#disk encryption
Explore tagged Tumblr posts
Text
VeraCrypt
Security on your device is crucial, especially if others frequently use your machine. VeraCrypt is an application designed to secure and encrypt partitions, ensuring sensitive files remain protected. The program is highly customizable, offering a variety of options. When you open VeraCrypt, you’ll find a simple interface, which some may consider outdated, guiding you through the available…
#Data Privacy#data security#disk encryption#disk encryption software#encryption#full disk encryption#password protection#secure data#VeraCrypt#volume encryption
0 notes
Text
How to encrypt your Data with Trellix Data Encryption
Trellix Data Encryption offers a full range of products to safeguard data and devices from unauthorized access. In this article, we will discuss how to encrypt your Data with Trellix Data Encryption. Trelix also makes it possible to protect corporate-owned devices and shared servers with comprehensive encryption and integrated centralized management. Please see How to upgrade Trellix ePolicy…

View On WordPress
#Automatic Device Encryption#Disk Encryption#Encryption#Microsoft Windows#Trellix#Trellix Agent deployment#Trellix DE#Windows#Windows 10#Windows 11#Windows Server#Windows Server 2012#Windows Server 2016#Windows Server 2019#Windows Server 2022#Windows Server 2025
0 notes
Text
they say that there's a point where you can have too much security and it impedes the usability of a system—however i'd like to commend online banking platforms for somehow simultaneously having security measures that make them incredibly inconvenient to use every day, whilst also offering fairly low actual security and being not particularly difficult to bypass if you're dedicated enough
#like none of the online banking platforms ive used have let me use an actual password?#nor do they let me set up 2fa with an authenticator app besides their own proprietary banking app#they all seem to send all verification codes by sms with the only way to authenticate otherwise is through their proprietary apps. which i#am not installing.#also perhaps this serves some purpose i dont understand but why do they frequently ask for the nth character of your pin or whatever#instead of asking for the whole pin?#like all the 'password' equivalents seem very easy to bruteforce and the sms verification can be bypassed by someone else just getting a#sim card for your number#and the fact that they never keep you logged in is annoying like i have full disk encryption on all my devices im not worried about someone#using my own device to access my bank account. i dont particularly think theres anyone trying to get into my bank account but if there were#they'd be getting in through their own device not mine... you can keep me logged in on mine...
6 notes
·
View notes
Text
I’m like if a girl had OneHalf installed on her Master Boot Record..
#blue chatter#Functionally very similar but Something’s going on in there that u can’t see#OneHalf is a computer virus which infected .exe files of MS-DOS computers#It wrote a decryption key to the master boot record#as well as instructions to encrypt the last two unencrypted sectors of the hard disk upon startup#it was found in the wild in 1994#removing OneHalf without a specialized tool completely bricked your computer depending on how long you had it#bc if you attempted to install a clean copy of the MBR without carefully decrypting your encrypted data first#there’d be no way to unencrypt your files and you’d be screwed
3 notes
·
View notes
Text
It's Just a Game, Right? Pt 8
Masterpost
"So I think they're using other languages," Tim says, the moment Bernard opens the door.
"Well hello to you too my beloved boyfriend," Bernard responds, kissing Tim on the cheek and pulling him into the apartment.
"Shut up," Tim says, following Bernard to the table. This is hardly the first time Tim has skipped past pleasantries like that, and Bernard seems to find it more amusing every time.
"Aw, I dunno if I can do that. I really like to talk to you," Bernard grins conspiratorially. "Plus, then I wouldn't get to tell you that you're half right."
"What do you mean?"
"Well, obviously other people noticed the comment, right?" Bernard, gestures towards the computer, where Tim can see the cryptic comment. It already has dozens of responses. "Mostly people are just freaking out about it, because this is like, our first instance of direct communication from them, but one of the people who saw it actually recognized what language it is."
"Just one?" Tim frowns.
"Yeah. It's called esperanto. I googled it and apparently it's a conlang from the late 1800s which is pretty cool. It was, like, invented to be kind of a universal language, I guess? It pulls from a lot of different languages, so that's why it looks like multiple languages."
"Huh."
"But! There's still the encoded portions to figure out, because the translation as-is doesn't really make any sense." Bernard scrolls and points to the translation that a commenter had offered. It reads To be fqzuhsx-ayccas is to be qtdkv-avnwkwkb; the veil afph-gqkduik but it is meant to igpmtwi-ocdq. Determination in the face of doubt.
"Huh," Tim studies the text, then notices something. "They've specifically encoded the verbs."
"Yep," Bernard shrugs. "I haven't tried anything for the encrypted stuff yet; figured i might as well wait for you."
"Okay, well I guess we start with the simplest? We know they've used caesar ciphers before, plus this is in response to what we did with the first caesar ciphers before, so we might as well try one of your decoder websites for that first."
"Seems reasonable," Bernard says, pulling up the website from before. He quickly copies the first word over and hits the button. "Well shit, that was quick."
"Only the first half, though." Tim mutters. "Do it to the rest of them." Bernard copies and decodes the rest. In short order, they have a the first half of each encryption decoded.
"To be gravity is to be orbit, the veil disk but it is meant to eclipse?" Bernard frowns. "That... doesn't make much more sense."
