#full disk encryption
Explore tagged Tumblr posts
Text
VeraCrypt
Security on your device is crucial, especially if others frequently use your machine. VeraCrypt is an application designed to secure and encrypt partitions, ensuring sensitive files remain protected. The program is highly customizable, offering a variety of options. When you open VeraCrypt, you’ll find a simple interface, which some may consider outdated, guiding you through the available…
#Data Privacy#data security#disk encryption#disk encryption software#encryption#full disk encryption#password protection#secure data#VeraCrypt#volume encryption
0 notes
Text
Manage BitLocker and FileVault with Trellix Native Encryption
In today’s enterprises, the proliferation of data and devices has heightened the complexity of safeguarding confidential information and adhering to compliance requirements. With substantial amounts of data stored on PCs, tablets, and other devices. Ensuring the security of sensitive data has become more critical than ever. In this article, we shall discuss How to Manage BitLocker with Trellix…

View On WordPress
#Disk Encryption#Full Disk Encryption#Full Disk Encryption (FDE)#Insight to Full Disk Encryption#MacOS#macOS Big Sur#macOS Monterey#macOS Ventura#Microsoft Windows#Windows#Windows 10#Windows Server#Windows Server 2012#Windows Server 2016#Windows Server 2019#Windows Server 2022#Windows Server 2025
0 notes
Text
they say that there's a point where you can have too much security and it impedes the usability of a system—however i'd like to commend online banking platforms for somehow simultaneously having security measures that make them incredibly inconvenient to use every day, whilst also offering fairly low actual security and being not particularly difficult to bypass if you're dedicated enough
#like none of the online banking platforms ive used have let me use an actual password?#nor do they let me set up 2fa with an authenticator app besides their own proprietary banking app#they all seem to send all verification codes by sms with the only way to authenticate otherwise is through their proprietary apps. which i#am not installing.#also perhaps this serves some purpose i dont understand but why do they frequently ask for the nth character of your pin or whatever#instead of asking for the whole pin?#like all the 'password' equivalents seem very easy to bruteforce and the sms verification can be bypassed by someone else just getting a#sim card for your number#and the fact that they never keep you logged in is annoying like i have full disk encryption on all my devices im not worried about someone#using my own device to access my bank account. i dont particularly think theres anyone trying to get into my bank account but if there were#they'd be getting in through their own device not mine... you can keep me logged in on mine...
6 notes
·
View notes
Text
i can do better than that previous poll. 1 point per recommendation followed, interpret conservatively.
automatic backups (and tested!!)
ransomware resilient
2nd factor on all important accounts
2nd factor, not sms, phishing resistant everywhere where feasible
unique passwords on all important accounts
unique passwords everywhere
bitlocker/full disk encryption and secureboot
bonus point for measures not listed (tags plssss)
26 notes
·
View notes
Text
CrowdStrike'd and BitLocker'd
With yesterday's CrowdStrike outage. I'm sure a number of you are probably wondering "what does BitLocker have to do with any of this?" Well, it all has to do with an added layer of security many organizations use to keep data from being stolen if a computers ends up in the hands of an "unauthorized user."
To start, let me briefly explain what the CrowdStrike driver issue did and what the fix for it is.
After the update was automatically installed to computers running the CrowdStrike Falcon Sensor, a faulty driver file caused the Windows kernel on those computers to crash and display a Blue Screen of Death. How Windows typically handles a crash like this is to create a crash log file, then perform a reboot. Since this driver would launch shortly after Windows finished booting, it would cause the operating system to crash and reboot again. When two crashes have occurred in sequence, Windows will automatically boot into Recovery Mode. Hence why we say several pictures of the Recovery Mode screen across social media yesterday.

Unfortunately, this update was automatically pushed out to around 8.5 million computers across several organizations, causing widespread chaos within the matter of a few hours. And the fix for this issue had to be performed by physically accessing each computer, which required those of us working in I.T. to have to run around several facilities, locate each affected computer, and apply the fix one by one.
The short and simple of the fix is either one of two options. You can either use the Recovery Mode that Windows was already booted into to navigate to Start-Up Setting, and launch Safe Mode. Once Windows boots into Safe Mode, the technician can navigate to C:\Windows\System32\Drivers\CrowdStrike, and delete the file C00000291-*.sys. After that the computer can be rebooted as normal, and the crashing will stop.
Or the technician can open System Restore from Recovery Mode. And, assuming there is a recovery point, restore the computer back to a good known working state.
Now, this may all seem simple enough. So why were so many organizations having trouble running this fix? That all has to do with BitLocker. As an added security measure, many organizations use BitLocker on their computers to perform a full hard disk encryption. This is done so that if a computer ends up being lost or stolen, and ends up in the hands of an "unauthorized user" they will not be able to access any of the data stored on the computer without a password to log into the computer, or the computer's BitLocker recovery key.
This presented a problem when trying to restore all of these affected computers, because when either trying to launch Safe Mode or System Restore, the user would be prompted for the BitLocker recovery key.
