#fleet operations software
Explore tagged Tumblr posts
Text
Top Insurance CRM System for Agents
Elevate your insurance agency's efficiency with the top insurance CRM system for agents. Our platform offers comprehensive tools tailored to streamline client management, policy tracking, and claims processing. With intuitive features and a user-friendly interface, agents can effortlessly organize client information, track policy renewals, and provide exceptional customer service. Say goodbye to manual processes and hello to increased productivity and client satisfaction with our cutting-edge CRM system. Trusted by agents worldwide, our platform is designed to optimize workflows, enhance communication, and drive business growth. Experience the power of the top insurance CRM system and take your agency to new heights today.
#customer service#customer service software#crm system customer service#sales and service software#dispatch management#dispatch system software#dispatch fleet management system#fleet dispatch software#fleet operations software#fleet operations management#insurance crm system#insurance client management system#general crm#client management crm#crm client relationship management#financial management solutions#management solution#account tracking software#financial tracking software#self service payroll system#payroll analytics#payroll and hr management#asset inventory system#inventory asset tracking#IT asset inventory system
1 note
·
View note
Text
Enhancing Operational Efficiency with REACH | Vantage Solutions: The Future of Fleet Maintenance and Management Software
Introduction
In an era where logistics and transportation drive global commerce, efficiency in fleet operations has never been more critical. Whether it’s coordinating vehicle repairs, managing intermodal maintenance, or optimizing dispatches, the need for robust, intelligent, and scalable solutions is paramount. At the forefront of this transformation stands REACH | Vantage Solutions, a technology partner that empowers fleet-based organizations to streamline their operations with innovative digital tools.
With its suite of solutions, REACH | Vantage Solutions revolutionizes how businesses approach fleet maintenance software, offering a seamless integration of repair management, dispatch tracking, intermodal M&R platforms, and mobile coordination tools. This comprehensive approach addresses key challenges faced by trucking companies, intermodal operators, and fleet managers, paving the way for reduced downtime, cost savings, and superior operational control.
Fleet Maintenance Software for Trucking Companies: A Game Changer
Trucking companies operate under tight deadlines and cost pressures. The margin for error is razor-thin, and unplanned vehicle downtime can have cascading effects across supply chains. This is where REACH | Vantage Solutions’ fleet maintenance software for trucking companies steps in. Designed to provide full visibility into vehicle health and repair history, the software empowers trucking companies to take proactive control of maintenance schedules.
By centralizing data on wear-and-tear components, scheduled service intervals, and real-time alerts, the platform minimizes the risk of unexpected breakdowns. Additionally, automated notifications ensure timely inspections, service, and part replacements, significantly enhancing vehicle uptime and driver safety.
Comprehensive Intermodal M&R Platform Integration
The intermodal industry faces unique challenges when it comes to Maintenance and Repair (M&R). Containers, chassis, and equipment frequently move between terminals, railroads, and depots, creating a fragmented and often manual repair ecosystem. REACH | Vantage Solutions offers a robust intermodal M&R platform that unifies stakeholders under a single digital framework.
This platform allows operators to log damage reports, approve estimates, track repairs, and generate compliance records — all within a user-friendly interface. Integration with telematics and IoT devices further enriches data collection, enabling predictive maintenance strategies and minimizing container idling time. With every repair decision recorded digitally, accountability and auditability improve dramatically.
A Scalable Repair Management Solution for Fleet Operators
Managing repairs across dozens or hundreds of vehicles and assets is a logistical challenge that can no longer rely on spreadsheets or siloed systems. REACH | Vantage Solutions delivers a scalable repair management solution for fleet operators that addresses this complexity head-on.
Fleet operators benefit from a unified dashboard that provides real-time insight into the status of every repair ticket, work order, and service action across the fleet. Through intelligent automation, the system assigns tasks to vendors, monitors progress, and controls costs with granular approval workflows. This eliminates communication gaps, reduces administrative overhead, and enhances vendor accountability.
From light-duty vans to heavy-duty rigs, every asset type can be included, making this solution ideal for mixed fleets. Moreover, integration with accounting systems and inventory tools helps ensure precise cost tracking and parts management.
Mobile Fleet Repair Coordination Tool for On-the-Go Control
In a fast-moving industry, stationary solutions are no longer sufficient. Fleet supervisors, drivers, and mechanics often operate in the field, requiring tools that work wherever they are. REACH | Vantage Solutions provides a powerful mobile fleet repair coordination tool, offering users a full suite of features accessible from smartphones and tablets.
With the mobile tool, users can:
Submit damage reports with photos
Access repair history instantly
Receive push notifications on job updates
Approve estimates in real time
Locate nearby service vendors
This real-time coordination minimizes delays, reduces manual communication, and ensures faster resolution of repair needs. As a result, vehicles return to service faster, and fleet productivity rises.
Dispatch and Repair Tracking Software: Operational Transparency Redefined
For companies that juggle multiple dispatches daily, visibility is everything. The dispatch and repair tracking software by REACH | Vantage Solutions merges dispatch scheduling with maintenance workflows, creating a synchronized view of both operations. This prevents scheduling conflicts, ensures vehicle readiness before assignment, and helps dispatchers allocate resources more efficiently.
The system enables users to view dispatch status alongside pending or ongoing repair tasks. If a vehicle is under repair, the dispatcher is automatically notified, preventing accidental assignments. This real-time insight reduces idle labor, enhances planning accuracy, and improves customer satisfaction by reducing missed delivery windows.
A Versatile and User-Centric Fleet Management App
Today’s workforce expects intuitive, mobile-first experiences, and REACH | Vantage Solutions delivers with its fleet management app. Designed for ease of use, the app centralizes maintenance alerts, inspection records, vehicle locations, and repair workflows in one cohesive interface.
Whether it’s a driver completing a daily inspection checklist, a supervisor reviewing repair KPIs, or a technician updating a work order, every user type benefits from tailored functionality. The app's design ensures that all stakeholders are connected and informed, no matter where they are.
The ability to access this level of operational control from a mobile app helps companies remain agile, efficient, and competitive in today’s logistics-driven economy.
End-to-End Vehicle Maintenance Software
Preventative maintenance is the backbone of a reliable fleet. REACH | Vantage Solutions provides a comprehensive vehicle maintenance software platform that takes the guesswork out of vehicle care. It tracks service schedules, maintenance milestones, part replacements, and inspection compliance — all from a centralized cloud-based system.
Managers can generate customized service plans per vehicle type, assign recurring tasks to vendors or internal teams, and ensure compliance with DOT or industry-specific regulations. Historical data analytics allow managers to forecast maintenance costs, identify high-risk assets, and optimize fleet lifecycle decisions.
Tailored Fleet Management Solutions for Modern Operators
No two fleets are the same. Whether a business operates 10 vehicles or 1,000, flexibility is essential. REACH | Vantage Solutions offers fleet management solutions that can be tailored to each client’s operational model, asset mix, and regulatory environment.
Key features include:
Multi-location support
Custom workflows
Role-based user access
API integrations with GPS, ERP, or fuel card systems
Advanced reporting dashboards
This modular architecture allows companies to scale with ease and adapt quickly to industry changes or business growth.
Enterprise-Ready Fleet Management Software
For enterprise clients, the demand for performance, scalability, and security is paramount. REACH | Vantage Solutions offers enterprise-grade fleet management software that meets these needs. With cloud infrastructure, role-based access, secure data storage, and audit trails, it’s built for businesses that can’t afford downtime or inefficiency.
The platform offers seamless integration with ERP, CRM, and HR systems, allowing for cross-departmental data sharing. Fleet administrators gain access to robust analytics and real-time alerts, while finance teams benefit from transparent cost breakdowns and budget tracking.
With extensive configuration options, large organizations can tailor workflows, automate decision-making rules, and enforce maintenance policies across multiple departments or regions.
#Fleet maintenance software for trucking companies#Intermodal M&R platform#Repair management solution for fleet operators#Mobile fleet repair coordination tool
0 notes
Text
#Best trucking software for owner operators#Small trucking company software#Best trucking accounting software#Best accounting software for owner operators#Trucking management software#Trucking software for small fleets#Truck management software#Truck management system#Truck dispatching software#Dispatch Software for small trucking#Dump Truck Logistics Software#Best trucking software
0 notes
Text
Power Up Your EV Fleet with Smarter Management ⚡️
Going electric with your fleet? Make the switch seamless with our cutting-edge EV fleet management software! Here's what you get:
Real-time tracking & analytics: Monitor your EVs' location, battery health, charging status, and optimize routes for maximum efficiency.