"What's up with the focus on astronomy, too."
"Oh, right, we haven't gotten that far yet. They keep referencing space stuff. There's like, a running theory about these messages being supposed to have come through a black hole?"
"Is that even possible? i thought black holes ate stuff forever."
"I dunno, I'm not really into space stuff. Besides it's like, sure there's evidence for it, and space seems to be narratively important? But the premise seems kind of contrived to me."
"You think they're doing something bigger than what everybody is seeing." Tim stares at the forum thread. If anything was going to give Bernard's theory some credence, it would be what literally just happened.
"Exactly." Bernard posted on a forum arguing that he thought the game ran deeper than people realized. And the creators, who so far hadn't interacted directly, had responded to that post, with a triple-encrypted message.
"Each shift was one further away than the last," Tim thinks rapidly. "It started with language, which could be either a part of the effort to encrypt it, or a part of the intended meaning. Possibly both. Then, they used caesar ciphers for the first layer of encryption, the same thing they used in their first post. How did they encrypt things in the second post?"
"I think I kind of mentioned it before, but the second post used a vigenere cipher. The names of the people in the first video were the keys, if I remember right."
"The first is the key to the second."
"What-"
"Take the second part and decode it with the first."
"Dude your mind is scary sometimes," Bernard laughs, but moves to do as Tim says, revealing the first encrypted word. "To be seen. That works..."
Tim starts writing down the full message, as Bernard decodes the rest. Finally, they have the full text of the message the creators intended to send.
"To be seen is to be remembered; the veil distracts but it is meant to hide. Determination in the face of doubt." Tim reads.
"Huh," Bernard says, leaning over to read it for himself. "Well, now we know what it says. Now we just need to figure out what that means."
#dp x dc#the one where the amity parkers make an arg#this part got long lol but i didnt wanna leave off in the middle of them solving the riddle#i put so much thought into this message and its encryption#its v hard to tell from the inside if youre actually making something that it's reasonable for ppl to solve#but luckily i get to just give you guys the solutions!#though as this goes on they are gonna get harder#eventually they wont be given and solved in the same post lol#so have fun looking forward to that i guess
195 notes
·
View notes
Text
Some Science Vocabulary

for your next poem/story
Word — Science Meaning; Public Meaning
Bank - land alongside a river/lake; a place where people store money
Bar - unit of measure of atmospheric pressure; place to drink alcoholic beverages
Belt - collection of asteroids in a disc shape; materials worn around waist to support clothes
Bonding - electrostatic attraction between atoms; making an emotional connection
Charge - force experienced by matter when in an electromagnetic field; demand a price for rendered goods/services
Code - software/computer language; encrypted message
Crust - outermost layer of planet; edge of pizza/pie
Current - water or air moving in a direction; belonging to the present time
Cycling - flow of nutrients or elements; riding a bicycle
Dating - determining age of site/artifact; initial stage of romantic relationship
Driver - influential factor; someone who drives a vehicle
Dwarf - celestial body resembling small planet; characters from Snow White
Fault - fracture in a rock with movement; responsible for accident/misfortune
Fetch - distance traveled by wind/waves over water; go far and then bring back something/someone
Force - strength/energy of action/movement; make someone do something against their will
Grade - gradient/slope; level of proficiency
Hertz - the SI unit of frequency; rental car company
Jet - gas stream ejected from an accretion disk surrounding star; an aircraft powered by jet engines
Mantle - planet layer between crust and core; important role passed from person to person
Matter - physical substance in general; be of importance, have significance
Model - computer simulation; promotes fashion/product
Mole - SI unit used to measure amount of something; small rodent-like mammal
Plastic - substance that is easily shaped/molded; synthetic material
Pressure - force per unit area that gas/liquid/solid exerts on another; use of persuasion to make someone do something
Productive - creating organic matter through photo/chemosynthesis; busy and efficient
Sample - to take a sample for analysis; a small part of something
Scale - system of marks used for measuring; device used for measuring weight
Shear - difference in wind speed/direction; cut wool off of
Shelf - a submarine bank; a surface for displaying/storing objects
Stress - pressure/tension exerted on a material object; mental/emotional strain
Submarine - existing/occurring under the sea surface; a ship that stays submerged under water for extended periods
Surf - line of foam on seashore from breaking waves; riding a surfboard
Swell - sea movement in rolling waves that do not break; to become larger in size (e.g. a body part)
Source ⚜ More: Word Lists
#word list#science#writeblr#spilled ink#dark academia#writing reference#writers on tumblr#literature#writing prompt#poetry#poets on tumblr#langblr#linguistics#light academia#creative writing#writing inspo#writing ideas#writing inspiration#terminology#writing resources
119 notes
·
View notes
Note
what is the best way to get safer/more anonymous online
Ok, security and anonymity are not the same thing, but when you combine them you can enhance your online privacy.
My question is: how tech literate are you and what is your aim? As in do you live in a country where your government would benefit from monitoring private (political) conversations or do you just want to degoogle? Because the latter is much easier for the average user.
Some general advice:
Leave Windows and Mac operating systems and switch to Linux distributions like Fedora and Ubuntu (both very user friendly). Switch from Microsoft Office or Pages/Numbers/Keynote (Mac) to LibreOffice.