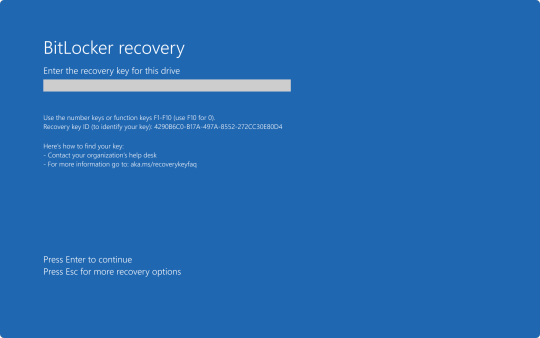
In my organization's case, we found we could save time by providing our end user the steps to perform one of the two fixes on their own to save time. But the problem we still continue to run into is the need for these BitLocker recovery keys. In my case, I've been fielding several calls where I've had end users walking from one computer to another while I provide them with the key as they walk through reverting back to a previous restore point.
Again, a pretty long story, but hopefully that can provide some context as to what's been happening over the past 48 hours.
30 notes
·
View notes
Text
All right, since I bombarded a poor mutual yesterday...
Privacy is not security and security is not privacy. These terms are not interchangeable, but they are intrinsically linked.
While we're at this, anonymity =/= security either. For example, Tor provides the former, but not necessarily the latter, hence using Https is always essential.
It is impossible to have privacy without security, but you can have security without privacy.
A case in point is administrators being able to view any data they want due to their full-access rights to a system. That being said, there are ethics and policies that usually prevent such behavior.
Some general tips:
Operating System: Switch to Linux. Ubuntu and Linux Mint are widely used for a reason. Fedora too. And don't worry! You can keep your current operating system, apps and data. If you're on a Mac computer, you can easily partition your hard drive or SSD by using Disk Utility. If you're on Windows, you can follow this guide.
You want to go a step further? Go with Whonix or Tails. They're Linux distributions as well, but they're both aiming for security, not beauty so the interface might not be ideal for everyone. Many political activists and journalists use them.
You want anonymity? Then you need to familiarize yourself with Tor. Also, Tor and HTTPS and Tor’s weaknesses. When you're using it, don't log in to sites like Google, Facebook, Twitter etc. and make sure to stay away from Java and Javascript, because those things make you traceable.
Alternatives for dealing with censorship? i2p and Freenet.
Is ^ too much? Welp. All right. Let's see. The first step is to degoogle.
Switch to a user-friendly browser like Firefox (or better yet LibreWolf), Brave or Vivaldi. There are plenty of hardened browsers, but they can be overwhelming for a beginner.
Get an ad blocker like Ublock Origin.
Search Engine? StartPage or Duckduckgo. SearXNG too. Like I said degoogle.
Get a PGP encrypted e-mail. Check Protonmail out.
There's also Tutamail that doesn't cover PGP, but uses hybrid encryption that avoids some of the cons of PGP.
Skiff mail is also a decent option.
Use an e-mail aliasing service such as SimpleLogin or AnonAddy.
Check OpenPGP out. Claws Mail is a good e-mail client for Windows and Linux, Thunderbird for Mac OS.
Gpg4win is free and easy to use for anyone that wants to encrypt/decrypt e-mails.
Instead of Whatsapp, Facebook messenger, Telegram etc. use Signal for your encrypted insant messaging, voice and video calls.
Get a metadata cleaner.
Get a firewall like Opensnitch, Portmaster or Netguard which can block Internet for trackers.
Alternatively, go with a private DNS that blocks these trackers. NextDNS is a good paid service. Rethink a good free option.
Replace as many of your applications as you can with FOSS (free and open source) ones. Alternativeto can help you.
Always have automatic updates on. They are annoying af, I know, but they are necessary.
Keep your distance from outdated software.
Always have two-factor authentication (2FA) enabled.
Do not use your administrator account for casual stuff. If you're on Linux, you probably know you can be sudo, but not root.
On Linux distributions use AppArmor, but stay away from random antivirus scanners. Other distributions default to SELinux, which is less suited to a beginner.
Never repeat your passwords. If you can't remember them all, use a password manager like KeePass.
Encrypt your drive.
Honestly, VPNs have their uses and ProtonVPN, Mullvad and Windscribe are decent, but eh. If you don't trust your ISP, why would you trust the VPN provider that claims they don't log you when you can't verify such a thing?
57 notes
·
View notes
Note
After I deleted a bunch of projects (thankfully non-critical, though representing a great deal of work in total) during a recent fresh OS install, I realized that my backup practices are practically non-existent. Any tips or sources on getting started making, and eventually automating, effective backups?
I am stealing the concept here from jwz's backup guide, but I am recommending different tools, focusing on personal files only, and also addressing Windows. jwz's guide is a good reference:
Doing a way, way better job than most people of backing up one single system is very easy. Let us begin.
The most basic step of having decent backups is getting your hands on two external hard drives at least big enough to hold your entire system, and putting a label on them that says "BACKUP ONLY DO NOT USE FOR ANYTHING ELSE I AM BEING FOR REAL HERE"
Once you've got those, plug one into your system wherever it spends the most time. If you have a desktop then that's solved, if it's a laptop hopefully you already have a USB hub you plug it into when you sit down to work or whatever and you can just leave it there.
