#fix browser hijacker
Explore tagged Tumblr posts
Text
Some recentish shows of note, or lack thereof:
COUNT ABDULLA: Charming comedy about a Pakistani doctor who gets turned into a vampire by a white vamp with a fetish for brown men, and the many complications that ensue. Not so much a horror story as a witty parable about the travails of being a person of color in Tory Britain today. (So, a horror story after all, then.) Jaime Winstone needs to dial it back, but the rest of the cast delights.
DEADLOCH: Snarky comedy-mystery by a well-known Australian comedy team, about mismatched cops investigating a gruesome murder in a small town. The mystery is clever; the payoff is blah; and despite the predominantly female, mostly LGBT cast, the humor is awfully reliant on misogynistic and homophobic cracks that frequently cross a line from "laughing with" to "laughing at."
HIJACK: Tense but very contrived seven-part thriller about the hijacking of a British airliner on a seven-hour-flight from Dubai to London, with passenger Idris Elba the wildcard. Gripping, but not terribly plausible, and the many false climaxes become exhausting, especially if you watch the episodes back to back.
THE LAZARUS PROJECT: Convoluted, intermittently fascinating, unpleasantly mean Sky sci-fi thriller about an app developer named George Addo (Paapa Essiedu), who's drawn into a secret organization that can undo world-ending disasters (natural or manmade) by resetting time to a predetermined save point, like a video game, although this has harrowing consequences for the handful of people capable of remembering the repeated resets. At first, this is basically just window dressing for grim espionage procedural nonsense, with some extremely questionable character motivations, but after a relentlessly bleak midsection, the first season finds its dramatic footing in the unexpectedly interesting final episodes, in which the premise is pushed to its breaking point and the grimness gives way to black comedy. This is the note on which the considerably more complicated second season begins, but it again grows uglier and bleaker as it goes on, and any sympathy for George, positioned at the start of the show as a relatable everyman, has long since evaporated. There are some provocative ideas and a number of surprisingly funny moments, but the whole story is predicated on pushing the characters into morally compromised positions (one assumes creator Joe Barton always has a browser tab open to the TV Tropes "Moral Event Horizon" page), and the fact that some of the (many) atrocities the characters perpetrate in hopes of fixing the existential catastrophes they've set in motion are subsequently undone doesn't make them any easier to stomach. Anjli Mohindra (who plays Archie, the veteran agent who initially recruits George into the project) remains frustratingly under-utilized in both seasons.
THE MORNING SHOW: Big-budget, all-star TV news drama is all dressed up with nothing to say, undone at every turn by truly spineless whataboutism and a centrist world view so gormless it makes Aaron Sorkin seem like Alexander Berkman. Reese Witherspoon is pretty good as closeted bisexual cohost Bradley Jackson, but costar Jennifer Anniston's limited range becomes a problem, particularly as the quality of the scripts declines noticeably in later seasons. You could always just watch BROADCAST NEWS.
THE OTHER BLACK GIRL: Disjointed adaptation of the 2021 Zakiya Dalila Harris novel scores when it focus on the workplace drama of a young Black woman in a painfully white publishing company, but trips over its own feet in its attempts to also be a paranoid thriller, with plenty of bad vibes that never add up to a coherent sense of threat and a conspiracy plot that doesn't really make any sense.
THE PERIPHERAL: Misfired adaptation of the 2014 William Gibson novel is executive-produced by the same people as the recent WESTWORLD series and has the same problems: big ideas that don't translate into action and an infuriating tendency to consign characters of color to marginal or villainous roles. Worse, it eventually becomes clear that several more compelling characters have been sidelined in favor of the poor white trash leads (Chloë Grace Moretz and Jack Reynor), who are neither very interesting nor especially sympathetic.
WHO IS ERIN CARTER?: Kinetic but preposterous seven-part action thriller with Evin Ahmad as a suburban mom in Barcelona who is secretly an incredible badass with a shady past. Basically a violent Walter Mitty fantasy for soccer moms who love the JOHN WICK movies, with a showy supporting role for Denise Gough from ANDOR.
#teevee#count abdulla#deadloch#hijack#the lazarus project#the morning show#the peripheral#who is erin carter#idris elba#chloe grace moretz#jack reynor#reese witherspoon#jennifer aniston#evin ahmad#denise gough#anjli mohindra#the other black girl#the morning show is also guilty of using characters of color as props#which it acknowledges in S03 while continuing to do it
9 notes
·
View notes
Text
A Bookmarklet (Javascript Bookmark)
Light text on a dark background quickly gets hard for me to read, so I have a Javascript bookmark that replaces the color settings of the page and forces every piece of text to be black on a white background, with boring old-fashioned blue/purple colors for links. It’s not aesthetically pleasing, but it’s more or less guaranteed to be readable. (An example and the text of the bookmark below the fold.)
As a demonstration, here’s a screen capture of a randomly-selected Tumblr blog with color as it appears normally:

After running the script, it looks like this:
(If you have other color preferences, you can just swap out “black” and “white” in the script with your choices.)
To make this work, add a bookmark in your browser, then use whatever mechanism your browser has for editing bookmarks to rename it something appropriate and replace the URL with the red text below:
javascript:(function(){var%20newSS,%20styles='%20{%20background:%20white%20!%20important;%20color:%20black%20!important%20}%20:link,%20:link%20%20{%20color:%20#0000EE%20!important%20}%20:visited,%20:visited%20*%20{%20color:%20%23551A8B%20!important%20}';%20if(document.createStyleSheet)%20{%20document.createStyleSheet(%22javascript:'%22+styles+%22'%22);%20}%20else%20{%20newSS=document.createElement('link');%20newSS.rel='stylesheet';%20newSS.href='data:text/css,'+escape(styles);%20document.getElementsByTagName(%22head%22)[0].appendChild(newSS);%20}%20})();
(That should be one single line with no spaces or line breaks, in case either Tumblr or your browser decides to play games with it.)
…as long as I’m at it, here’s a second very specialized utility script bookmark. Years ago, there was an epidemic of sites which would hijack your browser window and refuse to let you close the window or quit the browser, and the only way to get out of it was to force-quit your browser — and then make sure it wouldn’t auto-reload the content from the previous session when you opened it back up. I believe there are technical fixes in place now which prevent that form of attack, but just in case I still have my script bookmark which breaks out of that deadlock. Without changing the URL (which lets the page know you’re trying to get away) it uses the “document.write” function… which, notoriously, if used when the page has finished loading, replaces the entire page. This breaks any scripts the page may have in place to monitor your behavior, and the window/tab can then be closed. (But the URL in the location bar remains the same, and the browser thinks you’re still on the page, so the reload button will restore whatever was there before.) It is possible that this might be useful in other contexts, so here it is. The result looks like this:

To make it work, do the same as for the previous script, but replace the URL with this instead:
javascript:%20void(function(){document.write('%3Chtml%3E%3Chead%3E%3Ctitle%3E%2D%2D%20Page%20has%20been%20erased%20%2D%2D%3C%2Ftitle%3E%3C%2Fhead%3E%3Cbody%20style%3D%22margin%3A0in%3Bpadding%3A25%25%3B%22%3E%3Ch1%20style%3D%22size%3Axx%2Dlarge%3Btext%2Dalign%3Acenter%3Bcolor%3Ared%3Bmargin%3A25%25%3Bfont%2Dweight%3Abold%3B%22%3EThis%20page%20was%20erased%20using%20a%20bookmarklet%2E%3C%2Fh1%3E%3Cp%20style%3D%22text%2Dalign%3Acenter%3B%22%3EThis%20page%20has%20had%20its%20content%20replaced%20with%20this%20message%2E%20If%20you%20want%20the%20content%20back%2C%20you%20will%20need%20to%20reload%20the%20page%2E%3C%2Fp%3E%3C%2Fbody%3E%3C%2Fhtml%3E');}())
(Once again, that should be one long line with no spaces or line breaks.)
2 notes
·
View notes
Text
I'm going to hijack this post and share some resources:
- wikiversity.org: learning resources in various languages.
- majorgeeks.com: tutorials, tools, etc for your PC.
- mdgx.com: tricks, fixes, etc for your PC (if your PC is a bit old it might struggle loading it though, mine did...).
- devdocs.io: API documentations for different programming languages, frameworks, etc.
- cheat.sh (search on github): cheat sheets about programming languages and some tools. You can get it on your browser or on your shell.
i hate seeing people drink the openai/chatgpt koolaid 😭😭😭 genuinely feels like watching someone get seduced by scientology or qanon or something. like girl help it's not intelligent it's Big Autocomplete it's crunching numbers it's not understanding things i fuckign promise you. like ohhh my god the marketing hype fuckign GOT you
56K notes
·
View notes
Text
Chrome Searches Always Switch to Yahoo
If your Chrome searches keep redirecting to Yahoo, your browser might be hijacked. This is often caused by unwanted software or a malicious extension.
Google Chrome Logo – Transparent
Follow these steps to fix it:
Remove Suspicious Extensions
Open Chrome. Click the three-dot menu in the top-right corner.
Go to More tools > Extensions.
Look for extensions you don’t recognize. Click Remove to…
0 notes
Text
Hackers Exploit Outdated WordPress Versions and Plugins in Widespread Malware Attack

Source: prontomarketing.com
Share Post:
LinkedIn
Twitter
Facebook
Reddit
Pinterest
Hackers Target Vulnerable Websites
A large-scale malware attack is underway, as Hackers Exploit WordPress versions and plugins to compromise thousands of websites. Belgian security firm C/side has raised the alarm about this widespread cyber threat, which is affecting both high-profile and lesser-known websites. According to security experts, websites running outdated versions of WordPress or using outdated plugins are particularly vulnerable to these malicious attacks. Hackers are using these weaknesses to hijack sites and distribute malware to unsuspecting visitors.
Malicious Campaign Unveiled
The attack, carried out as Hackers Exploit WordPress, involves injecting a fake Chrome update page into compromised websites. When visitors load an infected website, the page appears to prompt them to download and install a browser update to continue browsing the site. In reality, this so-called “update” is a disguised file that contains malicious software. The malware is tailored for both Windows and Mac users, with specific variants targeting each operating system. Windows users are infected with the SocGholish malware, while Mac users are targeted by the Amos (Amos Atomic Stealer) malware.
Both malware types are designed to steal sensitive information such as usernames, passwords, session cookies, and cryptocurrency wallets. The attack has been identified as an “info-stealer” campaign, to compromise personal data from affected users. Security experts have warned that these types of malware pose significant risks to individuals and organizations, especially those who may have saved sensitive data in their browsers or online accounts.
Scale of the Attack and Discovery Process
The scale of the attack is alarming, with C/side reporting that more than 10,000 websites, including some prominent ones, have already been compromised. As Hackers Exploit WordPress, this malware campaign is categorized as a “spray and pray” attack, meaning it targets anyone who visits the infected websites, rather than focusing on specific individuals or groups. Researchers discovered the scope of the attack by crawling the internet for malicious scripts and performing reverse DNS lookups to identify more compromised domains linked to the same IP address.
After uncovering the widespread infection, C/side alerted Automattic, the company behind WordPress, about the ongoing malware campaign. The security firm provided a list of affected websites to Automattic, who confirmed receipt of the report. Although no immediate fix has been issued, the exposure of the attack has brought attention to the critical need for website owners to maintain updated versions of WordPress and its plugins to prevent further compromises.
1 note
·
View note
Text
Professional Virus and Malware Removal Service in Perth
Is your computer sluggish, freezing, or displaying unexpected pop-ups? These are often tell-tale signs of a virus or malware infection, which can seriously compromise your device’s performance and security. In Perth, you don’t have to worry about handling this alone—Virus Malware Removal Service Perth by Perth Computer Experts is here to help.