You want to go more hardcore with a very privacy-focused operating system? There are Whonix and Tails (portable operating system).
Try to replace all your closed source apps with open source ones.
Now, when it comes to browsers, leave Chrome behind. Switch to Firefox (or Firefox Focus if you're on mobile). Want to go a step further? Use LibreWolf (a modified version of Firefox that increases protection against tracking), Brave (good for beginners but it has its controversies), DuckDuckGo or Bromite. You like ecofriendly alternatives? Check Ecosia out.
Are you, like, a journalist or political activist? Then you probably know Tor and other anonymous networks like i2p, freenet, Lokinet, Retroshare, IPFS and GNUnet.
For whistleblowers there are tools like SecureDrop (requires Tor), GlobaLeaks (alternative to SecureDrop), Haven (Android) and OnionShare.
Search engines?
There are Startpage (obtains Google's results but with more privacy), MetaGer (open source), DuckDuckGo (partially open source), Searx (open source). You can see the comparisons here.
Check libRedirect out. It redirects requests from popular socmed websites to privacy friendly frontends.
Alternatives to YouTube that value your privacy? Odysee, PeerTube and DTube.
Decentralized apps and social media? Mastodon (Twitter alternative), Friendica (Facebook alternative), diaspora* (Google+ RIP), PixelFed (Insta alternative), Aether (Reddit alternative).
Messaging?
I know we all use shit like Viber, Messenger, Telegram, Whatsup, Discord etc. but there are:
Signal (feels like Whatsup but it's secure and has end-to-end encryption)
Session (doesn't even require a phone or e-mail address to sign up)
Status (no phone or e-mail address again)
Threema (for mobile)
Delta Chat (you can chat with people if you know their e-mail without them having to use the app)
Team chatting?
Open source options:
Element (an alternative to Discord)
Rocket.chat (good for companies)
Revolt.chat (good for gamers and a good alternative to Discord)
Video/voice messaging?
Brave Talk (the one who creates the talk needs to use the browser but the others can join from any browser)
Jami
Linphone
Jitsi (no account required, video conferencing)
Then for Tor there are various options like Briar (good for activists), Speek! and Cwtch (user friendly).
Georestrictions? You don't want your Internet Provider to see what exactly what you're doing online?
As long as it's legal in your country, then you need to hide your IP with a VPN (authoritarian regimes tend to make them illegal for a reason), preferably one that has a no log policy, RAM servers, does not operate in one of the 14 eyes, supports OpenVPN (protocol), accepts cash payment and uses a strong encryption.
NordVPN (based in Panama)
ProtonVPN (Switzerland)
Cyberghost
Mullvad (Sweden)
Surfshark (Netherlands)
Private e-mails?
ProtonMail
StartMail
Tutamail
Mailbox (ecofriendly option)
Want to hide your real e-mail address to avoid spam etc.? SimpleLogin (open source)
E-mail clients?
Thunderbird
Canary Mail (for Android and iOS)
K-9 Mail (Android)
Too many complex passwords that you can't remember?
NordPass
BitWarden
LessPass
KeePassXC
Two Factor Authenticators?
2FAS
ente Authenticator
Aegis Authenticator
andOTP
Tofu (for iOS)
Want to encrypt your files? VeraCrypt (for your disk), GNU Privacy Guard (for your e-mail), Hat.sh (encryption in your browser), Picocrypt (Desktop encryption).
Want to encrypt your Dropbox, Google Drive etc.? Cryptomator.
Encrypted cloud storage?
NordLocker
MEGA
Proton Drive
Nextcloud
Filen
Encrypted photography storage?
ente
Cryptee
Piwigo
Want to remove metadata from your images and videos? ExifCleaner. For Android? ExifEraser. For iOS? Metapho.
Cloak your images to counter facial recognition? Fawkes.
Encrypted file sharing? Send.
Do you menstruate? Do you want an app that tracks your menstrual cycle but doesn't collect your data? drip.
What about your sexual health? Euki.
Want a fitness tracker without a closed source app and the need to transmit your personal data to the company's servers? Gadgetbridge.
34 notes
·
View notes
Text
The Brain and The Brawn



Word Count: 1.8K Summary: Seungmin didn’t trust easily. He had no reason to. He’d seen the system’s corruption up close, the people who were supposed to protect others turning into predators. And you? You had once been one of them. A part of the very machinery they now fought against. Pairing: Seungmin X fem reader
Disclaimer: Please be aware that this is apart of the from the ashes series. This series will have aspects of violence, weapons, angst, blood, injuries, killing, and will heavily focus on oppression and segregation of mutants, Look after your mental state if any of these make you uncomfortable please.
Series Masterlist
Navigation
The dim light of the underground base flickered as Seungmin sat hunched over a row of computer screens, his fingers flying over the keyboard. Lines of code scrolled rapidly, the soft hum of machines filling the room. His mind was in hyperdrive, always processing multiple tasks at once. His sharp, focused eyes were the perfect contrast to the rest of the chaotic resistance base.
He didn’t need to look up to know when you entered the room. The air shifted slightly, and your boots made the faintest click on the concrete floor. He could feel the weight of your presence before you said a word.