Now set up regular scheduled backups to that device. On Windows and Mac, there's a built in tool for backing up your system to an external drive. We'll assume that you just want to back up your user files on Windows and Linux, since doing full system backups isn't tricky but is kind of unnecessary.
(Ugh. Windows seems to be trying to phase out Windows Backup and Restore in favour of their File History thing. That's annoying, let me log in to windows and check how this actually works. Mac in the meantime)
Mac has Time Machine. Time Machine is extremely good, and you can tell Time Machine to save its backups to a disk. Point Time Machine at your external hard drive and tell it to schedule a backup however frequently you want. If anything goes wrong in the future, you can ask Time Machine to look at that backup disk and it'll show you a few versions of whatever you backed up there. I'm not a Mac user but I think you can even use Time Machine to transfer between an old computer and a new one.
Windows now has File History which I have never used in my life, they added it after I stopped using Windows. Same idea though, pick some folders and back them up to an external storage device. If anything goes wrong, use File History to go back through that device and find the version of the file you wanted. I don't know if there's still a way to access the older Backup and Restore system.
On Linux, my favoured way to manage simple desktop backups is Deja Dup, a GUI for Duplicity. Duplicity can do a lot more than just backup to a disk, but we'll start there. Install Deja Dup, open it up, and follow the prompts to back up your user files to the external drive. Deja Dup can also do backups to remote storage servers, Google Drive/Onedrive, and commercial storage providers like Amazon and Backblaze. It will even encrypt your backups if you are worried about Amazon spying on your files or whatever. If something goes wrong, point Deja Dup at your backup drive and it will offer you a suite of restore options covering a few versions.
Now, you have a permanently plugged in hard drive that will always get rolling backups you can restore from. These aren't safe from, say, ransomware, or your house burning down, but at least you won't lose anything when you update a computer or accidentally delete something and have an ohshit moment.
Now you take that other drive you bought, and do the same backup you're already doing to that. Now you go put it somewhere else where it's readily accessible and won't be accidentally used for anything, keep it at the office, give it to your dad, whatever. Set a reminder on your phone for once a month. Once a month, go get that drive, run another backup, and put it back. You now have better backups than many medium sized businesses.
This is impractical to scale beyond one PC, but if we're being honest even when I had like half a dozen laptops, only one contained much of value. Back up the system you care about.
Don't worry too much about making sure your backups are space efficient, like, yeah it would be a good idea to exclude game installs and stuff from your backups to save space but if that sounds daunting or time consuming literally do not do it. Decision paralysis is brain poison, just back it up and sort it out later. 2TB external hard drives are cheap.
FURTHER STEPS YOU CAN TAKE:
Easy Cloud backup: Backblaze personal backup on Windows and Mac is $6/month and pretty easy to use. If you are struggling to keep track of a monthly remote backup, or you want an easy remote backup. Backblaze is a reasonably reliable company and one of the Go To Companies in the world of data reliability. Yes, it's a cloud subscription. If you don't want that don't use it.
Network backup: If you have access to a storage server, that can be a good way to make a remote backup without having to shuttle disks around. That could be a physical server if you maintain some kind of lab, or it could be a cloud storage provider like Backblaze B2 or Onedrive or whatever. Deja Dup specifically supports backing up to a lot of different network storage providers, and even if you only have a fifty or sixty gigabytes of network storage on hand, your most essential personal files can probably fit in there.
Drive failures: Eventually one of your drives will fail, either your storage drive or your backup drive. If the storage drive fails, well, that's what the backup is for, go get a replacement and restore from the backup. If your backup drive fails, well, that's why you have two of them. As soon as humanly possible go get a replacement drive, and substitute it in for the dead one.
101 notes
·
View notes
Text
building an opensource collection of 'net services
hi there! im mia :) im a computer nerd with too much time on her hands.
im making this post to bring a project of mine into the world; a fully opensource and collaborative collection of online tools. this will grow over time, but for now, there is one thing active and two planned. (read on below)
CalicoDrive
a nextcloud instance! currently offering a bunch of very useful things:
50GB of free cloud storage
a Markdown notetaking tool
a shareable, open calendar
a photo gallery
web bookmark storage, and
some organisation and collaboration tools.
many of the cloud storage services we rely on are corporate, and require exorbitantly priced subscriptions. alongside that, data on them is often subject to a huge array of impenetrable terms/conditions.
what makes this different? firstly, your data is controlled by you. it is entirely encrypted on disk and can only be decrypted with your selected password. you own the data the same way you would were it on an external hard drive or flashstick.
secondly- its free! while you can pay 20$ once off or 5$ a month to upgrade storage quota and support the project, the core of it is entirely and utterly free to use.
matrix.calicocore
(full disclaimer- this service isn't online yet. it's planned to be active within the next month at the very maximum, very likely sooner.)
what's matrix? i am absolutely sure you've heard of IRC- internet relay chat. im also sure you've heard of discord.
matrix is a modern federated chat protocol- if you took the best of IRC, and you took the best of Discord, and combined them into an opensource and *free* protocol for real-time messaging? that's matrix, baby!
matrix functions similarly to the fediverse (more on that later). when you sign up, you select a homeserver, which is the infrastructure your account is hosted on. your homeserver determines who you're federated with, your most easily accessible spaces, and the little tag at the end of your name.