Simplified charging management: Schedule charging, locate stations, and track energy consumption - all in one place.
Reduced downtime: Proactive maintenance alerts keep your EVs running smoothly, minimizing downtime and maximizing productivity. ⏱️
Cost savings: Optimize charging cycles, reduce fuel costs, and gain valuable insights for smarter fleet operations.
Ready to unlock the full potential of your EV fleet? https://iris.steam-a.com/
0 notes
Text
Driving Efficiency: Fleet Management Software Solutions in Dubai
In the heart of the bustling metropolis of Dubai, where every minute counts and precision is paramount, efficient fleet management is crucial for businesses to stay ahead of the curve. From logistics companies navigating the city's intricate road network to construction firms overseeing a fleet of heavy machinery, the ability to monitor, track, and optimize fleet operations can make all the difference. This is where fleet management software solutions in Dubai come into play, offering innovative tools to streamline processes, enhance productivity, and drive business growth. Let's explore some of the top fleet management software solutions making waves in Dubai's dynamic business landscape.
1. Trinetra
Trinetra is a leading provider of fleet management software solutions, offering a comprehensive suite of tools to help businesses optimize their fleet operations. With features such as real-time tracking, route optimization, and driver behavior monitoring, Trinetra empowers businesses to improve efficiency, reduce costs, and enhance customer satisfaction. Whether it's managing a fleet of delivery vehicles or a construction fleet, Trinetra's customizable solutions cater to a wide range of industries and business needs.
2. Chekhra Business Solutions
Chekhra Business Solutions specializes in fleet management software tailored to the unique requirements of businesses in Dubai and the wider UAE. Their user-friendly platform offers advanced features such as GPS tracking, fuel management, and maintenance scheduling, allowing businesses to gain real-time insights into their fleet operations. With a focus on innovation and customer satisfaction, Chekhra Business Solutions is committed to helping businesses maximize their productivity and profitability.
3. Carmine
Carmine is a cloud-based fleet management software solution designed to meet the needs of businesses of all sizes in Dubai. With features such as vehicle tracking, driver management, and compliance monitoring, Carmine helps businesses streamline their operations and ensure regulatory compliance. Its intuitive interface and customizable reporting tools make it easy for businesses to track their fleet performance and make data-driven decisions to optimize efficiency and reduce costs.
4. Fleet Complete
Fleet Complete is a global leader in fleet management software solutions, with a strong presence in Dubai and the UAE. Their comprehensive platform offers a wide range of features, including GPS tracking, route optimization, and asset management, enabling businesses to maximize the efficiency of their fleet operations. With real-time visibility into vehicle location, status, and performance, Fleet Complete empowers businesses to improve productivity, reduce fuel consumption, and enhance customer service.
5. GPSit
GPSit is a trusted provider of fleet management software solutions, offering cutting-edge technology to businesses across Dubai and the UAE. Their platform provides real-time tracking, route optimization, and driver behavior monitoring, helping businesses optimize their fleet operations and improve overall efficiency. With a focus on reliability, scalability, and customer support, GPSit is committed to helping businesses achieve their fleet management goals and drive success in a competitive marketplace.
Conclusion
In the fast-paced business environment of Dubai, where efficiency and productivity are paramount, the adoption of fleet management software solutions is essential for businesses to stay competitive and thrive. Whether it's optimizing routes, improving fuel efficiency, or ensuring regulatory compliance, these software solutions offer a comprehensive suite of tools to help businesses streamline their operations and drive growth. By harnessing the power of technology and innovation, businesses in Dubai can unlock new opportunities for success and maintain their position as leaders in their respective industries.
#In the heart of the bustling metropolis of Dubai#where every minute counts and precision is paramount#efficient fleet management is crucial for businesses to stay ahead of the curve. From logistics companies navigating the city’s intricate r#the ability to monitor#track#and optimize fleet operations can make all the difference. This is where fleet management software solutions in Dubai come into play#offering innovative tools to streamline processes#enhance productivity#and drive business growth. Let’s explore some of the top fleet management software solutions making waves in Dubai’s dynamic business lands#1. Trinetra#Trinetra is a leading provider of fleet management software solutions#offering a comprehensive suite of tools to help businesses optimize their fleet operations. With features such as real-time tracking#route optimization#and driver behavior monitoring#Trinetra empowers businesses to improve efficiency#reduce costs#and enhance customer satisfaction. Whether it’s managing a fleet of delivery vehicles or a construction fleet#Trinetra’s customizable solutions cater to a wide range of industries and business needs.#2. Chekhra Business Solutions#Chekhra Business Solutions specializes in fleet management software tailored to the unique requirements of businesses in Dubai and the wide#fuel management#and maintenance scheduling#allowing businesses to gain real-time insights into their fleet operations. With a focus on innovation and customer satisfaction#Chekhra Business Solutions is committed to helping businesses maximize their productivity and profitability.#3. Carmine#Carmine is a cloud-based fleet management software solution designed to meet the needs of businesses of all sizes in Dubai. With features s#driver management#and compliance monitoring#Carmine helps businesses streamline their operations and ensure regulatory compliance. Its intuitive interface and customizable reporting t#4. Fleet Complete
0 notes
Text
Control and Optimize your Fleet Operations with Fleet Management Software

UNIFIED FLEET MANAGEMENT
A single place to Induct, Manage, Track, and maintain all of your fleets.

COST-EFFECTIVE FLEET RETIREMENT
Fleet retirement recommendations based on comprehensive parameters, encompassing usage history, present condition, and more.

WORKSHOP MAINTENANCE
Integrated workshop module to manage all the workshop operations, inventory, parts, and billing.
OPTIMIZED RESOURCE ALLOCATION
Fleet allocation recommendations based on maintenance schedules and cargo compatibility for optimized trip-vehicle matching.

WORK ORDER CAPITALIZATION
Provision for partial and full capitalization of the work order.

FLEET MAINTENANCE
End to end tracking of all maintenance activities across the entire fleet through a single system.
Source Link
0 notes
Text
Ethera Operation!!
You're the government’s best hacker, but that doesn’t mean you were prepared to be thrown into a fighter jet.
Bradley "Rooster" Bradshaw x Awkward!Hacker! FemReader
Part I


This was never supposed to happen. Your role in this operation was simple—deliver the program, ensure it reached the right hands, and let the professionals handle the breaching.
And then, of course, reality decided to light that plan on fire.
The program—codenamed Ethera—was yours. You built it from scratch with encryption so advanced that even the most elite cyber operatives couldn’t crack it without your input. A next-generation adaptive, self-learning decryption software, an intrusion system designed to override and manipulate high-security military networks, Ethera was intended to be both a weapon and a shield, capable of infiltrating enemy systems while protecting your own from counterattacks in real-time. A ghost in the machine. A digital predator. A weapon in the form of pure code. If it fell into the wrong hands, it could disable fleets, and ground aircraft, and turn classified intelligence into an open book. Governments would kill for it. Nations could fall because of it.
Not that you ever meant to, of course. It started as a little experimental security measure program, something to protect high-level data from cyberattacks, not become the ultimate hacking tool. But innovation has a funny way of attracting the wrong kind of attention, and before you knew it, Ethera had become one, if not the most classified, high-risk program in modern times. Tier One asset or so the Secret Service called it.
It was too powerful, too dangerous—so secret that only a select few even knew of its existence, and even fewer could comprehend how it worked.
And therein lay the problem. You were the only person who could properly operate it.
Which was so unfair.
Because it wasn’t supposed to be your problem. You were just the creator, the brain behind the code, the one who spent way too many sleepless nights debugging this monstrosity. Your job was supposed to end at development. But no. Now, because of some bureaucratic nonsense and the fact that no one else could run it without accidentally bricking an entire system, you had been promoted—scratch that, forcibly conscripted—into field duty.
And your mission? To install it in an enemy satellite.
A literal, orbiting, high-security, military-grade satellite, may you add.
God. Why? Why was your country always at war with others? Why couldn’t world leaders just, you know, go to therapy like normal people? Why did everything have to escalate to international cyber warfare?