You were the type to operate in the shadows—quiet, efficient, dangerous. Your past was a mystery to everyone here, except for Seungmin. He knew you’d been part of the system, the very one they were fighting against now. That didn't sit well with him.
“Got something for me?” he asked without looking up, his voice cold, betraying none of the thoughts racing in his mind.
You stepped closer, setting down a small, encrypted disk on the table beside him. “I got us the location of their main server. It’s in the city’s heart. We take it down, we hit them where it hurts.”
Seungmin’s eyes flickered to the disk, then back to the screen. "You’ve been through the system’s firewalls before," he said flatly, a hint of suspicion in his tone. "This isn’t the kind of information just anyone can steal."
“You know I’m good,” you replied, your tone even, but with an undercurrent of steel that made Seungmin raise an eyebrow. "This will work. Trust me."
Seungmin didn’t trust easily. He had no reason to. He’d seen the system’s corruption up close, the people who were supposed to protect others turning into predators. And you? You had once been one of them. A part of the very machinery they now fought against.
But despite his reservations, he couldn’t deny it. Your information had always been spot on. Your skills were unmatched, and your knowledge of their operations was invaluable.
Still, he hated that part of you—your past, the one that linked you so directly to the system they were trying to take down. Seungmin wasn't one for forgiveness, but he couldn’t help but admire the way you seamlessly blended into the resistance.
“I’ll crack it,” Seungmin finally muttered, his fingers pausing over the keyboard. He was never one to admit it, but your presence was a force. “But this better not be another dead end, Y/N.”
You didn’t flinch at his words. Instead, you stood beside him, watching his every move. You knew exactly how to stay out of his way and when to push him just enough to get things done. The dynamic between the two of you was strange. Unspoken, yet undeniably effective.
“I don’t make mistakes.” The confidence in your voice was almost eerie.
Seungmin chuckled darkly, his gaze lifting just for a moment to meet your eyes. “That’s the problem. You think you’re invincible.”
“And you’re too stubborn to admit when you need help,” you shot back.
He rolled his eyes, but there was a smirk tugging at his lips now. “We’ll see about that.”
As he began to type, the room went quiet again, save for the rhythmic clacking of keys and the steady beeping of the machines. Every now and then, Seungmin would glance over at you, catching the subtle tension in your posture, the way you never quite let your guard down.
It wasn’t easy, working with someone who had so much of the system’s blood on their hands. But somehow, you were making this partnership work. And despite everything, Seungmin found himself trusting you more than he would have liked.
“You’ll be good on the ground?” Seungmin finally asked, his voice low.
You nodded, unflinching. “I’m always good on the ground. And I’m not about to let you do all the work, hacker.”
“I never do all the work,” he muttered, focused on the screen. “But I’ll make sure your job’s easier this time.”
His fingers flew over the keys, cracking through layers of security as he went. You leaned over slightly, watching his quick movements, his mind working like an intricate machine of its own. You had always admired how he could think on his feet, how seamlessly he could break into systems that were supposed to be impenetrable.
But this mission wasn’t just another data breach. If they succeeded, they would be closer to bringing down the system once and for all.
Seungmin took a breath, finally cracking the final code. The screen flickered, displaying the server's location—a heavily fortified building in the heart of the city.
"We’re in," he said, his voice steady, but a rare hint of satisfaction in his eyes.
You gave him a nod, your gaze unwavering. "Time to end this."
The night was eerily quiet as you and Seungmin approached the heart of the city, the building looming ahead like a fortress. The air was thick with the hum of the city, but in this part, the streets were empty—intentionally, perhaps. The resistance had done their best to cover your tracks, but everyone knew the risks. No matter how good Seungmin’s hacking was, there was always the chance of getting caught.
Seungmin glanced over at you, his eyes sharp behind his glasses. "You ready for this?" His voice was low, betraying just a hint of the nerves he never showed in the safety of his hacker den.
"Always," you said, the familiar, determined glint in your eyes returning. "We’ve got this."
The plan was simple: infiltrate the building, disable the security system long enough for Seungmin to upload the virus to the main server, and get out before the reinforcements arrived. But simple plans often fell apart under pressure.
You both crouched near the entrance, a faint blue glow from Seungmin’s tablet illuminating his face. "I’m starting the hack," he said, fingers already moving with practiced precision. "But we’re on a time limit. Once the system detects the intrusion, they’ll lock the entire building down. We’ve got less than 10 minutes before that happens."
"Got it. I’ll make sure we’re not interrupted," you responded, checking your gear one last time.
Without a sound, you slipped through the door, your steps quick and silent. You were the one who’d handle the physical side of things while Seungmin worked his magic. The tension between you was palpable; every step you took brought you closer to the danger you knew awaited inside.
The hallway stretched before you, its fluorescent lights flickering ominously. You moved swiftly, already scanning the surroundings for any guards.
"Five minutes," Seungmin's voice crackled through the comms in your ear, pulling you out of your thoughts.
“Stay focused,” you muttered to yourself, slipping into an alcove as a pair of guards walked by. You held your breath, waiting until they were gone before moving on.
You had grown accustomed to moments like this—when life and death were separated by a single heartbeat—but there was something different about this mission. The stakes were higher, the pressure more intense. If Seungmin failed, it wouldn’t just be a loss for the resistance; it would be a failure that could cost both of you everything.