so what's matrix.calicocore going to be? a homeserver! the idea here is to bring communication and community into our hands, and away from the hands of big tech corporations who really don't care about us. it'll be federated with other spaces and servers, and run collectively.
fedi.calicocore
if you've ever used mastodon, fedi.calicocore will be a server compatible with it. this is still in the very very early stages as a project, so i cant detail much, but stay tuned.
things to note, disclaimers, etc
this project is in its early days. i cant guarantee perfect stability, though it has been tested and run for a few days already. please don't expect a perfect replacement for existing services YET.
secondly, in regards to calicodrive; your data is fully encrypted in two ways, both within the nextcloud instance and on the physical spinning rust. this means if you majorly forget your password, there's a possibility of losing it- but that trade-off is worth it for the security.
this all sounds great! how can i sign up?
for now, this is the link to the nextcloud:
https://drive.calicocore.space
in the very near future, there'll be a central discussion space on the matrix, too, which you're encouraged to introduce yourself on!
lastly:
who is this for?
these services and tools are made by a disabled trans woman. they will prioritise people vulnerable on the current internet, and focus on building a safe space for trans, non-binary, and queer people; as well as disabled people and people of colour.
you can sign up if you are not one of these, however you will be expected to defer to the marginalised members and be generally respectful of the purpose of the space!
8 notes
·
View notes
Text
Echoes of the Republic - Obi-Wan Kenobi x fem!OC

this is only a snippet from the second chapter of my fanfic over on ao3 <3
Pairing: Obi-Wan Kenobi x fem!OC Summary: Anya Dashal is the disgraced daughter of Nabooian diplomat, ex-handmaiden to Padme Amidala, and now, bounty hunter in the Outer Rim. She wants nothing to do with Coruscant, yet when Padme begs her for her help, she cannot refuse. Anya reunites with her old friend, meets an all too attractive Jedi, and learns that no matter how far she runs, her past is never far. WC: fic is 4k words atm, this excerpt is 390 :) Warnings: the fic contains mentions of drugs, use of spice as weed, sexual content, graphic content and Anya suffers from a panic disorder
As she heard the door slide to a close, Anya let out a breath she didn’t realize she was holding. She was alone for the first time since she reached Coruscant and her heart and mind didn’t seem to know how to feel about it. The only part of her that seemed sure of something was her stomach, that was now grumbling louder than an angry gundark.
“Might as well,” she mused, pushing herself off the bed. She walked to the kitchen, toeing the pillow she’d thrown at Padmé out of the way. She was still in awe of the disgustingly luxurious apartment that was now hers. While she was apprehending the actual job, she couldn’t help the warmth spreading in her chest at having an actual home. It had been too long.
She continued her mission to find something to ease her growling stomach, searching the cooling drawers of the kitchen and the pantry. Padmé had left her with basic ingredients as well as prepared dishes, and, stars bless her soul, bottles of Corellian wine, whiskey & Nabooian amber liquor.
She poured herself a generous glass of top shelf Corellian whiskey and sat at the couch, reheating one of the pre-made meals. Looking around the living room, she recalled Padmé mentioning some datapads, and the familiar itch returned to her fingertips. Setting down her cool glass, she padded over to the drawers across from the sofa. She found music disks that would fit in the screen setup right above the drawers, books that she would probably never read, and more miscellaneous items for her entertainment, but no datapads. Before moving on to the next drawer, she grabbed a disk, slipping it into the slit in the screen. Soft jazz music filled the air, and she hummed contentedly. She opened the next drawer, finally finding those datapads. There were about half a dozen, chock full of separatist intel by the looks of the encryptions buzzing on the screens.
She sat back on the grossly plush couch and got to work, nursing her whiskey, the soft tunes accompanying her fingers dashing across the screens. The smell of fresh food wafted through the air, and the sounds of the city hummed in the background. All that was missing was a spice joint, and she’d be perfect.
Yeah, she could get used to this.
#obi wan x oc#obi wan kenobi#star wars#star wars prequels#the clone wars#star wars fanfiction#sw prequels#star wars oc#ao3 fanfic#fanfic
2 notes
·
View notes
Note
For jodie and woods
Pre- relationship
2 and 4
General
7
Domestic life
5 and 6
HONK
HONK!! My friend! Kings! ^u^
Pre Relationship
2. what was their first impression of each other?
So, I'll start with Jodie and then Frank.
When she first met Frank, when they first spoke and introduced themselves, Jodie noted the air about it. She gained a sense of "fuck around and find out". He's a no-nonsense person, focused soldier, with years of tactical and combative experience. She knew, when looking at him, that he had got the reputation he had for a reason.
His eyes also left a lasting impression on her, how they watched her carefully, cooly, and the sharp edge that almost dared her to say something stupid, ask why he and Mason were there. Or at least, that's what she felt. She also made a mental note to ignore the feeling in her chest. Like, it wasn't love at first sight or anything, but she definitely acknowledge he was handsome.
So, the short version is, Jodie's memory of her first impression of him was how good he looked but also how unnerved she was in his presence (it's Frank, he doesn't really like working with new people so he was about to jump and dance and make buddies).