Which is how you ended up here.
At Top Gun. The last place in the world you wanted to be.
You weren’t built for this. You thrive in sipping coffee in a cosy little office and handling cyber threats from a safe, grounded location. You weren’t meant to be standing in the halls of an elite fighter pilot training program, surrounded by the best aviators in the world—people who thought breaking the sound barrier was a casual Wednesday.
It wasn’t the high-tech cyberwarfare department of the Pentagon, nor some dimly lit black ops facility where hackers in hoodies clacked away at keyboards. No. It was Top Gun. A place where pilots use G-forces like a personal amusement park ride.
You weren’t a soldier, you weren’t a spy, you got queasy in elevators, you got dizzy when you stood too fast, hell, you weren’t even good at keeping your phone screen from cracking.
... And now you were sweating.
You swallowed hard as Admiral Solomon "Warlock" Bates led you through the halls of the naval base, your heels clacking on the polished floors as you wiped your forehead. You're nervous, too damn nervous and this damned weather did not help.
"Relax, Miss," Warlock muttered in that calm, authoritative way of his. "They're just pilots."
Just pilots.
Right. And a nuclear warhead was just a firework.
And now, somehow, you were supposed to explain—loosely explain, because God help you, the full details were above even their clearance level—how Ethera, your elegant, lethal, unstoppable digital masterpiece, was about to be injected into an enemy satellite as part of a classified mission.
This was going to be a disaster.
You had barely made it through the doors of the briefing room when you felt it—every single eye in the room locking onto you.
It wasn’t just the number of them that got you, it was the intensity. These were Top Gun pilots, the best of the best, and they radiated the kind of confidence you could only dream of having. Meanwhile, you felt like a stray kitten wandering into a lion’s den.
Your hands tightened around the tablet clutched to your chest. It was your lifeline, holding every critical detail of Ethera, the program that had dragged you into this utterly ridiculous situation. If you could’ve melted into the walls, you absolutely would have. But there was no escaping this.
You just had to keep it together long enough to survive this briefing.
So, you inhaled deeply, squared your shoulders, and forced your heels forward, trying to project confidence—chin up, back straight, eyes locked onto Vice Admiral Beau "Cyclone" Simpson, who you’d been introduced to earlier that day.
And then, of course, you dropped the damn tablet.
Not a graceful drop. Not the kind of gentle slip where you could scoop it back up and act like nothing happened. No, this was a full-on, physics-defying fumble. The tablet flipped out of your arms, ricocheted off your knee, and skidded across the floor to the feet of one of the pilots.
Silence.
Pure, excruciating silence.
You didn’t even have the nerve to look up right away, too busy contemplating whether it was physically possible to disintegrate on command. But when you finally did glance up—because, you know, social convention demanded it—you were met with a sight that somehow made this entire disaster worse.
Because the person crouching down to pick up your poor, abused tablet was freaking hot.
Tall, broad-shouldered, with a head of golden curls that practically begged to be tousled by the wind, and, oh, yeah—a moustache that somehow worked way too well on him.
He turned the tablet over in his hands, inspecting it with an amused little smirk before handing it over to you. "You, uh… need this?"
Oh, great. His voice is hot too.
You grabbed it back, praying he couldn't see how your hands were shaking. “Nope. Just thought I’d test gravity real quick.”
A few chuckles rippled through the room, and his smirk deepened like he was enjoying this way too much. You, on the other hand, wanted to launch yourself into the sun.
With what little dignity you had left, you forced a quick, tight-lipped smile at him before turning on your heel and continuing forward, clutching your tablet like it was a life raft in the middle of the worst social shipwreck imaginable.
At the front of the room, Vice Admiral Beau Cyclone Simpson stood with the kind of posture that said he had zero time for nonsense, waiting for the room to settle. You barely had time to take a deep breath before his voice cut through the air.
“Alright, listen up.” His tone was crisp, commanding, and impossible to ignore. “This is Dr Y/N L/N. Everything she is about to tell you is highly classified. What you hear in this briefing does not leave this room. Understood?”
A chorus of nods. "Yes, sir."
You barely resisted the urge to physically cringe as every pilot in the room turned to stare at you—some with confusion, others with barely concealed amusement, and a few with the sharp assessing glances of people who had no clue what they were supposed to do with you.
You cleared your throat, squared your shoulders, and did your best to channel even an ounce of the confidence you usually had when you were coding at 3 AM in a secure, pilot-free lab—where the only judgment you faced was from coffee cups and the occasional system error.
As you reached the podium, you forced what you hoped was a composed smile. “Uh… hi, nice to meet you all.”
Solid. Real professional.
You glanced up just long enough to take in the mix of expressions in the room—some mildly interested, some unreadable, and one particular moustached pilot who still had the faintest trace of amusement on his face.
Nope. Not looking at him.
You exhaled slowly, centering yourself. Stay focused. Stay professional. You weren’t just here because of Ethera—you were Ethera. The only one who truly understood it. The only one who could execute this mission.
With another tap on your tablet, the slide shifted to a blacked-out, redacted briefing—only the necessary information was visible. A sleek 3D-rendered model of the enemy satellite appeared on the screen, rotating slowly. Most of its details were blurred or omitted entirely.
“This is Blackstar, a highly classified enemy satellite that has been operating in a low-Earth orbit over restricted airspace.” Your voice remained even, and steady, but the weight of what you were revealing sent a shiver down your spine. “Its existence has remained off the radar—literally and figuratively—until recently, when intelligence confirmed that it has been intercepting our encrypted communications, rerouting information, altering intelligence, and in some cases—fabricating entire communications.”
Someone exhaled sharply. Another shifted in their seat.
“So they’re feeding us bad intel?” one of them with big glasses and blonde hair asked, voice sceptical but sharp.
“That’s the theory,” you confirmed. “And given how quickly our ops have been compromised recently, it’s working.”
You tapped again, shifting to the next slide. The silent infiltration diagram appeared—an intricate web of glowing red lines showing Etherea’s integration process, slowly wrapping around the satellite’s systems like a virus embedding itself into a host.
“This is where Ethera comes in,” you said, shifting to a slide that displayed a cascading string of code, flickering across the screen. “Unlike traditional cyberweapons, Ethera doesn’t just break into a system. It integrates—restructuring security protocols as if it was always meant to be there. It’s undetectable, untraceable, and once inside, it grants us complete control of the Blackstar and won’t even register it as a breach.”
“So we’re not just hacking it," The only female pilot of the team said, arms crossed as she studied the data. “We’re hijacking it.”
“Exactly,” You nodded with a grin.
You switched to the next slide—a detailed radar map displaying the satellite’s location over international waters.
“This is the target area,” you continued after a deep breath. “It’s flying low-altitude reconnaissance patterns, which means it’s using ground relays for some of its communication. That gives us a small window to infiltrate and shut it down.”
The next slide appeared—a pair of unidentified fighter aircraft, patrolling the vicinity.
“And this is the problem,” you said grimly. “This satellite isn’t unguarded.”
A murmur rippled through the room as the pilots took in the fifth-generation stealth fighters displayed on the screen.
“We don’t know who they belong to,” you admitted. “What we do know is that they’re operating with highly classified tech—possibly experimental—and have been seen running defence patterns around the satellite’s flight path.”
Cyclone stepped forward then, arms crossed, his voice sharp and authoritative. “Which means your job is twofold. You will escort Dr L/N’s aircraft to the infiltration zone, ensuring Ethera is successfully deployed. If we are engaged, your priority remains protecting the package and ensuring a safe return.”
Oh, fantastic, you could not only feel your heartbeat in your toes, you were now officially the package.
You cleared your throat, tapping the screen again. Ethera’s interface expanded, displaying a cascade of sleek code.
“Once I’m in range,” you continued, “Ethera will lock onto the satellite’s frequency and begin infiltration. From that point, it’ll take approximately fifty-eight seconds to bypass security and assume control."
Silence settled over the room like a thick cloud, the weight of their stares pressing down on you. You could feel them analyzing, calculating, probably questioning who in their right mind thought putting you—a hacker, a tech specialist, someone whose idea of adrenaline was passing cars on the highway—into a fighter jet was a good idea.
Finally, one of the pilots—tall, broad-shouldered, blonde, and very clearly one of the cocky ones—tilted his head, arms crossed over his chest in a way that screamed too much confidence.