A soft beep came from your comms, Seungmin’s voice flooding through, tight with urgency. "I’ve got the code in—almost there. Just hold out a little longer."
"I’m not going anywhere," you replied, voice steady, but adrenaline coursing through your veins.
The server room was just ahead. Your pulse quickened as you approached, eyes scanning for any movement. You were almost there. The last guard was stationed at the door, and you could see his back turned, his attention elsewhere. It was now or never.
You moved swiftly, the knife in your hand gleaming under the harsh light. A quick, precise strike to his pressure point, and he collapsed to the floor, unconscious before he even had a chance to react.
“Clear,” you whispered into your comms. “Get in here, Seungmin.”
The door slid open with a hiss, revealing the massive server bank that controlled everything. Seungmin was right behind you, tablet in hand. His face was tense, but he wasted no time getting to work.
"Time’s up," Seungmin muttered, fingers flying across the screen as he initiated the virus upload.
“Five minutes until they lock us in,” you reminded him, your eyes scanning the room for any more guards.
“Noted.” His voice was sharper now, focused entirely on his task.
But you could feel it—the shift in the air. You weren’t alone anymore. The sound of boots on the metal floor echoed through the room, getting closer.
"Seungmin, they’re here," you hissed, drawing your weapon as you prepared for the confrontation.
Seungmin didn’t even flinch, his attention solely on the tablet as he typed furiously. "Just hold them off for a few more seconds."
You heard the door behind you slam open, followed by the distinct sounds of armored boots hitting the ground. You didn’t hesitate—moving like a shadow, you lunged toward the closest guard, disabling him with a swift strike to the throat. Another one appeared, but you dodged, twisting to deliver a punch that sent him crashing to the floor.
The fight was chaotic—Seungmin was still focused on the upload, his fingers moving faster than you thought possible. The guards were relentless, but you were faster. Every move was calculated, every strike a testament to your experience.
But as the seconds ticked by, the numbers stacked against you. Another guard lunged at you from behind, forcing you into a desperate roll to avoid a deadly blow. The world slowed for a moment, everything feeling like it was hanging by a thread.
“Seungmin!” you shouted as you spun to face the oncoming attacker.
He didn’t reply, still absorbed in his task. But you saw it—the final piece of code he was entering. A few more seconds.
A sharp pain shot through your side as a guard’s baton connected with you, but you didn’t falter. With a determined roar, you took out the last guard in your path, then turned toward Seungmin. The virus was almost in.
“Done,” Seungmin said, eyes finally lifting from his tablet. His gaze met yours, and for a split second, you saw something shift in his expression—relief, maybe a little admiration. "We’re out of time, let’s go!"
You didn’t need another word. You dashed for the door, Seungmin following close behind. But the second you stepped into the hallway, alarms blared—louder, more insistent than before. Red lights flashed, signaling that the building was on lockdown.
“You said five minutes!” you growled, but Seungmin wasn’t fazed.
"Guess we’re cutting it close." He gave a quick, crooked smile. "Follow my lead."
And as you both ran through the corridors, dodging guards, taking desperate risks, one thing was clear: the mission was only the beginning. Now, it was all about getting out alive.
#stray kids#stray kids x reader#stray kids imagines#stray kids fluff#stray kids fanfic#skz imagines#skz x reader#skz fanfic#skz fluff#skz scenarios#skz#kim seungmin#seungmin imagines#seungmin x reader#seungmin stray kids#seungmin skz#seungmin fluff#kim seungmin x reader#Fromtheashesseries
25 notes
·
View notes
Text
TECH MOMENTS PT. 6
The Bad Batch S1 E2: Cut and Run

- “That would be dirt.”
- The way that he kind of smirks when he points out that they're deserters to Echo. Like he's almost proud of that fact. ❤
- The way he immediately starts paying attention when Omega speaks up about the inhibitor chips.
- “How else did you think it worked?” ❤
- I love that he looks up to watch how happy the kids are with Wrecker.
- Tech RUNS when he hears Omega is out past the fence.
- HE LOOKS UPSET WHEN OMEGA IS APOLOGIZING. ❤
- The worried look he gives Omega as Cut carries her away.
- “All in all, I would say that could have gone much worse.” ❤
- Hunter: "Tech, you think you could forge some chain codes?"
Tech: "I only learned of them moments ago, but yes." ❤
- I love his pose, leaning back against the navicomputer, looking down at his datapad… I adore him.
- “It’s… ingenious.”
- “Already thought of that.”
- Echo: “You’re suggesting we call the authorities and have them seize our ship?”
Tech: “That is exactly what I am saying.” ❤
- "This was the simplest solution."
- "I have this under control."
- He looks genuinely concerned when he realizes that he roped Omega into his plan.
- The way he’s bracing himself above Omega to look out the hatch and down into the ship. He’s so subtly protective of her, and I love it.
- I NEVER NOTICED THAT HE STRAIGHT-UP FLIPS OVER OMEGA AND OUT THE HATCH! Show off. ❤
- Waving Omega down so he can catch her. Something about that little movement drives me crazy.
