achievement of your life thus far.
Now, you sat in a dingy studio apartment. Staring at your Dell laptop at overdue bill emails. Student loans, rent, and credit card payments all accumulated with no significant income to pay them. You graduated from MIT but at the cost of over $80,000 in student loans. You couldn't find a job in the computer science field; the only work you landed was as a bartender at the bar down the street from your place. At least you were good at making drinks; tips kept the lights on, but you were sure you'd never make it out of the financial ruin you sadly got yourself into.
Whenever the manager encountered computer issues, you were always the first one he'd call. One day, while on the clock, you sat in his office, updating his pc to Windows 10. He watched as you had no issues clicking here and there; it was almost infuriating because, to him, what you did so effortlessly would have taken him hours to achieve just step one.
"You know, sweetheart, you need to get out of here and get a job in the computer field." Mike, the manager, said gruffly as he leaned arms crossed on his office door frame.
"Would if I could, Mike. I've all about givin' up on that dream." You replied, still staring at the blue computer screen.
"Don't cut yourself short. You are young, beautiful, and way smarter than any of the other idiots I have working here. Bring in the most money, too. I would miss that, though, if ya leave."
You let out a half-hearted chuckle. "Yeah, well, I use my pretty privilege more than my fucking MIT degree. But it helped me pull a $100 tip last week from the bachelor party, though. So don't worry, I'm not going anywhere, Mike."
Mike stands quietly and clears his throat, waiting a brief moment before he speaks again.
"Don't tell anyone I told ya, alright? But my buddy David knows a kinda underground Dark Web group that is always looking for someone like you. You know, that knows how to do computer stuff." He talked as he gestured vaguely with his hands.
You turn your head to Mike with a curious, almost dumbfounded look. "I don't know, Mike. The Dark Web is a pretty scary place I've heard. But they have open computer science jobs?"
"Yeah, from what I could understand, it's like a job forum, I guess. They have special passwords and whatever, but if you get in, they post jobs for people to take up and work."
You couldn't help but chuckle at Mike, but you appreciated his thoughtfulness in thinking of you, so you decided to take the bait.
"Sure, you give me the info, and I'll look into it, boss man."
A few days later, you received an email from someone you guessed was Mike's buddy, David, on your day off and clicked the link that opened a new web browser to a black screen. You fiddled with the settings on your old Dell laptop while sitting cross-legged on your thrifted couch when you increased the brightness to see a small set of instructions.
"I'll be dammed." You spoke quietly as you began your journey to unlock the puzzles hidden in the code.
It took five hours to finally get to the last section that unlocked access to the Dark Web forum. Sure enough, there were jobs from all around the world posted. As quickly as your excitement grew, worry flooded over you. These were not regular hacking jobs. Some were as simple as finding passwords to ex-lovers' accounts, but others were looking for classified government data locked away behind high-security firewalls. The thought of possible jail time or worse was frightening, so you shut your laptop and went to shower before bed. That night, you couldn't sleep, primarily due to the fear of the unknown but also because some of the jobs posted had the amount of money they were offering when completed. The memory of a 10,000 dollar payout for a hacking job bounced around your mind, toying with you. It danced along in bitter-sweet harmony with the memory of the 10k scholarship you won so many years ago.
On your next day off, you entered the forum again. It was too hard to resist the temptation of a simple job paying your rent for the month. So you avoided the big, scary ones and stuck to hacking into wealthy civilian accounts. You created an online persona account that allows the clients to send money and messages as needed. You called yourself "Cookie," a play on Cookie pop-ups for advertisers to gather your online information. Soon, you grew a small following and became recognized for your impressive hacking abilities and Trojan Virus creations. You told yourself repeatedly you were only ruining wealthy people's lives. What is a million dollars stolen from a billionaire anyway? It only took eight months to pay back almost all your debts. You've paid your rent up, no more credit card bills, and you've paid $5,000 into your student loan debts. You felt on top of the world and proud of your mischievous achievements.