Why Choose a Professional Virus and Malware Removal Service?
While some viruses are simply a nuisance, others can lead to severe data breaches or system failures, especially if left untreated. Perth Computer Experts offers a trusted Virus Malware Removal Service Perth that is thorough, efficient, and reliable. Our experienced team ensures that your computer is not only cleared of viruses but also optimized for future security.
Benefits of Choosing Perth Computer Experts
Expert Diagnosis and Removal: Our team specializes in detecting and eliminating all types of malicious software, including trojans, spyware, ransomware, and adware.
System Optimization: We don’t just remove the virus; we also clean and optimize your computer, restoring its speed and performance.
Prevention Tips: Beyond the immediate fix, our experts offer advice on how to safeguard your device against future malware threats.
Signs Your Computer Needs a Virus and Malware Removal Service
Slow Performance: A virus can slow down your system, making even simple tasks frustratingly slow.
Unexpected Crashes: Frequent system crashes and error messages are often caused by malicious software.
Pop-Up Ads and Browser Redirection: If you notice excessive ads or your browser redirecting without your consent, your device may be infected.
Perth Computer Experts specializes in diagnosing and removing harmful software, ensuring that your system regains its health and performance. Here’s why we stand out:
Expert Detection: Our team uses advanced tools to identify and remove even the most complex viruses and malware.
Fast Service: We understand the urgency of resolving malware issues and work quickly to restore your computer’s functionality.
Comprehensive Protection: Beyond removal, we strengthen your system's defenses, helping prevent future infections.
Signs Your Computer May Be Infected
Common signs of virus or malware infection include:
Slow Performance: Malware often consumes resources, slowing down your device.
Unexpected Pop-Ups: Intrusive ads and unwanted pop-ups can indicate spyware or adware infections.
Crashing Programs: If your applications frequently crash, it might be due to a malware issue.
Suspicious Email Activity: Viruses can hijack your email account, sending spam or phishing messages to your contacts.
If you notice any of these signs, it’s time to contact Perth Computer Experts for their Virus Malware Removal Service Perth.
What to Expect from Our Service
When you choose Perth Computer Experts for malware and virus removal, we provide:
Thorough Scanning: We run deep scans to detect all malicious software on your system.
Secure Removal: Our specialists remove malware safely, ensuring no further harm is done.
System Restoration: We work to recover files and improve system health after malware has been removed.
Prevention Advice: Our team offers guidance on keeping your system secure, helping prevent future infections.
Serving Perth's Homes and Small Businesses
Whether you are a home user or a small business owner, Perth Computer Experts has solutions tailored to your needs. We provide reliable, fast, and professional Virus Malware Removal Service Perth, ensuring minimal downtime and optimal results.
0 notes
Text
Locking the Digital Doors: Understanding Web and Mobile App Security

In our digital world, apps on our phones and websites we visit are like doors to a house. But just like we lock our doors to keep bad guys out, we need to protect these apps from cyber bad guys. One way we do this is through something called a Web Application Firewall, which acts like a security guard for our apps. It stops the bad guys from sneaking in and causing trouble.
Another important thing to know is that these apps talk to each other using something called APIs. APIs help them share information. But if not handled carefully, they can accidentally spill sensitive information. OWASP help us understand the risks associated with these APIs, so we can make sure our apps are safe and sound. Together, let’s learn more about keeping our apps safe and our digital world secure!
Web and Mobile application Security
Securing web and mobile applications is crucial to protect sensitive data and ensure user safety. Here are the top 10 things to do:
Authentication and Authorization: Implement strong user authentication and authorization mechanisms to ensure that only authorized users can access certain features or data.
Data Encryption: Use encryption techniques (SSL/TLS) to protect data transmission between the client and server. Also, encrypt sensitive data at rest.
Input Validation: Validate and sanitize all user inputs to prevent common vulnerabilities like SQL injection and cross-site scripting (XSS).
Session Management: Implement secure session management practices to prevent session hijacking and fixation attacks.
API Security: Secure your APIs with authentication tokens, rate limiting, and proper access controls. Use API keys or OAuth for authorization.
Code Review and Testing: Regularly review and test your code for vulnerabilities. Use static analysis and dynamic testing tools to identify and fix security issues.
Patch Management: Keep all software components, libraries, and frameworks up to date with the latest security patches.
Error Handling: Implement proper error handling to avoid revealing sensitive information in error messages.
Security Headers: Use security headers like Content Security Policy (CSP), HTTP Strict Transport Security (HSTS), and Cross-Origin Resource Sharing (CORS) to control browser behavior.
Security Training and Awareness: Train your development and QA teams in secure coding practices and keep them updated on the latest security threats and best practices.
Regular security audits and penetration testing should also be part of your security strategy to proactively identify and mitigate vulnerabilities in your web and mobile applications.