- He barely strains at all when she lands in his arms, my man is strong! ❤
- “Excellent.” ❤
- "In progress. The encryption shouldn't be a problem."
- “Don't worry. I can slip through security unnoticed and deliver the disks to you momentarily.”
- “Found her.” His eyes look like he’s smiling. ❤
- He looks a little irritated by Echo’s jabs, but he knows better than to snap back, especially after all these years dealing with Crosshair.
- “We cannot get caught with these chain codes.” His EYES. Beautiful!
- “Well, we didn’t let her go. She ran off on her own.”
- "What is taking so long with the boot? Are you trying to get caught?" ❤
- He must have run outside SO fast to get that trooper who found Echo, which was an epic moment. ❤
- “That is not ideal.”
- “Hunter, we have worn out our welcome. We need to go right now.” Sir, how are you always so calm?
- Putting up his blasters for a second to watch when Hunter joins the fight.
- “Glad you could make it.” ❤
- Shooting as he runs onto the ship.
BONUS: GIFs of my favorite 10 seconds of the episode


#tech moments#tech tuesday#the bad batch#tbb#sw the bad batch#star wars tbb#bad batch#tbb tech#star wars#sw tbb#tech bad batch#tech tbb#bad batch tech
34 notes
·
View notes
Text
Hi yes I would like to start down this rabbit hole please because I'm totally normal about this ... I am convinced Jon and Martin are part of a tape drive. It links with the tapes from TMA and the trailer for TMP especially with the opening computer screen (I already posted about my thoughts on that).
What is a tape drive?
A tape drive is a device that stores computer data on magnetic tape, especially for backup and archiving purposes. Like an ordinary tape recorder, a tape drive records data on a loop of flexible celluloidlike material that can be read and also erased.
Tape drives differ from hard disk drives (HDDs) and solid-state drives (SSDs) in the way data is read and written to the storage media. Tapes store data sequentially, whereas HDDs and SSDs use rotating disks with rapidly moving seek heads, nonmoving flash memory or similar technology to transfer data.
Drives come in many sizes and capabilities. They are sold as standalone units or stacked in data center racks, creating tape libraries. The tapes themselves are often housed in sealed cassettes that can be inserted into the drive and activated.
There are several benefits to using tape drives, particularly for backup and archival uses. They include the following:
Capacity. Tapes have a large capacity for storing data when compared to HDDs.
Low cost. They are economical when compared to other storage media.
Life span. Tapes stored in a suitable environment can last for decades, an important factor for archival storage.
Transportable. Tapes can be easily moved from one location to another and are considered off-line storage.
Disaster recovery. Tape is often the storage medium of choice for data backup and DR. Storing critical systems and data on tape creates an air gap between systems that are at risk from cyber attacks simply by removing the tape cassette from the drive.
Security. Today, tapes support encryption such as Advanced Encryption Standard-256 and provide varying levels of data protection.



#the magnus archives#martin blackwood#jonathan sims#tma#jonmartin#the magnus protocol#magnus pod#tmp#tmp theory#jon sims#jmart#jonny sims#tape drive#tapes!#jmart is in the tapes!
191 notes
·
View notes
Text
Manage BitLocker and FileVault with Trellix Native Encryption
In today’s enterprises, the proliferation of data and devices has heightened the complexity of safeguarding confidential information and adhering to compliance requirements. With substantial amounts of data stored on PCs, tablets, and other devices. Ensuring the security of sensitive data has become more critical than ever. In this article, we shall discuss How to Manage BitLocker with Trellix…

View On WordPress
#Disk Encryption#Full Disk Encryption#Full Disk Encryption (FDE)#Insight to Full Disk Encryption#MacOS#macOS Big Sur#macOS Monterey#macOS Ventura#Microsoft Windows#Windows#Windows 10#Windows Server#Windows Server 2012#Windows Server 2016#Windows Server 2019#Windows Server 2022#Windows Server 2025
0 notes
Text
Random Cog Headcanons: Memories
I'm back again with a slightly shorter yap than the last one, this time focusing on how suits process and store memories! Tried to go for the bullet point format again since my last post was pretty dense. Summary: Suits have different kinds of memories, with the two main kinds being consolidated and unconsolidated. Both serve different purposes and function in different ways, allowing suits to balance the preservation of disk space with the preservation of detailed memories deemed to be the most important.