For Frank, his first impression actually came from like... watching her from a distance. He was being explained who she was by Adler, as he and Mason had just arrived at the safe house, and she was sat at her desk, pouring over the data from the encrypted floppy disk. Her pencil was scribbling furiously, fingers of her left hand tapping agitatedly on the surface of the table. He couldn't really see her face, at first, but he could tell with how hunched over she was, that she'd been sat working at the spot for quite a while. Not to mention the amount of empty paper cups stained with coffee gave away that notion, too.
Then, Adler had called to her, introduced her, and she stuck her hand out stiffly. He took it, regarding her apprehensively, eyes flickering narrowed as he took in her dishevelled, tired appearance. He got the impression that she was working herself into the ground and that she hadn't slept in days.
Despite her agitation, her stiff body language, he noted something else about her - a distant look in her eyes, something unsettled.
She reminded him of someone, but he shook that thought away, putting it down to how tired she looked.
4. Who felt romantic feelings first?
Frank. He actually accepted his feelings first, too; Jodie put those emotions deep down somewhere for a little while longer, but Frank came to the realisation first. I think Jodie just didn't trust what she was feeling and it took her a bit to allow her body to feel something romantic.
General
7. who takes the lead in social situations?
Frank! So, because of what Jodie has been through, she's very hesitant to approach people. Frank also has that protective streak, wants to make sure she doesn't have deal with any more shit.
Later on in their relationship, this does level out and it does depend on the context as to which one will take the lead.
Domestic Life
5. Who's the stricter parent?
AAAAAHH this is tough. Jodie, though, would be the stricter parent. But it's not strictness for the sake of strictness, it comes from a place of deep-seated protection that stems from fear. As Ashley grows up, she'd chill out a little bit.
Guaranteed, though, Ashley could ask "hey, Mom, can I go out tonight with some friends?"
"No."
She'd then go to Frank.
"Hey, Dad-"
"What did your Mom say?"
Ashley can whittle him down though and sometimes Frank relents. How can he not?
6. who worries the most?
Jodie - again, I think it comes from her past and her fear that it'll turn into a full blown haunting (which it does in the form of Keith!)
#gooseanswers#thank you for the ask Kings!#woods/bell oc#frank woods#jodie hall#call of duty#black ops cold war#cod bell oc#bocw oc#Ashley woods
9 notes
·
View notes
Text
Best Practices for Data Lifecycle Management to Enhance Security
Securing all communication and data transfer channels in your business requires thorough planning, skilled cybersecurity professionals, and long-term risk mitigation strategies. Implementing global data safety standards is crucial for protecting clients’ sensitive information. This post outlines the best practices for data lifecycle management to enhance security and ensure smooth operations.
Understanding Data Lifecycle Management
Data Lifecycle Management (DLM) involves the complete process from data source identification to deletion, including streaming, storage, cleansing, sorting, transforming, loading, analytics, visualization, and security. Regular backups, cloud platforms, and process automation are vital to prevent data loss and database inconsistencies.
While some small and medium-sized businesses may host their data on-site, this approach can expose their business intelligence (BI) assets to physical damages, fire hazards, or theft. Therefore, companies looking for scalability and virtualized computing often turn to data governance consulting services to avoid these risks.
Defining Data Governance
Data governance within DLM involves technologies related to employee identification, user rights management, cybersecurity measures, and robust accountability standards. Effective data governance can combat corporate espionage attempts and streamline database modifications and intel sharing.
Examples of data governance include encryption and biometric authorization interfaces. End-to-end encryption makes unauthorized eavesdropping more difficult, while biometric scans such as retina or thumb impressions enhance security. Firewalls also play a critical role in distinguishing legitimate traffic from malicious visitors.
Best Practices in Data Lifecycle Management Security
Two-Factor Authentication (2FA) Cybercriminals frequently target user entry points, database updates, and data transmission channels. Relying solely on passwords leaves your organization vulnerable. Multiple authorization mechanisms, such as 2FA, significantly reduce these risks. 2FA often requires a one-time password (OTP) for any significant changes, adding an extra layer of security. Various 2FA options can confuse unauthorized individuals, enhancing your organization’s resilience against security threats.
Version Control, Changelog, and File History Version control and changelogs are crucial practices adopted by experienced data lifecycle managers. Changelogs list all significant edits and removals in project documentation, while version control groups these changes, marking milestones in a continuous improvement strategy. These tools help detect conflicts and resolve issues quickly, ensuring data integrity. File history, a faster alternative to full-disk cloning, duplicates files and metadata in separate regions to mitigate localized data corruption risks.
Encryption, Virtual Private Networks (VPNs), and Antimalware VPNs protect employees, IT resources, and business communications from online trackers. They enable secure access to core databases and applications, maintaining privacy even on public WiFi networks. Encrypting communication channels and following safety guidelines such as periodic malware scans are essential for cybersecurity. Encouraging stakeholders to use these measures ensures robust protection.
Security Challenges in Data Lifecycle Management
Employee Education Educating employees about the latest cybersecurity implementations is essential for effective DLM. Regular training programs ensure that new hires and experienced executives understand and adopt best practices.
