#ethicalhacking'
Explore tagged Tumblr posts
Text

#hackerman#mr robot#the mainframe#im in!#ethicalhacking#haha#litterally me#hahaha#ha ha funny#relatable#relatable memes#dank memes#funny memes#meme#shitpost#cat#cute cats#meow#memes#funny#lmao#humor#caturday
64 notes
·
View notes
Text
Need to find a cute trans girl who’s into ethical hacking, so she can do penetration testing on me :3
14 notes
·
View notes
Text

Can't bots just trust we're human without the robot dance-off? 😄
#linux#linuxfan#linuxuser#ubuntu#debian#dev#devops#webdevelopment#programmingmemes#linuxmemes#memes#cat#coding#developer#tech#ethicalhacking#computerscience#coder#security#infosec#cyber
154 notes
·
View notes
Photo

(via Pin page)
#Cybersecurity#Infosec#Privacy#EthicalHacking#DataProtection#CybersecurityAwareness#Hacking#Security#PenetrationTesting#CyberAttacks#NetworkSecurity#DigitalSecurity#Malware#Phishing#CyberDefense#CyberThreats#Encryption#SecurityResearch#Firewalls#SecurityBreach#CyberSecurityNews#SecurityCommunity#CyberCrime#ThreatHunting#RedTeam#BlueTeam#InformationSecurity
10 notes
·
View notes
Text
The Complete Manual for Understanding Ethical Hacking
In order to evaluate an organization's defenses, ethical hacking—also referred to as penetration testing or white-hat hacking—involves breaking into computers and other devices lawfully. You've come to the correct spot if you're interested in finding out more about ethical hacking. Here's a quick start tutorial to get you going.

1. "Getting Started with the Basics"
Networking and computer science principles must be thoroughly understood before getting into ethical hacking. Here are some crucial aspects to pay attention to: Operating Systems: Acquire knowledge of several operating systems, with a focus on Linux and Windows. Learning Linux is essential because a lot of hacking tools are made to run on it. Networking: It's essential to comprehend how networks operate. Find out more about
protocols include HTTP, HTTPS, DNS, TCP/IP, and others. Understanding data flow across networks facilitates vulnerability detection. Programming: It's crucial to know at least a little bit of a language like Python, JavaScript, or C++. Writing scripts and deciphering the code of pre-existing tools are made possible by having programming expertise.
2. Making Use of Internet Resources To learn more about ethical hacking, there are a ton of internet resources available. Here are a few of the top ones: Online Education: Online learning environments such as Pluralsight, Coursera, and Udemy provide in-depth instruction in ethical hacking. "Penetration Testing and Ethical Hacking" on Pluralsight and "The Complete Ethical Hacking Course: Beginner to Advanced" on Udemy are two recommended courses. Channels on YouTube: HackerSploit, The Cyber Mentor, and LiveOverflow are just a few of the channels that offer helpful tutorials and walkthroughs on a variety of hacking tactics.
3. Exercising and Acquiring Knowledge The secret to being a skilled ethical hacker is experience. Here are some strategies to obtain practical experience:
Capture the Flag (CTF) Tournaments: Applying your abilities in CTF tournaments is a great idea. CTF challenges are available on websites like CTFtime and OverTheWire, with difficulty levels ranging from novice to expert. Virtual Labs: It is essential to set up your virtual lab environment. You can construct isolated environments to practice hacking without worrying about the law thanks to programs like VMware and VirtualBox. Bug Bounty Programs: Websites such as HackerOne and Bugcrowd link corporations seeking to find and address security holes in their systems with ethical hackers. Engaging in these initiatives can yield practical experience and financial benefits.