It had been a long shift at the bar, and you entered your tiny apartment completely exhausted. You reheated some leftovers and took your regular seat on the couch. You open your laptop to see a new message on your Dark Web account.
"Hallo, Cookie. I am very impressed by your work. Care to look at a job I think you would be perfect for?"
You stared at the message as your curiosity peaked. You click on the stranger's profile to learn more about the mysterious sender. There is no profile picture, but in a small bio, the sender had "Austria" with a cute little red and white flag. They identified themselves as male, and his username was "TheKingCol."
That's interesting, you thought. You haven't worked with many international clients thus far. Your eyes began to cross as exhaustion set in deep in your bones. So, you decided to pick back up with the stranger tomorrow after sending him a message.
"Thank you for your message; yes, I would like to speak further with you. Let's chat more tomorrow."
You woke up later than usual with the sun high in the sky, peeking through your closed curtains. You stretched your body, and after a trip to the bathroom, you returned to your laptop. A new message was waiting for you, and you clicked it open to read. It was a Word Document link with what the client needed. He needed a Trojan Virus, and it had to be discreet so that the victim downloading it wouldn't know it was a fake link.
"That's not too bad." You thought to yourself.
You had created multiple Trojans up to this point, but it helps tremendously if you know what would make the victim unsuspecting to download the disguised Trojan.
"Hello again. I received your instructions, but I would like to discuss more details needed to create the perfect Trojan you are looking for, if possible."
You sent the message and waited a few minutes before your stomach began to growl. You stood up and began to rummage through your fridge for anything you could make to resemble breakfast and settled on making two fried eggs and a buttered piece of toast.
Once you ate your food, you returned to your seat to see another message had come through.
"Ja, may I call you to discuss details?"
You stared at the email, re-reading it. You quickly googled what language is spoken in Austria, and it said that mainly German is spoken. "He must not be a native English speaker," you thought, but that shouldn't be a problem. You, however, only knew English and maybe one or two words in Spanish.
"I'm sorry, I do not make phone calls or talk to clients outside the forum." You sent the message back and waited while you took sips of coffee from your favorite mug.
"Ah, but can't you make an exception for me? I understand your concern, little maus. I see you are a woman, no? Your father taught you well not to trust strangers on the internet."
You scoffed out loud at his message, placed your mug on the coffee table in front of you, and typed him back before thinking.
"Let's be clear that my Father has never done shit for me, first of all." You instantly regretted the message sent, normally you would write messages but always caught them before you tapped the enter button. There is no way to unsend a message like on Facebook. Airing out such dirty laundry to a client was entirely uncalled for and absolutely embarrassing.
"I'm sorry, that was very unprofessional of me. Please ignore that comment." You sent another message as quickly as you could type it. A few agonizing minutes later, you received a response.
"Is that so? A woman needs a supportive father to look after her, you know. No need to apologize Liebling. Here is my phone number; please call me if you decide to proceed. I will not discuss any more details by message."
That was the last message he sent before his profile was marked as "offline."
A day later, you paced around your living room. You held your phone tightly in your right hand. There was something about what he said that stuck with you long after you read it. Why on earth did you let your daddy's issues slip through to a prospective client? Embarrassment washed over you all over again, and soon enough, the anxiety of calling a client outside the forum was an afterthought. Before you knew it, you had typed in the number and hit the green call button.
The phone connected, but on the other side of the receiver was quiet.
"Hello?" You called out. "It's um, Cookie, from the forum." A second passed before you heard a voice from the other end.
"Ah, my little maus, so happy you've finally called."
37 notes
·
View notes
Text
during the week when I played seekL I was literally learning about the ethics of hacking in my class
sir if hacker man bad then why hacker man (odxny) hot