Voluntary Compliance Balancing convenience and security is a common challenge. While employees may complete security training, consistent daily adoption of guidelines is uncertain. Poorly implemented governance systems can frustrate employees, leading to resistance.
Productivity Loss Comprehensive antimalware scans, software upgrades, hardware repairs, and backups can impact productivity. Although cybersecurity is essential, it requires significant computing and human resources. Delays in critical operations may occur if security measures encounter problems.
Talent and Technology Costs Recruiting and developing an in-house cybersecurity team is challenging and expensive. Cutting-edge data protection technologies also come at a high cost. Businesses must optimize costs, possibly through outsourcing DLM tasks or reducing the scope of business intelligence. Efficient compression algorithms and hybrid cloud solutions can help manage storage costs.
Conclusion
The Ponemon Institute found that 67% of organizations are concerned about insider threats. Similar concerns are prevalent worldwide. IBM estimates that the average cost of data breaches will reach 4.2 million USD in 2023. The risks of data loss, unauthorized access, and insecure PII processing are rising. Stakeholders demand compliance with data protection norms and will penalize failures in governance.
Implementing best practices in data lifecycle management, such as end-to-end encryption, version control systems, 2FA, VPNs, antimalware tools, and employee education, can significantly enhance security. Data protection officers and DLM managers can learn from expert guidance, cybersecurity journals, and industry peers’ insights to navigate complex challenges. Adhering to privacy and governance directives offers legal, financial, social, and strategic advantages, boosting long-term resilience against the evolving threats of the information age. Utilizing data governance consulting services can further ensure your company is protected against these threats.
3 notes
·
View notes
Text
This day in history

On September 12 at 7pm, I'll be at Toronto's Another Story Bookshop with my new book The Internet Con: How to Seize the Means of Computation.
On September 14, I'm hosting the EFF Awards in San Francisco.

#15yrsago Canadian man changes name to beat no-fly list https://web.archive.org/web/20080917202919/https://www.cbc.ca/canada/montreal/story/2008/09/11/nofly-name.html
#15yrsago Michigan GOP attacks right-to-vote for the recently foreclosed https://web.archive.org/web/20080911193036/https://michiganmessenger.com/4076/lose-your-house-lose-your-vote
#15yrsago North Texas house burns because local authorities switched off hydrants “to fight terrorism” https://web.archive.org/web/20080913150058/https://www.wfaa.com/sharedcontent/dws/wfaa/latestnews/stories/wfaa080827_lj_hawes.1983f2d0.html
#15yrsago Terror cops hunt down ornamental castor bean plant https://web.archive.org/web/20080914224719/http://www.abc4.com/news/local/story.aspx?content_id=f2396fa3-c730-457d-825c-257c263a831c
#15yrsago Seaweed: Lush, hilarious oversized indie graphic novel https://memex.craphound.com/2008/09/11/seaweed-lush-hilarious-oversized-indie-graphic-novel/
#10yrsago NSA reveals that it illegally gathered thousands of phone records, to the appalled astonishment of FISA court judge https://www.theguardian.com/world/2013/sep/10/nsa-violated-court-rules-data-documents
#10yrsago Revisiting Milgram’s obedience experiment: what did he actually prove? https://psmag.com/social-justice/electric-schlock-65377
#10yrsago This is the crypto standard that the NSA sabotaged https://archive.nytimes.com/bits.blogs.nytimes.com/2013/09/10/government-announces-steps-to-restore-confidence-on-encryption-standards/
#10yrsago How the feds asked Microsoft to backdoor BitLocker, their full-disk encryption tool https://mashable.com/archive/fbi-microsoft-bitlocker-backdoor
#5yrsago California Farm Bureau sells out farmers, hands John Deere a monopoly over tractor repair https://www.vice.com/en/article/kz5qgw/california-farm-bureau-john-deere-tractor-hacking-right-to-repair
#5yrsago 2018’s Blue Wave needs to take down Trump, and the right-wing establishment of the Democratic Party https://www.theguardian.com/commentisfree/2018/sep/10/trump-neoliberal-democratic-party-america
#5yrsago History’s solutions to runaway inequality: warfare, revolution, state collapse and plague https://www.economist.com/open-future/2018/09/10/can-inequality-only-be-fixed-by-war-revolution-or-plague
#5yrsago The EU’s copyright plans will let anyone mass-censor the internet https://www.eff.org/deeplinks/2018/09/how-eus-copyright-filters-will-make-it-trivial-anyone-censor-internet
#5yrsago Wanting It Badly Is Not Enough: Real Problems For Creators Deserve Real Solutions https://www.eff.org/deeplinks/2018/09/wanting-it-badly-not-enough-real-problems-creators-deserve-real-solutions
#5yrsago Woman World: the hilarious man-free apocalypse we’ve all been waiting for https://memex.craphound.com/2018/09/11/woman-world-the-hilarious-man-free-apocalypse-weve-all-been-waiting-for/
#5yrsago What developers need to do to save the internet from the EU’s looming copyright disaster https://github.blog/2018-09-10-how-developers-can-defend-open-source-from-the-eu-copyright-proposal/


10 notes
·
View notes
Text
i remember a few months ago i realized i'd completely forgotten the full disk encryption password for my laptop, which is isomorphic to total data loss (but with a functioning disk), so i get to do a live-fire test of my backups
fortunately everything worked, though i had a hard time finding the encryption key for my backups... (i pulled it off my old laptop)
7 notes
·
View notes
Note
to answer ur Linux question, dual boot default into Linux. you could also run a VM using QEMU with GPU passthrough if you have more than 1 GPU (but I dont expect that lol) or remote into a windows PC using smth like moonlight.
yeah i wanna do a dual boot that's usually the best option but also i can never be assed to shut down my computer and turn it back on, plus windows likes to fuck with boot settings.
also getting files from one instance to the other is a pain in the ass. Windows is encrypted with bitlocker and linux has LUKS. If i wanna send things from one side to the other.