Dedication and ongoing education are necessary to learn ethical hacking. You can become a skilled ethical hacker by learning the fundamentals, using internet resources, and acquiring real-world experience. Always remember to hack wisely and ethically. Cheers to your hacking! I appreciate your precious time, and I hope you have an amazing day.
9 notes
·
View notes
Text
IoT Security Challenges in India: Protecting Smart Homes & Connected Devices

IoT is transforming the way people live by making their homes smart with devices such as security cameras, smart locks, and voice assistants. In India, IoT technology is adopted at a pace that cyber threats are rising rapidly. With weak security protocols, outdated software, and unawareness, Indian households are vulnerable to cyberattacks. In this blog, we will explore the major IoT security challenges in India and how individuals can safeguard their smart homes and connected devices. If you are looking to strengthen your understanding of cybersecurity, enrolling in a cyber security course can be a game-changer.
The IoT Boom in India
India is witnessing the highest adoption of IoT across homes and businesses. From smart TVs to intelligent thermostats, IoT is revolutionizing life. This booming technology, however, offers a large target size for hackers too who exploit the vulnerability of devices to gain unauthorized access to data.
Fundamental Drivers of IoT Adoption in India:
Increased internet penetration with low-priced data plans
Government initiatives such as Smart Cities Mission and Digital India
Increasing adoption of smart home devices as they become increasingly affordable
Growing application of industrial IoT in health, agriculture, and manufacturing
Chief IoT Security Challenges in India
Poor Authentication & Default Passwords
Most IoT devices have a factory-set password that the user ignores or fails to change. Hackers exploit these default credentials to take over the devices, entry private networks, and crack sensitive information.
Lack of Security Updates & Patches
Most smart devices have limited or no firmware updates, which makes them vulnerable to cyber threats. Many Indian consumers do not check for security updates, leaving their devices susceptible to known exploits.
Data Privacy Concerns
Smart devices collect vast amounts of personal data, from voice recordings to daily routines. Without stringent data protection policies, this information can be misused or leaked by malicious actors.
Botnet Attacks & DDoS Threats
Cybercriminals hijack unprotected IoT devices to form botnets, which are used to launch massive Distributed Denial of Service (DDoS) attacks. These attacks can cripple networks and cause disruptions to online services.
Unsecured Wi-Fi Networks
Many Indian households rely on poorly secured Wi-Fi connections, providing an easy entry point for hackers. Without encryption or strong passwords, attackers can intercept sensitive information and compromise connected devices.
Absence of Specific Cybersecurity Legislation for IoT
India has advanced in data protection with the Digital Personal Data Protection Act, but there is no dedicated IoT security framework. The absence of it leaves the manufacturer to choose cost over security and sell devices which are not so well protected in the market.
How to Secure Smart Homes & Connected Devices
Change Default Credentials
Always change the default usernames and passwords of the IoT after installation. Use strong, unique passwords and implement multi-factor authentication wherever possible.
Update Firmware Periodically
Scan for software and security updates on all smart devices, and install them as soon as they are available. In case your device can no longer get any updates, consider replacing it with a newer version that is at least as secure.
Secure Your Wi-Fi Network
Use a robust Wi-Fi password, and make sure WPA3 encryption is turned on. Limit remote access to your router, and make an IoT-specific network so that those devices can't contaminate your primary network.
Firewall & Security Solutions The use of firewalls and network security solutions monitors traffic and can block malicious activity on IoT networks. 5. Limit Data Sharing & Permissions
Assess permission for smart appliances and reduce or limit the devices from accessing unsecured personal information. De-activate unused add-ons, remote access in devices.
Cyber Security Courses
IoT-based cyber-attacks are minimized if awareness against the threat builds. To boost that awareness further, take time out to become a certified graduate of cyber security by signing for courses in areas like best security practices, principles of ethical hacking, and defending digital systems.
Road Ahead to Improving Indian IoT Security:
The Indian government, device manufacturers, and consumers must take proactive steps to mitigate IoT security risks. Stronger security standards, public awareness, and robust cybersecurity laws are the need of the hour to secure the future of IoT in India.