216 notes
·
View notes
Text



How was Felix's case going? Not good. Their current tactics in exploiting the scammers were not enough for the court. From their sources, the Sterling-Ricos had hacked into the bank organisation to steal Felix's money. Apparently, the bank had a request to fortify their system security from any tech company and since Isaac was a certified ethical hacker, he secured the job before anyone else! Through this method, he also found concrete evidence to end the scammers! He looked up after learning of the new data...

"I found something." All his new findings were enough for legal proceedings on their half, but there was also evidence concerning corruption or money laundering schemes...meaning the Sterling-Rico family could be connected to something bigger.

"Let's transfer this over to detectives, it's not something of our scope," Vincent thought. "Good job Isaac, I'm glad you spotted this."

With Isaac as his right-hand man, Vincent believes they could take on anything. "Anyway, where'd you learn how to hack?" he was curious. "Oh, I took some cybersecurity classes during law school. More hard work and now here I am, eyes as sharp as an eagle," Isaac joked around with his nickname back then. Vincent laughed and sat down, "Lucky you're on our side with that!"

Isaac took off his glasses and chuckled, "Heh, they don't call me Eagle Eyes for nothing."
#ts4#sims 4#ts4 gameplay#ts4 legacy#postcard legacy#postcard gen 3#vincent kingsley#isaac kingsley#pam thawatchai#i just noticed isaacs wearing eyeliner lmao#isaac wearing glasses something i wanted to see 😏 so attractive#vincents old office was a bit beige so i gave it a new makeover!!#and hell yeah they finally got that evidence for court and now to win!#the amount of research im doing for story 😂 like im researching law/detective stuff making things kind of accurate#but its sims doesnt have to be 100% realistic so making own twists#also i feel i can be more descriptive like this instead of writing dialogue in the pics! love using both methods for dialogue
92 notes
·
View notes
Text

“That bit is upside down,” Jen chews her lip, holding two halves of a tent pole. “Or is it? I don’t know. Maybe you were right.”
“I have no clue, to be honest.” I hold my hands up in surrender and back away from the crumpled heap that is our shared tent for the weekend, the sight of which fills me with increasing dread. “You know what I’m like. I can’t do stuff like this.”

“Like read?” She scrutinises the crumpled instruction sheet for the tenth time. “This shouldn’t be so hard for us. Do you think we should have been assessed in school?”
“For a learning difficulty? What? No. There weren’t classes for this kind of complicated stuff. It’s not our fault.”

“It’s piss easy,” Shane comments. He assembled both his tent and Claire’s and Evie’s in the time it took Jen and me to wrestle our tent parts from the bag. “You put the poles together, thread them through the tarp, and stick the pins in the ground. What’s the matter with ye?”
“Dunno. We’re just fucking stupid, I suppose.”
“Push over, I’ll do it.”
Jen lets the poles roll off her palm onto the ground and we let him, watching uselessly as he slots the poles together with some sort of insane, military efficiency and has the whole thing standing neatly, our perfect, nylon dome, in about two minutes flat.


“Thanks,” I say.
Jen echoes. “Yeah, jeez, cheers for that.”
“Do you ever think the real world is, like, going to come and bite ye in the arses?” Shane wonders, wiping the sweat from his face with the hem of his t-shirt. “When you go off and start living on your own, I mean. Do you ever worry you won’t be able to hack it?”
I look at Jen, and she at me. I shrug. “I’m moving to a city, like, do you think there’ll be wilderness excursions there, or something?”
“You might eventually need to read instructions, is all.”
I grin. “Someone else can do it for me.”

“Right, yeah.” his brow furrows. “I’m just saying, like, you might get a bit of a shock when you’re out there on your own.”
“I’ve been alone though,” I argue. “It’s not like my parents do everything for me. I’m not one of those kids who was-”
“Yeah, not with all things, just some things. Like, what if you ever needed to earn your own money, to get a job in a restaurant or something? Do you not think you’d need a bit of know-how, a bit of practical experience?”
I scoff. “Why would I need to do that?”
“Because sometimes people have to work.” I hate the way he’s saying it, and feel my body stiffen like hackles are rising along my spine. Of course, Shane is going on about this. Proper job this, practical experience that.

This is the tone that accompanies every tactful reminder that he comes from a hardworking family and I, apparently, do not. Like my parents’ academic backgrounds lessen their credibility. Like it makes them snobbier, lazier, more willing to sneer at ordinary folk. What's true for them does not automatically extend to me. To think so is an insult.
Shane’s dad is the head chef in some hotel in Tullamore, his mother a florist who works seven days a week, and they have drilled into him and Kelly their extraordinary, frankly ridiculous work ethic. They think it’s normal, aspirational even, to get up at five in the morning for some mundane job. But I know something with more truth to it: that there’s merit in taking it easy, with relaxing, sleeping in, and spending time with the things you enjoy. And, by the way, what does all of this have to do with a tent?

I plaster on my best laid back smile and drop a hand onto his shoulder.
“This is a boring conversation.” I insist, in the hopes that I will embarrass him out of putting me through this conversation. “Let’s grab a few drinks, yeah? Talking about future stuff should be off-limits for the weekend.”
He shrugs. “I suppose, yeah. I’ll drop it.”
“Thanks, mate.”