2. Top 10 OWASP API Security Risk
The Open Web Application Security Project (OWASP) provides a list of the top 10 most critical web application security and API Risk official website (https://owasp.org)
API1:2023 – Broken Object Level Authorization–
APIs tend to expose endpoints that handle object identifiers, creating a wide attack surface of Object Level Access Control issues. Object level authorization checks should be considered in every function that accesses a data source using an ID from the user.
API2:2023 – Broken Authentication–
Authentication mechanisms are often implemented incorrectly, allowing attackers to compromise authentication tokens or to exploit implementation flaws to assume other user’s identities temporarily or permanently. Compromising a system’s ability to identify the client/user, compromises API security overall
API3:2023 – Broken Object Property Level Authorization–
This category combines API3:2019 Excessive Data Exposure and API6:2019 – Mass Assignment, focusing on the root cause: the lack of or improper authorization validation at the object property level. This leads to information exposure or manipulation by unauthorized parties.
API4:2023 – Unrestricted Resource Consumption–
Satisfying API requests requires resources such as network bandwidth, CPU, memory, and storage. Other resources such as emails/SMS/phone calls or biometrics validation are made available by service providers via API integrations, and paid for per request. Successful attacks can lead to Denial of Service or an increase of operational costs.
API5:2023 – Broken Function Level Authorization–
Complex access control policies with different hierarchies, groups, and roles, and an unclear separation between administrative and regular functions, tend to lead to authorization flaws. By exploiting these issues, attackers can gain access to other users’ resources and/or administrative functions
API6:2023 – Unrestricted Access to Sensitive Business Flows–
APIs vulnerable to this risk expose a business flow – such as buying a ticket, or posting a comment – without compensating for how the functionality could harm the business if used excessively in an automated manner. This doesn’t necessarily come from implementation bugs.
API7:2023 – Server Side Request Forgery–
Server-Side Request Forgery (SSRF) flaws can occur when an API is fetching a remote resource without validating the user-supplied URI. This enables an attacker to coerce the application to send a crafted request to an unexpected destination, even when protected by a firewall or a VPN.
API8:2023 – Security Misconfiguration–
APIs and the systems supporting them typically contain complex configurations, meant to make the APIs more customizable. Software and DevOps engineers can miss these configurations, or don’t follow security best practices when it comes to configuration, opening the door for different types of attacks.
API9:2023 – Improper Inventory Management–
APIs tend to expose more endpoints than traditional web applications, making proper and updated documentation highly important. A proper inventory of hosts and deployed API versions also are important to mitigate issues such as deprecated API versions and exposed debug endpoints.
API10:2023 – Unsafe Consumption of APIs–
Developers tend to trust data received from third-party APIs more than user input, and so tend to adopt weaker security standards. In order to compromise APIs, attackers go after integrated third-party services instead of trying to compromise the target API directly.
3. Importance of WAF web application firewall
A Web Application Firewall (WAF) is a crucial component in modern cybersecurity, primarily focused on protecting web applications from a variety of online threats and attacks. Here are several key reasons highlighting the importance of WAF:
Protection from Web Application Attacks: WAFs are designed to defend against common web application attacks, including SQL injection, cross-site scripting (XSS), cross-site request forgery (CSRF), and more. These attacks can compromise data integrity, steal sensitive information, or disrupt application functionality.
Zero-Day Attack Mitigation: WAFs can detect and mitigate new and emerging threats, even before patches or security updates are available. They do this by analyzing incoming traffic patterns and behavior anomalies.
Reduced Attack Surface: By filtering and monitoring incoming web traffic, WAFs help reduce the attack surface of web applications. They can block malicious requests before they reach the application server, minimizing the risk of exploitation.
DDoS Attack Mitigation: Some advanced WAFs have Distributed Denial of Service (DDoS) protection capabilities. They can identify and mitigate large-scale traffic floods, helping maintain service availability during attacks.
Compliance Requirements: Many regulatory standards and compliance frameworks, such as PCI DSS and HIPAA, mandate the use of security measures like WAFs to protect sensitive data. Implementing a WAF can help organizations meet these requirements.
Logging and Auditing: WAFs provide detailed logs of incoming traffic and blocked threats. These logs can be invaluable for security audits, incident response, and forensic analysis.
Real-Time Threat Monitoring: WAFs offer real-time monitoring of web traffic, enabling security teams to identify and respond to threats quickly. They can trigger alerts or automated responses to specific attack patterns.
Traffic Normalization: WAFs can normalize incoming traffic, filtering out malicious or malformed requests. This helps ensure that only legitimate, well-formed requests reach the application, improving its overall stability.
Protection for Legacy Applications: WAFs can protect older or legacy web applications that may not have been built with modern security practices in mind. They act as an additional layer of security for such applications.
Cost-Efficient Security: Implementing a WAF can be more cost-effective than addressing vulnerabilities and responding to security incidents after an attack has occurred. It provides proactive, continuous protection.
In summary, a Web Application Firewall is a critical security component for safeguarding web applications from a wide range of threats. It helps organizations maintain the confidentiality, integrity, and availability of their web services and sensitive data.
Simple antivirus software is designed primarily to detect and remove known malware and viruses based on predefined signatures and patterns. While antivirus programs are important for basic protection, they have limitations that make them insufficient in today’s complex cybersecurity landscape.
Here’s why EDR (Endpoint Detection and Response) is necessary:
1.Limited Detection Capabilities: Antivirus relies on known signatures and patterns to identify threats. It may miss zero-day attacks and sophisticated malware that haven’t been previously identified.
2.Lack of Behavioral Analysis: EDR solutions monitor the behavior of files and processes on an endpoint. They can detect suspicious activities, such as unusual system behavior or data exfiltration, even if there are no known malware signatures involved.
3.Advanced Threats: EDR solutions are better equipped to detect advanced threats like fileless malware and polymorphic malware that can change their code to evade traditional antivirus scans.
4.Incident Response: EDR provides real-time monitoring and alerting, helping organizations respond quickly to security incidents. Antivirus software typically lacks these features.
5.Visibility and Investigation: EDR solutions provide detailed information about endpoint activity, allowing security teams to investigate incidents thoroughly, trace the source of an attack, and understand its scope.
6.Threat Hunting: EDR enables proactive threat hunting. Security analysts can search for signs of compromise and anomalies to detect threats that may have gone unnoticed by traditional antivirus.
7.Compliance and Reporting: EDR solutions often provide extensive reporting capabilities, which are crucial for compliance with data protection regulations and for demonstrating a proactive approach to security.
8.Adaptive Protection: EDR can adapt its response to evolving threats, applying behavioral analysis and machine learning to identify new attack patterns.
In summary, while antivirus software is a fundamental layer of protection, EDR complements it by offering advanced threat detection, real-time monitoring, incident response capabilities, and the ability to investigate and mitigate complex security incidents. In today’s rapidly evolving threat landscape, EDR is a critical component of a comprehensive cybersecurity strategy.
This blog emphasizes the critical importance of securing web and mobile applications in our digital era. It highlights the escalating threat landscape targeting crucial elements of our digital infrastructure. APIs (Application Programming Interfaces) are crucial for application functionality but can pose significant security risks if not adequately protected. The OWASP API Security Top 10 is a vital resource that sheds light on prevalent vulnerabilities in the API landscape. The blog delves into these risks, providing a comprehensive analysis of their implications and suggesting potential solutions. Additionally, the blog underlines the fundamental role of a Web Application Firewall (WAF) in enhancing digital security by monitoring and filtering traffic, acting as a defense against cyber threats. It invites readers to join this journey to enhance their understanding of web and mobile application security, fostering a safer digital future.
0 notes
Text
oh lovely now my laptop has a virus
#why#cant go to the mall to fix it either!!!!#i knew something has been wonky lately...#it's the search browser and i looked it up and it's a hijack browser and idk how to get rid of it...
3 notes
·
View notes
Text
The Switch was designed to be as resilient to hacking as possible, after people mocked them for years about the DS, Wii, 3DS, and Wii U. Its operating system was built from the ground up, in-house, using as little outside code as possible.
Literally only the WiFi driver, Nvidia graphics driver, and the exFAT filesystem driver were developed outside Nintendo. Coincidentally, the exFAT filesystem driver is unreliable as shit and causes all sorts of data corruption everywhere, Nvidia's graphics driver was so insecure they had to turn on a secret hardware feature to keep it from breaking everything, and networking on the Switch is subpar.
The Switch's OS, in modern times, has effectively zero security vulnerabilities. It also has the bare-minimum features people expect an operating system to have.
It has no themes, because of menuhax on the 3DS (malicious custom theme hijacked the home menu, one of the only processes with permission to launch software, and used it to launch custom homebrew software.) It has no eShop music because the eShop is running in a web browser from 2016 with every security patch since 2016 applied, but almost every "modern web" feature disabled.
There's a concept in security called "attack surface"—that is, how much stuff is exposed to people outside your organization. Nintendo built the Switch's OS to minimize attack surface first and be functional second. They ended up with the most secure mobile operating system on the planet, at the cost of features.
And then got hacked anyway due to multiple flaws in Nvidia's hardware: namely, a buffer overflow in the Tegra X1's recovery mode that got fixed in 2018; and in later consoles, an unguarded boot-time signature check allows an attacker listening on the storage data lines to shut off the CPU for a fraction of a clock cycle when it tries to set the "signature check failed" flag. Since the flag is not set, the next boot stage continues with unsigned code.
Neither vulnerability is in the OS they painstakingly crafted to be secure. However, there's evidence that they're updating the Switch's OS for new hardware (added support for dynamically detecting how much RAM is in the system, up to 64 CPU cores, etc.)
i keep needing to remind myself that the switch is in fact six years old and not at the beginning of its lifecycle. it still feels kind of vaguely unfinished to me for some weird reason why does it have a themes section with no themes why is everything more homogenized why is there no streetpass. like it’s got a fantastic library of games but it just feels kind of. empty and uninspired compared to its predecessors, y’know?
270 notes
·
View notes
Text
Defense on being different - Firefox
I decided that I'd start my own post rather than hijacking the other, since I don't think that person actually WANTS to be talked into firefox*.
But I wanted to recommend that people get firefox as a backup browser even if they don't plan to use it (though I do encourage it's use!)
This is because of my experience as the escalation for "hey we've got another weird one" IT problems; and how Firefox just works differently from other browsers.
Once upon a time, a client saw me installing firefox as part of their standard organisation set up they queried "why would you bother".
But they also understood completely I explained the following:
- Because Firefox works a different way than other browsers, it will sometimes work with connecting people to the internet when a bunch of other apps are broken. So sometimes we can use firefox to get a client online while IT works to solve the issue.
Case where this has occurred for me personally!
There's a problem with windows "internet options". Teams, Zoom, Outlook, Internet Explorer, Edge, Chrome and all Chrome clones all tap into the windows settings for internet options. But firefox does not. This means if there is a problem in the internet options, firefox will continue to work but all of those other programs will be broken.
** This happened to me a lot about a decade ago when I was dealing with the aftermath of some rogue proxies being installed in the internet options on all these different individual business computers that used the same ISP, though I've run into it in different ways. If we discount the weird ISP (which was hundreds) then certainly at least a dozen times in the past decade. So not a daily problem by any means, but if you're in IT long enough you might run into it, if you don't just try reinstalling the OS and all network settings.
Firefox also uses a different way of accessing certificates, which meant that some computers with certificate issues couldn't access the web or could only access pages insecurely (see apps listed in point 1 for what was affected) but they could work normally in Firefox at least. I can name three of my clients where this has happened in the past decade specifically for certificates, one of which was just this year in May (2022).
Given that I support my clients primarily remotely it was a real lifesaver as I could get them to grant me access through Firefox and then I could fix it for them on the phone without having to figure out how to get to them if they were not nearby.
And for people who are saying that's all windows - the equivalent has happened on macs too, where something weird occurred in Safari and Firefox was the simple and easy fix to get the client working before the real fix could be implemented.
Especially since there's no way to fix some of the Safari issues without reinstalling the OS on the macs since it's a default inbuilt app. Also some of the other mac things run on top of Safari's webkit so if that's broken other things will be too.
I mention reinstalling the OS, that's what a lot of my cohort who work in more standardized IT environment would do, but due to my unusual client base and the fact that I often do adhoc support, I often don't have it as an easy option. Plus, reformatting takes time, so even if it's an option sometimes I want to keep the client limping a long until 5:00 pm.
So when people are saying that Firefox is important to the ecosystem with how it's maintaining independence from Chrome and Safari - this applies in a bunch of ways!
Basically, please install firefox even if you don't think you'll use it, as it might just save the day with getting you online when everything else is broken.
I do also want to stress, it's pretty easy to move to firefox if you're only concerned about data. Things like, cookies, browsing history, saved passwords and bookmarks - even if you have a lot of folders etc are SUPER easy to bring across. Appearance is harder, firefox has locked down some of the options that used to make it the most customizable in changing how it looked and felt, but there are a lot of good addons and themes out there to help make it more effective for you.
It also might be less of a shock the switch if you use it for a different purpose. For example if you're using it as your ebook reader to avoid the tabs getting mixed up with normal browsing etc, and then as you build up experience with it, it becomes more comfortable making it the primary browser.
11 notes
·
View notes
Text