“So, let me get this straight.” His voice was smooth, and confident, with just the right amount of teasing. “You, Doctor—our very classified, very important tech specialist—have to be in the air, in a plane, during a mission that has a high probability of turning into a dogfight… just so you can press a button?”
Your stomach twisted at the mention of being airborne.
“Well…” You gulped, very much aware of how absolutely insane this sounded when put like that. “It’s… more than just that, but, yeah, essentially.”
A slow grin spread across his face, far too entertained by your predicament.
“Oh,” he drawled, “this is gonna be fun.”
Before you could fully process how much you already hated this, Cyclone—who had been watching the exchange with his signature unamused glare—stepped forward, cutting through the tension with his sharp, no-nonsense voice.
“This is a classified operation,” he stated, sharp and authoritative. “Not a joyride.”
The blonde’s smirk faded slightly as he straightened, and the rest of the pilots quickly fell in line.
Silence lingered for a moment longer before Vice Admiral Beau Cyclone Simpson let out a slow breath and straightened. His sharp gaze swept over the room before he nodded once.
“All right. That’s enough.” His tone was firm, the kind that left no room for argument. “We’ve got work to do. The mission will take place in a few weeks' time, once we’ve run full assessments, completed necessary preparations, and designated a lead for this operation.”
There was a slight shift in the room. Some of the pilots exchanged glances, the weight of the upcoming mission finally settling in. Others, mainly the cocky ones, looked as though they were already imagining themselves in the cockpit.
“Dismissed,” Cyclone finished.
The pilots stood, murmuring amongst themselves as they filed out of the room, the blonde one still wearing a smug grin as he passed you making you frown and turn away, your gaze then briefly met the eyes of the moustached pilot.
You hadn’t meant to look, but the moment your eyes connected, something flickered in his expression. Amusement? Curiosity? You weren’t sure, and frankly, you didn’t want to know.
So you did the only logical thing and immediately looked away and turned to gather your things. You needed to get out of here, to find some space to breathe before your brain short-circuited from stress—
“Doctor, Stay for a moment.”
You tightened your grip on your tablet and turned back to Cyclone, who was watching you with that unreadable, vaguely disapproving expression that all high-ranking officers seemed to have perfected. “Uh… yes, sir?”
Once the last pilot was out the door, Cyclone exhaled sharply and crossed his arms.
“You realize,” he said, “that you’re going to have to actually fly, correct?”
You swallowed. “I—well, technically, I’ll just be a passenger.”
His stare didn’t waver.
“Doctor,” he said, tone flat, “I’ve read your file. I know you requested to be driven here instead of taking a military transport plane. You also took a ferry across the bay instead of a helicopter. And I know that you chose to work remotely for three years to avoid getting on a plane.”
You felt heat rise to your cheeks. “That… could mean anything.”
“It means you do not like flying, am I correct?”
Your fingers tightened around the tablet as you tried to find a way—any way—out of this. “Sir, with all due respect, I don’t need to fly the plane. I just need to be in it long enough to deploy Ethera—”
Cyclone cut you off with a sharp look. “And what happens if something goes wrong, Doctor? If the aircraft takes damage? If you have to eject mid-flight? If you lose comms and have to rely on emergency protocols?”
You swallowed hard, your stomach twisting at the very thought of ejecting from a jet.
Cyclone sighed, rubbing his temple as if this entire conversation was giving him a migraine. “We cannot afford to have you panicking mid-mission. If this is going to work, you need to be prepared. That’s why, starting next week you will train with the pilots on aerial procedures and undergoing mandatory training in our flight simulation program.”
Your stomach dropped. “I—wait, what? That’s not necessary—”
“It’s absolutely necessary,” Cyclone cut in, his tone sharp. “If you can’t handle a simulated flight, you become a liability—not just to yourself, but to the pilots escorting you. And in case I need to remind you, Doctor, this mission is classified at the highest level. If you panic mid-air, it won’t just be your life at risk. It’ll be theirs. And it’ll be national security at stake.”
You inhaled sharply. No pressure. None at all.
Cyclone watched you for a moment before speaking again, his tone slightly softer but still firm. “You’re the only one who can do this, Doctor. That means you need to be ready.”
You exhaled slowly, pressing your lips together before nodding stiffly. “Understood, sir.”
Cyclone gave a small nod of approval. “Good. Dismissed.”
You turned and walked out, shoulders tense, fully aware that in three days' time, you were going to be strapped into a high-speed, fighter jet. And knowing your luck?
You were definitely going to puke.
Part 2???
#top gun movie#top gun#top gun maverick#top gun fanfiction#top gun one shot#top gun fluff#bradley bradshaw#bradley rooster bradshaw#rooster bradshaw#bradley bradshaw x reader#bradley bradshaw fanfiction#bradley bradshaw imagine#bradley bradshaw x y/n#bradley bradshaw x you#bradley bradshaw x female reader#bradley bradshaw fic#bradley bradshaw fluff#top gun rooster#rooster fanfic#rooster x reader#rooster top gun#top gun maverick fanfic#top gun maverick fluff#top gun maverick x reader#jake seresin#jake seresin x reader#phoenix x reader#bob x reader#top gun hangman#pete maverick mitchell
2K notes
·
View notes
Text
Cloudfleet is proud to unveil a game-changer for your business - our state-of-the-art Driver and Asset Management System! 🌟
Key Features:
✅ Real-time location tracking 📍
✅ Driver performance monitoring 🚦
✅ Vehicle health and maintenance tracking 🚗🔧
✅ Enhanced efficiency and productivity 📈
Reach out to us for more details
Email: [email protected]
Call: +1 262-421-6834

#fleet management#truckingindustry#fleet operations#vehicle fleet management#applicant tracking software#background checks#driver for hire#compliance management
0 notes
Text
Streamline Your Operations: Carrier Tracking
Streamline Your Operations: Carrier Tracking - At iTruck Dispatch, we empower you to optimize your operations through advanced carrier tracking capabilities. Monitor your carriers' movements in real-time, enabling precise scheduling, enhanced communication, and streamlined logistics management for a more efficient and competitive business.
#Operational Efficiency#Fleet Management#Supply Chain Visibility#Shipping Solutions#Dispatch Software
0 notes
Text
During the night of June 1, Ukraine launched an audacious, long-planned drone operation deep in Russian territory, targeting Moscow’s strategic bomber fleet at multiple bases. Ukraine said the mission—codenamed “Spiderweb”—hit 41 bombers, with at least 13 fully destroyed. Reports suggest that Tu-95 and Tu-22M bombers were hit.
Notably, Ukraine apparently chose not to target Russia’s most modern, nuclear-capable Tu-160 bombers, focusing instead on the Tu-95 and Tu-22M, which have been used extensively in conventional cruise missile attacks on Ukrainian cities.
Ukraine reportedly deployed 117 kamikaze-style, first-person-view drones to strike multiple Russian air bases scattered across several time zones, from Murmansk near the Arctic Circle to the Amur region almost 5,000 miles from the Ukrainian border. The drones were covertly transported into Russia over many months, hidden inside wooden cabins mounted on the backs of trucks with remotely operated detachable roofs. Ukrainian intelligence operatives managed to smuggle the drones close to the air bases, and, in some cases, used unwitting Russian truck drivers to do so. Then, at the precise moment, the cabin roofs were opened remotely, allowing the drones to launch toward their objectives using commercial and open-source technology, including 4G LTE networks and ArduPilot software. Each drone had its own dedicated operator, reportedly based at a covert command center near a Federal Security Service (FSB) office inside Russia. According to Politico, Ukrainian intelligence said that some drones relied on artificial intelligence to complete their missions along preset routes when they lost signal, automatically activating their explosives as they reached and identified their assigned targets.
For all its complexity, creativity, and audaciousness, the raid’s immediate impact on Russian operations in Ukraine is likely to be limited. Russia typically employs between seven and 11 bombers per cruise missile salvo, and the loss of a dozen or more aircraft out of a total operable fleet of around 100 long-range bombers will not immediately halt cruise missile attacks on Ukrainian cities. The impact would have been greater in 2024, when Russia relied more heavily on bomber formations to strike Ukraine than it does now. With increased production of drones and ballistic missiles, air-launched cruise missiles have become less critical and are now mainly used for select high-value, stationary targets. Additionally, Ukraine might have hesitated to launch such a raid in 2024, when it was more dependent on U.S. aid and following U.S. concerns over previous attacks on elements of Russia’s nuclear deterrent.