I amble over to where the girls hang out on the grass and join them, getting Claire to pass me of the drinks we smuggled through among an inaccessible pile of socks and underwear at the bottom of her bag. I crack it open and swish the beer around my mouth. It’s warm, horrible, but it’s wonderful in another way. It’s the most authentic experience possible. Here I am, in a field, drinking warm beer with the sun on my face. Carefree, with the rhythmic beat from the main stage pulsing through the earth beneath me. I could get used to things being simple.
Beginning // Prev // Next
42 notes
·
View notes
Text
0 notes
Text
Masterlist of Free PDF Versions of Textbooks Used in Undergrad SNHU Courses in 2025 C-1 (Jan - Mar)
Literally NONE of the Accounting books are available on libgen, they all have isbns that start with the same numbers, so I think they're made for the school or something. The single Advertising course also didn't have a PDF available.
This list could also be helpful if you just want to learn stuff
NOTE: I only included textbooks that have access codes if it was stated that you won't need the access code ANYWAY
ATH (anthropology)
only one course has an available pdf ATH-205 - In The Beginning: An Introduction to Archaeology
BIO (Biology)
BIO-205 Publication Manual of the American Psychological Association Essentials of Human Anatomy & Physiology 13th Edition
NOTE: These are not the only textbook you need for this class, I couldn't get the other one
CHE (IDK what this is)
CHE-329
The Aging Networks: A Guide to Policy, Programs, and Services
Publication Manual Of The American Psychological Association
CHE-460
Health Communication: Strategies and Skills for a New Era
Publication Manual Of The American Psychological Association
CJ (Criminal Justice)
CJ-303
The Wisdom of Psychopaths: What Saints, Spies, and Serial Killers Can Teach Us About Success
Without Conscious: The Disturbing World of the Psychopaths Among Us
CJ-308
Cybercrime Investigations: a Comprehensive Resource for Everyone
CJ-315
Victimology and Victim Assistance: Advocacy, Intervention, and Restoration
CJ-331
Community and Problem-Oriented Policing: Effectively Addressing Crime and Disorder
CJ-350
Deception Counterdeception and Counterintelligence
NOTE: This is not the only textbook you need for this class, I couldn't find the other one
CJ-405Private Security Today
CJ-408
Strategic Security Management-A Risk Assessment Guide for Decision Makers, Second Edition
COM (Communications)
COM-230
Graphic Design Solutions
COM-325McGraw-Hill's Proofreading Handbook
NOTE: This is not the only book you need for this course, I couldn't find the other one
COM-329
Media Now: Understanding Media, Culture, and Technology
COM-330The Only Business Writing Book You’ll Ever Need
NOTE: This is not the only book you need for this course, I couldn't find the other one
CS (Computer Science)
CS-319Interaction Design
CYB (Cyber Security)
CYB-200Fundamentals of Information Systems Security
CYB-240
Internet and Web Application Security
NOTE: This is not the only resource you need for this course. The other one is a program thingy
CYB-260Legal and Privacy Issues in Information Security
CYB-310
Hands-On Ethical Hacking and Network Defense (MindTap Course List)
NOTE: This is not the only resource you need for this course. The other one is a program thingy
CYB-400
Auditing IT Infrastructures for Compliance
NOTE: This is not the only resource you need for this course. The other one is a program thingy
CYB-420CISSP Official Study Guide
DAT (IDK what this is, but I think it's computer stuff)
DAT-430
Dashboard book
ECO (Economics)
ECO-322
International Economics
ENG (English)
ENG-226 (I'm taking this class rn, highly recommend. The book is good for any writer)
The Bloomsbury Introduction to Creative Writing: Second Edition
ENG-328
Ordinary genius: a guide for the poet within
ENG-329 (I took this course last term. The book I couldn't find is really not necessary, and is in general a bad book. Very ablest. You will, however, need the book I did find, and I recommend it even for people not taking the class. Lots of good short stories.)
100 years of the best American short stories
ENG-341You can't make this stuff up : the complete guide to writing creative nonfiction--from memoir to literary journalism and everything in between
ENG-347
Save The Cat! The Last Book on Screenwriting You'll Ever Need
NOTE: This i snot the only book you need for this course, I couldn't find the other one
ENG-350
Linguistics for Everyone: An Introduction
ENG-351Tell It Slant: Creating, Refining, and Publishing Creative Nonfiction
ENG-359 Crafting Novels & Short Stories: Everything You Need to Know to Write Great Fiction
ENV (Environmental Science)
ENV-101
Essential Environment 6th Edition The Science Behind the Stories
ENV-220
Fieldwork Ready: An introductory Guide to Field Research for Agriculture, Environment, and Soil Scientists
NOTE: You will also need lab stuff
ENV-250
A Pocket Style Manual 9th Edition
ENV-319
The Environmental Case: Translating Values Into Policy
Salzman and Thompson's Environmental Law and Policy
FAS (Fine Arts)
FAS-235Adobe Photoshop Lightroom Classic Classroom in a Book (2023 Release)
FAS-342 History of Modern Art
ALRIGHTY I'm tired, I will probably add ore later though! Good luck!
22 notes
·
View notes
Text
By: David Averre and Elena Salvoni
Published: Nov 27, 2024
Samuel Paty, 47, was brutally stabbed and decapitated on October 16, 2020
The Muslim schoolgirl who accused her teacher of Islamophobia and began rumours that led to a jihadist decapitating him in the street in France has admitted lying and apologised to the victim's family in a remarkable court hearing today.
History and geography teacher Samuel Paty was murdered on October 16, 2020 by Abdoullakh Anzorov, an 18-year-old Islamist radical of Chechen origin.
Anzorov tracked down 47-year-old Paty and brutally hacked his head off after seeing pictures and videos of him circulated on social media as part of a ruthless campaign of harassment.
It began after the schoolgirl in question claimed that Paty had ordered Muslim students to leave his classroom while he showed the rest of the class caricatures of the Prophet Muhammad by satirical newspaper Charlie Hebdo.
But she revealed today that she had not even been present in the class and invented the lie, fearing repercussions from her parents after she was suspended two days for bad behaviour.
The student, who was 13 at the time of the murder and whose identity remains protected due to her age, cried as she addressed Paty's family.
'I know it's hard to hear, but I wanted to apologise... I wanted to apologise sincerely. I'm sorry for destroying your life,' she reportedly said through tears.
'I apologise for my lie that brought us all back here,' she added, admitting to those in attendance, including the accused: 'Without me, no one would be here.'
The schoolgirl's father, Brahim Chnina, is accused of launching the online harassment campaign against Paty, while other teen students were tried last year after they identified him for the attacker in exchange for a few hundred euros.
Anzorov, who had requested asylum in France and travelled more than 60 miles to cut down Paty in public, was killed by police shortly after the murder near the school in Conflans-Sainte-Honorine west of Paris.