Spybot Search Destroy Free Download Now
A well-known program for removing malware, spyware, and adware is called Spybot Search Destroy. Like the majority of malware scanners, Spybot S&D checks the RAM and hard drive of the machine for spyware.
In addition to repairing issues with tracking cookies, system internals (Registry), Winsock LSPs, ActiveX objects, browser hijackers, and BHOs, Spybot Search Destroy can help certain users preserve their privacy by erasing usage logs. Additionally, Spybot has a tool called “Immunize” that prevents spyware from ever being installed. A file shredder is another tool included in Spybot for the safe disposal of files.
Spybot Search Destroy has two starting settings: Easy mode for novice users who only need the essential functionality and Advanced mode for experts and power users. Both are included in the free version
Features of Spybot Search & Destroy:
Removal of trojans, dialers, keyloggers, adware, spyware, and other pesky software, as well as used records…
A user-expandable database integrated capability for weekly revisions and email notification of updates.
Shred threats to prevent their removal.
Backed up each issue that was fixed.
Constantly preventing dangerous ActiveX downloads, known tracking cookies, and dangerous downloads in IE.
Command line options for job automation
Options for automating scan, erasure, and update
Skins to customize the user interface.
1 note
·
View note
Text
Speechbubble making guide
I don't know who wants or needs this, but here it is anyway
Long post, it's under the cut
Making speechbubbles (this is how I make them)
1. Open Pixlr
Pixlr is a free in-browser photo editor. You want the Pixlr E Advanced photo editor, not the Pixlr X. Open "create new"