I think i can use LibreCrypt to access the linux files (tool i didnt know about before but just found out, nice), but for bitlocker it seems to be kinda complicated (i'll figure it out) it just sucks to have to go through everything instead of just having it as like two disks together.
i hear theres full disk encryption over all (non-boot) partitions or through the bios but idk how well that is.
also storage space. i wanna get an 4tb drive or something like that and i really dont wanna fuck with partitioning more than i have to so i want to have a seperate physical drive for windows but then like how big do i wa-
i could totally do it. like theres not too much reason for me to not dual boot i'm just a whiney bitch
2 notes
·
View notes
Text
Speed Unleashed: Embrace Excellence with SSD VPS Server Hosting
In the fast-paced digital landscape, where every millisecond counts, the choice of hosting service can make or break your online presence. At our cutting-edge hosting platform, we understand the paramount importance of speed and reliability. This article explores the unparalleled benefits of SSD VPS Server Hosting, propelling your website to new heights in performance and user satisfaction.
Harnessing the Power of Solid State Drives (SSD)
In the realm of web hosting, speed is synonymous with success. Traditional hosting services often rely on Hard Disk Drives (HDD), which, although cost-effective, pale in comparison to the sheer speed and efficiency offered by SSD technology. SSDs use flash memory to store data, eliminating the mechanical delays associated with HDDs. This means faster data retrieval, quicker load times, and an overall seamless user experience.
Turbocharging Your Website
Picture this: a website that loads at lightning speed, capturing the user's attention instantly. With SSD VPS hosting, this is not just a dream but a reality. Our servers leverage the full potential of SSDs, ensuring that your website not only meets but exceeds user expectations. From e-commerce platforms to content-heavy blogs, the accelerated performance of SSD VPS hosting is the secret sauce for online success.
Reliability Redefined: The Robust Architecture of SSD VPS Servers
Virtual Private Servers (VPS) for Enhanced Stability
In the competitive online landscape, downtime is not an option. Unlike shared hosting, SSD VPS hosting provides you with a dedicated virtual environment, offering a slice of the server exclusively for your website. This not only enhances security but also ensures that the performance of neighboring websites has no impact on yours. Enjoy the benefits of a private server without the hefty price tag.
Advanced Hardware for Unmatched Reliability
At our hosting infrastructure, we prioritize reliability by investing in state-of-the-art hardware. Our SSD VPS servers boast high-end processors, ample RAM, and redundant storage solutions. This means that even during peak traffic, your website stands strong, delivering content without a hiccup. Say goodbye to the worries of server crashes and hello to a resilient online presence.
Unleashing Excellence: The Advantages of SSD VPS Hosting
Security is non-negotiable in the digital age. SSD VPS hosting takes security to the next level, with isolated virtual environments and advanced encryption protocols. Safeguard your data and user information with our fortress-like hosting solutions, providing you with peace of mind and building trust among your audience.
Scalability Tailored to Your Needs
As your online presence grows, so should your hosting capabilities. SSD VPS hosting offers unparalleled scalability, allowing you to seamlessly upgrade resources as your website evolves. Whether you're experiencing a sudden surge in traffic or planning for future expansion, our hosting solutions adapt to your needs, ensuring uninterrupted excellence.
Conclusion: Elevate Your Online Presence with SSD VPS Hosting
In the competitive digital landscape, the quest for speed and reliability is never-ending. With our SSD VPS hosting services, you're not just choosing a hosting provider; you're investing in a powerful ally for your online success. Embrace excellence, leave slow loading times behind, and propel your website to the forefront of the digital race.
2 notes
·
View notes
Text
Transformers: Prime- Mirage
Full prologue to this new mirage series imma start. Hahahaha im super excited to dig deeper into this universe! Especially for mirage. And this Oc im super proud of her. I’ll describe her description soon enough and i have art of her already :) without further ado, enjoy.

Gun and blaster fire surrounded them as Decepticons shot at the Iacon Hall of Records. Megatron led the front barking orders to his Decepticon lackies. Explosions echo as the door to the building. "Mirage, you copy? Are the cons in yet?" A female voice spoke into his audio receptors.
"Loud and clear Swifty," he muttered under his breath, "con are just busting in, you ready with evac?" He ran through the blaster fire to be the first to Iacon consoles. Quickly getting to work downloading bits of Iacons database down to a data chip. "Come on, come one. Hurry up!" Mirage pressed buttons on the consoles as he looks over the information as it comes in. "Scrap, its all encrypted..."