Conclusion
IoT devices offer incredible convenience but also introduce significant security risks. Protecting smart homes and connected devices requires a combination of best practices, awareness, and robust cybersecurity measures. By staying informed and adopting the right security strategies, individuals can ensure a safer IoT experience.
If you’re passionate about cybersecurity and want to build expertise in protecting digital systems, consider taking a cyber security course to gain hands-on knowledge and skills in ethical hacking, network security, and data protection.
3 notes
·
View notes
Text
Buy GitHub Account
A strong online presence is significant for businesses. Your GitHub account plays a crucial role in establishing your presence. Buy GitHub account saves you time by giving you access to advanced features and setting up a reliable profile. GitHub is widely used for code hosting project management and collaboration with teams. Businesses can showcase their technical expertise and help build a presence by presenting a professional GitHub profile. This is especially important for startups and companies wanting to grow their online presence quickly. So, buy GitHub account.
Our Services
✔ Complete irreversibility of a GitHub account
✔ Active GitHub account
✔ Very affordable prices.
✔ High quality services.
✔ 100% money back guarantee.
✔ Be ready to provide customers with a 24/7 service.
✔ Each of the provided services has additional options with bonuses.
✔ Note that, if you wish to buy this product, you must make a down payment.
For more information please get in touch with me
Email: [email protected]
Telegram: @usamarketingit
WhatsApp: +1 (501) 494-6400
#computerscience#css#kalilinux#coder#coders#webdeveloper#webdevelopment#hacking#softwaredeveloper#codinglife#machinelearning#stackoverflow#ethicalhacking#cybersecurity#code#hacker
2 notes
·
View notes
Text
Buy GitHub Account
A strong online presence is significant for businesses. Your GitHub account plays a crucial role in establishing your presence. Buy GitHub account saves you time by giving you access to advanced features and setting up a reliable profile. GitHub is widely used for code hosting project management and collaboration with teams. Businesses can showcase their technical expertise and help build a presence by presenting a professional GitHub profile. This is especially important for startups and companies wanting to grow their online presence quickly. So, buy GitHub account.
Our Services
✔ Complete irreversibility of a GitHub account
✔ Active GitHub account
✔ Very affordable prices.
✔ High quality services.
✔ 100% money back guarantee.
✔ Be ready to provide customers with a 24/7 service.
✔ Each of the provided services has additional options with bonuses.
✔ Note that, if you wish to buy this product, you must make a down payment.
For more information please get in touch with me
Email: [email protected]
Telegram: @usamarketingit
WhatsApp: +1 (501) 494-6400
#computerscience#css#kalilinux#coder#coders#webdeveloper#webdevelopment#hacking#softwaredeveloper#codinglife#machinelearning#stackoverflow#ethicalhacking#cybersecurity#code#hacker
3 notes
·
View notes
Text
3 notes
·
View notes
Text
Hackers Unveiled: Exploring the Dual Worlds of Cyber Warriors
Summary: Discover the captivating world of hackers in Hackers: Revealing the Hidden World of Cyber Warriors. This article examines how hackers operate as both guardians and adversaries in the digital sphere, balancing ethical innovation with malicious intent.
Understand the latest cybersecurity trends and challenges by visiting the Tech Trends section of Amaranth Magazine. This must-read analysis sheds light on how hackers are reshaping our understanding of the digital frontier.
For more insights into technology and its impact on society, explore the Amaranth Magazine homepage to access a wide range of expert articles.
Stay Updated With Amaranth Magazine: Gain exclusive access to cybersecurity insights and digital innovations by subscribing to our updates through the Amaranth Magazine subscription page. If you’re passionate about sharing your expertise, consider contributing via the Amaranth content submission portal.
Collaborate With Us: Organizations specializing in cyber defense and technological solutions can partner with Amaranth Magazine. Learn more about opportunities through our Advertising Portal or review our Advertising Policy.
Additional Resources: Explore a curated archive of tech-focused articles or connect with us via the Amaranth Magazine contact page for inquiries.
Call to Action: Unearth the secrets of cyber warriors and their influence on the digital age by reading the full article, Hackers: Revealing the Hidden World of Cyber Warriors, in the Tech Trends section of Amaranth Magazine.