Russia will now have to spend precious resources to harden air bases and other critical facilities by establishing robust, layered counter-drone defenses—combining electronic warfare, anti-air weapons systems, and physical barriers such as concrete hangars. This redeployment is unlikely to substantially impact air cover on the front line, however, given Russia’s relative abundance of air defense systems.
However, the long-term implications of the Ukrainian raid should not be underestimated. The Tu-95 and Tu-22M bombers are no longer in serial production, and their loss reduces Russia’s capacity for long-range force projection. The reported but still unconfirmed damage to A-50 aircraft would further degrade Russian air surveillance and command-and-control capabilities, complicating Moscow’s ability to coordinate complex air operations in a future war against NATO.
Psychologically, the raid is a major blow to Russian prestige and credibility. It undermines the narrative of Russian military prowess and demonstrates Ukraine’s ability to strike at the heart of Russian military power. The operation also illustrates once again that Ukraine does not need to have an equivalent arsenal to Russia’s: Small, low-cost platforms can inflict serious damage on high-value targets.
Yet raids alone do not win wars. Ultimately, the trajectory of the war in Ukraine will be determined by how well Ukraine can continue to attrit Russian forces along the front line in the coming months, thereby changing the Kremlin leadership’s mind about whether it is worthwhile to pursue the war given the high costs and limited gains. That said, last weekend’s significant loss of hard-to-replace strategic assets far from the front may, in the best outcome, nudge the Kremlin a bit closer to seeing that the costs of the conflict are becoming too much for Russia and the regime.
While some observers have heralded this operation as the advent of a new type of warfare, its true significance lies elsewhere. What the Ukrainians have done is adapt a classic tactic of European warfare—the military raid—to the 21st century.
Once the principal form of military engagement across Europe, raiding warfare typically unfolds in several phases: covert infiltration, a surprise assault, and a swift withdrawal. Underdogs have often employed the tactic to maintain pressure on a stronger enemy. The dawn of the modern raid can be traced back to British Prime Minister Winston Churchill’s order to his minister of economic warfare, Hugh Dalton, to “set Europe ablaze” following the devastating defeat of British forces in France in 1940; to that end, Dalton established the Special Operations Executive for sabotage and resistance in German-occupied Europe. But history abounds with other examples of such audacious operations. In October 1757, during the Seven Years’ War, Austrian forces under Andras Hadik executed a daring raid on Berlin using a small, fast-moving contingent of mostly Hungarian hussars. Despite being outnumbered by the city’s garrison, Hadik’s troops surprised the defenders, briefly occupied Berlin, and extracted a substantial ransom before withdrawing.
Modern raids involving air power were regularly employed for the first time in World War II. In November 1940, the British Royal Navy launched a surprise attack on the Italian fleet in the harbor of Taranto, Italy, using only 21 obsolete Fairey Swordfish biplanes from the aircraft carrier HMS Illustrious. The raid disabled three Italian battleships and damaged several other vessels, demonstrating how a small force in the air could achieve outsized operational effects. Similarly, in March 1942, British commandos assaulted the heavily defended dry dock at Saint-Nazaire, France, using a destroyer packed with explosives to deny the Germans a crucial facility for their battleships. And then there was the German Luftwaffe’s Poltava raid on the U.S. Air Force in 1944, when German fighters targeted Allied bomber formations stationed in Ukraine and inflicted heavy casualties and aircraft losses.
At its most basic level, therefore, Ukraine’s Operation Spiderweb belongs to a long tradition of daring raids. It does not mark the dawn of a new age—it is simply the latest adaptation of an enduring tactical approach.
On the one hand, however, the raid illustrates that high-impact, long-distance raids are made easier by new technologies like drones. Any assumption that military assets and infrastructure deep in the rear are immune from attack was just shattered by Ukraine. Russia will now have to spend precious resources hardening air bases and other critical facilities, as well as disperse its assets to reduce their vulnerability. The need for robust, layered anti-drone defenses—combining electronic warfare, kinetic interceptors, and physical barriers—will also become an urgent priority. The distinction between the frontline and the rear has blurred.
The raid also illustrated that a non-nuclear power could raid the strategic assets of a nuclear power. The only feasible way for Kyiv to do so safely was to consciously avoid targeting certain assets. The raid’s limitations—both in terms of the targets chosen and the damage inflicted—highlight the constraints imposed by the risk of escalation. Ukraine’s restraint in targeting nuclear-capable bombers and other sensitive infrastructure serves as a reminder that, in an era of nuclear-armed adversaries, even the most successful raids must be carefully calibrated to avoid crossing invisible but potentially disastrous red lines.
Russia’s nuclear doctrine, updated in late 2024, explicitly reserves the right to use nuclear weapons in response to attacks on its territory by a non-nuclear state that is backed by a nuclear-armed one. Although Ukraine is not directly backed in any strict sense by a nuclear state, the presence of NATO support and the risk of Western intervention looms large in Russian strategic thinking. The Kremlin’s repeated nuclear threats—including tactical strikes, high-altitude detonations, and missiles fired on European capitals—have been a constant feature of the war, even as most of the Kremlin’s supposed red lines have been crossed without triggering nuclear use.
This dynamic creates a paradox: the more effective Ukraine’s raids, the greater the risk of a disproportionate escalation by Russia. For some observers in the West, the fear of a severe Russian reaction almost overshadows the operational success of the raid itself. This plays into a culture of Western self-deterrence in response to Russian threats, whereby Russia actively uses nuclear and conventional saber-rattling not merely in a neutral strategic context, but also as a deliberate tool to manage and constrain Western behavior.
Operation Spiderweb will enter military history as one of the more daring raids and one of the first conducted with remotely controlled strike drones. But it does not herald the dawn of a new age. Rather, it is the latest iteration of the classic raid, adapted to the realities of 21st century warfare under the nuclear threat.
25 notes
·
View notes
Note
I've read a lot about subterranean Iranian bases, and how Israel lacks the planes and bunker-buster bombs to destroy them without US intervention. Thing is, couldn't the US just sell the bombs and the planes to Israel?
I've mentioned this before, but selling a plane and bomb is hardly a simple matter. There's a host of concerns to include training, software, spare parts, and other issues. Then you factor in the exposure for selling capabilities. You have to assume that any piece of defense equipment you sell will be reverse-engineered and almost certainly have the blueprints end up in the hands of your enemy - this is why most countries sell lower-grade export models rather than their top-tier stuff.
You also have to factor, the reason why Israel doesn't operate a strategic bomber fleet is that Israel has a large defense budget (about the size of South Korea's) but doesn't have anywhere near the population base or GDP. Strategic bomber fleets are expensive to operate and maintain.
So, they could in theory, but it would probably create difficult problems.
Thanks for the question, Anon.
SomethingLikeALawyer, Hand of the King
7 notes
·
View notes
Text
The Best Insurance Client Management System
Discover the ultimate solution for managing your insurance clients with Elisops Insurance Client Management System. Our platform offers a comprehensive suite of tools designed to streamline every aspect of client management, from policy tracking to claims processing and customer support. With Elisops, you can efficiently manage client information, track policy renewals, and handle claims seamlessly, all in one centralized system. Our user-friendly interface and intuitive features make it easy for insurance agents to stay organized and provide exceptional service to clients. Say goodbye to manual processes and hello to increased productivity and customer satisfaction with Elisops Insurance Client Management System. Experience the best-in-class solution trusted by insurance professionals worldwide to optimize their client management processes and drive business growth.