The memories of suits are all contained in memory chips connected to a memory processor that interprets, sorts, and consolidates memories. ⠀
>> Damage to the former can result in loss of current memories, while damage to the latter can cause impairments forming new memories. ㅤ
Memories are immediately processed in a 1:1 visual form, but are quickly stripped down to the essentials and encrypted for the sake of both data security and saving valuable disk/memory space. This process is known as memory consolidation. ⠀
Due to this process, cogs often cannot 'replay' moments in their minds, especially if they're mundane. They may intuitively know what happened, when it happened, how it happened, how it made them feel, etc., but it's not like they're mentally seeing it. ⠀ㅤ
That being said, if a moment is really important to a suit, they can consciously choose to record memories and keep them in their original form. It's a sacrifice of space, but if it's something they really want to remember and be able to play back with every present detail, it might be worth it. Real wholesome potential for that, honestly. Though there's painful potential there, too. ⠀ㅤ
>> For example, some may choose to save precious moments from their wedding day, while others can’t stop mulling over a nasty breakup, unable to decide if they should just consolidate those old memories for their own good. Video evidence of workplace misconduct always makes reports stronger, too, so there’s that. ㅤ
>> Given that any process can be subject to malfunction, it may be possible under some circumstances for a memory to be unable to be consolidated by no fault of the suit themselves. This could, in theory, result in PTSD-like flashbacks when the memory is triggered (though that doesn’t mean consolidated memories cannot also be traumatic). ㅤ
Memories that have not been encrypted and consolidated can be accessed and shared between suits if desired. Typically, they are just transferred to an external device and projected in a video format, as one would a normal file. ⠀
Emotional data in unconsolidated memories is ignored when processed by normal machines, such as an office computer or projector, but can be experienced by another directly if two suits link up. ⠀ㅤ
The process of linking up is quite literal, being a wired or wireless connection established between two or more suits. Wired is most common, though some fancier suits may have some equivalent to Bluetooth. ㅤ
Because all memories start out as unconsolidated and unencrypted, it’s possible to feel another’s emotions or experiences in real time through linking up as well if that happens to be the goal. ㅤ
Linking up is considered to be very intimate, but typically non-sexual. It can occur among trusted friends or family in addition to partners. ㅤ
Linking up will not work if one or more parties does not want to participate. It is by definition two or more machines communicating with one another, with information requests going back and forth that can be easily denied at any time. ㅤ
Memory chips are physical, and are therefore subject to degradation and/or reorganization over time. Consolidated memories may lose some factual details or end up purged for space if deemed unimportant, while unconsolidated memories that are exceptionally old may begin to have a decrease in clarity or become a bit fuzzy, as if recorded on an old camera.
18 notes
·
View notes
Text
i can do better than that previous poll. 1 point per recommendation followed, interpret conservatively.
automatic backups (and tested!!)
ransomware resilient
2nd factor on all important accounts
2nd factor, not sms, phishing resistant everywhere where feasible
unique passwords on all important accounts
unique passwords everywhere
bitlocker/full disk encryption and secureboot
bonus point for measures not listed (tags plssss)
26 notes
·
View notes
Text

Palm Disk Ink Art from page 72 of The Mutant Epoch RPG Expansion Rules
These were the most common housings for digital beings and often serve as the core CPU container within larger vessels. Palm disks come in many shapes and sizes but generally perch in an open hand, on a shelf, in a vehicles cup holder or back pocket.
These disks sometimes feature a bonus add-on. Roll 1d10. 1-3. No add-on.
Waterproof and will float if dropped in liquid.
Pop out spider legs: climbing 3 skill points, movement rate 4m, scratch opponents SV +0, DMG 1pt
Extra encryption: Improved firewall bonus of -20 FW.
Ultra memory: Can contain 150TB of data
Military Grade Toughness: Add +2d6 Endurance and increase DV by -13.
Pop out rotors: This unit can fly like a small drone, although makes the same amount of noise as a bumblebee when active. Movement rate 12m, with flight duration 1 hour before a 12 hour recharge period must take place. While flying, increase defense value -20 DV.
Two add-ons (roll 1d6+3, twice on this table but down-pick or re-roll duplicated results).
New to the Mutant Epoch RPG? Grab the free quick Start rules PDF and the included Adventure, ‘Muddy Mayhem’: https://www.outlandarts.com/qsr.htm
#palmdisk#cowboy#hologram#palmprojector#digicowboy#digitalbeing#AIentity#selfaware#computerized#hand#projector#relic#cowpoke#mutantepoch#apocalyptic#expansionrules#postapocalyptic#themutantepoch#outlandsystem#RPG#ttrpg#outlandarts#mutants#mutant#epoch#wastelandweekend#inkartist#gameart#rpgart#TME
6 notes
·
View notes
Text
CrowdStrike'd and BitLocker'd
With yesterday's CrowdStrike outage. I'm sure a number of you are probably wondering "what does BitLocker have to do with any of this?" Well, it all has to do with an added layer of security many organizations use to keep data from being stolen if a computers ends up in the hands of an "unauthorized user."
To start, let me briefly explain what the CrowdStrike driver issue did and what the fix for it is.
After the update was automatically installed to computers running the CrowdStrike Falcon Sensor, a faulty driver file caused the Windows kernel on those computers to crash and display a Blue Screen of Death. How Windows typically handles a crash like this is to create a crash log file, then perform a reboot. Since this driver would launch shortly after Windows finished booting, it would cause the operating system to crash and reboot again. When two crashes have occurred in sequence, Windows will automatically boot into Recovery Mode. Hence why we say several pictures of the Recovery Mode screen across social media yesterday.

Unfortunately, this update was automatically pushed out to around 8.5 million computers across several organizations, causing widespread chaos within the matter of a few hours. And the fix for this issue had to be performed by physically accessing each computer, which required those of us working in I.T. to have to run around several facilities, locate each affected computer, and apply the fix one by one.
The short and simple of the fix is either one of two options. You can either use the Recovery Mode that Windows was already booted into to navigate to Start-Up Setting, and launch Safe Mode. Once Windows boots into Safe Mode, the technician can navigate to C:\Windows\System32\Drivers\CrowdStrike, and delete the file C00000291-*.sys. After that the computer can be rebooted as normal, and the crashing will stop.