2 notes
·
View notes
Text
5 notes
·
View notes
Text

Kali Linux is a powerful OS for ethical hacking and cybersecurity tasks. Packed with tools for testing and analysis, it's a must for security pros! ⚡💻🔐
For the tutorial on Kali Linux click here: https://bit.ly/4jzJ0ga
2 notes
·
View notes
Text
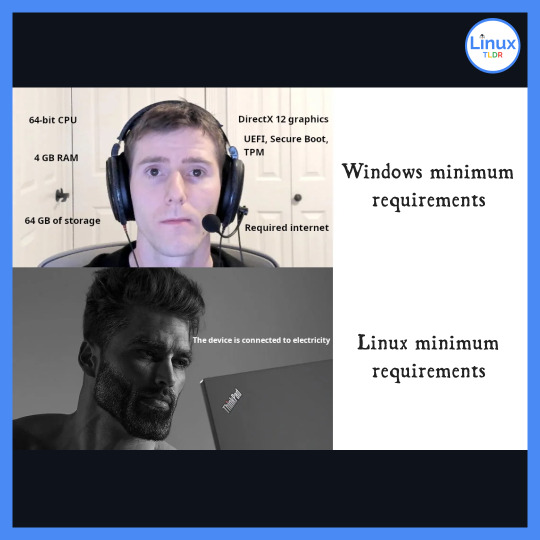
Windows: Hungry beast, Linux: Energy sipper!
#linux#linuxfan#linuxuser#ubuntu#debian#dev#devops#webdevelopment#programmingmemes#linuxmemes#memes#cat#coding#developer#tech#ethicalhacking#computerscience#coder#security#infosec#cyber
124 notes
·
View notes
Photo

(via How to DIY a ground station)
#Cybersecurity#Infosec#Privacy#EthicalHacking#DataProtection#CybersecurityAwareness#Hacking#Security#PenetrationTesting#CyberAttacks#NetworkSecurity#DigitalSecurity#Malware#Phishing#CyberDefense#CyberThreats#Encryption#SecurityResearch#Firewalls#SecurityBreach#CyberSecurityNews#SecurityCommunity#CyberCrime#ThreatHunting#RedTeam#BlueTeam#InformationSecurity
4 notes
·
View notes
Text

"Boost your business with strategic digital marketing, driving growth and engagement online effortlessly." ENROLL NOW !
#DigitalMarketing #GraphicDesigning #WebDevelopment #EthicalHacking
3 notes
·
View notes
Text
Deep Dive into Wi-Fi Hacking: How Ethical Hackers Secure Your Wireless Networks