#customer service#customer service software#crm system customer service#sales and service software#dispatch management#dispatch system software#dispatch fleet management system#fleet dispatch software#fleet operations software#fleet operations management#insurance crm system#insurance client management system#general crm#client management crm#crm client relationship management#financial management solutions#management solution#account tracking software#financial tracking software#self service payroll system#payroll analytics#payroll and hr management#asset inventory system#inventory asset tracking#IT asset inventory system
1 note
·
View note
Text
AU Space Shuttle Enterprise
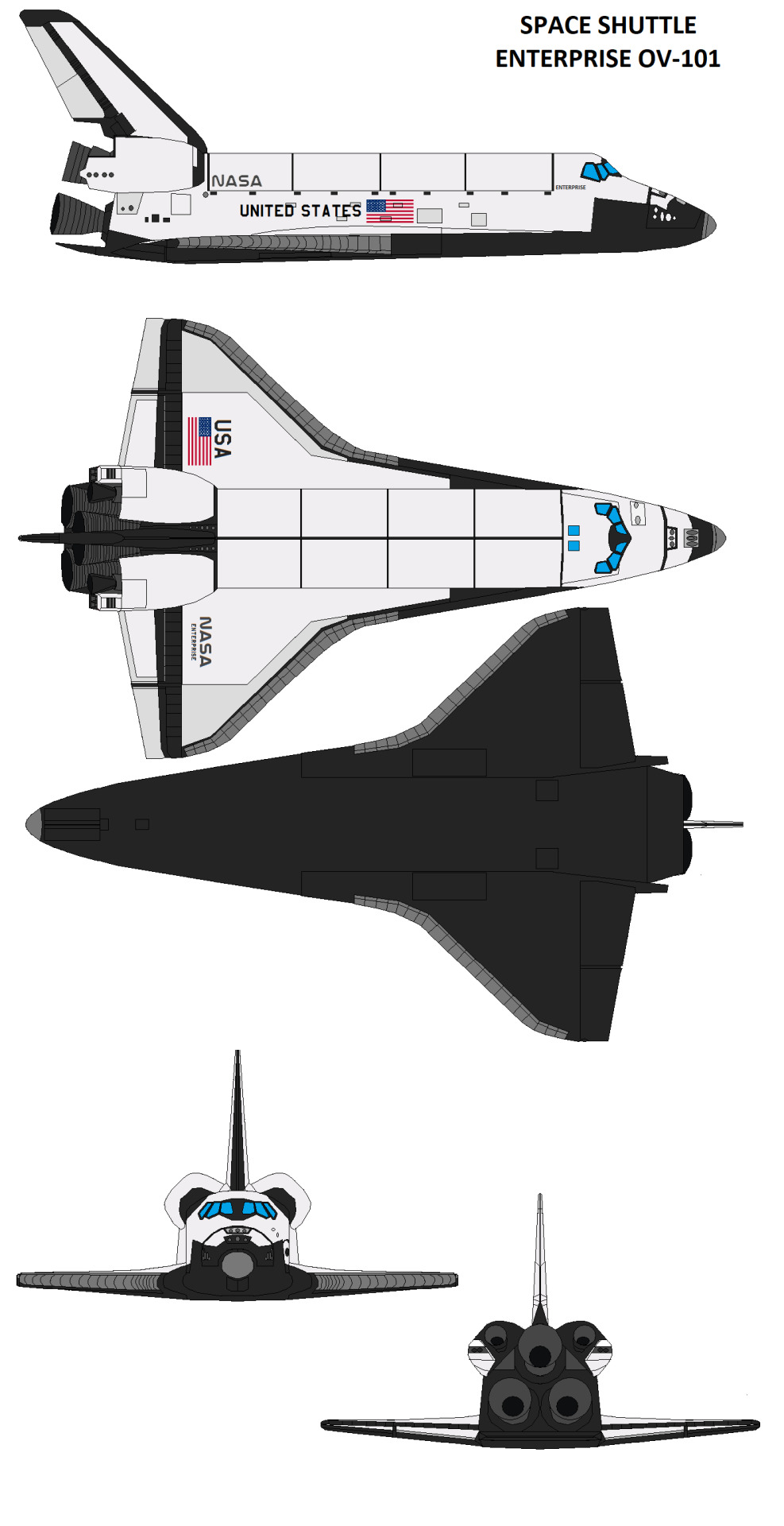
Circa 1985 to 1987
From my Alternative History Post (link) this is how the Space Shuttle Enterprise evolved from the 4th operational orbiter in 1985 to the prototype unmanned shuttle.
More History on the Shuttle:
• April 1983: Enterprise is returned to Palmdale for her disassembled and rebuild.
• As a weight saving measure her mid-fuselage is returned to Convair for a complete rebuild to bring it inline with OV-103 and OV-104.
• to further lighten her frame, her aft-fuselage is rebuilt with similar materials as her sisters.
• Engineers at Rockwell suggests rebuilding or replacing her wings as well but NASA doesn't have room in the budget.
• May 1985: at long last, Enterprise is rolled out and joins the fleet. She weighs slightly less than Columbia. Her main issue is her wings are heavier and weaker than the other Orbiters.
• September 1985: STS-21 is Enterprise's first mission
• 1987: During the Shuttle hiatus following the Challenger Disaster, she went through a mini refit that saw her exterior markings change. (NASA in this timeline returned to the Meatball logo sooner than in the OTL)
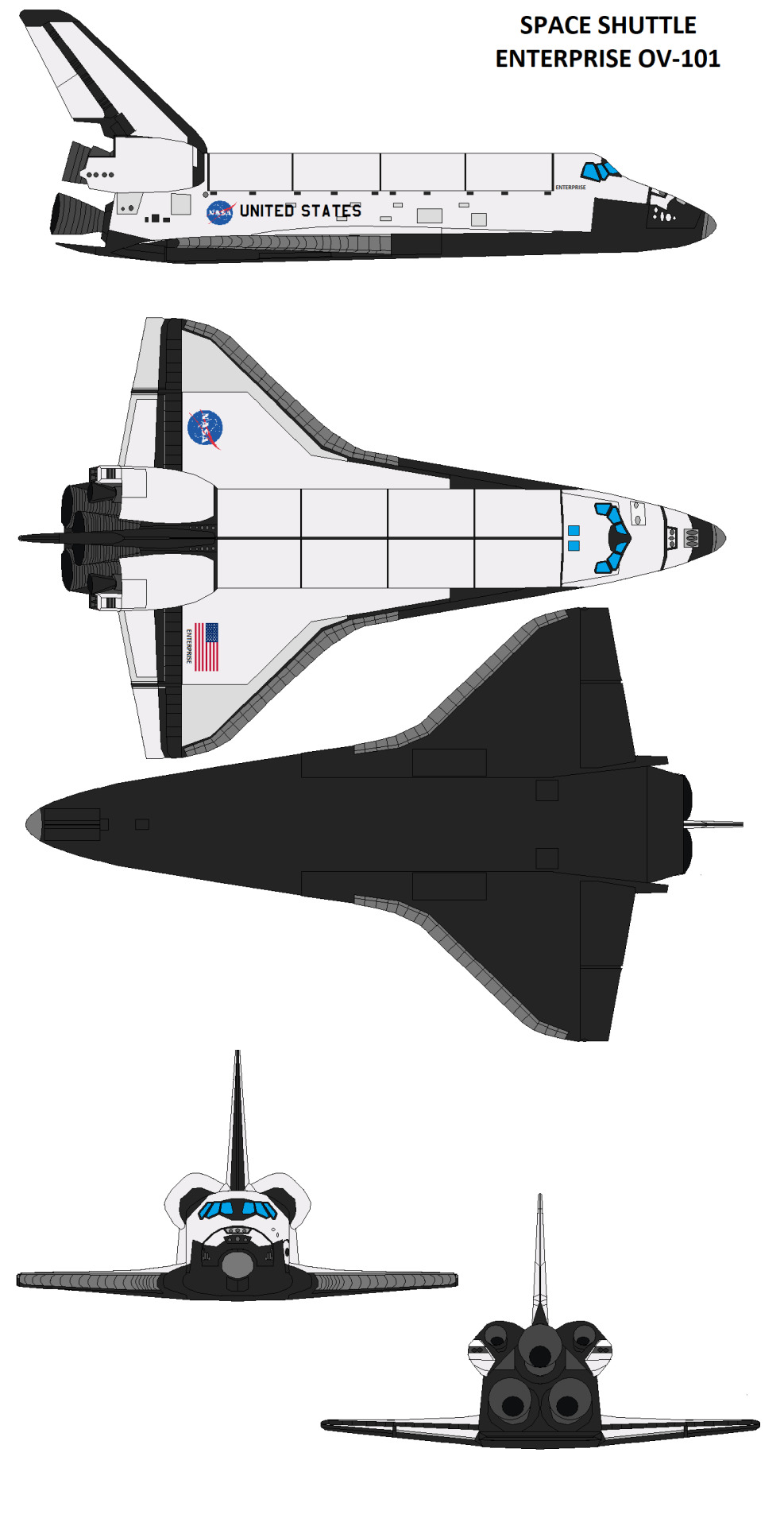
Circa 1988 to 1993
• April 1988: STS-30 is Enterprise's first launch following the hiatus.