"Just get the info we will worry about the encryption later!" Swift exclaimed, "Just get as much info as you can and let's get out while we are ahead!"
"You can say that again..." Mirage sighed as he filled the data disk.
"At least Megatron won't get his hands on it... that's all we can ask for..." his eyes narrowed with the brisk flashback of the endless war. The lives of both Autobot and Decepticons he had already taken. All those flashing inside his head. "Mirage..." her voice brought him back to reality. "You alright?"
"Yeah... just thinking..." Mirage sighed, console beeped saying that the data disk was filled and made sure to make it seem like the Data never existed. Behind him, the door bashed open and there stood the Decepticon leader.
"You there! What are you doing!?" The mighty con stood tall, casting a shadow on the smaller Autobot.
"Why scourging the databases, my lord." His voice shook with his unease, hiding the data chip behind his back.
"Is that so? Was it, Mirage?" He chuckled as he looked at him, "Autobot turned Decepticon..." his words trailed as he took a step closer, "but are you really? What's behind your back, my humble servant." Megatron's voice was low and soft while his eyes glared daggers so sharp that if look were to kill, mirage would have been slaughtered.
"I know not of what you mean, Lord Megatron." Mirages calmed himself down as he eyes Megatron with great caution.
"Then please, show your hands." Megatron's tone became deep and dark. One could feel the venom coming from his metallic mouth. Mirage's eyes widened with shock, he gripped the data chip.
"Scrap...." He scoffed, mirage looked around briefly. Noticing a door to the side he could escape from. If he tells the truth or lies either way he's a goner. "Well~ it's been a good run. See ya on the flip side Megatron!" winking as he made a break for the side entrance.
"GET HIM!" Mirage hears the scream behind him as he ran down the hall as fast as his cybertronian legs could take him.
"Swift, evac now!" Mirage called out, as he ran through the building like a maze.
"I'm triangulating your location now! Just keep running and try to lay low!" Mirage huffed as he pressed himself to a wall, holding his breath as Decepticons ran by him.
"I'll do my best, the place is crawling with them..." he raised his arm and formed a blaster. He took soft steps, well... as soft steps a man made of pure metal could muster. He aimed his blaster and turned the corner in front was well a whole group of cons. Too many to just shoot down.
"There he is!" Mirage shot about 3 of the group before turning tail and running.
"Scrap, scrap, scrap!!" Mirage shot behind him knocking a few cons off their feet. "Swift!"
"Okay! I'm tracking you!" Her voice exhaled in relief, "I'll lead you to the front it will be hot but it is the only exit."
"Lead the way! I have a sea of cons behind me!" Sparks fly as he sharply turned the corner.
"Of course you do!" She audibly groaned. "Take the next right! It will lead you to a fork where you can confuse them!"
"Alrighty~ time to flex my stuff!" He sharply turned the right and in a haze of blue light, two clones ran alongside him. As the fork quickly approached, "yeah, baby! Alright, now where I'm heading?"
"To the left! after that make another left!" He chuckled as he hopped between his clones, mixing them up before heading down the left path. Smirking as he listened to his pursuers' confusion on who to follow.
"Haha! Get fragged you buckets of the bolt!" He continued on, shooting any others he runs into along the way. "Kay, Swift! Entrance in sight you ready!"
"As ready as you are Mirage!"
"Alrighty then..." he took a deep breath as the door only became closer. blocking and weaving through enemy fire. "Let's bail this heap, hell maybe some time away from the war will be nice~"
"MIRAGE!" the mighty roar of Megatron called from behind him, barreling to him once again a sea of Decepticons. "GET THAT CHIP!" mirage smiled as he slowed down at the courtyard's center outside the halls. Smiling and shooting to the hoard of 'Cons.
"Not now, Not ever~" mirage winked as he extended his hand and grabbed the open hatch of his escape ship. "Oh yeah! What a rush!!"He let out a boisterous laugh as he climbed in. As he enters the door, he sees his partner in crime seated in the pilot's seat. Ship speeding off away from the Decepticons. "Wasn't that great Swift! The whole thing went off without a hitch!"
"but now... our home is lost." Swift's blue eyes narrowed as ahead of them rested the remains of what once was their home. "Megatron won... and took everything down with him." She pressed a button, turning on autopilot. Standing up from the chair, she walked to Mirage. "I'm just glad you're okay... The data chip?" Swift smiled softly as she gently grasped his arm. Mirage sighed as he gave her the chip. "For all we know this might be the only info left of Cybertron's salvation..."
"Woah... calm down." Mirage placed a hand on her shoulder, "You heard Prime's message, all we have to do is survive to see it." He smiled at her, trying his hardest to lift his partner's spirits. She takes the chip back to the seat and views its content through a port on the ship.
"I hope we do..." she sighed, as she tried to make sense of the data it is heavily encrypted. "how are we going to make this data useful?"
"I can decode it." Mirage took his seat in the co-pilot's chair. "It will take me a long, long time... but I can do it.."
"Well," she grabs onto the flight controls, "lucky for us, we have plenty of time and energon... for now."
#transformers rise of the beasts#transformers prime#transformers#mirage transformers#rotb mirage#mirage#tfp
19 notes
·
View notes