[ History and geography teacher Samuel Paty, 47, was decapitated outside a school near Paris ]
Paty is regarded as a free-speech hero by many in France.
He had shown the Charlie Hebdo caricatures to students as part of an ethics class in which his pupils were discussing the fallout of the 2015 terror attack on newspaper's offices in which 12 people were murdered by extremists.
But he had not ordered any students to leave the room, instead telling them what he was going to do as part of the ethics lesson before inviting them to turn away if they thought they would be offended by the caricatures.
Seven men and one woman are appearing at the Special Assize Court in Paris amid the trial over his murder, which is set to last until December 20.
Chnina is one of them, facing charges of association with a terrorist organisation for his alleged involvement in the online campaign targeting Paty.
Six students, including Chnina's daughter, were tried last year for their role in Paty's death.
The schoolgirl had accompanied her father to file a complaint at the time. 'I wanted to tell my parents that it was false, I knew that my father was not going to do anything to me , but I was afraid to say it,' she said in court today.
After Paty's murder, she was taken into police custody, during which time she continued to lie. 'My teacher had been decapitated, my father was in police custody, I couldn't say it was false,' she said.
She finally confessed the truth after 30 hours and two police interviews.
The schoolgirl received an 18-month suspended sentence for the slanderous allegations she made against Paty that ultimately proved the catalyst for his murder.
Her five co-defendants, all of whom were aged 14 or 15 at the time of the murder, faced charges of criminal conspiracy with the aim of preparing aggravated violence.
Four were handed suspended sentences but one received a six-month term with an electronic tag after being identified as the person who pointed Paty out to Anzorov.