2. Screenshot the picture you want to make into a speechbubble and paste it into Pixlr (Sidenote: I screenshot the pictures either from the site I watch spn or the spn mega drive)

3. Take a screenshot of a white rectangle (literally just get a site or picture with pure white in it and take any sized screenshot) and paste it in Pixlr

4. Drag the white rectangle to the upper left corner and set the aspect (the bright blue button at the top) to free ( Note: Make sure that when you're changing the size of the photo you keep the aspect fixed not free so it doesn't distort the picture. Only use free for the bubble part) Stretch the rectangle until it goes completely across the top of the photo.

5. Select Shapes from the sidebar

6. Select Draw from the topbar
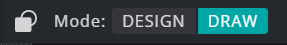
7. Use one of these (which one depends on whether you want a sharp bubble or a rounder bubble)
8. Make sure the white rectangle is selected in layers. Add the lines of your bubble to the white rectangle.

9. Select fill from the sidebar and click on the area between the bubble lines (again, make sure the white rectangle is selected in layers)

10. Your speechbubble is completed. Either screenshot it or export it to your computer and you're all set to hijack a post.

Tips:
After you fill the bubble it has little dark specks around the edge. If these bother you just paint over them with the brush function.
If a photo has a light background and you can't see the white speechbubble, go under Filters and click outline to add a dark outline to make the bubble stand out in the photo.
If a rounded speechbubble (like the one shown here) doesn't fit on the photo try a straight one. They fit better sometimes.
You can edit the photo(lighting, coloring, sharpness) in Pixlr before you add the bubble too
25 notes
·
View notes
Text
Why having SSL Certificate installed on your Website is no longer a matter of choice, but rather a priority?
If you have a website or web application with no SSL configured, you're in big trouble. Modern web browsers like Google Chrome or Microsoft edge conveniently flag off any website that's deemed insecure to visit.
One of the parameters that web browsers use to intelligently define an 'insecure website' is lack of SSL certificate.