• December 1993: following STS-61, Enterprise is retired due to being the oldest in the fleet. Endeavour takes her place in the fleet.
• June 1994: Enterprise is flown to Dulles Airport, Washington DC, and is given to the Smithsonian for eventual display when the Steven F. Udvar-Hazy Center is built. NASA retains the option recalled her if needed.
• 1998: NASA studies modifying the Shuttle-C software to work on the Space Shuttle and potentially using Enterprise as a reusable Shuttle-C. The reasoning behind this option this configuration would be a cheaper alternative to the X-33 program. However, while the shuttle could be retrofitted with the software, the shuttle would have less cargo capacity than the X-33 and still required use of expensive legacy launch facilities (ie VAB and LC-39). The study ends with only the software in a beta state.
• December 2003: Steven F. Udvar-Hazy Center is opened with Enterprise being one of its major exhibits.
• November 2003: the Shuttle-C software is used to return STS-118 Columbia to Earth and with critical damage to her structure (mainly her port wing and some internal damage from a collapsed landing gear).
• May 2004: NASA recalls Enterprise to replace Columbia.
• August 2004: initial plans are to return her flight, unmodified. However, NASA develops the Shuttle-C software further and changes it's name to A.S.Tr.O.S (Autonomous Space Transport Operating System).
• New wings! Enterprise is fitted with new wings which are of a modified design and lighter and stronger than the wings of her sisters. With other upgrades and modifications, she is slightly lighter than her younger sisters.
• Some within NASA joking refer to her as Enterprise-A, as a reference to Star Trek.
• September 2006: to commemorate the 30th anniversary of her unveiling to the media, Lockheed-Rockwell rolls her out of their Palmdale facility to rechristen the Shuttle. In attendance, Leonard Nimoy, George Takei, Nichelle Nicholas, Walter Koenig, Christopher Doohan and Rod Roddenberry.
- when asked by the media, Leonard remarked she is still a sight to behold and is glad she will continue her mission of exploration.
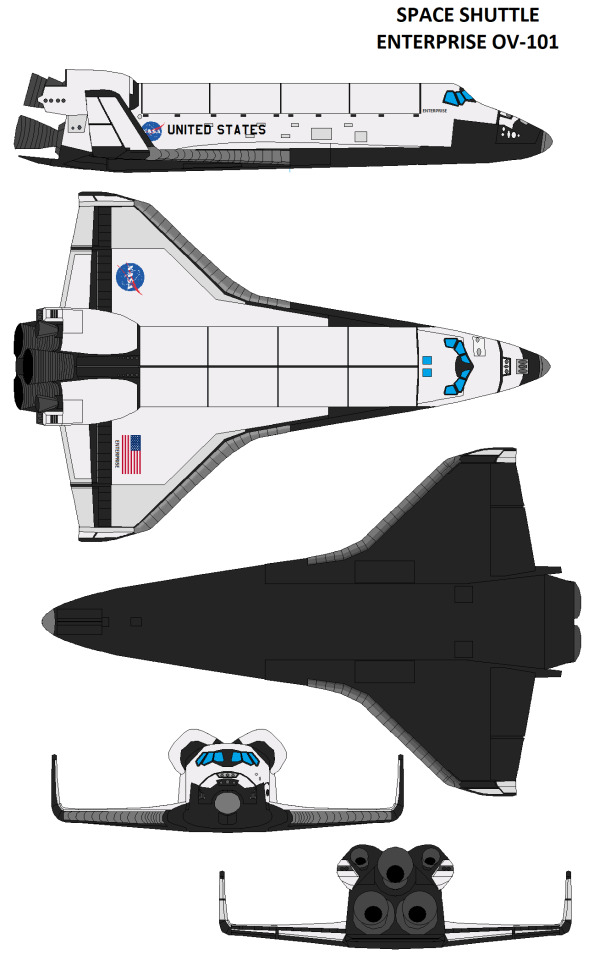
Enterprise A (unmanned)
• July 2006: to test the A.S.Tr.O.S. during a return to earth and landing, a new series of Approach and Landing Tests (ALT) were conducted with NASA's 747 SCA (N905NA) at the Dryden Flight Research Center, Edwards Air Force Base. 15 flights are flown to put the software in the real world, with two astronauts on board to step in when needed. Barring some higher than normal landing speeds, the software passes all of its objectives.
• It should be noted, while the rebuilt Enterprise is mainly used as an unmanned orbiter, this is a misnomer. It is more accurate to call her a hybrid shuttle. NASA has the option to convert her back into a manned shuttle if desired or needed.
- This nearly was used in 2015 during STS-154. Space Shuttle Atlantis was after conducting maintenance/upgrades on the Hubble Space Telescope (HST), the crew was unable to disconnect the shuttle from the telescope. CTS-48 Enterprise was already on LC-39B for a cargo mission to the International Space Station. All that was needed was to remove supplies from the payload bay and reinstall the seats in her crew space. Fortunately, this rescue wasn't needed as the Astronauts conducted an unscheduled EVA and manually disconnected the Shuttle from the HST.
• November 2008: first flight of Enterprise-A (CTS-11)
• When Columbia was given a cosmic restoration for her display, the first set of wings from Enterprise was used to replace her damaged one.
• 2019: Enterprise is retired for the final time following CTS-74.
• 2020: Enterprise is on display at Space Center Houston with the restored Star Trek Galileo Shuttlecraft prop.
Original artwork by bagera3005: link, link, link
#Space Shuttle#Space Shuttle Enterprise#Enterprise#OV-101#Orbiter#NASA#Space Shuttle Program#Enterprise-A#alt history#Alternative History#AU#Complete Shuttle Fleet Timeline#my post
95 notes
·
View notes
Text

B-2 Gets Big Upgrade with New Open Mission Systems Capability
July 18, 2024 | By John A. Tirpak
The B-2 Spirit stealth bomber has been upgraded with a new open missions systems (OMS) software capability and other improvements to keep it relevant and credible until it’s succeeded by the B-21 Raider, Northrop Grumman announced. The changes accelerate the rate at which new weapons can be added to the B-2; allow it to accept constant software updates, and adapt it to changing conditions.
“The B-2 program recently achieved a major milestone by providing the bomber with its first fieldable, agile integrated functional capability called Spirit Realm 1 (SR 1),” the company said in a release. It announced the upgrade going operational on July 17, the 35th anniversary of the B-2’s first flight.
SR 1 was developed inside the Spirit Realm software factory codeveloped by the Air Force and Northrop to facilitate software improvements for the B-2. “Open mission systems” means that the aircraft has a non-proprietary software architecture that simplifies software refresh and enhances interoperability with other systems.
“SR 1 provides mission-critical capability upgrades to the communications and weapons systems via an open mission systems architecture, directly enhancing combat capability and allowing the fleet to initiate a new phase of agile software releases,” Northrop said in its release.
The system is intended to deliver problem-free software on the first go—but should they arise, correct software issues much earlier in the process.
The SR 1 was “fully developed inside the B-2 Spirit Realm software factory that was established through a partnership with Air Force Global Strike Command and the B-2 Systems Program Office,” Northrop said.
The Spirit Realm software factory came into being less than two years ago, with four goals: to reduce flight test risk and testing time through high-fidelity ground testing; to capture more data test points through targeted upgrades; to improve the B-2’s functional capabilities through more frequent, automated testing; and to facilitate more capability upgrades to the jet.
The Air Force said B-2 software updates which used to take two years can now be implemented in less than three months.
In addition to B61 or B83 nuclear weapons, the B-2 can carry a large number of precision-guided conventional munitions. However, the Air Force is preparing to introduce a slate of new weapons that will require near-constant target updates and the ability to integrate with USAF’s evolving long-range kill chain. A quicker process for integrating these new weapons with the B-2’s onboard communications, navigation, and sensor systems was needed.
The upgrade also includes improved displays, flight hardware and other enhancements to the B-2’s survivability, Northrop said.
“We are rapidly fielding capabilities with zero software defects through the software factory development ecosystem and further enhancing the B-2 fleet’s mission effectiveness,” said Jerry McBrearty, Northrop’s acting B-2 program manager.