[ This court sketch made and published on November 4, 2024, shows (L-R) defendants Abdelhakim Sefrioui, Louqmane Ingar, Azim Epsirkhanov, Priscilla Mangel and Yusuf Cinar sitting during the trial of eight adults charged with contributing to the climate of hatred that led to an 18-year-old Islamist radical in the 2020 beheading teacher Samuel Paty ]

[ Paty was violently stabbed to death and then decapitated by 18-year-old Chechen refugee Abdoullakh Anzorov on October 16, 2020 ]
Also on trial at the court in Paris is Abdelhakim Sefrioui, a 65-year-old Franco-Moroccan Islamist activist.
He and Chnina spread the teenager's lies on social networks with the aim, according to the prosecution, of 'designating a target', 'provoking a feeling of hatred' and 'thus preparing several crimes'.
Both men have been in pre-trial detention for the past four years.
Between October 9 and 13, Chnina spoke to Anzorov nine times by telephone after he published videos criticising Paty, the investigation showed.
Sefrioui meanwhile posted a video criticising what he considered to be Islamophobia in France and describing Paty as a 'teaching thug'.
He insisted to investigators he was only seeking 'administrative sanctions' against Paty, not violence.
Two young friends of the attacker are facing even graver charges of 'complicity in terrorist murder', a crime punishable by life imprisonment.
Naim Boudaoud, 22, and Azim Epsirkhanov, 23, a Russian of Chechen origin, are accused of having accompanied Anzorov to a knife shop in the northern city of Rouen the day before the attack.
'Nearly three years of investigation have never managed to establish that Naim Boudaoud had any knowledge of the attacker's criminal plans,' his lawyers Adel Fares and Hiba Rizkallah said.
Boudaoud is accused of accompanying Anzorov to buy two replica guns and steel pellets the day of the attack.
Epsirkhanov admitted he had received 800 euros from Anzorov to find him a real gun but had not succeeded.
Four other defendants interacted with Anzorov online prior to Paty's murder.
Yusuf Cinar, a 22-year-old Turkish national, shared a jihadist Snapchat account with him, that later published images of Paty's killing.
Ismail Gamaev, a 22-year-old Russian of Chechen origin with refugee status, and Louqmane Ingar, also 22, exchanged jihadist content on a Snapchat group with Anzorov. The first posted an image of Paty's head with smiley faces after the killing.
The only woman on trial is 36-year-old Priscilla Mangel, a Muslim convert who conversed with Paty's killer on X, describing the teacher's class as 'an example of the war waged by (France's) Republican institutions against Muslims'.
Thibault de Montbrial and Pauline Ragot, lawyers for Mickaelle Paty, one of the sisters of the murdered teacher, said his killing had highlighted the 'depth of Islamist infiltration in France'.
The trial should 'allow our society to become aware of a mortal peril', they added.
==
It's so weird because we're always told that women never make false accusations, or when they do, they're not consequential and don't ruin lives. /s
When people say that men are more aggressive than women, they leave out the part where women wield men's aggression as a weapon.
19 notes
·
View notes
Text
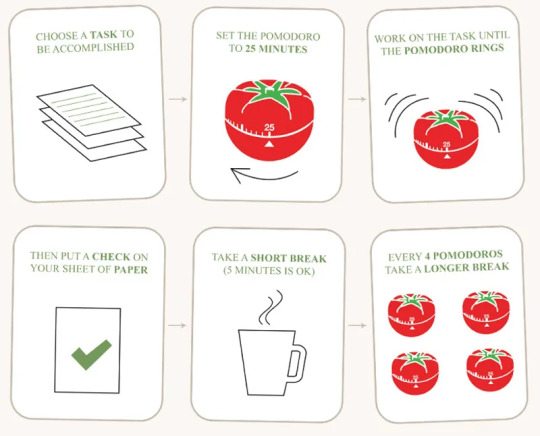
WHAT IS POMODORO AND WHAT DO YOU EAT IT WITH?
First… what is the Pomodoro method?!
The Pomodoro (Italian for tomato) technique was created by Francesco Cirillo in the 80s. Cirillo is an author and owner of a consulting company. He created this time managing technique that breaks down your study time into manageable intervals with breaks between each study session. With the countless distractions we have today, there’s no wonder it is still one of the most popular and helpful techniques for increasing productivity!
1. You need to plan your tasks
This will help you gauge how many sessions you will need. Will you be reading? Watching a lecture and taking notes? When planning what I will study, I know that watching a lecture and taking notes will take me sooo much longer than doing a reading or flashcards (less strenuous things). I also know that my core science courses will typically take much more studying time than one of my electives.
Determine what is most time-consuming and plan accordingly. The Pomodoro method is perfect for concentrating on any task, but you want to have in mind the classes that require more focus and time than others.
2. Set a 25-minute timer