Or the technician can open System Restore from Recovery Mode. And, assuming there is a recovery point, restore the computer back to a good known working state.
Now, this may all seem simple enough. So why were so many organizations having trouble running this fix? That all has to do with BitLocker. As an added security measure, many organizations use BitLocker on their computers to perform a full hard disk encryption. This is done so that if a computer ends up being lost or stolen, and ends up in the hands of an "unauthorized user" they will not be able to access any of the data stored on the computer without a password to log into the computer, or the computer's BitLocker recovery key.
This presented a problem when trying to restore all of these affected computers, because when either trying to launch Safe Mode or System Restore, the user would be prompted for the BitLocker recovery key.
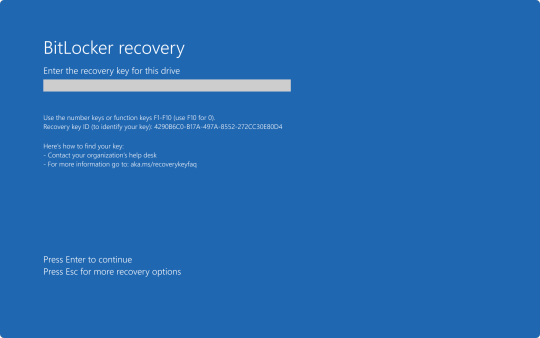
In my organization's case, we found we could save time by providing our end user the steps to perform one of the two fixes on their own to save time. But the problem we still continue to run into is the need for these BitLocker recovery keys. In my case, I've been fielding several calls where I've had end users walking from one computer to another while I provide them with the key as they walk through reverting back to a previous restore point.
Again, a pretty long story, but hopefully that can provide some context as to what's been happening over the past 48 hours.
30 notes
·
View notes
Text
All right, since I bombarded a poor mutual yesterday...
Privacy is not security and security is not privacy. These terms are not interchangeable, but they are intrinsically linked.
While we're at this, anonymity =/= security either. For example, Tor provides the former, but not necessarily the latter, hence using Https is always essential.
It is impossible to have privacy without security, but you can have security without privacy.
A case in point is administrators being able to view any data they want due to their full-access rights to a system. That being said, there are ethics and policies that usually prevent such behavior.
Some general tips:
Operating System: Switch to Linux. Ubuntu and Linux Mint are widely used for a reason. Fedora too. And don't worry! You can keep your current operating system, apps and data. If you're on a Mac computer, you can easily partition your hard drive or SSD by using Disk Utility. If you're on Windows, you can follow this guide.
You want to go a step further? Go with Whonix or Tails. They're Linux distributions as well, but they're both aiming for security, not beauty so the interface might not be ideal for everyone. Many political activists and journalists use them.
You want anonymity? Then you need to familiarize yourself with Tor. Also, Tor and HTTPS and Tor’s weaknesses. When you're using it, don't log in to sites like Google, Facebook, Twitter etc. and make sure to stay away from Java and Javascript, because those things make you traceable.
Alternatives for dealing with censorship? i2p and Freenet.
Is ^ too much? Welp. All right. Let's see. The first step is to degoogle.
Switch to a user-friendly browser like Firefox (or better yet LibreWolf), Brave or Vivaldi. There are plenty of hardened browsers, but they can be overwhelming for a beginner.
Get an ad blocker like Ublock Origin.
Search Engine? StartPage or Duckduckgo. SearXNG too. Like I said degoogle.
Get a PGP encrypted e-mail. Check Protonmail out.
There's also Tutamail that doesn't cover PGP, but uses hybrid encryption that avoids some of the cons of PGP.
Skiff mail is also a decent option.
Use an e-mail aliasing service such as SimpleLogin or AnonAddy.
Check OpenPGP out. Claws Mail is a good e-mail client for Windows and Linux, Thunderbird for Mac OS.
Gpg4win is free and easy to use for anyone that wants to encrypt/decrypt e-mails.
Instead of Whatsapp, Facebook messenger, Telegram etc. use Signal for your encrypted insant messaging, voice and video calls.
Get a metadata cleaner.
Get a firewall like Opensnitch, Portmaster or Netguard which can block Internet for trackers.
Alternatively, go with a private DNS that blocks these trackers. NextDNS is a good paid service. Rethink a good free option.
Replace as many of your applications as you can with FOSS (free and open source) ones. Alternativeto can help you.
Always have automatic updates on. They are annoying af, I know, but they are necessary.
Keep your distance from outdated software.
Always have two-factor authentication (2FA) enabled.
Do not use your administrator account for casual stuff. If you're on Linux, you probably know you can be sudo, but not root.
On Linux distributions use AppArmor, but stay away from random antivirus scanners. Other distributions default to SELinux, which is less suited to a beginner.
Never repeat your passwords. If you can't remember them all, use a password manager like KeePass.
Encrypt your drive.
Honestly, VPNs have their uses and ProtonVPN, Mullvad and Windscribe are decent, but eh. If you don't trust your ISP, why would you trust the VPN provider that claims they don't log you when you can't verify such a thing?
57 notes
·
View notes