The upgrade makes the B-2 the first legacy nuclear weapons platform “to utilize the Department of Defense’s DevSecOps [development, security, and operations] processes and digital toolsets,” it added.
The software factory approach accelerates adding new and future weapons to the stealth bomber, and thus improve deterrence, said Air Force Col. Frank Marino, senior materiel leader for the B-2.
The B-2 was not designed using digital methods—the way its younger stablemate, the B-21 Raider was—but the SR 1 leverages digital technology “to design, manage, build and test B-2 software more efficiently than ever before,” the company said.
The digital tools can also link with those developed for other legacy systems to accomplish “more rapid testing and fielding and help identify and fix potential risks earlier in the software development process.”
Following two crashes in recent years, the stealthy B-2 fleet comprises 19 aircraft, which are the only penetrating aircraft in the Air Force’s bomber fleet until the first B-21s are declared to have achieved initial operational capability at Ellsworth Air Force Base, S.D. A timeline for IOC has not been disclosed.
The B-2 is a stealthy, long-range, penetrating nuclear and conventional strike bomber. It is based on a flying wing design combining LO with high aerodynamic efficiency. The aircraft’s blended fuselage/wing holds two weapons bays capable of carrying nearly 60,000 lb in various combinations.
Spirit entered combat during Allied Force on March 24, 1999, striking Serbian targets. Production was completed in three blocks, and all aircraft were upgraded to Block 30 standard with AESA radar. Production was limited to 21 aircraft due to cost, and a single B-2 was subsequently lost in a crash at Andersen, Feb. 23, 2008.
Modernization is focused on safeguarding the B-2A’s penetrating strike capability in high-end threat environments and integrating advanced weapons.
The B-2 achieved a major milestone in 2022 with the integration of a Radar Aided Targeting System (RATS), enabling delivery of the modernized B61-12 precision-guided thermonuclear freefall weapon. RATS uses the aircraft’s radar to guide the weapon in GPS-denied conditions, while additional Flex Strike upgrades feed GPS data to weapons prerelease to thwart jamming. A B-2A successfully dropped an inert B61-12 using RATS on June 14, 2022, and successfully employed the longer-range JASSM-ER cruise missile in a test launch last December.
Ongoing upgrades include replacing the primary cockpit displays, the Adaptable Communications Suite (ACS) to provide Link 16-based jam-resistant in-flight retasking, advanced IFF, crash-survivable data recorders, and weapons integration. USAF is also working to enhance the fleet’s maintainability with LO signature improvements to coatings, materials, and radar-absorptive structures such as the radome and engine inlets/exhausts.
Two B-2s were damaged in separate landing accidents at Whiteman on Sept. 14, 2021, and Dec. 10, 2022, the latter prompting an indefinite fleetwide stand-down until May 18, 2023. USAF plans to retire the fleet once the B-21 Raider enters service in sufficient numbers around 2032.
Contractors: Northrop Grumman; Boeing; Vought.
First Flight: July 17, 1989.
Delivered: December 1993-December 1997.
IOC: April 1997, Whiteman AFB, Mo.
Production: 21.
Inventory: 20.
Operator: AFGSC, AFMC, ANG (associate).
Aircraft Location: Edwards AFB, Calif.; Whiteman AFB, Mo.
Active Variant: •B-2A. Production aircraft upgraded to Block 30 standards.
Dimensions: Span 172 ft, length 69 ft, height 17 ft.
Weight: Max T-O 336,500 lb.
Power Plant: Four GE Aviation F118-GE-100 turbofans, each 17,300 lb thrust.
Performance: Speed high subsonic, range 6,900 miles (further with air refueling).
Ceiling: 50,000 ft.
Armament: Nuclear: 16 B61-7, B61-12, B83, or eight B61-11 bombs (on rotary launchers). Conventional: 80 Mk 62 (500-lb) sea mines, 80 Mk 82 (500-lb) bombs, 80 GBU-38 JDAMs, or 34 CBU-87/89 munitions (on rack assemblies); or 16 GBU-31 JDAMs, 16 Mk 84 (2,000-lb) bombs, 16 AGM-154 JSOWs, 16 AGM-158 JASSMs, or eight GBU-28 LGBs.
Accommodation: Two pilots on ACES II zero/zero ejection seats.
21 notes
·
View notes
Text
EV Drivers & CPOs: Tired of the Charge? ⚡️ EV CMS is Here!

Ever driven around with a low battery, desperately searching for an available charger? Or are you a CPO struggling to manage your charging network?
EV CMS is the game-changer you've been waiting for!
Drivers: Locate stations, see real-time availability, & pay seamlessly.
CPOs: Monitor stations remotely, optimize operations, & gain valuable data.
Learn how EV CMS creates a smoother ride for everyone! ➡️ https://iris.steam-a.com/
0 notes
Text

The Vera C. Rubin Observatory will detect millions of exploding stars
Measuring distances across the universe is much more challenging than measuring distances on Earth. Is a brighter star closer to Earth than another, or is it just emitting more light? To make confident distance measurements, scientists rely on objects that emit a known amount of light, like Type Ia supernovae.
These spectacular explosions, among the brightest to ever be recorded in the night sky, result from the violent deaths of white dwarf stars and provide scientists with a reliable cosmic yardstick. Their brightness and color, combined with information about their host galaxies, allow scientists to calculate their distance and how much the universe expanded while their light made its journey to us. With enough Type Ia supernovae observations, scientists can measure the universe's expansion rate and whether it changes over time.
Although we've caught thousands of Type Ia supernovae to date, seeing them once or twice is not enough—there is a goldmine of information in how their fleeting light varies over time. NSF–DOE Vera C. Rubin Observatory will soon begin scanning the southern hemisphere sky every night for ten years, covering the entire hemisphere approximately every few nights. Every time Rubin detects an object changing brightness or position it will send an alert to the science community. With such rapid detection, Rubin will be our most powerful tool yet for spotting Type Ia supernovae before they fade away.
Rubin Observatory is a joint program of NSF NOIRLab and DOE's SLAC National Accelerator Laboratory, which will cooperatively operate Rubin.
Scientists like Anais Möller, a member of the Rubin/LSST Dark Energy Science Collaboration, look forward to Rubin's decade-long Legacy Survey of Space and Time (LSST), during which it's expected to detect millions of Type Ia supernovae.
"The large volume of data from Rubin will give us a sample of all kinds of Type Ia supernovae at a range of distances and in many different types of galaxies," says Möller.
In fact, Rubin will discover many more Type Ia supernovae in the first few months of the LSST than were used in the initial discovery of dark energy—the mysterious force causing the universe to expand faster than expected based on gravitational theory. Current measurements hint that dark energy might change over time, which—if confirmed—could help refine our understanding of the universe's age and evolution. That in turn would impact what we understand about how the universe formed, including how quickly stars and galaxies formed in the early universe.
With a much larger set of Type Ia supernovae from across the universe scientists will be able to refine our existing map of space and time, getting a fuller picture of dark energy's influence.
"The universe expanding is like a rubber band being stretched. If dark energy is not constant, that would be like stretching the rubber band by different amounts at different points," says Möller. "I think in the next decade we will be able to constrain whether dark energy is constant or evolving with cosmic time. Rubin will allow us to do that with Type Ia supernovae."
Every night Rubin Observatory will produce about 20 terabytes of data and generate up to 10 million alerts—no other telescope in history has produced a firehose of data quite like this. It has required scientists to rethink the way they manage rapid alerts and to develop methods and systems to handle the large incoming datasets.
Rubin's deluge of nightly alerts will be managed and made available to scientists through seven community software systems that will ingest and process these alerts before serving them up to scientists around the world. Möller, together with a large collaboration of scientists across expertises, is developing one of these systems, called Fink.
The software systems collect the alerts from Rubin each night, merge Rubin data with other datasets, and using machine-learning, classify them according to their type, such as kilonovae, variable stars, or Type Ia supernovae, among others. Scientists using one of Rubin's community systems, like Fink, will be able to sort the massive dataset of alerts according to selected filters, allowing them to quickly home in on the data that are useful for their research.
"Because of the large volumes of data, we can't do science the same way we did before," says Möller. "Rubin is a generational shift. And our responsibility is developing the methods that will be used by the next generation."
7 notes
·
View notes