The primary importance of SSL is to encrypt sensitive HTTP data in transit.
For instance, e-commerce websites like Amazon, Alibaba, or eBay have millions of users who carryout online transactions on these platforms. For customers to successfully buy products on these platforms, they have to create accounts or sign-up and then, fill in their credit card info to allow successful purchases. This information is very sensitive and any slight leakage could give wrong actors the ability to steal people's Money using the leaked info.
Since the internet is a huge uncontrollable space, it is full of all categories of people; good and bad. So, Whenever you make a purchase online, let's say you've purchased something from eBay or Amazon, your information will travel through the internet until it reaches final destination for authentication and authorization.
If we didn't have SSL, such critical and sensitive information especially credit card info could have been in plain text during POST & GET http transit. This would have given wrong actors the ability to eavesdrop by positioning themselves in the middle between you and the remotely-located eBay or Amazon Web servers, responsible for authenticating online transactions.
So, SSL is used to turn the plain-text version of sensitive data into unreadable encrypted format, during HTTP handshake. When wrong actors try to position themselves in the middle of any https connection, they wouldn't succeed hijacking any useful information.
Originally, E-commerce websites or Websites that used to carry sensitive information predominantly needed this security feature. However, things have changed these days as almost every website needs SSL.
Whether you run a small blog or you have a simple website, SSL certificate is a must to have. In other words, you don't need to have a website that stores sensitive data to get SSL.
The internet browsing rules are drastically changing, and websites with SSL certificates are prioritized by search engines like Google. If you don't embrace the trend, you're definitely going to be left out in terms of favourable search engine ranking & good site traffic induction for your website.
You don't want your site to be flagged or labelled insecure as this could hurt your credibility before potential customers. Nobody is gonna trust your services or products you market on your site if it's being flagged as a security risk to potential visitors.
Let's help you configure or fix SSL issues on your site. Stay on top of your game finding us on Fiverr. Get free SSL today avoid losing traffic on your site.
Find us on Fiverr;
1 note
·
View note
Text
Web Application Penetration Testing Checklist
Web-application penetration testing, or web pen testing, is a way for a business to test its own software by mimicking cyber attacks, find and fix vulnerabilities before the software is made public. As such, it involves more than simply shaking the doors and rattling the digital windows of your company's online applications. It uses a methodological approach employing known, commonly used threat attacks and tools to test web apps for potential vulnerabilities. In the process, it can also uncover programming mistakes and faults, assess the overall vulnerability of the application, which include buffer overflow, input validation, code Execution, Bypass Authentication, SQL-Injection, CSRF, XSS etc.
Penetration Types and Testing Stages
Penetration testing can be performed at various points during application development and by various parties including developers, hosts and clients. There are two essential types of web pen testing:
l Internal: Tests are done on the enterprise's network while the app is still relatively secure and can reveal LAN vulnerabilities and susceptibility to an attack by an employee.
l External: Testing is done outside via the Internet, more closely approximating how customers — and hackers — would encounter the app once it is live.
The earlier in the software development stage that web pen testing begins, the more efficient and cost effective it will be. Fixing problems as an application is being built, rather than after it's completed and online, will save time, money and potential damage to a company's reputation.
The web pen testing process typically includes five stages:
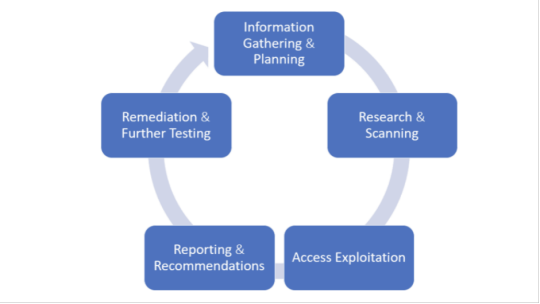
1. Information Gathering and Planning: This comprises forming goals for testing, such as what systems will be under scrutiny, and gathering further information on the systems that will be hosting the web app.
2. Research and Scanning: Before mimicking an actual attack, a lot can be learned by scanning the application's static code. This can reveal many vulnerabilities. In addition to that, a dynamic scan of the application in actual use online will reveal additional weaknesses, if it has any.
3. Access and Exploitation: Using a standard array of hacking attacks ranging from SQL injection to password cracking, this part of the test will try to exploit any vulnerabilities and use them to determine if information can be stolen from or unauthorized access can be gained to other systems.
4. Reporting and Recommendations: At this stage a thorough analysis is done to reveal the type and severity of the vulnerabilities, the kind of data that might have been exposed and whether there is a compromise in authentication and authorization.
5. Remediation and Further Testing: Before the application is launched, patches and fixes will need to be made to eliminate the detected vulnerabilities. And additional pen tests should be performed to confirm that all loopholes are closed.
Information Gathering

1. Retrieve and Analyze the robot.txt files by using a tool called GNU Wget.
2. Examine the version of the software. DB Details, the error technical component, bugs by the error codes by requesting invalid pages.
3. Implement techniques such as DNS inverse queries, DNS zone Transfers, web-based DNS Searches.
4. Perform Directory style Searching and vulnerability scanning, Probe for URLs, using tools such as NMAP and Nessus.
5. Identify the Entry point of the application using Burp Proxy, OWSAP ZAP, TemperIE, WebscarabTemper Data.
6. By using traditional Fingerprint Tool such as Nmap, Amap, perform TCP/ICMP and service Fingerprinting.
7.By Requesting Common File Extension such as.ASP,EXE, .HTML, .PHP ,Test for recognized file types/Extensions/Directories.
8. Examine the Sources code From the Accessing Pages of the Application front end.
9. Many times social media platform also helps in gathering information. Github links, DomainName search can also give more information on the target. OSINT tool is such a tool which provides lot of information on target.
Authentication Testing

1. Check if it is possible to “reuse” the session after Logout. Verify if the user session idle time.
2. Verify if any sensitive information Remain Stored in browser cache/storage.
3. Check and try to Reset the password, by social engineering crack secretive questions and guessing.
4.Verify if the “Remember my password” Mechanism is implemented by checking the HTML code of the log-in page.
5. Check if the hardware devices directly communicate and independently with authentication infrastructure using an additional communication channel.
6. Test CAPTCHA for authentication vulnerabilities.
7. Verify if any weak security questions/Answer are presented.
8. A successful SQL injection could lead to the loss of customer trust and attackers can steal PID such as phone numbers, addresses, and credit card details. Placing a web application firewall can filter out the malicious SQL queries in the traffic.
Authorization Testing