With our hyper-connected world, Wi-Fi is the unseen lifeline keeping us online today. From streaming your favorite shows to managing your smart home devices, Wi-Fi is everywhere. But have you ever stopped to think about just how secure your wireless network really is? What if someone could sneak into your network, steal your data, or even hijack your devices? Scary, right? That’s where ethical hackers come in—the unsung heroes of the digital age who use their skills to protect, not exploit. If you’ve ever been curious about how they do it, or if you’re considering a cybersecurity and ethical hacking course, this blog is for you.
The Dark Side of Wi-Fi: Why It’s a Hacker’s Playground
Well, face it: Wi-Fi networks are a goldmine for cybercriminals. Why? Because they are usually the easiest weakness in our digital defense. It has weak passwords, outdated encryption, and misconfigured routers. That's not to mention stealing your Netflix login. Hackers can use it as an open gateway to access more of your digital life.
Here's your scenario: You're having your favorite coffee at a quaint little café while making use of their free Wi-Fi. Well, a hacker within some tables from you is running Aircrack-ng or Wireshark for quite a bit on your data that's going by. Before you realize it, they have gotten your login credentials, credit card information, or even obtained access to your corporate emails. How scary does that sound?
Enter Ethical Hackers: The Good Guys of Wi-Fi Security
That is when the ethical hackers come in. Cybersecurity professionals use the same hacking tools and techniques as evil hackers, with one difference though: they work for you. Their job is to find a hole before a hacker does so that they may fix it before hackers can gain entry into your network.
How do they go about it? Let's dissect this:
Reconnaissance: Ethical hackers first gather information about the target network. They use tools such as Kismet or NetStumbler to identify the network's SSID, encryption type, and connected devices.
Exploitation: Once they have identified potential weaknesses, they try to exploit them. For example, if the network uses outdated WEP encryption (which is notoriously weak), they might use tools like Aircrack-ng to crack the password.
Post-Exploitation: Having obtained access, the ethical hacker calculates the potential damage that can be done. Could they have accessed sensitive files? Could they have launched a man-in-the-middle attack? This step will give them a sense of real-world impact from the vulnerability.
Reporting and Patching: They finally document their findings and collaborate with the owner of the network to fix the issues. It may involve updating firmware, changing passwords, or enabling stronger encryption like WPA3.
Why You Should Care About Wi-Fi Security
You may be thinking: "I am an average user, so why would somebody even bother with me?" The thing is, hackers don't discriminate. Whether you are just an individual, a small business owner, or part of a large corporation, your Wi-Fi network is a potential target. And with the emergence of IoT devices, such as smart thermostats, security cameras, and voice assistants, the risk is much bigger than ever.
Here's the good news: You don't need to be a tech genius to protect yourself. By learning the basics of Wi-Fi security or even enrolling in a cybersecurity and ethical hacking course, you can take control of your digital safety.
How to Secure Your Wi-Fi Network: Tips from the Pros
Want to make your Wi-Fi network hacker-proof? Here are some practical tips inspired by ethical hackers:
Use Strong Passwords: Avoid using common passwords, such as "admin" or "password123." Instead, use long complex phrase with letters, numbers, and symbols.
Enable WPA3 Encryption: The latest Wi-Fi encryption protocol is WPA3; if your router supports it, switch to WPA3.
Update Your Router's Firmware: Manufacturers in their official websites may have coming updates that address security vulnerabilities. Check and update the firmware on your router to a newer edition.
WPS: Wi-Fi Protected Setup is convenient but highly insecure. Just turn it off to minimize brute-force attacks.
Check Connected Devices: You would be surprised to know which device is connected to your network if you don't check it periodically. If something looks suspicious, investigate immediately.
Ready to Be a Wi-Fi Warrior?
If this deep dive into Wi-Fi hacking has piqued your interest, why not take it further? A cybersecurity and ethical hacking course can teach you the skills you need to protect yourself—and maybe even turn your passion for tech into a rewarding career. Imagine being the person who uncovers vulnerabilities, thwarts cyberattacks, and keeps the digital world safe. Sounds exciting, doesn't it?
Ethical hacking is not the art of hacking into systems, but understanding how they work so that such knowledge can be applied to strengthen their defenses. In a world that is ever changing with threats through cyber, it has never been a better time to learn.
Final Thoughts
It sounds like something out of a spy movie, but the truth is that Wi-Fi hacking is an everyday threat in your life. The good news is that with the right information and tools you can protect yourself and your loved ones from becoming cybercrime victims. However, whether you are a tech enthusiast or a complete beginner, a course in cybersecurity and ethical hacking will empower you to take the lead in digital security.
Remember the next time you connect to a Wi-Fi network: those invisible waves keeping you online can be the doors for hackers. Stay informed and vigilant, and maybe you will end up being that ethical hacker who saves the day.
So, stay safe and happy ethical hacking!
2 notes
·
View notes