25 minutes is only a recommendation and you can increase the time or lower it depending on how long you believe you can stay focused without interruptions. I mean, I don’t recommend you set a 5-minute timer to study and then a 5-minute break. But a session somewhere between 20-30 minutes is great (and how long I set my timer while studying)!
One other thing that Cirillo notes is that this time cannot be broken. You must work the entire 25 minutes without any distractions! One of my favorite ways to cancel out distractions is to:
-Put my phone in another room, or in my closet
-Or use the Forest app, which is a timer app that restricts you from leaving the app while completing work/other tasks. This guarantees I stay on task the whole time I am working!
3. Set a 5-minute timer for a break
Between each 25-minute study session, you need a break. You deserve it! So Cirillo recommends only a 5-minute break in between each study session. Do something that doesn’t bring you stress.
Tip: Make sure you do NOT work throughout the break at all. This break is meant to be a relaxing period to take your mind off of your work.
4. Repeat the process 3 times
This studying technique includes four sessions. So do this same process 3 more times. Work diligently and remember to stay focused.
5. After your 4th session, extend the break time to 20-30 minutes long
Once you have finished your fourth session, take a longer break! This is a huge accomplishment and after you have completed it, you will (and should) be so proud. The longer break allows you to take your mind off of your work and reset so you can get back into it.
Why It Benefits You...
IT WORKS FOR ANY TASK
Don’t think I only use this productivity hack for studying! This can be used while cleaning, organizing, reading, and so many other things! Remember, you can tweak the time frames depending on the task and depending on how much time you have to complete it. This is an amazing life hack that I believe everyone should be implementing to help with time management.
IMPROVES CONCENTRATION
Like I noted earlier, this is a distraction-free strategy! It’s on you to remove the distractions from your sessions, and when you do, you will see significant improvements in your work ethic. This technique was created to allow complete concentration on the task at hand. It will improve your focus, productivity, and concentration.
BEATS PROCRASTINATION
The Pomodoro technique breaks the time down into consumable segments. Would you feel more confident with saying you will study for 2 hours or 4 sessions of 25 minutes? I’m confident I would choose the latter every single time. This technique gives our brains manageable chunks of time to study so we result in more work getting done in the end. So just start working!
REMEMBER TO UTILIZE YOUR BREAKS
by Ania Henderson
#university#blogger#study blog#study motivation#study#study aesthetic#study buddy#study hard#study space#study tips#studygram#studyspo#studystudystudy
31 notes
·
View notes
Text
Print "Hello World"
Who I Am
My name is Emmanuel Igboanusi, and I’ve always had a passion for technology, particularly in the realm of security. Outside of tech, one of my biggest hobbies is riding motorcycles, which allows me to appreciate both speed and precision. I’m currently taking a technology program because I want to dive deeper into how we can protect sensitive data and improve cybersecurity systems. Through this class, I hope to gain valuable insights that will help me become a better security professional.
Areas of Interest and Strength
I’m especially interested in cybersecurity. My focus is on protecting data, analyzing potential threats, and ensuring that confidential information is safe from unauthorized access. I find it fascinating to explore different ways to confiscate compromised data and mitigate risks before they escalate. I also enjoy hands-on experiences like working with servers, configuring networks, and ensuring they meet compliance standards. I hope to develop my skills further, especially in the areas of ethical hacking and encryption technologies.
Emerging Technologies
Emerging technologies refer to cutting-edge developments that have the potential to disrupt industries and change the way we live and work. These can include advancements like artificial intelligence (AI), and blockchain. I believe staying up to date on these technologies is crucial, especially as they play a major role in enhancing security frameworks. Understanding and integrating these innovations will help to better protect systems and data in the future.
9 notes
·
View notes