1. Test the Role and Privilege Manipulation to Access the Resources.
2.Test For Path Traversal by Performing input Vector Enumeration and analyze the input validation functions presented in the web application.
3.Test for cookie and parameter Tempering using web spider tools.
4. Test for HTTP Request Tempering and check whether to gain illegal access to reserved resources.
Configuration Management Testing
1. Check file directory , File Enumeration review server and application Documentation. check the application admin interfaces.
2. Analyze the Web server banner and Performing network scanning.
3. Verify the presence of old Documentation and Backup and referenced files such as source codes, passwords, installation paths.
4.Verify the ports associated with the SSL/TLS services using NMAP and NESSUS.
5.Review OPTIONS HTTP method using Netcat and Telnet.
6. Test for HTTP methods and XST for credentials of legitimate users.
7. Perform application configuration management test to review the information of the source code, log files and default Error Codes.
Session Management Testing
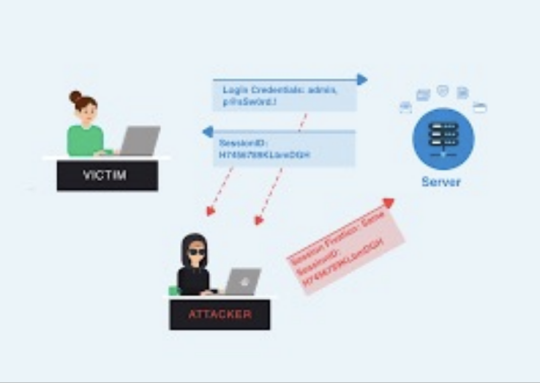
1. Check the URL’s in the Restricted area to Test for CSRF (Cross Site Request Forgery).
2.Test for Exposed Session variables by inspecting Encryption and reuse of session token, Proxies and caching.
3. Collect a sufficient number of cookie samples and analyze the cookie sample algorithm and forge a valid Cookie in order to perform an Attack.
4. Test the cookie attribute using intercept proxies such as Burp Proxy, OWASP ZAP, or traffic intercept proxies such as Temper Data.
5. Test the session Fixation, to avoid seal user session.(session Hijacking )
Data Validation Testing
1. Performing Sources code Analyze for javascript Coding Errors.
2. Perform Union Query SQL injection testing, standard SQL injection Testing, blind SQL query Testing, using tools such as sqlninja, sqldumper, sql power injector .etc.
3. Analyze the HTML Code, Test for stored XSS, leverage stored XSS, using tools such as XSS proxy, Backframe, Burp Proxy, OWASP, ZAP, XSS Assistant.
4. Perform LDAP injection testing for sensitive information about users and hosts.
5. Perform IMAP/SMTP injection Testing for Access the Backend Mail server.
6.Perform XPATH Injection Testing for Accessing the confidential information
7. Perform XML injection testing to know information about XML Structure.
8. Perform Code injection testing to identify input validation Error.
9. Perform Buffer Overflow testing for Stack and heap memory information and application control flow.
10. Test for HTTP Splitting and smuggling for cookies and HTTP redirect information.
Denial of Service Testing

1. Send Large number of Requests that perform database operations and observe any Slowdown and Error Messages. A continuous ping command also will serve the purpose. A script to open browsers in loop for indefinite no will also help in mimicking DDOS attack scenario.
2.Perform manual source code analysis and submit a range of input varying lengths to the applications
3.Test for SQL wildcard attacks for application information testing. Enterprise Networks should choose the best DDoS Attack prevention services to ensure the DDoS attack protection and prevent their network
4. Test for User specifies object allocation whether a maximum number of object that application can handle.
5. Enter Extreme Large number of the input field used by the application as a Loop counter. Protect website from future attacks Also Check your Companies DDOS Attack Downtime Cost.
6. Use a script to automatically submit an extremely long value for the server can be logged the request.
Conclusion:
Web applications present a unique and potentially vulnerable target for cyber criminals. The goal of most web apps is to make services, products accessible for customers and employees. But it's definitely critical that web applications must not make it easier for criminals to break into systems. So, making proper plan on information gathered, execute it on multiple iterations will reduce the vulnerabilities and risk to a greater extent.
1 note
·
View note
Text
Ponyhoof and the new Facebook.com design

Here is the latest state of Ponyhoof and the new Facebook.com design that is rolling out soon. I apologize for being quiet and not posting any updates about this which led to several people reaching out for details, so here is a rundown.
Wait, what is happening?
In case you are unaware or ‘lucky’ not seeing any new design, Facebook is rolling out an all-new design for desktop.
Not only the design is changed, but all the internal coding have changed as well which means any software/extension that integrates with Facebook.com is going to be broken in some way.
What is the current state of Ponyhoof on this new design?
Ponyhoof technically still works, and there have been several tweaks such as supporting dark mode and avoiding totally unusable experiences such as black text on a dark background, but yes, the ponies appear to be missing and that’s no good. 😡
(Brief note: Using dark mode + pastel colored pony backgrounds don’t match 😛, if you use dark mode, then I chose to let the dark background ‘win’ over the pony’s color)
Although the button to open Ponyhoof Options is missing on the logout menu, it’s still possible to access it by clicking the Ponyhoof icon at the top-right of your browser, though some of the options such as notification sounds are broken on the new design as well.

Will Ponyhoof be updated to work on this new design?
Ideally yes, I would love to, I haven’t quit the fandom 😉 and still catch up watching the cursed Pony Life weekly (pls send help). So what’s holding up the fix?
First of all, from the very beginning, apart from one server administrator, practically all of Ponyhoof’s development/coding is done by one stallion, so the project’s bus factor is a risky 1.
Handing off the software to another person is risky as it would be hard to find someone that actually wants to deal with Facebook’s intricacies. Also there’s the possibility of the extension being hijacked by an ad company.
This was announced last year but I guess it’s not well known, I’m working for Facebook (yes, the company) starting last year and it’s easy to see why there’s a potential conflict of interest. There is no explicit instructions that I *must* stop development, nor is there any confirmation that it’s fine to proceed, so Ponyhoof is in this weird limbo state.
Finally, let’s be frank, now that I’m working a full-time job doing software work, I don’t want to stare at *more* of that after work.
That’s the summary of what’s happening with Ponyhoof and my life, if you have any other questions, then feel free to comment at the original post.
(top banner: https://www.deviantart.com/molecularkogwheel/art/This-Is-Not-Fine-729351563)
8 notes
·
View notes
Link
0 notes